Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Secondary Identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
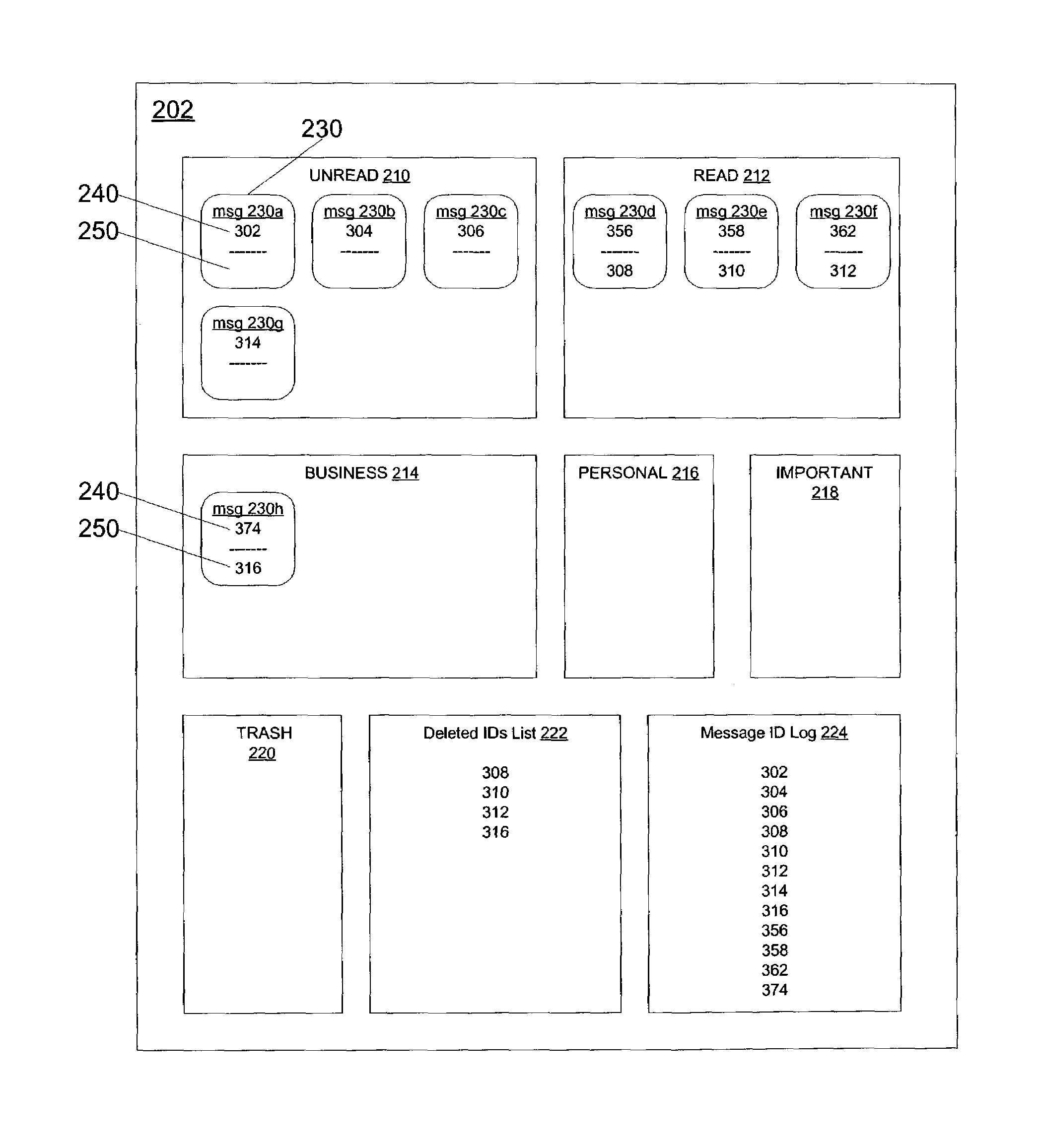
Secondary Identifiers. The names of divisions, colleges, departments and programs will be incorporated into the formal and informal logos using a secondary identifier, as represented by the samples below.
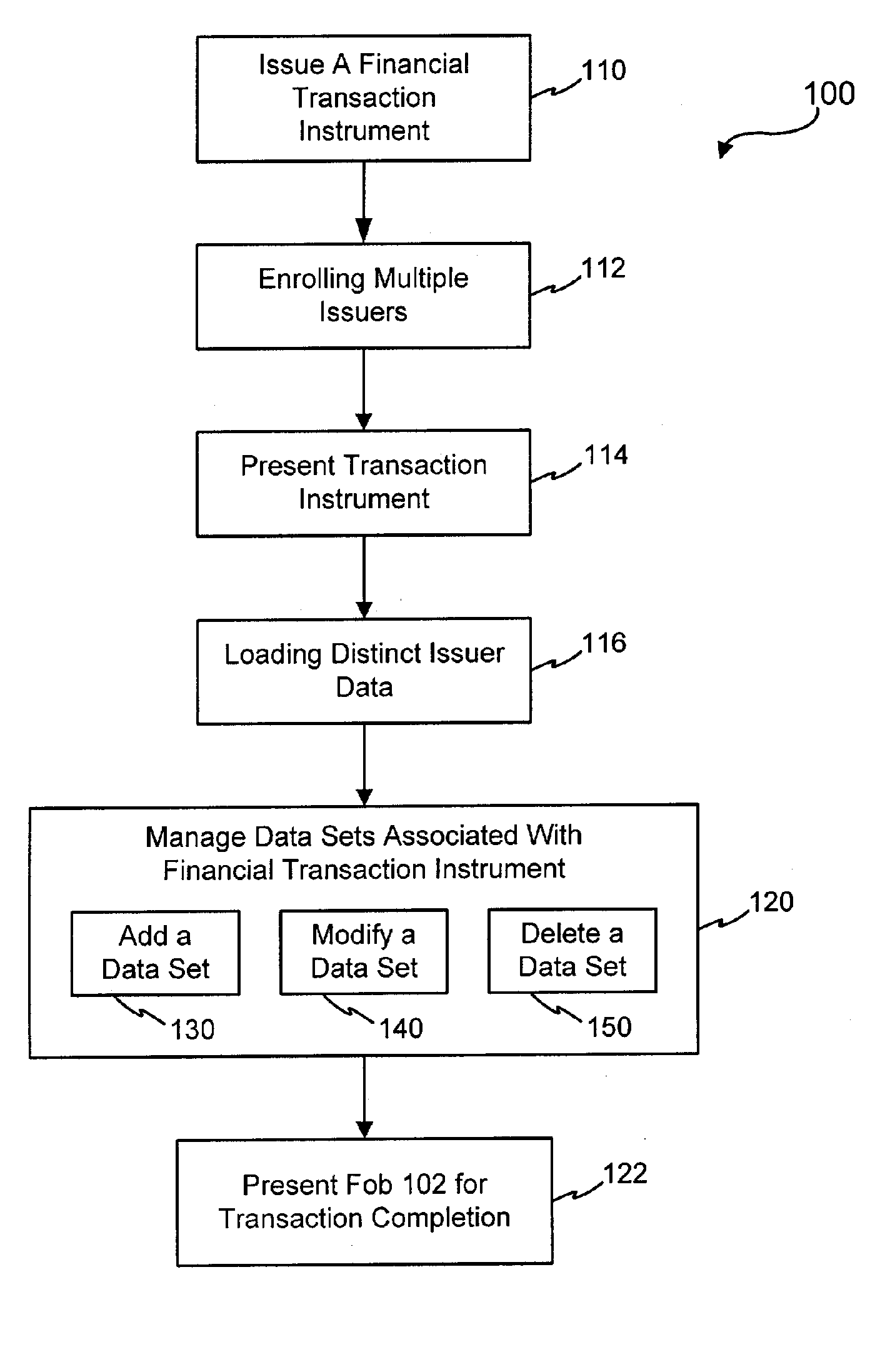
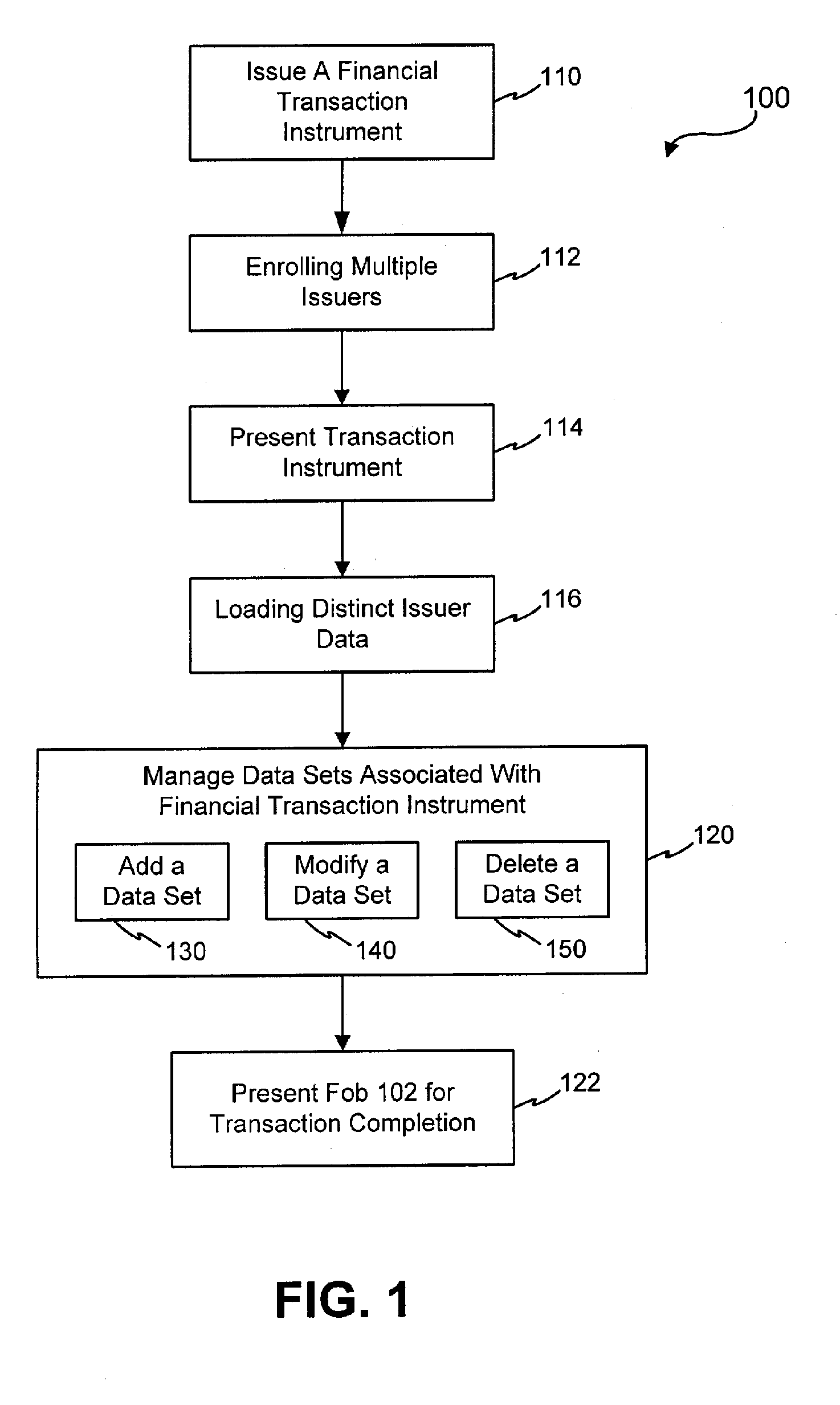
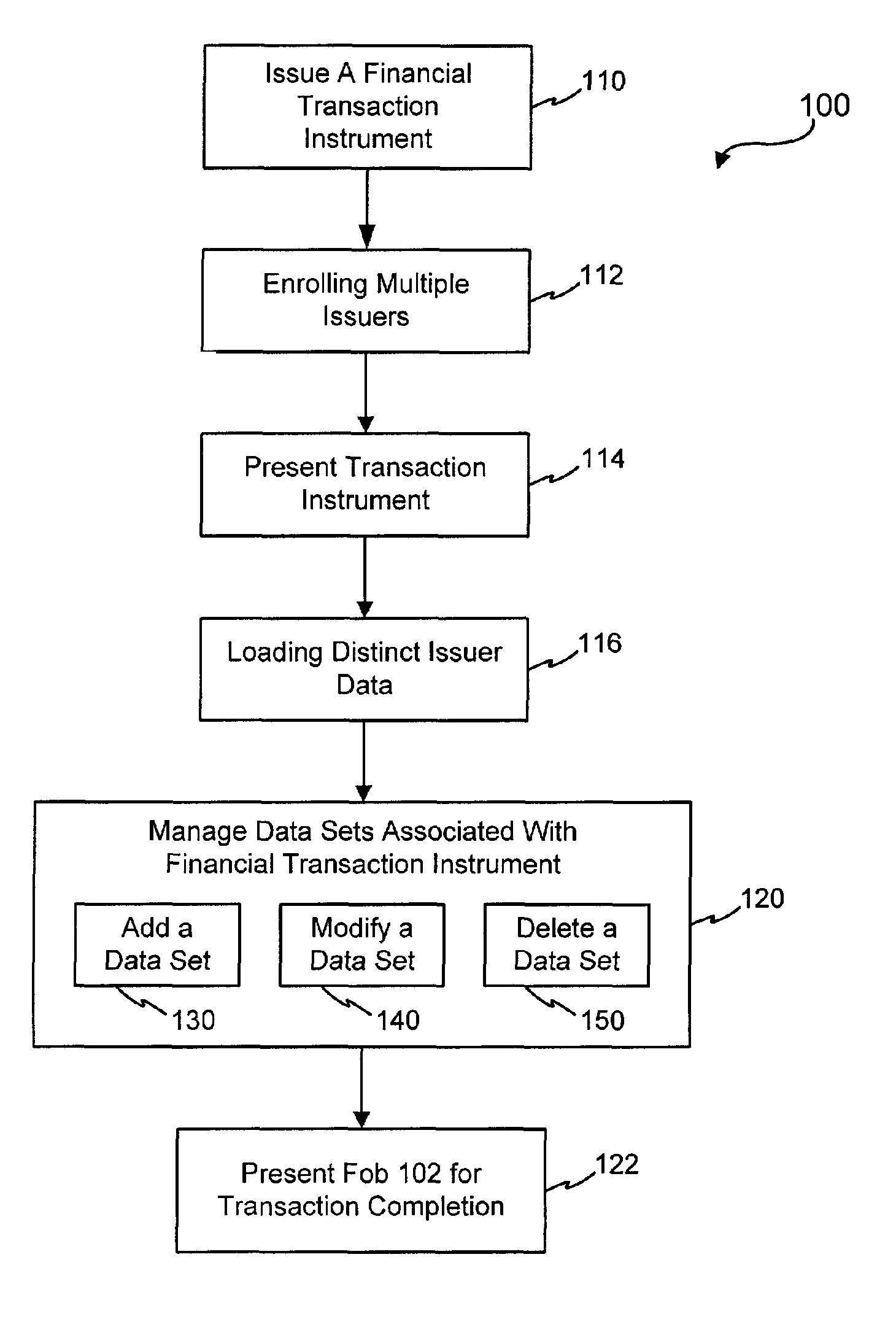
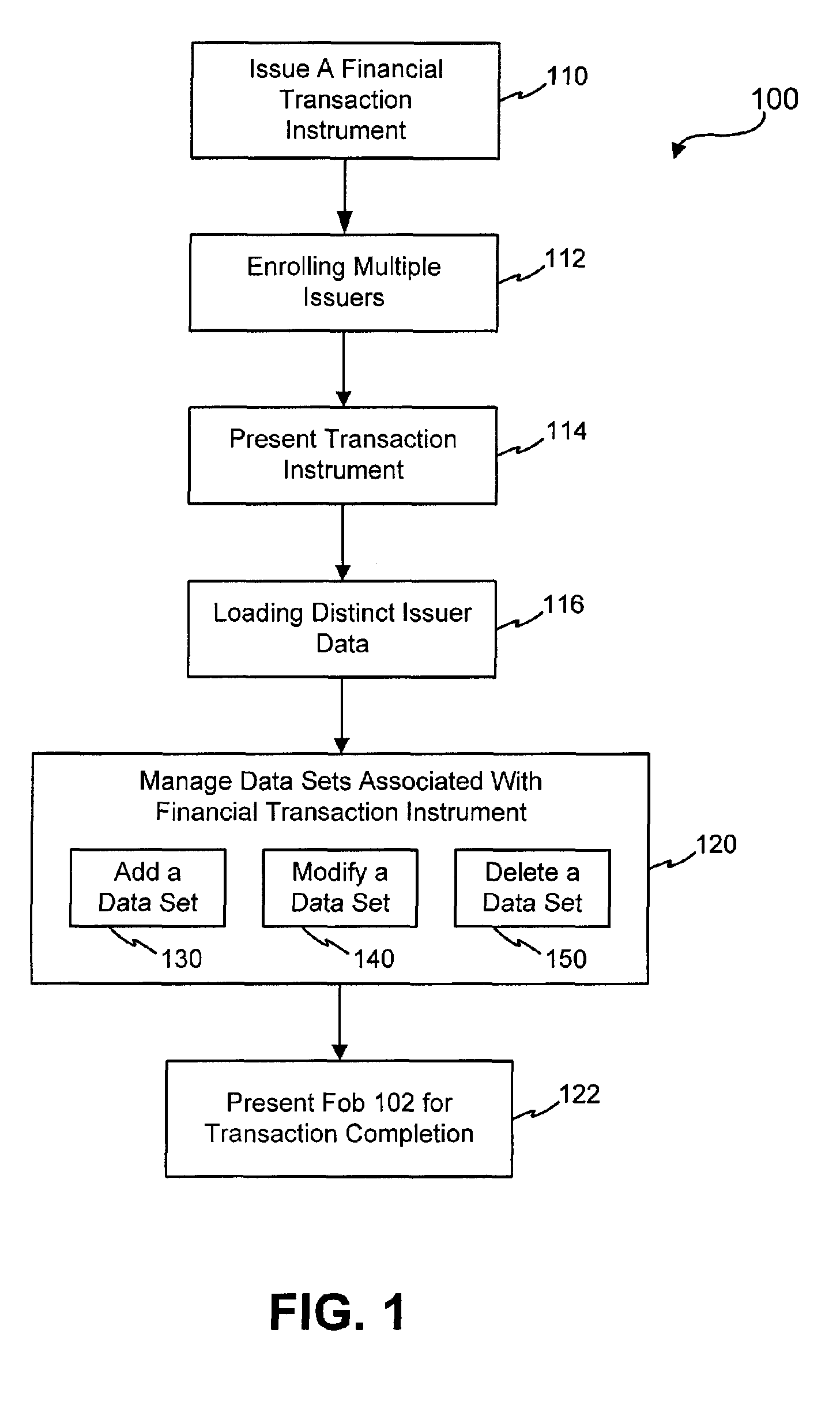
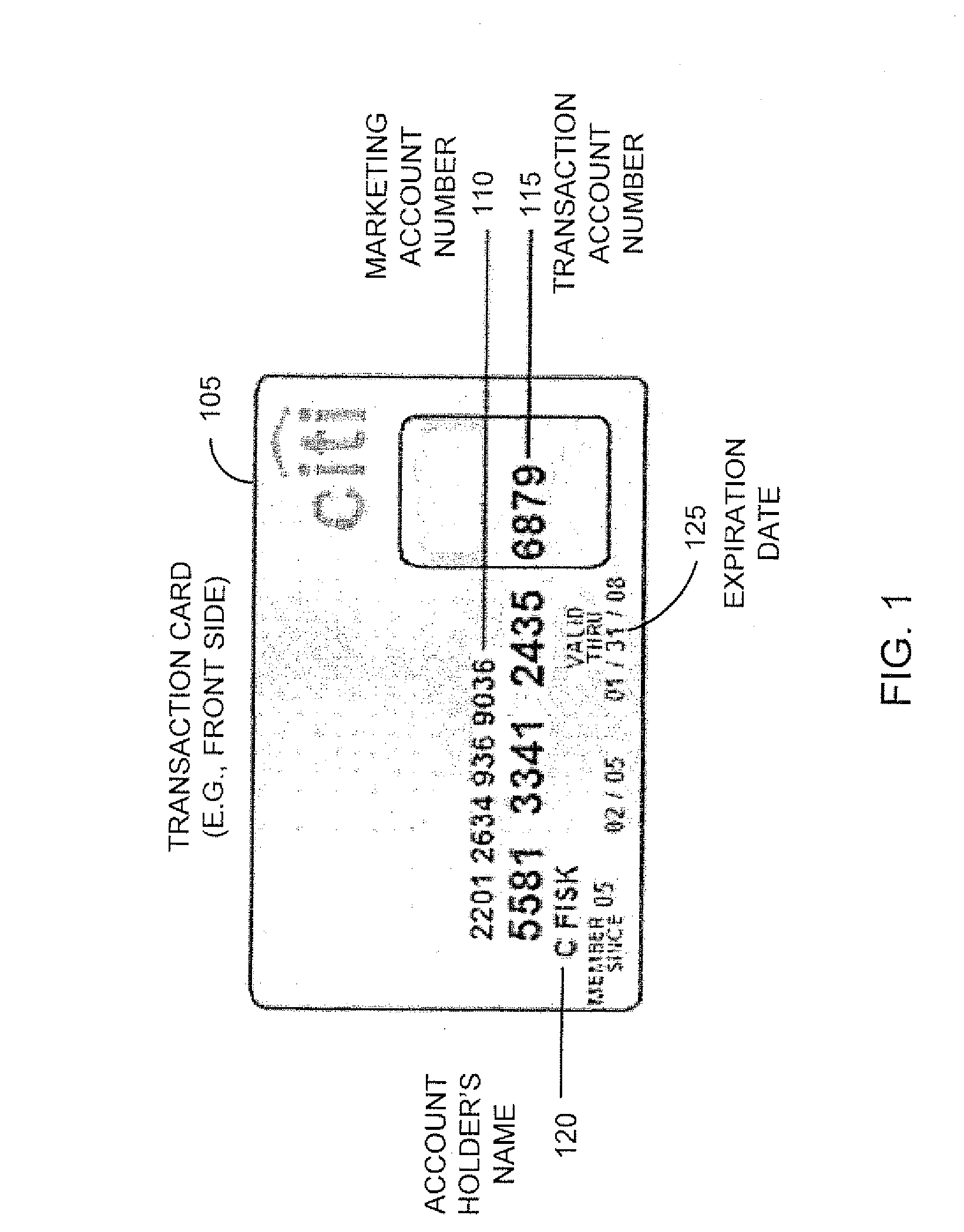
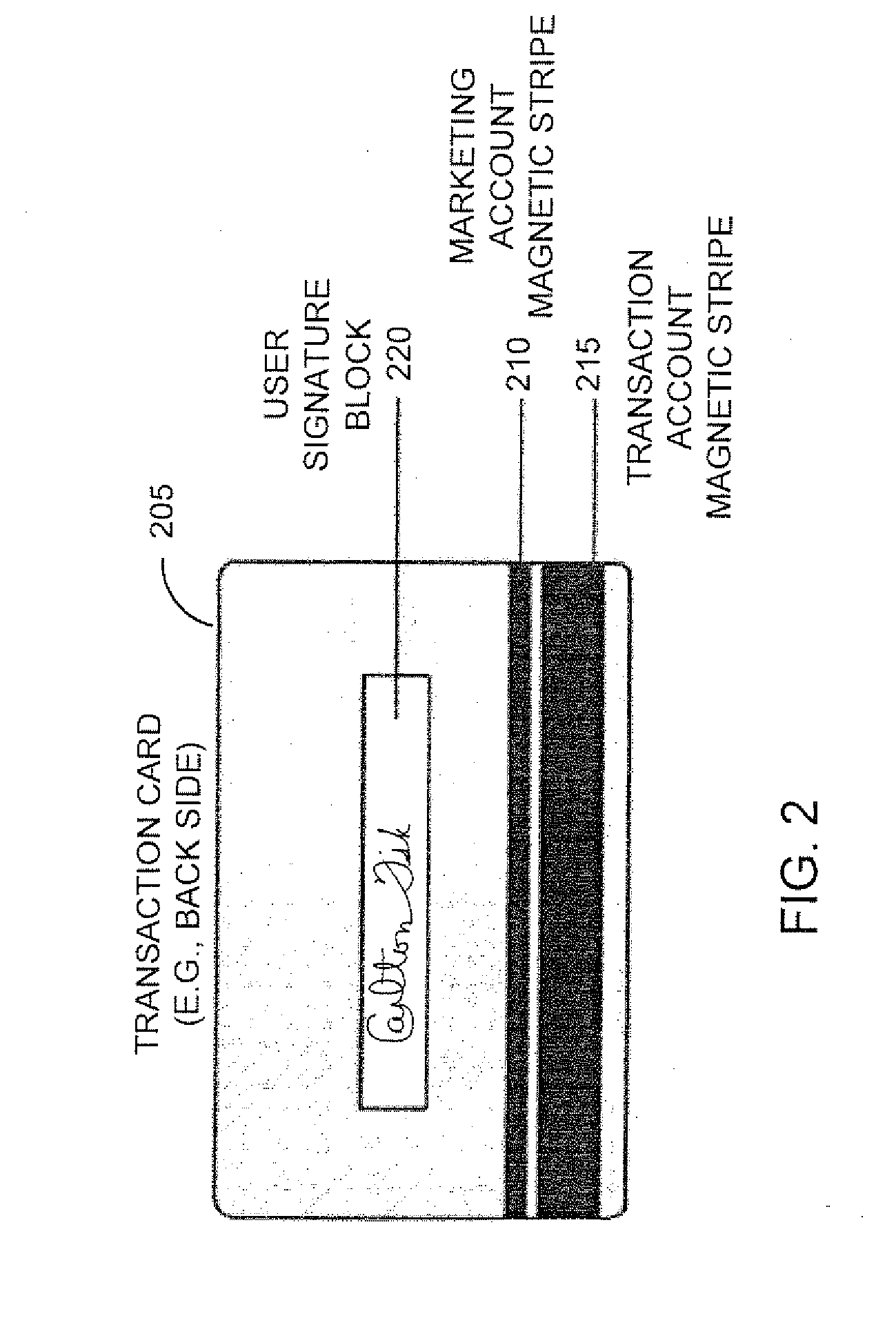
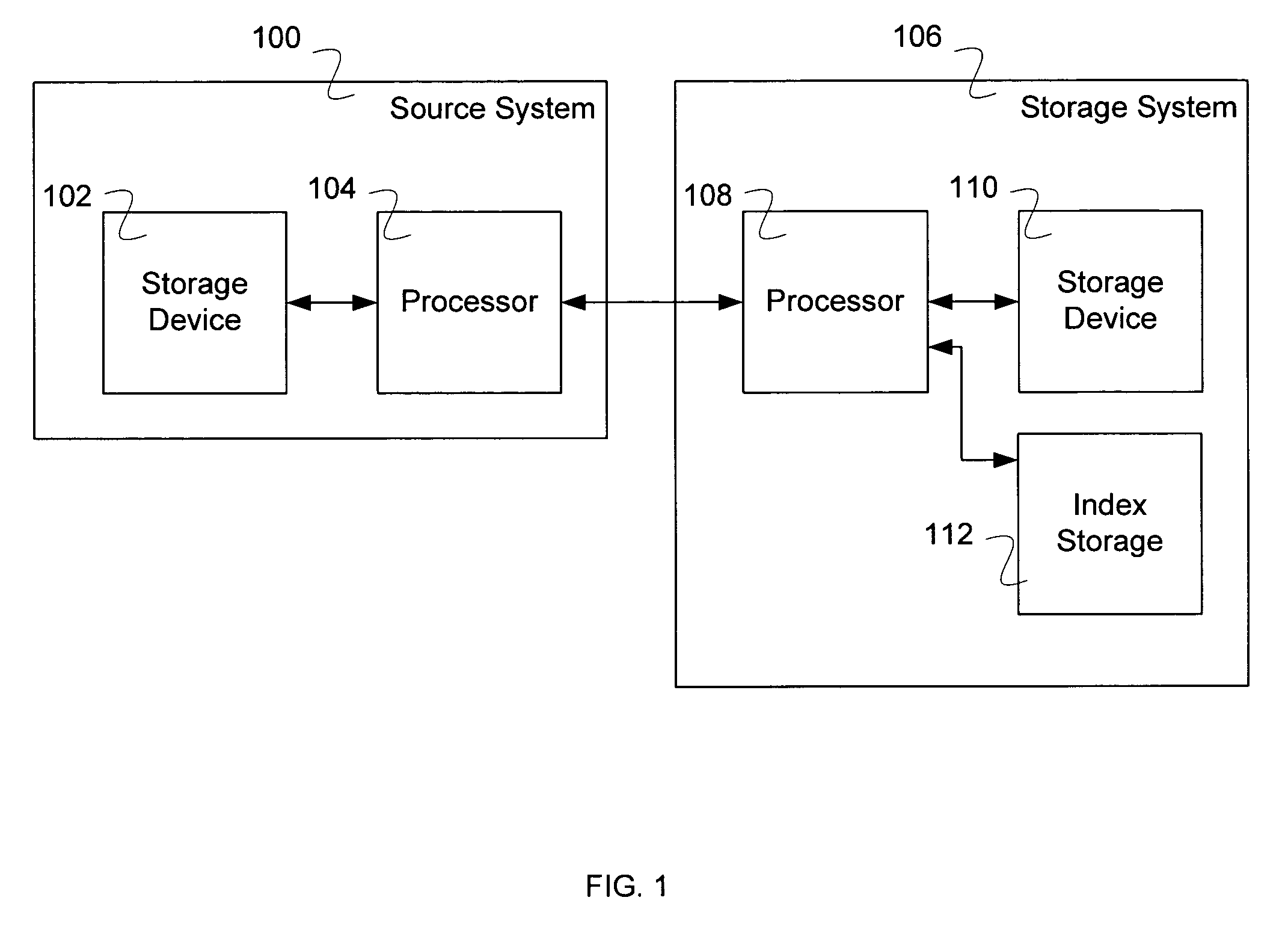
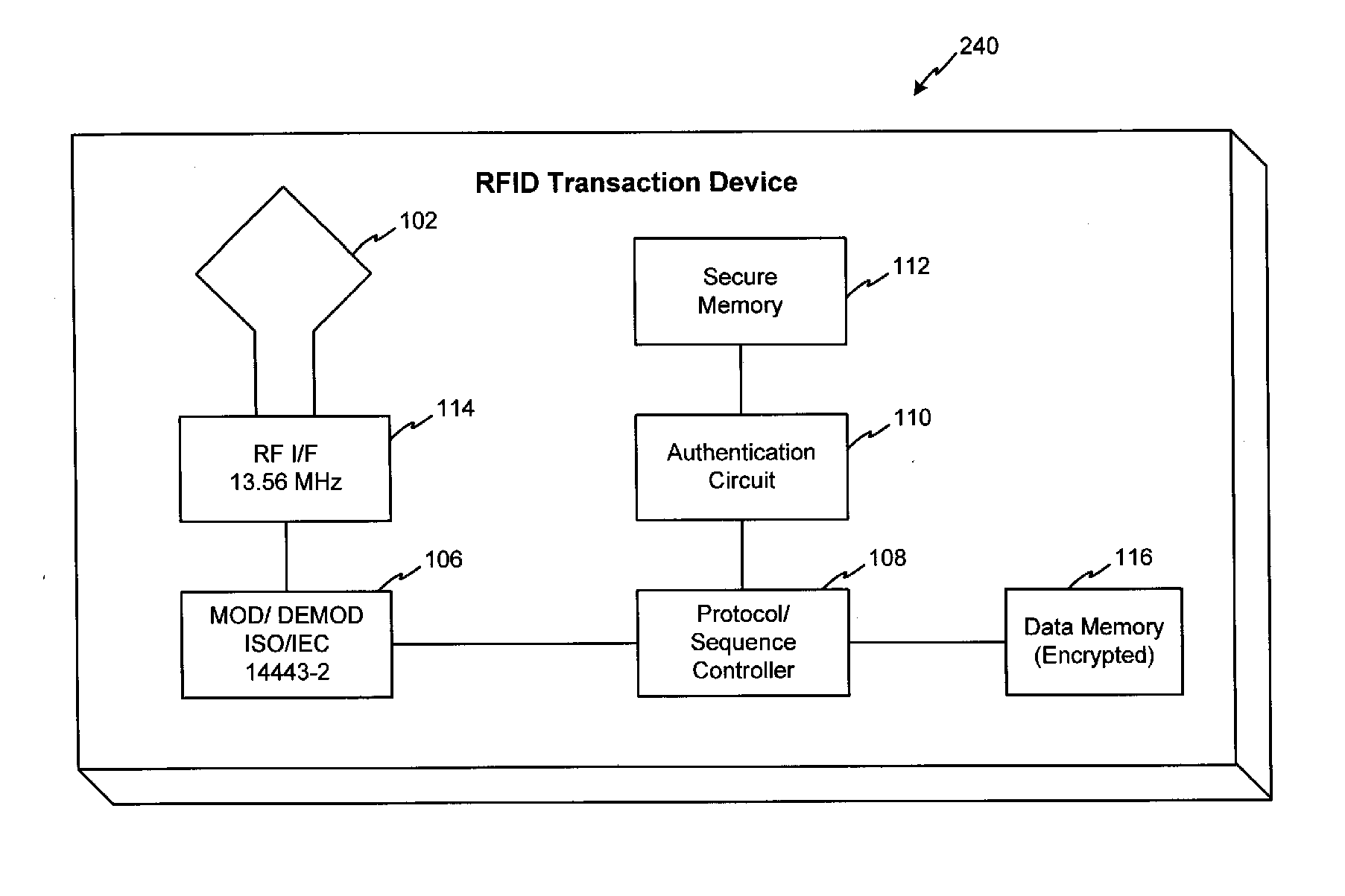
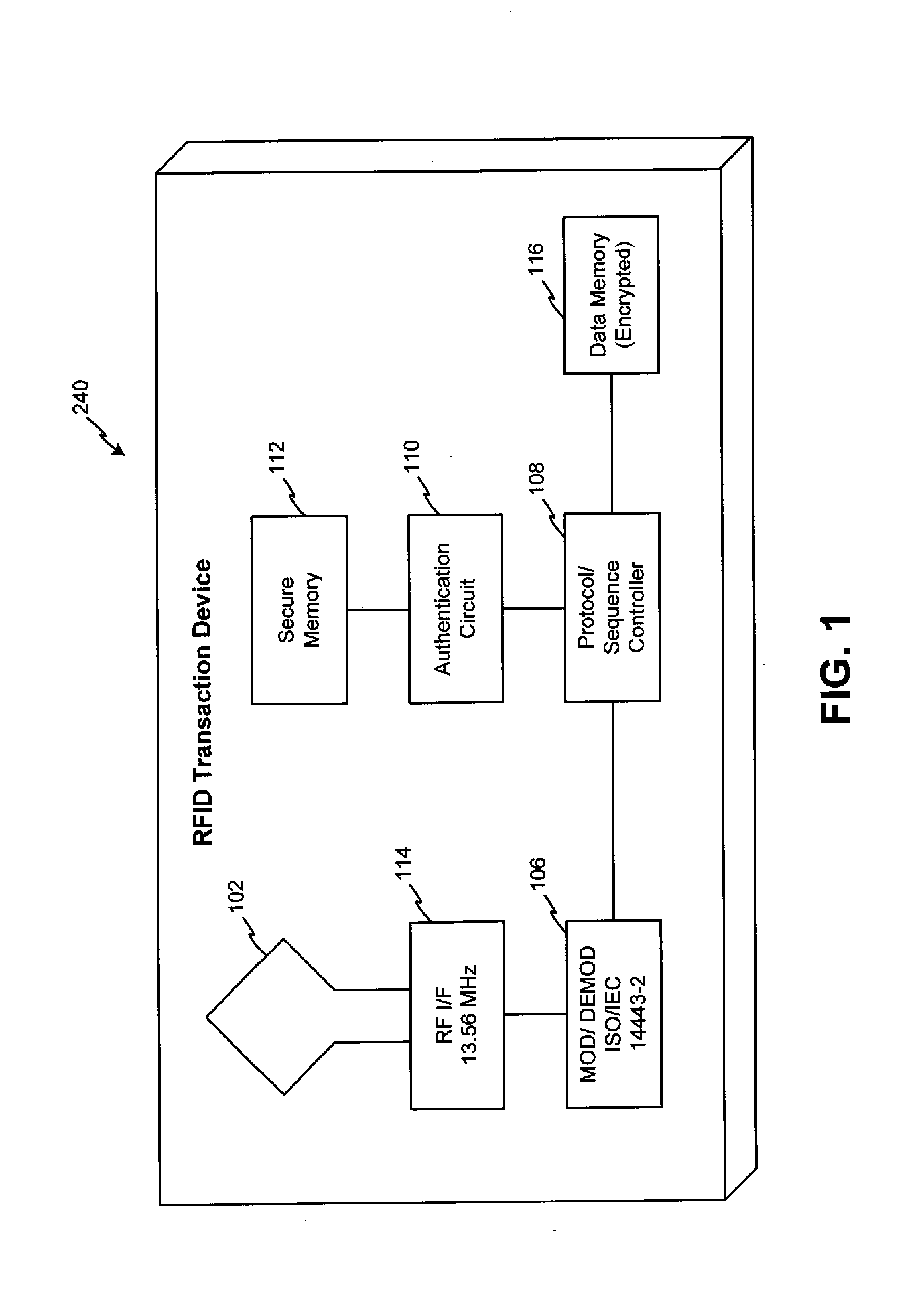
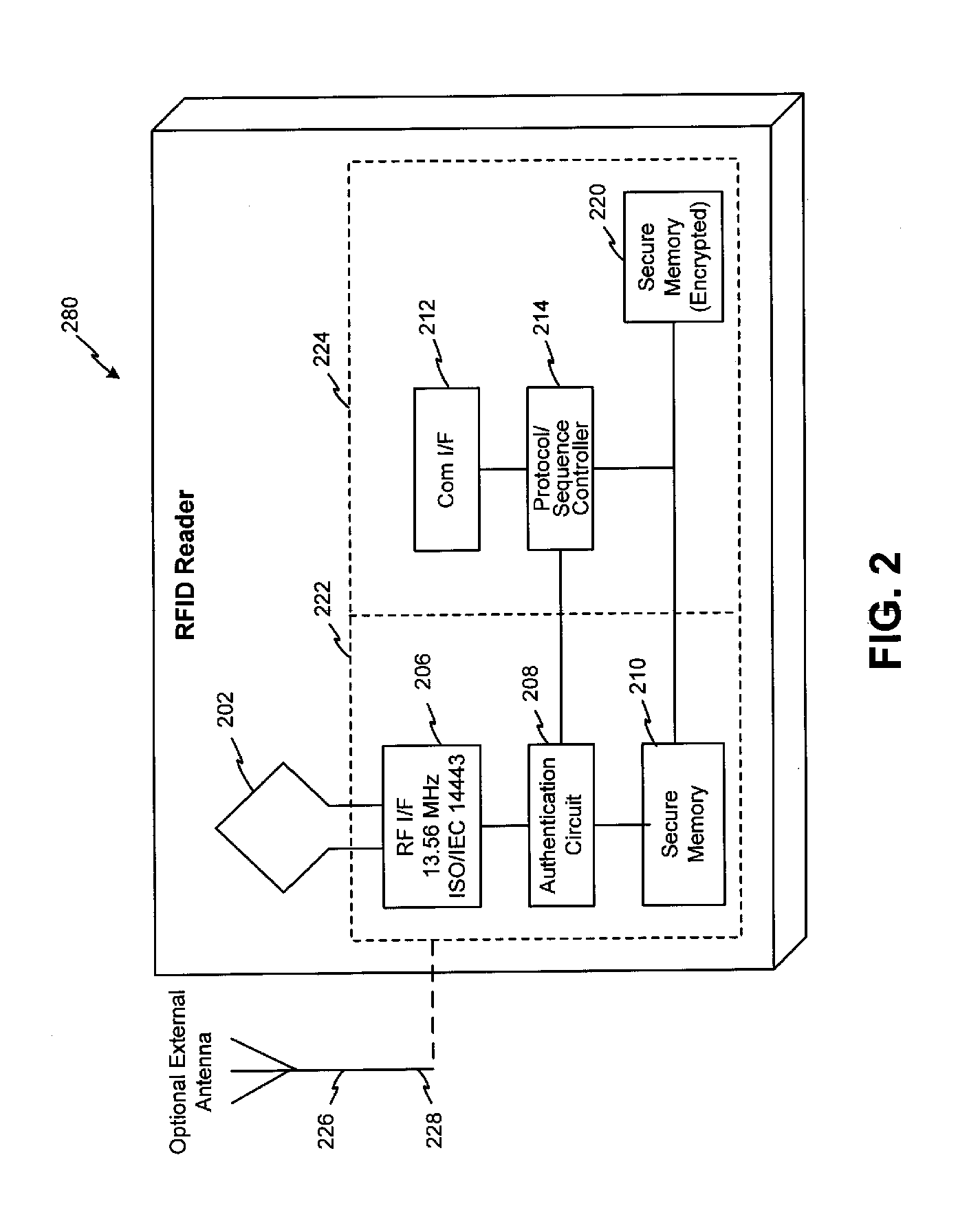
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
InactiveUS20050171898A1Easy to manageEliminate needAcutation objectsFinanceData setFinancial transaction
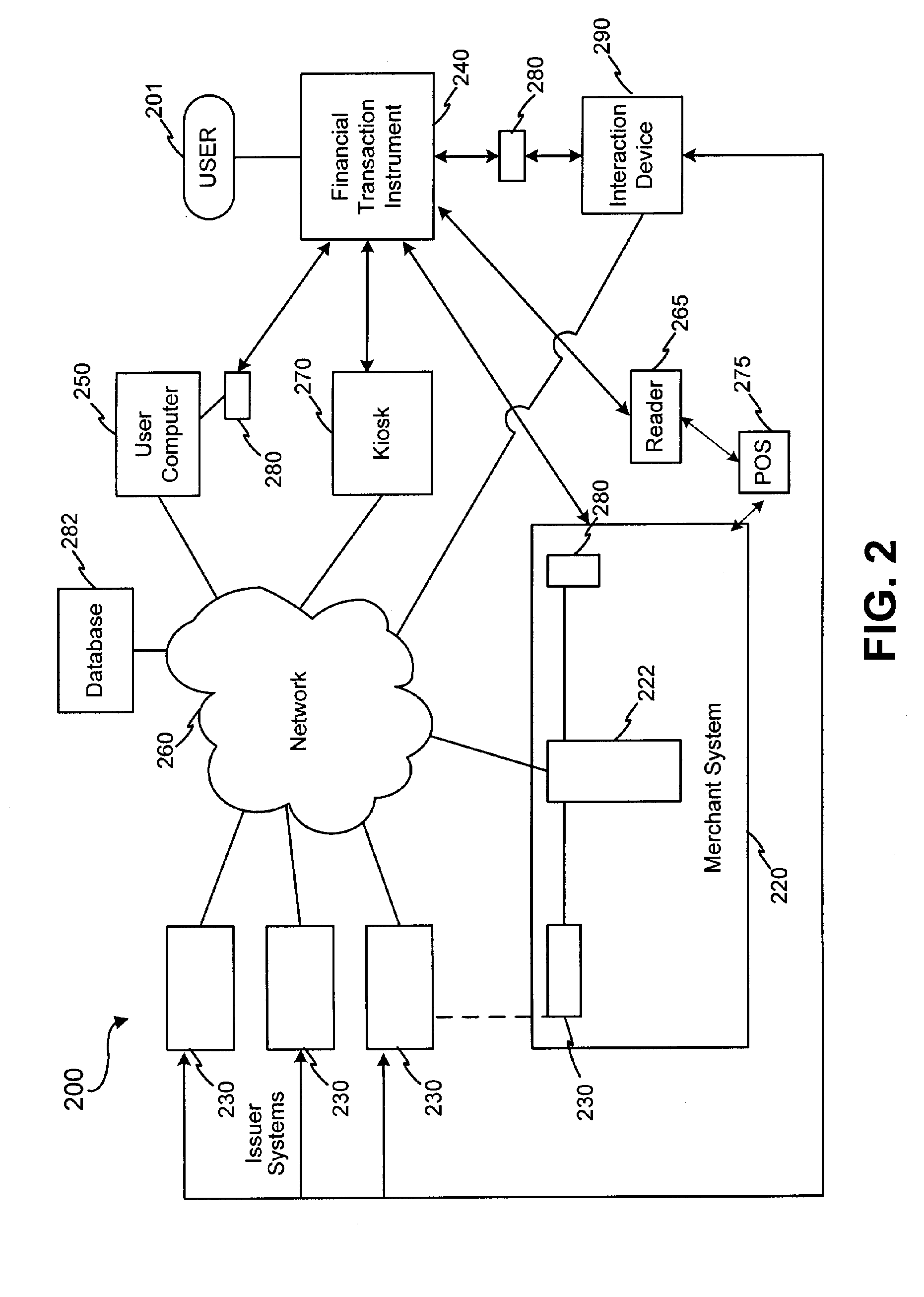
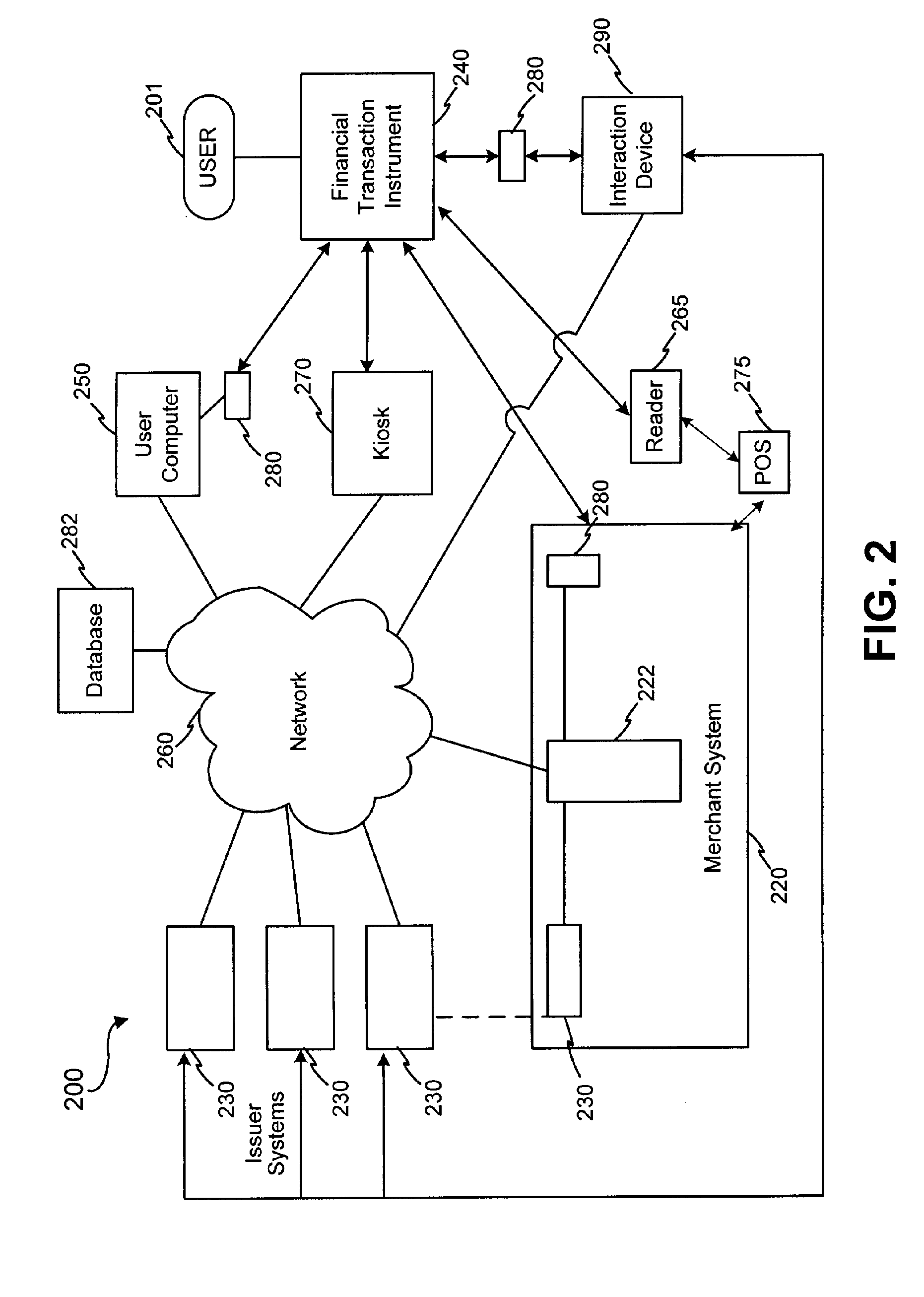
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
System and method for advertising
InactiveUS20150170209A1Avoid the needCongest the advertising spaceMarketingSecondary IdentifierAd serving
