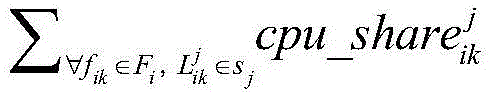Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
126 results about "System virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
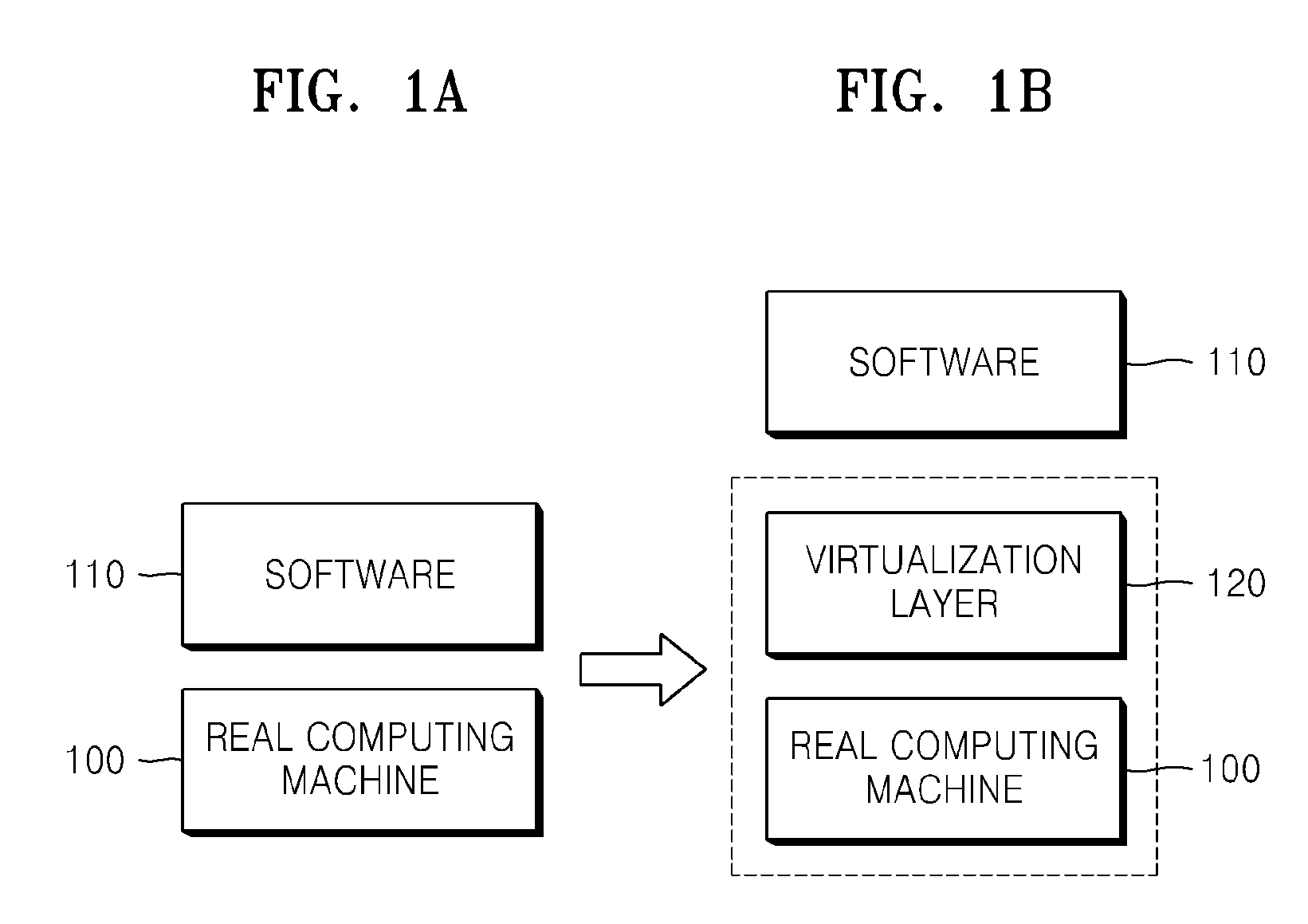
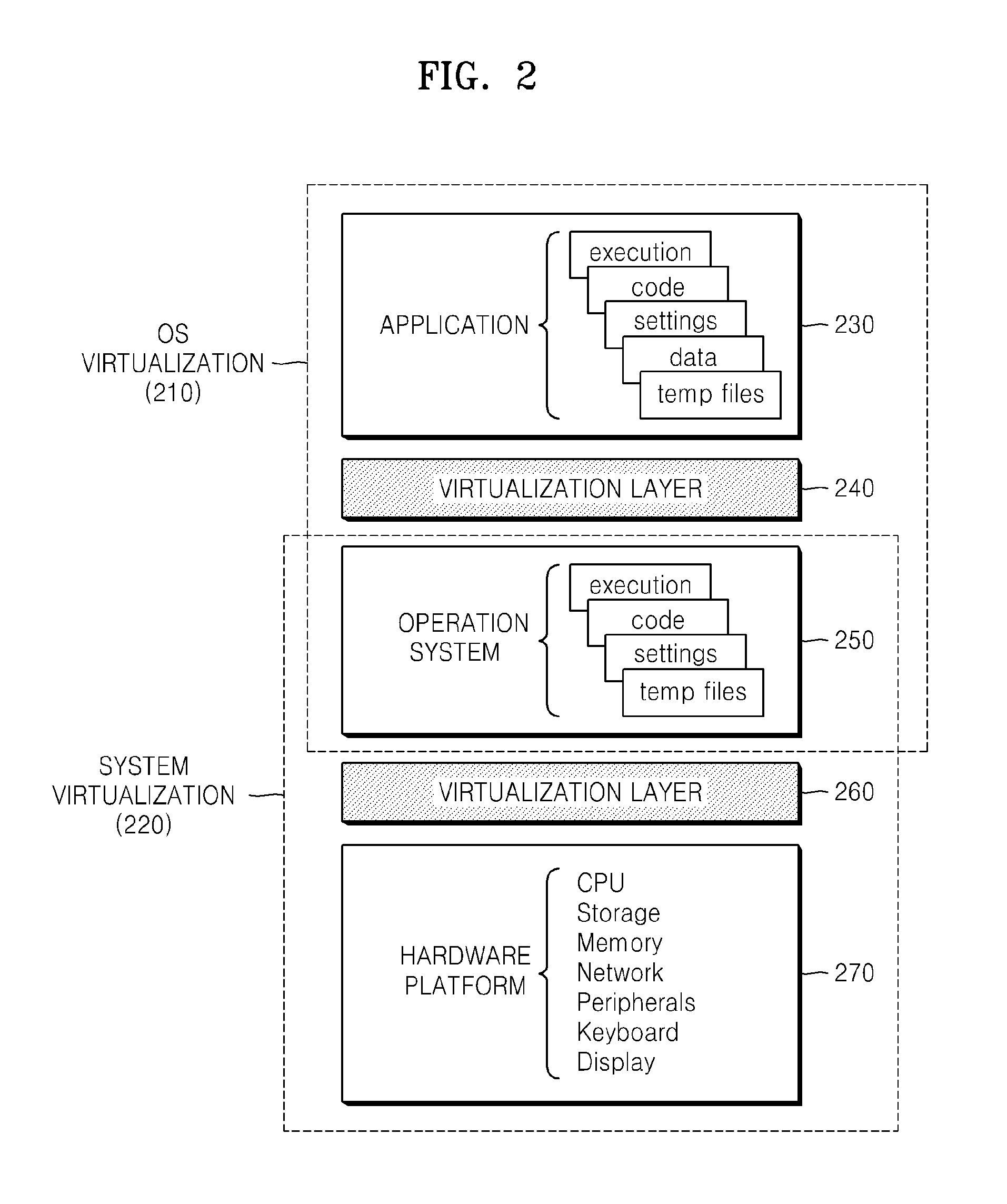
Operating system virtualization (OS virtualization) is a server virtualization technology that involves tailoring a standard operating system so that it can run different applications handled by multiple users on a single computer at a time. The operating systems do not interfere with each other even though they are on the same computer.
Network consolidation for virtualized servers
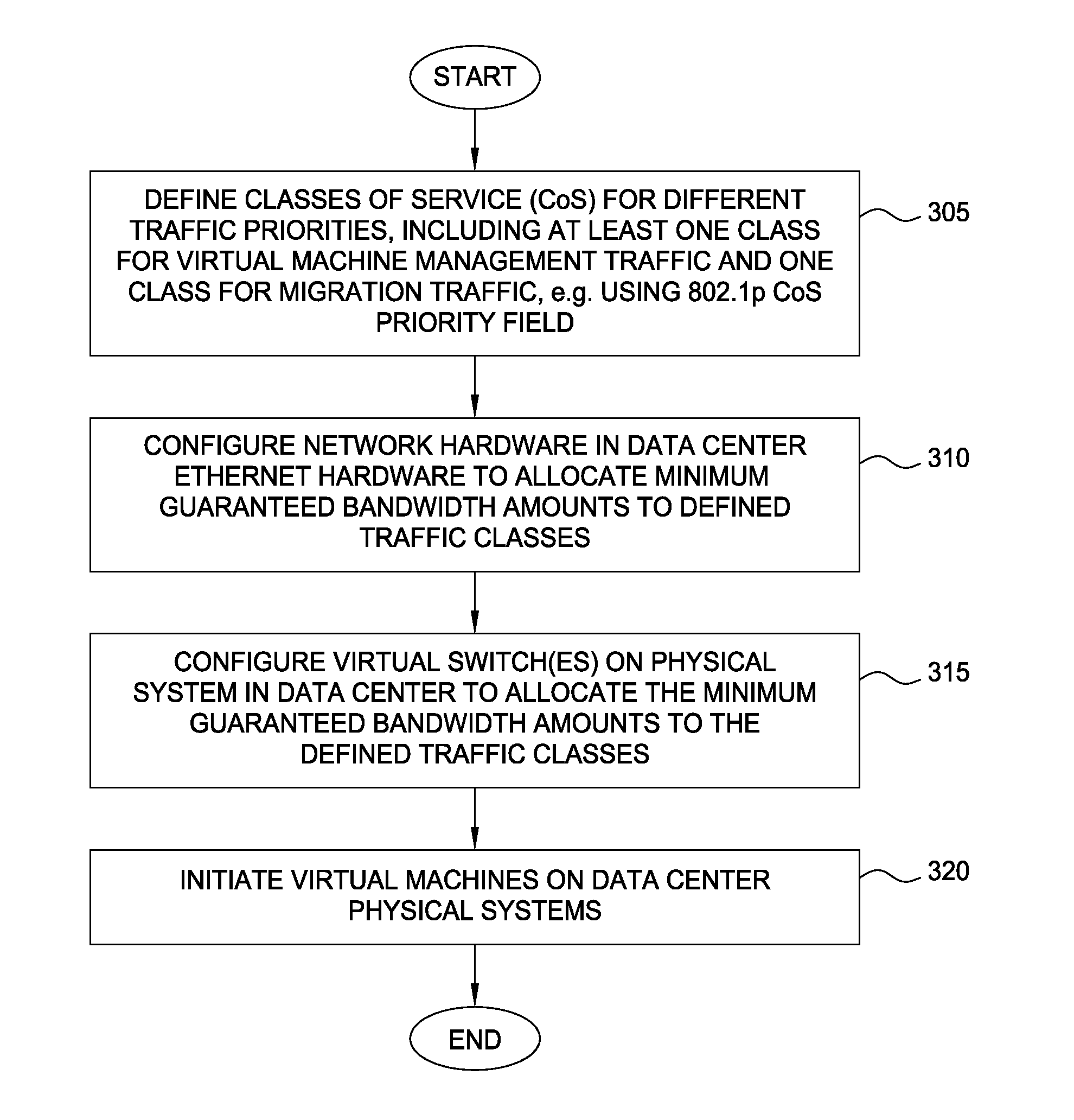
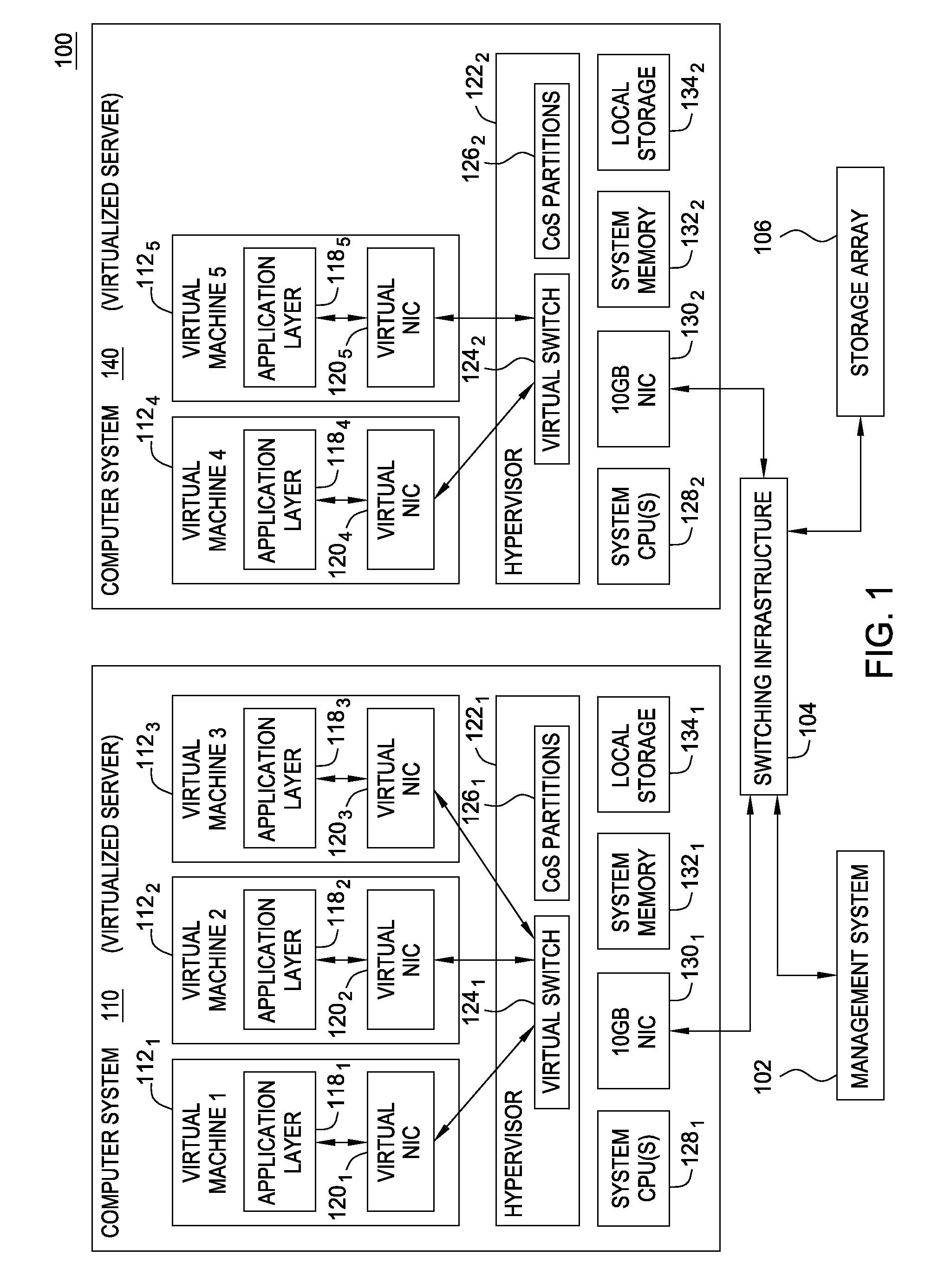
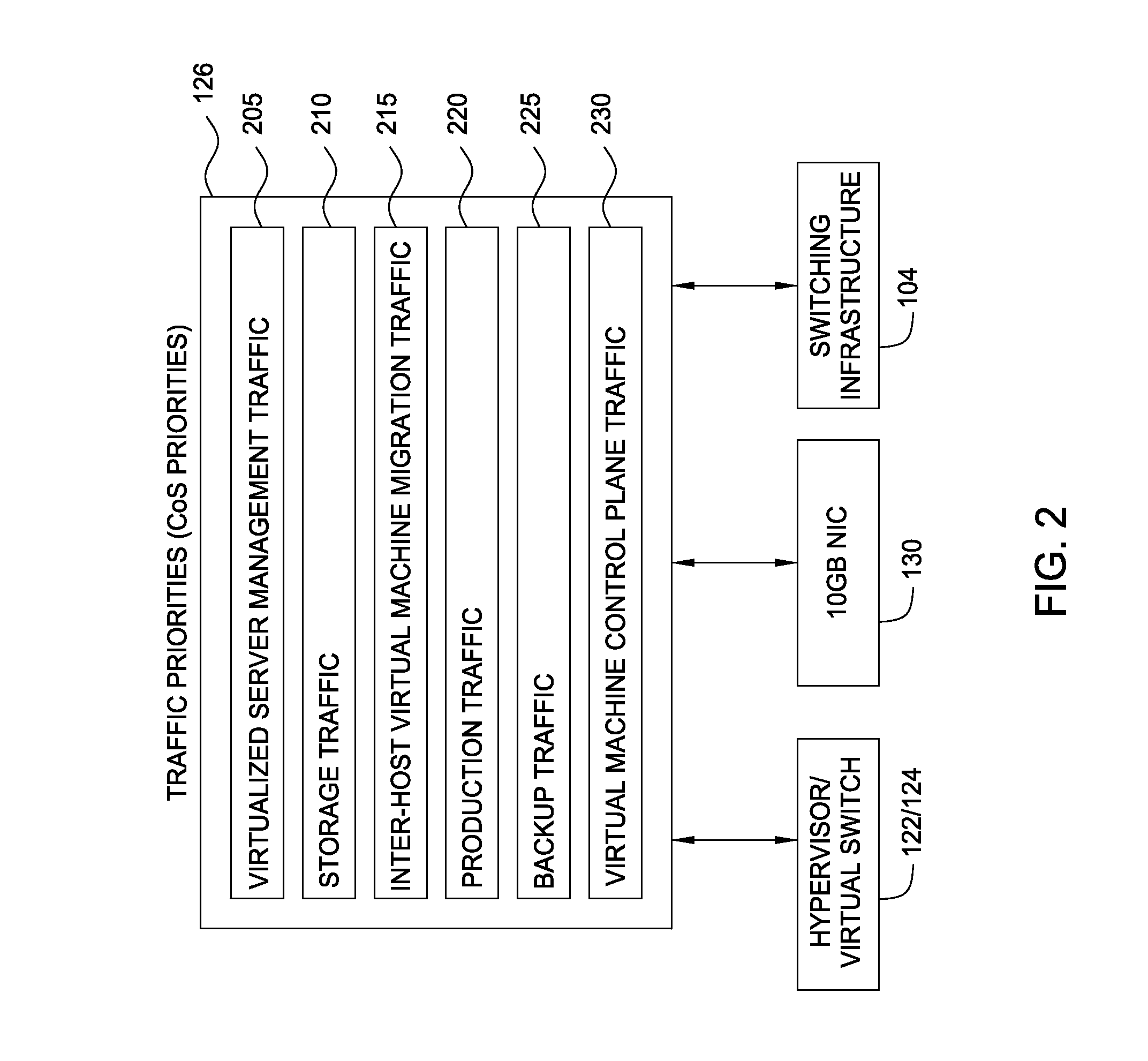
Techniques are disclosed for virtualized server kernel and virtual networks consolidation. The network consolidation allows a data center to migrate from an infrastructure that uses multiple dedicated gigabit Ethernet Network Adapters to manage system virtualization and migration to an infrastructure using consolidated, redundant, 10 gigabit Ethernet adapters. Different priority classes may be defined for different classes of network traffic such as hypervisor management traffic, inter-host virtual machine migration traffic, virtual machine production traffic, virtualized switching control plane traffic, etc. Further, an enhanced transmission standard may be used to specify a minimum bandwidth guarantee for certain traffic classes. Thus, the hypervisor management and inter-host virtual machine migration traffic may be transmitted, even the presence of congestion.
