Permission-based Android malicious software hybrid detection method
A malware and detection method technology, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of unsatisfactory application detection effect, long detection time, false positive detection results, etc., to achieve behavior detection analysis method Perfect and accurate, fast detection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The specific embodiments of the present invention will be described in detail below with reference to the accompanying drawings. If these embodiments have exemplary contents, they should not be construed as limiting the present invention.
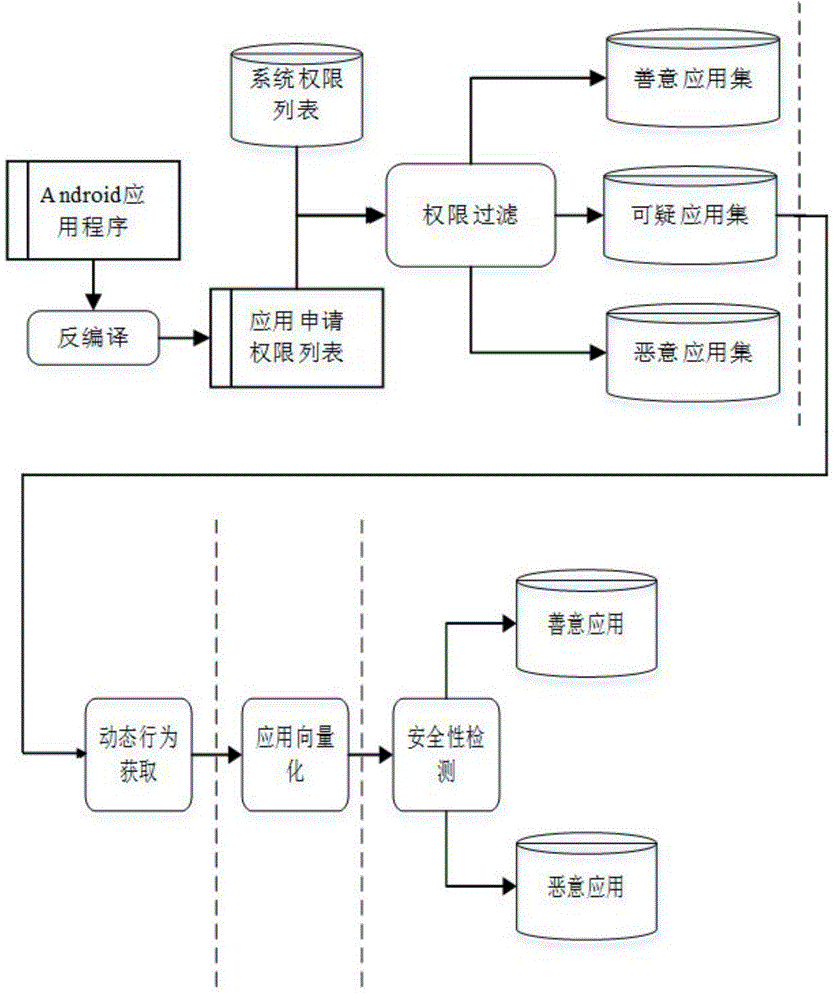
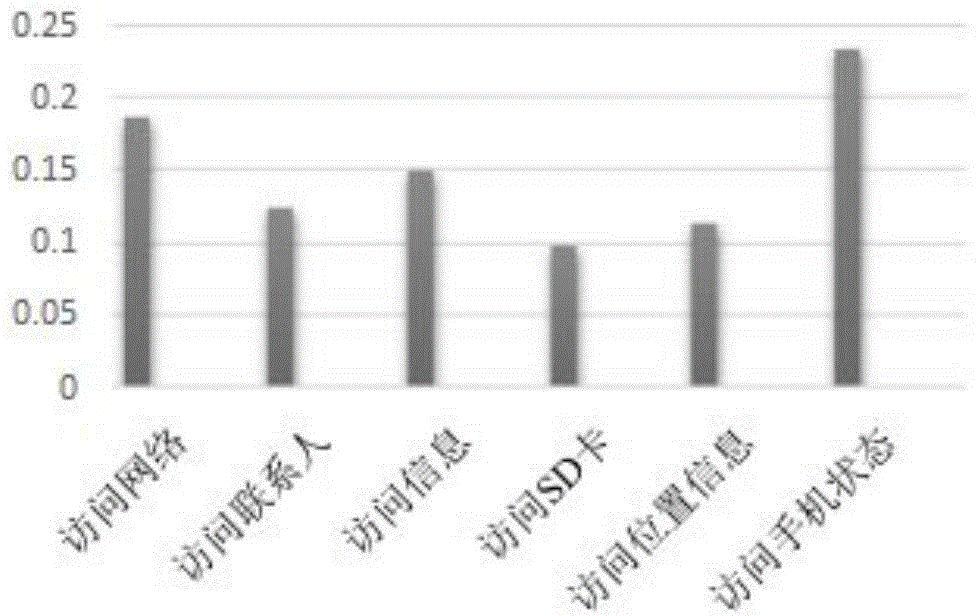
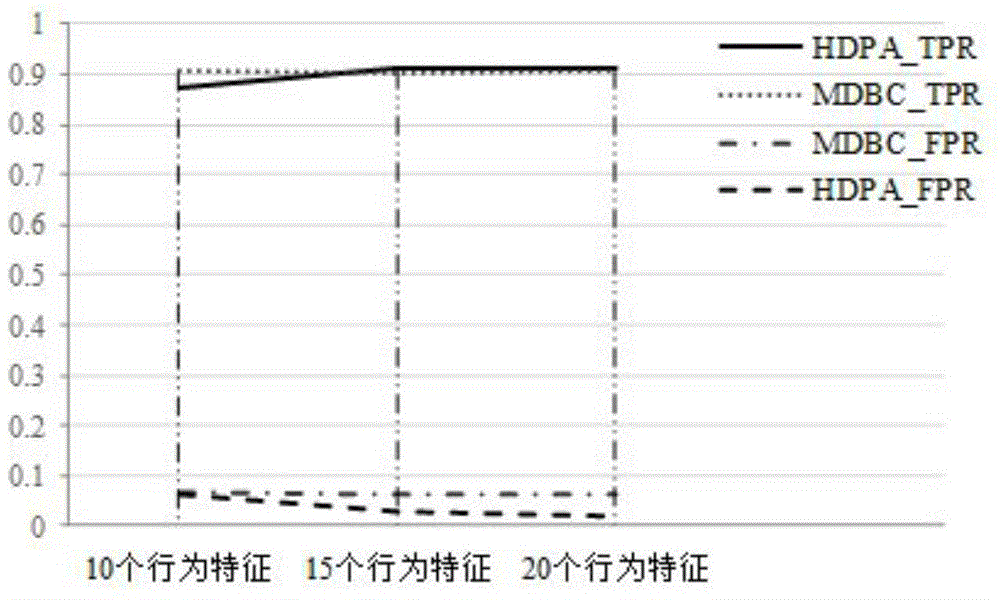
[0017] The present invention proposes a permission-based hybrid detection framework: 1) firstly perform preliminary detection according to the permission applied for by the application to detect benign applications and malicious applications; then track the behavior of suspicious applications, and collect interface calls related to sensitive permissions for detection , and then determine the application type; 2) Introduce a space vector model. When detecting suspicious applications, the application is algebraicized according to the collected sensitive information, and a vector space model is introduced to represent the application; 3) Euclidean distance and cosine similarity methods are used. The Euclidean distance and cosine similar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com