Android malicious software sorting method based on dynamic behavior dependency graph
A malicious software and classification method technology, applied in the field of network security, can solve problems such as the inability to effectively determine the type of malicious software, divide thread behavior attacks, etc., and achieve the effects of strong flexibility, scalability, and high detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below through specific embodiments and accompanying drawings.
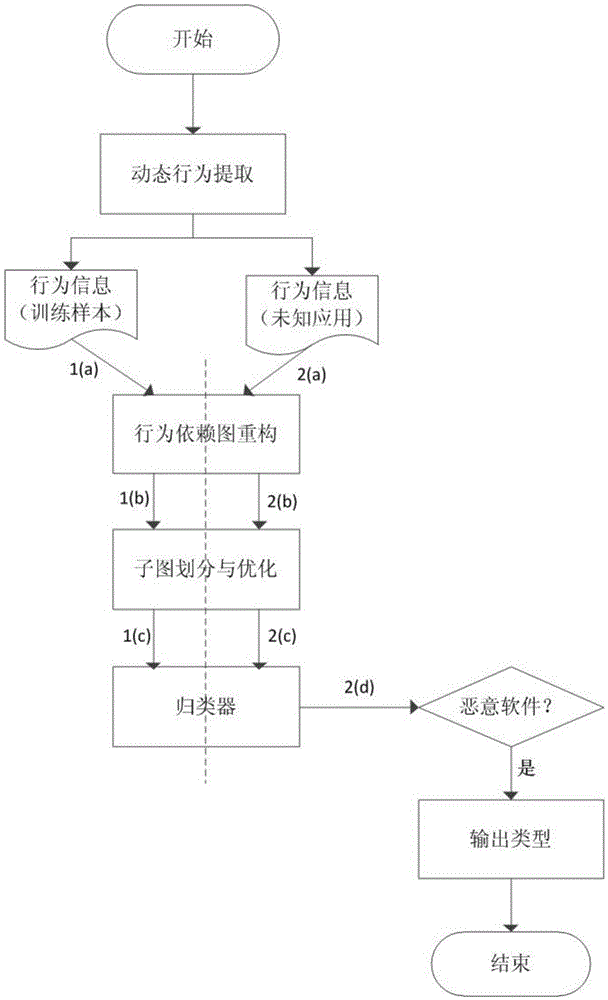
[0035] figure 1 It is a flow chart of steps of the Android malicious program classification method of the present invention, wherein 1(a), 1(b), 1(c) are the processing procedures of Android application training samples, 2(a), 2(b), 2( c) is the processing process of an unknown Android application. The method specifically includes the following steps:
[0036] 1) Dynamic behavior information extraction
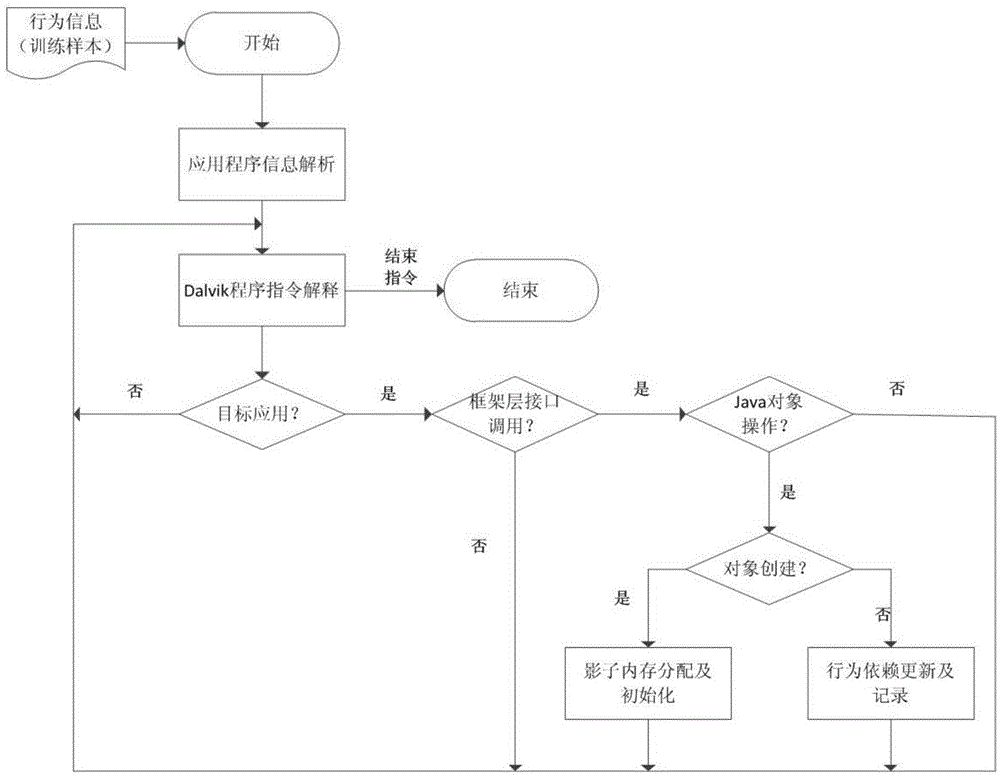
[0037] figure 2It is the basic process diagram for Dalvik sandbox to execute Android applications and extract behaviors and dependencies between behaviors. The Android application is first executed in a specially constructed execution sandbox, extracting its framework layer interface call behavior and the dependencies between the behaviors. In this process, the Java instruction interpretation process in the Dalvik virtual machine is in charge. When a fun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com