A system and method for generating advertisements is described. The system and method selects from one or more advertisement templates. One or more advertisement types are selected from the one or more advertisement templates. One or more unique primary identifiers are associated with the advertisement and a secondary identifier is associated with each of the one or more unique primary identifiers.
Owner:ASTARICKS GRP
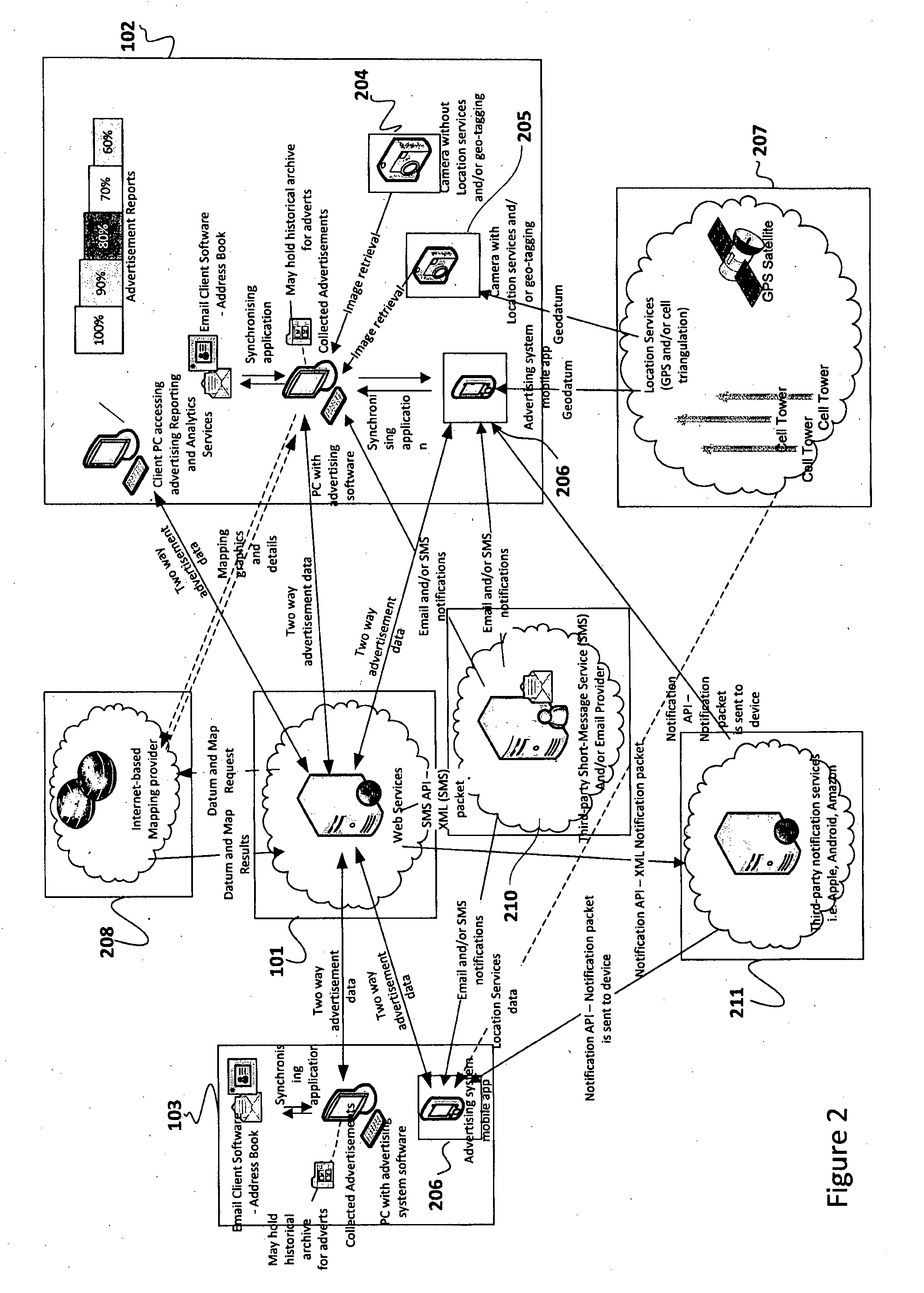
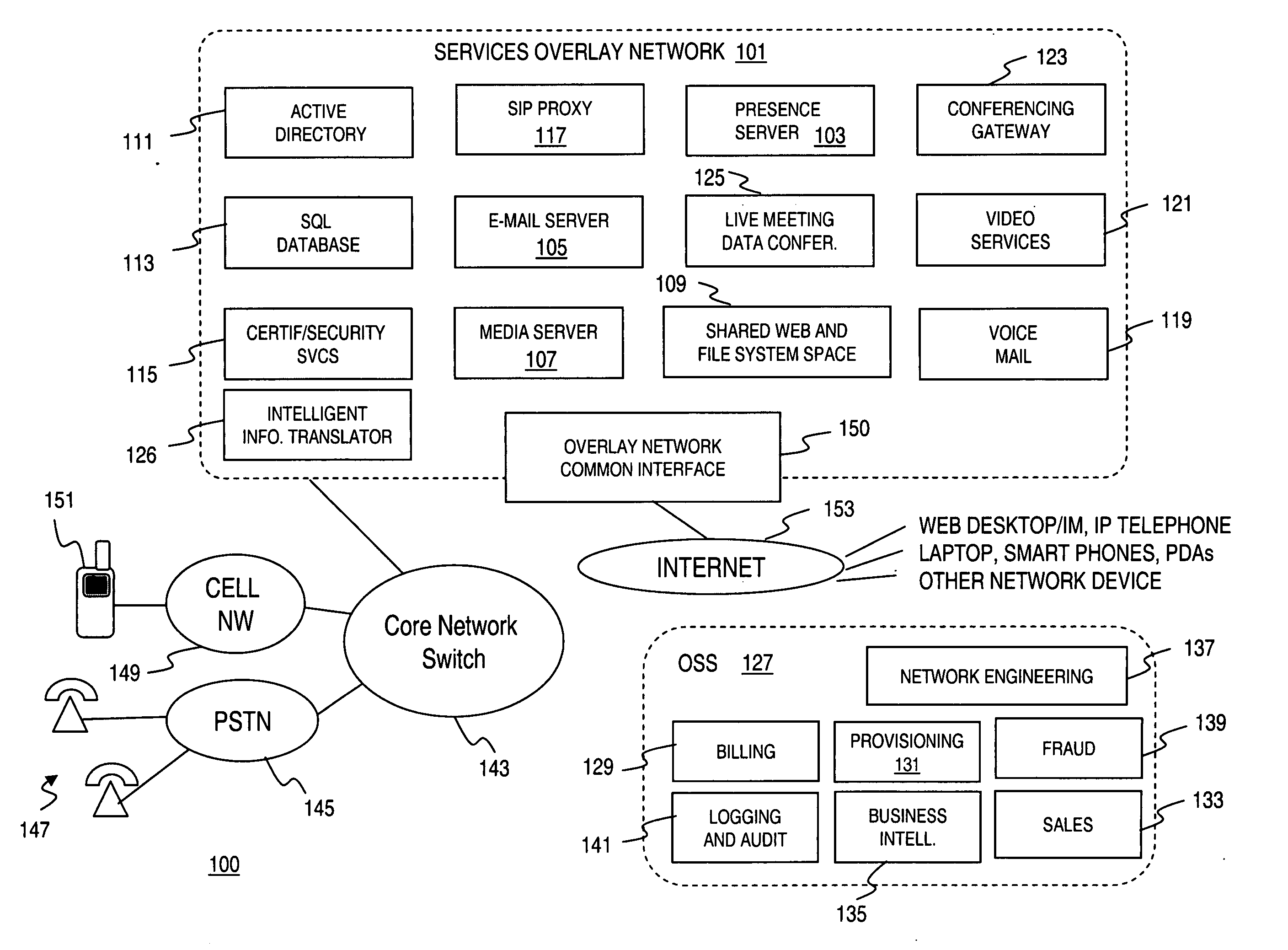
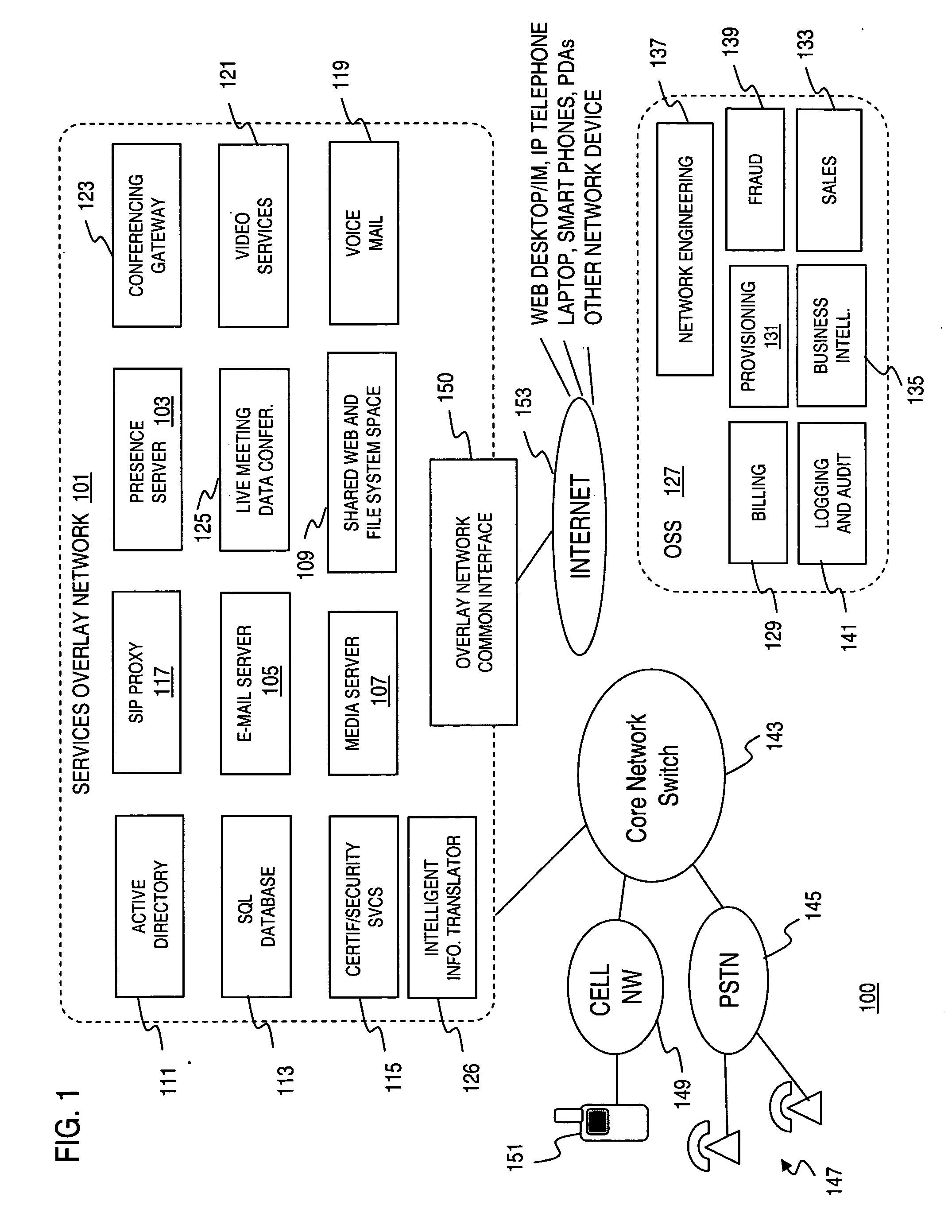
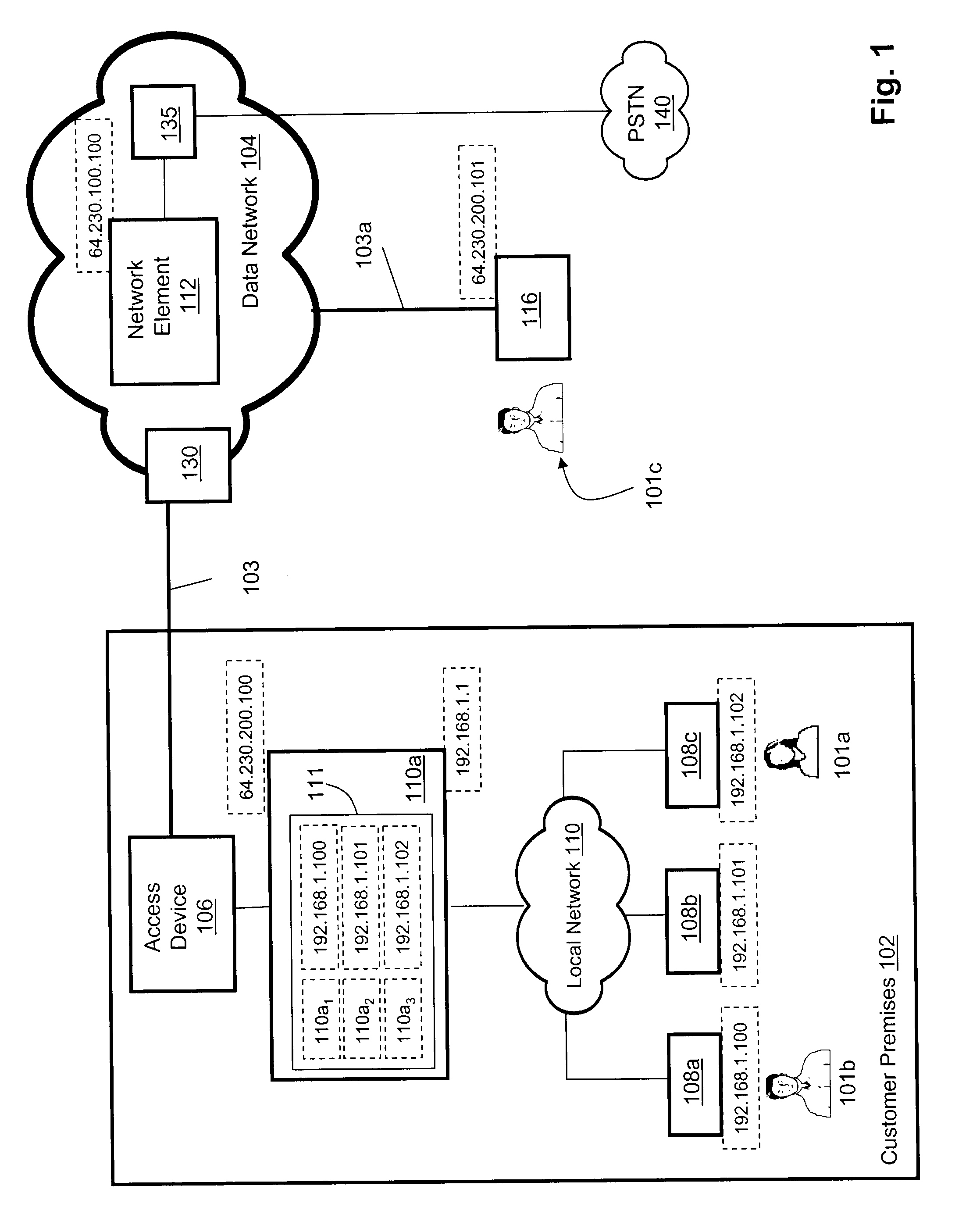
Comprehensive communication services system
ActiveUS20050163108A1Reduce needMultiplex system selection arrangementsInterconnection arrangementsTelephone networkUser identifier
An approach is provided for offering communication services supported by a data network and a telephony network. A primary identifier is assigned to a user for access to the communication services, wherein the primary identifier is used by a party seeking to communicate with the user via one of the communication services. The primary identifier is mapped to one of a plurality of secondary identifiers corresponding to the respective communication services. The one secondary identifier is used by at least one of the data network and the telephony network to establish a communication session between the party and the user.
