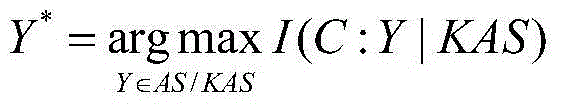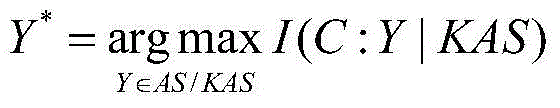Android malware detection method based on improved Bayesian algorithm
A Bayesian algorithm and malware technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as high false positive rate and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
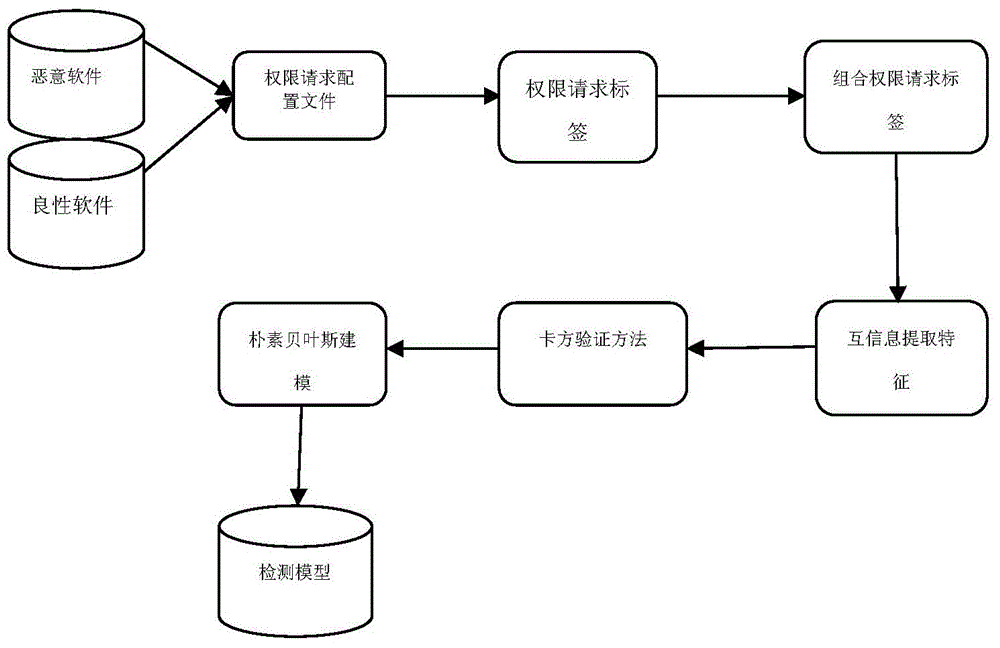
[0020] This method extracts permission request files from malicious software and benign software, and then counts the combination of every two permission request labels as a feature attribute, and then uses the concept of mutual information to extract feature attributes with the mutual information evaluation function. The basic task of feature extraction is to extract from many From the feature attributes, find out those feature attributes that have a significant impact on the classification, and select these features as the feature attributes of the classification. Then the chi-square test method is used to remove the influence of redundant permission request label combinations on malware detection, and finally the naive Bayesian algorithm is used to establish mathematical modeling and generate a detection model. The invention proposes a method for detecting Android malware based on the improved Bayesian algorithm, which is composed of three parts: data collection, data proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com