Monitoring method for multi-level Android system malicious behaviors
A behavioral and malicious technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of poor monitoring comprehensiveness, inability to analyze malicious code hidden behavior, etc., and achieve the effect of comprehensive analysis results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with the accompanying drawings and practical examples. Here, the exemplary embodiments of the present invention and the description therein are used to explain the present invention, but not as a limitation to the present invention.
[0042] The implementation use case includes a smart phone, using Android system.
[0043] First link
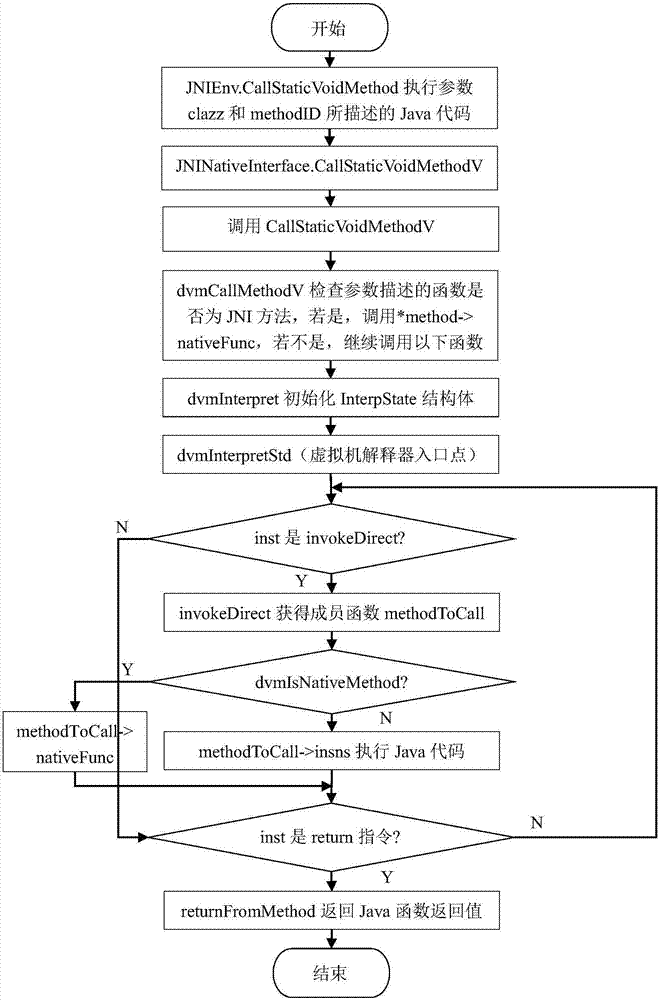
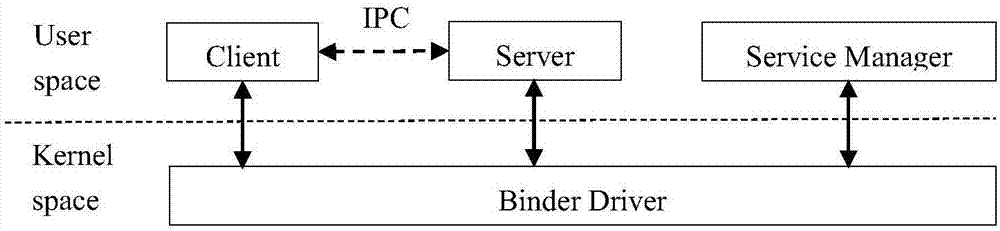
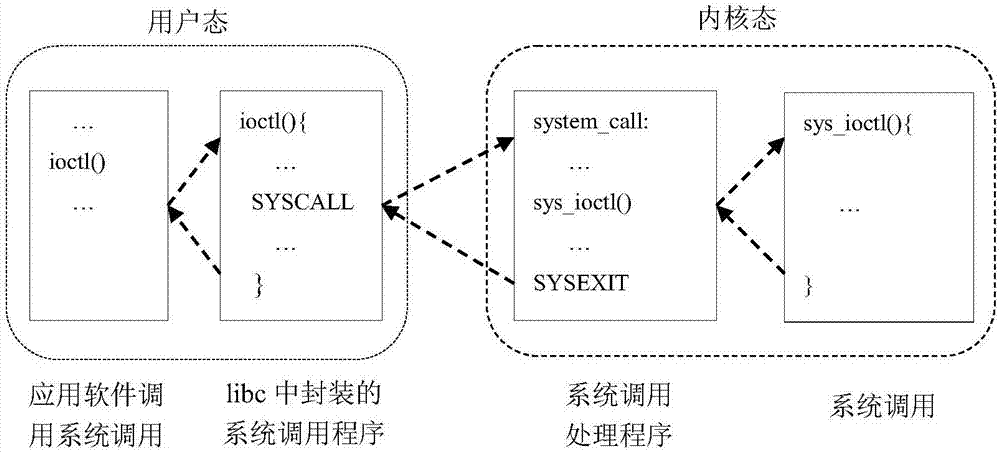
[0044] The purpose of this link is to monitor the malicious behavior of the Java layer, use the Dalvik virtual machine interception technology to monitor the malicious behavior of the Java layer, and output a list of malicious behavior 1, as attached figure 1 Shown. The specific implementation steps are as follows:
[0045] Step 1.1, take the interceptKeyBeforeQueueing function that intercepts the member function in the PhoneWindowManager class for pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com