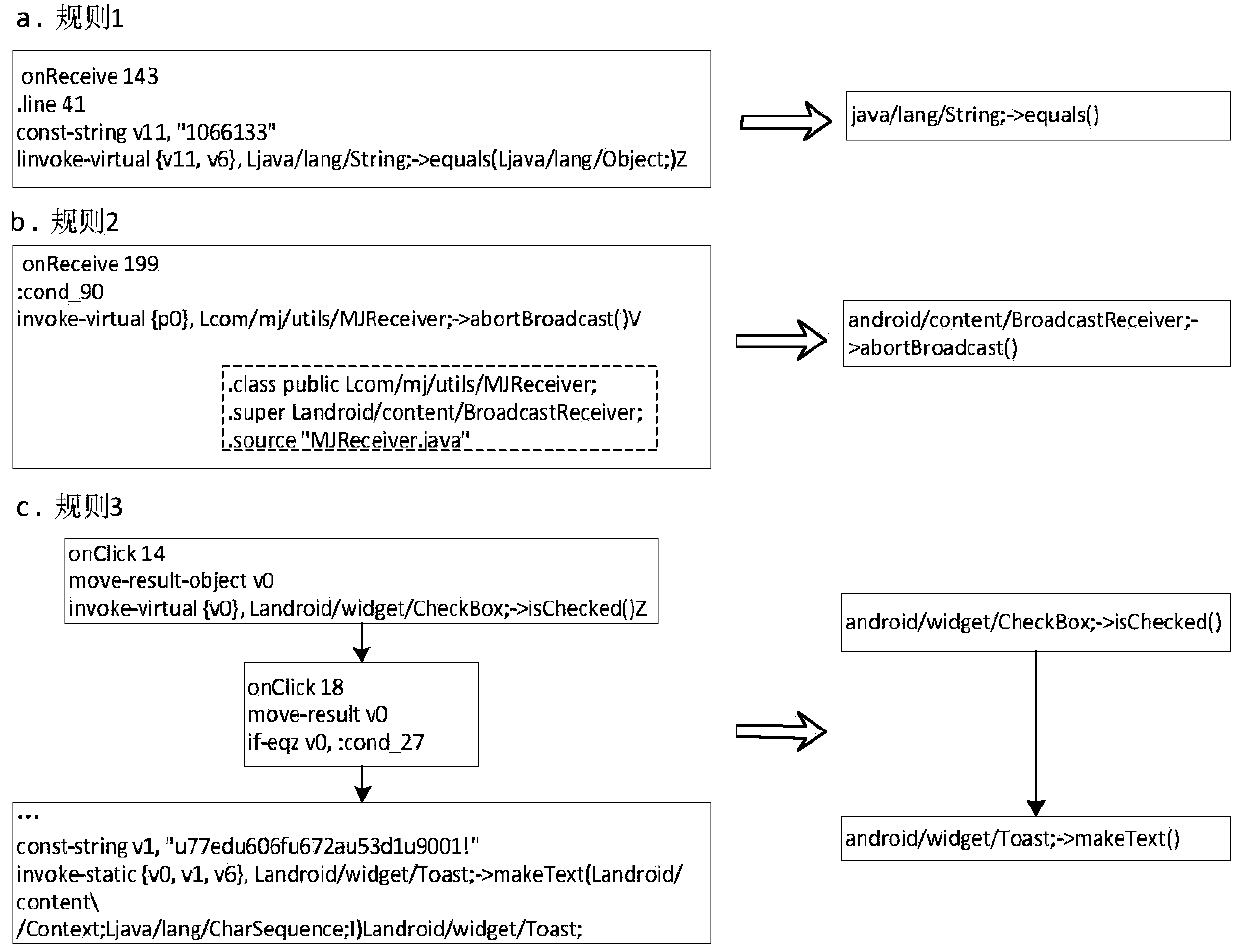
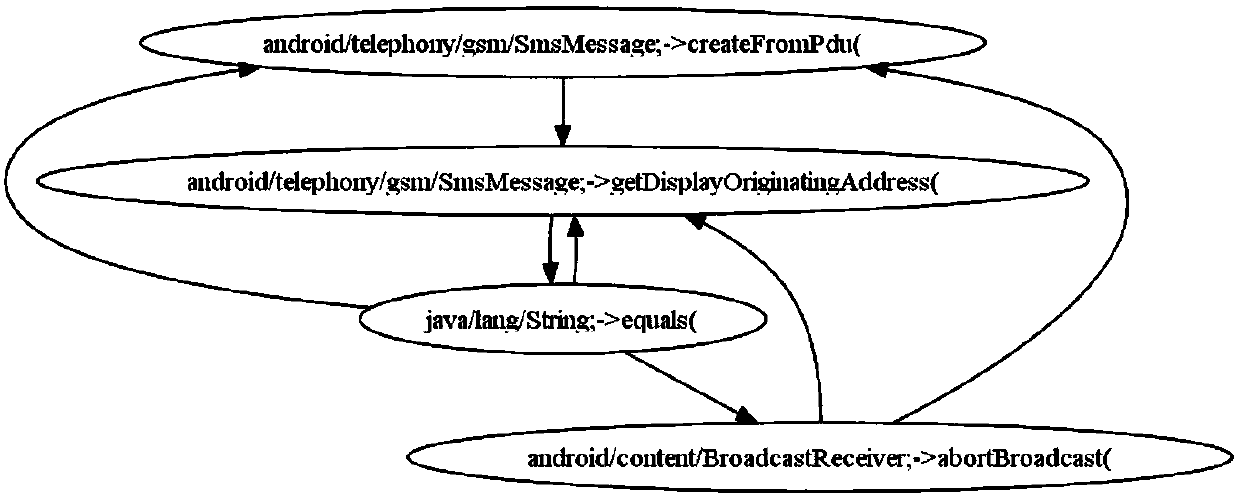
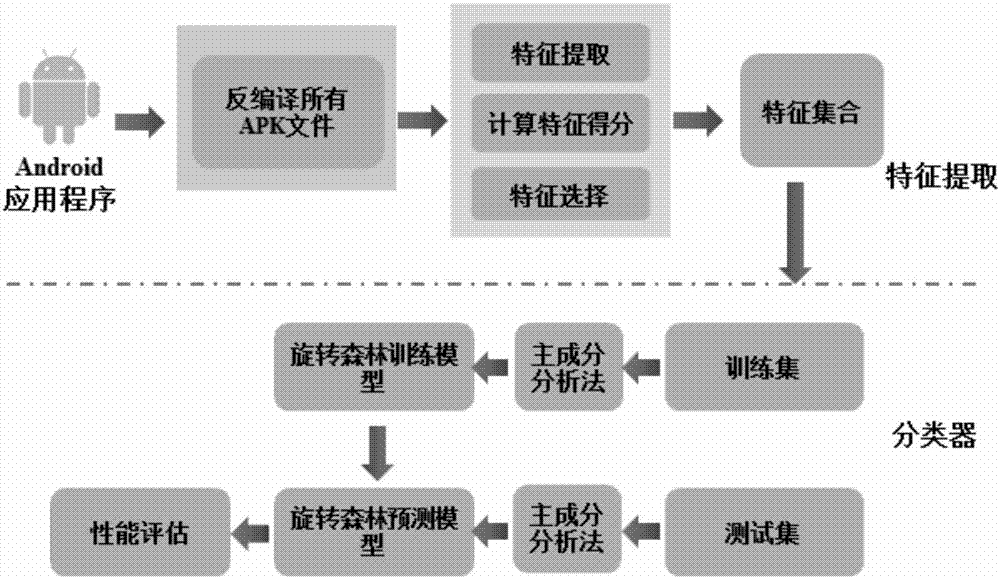
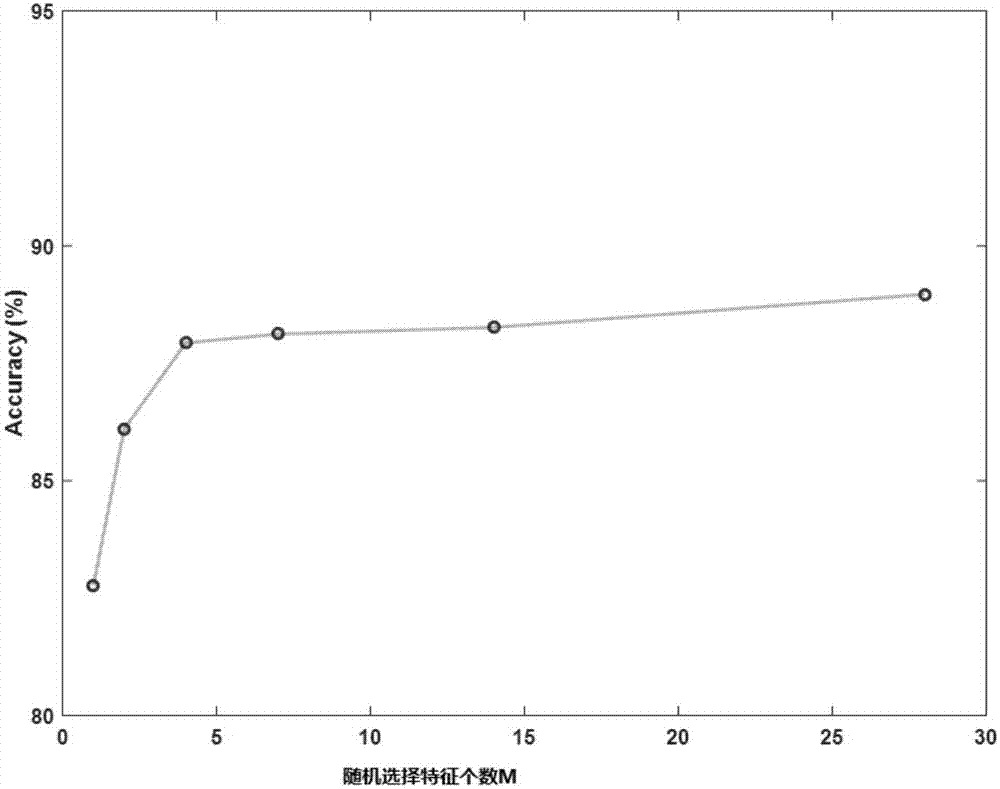
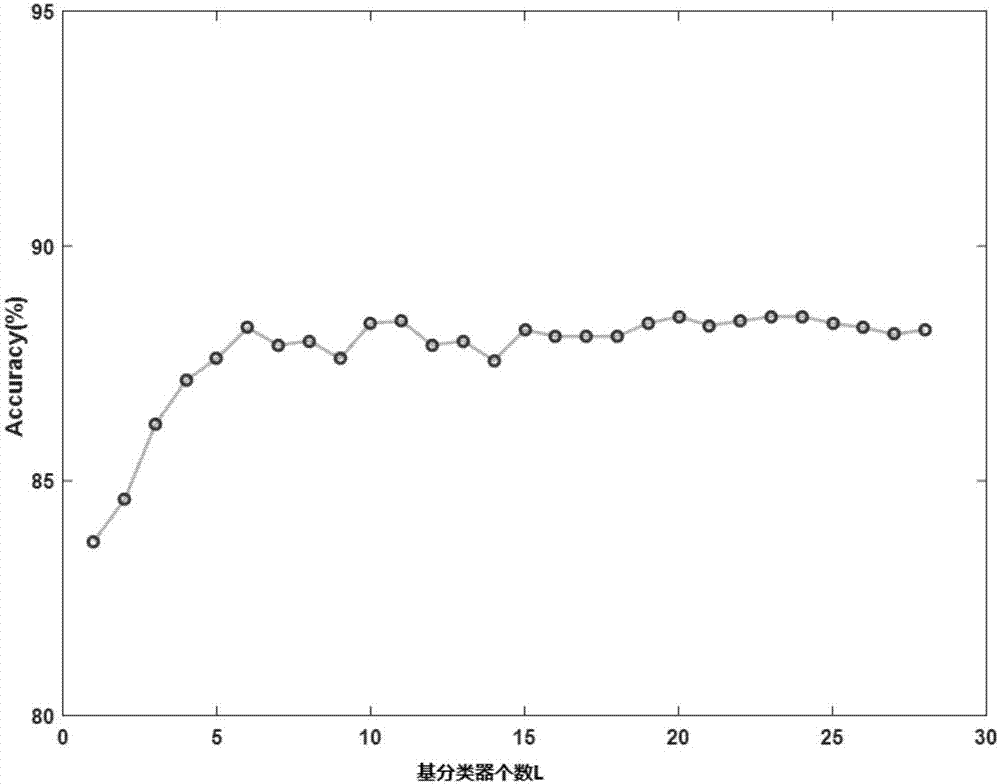
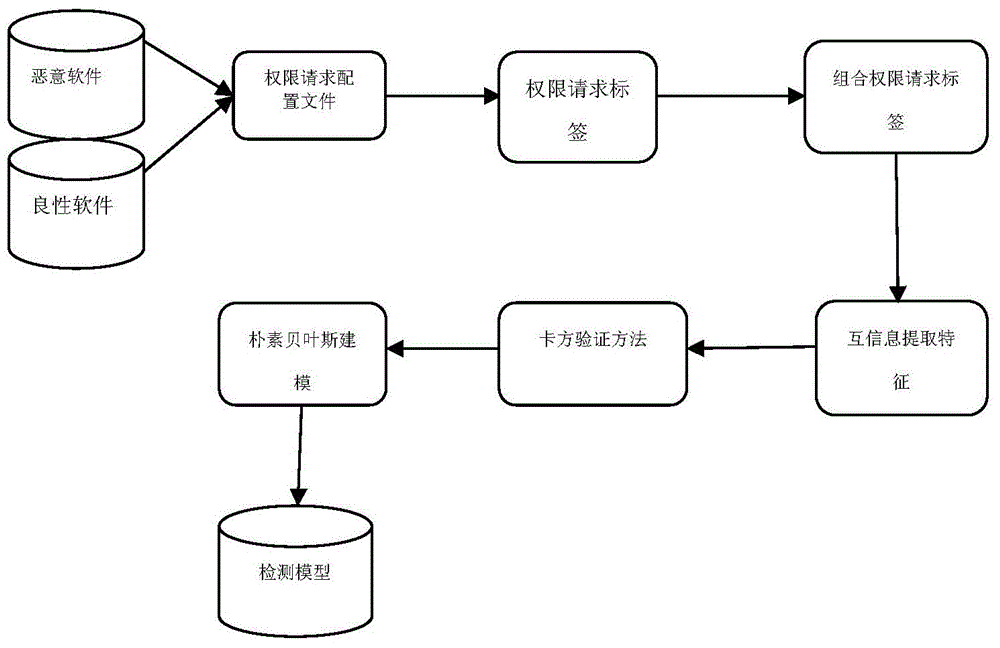
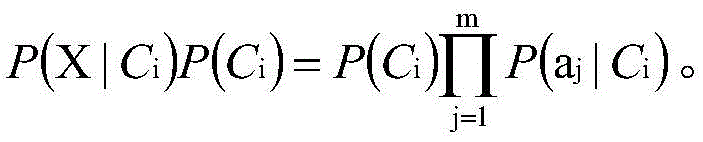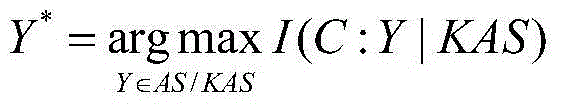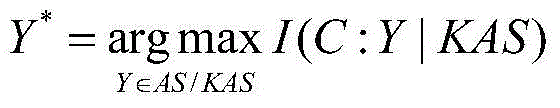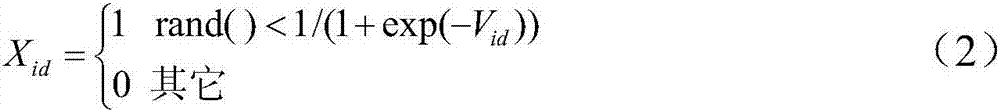Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
83 results about "Android malware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Android malware usually operates through Ads (as mentioned), but can sometimes employ alternative means. As an example a certain Malware operated through the Ad Network Air Push. Infected devices had pop-ups added to their Apps, which asked the user to pay money for program updates that should have been free otherwise.
