Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
135results about How to "Guarantee management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
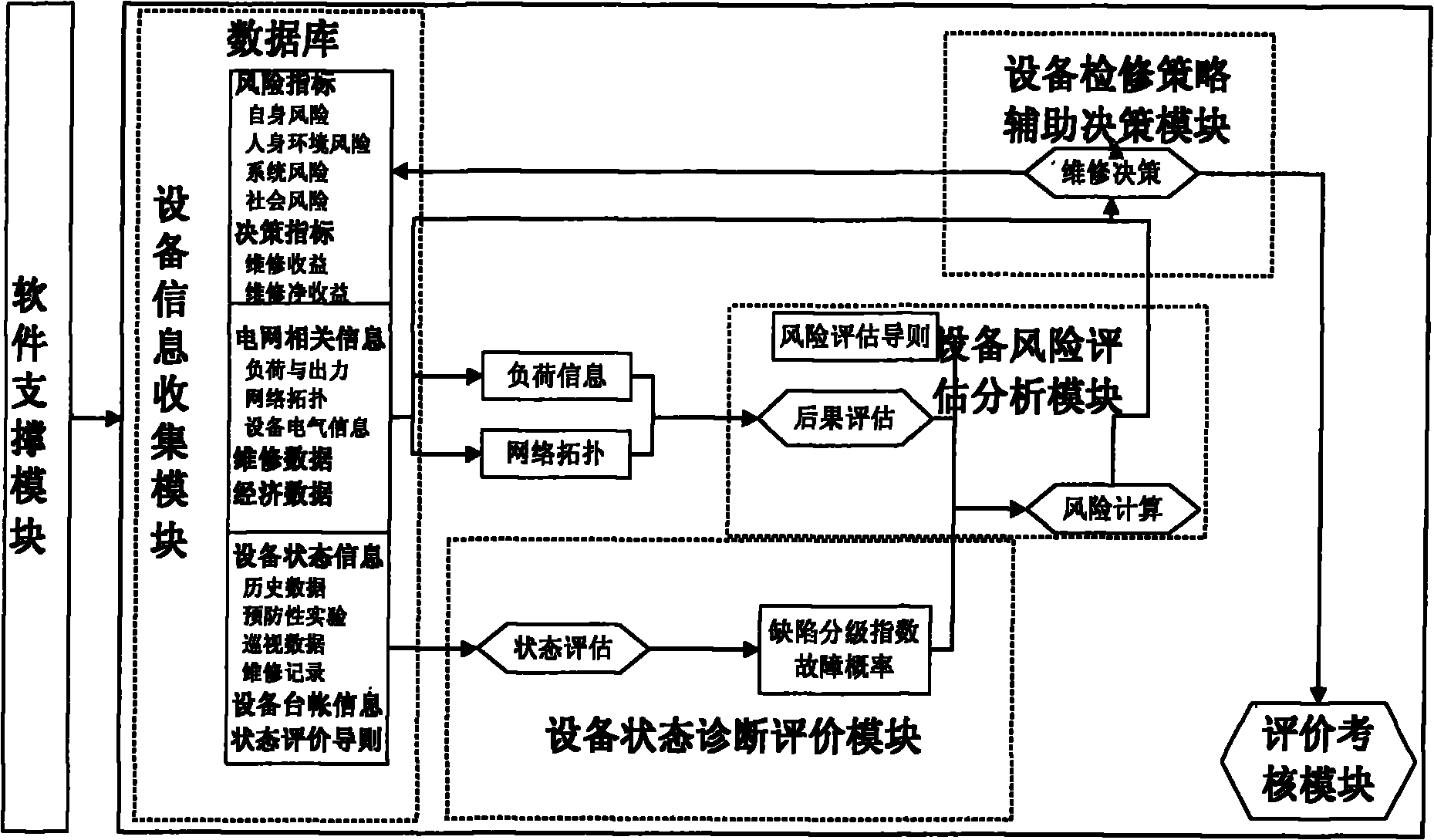
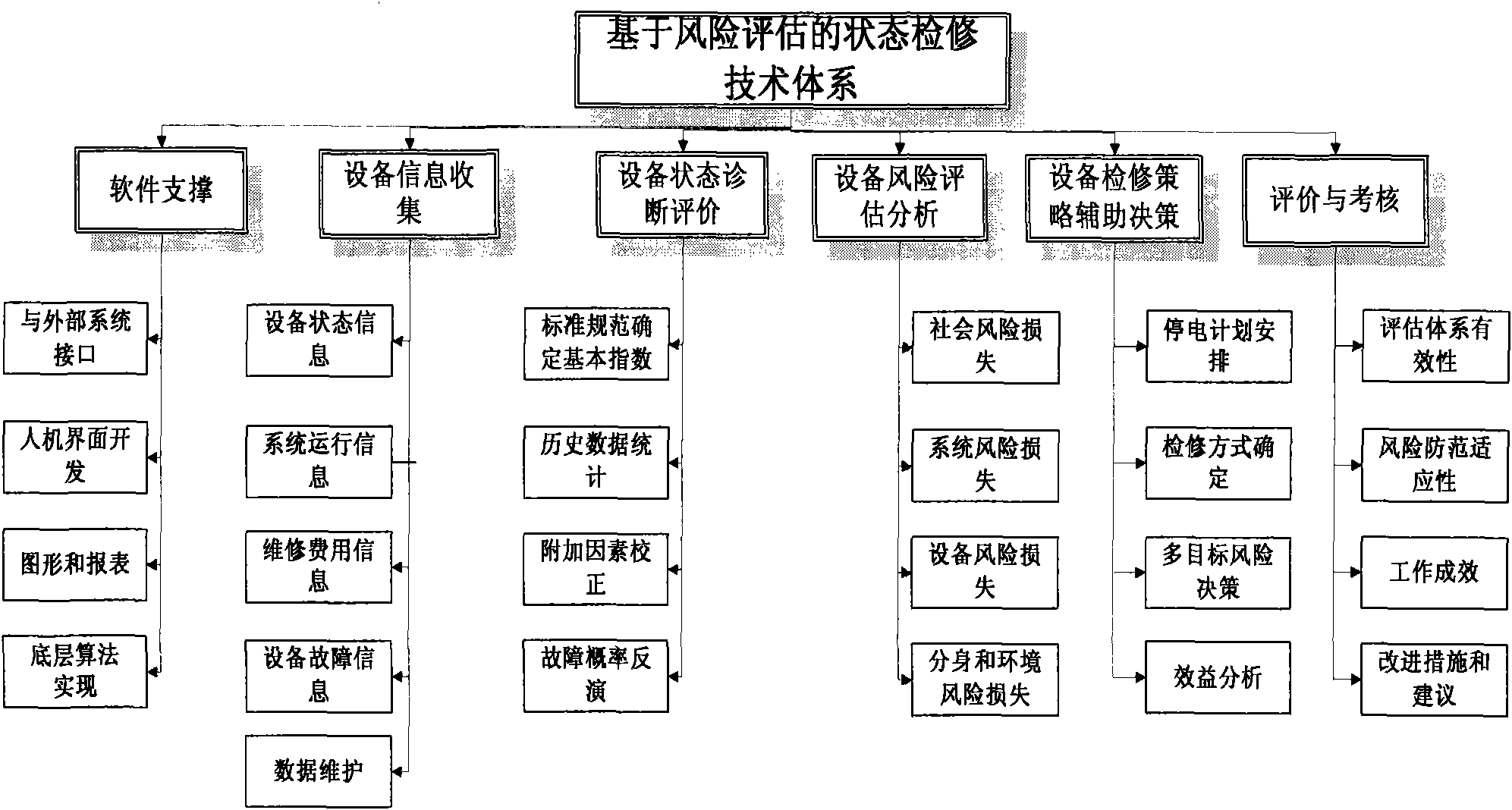
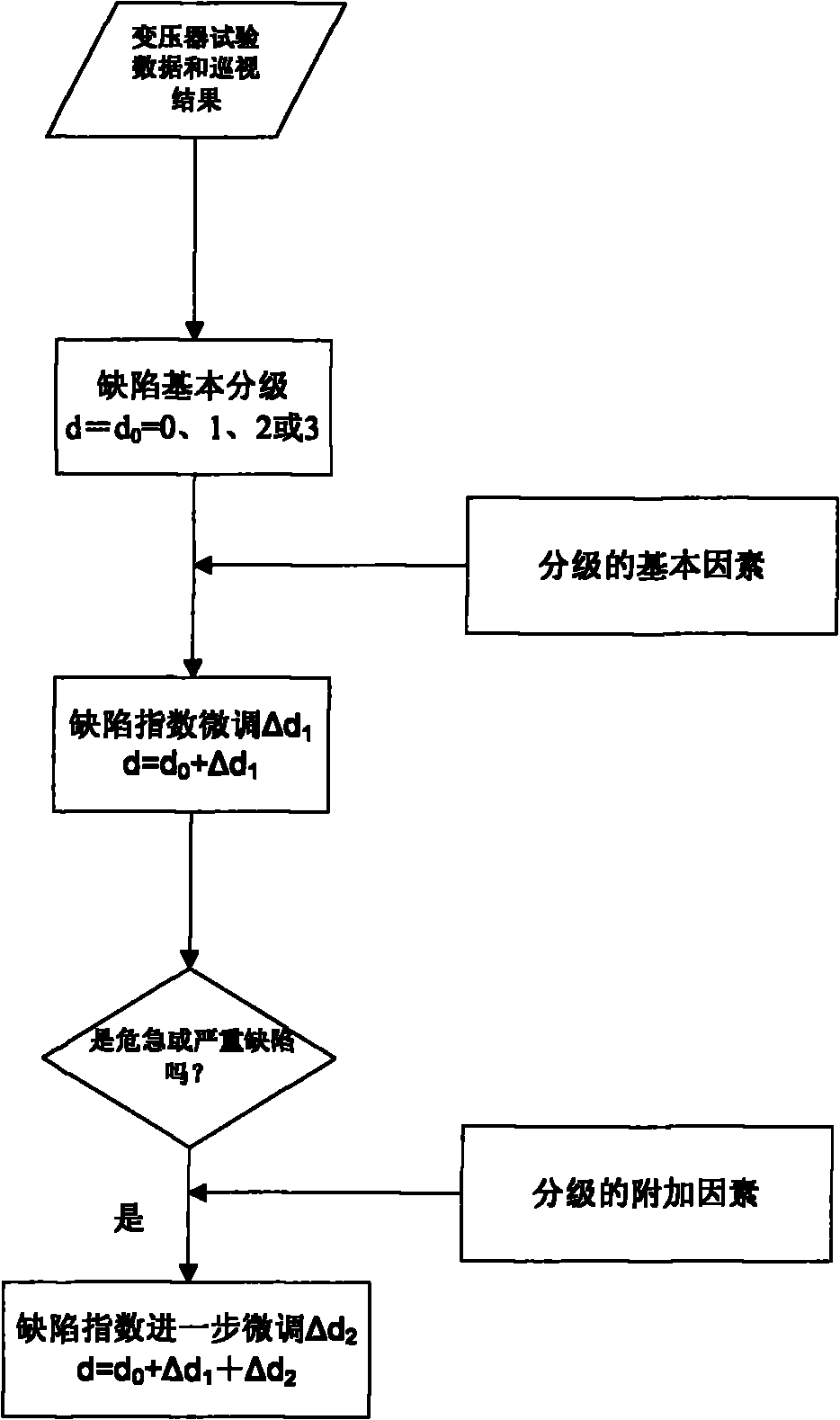
Power transmission and transformation equipment state overhauling system based on risk evaluation
InactiveCN101859409ARealize quantitative scientific evaluationAvoid influenceInstrumentsAc network circuit arrangementsData informationPower grid
The invention discloses a power transmission and transformation equipment state overhauling system based on risk evaluation. The system consists of a software supporting module, an equipment information collecting module, an equipment state diagnosing and evaluating module, an equipment risk evaluating and analyzing module, an equipment overhauling strategy auxiliary decision making module and an evaluating and checking module. The six modules are sequentially connected and mutually supported from bottom to top to form a pyramid type decision making flow path. The invention implements one set of complete system on the data information and equipment maintenance of a power network, makes a dynamic, timely, high-reliability and economic maintenance plan for the power transmission and transformation equipment under the condition of carrying out quantitative calculation on risks, greatly reduces the unnecessary maintenance, decreases the equipment damage caused by maintenance, saves the maintenance and management cost, and enhances the reliability of the power network.
