Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Memory corruption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
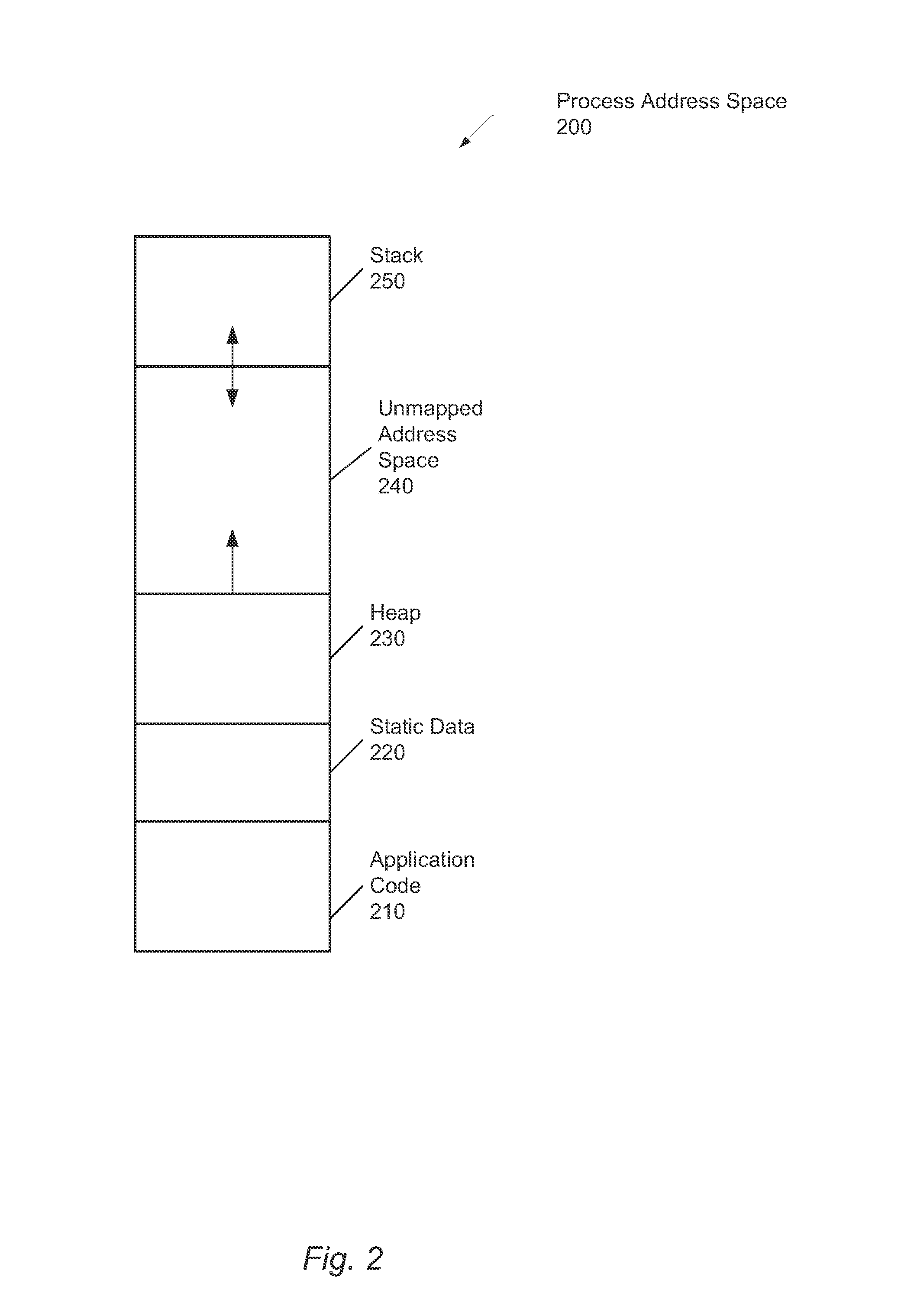
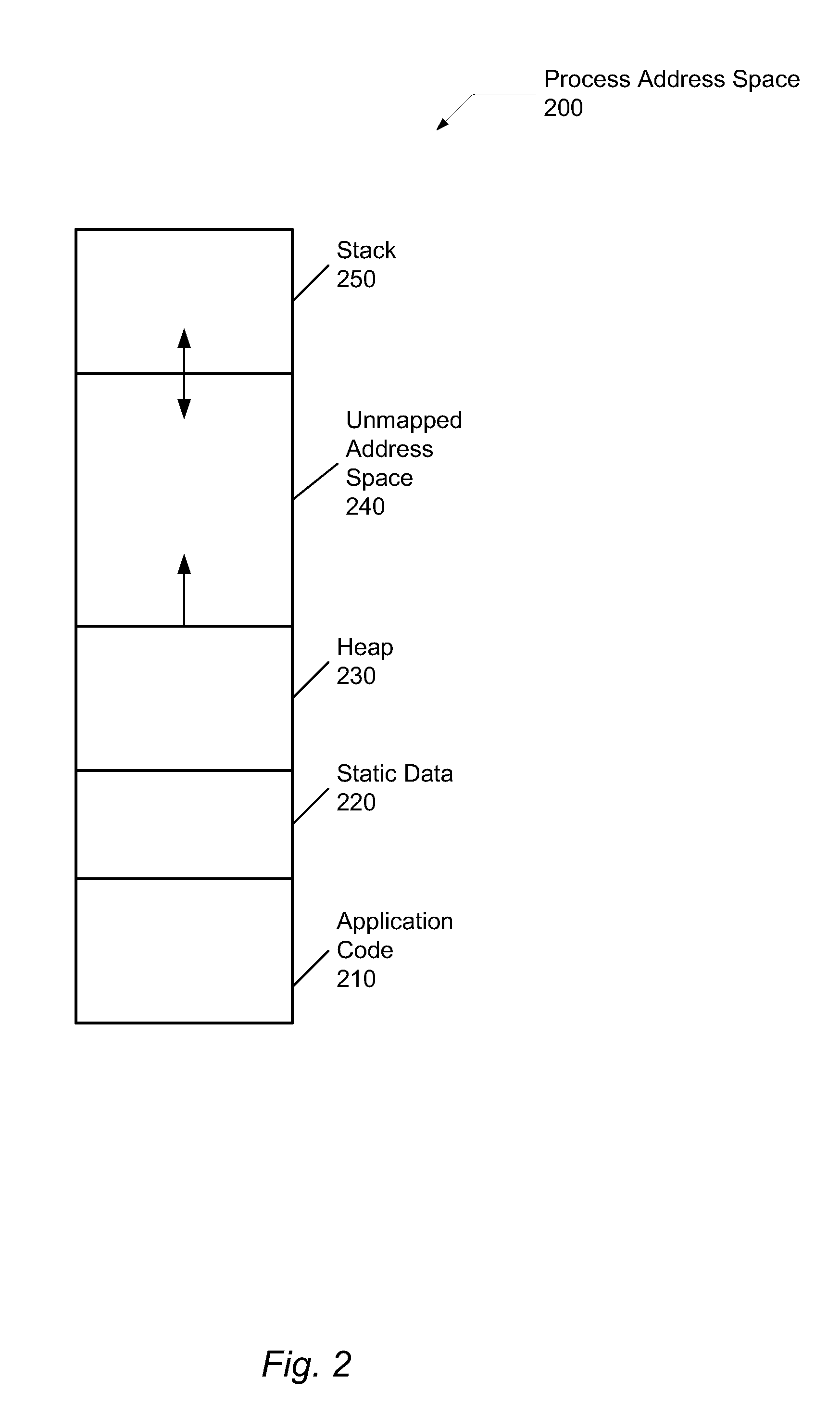
Memory corruption occurs in a computer program when the contents of a memory location are modified due to programmatic behavior that exceeds the intention of the original programmer or program/language constructs; this is termed violating memory safety. The most likely cause of memory corruption is programming error. When the corrupted memory contents are used later in that program, it leads either to program crash or to strange and bizarre program behavior. Nearly 10% of application crashes on Windows systems are due to heap corruption.
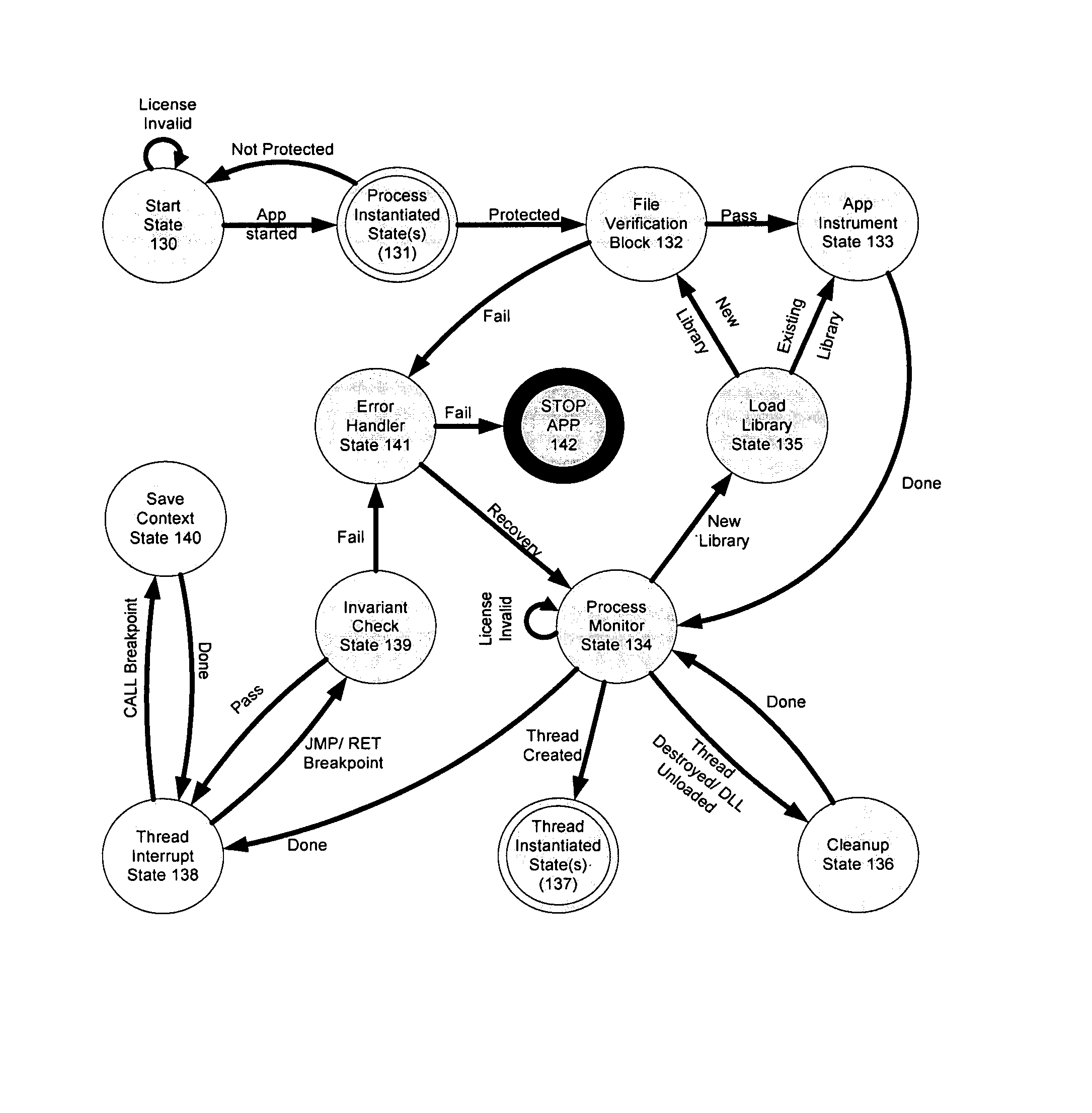
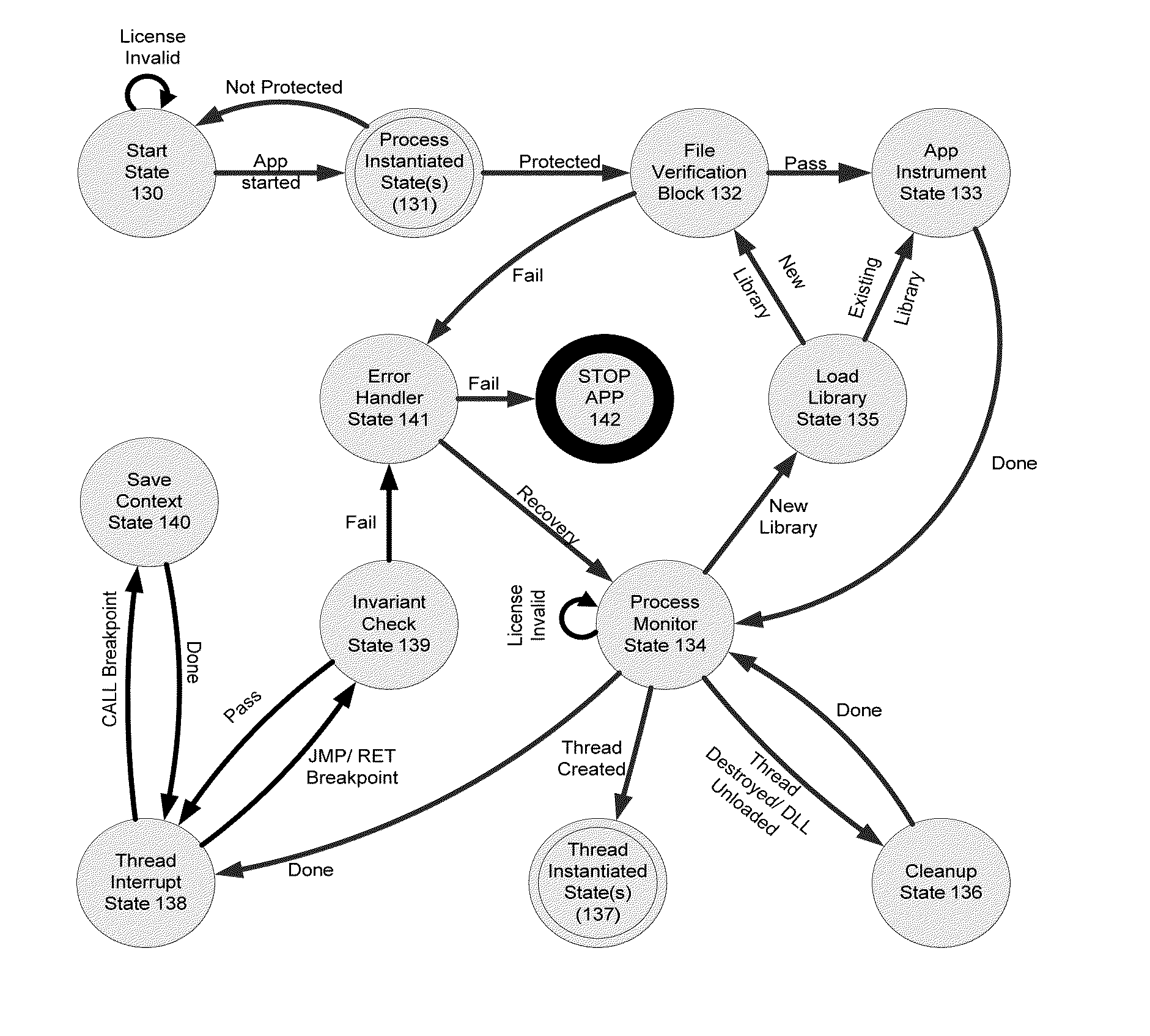
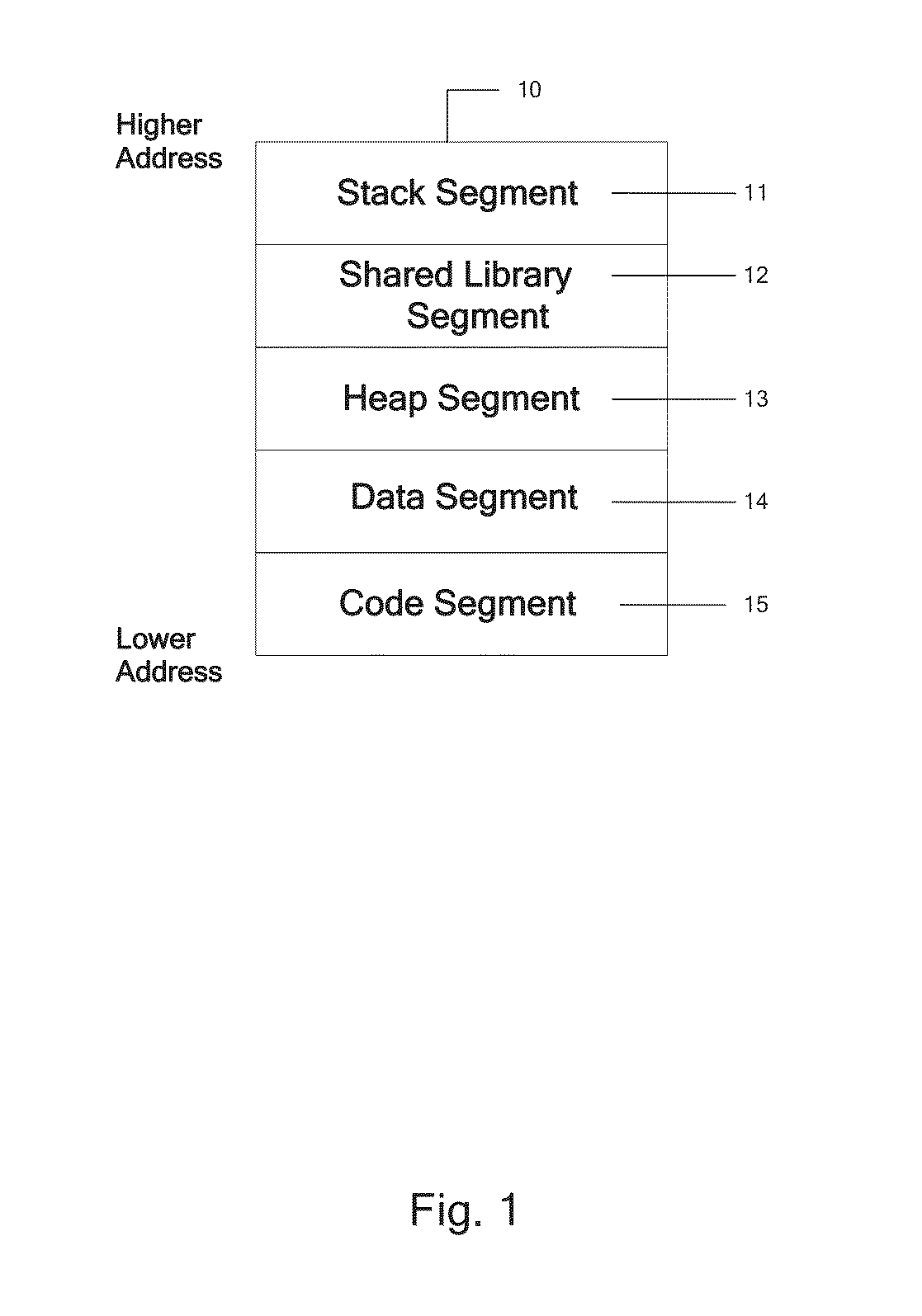
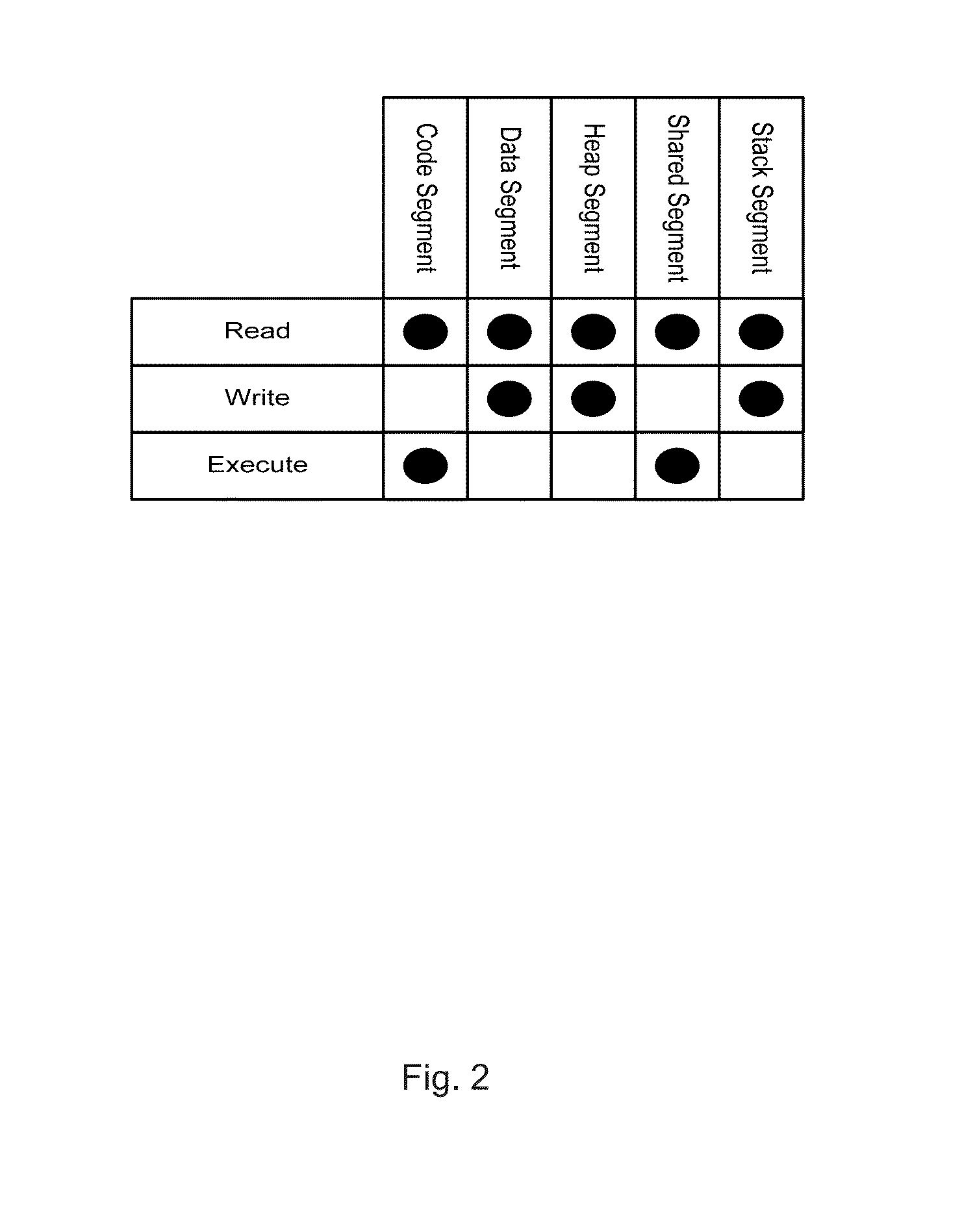
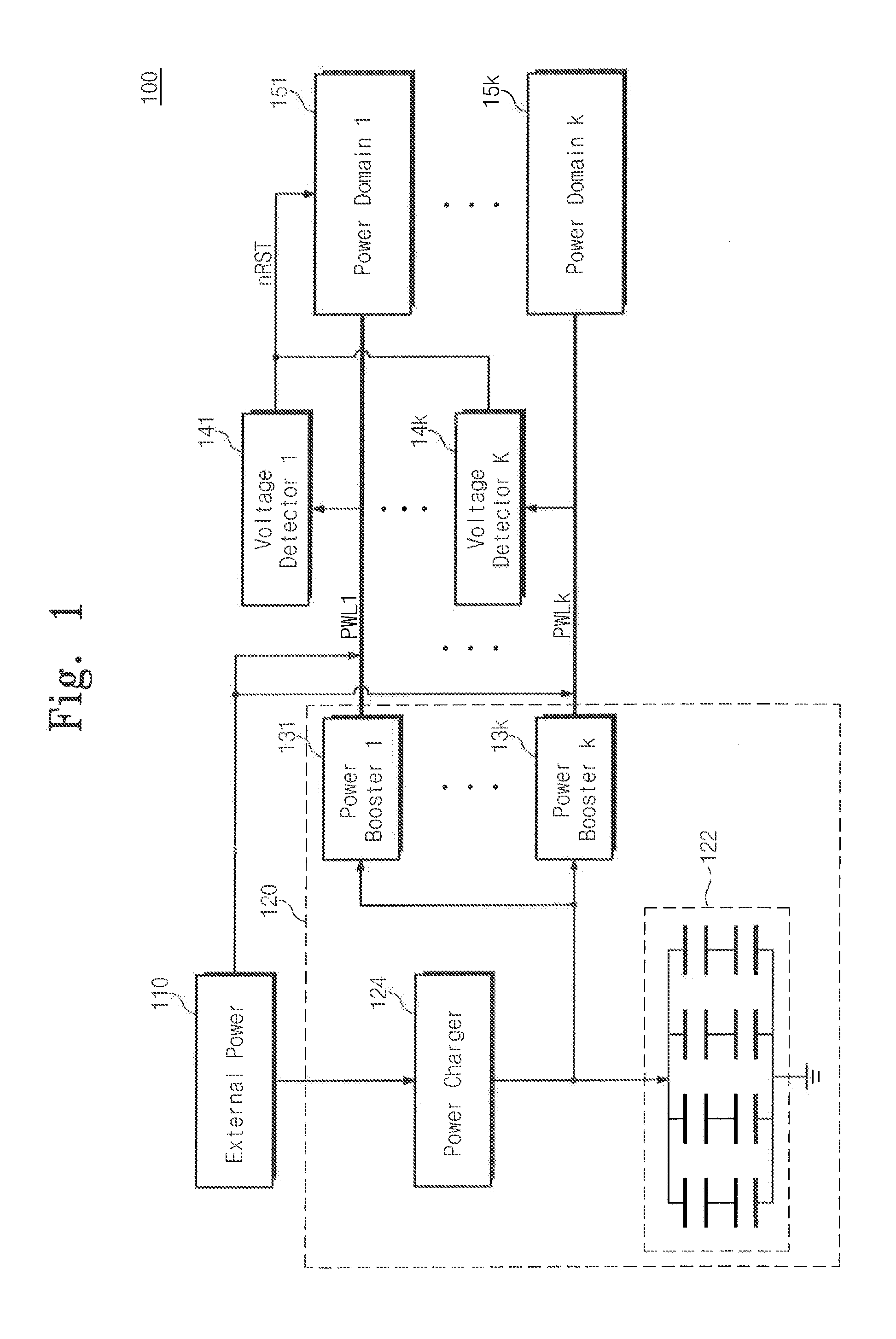
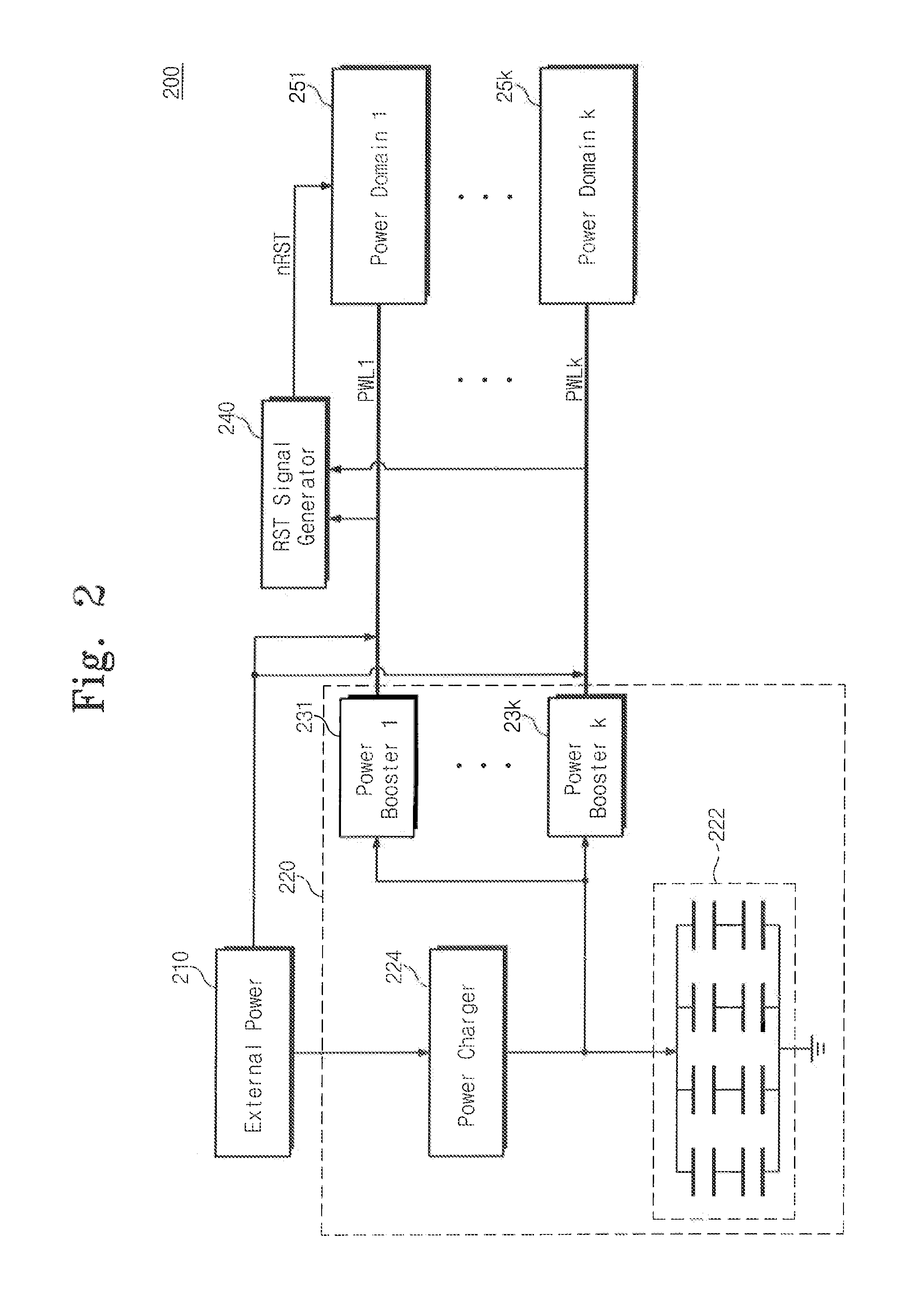
System and methods for run time detection and correction of memory corruption
ActiveUS8510596B1Improve productivitySubstantial time windowNon-redundant fault processingPlatform integrity maintainanceRunning timeBackup
A method or apparatus detects a memory corruption of at least one portion of memory during run-time and corrects the memory corruption of the at least one portion of memory by replacing the at least one portion of memory with a backup of the at least one portion of memory. In this way, memory corruption can be corrected in a timely fashion while minimizing security risks.