Owner:CISCO TECH INC
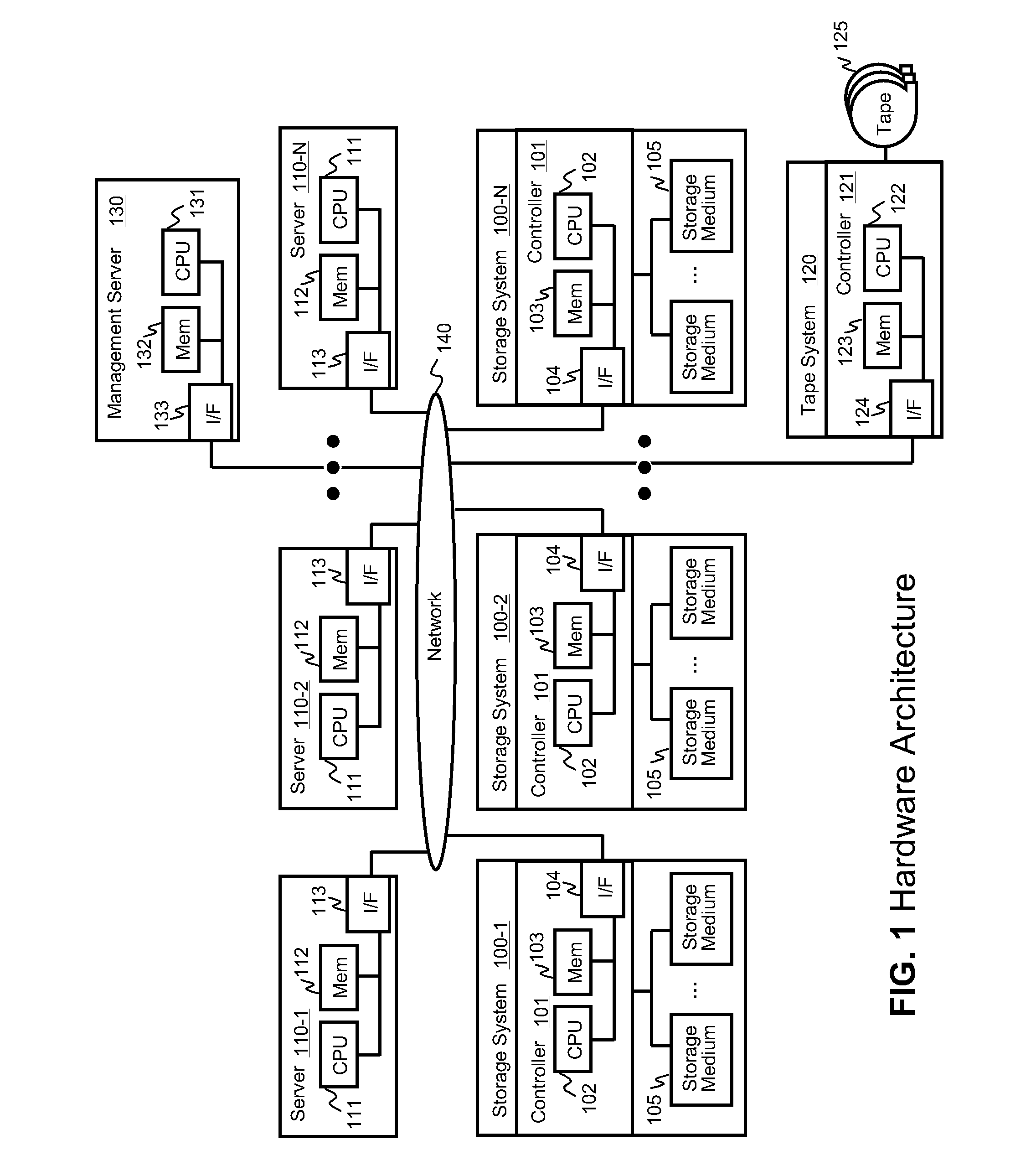
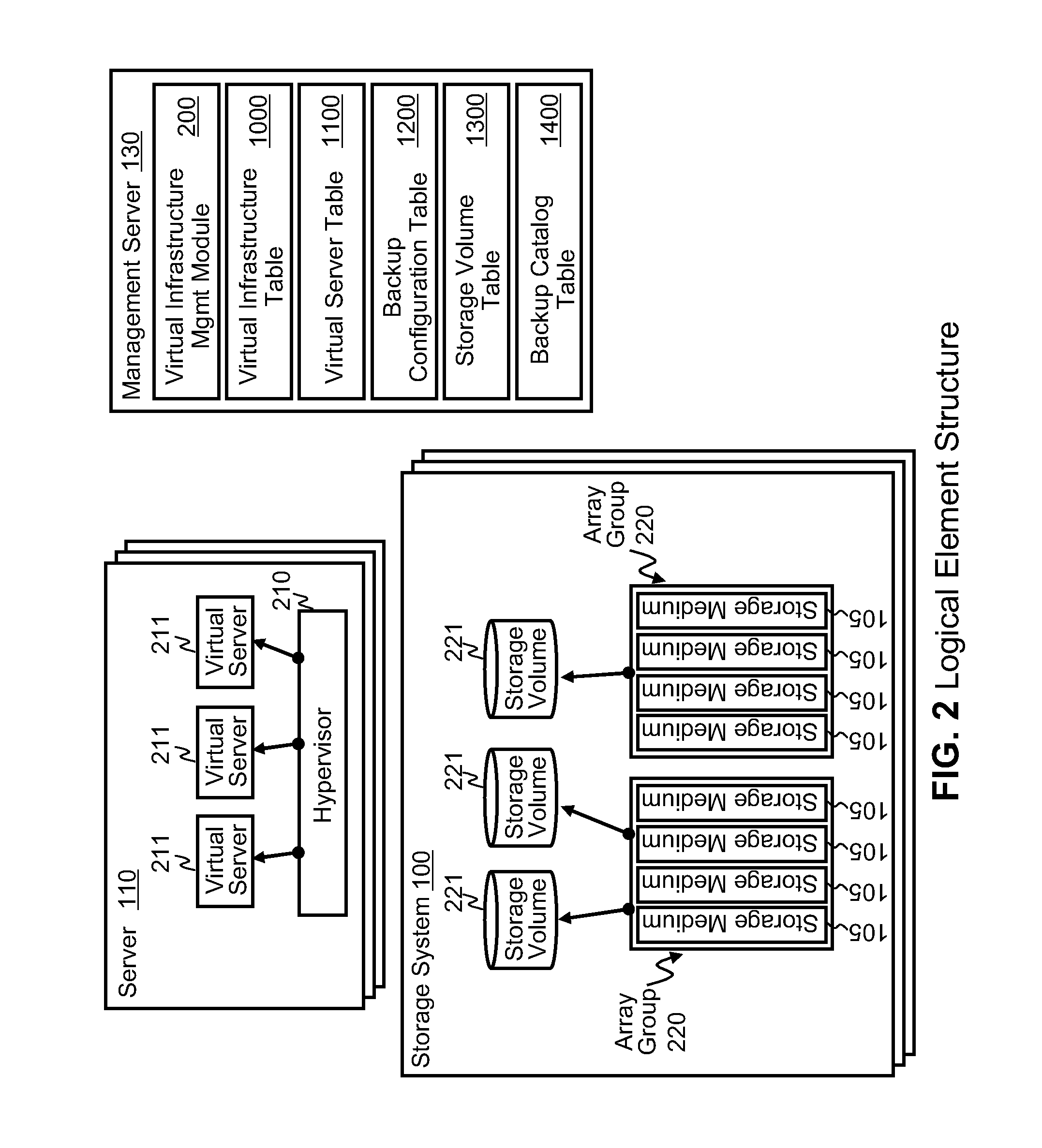
Data backup system and method for virtual infrastructure
InactiveUS20100125712A1Reduce in quantityMinimize the numberMemory loss protectionDigital data processing detailsResource poolData center
Systems for backing up the data of an IT system by utilizing server or storage virtualization technology to create and move logical IT infrastructures dynamically. A virtualized IT system provides a server resource pool and a storage resource pool composed from multiple physical devices either within a datacenter or a globally located plurality of datacenters. The virtual server and the storage volume provisioned from those pools will be paired to form the virtual infrastructure. In other words, the virtual infrastructure becomes a logical IT environment build with the required computing and storage resources needed in order to execute specific applications. The virtual infrastructure can also be migrated within / among datacenter sites.