Owner:ELECTRIC POWER RES INST OF GUANGXI POWER GRID CO LTD +1
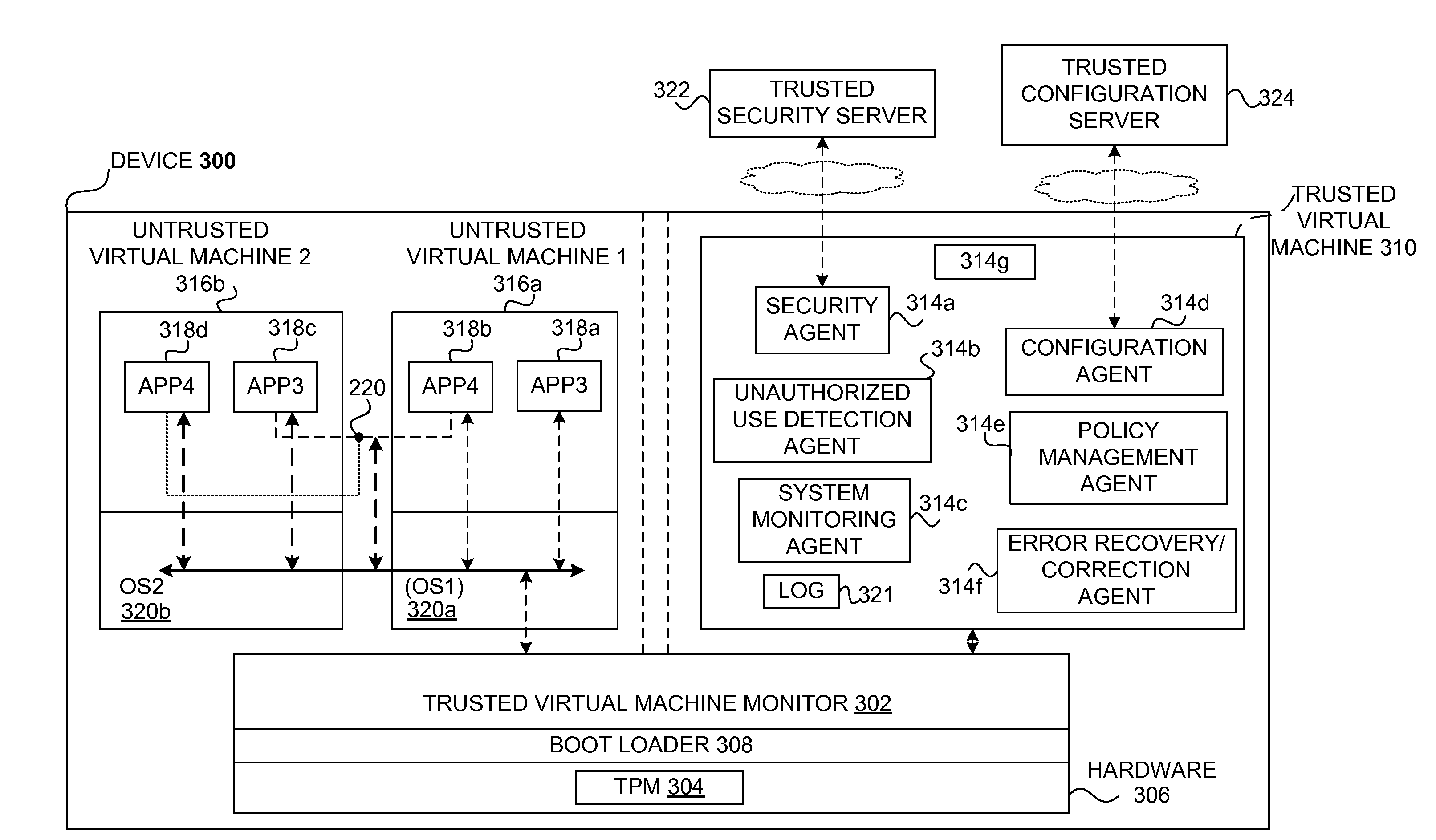
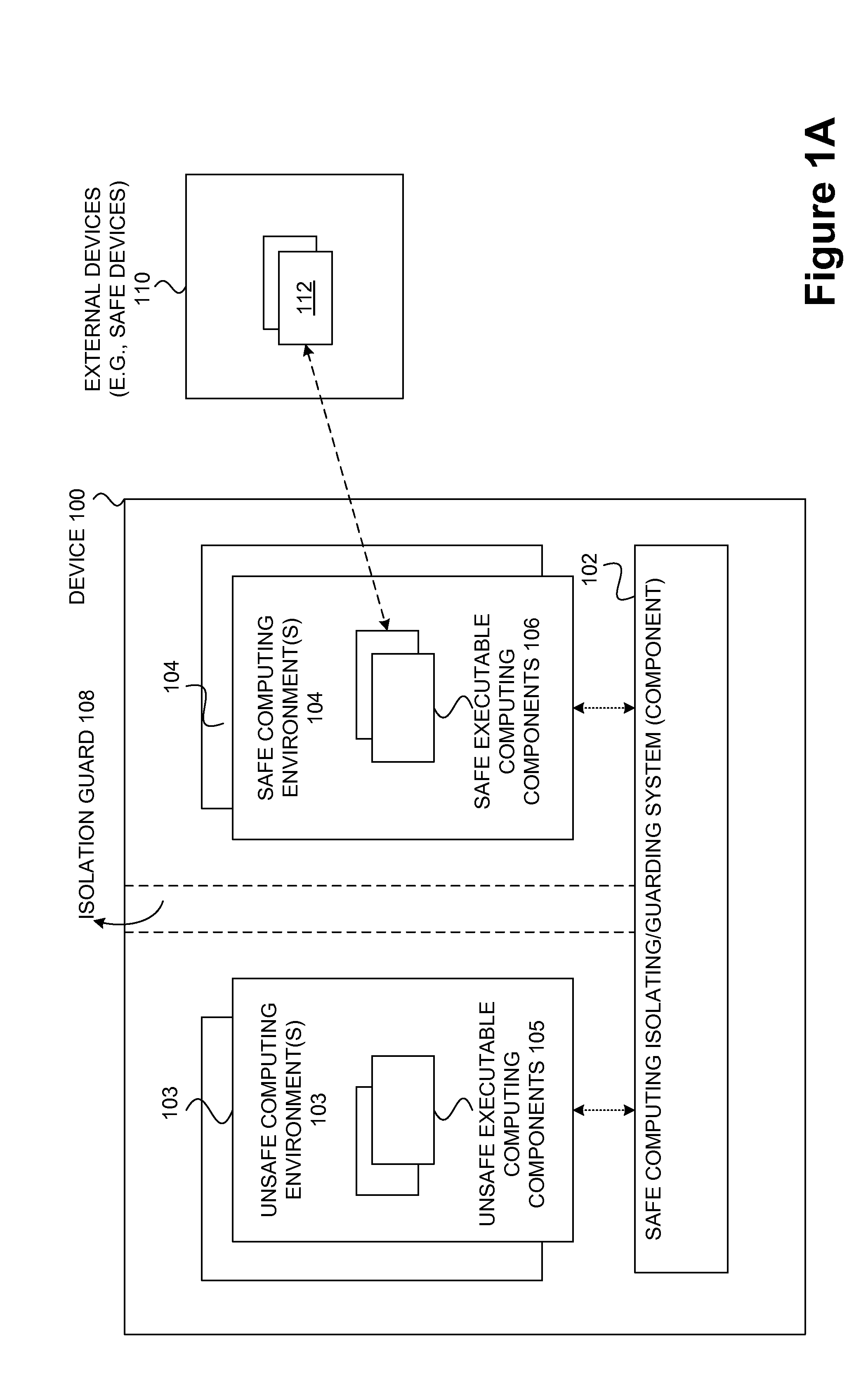
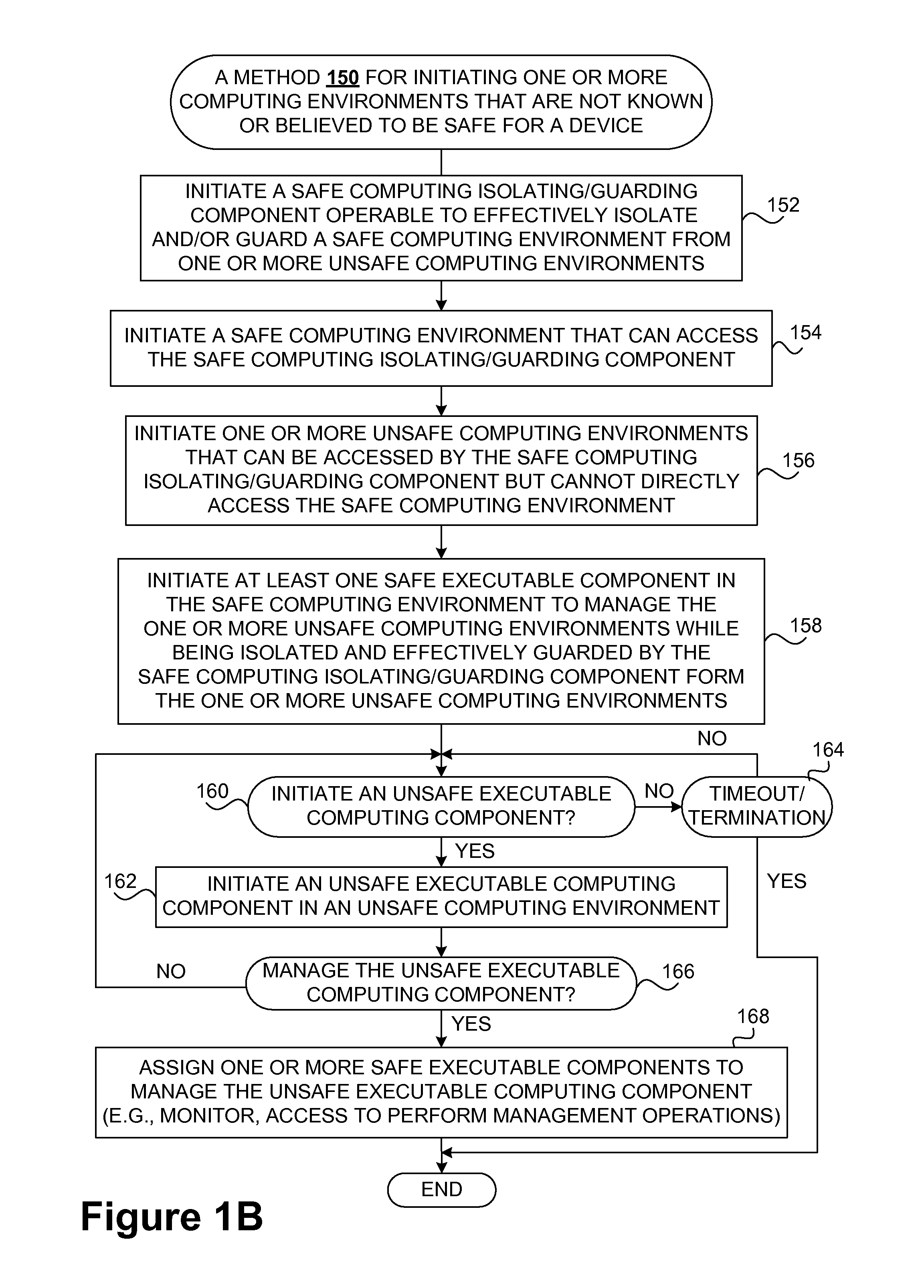
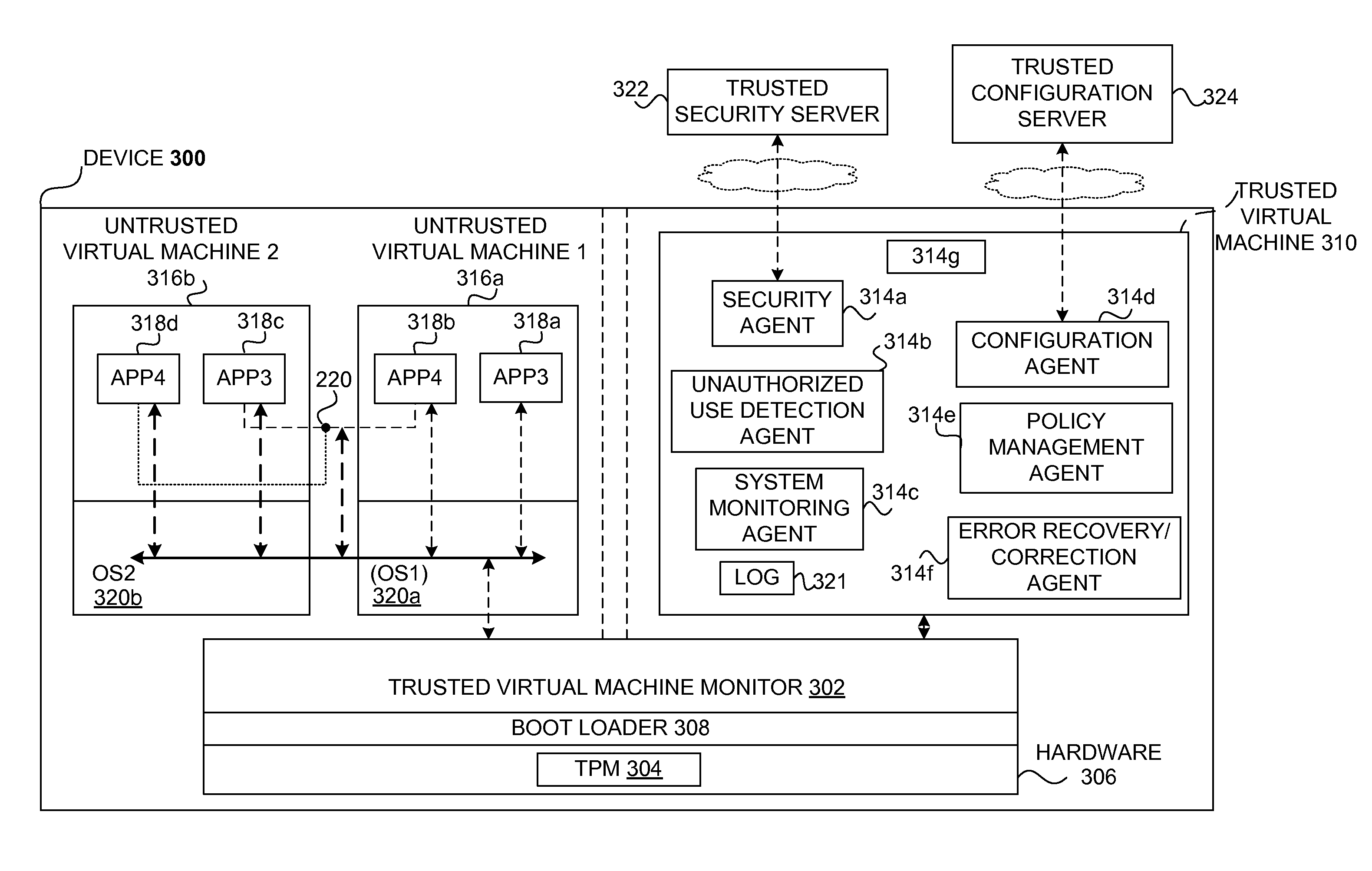
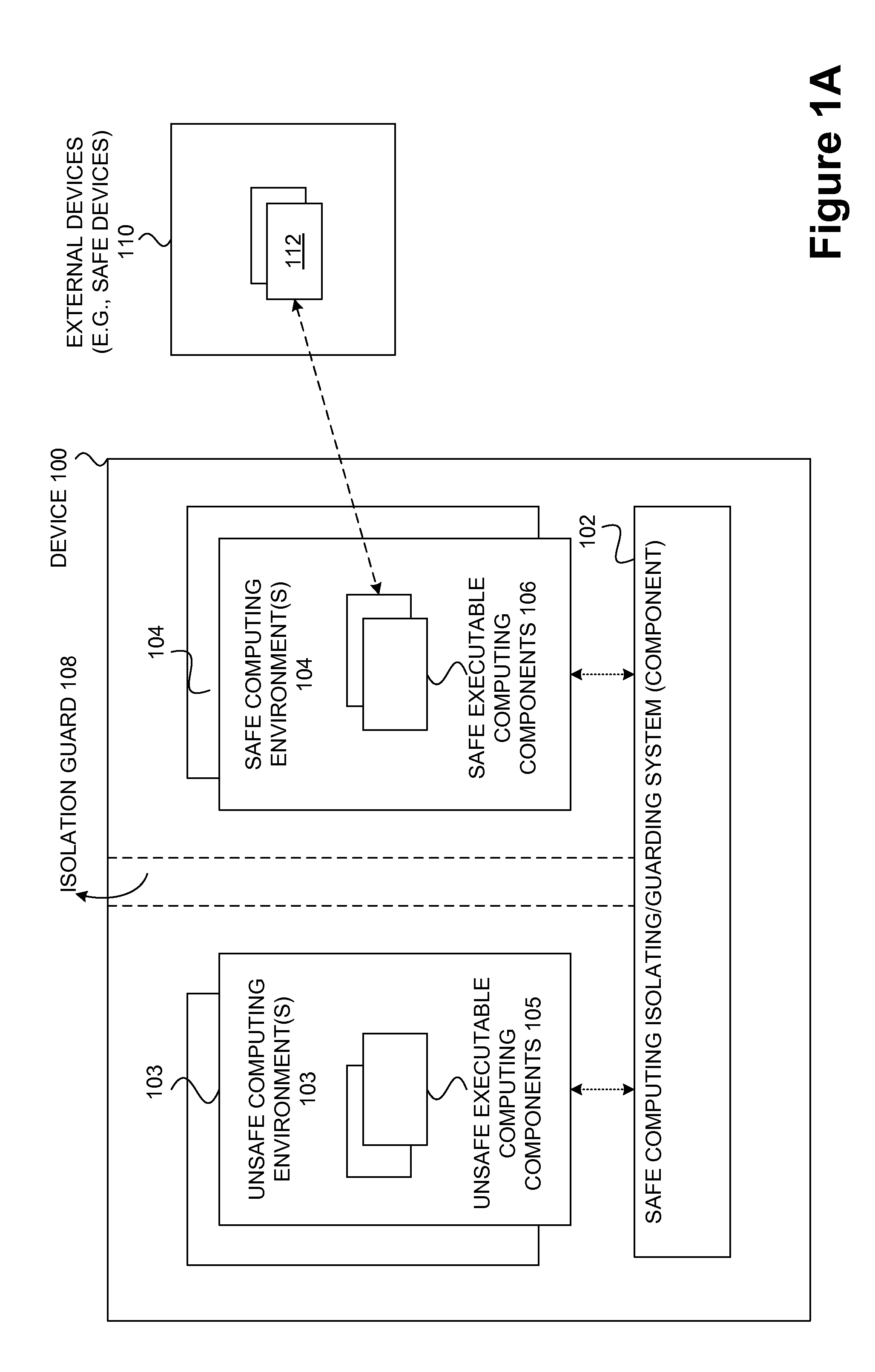
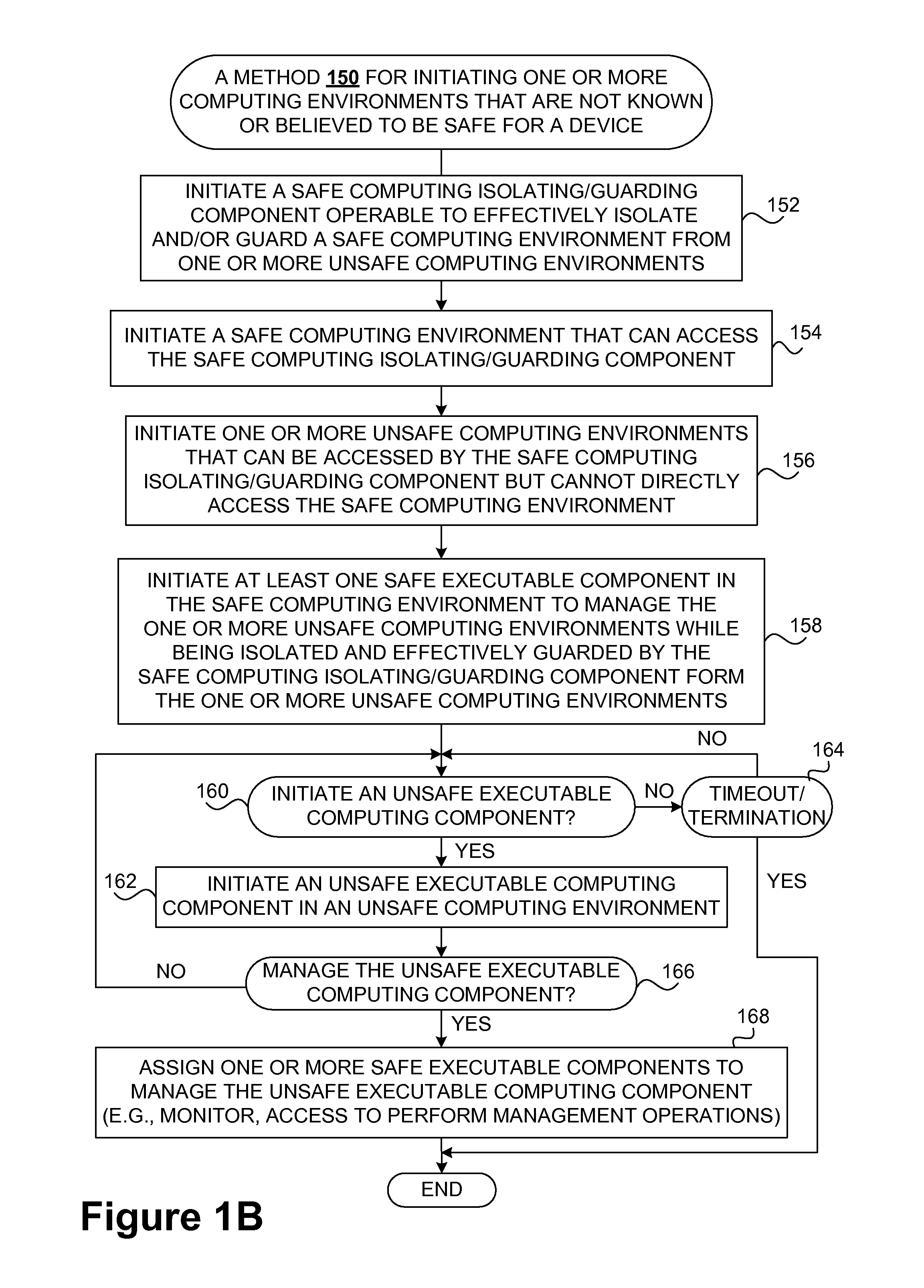
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
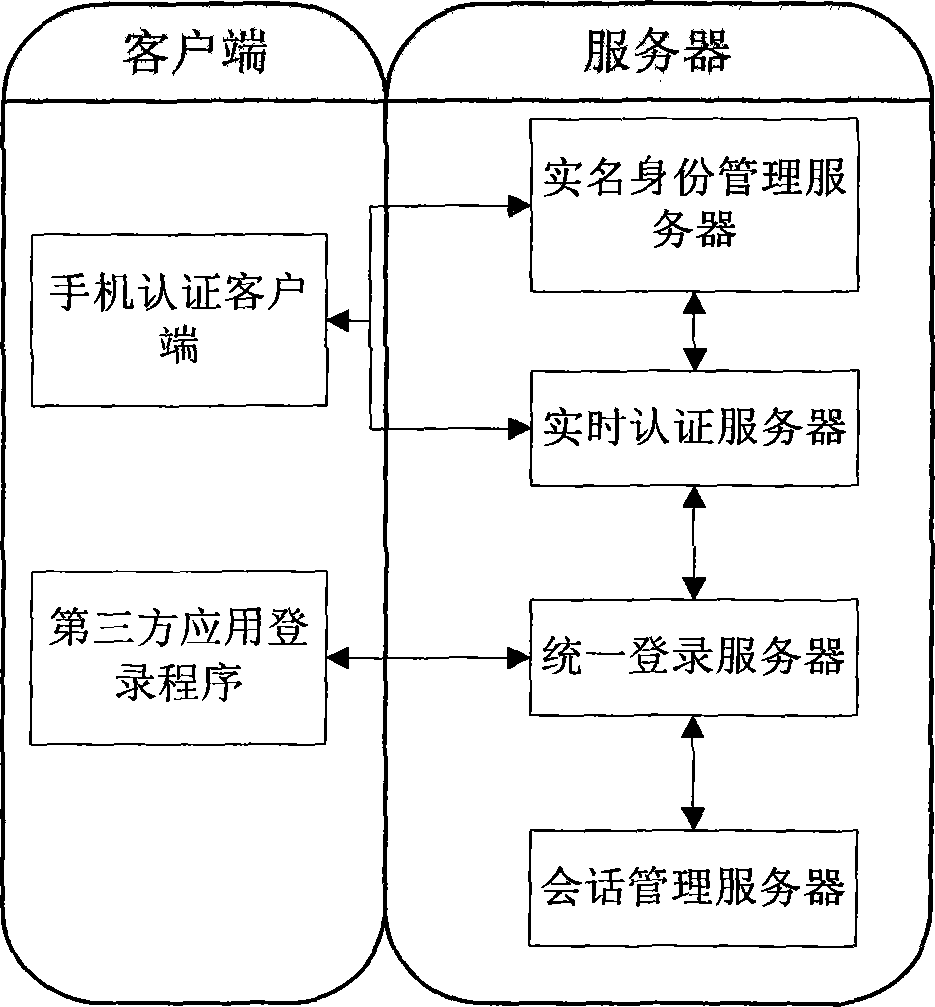
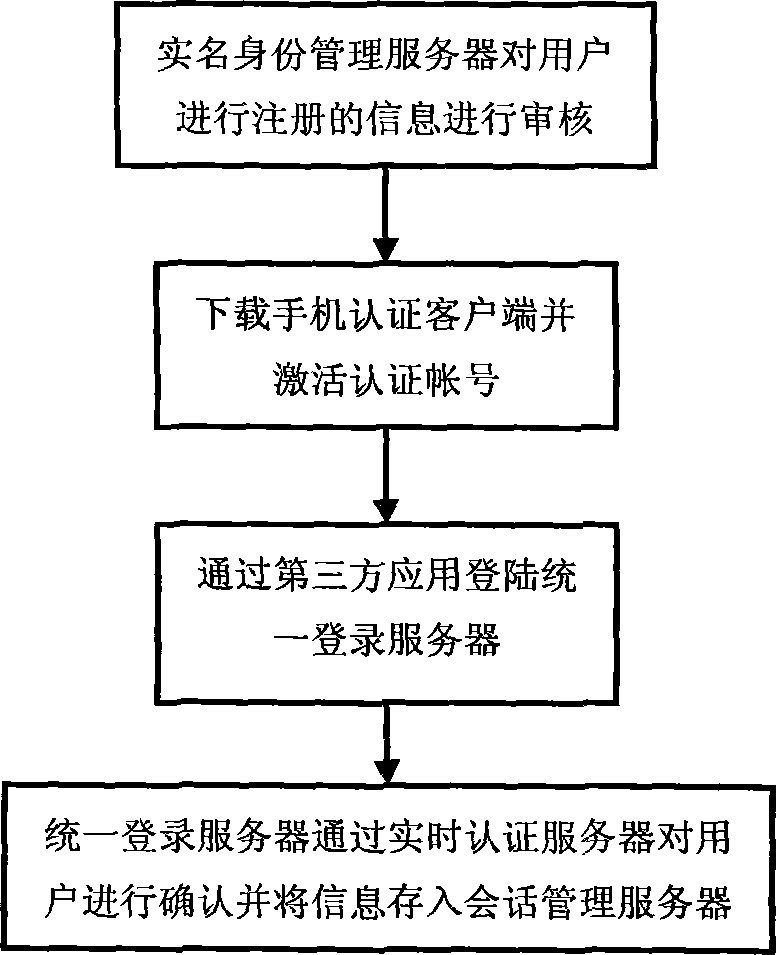
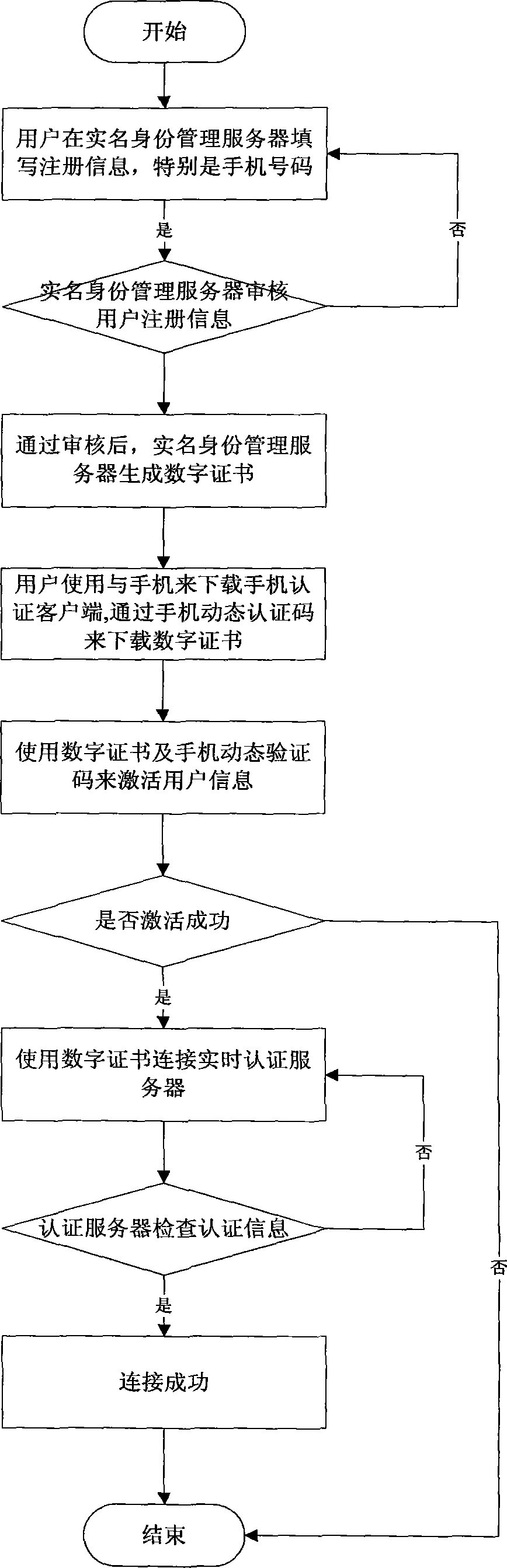
Real-name authentication safe login method and system based on cell phone number
InactiveCN103269270AImprove securityEasy to manageUser identity/authority verificationSecurity arrangementMobile Telephone NumberSession management
The invention discloses a real-name authentication safe login method and system based on a cell phone number, and relates to the field of internet real-name authentication. The method includes the steps that a real-name identity management server carries out verification and registration according to identity information provided by a user; the user activates an account number through cell phone dynamic verification codes and a digital certificate after passing the verification; a third-party application applies for a login service, a request is sent to a unified login server and transmitted to a real-time authentication server, the real-time authentication server sends the request to the user for validation, the unified login server adjusts whether the third-party application is allowed to log in according to a result returned to the unified login server, and the unified login server saves session information in a session management server and returns the information to the third-party application if the third-party application is allowed to log in. The real-name authentication safe login method and system based on the cell phone number solve the problem that the user relies on user information in different applications, can guarantee safety of the information through cell phone authentication and brings convenience to management for network management departments, the user does not need to maintain personal information again in all the applications, convenience is brought to the user, and worry about privacy disclosure of the user is reduced.
Owner:安徽杨凌科技有限公司
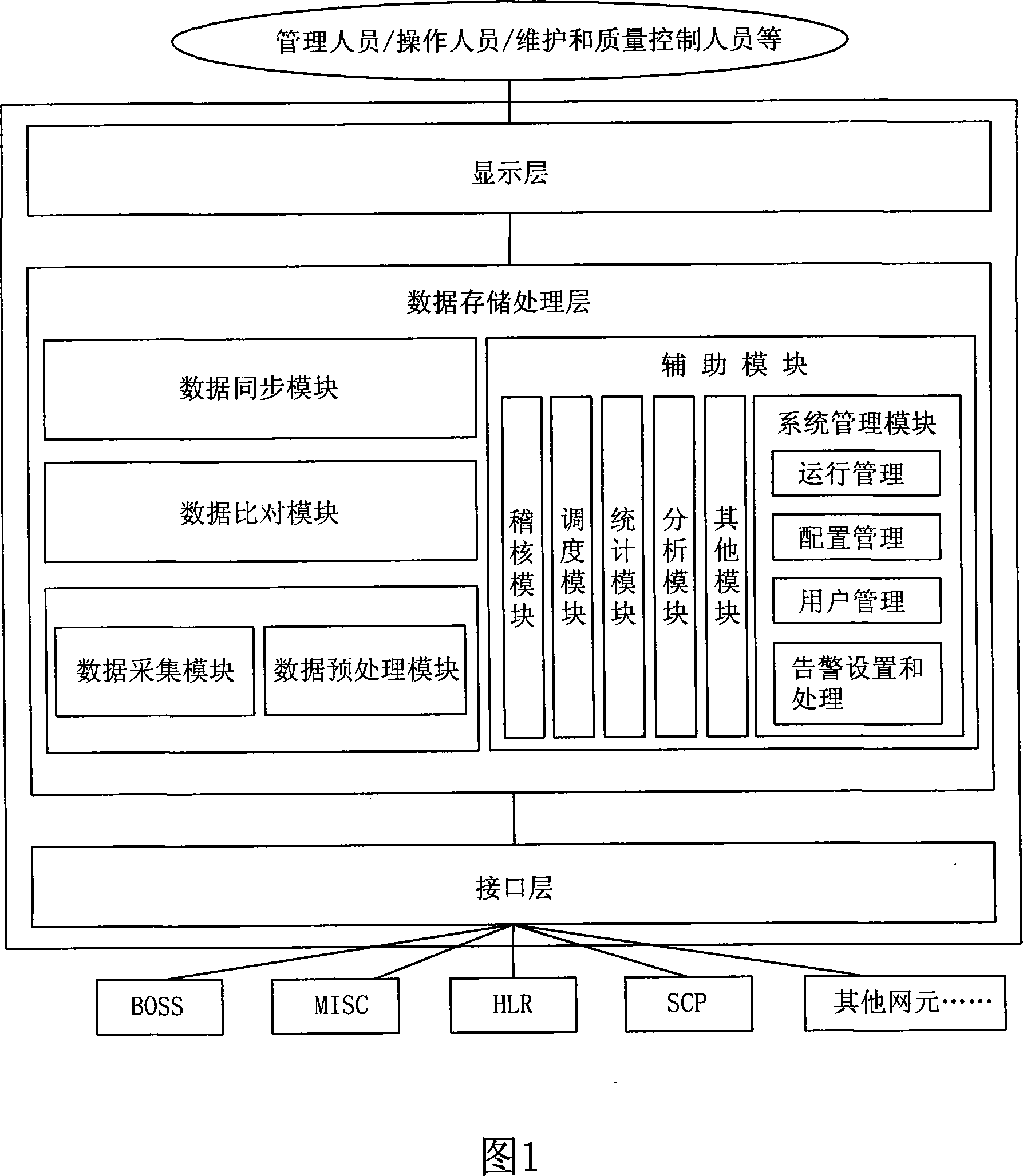