Owner:VIRSEC SYST
Block memory engine with memory corruption detection
ActiveUS20140115283A1Memory loss protectionError detection/correctionParallel computingMemory operation
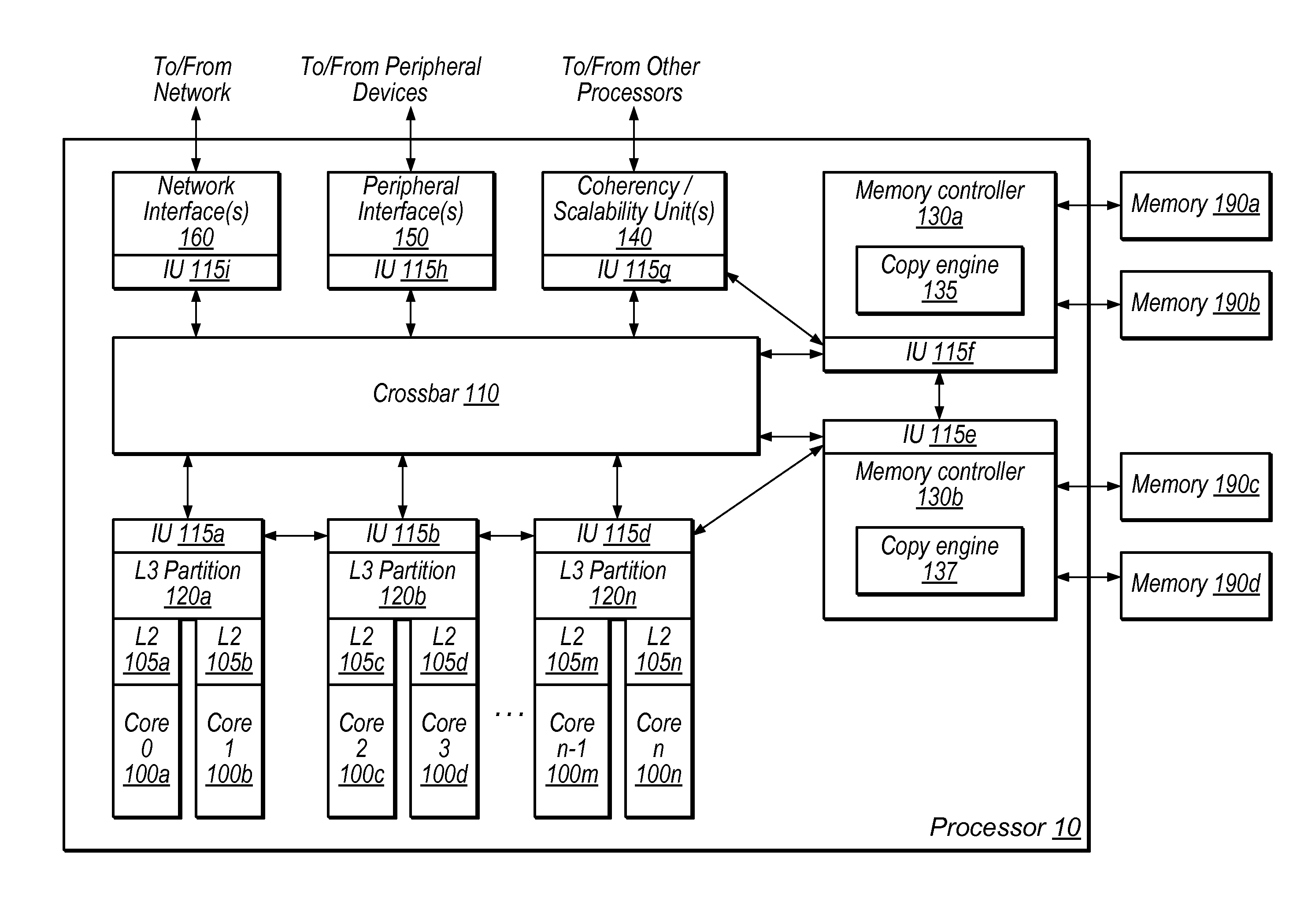
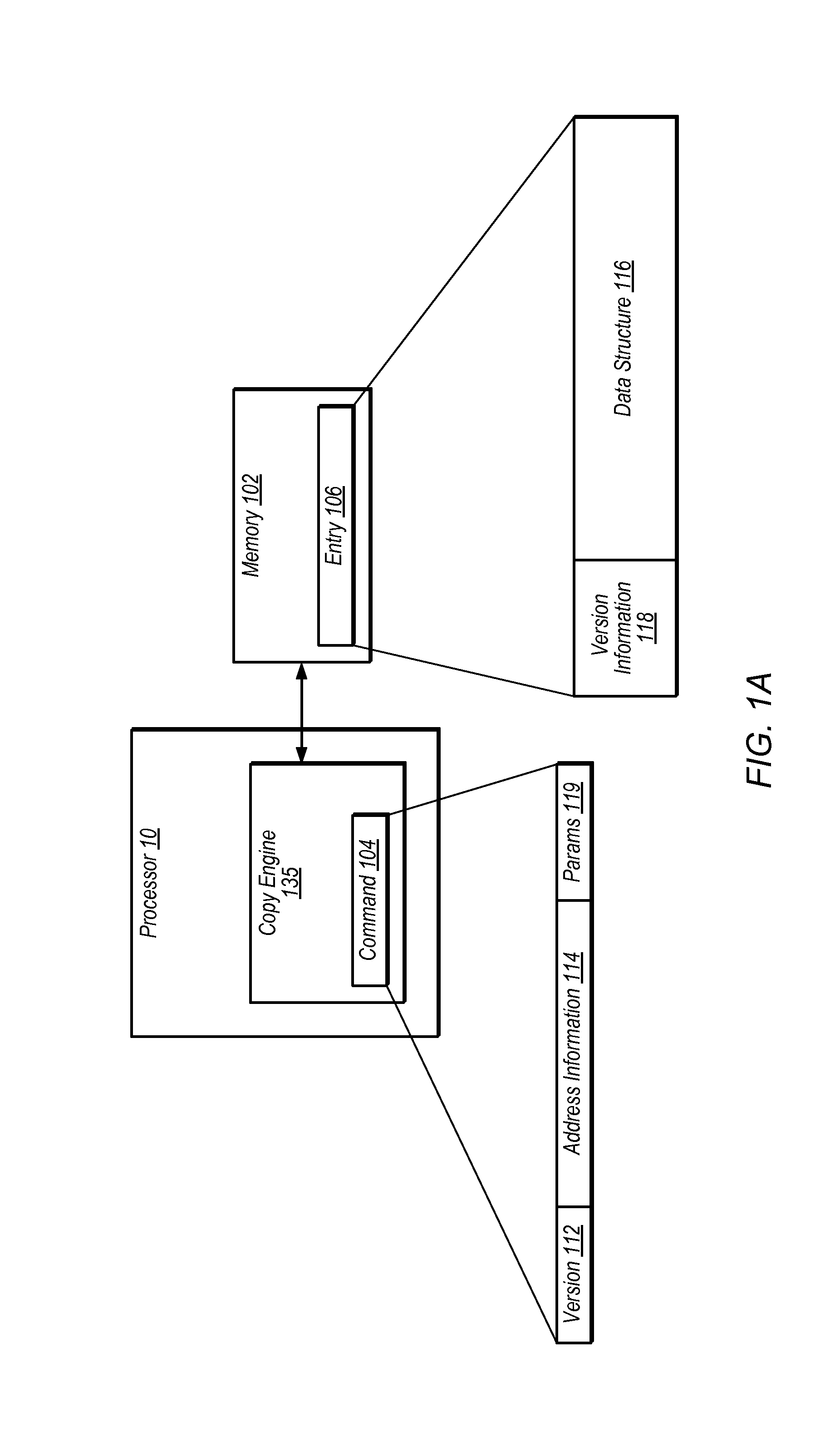
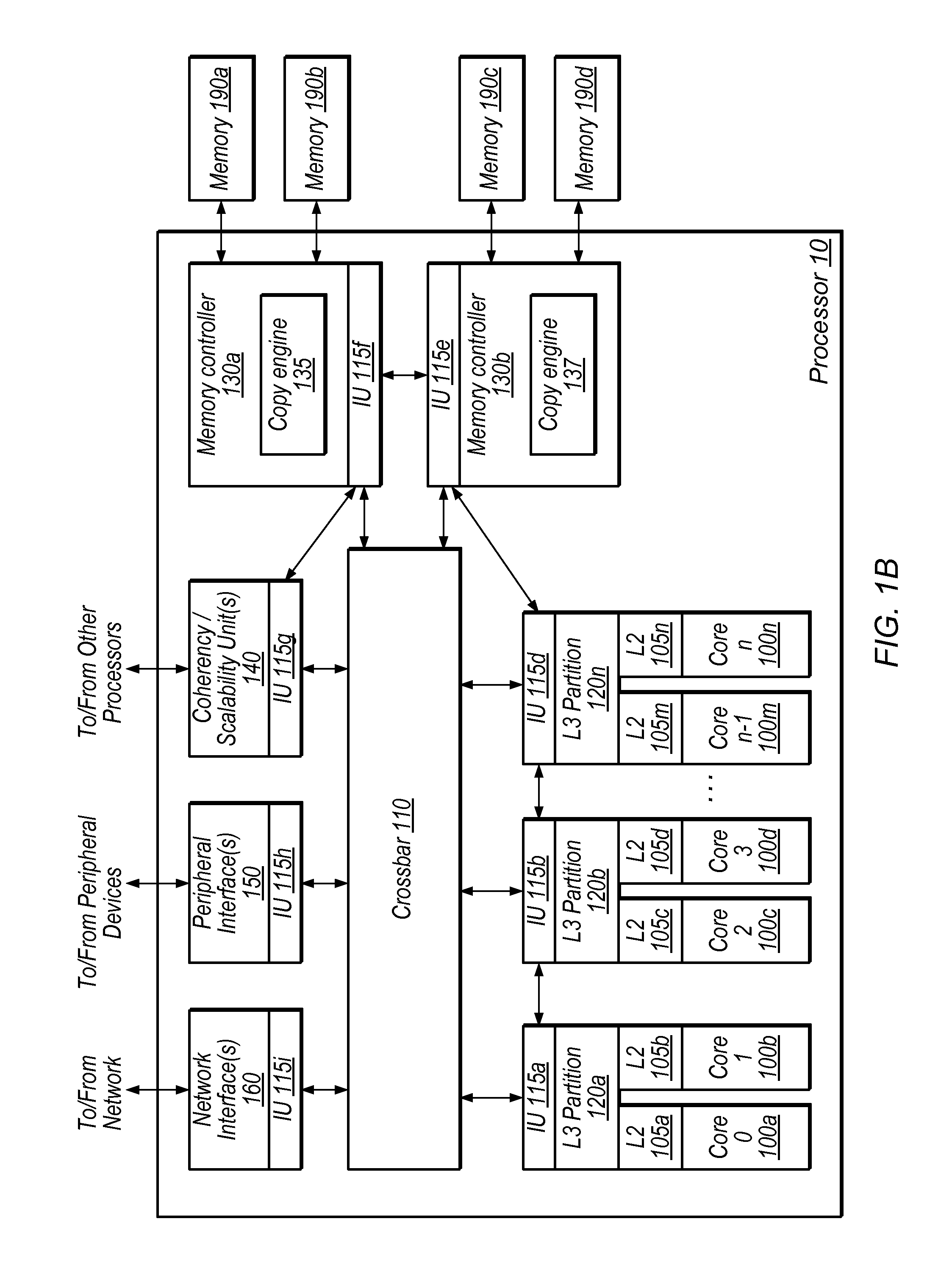
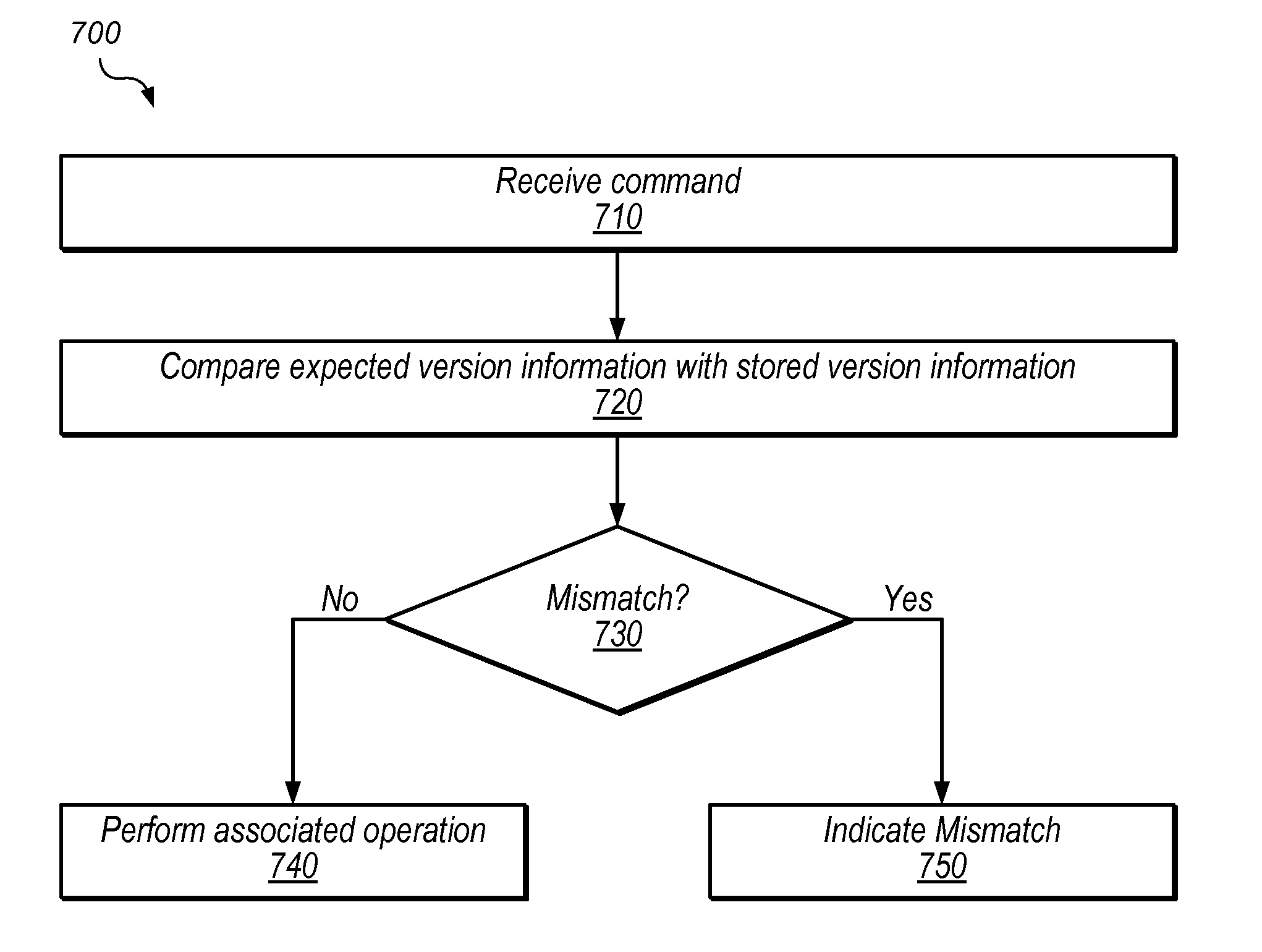
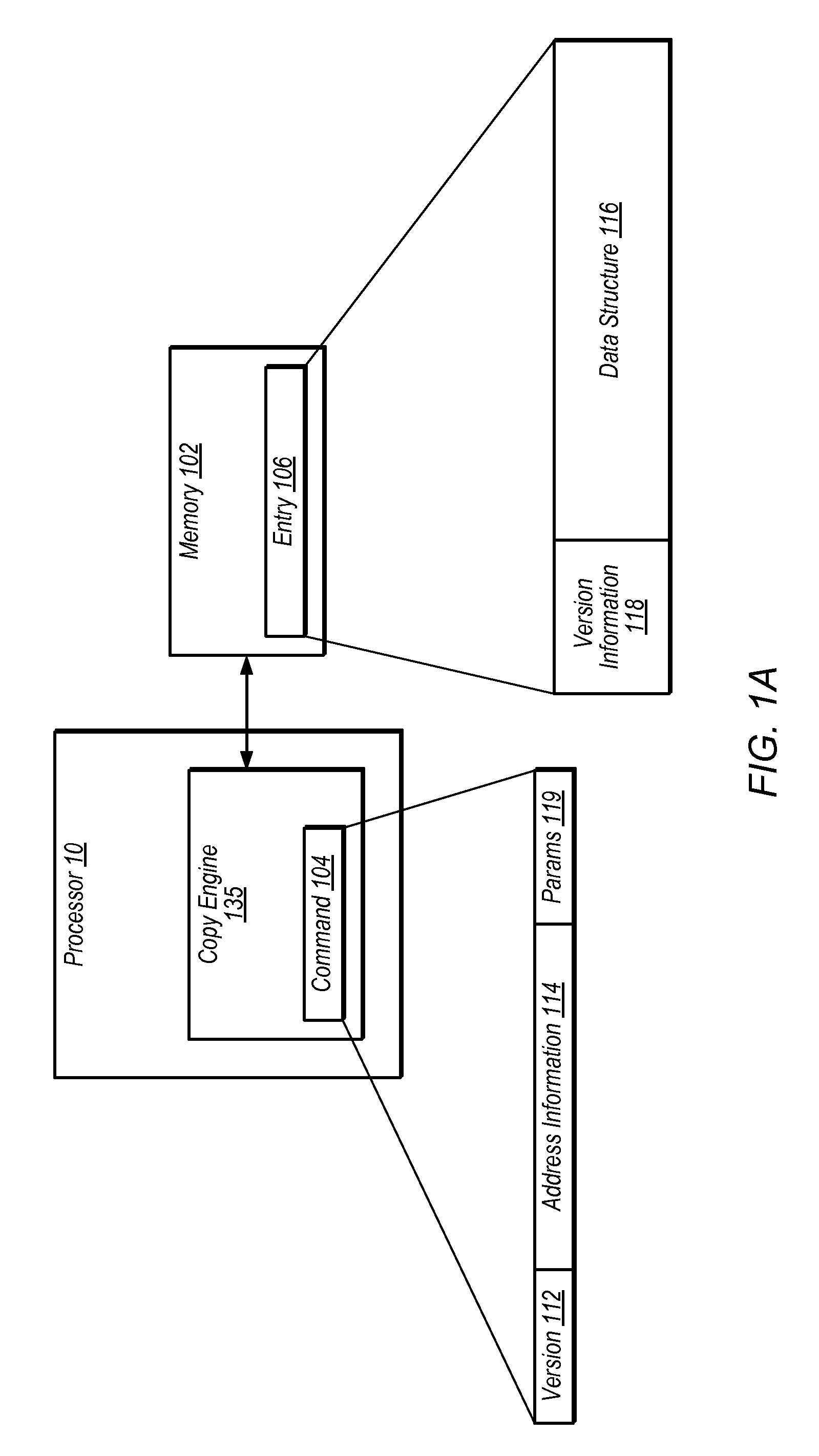
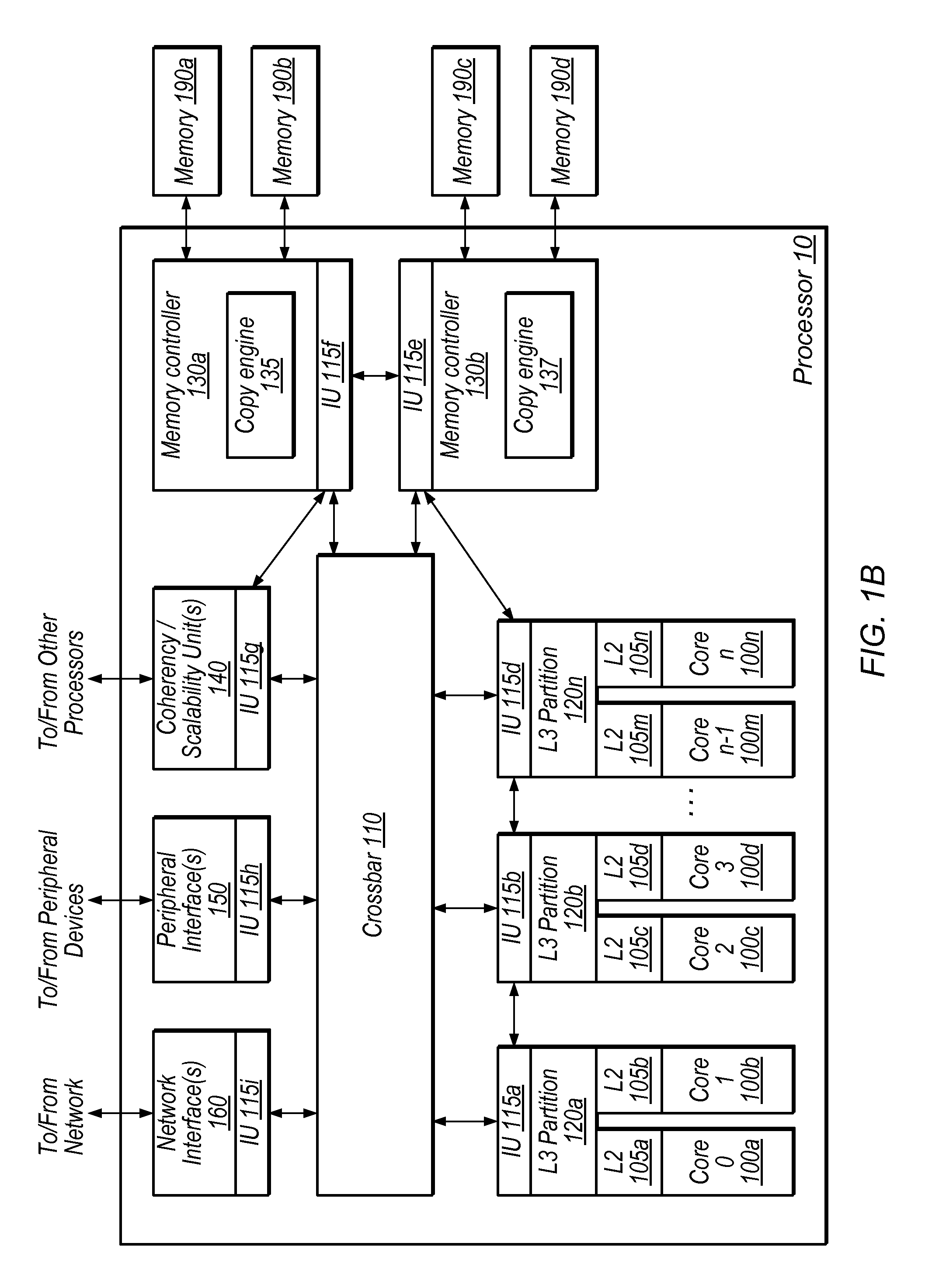
Techniques for handling version information using a copy engine. In one embodiment, an apparatus comprises a copy engine configured to perform one or more operations associated with a block memory operation in response to a command. Examples of block memory operations may include copy, clear, move, and / or compress operations. In one embodiment, the copy engine is configured to handle version information associated with the block memory operation based on the command. The one or more operations may include operating on data in a cache and / or modifying entries in a memory. In one embodiment, the copy engine is configured to compare version information in the command with stored version information. The copy engine may overwrite or preserve version information based on the command. The copy engine may be a coprocessing element. The copy engine may be configured to maintain coherency with other copy engines and / or processing elements.
