Data resource authorization and authentication method, device and system based on Hash tree
A data resource and hash tree technology, applied in the field of authorization and authentication of digital resources, can solve problems such as large data volume, excessive exposure of authorization information, increase of authorization information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Various exemplary embodiments of the present disclosure will now be described in detail with reference to the accompanying drawings. Relative arrangements of components and steps, numerical expressions and numerical values set forth in these embodiments do not limit the scope of the present disclosure unless specifically stated otherwise.
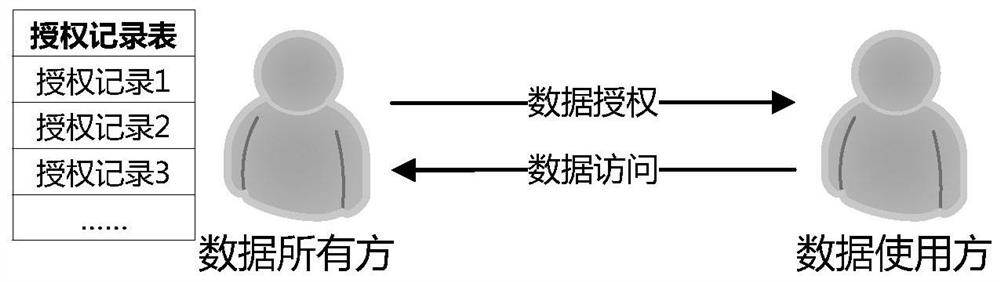
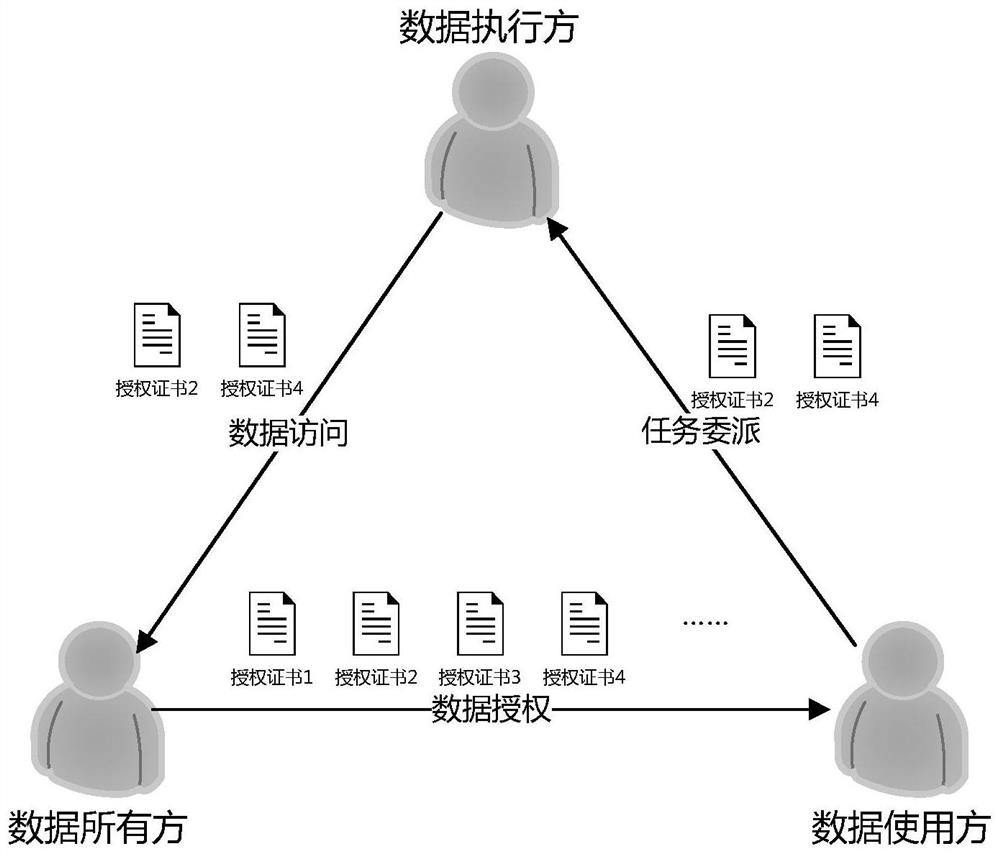
[0037] On the whole, the present invention uses a hash tree to construct authorization certificates that can be used for authority authentication. Figure 5 It shows an example of improved data authorization and access control according to the present invention. In this control example, the data owner authorizes multiple data resources in batches, and in the authentication process, the data user only needs to provide The authority record of the data resource to be authenticated, without providing the authority record of other data resources to be authorized in batches. In addition, an embodiment of the present invention also uses ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com