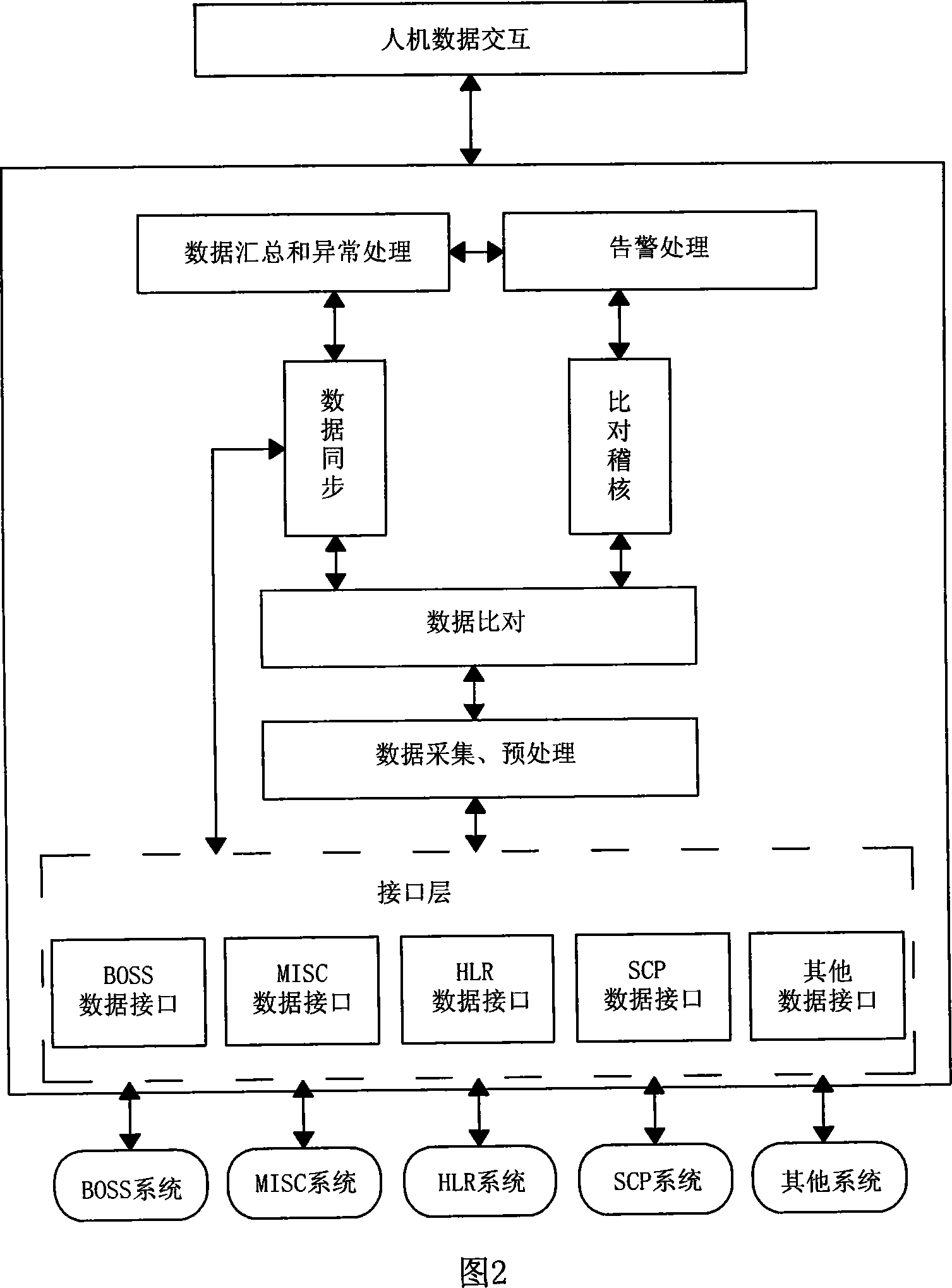
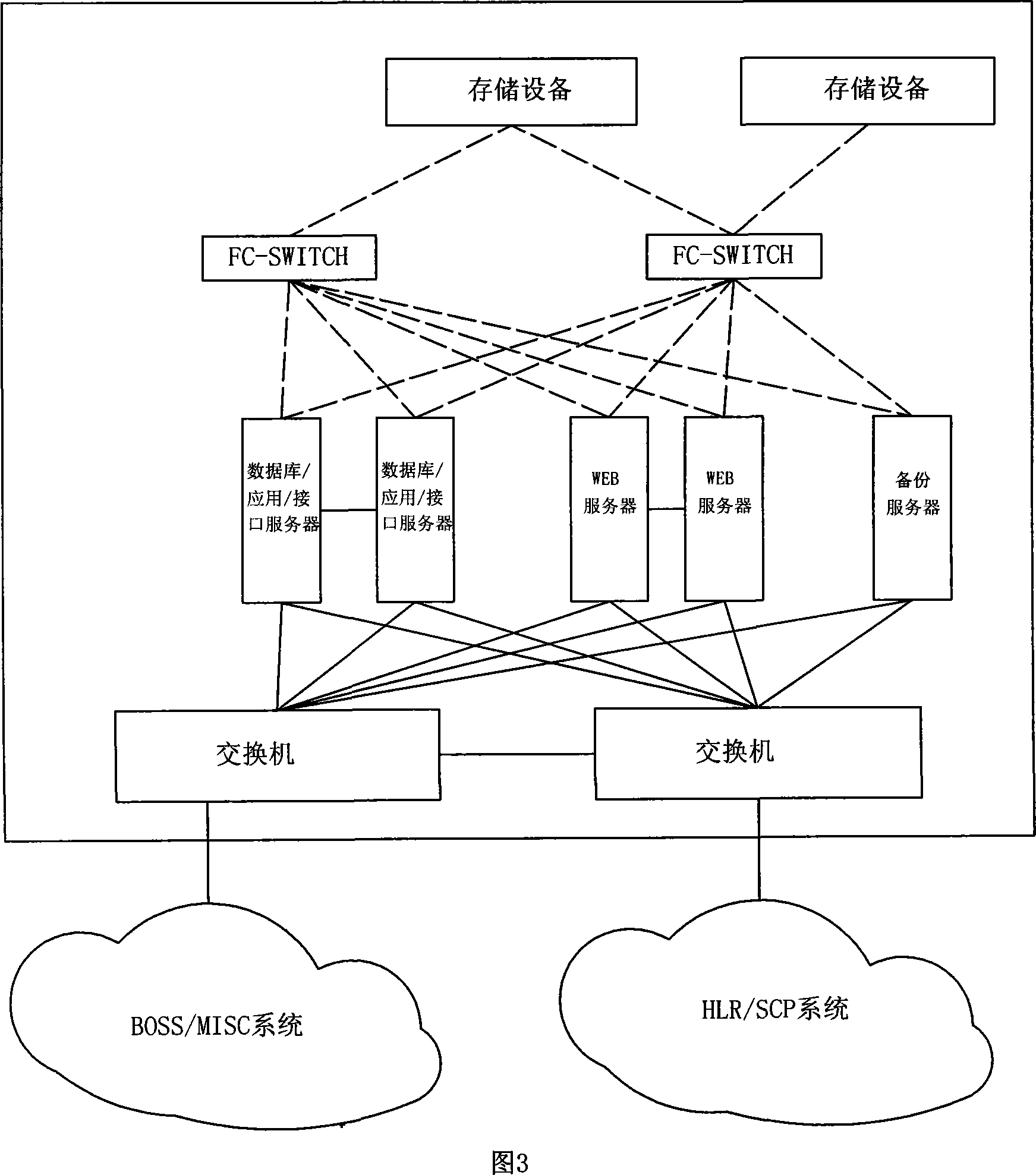
System and method for synchronizing comparison of data consistency
ActiveCN101094051AAvoid complaintsImprove effectivenessSynchronisation signal speed/phase controlData switching networksData synchronizationDifference list
It includes display layer, data storage / procession layer (SP) and system interface layer (SI). SP includes data collect module (DL), data pre-processing module (DP), data comparison module (DM), data sync, module (DS) and assistant module. Via SI, the business backup and bearing nets (BBB) realize mutual comm. between net elements (NE). From BBB, DL collects NE data requiring keeping coincident. DP / DM pre-processes and compares these data. Non-coincident data are recorded in the error list. According to availability test rule, DS verifies availability of data difference, generates corresponding synchronization data against valid data difference base on sync. rule and sends to related NE to keep coincidence of data between NEs. This invention raises data comparison synchronization level, system running efficiency and resource utilization. It ensures accuracy and coincidence of system data. It extensively is applied in multi-NE cooperation fields, such as comm., insurance and banking.
Owner:CHINA MOBILE GROUP SICHUAN
Enterprise informatization management system
InactiveCN104992308AEfficient managementStandardized management management modeResourcesCapability managementInformatization
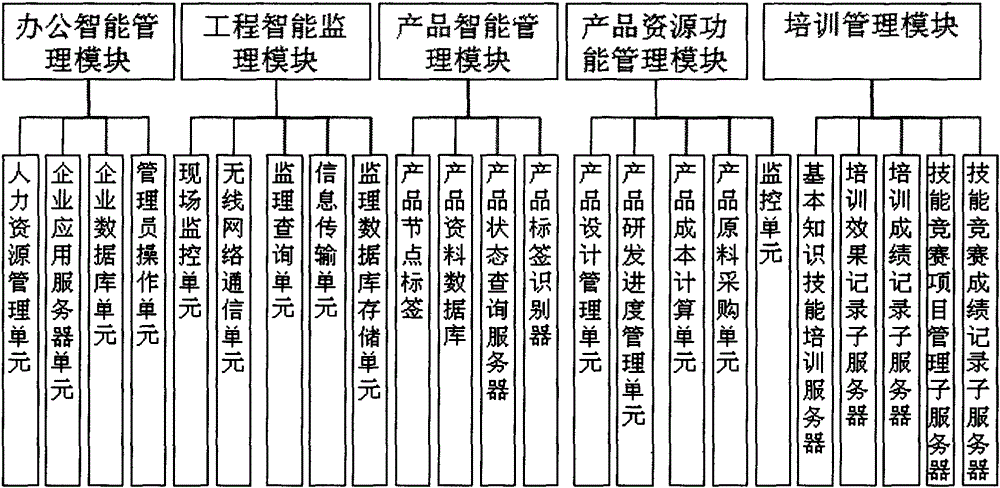
The invention provides an enterprise informatization management system which comprises an office intelligent management module, an intelligent project supervision module, an intelligent product management module, a product resource function management module and a training management module. The system not only can realize automatic unification and query of attendance, leave, resumption from leave and payment of employees, but also can realize unified management and query of periodical management and maintenance of the products, specifically comprising purchase of raw materials, product research and development, product production, product sale and later maintenance and repair of the products. According to the enterprise informatization management system, complete-course tracking and service of each product can be realized, not only management of employee information is guaranteed, but also effective management of the products is realized, thereby helping to manage the management mode of an enterprise in a standard manner, improving management efficiency, reducing management cost and allowing the enterprise informatization management system to be more perfect.
