Function-call-based Android malicious code detection method
A malicious code detection and malicious code technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of building Android program behavior characteristics, inability to fine-grained and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
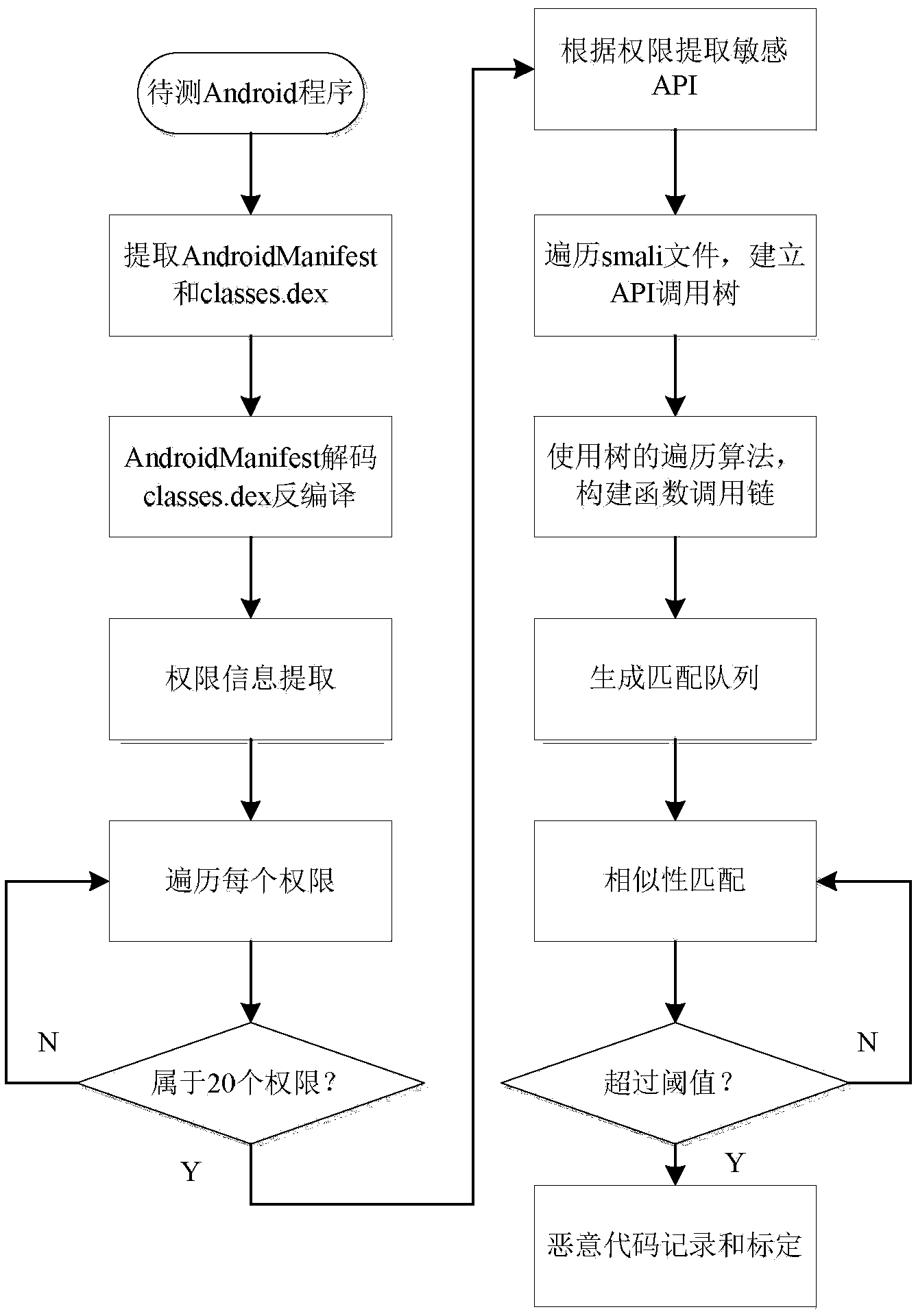
[0020] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0021] The overall idea of the present invention is to perform authority-based statistical analysis on the existing Android malicious code, extract the authority with high usage rate as sensitive authority, and then use the APIs that use these authorities as entry points to construct function chains that call these APIs, and perform Android malicious code detection based on function calls.
[0022] refer to figure 1 , in a specific embodiment, the present invention comprises the following steps:
[0023] The first step is to collect Android malicious code samples, conduct manual analysis, and extract key permissions and API functions that execute malicious behaviors. For example, malicious code with the function of sending SMS will apply for the SEND_SMS permission and use the sendTextMessage API.
[0024] The second step is to statisti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com