Method and apparatus for performing failure checking on service of remote method invocation
A technology of remote method invocation and failure, applied in the field of distributed systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] see figure 1 , which is a flow chart of a method for diagnosing a service remote method call provided by an embodiment of the present invention, the method includes the following steps:
[0057] Step 101: the client connects to the Zookeeper service cluster, wherein the service provided by the server creates its own temporary node on the Zookeeper service cluster;
[0058] Each service provided by the server to the client will establish a temporary node on the Zookeeper service cluster during the initialization phase of operation, and name the temporary node with the service identifier. The identification name of each service is the IP address of the server providing the service + the port number of the service.
[0059] Step 102: The client initiates a request to the Zookeeper service cluster to monitor the temporary node of the service, and the request is used to trigger the Zookeeper service cluster to delete the temporary node of the service when deleting the tempo...
Embodiment 2
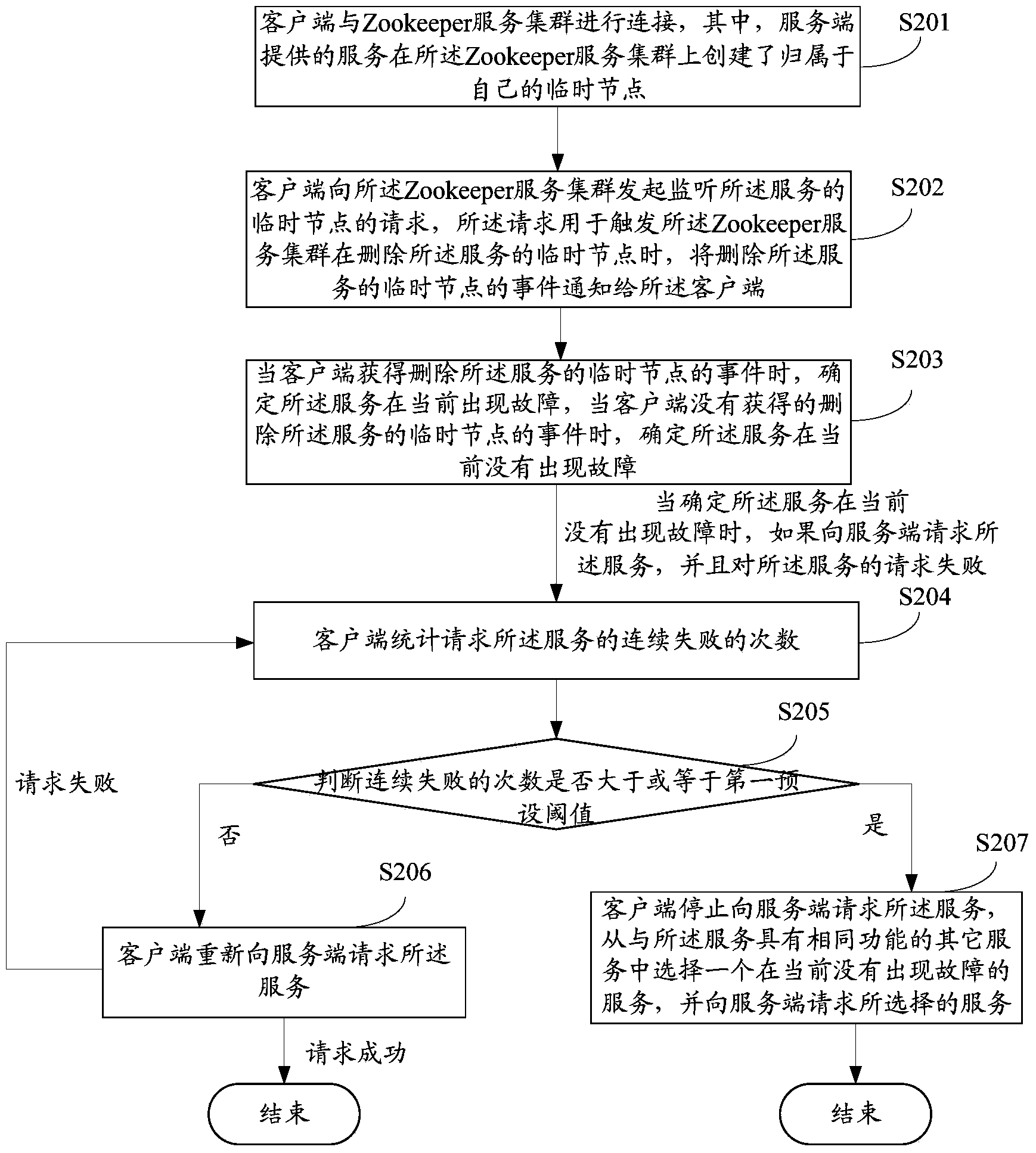
[0072] The difference between the second embodiment and the first embodiment is that after the client can determine whether the service is currently faulty according to whether it receives the event of deleting the temporary node of a certain service, for the service that is not currently faulty, if the If the server requests the service, and the request for the service fails, the client can further re-request the service until the request for the service succeeds, so as to realize the disaster recovery processing of the service through continuous retries. see figure 2 , which is a flow chart of a method for performing disaster recovery processing on a service called by a remote method provided by an embodiment of the present invention, and the method includes the following steps:
[0073] Step 201: the client connects to the Zookeeper service cluster, wherein the service provided by the server creates its own temporary node on the Zookeeper service cluster;
[0074] Step 20...