Owner:HITACHI LTD
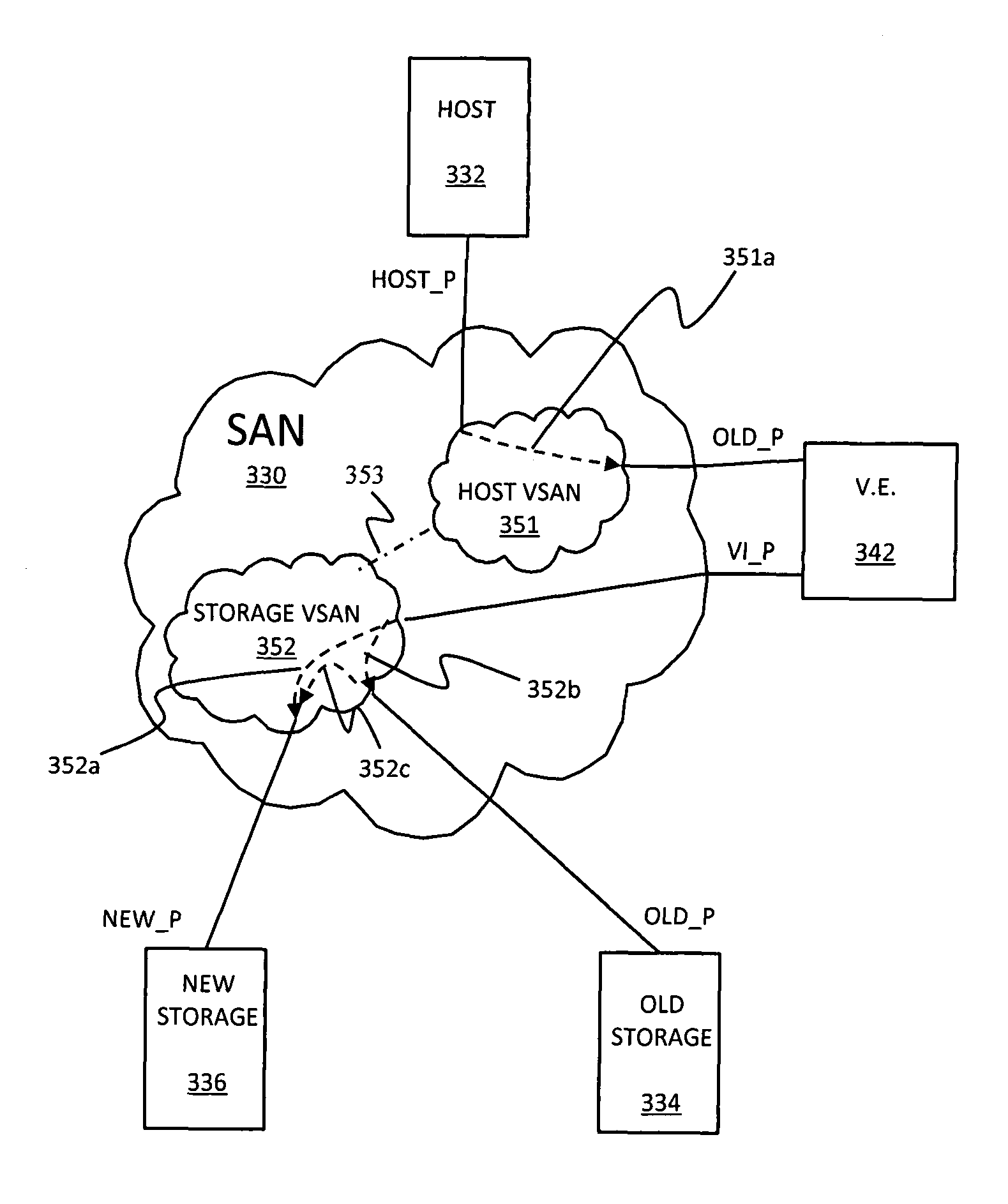
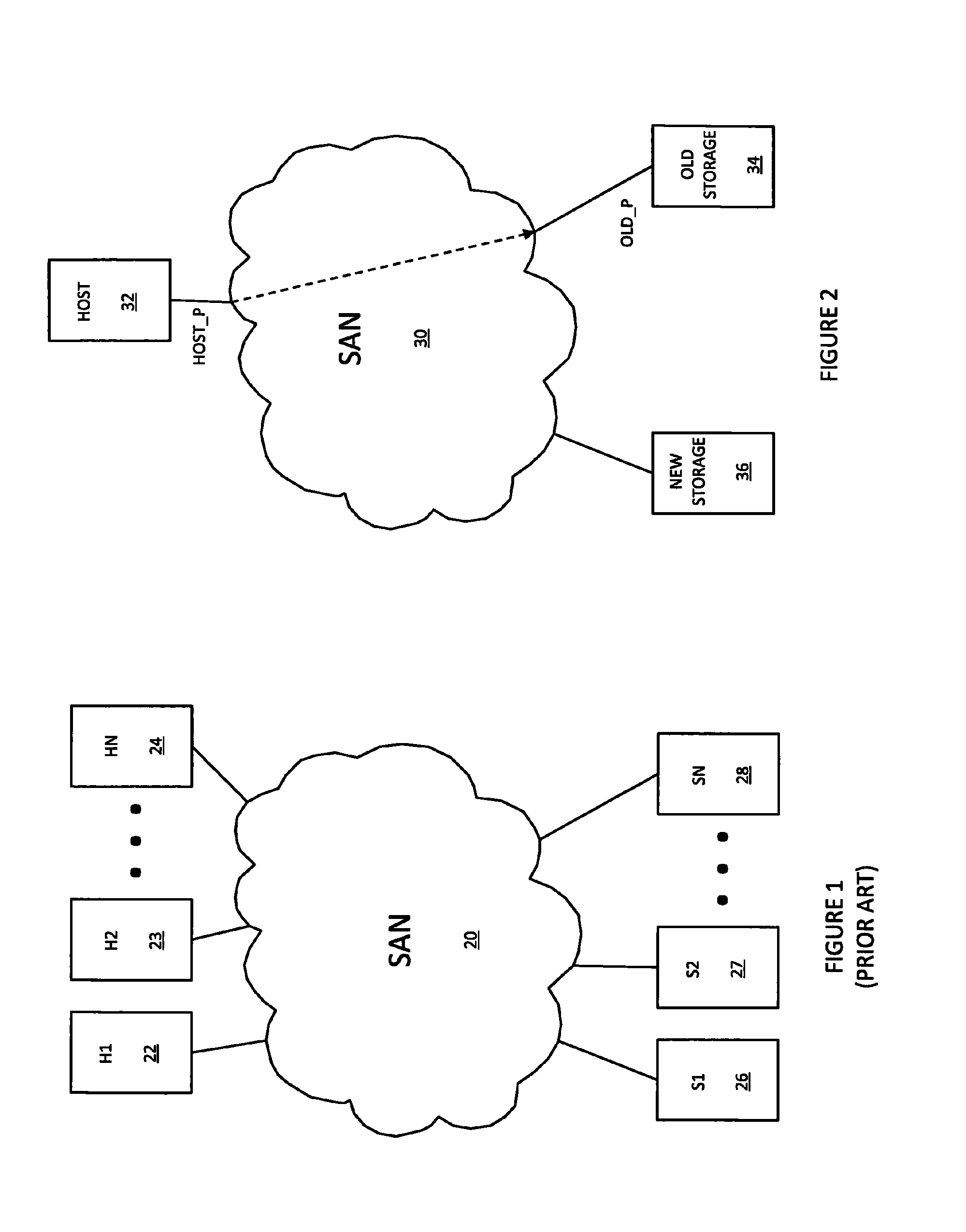
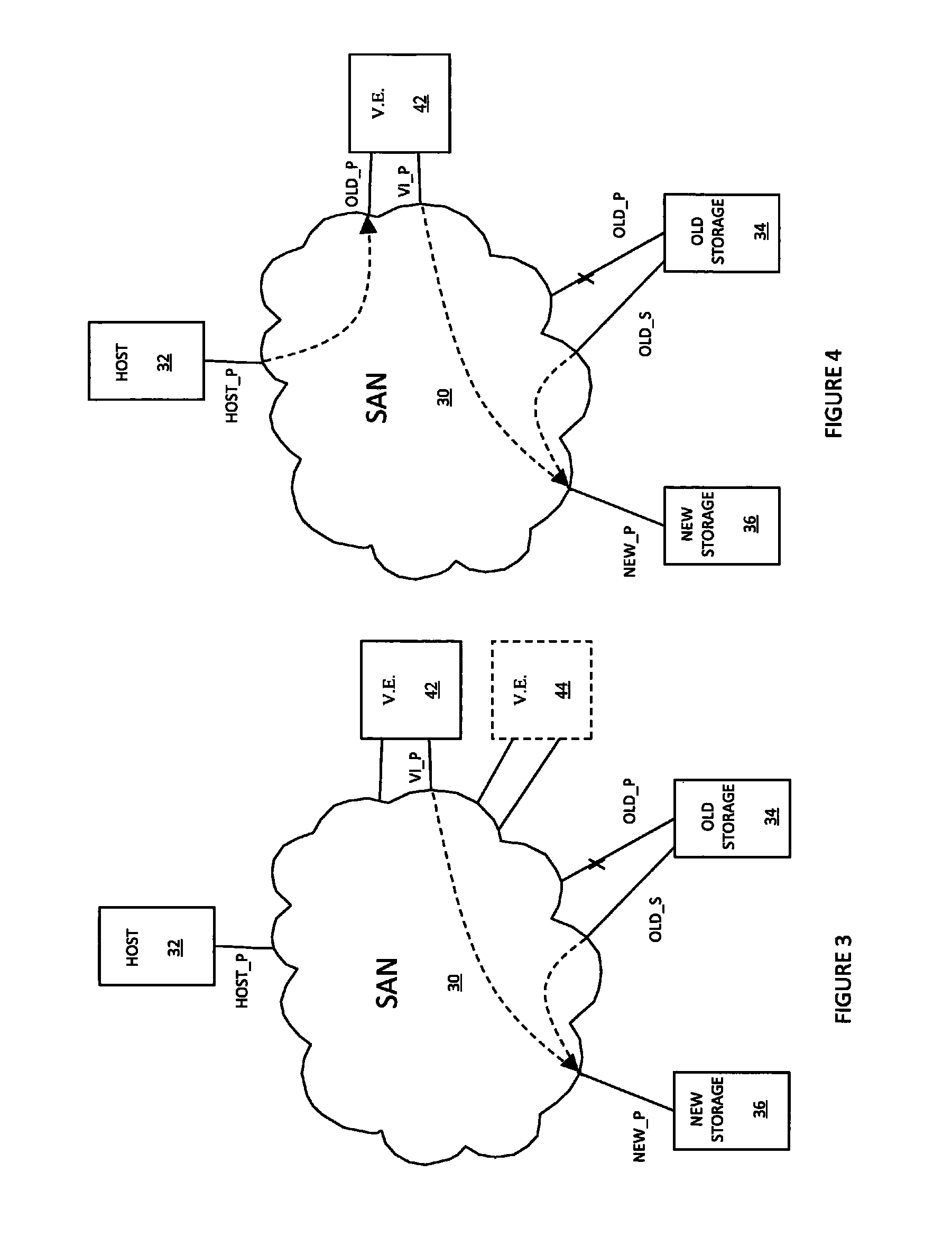
Non-disruptive data mobility using virtual storage area networks with split-path virtualization
ActiveUS8028062B1Computer security arrangementsMultiple digital computer combinationsArea networkName server
A system creates a storage area network (SAN) centric storage virtualization layer in front of storage devices. The system allows data mobility and migration without disruption to the one or more host servers attached to the SAN. Specifically, the host servers are not disrupted when switching I / Os between physical and virtual storage, for example, by taking advantage of WWPN spoofing and Fibre Channel VSAN technology. The use of VSANs effectively allow multiple virtual directors and / or switches to be created within a physical director and / or switches, each with their own separate name server, thereby providing complete isolation from one another. The host-storage pathing information is unchanged as the original physical storage port's WWPNs are spoofed by the virtual storage port. The result is two identical WWPNs within the SAN which is normally disallowed; however, by separating the physical port WWPN into one VSAN and the virtual port WWPN into another, the restriction may be circumvented.
Owner:EMC IP HLDG CO LLC
Control method of device in storage system for virtualization
InactiveUS20070055840A1Memory systemsInput/output processes for data processingVirtualizationData storing
In a system where a first storage system and a second storage system are connected to a third storage system, when the first storage system virtualizes and provides a device in the third storage system as a device in its own storage system, update data stored in a cache in the first storage system is written into the device of the third storage system to be reflected, attributes of the device are transferred to the second storage system, and the second storage system virtualizes the device of the third storage system as a device of its own storage system.
Owner:HITACHI LTD
Virtual machine scheduling method for public cloud platform
ActiveCN102307133AQuick responseSolve the problem that is easy to cause congestionData switching networksSoftware simulation/interpretation/emulationService efficiencyComputing systems
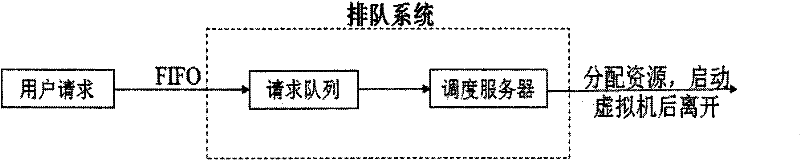
The invention belongs to the technical field of computing system virtualization, and particularly relates to a virtual machine scheduling method for a public cloud platform. The technical scheme is that: a plurality of scheduling servers are set to process user requests. By the multi-scheduler scheduling method, the optimization of platform resources and the setting of virtual machine migration, the problem that congestion is easy to cause by a single-scheduler scheduling method is effectively solved; a quick response to the user request can be made to improve service efficiency; and the method can be widely applied to the virtual machine scheduling of the public cloud platform.
Owner:G CLOUD TECH
Integrated intrusion deflection, detection and introspection
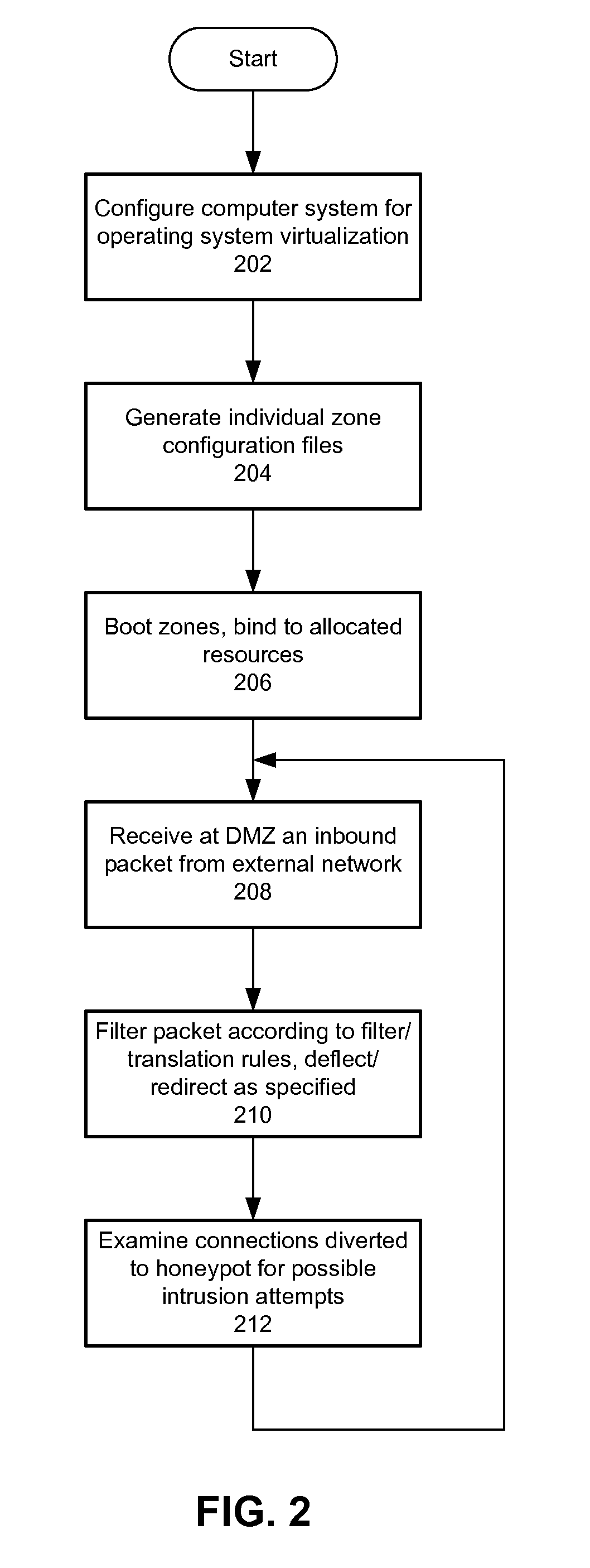
ActiveUS20110067107A1Easy to manageImprove securityError preventionFrequency-division multiplex detailsVirtualizationLimited resources
Methods and apparatus are provided for integrated deflection, detection and intrusion. Within a single computer system configured for operating system virtualization (e.g., Solaris, OpenSolaris), multiple security functions execute in logically independent zones or containers, under the control and administration of a global zone. Such functions may illustratively include a demilitarized zone (DMZ) and a honeypot. Management is facilitated because all functions work within a single operating system, which promotes the ability to configure, monitor and control each function. Any given zone can be configured with limited resources, a virtual network interface circuit and / or other features.
Owner:ORACLE INT CORP
Method for intensively storing and backing up data based on operating system virtualization theory
InactiveCN102214127ASignificant progressIncrease profitTransmissionSoftware simulation/interpretation/emulationVirtualizationOperational system
The invention relates to a method for intensively storing and backing up data based on an operating system virtualization theory in the technical field of computer application. The method is characterized by comprising the following steps of: constructing one to a plurality of virtual isolation environments on a host operating system of a physical host machine, wherein each virtual isolation environment has a use mode which is totally the same as the use mode of the host operating system; and completely isolating data produced in the virtual isolation environment from data produced by the host operating system, and storing the data to different physical storage positions respectively. By storing an application program relative to a working service of a user into the virtual isolation environment and running the application program, and redirecting the physical storage position to a storage server in a network through a common internet file system (CIFS) or internet small computer system interface (iSCSI) protocol, a manager only needs to back up the data on the storage server at a time when the data of all client hosts are needed to be backed up, so the working efficiency is improved greatly; meanwhile, only the data relative to the working service is backed up, so the backup storage space is saved and useless data restoration is avoided.
