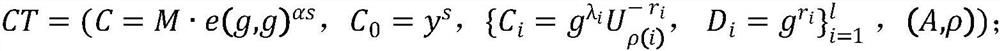Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
159results about How to "Guaranteed sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
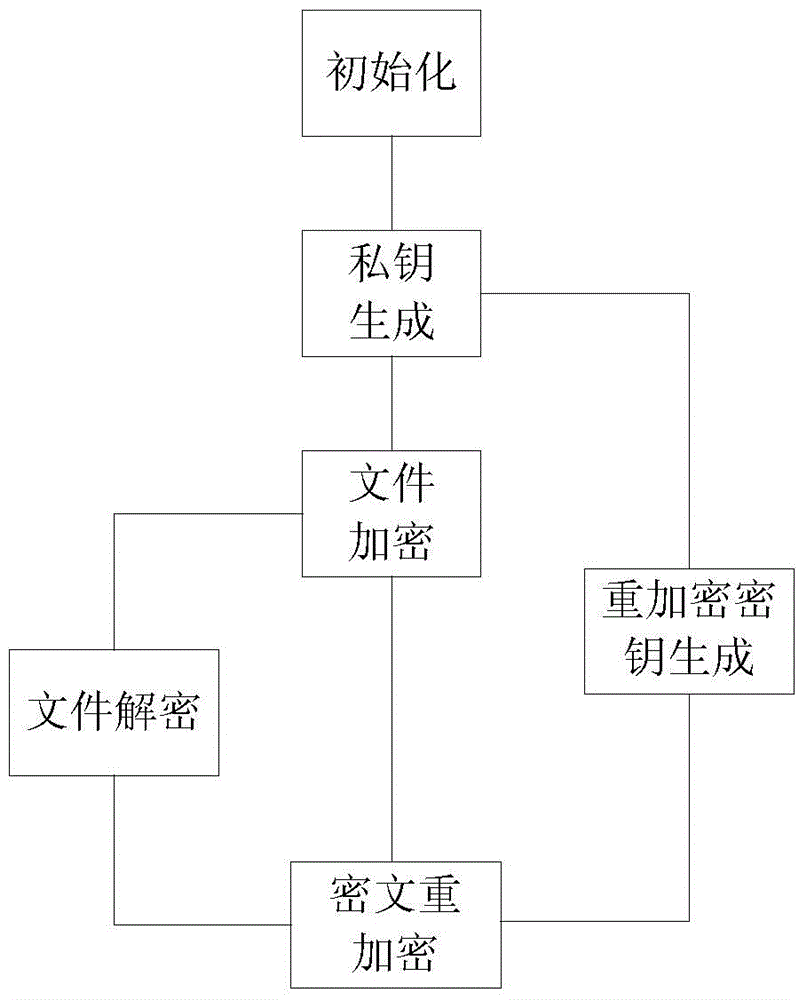
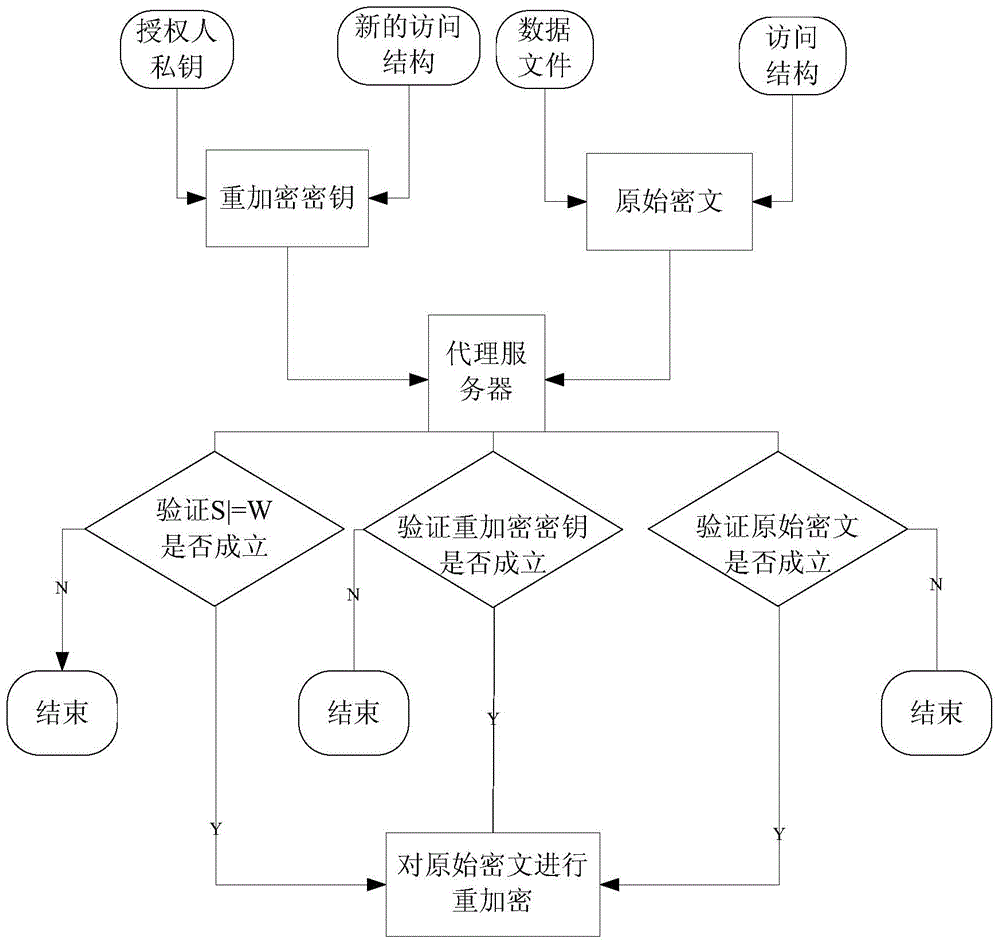
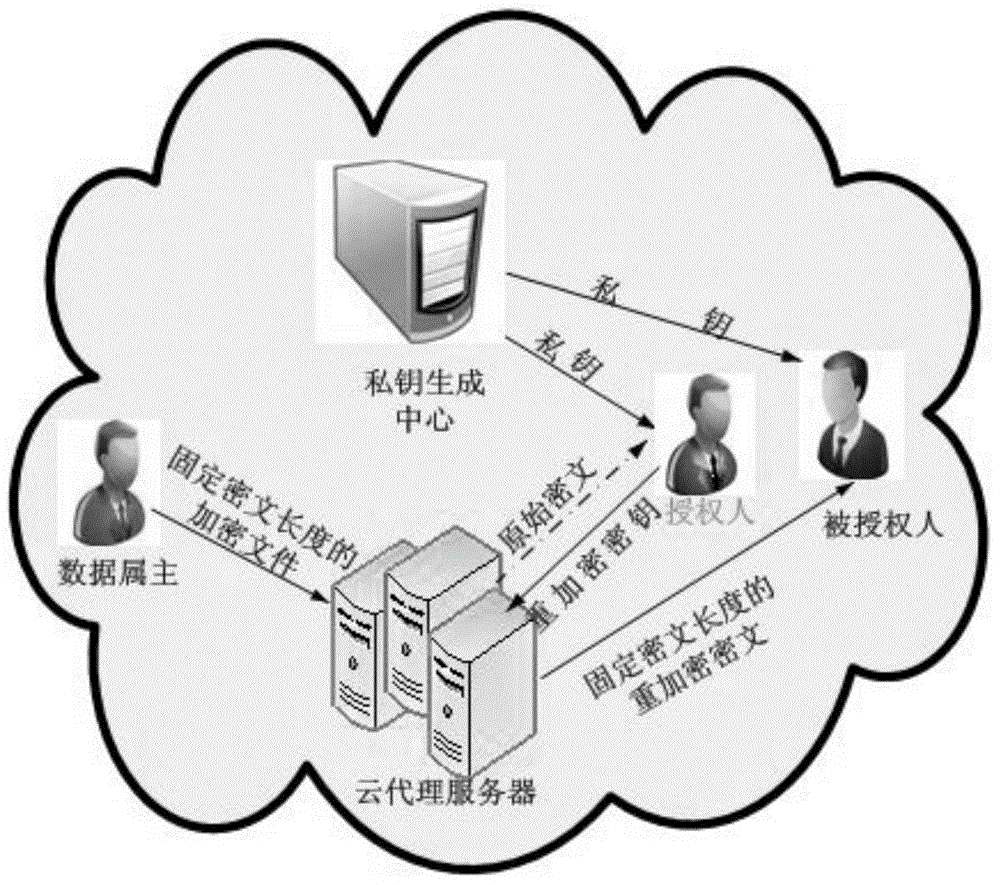
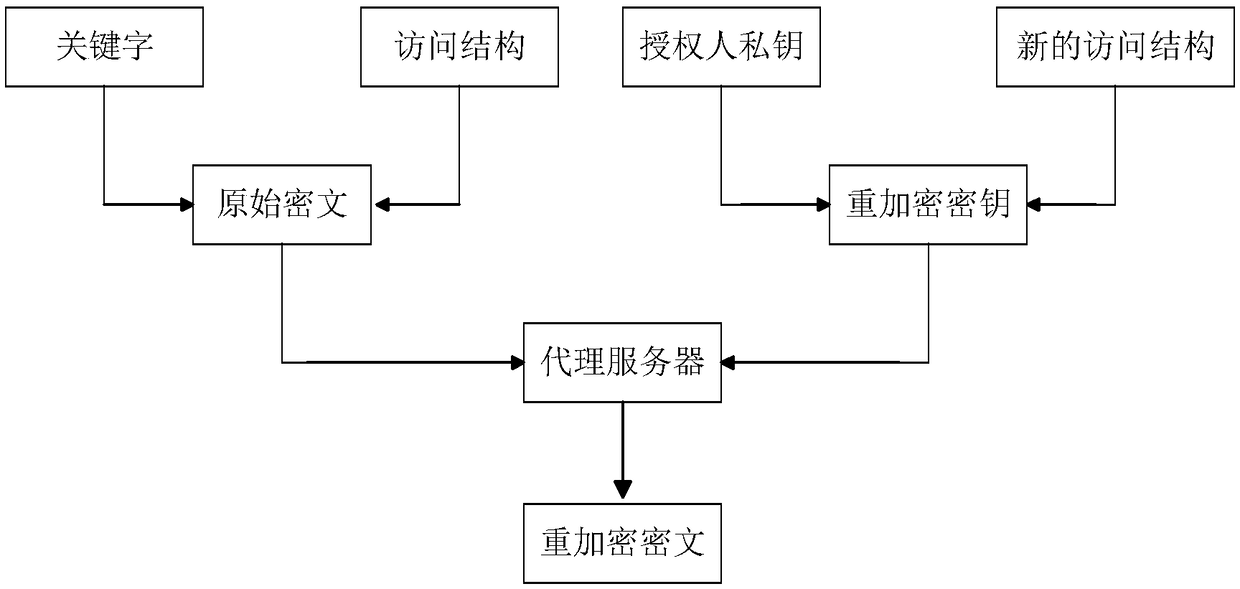
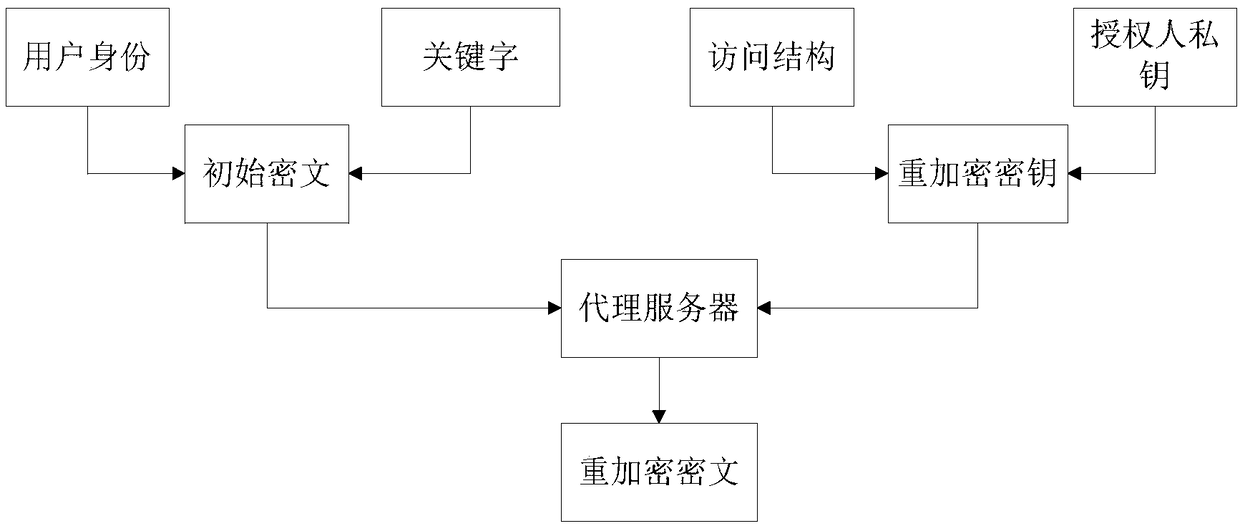
CP-ABE-based fixed ciphertext length proxy re-encryption system and method in cloud computing
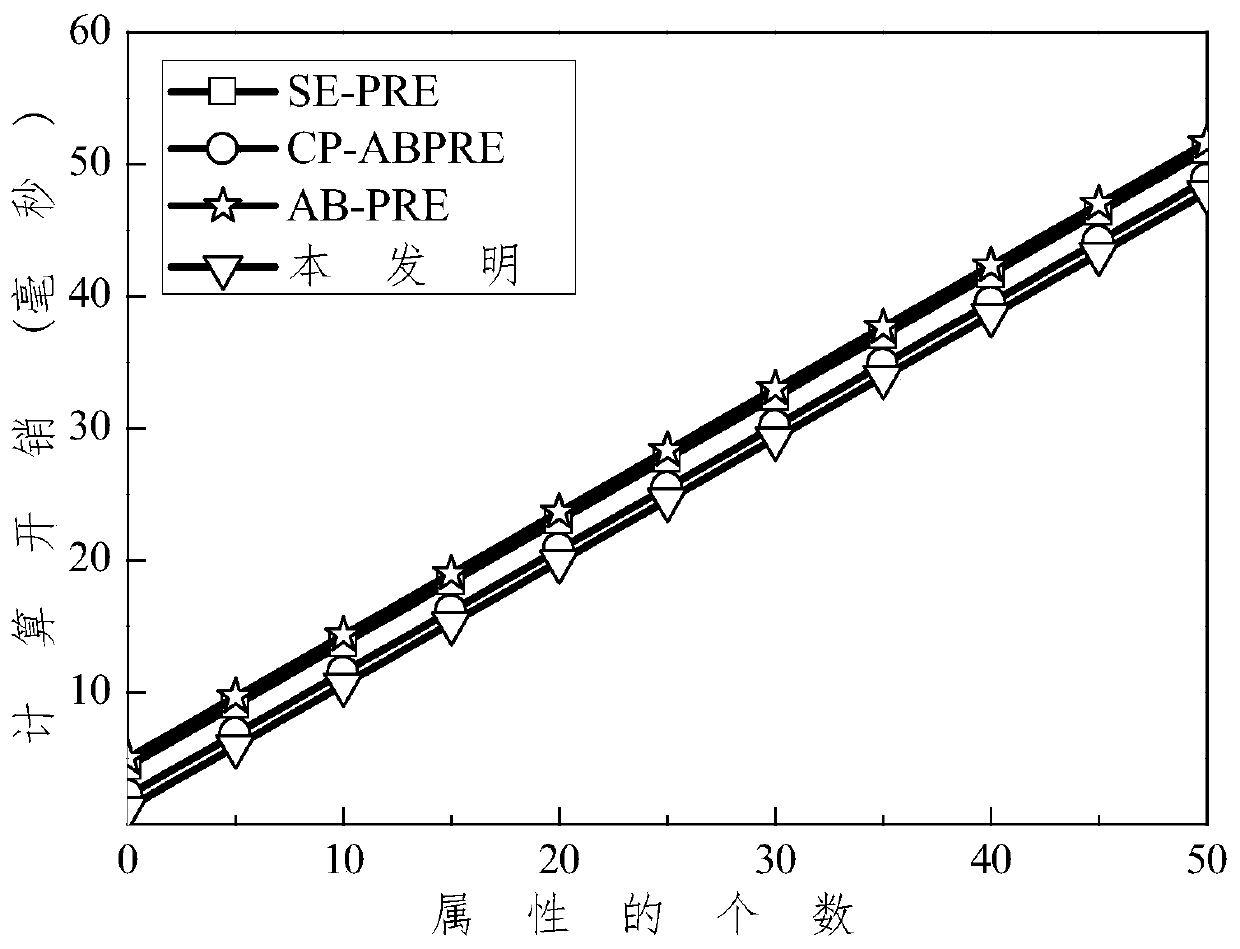
The invention discloses a CP-ABE-based fixed ciphertext length proxy re-encryption system and method in cloud computing. By the adoption of the method, efficient safe