Owner:ORACLE INT CORP
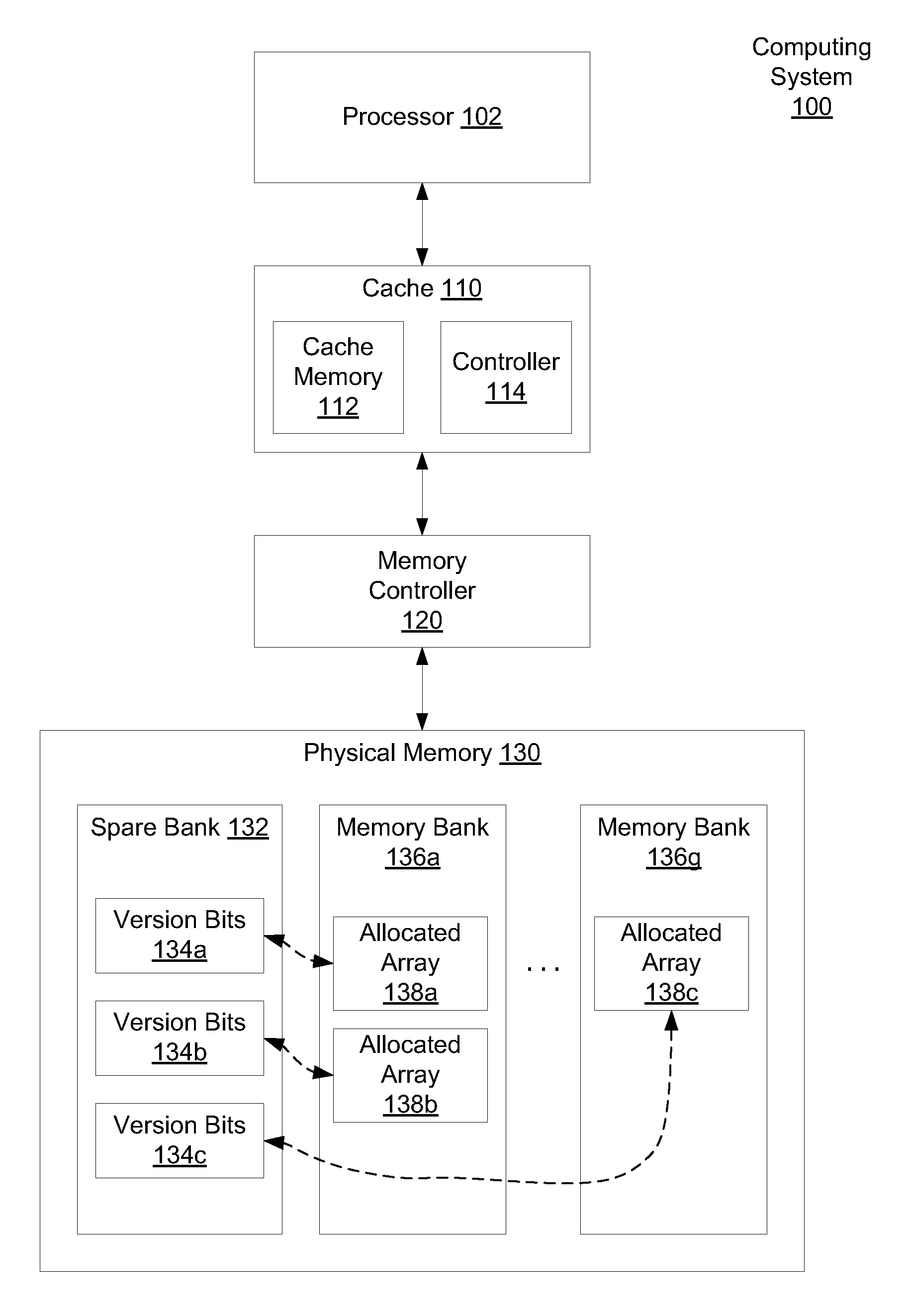
Efficient storage of memory version data
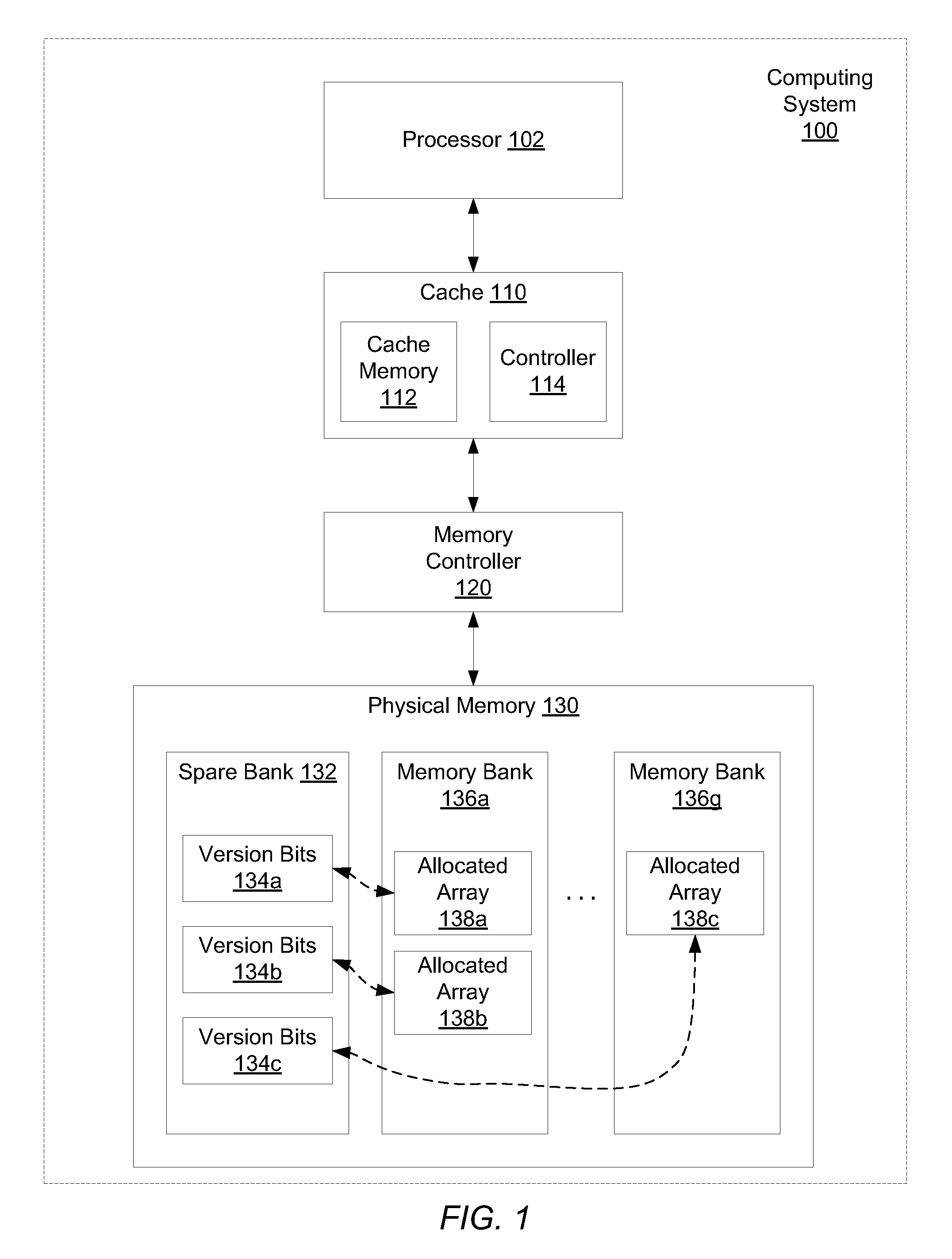
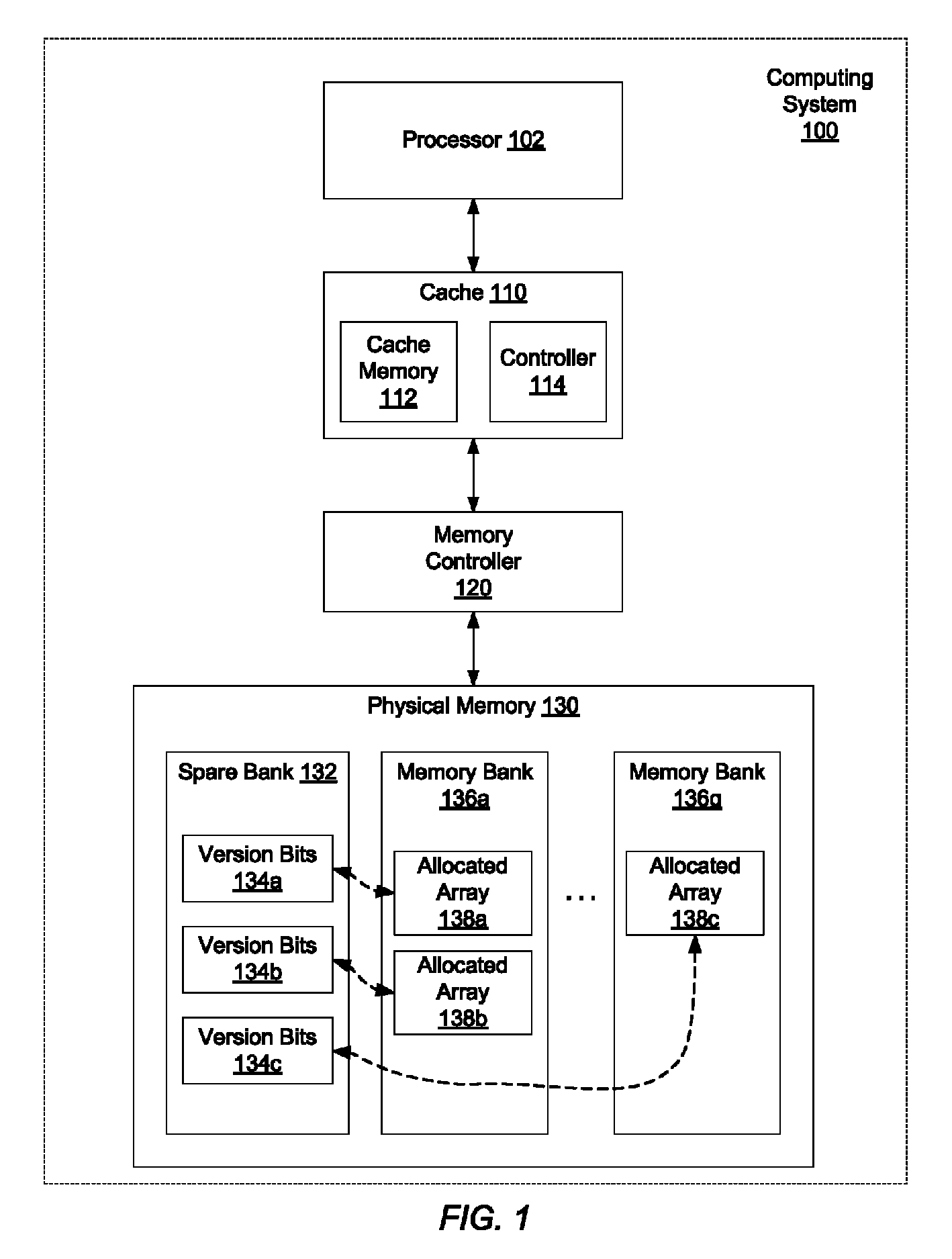
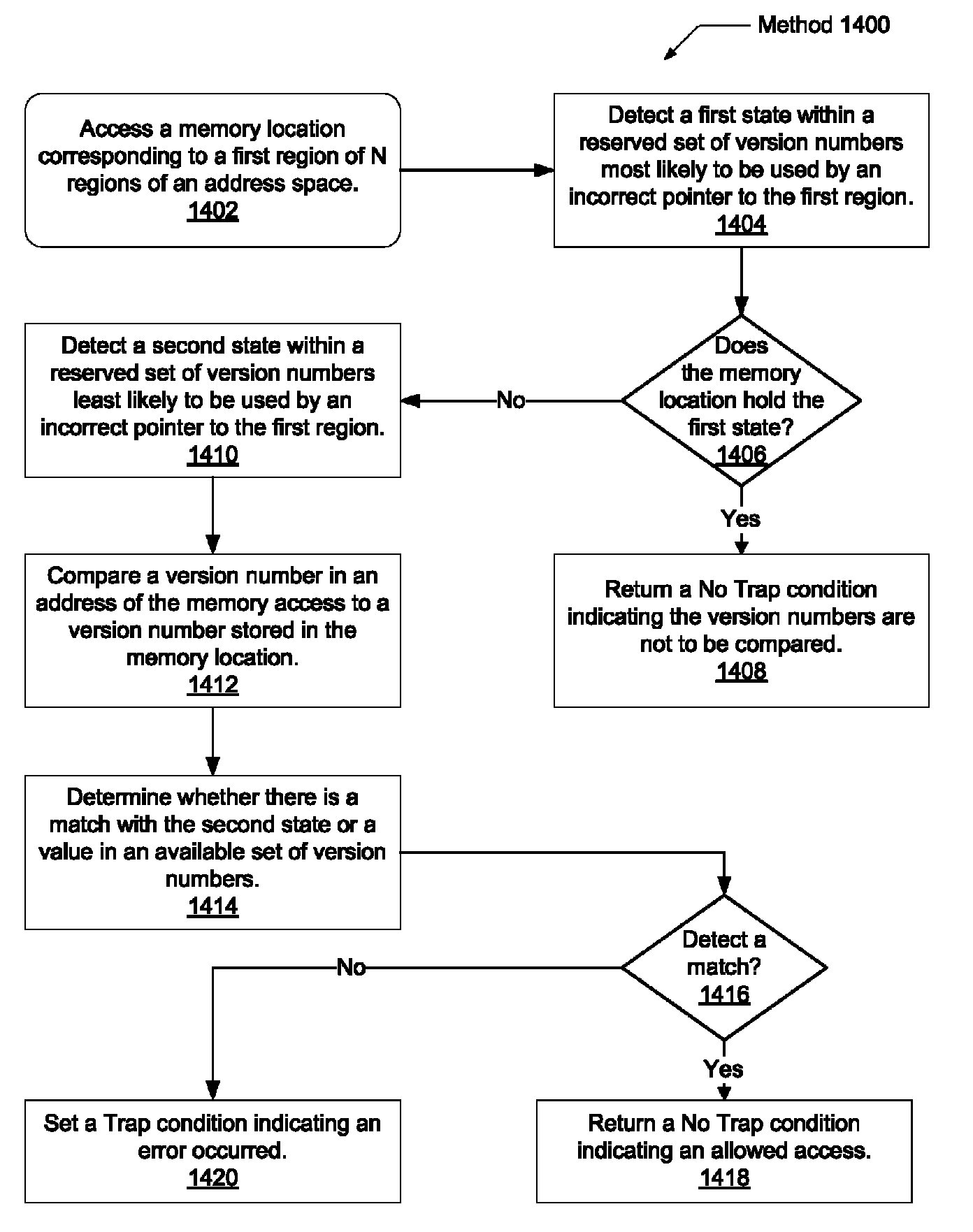
ActiveUS20130013843A1Memory adressing/allocation/relocationPlatform integrity maintainanceFailoverMemory address
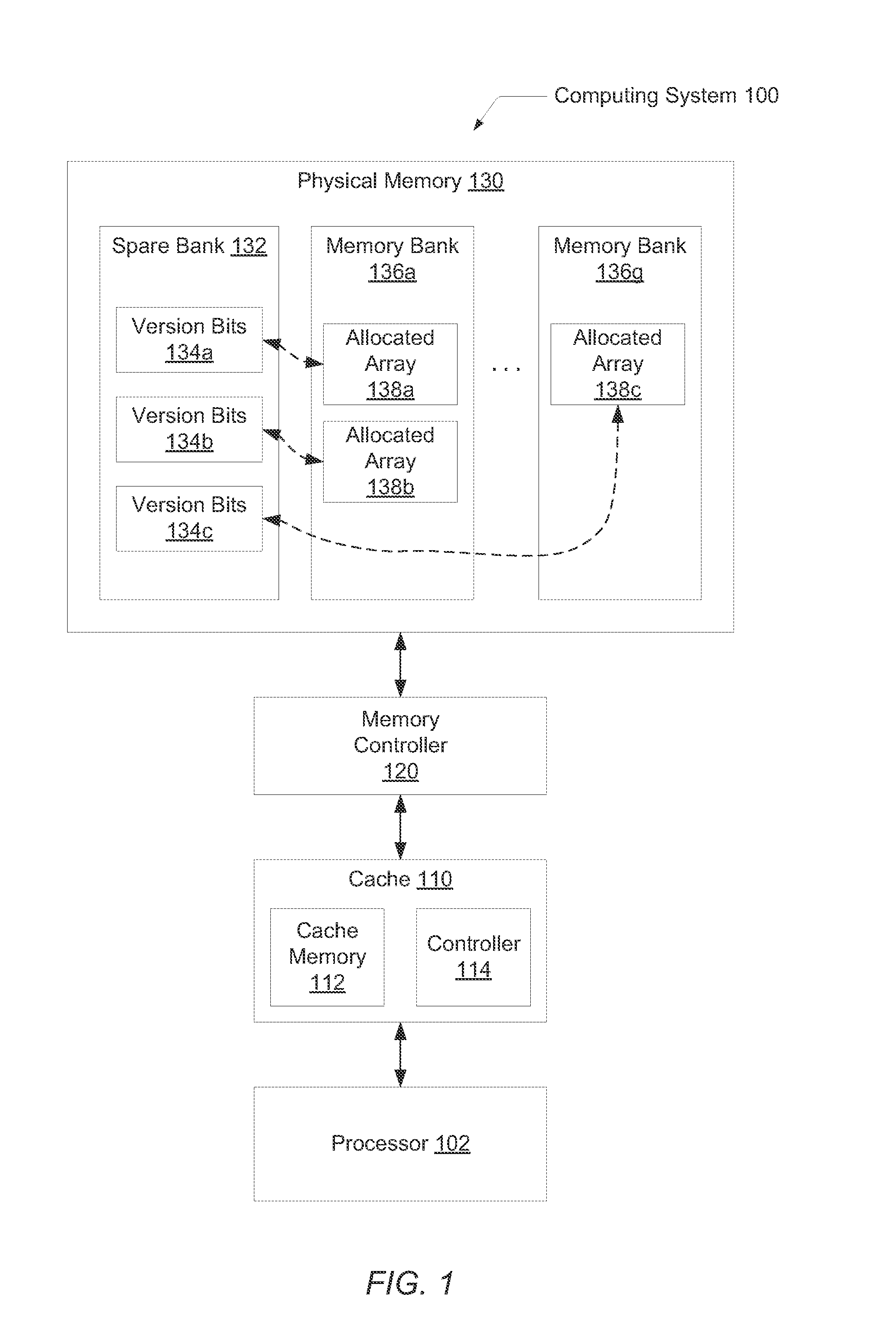
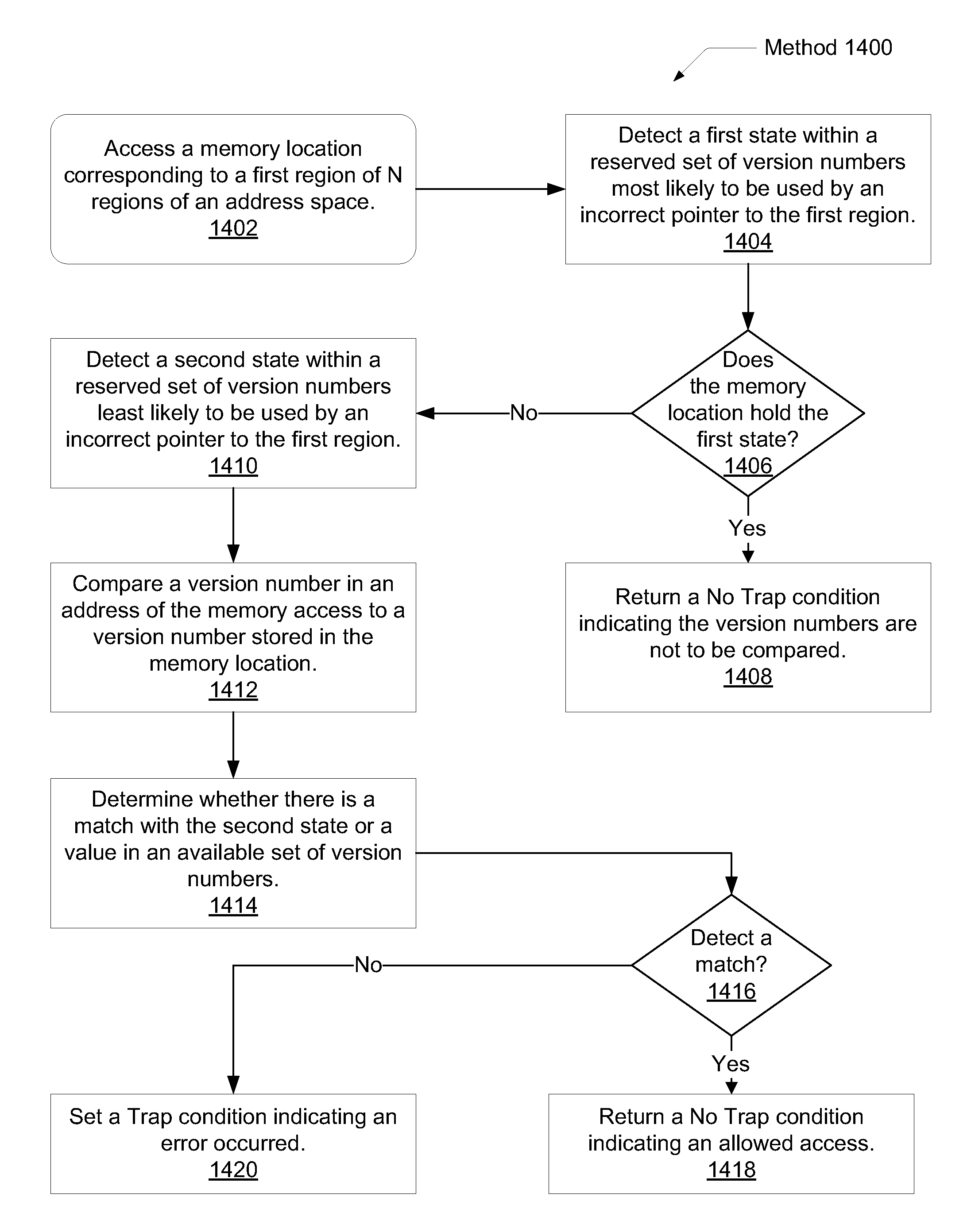
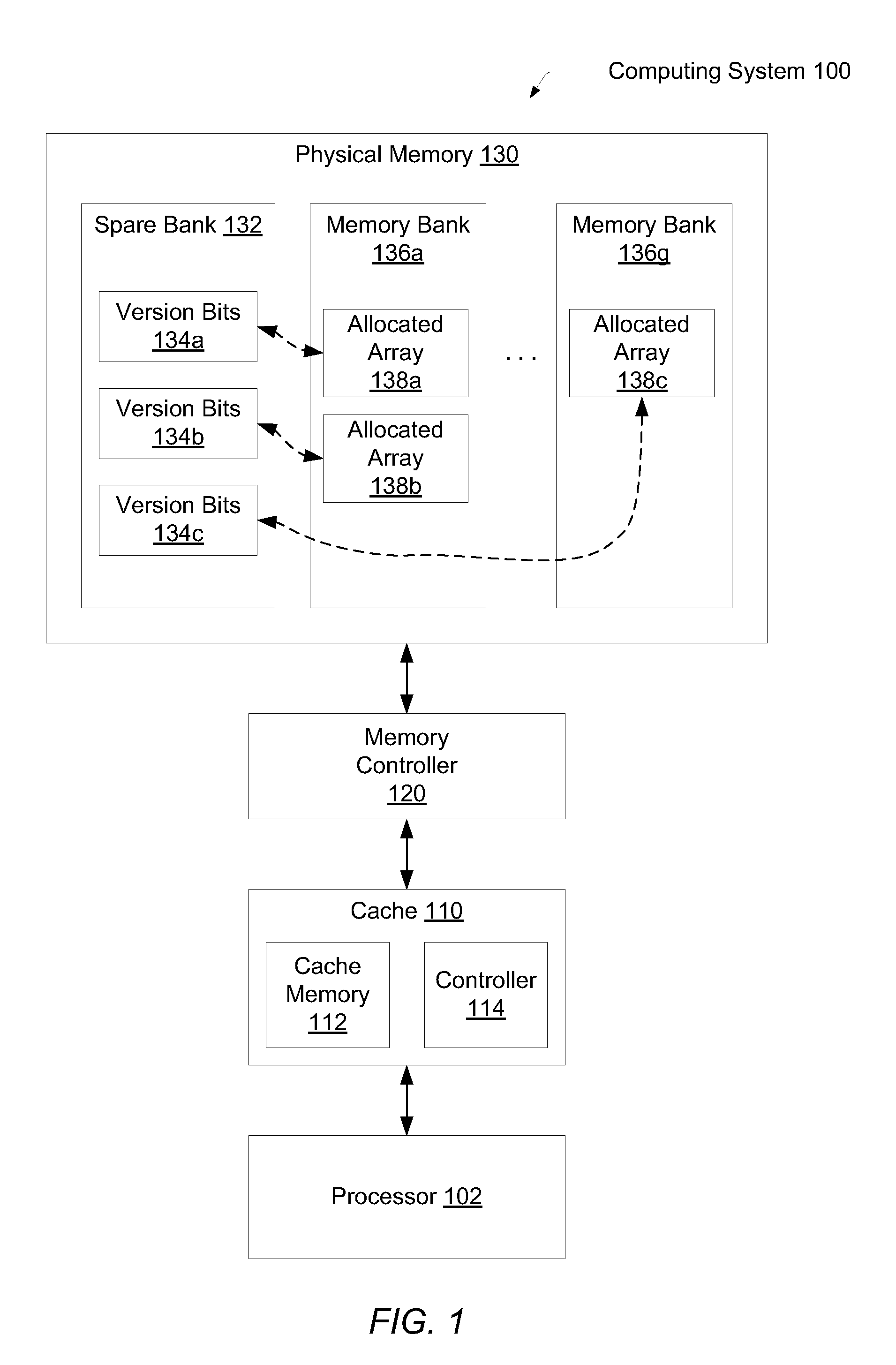
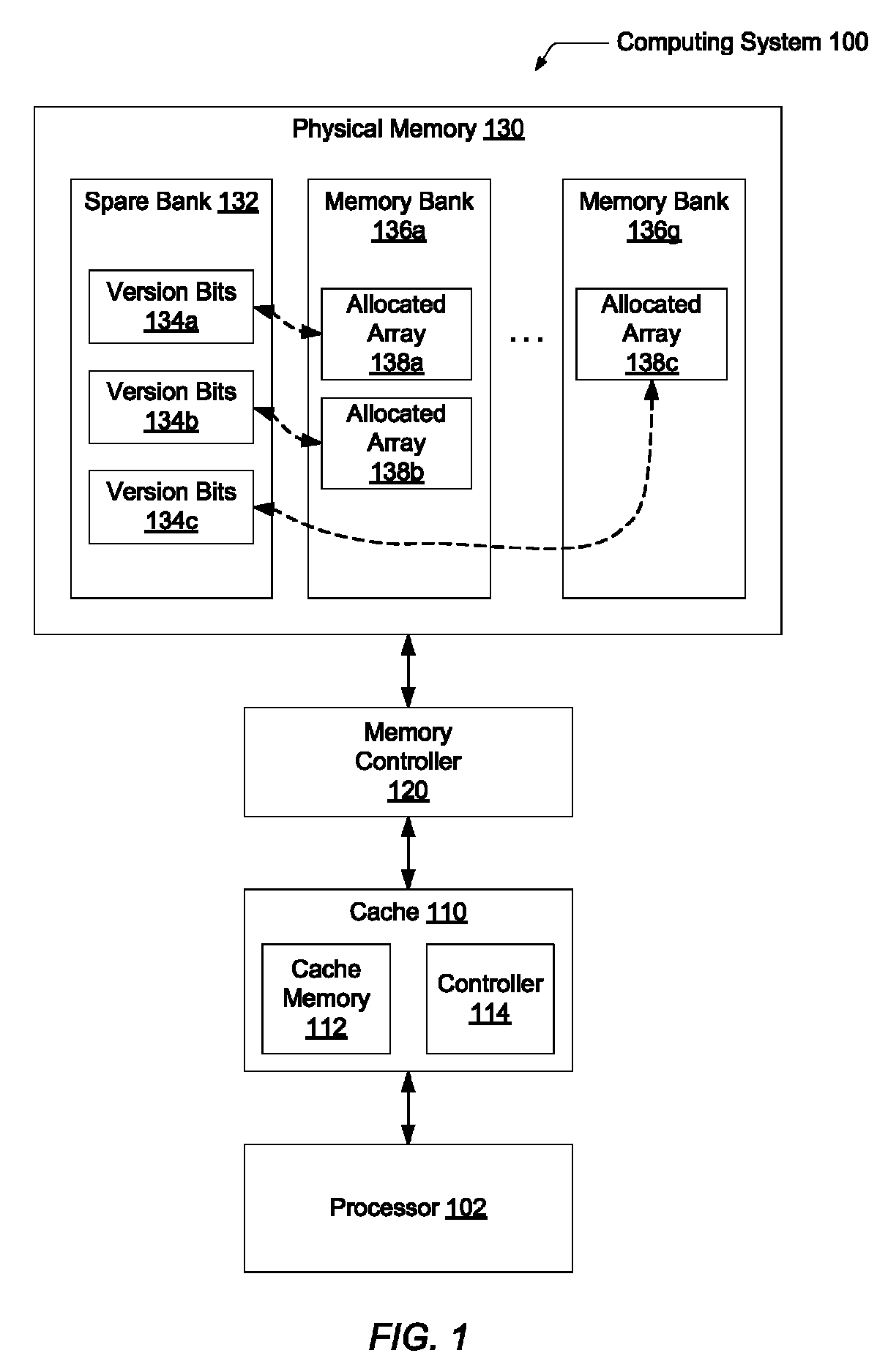
Systems and methods for efficient memory corruption detection in a processor. A processor detects a first data structure is to be allocated in a physical memory. The physical memory may be a DRAM with a spare bank of memory reserved for a hardware failover mechanism. Either the processor or an operating system (OS) determines a first version number corresponding to the first data structure. During initialization of the first data structure, the first version number may be stored in a first location in the spare bank. The processor receives from the OS a pointer holding the first version number. When the processor executes memory access operations targeting the first data structure, the processor compares the first version number with a third version number stored in a location in the physical memory indicated by the memory access address. The processor may set a trap in response to determining a mismatch.