Owner:VERIZON PATENT & LICENSING INC
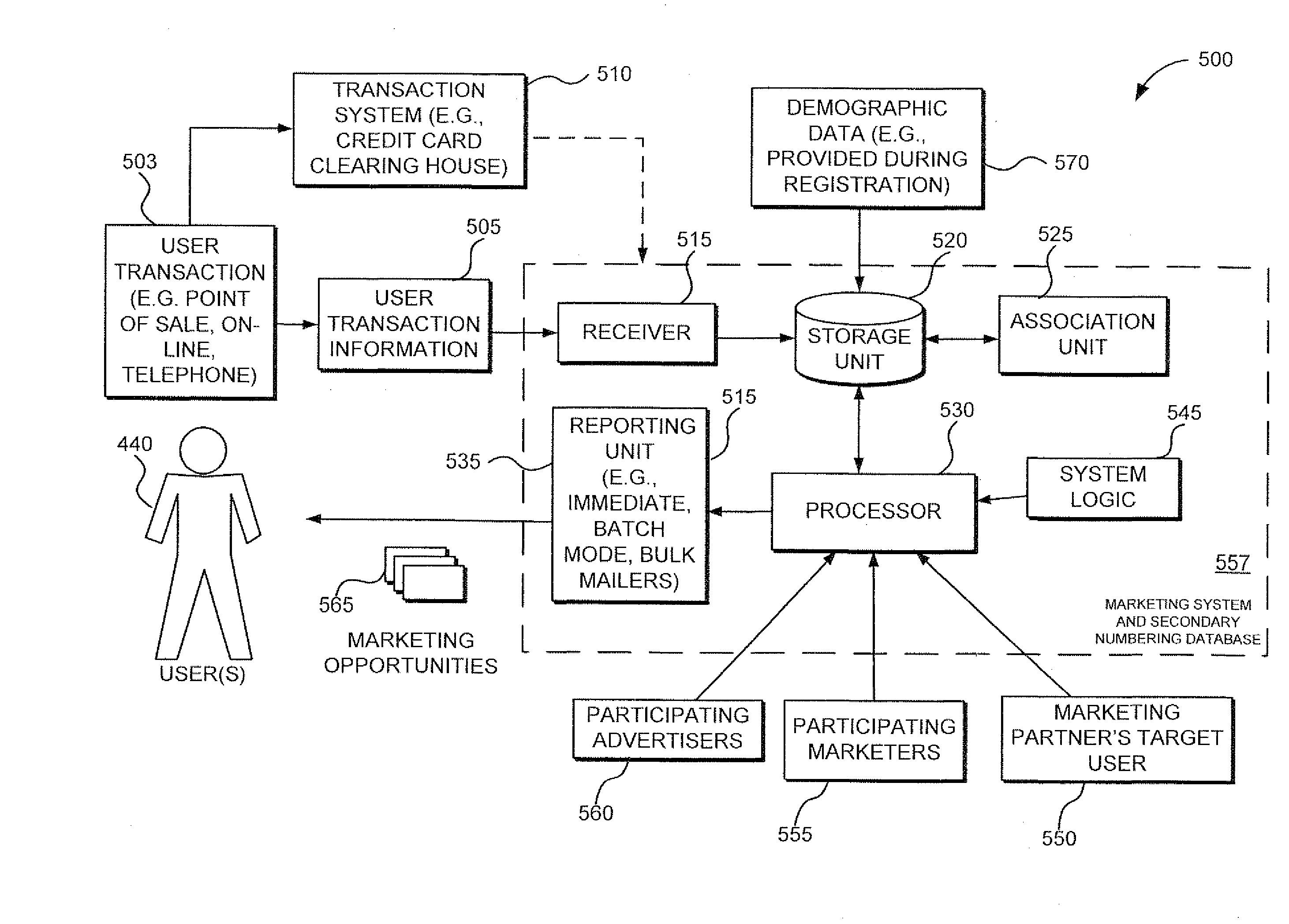
Method and Apparatus for Processing and Transmitting Demographic Data Based on Secondary Marketing Identifier in a Multi-Computer Environment
InactiveUS20090094158A1Reduce fraudReduce piracyMarket predictionsUser identity/authority verificationAnalysis dataDemographic data
A method and system for transmitting targeted marketing opportunities to a user includes providing a primary identifier associated with a transaction account, and a secondary identifier associated with a marketing account. Received transaction information related to the transaction account is associated with the secondary identifier and stored. A user is associated with the secondary identifier. The stored transaction information is processed to generate targeted marketing opportunities for presentation to the user associated with the secondary identifier.In use, the apparatus and method may externally transfer data between a plurality of computers (e.g., between a computerized point-of-transaction unit and a transaction / marketing system). The point-of-transaction unit may extract, process, and transfer data pertaining to a user's transaction to at least one other computerized system (e.g., multiplatform marketing and research system) where the data may be analyzed to determine targeted marketing opportunities for transmission to a user or group of users, for example.
Owner:GEFEMER RES ACQUISITIONS
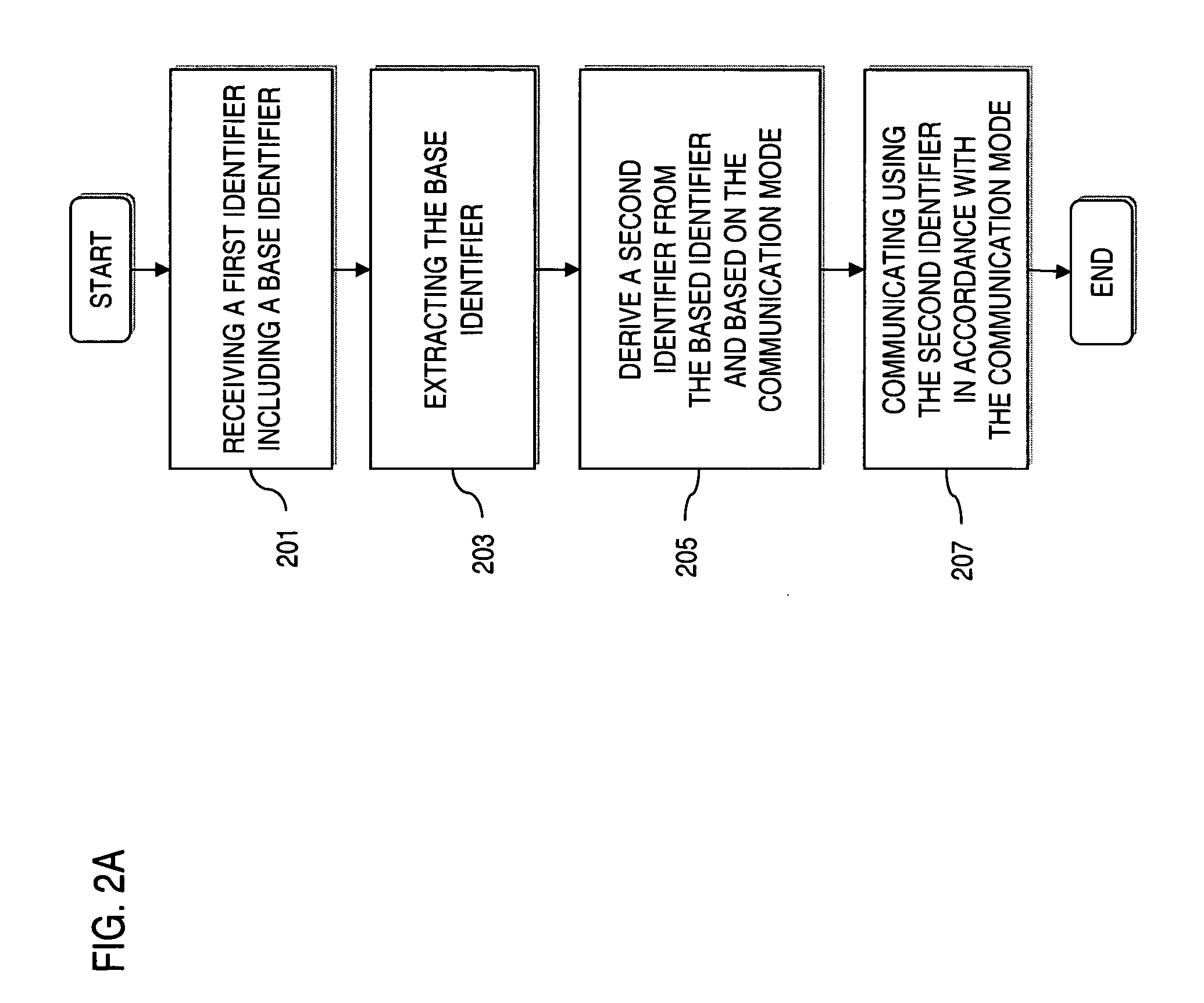
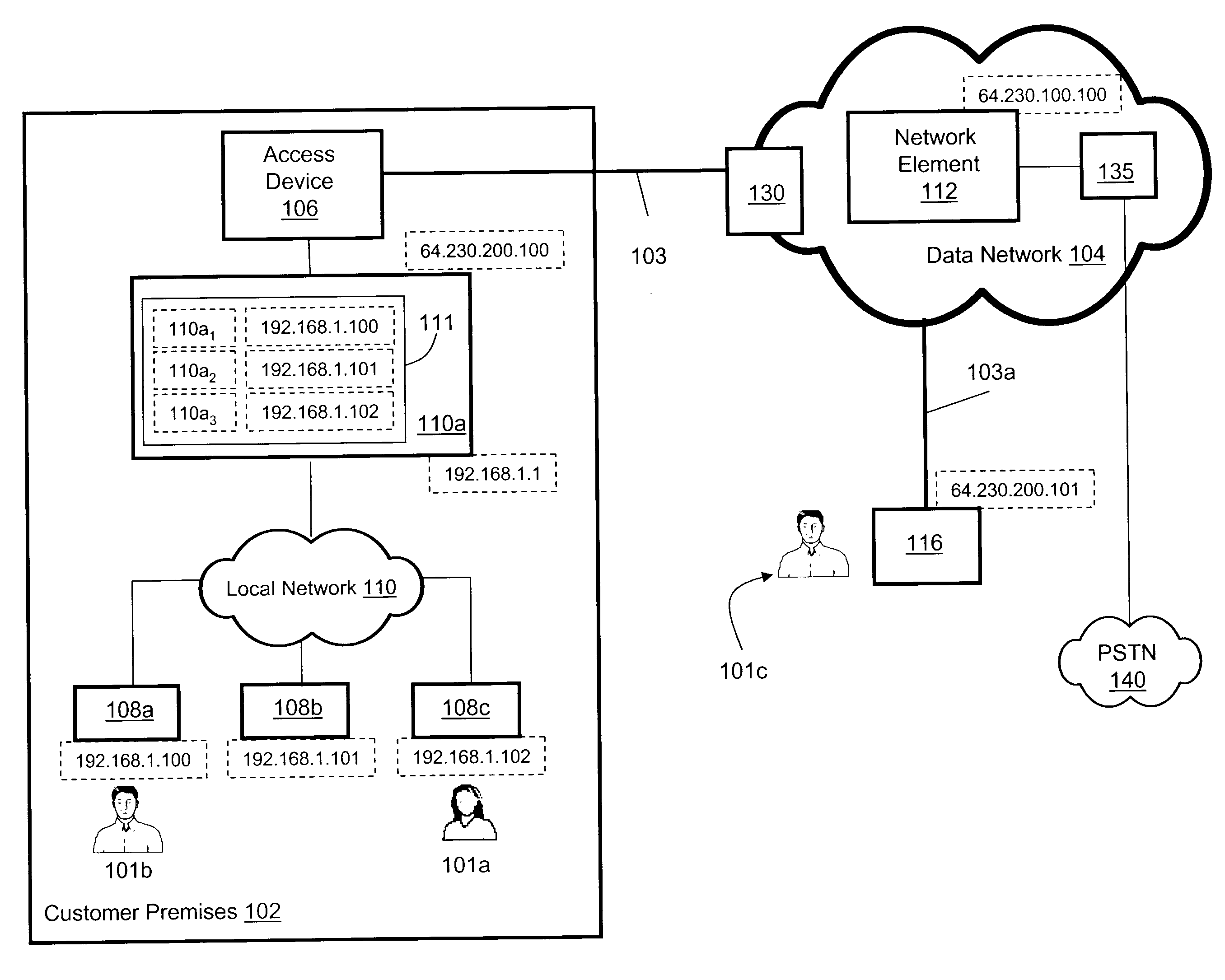
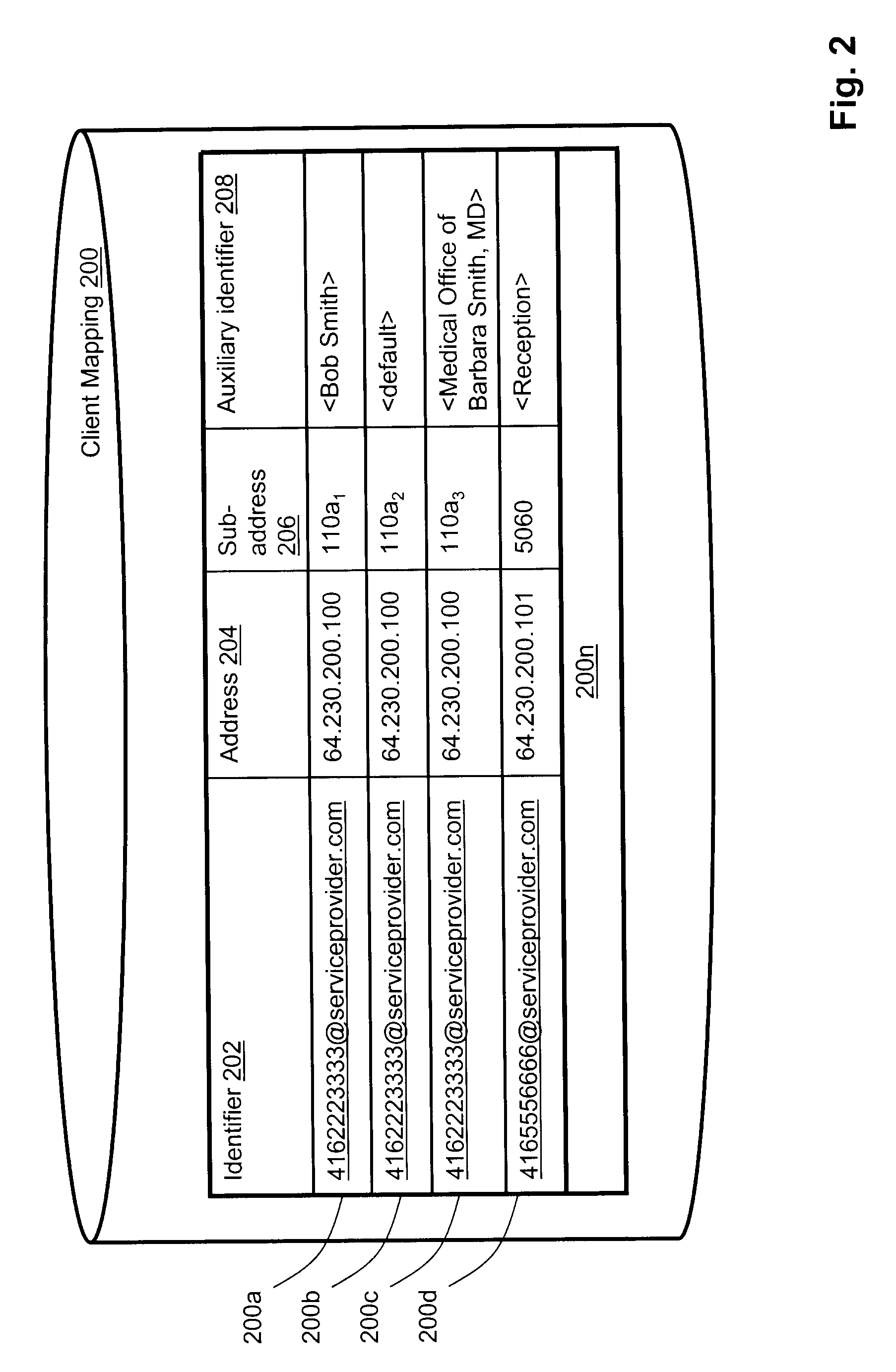
Method, system and apparatus for providing calling name identification
ActiveUS20110026700A1Calling susbscriber number recording/indicationAutomatic exchangesNetwork addressingNetwork address
Embodiments of the present invention are directed to a method, system and apparatus for providing customized calling identification. A method for providing customized calling identification comprises receiving a request for initiating an out-going call from a communication client, the communication client being registered in association with a network address and being associated with a communication client identifier. The method further comprises, based on the communication client identifier, determining an auxiliary identifier associated with the communication client. The method further comprises augmenting the request for initiating an outgoing call with the auxiliary identifier to generate an augmented request.
Owner:BCE
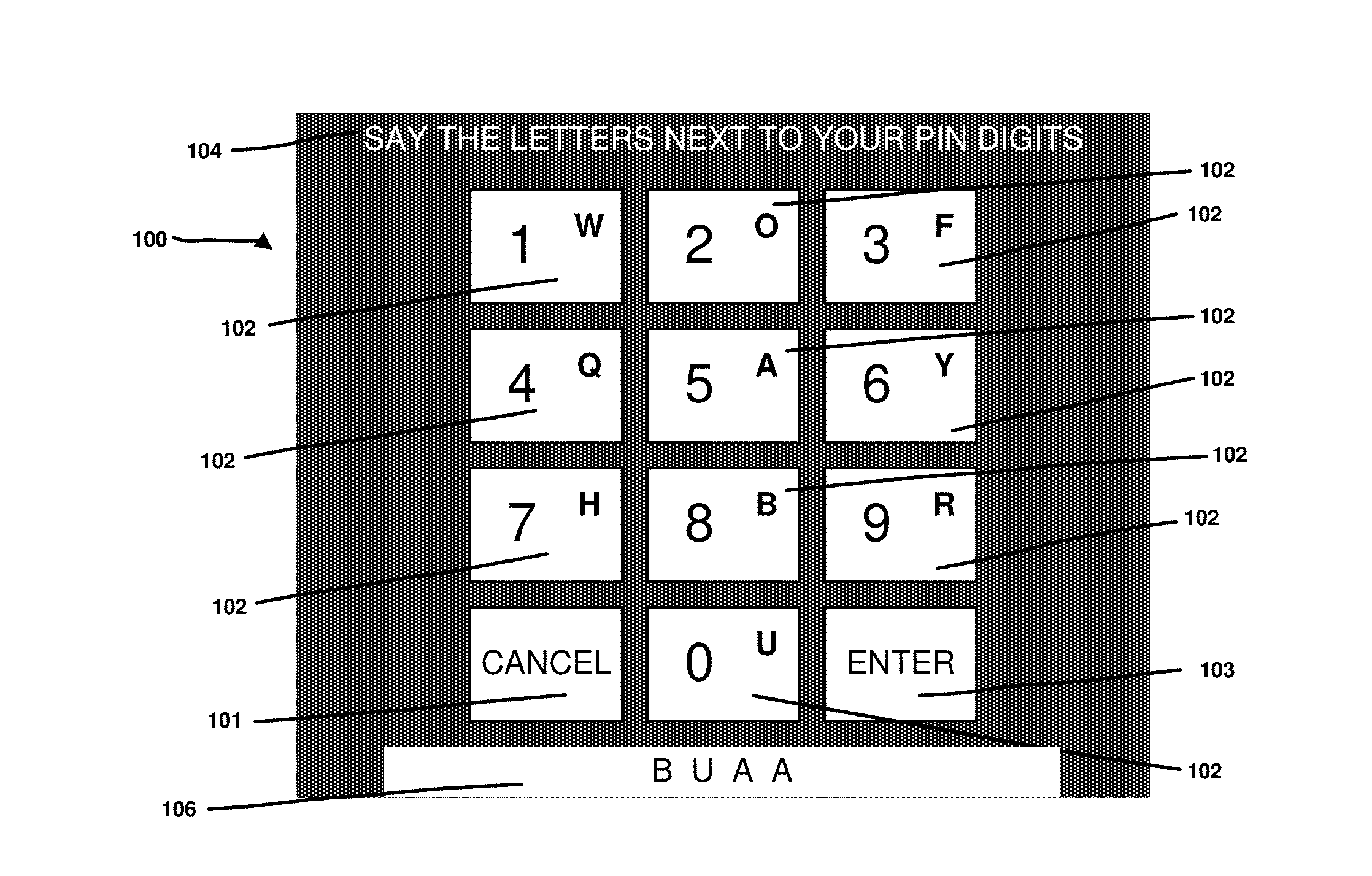
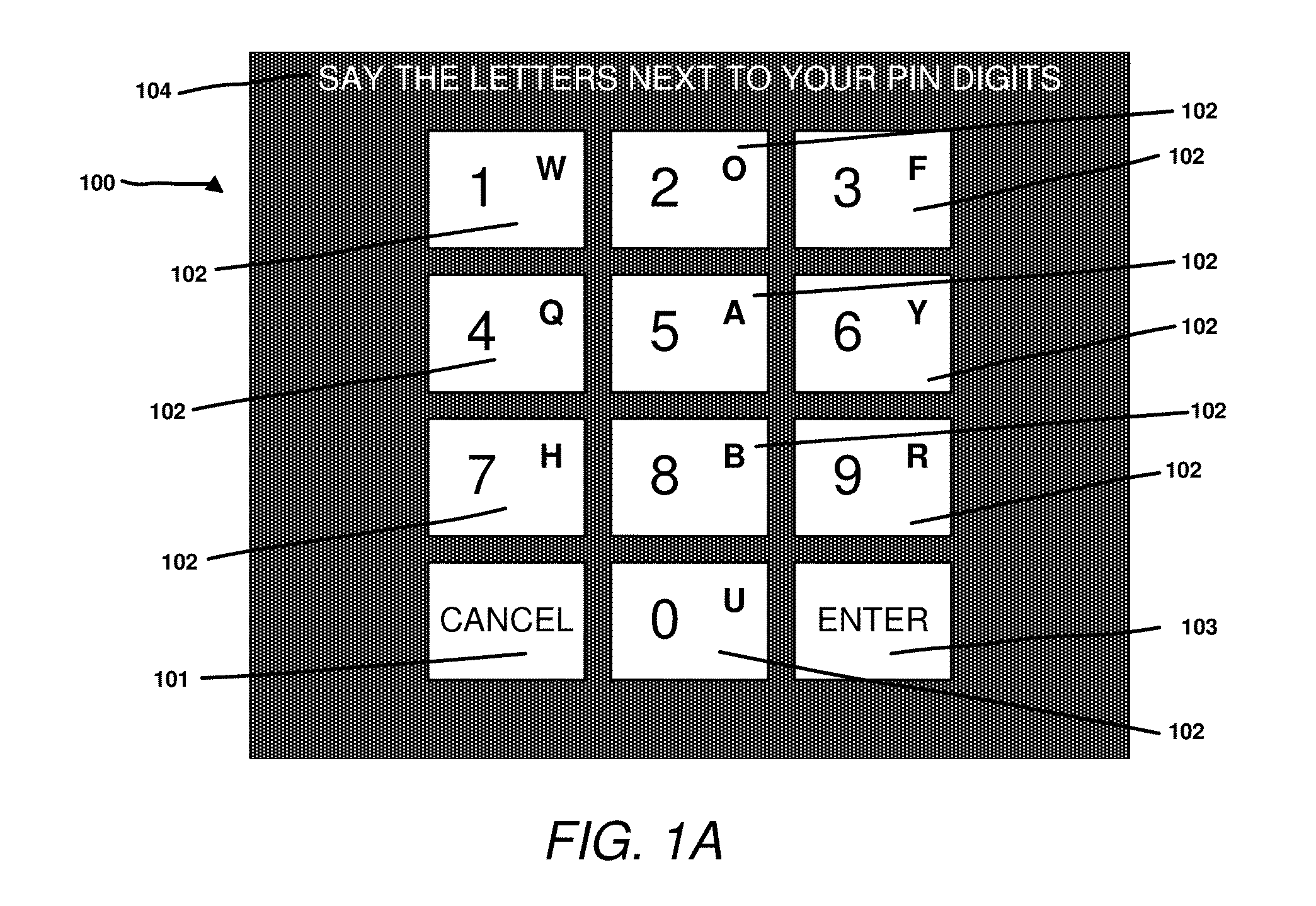
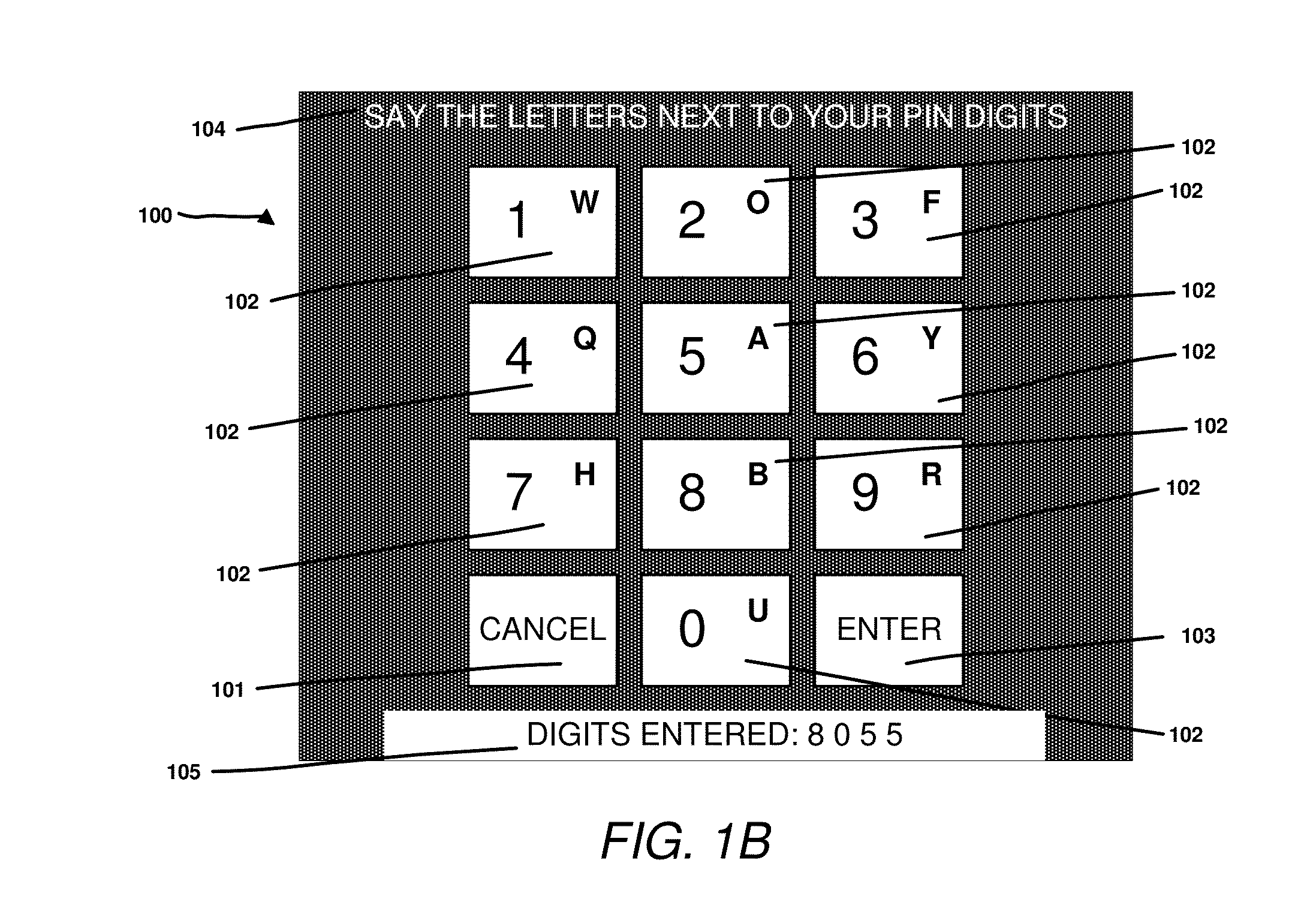
Secure entry of secrets
InactiveUS20150332038A1Acutation objectsDigital data processing detailsDisplay deviceSecondary Identifier
Disclosed is a method for enabling the input of a secret at an electronic device. The method includes establishing a plurality of primary identifiers and a plurality of secondary identifiers; associating each secondary identifier with a corresponding primary identifier by use of a mapping function; on a display configured such that it is only viewable by a single user displaying the plurality of primary identifiers and the plurality of secondary identifiers, with each secondary identifier being associated with a corresponding primary identifier; receiving one or more inputs from the user indicating a secondary identifier, translating each input secondary identifier using the mapping function to its corresponding primary identifier to generate one or more primary identifiers and using the generated primary identifiers as an input to an authentication function where the authentication function allows access to private data or functionality associated with an electronic device.