Owner:上海安纵信息科技有限公司
Apparatus and system for providing software service using software virtualization and method thereof
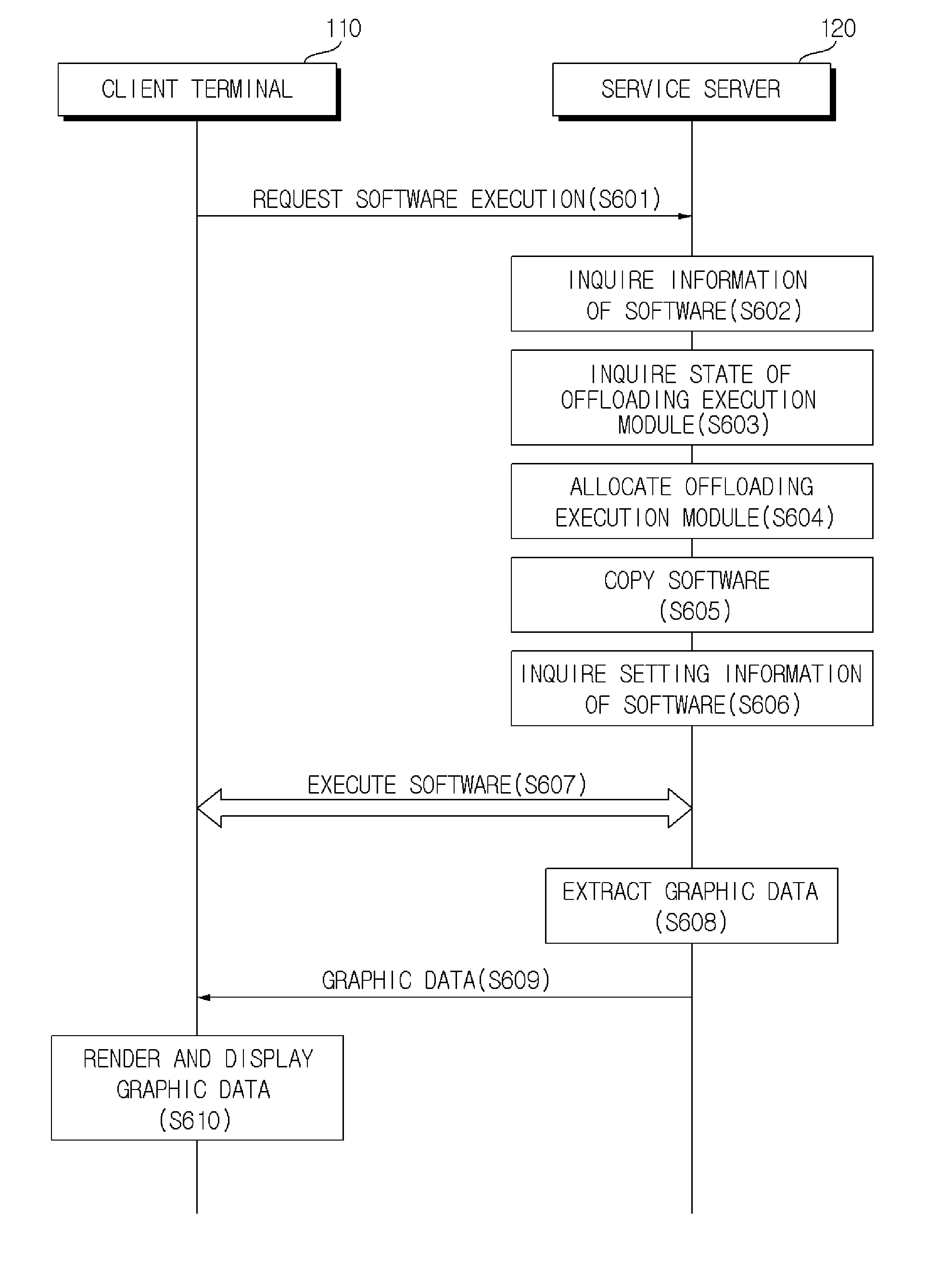
InactiveUS20140143305A1Easy to manageMaximize availabilityMultiple digital computer combinationsProgram controlGraphicsCommunication unit
Provided are an apparatus and a system for providing a software service, using software virtualization, and a method thereof. The apparatus for providing a software service, using software virtualization, includes: an input unit receiving information according to operation of a menu or keys from a user; a communication unit interlocking to a service server implemented to execute software in a virtual execution environment in accordance with the received information; a control unit receiving graphic data of the software executed in the interlocking service server, performing rendering on the received graphic data with its own graphic processing unit, and generating a video as the result of rendering; and a display unit displaying the generated video.
Owner:ELECTRONICS & TELECOMM RES INST
Docker Swarm cluster resource scheduling optimization method based on load prediction
ActiveCN107045455AImprove performanceAvoid resource competitionProgram initiation/switchingResource allocationVirtualizationResource utilization
The invention discloses a Docker Swarm cluster resource scheduling optimization method based on load prediction and belongs to the technical field of computer system virtualization. The Docker Swarm cluster resource scheduling optimization method based on load prediction comprises the steps of utilizing an API interface function of a docker daemon to periodically collect resource historical use amount of a container; utilizing an ARIMA-RBF model to model and predict the resource historical use amount, obtaining resource future usage amount and combining resource current use situation to adjust resource use upper limit and resource use authority limit; determining a resource use deviation degree of the container according to the resource historical use amount of the container; choosing a node with the most balanced resource use deviation according to the container and a resource use deviation degree of a node set capable of meeting a container resource requirement to deploy a new container after the container is added when the new container is started in a cluster. The Docker Swarm cluster resource scheduling optimization method disclosed by the technical scheme of the invention improves Docker Swarm cluster resource utilization rate and can improve actual operation performance of all the containers.
Owner:HUAZHONG UNIV OF SCI & TECH
Storage pool building method and system
InactiveCN106201357AImplement the buildMeet performance needsInput/output to record carriersSpatial integrationData virtualization
The invention discloses a storage pool building method and system. The method comprises the steps that a storage environment is set up; LUN mapping is created, and a host scans LUN mapping to conduct initialization; management service of a storage pool is conducted by means of sanlock service and agent service; a storage pool command is created by means of LVM, a corresponding physical volume and volume group are created for each LUN separately, the LUNs are in one-to-one correspondence with the LVM storage pools, a logical volume is created, and lockspace of the sanlock service is initialized according to an incoming path of the logical volume; a lightweight storage pool building method is achieved; for storage virtualization, hardware resource storing is shown in an abstraction mode, scattered storage spaces are integrated, and partition and distribution are conducted again to meet the requirements of different applications on performance and capacity. Meanwhile, data security of backup of stored data, failure recovery and the like can be planed uniformly.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
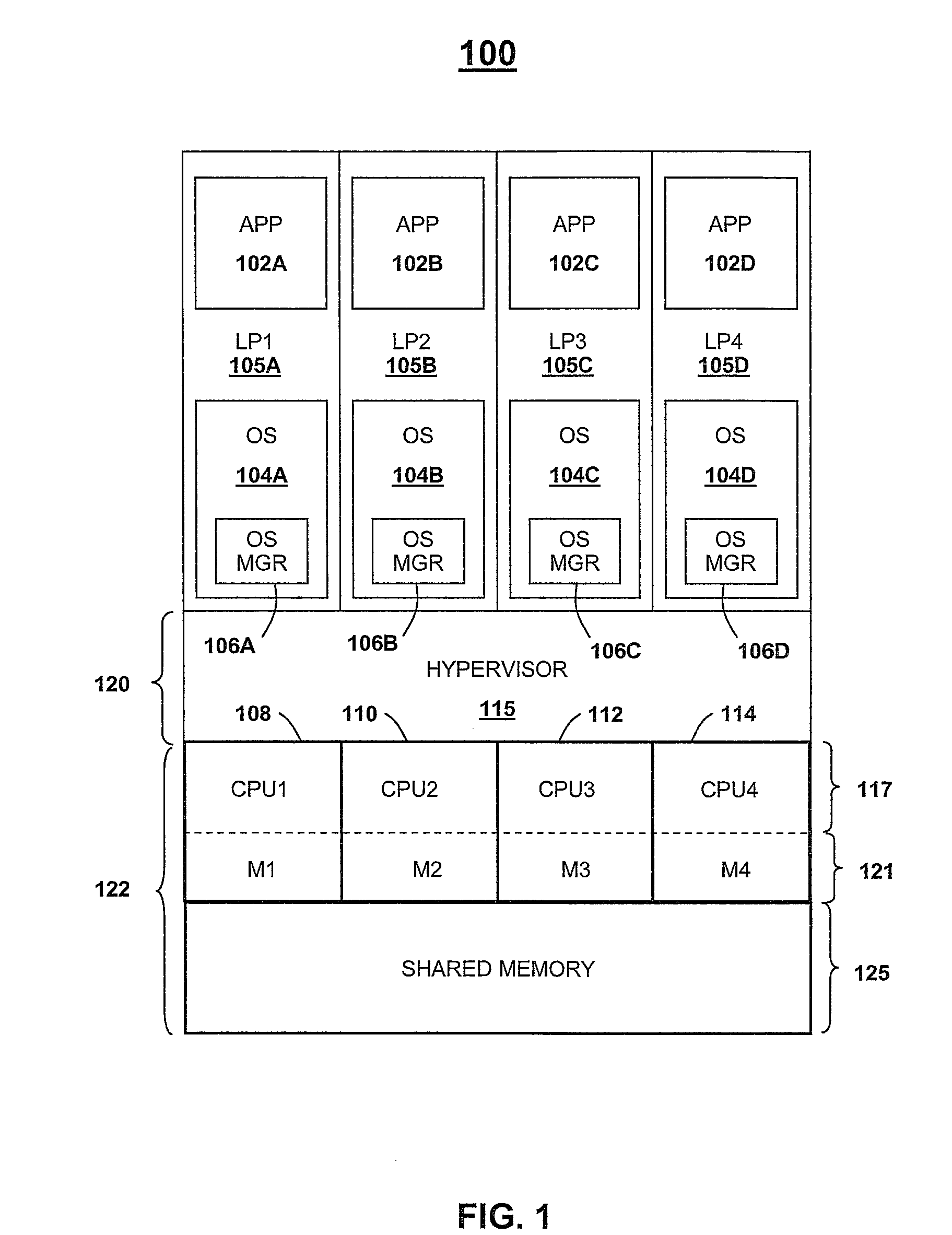
Workload management in virtualized data processing environment
ActiveUS7698531B2Error detection/correctionDigital computer detailsVirtualizationComputerized system
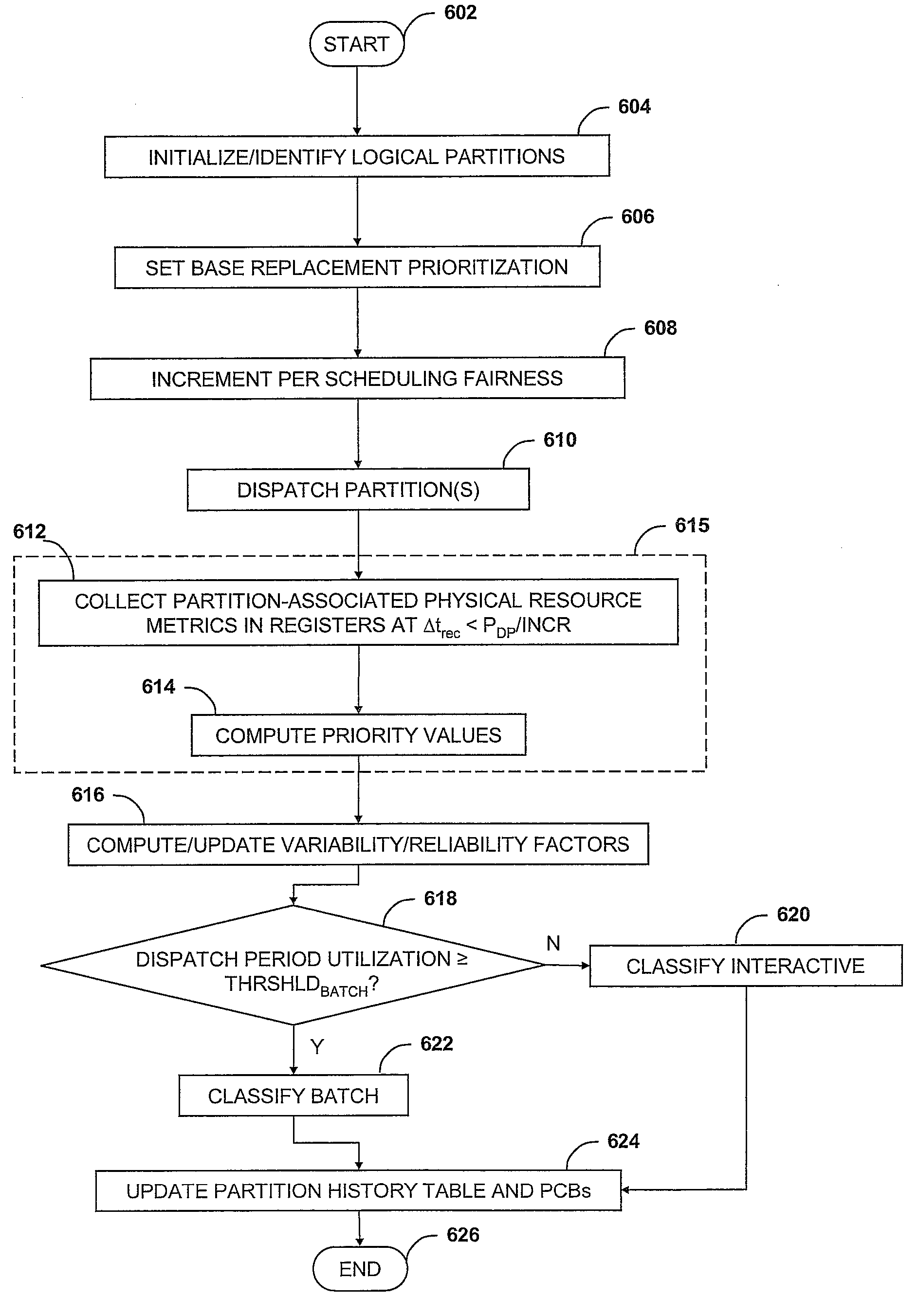
A system, method and computer-readable medium for balancing access among multiple logical partitions to the physical system resources of a computer system employing system virtualization. Each of the logical partitions is classified, initially during a startup period, in accordance with a level of allocated dispatch window utilization. Performance metrics of one or more of the physical system resources are determined in association with one or more of the logical partitions. The performance metrics determination is performed at a hardware level independent of programming interrupts. During a dispatch window in which a given set of the physical system resources are configured for allocation to one of the logical partitions, the given set of physical system resources are re-allocated to a replacement logical partition in accordance with the determined performance metrics associated with the replacement logical partition and the dispatch window utilization classification of the replacement logical partition.
Owner:INT BUSINESS MASCH CORP
A virtual computer cluster and its implementation method
InactiveCN102271145ALow costImprove efficiencyNetworks interconnectionVirtualizationComputer cluster
The invention relates to the technical field of computing system virtualization, in particular to a virtual computer cluster and an implementation method thereof. Including a front-end machine and several cluster nodes, the front-end machine is a virtual machine or a physical machine; the cluster node is a virtual machine node or a physical machine node; the front-end machine is connected to the cluster node and the cluster node through a physical or virtual network card . During the cluster implementation process, the cluster management software is installed on the front-end computer, and the node monitoring program is installed on each node to construct a software system of virtual computer cluster. The cluster and its implementation method of the present invention provide a single virtual resource expansion method to support occasions where users have special requirements for computing resources, storage resources, security and stability of computing systems. It can be widely used in computer virtualization technology.
