Method and system for preventing and detecting security threats
A technology for security, security software, applied in the field of security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] While applicable to any mobile phone, game console, tablet, set-top box, television, or other consumer electronic device, the embodiments described herein will be based on such an device. In particular, the preferred embodiments will be shown and described with respect to the Android® OS for illustrative purposes only and should not be construed to limit the intended scope of the present disclosure. In fact, some of the advantages described in terms of preventing the installation of rootkits or probing the weaknesses of the OS are generally applicable to any device OS where there is a risk to any open device due to the inherently greater security risks associated with such an open device. special use.
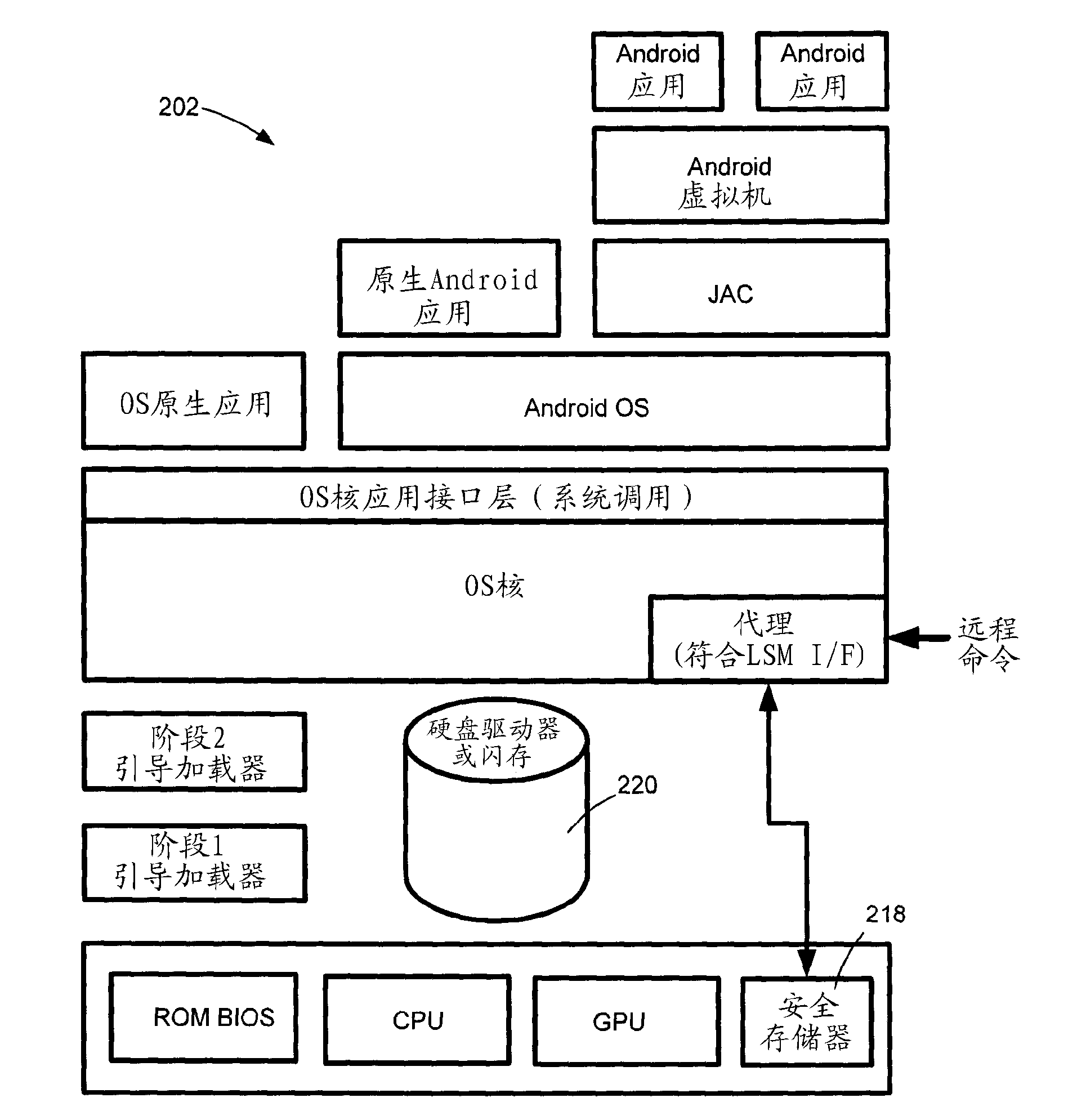
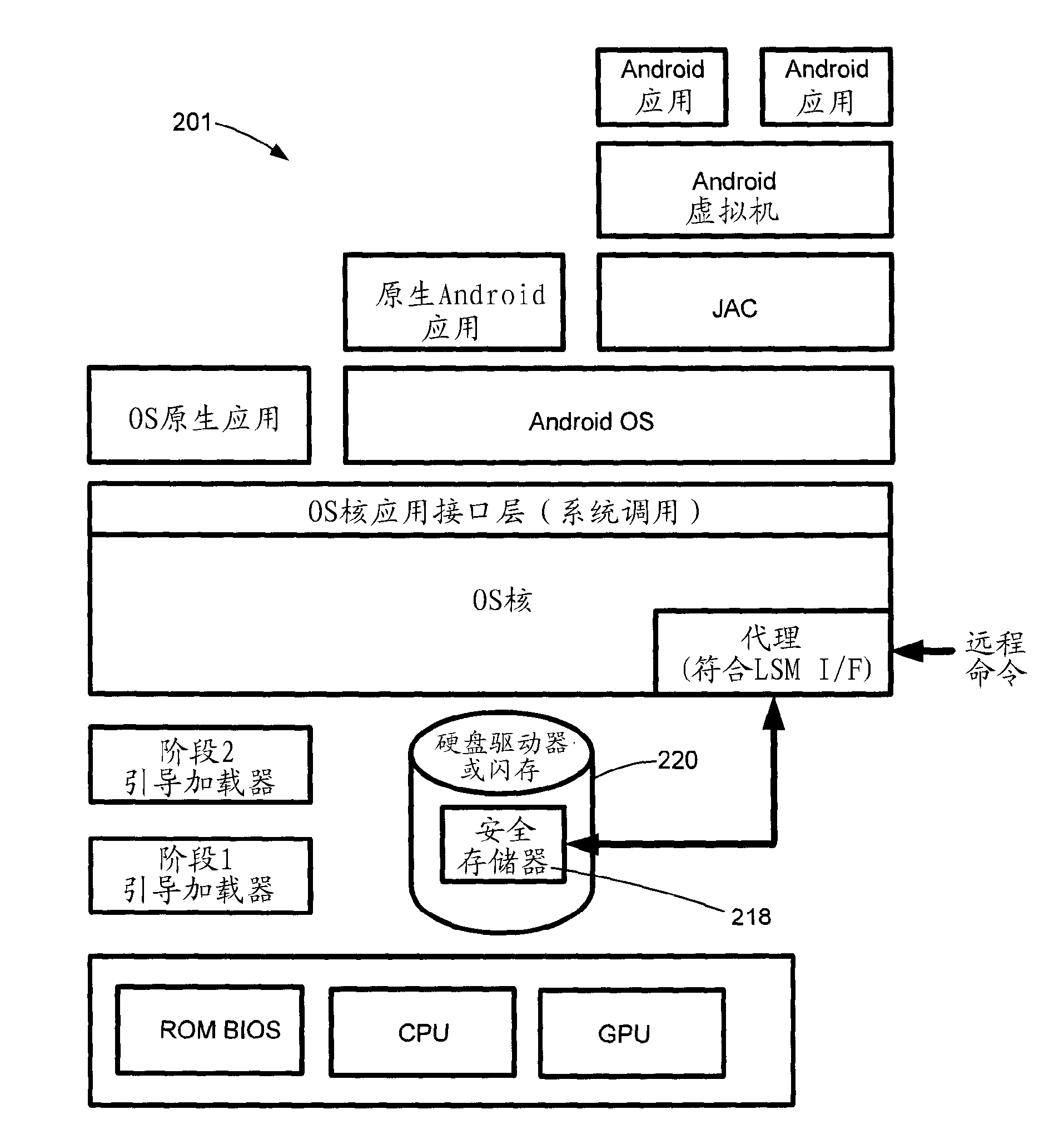
[0046] refer to Figure 2A -C, an overall layer diagram 200 of the Android™ OS environment showing the basic structure of the layered execution stack. Base layer 219 involves typical system-on-chip (SOC) components, including the central processing unit (CPU), graphic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com