Owner:ORACLE INT CORP
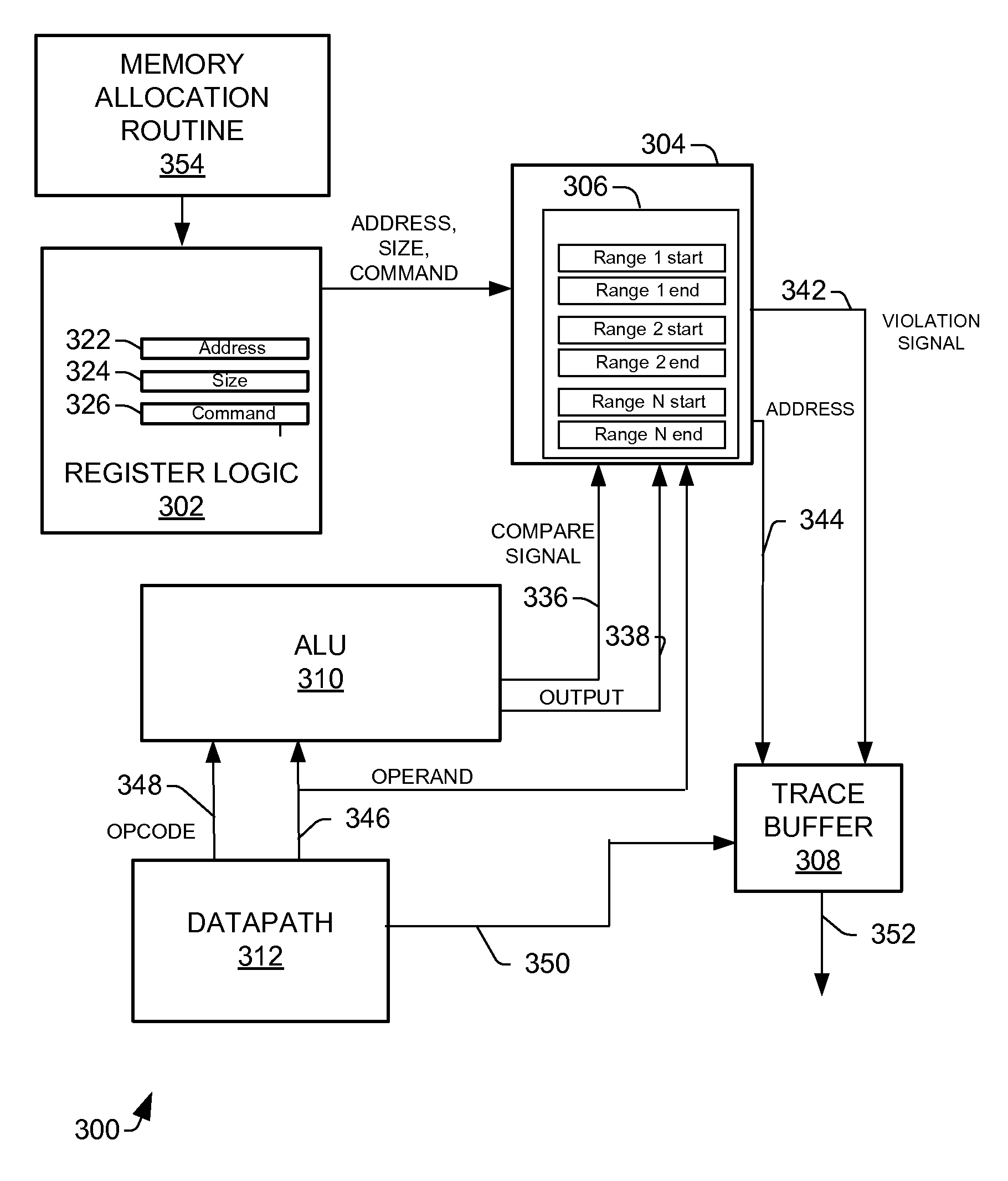
Method and apparatus for realtime detection of heap memory corruption by buffer overruns
ActiveUS8930657B2Transformation of program codeMemory adressing/allocation/relocationHeap overflowArithmetic logic unit
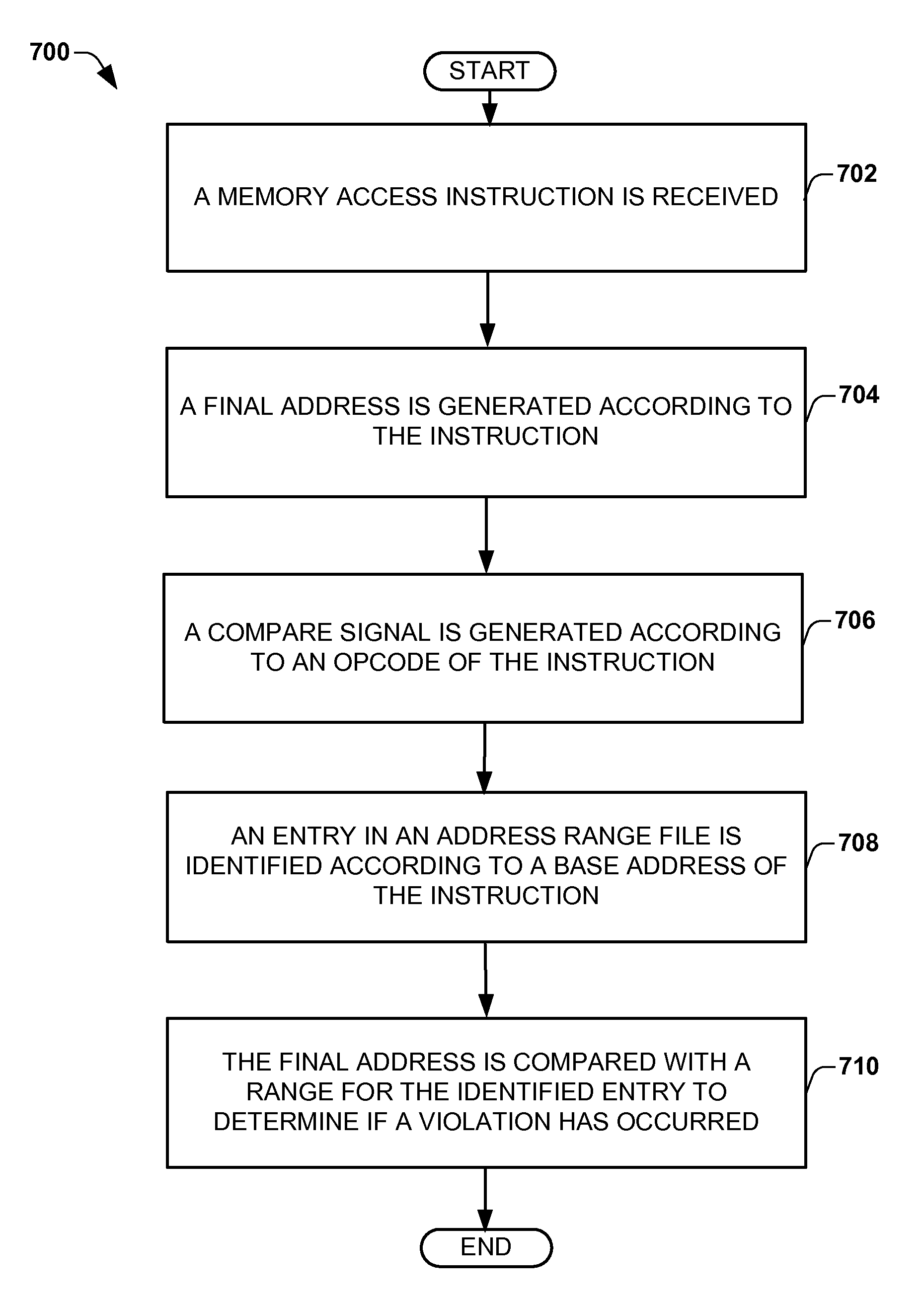
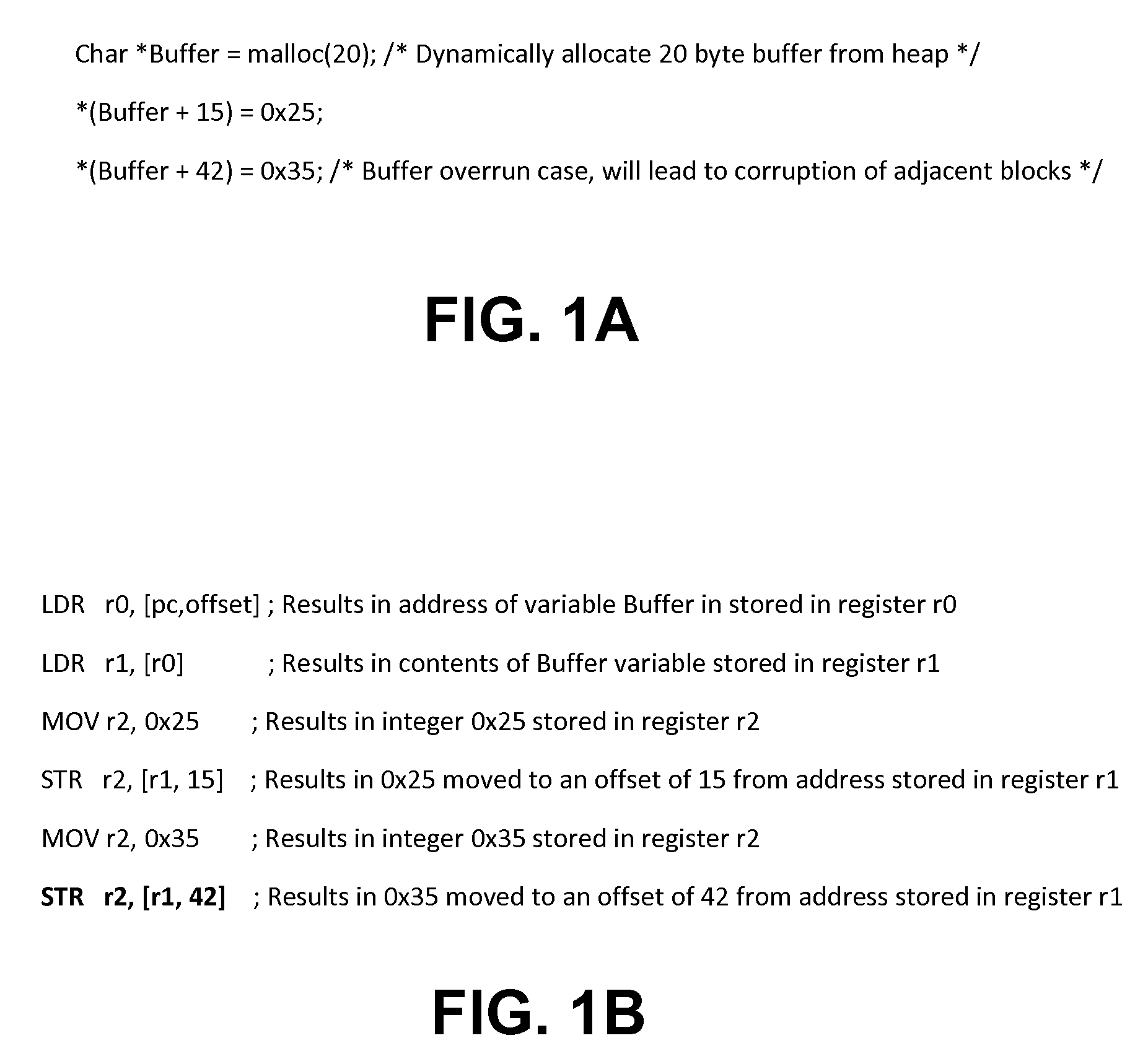
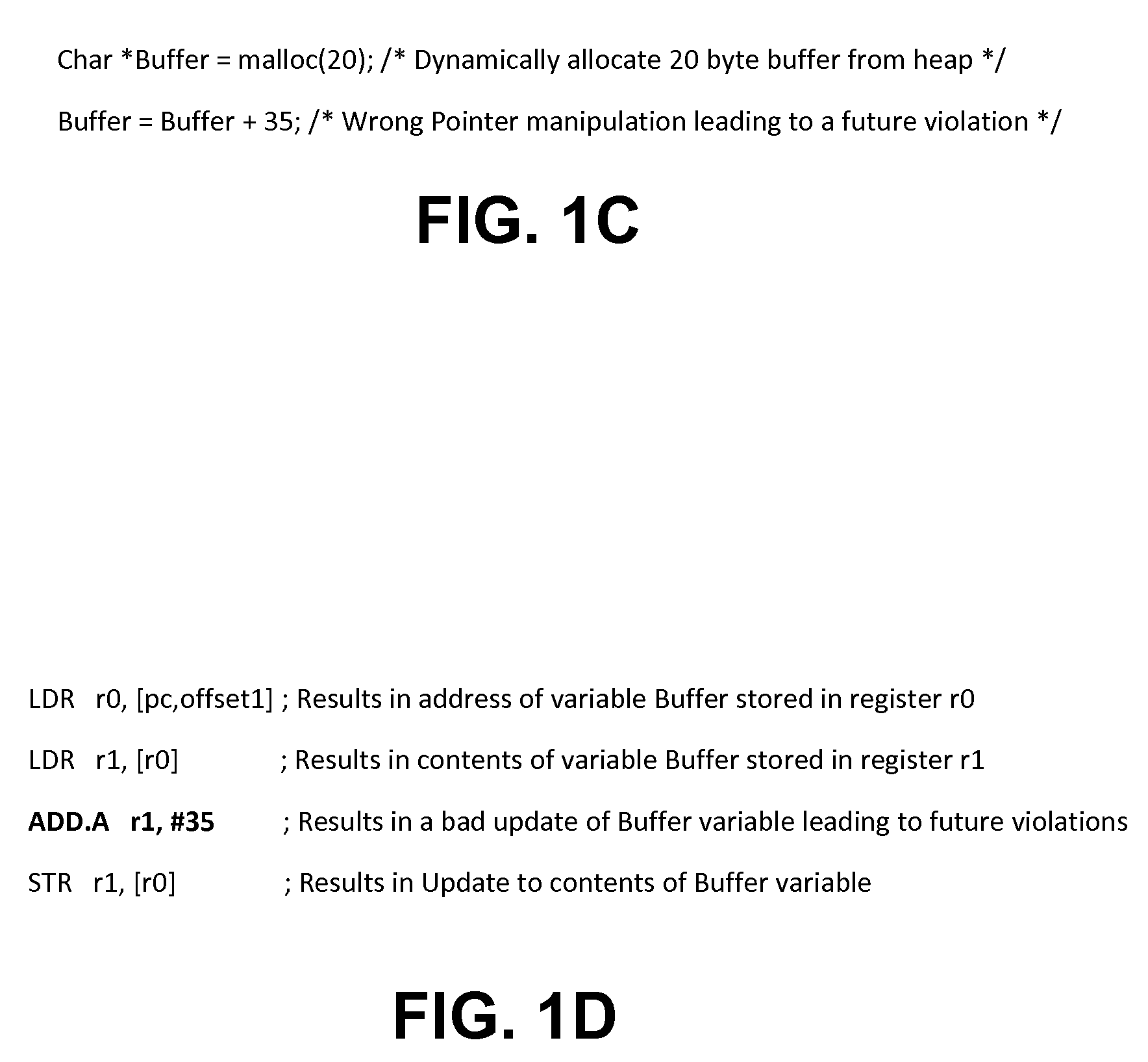
One embodiment of the present invention relates to a heap overflow detection system that includes an arithmetic logic unit, a datapath, and address violation detection logic. The arithmetic logic unit is configured to receive an instruction having an opcode and an operand and to generate a final address and to generate a compare signal on the opcode indicating a heap memory access related instruction. The datapath is configured to provide the opcode and the operand to the arithmetic logic unit. The address violation detection logic determines whether a heap memory access is a violation according to the operand and the final address on receiving the compare signal from the arithmetic logic unit.
Owner:INFINEON TECH AG
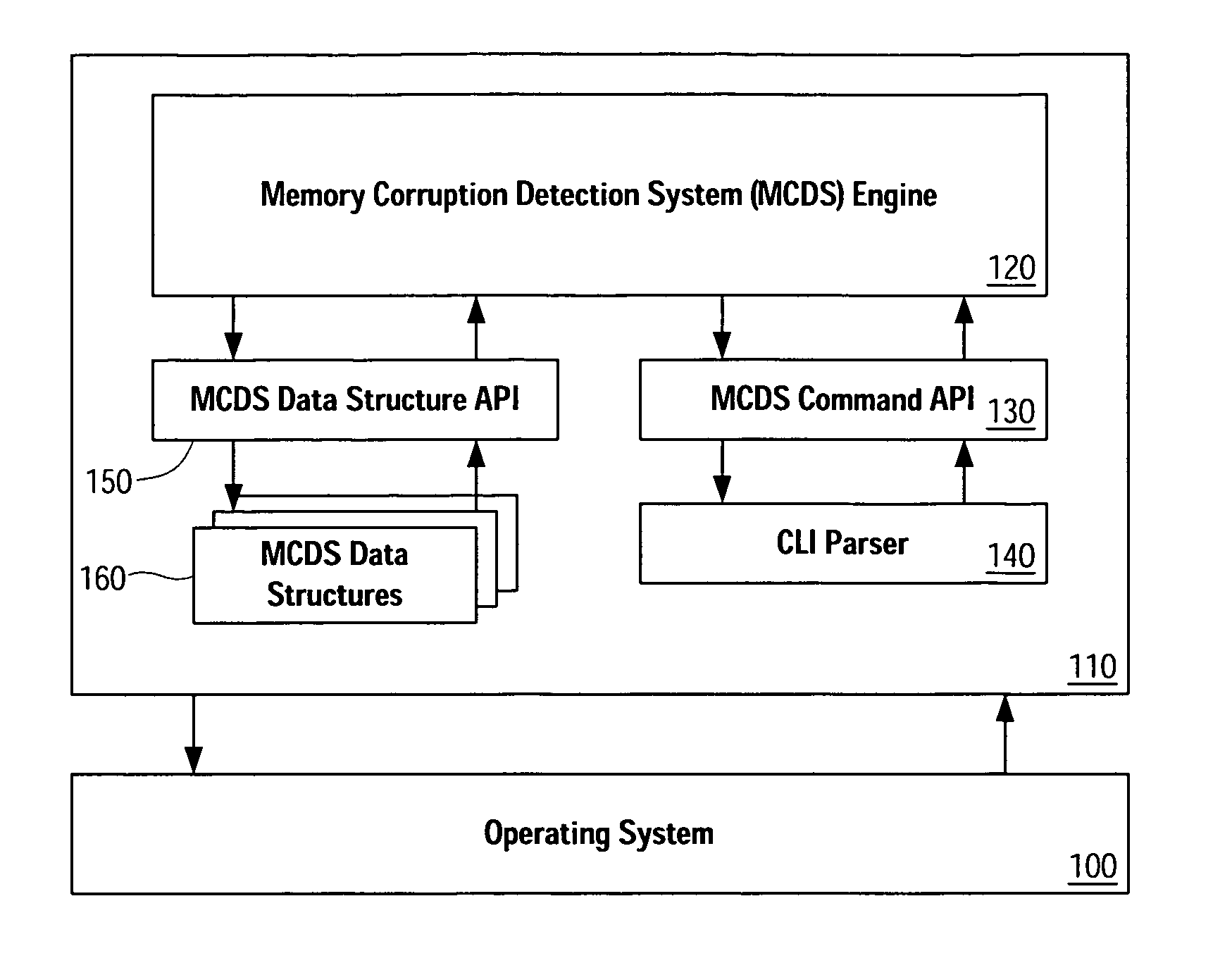
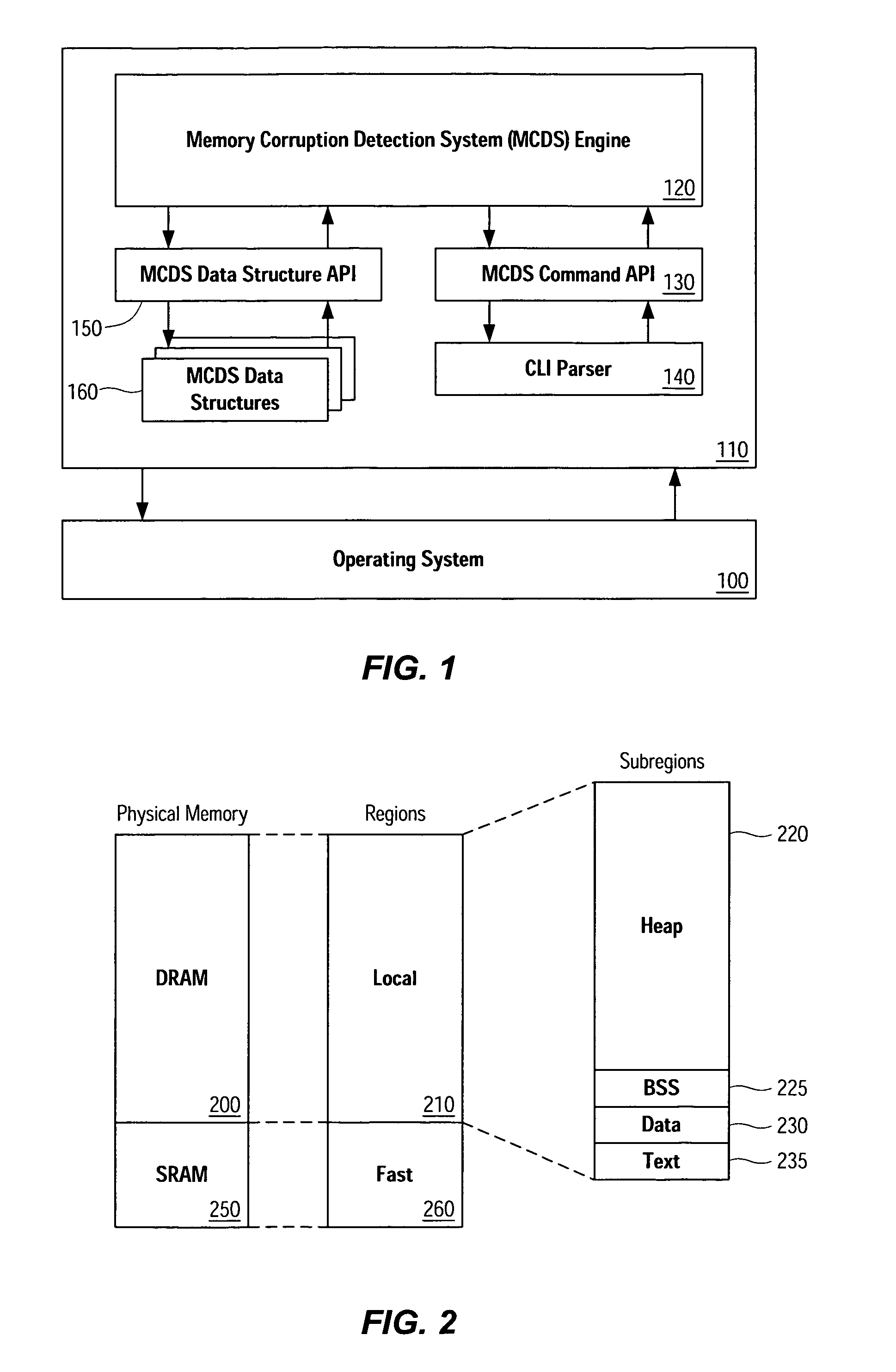
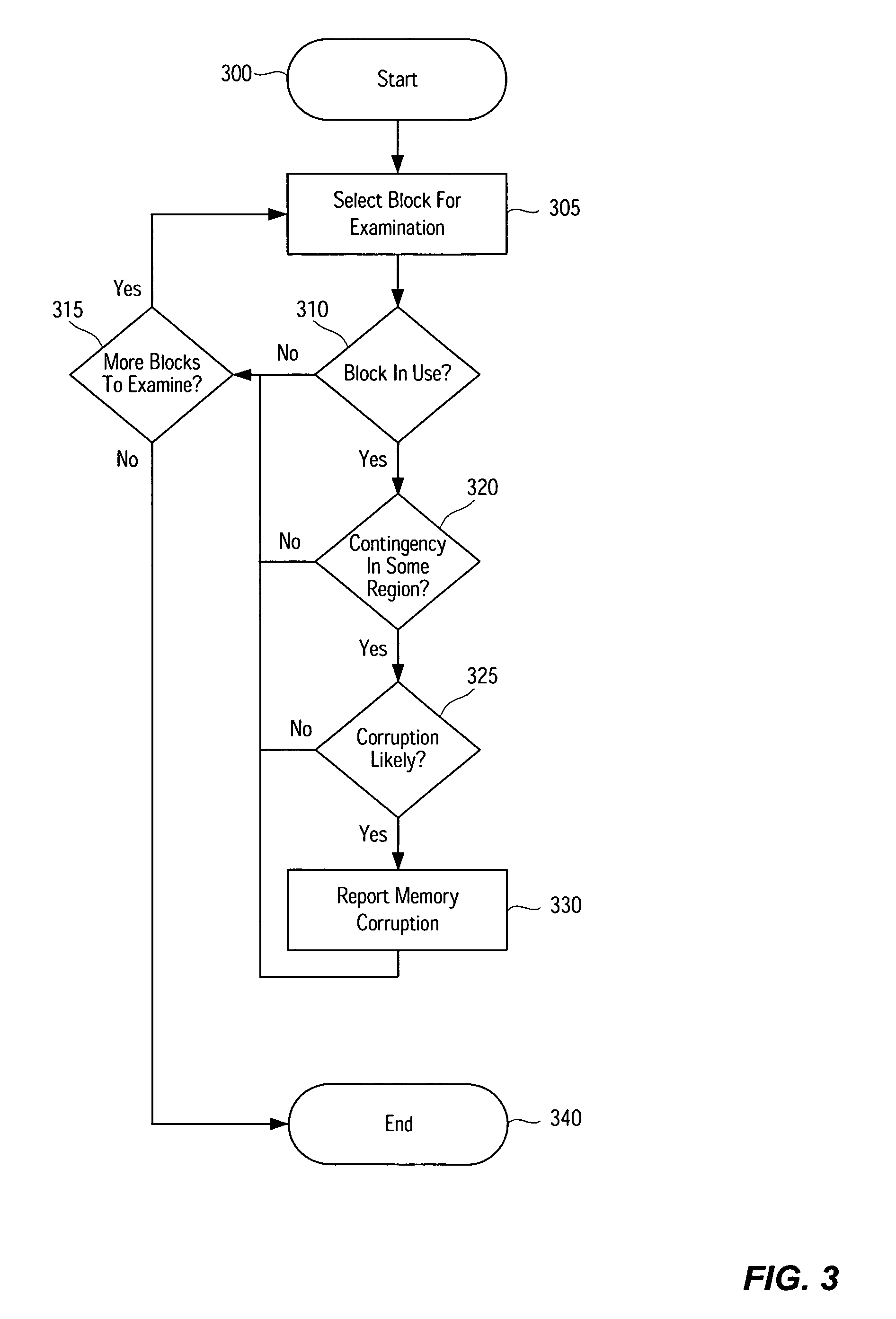
Memory corruption detection system and method using contingency analysis regulation
Systems, methods, apparatus and software can be implemented to detect possible instances of memory corruption. By analyzing memory blocks stored in a memory, provided in a snapshot file, or provided in a core dump, implicit and / or explicit contingency chains can be obtained. Analysis of these contingency chains identifies potential memory corruption sites, and subsequent verification provides greater confidence in the identification.