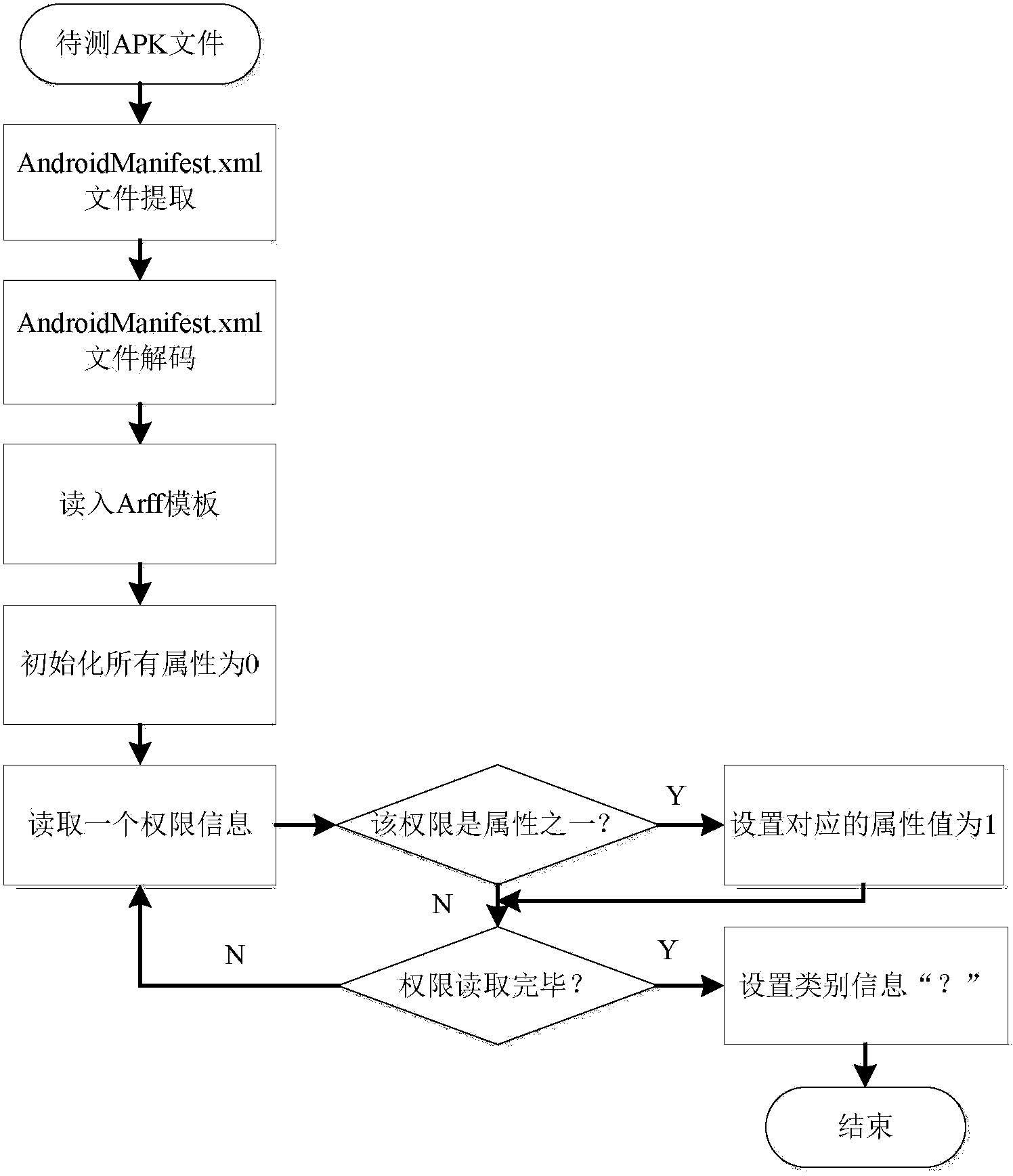
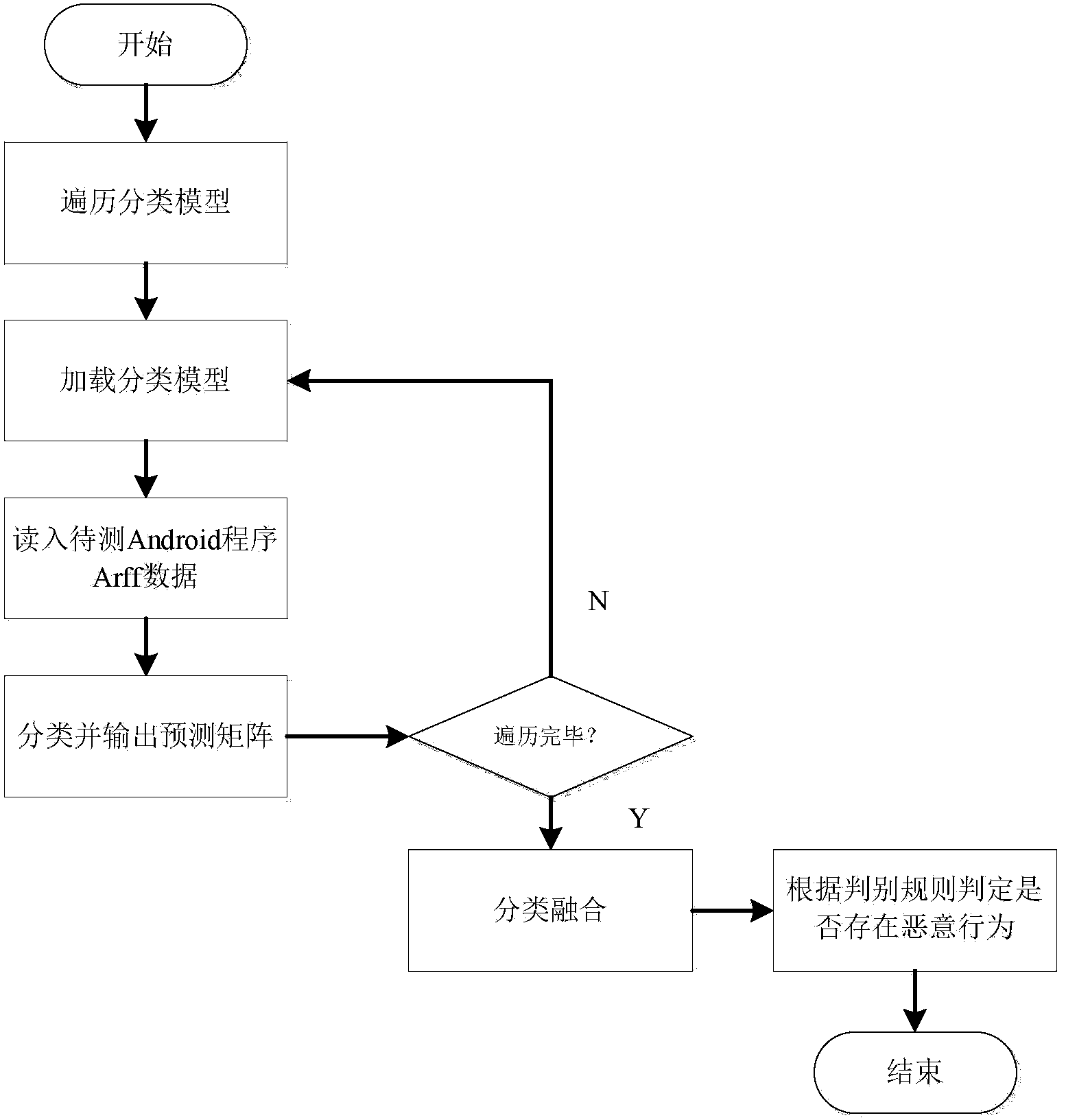
Automatic detection method for Android malicious software
InactiveCN103186740AHigh static detection efficiencyStrong coveragePlatform integrity maintainanceApplication programming interfaceSystem safety
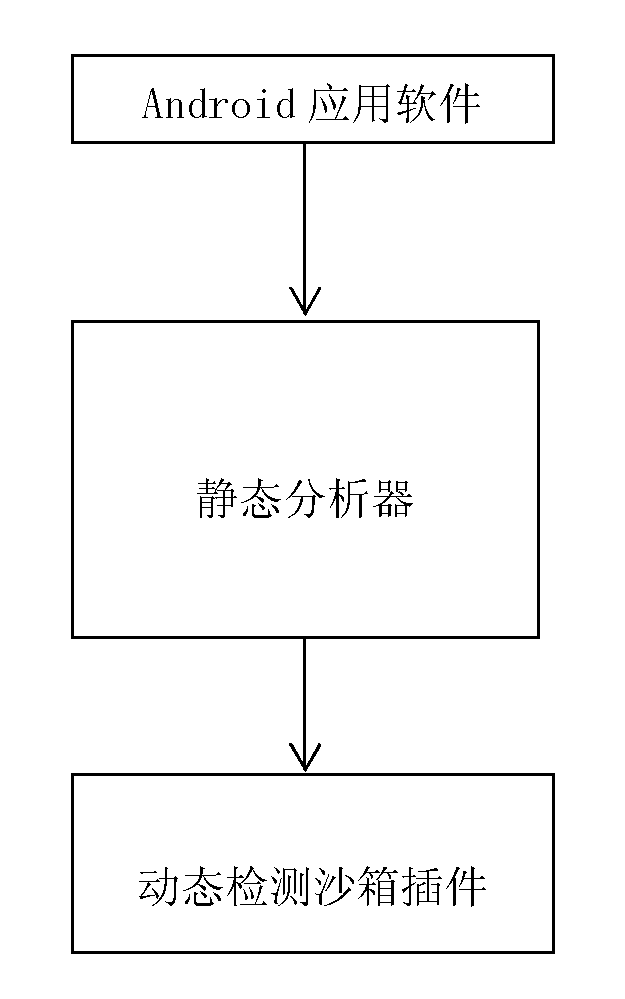
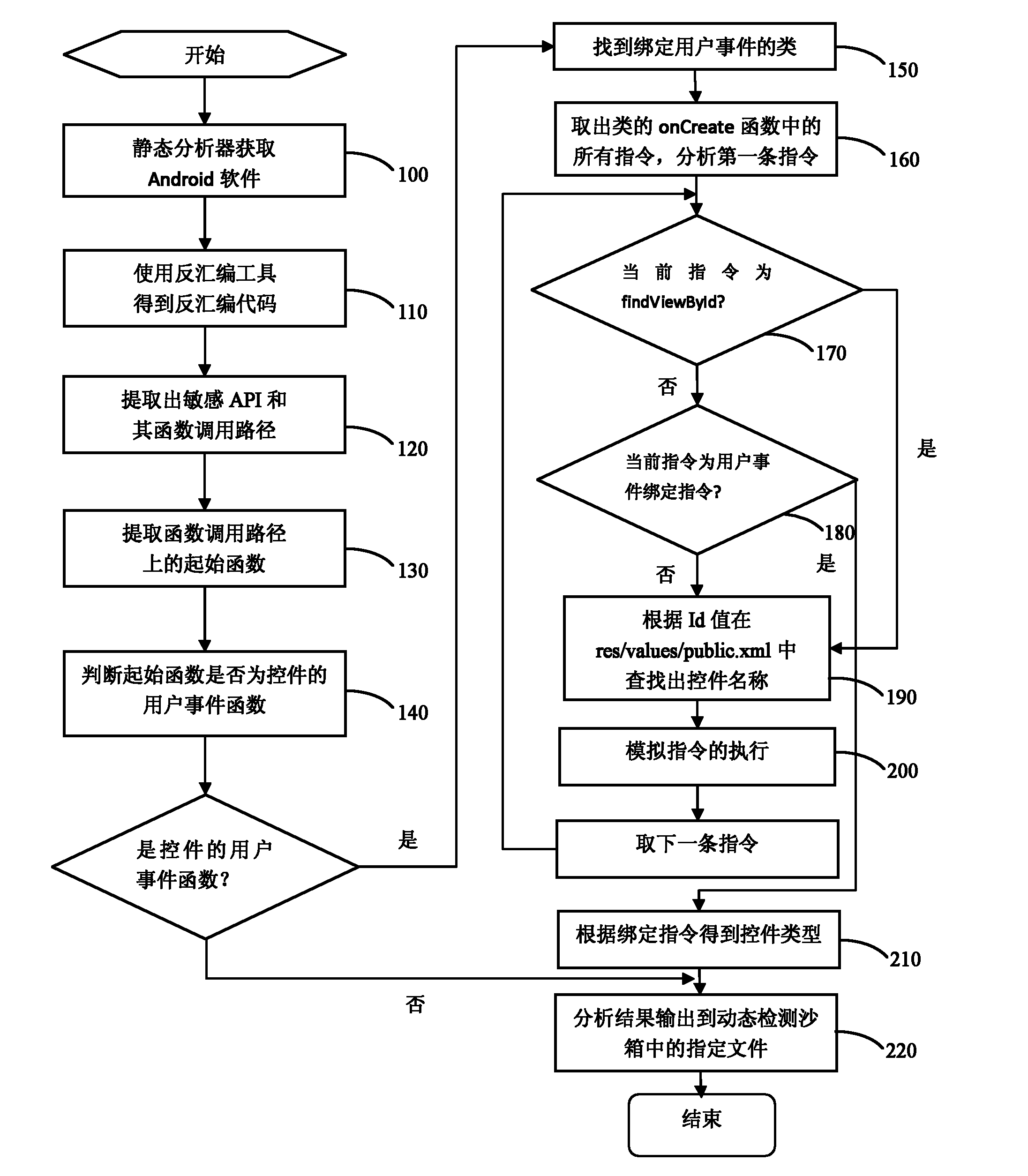
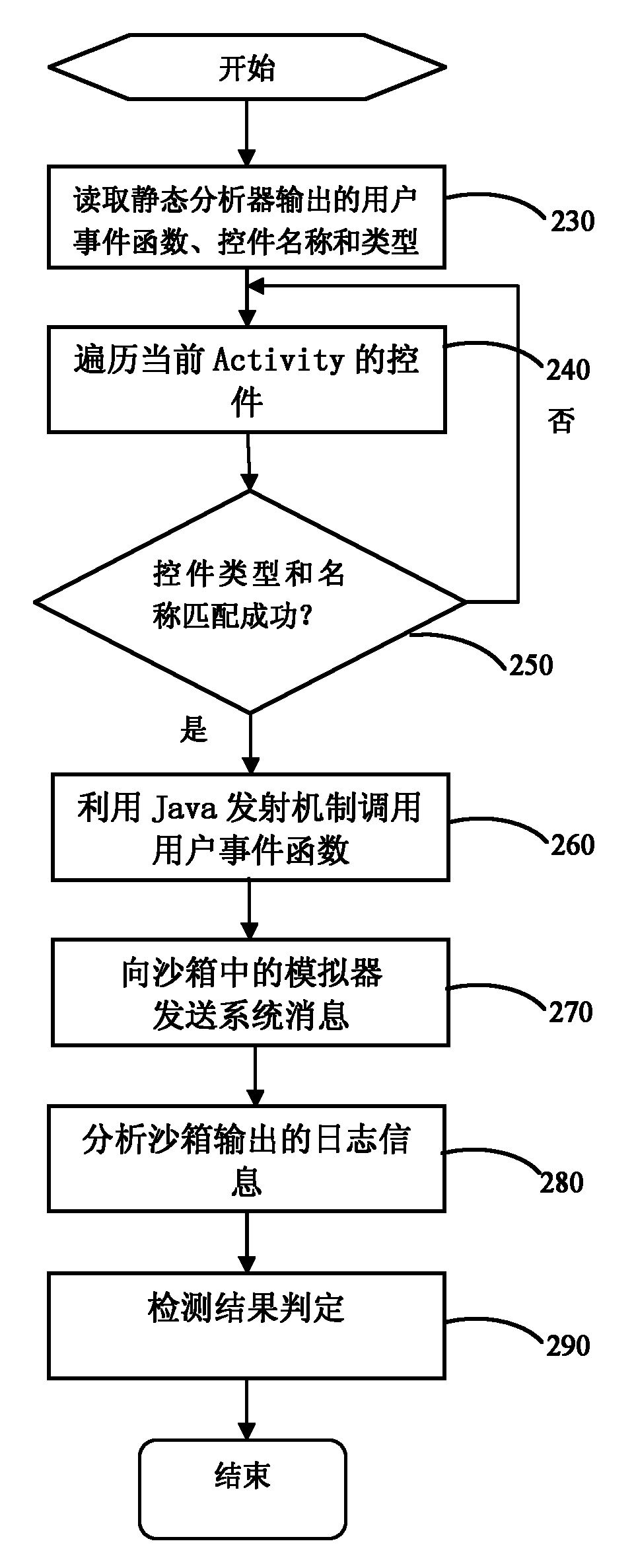
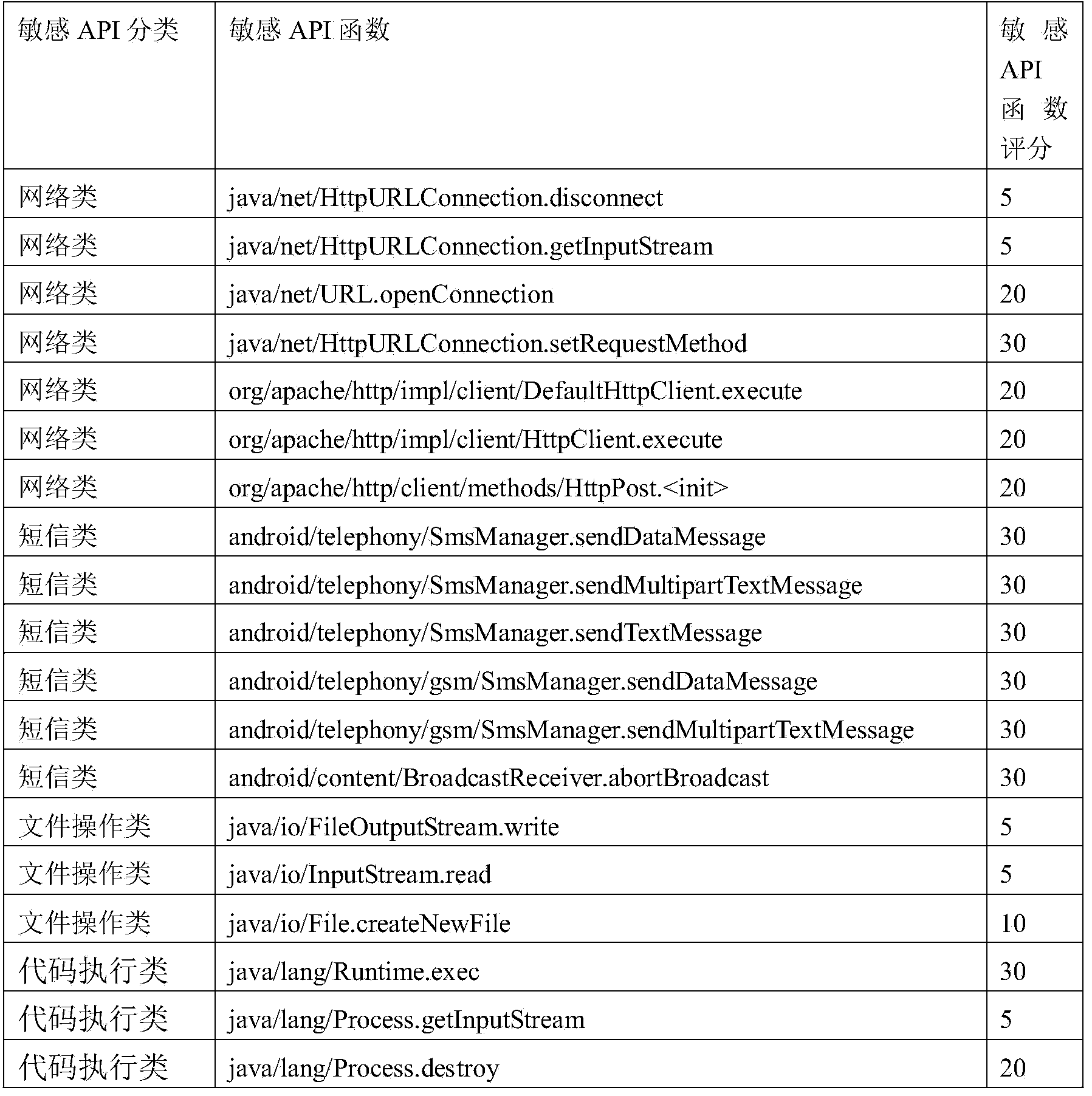
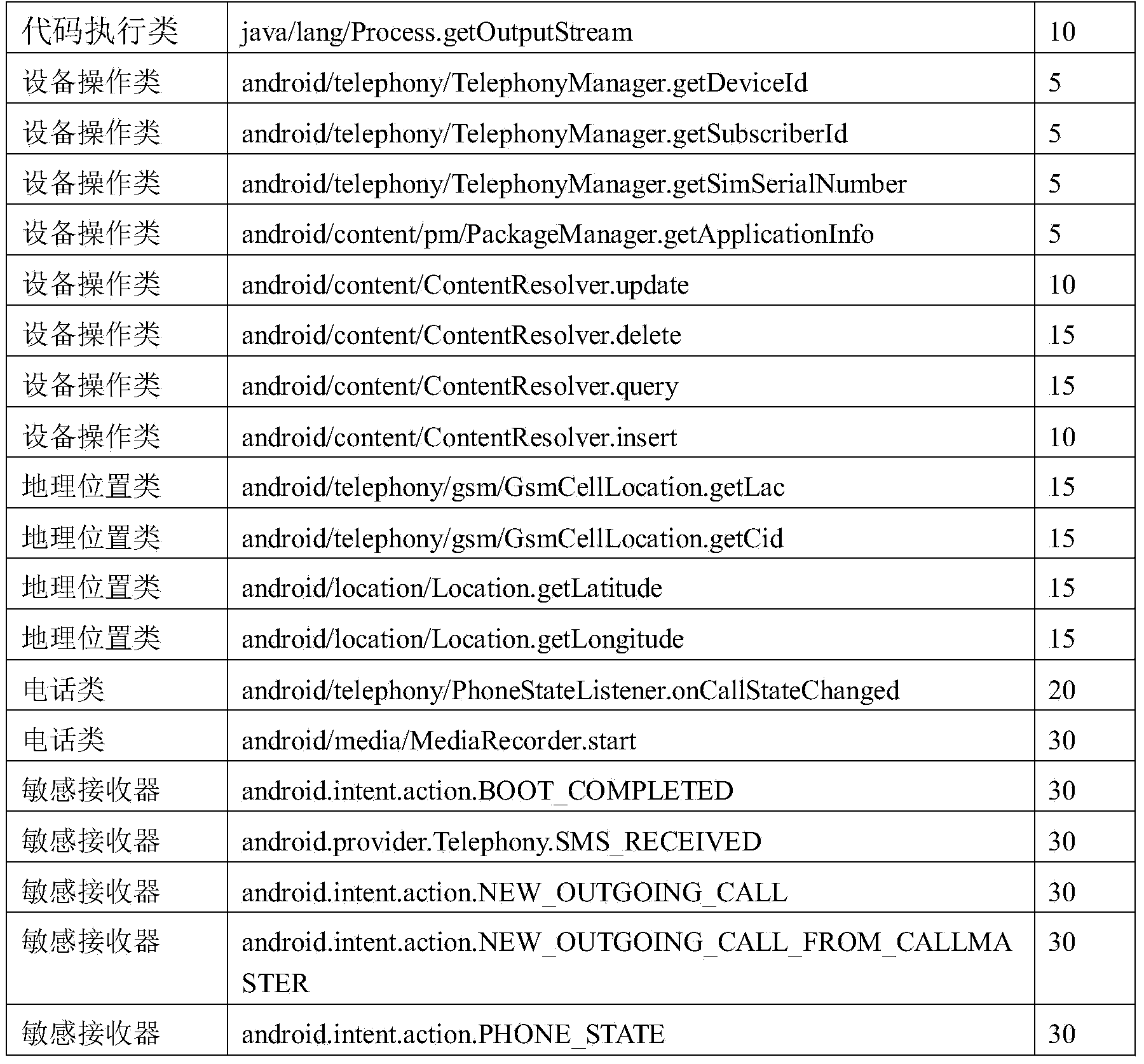
The invention discloses an automatic detection method for Android malicious software, and belongs to the technical field of system security. The method comprises the following steps: 1) setting a plurality of application programming interface (API) functions as sensitive APIs, disassembling software to be detected and analyzing all sensitive APIs and function call paths from a disassembled code; 2) judging the trigger mode of each sensitive API, analyzing control information triggering the sensitive API, inputting the control information into a dynamic detection sandbox and executing the control to automatically trigger a malicious act if the trigger mode is a user trigger mode, and sending system messages to the dynamic detection sandbox to trigger the malicious act if the trigger mode is a system message trigger mode; and (3) monitoring and recording the conditions of calling the sensitive API by the software and operating data through the dynamic detection sandbox, and judging the software as the malicious software if the call of the sensitive API and the operating data of the call indeed exist. By the method, manual intervention is not required, and the method provides powerful support for detecting large-scale malicious software.