Owner:刘鸣
Browser-based mobile phone middleware
ActiveCN101930366ACross-platform deployment guaranteeGuarantee managementSubstation equipmentSpecific program execution arrangementsMiddlewareComputer science
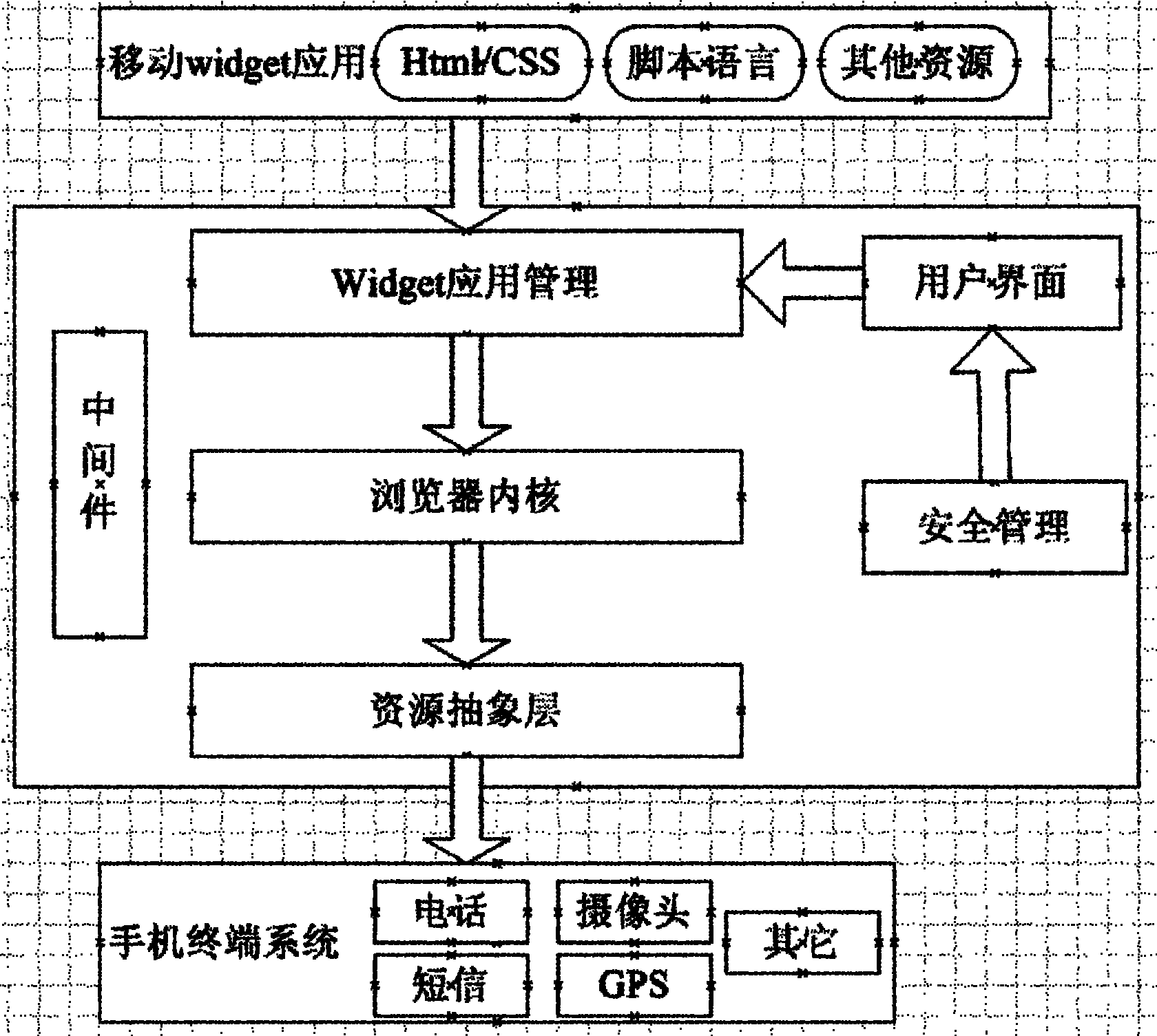
The invention discloses a browser-based mobile phone runtime system. The mobile phone middleware can be deployed on multiple mobile phone terminal platforms by integrating a browser kernel; and the mobile phone middleware can resolve and render mobile Widget application and interact with a user, and provides support for the mobile Widget by encapsulating the access capability on local mobile phone resources and Internet resources. The Widget application and the runtime system can adjust the distribution mode aiming at the service demand, can integrate the distribution, and also can separately perform distribution. The invention breaks through the mode that the traditional mobile phone terminal application performs development by using platform native languages and technology, and radically provides an implementation method for browser technology-based cross-platform mobile phone application so as to realize the thought of 'one-time development and multi-place deployment'.
Owner:WUHAN TIANYU INFORMATION IND
Group message displaying method and apparatus for instant messaging application
ActiveCN104980345AImprove flexibility and accuracyIncrease flexibilityData switching networksContactorMultimedia
The embodiment of the present invention provides a group message displaying method and apparatus for instant messaging application. The method includes dividing a plurality of contactors in a group of the instant messaging application into at least two groups, and dividing the message displaying interface of the group into at least two displaying areas. When messages are received from the at least two groups of contactors, the messages from the at least two groups of contactors are displayed on the at least two displaying areas respectively.