Owner:CISCO TECH INC
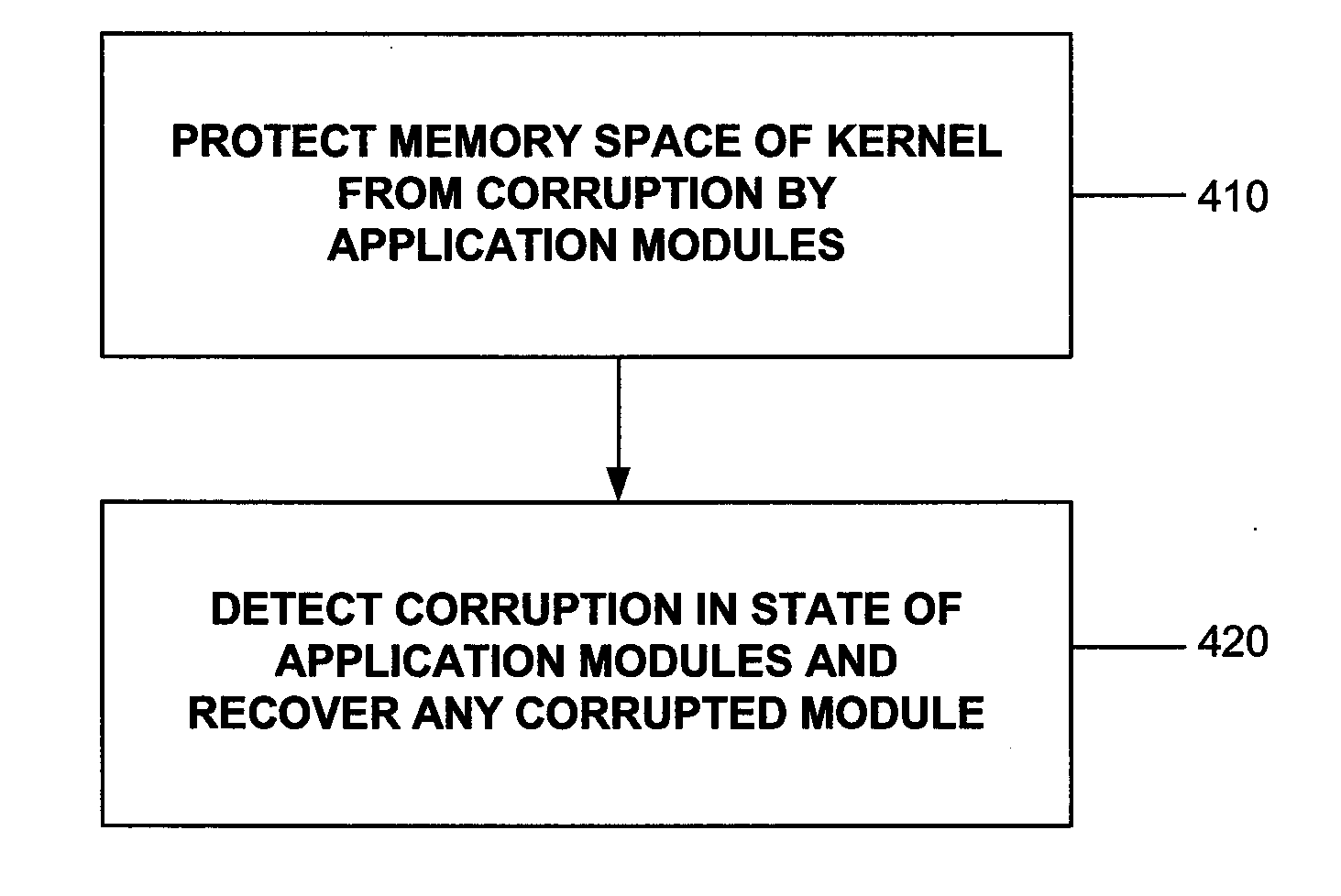
Method and system usable in sensor networks for handling memory faults
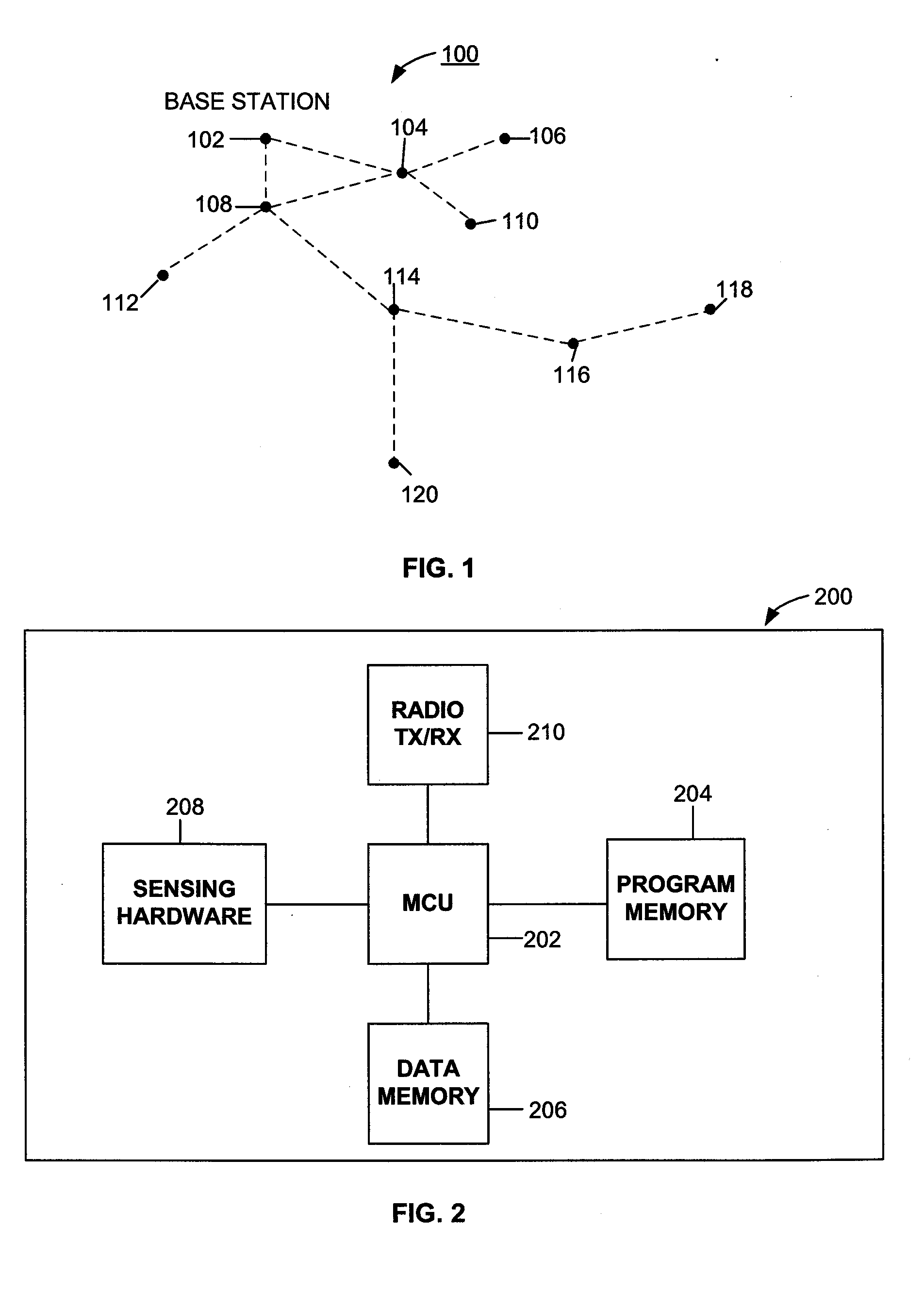
InactiveUS20070156951A1Corrupt stateProtection operationError detection/correctionMemory systemsMemory faultsOperational system
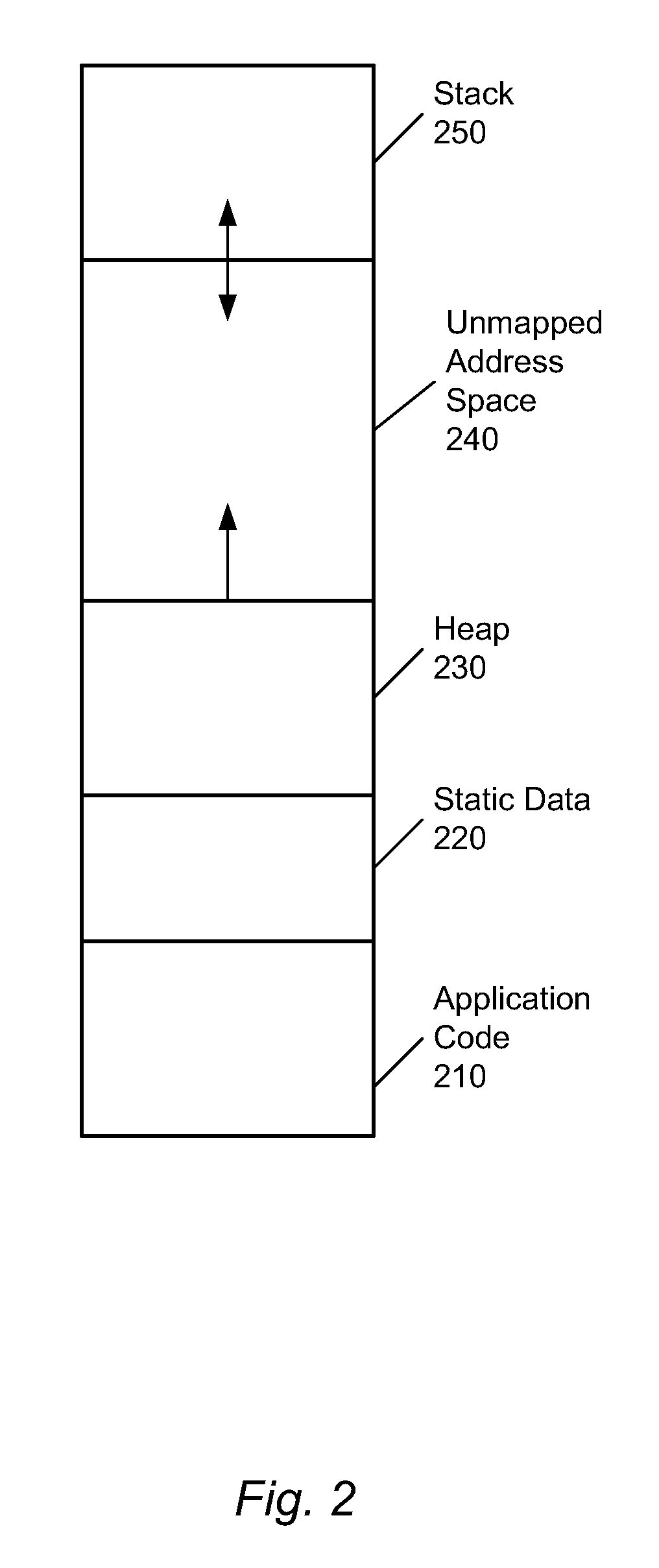
A method and system usable in sensor networks for handling memory faults is disclosed. In order to protect the operating system of a sensor node, coarse-grained memory protection is provided by creating and enforcing an application fault domain in the data memory address space of the sensor node. The data memory accessed by the application modules is restricted to the region (which defines the application fault domain) within the data memory address space. The application modules are prevented from accessing memory outside the application fault domain through software-based run-time checks. The state belonging to the operations system is maintained outside of the application fault domain, and is thus protected from memory corruption from any application module. In order to ensure that an application module does not operate on a corrupted state, fine-grained error detection and recovery is provided within the application fault domain. Any corruption of memory within the application fault domain is detected by a run-time memory integrity verifier implemented in the operating system kernel. Recovery involves purging the corrupted state and restarting only the affected application module to operate on an uncorrupted state.
Owner:NEC CORP
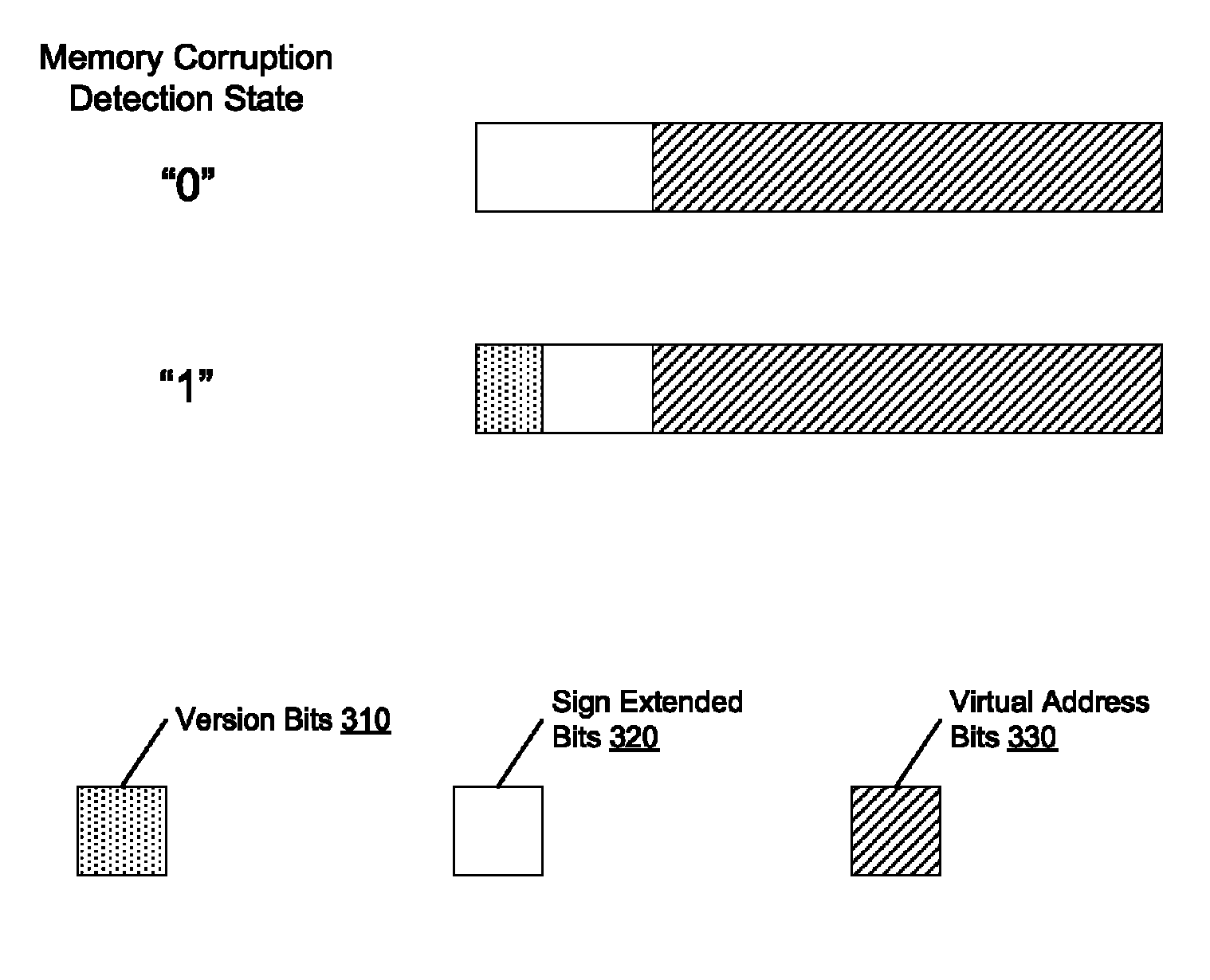
Maximizing encodings of version control bits for memory corruption detection
ActiveUS20130036332A1Platform integrity maintainanceStatic storageParallel computingVirtual address space
Systems and methods for maximizing a number of available states for a version number used for memory corruption detection. A physical memory may be a DRAM comprising a plurality of regions. Version numbers associated with data structures allocated in the physical memory may be generated so that version numbers of adjacent data structures in a virtual address space are different. A reserved set and an available set of version numbers are associated with each one of the plurality of regions. A version number in a reserved set of a given region may be in an available set of another region. The processor detects no memory corruption error in response to at least determining a version number stored in a memory location in a first region identified by a memory access operation is also in a reserved set associated with the first region.
Owner:ORACLE INT CORP
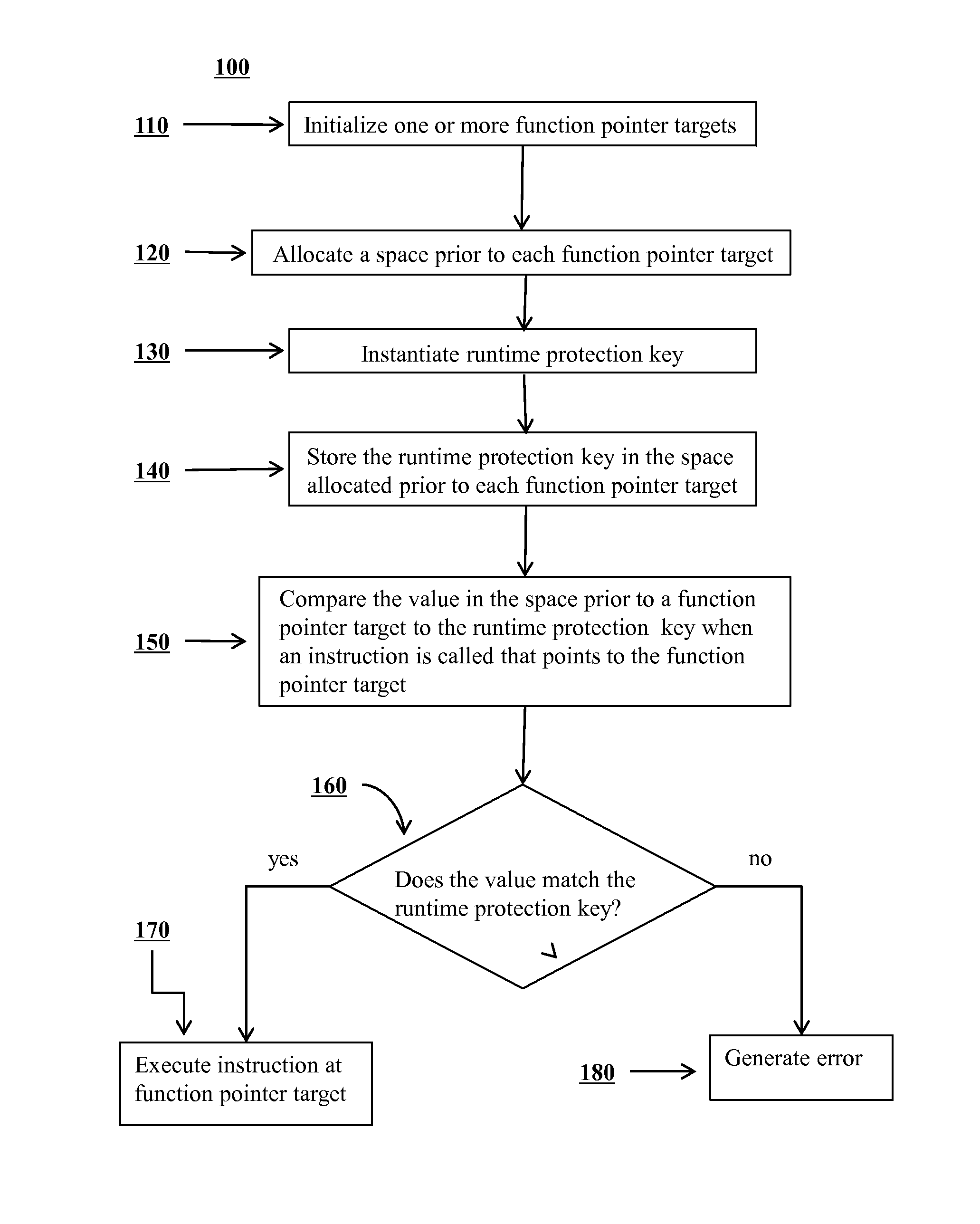
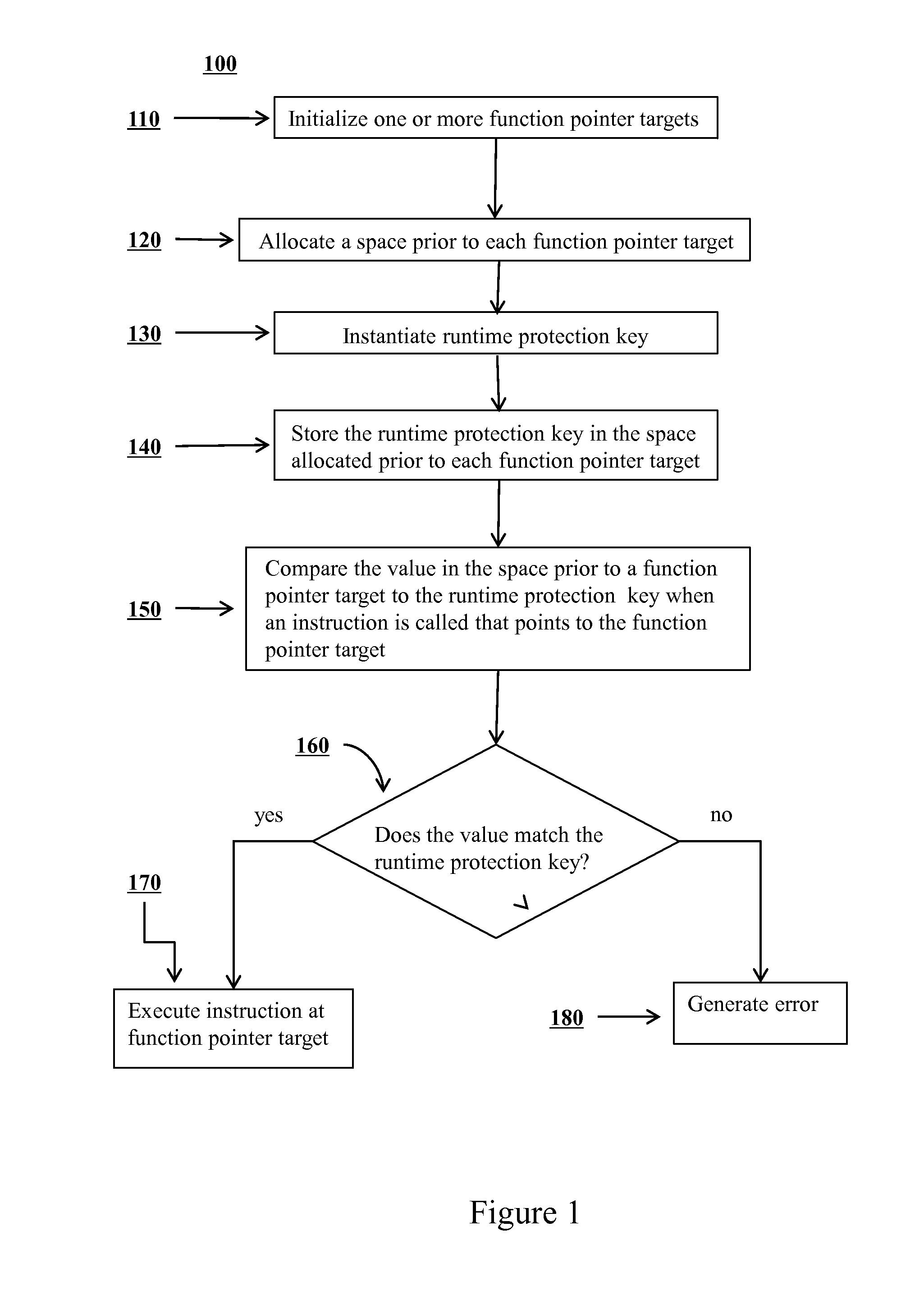
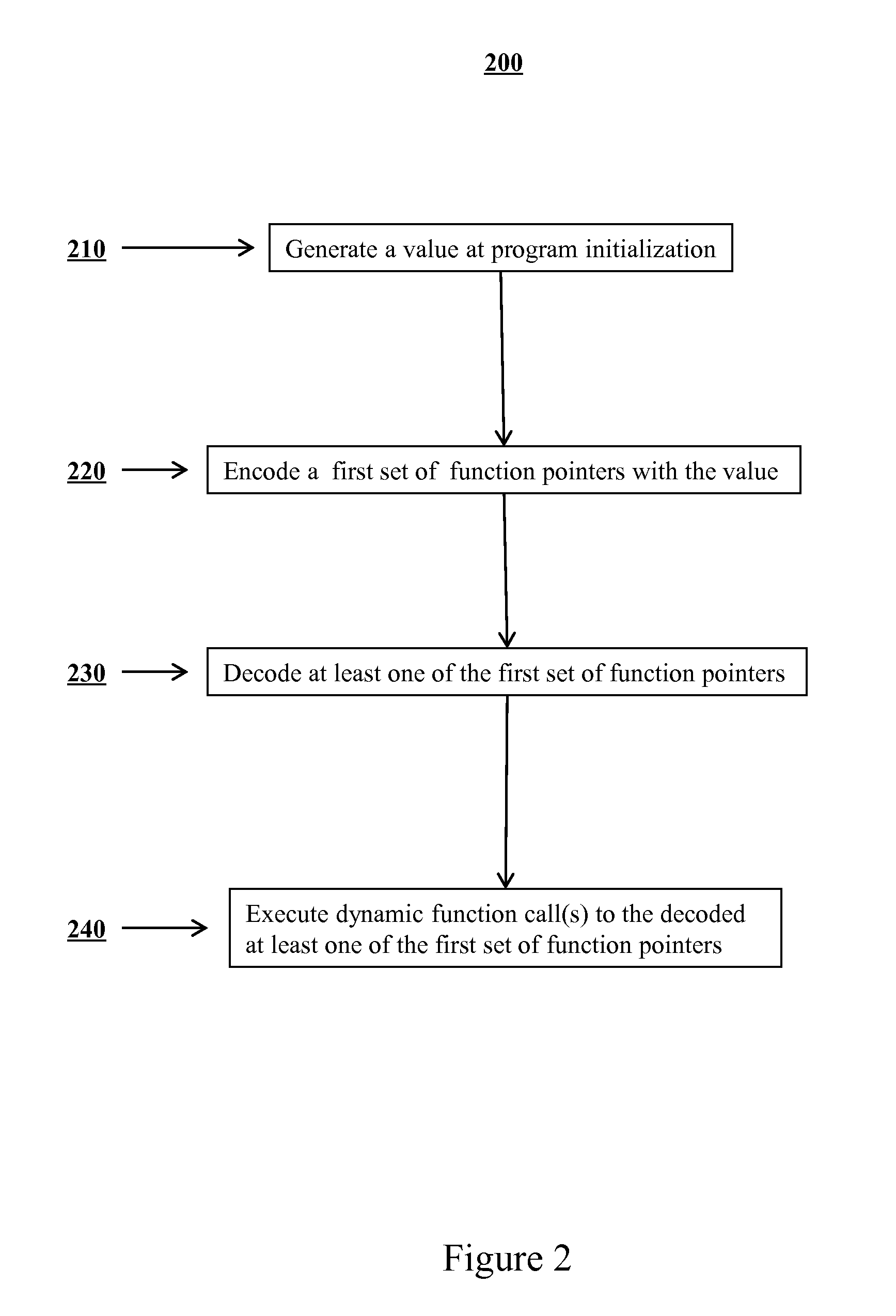
Mitigation of function pointer overwrite attacks
ActiveUS20140020092A1Reduce attackMitigating function pointer overwrite attackMemory loss protectionError detection/correctionFunction pointerExecution control
Methods are disclosed for improving security of computer software and preventing potential attackers from gaining control of computer software via function pointer overwrite attacks. One or more additional layers of complexity may be imposed that would have to be circumvented in order to gain execution control over portions of software. One or more function pointers can be encoded using a value that may be generated on program initialization and decoded before any dynamic function call occurs. In the event of memory corruption that affects an encoded function pointer, the value will cause the destination of the function pointer to decode to an invalid and random address and will induce an error. An application may be prevented from calling an attacker corrupted function pointer by introducing various checks around the call point at compile time that check the validity of the destination to which the function pointer points.
Owner:LEVIATHAN SECURITY GRP
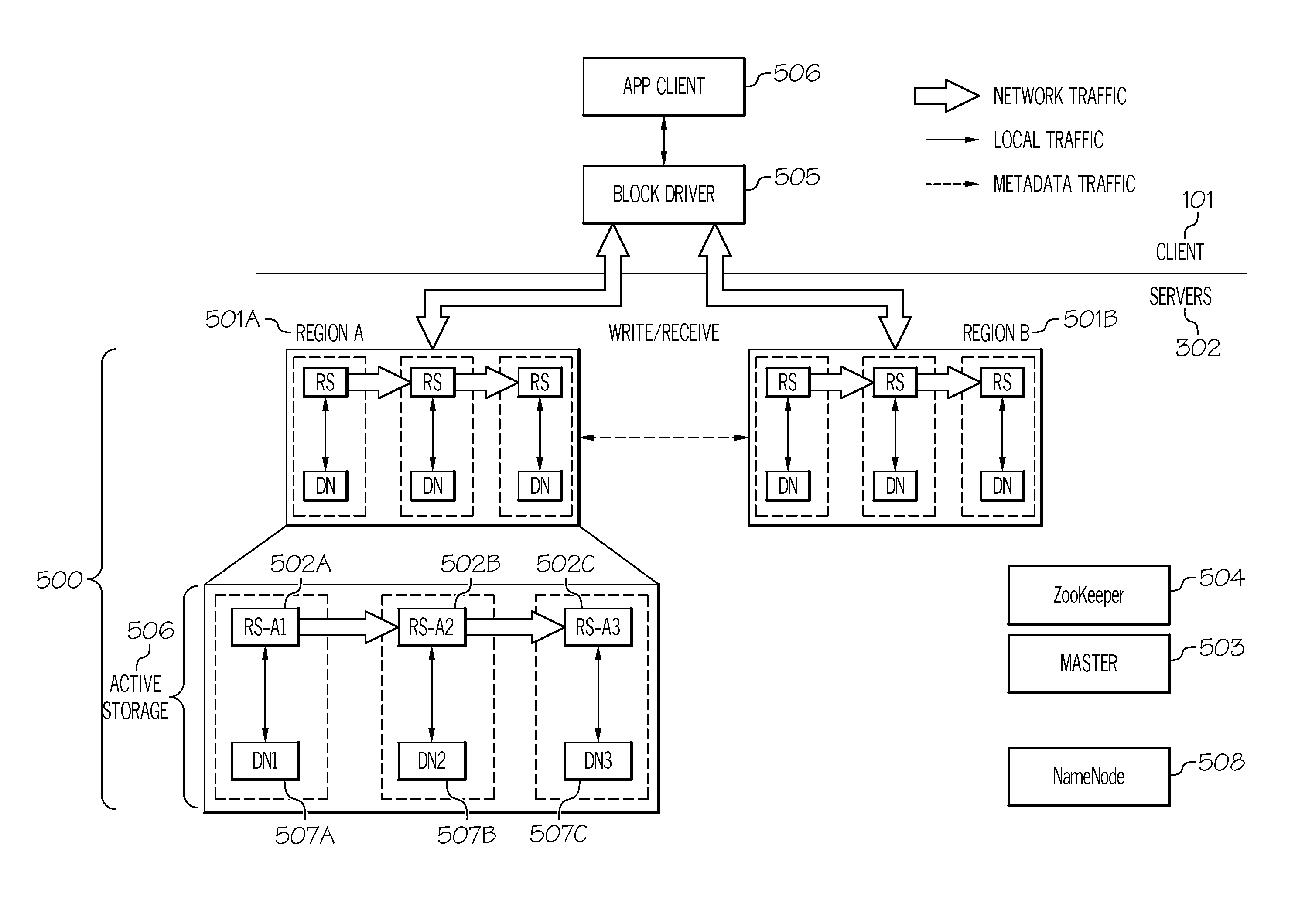
Robustness in a scalable block storage system
InactiveUS20140143367A1RobustnessDigital computer detailsInput/output processes for data processingDistributed computingMagnetic disks
A storage system that accomplishes both robustness and scalability. The storage system includes replicated region servers configured to handle computation involving blocks of data in a region. The storage system further includes storage nodes configured to store the blocks of data in the region, where each of the replicated region servers is associated with a particular storage node of the storage nodes. Each storage node is configured to validate that all of the replicated region servers are unanimous in updating the blocks of data in the region prior to updating the blocks of data in the region. In this manner, the storage system provides end-to-end correctness guarantees for read operations, strict ordering guarantees for write operations, and strong durability and availability guarantees despite a wide range of server failures (including memory corruptions, disk corruptions, etc.) and scales these guarantees to thousands of machines and tens of thousands of disks.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Method and apparatus for realtime detection of heap memory corruption by buffer overruns
ActiveUS20130024631A1Transformation of program codeComputer security arrangementsHeap overflowArithmetic logic unit
One embodiment of the present invention relates to a heap overflow detection system that includes an arithmetic logic unit, a datapath, and address violation detection logic. The arithmetic logic unit is configured to receive an instruction having an opcode and an operand and to generate a final address and to generate a compare signal on the opcode indicating a heap memory access related instruction. The datapath is configured to provide the opcode and the operand to the arithmetic logic unit. The address violation detection logic determines whether a heap memory access is a violation according to the operand and the final address on receiving the compare signal from the arithmetic logic unit.