Owner:LYONS ADRIANA
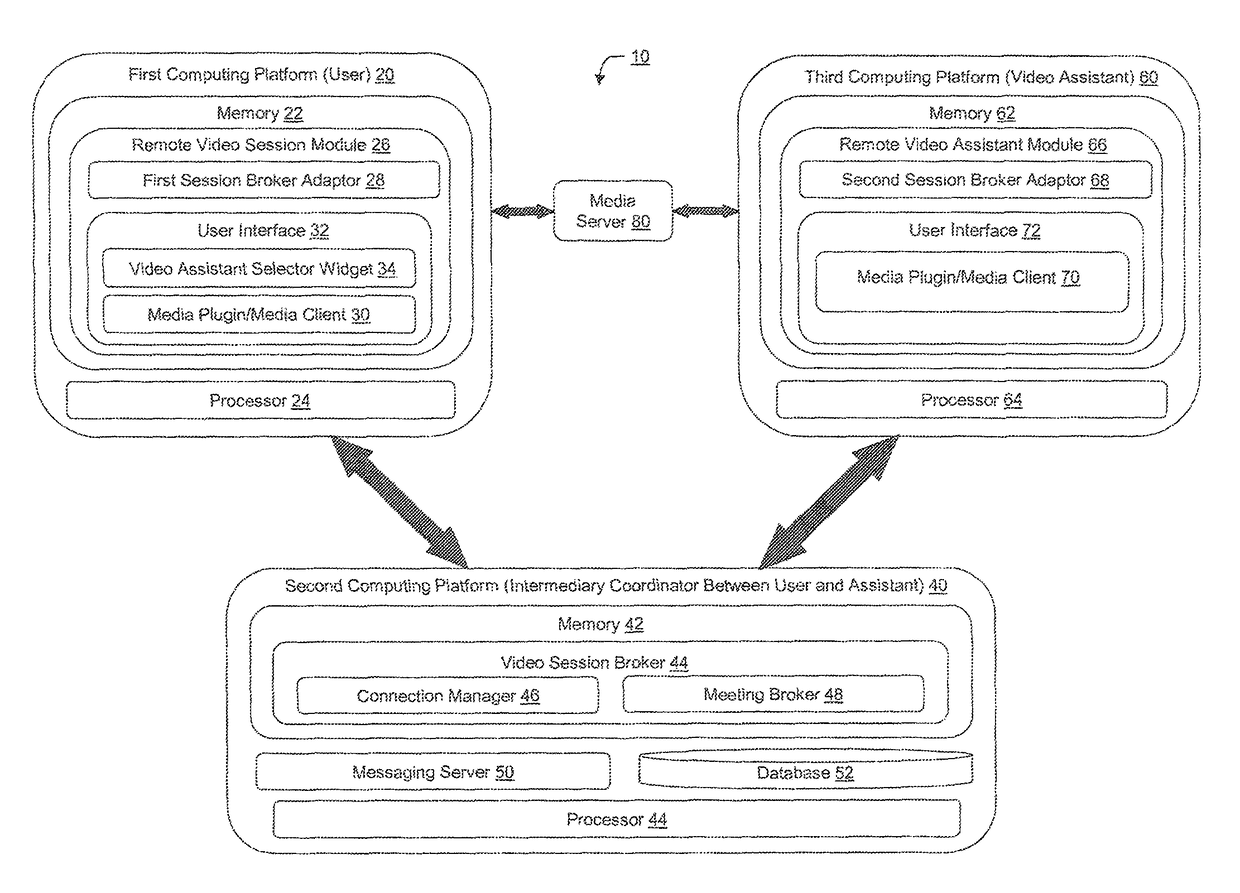
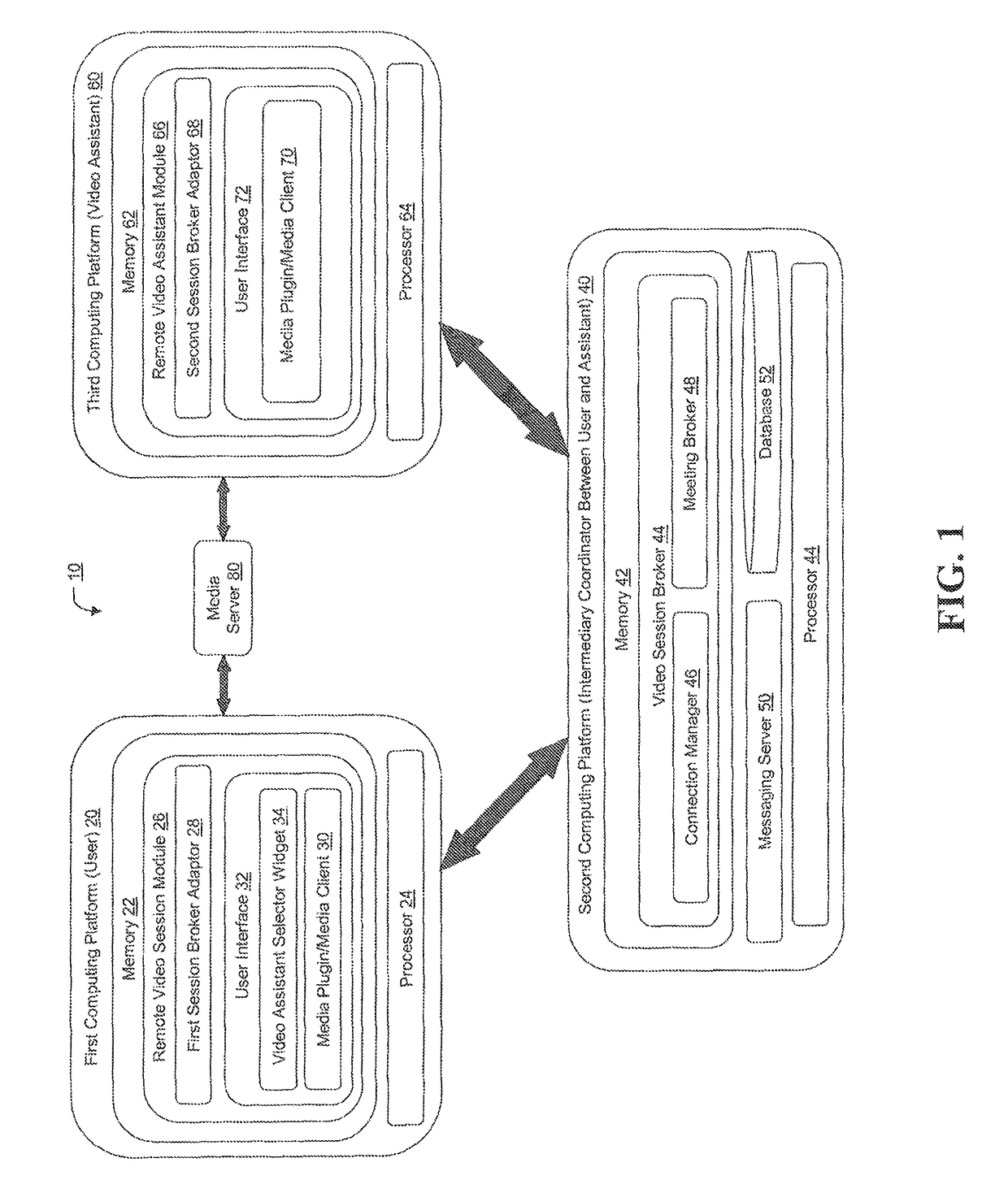
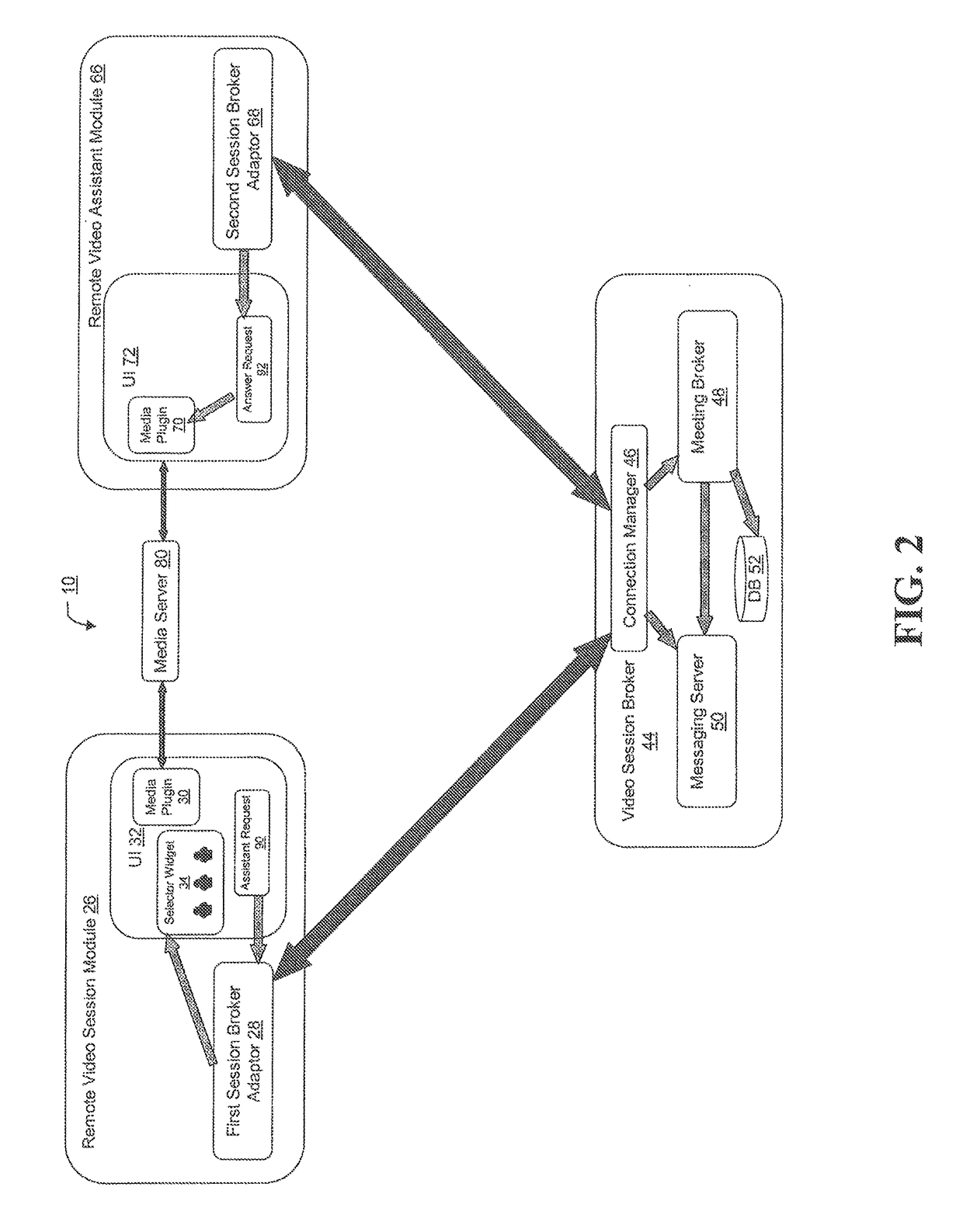
Personalized presentation of performance ratings of remote video assistant during remote video assistant selection
The present invention relates to capturing and presenting, in conjunction with video assistant selection, personalized, user-specific performance ratings for video assistants that the user has transacted / interacted with in the past. Once a user logs in or otherwise presents identifying credentials, the system or methodology accesses the user's recent remote video assistant session data (i.e., which video assistants the user previously transacted with and at least one corresponding user-specific performance rating) and presents a listing of the video assistants which the user previously interacted with along with at least one user-specific performance rating for each remote video assistant. By providing for display of the user-specific performance rating along with the video assistant identifier, the user is aware of not only which video assistants they conducted transactions / interactions with in the past, but also how the remote video assistant performed for the user during the previous transactions / interactions.
Owner:BANK OF AMERICA CORP
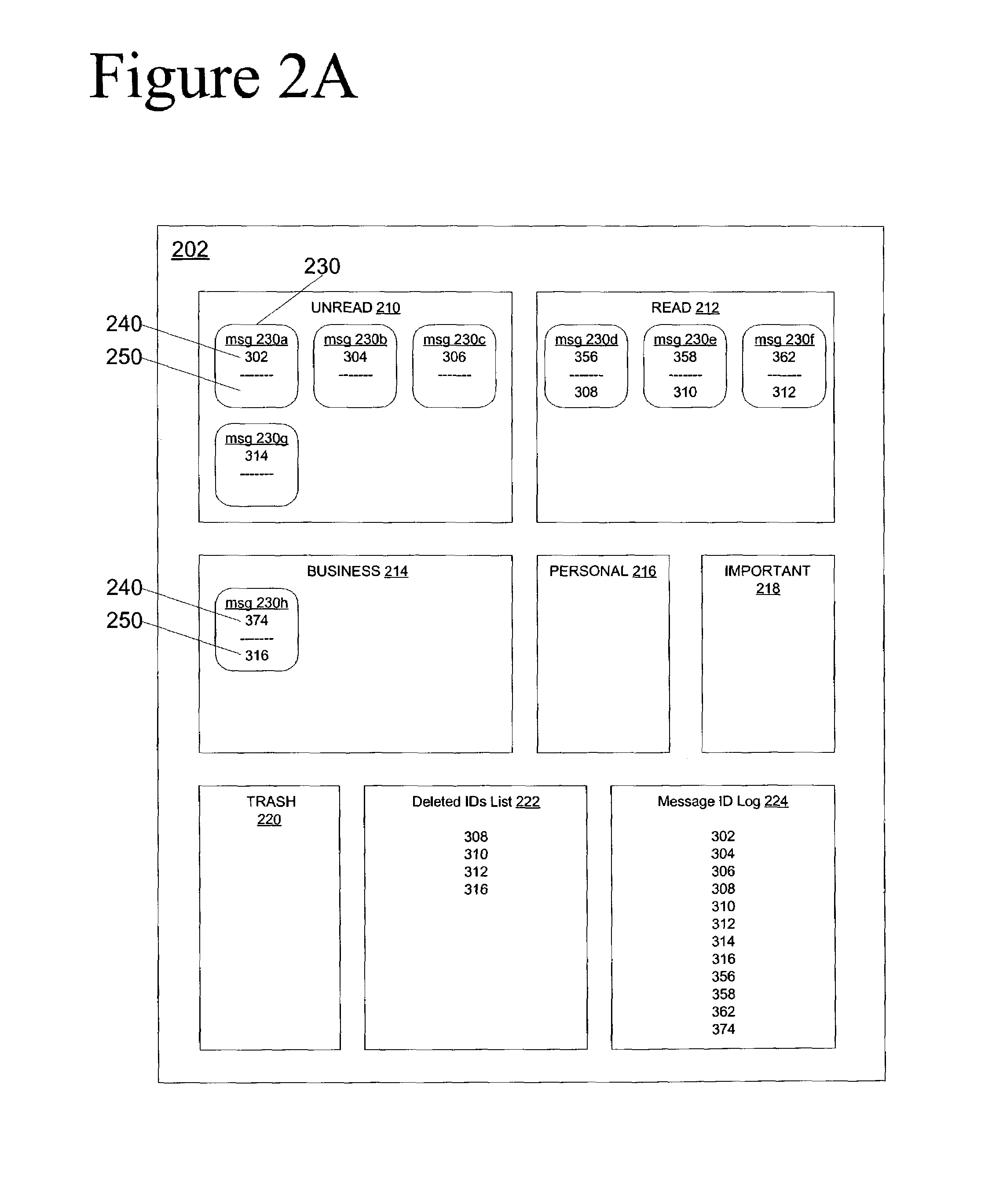
Mail system synchronization using multiple message identifiers
InactiveUS7107314B2Data processing applicationsMultiplex communicationComputer hardwareSystem maintenance
An electronic mail system includes multiple devices, on each of which a user may have an electronic mailbox. The electronic mailboxes can be synchronized, so that actions taken on one device are reflected on other devices. Each mail message is assigned a unique message identifier. When the message is read or moved from one folder to another folder, it is assigned a new message identifier. The system maintains a list of subsidiary identifiers for each message, which identifies the prior message identifiers for the message. The system identifies message identifiers that have been added since the last synchronization. During synchronization, by examining messages having a current or prior message identifier that is found in the list of subsidiary identifiers for a message having a new message identifier, the system is able to synchronize the mailboxes on the devices. Following synchronization, each synchronized device will have the same messages in the same folders, with the same message identifiers, and duplicates caused by taking the same action on two different devices are removed.
Owner:RED HAT
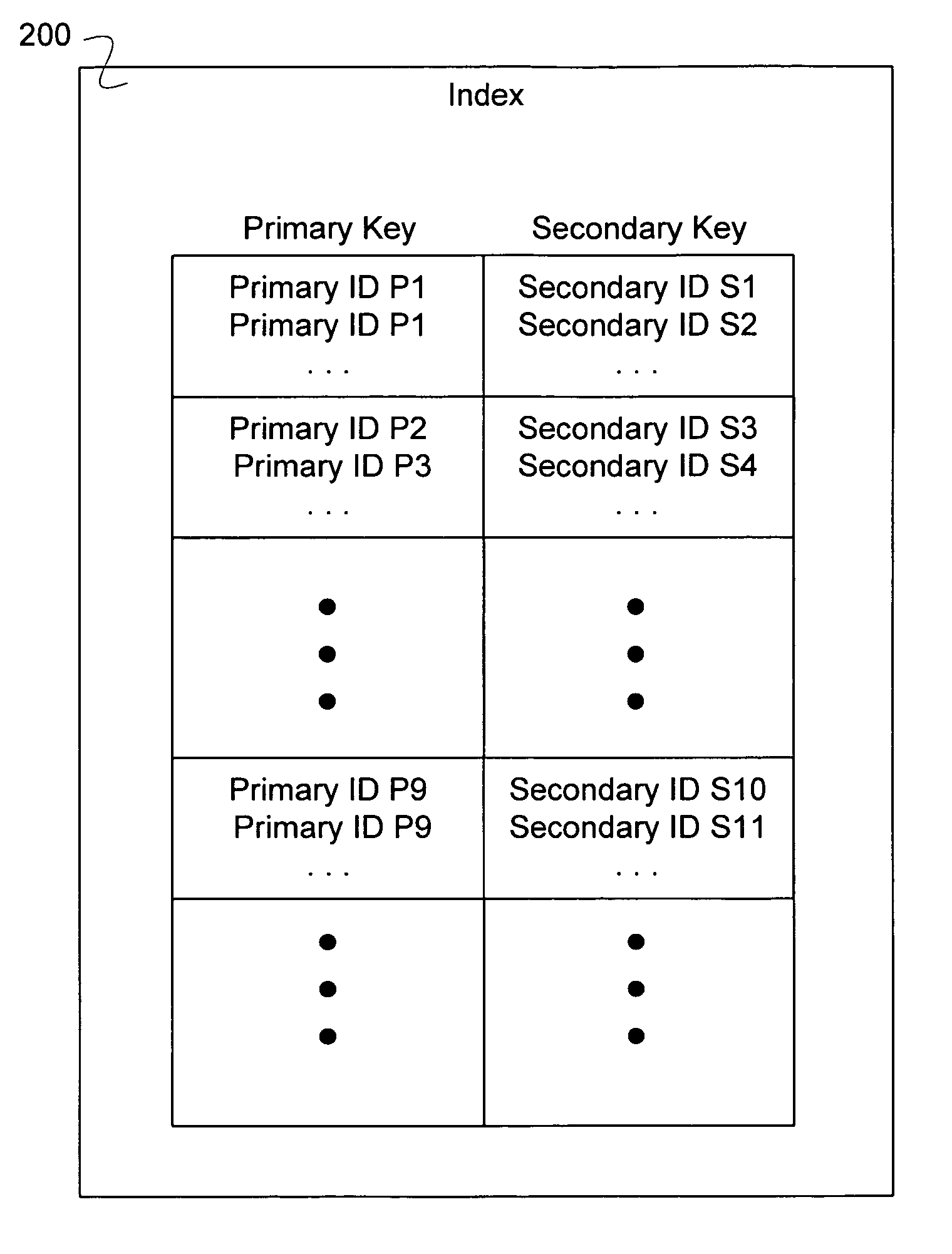
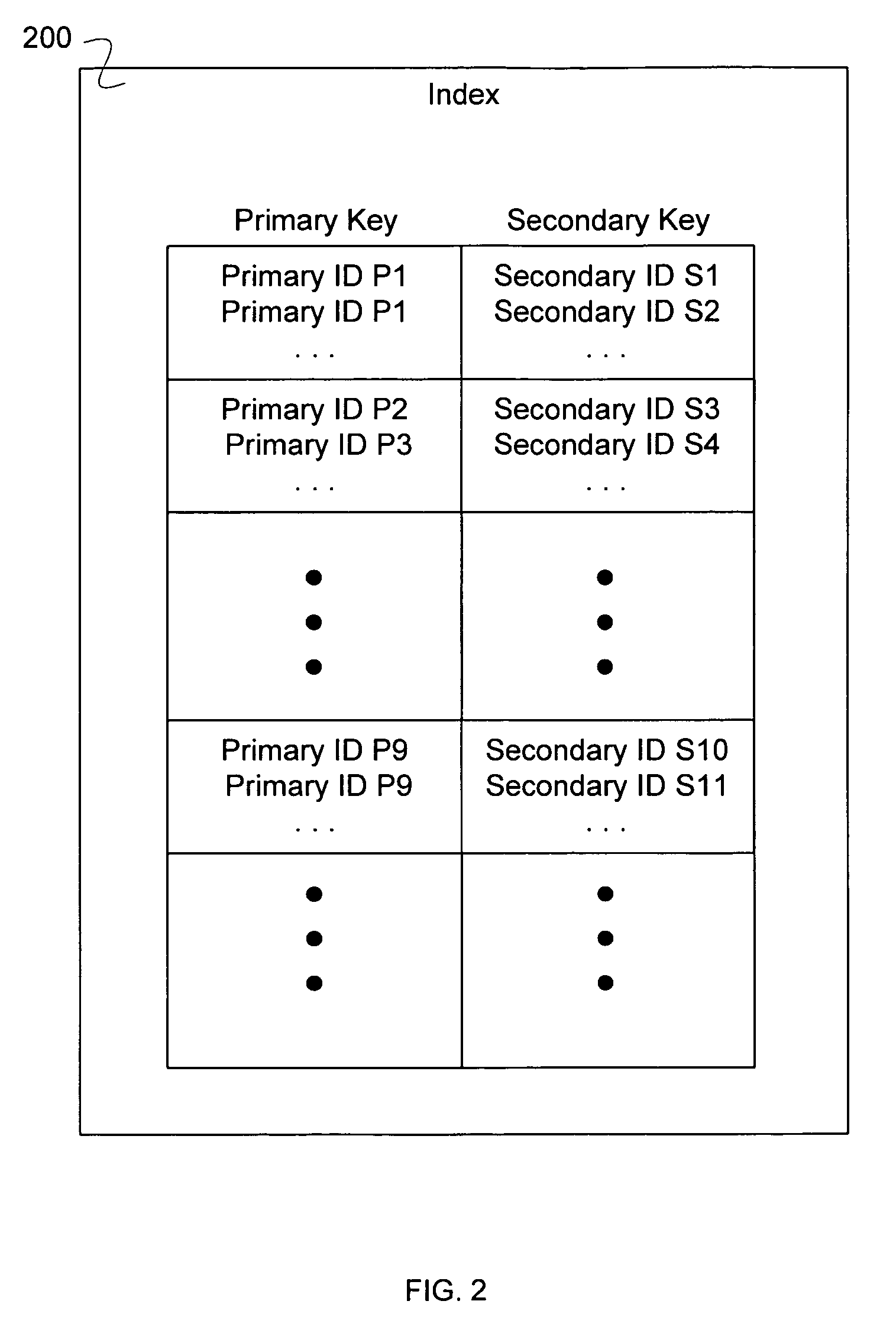
Tolerating and reporting collisions in content-derived identifiers of data segments using secondary identifiers
ActiveUS7870103B1Digital data information retrievalDigital data processing detailsData segmentUser identifier
A method for tolerating collisions of identifiers for data segments is disclosed. The method comprises combining a primary identifier and secondary identifier of a first segment to make a combined identifier of the first segment and combining a primary identifier and secondary identifier of a second segment to make a combined identifier of the second segment. The method further comprises determining if the combined identifier of the first segment is the same as the combined identifier of the second segment.
Owner:EMC IP HLDG CO LLC
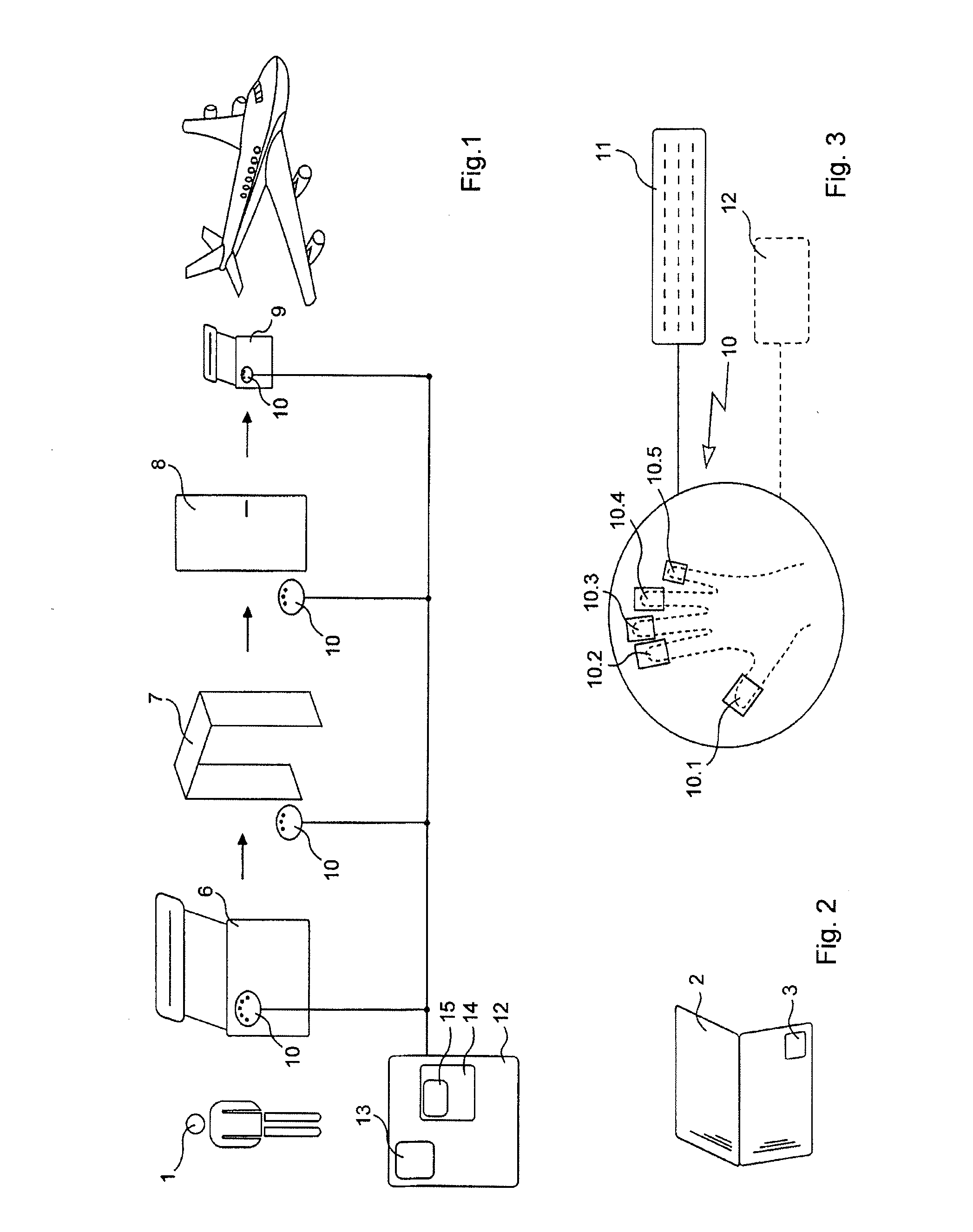
System and method of aircraft surveillance and tracking
ActiveUS20180027382A1Minimize information exchangedThe calculation process is simpleNetwork topologiesBroadcast service distributionData storingComputer science
Described are systems and methods of aircraft surveillance and tracking. A method for aircraft tracking includes partitioning an airspace region into multiple sectors and generating multiple data structures corresponding respectively to each of the multiple sectors. Each data structure has a primary identifier and at least one secondary identifier that matches the primary identifier corresponding to the at least one other sector. The method includes receiving at least one data packet from an aircraft located within one of the multiple sectors, storing the aircraft data from the data packet within the data structure corresponding to the one of the sectors, storing the aircraft data within each of the data structures that has a secondary identifier matching the primary identifier, and for each of the multiple sectors, sending each aircraft within the sector aircraft data stored within the data structure corresponding to the sector.
