Container escape detection and blocking method, device and equipment and storage medium
A container and process technology, applied in multi-program devices, program control devices, computer security devices, etc., can solve problems such as unable to kill escaped processes in time, achieve the effect of low performance consumption and protection of the operating system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
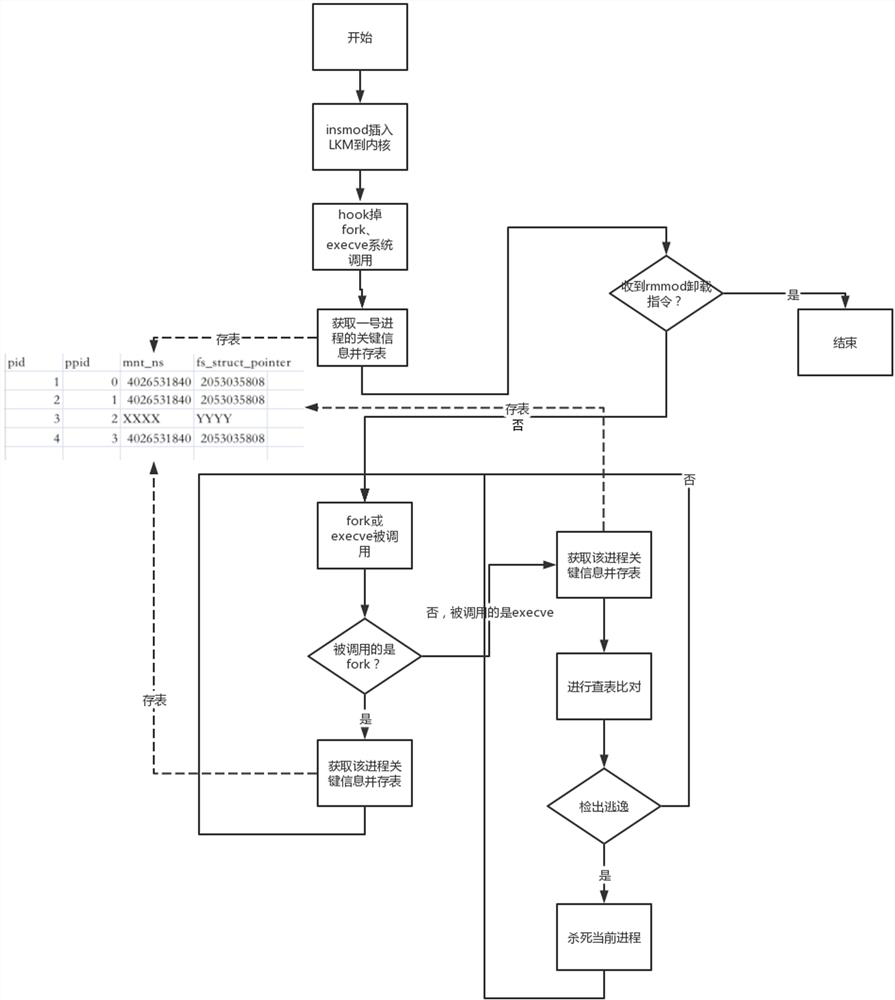
[0038] like figure 1 As shown, a container escape detection and blocking method includes the following steps:
[0039] S110, load a dynamically loadable kernel module in the system, and make the dynamically loadable kernel module hook a fork function for creating a subprocess and an execve function for converting the process into a binary program;
[0040] S120: Acquire key information of the host process and store it in the global table, where the key information includes its process identifier, the process identifier of its parent process, the string value of its namespace, and the value in its fs_struct structure ;
[0041] S130, when the fork function or the execve function is called by the container process, obtain key information of the container process and store it in the global table;
[0042] S140. Search the global table for the key information of the host process and compare it with the key information of the container process to determine whether the container p...
Embodiment 2
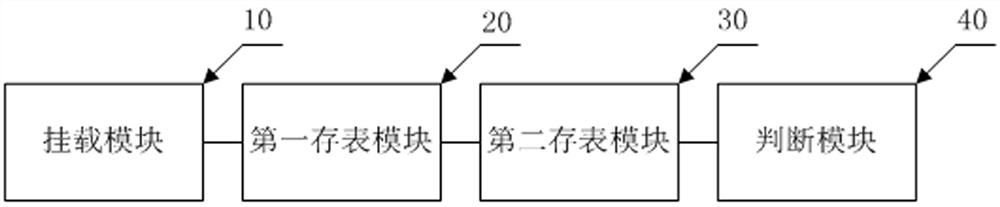
[0105] like figure 2 As shown, a container escape detection and blocking device includes:
[0106] The mount module 10 is used for loading a dynamically loadable kernel module in the system, and making the dynamically loadable kernel module hook a fork function for creating a child process and an execve function for converting a process into a binary program;
[0107] The first storage table module 20 is used to obtain the key information of the host process and store it in the global table, the key information includes its process identifier, the process identifier of its parent process, the string value of its namespace and The value in its fs_struct structure;
[0108] The second storage table module 30 is configured to acquire key information of the container process and store it in the global table when the fork function or the execve function is called by the container process;
[0109] The judgment module 40 is used to look up the key information of the host process ...
Embodiment 3
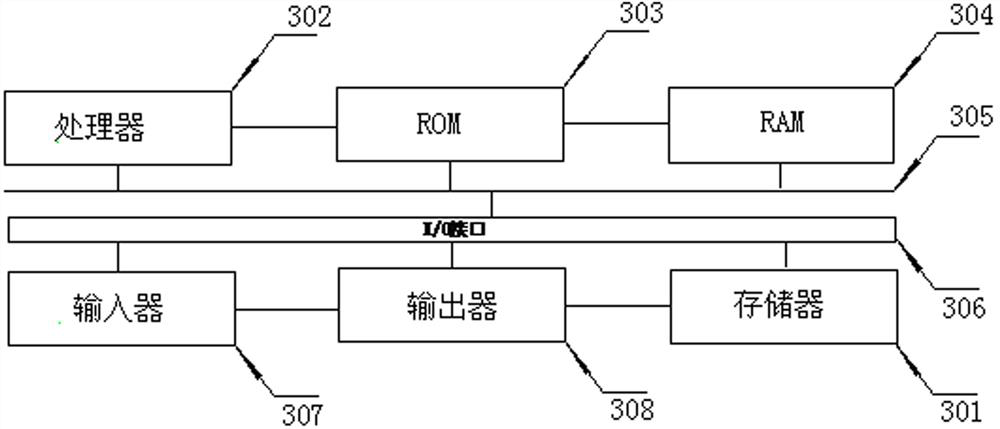
[0112] like image 3 As shown, an electronic device includes a memory 301 and a processor 302, the memory 301 is used to store one or more computer instructions, wherein the one or more computer instructions are executed by the processor 302 to achieve the above A container escape detection and blocking method. Those skilled in the art can clearly understand that, for the convenience and brevity of description, for the specific working process of the electronic device described above, reference may be made to the corresponding process in the foregoing method embodiments, which will not be repeated here. A computer-readable storage medium storing a computer program, the computer program enables the computer to implement the above-mentioned container escape detection and blocking method. Exemplarily, the computer program can be divided into one or more modules / units, one or more modules / units are stored in the memory 301 and executed by the processor 302, and the data is comple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com