Owner:PEKING UNIV
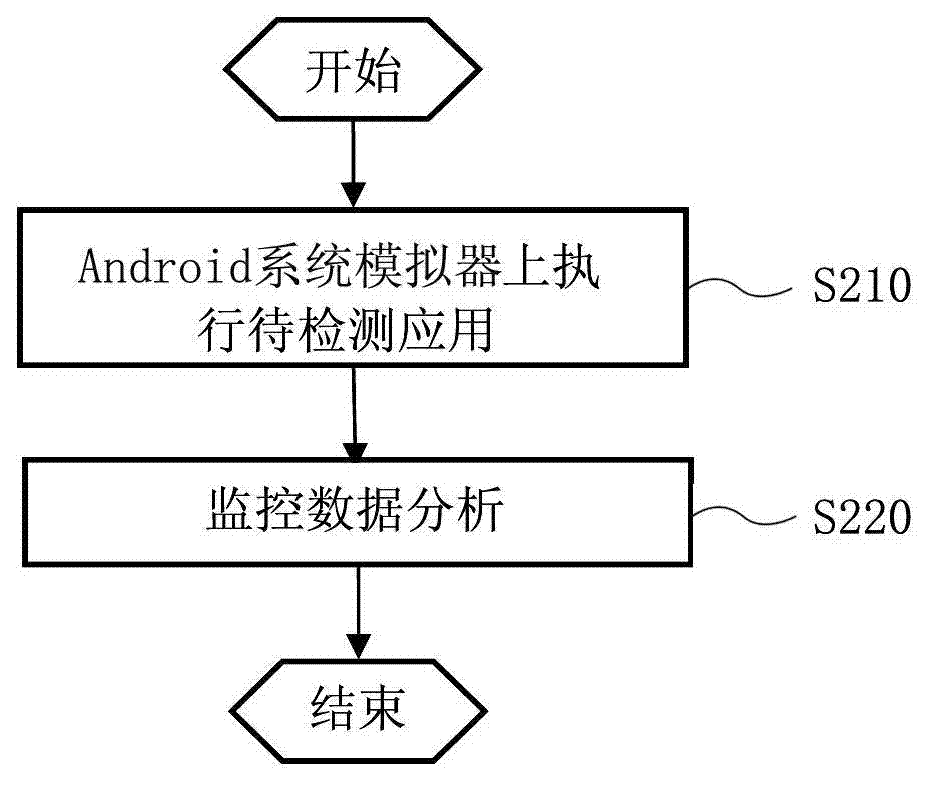
Device and method for detecting Android malware
ActiveCN103207969AMinimize Safety HazardsPlatform integrity maintainanceComputer hardwareInstrumentation
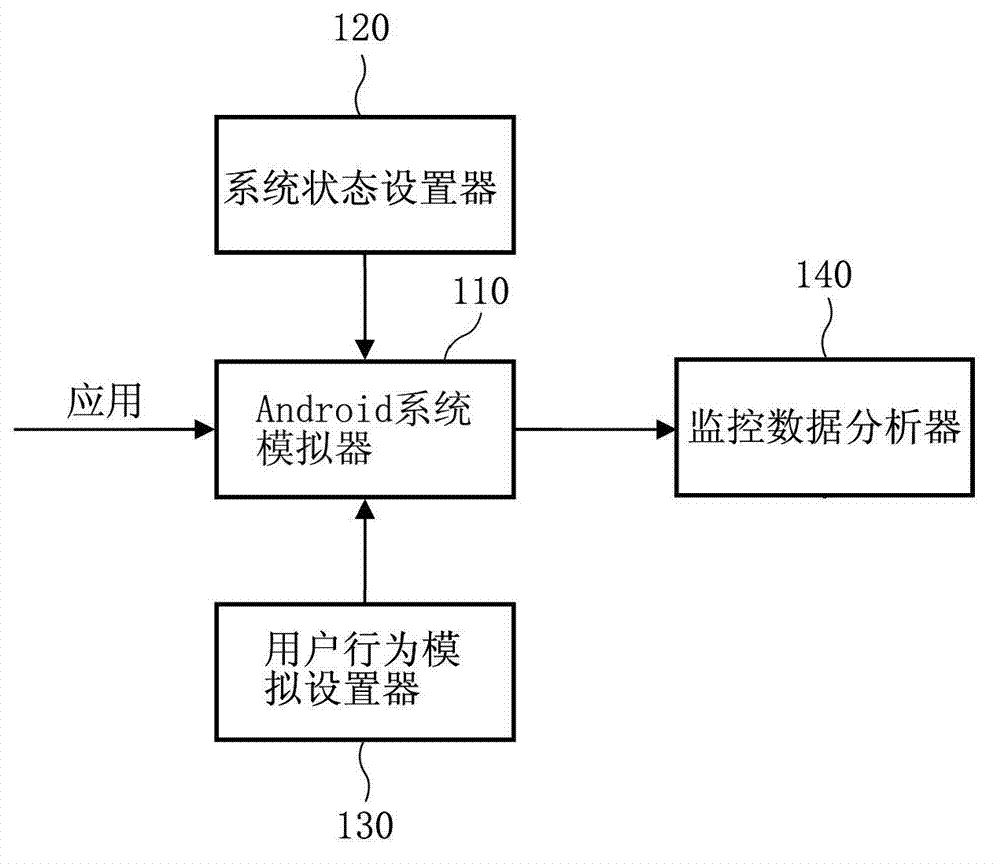
The invention provides a device and a method for detecting Android malware. The device for detecting the Android malware comprises an Android system simulator and a monitoring data analyzer, software to be detected is executed on the Android system simulator, instrumentation monitoring codes of at least one predefined function or command are preset in the Android system simulator and used for intercepting invoked invoking status data of the predefined functions or commands, and the monitoring data analyzer is used for analyzing the intercepted invoked invoking status data of the predefined functions or commands so as to determine whether the software to be detected includes malicious codes or not.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
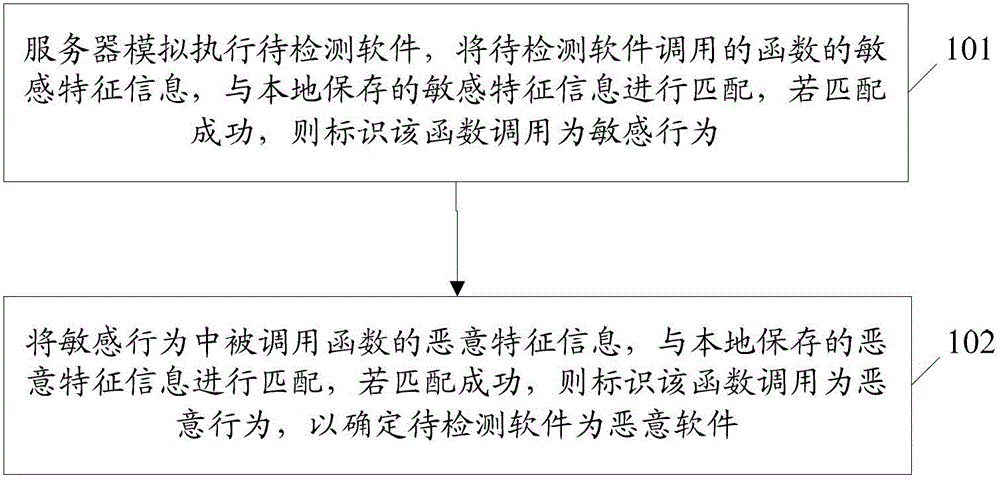
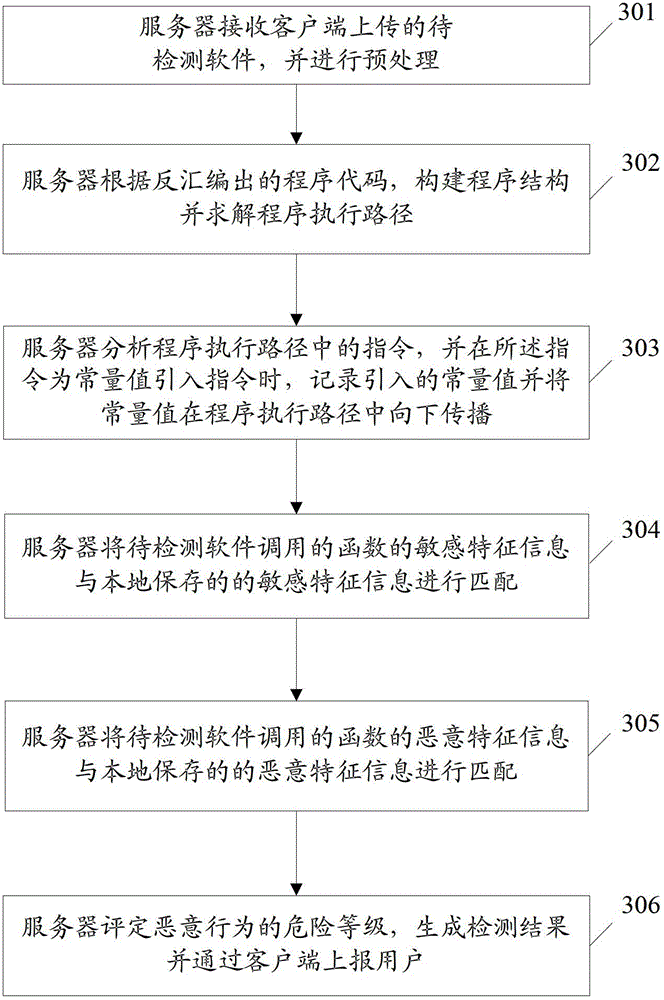
Method, system and device for detecting Android malicious software
ActiveCN102945347AAccurate and timely malicious behavior detectionThere is no problem of lagging period in test resultsPlatform integrity maintainanceSecurity arrangementSoftware engineeringSoftware
The invention discloses a method for detecting Android malicious software. The method comprises the following steps: a server simulates and executes the to-be-detected software, and matches sensitive feature information and malicious feature information of the function invoked by the to-be-detected software with the sensitive feature information and the malicious feature information stored locally; and if the matching is successful, the function invoking is determined to be malicious, and the to-be-detected software is malicious. The invention further discloses a system and a device for detecting Android malicious software. By virtue of the technical scheme, the problem that the software cannot be detected to be the malicious software for a long time caused by the situations that the existing technology for detecting the Android malicious software has a lag phase, and the triggering conditions for malicious behaviors of some malicious software are complicated can be avoided.
Owner:ZTE CORP +1
Function-call-based Android malicious code detection method
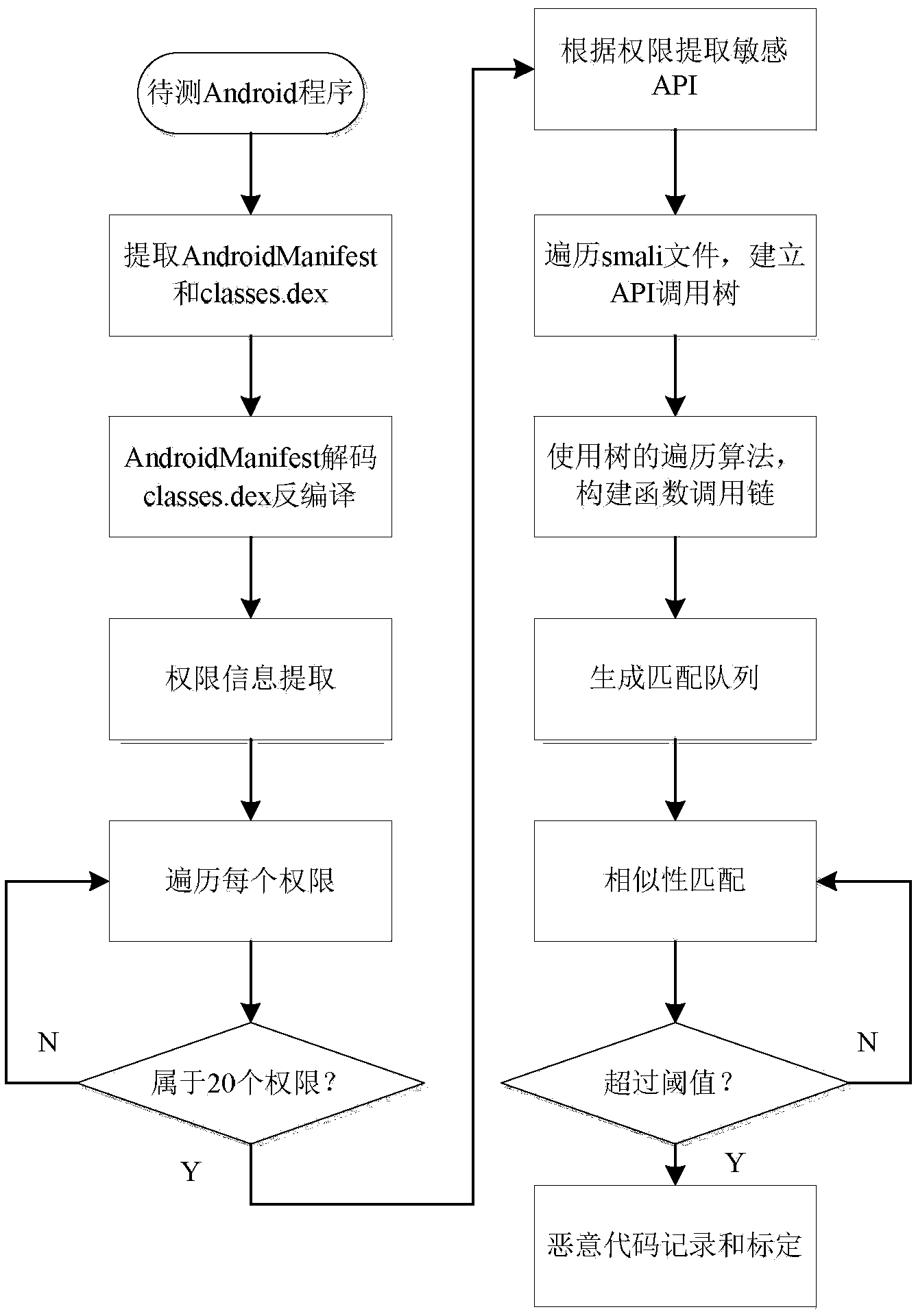
The invention provides a function-call-based Android malicious code detection method, and aims at solving the problems that the Android program characteristic can be established in a fine-grained manner by adopting an existing Android malicious code detection technology. The method comprises the steps: firstly, conducting authority-based statistic analysis on existing Android malicious codes, extracting an authority with a relatively high utilization rate as a sensitive authority, and then establishing a function chain capable of calling APIs (Application Program Interface) by using the APIs of the authority as entry points, so as to conduct function-call-based Android malicious code detection. Through the function-call-based Android malicious code detection method, the behavior characteristic of the Android program can be established in a fine-grained manner, and therefore, the Android malicious codes can be relatively well detected.
Owner:XI AN JIAOTONG UNIV
Detection method for repackage application in android market
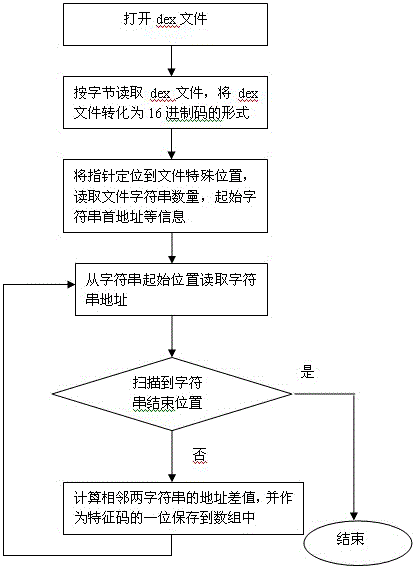
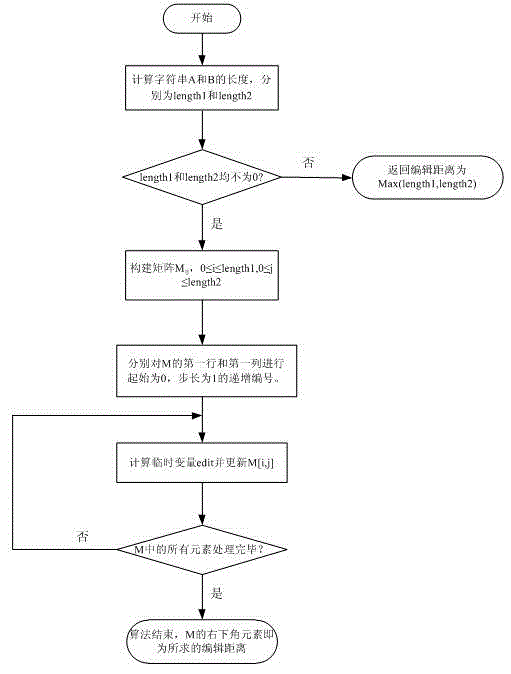
The invention discloses a detection method for repackage application in an android market. The method comprises the steps: calculating the length of character string used according to dex files of android applications so that the lengths are taken as feature codes for distinguishing different applications, calculating the edition distance between the features codes of the different applications to obtain the similarity of different android applications, comparing the similarity with a given threshold, thus determining whether the repackage application exists. The detection method can be used as an effective assistant means for detecting android malware.
Owner:SOUTHEAST UNIV
Android malicious software sorting method based on dynamic behavior dependency graph
ActiveCN105653956AIncrease flexibilityStrong scalabilityPlatform integrity maintainanceExtensibilityLayer interface
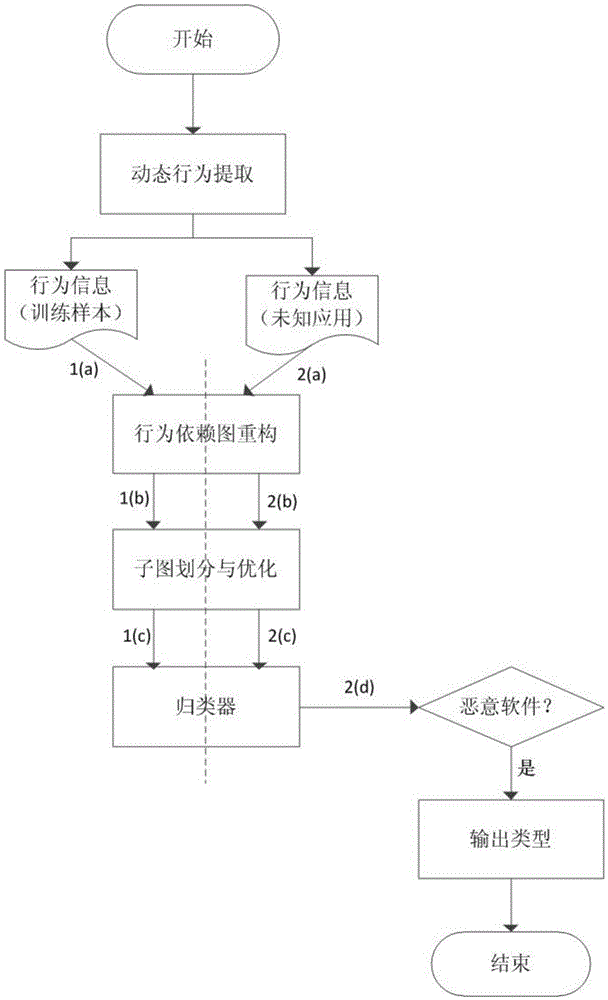
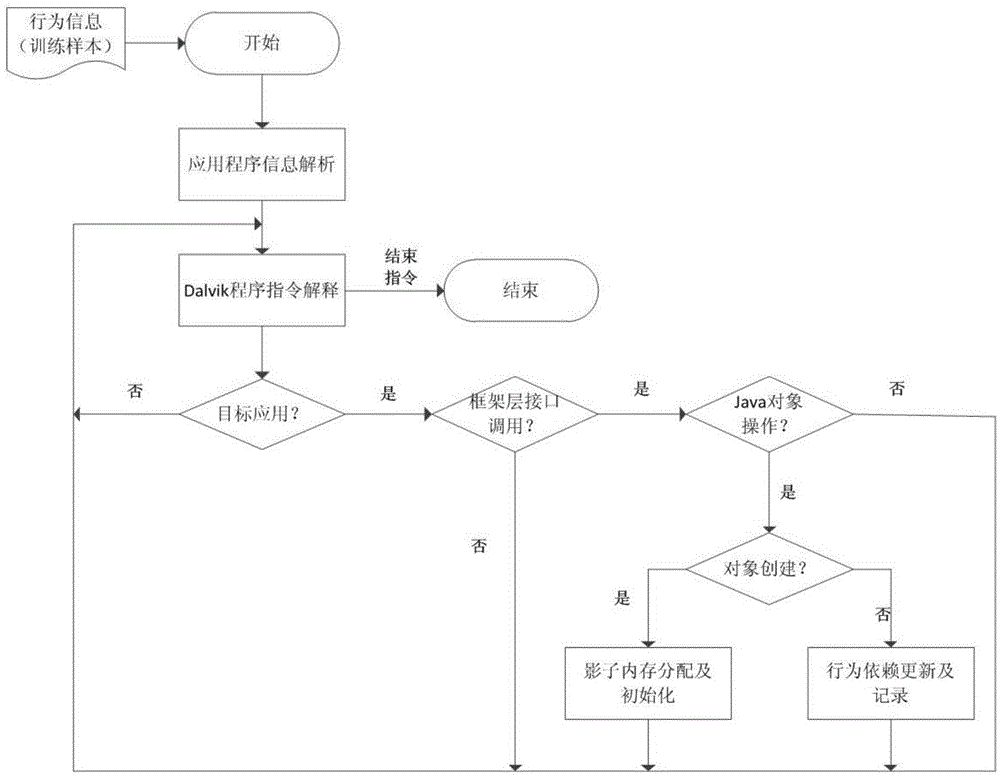
The invention relates to an Android malicious software sorting method based on a dynamic behavior dependency graph. The sorting method includes the steps that an APP is run through a user-defined Dalvik virtual machine, and dynamic behavior information such as framework layer interface calling behaviors and dependency among the behaviors is extracted; the corresponding dynamic behavior dependency graph is constructed according to the dynamic behavior information; the dynamic behavior dependency graph is optimized and divided into subgraphs; similar subgraph structures are extracted from a set composed of Android malicious software of different types and are used as essential characteristics; according to the essential characteristics, model training is conducted on a training set composed of known malicious software and normal software to obtain a classifier; unknown APPs are classified and judged through the classifier; the method is verified and assessed. Similarity of the behavior subgraphs is measured with the graph editing distance, basic characteristics are found on the basis, and the sorting method has good flexibility and expandability.