Owner:THE BOEING CO
Medical manager
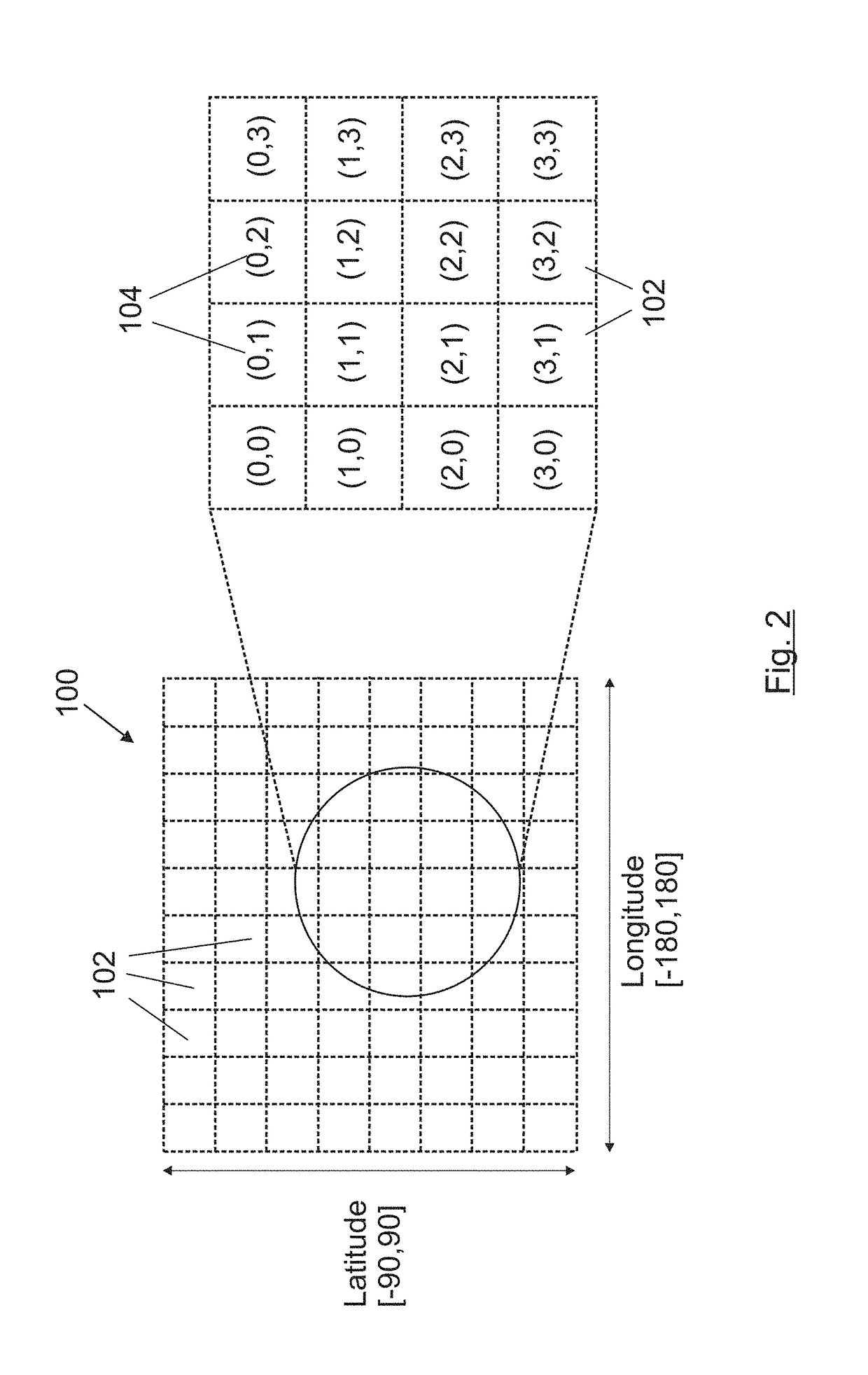
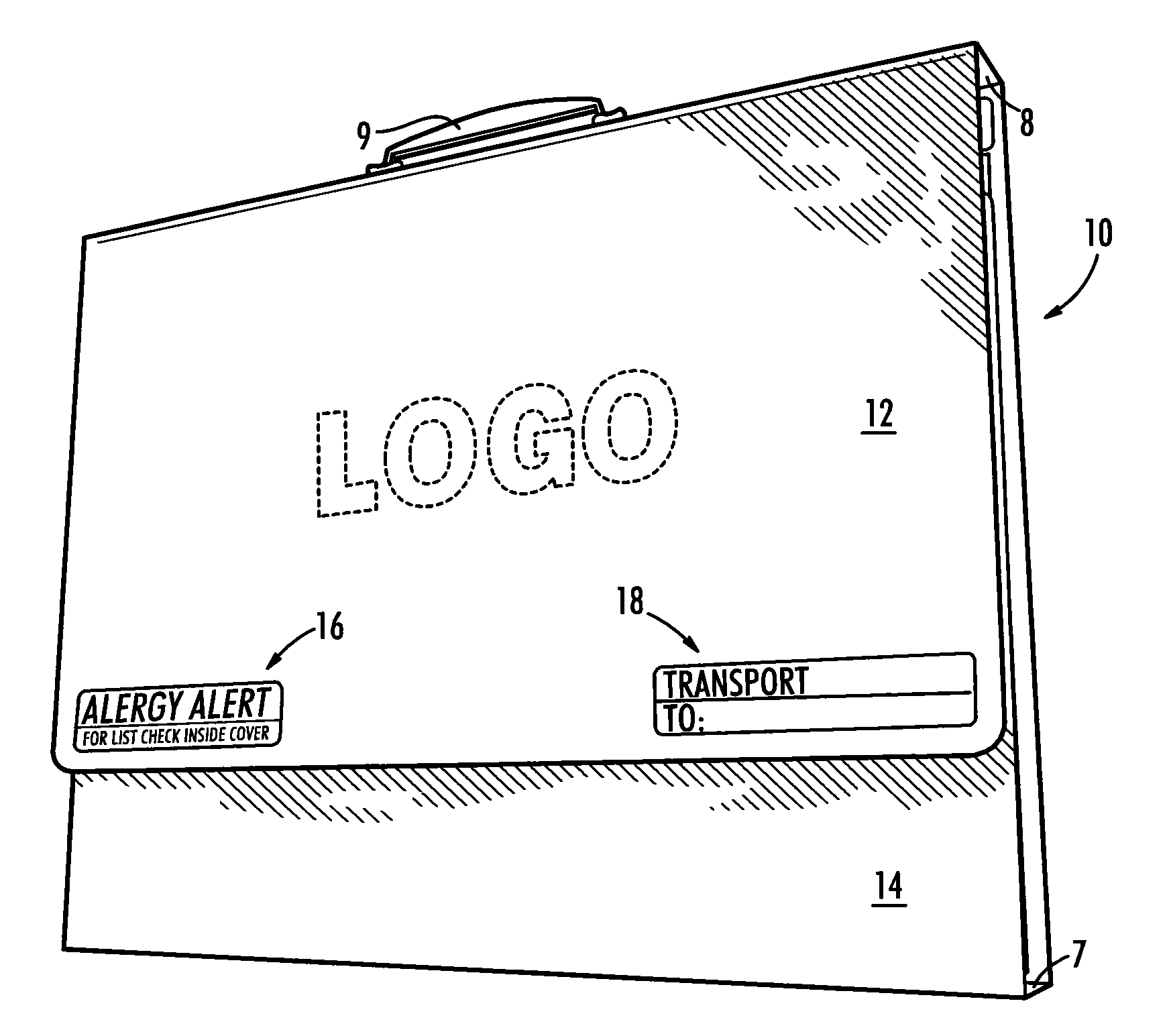
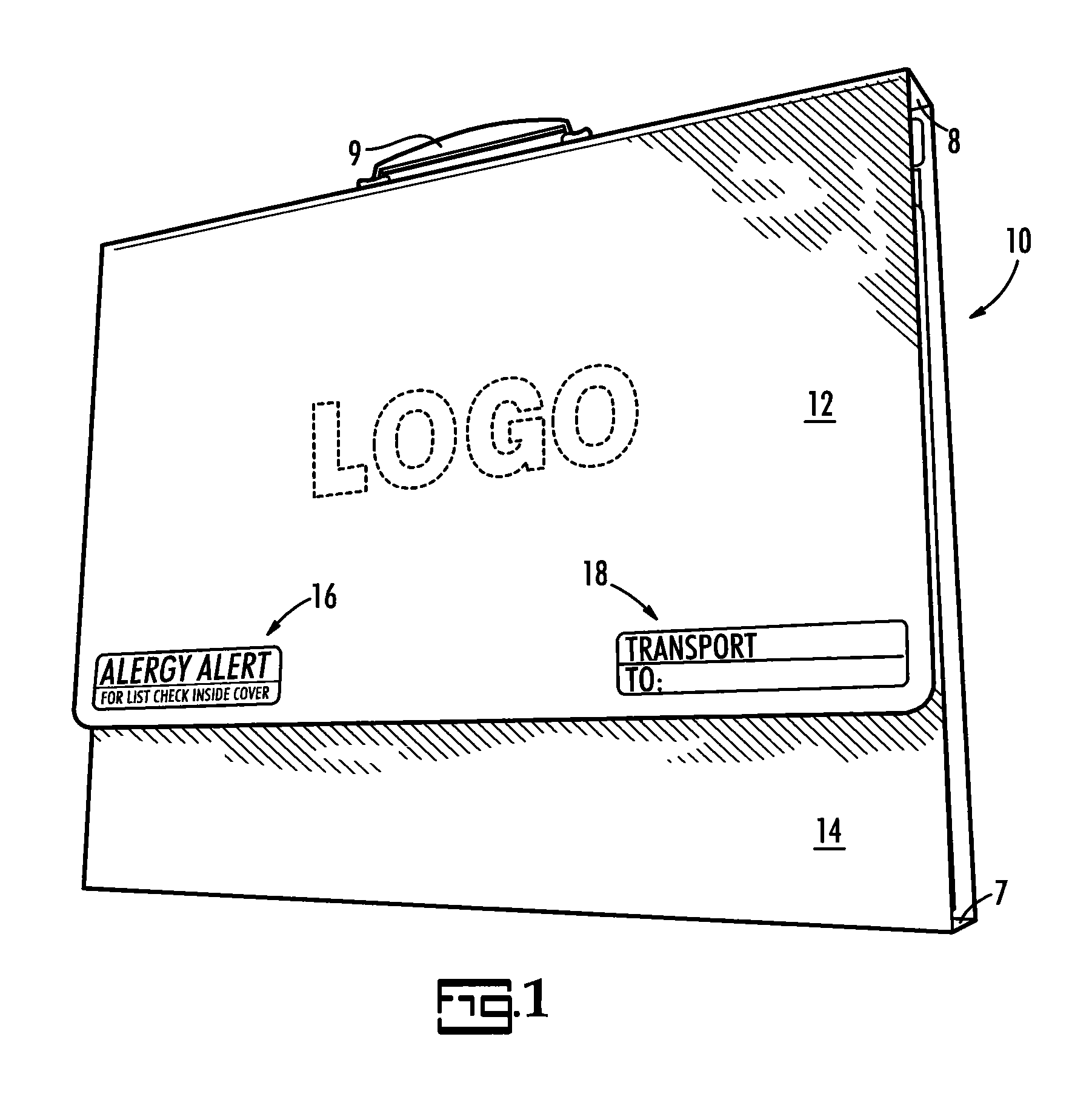
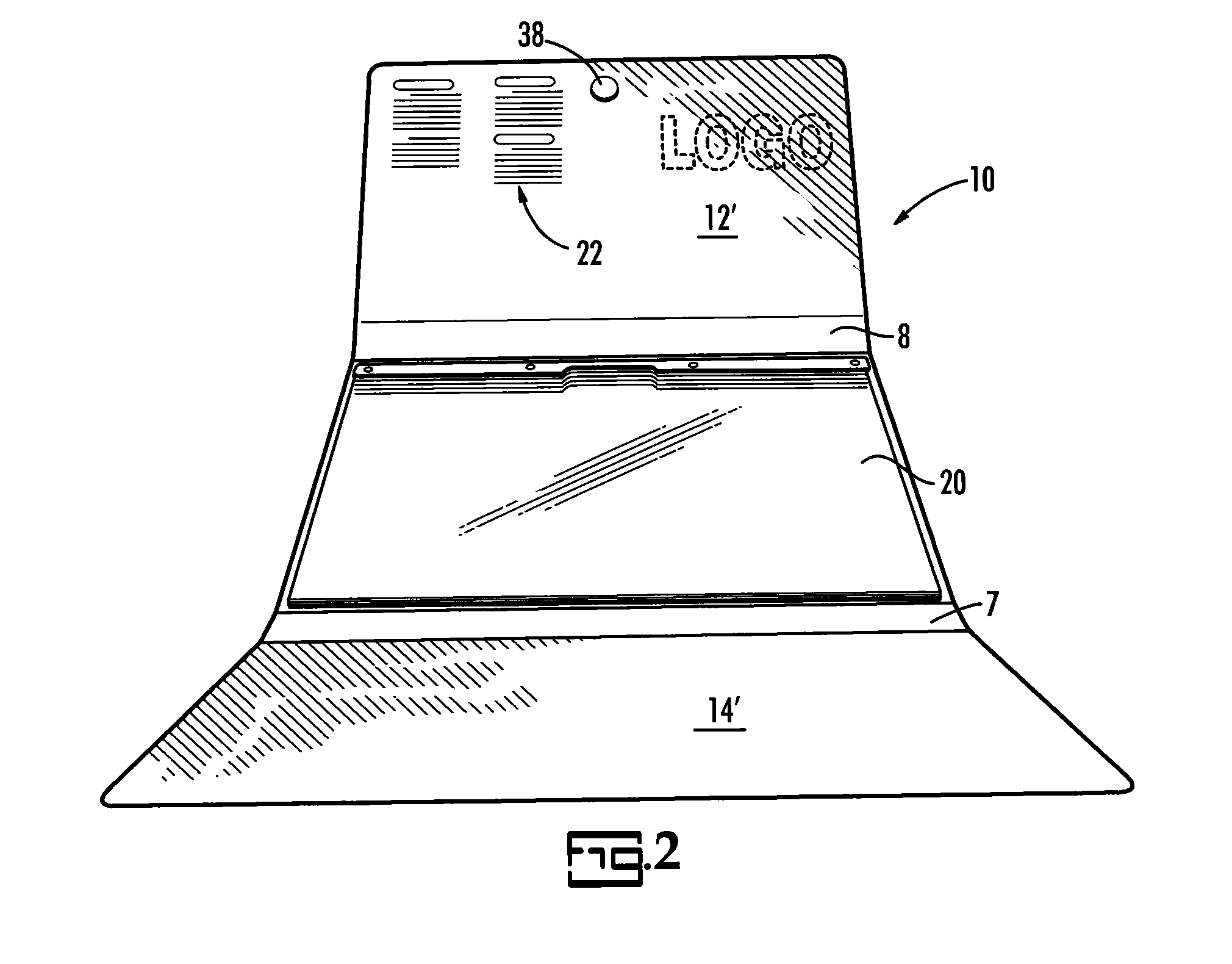
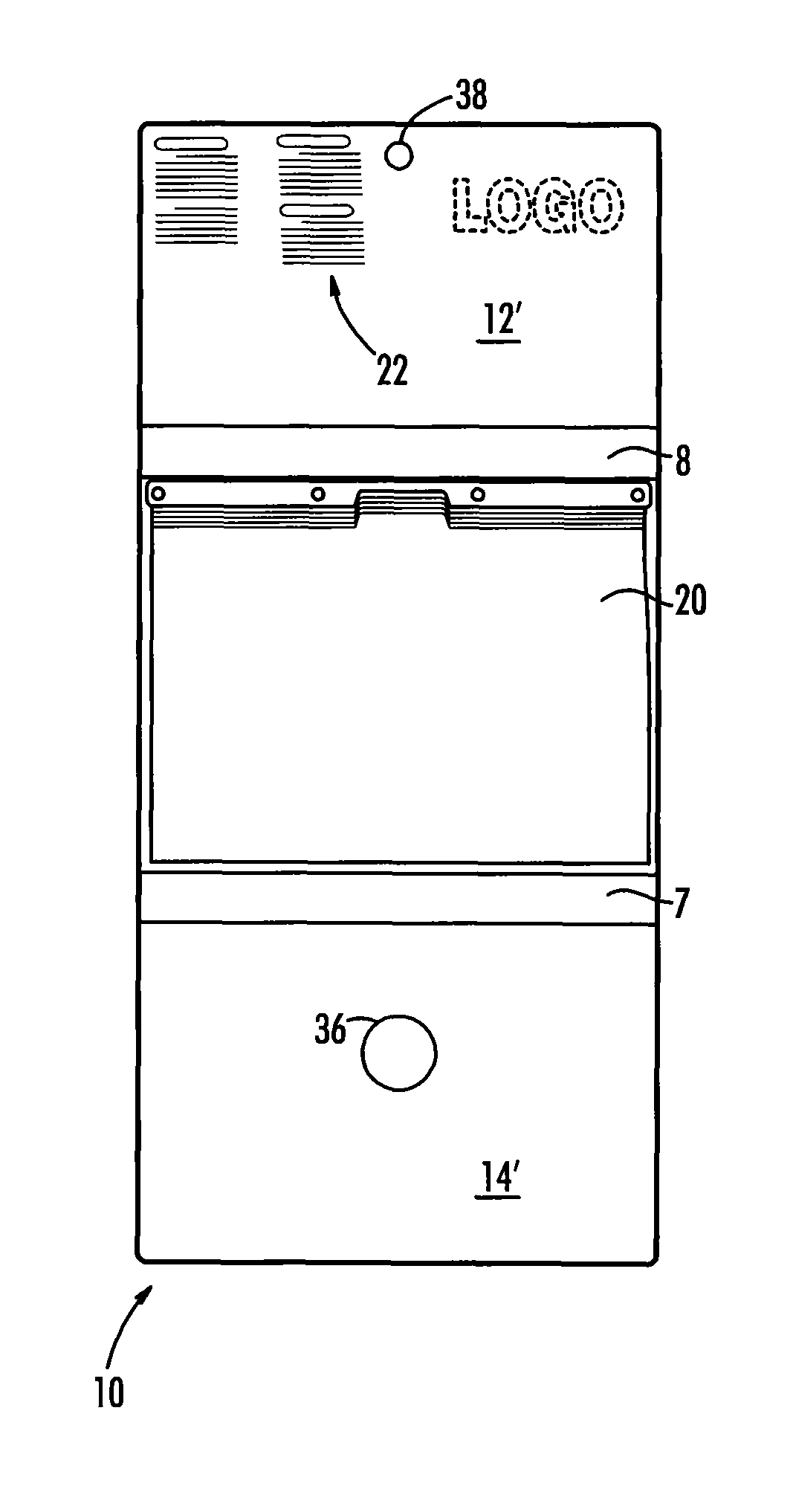
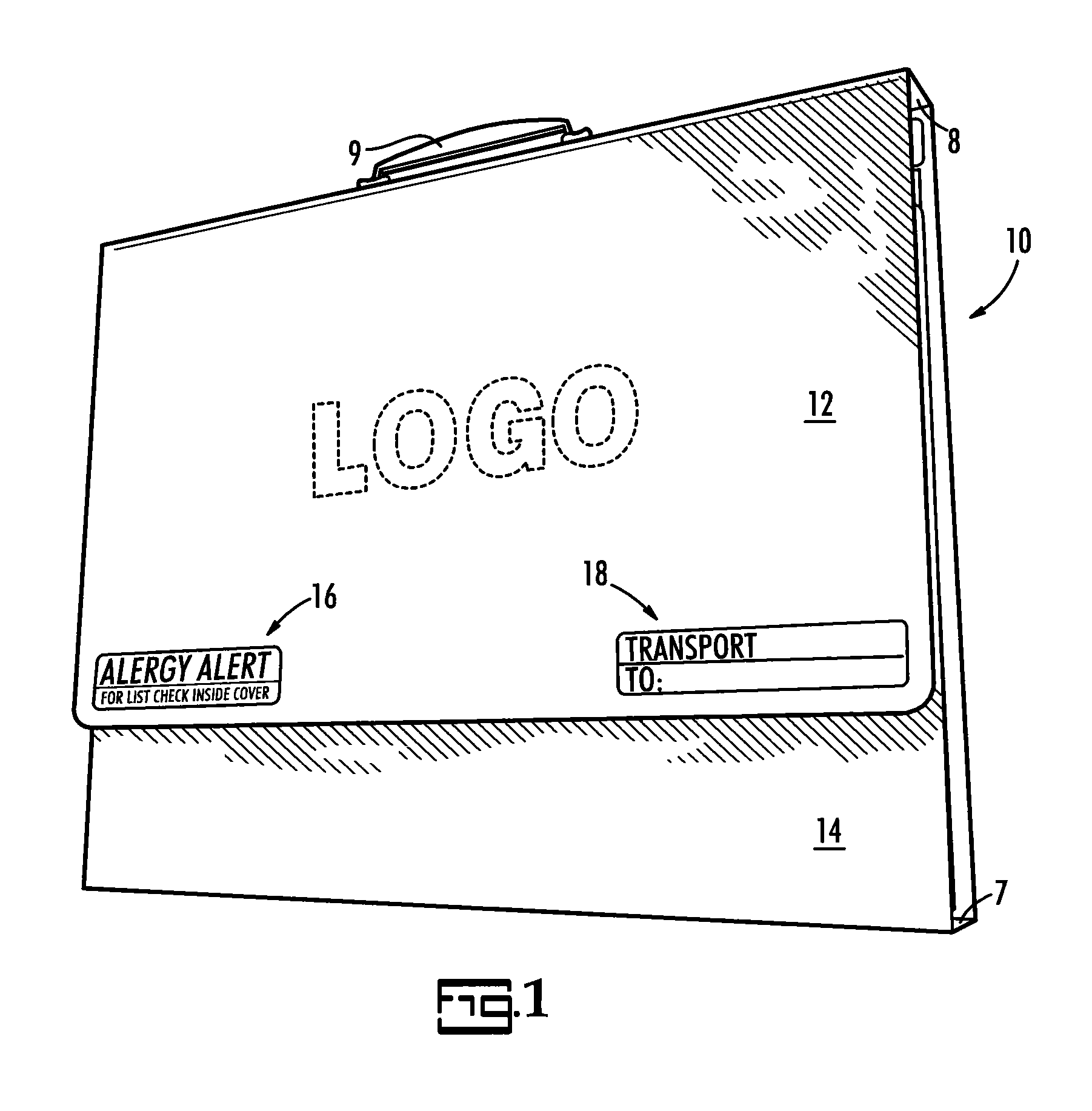
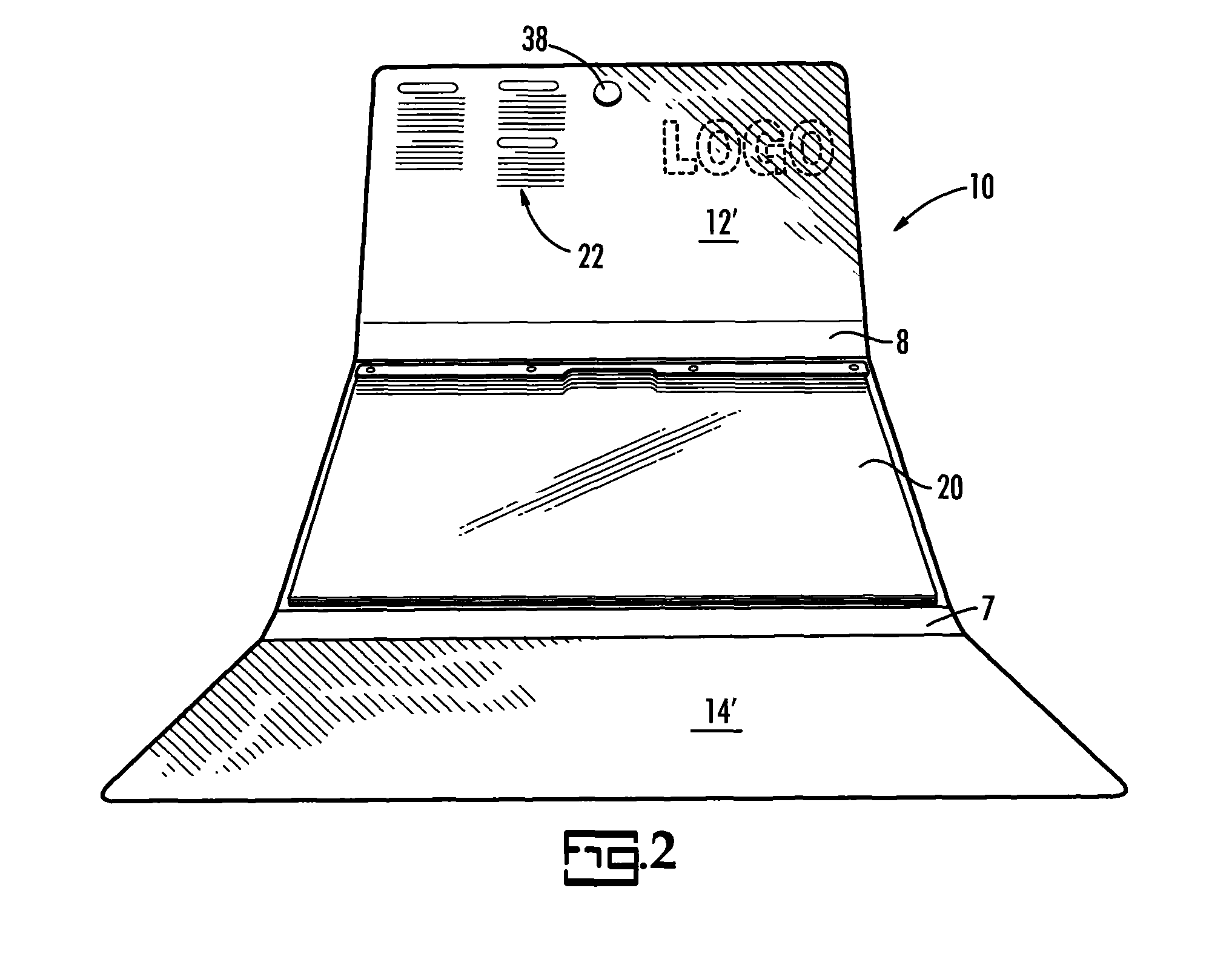
A system for alerting medical emergency personnel to a medical history of a patient. The system has a primary identifier suitable for attachment near an entrance to a building. The primary identifier has an indicia noting that a tri-fold portfolio is present. A secondary identifier is provided suitable for placement in the building wherein the secondary identifier has the indicia and a location of the tri-fold portfolio. The tri-fold portfolio has an outer portion with a top front cover and a bottom front cover with a back hingedly attached there between. Cascading file folders are attached to an interior of the back wherein when the top front cover and the bottom front cover are folded the cascading file folders are covered.
Owner:GOSLEE JANET M
Medical manager
A system for alerting medical emergency personnel to a medical history of a patient. The system has a primary identifier suitable for attachment near an entrance to a building. The primary identifier has an indicia noting that a tri-fold portfolio is present. A secondary identifier is provided suitable for placement in the building wherein the secondary identifier has the indicia and a location of the tri-fold portfolio. The tri-fold portfolio has an outer portion with a top front cover and a bottom front cover with a back hingedly attached there between. Cascading file folders are attached to an interior of the back wherein when the top front cover and the bottom front cover are folded the cascading file folders are covered.
Owner:GOSLEE JANET M
Procede d'identification biometrique
ActiveUS20160125179A1Reliability of the identificationLow implementation costProgramme controlElectric signal transmission systemsUser identifierComputer science
The invention relates to a method for identifying a person to be identified having a certified data medium linking a primary identifier and a primary biometric characteristic of a holder of the data medium, acquiring, during a unique operation, the first biometric characteristic on the person to be identified and a second, distinct biometric characteristic, verifying that the person to be identified corresponds to the holder of the data medium by comparing the first acquired biometric characteristic to that of the data medium, storing the second acquired biometric characteristic and associating it with a secondary identifier and during a subsequent identification, acquiring the second biometric characteristic on the person to be identified and comparing it to the second biometric characteristic.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
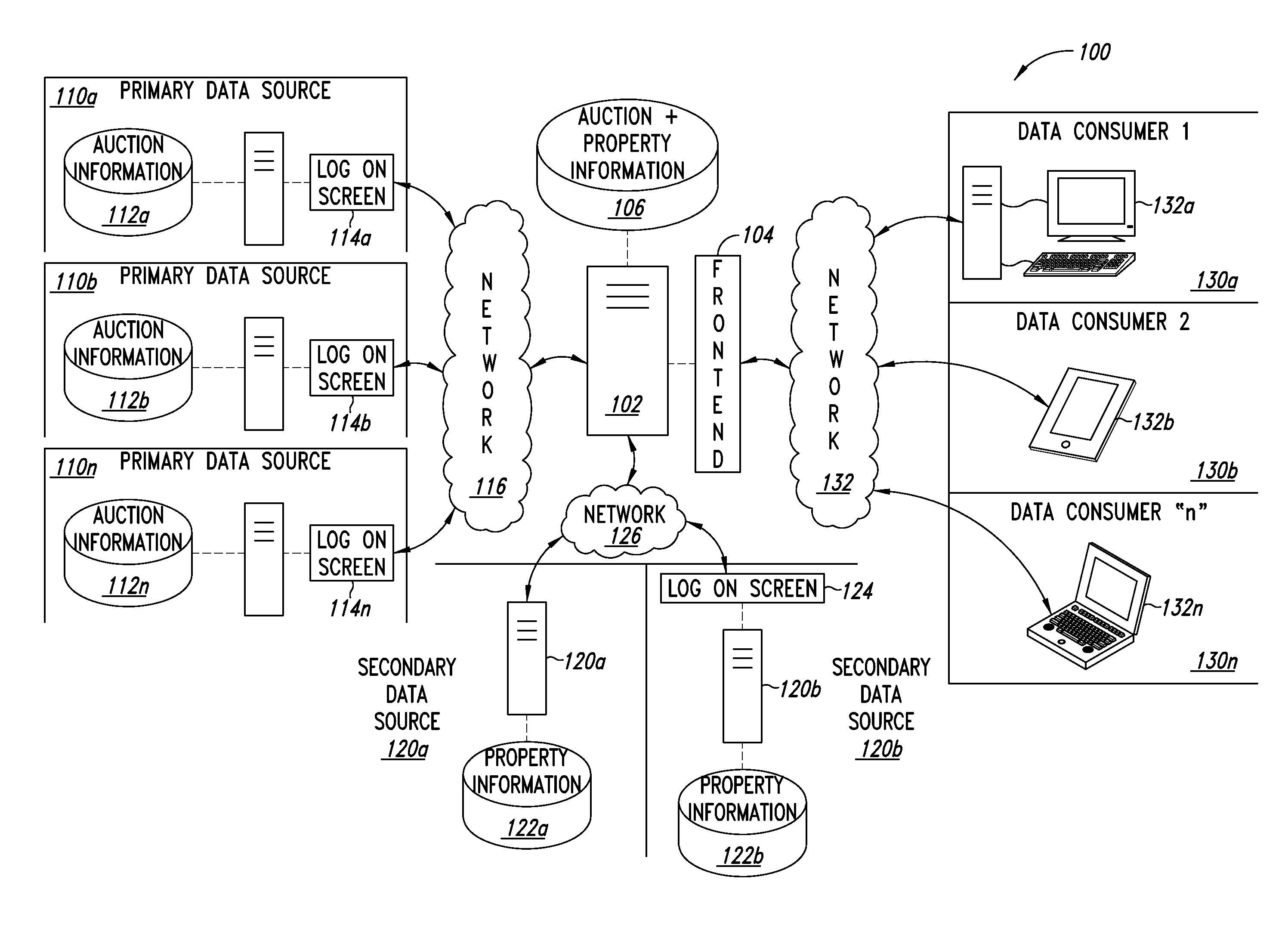
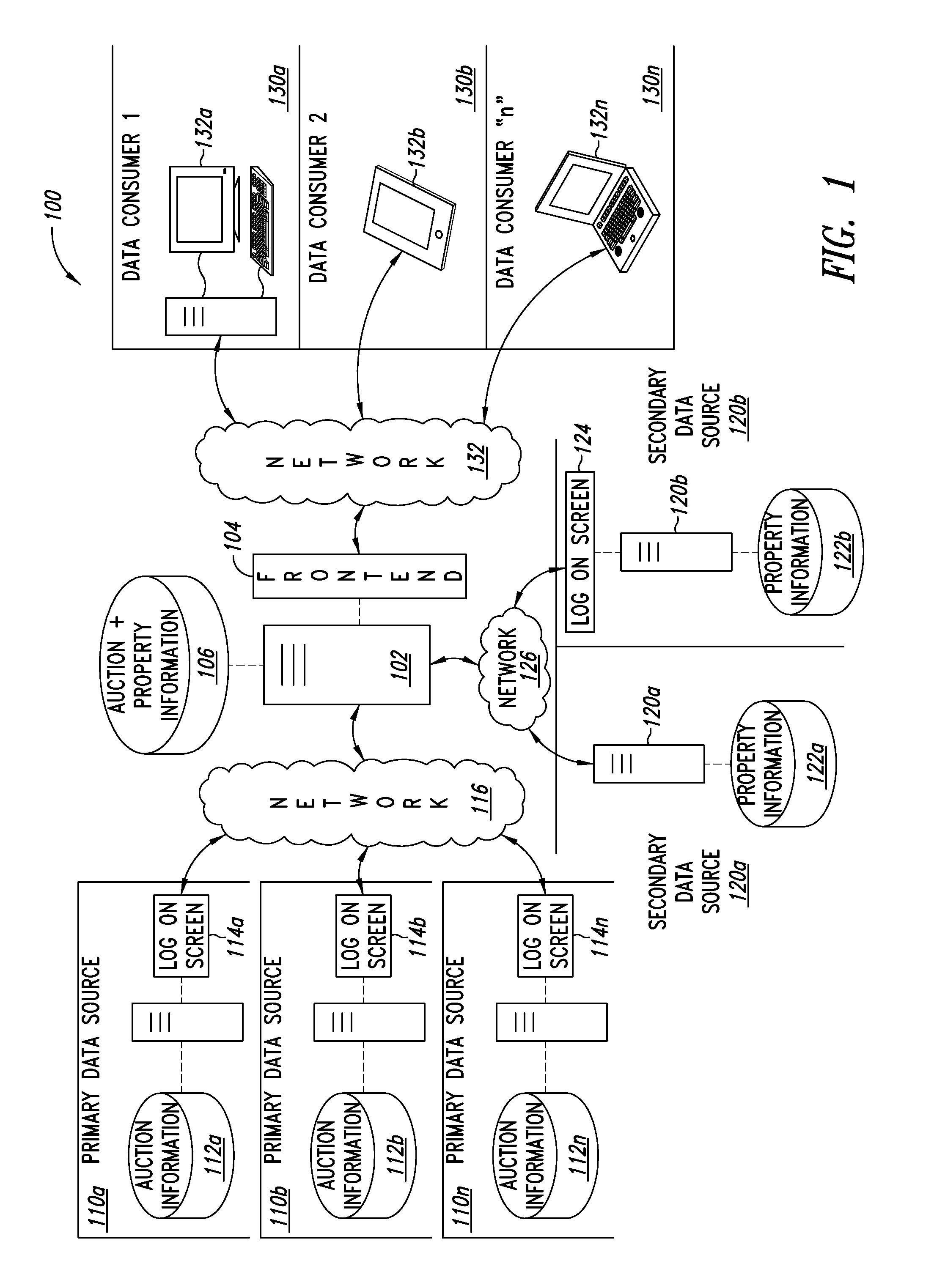
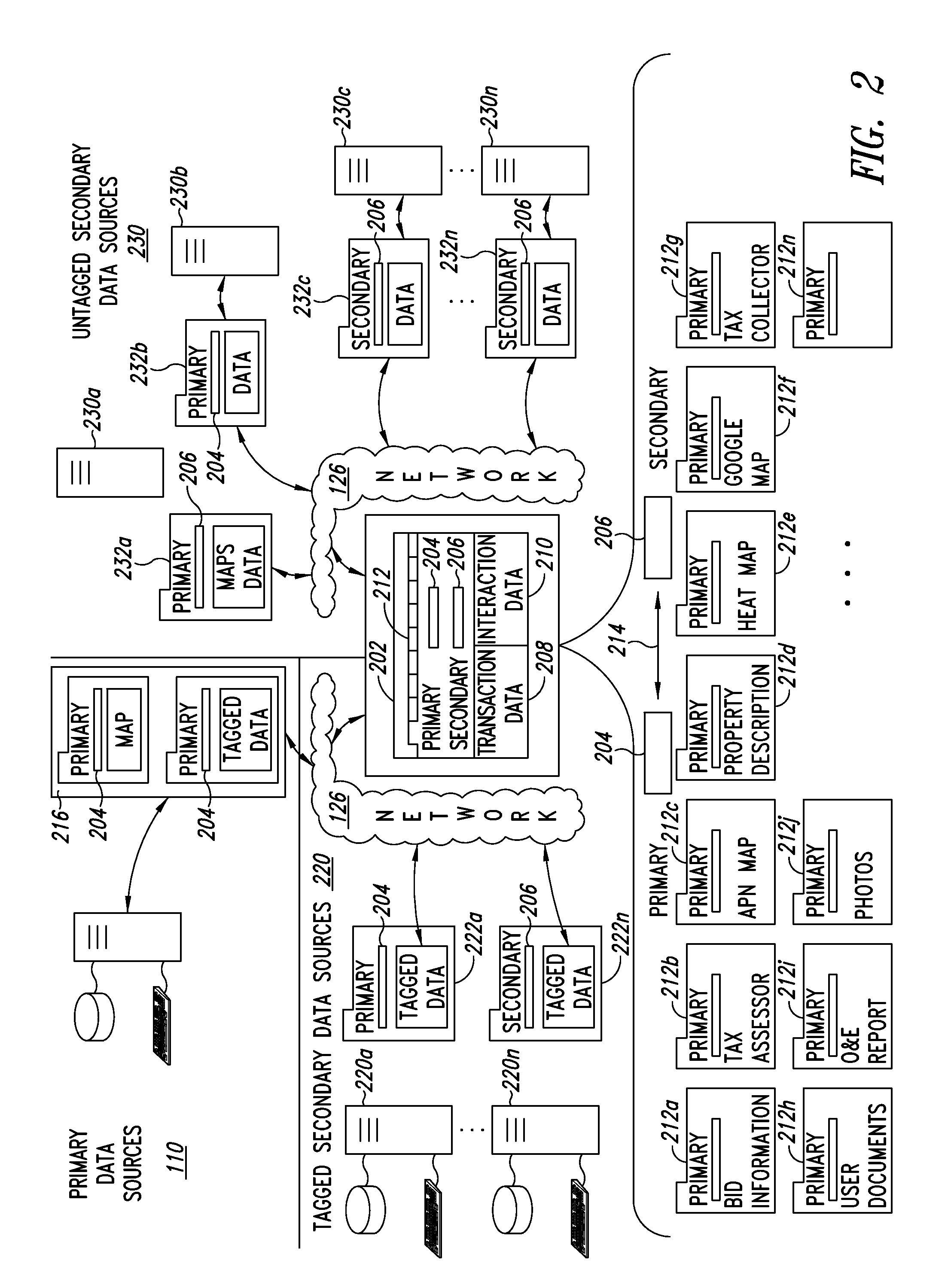
Parcel data collection and analysis systems, devices, and methods
Distressed real property is offered for sale at real property parcel auction events. Such distressed real property presents an investment opportunity. The parcels available at real property parcel auction events are often identified using a primary identifier assigned by a taxation authority or municipal utility. Such identifiers can be autonomously retrieve, collect, and analyze primary parcel specific information. One or more secondary identifiers such as a street address may be autonomously extracted from the primary parcel specific information. Using the one or more secondary identifiers, secondary parcel specific information may be obtained. The retrieved primary and secondary parcel specific information is collected, organized, and analyzed by the parcel data collection and analysis system. The parcel data collection and analysis system then presents the collected, organized and analyzed primary and secondary parcel specific information in tabbed or tabular user interface formats.