Owner:INFINEON TECH AG
System and method for detecting DMA-generated memory corruption in a PCI express bus system
InactiveUS20050182862A1Easy to detectEasy to identifyElectric digital data processingMemory addressDirect memory access
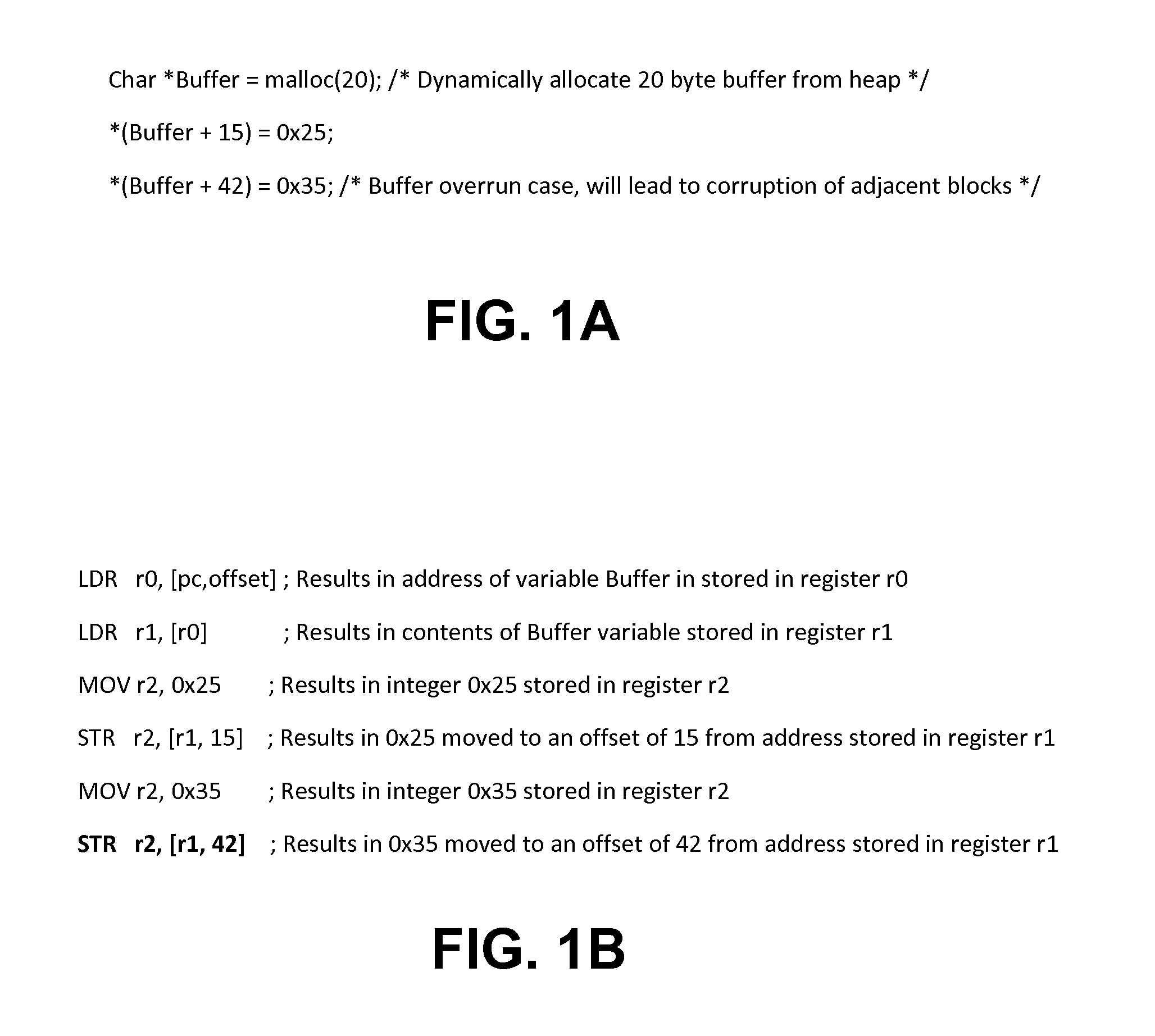
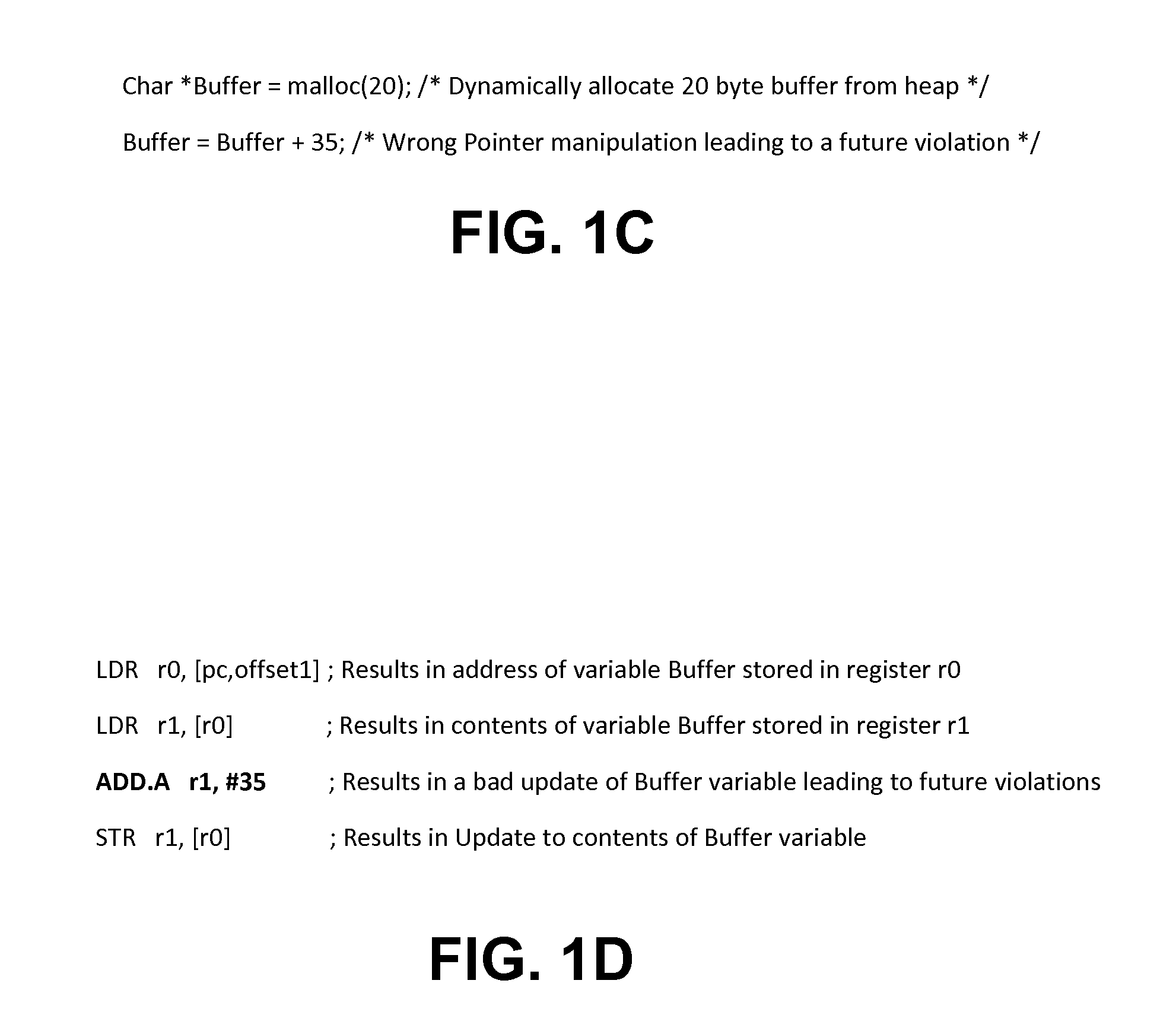
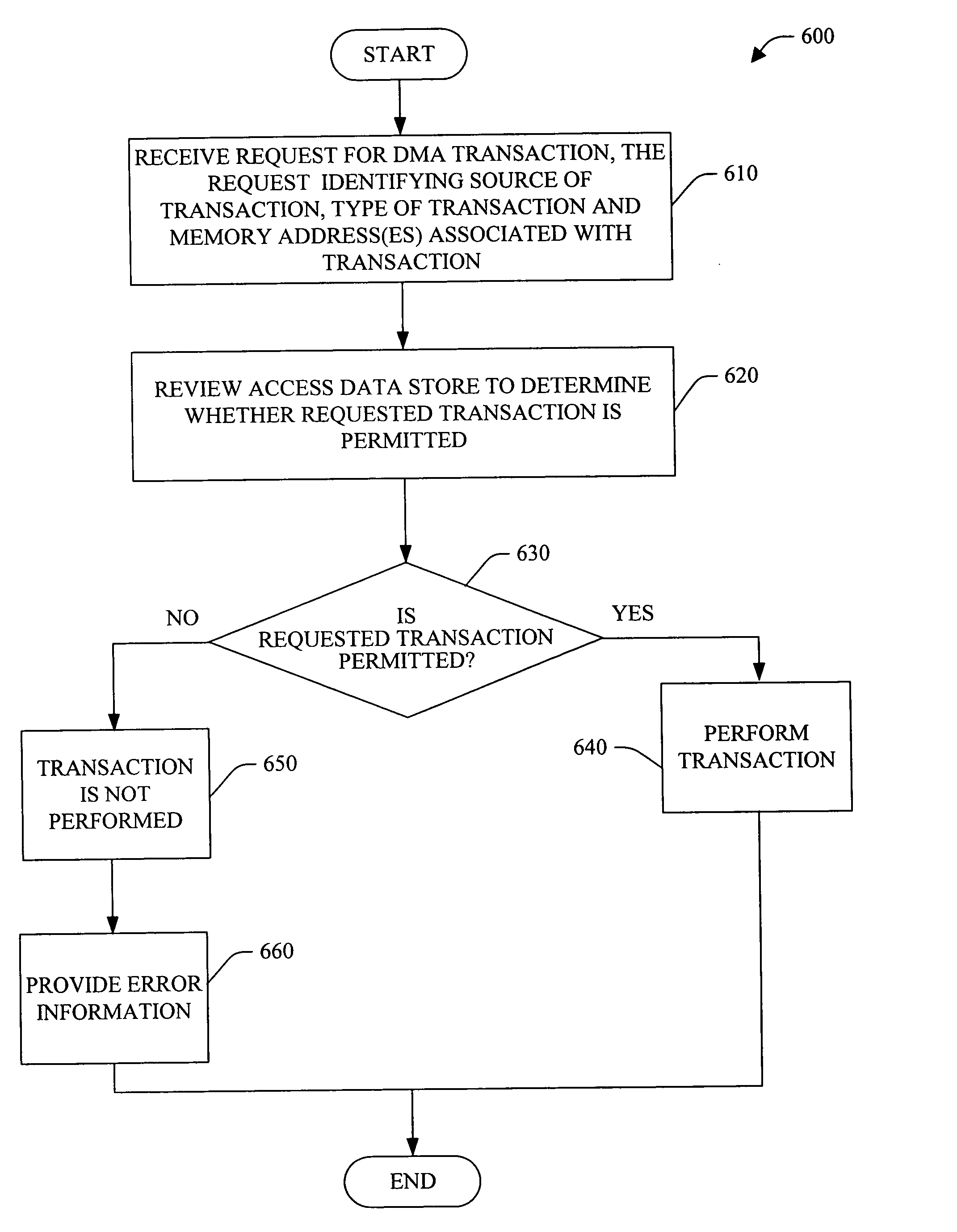
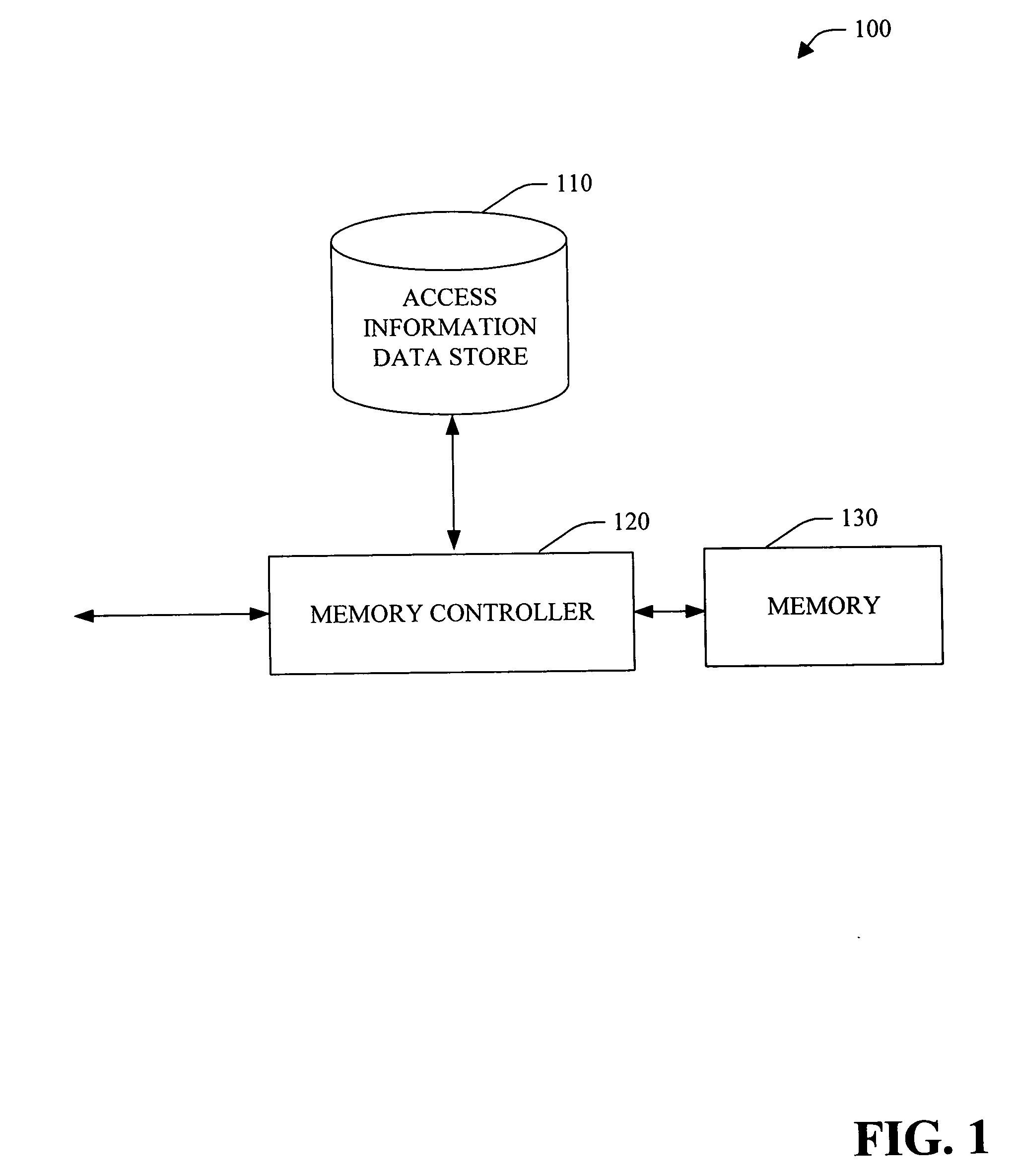
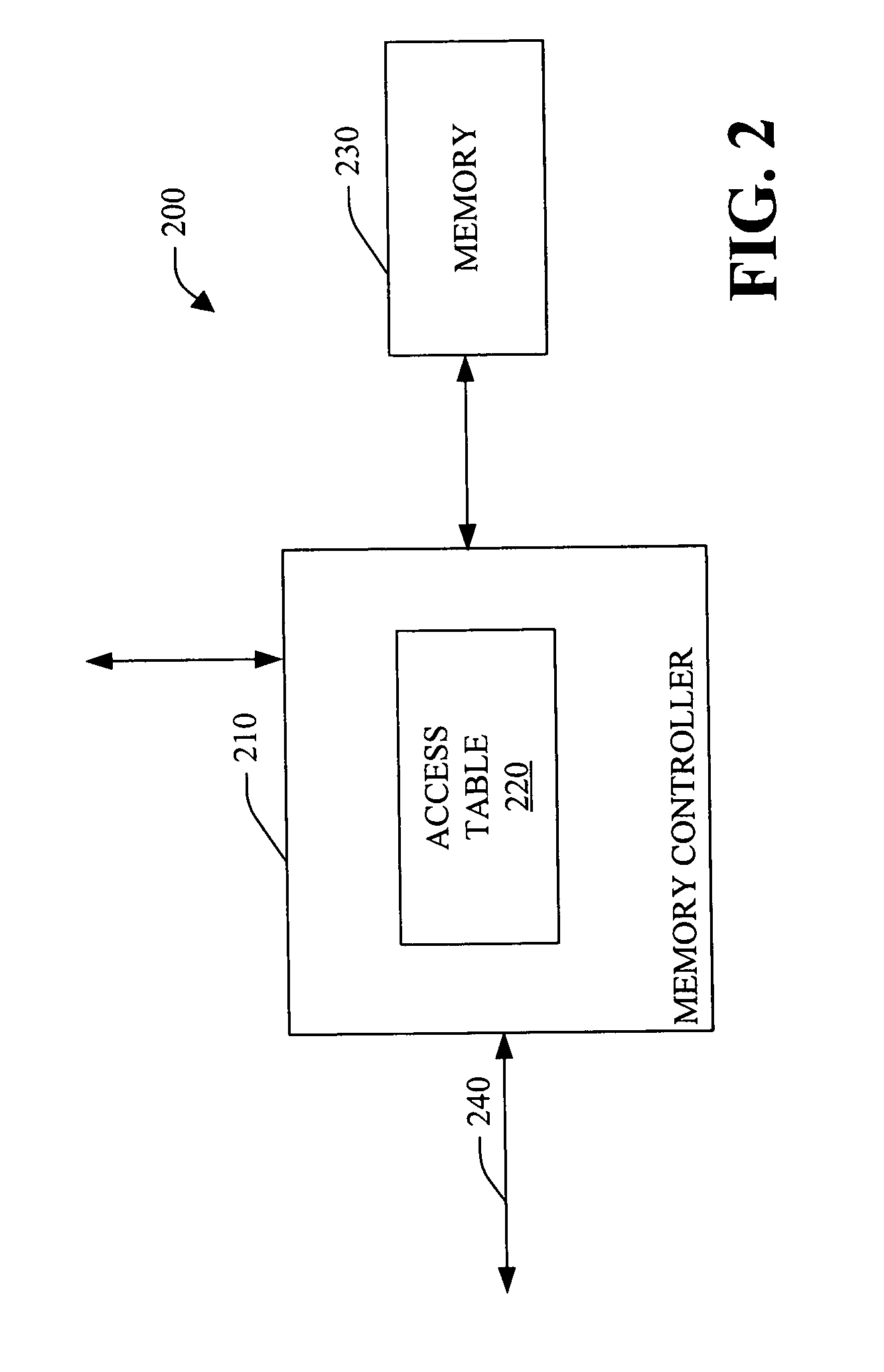
A system and method that facilitate detection of direct memory access (DMA) corruption is provided. The system can mitigate DMA memory corruption in computer system(s) employing transaction-based DMA bus system(s) (e.g., PCI Express). DMA transaction(s) cannot normally be traced; however, in accordance with an aspect of the present invention, the system is extended to include an interface to specify “allowed” and / or “disallowed” memory range(s) for a DMA transaction. If a DMA transaction occurs in a disallowed range, then it is rejected and, optionally, an error is raised. Thus, the system of the present invention can facilitate detection of direct memory access transaction(s) that can, if permitted, cause memory corruption. The system includes an access information data store (e.g., access table) and a memory controller. The access information can include, for example, a source identifier, a memory range (e.g., one or more contiguous memory address(es)) and access attribute(s) (e.g., read access, read and write access, write access, no access permitted, etc.).
Owner:MICROSOFT TECH LICENSING LLC
Systems and/or methods for automatically protecting against memory corruption vulnerabilities
ActiveUS20160026791A1Efficient and robustMemory loss protectionError detection/correctionApplication softwareVulnerability
Certain example embodiments described herein relate to techniques for automatically protecting, or hardening, software against exploits of memory-corruption vulnerabilities. The techniques include arranging a plurality of guard regions in the memory in relation to data objects formed by the application program, identifying an access by the application program to a guard region arranged in the memory as a disallowed access, and modifying the execution of the application program in response to the identifying, the modifying being in order to prevent exploitation of the memory and / or to correctly execute the application program.
Owner:GRAMMATECH
System and methods for run time detection and correction of memory corruption
ActiveUS8966312B1Improve productivityPotential for loss of intellectual property and personal information is also reducedPlatform integrity maintainanceNon-redundant fault processingRunning timeBackup
A method or apparatus detects a memory corruption of at least one portion of memory during run-time and corrects the memory corruption of the at least one portion of memory by replacing the at least one portion of memory with a backup of the at least one portion of memory. In this way, memory corruption can be corrected in a timely fashion while minimizing security risks.
Owner:VIRSEC SYST
Instructions to set and read memory version information
ActiveUS20130036276A1Digital computer detailsNon-redundant fault processingFailoverParallel computing
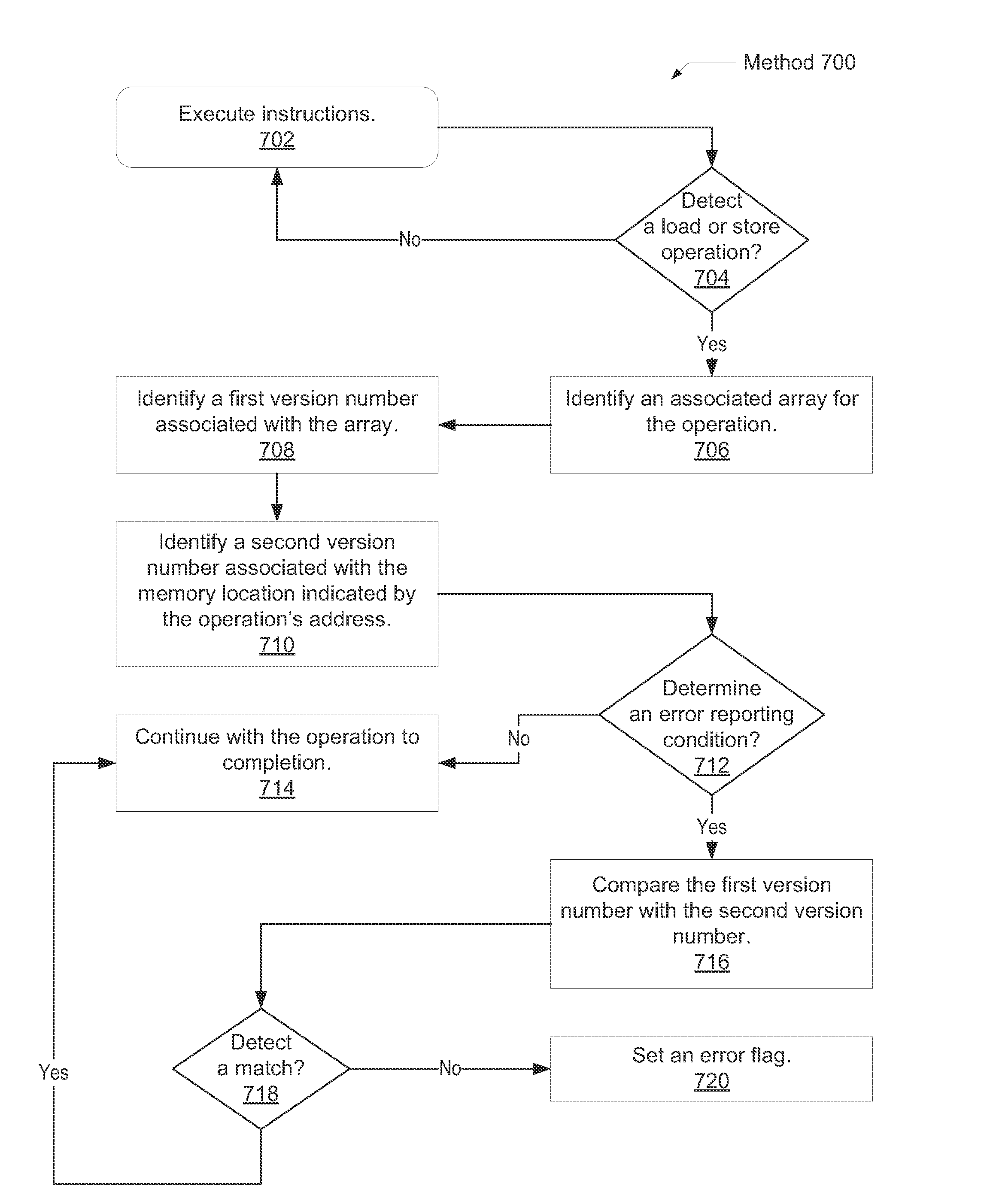
Systems and methods for providing additional instructions for supporting efficient memory corruption detection in a processor. A physical memory may be a DRAM with a spare bank of memory reserved for a hardware failover mechanism. Version numbers associated with data structures allocated in the memory may be generated so that version numbers of adjacent data structures are different. A processor determines that a fetched instruction is a memory access instruction corresponding to a first data structure within the memory. For instructions that are not a version update instruction, the processor compares the first version number and second version number stored in a location in the memory indicated by the generated address and flags an error if there is a mismatch. For version update instructions, the processor performs a memory access operation on the second version number with no comparison check.
Owner:ORACLE INT CORP
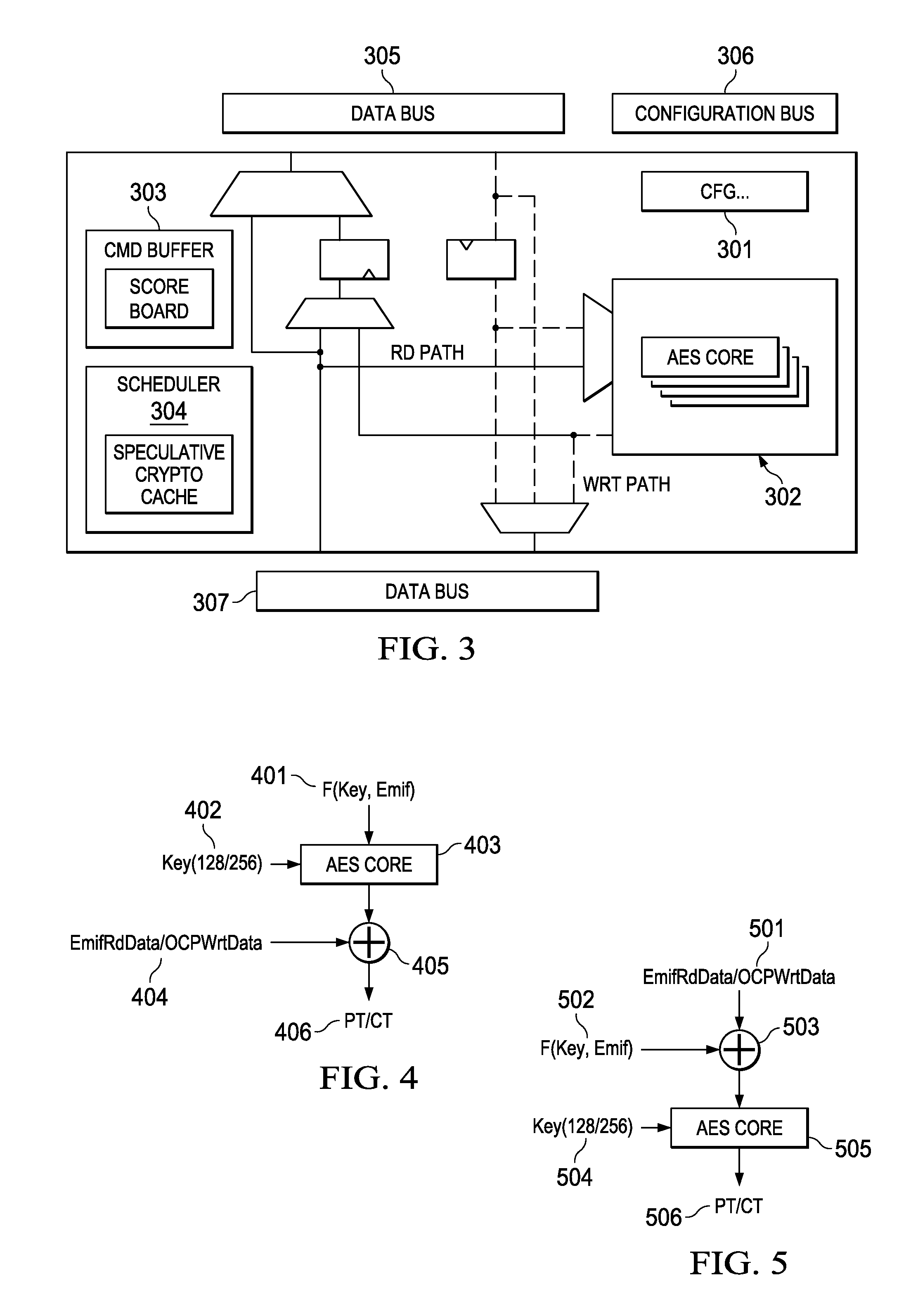
High performance autonomous hardware engine for inline cryptographic processing
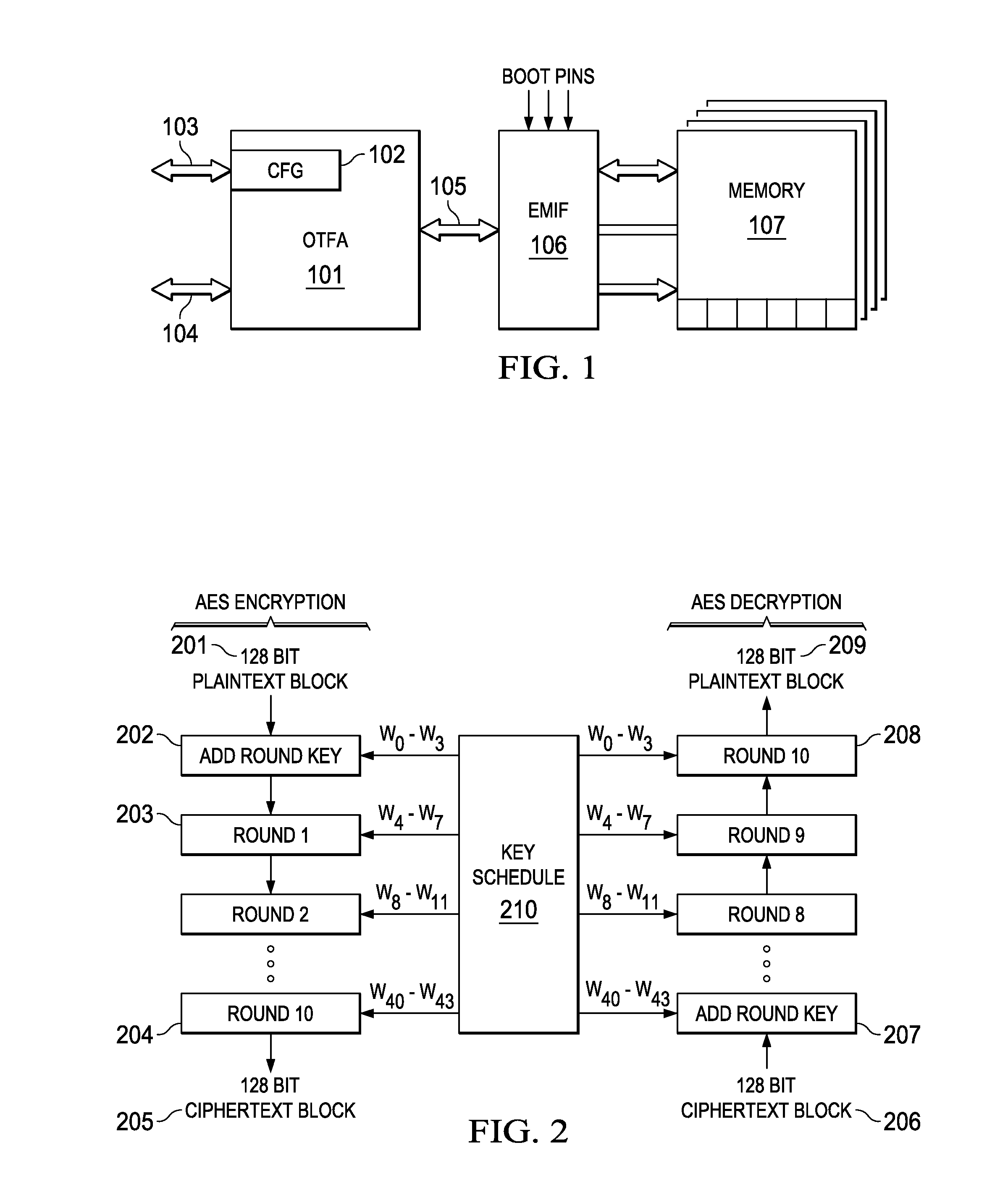
InactiveUS20150363333A1Memory architecture accessing/allocationUnauthorized memory use protectionExternal storageEncrypted function
A real time, on-the-fly data encryption system is shown operable to encrypt and decrypt the data flow between a secure processor and an unsecure external memory system. Multiple memory segments are supported, each with its own separate encryption capability, or no encryption at all. A Message Authentication Code is also employed to detect any memory corruption or unauthorized memory modification.