Owner:G CLOUD TECH
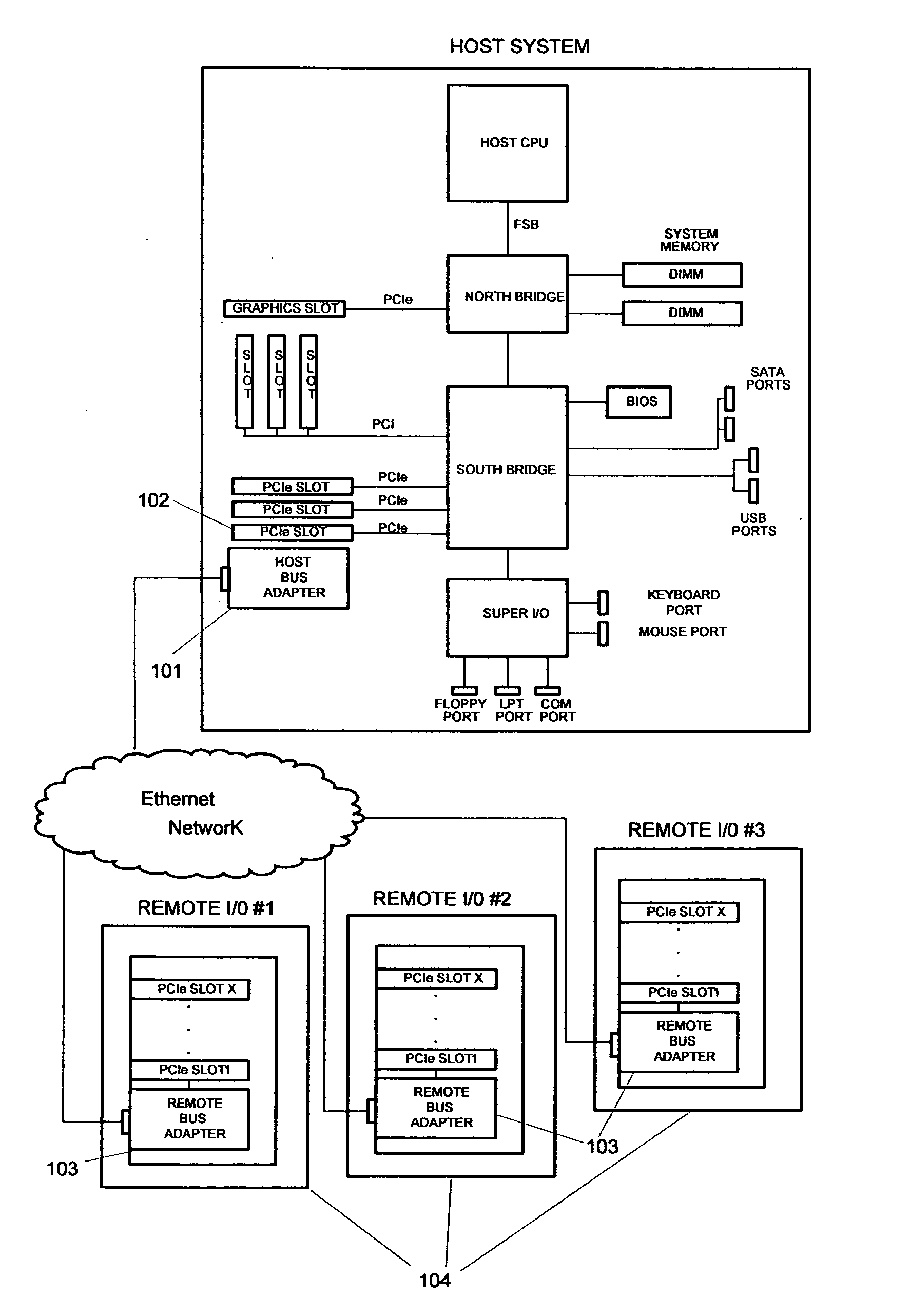
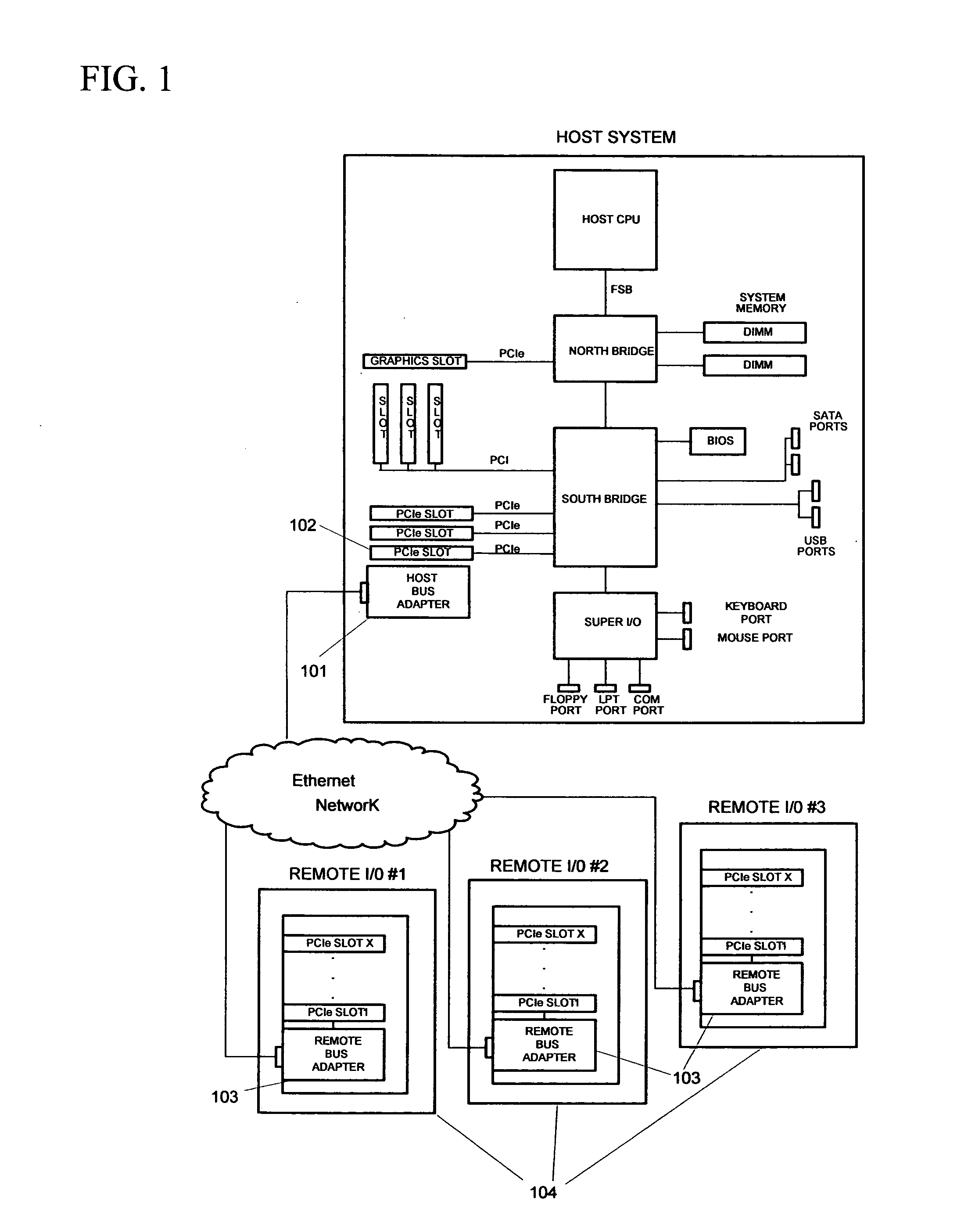
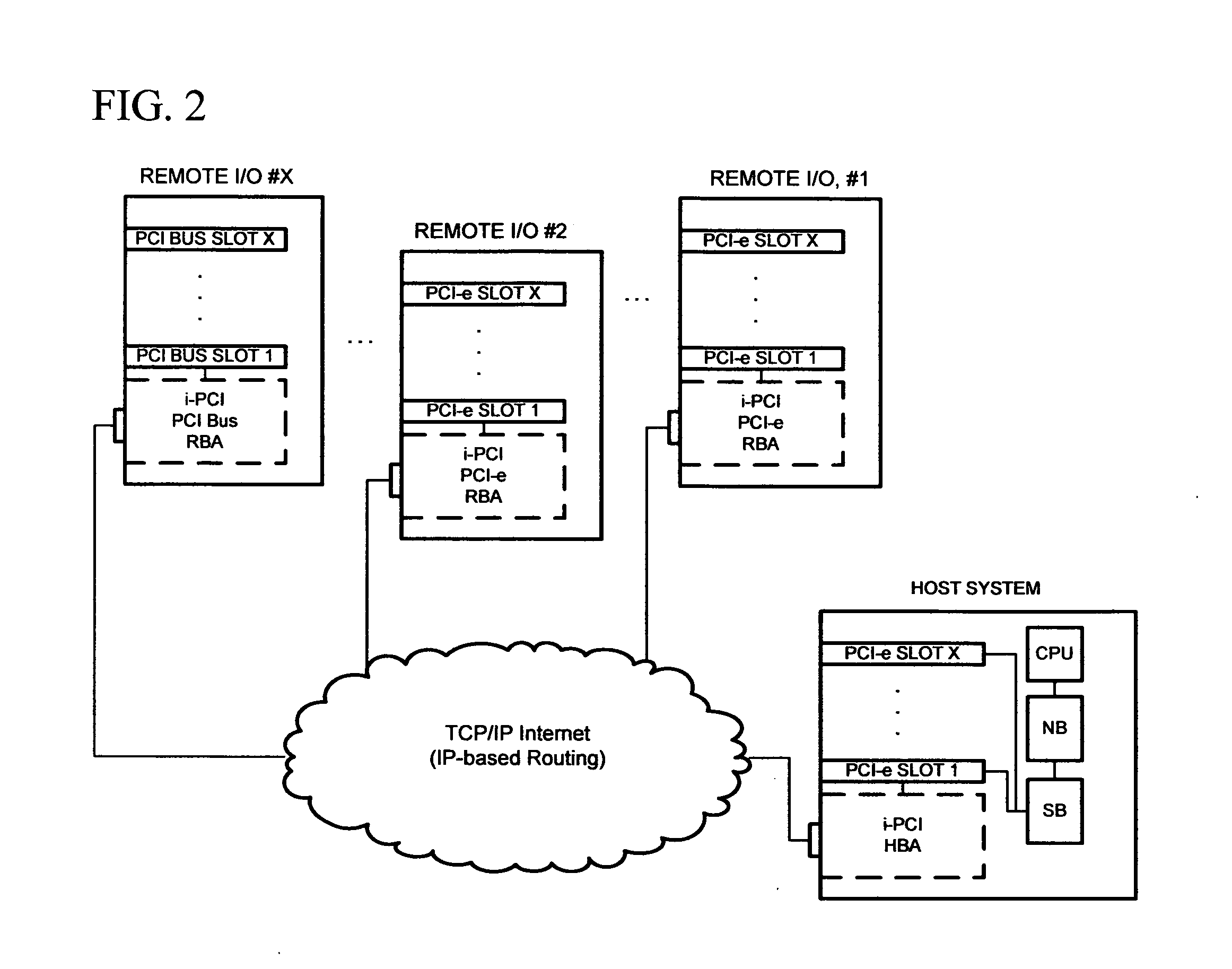
Virtualized PCI endpoint for extended systems
InactiveUS9064058B2Simple virtualizationLess powerTransmissionElectric digital data processingVirtualizationThe Internet
Owner:NUON
Integrated intrusion deflection, detection and introspection
ActiveUS8413241B2Improve securityEasy to configureError preventionFrequency-division multiplex detailsVirtualizationLimited resources
Methods and apparatus are provided for integrated deflection, detection and intrusion. Within a single computer system configured for operating system virtualization (e.g., Solaris™, OpenSolaris™), multiple security functions execute in logically independent zones or containers, under the control and administration of a global zone. Such functions may illustratively include a demilitarized zone (DMZ) and a honeypot. Management is facilitated because all functions work within a single operating system, which promotes the ability to configure, monitor and control each function. Any given zone can be configured with limited resources, a virtual network interface circuit and / or other features.