Owner:ZHEJIANG YIXIN TECH
Virtual encryptor device, financial encryptor and method of encrypting message
InactiveCN103634339AGuarantee managementTimely processingTransmissionSoftware simulation/interpretation/emulationConfiguration Management (ITSM)Computer engineering
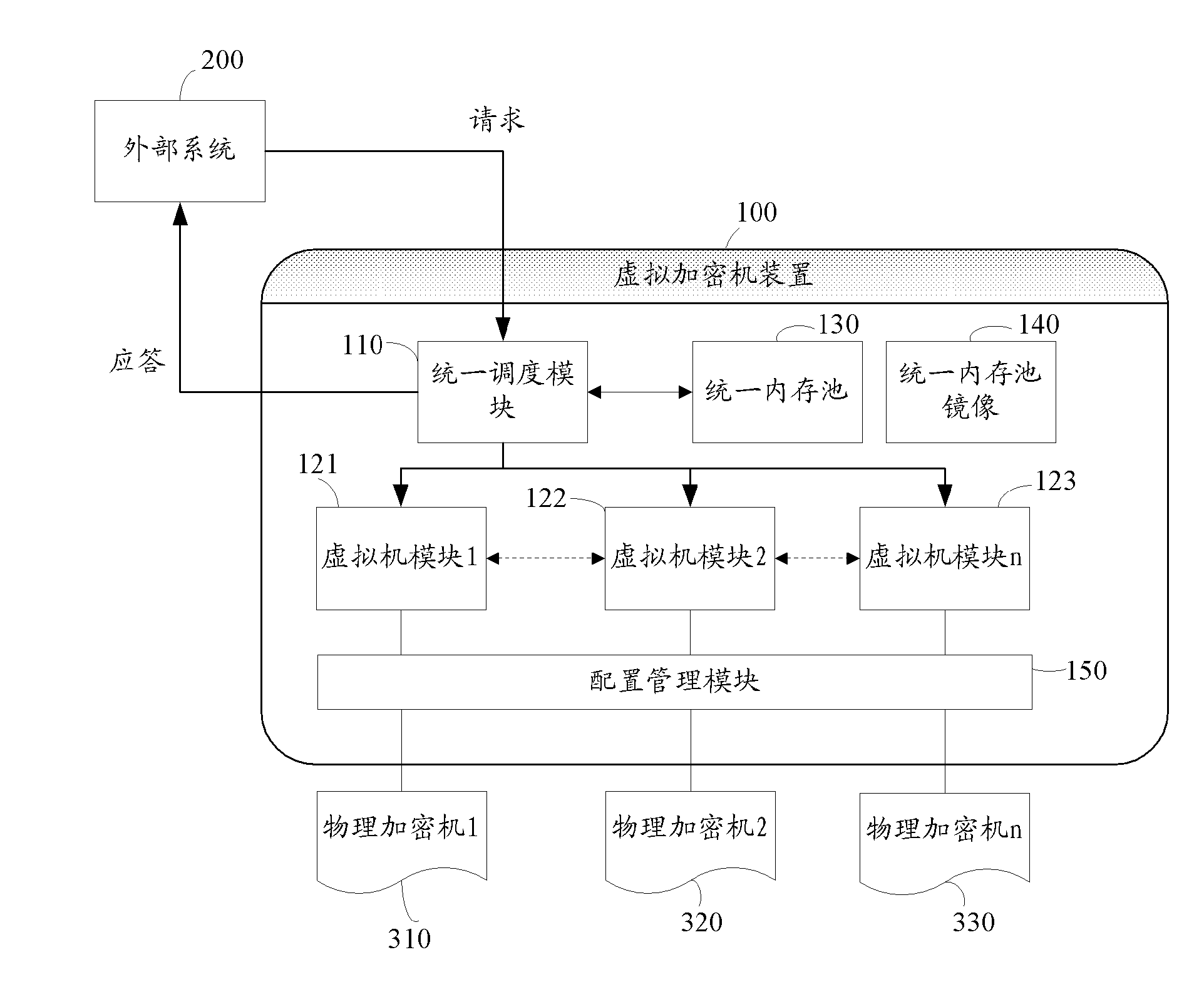
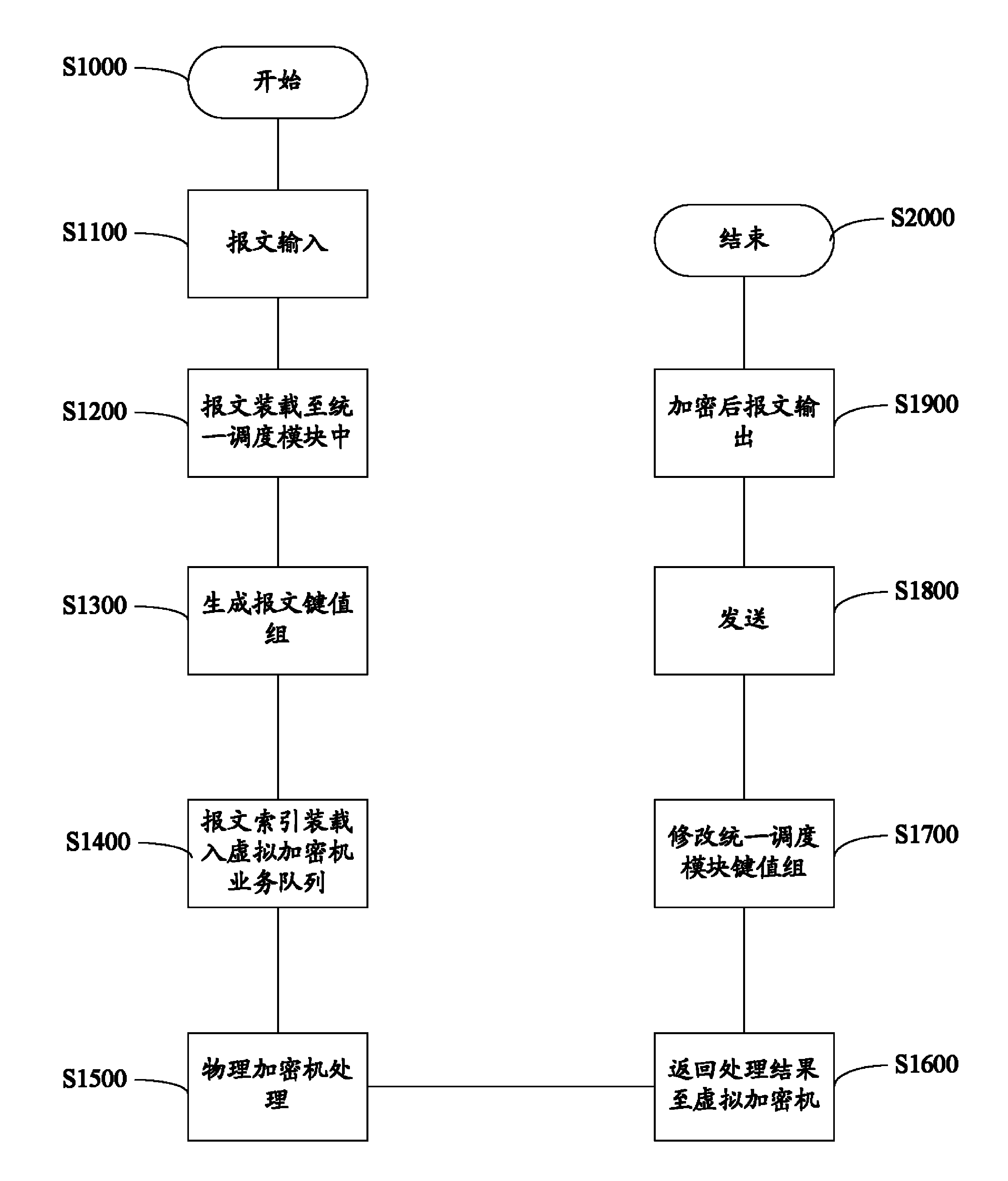
The invention discloses a virtual encryptor device including one or more virtual machine modules; a configuration management module for configuring a corresponding virtual machine module for each physical encryptor; and a unified scheduling module for receiving a message to be encrypted from an external system. A key value group matrix of the message to be encrypted is generated according to a scheduling algorithm; and based on the key value group matrix, dual processing load of the physical encryptors and the message to be encrypted is determined and the virtual machine module is selected for preprocessing the message to be encrypted. The invention also discloses a financial encryptor including the virtual encryptor device and a method of encrypting a message by use of the virtual encryptor device.
Owner:CHINA UNIONPAY
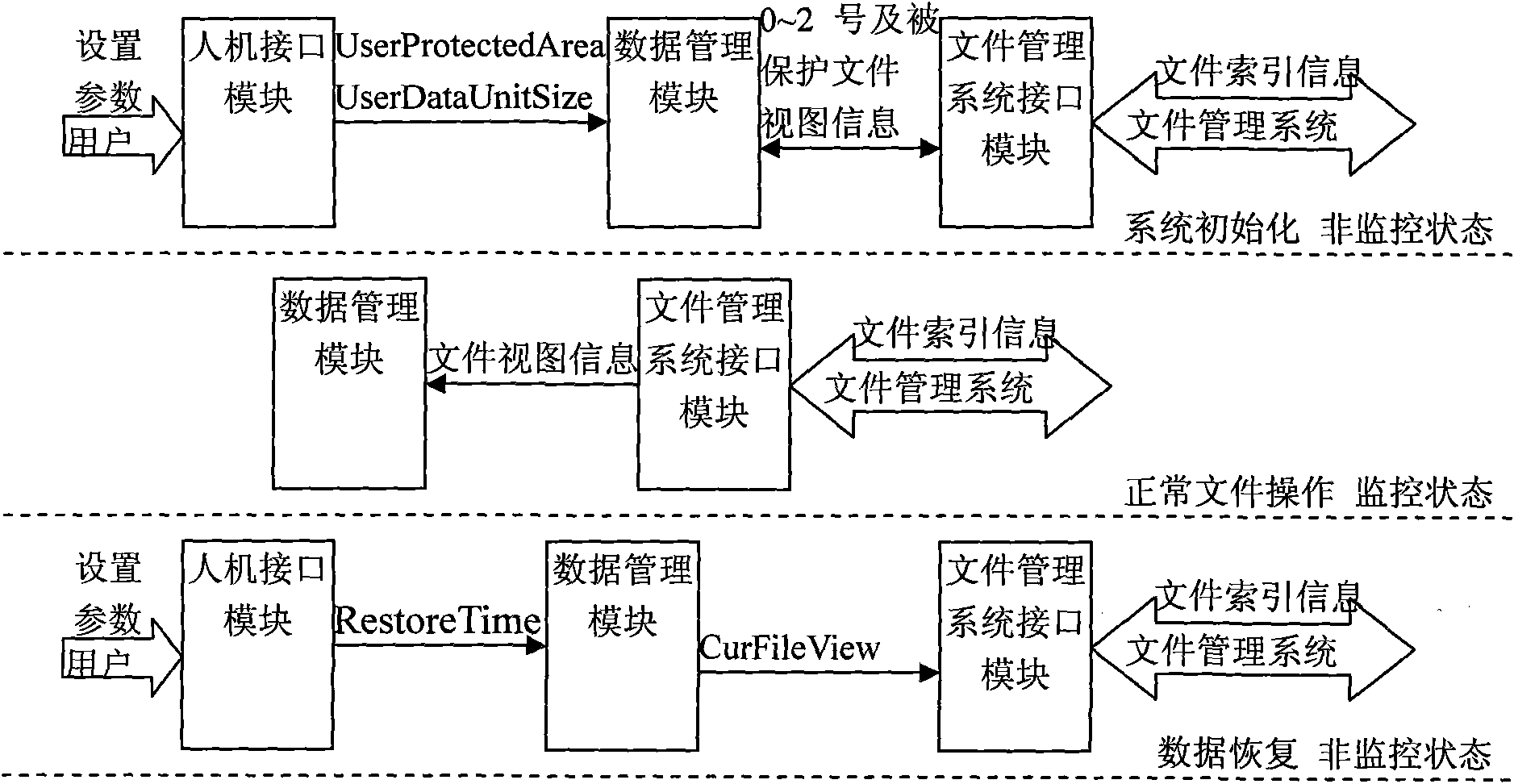
System and method for protecting continuous data for establishing data view based on time stamp
InactiveCN101576834AGuarantee managementImprove protectionRedundant operation error correctionSpecial data processing applicationsData viewRelational database management system
The invention relates to a system and a method for protecting continuous data for establishing data view based on time stamp, and belongs to the field of data protection. The method comprises the following steps: by using a thought of establishing different views according to a database aiming at different user requirements in a relational database management system, and by recording storage information, change information and change time of a data unit, establishing a storage and change database of the protected data; and recovering data through a mode of providing a data view established based on a time node set by a user to a file management system as index basis. The system and the method have the advantages of achieving the aims of effectively protecting data and improving the stability and reliability of the system, and ensuring that all protected data are managed by the file management system.
Owner:XIAN BLUE OCEAN SOURCE INFORMATION TECH
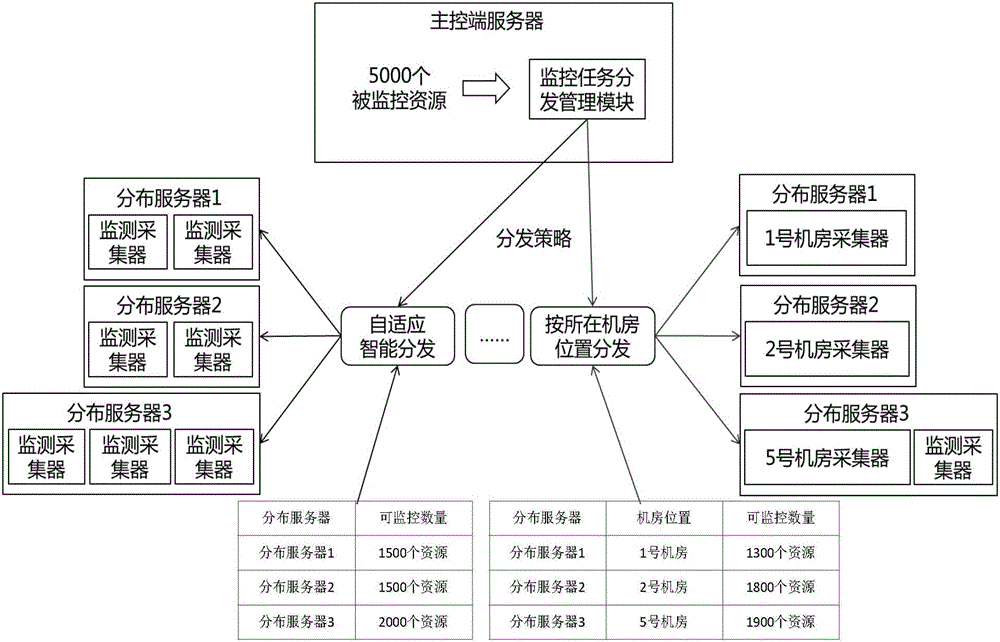
Data center monitoring system and method
InactiveCN106209482AGuaranteed uniform deploymentGuarantee managementData switching networksTerminal serverData center
The invention discloses a data center monitoring system and method. The system comprises a master control terminal server, wherein the master control terminal server comprises a monitoring task distribution management module which is used for distributing a monitoring task to a corresponding distribution server according to a selected monitoring task distribution strategy; a scheduling management module used for allocating the monitoring task to a monitoring collector of the corresponding distribution server, and processing received monitoring data; a distribution server management module used for supervising each distribution server through heartbeat connection; the distribution server comprises the monitoring collector, which adds the received monitoring task in a polling queue, orderly starts the monitoring process of the corresponding monitoring task to perform data acquisition in sequence, performs analysis and process and alarm status judgment on the data to obtain the monitoring data, and transmits the monitoring data to a database server and the scheduling management module; and the database server receives data transmitted by the monitoring collector. Therefore, the data center monitoring system provided by the invention improves the monitorable capacity of large-scale data center monitoring, and guarantees the allocation and management of the distribution server.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
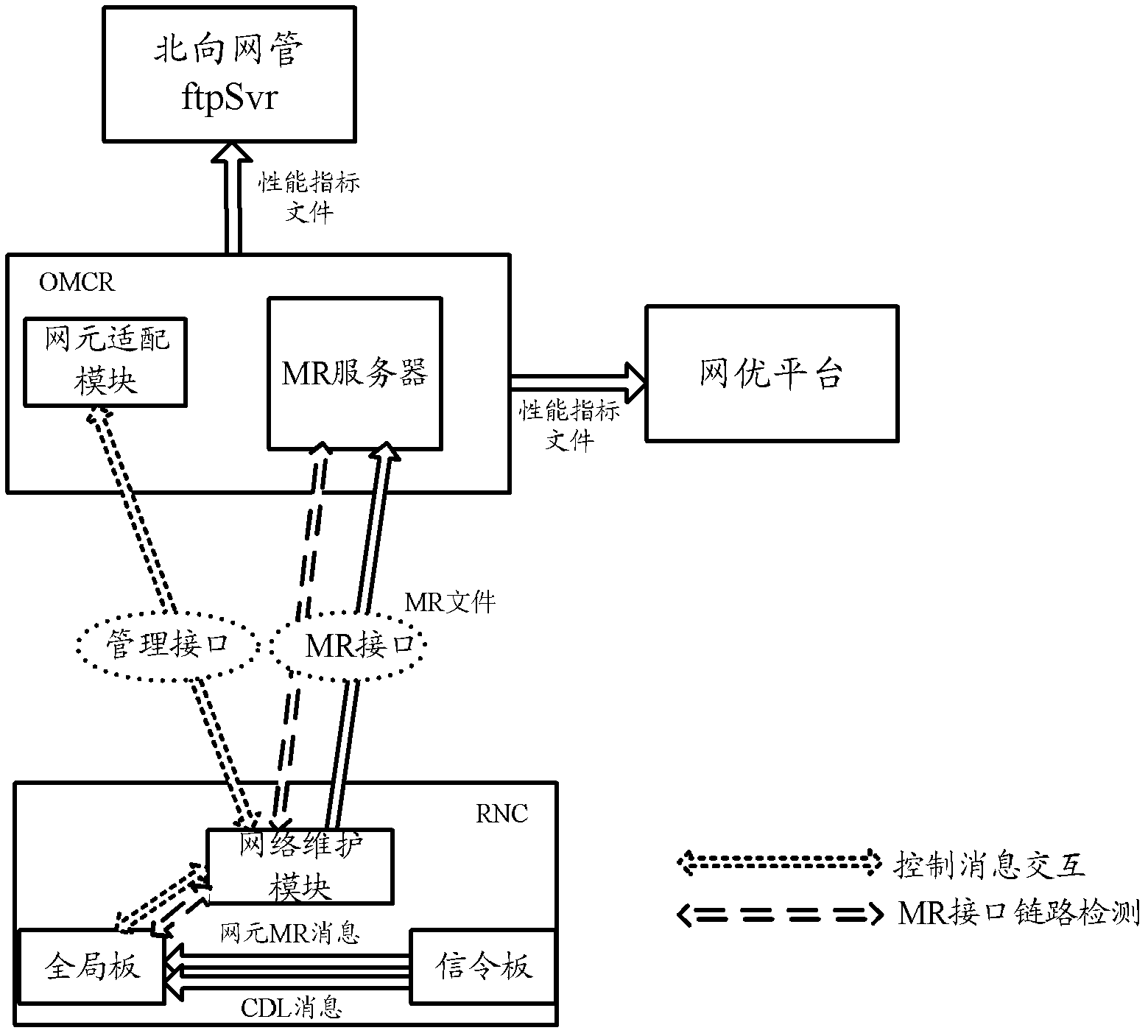
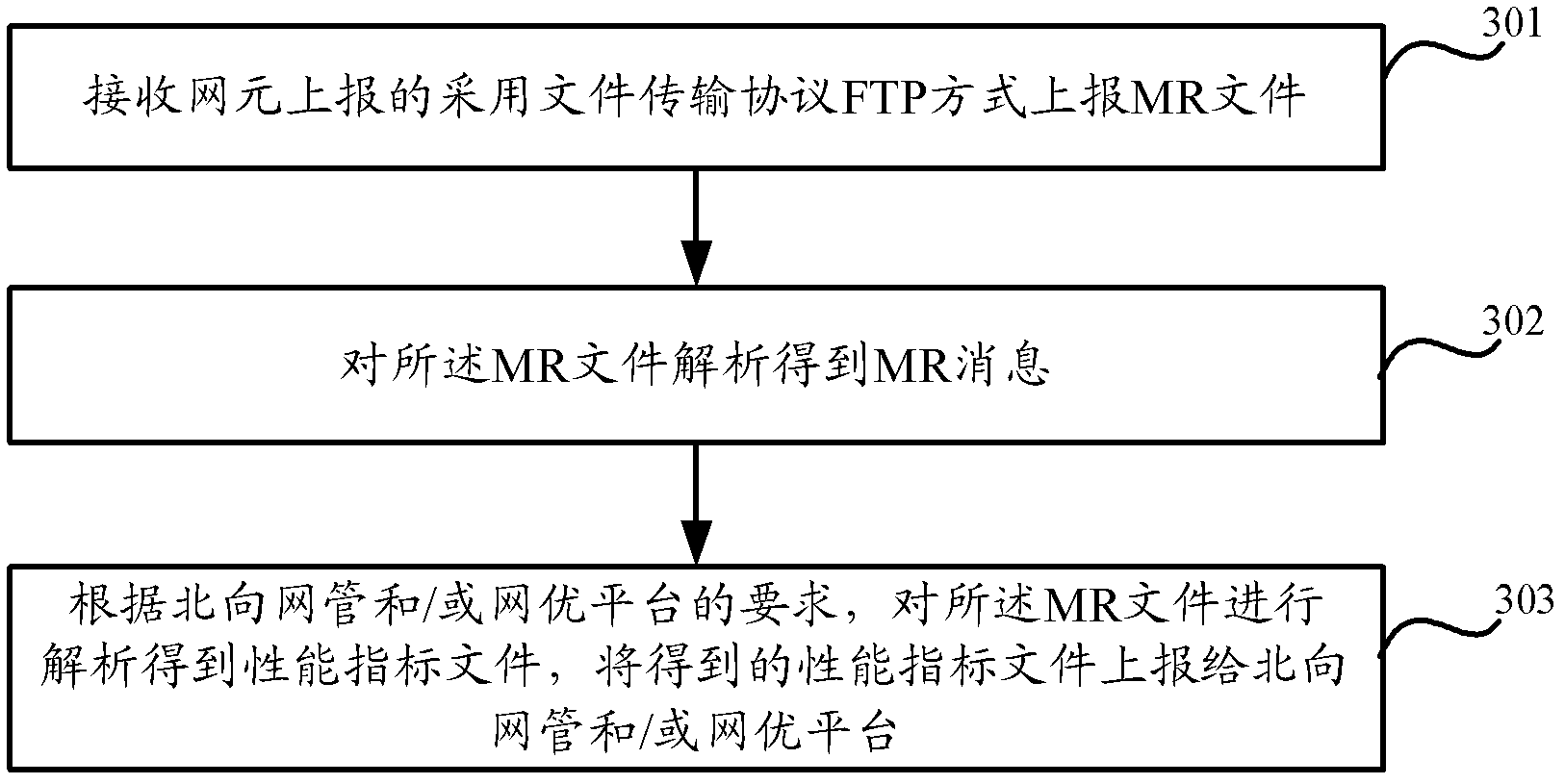
Network element and method for uploading MR (Measure Report) messages by network element
ActiveCN102571451AReduce performance pressureImprove processing powerData switching networksFile transferNetwork element
The invention discloses a network element and a method for uploading MR (Measure Report) messages by the network element. The method comprises the following steps of: receiving the MR messages and CDL (Call Detail Logs) messages which are reported by a terminal and a base station; independently forming an MR file from the received MR messages; when determining that an MR interface link between the network element and an MR server is normal, reporting the MR file to the MR server by adopting a mode of an FTP (File Transfer Protocol), so that the MR server generates a performance index file according to the MR messages in the MR file. According to the network element and the device disclosed by the invention, the processing capability of the network element which receives the reported MR messages is improved; the packet loss problem of the MR messages is ensured not to exist; the correctness of the performance index files obtained by a network optimization platform and a northbound webmaster is powerfully guaranteed; and the processing efficiency of the northbound webmaster on the performance index files is effectively promoted.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Virtual resource management method and device and computer readable storage medium
ActiveCN108337110AIncrease success rateGuaranteed to be properly maintainedNetwork traffic/resource managementData switching networksVirtualizationNetwork Functions Virtualization
The invention provides a virtual resource management method and device and a computer readable storage medium. The virtual resource management method comprises the steps that a virtual resource processing device collects virtual resource data from network function virtualization arrangement and management; and virtual resource related processing is executed according to the virtual resource data.According to the scheme, by collecting the virtual resource data and executing virtual resource related processing, concentrated management on virtual resources is achieved, and the efficiency of virtual resource related processing is improved.