access and sharing of a data file in the cloud computing environment are achieved. According to the method, on one hand, the proxy re-encryption technology is adopted for ciphertext conversion so that a ciphertext which can be decrypted by an authorizer can be converted into a ciphertext which can be decrypted by an authorized person, to be specific, after a file of a data owner is encrypted and uploaded to a cloud proxy server, under the condition that the authorizer is not available, the cloud proxy server re-encrypts the encrypted file, and the authorized person can acquire a plaintext through decryption with a private key of the authorized person after acquiring the re-encrypted file from the cloud proxy server, so that safe access and sharing of data are guaranteed; on the other hand, during ciphertext encryption, the CP-ABE-based fixed ciphertext length algorithm is adopted for ciphertext computing, so that the length of the ciphertext is fixed and does not increase along with the increase of the number of attributes, and then computing expenses are effectively reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
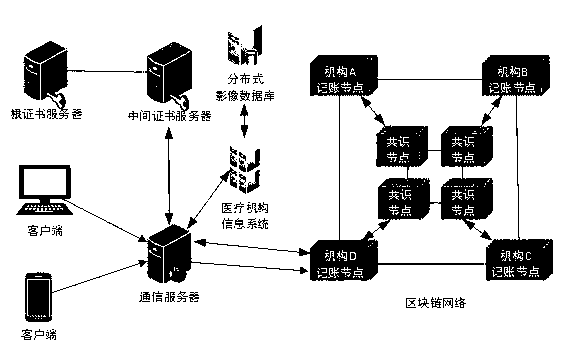
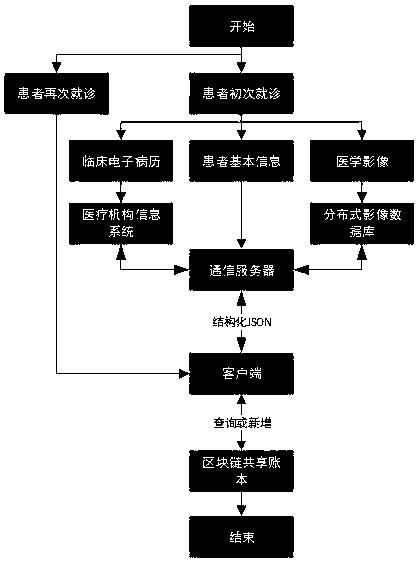
Medical data platform based on block chain technology
InactiveCN109243548AIsolation damageReduce risk of leakageDigital data information retrievalPublic key for secure communicationData synchronizationData platform
The invention discloses a medical data platform based on the block chain technology. The medical data platform comprises a terminal, a server module, a data storage module and a block chain network. The terminal exchanges data with the data storage module and the block chain network through the server module. The server module comprises a communication server, an intermediate certificate server and a root certificate server and is used for processing data interaction between the modules and allocating certificates to the block chain network nodes. The data storage module comprises a medical information system and a distributed image database and is used for data storage. The block chain network comprises multiple institutional accounting nodes and multiple consensus nodes. The accounting nodes perform mutual data synchronization. The medical data platform based on the block chain technology has the advantages that the existing medical information is stored in the block chain shared account book so that all the medical institutions can share the medical information related to the patients, and the privacy protection function of the medical data can be realized by using the encryption algorithm and thus sharing of the medical data can be facilitated and the security of the sensitive information can also be protected.