Owner:ORACLE INT CORP
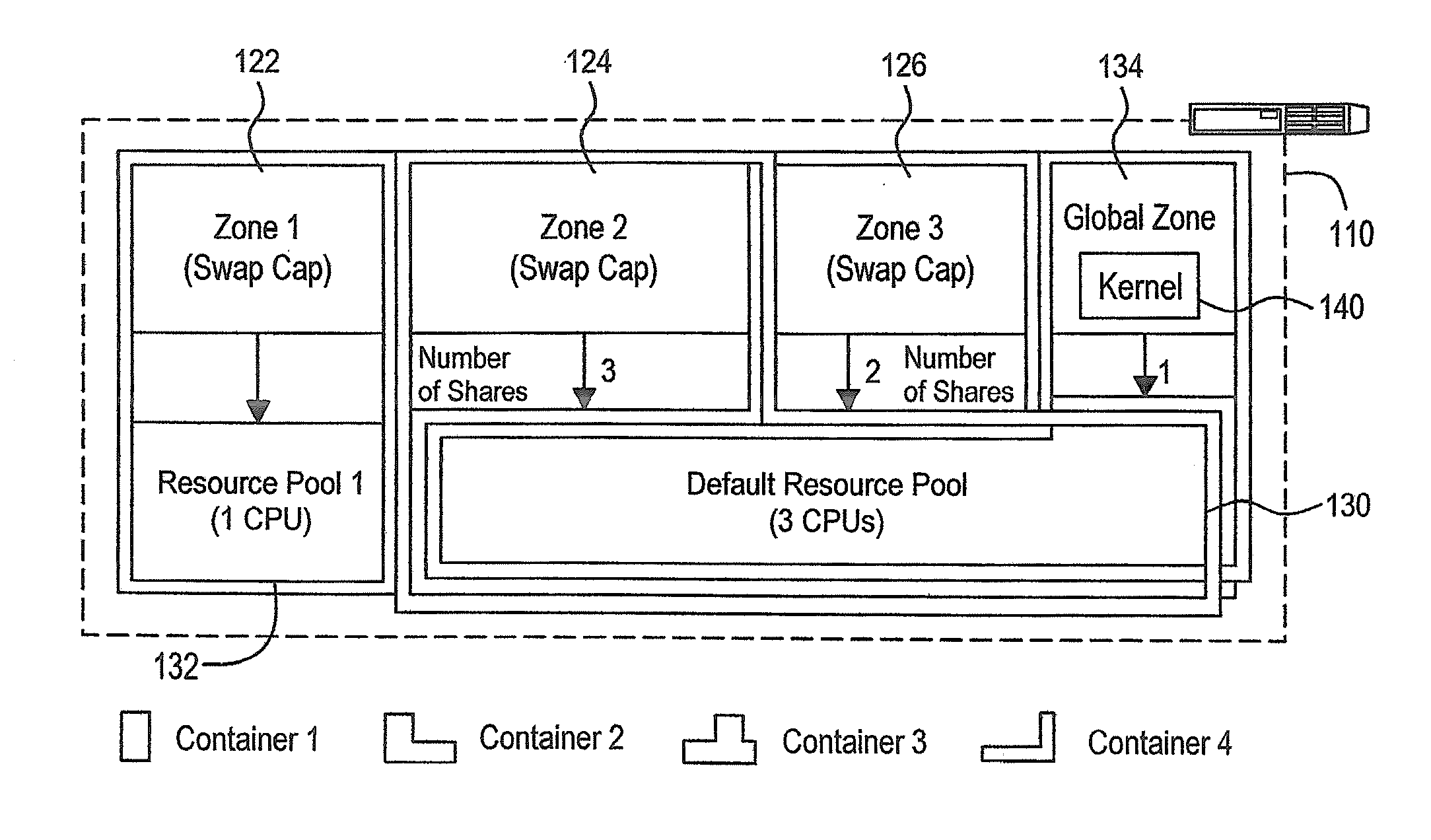
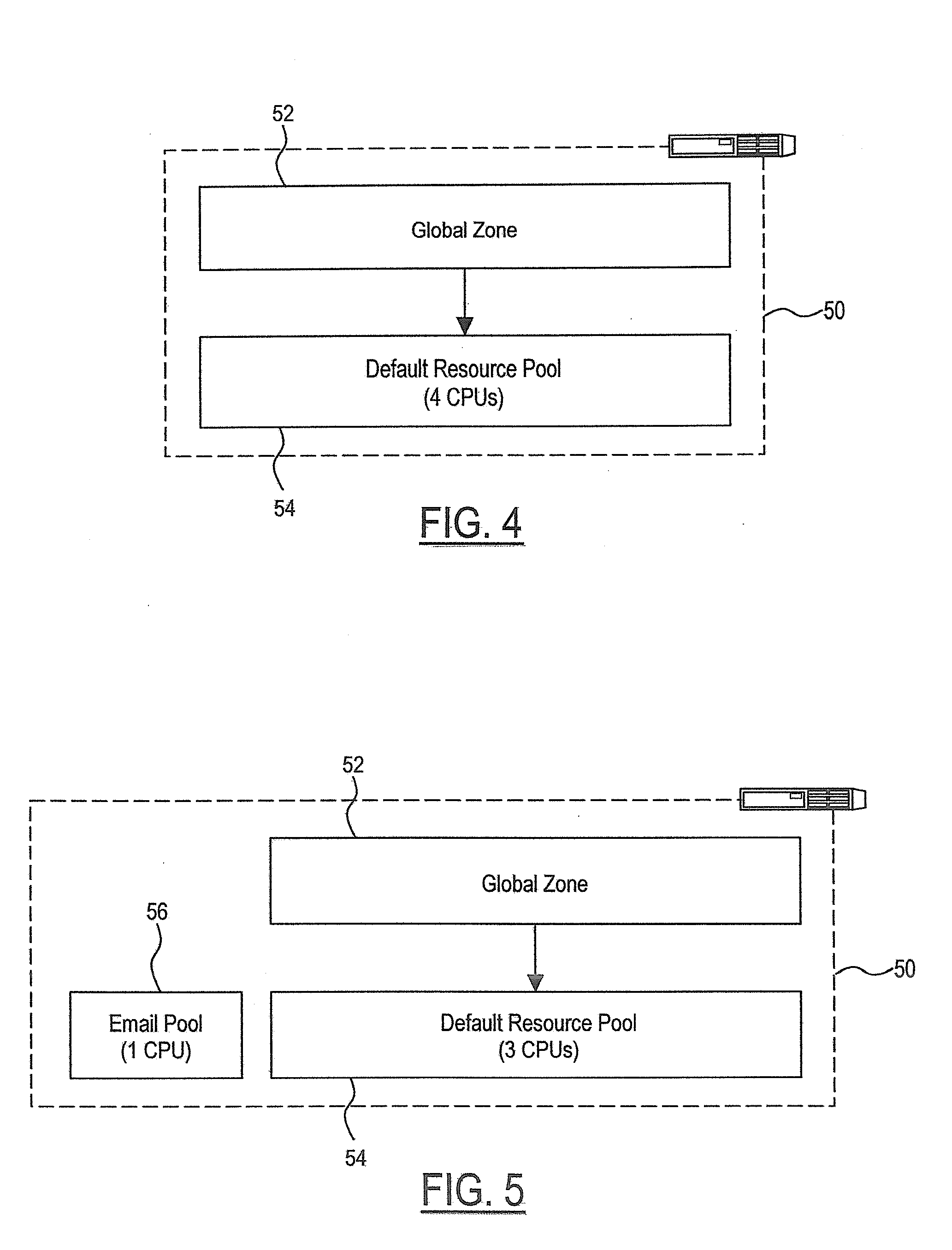
Swap cap resource control for use in virtualization
ActiveUS20090007126A1Control consumptionAvoid negative effectsEnergy efficient ICTResource allocationVirtualizationOperational system
A method of implementing virtualization involves an improved approach to virtual memory management. An operating system includes a kernel, a resource control framework, a virtual memory subsystem, and a virtualization subsystem. The virtualization subsystem is capable of creating separate environments that logically isolate applications from each other. The virtual memory subsystem utilizes swap space to manage a backing store for anonymous memory. The separate environments share physical resources including swap space. When a separate environment is configured, properties are defined. Configuring a separate environment may include specifying a swap cap that specifies a maximum amount of swap space usable by the separate environment. The resource control framework includes a swap cap resource control. The swap cap resource control is enforced by the kernel such that during operation of the separate environment, the kernel enforces the swap cap specified when the separate environment was configured.
Owner:SUN MICROSYSTEMS INC
Method of mutually authenticating between software mobility device and local host and a method of forming input/output (i/o) channel
InactiveUS20090055918A1Ensure safetyDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareVirtualization
A method of mutually authenticating between a local host and a software mobility device including an operating system virtualization layer, and a method of forming an input / output (I / O) channel. The method of authenticating a local host in the software mobility device includes requesting a certificate from the local host in which an integrity value of the local host is stored, and receiving the certificate from the local host; receiving an integrity value measured in the local host and comparing the measured integrity value with the integrity value included in the certificate to verify the local host; and when the local host is verified, encrypting a security profile of the software mobility device and transmitting the encrypted security profile to the local host so as to provide secure communication between the local host and the software mobility device.
Owner:SAMSUNG ELECTRONICS CO LTD
Virtualized PCI endpoint for extended systems
InactiveUS20100161870A1Simple virtualizationLess powerTransmissionElectric digital data processingVirtualizationThe Internet
Virtualization of a PCI Endpoint via the Internet and LANs. The invention is a solution that allows the use of low-complexity, low-cost PCI Express Endpoint Type 0 cores or custom logic for relatively simple virtualization applications. The invention combines two physically separate assemblies in such a way that they appear to the host system as one local multifunctional PCI Express Endpoint device.
Owner:NUON
Data anti-leakage method based on operating system virtualization principle
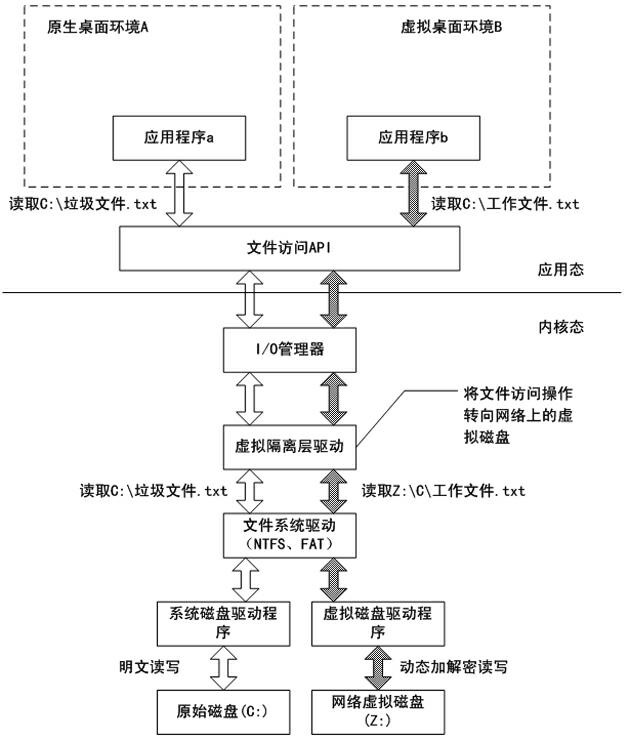
InactiveCN102004886AReduce difficultySignificant progressDigital data protectionVirtualizationOperational system
The invention relates to a data anti-leakage method based on an operating system virtualization principle, belonging to the technical field of computer application. The data anti-leakage method is characterized by comprising the following steps of: increasing a virtual isolating layer and a virtual storage area in a host operating system of a computer on the basis of the operating system virtualization principle; structuring one or more virtual isolated environments on the basis of the virtual isolating layer and the virtual storage area by combining with a virtual desktop technology; and completely isolating and protecting data resources which are stored in each virtual isolated environment and include files and registration forms to ensure that data generated in the virtual isolated environments is not leaked out of the virtual isolated environments so as to prevent active or passive data leakage behaviors. The invention greatly enhances the operating efficiency of a data anti-leakage system by utilizing the innate advantages of the operating system virtualization principle, reduces the difficulty of applying a data anti-leakage scheme and enhances the easy use and the work efficiency of the data anti-leakage system.
Owner:上海安纵信息科技有限公司
Workload management in virtualized data processing environment
ActiveUS7617375B2Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
Owner:IBM CORP
Honeypot defense method and system based on mimicry defense, equipment and medium
The invention discloses a honeypot defense method and system based on mimicry defense, equipment and a medium, which are applied to the technical field of network security. A virtualization managementsubsystem comprises a mirror image management module, a honeypot management module, a virtual network management module and a control scheduler which are connected in sequence, the mirror image management module constructs a mimicry honeypot mirror image through a KVM virtual machine mirror image technology, a plurality of virtual high-interaction honeypots and a mimicry honeypot system are obtained, and the honeypots are mimicry honeypots; the honeypot management module manages the honeypots and monitors the state of the honeypots; the virtual network management module controls the honeypotsystem to perform data access and network communication; and a control scheduler dynamically switches the mimicry honeypots and the network according to the output judgment result of the mimicry honeypots. According to the invention, mimicry defense is combined with the honeypot system, so that the security and controllability of network space security defense are improved.