Embodiment 3
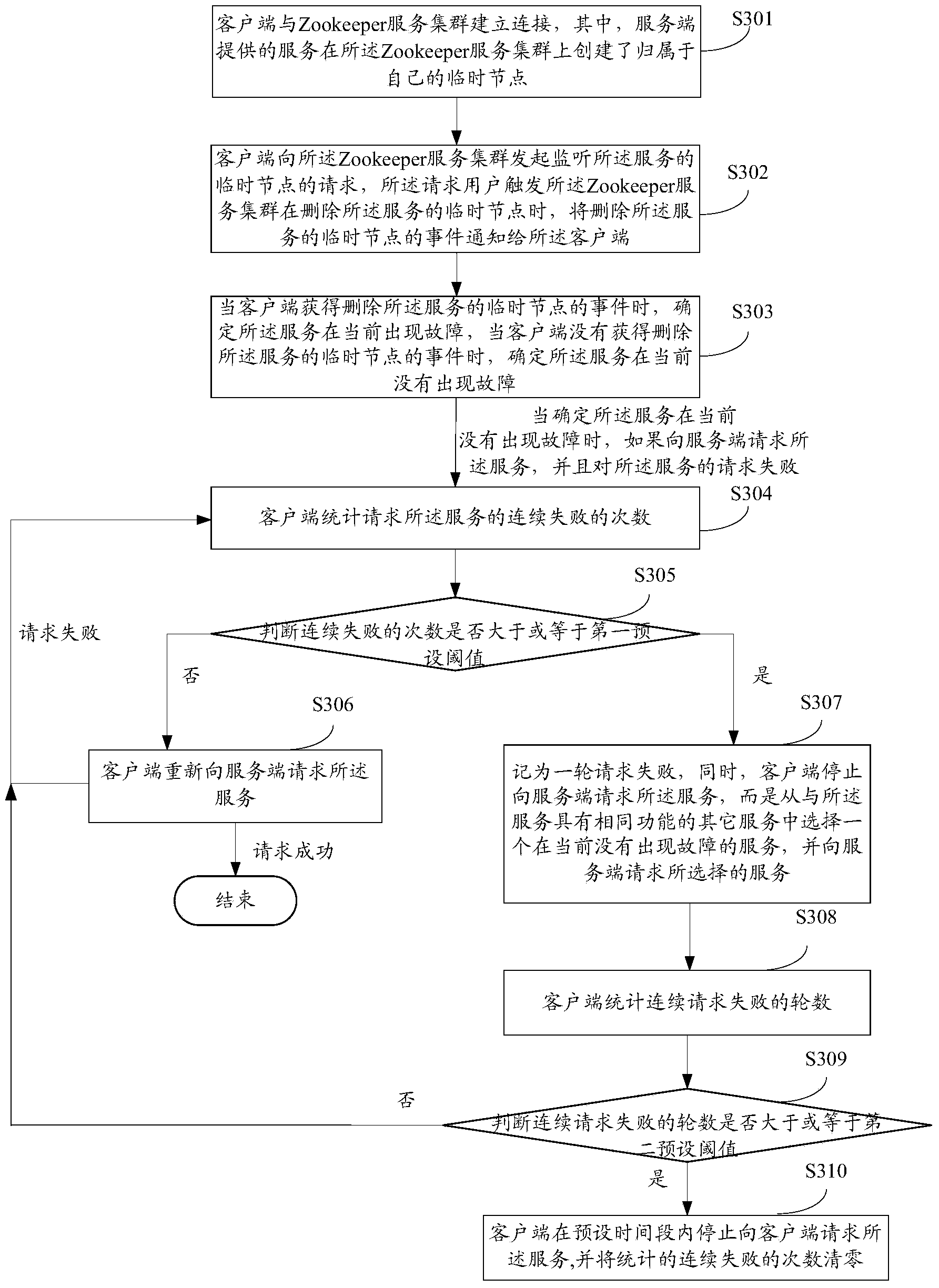
[0089] On the basis of the technical solution shown in Embodiment 2, in addition to implementing disaster recovery processing by retrying and jumping to other services, Embodiment 3 can further implement disaster recovery processing by shielding services. see image 3 , which is a flow chart of another method for performing disaster recovery processing on a service called by a remote method provided by an embodiment of the present invention, and the method includes the following steps:
[0090] Step 301: the client connects to the Zookeeper service cluster, wherein the service provided by the server creates its own temporary node on the Zookeeper service cluster;
[0091] Step 302: The client initiates a request to the Zookeeper service cluster to monitor the temporary node of the service, and the requesting user triggers the Zookeeper service cluster to delete the temporary node of the service when deleting the temporary node of the service Notify the client of the event;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com