Owner:ZTE CORP
An intelligent bus system based on communication and grid computing technology
InactiveCN101123551ALess investmentLow costData switching by path configurationSupercomputerInformation resource
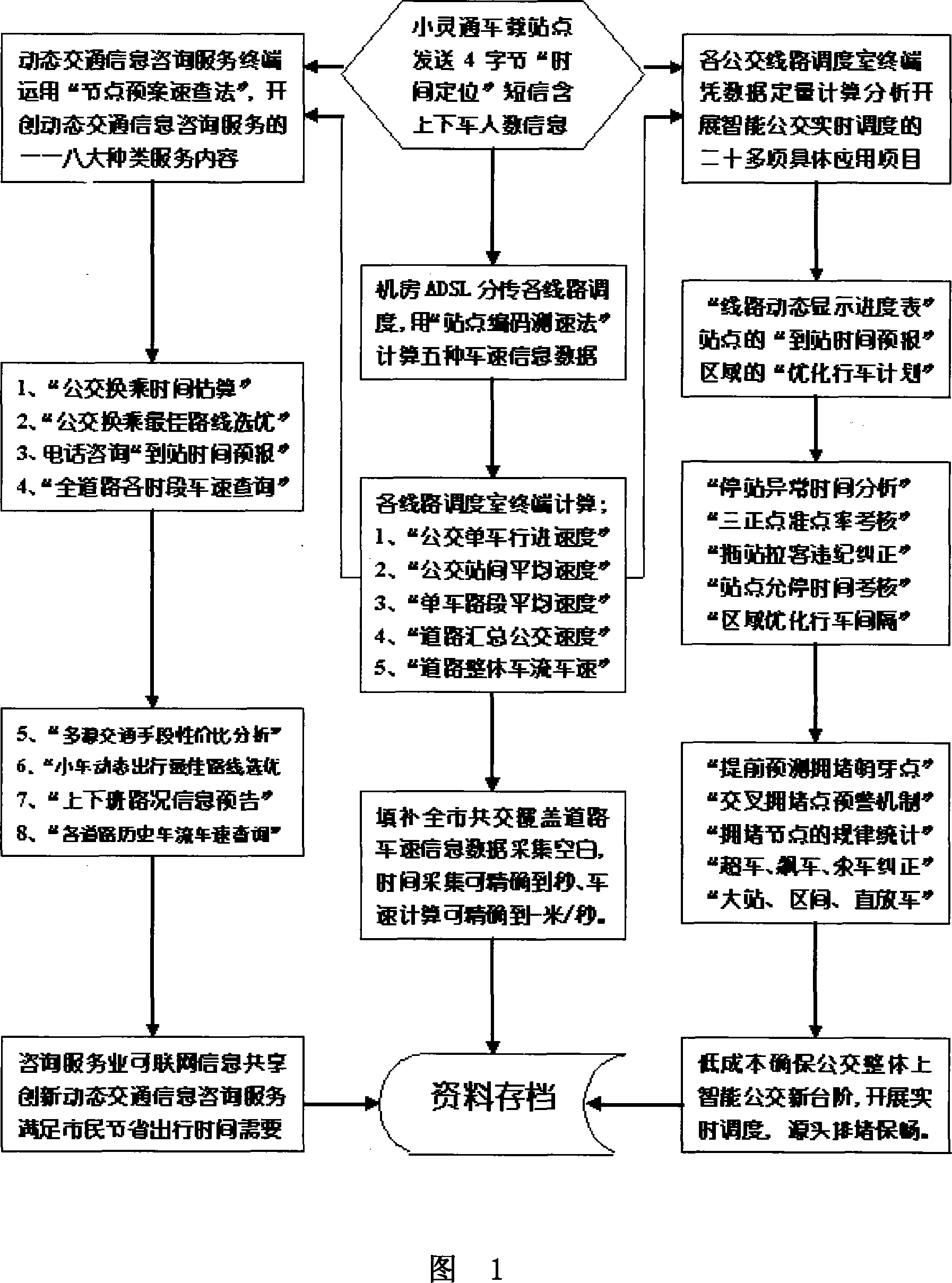
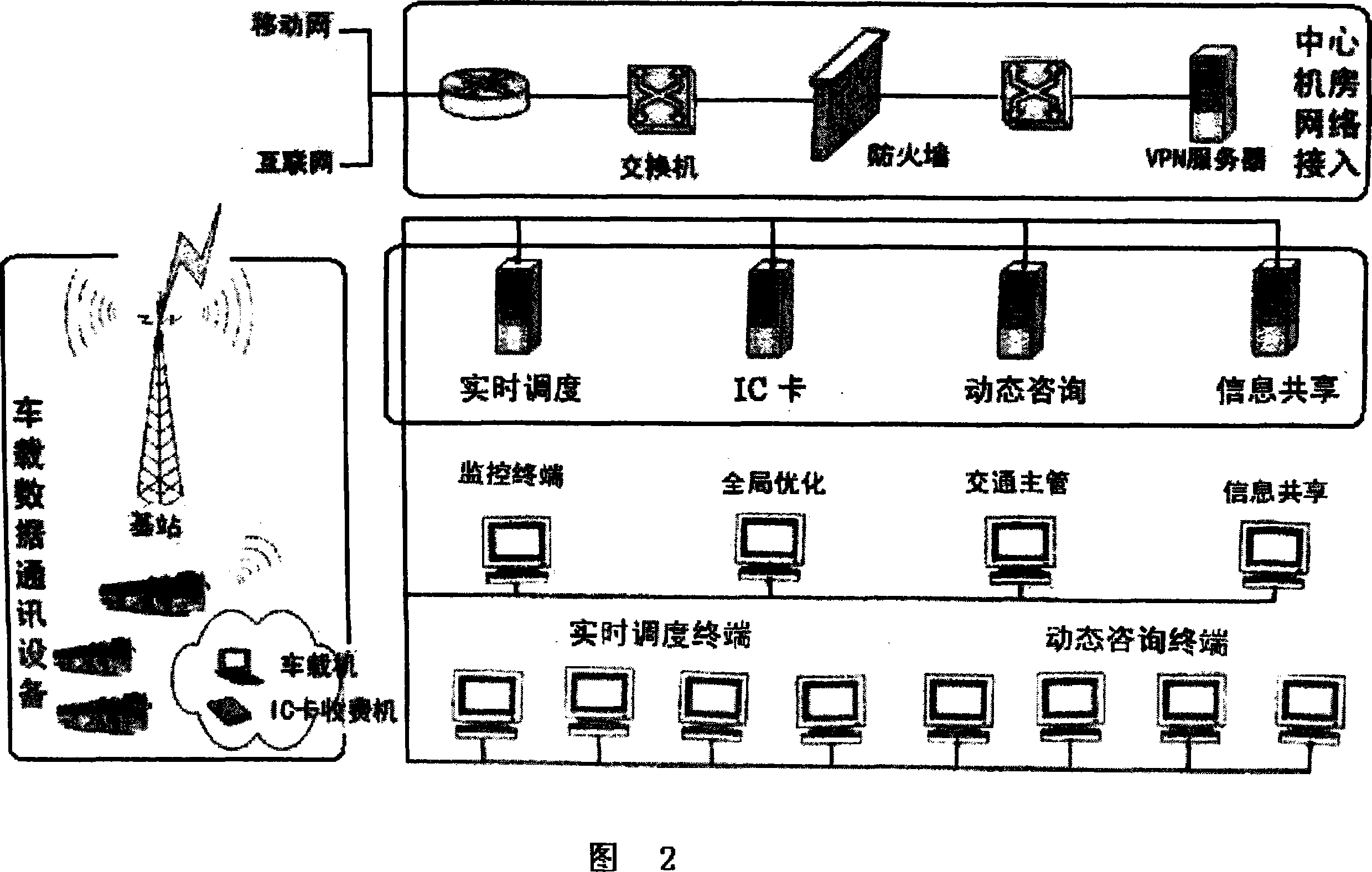
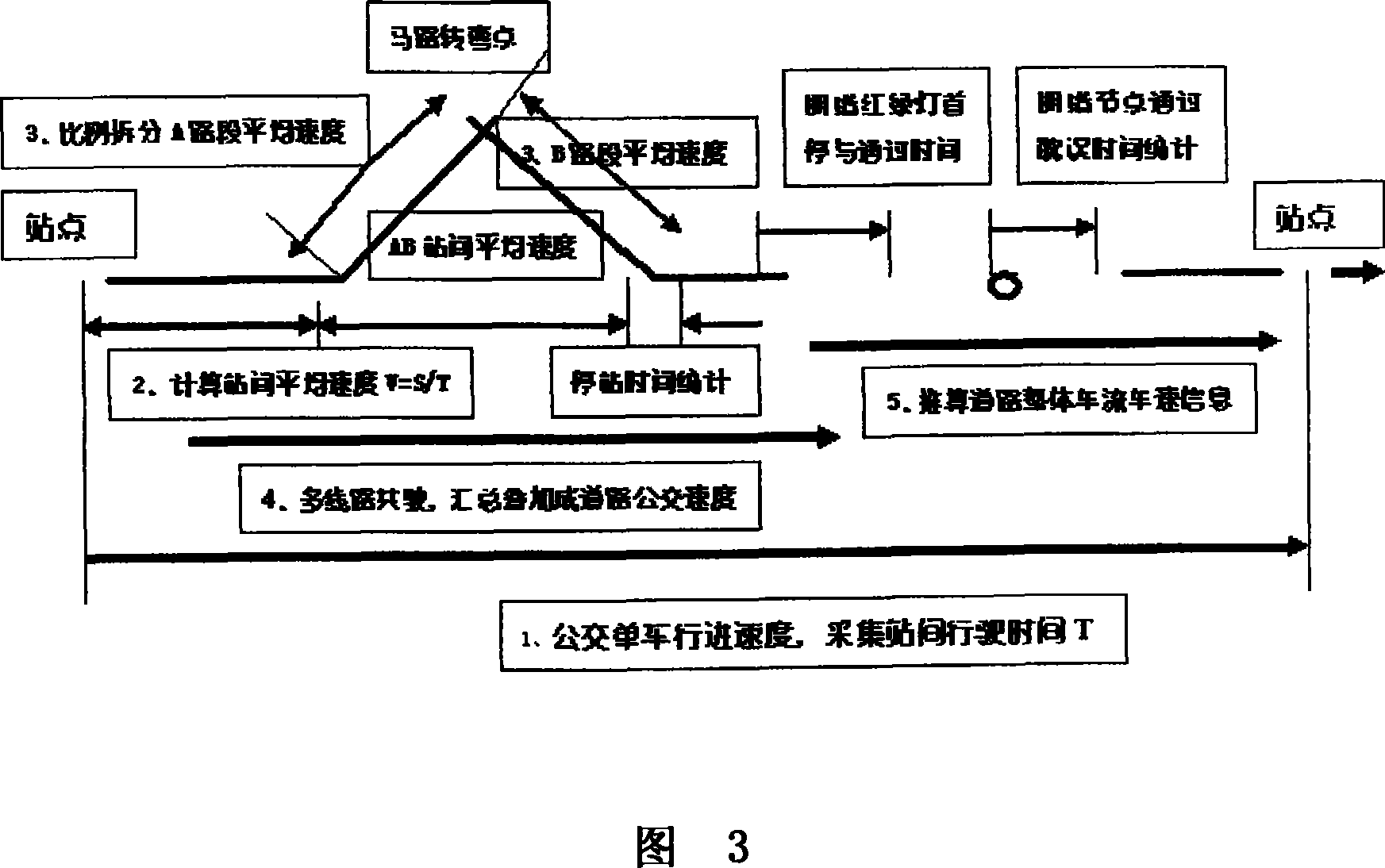
The invention relates to an intelligent public transportation system based on communication and grid computing technology. It is characterized in that it uses the Internet and VPN technology to connect the dispatching room terminals of each bus line and thousands of computers sharing computing resources in the dispatching system form a "virtual supercomputer" sharing computing resources and information resources; each bus The computer in the team dispatching room calculates the "average speed between stops" of the bus on this line based on the real-time positioning information sent back by the buses in real time during the operation of each line, confirms the specific location of the bus, and will need to share the overall "Road average vehicle speed" is uploaded to the summary platform, and each team can read the dynamic road condition information such as congestion stations, congestion intersections, congestion bottleneck nodes and other relevant road sections related to the driving status of this line. It is a low-cost, high-precision, and reliable operation. , high efficiency and good stability, and easy to popularize intelligent public transportation system.