Owner:INST OF INFORMATION ENG CAS
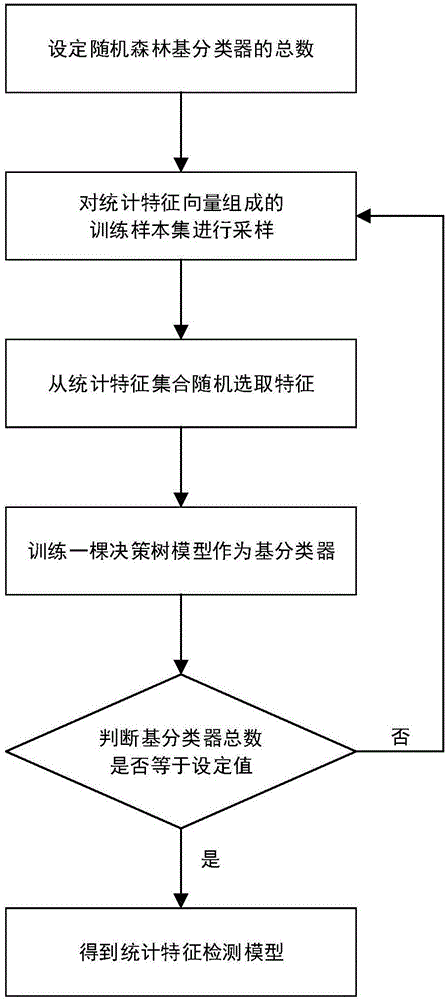
Android malware static detection method based on random forest
InactiveCN106845240AComprehensive and efficient detection processingEnsure objectivityCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorAlgorithm
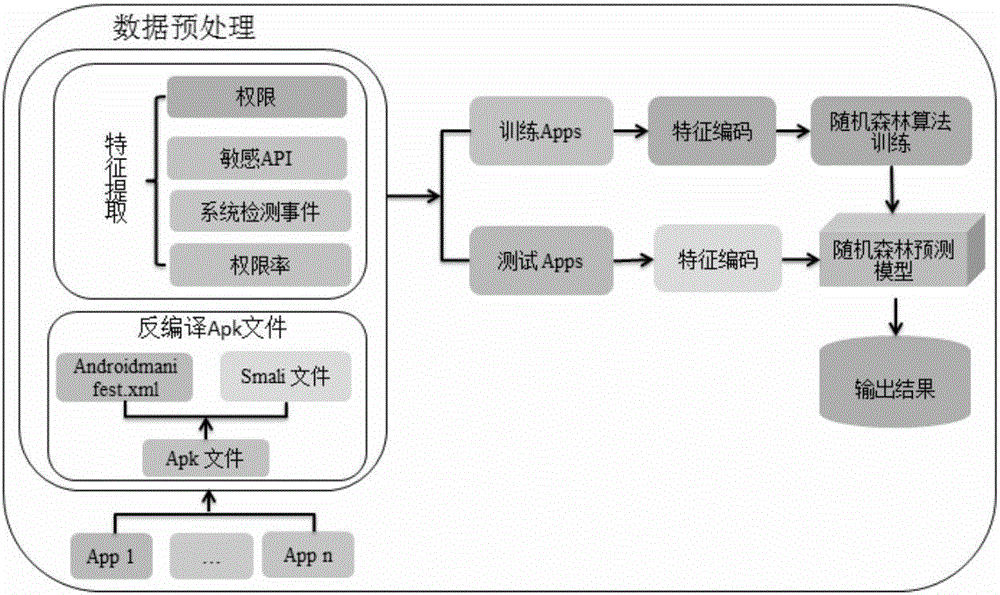
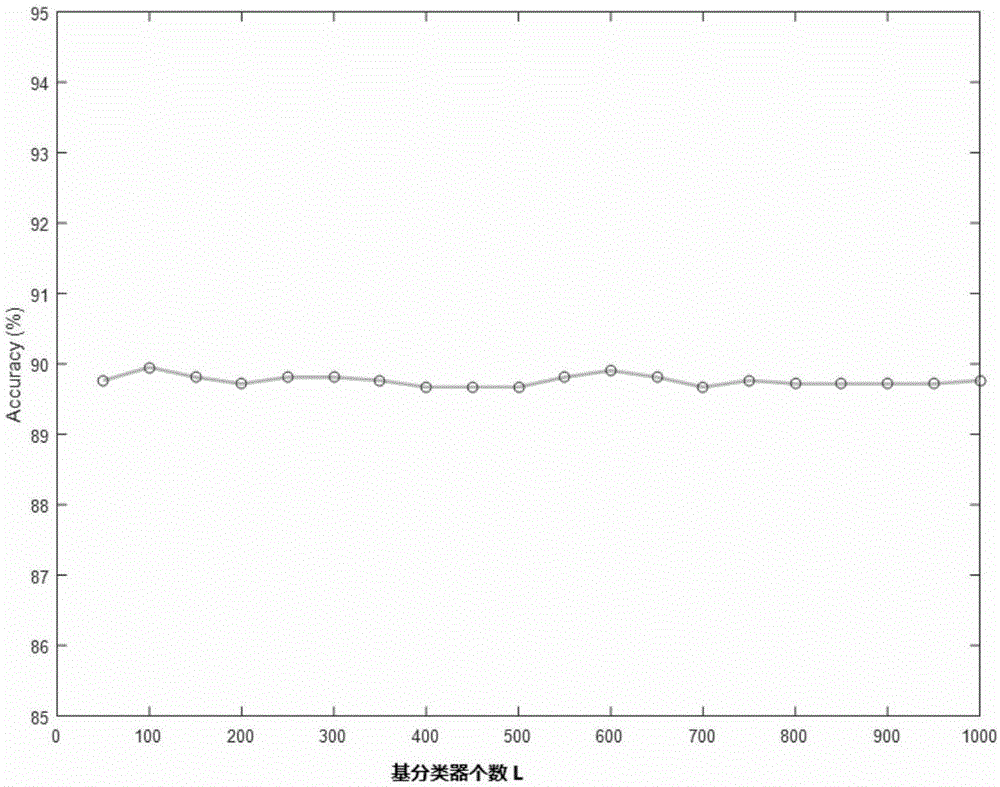
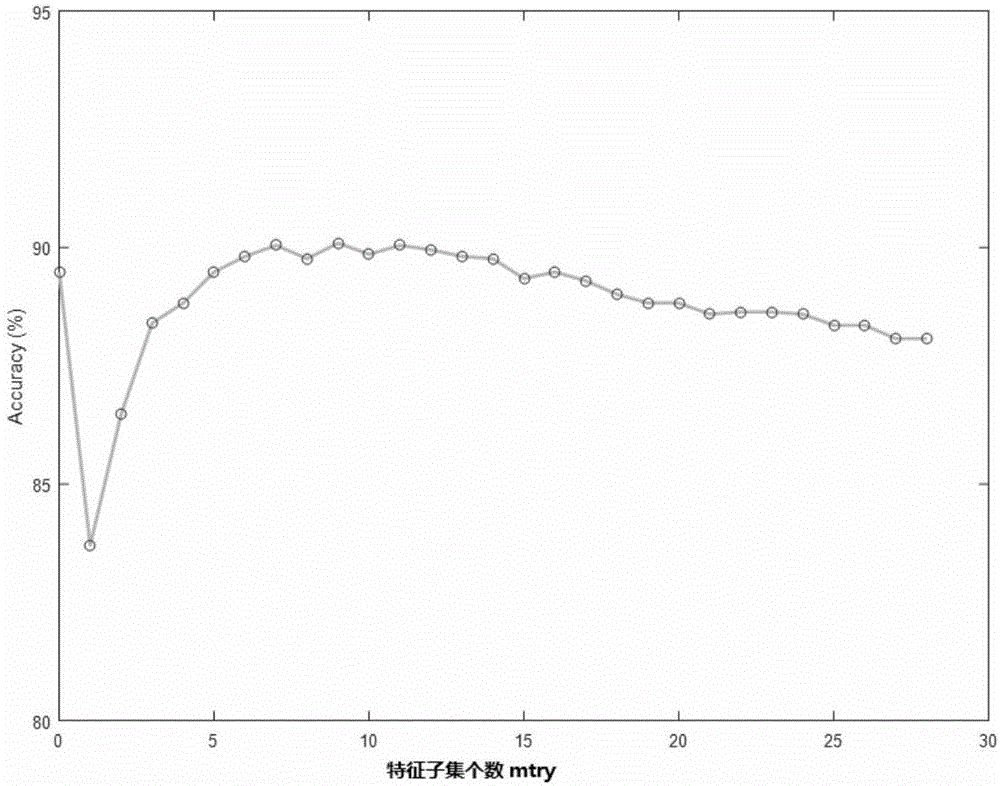
The invention relates to an Android malware static detection method based on random forest and belongs to the technical field of network security. According to the method, characteristic vectors consisting of permissions, monitored system events, sensitive APIs and permission rates are constructed, a training model and a prediction model of Android malware based on a random forest algorithm in support machine learning are established, then, the validity of the models is verified through sample calculation with a tenfold cross validation method. The prediction accuracy of the model can reach 89.91%. The method has the significant advantages as follows: 1) main characteristics involved in each Android application are acquired with a simple and quick static analysis method, besides, no dynamic tracking is involved, and the characteristics of low cost and high efficiency are realized; 2) the used four groups of characteristic vectors comprising the permissions, monitored system events, sensitive APIs and permission rates can be captured easily by each Android application, and the method is easy to popularize on an Android platform.
Owner:XIJING UNIV
Android malicious software detection method based on method call graph
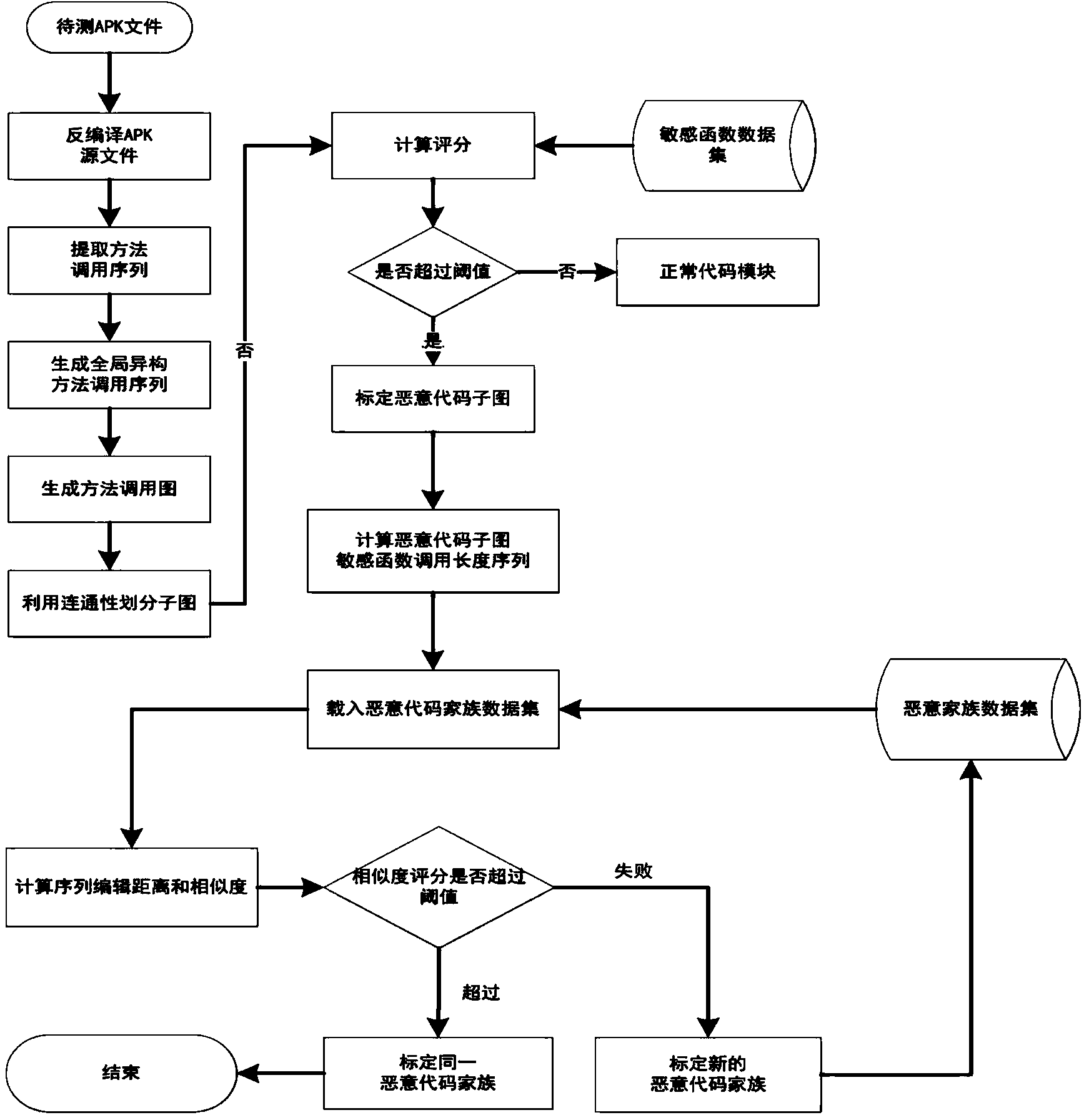
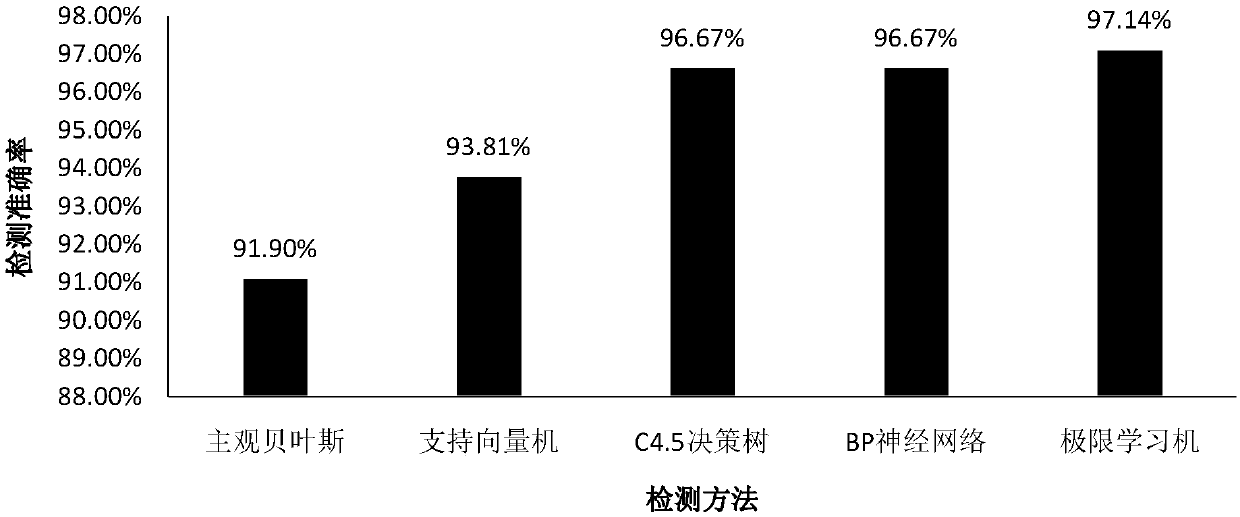
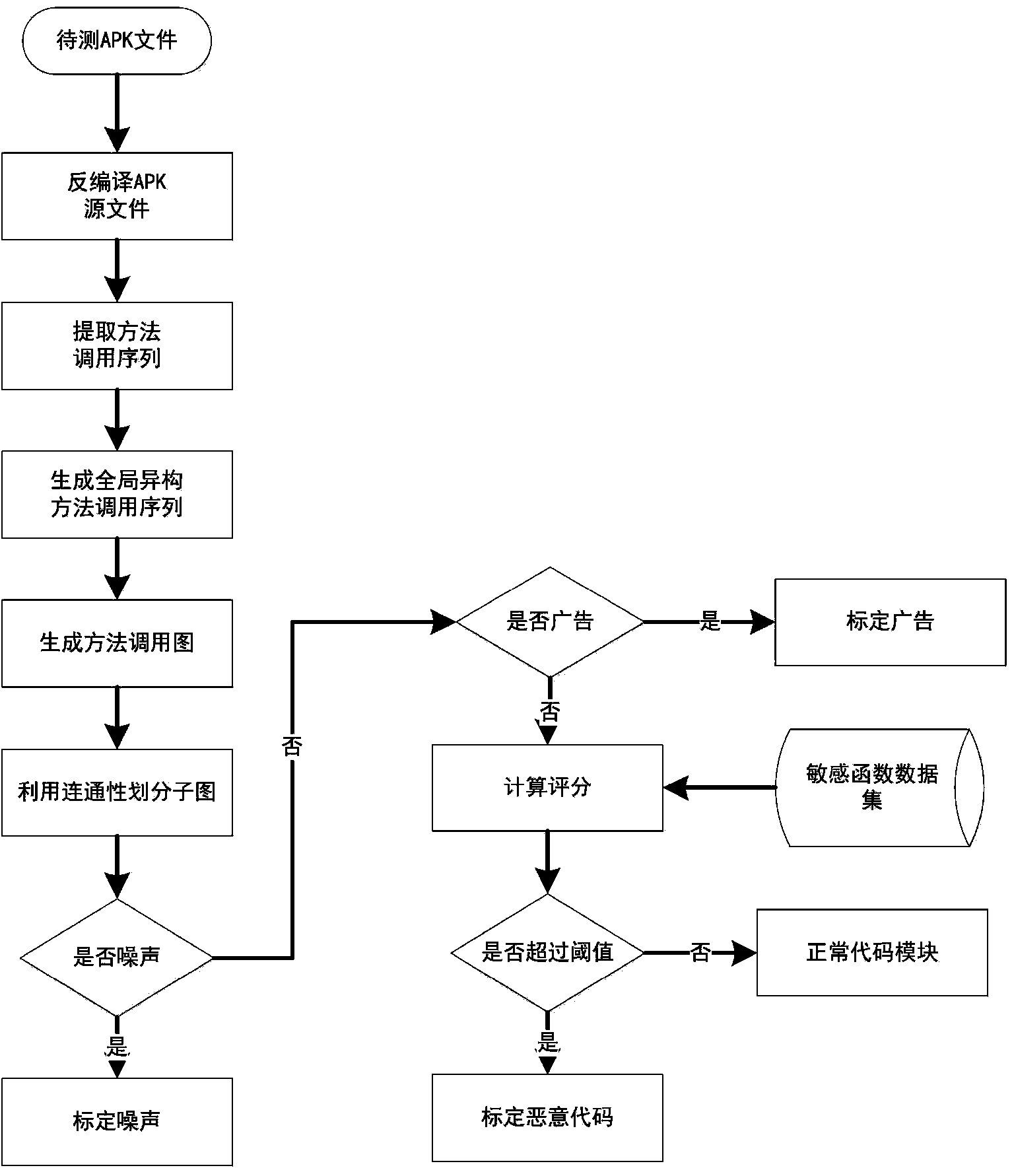
ActiveCN103473507AEasy to identifyGood killing effectPlatform integrity maintainanceCode moduleThird party
The invention provides an Android malicious software detection method based on a method call graph. A heterogeneous method call graph for constructing Android application Apk software is adopted, a sensitivity function is calibrated, and malicious codes are subjected to location and family classification by using the connectivity of the graph. The specific flow comprises the following steps: scanning the connectivity of the graph on the heterogeneous method call graph to obtain each sub-graph; grading the sensitivity function of each sub-graph, wherein the sub-graphs surpassing a threshold value are determined as malicious code modules, and similar malicious code sub-graph structures in different Android software are determined as malicious code families. According to the Android malicious software detection method, unknown malicious software can be found heuristically, families of the unknown malicious software are calibrated, and safe scanning and protection are provided for broad Android third-party markets and personal users.
Owner:XI AN JIAOTONG UNIV
Android malware real-time detection method based on network flow analysis
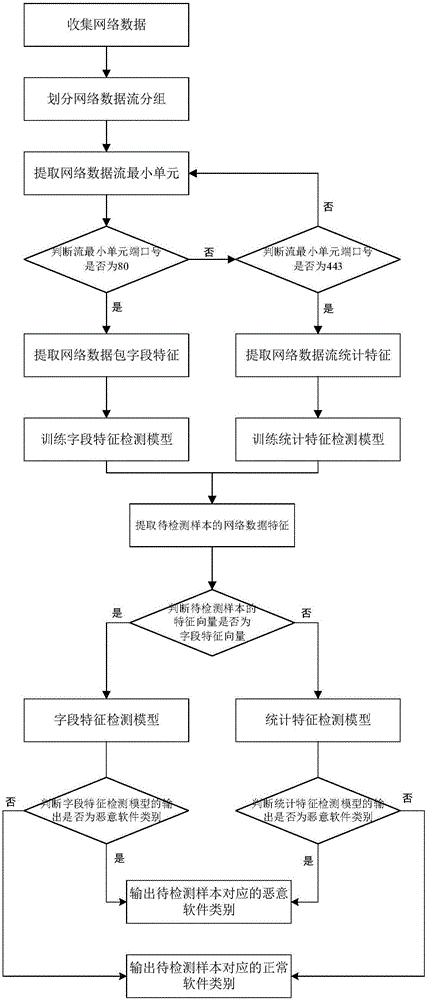
InactiveCN106657141AOvercome the shortcomings that real-time performance cannot be guaranteedImprove detection accuracyTransmissionFeature vectorData stream
The invention discloses an Android malware real-time detection method based on network flow analysis. The method comprises the following steps: (1) collecting network data; (2) dividing network data flow groups; (3) extracting a network data flow minimum unit; (4) judging whether a flow minimum unit port number is 80; (5) extracting network data packet field features; (6) judging whether the flow minimum unit port number is 443; (7) extracting network data flow statistical features; (8) training a statistical feature detection module; (9) training a field feature detection module; (10) extracting the network data feature of a to-be-detected sample; (11) judging whether a feature vector of the to-be-detected sample is a field feature vector; and (12) inputting the feature vector of the to-be-detected sample into the field feature detection model or a statistical feature detection model to obtain a detection result. By use of the real-time detection method disclosed by the invention, the malware can be detected in real time, and an encryption protocol can be used for detecting the software for performing the network data transmission.
