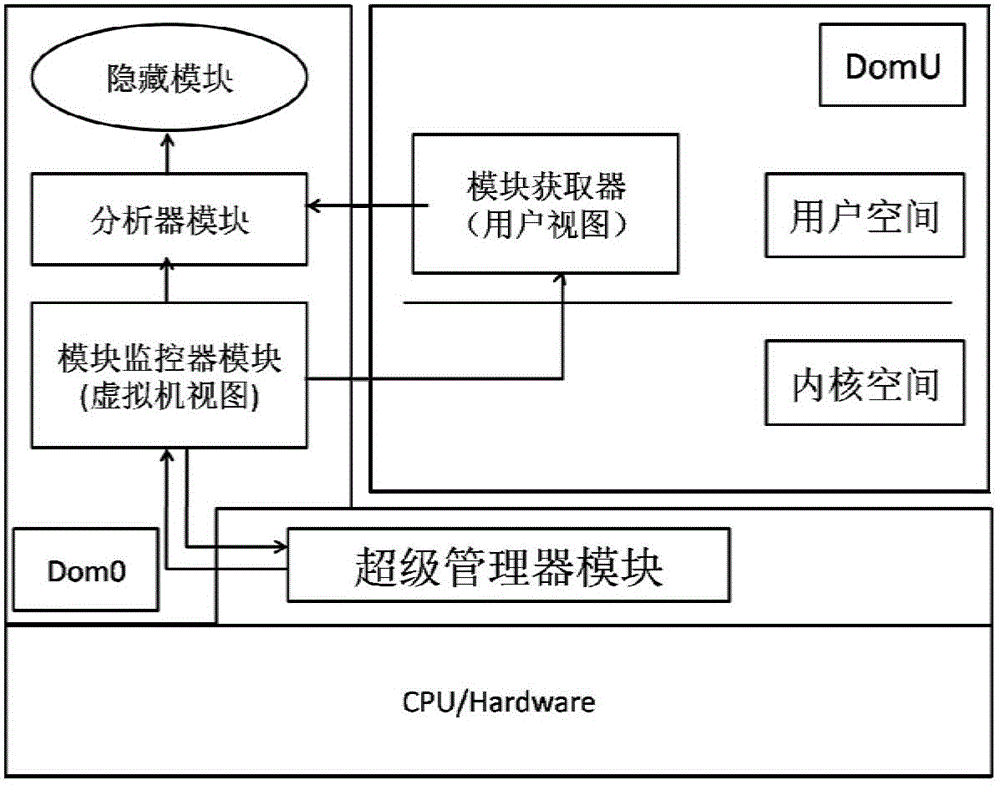
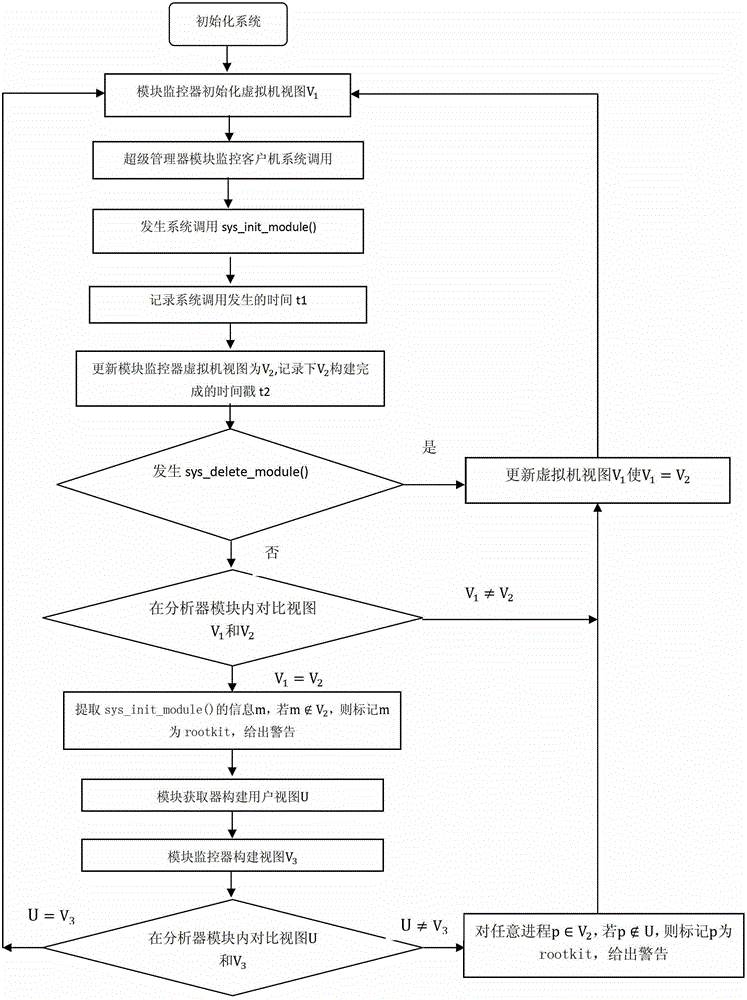
Kernel state rootkit detection method based on system virtualization technology
A technology of virtualization technology and detection method, which is applied in the field of rootkit detection technology in the kernel state, can solve problems such as failure of detection tools, and achieve the effect of ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
[0026] The meanings of the English abbreviations in this article are as follows:
[0027] 1) Rootkit: Rootkit is a special kind of malicious software. Its function is to hide information such as itself and specified files, processes, and network links on the installation target. What is more common is that Rootkits are generally related to Trojan horses, backdoors, etc. Malicious programs are used in combination. Rootkits modify the system kernel by loading special drivers to achieve the purpose of hiding information.
[0028] 2) LKM (Linux Kernel Module): Linux kernel module refers to a program that can be dynamically loaded into the Linux system kernel.
[0029] 3) LKM Rootkit: refers to the Rootkit that can be directly loaded into the Linux system kernel, that is, the rootkit in kernel mode.
[0030] 4) module_list: a list of modules (drivers), which records the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com