Method and system for carrying out vulnerability utilization generation on captured memory corruption vulnerability attack traffic
A technology for attacking traffic and vulnerabilities, applied in transmission systems, electrical components, etc., can solve problems such as inability to send data sequentially
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Hereinafter, the present invention will be described in detail with reference to the drawings, but the present invention is not limited to the following embodiments.
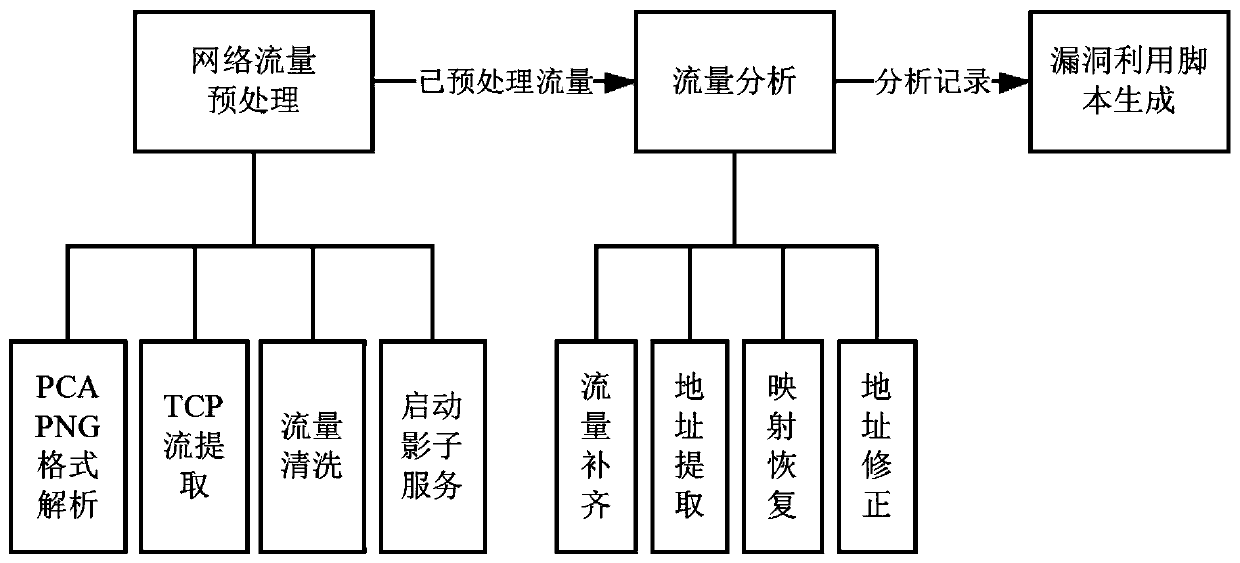
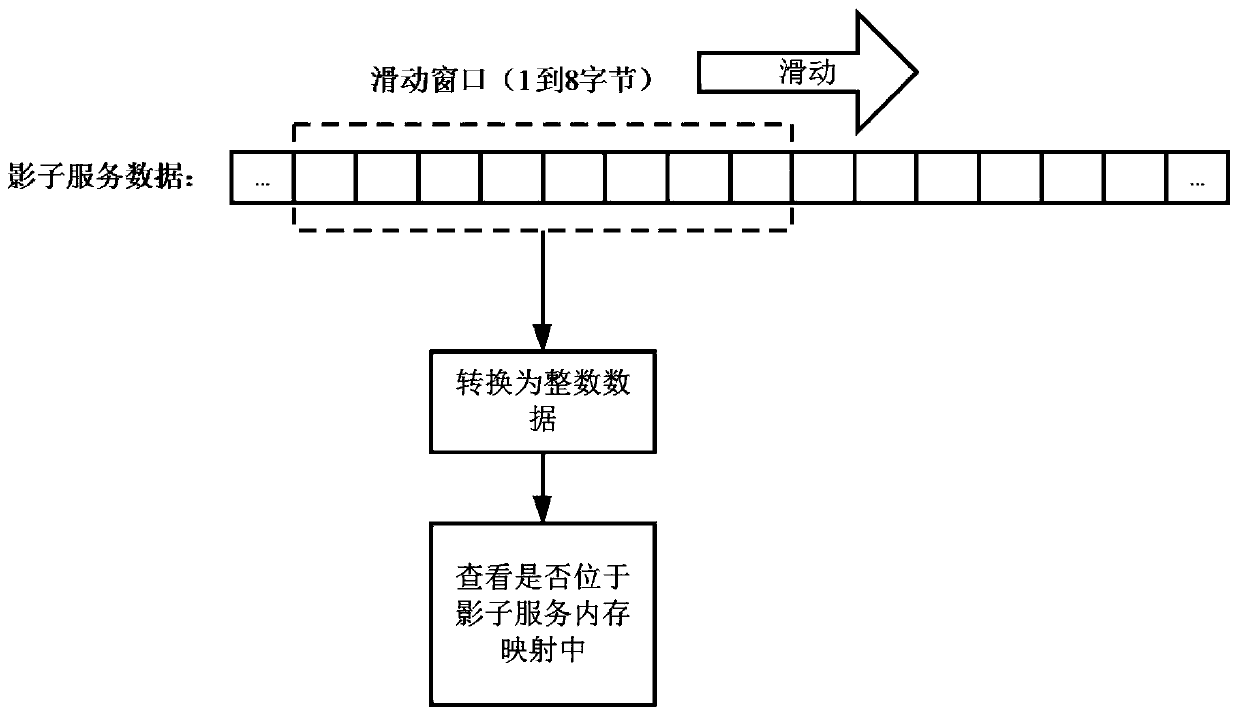
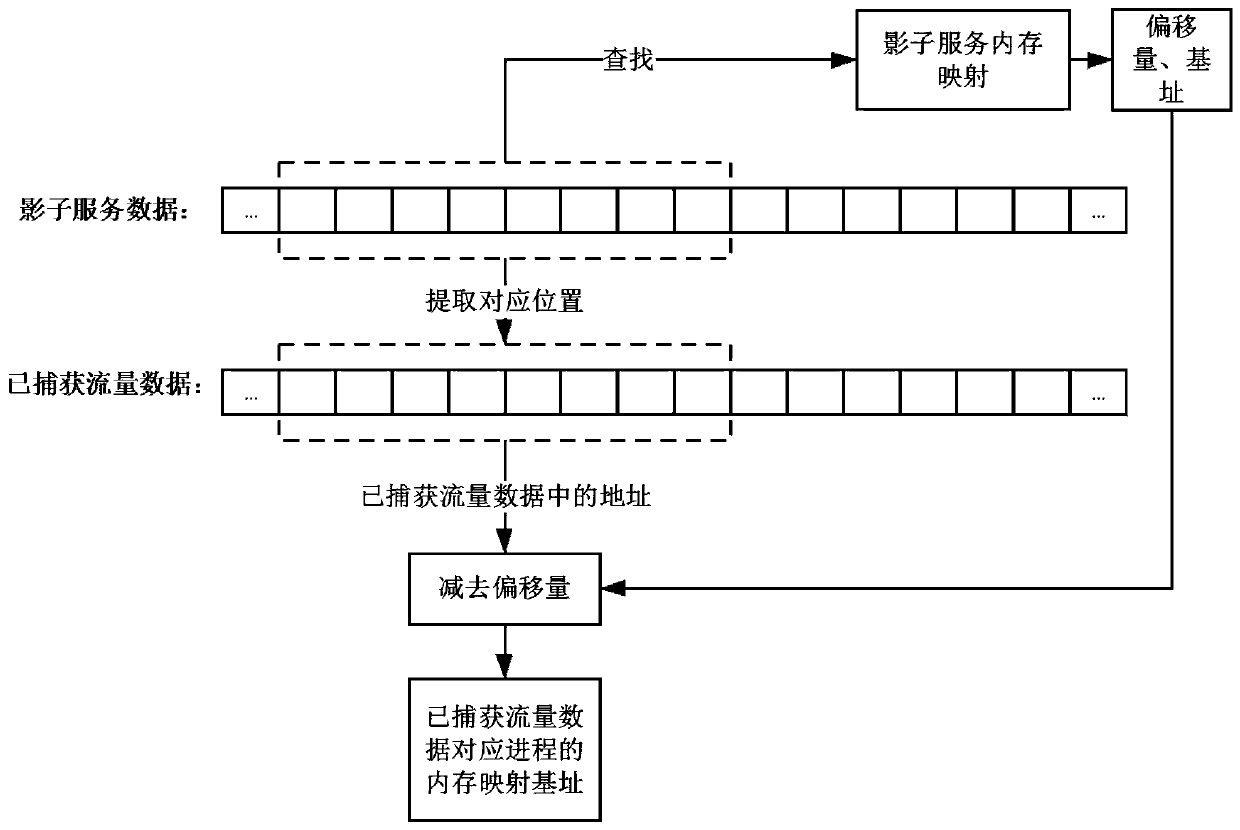
[0042] like figure 1 Shown is the overall flowchart. Firstly, through the network traffic preprocessing stage, the file format analysis and preliminary screening of the network traffic are performed, and then the shadow service and its attached backdoor interface are initialized and started. After that, the traffic is analyzed. The analysis process is completed by interacting with the shadow service, and traffic completion, address extraction, mapping recovery, and address correction are required. Through iterative interaction, an analysis record containing the interaction process and the process mapping information of the captured traffic target is obtained. Based on the analysis records, the final exploit script can be generated to obtain the exploit script.
[0043] The invention adopts the shadow s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com