Owner:XIDIAN UNIV
Permission-based Android malicious software hybrid detection method
InactiveCN104866763AQuick checkPerfect and accurate behavior detection and analysis methodsPlatform integrity maintainanceCosine similarityApplication software
The invention discloses a permission-based Android malicious software hybrid detection method. The method comprises the following steps: steps one, decompiling an Android application program and obtaining application program application permissions; step two, combining a system setting permission to carry out permission detection on the application program application permissions; dividing all applications to be detected into a kind application set, a malicious application set and a suspicious application set according to the difference of the conditions of the application program application permissions; step three, dynamically acquiring and detecting the behaviors of the application programs in the suspicious application set, collecting interface calling related to sensitive applications, giving vector space representation, and performing application program vectorization; step four, obtaining the detection result of kind application programs meeting safety detection standard through safety detection. Compared with the prior art, the permission-based Android malicious software hybrid detection method integrates two affecting factors of euclidean distance and cosine similarity, and the obtained detection result is more comprehensive and higher in accuracy.
Owner:TIANJIN UNIV
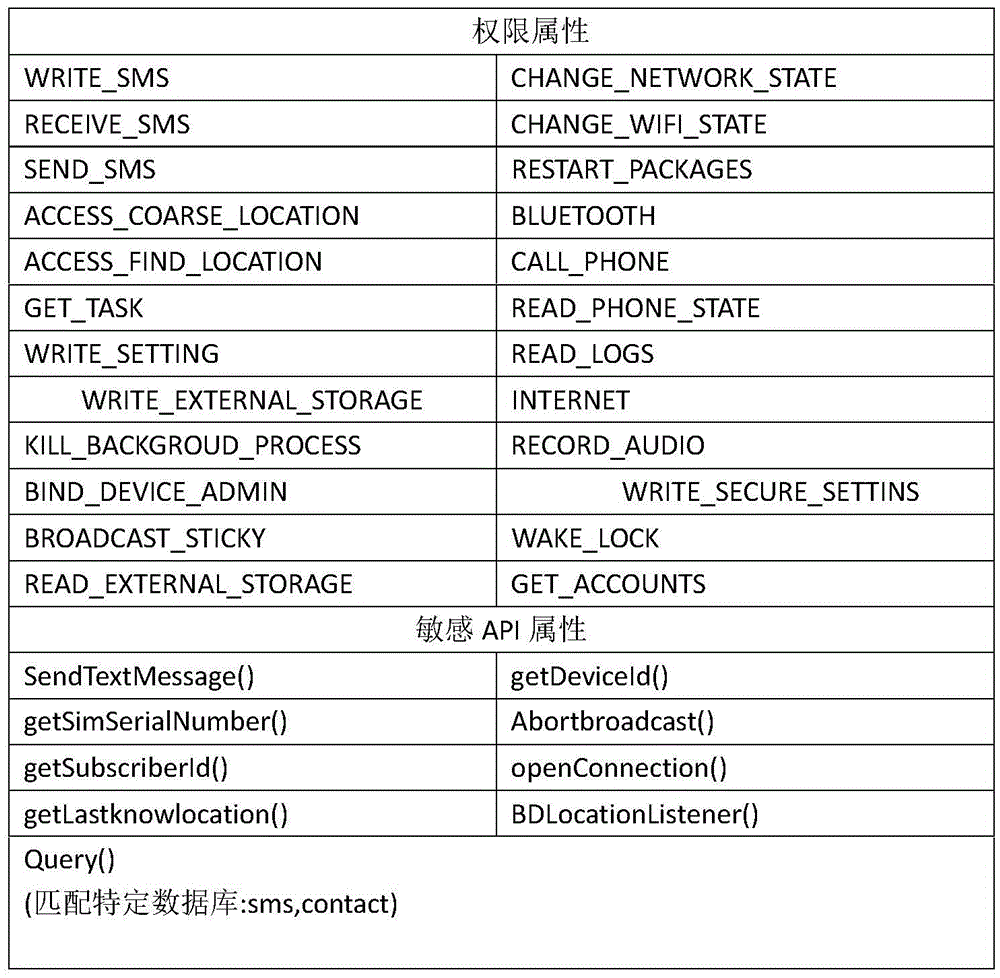
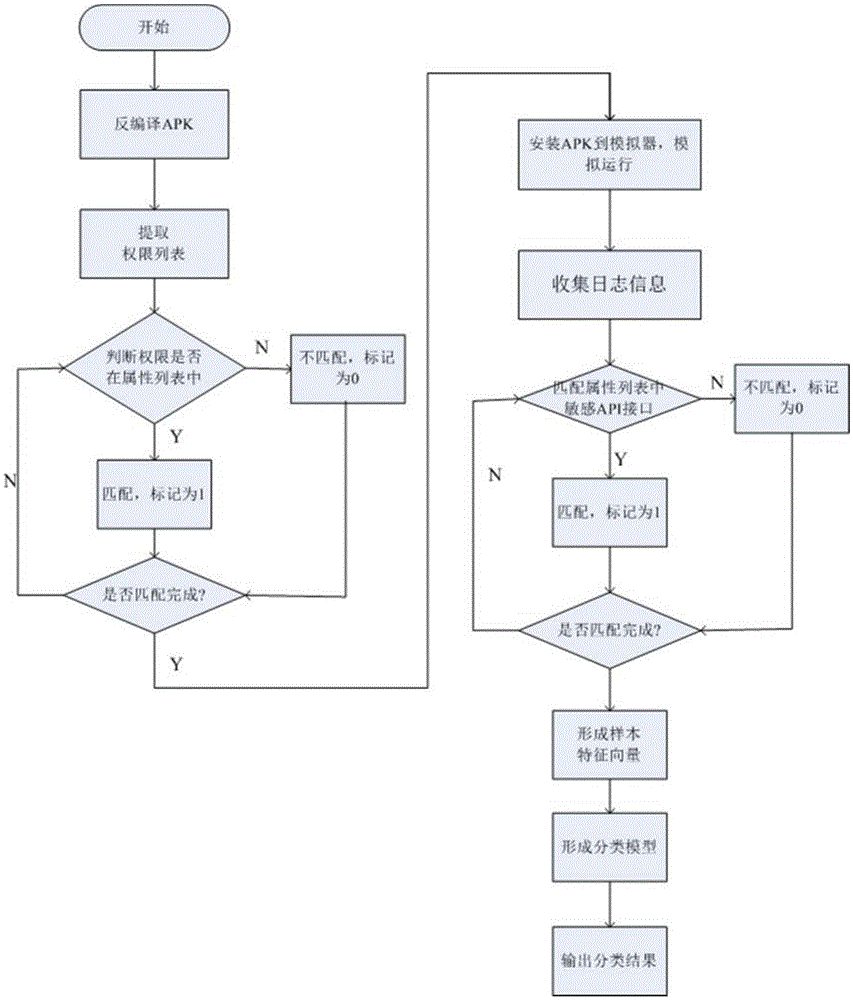
Method and device for Android malicious software classification based on Naive Bayes
InactiveCN105468977APlatform integrity maintainanceApplication programming interfaceMachine learning
The invention discloses a method and a device for Android malicious software classification based on Naive Bayes, wherein the method is used for extracting authority attribute characteristics and sensitive API (Application Programming Interface) attribute characteristics of malicious software mainly through a dynamic and static combination method, and performing classification through a Naive Bayes algorithm; and the device comprises a characteristic attribute set module, an authority characteristic attribute module, a sensitive API characteristic attribute module, a Naive Bayes classification model module, an output module and an updating module. The algorithm has firm mathematical foundation and steady classification efficiency, and needs relatively less parameters; the algorithm is simple; and malicious applications can be classified quickly and accurately, and thus, classification efficiency is improved.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
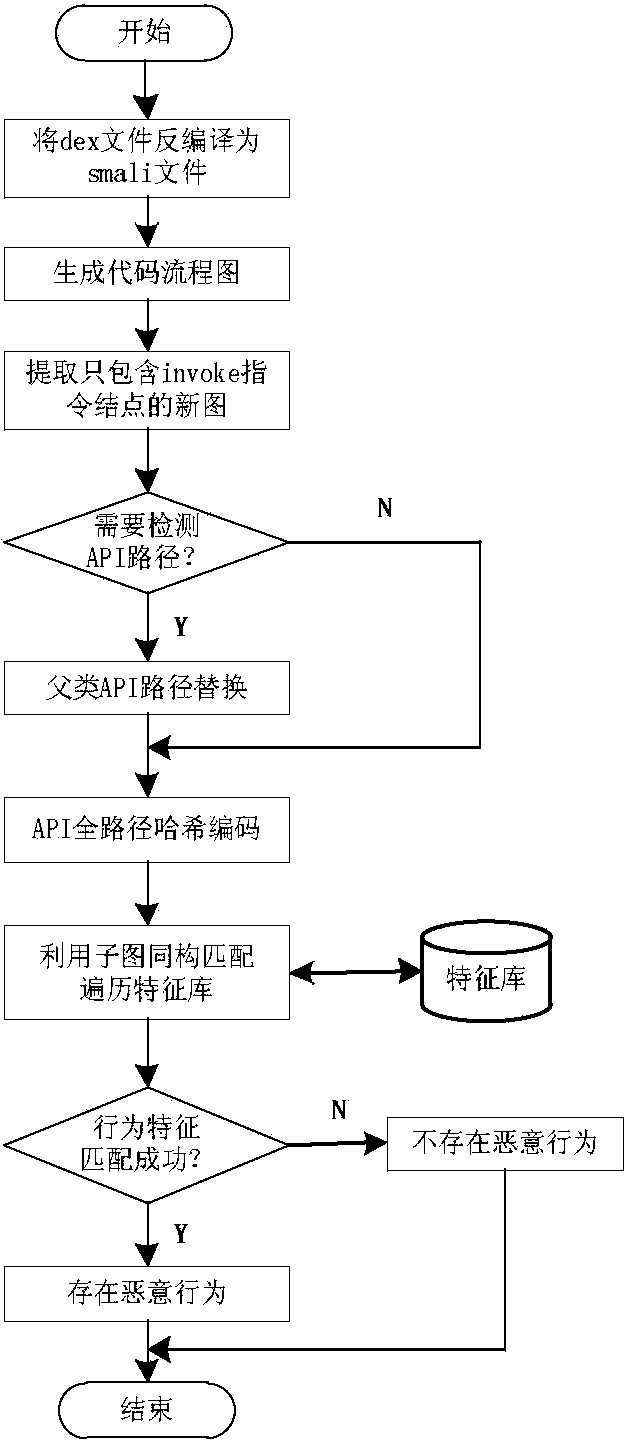
Method for detecting Android malicious software based on program flow chart
InactiveCN104021346AResistance to tamperingReduce sizePlatform integrity maintainanceSoftware engineeringBasic block
The invention discloses a method for detecting Android malicious software based on a program flow chart. Firstly, a basic block of an APK application program to be detected program is analyzed according to a smali file generated after decompilation, the flow chart of the program is obtained, a graph fingerprint formed by an API full-path hash coded value and the connecting relation of the coded value is taken as malicious behavior characteristics, and then on the basis of the subgraph isomorphism theory, behavior matching is performed on the malicious software. Compared with a traditional system for detecting the malicious software by utilizing a file signature scheme, the variant of the malicious software can be effectively recognized, and virus types which cannot be detected through signature schemes like the malicious code tampering scheme can be effectively resisted.
Owner:SOUTHEAST UNIV
Efficient Android malware detection model DroidDet based on rotating forest
InactiveCN106919841AEfficient detectionImprove scalabilityPlatform integrity maintainanceSupport vector machine svm classifierApplication software
Owner:XIJING UNIV
Android malware detection method based on improved Bayesian algorithm
InactiveCN104598825AImprove detection efficiencyReduce relevancePlatform integrity maintainanceNaive Bayes classifierData modeling
The invention provides an Android malware detection method based on an improved Bayesian algorithm. The feature attributes of Android malicious programs and well-behaved programs are analyzed and classified through the improved Bayesian algorithm to realize the malware detection method based on the improved Bayesian algorithm. A judgment on whether software is malware is implemented from the aspect of permission application of applications. According to the method, a permission request label in an Android permission request mechanism is taken as a detection data source. The malware and well-behaved software are distinguished in a permission request label combination way, and a detection model is built by using the improved Bayesian algorithm. The improved Bayesian algorithm is characterized in that mutual independence among attributes of the data source is considered, and a naive Bayesian classifier is used for performing data modeling, so that the detection index is increased greatly, the detection accuracy is increased, and the false alarm rate is lowered.
Owner:NANJING UNIV OF POSTS & TELECOMM
Android malicious code detection method based on class analysis
ActiveCN103473504AFacilitate automatic review functionPlatform integrity maintainanceTransmissionApplication softwareAndroid application
The invention provides an Android malicious code detection method based on class analysis. The method comprises the following steps: extracting permission information from an Android program to be detected by adopting a classifying method based on permission information; inputting the permission information into a classifying model for classifying; comparing a classification result with a claimed class; judging the malicious threat degree of the Android program to be detected according to a judging rule. The Android malicious code detection method is suitable for automatic malicious code detection of mass Android applications, and has the characteristics of easiness, high efficiency and high speed.
Owner:XI AN JIAOTONG UNIV
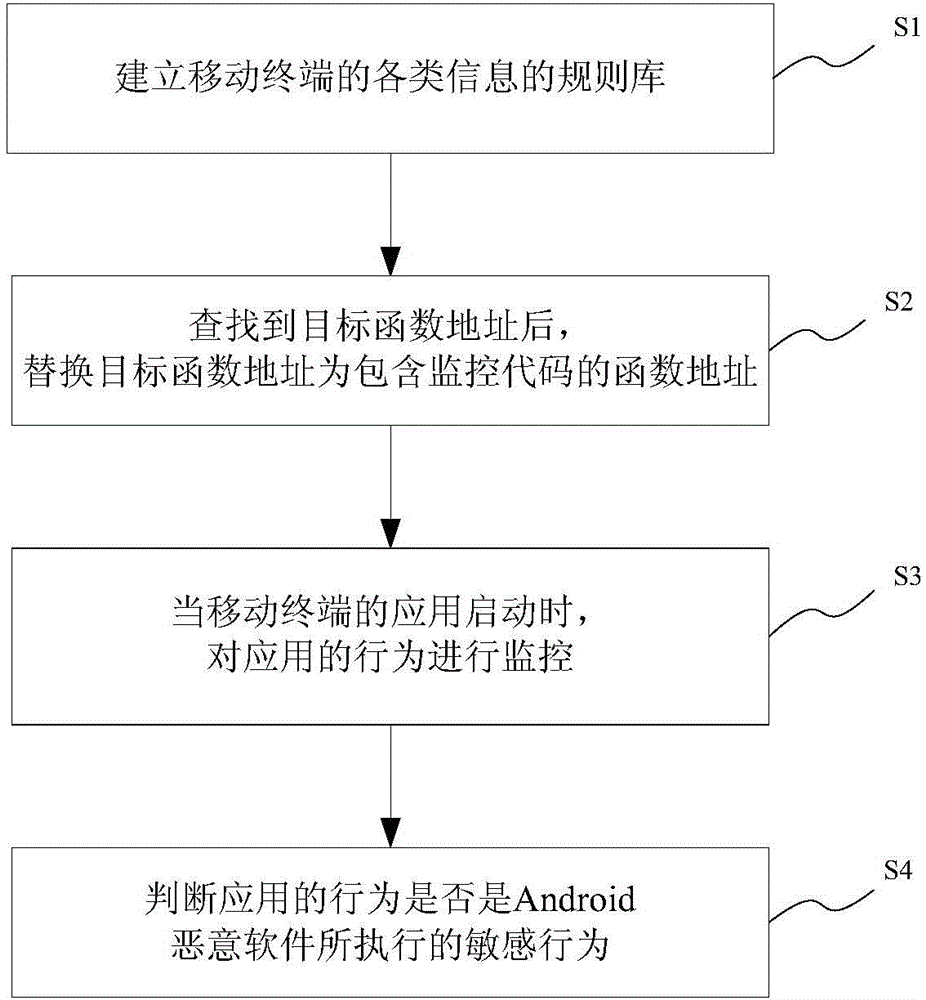
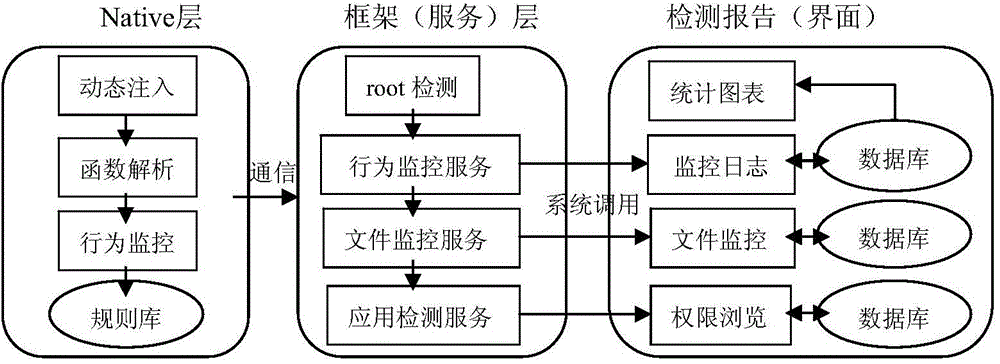
Android malicious software detection method and system based on dynamic monitoring
InactiveCN104809397AFlexible and convenient detectionRealize monitoringPlatform integrity maintainanceThird partyData stream
The invention provides an Android malicious software detection method and system based on dynamic monitoring. The method comprises the following steps: S1, establishing a rule library of various information of a mobile terminal; S2, after a target function address is looked up, replacing the target function address with a function address comprising monitoring codes; S3, when an application of the mobile terminal is started, monitoring the behavior of the application; S4, judging whether or not the behavior of the application is a sensitive behavior executed by Android malicious software. According to the Android malicious software detection method and system based on dynamic monitoring, the aim of effectively monitoring malicious software is fulfilled by simulating running of third-party application software, monitoring sensitive data streams and analyzing sensitive data leakage of application software and making a safety alarm when the sensitive data is tampered.