Owner:TEXAS INSTR INC
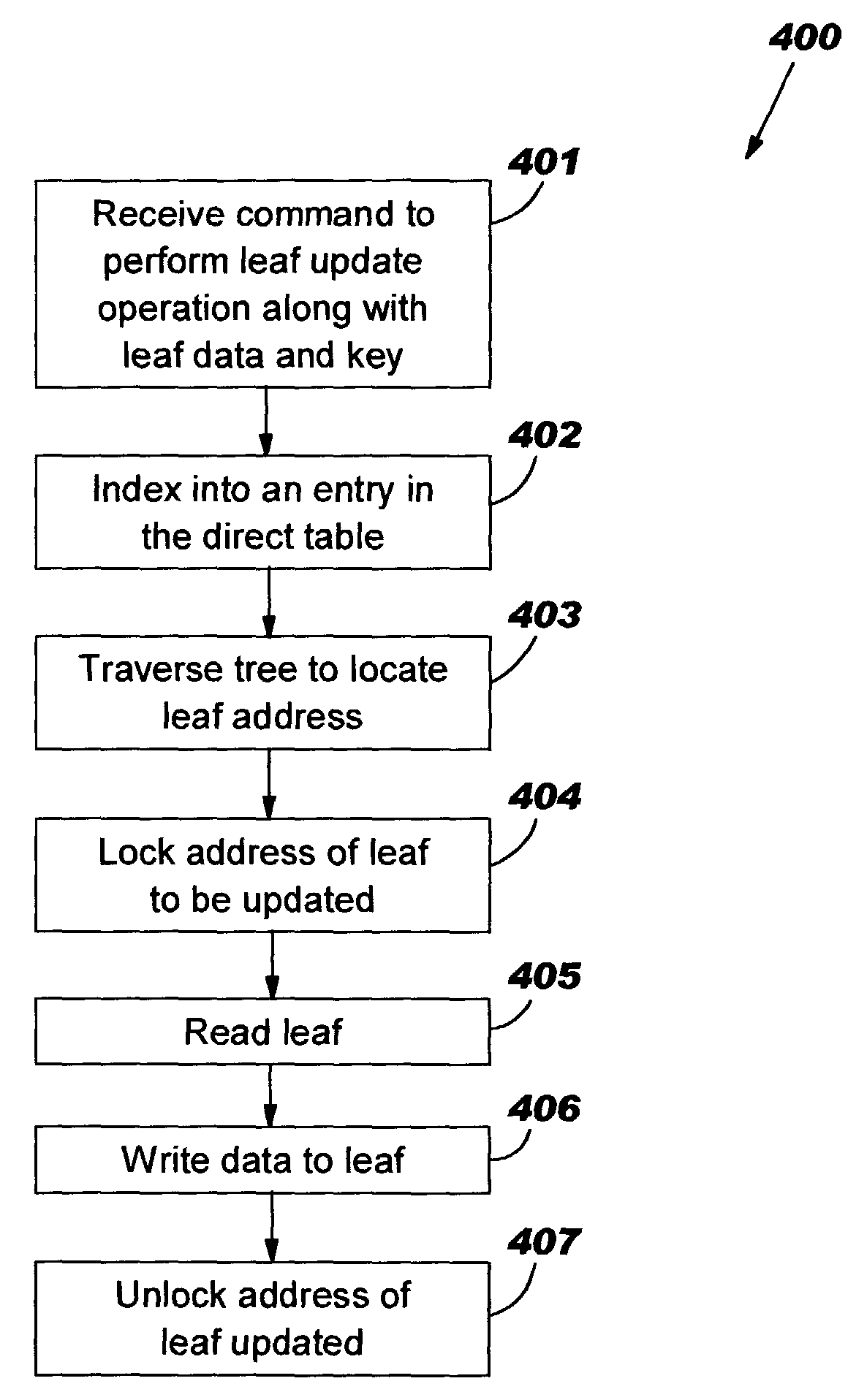
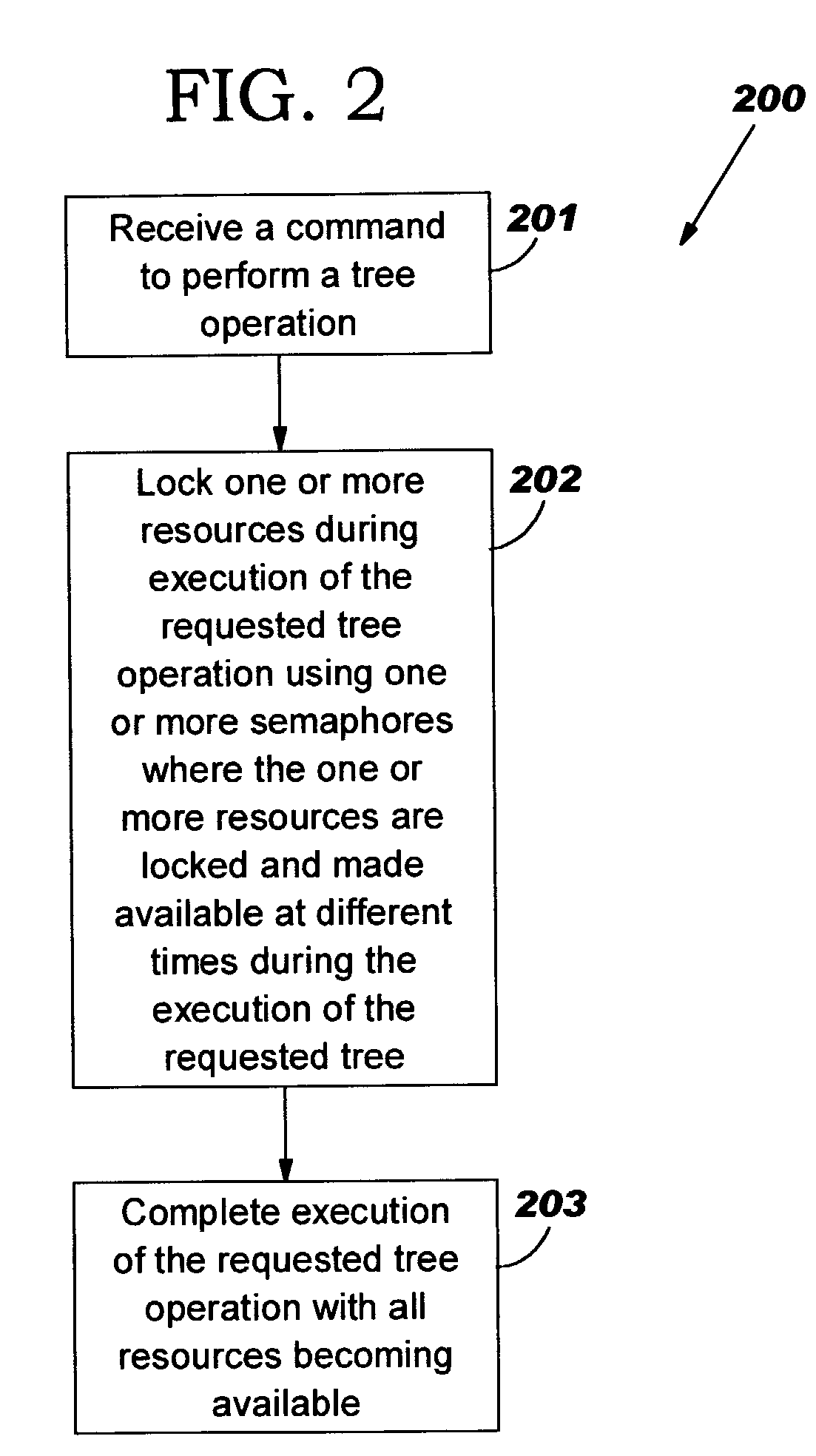
Eliminating memory corruption when performing tree functions on multiple threads
ActiveUS7036125B2Reduce usageMemory corruption may be eliminatedProgram synchronisationDigital computer detailsNetwork processorComputer program
A method, system and computer program product for eliminating memory corruption when performing multi-threaded tree operations. A network processor may receive a command to perform a tree operation on a tree on one or more of multiple threads. Upon performing the requested tree operation, the network processor may lock one or more resources during a portion of the execution of the requested tree operation using one or more semaphores. A semaphore may refer to a flag used to indicate whether to “lock” or make available the resource associated with the semaphore. Locking may refer to preventing the resource from being available to other threads. Hence, by locking one or more resources during a portion of the tree operation, memory corruption may be eliminated in a multiple thread system while preventing these resources from being used by other threads for a minimal amount of time.
Owner:TWITTER INC
Method for monitoring memory in real time by embedded system
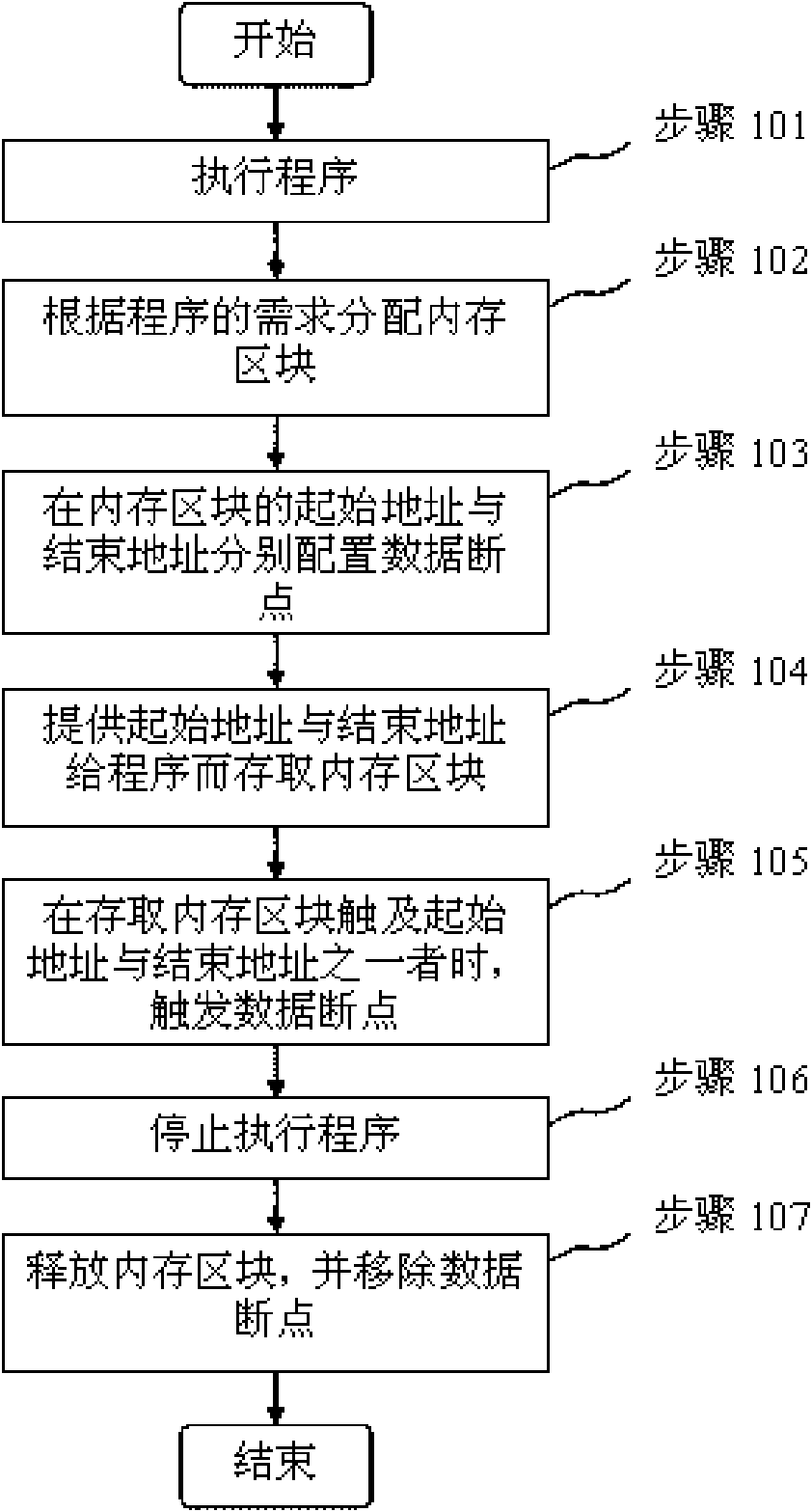
InactiveCN101625659ASpeed up development and troubleshootingShorten the development cycleResource allocationSoftware testing/debuggingDemand assignmentMemory block
The invention relates a method for monitoring a memory in real time by an embedded system, which comprises the following steps: (1) executing programs; (2) allocating a memory block according to the requirements of the programs; (3) respectively collocating data breakpoints at an initial address and an end address of the memory block; (4) providing the initial address and the end address to the programs and storing the memory block; and (5) triggering the data breakpoints when the stored memory block touches one of the initial address and the end address. The invention can position the mistake of program memory violation rapidly, lighten the debugging difficulty to the memory corruption problem for a user, accelerate the software development and removal speed, shorten the development cycle, save the developed labor cost and prompt the software quality.
Owner:WUDI SCI & TECH (XIAN) CO LTD
Block memory engine with memory corruption detection
ActiveUS9043559B2Memory loss protectionError detection/correctionParallel computingCollaborative processing
Owner:ORACLE INT CORP
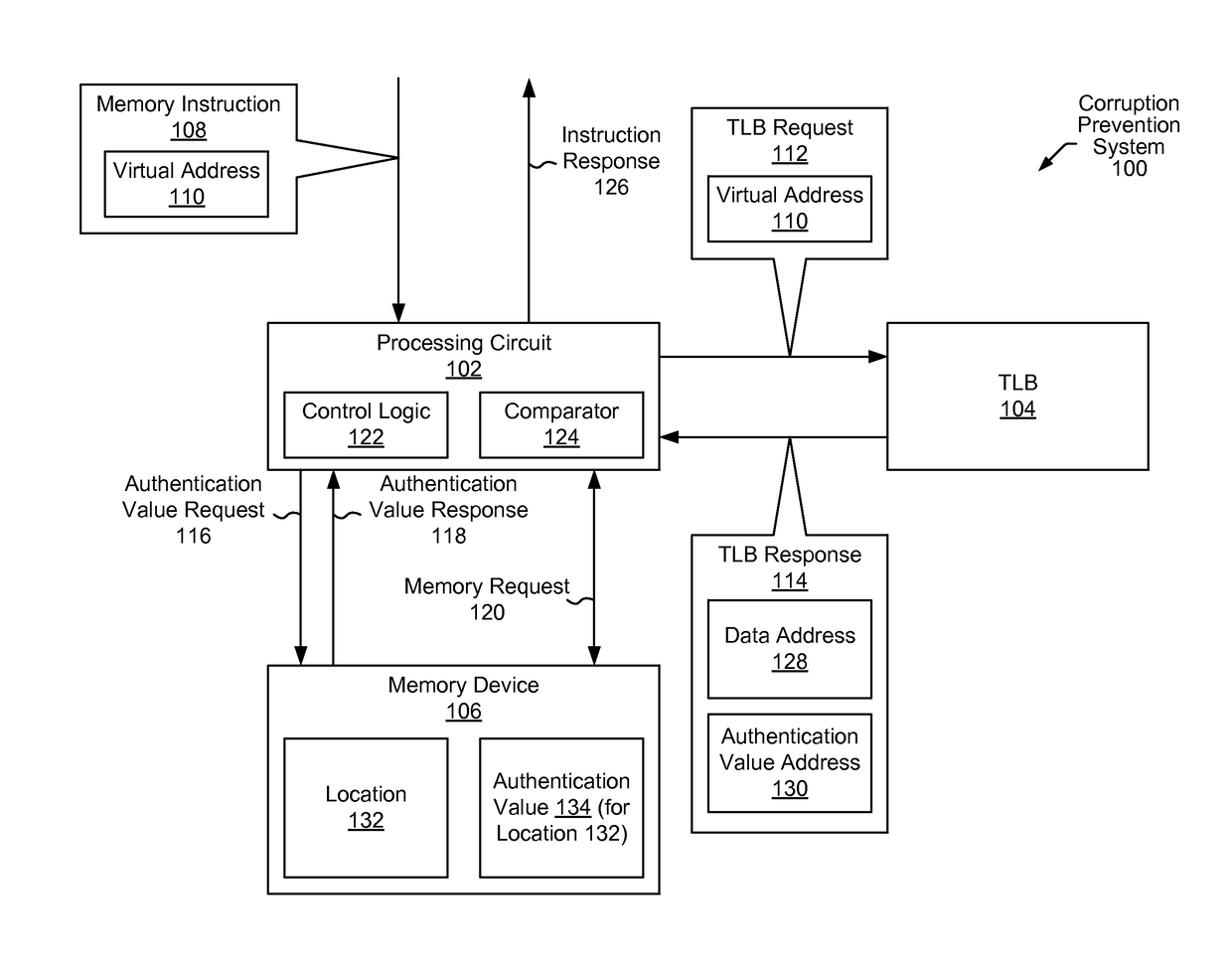
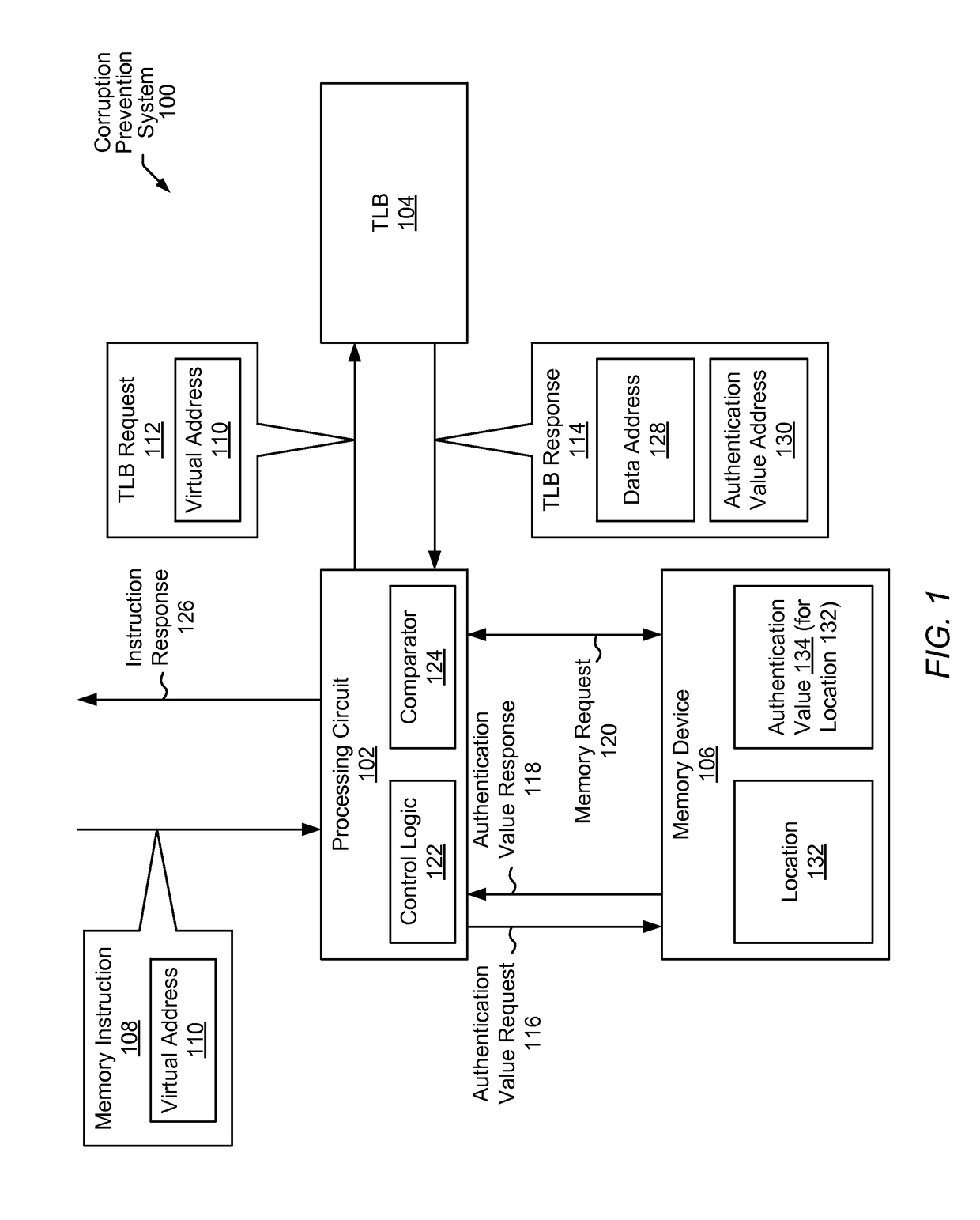
Memory corruption prevention system
ActiveUS20170075817A1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryMemory address
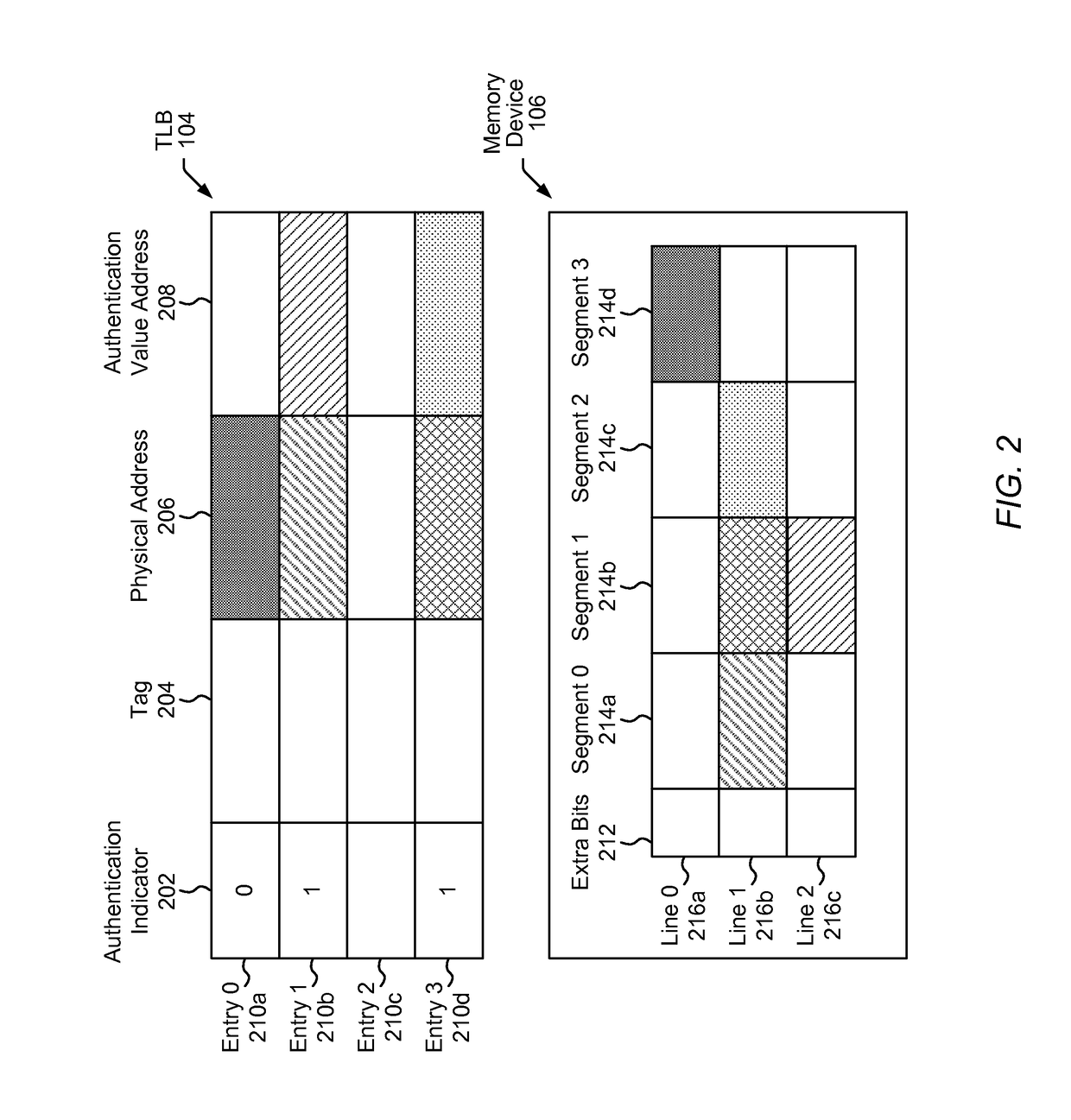
In some embodiments, a memory corruption prevention process includes detecting a memory instruction of a program, where the memory instruction specifies a virtual memory address of data. The memory corruption prevention process further includes accessing, in response to the memory instruction, a translation lookaside buffer (TLB) using at least a portion of the virtual memory address. The memory corruption prevention process further includes, in response to accessing the TLB, obtaining a physical memory address corresponding to the virtual memory address, where the physical memory address corresponds to the data. The memory corruption prevention process further includes, in response to accessing the TLB, obtaining an authentication value corresponding to the physical memory address. The memory corruption prevention process further includes determining, using the authentication value, whether the memory instruction is authorized to proceed.
Owner:ORACLE INT CORP
Scheduling optimization of aliased pointers for implementation on programmable chips
Various high-level languages are used to specify hardware designs on programmable chips. The high-level language programs include pointer operations that may have same iteration and future iteration dependencies. Single loop iteration pointer dependencies are considered when memory accesses are assigned to clock cycles. Multiple loop iteration pointer dependencies are considered when determining how often new data can be entered into the generated hardware pipeline without causing memory corruption. A buffer can be used to forward data from a memory write to a future read.