Owner:PURPLE MOUNTAIN LAB +1
Workload management in virtualized data processing environment
ActiveUS20080244215A1Error detection/correctionDigital computer detailsVirtualizationComputerized system
A system, method and computer-readable medium for balancing access among multiple logical partitions to the physical system resources of a computer system employing system virtualization. Each of the logical partitions is classified, initially during a startup period, in accordance with a level of allocated dispatch window utilization. Performance metrics of one or more of the physical system resources are determined in association with one or more of the logical partitions. The performance metrics determination is performed at a hardware level independent of programming interrupts. During a dispatch window in which a given set of the physical system resources are configured for allocation to one of the logical partitions, the given set of physical system resources are re-allocated to a replacement logical partition in accordance with the determined performance metrics associated with the replacement logical partition and the dispatch window utilization classification of the replacement logical partition.
Owner:IBM CORP
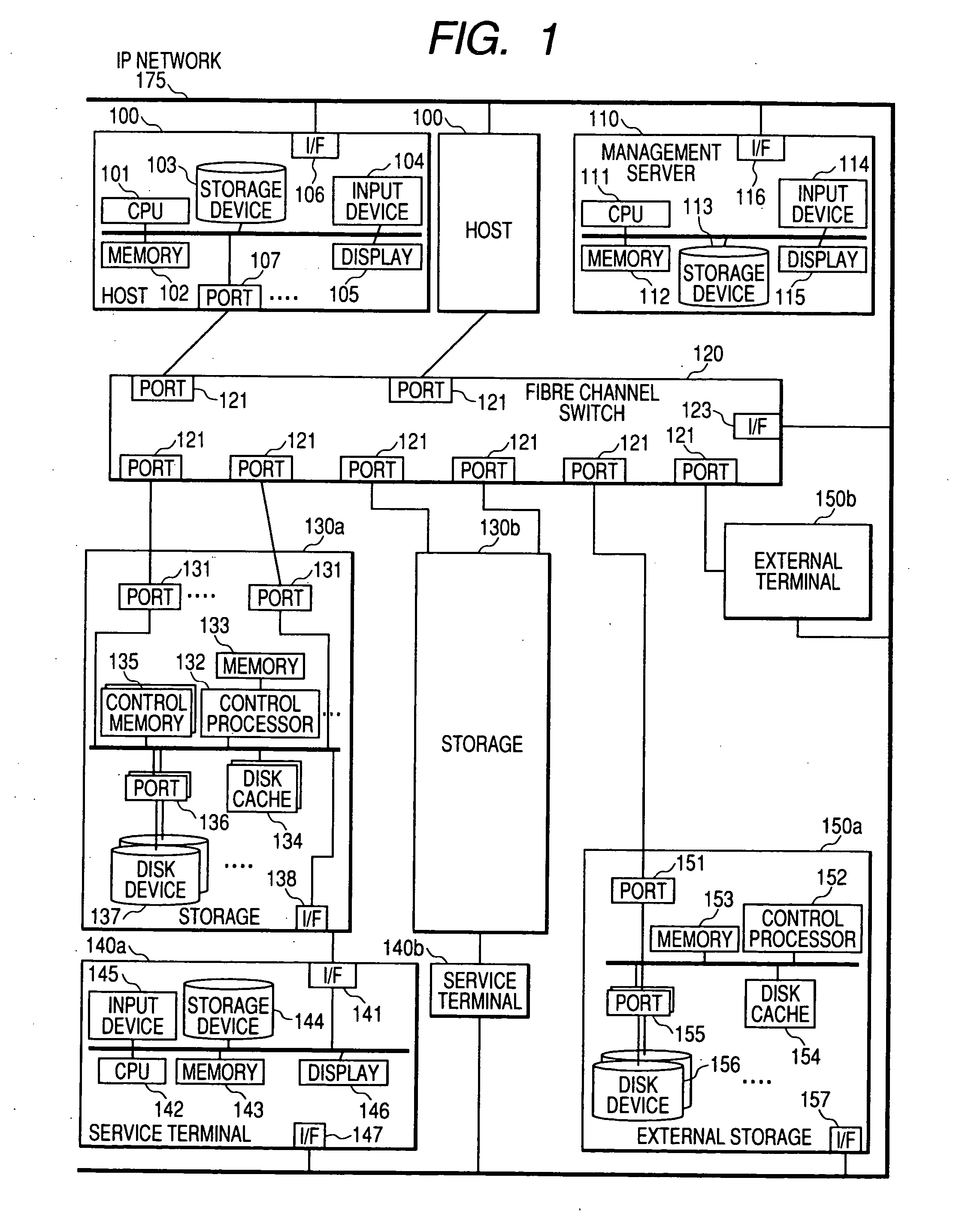
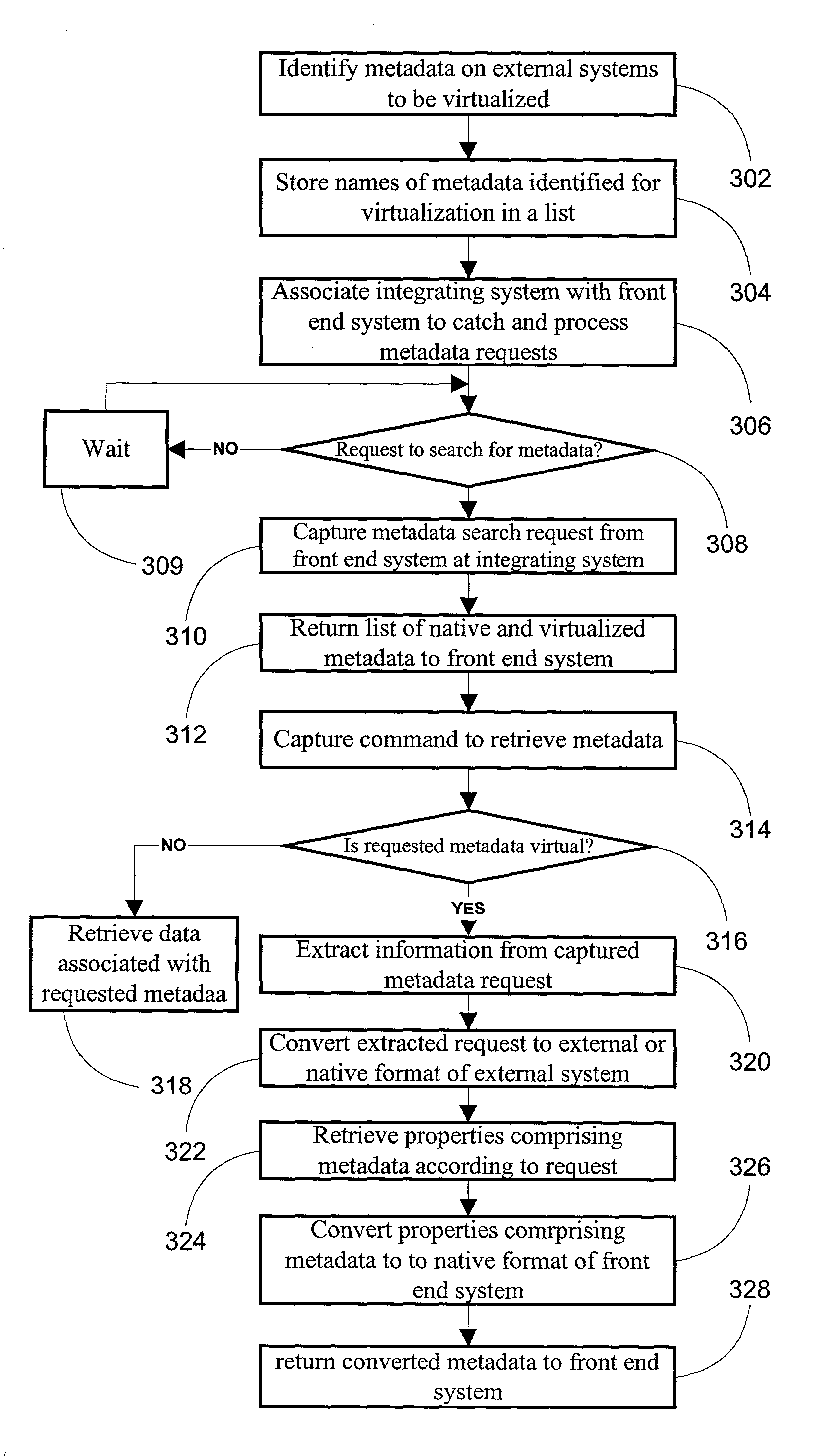
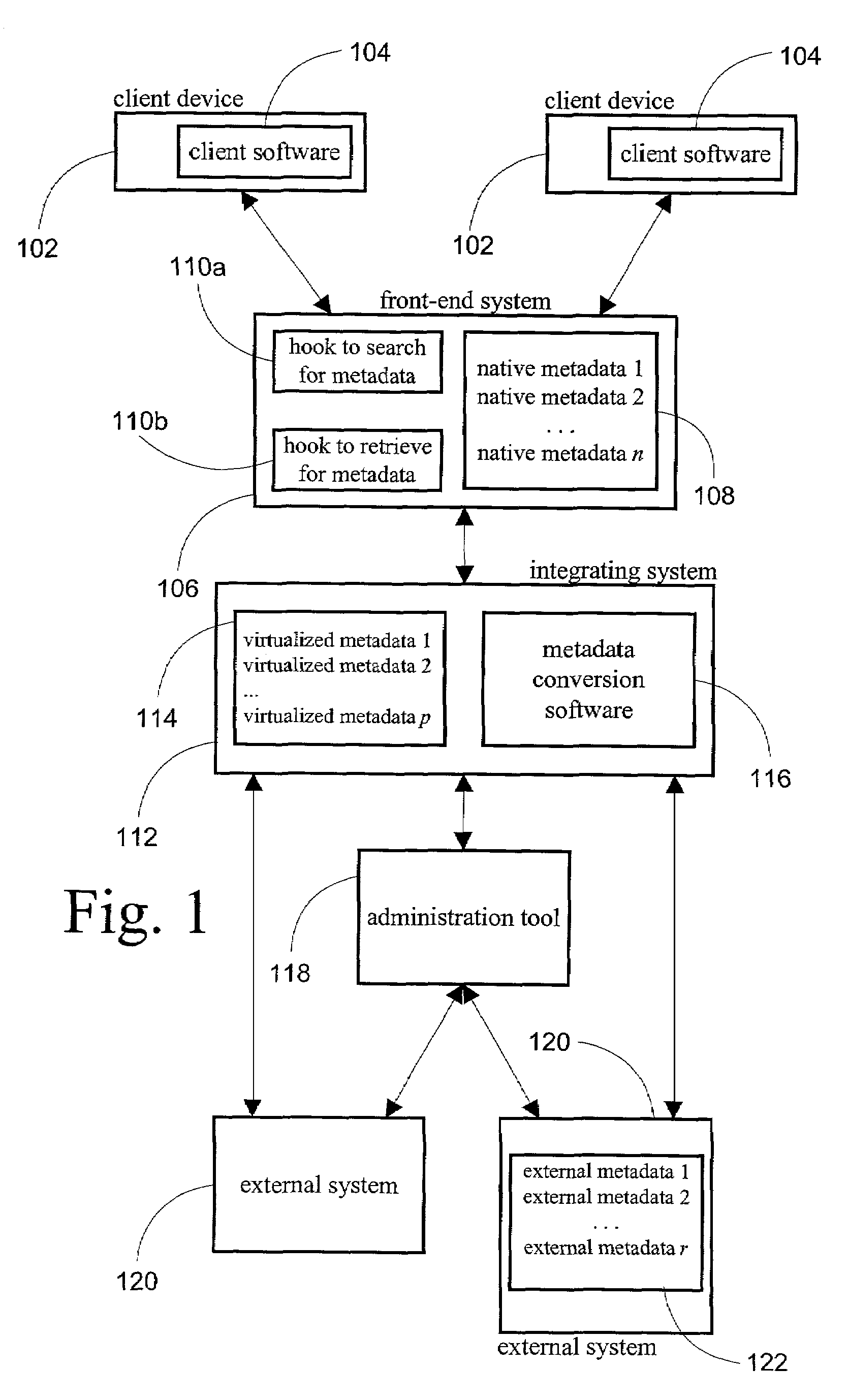
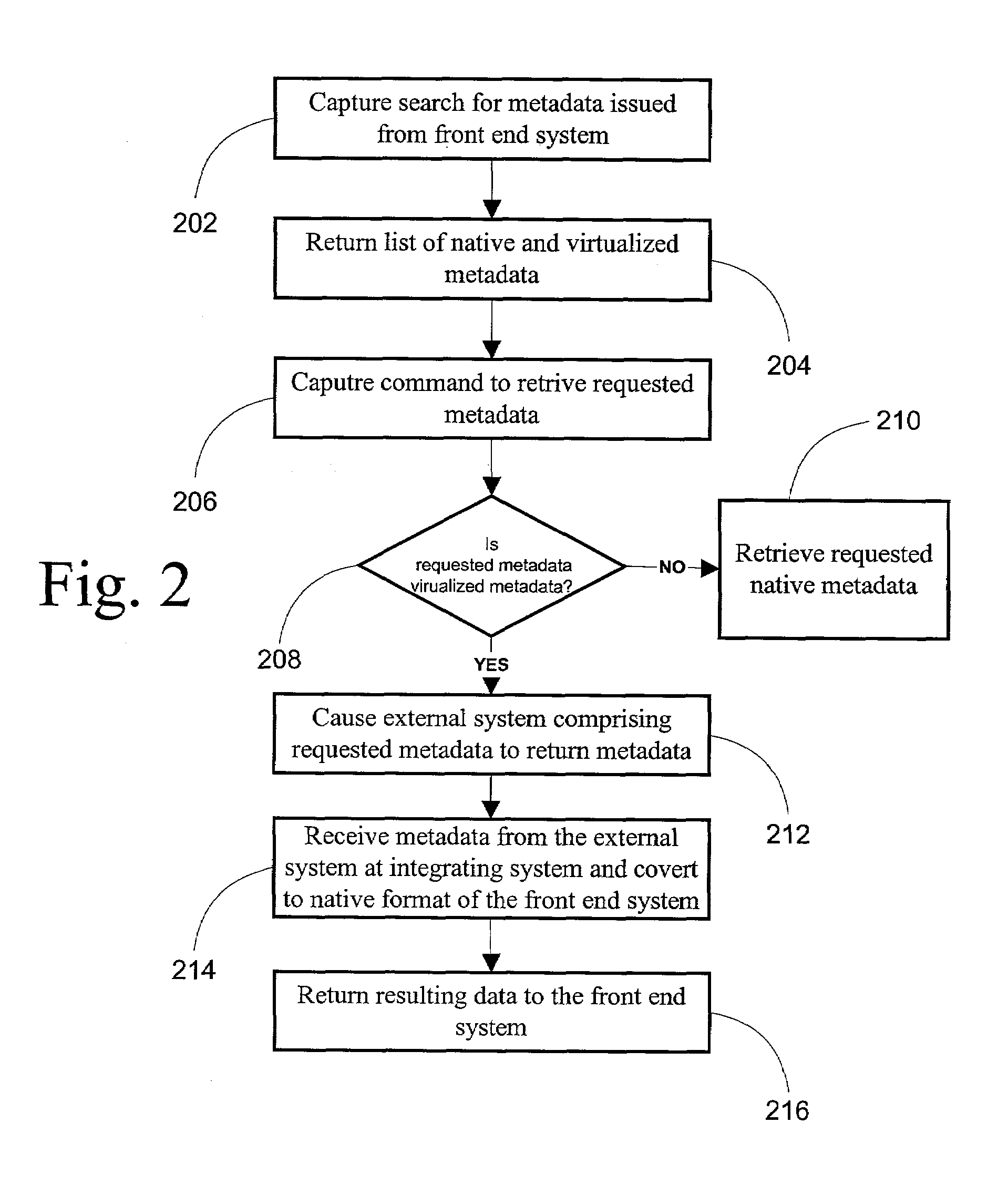
Method and system for virtualizing metadata between disparate systems
InactiveUS7483979B1Minimize development timeAvoid disadvantagesDatabase management systemsMultiple digital computer combinationsVirtualizationEnd system
A non-programmatic method for virtualizing the metadata of external systems at a front-end system is disclosed. The front-end system is provided with programmatic hooks that enable the external capture of its search for metadata and its commands to retrieve properties comprising selected metadata. When an end user of the front-end system requests to retrieve properties comprising selected metadata, typically through the use of a client device, an integrating system captures the search for metadata and provides a list of metadata both native to the front-end system and virtualized from disparate external systems.The end user selects metadata in order to retrieve properties comprising the metadata. The integrating system captures the front-end system's command to retrieve the metadata. The integrating system converts the metadata request from the format of the front-end system to the format of the external system whose metadata was selected. The external system returns the properties comprising the requested metadata. The integrating system receives the resultant properties comprising the metadata, converts it to the format of the front-end system, and passes the resultant converted properties comprising the metadata to the front-end system for presentation to the end user.
Owner:IBM CORP
Memory access to virtual target device
InactiveUS20070067151A1Improve efficiencyImprove reliabilityComputer security arrangementsSoftware designGeneral Packet Radio ServiceVirtualization
A software development technique is provided using target system virtualization software simulating behaviour of a target system. A target device driver running on a host system issues memory access commands to the target system virtualization software rather than to a memory interface unit of the host system. The memory interface unit may be an SRAM (Static Random Access Memory) interface. The target system may be an EGPRS (Enhanced General Packet Radio Service) modem.
Owner:CHRONOCLOUD MEDTECH (SHANGHAI) CO LTD
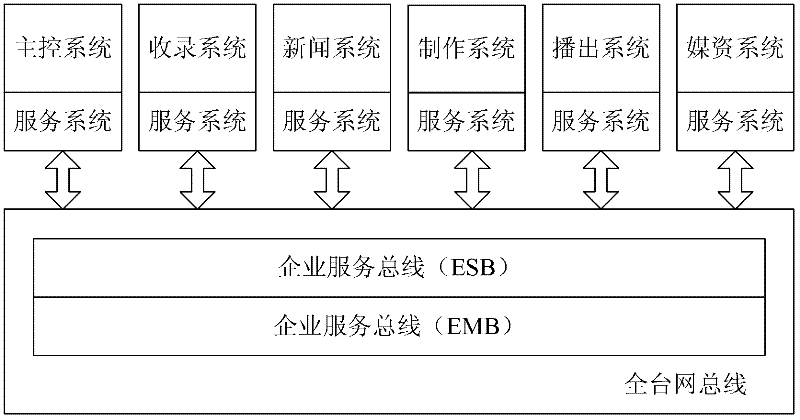
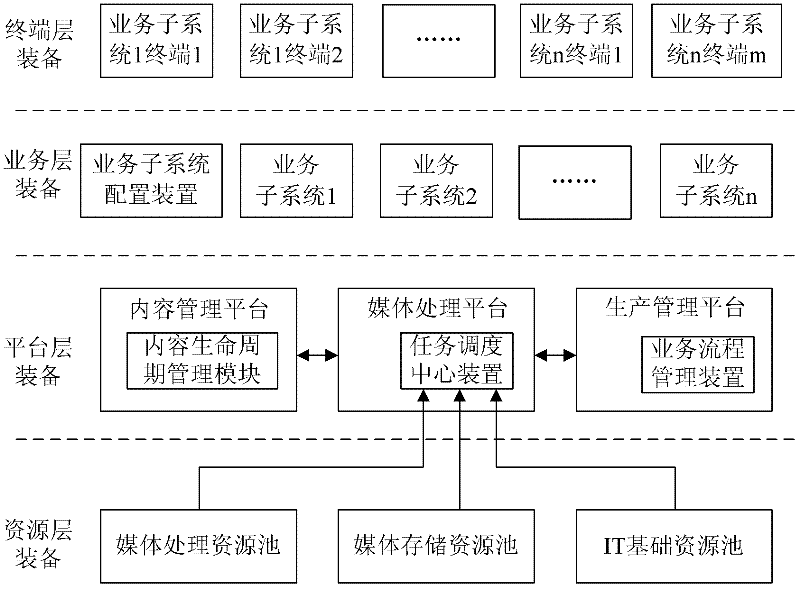
Method and device for configuring business subsystem in television station production system
The invention provides a device and device for configuring a business subsystem in a television station production system. The device comprises a subsystem resource configuration module and a subsystem building module, wherein the subsystem resource configuration module is used for configuring corresponding business subsystem resources according to a business request provided by a terminal device and outputting the corresponding business subsystem resources to the subsystem building module; and the subsystem building module is used for building the corresponding business subsystem according to the input business subsystem resources and returning the corresponding business subsystem to the terminal device providing the business request. By using a cloud computing resource pool, virtualization, distribution and other technologies, according to a layered architecture of hardware source pooling, core service platformization and production system virtualization, the invention realizes that the computation is provided, IT resources are integrated and multiple items of businesses of an application are provided oriented to broadcast and television programs, thus a business product production and delivery mode of plug and play is provided for a television station production system user.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
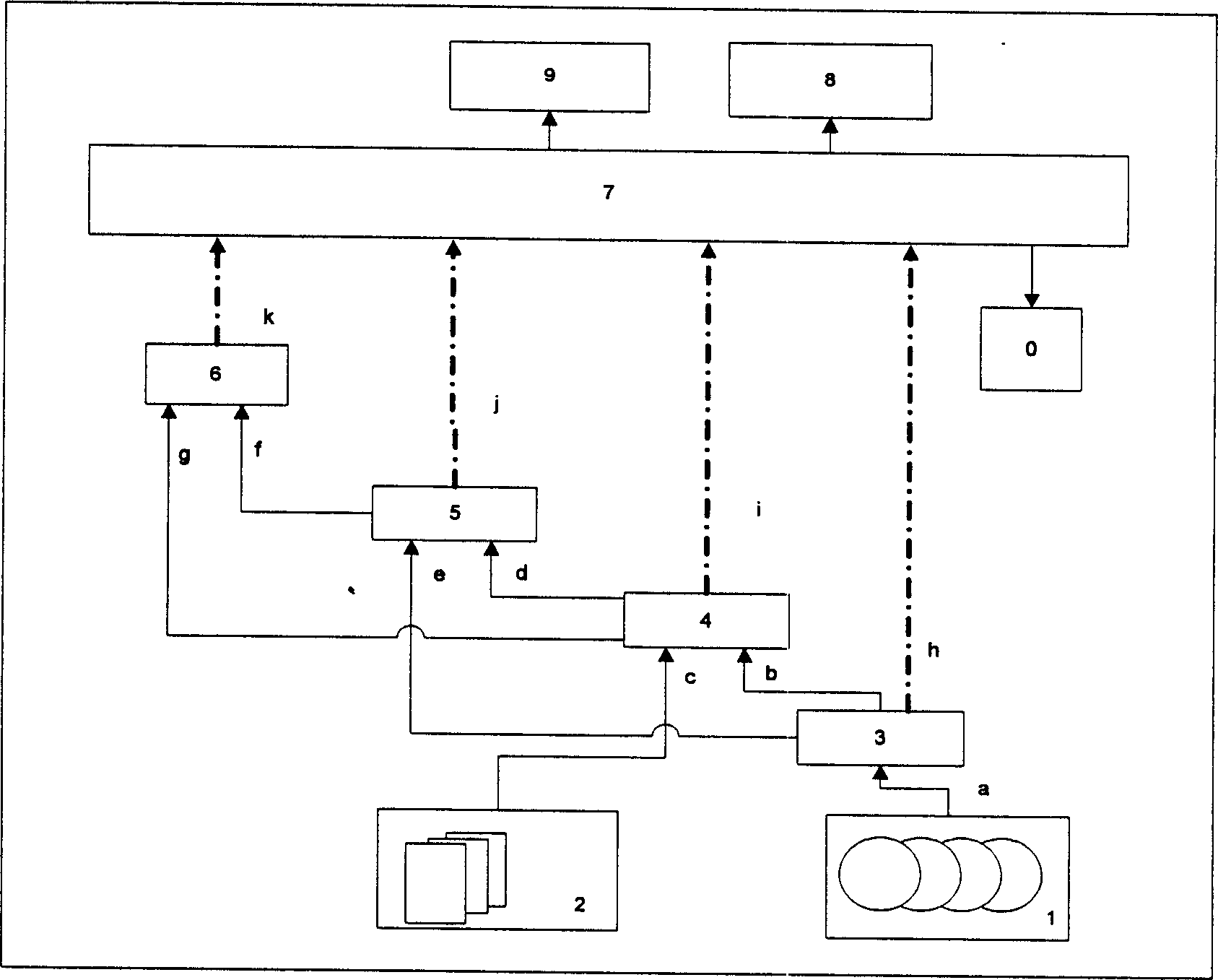
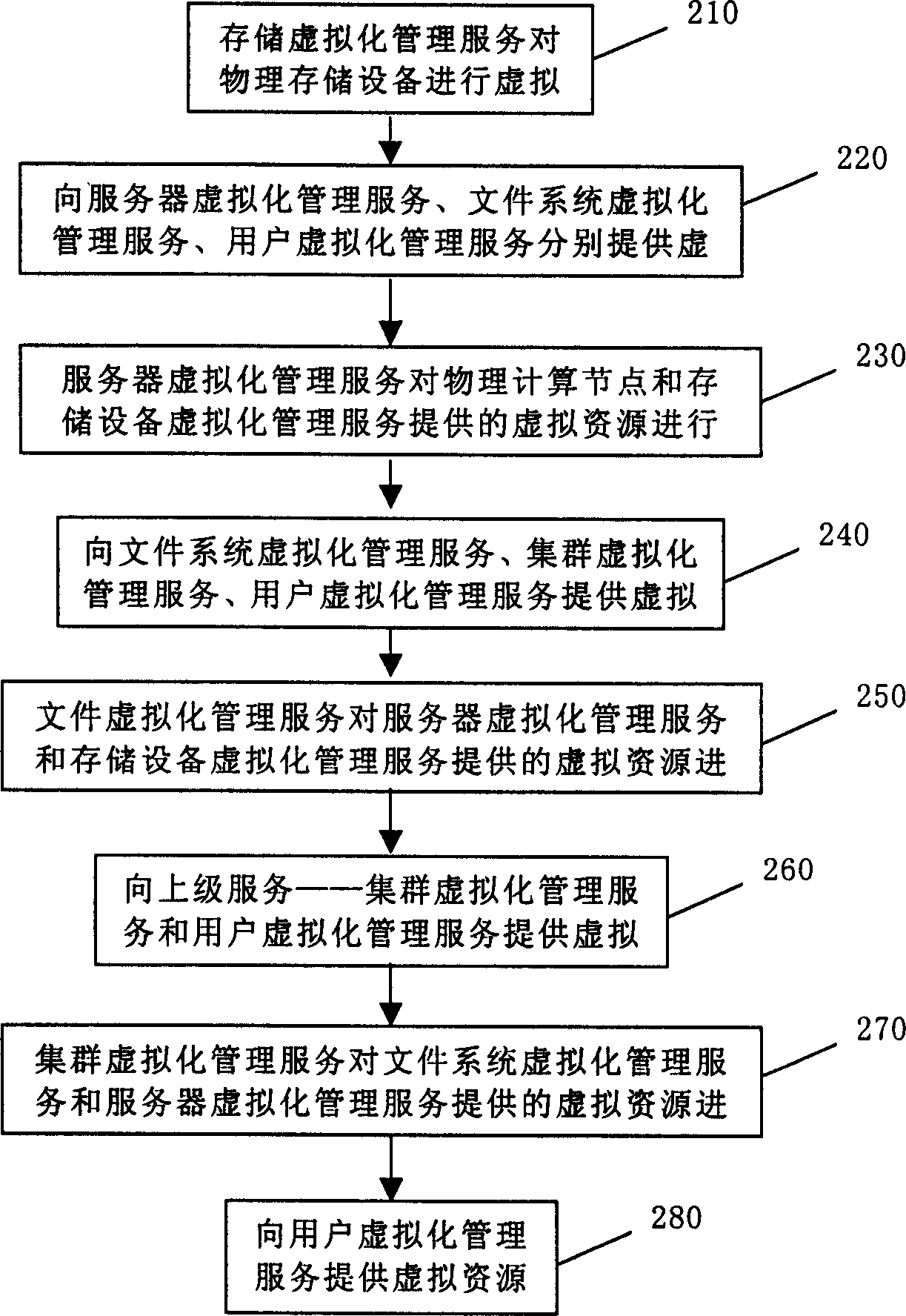
Management system and method for large service system based on network storage and resource virtual process
InactiveCN1642169ASimple and easy researchEasy to developTransmissionStructure of Management InformationResource virtualization