Owner:X STREAM INFO
Using a secondary identifier to select a data set
Systems and methods are configured to manage data sets associated with multiple transaction devices. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction devices user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts from multiple transaction devices.
Owner:LIBERTY PEAK VENTURES LLC
On-line repairing work processing method of cell
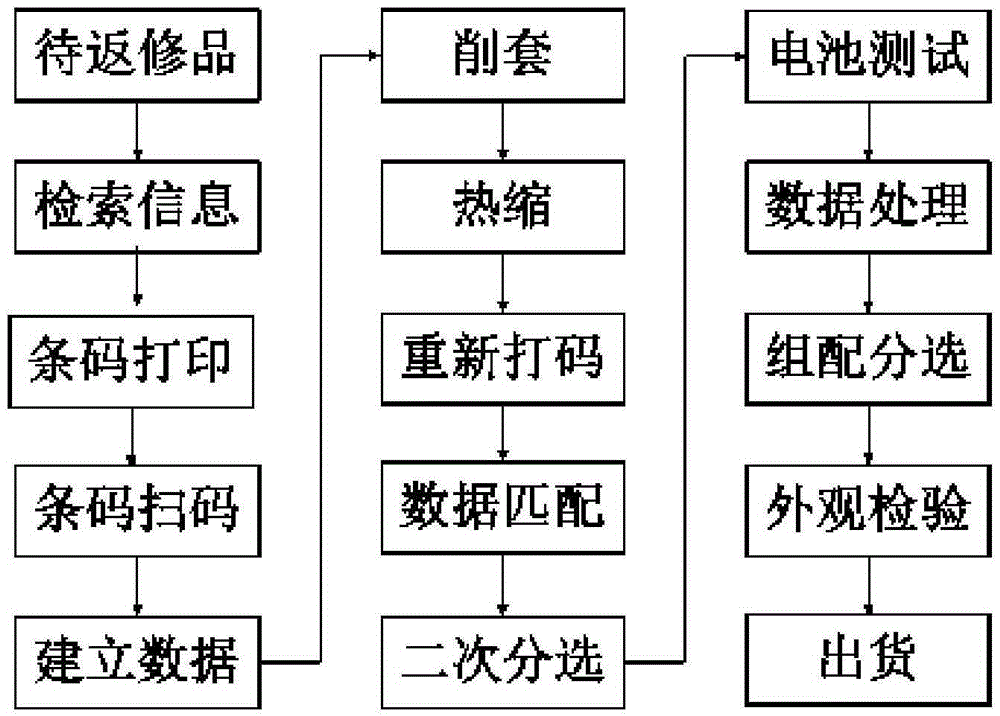
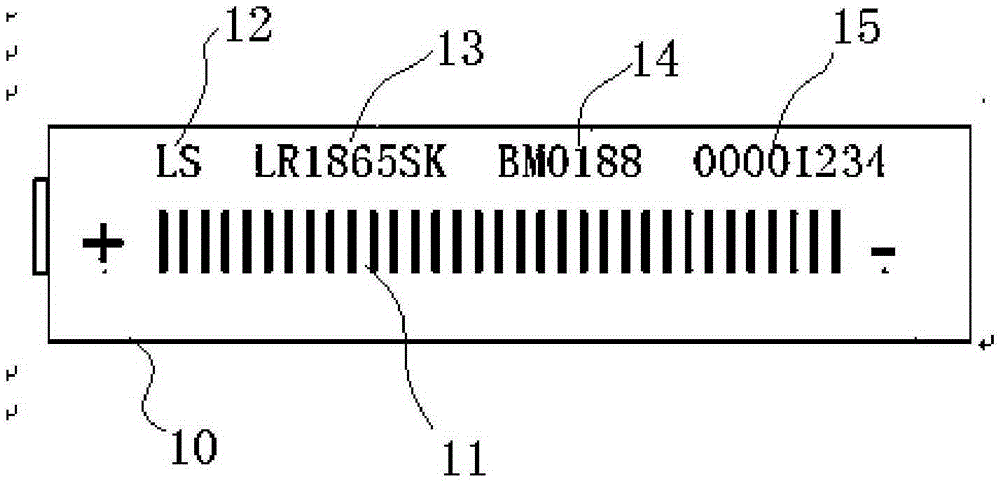
InactiveCN105335787AConvenience for combined queriesEnsure one-to-one correspondenceInstrumentsManufacturing cost reductionCell based
The invention relates to an on-line repairing work processing method of a cell. The method comprises: information of a to-be-repaired cell is retrieved, an original bar code is printed for the to-be-repaired cell and is scanned into a database, and a correspondence relation with the to-be-repaired cell information is established; sleeve peeling and thermal shrinkage are carried out on the to-be-repaired cell according to a new processing batch, a cell printing batch number is established again and corresponding and continuous bar code information in a descending order is printed and is inputted into the database, a secondary identifier is generated at a corresponding position in initial inputting information of the to-be-repaired cell in the database according to the one-to-one correspondence relation, so that the same cell has original process data and after-repairing data; and secondary sorting and cell testing are carried out on the cell needing repairing, and then assembling and sorting are carried out on the cell based on the original process data and the after-repairing data. With the method, the yield can be substantially improved and the manufacturing cost can be lowered.
Owner:TIANJIN LISHEN BATTERY
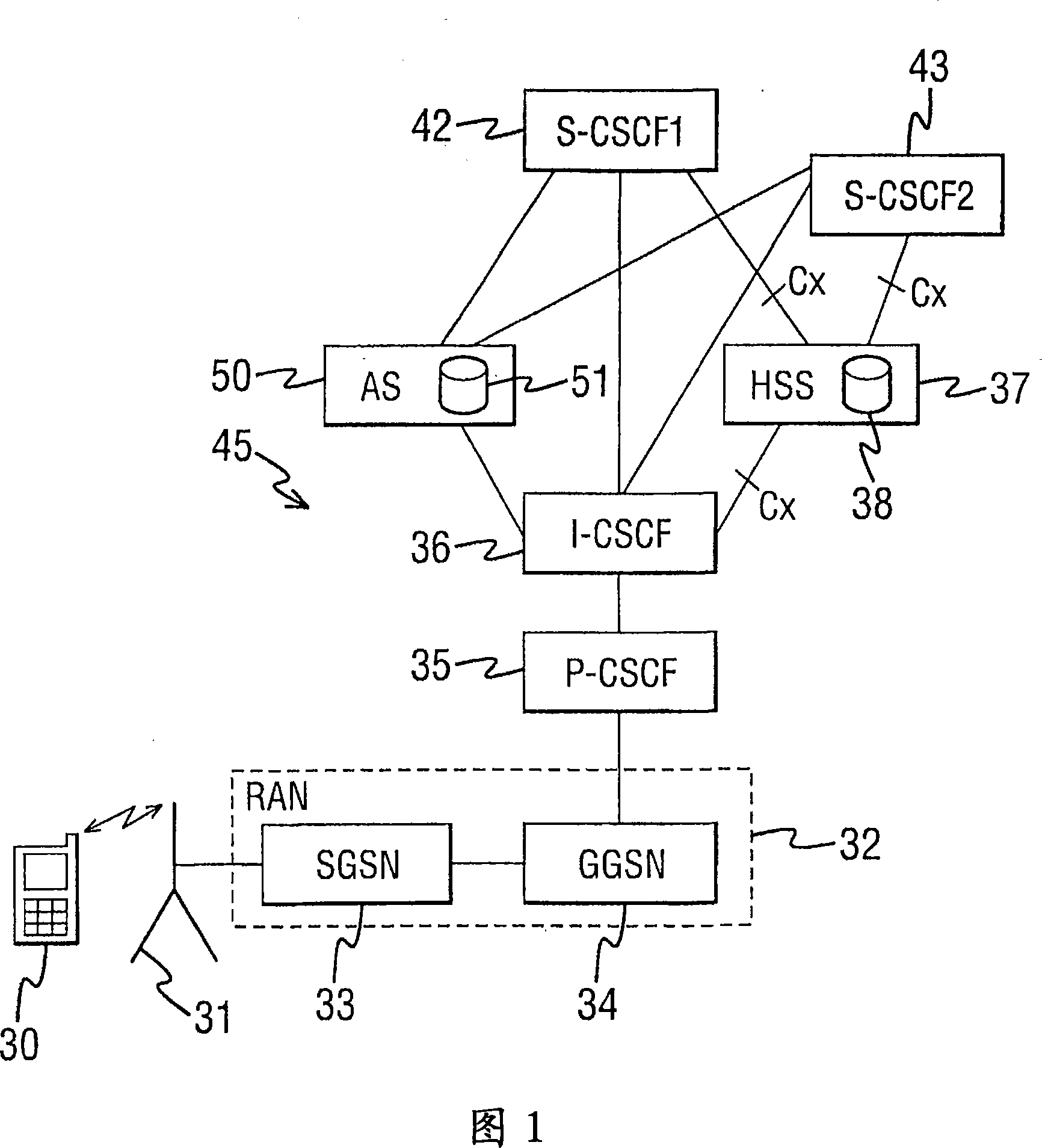
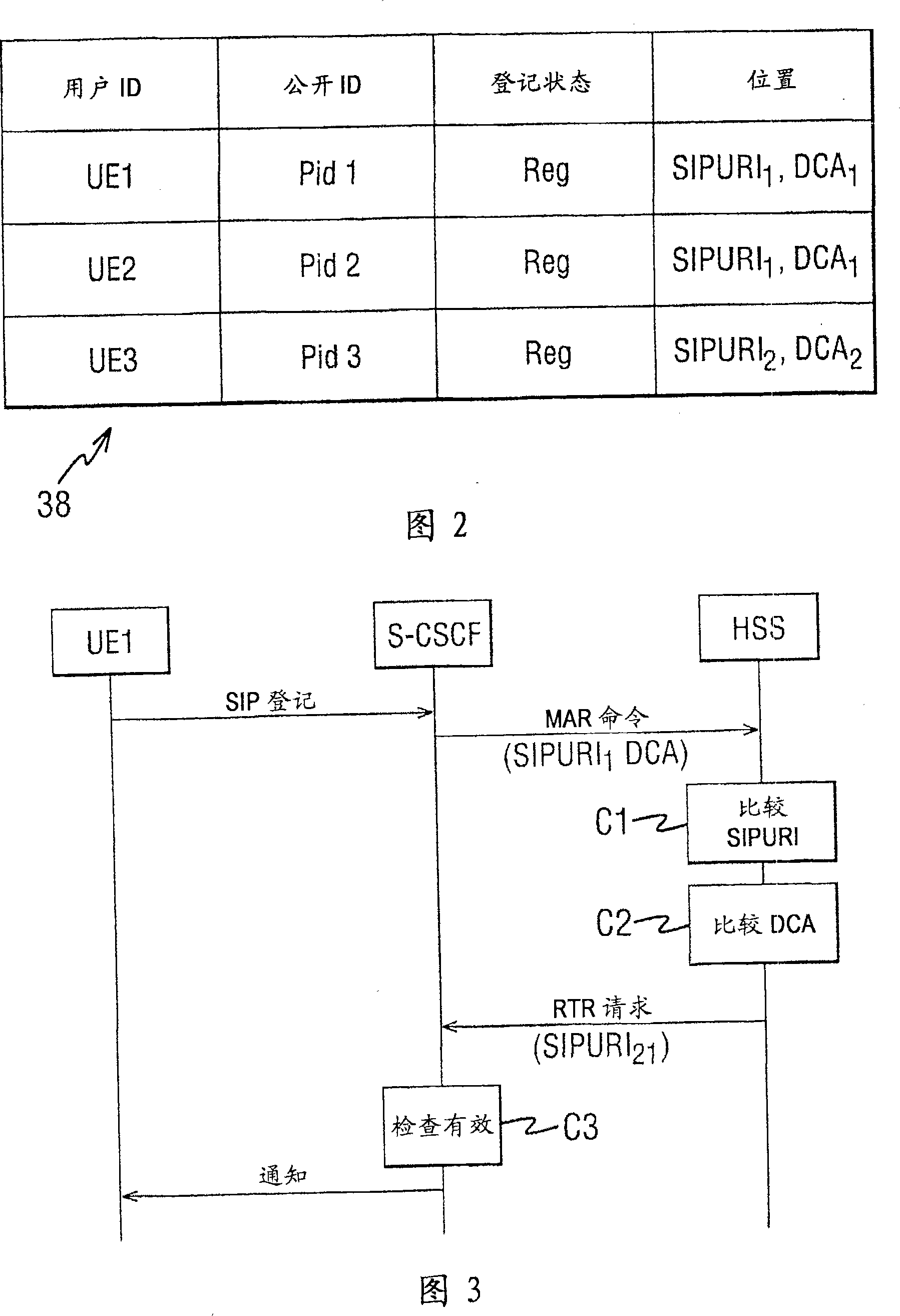
User registration in a communication system
ActiveCN101023700ARadio/inductive link selection arrangementsData switching networksCommunications systemService control
A method of registering users in a mobile communications system, the method comprising the steps of: storing in a user information store primary and secondary identifiers identifying a first serving controller; receiving a request from a serving controller, said request identifying that serving controller using primary and secondary identifiers; comparing the primary identifier in the user information store with the primary identifier in said request and, if there is a mismatch, comparing the secondary identifier in the user information store with the secondary identifier in said request wherein, when there is a mismatch between the secondary identifiers it is determined that the serving controller identified in the request is not the first serving controller; and when there is a match between the secondary identifiers it is determined that the serving controller identified in the request is the first serving controller.
Owner:NOKIA TECHNOLOGLES OY
Image processing device and image processing method
InactiveCN103748884AAvoid redundant transmissionPulse modulation television signal transmissionDigital video signal modificationImaging processingComputer science
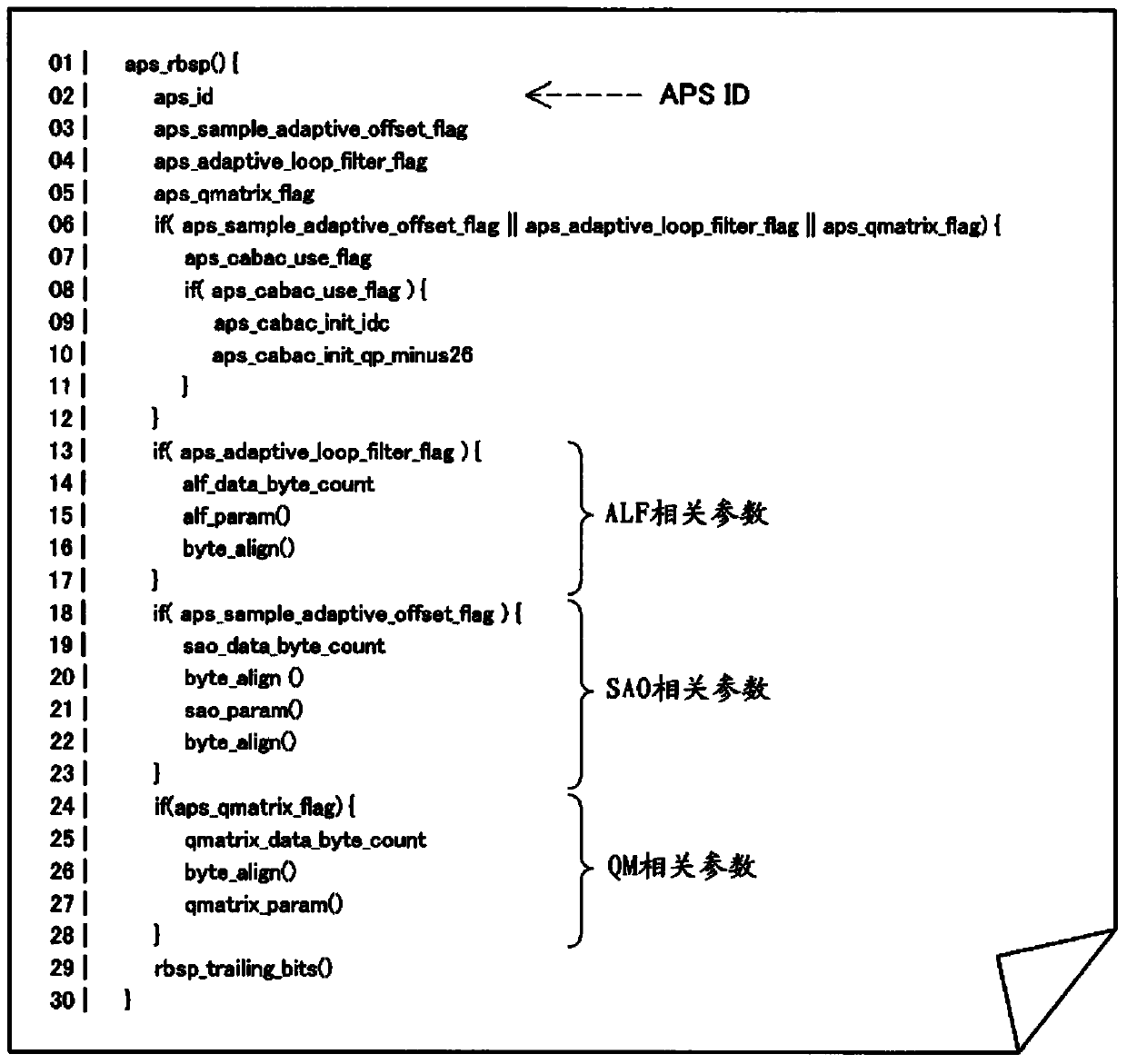
To avoid redundant transfer of parameters, in instances in which parameters of mutually different qualities are included in a common parameter set. Provided is an image processing device equipped with: an acquisition section for acquiring, from a parameter set of an encoded stream, a parameter group including one or more parameters for use when encoding or decoding an image, and an auxiliary identifier for identifying the parameter group in question; and a decoding section for decoding the image, using the parameters within the parameter group that has been looked up using the auxiliary identifier that was acquired by the acquisition section.
Owner:SONY CORP
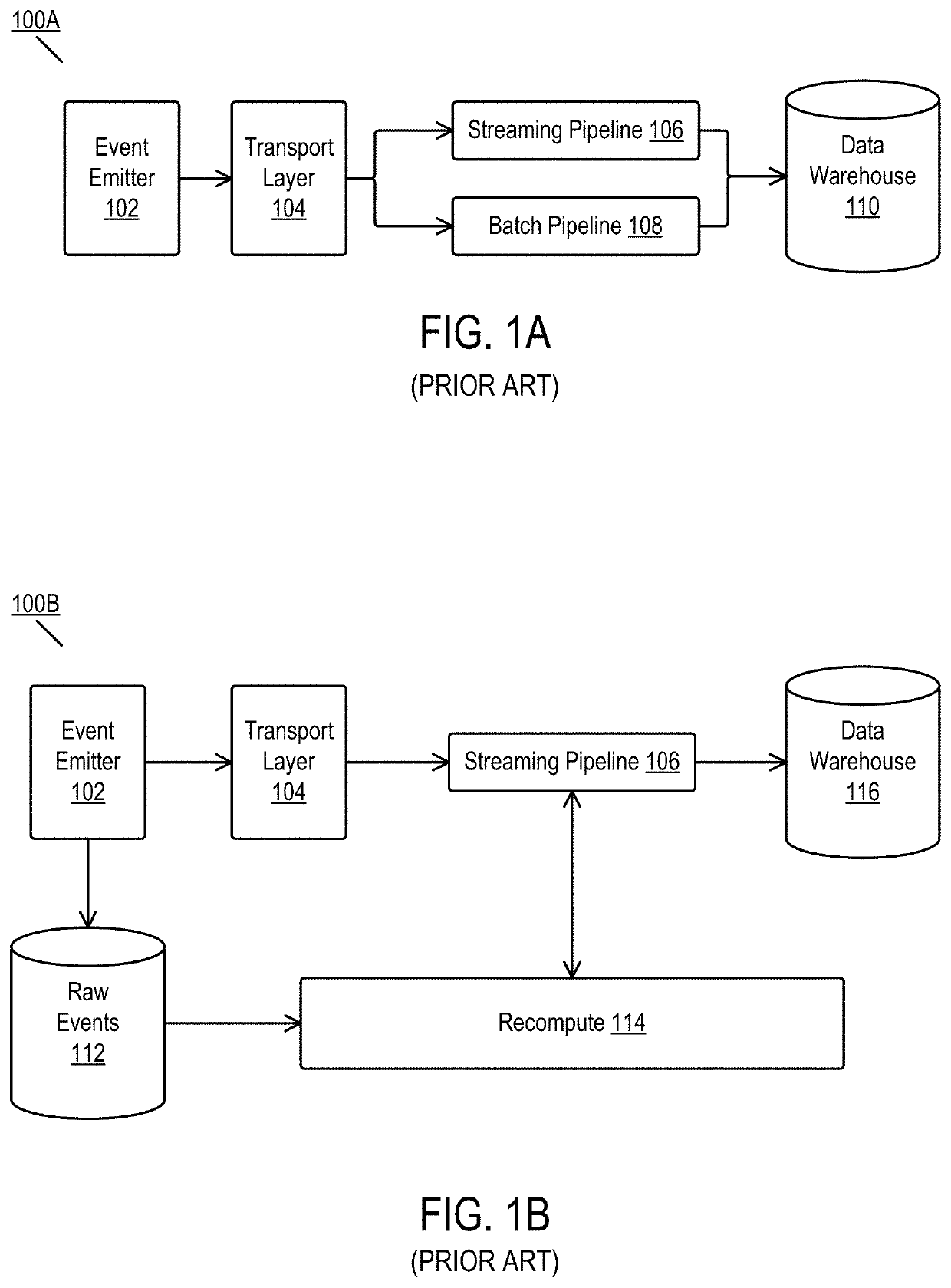
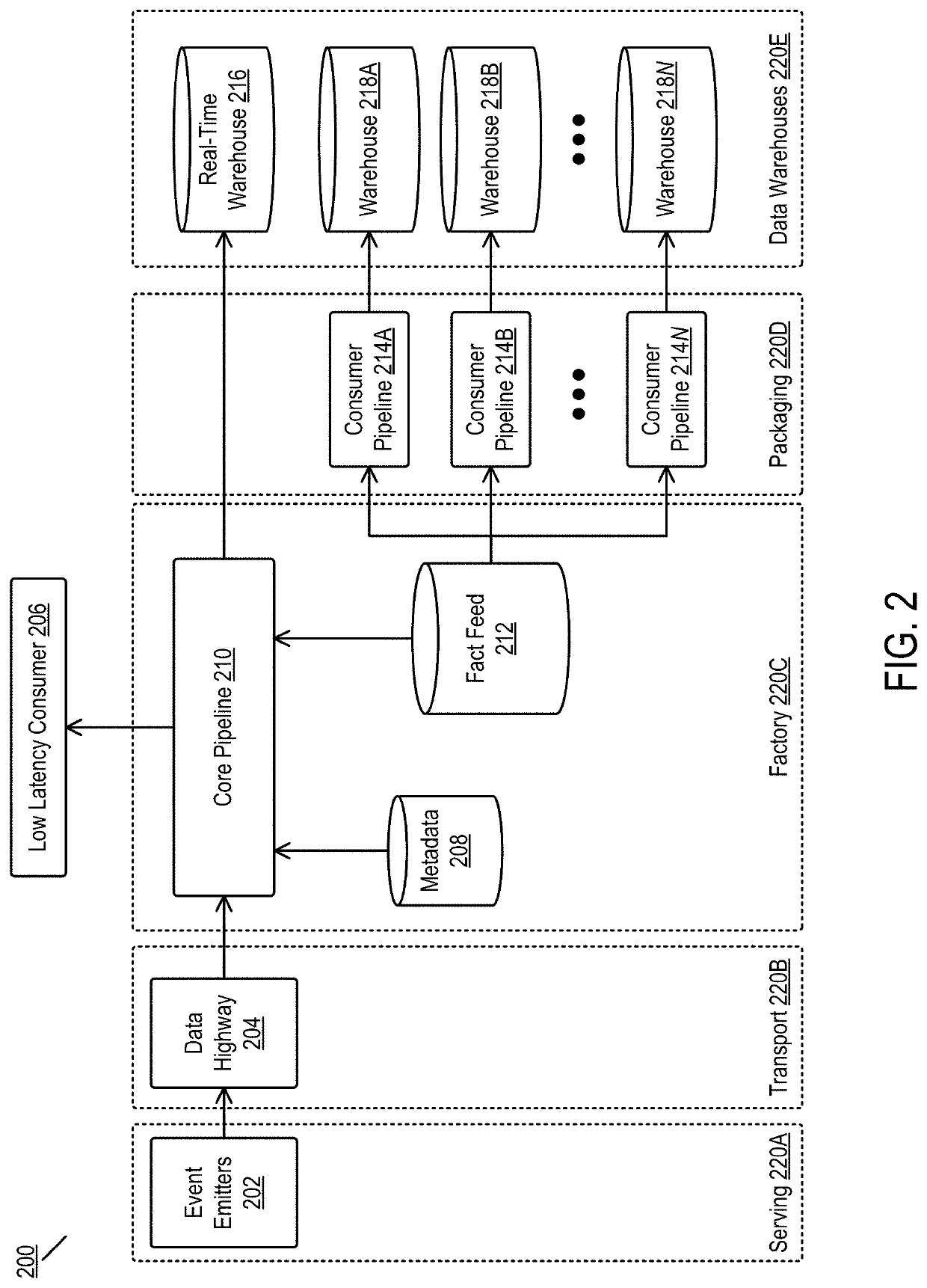
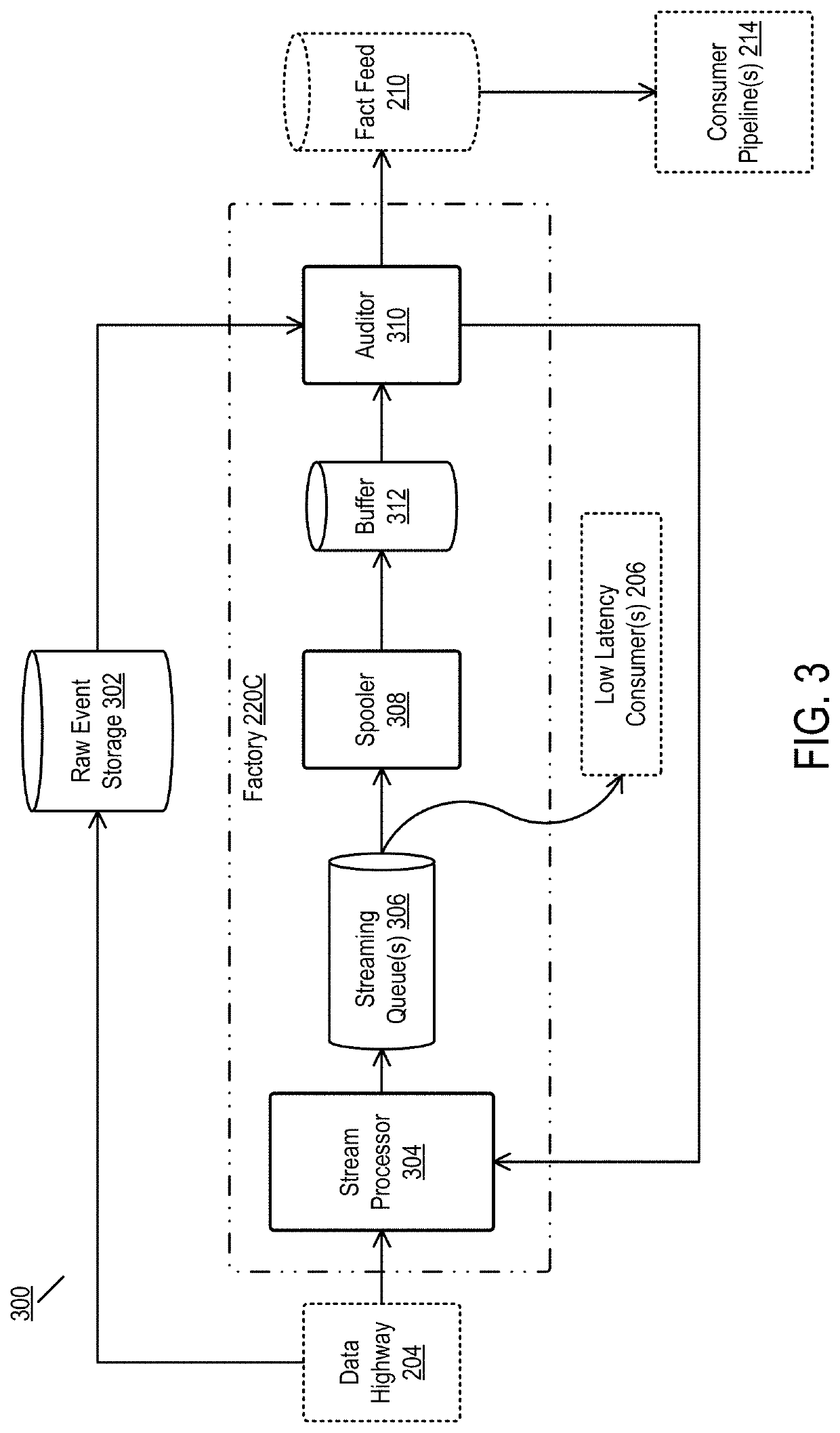
Exactly-once performance from a streaming pipeline in a fault-vulnerable system
ActiveUS11416497B2No risk of variationReduce dataInterprogram communicationFile system functionsTable (database)Batch processing
Owner:YAHOO ASSETS LLC
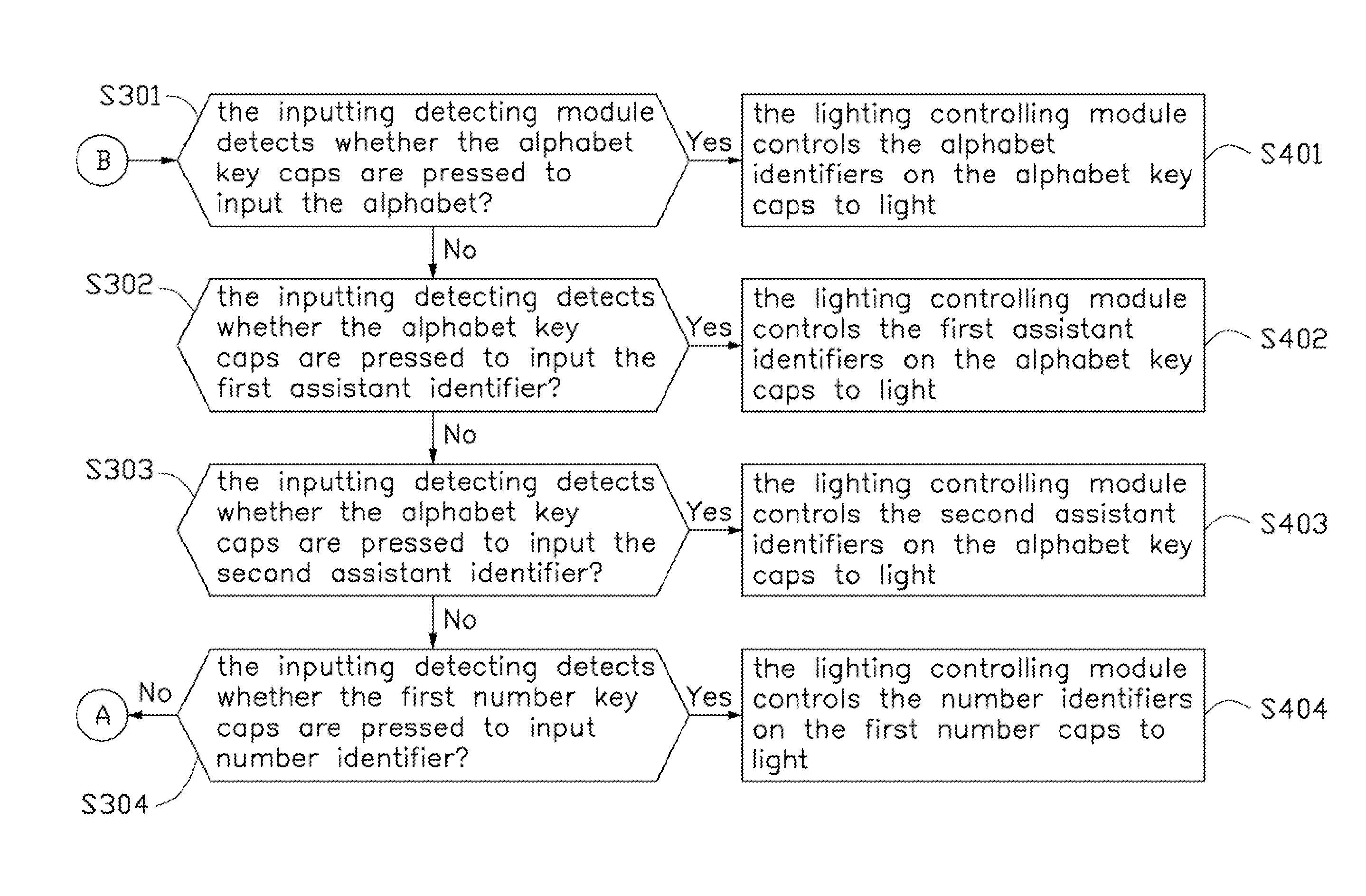
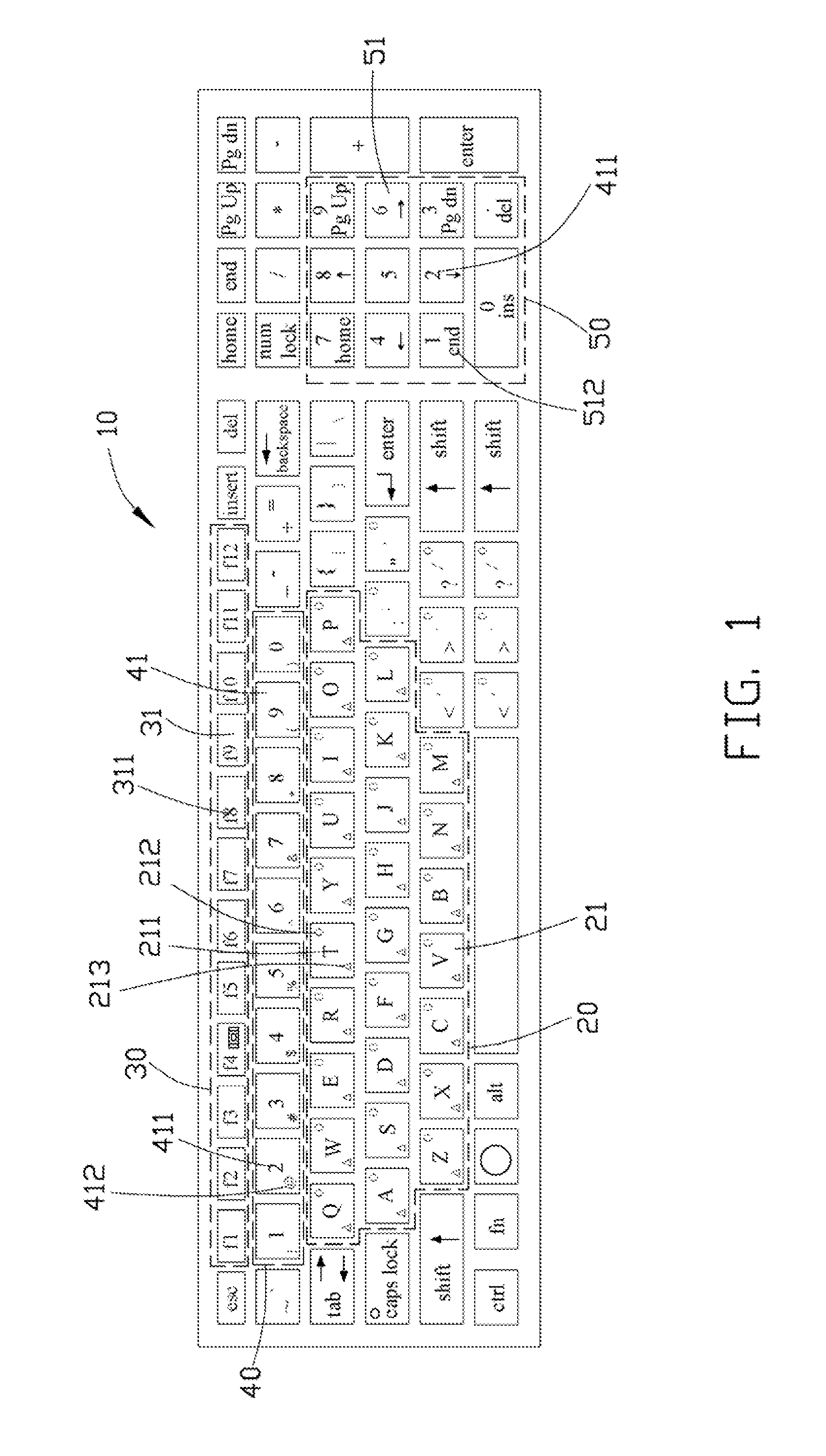
Keyboard with lighting apparatus and lighting method thereof
InactiveUS20140168088A1Input/output for user-computer interactionLegendsComputer hardwareEffect light
Owner:HON HAI PRECISION IND CO LTD
Exactly-once performance from a streaming pipeline in a fault-vulnerable system
ActiveUS20210365462A1Reduce certification timeReduce dataInterprogram communicationSpecial data processing applicationsTable (database)Batch processing
Disclosed are embodiments for providing batch performance using a stream processor. In one embodiment, a method is disclosed comprising receiving a stream of events, where each event comprises a header including an event type field and a timestamp. and identifying that the header of a given event in the stream of events includes at least one secondary event in a list of secondary identifiers included in the header. A flag is set in a distributed database for the at least one secondary event, then writing the given event to a table in the distributed database occurs, the table selected based on a respective event type field and timestamp associated with the given event. Deduplicating the given event and the at least one secondary event in response to a close of books (COB) signal occurs, after which writing at least one deduplicated event to a storage device occurs, the at least one deduplicated event selected from the group consisting of the given event and the at least one secondary event.