Owner:ALTERA CORP
Method and apparatus for disabling corrupted memory by using BMC
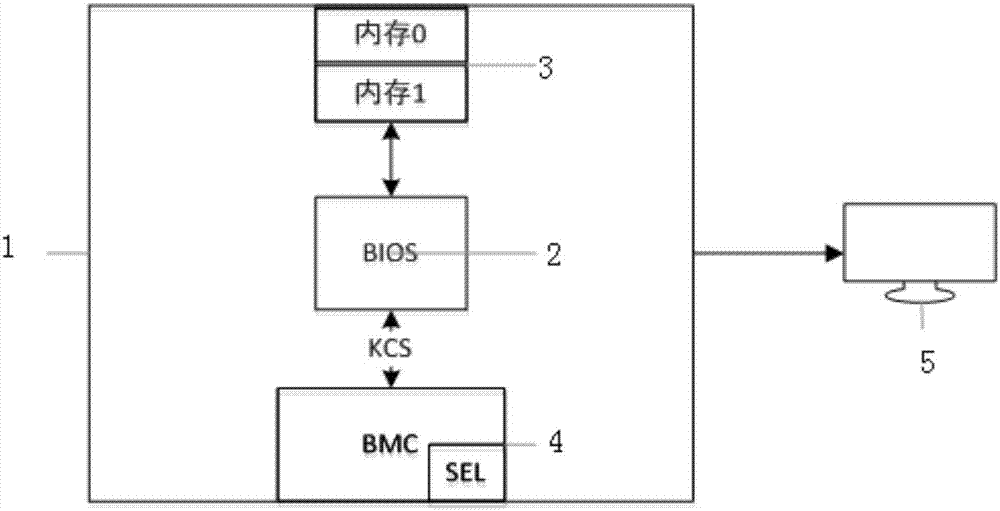
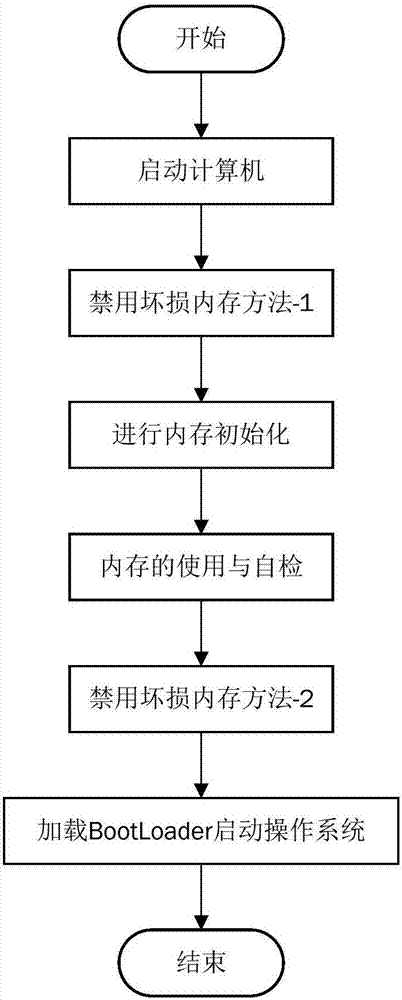
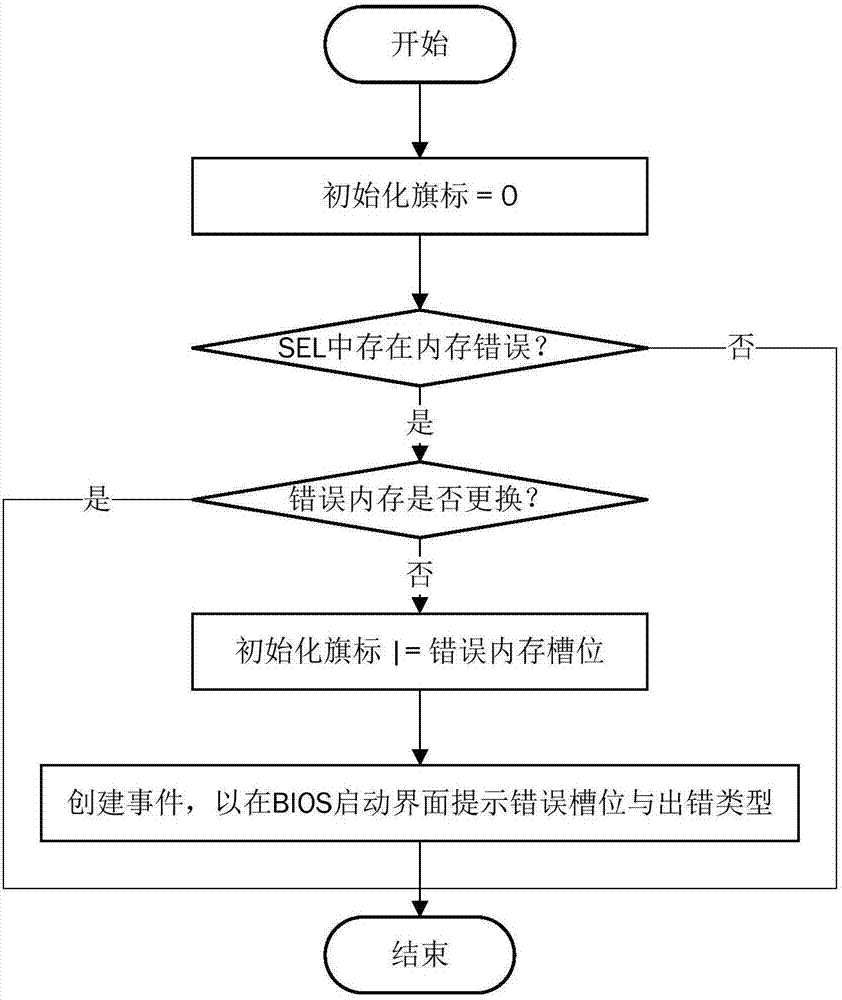
InactiveCN107066361AFriendly reminderWon't crashFaulty hardware testing methodsNon-redundant fault processingBad memoryBIOS
The present invention discloses a method for disabling a corrupted memory by using the BMC. The method comprises: (1) obtaining a preset initialization flag value pi for the memory on each memory slot i when the BIOS is running until the memory is ready to be initialized after the computer is started; (2) when the initialization flag value pi corresponding to the memory on the memory slot i is 0, determining whether there is a memory error message in the BMC system event log, and if so, executing (3); (3) taking whether the serial number of the memory is changed as the basis, determining whether the corrupted memory is replaced by the user, and if not, executing (4); (4) carrying out the or operation on the initialization flag value corresponding to the corrupted memory and the number i of the memory slot, and taking the result as the updated initialization flag value; (5) creating the UEFI event, so that after the BIOS runs to the BIOS boot interface, a memory corruption message is prompted to the user; and (6) initializing the memory. The present invention also discloses an apparatus for disabling a corrupted memory by using the BMC. According to the method and apparatus disclosed by the present invention, the bad memory can be disabled, and system crash can be prevented.
Owner:南京百敖软件有限公司
Instructions to set and read memory version information
ActiveUS8751736B2Digital data processing detailsMemory adressing/allocation/relocationFailoverParallel computing
Systems and methods for providing additional instructions for supporting efficient memory corruption detection in a processor. A physical memory may be a DRAM with a spare bank of memory reserved for a hardware failover mechanism. Version numbers associated with data structures allocated in the memory may be generated so that version numbers of adjacent data structures are different. A processor determines that a fetched instruction is a memory access instruction corresponding to a first data structure within the memory. For instructions that are not a version update instruction, the processor compares the first version number and second version number stored in a location in the memory indicated by the generated address and flags an error if there is a mismatch. For version update instructions, the processor performs a memory access operation on the second version number with no comparison check.
Owner:ORACLE INT CORP
Systems and/or methods for automatically protecting against memory corruption vulnerabilities
ActiveUS20180247057A1Efficient and robustPlatform integrity maintainanceMemory systemsApplication softwareVulnerability
Owner:GRAMMATECH
Systems and methods for flash memory conflict avoidance
PendingUS20210263720A1Conflicts are thereby avoidedReduce chanceInput/output to record carriersRead-only memoriesTerm memoryReliability engineering
Systems and methods for flash memory conflict avoidance cause a firmware over the air (FOTA) update to be given priority over a scrubbing operation unless the memory element meets or exceeds a predefined health degradation parameter. When the memory element meets or exceeds the predefined health degradation parameter, the scrubbing operation is given priority over the FOTA update. By enforcing these priorities, scrubbing and FOTA updates do not occur at the same time and conflicts are thereby avoided. Since conflicts are avoided, the chance of memory corruption is decreased and the chance of “bricking” the computing device is likewise decreased.
Owner:QUALCOMM INC
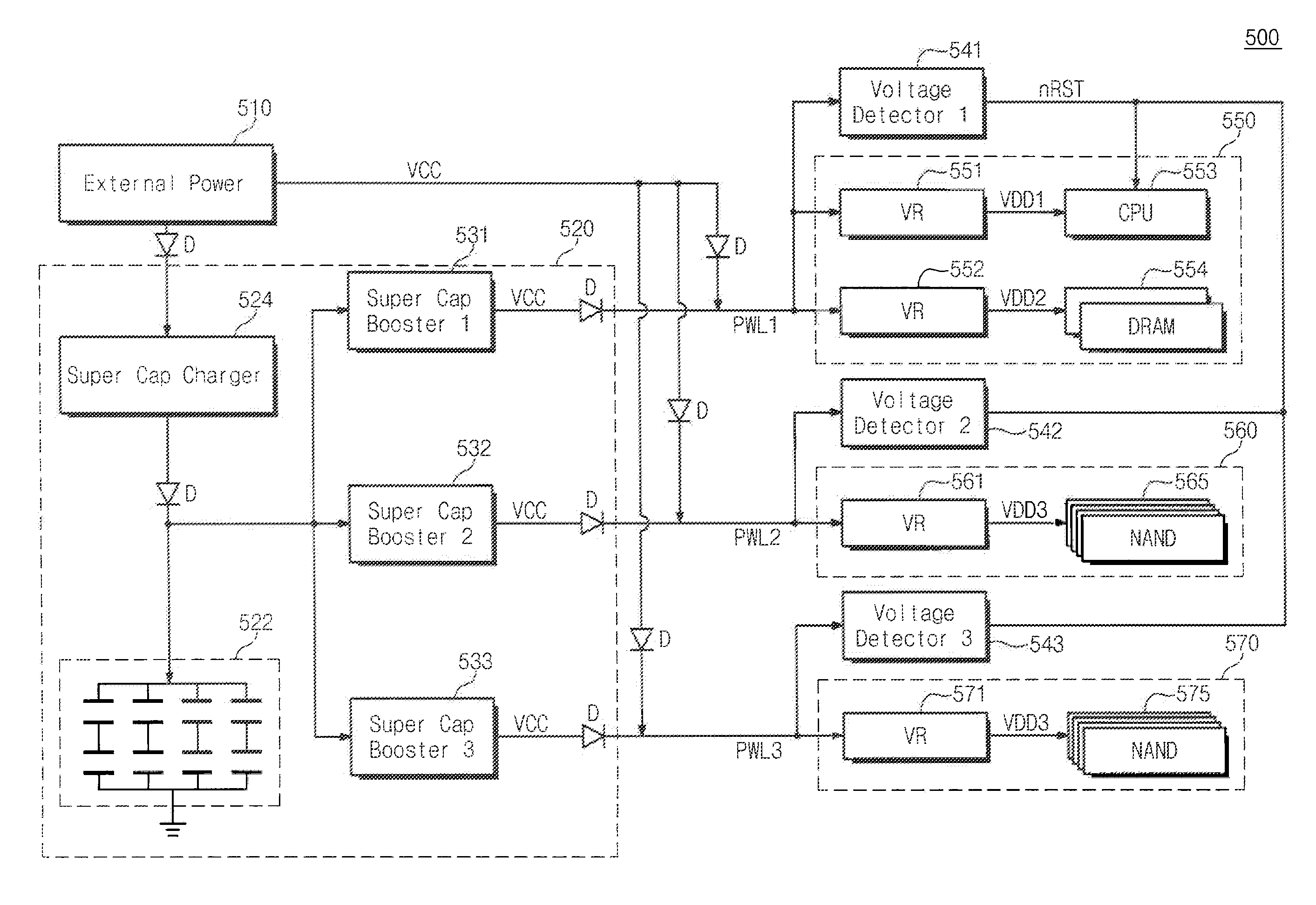
Memory system and reset method thereof to prevent nonvolatile memory corruption due to premature power loss
ActiveUS8904161B2High data reliabilityRead-only memoriesDigital computer detailsPower domainsMemory systems
Provided is a memory system that includes at least one nonvolatile memory device, a plurality of power lines and a plurality of power domains. The power lines receive a power source voltage. The power domains are respectively connected to the power lines. A reset signal is generated by using voltages which are detected from the power lines. The memory system and a reset method thereof detect the voltages of all power lines to generate a reset signal, and thus enhance reliability of data when a power is shut off.
Owner:SAMSUNG ELECTRONICS CO LTD
Maximizing encodings of version control bits for memory corruption detection
ActiveUS8572441B2Platform integrity maintainanceStatic storageParallel computingVirtual address space
Owner:ORACLE INT CORP
Information processing method and apparatus having data locations accessible by different devices in accordance with different permissions
InactiveUS7437526B2Memory architecture accessing/allocationInput/output to record carriersInformation processingWrite buffer
Memory corruption can be suppressed. When data stored in a random access area are read, the read data (physical block) are retrieved by a logic block number and newest data are read by referring to an incremental counter of data having that logic block number. When data are stored in the random access area, the incremental counter and the logic block number of data already stored in the random access area are referred and a physical block set to be unnecessary is set to a writer buffer, and then the data are written to this write buffer.
Owner:SONY CORP
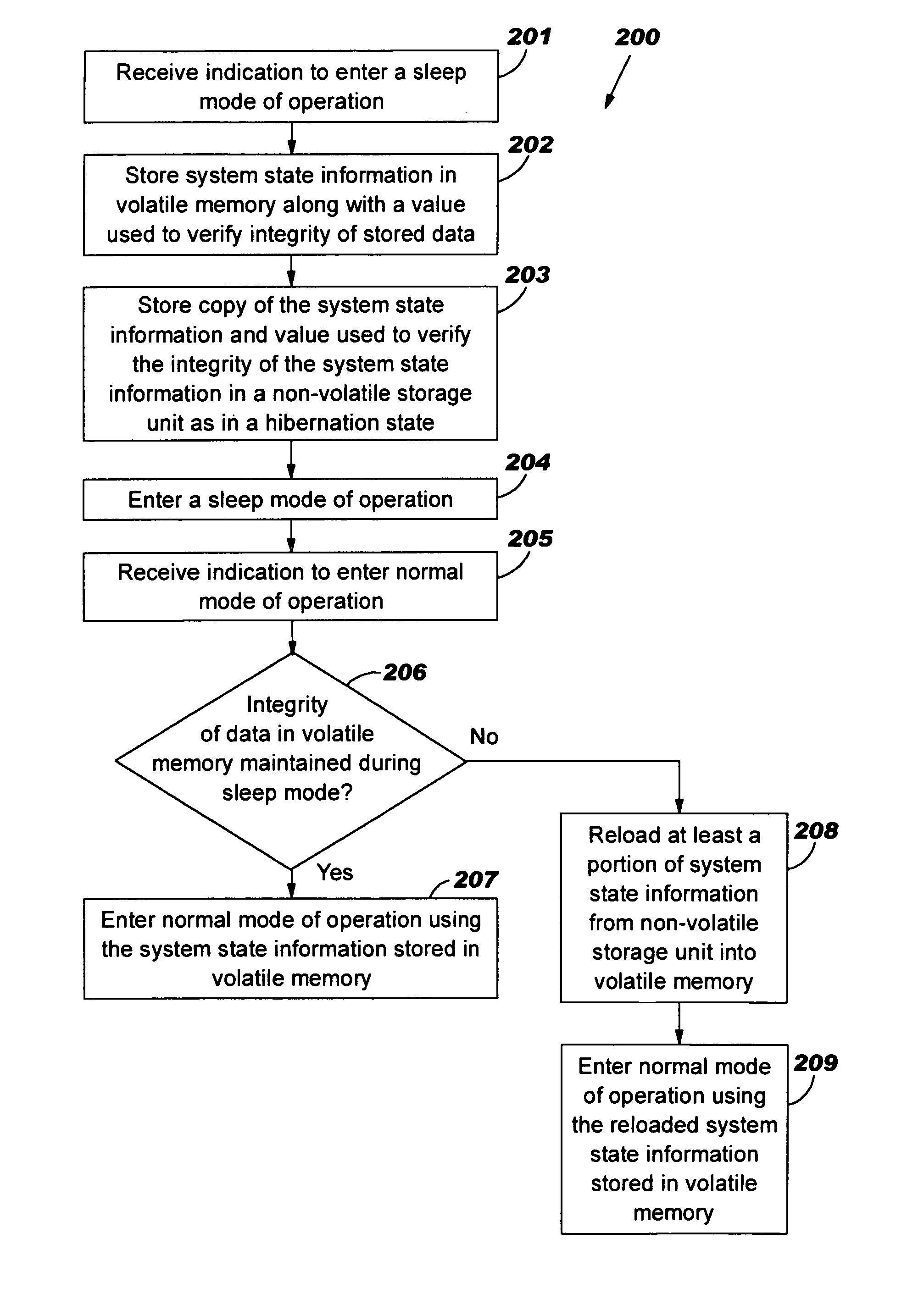
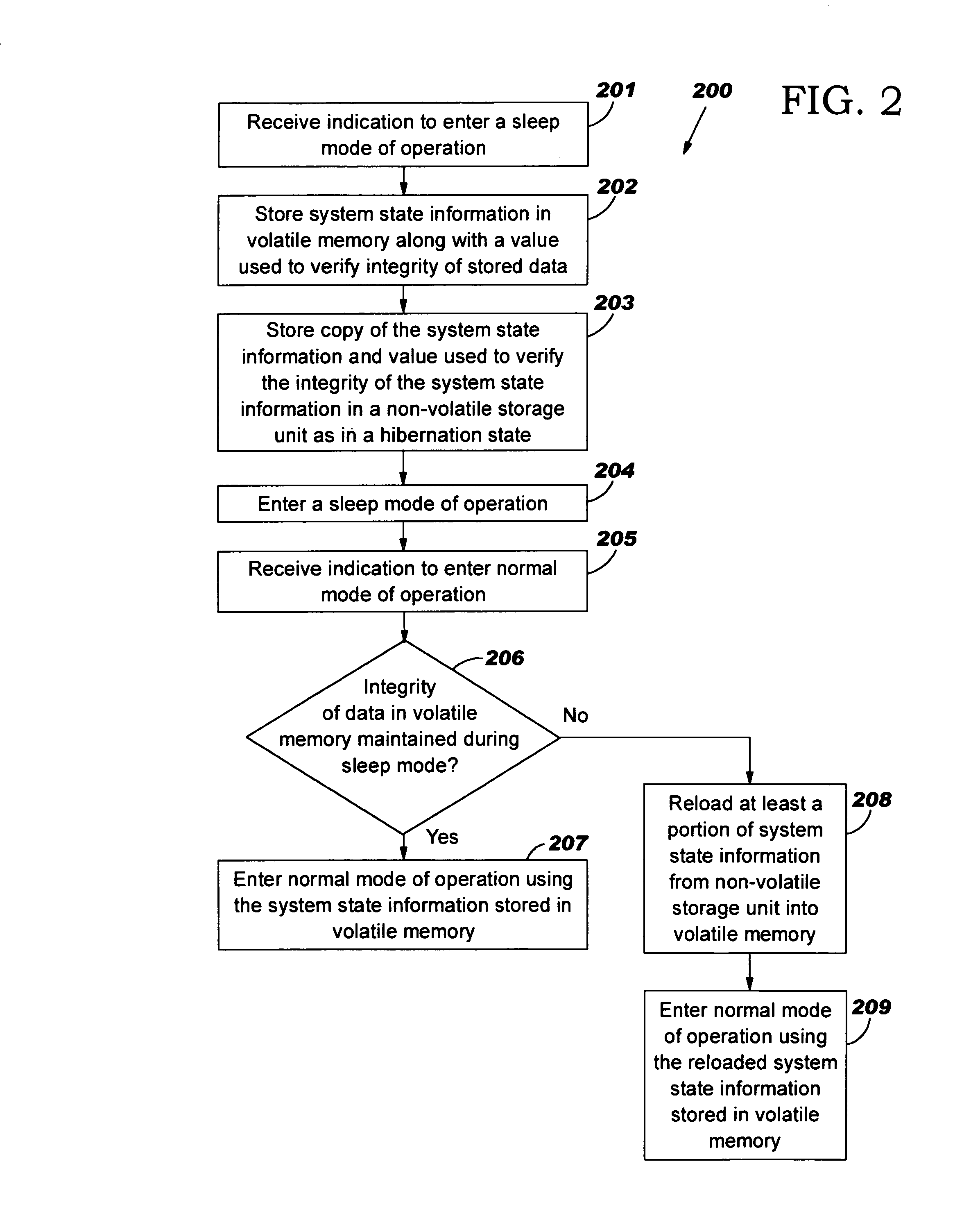
Fault tolerant sleep mode of operation
A method, system and computer program product for implementing a fault tolerant sleep mode of operation. The system state information may be stored in a volatile memory and in a non-volatile storage unit prior to entering the sleep mode of operation. If a memory corruption event, e.g., power outage, brownout, power surge, occurs during the sleep mode of operation, then, upon receiving an invocation to resume to a normal mode of operation, the system state information stored in the non-volatile storage unit may be reloaded into the volatile memory. By reloading the system state information stored in the non-volatile storage into the volatile memory, the computer system may resume to a normal mode of operation from a sleep mode of operation without any corruption or loss of data.
Owner:LENOVO PC INT
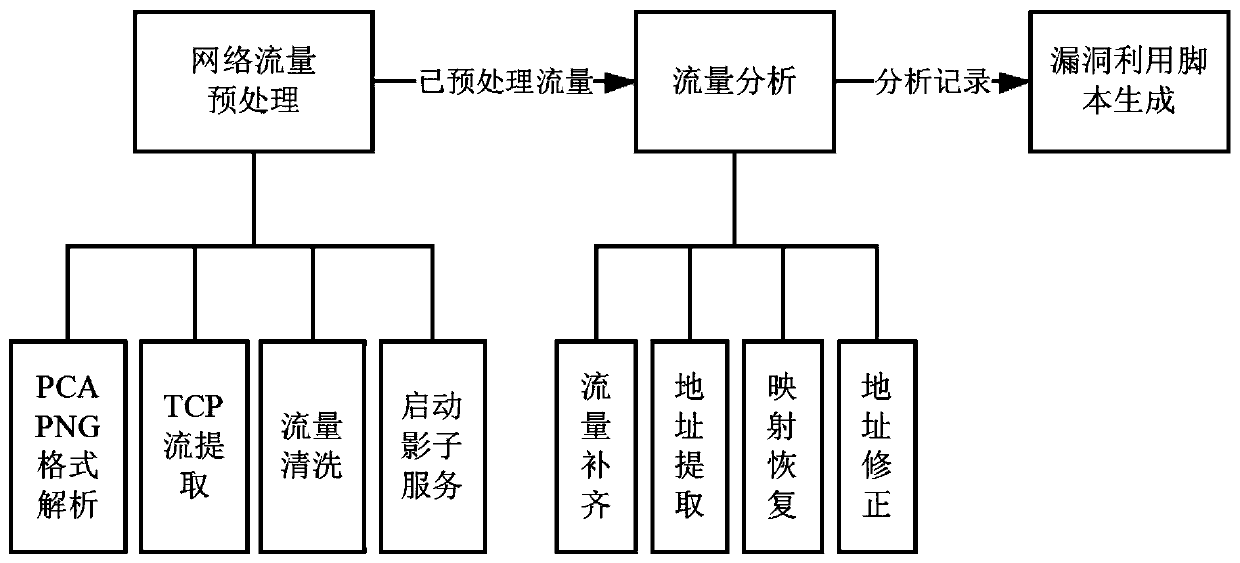
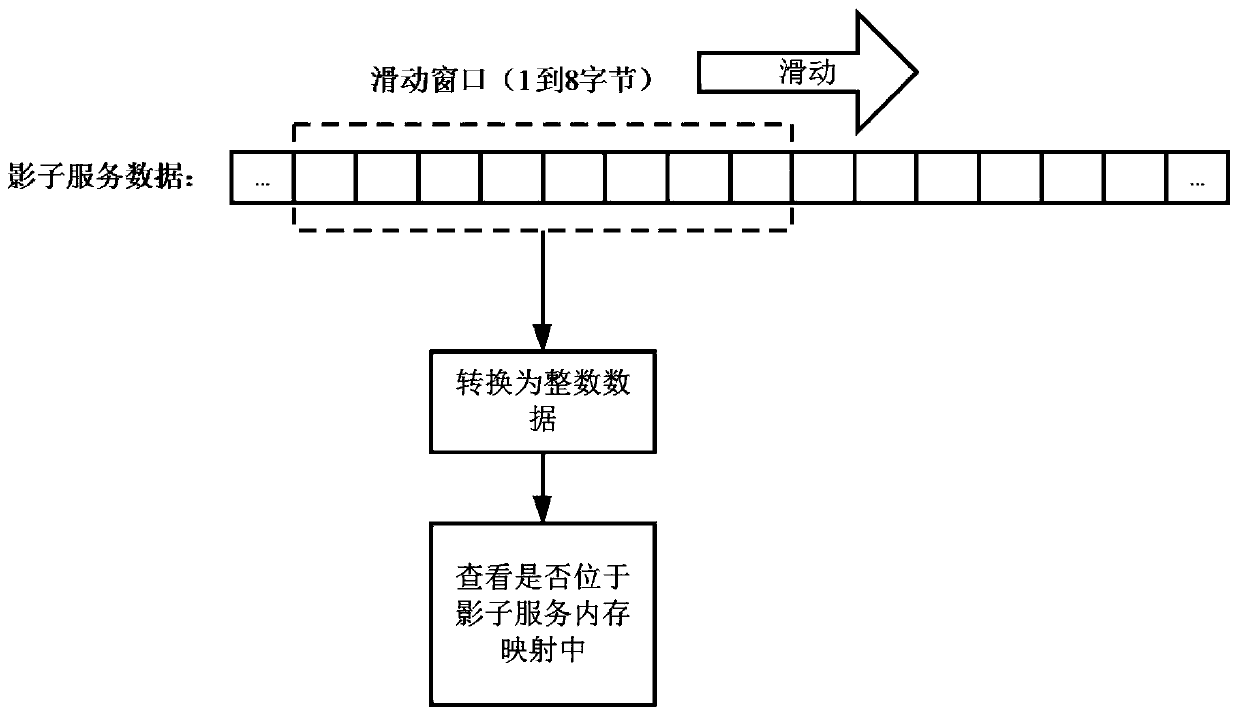
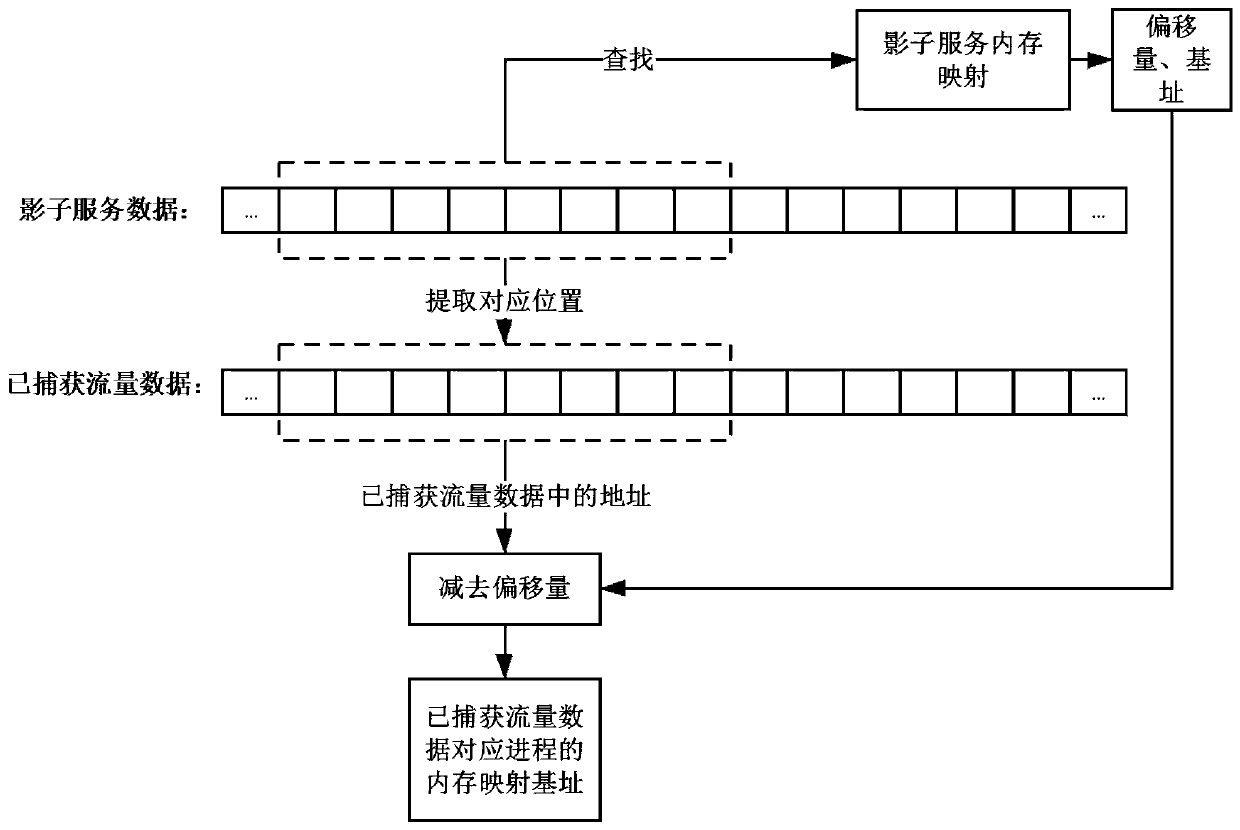
Method and system for carrying out vulnerability utilization generation on captured memory corruption vulnerability attack traffic
The invention discloses a method and a system for carrying out vulnerability utilization generation on captured memory corruption vulnerability attack traffic. The method comprises the steps: obtaining a memory mapping base address of captured data traffic and a corresponding position of the base address in received data after the data is received from a shadow service; before sending the data tothe shadow service, obtaining address information of a data sending part in the captured flow data and carrying out offset correction; and generating a vulnerability utilization script interacting with the target service according to the interaction process with the shadow service. The script can be used for obtaining evidences after the server is attacked or defending against further attacks of the same vulnerability.
Owner:PEKING UNIV
Fast estimation of binary data length using memory corruption
Various embodiments are described herein for a method and related device for processing a first dataset comprising a second dataset and a third dataset in order to locate the third dataset. The second dataset has a variable data length and terminates with an ending marker and the third dataset starts after the ending marker. The method involves preprocessing a memory element by storing a plurality of locater markers, storing the first dataset in the memory element thereby overwriting a portion of the plurality of locater markers, locating which of the plurality of locater markers is closest to the end of the first dataset,and locating the third dataset by searching for the ending marker of the second dataset based on the position of the closest locater marker.
Owner:BLACKBERRY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com