The invention is a managing system and method for a large-scale service system based on network storage and resources virtual treatment, including user virtual management service module, system virtual management service module and atomic part, where the atomic part includes physical calculating node and physical storage device node; and the system virtual management service module is used to realize system virtual service and management package, makes resource virtual treatment on the atomic part and provides shared interface for the previous-stage system virtual management service module and the user virtual management service module; and the system virtual management service module provides virtual resources for the previous-stage system virtual management service module and the user virtual management service module. The invention is based on the storage management and adopts a hiberarchy to effectively integrate server, management of various typical systems and management of user custom system, generally improving system performance.
Owner:TIANJIN ZHONGKE BLUEWHALE INFORMATION TECH +1
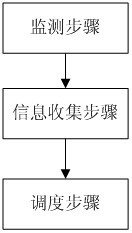
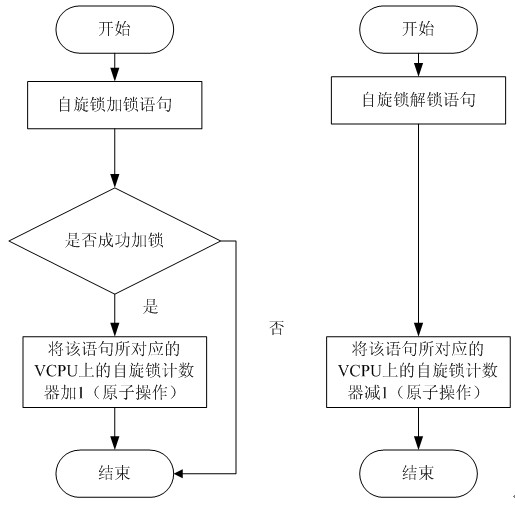
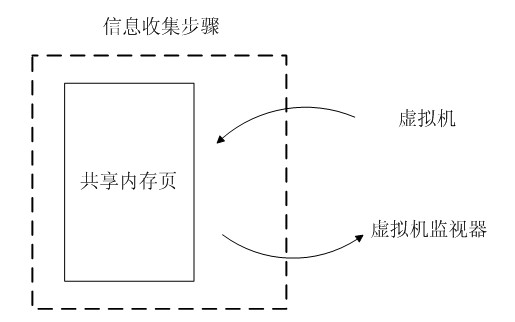
Virtual CPU dispatching method
InactiveCN102053858AImprove accuracyHigh precisionSoftware simulation/interpretation/emulationVirtualizationExtensibility
A virtual CPU (Central Processing Unit) dispatching method belongs to the technical field of computing system virtualization, solves the problem of lock holder preemption, and improves the performance of a virtual machine in a multiple processor system. The virtual CPU dispatching method is used in a multiprocessor virtualized environment and comprises a monitoring procedure, an information collecting procedure and a dispatching procedure, wherein the monitoring procedure performs real-time monitoring to spin lock operating commands of all virtual machine operating systems; the information collecting procedure extracts spin lock amount obtained by the monitoring procedure, to form spin lock counting information; and the dispatching procedure adopts fair and efficient dispatching method todispatch the virtual CPU according to the spin lock counting information extracted from the information collecting procedure. Compared with the prior art, the method can detect whether dispatching isavailable more accurately, so as to improve the utilization ratio of physical CPU, ensure that dispatching strategy has flexibility and expandability, as well as fairness, effectively solve the problem of lock holder preemption, and greatly improve the performance of virtual machine in a multiple processor system.
Owner:HUAZHONG UNIV OF SCI & TECH
Workload management in virtualized data processing environment
A system, method and computer-readable medium for balancing access among multiple logical partitions to the physical system resources of a computer system employing system virtualization. Each of the logical partitions is classified, initially during a startup period, in accordance with a level of allocated dispatch window utilization. Performance metrics of one or more of the physical system resources are determined in association with one or more of the logical partitions. The performance metrics determination is performed at a hardware level independent of programming interrupts. During a dispatch window in which a given set of the physical system resources are configured for allocation to one of the logical partitions, the given set of physical system resources are re-allocated to a replacement logical partition in accordance with the determined performance metrics associated with the replacement logical partition and the dispatch window utilization classification of the replacement logical partition.
Owner:IBM CORP
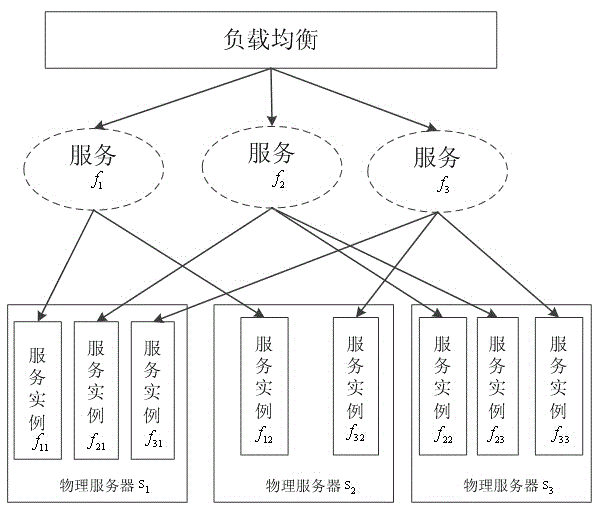
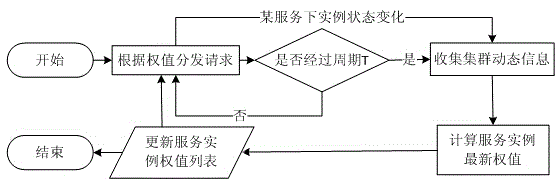
Method for load balancing of Web requests based on operating system virtualization
InactiveCN104902001ALoad balancingAvoid overloaded situationsTransmissionVirtualizationOperational system
The invention discloses a method for load balancing of Web requests based on operating system virtualization. The method comprises the following steps of firstly, carrying out collection and normalization of server resource information; secondly, collecting dynamic information of a server and service instances; thirdly, computing final weights of service instance copies of all services according to the server resource information and the periodically-collected dynamic information; and lastly, distributing the requests through weighted round robin. According to the method, the phenomenon that the different service instance copies on one server simultaneously receive a large amount of Web requests due to the lower server load to cause the server overload can be effectively avoided, the load balancing between the service instance copies and the server is implemented, the concurrence capacity of a Web cluster system is improved, and the average response time of the requests is reduced.
Owner:HANGZHOU DIANZI UNIV
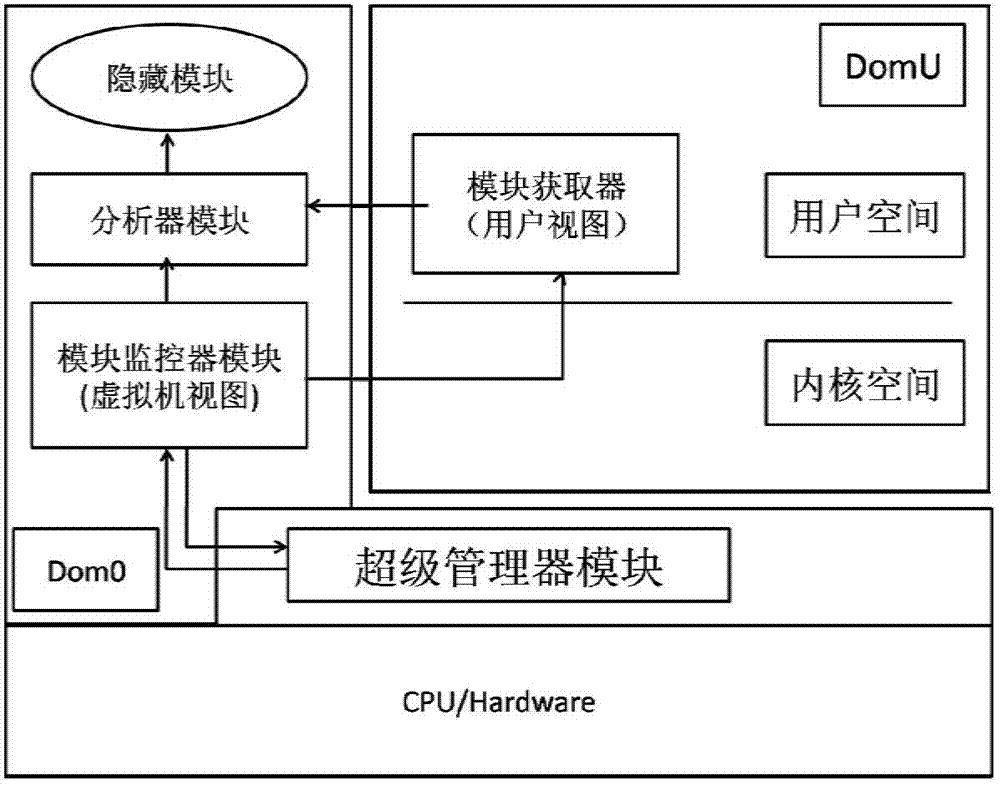
Kernel mode Rootkit detection method based on system virtualization technology
ActiveCN103310152AAvoid attackGuarantee authenticityPlatform integrity maintainanceVirtualizationSystem call
The invention provides a kernel mode Rootkit detection method based on system virtualization technology. A Rootkit principle, system calling and an LKM (Loadable Kernel Module) are analyzed deeply to obtain the behavior characteristic of hiding of own module information of kernel mode Rootkit. Specific to the characteristic, the Rootkit detection method based on cross view validation is designed. A Xen kernel is changed to intercept system calling, so that a credible view is constructed. An infected view is constructed by using a user mode tool of a target client. Hidden modules are found by comparing the credible view with the infected view.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com