Owner:PHICOMM (SHANGHAI) CO LTD
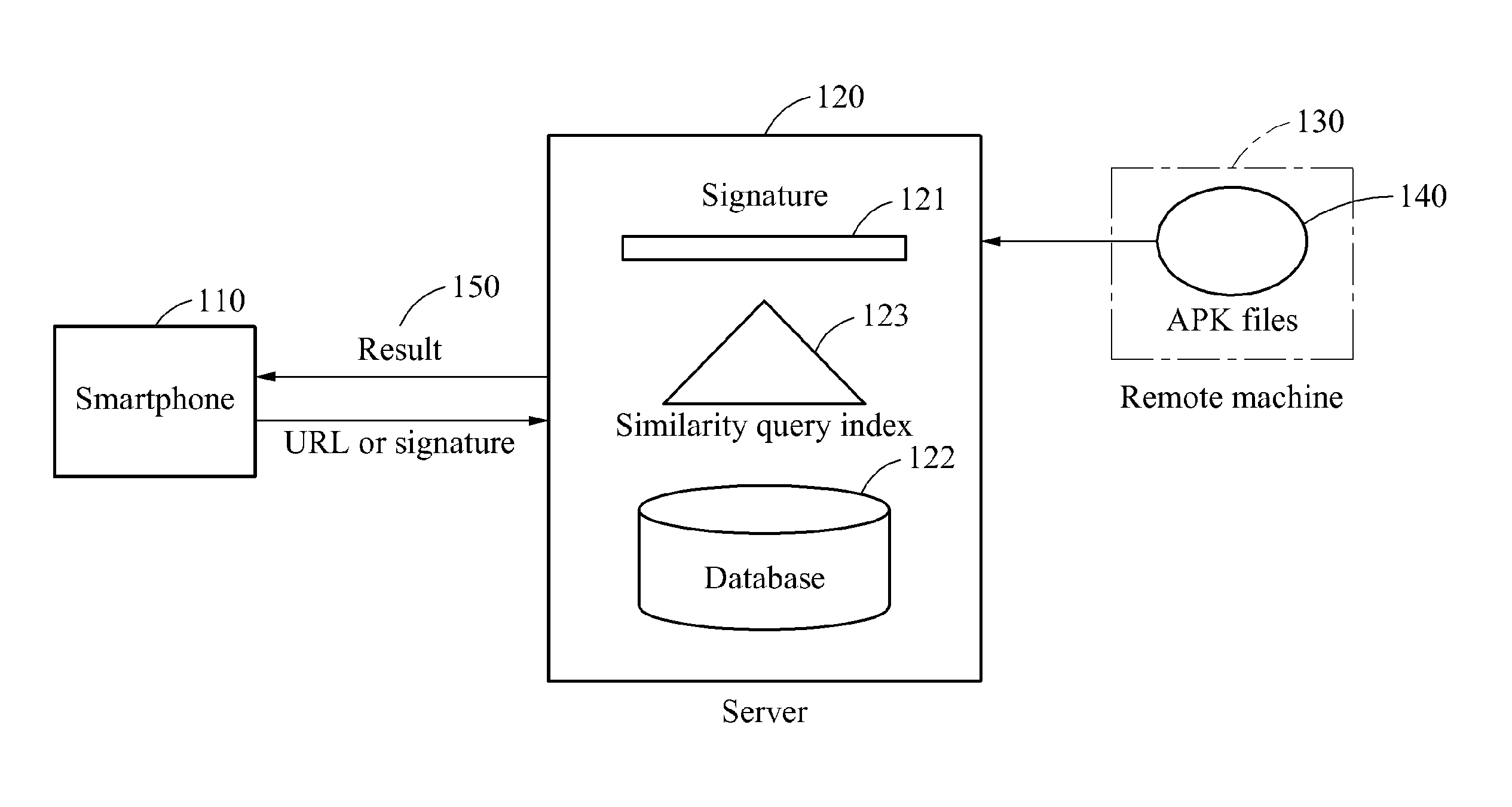
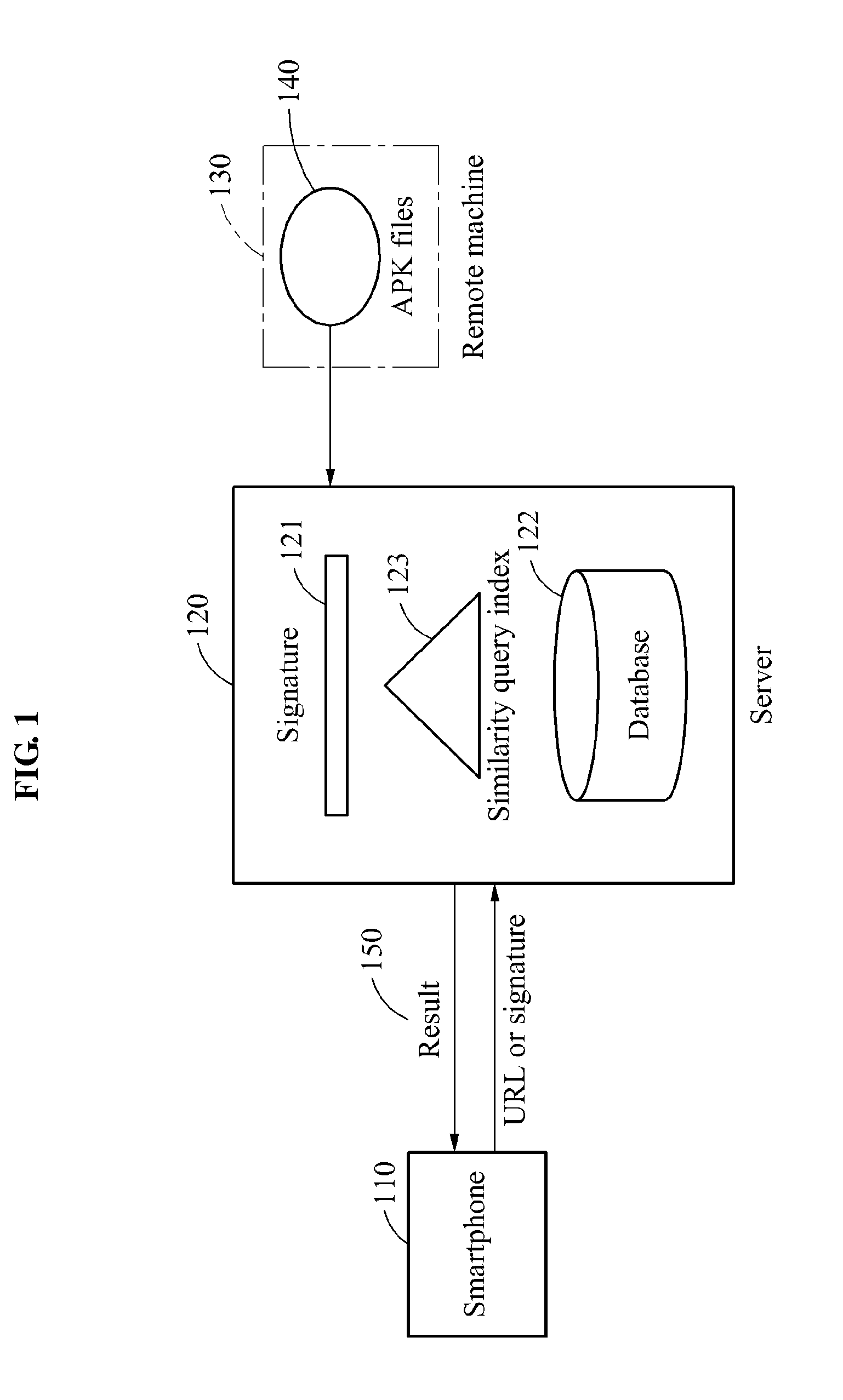
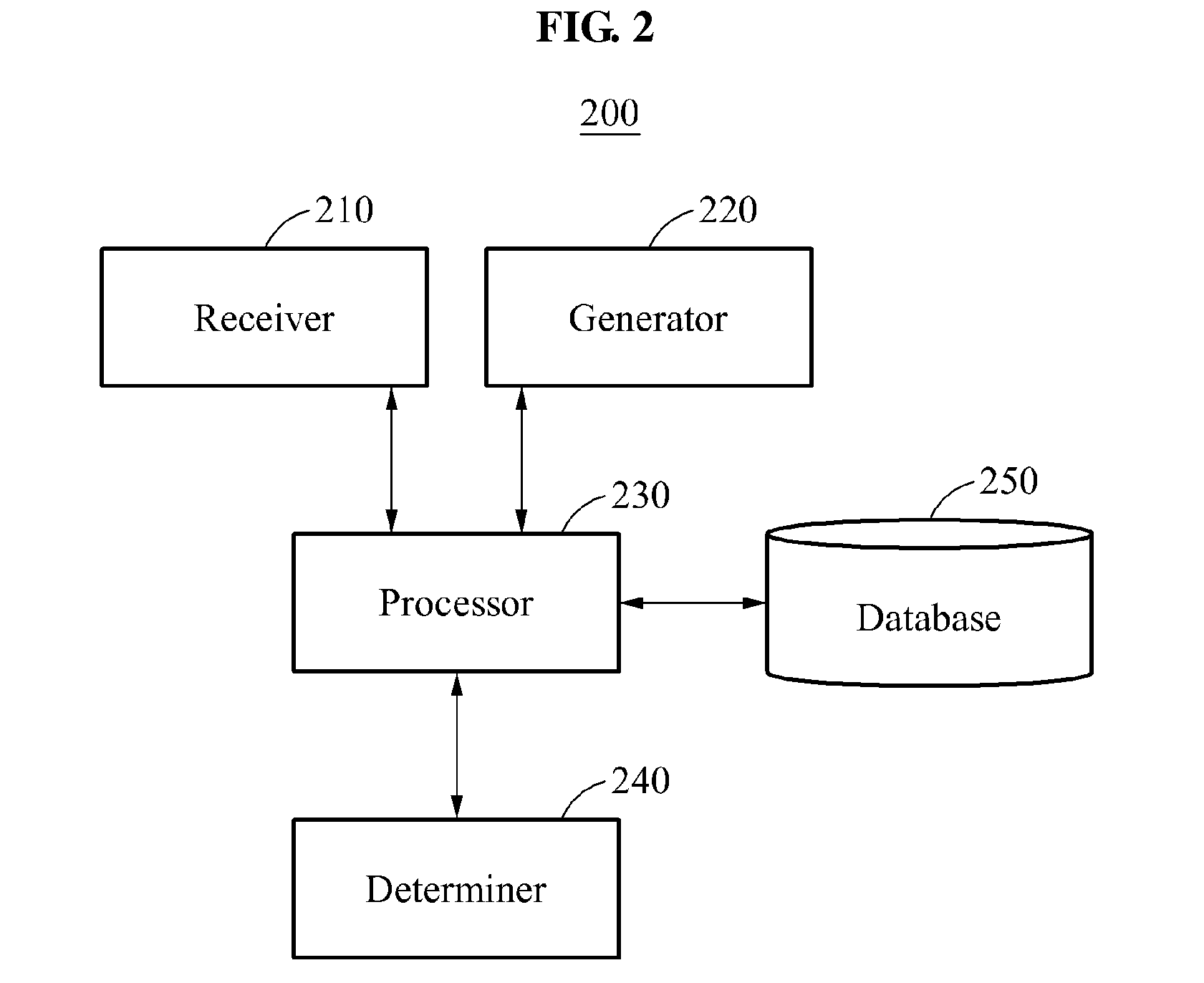
Method and system for fast inspection of android malwares
InactiveUS20160267270A1Fast conductionFast and efficient inspectionDigital data information retrievalNatural language data processingApplication softwareUniform resource locator
Provided is a system for conducting the fast inspection of Android malwares, the system including a processor configured to compute the similarity between the signature for a given target application and one of signatures stored in a database, and a determiner configured to determine whether the target application is a malware based on the computed similarity, wherein the system relates to the technology for examining whether a certain Android application, which can be downloaded via a uniform resource locator (URL), is malicious by examining how similar the application is with the malwares and normal applications verified earlier.
Owner:ELECTRONICS & TELECOMM RES INST
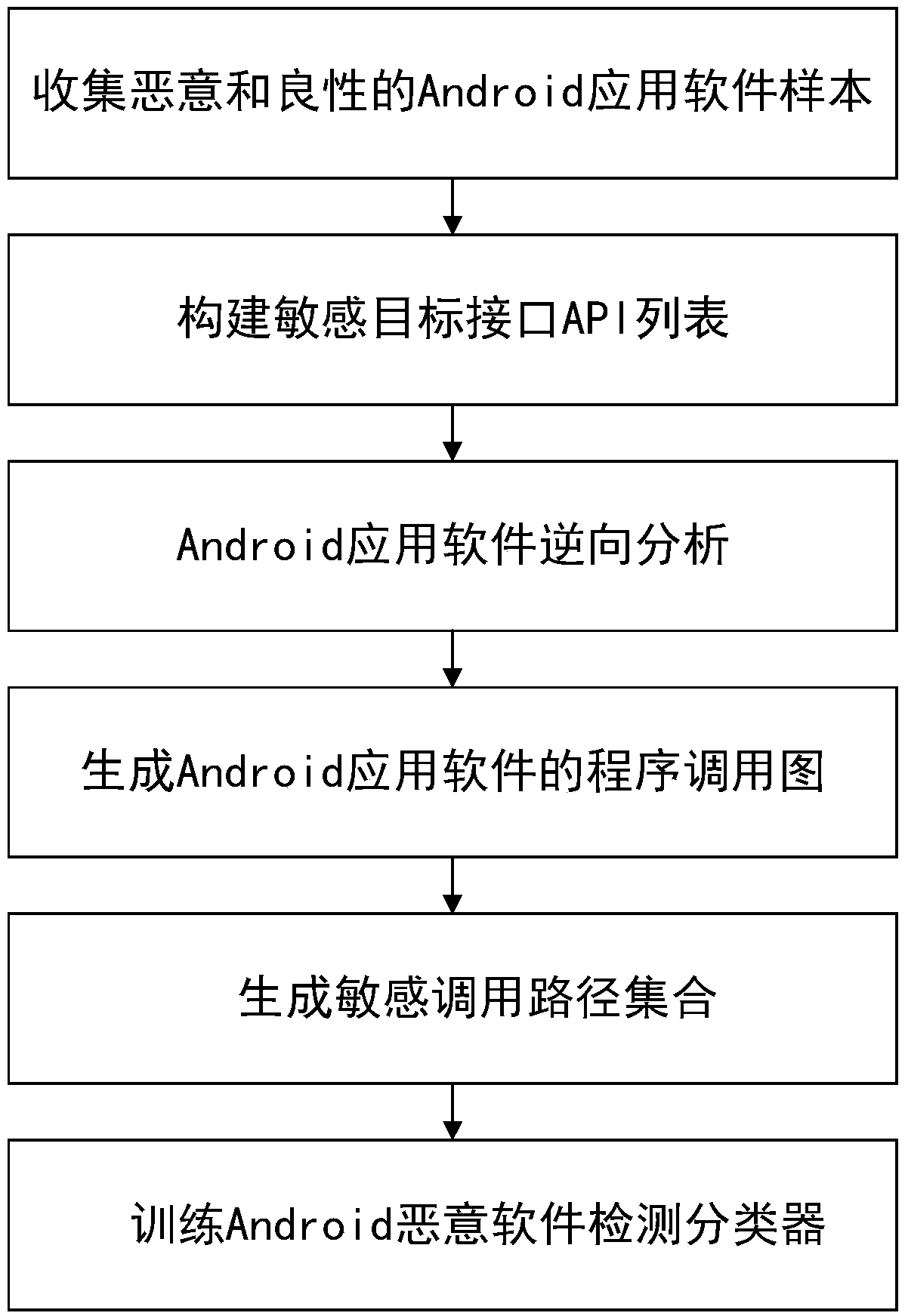
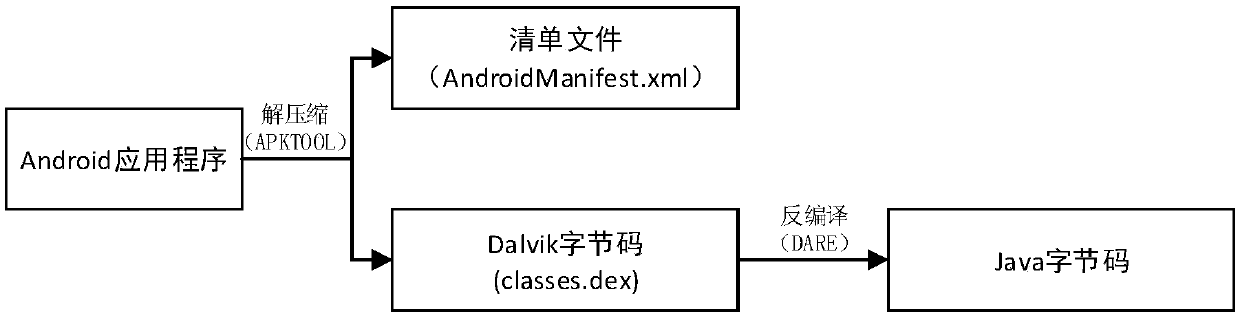
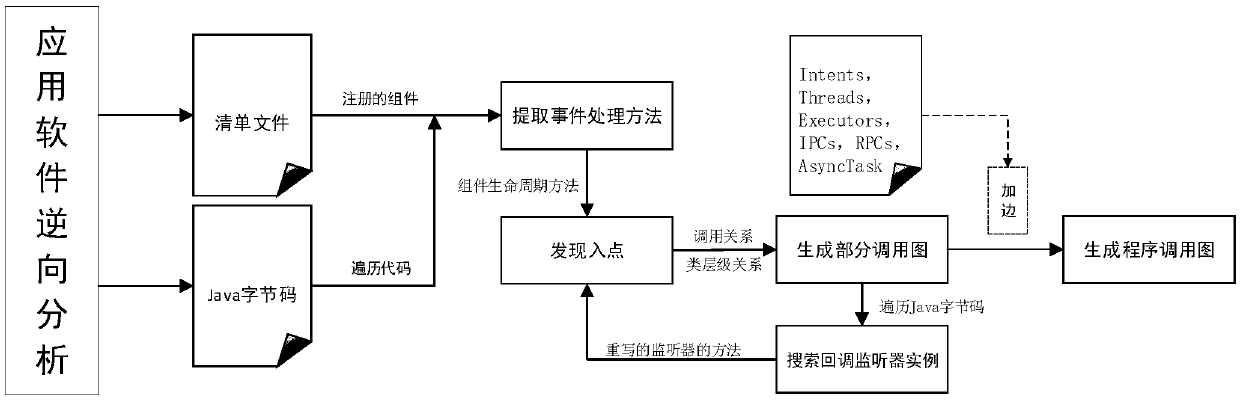
An Android malicious software detection method based on a sensitive calling path
ActiveCN109684840AAccurate identificationHigh precisionCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorReverse analysis
The invention discloses an Android malicious software detection method based on a sensitive calling path, and mainly solves the problem that an existing scheme is low in malicious software detection accuracy. According to the scheme, a sensitive target interface API list is constructed through a natural language processing technology; Generating a sensitive calling path set by using the Android application software subjected to reverse analysis; Taking the sensitive calling path as a feature, and establishing an Android sensitive calling path feature library by analyzing a large number of benign software and malicious software data sets; Processing the sensitive calling path set of the sample into a feature vector, and training a classifier model by adopting a supervised machine learning algorithm by utilizing the feature vector; And detecting whether the Android application software with unknown security is malicious software or not by using the trained classifier model. The method ishigh in precision, easy to expand and remarkable in intelligence, and can be used for automatic detection of the mobile terminal and examination and analysis of the Android application market.
Owner:XIDIAN UNIV
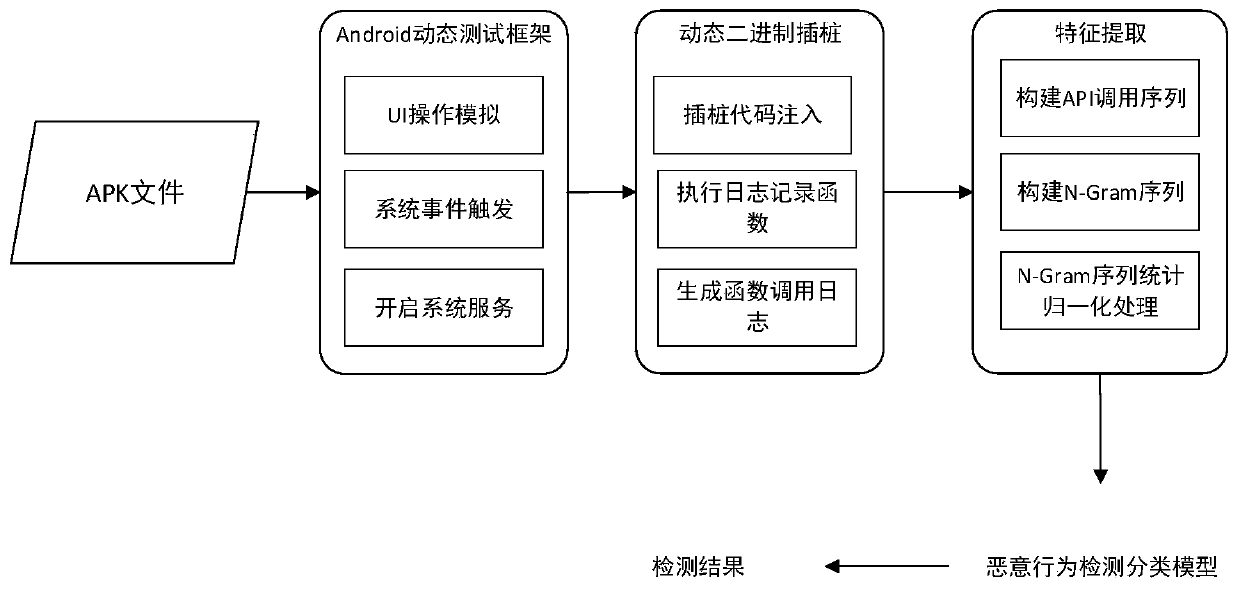
Android malicious behavior dynamic detection method based on binary dynamic instrumentation
InactiveCN109992968AImprove detection efficiencyImprove accuracyPlatform integrity maintainanceSoftware simulation/interpretation/emulationGranularityDynamic instrumentation
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
A large-scale Android malware automatic detection system and method
InactiveCN108985060AReflect maliciousnessComprehensive feature selectionPlatform integrity maintainanceSupport vector machineSoftware analytics
The invention relates to a large-scale malicious Android software automatic detection system and method based on multi-class features and machine learning. The method includes: collecting security andmalware libraries, using software analysis tools such as Androguard and Droidbox, collecting the characteristics of each software from both dynamic and static angles, processing the receipts of the forms, defining the thresholds in different angles, when a certain feature does not meet the threshold requirements, deleting the feature, and utilizing a support vector machine, a neural network, an ensemble learning algorithm and other algorithms for detection, and obtaining the optimal results of detection results are obtained, so as to realize the automatic detection of large-scale malware. Theinvention can be used for detecting and identifying large-scale malicious mobile phone software and protecting the privacy and safety of users.