Owner:YAHOO ASSETS LLC
Technique for authenticating a user device
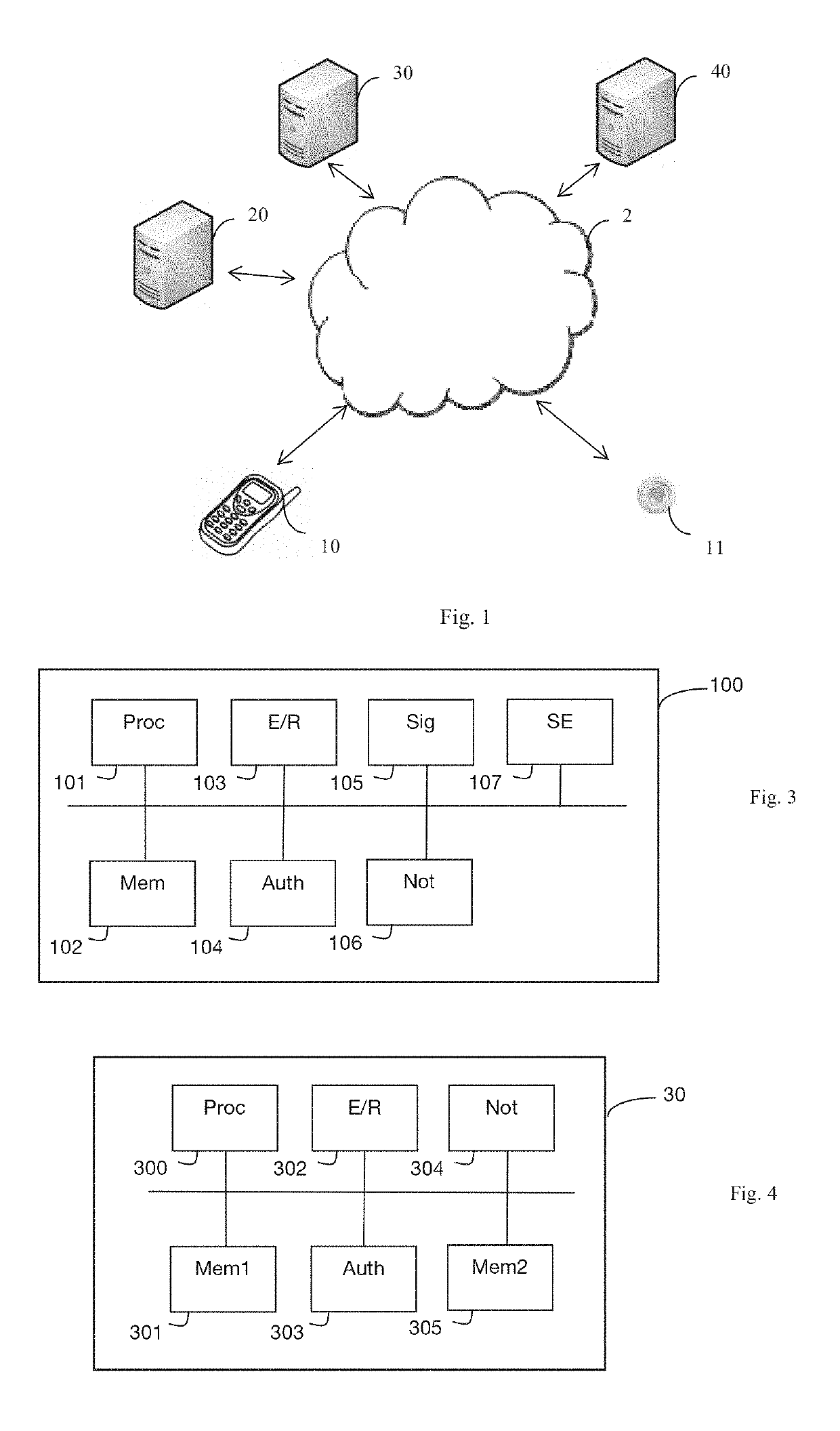
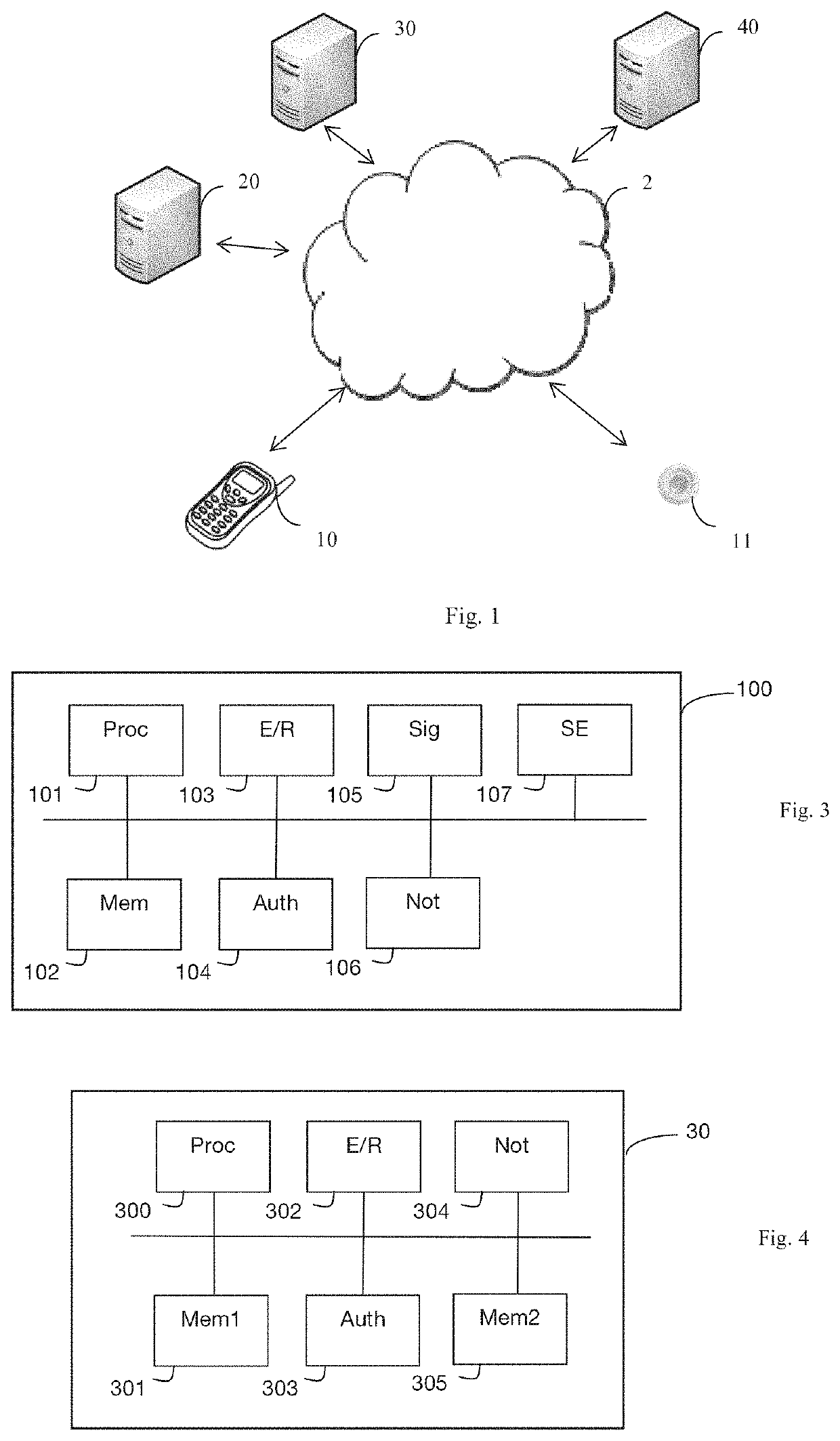
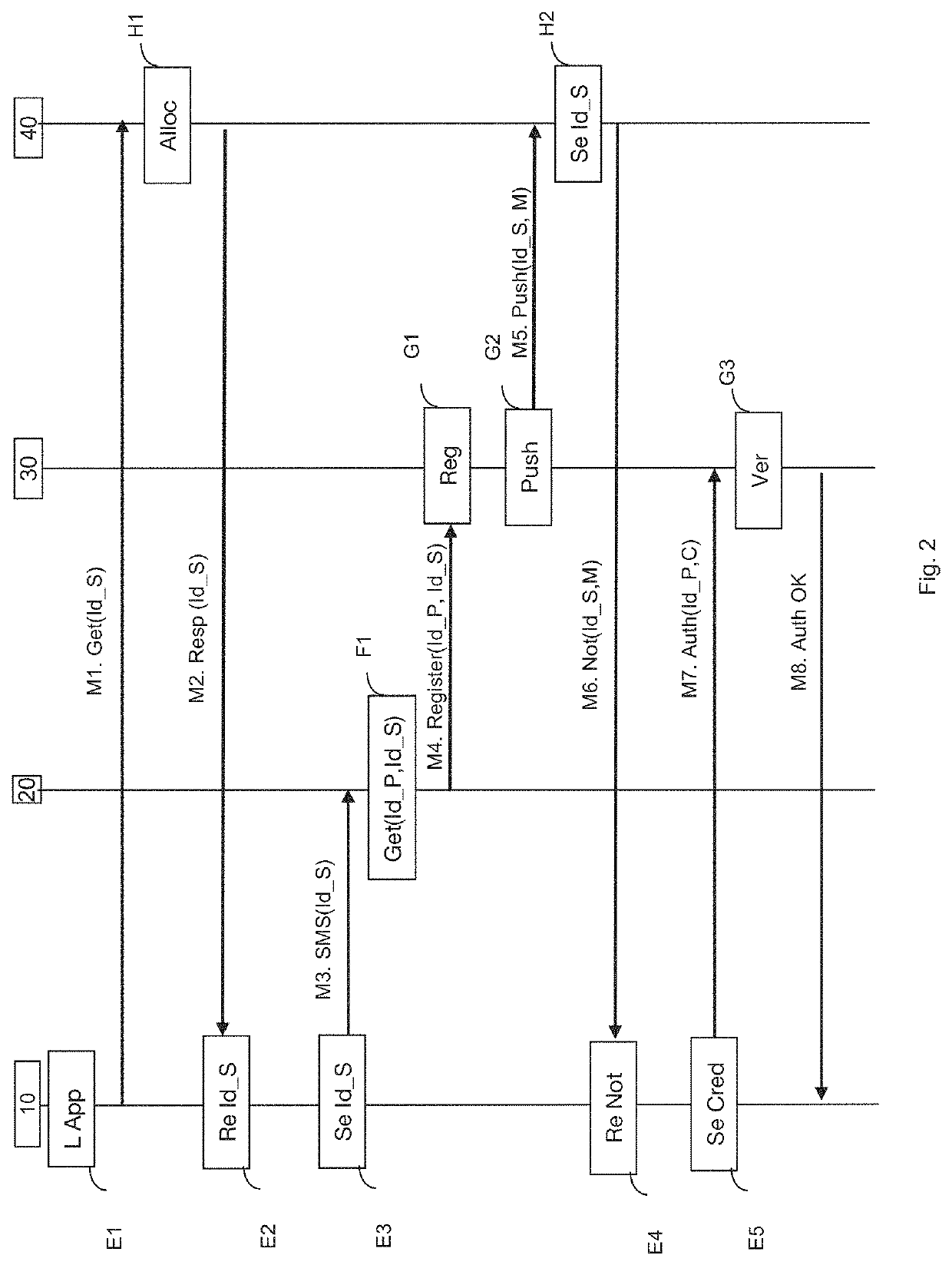
ActiveUS20190149991A1Reliable acquisitionClient path is highly simplified and secureConnection managementTransmissionUser deviceSecondary Identifier
A technique for authenticating a user device with an application package server implementing an application. The device obtains a secondary identifier, allowing it to receive notifications relating to the application. Next, the device dispatches, while being identified by a main identifier associated with the device by way of a security module, a signalling message including the secondary identifier. Subsequent to this dispatching, the device receives a notification relating to the application which is addressed to it while being identified by the secondary identifier. This notification, the dispatching of which has been commanded by the application package server, includes the main identifier and an authenticator. The device then dispatches an authentication request to the application package server. This authentication request includes the main identifier and the authenticator that was received. The device is authenticated by the application package server by using this main identifier in association with this secondary identifier.
Owner:ORANGE SA (FR)
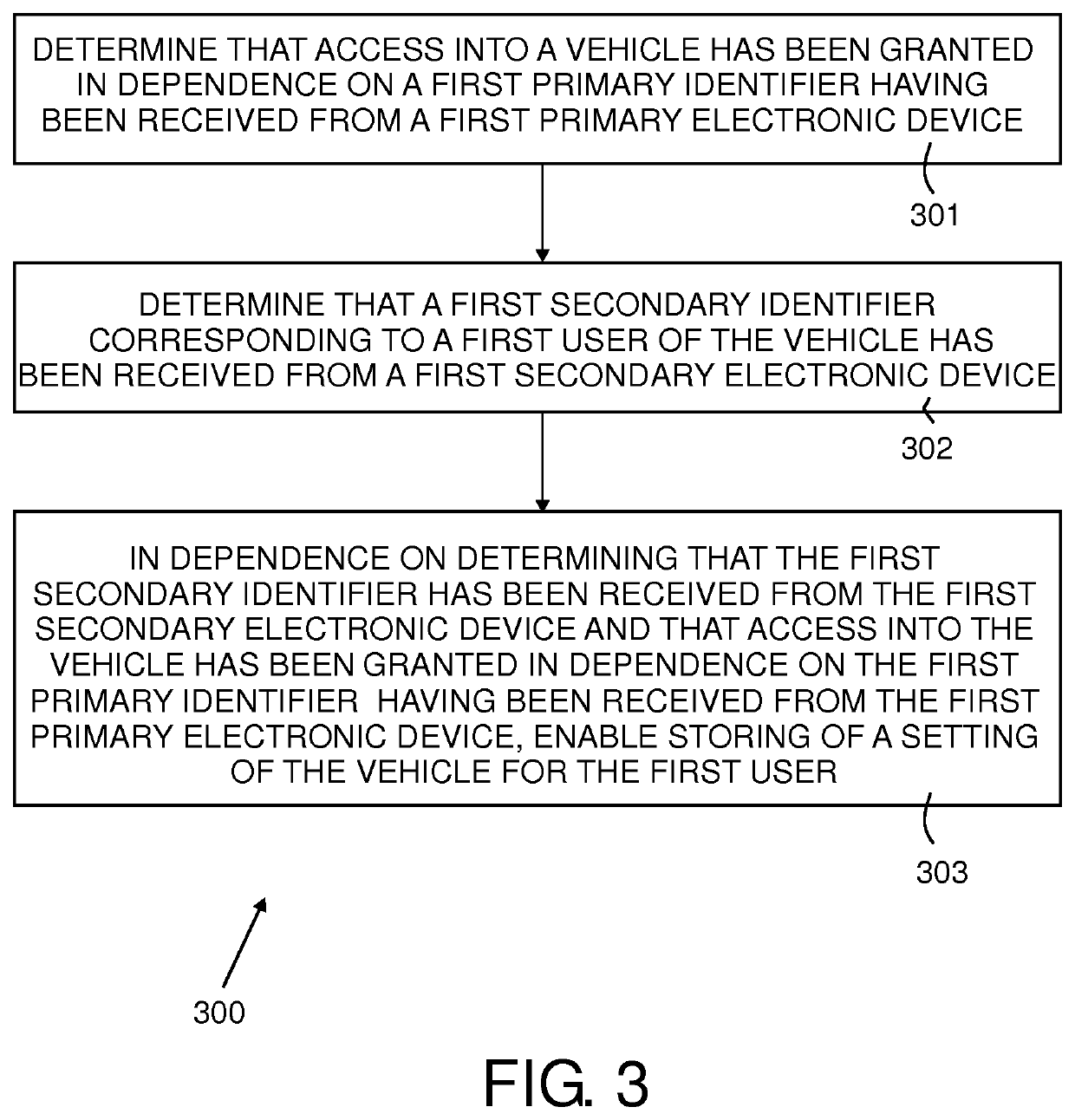
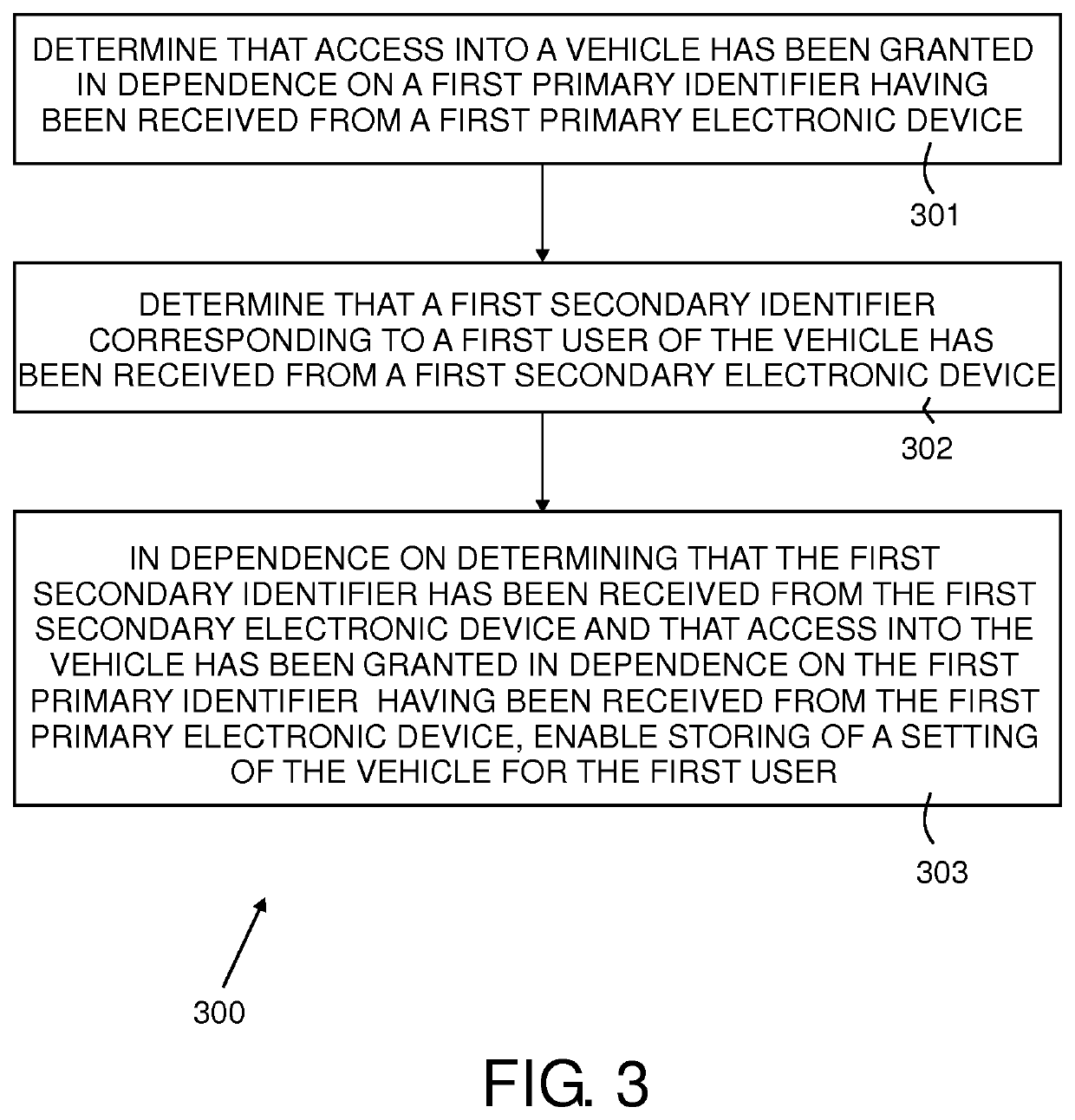
Apparatus and method for enabling storing of a user input vehicle setting
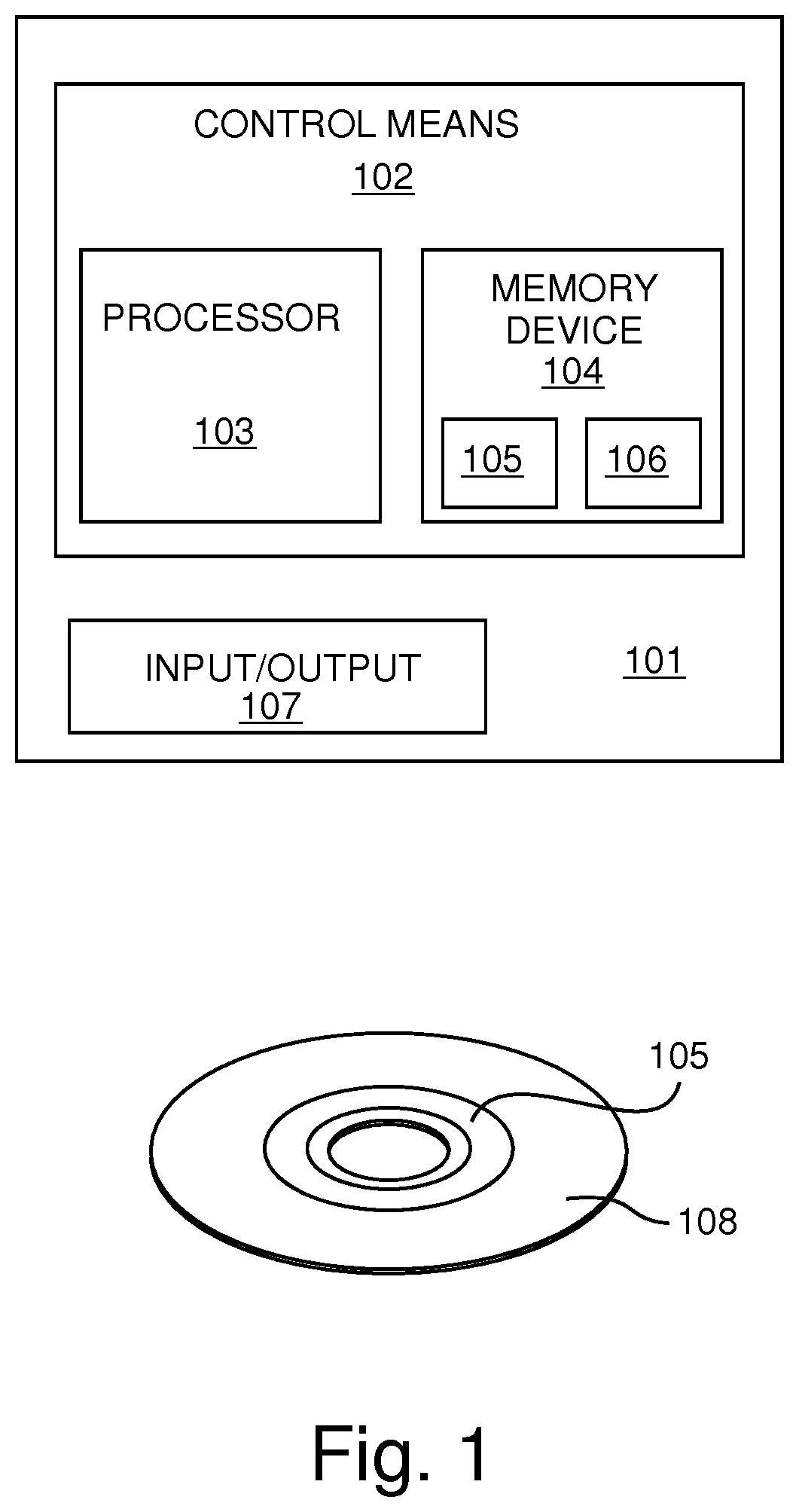
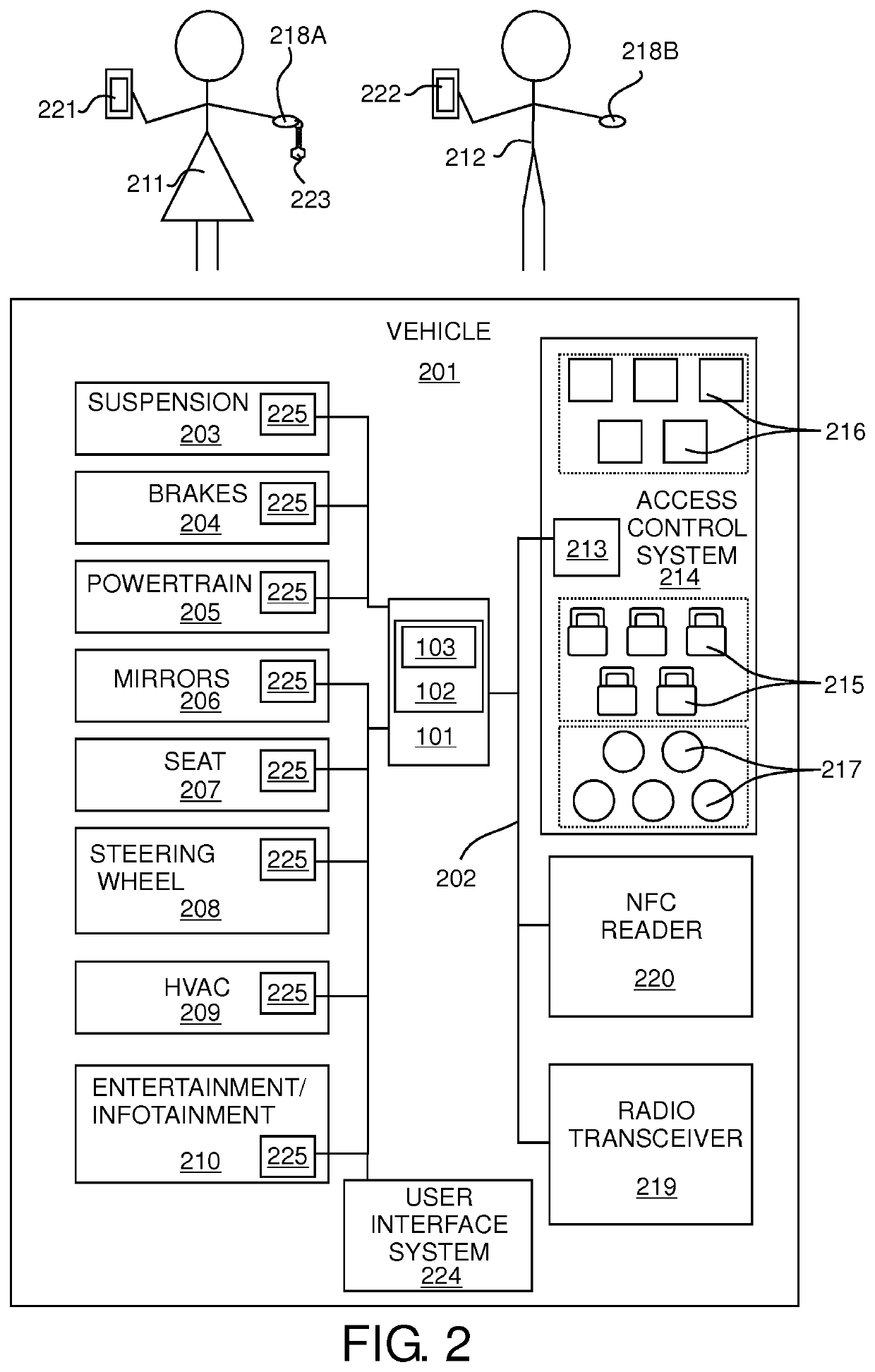
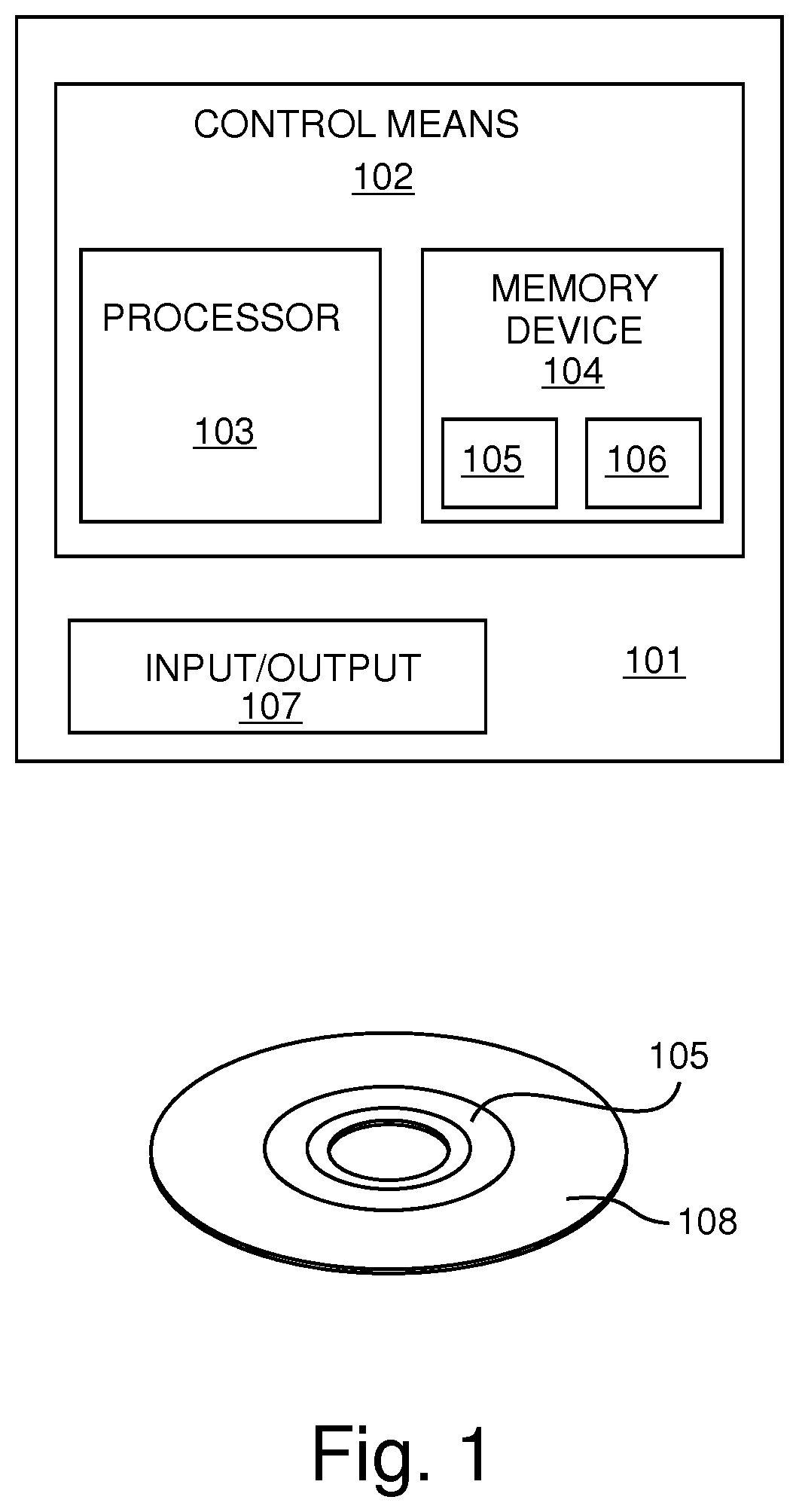
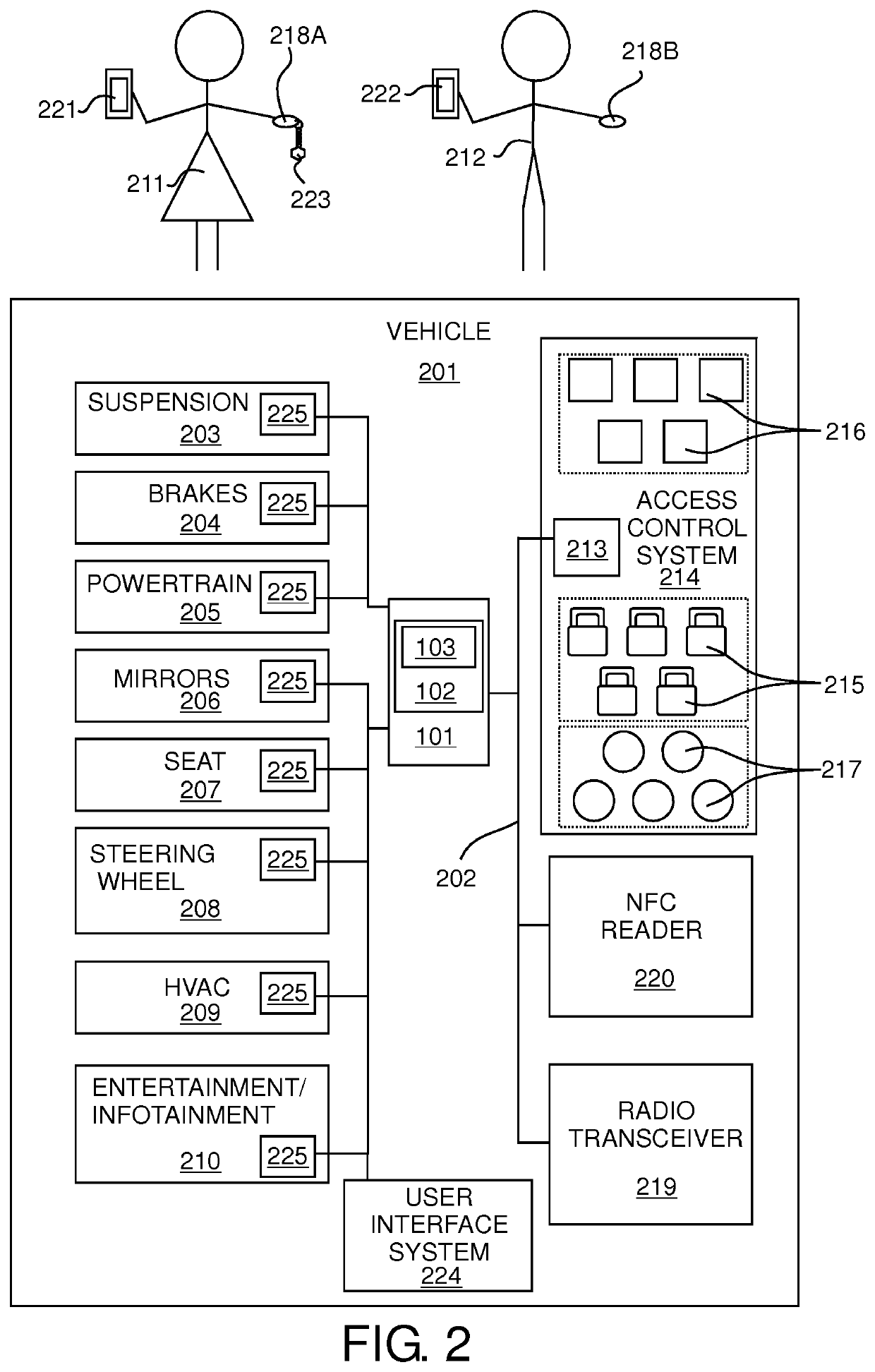
ActiveUS20200070758A1Avoid storage problemsAvoid changeAnti-theft devicesElectric/fluid circuitComputer hardwareUser input
An apparatus (101) for enabling storing of settings of a vehicle (201), a system, a vehicle (201), a method (300, 400, 500, 600), a computer program (105) and a non-transitory computer-readable storage medium (108) are disclosed. The apparatus (101) comprises a processing means and a memory means for storing at least one setting of the vehicle (201) for at least one user. The apparatus (101) is configured to determine that access into a vehicle (201) has been granted in dependence on a first primary identifier having been received from a first primary electronic device (218A) and determine that a first secondary identifier corresponding to a first user of the vehicle (201) has been received from a first secondary electronic device (221). The apparatus (101) is also configured to, in dependence on determining that the first secondary identifier has been received from the first secondary electronic device (221) and that access into the vehicle has been granted in dependence on the first primary identifier having been received from the first primary electronic device (218A), enable storing of a setting of the vehicle (201) for the first user.
Owner:JAGUAR LAND ROVER LTD
Method, system and apparatus for providing calling name identification
ActiveUS9060067B2Special service for subscribersCalling susbscriber number recording/indicationNetwork addressingNetwork address
Embodiments of the present invention are directed to a method, system and apparatus for providing customized calling identification. A method for providing customized calling identification comprises receiving a request for initiating an outgoing call from a communication client, the communication client being registered in association with a network address and being associated with a communication client identifier. The method further comprises, based on the communication client identifier, determining an auxiliary identifier associated with the communication client. The method further comprises augmenting the request for initiating an outgoing call with the auxiliary identifier to generate an augmented request.
Owner:BCE
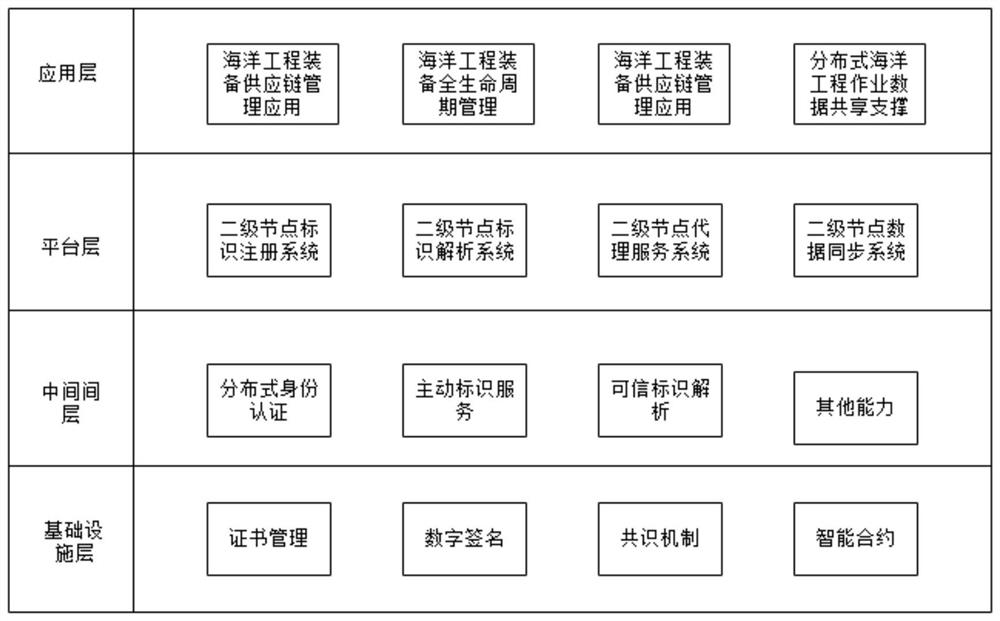
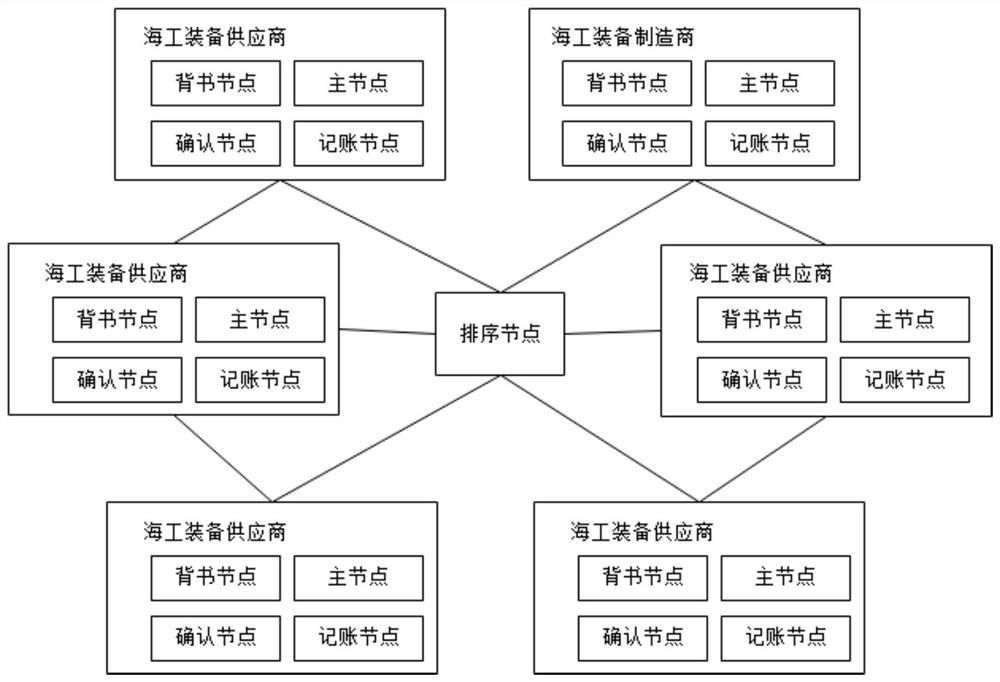
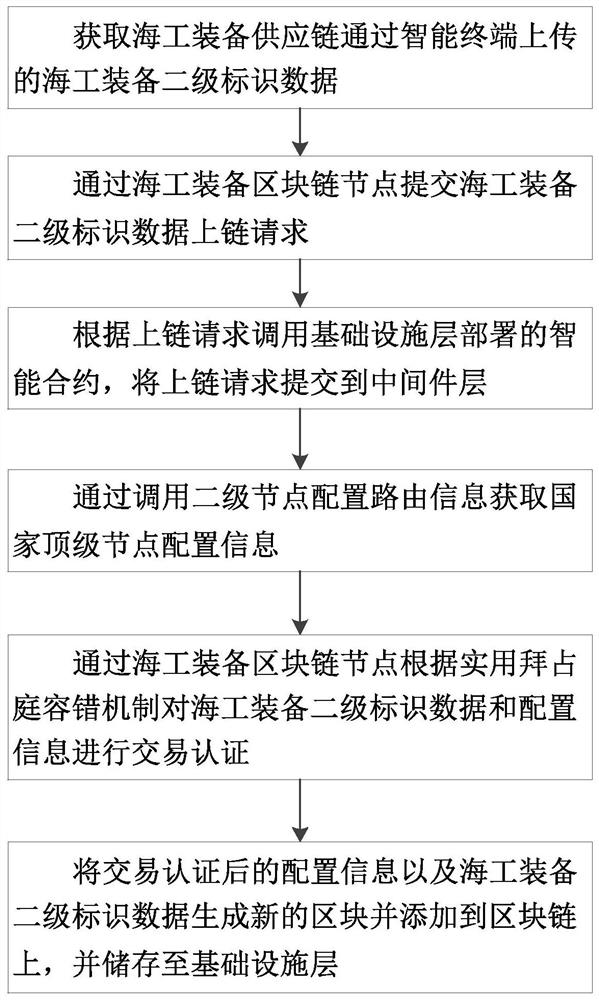
Industrial Internet of Things system and maritime work identification data storage and query method
PendingCN113886486AImplement storageImplement queryData processing applicationsDatabase distribution/replicationIndustrial InternetData store