Owner:刘靖宇
Method, system, network side equipment and UE for managing CSG membership
ActiveCN101931926AGuarantee managementEmergency connection handlingAssess restrictionTelecommunicationsUser equipment
The invention discloses a method, a system, network side equipment and UE for managing CSG membership. The method comprises the following steps that: when a user equipment (UE) resides in a CSG cell and establishes default loading, a network side detects whether the CSG membership of the UE is changed; and the network side triggers a Detach process between the network side and the UE by a channel existing between the network side and the UE and indicates the state information of the CSG membership of the UE when detecting that the CSG membership of the UE is changed, wherein the state information is used for making the UE operate in response to the change of the CSG membership according to the state information. In the embodiment of the invention, after the UE accesses the CSG cell in an urgent way and the CSG membership is generated, the network side manages the CSG membership of the UE by triggering the Detach process to ensure that the UE accesses the CSG cell again and manages local ACL.
Owner:SNAPTRACK
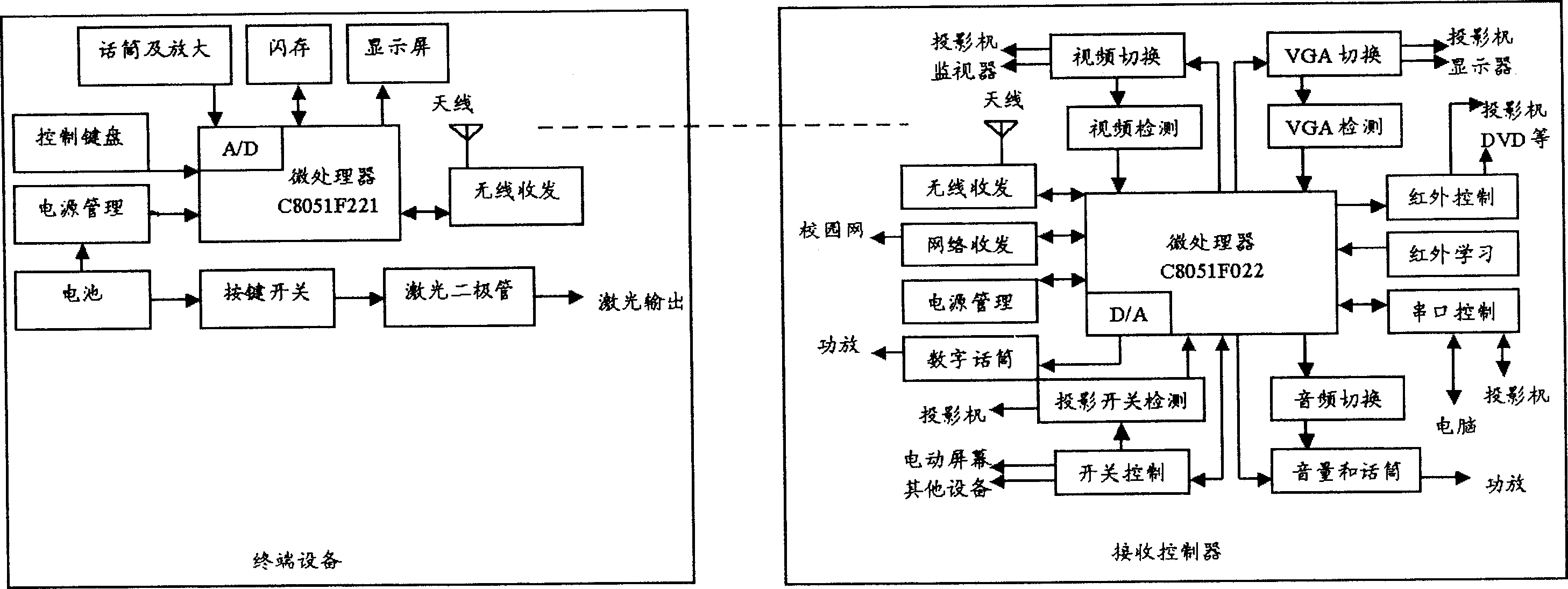
Radio control device and method for multimedium teaching
InactiveCN1725257AReduce in quantityEasy to operateTransmission systemsReadingWireless controlHuman–machine interface
A multimedia teaching wireless control device and a method includes a terminal device having the function of teaching instruction and a wireless mouse and sending remote information with the identifications of the terminal device to a receive controller to operate the multimedia devices and a receive controller receiving the remote control and operates multimedia devices.
Owner:廖锦新
License managing method and device for containers
ActiveCN108628658AImprove management efficiencyImprove securityResource allocationComputer security arrangementsMirror imageComputer science
The embodiment of the invention discloses a license managing method and device for containers. The license managing method for the containers comprises the following steps of: receiving a mirror imagedownloading request containing information for requesting a license, which is sent by a container managing background; acquiring a mirror image according to the mirror image downloading request; acquiring the information for requesting the license in the mirror image downloading request and generating a license mirror image layer corresponding to the information for requesting the license; addingthe license mirror image layer to the acquired mirror image; and sending the mirror image added with the license mirror image layer to the container managing background to enable the container managing background to start a container corresponding to the mirror image and detect whether the license mirror image layer is legal or not. By adopting the method disclosed by the embodiment of the invention, the license managing efficiency of the container can be improved.
Owner:HUAWEI TECH CO LTD
Intelligent construction site environment comprehensive monitoring system based on SAAS platform
PendingCN110888402AGuarantee managementImprove securityMeasurement devicesProgramme total factory controlVideo monitoringEnvironmental resource management
The invention discloses an intelligent construction site environment comprehensive monitoring system based on an SAAS platform. The intelligent construction site environment comprehensive monitoring system belongs to the technical field of construction site environment monitoring. The intelligent construction site environment comprehensive monitoring system comprises the SAAS platform and a construction site environment comprehensive monitoring terminal in data transmission connection with the SAAS platform by means of a wired or wireless network, wherein the construction site environment comprehensive monitoring terminal is connected with a video monitoring unit, an environment monitoring unit, a field equipment monitoring unit, an early warning unit and a construction site progress management and control unit by means of the wired or wireless network; the construction site environment comprehensive monitoring terminal is in signal connection with a voice module by means of a data line; and the construction site environment comprehensive monitoring terminal comprises a storage module, an environment monitoring comprehensive data analysis module, a display screen used for displaying environment monitoring information, a main control unit and an auxiliary control unit. The intelligent construction site environment comprehensive monitoring system can realize management cooperation of a construction site and interaction of a person, a machine and a platform, and improves management strength of the construction site.
Owner:NANJING HEZIZ INFORMATION TECH
Simple network management method and device based on multiple routing protocol instances
ActiveCN101977142AGuarantee managementEasy to manageData switching networksInformation repositoryManagement information base
The invention discloses a simple network management method based on multiple routing protocol instances, comprising the following steps: configuring identification information for each routing protocol instance; carrying identification information of the routing protocol instances to which data objects belong for all data objects in a management information base (MIB); and according to the identification information of the routing protocol instances carried by the data objects in the MIB, acquiring multi-instance information. The invention also discloses a simple network management device based on multiple routing protocol instances, comprising a configuration unit for configuring the identification information for each routing protocol instance and carrying the identification information of the routing protocol instances to which the data objects belong in the MIB, and an acquisition unit for acquiring the multi-instance information in accordance with the identification information of the routing protocol instances to which the data objects belong in the MIB. In the invention, the technical scheme of the invention is simple in realization, thereby preferably guaranteeing routing protocol management under the condition of the multiple routing protocol instances.
Owner:ZTE CORP
Intelligent building management method and device, medium and electronic device
PendingCN110703619AGuaranteed sharingGuarantee managementComputer controlProgramme total factory controlVideo monitoringHealth safety
The embodiment of the invention relates to the technical field of information, and provides an intelligent building management method and device, a medium and an electronic device. The method comprises the steps: collecting the position information, health information and environment information of personnel in an intelligent building, and carrying out the video monitoring; comparing the health information of the personnel in the intelligent building with a preset health standard, and predicting whether a health safety risk exists or not; comparing the environment information of the intelligent building with a preset environment standard, and predicting whether an environment safety risk exists or not; analyzing abnormal behaviors in the intelligent building according to video monitoring;and when at least one of the health safety risk, the environment safety risk and the abnormal behavior exists, sending risk prompt information in combination with the position information. According to the embodiment of the invention, the position information, the health information and the environment information of the personnel in the intelligent building are compared with the standard, the health of the personnel and the safety risk existing in the environment are predicted, and early warning information is given in time according to the prediction result.
Owner:TAIKANG LIFE INSURANCE CO LTD
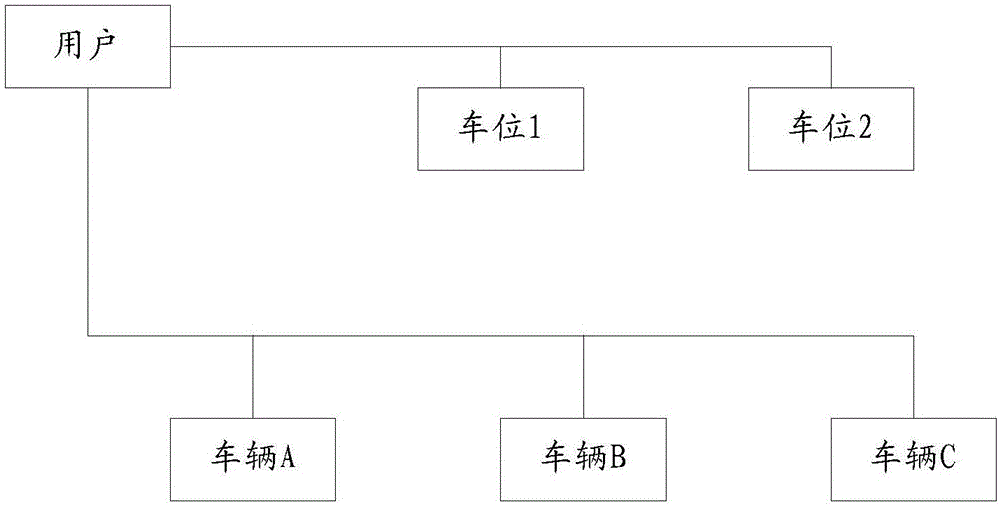
Method and system for realizing lease control on parking lot stalls
InactiveCN106340199AAvoid inconvenienceIncrease usageTicket-issuing apparatusIndication of parksing free spacesInformation repositoryParking space
The invention discloses a method and a system for realizing lease control on parking lot stalls. The method comprises steps that a stall lease request of a private user or an enterprise user is received; the information of multiple designated vehicles of the user in the stall lease request is stored in a vehicle information database, corresponding relationships between the designated vehicles and the quantity of designated stalls in a parking lot are established and are stored in the stall lease information database; according to the real-time-acquired coming-in and going-out information of the designated vehicles of the user, the lease stalls of the designated vehicles are distributed to the designated vehicles coming in and going out of the parking lot. Through the method, the lease stalls of the private user or the enterprise user can be managed, searching stalls is not required when the vehicles of the private user or the enterprise user enter the designated parking lot, use experience of the user is improved, and a stall utilization rate is improved.
Owner:北京悦畅科技有限公司
Display device stand for vehicle
InactiveCN1644428AEasy to installGuarantee managementPortable emergency signal deviceDisplay deviceEmbedded system
Owner:LEIJIN ELECTRONIC SHENYANG CO LTD
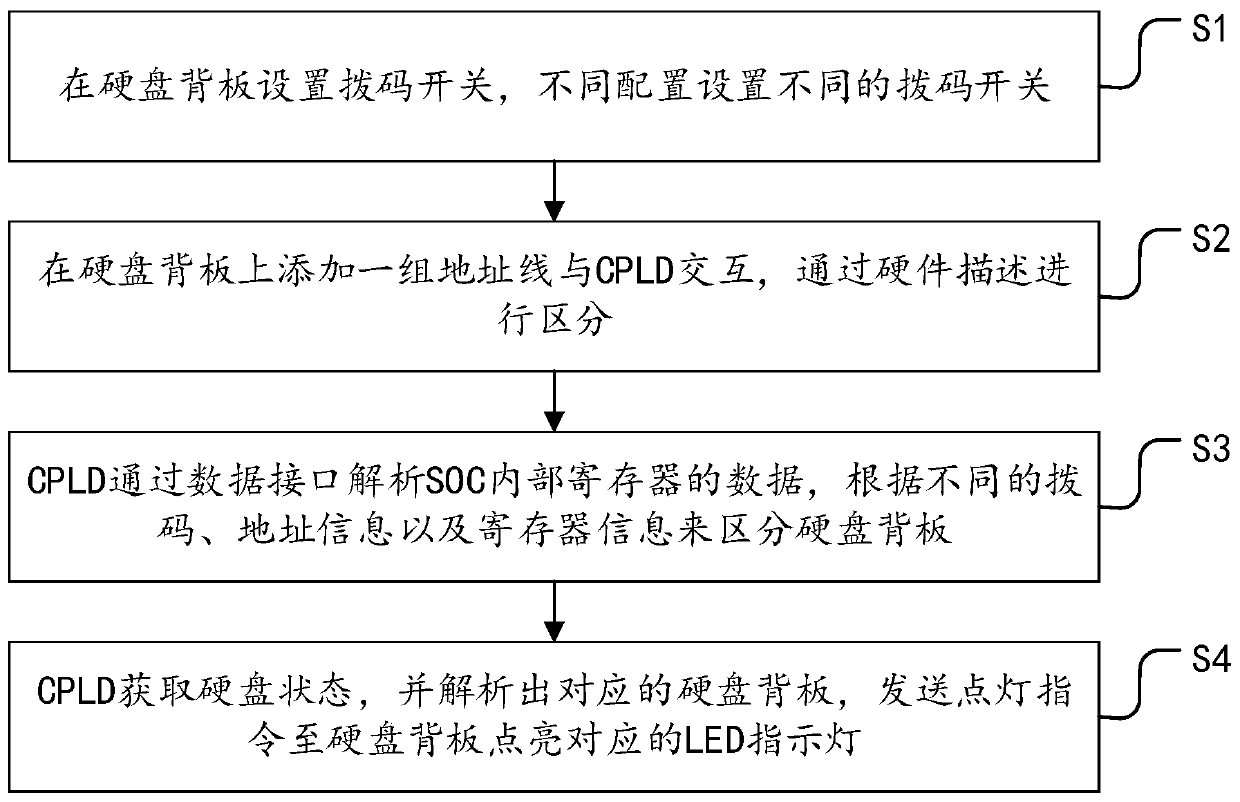
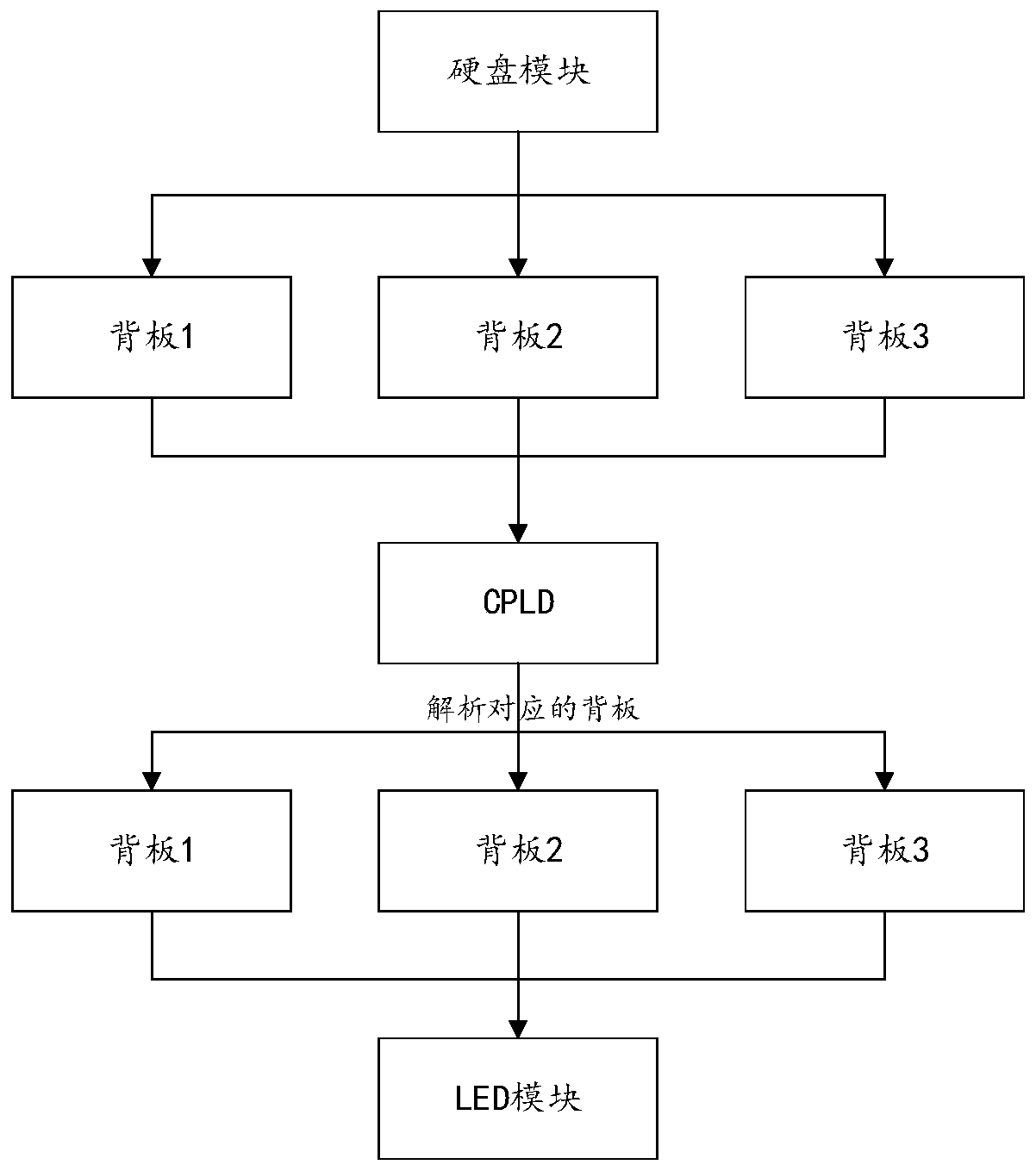
Method and system for achieving self-adaptive hard disk backboard lighting through CPLD CPLD
The invention provides a method and a system for achieving self-adaptive hard disk backboard lighting through a CPLD. The method comprises: respectively controlling a plurality of hard disks to lightthrough reasonably designed circuits and logic language design; the CPLD sending different states through the hard disk; judging a corresponding LED state to be controlled; through the difference of data transmission between the hard disk and the master controller, the CPLD selecting corresponding lighting instructions, if a plurality of back plate modules are used on one machine at the same time,indicating LED state control of the backboard at an accurate position through different dial codes, address information and register information. Multiple types and configurations of multiplexing backboard lighting are realized, the utilization rate of a single board is improved, inventory management is reduced, income is improved, new material number application and material management are saved, original communication and data transmission are ensured, reusability is ensured, and the burden of a whole purchasing and inventory system is reduced.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Multicast management method and multicast management system based on mark
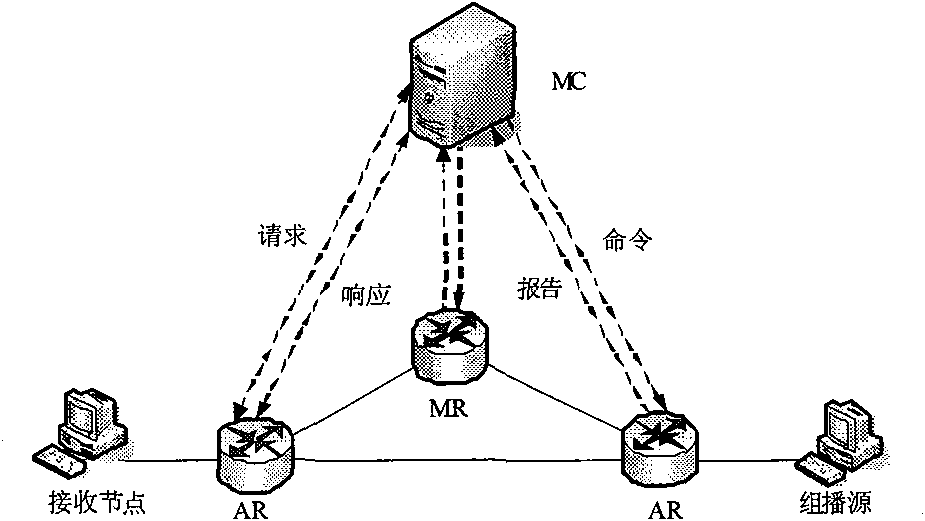
InactiveCN101635634AGuarantee managementEnsure safetySpecial service provision for substationComputer networkEngineering
The invention relates to a multicast management system based on a mark, comprising a multicast source, a receiving node, an AR, an MC and an MR, wherein the AR is used for receiving a multicast joining request of the receiving node; the MC is used for distributing an MGI being suitable for the AR; and the MR is used for establishing a route with the AR and transmitting multicast state information to the MC. The invention realizes management based on a node mark, guarantees the safety of multicast source data entering a network, also guarantees that the node can still maintain an own multicast service state after a network access position of the node is changed and can be applied to any types of networks.