Owner:中共中央办公厅电子科技学院
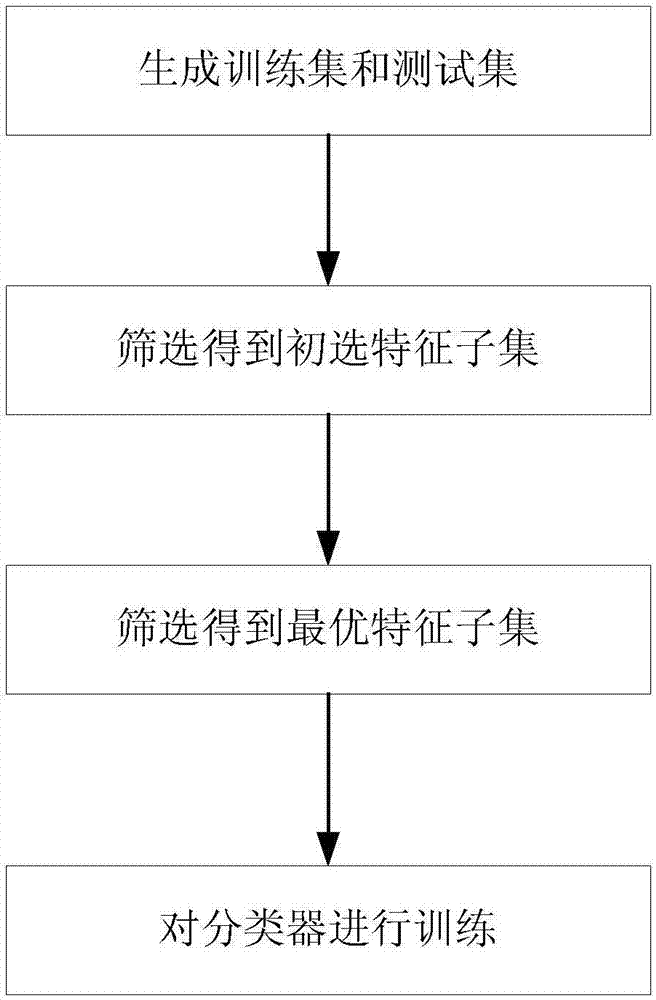
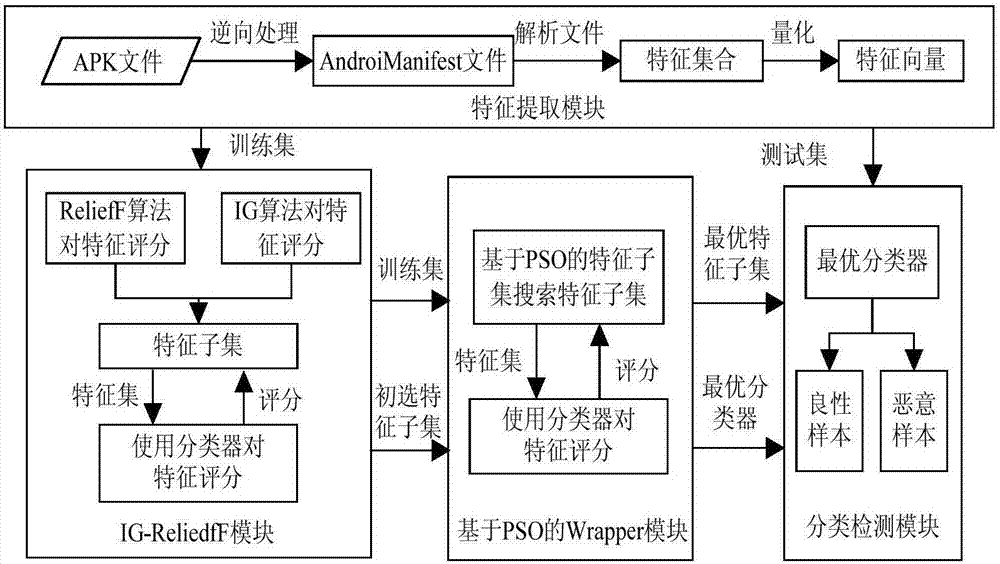
Hybrid feature screening method for Android malicious software detection
ActiveCN107577942AImprove detection efficiencyImprove detection accuracyCharacter and pattern recognitionPlatform integrity maintainanceFeature screeningAndroid malware
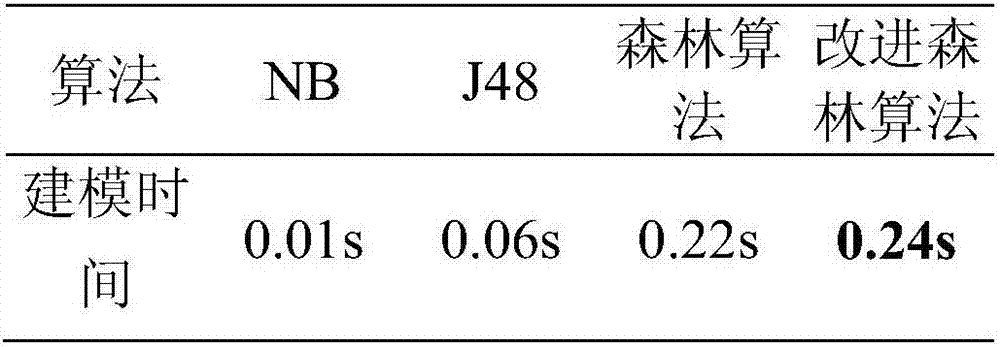
The invention discloses a hybrid feature screening method for Android malicious software detection. The method comprises the steps that a training set and a test set are generated according to existing data; a primary feature subset is screened out; an optimal feature subset corresponding to each type of classifiers is obtained; and the optimal feature subset is utilized to train the correspondingclassifiers. Through the hybrid feature screening method for Android malicious software detection, the optimal feature subset and a classification algorithm matched with the optimal feature subset can be screened out, modeling time of the classifiers is greatly shortened, and the detection efficiency and detection precision of Android malicious software detection can be improved.
Owner:CIVIL AVIATION UNIV OF CHINA
Android malicious software detection method based on combined feature mode
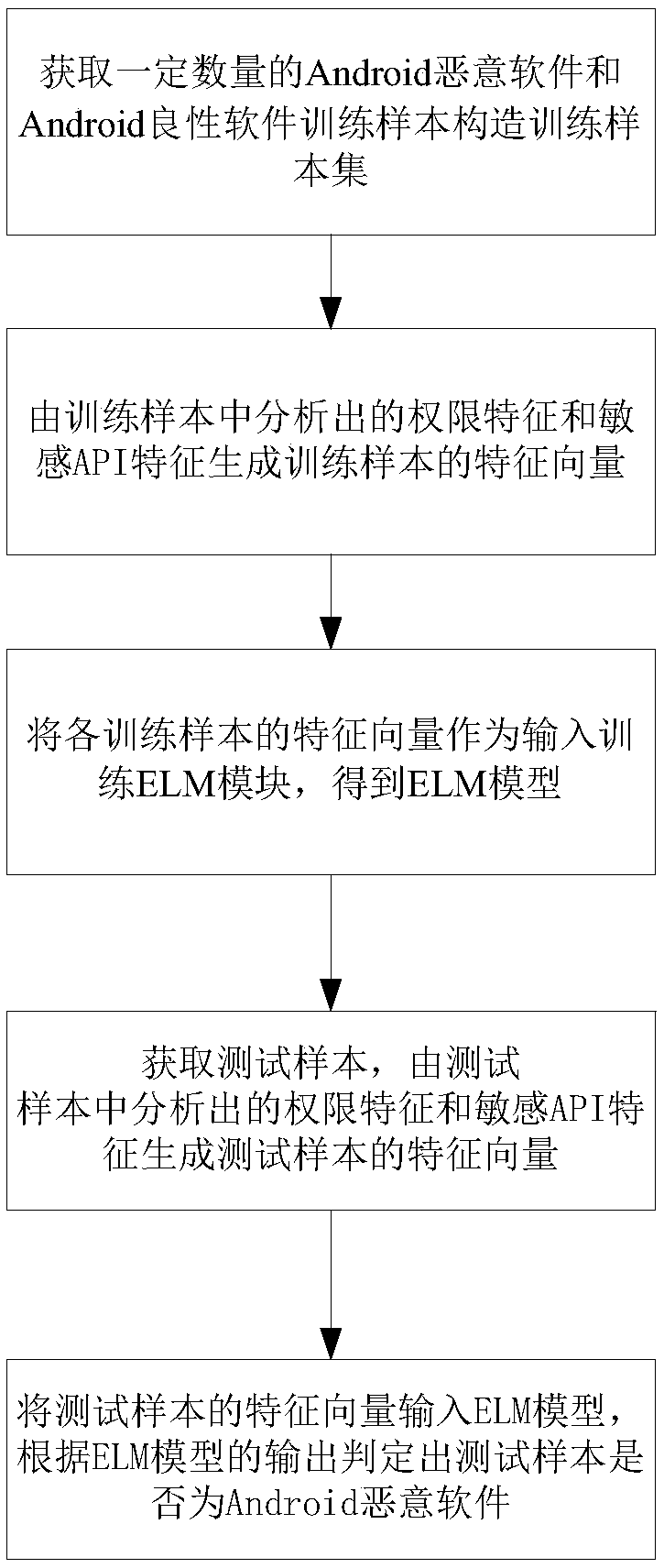
InactiveCN107832610AAccurate detectionShort learning timeCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorTest sample
The invention discloses an Android malicious software detection method based on a combined feature mode. Firstly, a certain amount of Android malicious software and Android benign software training samples are acquired to construct a training sample set; authority features and sensitive API features of each training sample are analyzed and combined to generate feature vectors of the training samples; the feature vectors of all the training samples serve as input to train an ELM, and the ELM is obtained; to-be-detected Android software serves as a test sample, and the authority feature and thesensitive API feature of the test sample are analyzed and combined to generate the feature vector of the test sample; the feature vector of the test sample is input into the ELM, and finally, whetherthe test sample is Android malicious software or not is judged by the ELM. The method has the advantages of being high in Android malicious software detection accuracy and short in learning time.
Owner:JINAN UNIVERSITY
Method for statically identifying malicious codes of Android system in heuristic manner
ActiveCN103440458AEasy to identifyGood killing effectPlatform integrity maintainanceCode moduleThird party
The invention provides an Android malicious software detection method. Graphs are called by adopting an isomerism method for constructing Apk software of Android application, sensitive functions are calibrated, and malicious codes are positioned according to the continuity of the graphs. The method specifically comprises the following steps of performing graph continuity scanning on the graphs called by the isomerism method to obtain all sub-graphs, performing sensitive function marking on all the sub-graphs, and determining that the sub-graphs of which the marks exceed a threshold value are malicious code modules. According to the method, unknown malicious software can be heuristically found, and security scanning and protection are supplied to a large range of Android third-party markets and individual users.
Owner:XI AN JIAOTONG UNIV
Mixed feature-based Android malicious software detection method and system
InactiveCN107180190AQuick buildImprove classification accuracyCharacter and pattern recognitionPlatform integrity maintainanceAlgorithmFeature data
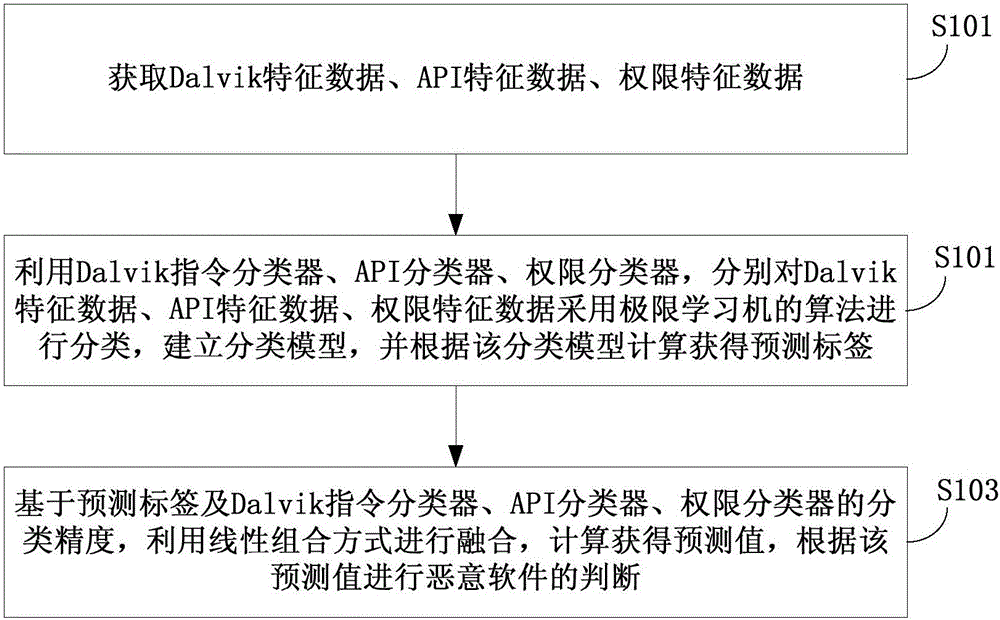
The invention discloses a mixed feature-based Android malicious software detection method and system. The method comprises the steps of obtaining Dalvik feature data, API feature data and permission feature data; by utilizing a Dalvik instruction classifier, an API classifier and a permission classifier, classifying the Dalvik feature data, the API feature data and the permission feature data by adopting an algorithm of an extreme learning machine, building a classification model, and performing calculation according to the classification model to obtain a prediction tag; and based on the prediction tag and the classification precision of the Dalvik instruction classifier, the API classifier and the permission classifier, performing fusion in a linear combination mode, performing calculation to obtain a prediction value, and performing malicious software judgment according to the prediction value. By utilizing the method and the system, the malicious software identification precision can be improved and the false alarm rate can be reduced.
Owner:SHENZHEN INST OF ADVANCED TECH
An Android malware detection method based on depth learning
ActiveCN109271788ARich software featuresImprove detection accuracyCharacter and pattern recognitionPlatform integrity maintainanceConfusionInformation science
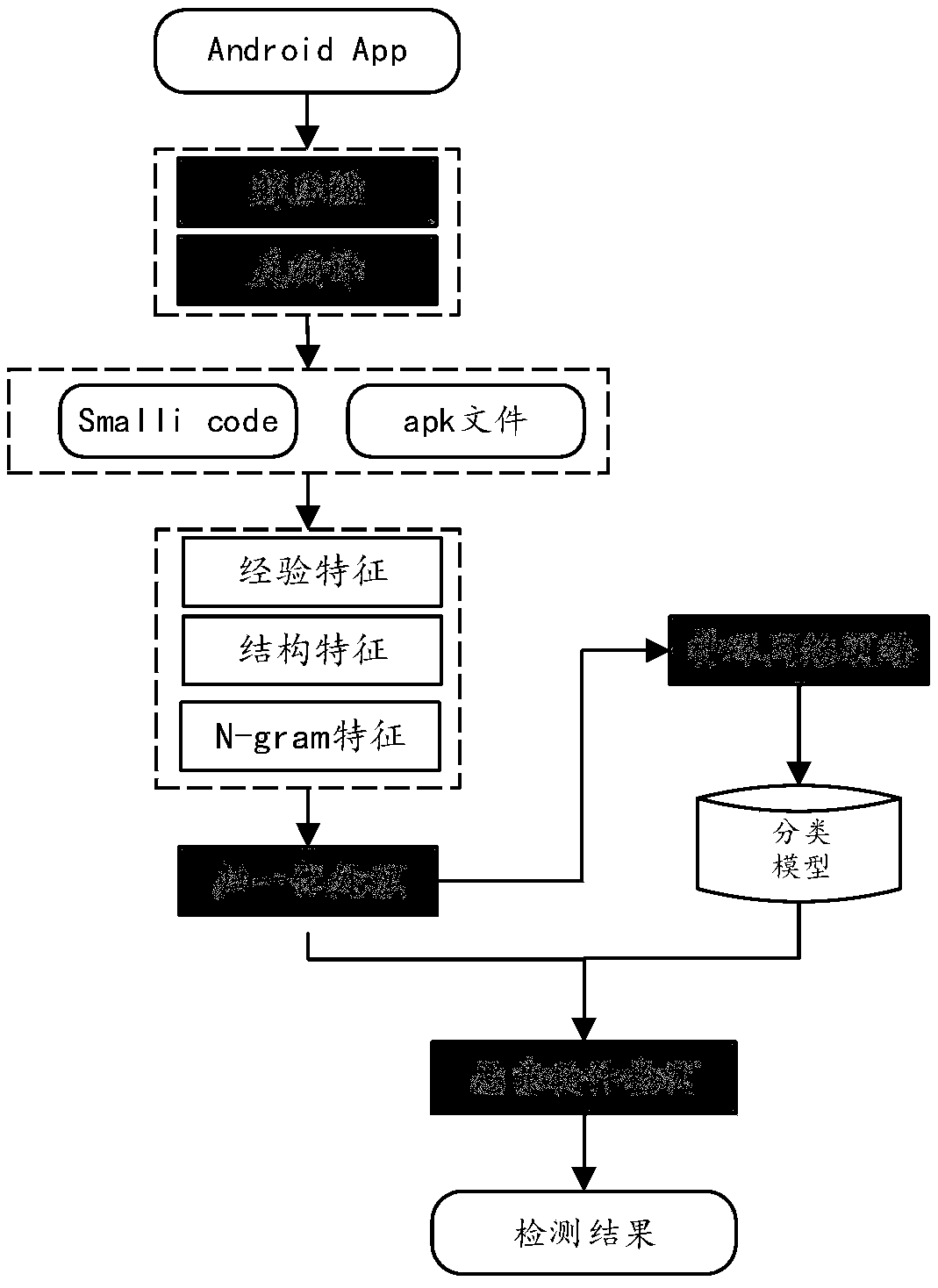
The invention relates to an Android malware detection method based on depth learning, belonging to the field of computer and information science and technology. The invention firstly extracts featuresof Android application software, and then extracts relevant security features by decompressing and decompressing Android application files. The extracted features include three aspects: file structure feature, security experience feature and N-Gram statistic characteristic. Then the extracted features are numerically processed to construct feature vectors. Finally, a DNN (Deep Neural Network) model is constructed based on the above extracted features. The new Android software is classified and identified by the constructed model. This method combines the analysis of instruction set and has the function of anti-malware confusion. At the same time, malware detection based on depth model can enhance the feature learning, can express the abundant information of big data, and can adapt to theevolving malware more easily.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Android malicious software detection system and method
ActiveCN106845220ASmall amount of calculationThe detection method is simplePlatform integrity maintainanceFeature extractionSoftware engineering
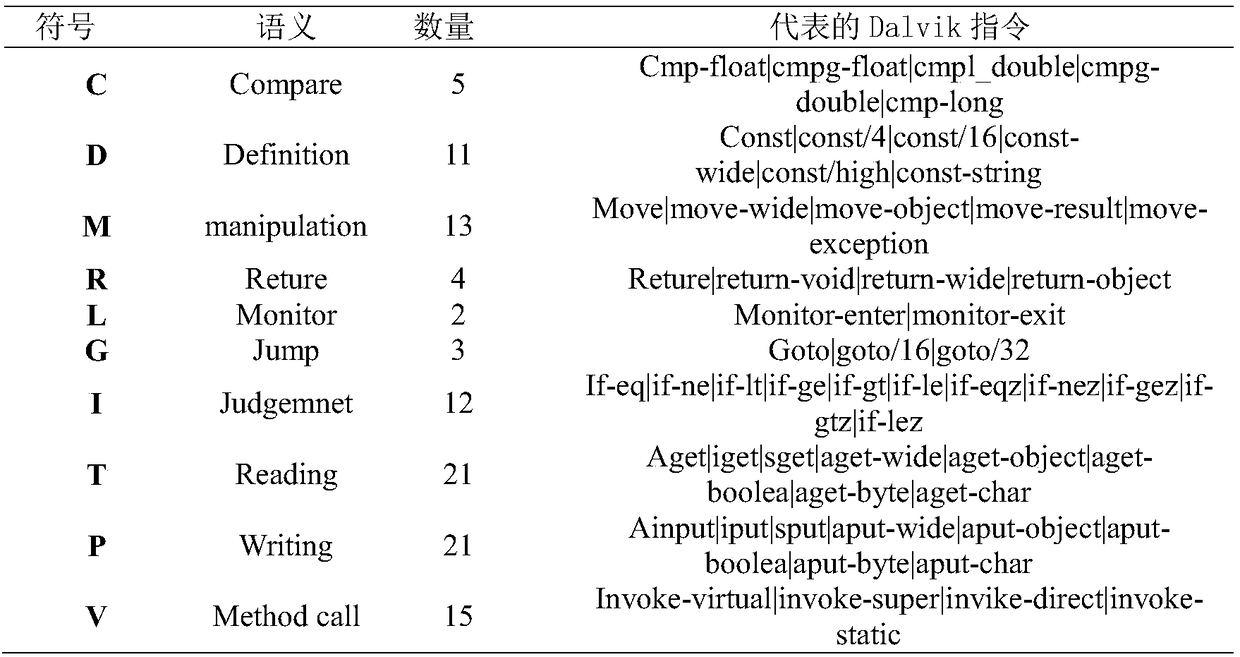
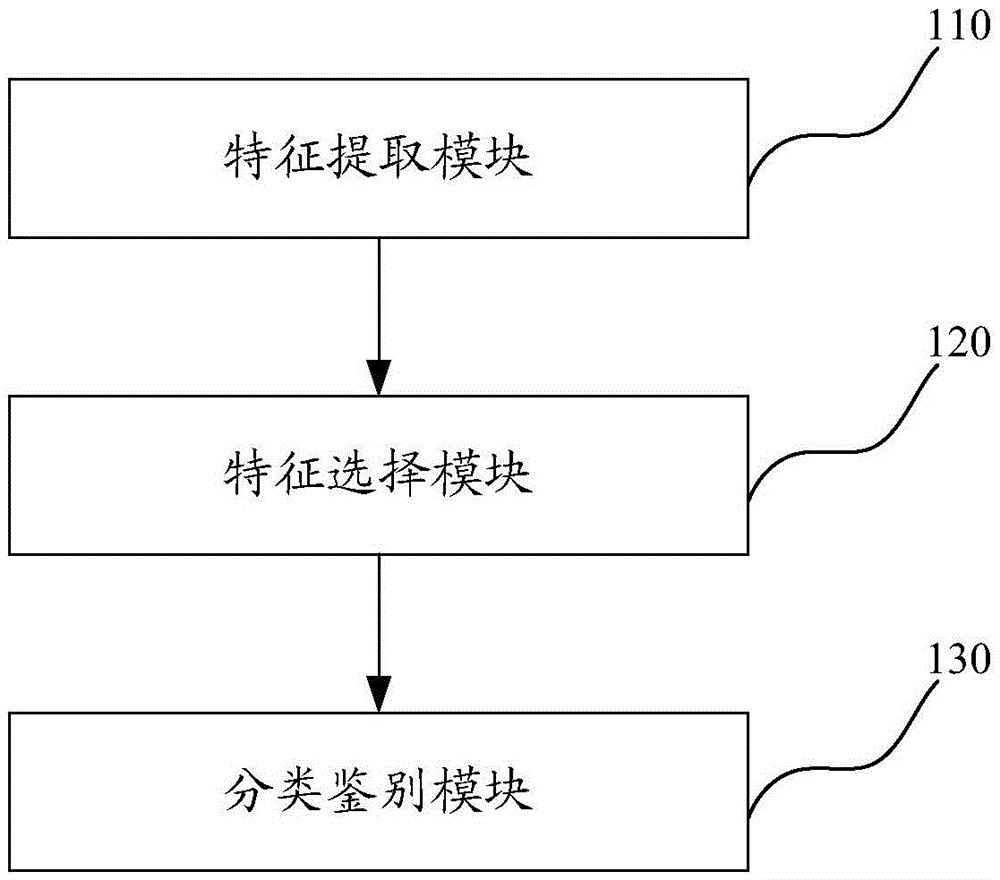
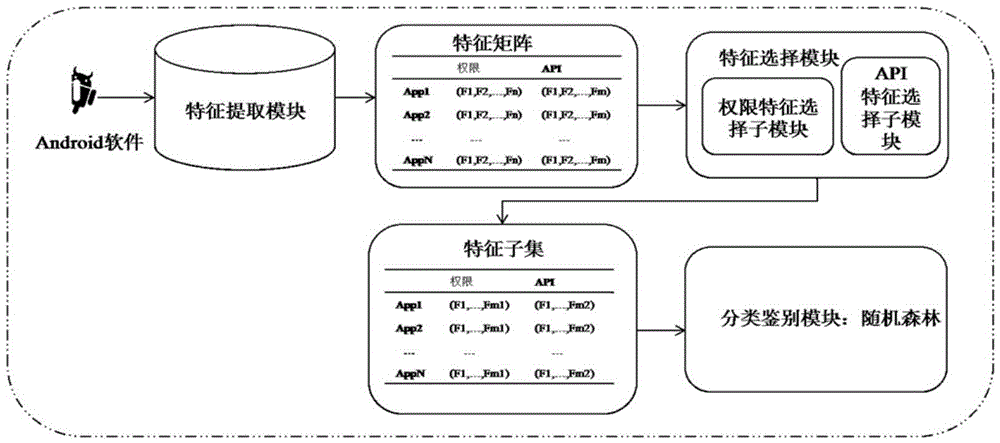
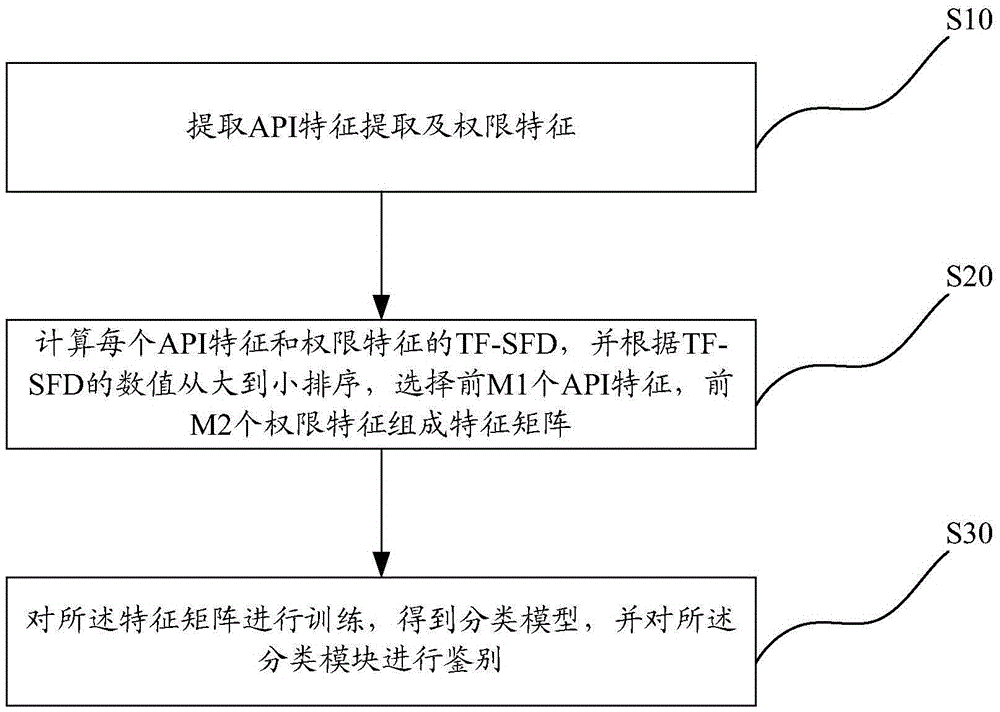
The invention provides an Android malicious software detection system and an Android malicious software detection method. The method comprises the steps of extracting API (Application Program Interface) characteristics and permission characteristics by use of a characteristic extraction module; calculating TF-SFD of each API characteristic and permission characteristic according to a characteristic selection module, ranking the numbers of TF-SFD from large to small, selecting first M1 API characteristics and M2 permission characteristics to form a characteristic matrix; and training the characteristic matrix through a class identification module to obtain a classification model, and identifying the classification module. The above-mentioned detection method is simple, small in calculated amount and relatively high in detection effect.