The invention discloses an industrial Internet of Things system and a maritime work identification data storage and query method, and the method comprises that an infrastructure layer employs a block chain architecture and is used for storing maritime work equipment secondary identification data and recording information of secondary identification data operation; a middleware layer is used for realizing data exchange between a national top-level node and a maritime work equipment industry second-level node by acquiring calculation and storage resources provided by the infrastructure layer; a platform layer is used for building a secondary node function system, and the secondary node function system is upwards butted with a national top-level node and downwards butted with an enterprise node, a mechanism node and a recursive node in the maritime work equipment industry; an application layer is connected with the middleware layer, verifies an identifier query instruction of a user and displays a secondary identifier data traceability result. According to the invention, storage and query of the secondary identification data can be realized, data interaction operation among different identities is realized, and the invention has the advantages of safety and reliability based on the block chain.
Owner:WUHAN UNIV OF TECH
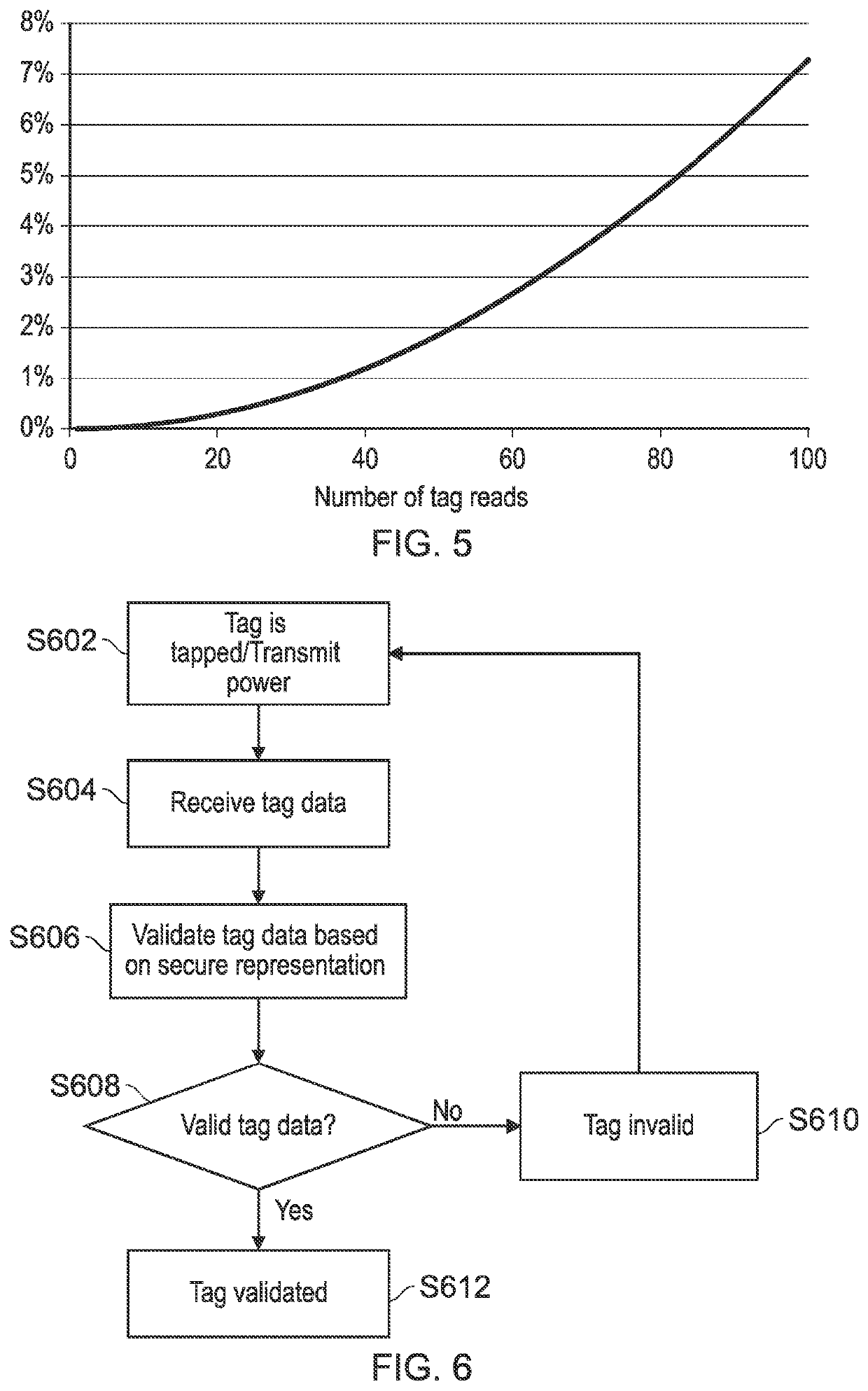
Secure RFID tag identification
ActiveUS20200213286A1Improve securityKey distribution for secure communicationUser identity/authority verificationComputer networkInternet privacy
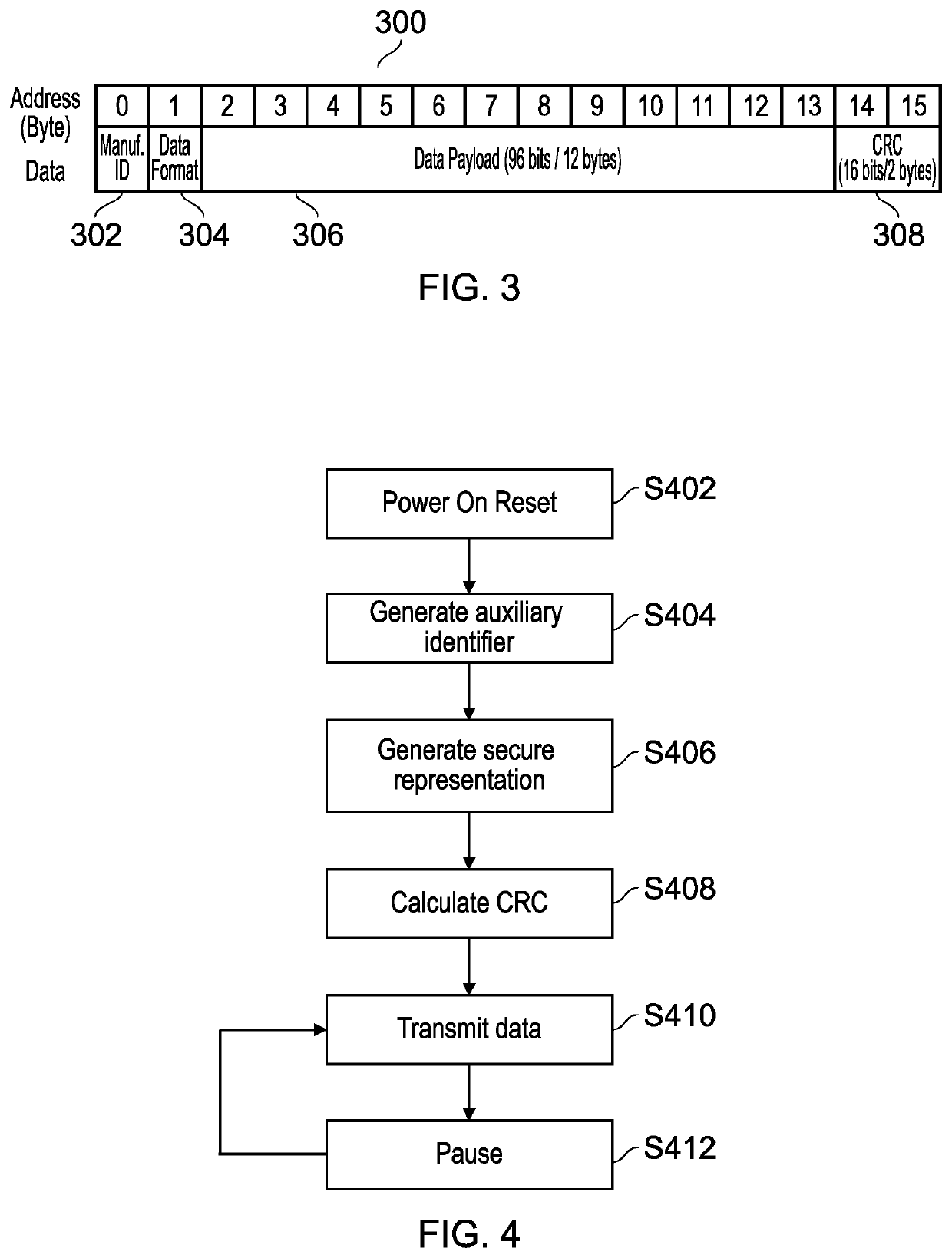
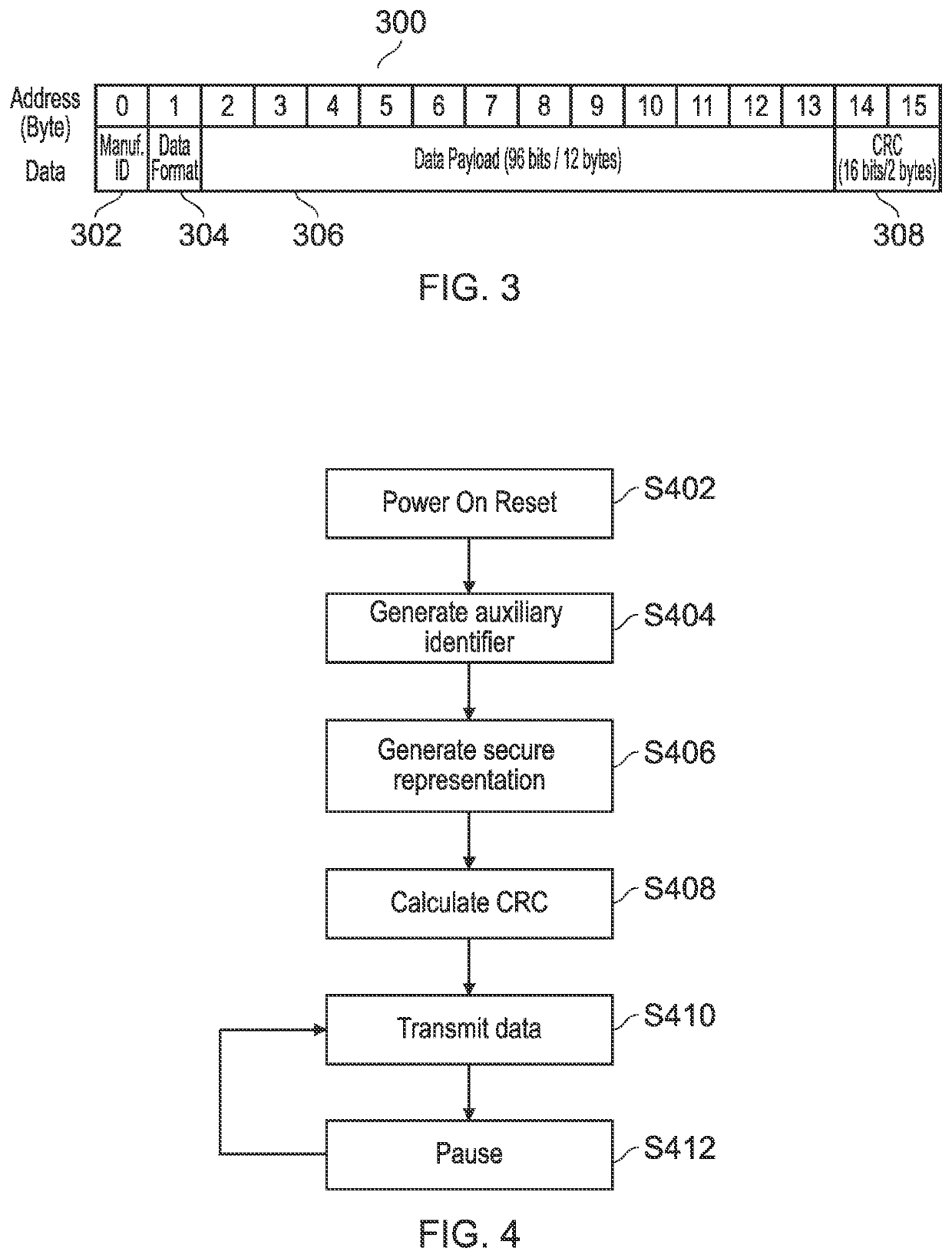
A method, apparatus and system for secure one-way RFID tag identifications provided. The method comprising generating, at an RFID tag, an auxiliary identifier; generating, at an RFID tag, a secure representation based on the auxiliary identifier; transmitting, from the RFID tag and receiving at an RFID reader, one or more representations of the auxiliary identifier and the tag identifier including the secure representation; and verifying the identity of the RFID tag based on the received representations.
Owner:PRAGMATIC PRINTING
Secure RFID tag identification
ActiveUS20220360572A1Improve securityKey distribution for secure communicationUser identity/authority verificationComputer networkInternet privacy
A method, apparatus and system for secure one-way RFID tag identification is provided. The method comprising generating, at an RFID tag, an auxiliary identifier; generating, at an RFID tag, a secure representation based on the auxiliary identifier; transmitting, from the RFID tag and receiving at an RFID reader, one or more representations of the auxiliary identifier and the tag identifier including the secure representation; and verifying the identity of the RFID tag based on the received representations.
Owner:PRAGMATIC PRINTING
Apparatus and method for enabling storing of a user input vehicle setting
ActiveUS11260812B2Avoid changeAvoid storage problemsAnti-theft devicesElectric/fluid circuitComputer hardwareUser input
An apparatus (101) for enabling storing of settings of a vehicle (201), a system, a vehicle (201), a method (300, 400, 500, 600), a computer program (105) and a non-transitory computer-readable storage medium (108) are disclosed. The apparatus (101) comprises a processing means and a memory means for storing at least one setting of the vehicle (201) for at least one user. The apparatus (101) is configured to determine that access into a vehicle (201) has been granted in dependence on a first primary identifier having been received from a first primary electronic device (218A) and determine that a first secondary identifier corresponding to a first user of the vehicle (201) has been received from a first secondary electronic device (221). The apparatus (101) is also configured to, in dependence on determining that the first secondary identifier has been received from the first secondary electronic device (221) and that access into the vehicle has been granted in dependence on the first primary identifier having been received from the first primary electronic device (218A), enable storing of a setting of the vehicle (201) for the first user.
Owner:JAGUAR LAND ROVER LTD
Technique for authenticating a user device
ActiveUS11070978B2Reliable acquisitionClient path is highly simplified and secureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser deviceApplication procedure
A technique for authenticating a user device with an application package server implementing an application. The device obtains a secondary identifier, allowing it to receive notifications relating to the application. Next, the device dispatches, while being identified by a main identifier associated with the device by way of a security module, a signalling message including the secondary identifier. Subsequent to this dispatching, the device receives a notification relating to the application which is addressed to it while being identified by the secondary identifier. This notification, the dispatching of which has been commanded by the application package server, includes the main identifier and an authenticator. The device then dispatches an authentication request to the application package server. This authentication request includes the main identifier and the authenticator that was received. The device is authenticated by the application package server by using this main identifier in association with this secondary identifier.
Owner:ORANGE SA (FR)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com