Owner:BEIJING JIAOTONG UNIV
Device and method for intelligently charging and discharging storage battery
InactiveCN101834459AUninterrupted charge and dischargeUninterrupted dischargeBatteries circuit arrangementsEmergency protective circuit arrangementsMicrocontrollerEngineering
The invention relates to a device for intelligently charging and discharging a storage battery. The input end of the device is connected with a DC input while the output end is connected with a load. The device comprises a battery module, a microcontroller, a charging protection module, two discharging protection modules, a charging switch, a discharging switch, an intelligent charging mode circuit and a detection module. The DC input is connected with the input end of the charging protection module and the input end of the first discharging protection module respectively. The output end of the charging protection module is connected with the input end of the charging switch. The output end of the charging switch is connected with the input end of the intelligent charging mode circuit. The output end of the intelligent charging mode circuit is connected with the anode of the battery module. The cathode of the battery module is connected with the detection module and the discharging switch respectively. The microcontroller is connected with and controls the charging switch, the discharging switch, the intelligent charging mode circuit and the detection module respectively. The invention also relates to a charging and discharging method. The device and the method of the invention can effectively complete the whole charging and discharging process, guarantee effective management of the battery while guaranteeing that the system works, and prolong the service life of the battery.
Owner:上海东洲罗顿通信股份有限公司
Safety and management of computing environments that may support unsafe components
InactiveUS8621551B2Ensuring the safety of a deviceEffectively guardMemory loss protectionDigital data processing detailsTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
Security management and control command system
InactiveCN103048976AImprove work efficiencyRealize personnel qualification management and reviewProgramme total factory controlFingerprintMicrophone
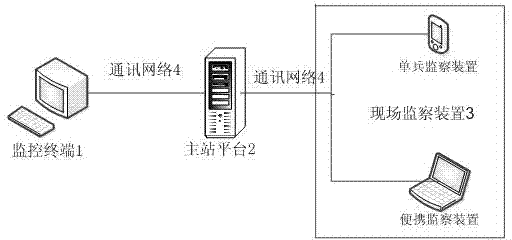
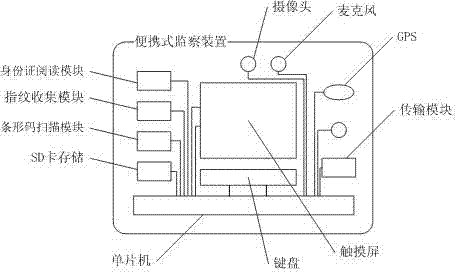
The invention discloses a security management and control command system, which comprise a monitor terminal, a master station platform, an on-site monitoring apparatus and a communication network, wherein the master station platform is respectively connected with the monitor terminal and the on-site monitoring device through the communication network, and the on-site monitoring device comprises an identity card reading module, a fingerprint collection module, a barcode scanning module, a camera, a microphone, a transmission module, a memory, a touch screen, a keyboard and a single chip microcomputer; and the identity card reading module, the fingerprint collection module, the barcode scanning module, the camera, the microphone, the transmission module, the memory, the touch screen and the keyboard are all connected with the single chip microcomputer, and the on-site monitoring device is connected with the master station platform through the transmission module. The system integrates multiple functions to realize the remote security monitoring and command management and control on a construction site.
Owner:KGE
Intelligent identification and diagnosis method for power digital link
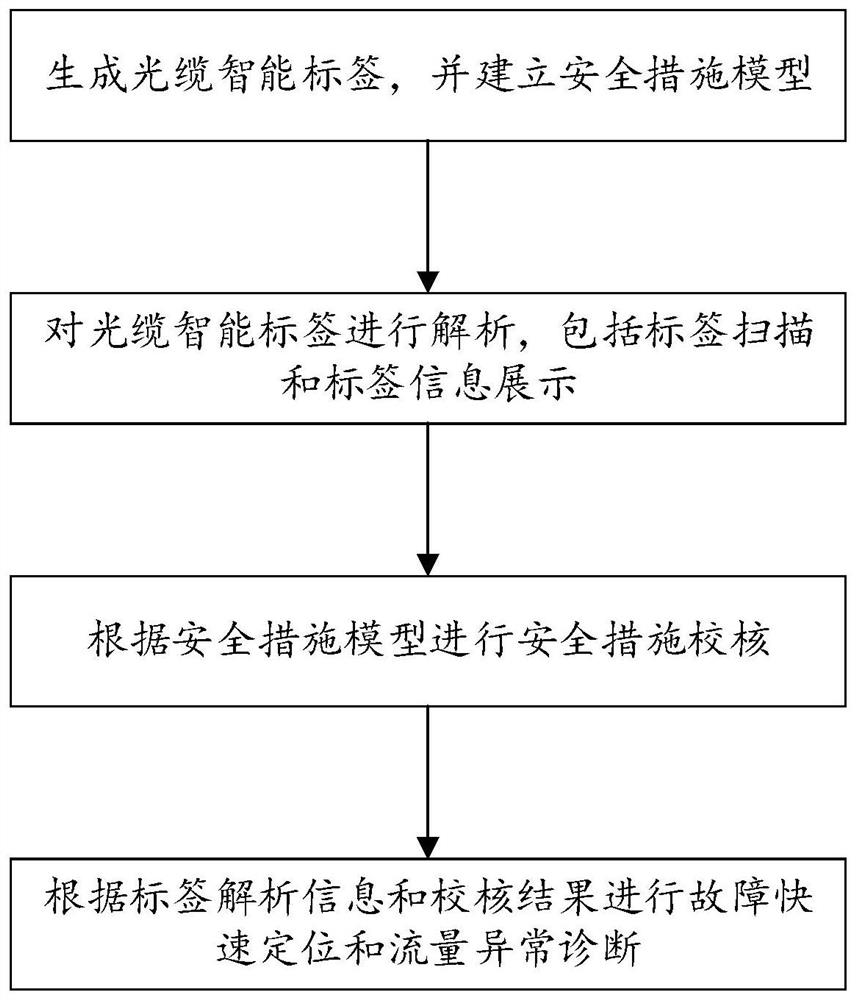
PendingCN113300765AQuickly understand the actual connection situationGuarantee managementDigital data information retrievalElectromagnetic transmissionComputer scienceData bank
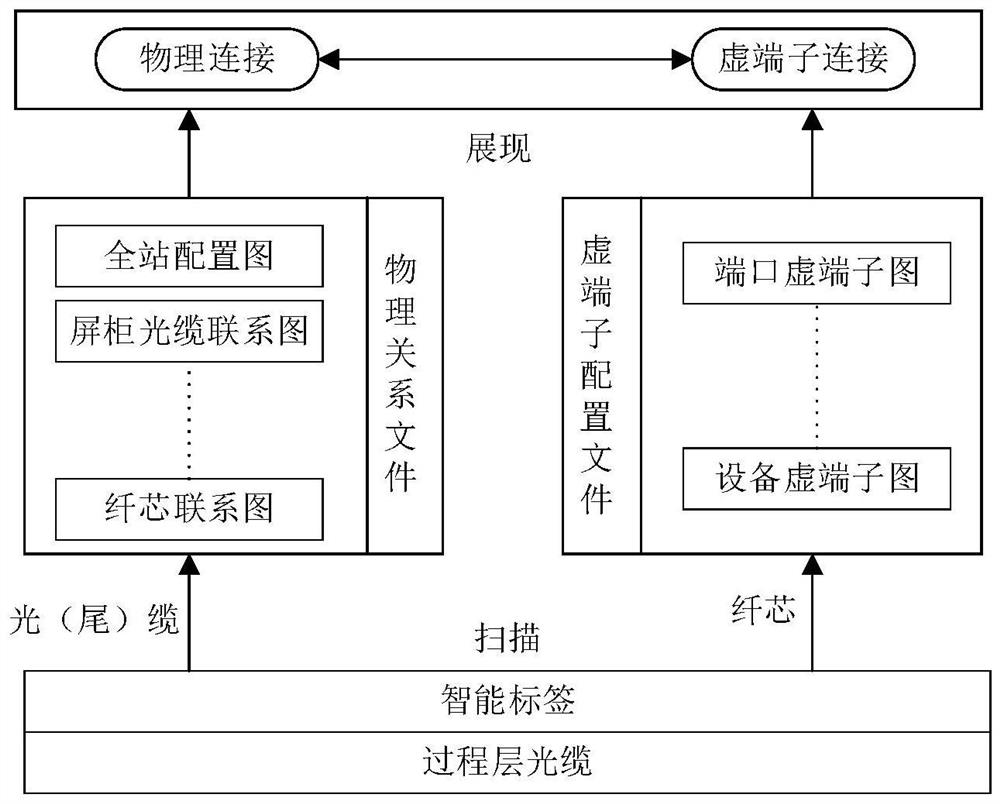
The invention discloses an intelligent identification and diagnosis method for a power digital link, and the method comprises the following steps: generating an optical cable intelligent label, and building a safety measure model; analyzing the optical cable intelligent label, wherein the analysis comprises label scanning and label information display; checking a safety measure according to the safety measure model; and according to the label analysis information and a checking result, rapidly positioning a fault and diagnosing traffic anomaly. According to the invention, the standardization of the field intelligent optical fiber label is realized by establishing an intelligent optical fiber standardization database and printing the standardization intelligent label; the complete loop in the optical fiber loop and the corresponding virtual loop information in the optical fiber loop are visually displayed through the optical fiber, so that the operation and maintenance personnel can quickly understand the actual connection condition of the on-site optical fiber, and the workload of the on-site working personnel is greatly reduced.
Owner:国网湖北省电力有限公司荆门供电公司
Printing device and its control method and consumpable device mounted on same
InactiveCN1540457AGuarantee managementElectrographic process apparatusDigital output to print unitsEmbedded systemStorage cell
This invention provides a printing apparatus which controls to inhibit any inadvertent write to a memory in an expendable so as to securely manage the exchange timing and the like of the expendable. For this purpose, the expendable such as a toner cartridge or the like comprises a rewritable nonvolatile memory (21) which holds information indicating whether or not its service life has expired. When the toner cartridge is attached to the printing apparatus, it is ready to communicate with a printer engine controller in the printing apparatus, and write to the nonvolatile memory (21) can be made in accordance with an instruction from a control unit. A lock functional unit (21a) writes information indicating write inhibition at a predetermined address in the nonvolatile memory (21), thus inhibiting write to the address position that stores the information indicating whether or not its service life has expired.
Owner:CANON KK
Quasi-synchronous master-slave remote education information management system and its implementation method
InactiveCN1336598AEfficient use ofReduce the burden onDigital computer detailsElectric digital data processingInformation resourceThe Internet
The invention relates to the areas of internet technique and satellite broadcast technique. It is composed of master station, multi passive station, and communication unit used to connect the master station and the passive station. The master station is a computer having an integrated system, background database and firewall. The integrated system provides editing and sending functions of networking school. The passive station consists of multi computers connected each other through local area network. One of the said computer is as a server connected to communication unit. The management information system and database of the passive station, and firewall is installed on the server station. Other passive stations connected to the server of passive stations through local area network of passive stations provides for logging user to use the courseware resources from database of the passive stations. The information resources is transmitted and managed with quasi-synchronous, master-slave style. The invention makes larner living in area where the switch in condition of Internet is poor being able to study through local area network. Thus one side, more students can share the education resources provided through Internet, on the other hand, the provider of the resources realizes effective centralizing management.
Owner:TSINGHUA UNIV
Software upgrade method of Internet of Things (IoT) system
InactiveCN107872488AReduce trafficEnsure unified control and managementTransmissionTraffic volumeTraffic capacity
The invention provides a software upgrade method of an Internet of Things (IoT) system. A part of the IoT terminals in the IoT system download and upgrade a software upgrade package from a cloud version server through wireless cellular communication; and with the subsequent cooperation of the control of the cloud version server and the IoT terminals currently having finished software upgrade, theIoT terminals to perform software upgrade download the software upgrade package from the IoT terminals currently having finished the software upgrade and upgrade the software through wireless short-distance communication, and the entire software download and upgrade process is first based on the wireless cellular communication and then based on the wireless short-distance communication and effectively saves the traffic compared with the entire process only based on the wireless cellular communication. Further, during the entire software upgrade process, the control flow is performed by the cloud version server through the wireless cellular communication, and the unified control and management of the software upgrade process is well guaranteed.
Owner:LEADCORE TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com