Owner:SHENZHEN INST OF ADVANCED TECH
An Android malware detection method and technology based on a behavior graph
InactiveCN109190371AImprove recognition rateImplement automatic updatesPlatform integrity maintainanceFeature extractionRandom combination
The invention relates to the technical field of mobile platform malicious code detection, aiming at providing an Android malware detection method and model based on a behavior graph. The method adoptsa detection scheme based on behavior graph, which comprises the following steps: converting application binary data into behavior graph containing directed edges; providing a new feature extraction method based on graph kernel, which extracts more complete feature information from the data of graph structure, wherein the feature contains context-related structured feature information, and can represent the specific behavior of application program more accurately; adopting a stochastic combinatorial updating machine learning algorithm based on on-line multi-core learning to update the model automatically to adapt to the ever-changing distribution; by designing comparative experiments, recording experimental data, and counting the general differences in the criteria for the designation ofthe method. This model has wide applicability and can detect unknown malware effectively. The invention provides a new solution for detecting Android malicious software.
Owner:SICHUAN UNIV
Improved forest algorithm-based Android malicious software detection method
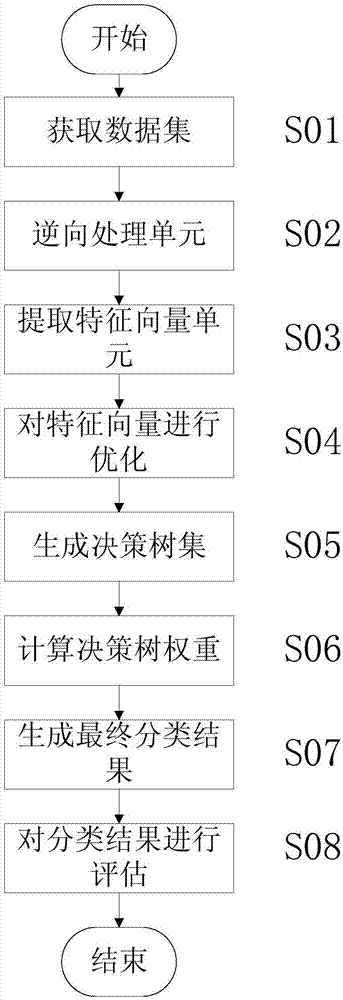
InactiveCN107092827AImprove accuracyReduce the probability of attackPlatform integrity maintainanceFeature vectorData set
The invention discloses an improved forest algorithm-based Android malicious software detection method. The method comprises an S01 stage of obtaining a data set, an S02 stage of carrying out reverse processing, an S03 stage of extraction feature vectors, an S04 stage of optimizing the feature vectors, an S05 stage of generating a decision tree set, an S06 stage of calculating a decision tree weight, an S07 stage of generating a final classification result and an S08 stage of assessing the classification result. Compared with the traditional detection method, the improved forest algorithm-based Android malicious software detection method has higher classification precision, and has the effects of improving the correctness of malicious software detection and reducing the probability that Android systems are attacked due to detection errors.
Owner:CIVIL AVIATION UNIV OF CHINA
Android malicious software detection method and system based on RNN and CNN
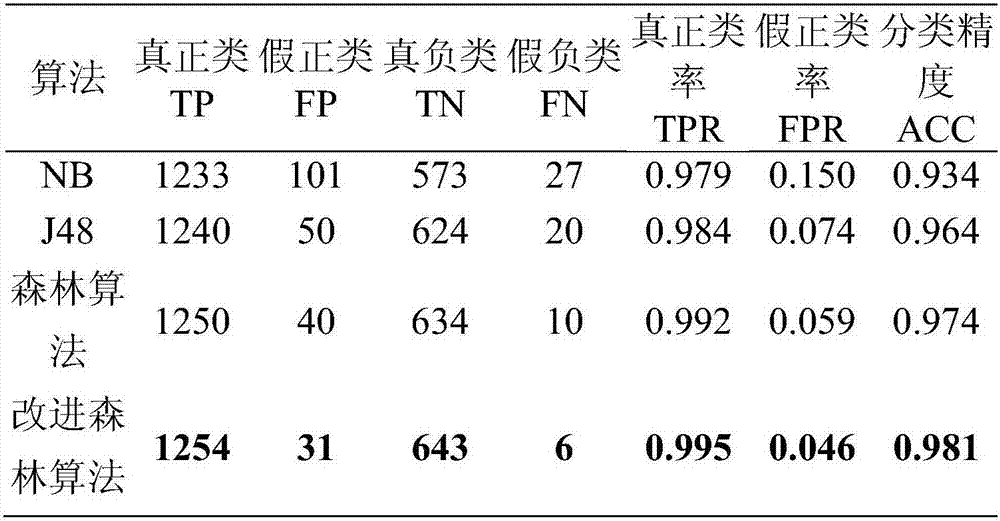
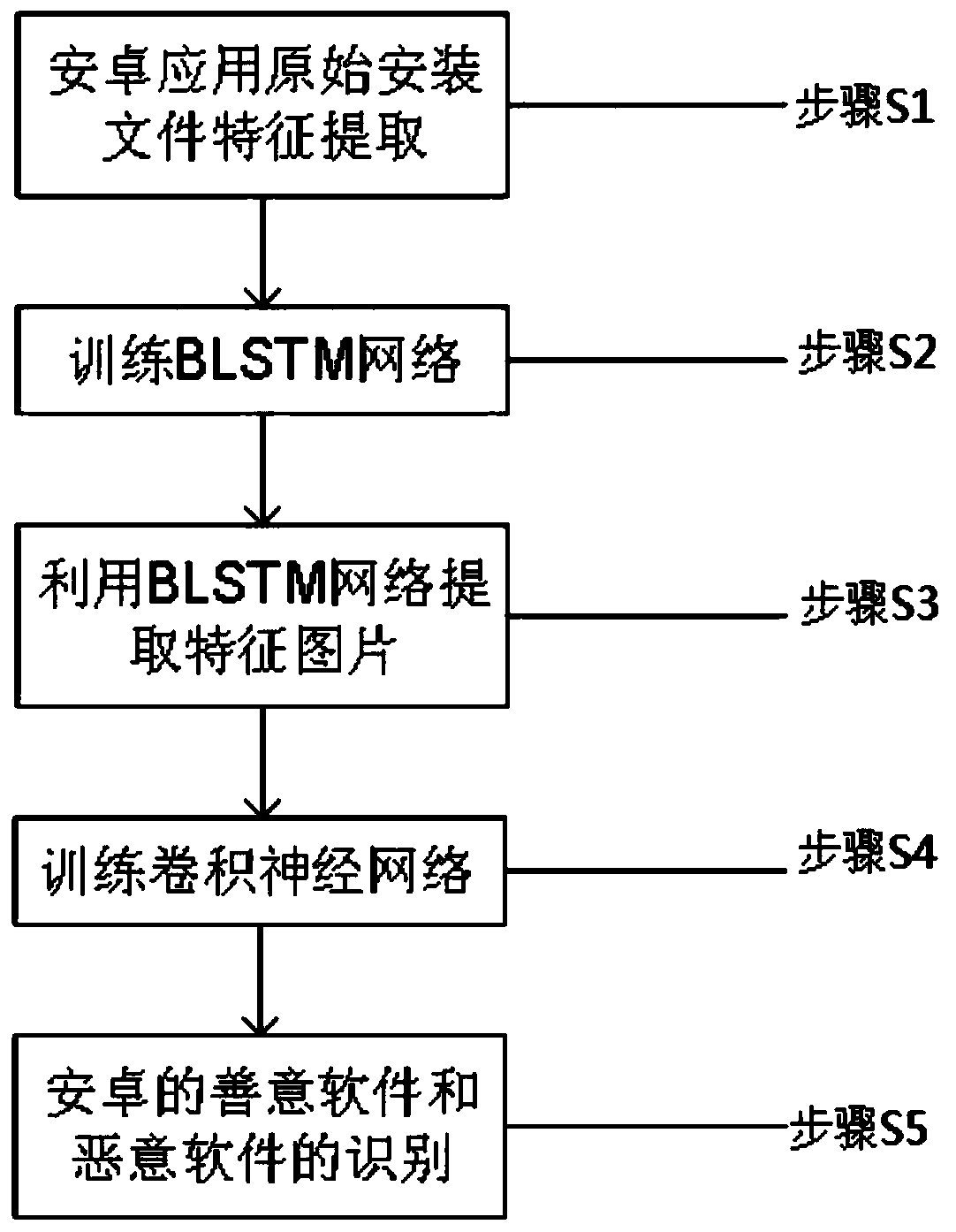
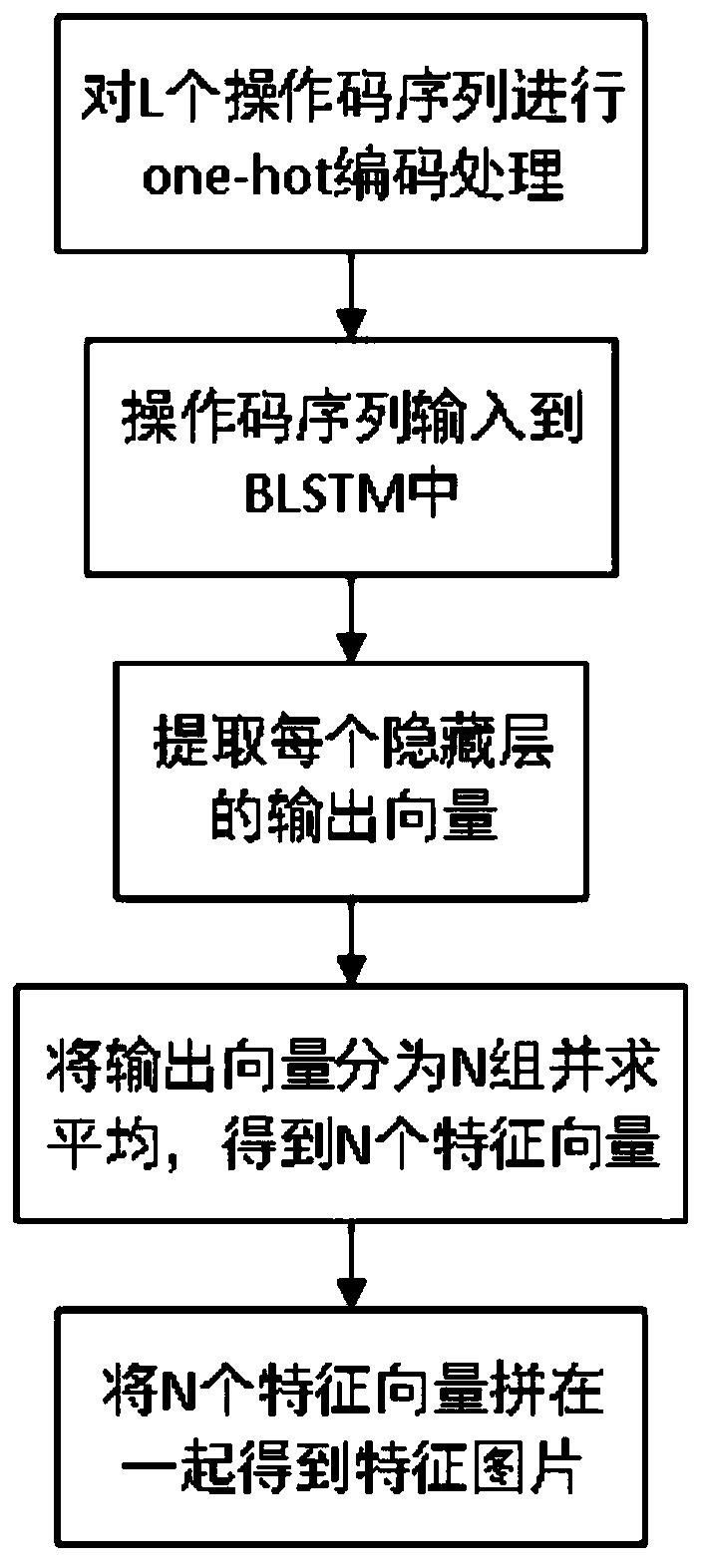
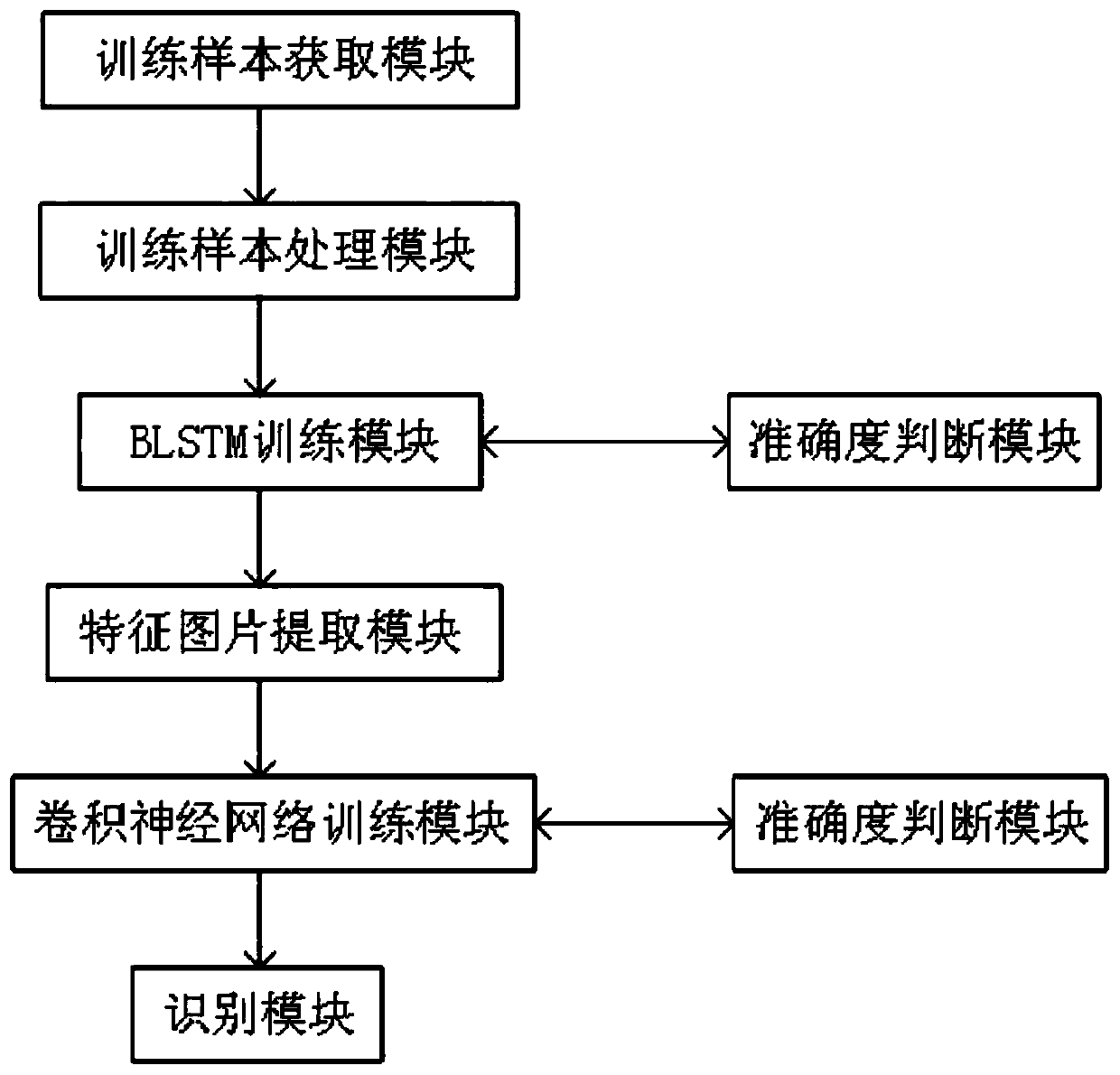
ActiveCN110489968AImprove recognition accuracyEasy extractionDecompilation/disassemblyPlatform integrity maintainanceFeature extractionComputer science
The invention provides an Android malicious software detection method and system based on RNN and CNN, and the method comprises the steps: carrying out the feature extraction of an original installation file of a training sample, and obtaining an operation code sequence; training a BLSTM network by using the operation code sequence; extracting the operation code sequence as a feature picture by using the trained BLSTM network; training a convolutional neural network by utilizing the feature pictures. Firstly, feature extraction is conducted on an installation file of a to-be-detected Android application, and an operation code sequence of the to-be-detected Android application is obtained. The operation code sequence is input into a trained BLSTM network, and a feature picture is extracted.Finally, the feature picture is input into a trained convolutional neural network, and a classification result that whether the feature picture belongs to malicious software or not is output. According to the method, recognition and distinguishing of good software and malicious software under the Android platform are achieved, and the safety of the Android software platform is improved.
Owner:东北大学秦皇岛分校
Android malicious software detection method based on program slicing technology
InactiveCN103971055ASolve semantic understandingSolve reverse analysisPlatform integrity maintainanceProgram slicingSoftware engineering
The invention provides the design scheme of an Android malicious software detection method based on a program slicing technology. According to the scheme, starting from an installation file APK of an installation application, source codes of the application are analyzed through the program slicing technology, key nodes affecting the safety of the application are found out, Android malicious software is detected, and the purpose of reducing manual operation is achieved. The test result shows that the Android malicious software detection method based on the program slicing technology can reliably detect the Android malicious software; the method based on the program slicing is more accurate than a traditional detection method; the Android malicious software is analyzed from the angle of the source codes, and flexibility is higher for continuously updated viruses and Trojan variants.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com