Owner:GUANGDONG UNIV OF TECH
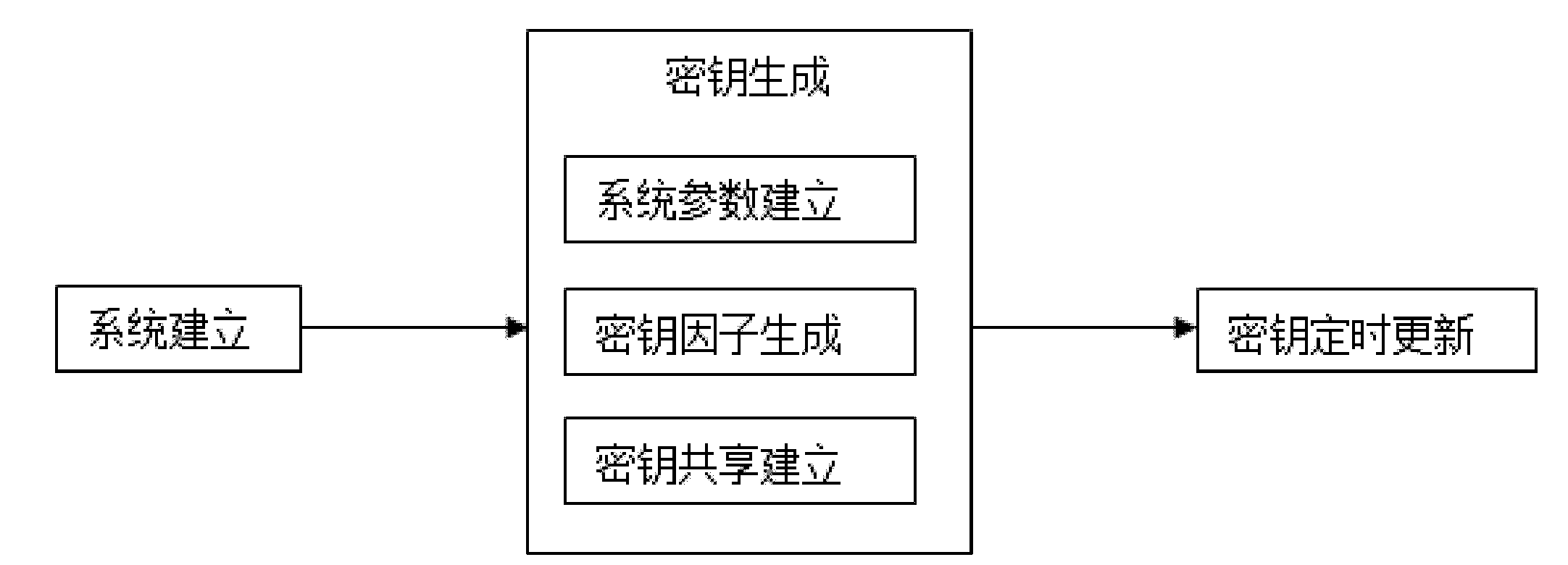
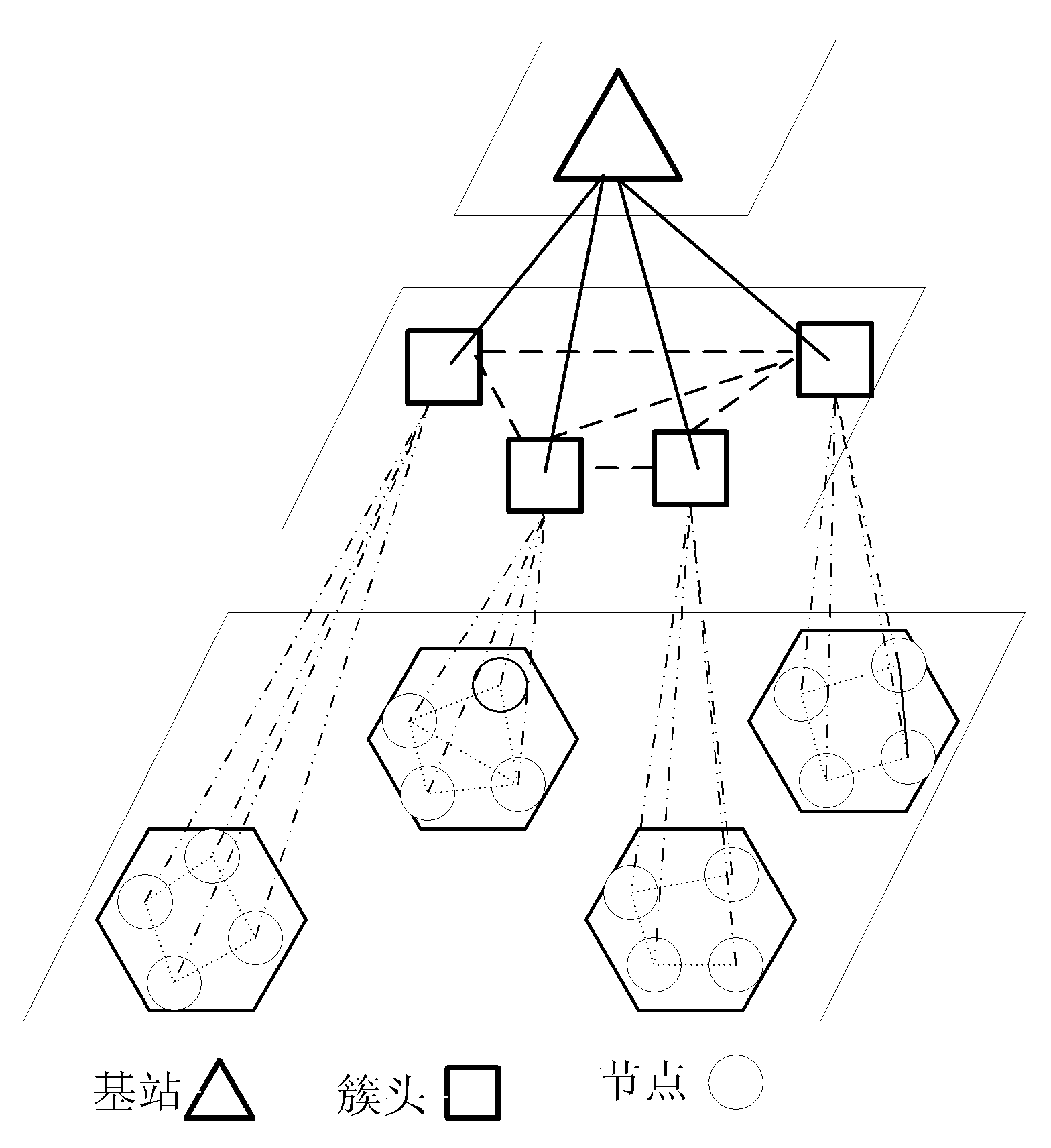
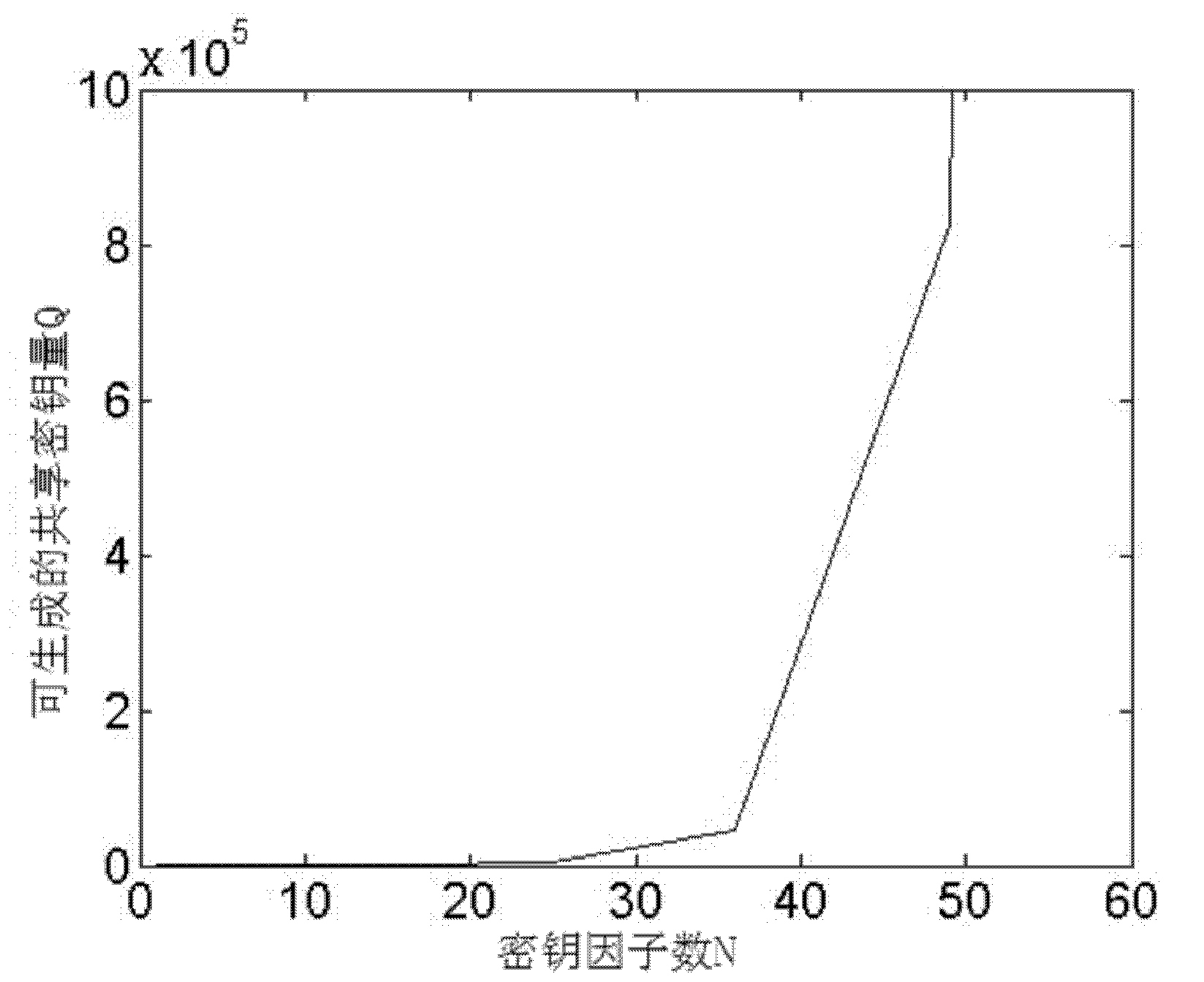
Key management method used for wireless sensor network
InactiveCN102164367AImprove securityIncrease storage capacitySecurity arrangementHigh level techniquesKey generationKey factors
The invention relates to a key management method used for a wireless sensor network, in particular relates to a key management method adopting the combined key technology, and belongs to the field of wireless sensor network safety technology. The key management method comprises the three steps as follows: system building, key generation and key updating, wherein the step of key generation comprises three processes of system parameter building, key factor and mapping algorithm generation, and shared key building. Compared with the prior art, the key management method has certain degrees of improvements on safety, storage and energy conservation, solves the problem that the sensor mode storage space is limited, ensures that any adjacent nodes can share a key, makes up for a deficiency that the sensor network is not provided with an authentication center, and saves the storage space.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
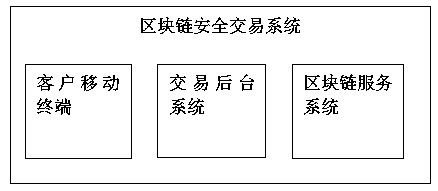
A secure transaction system based on a block chain and a method thereof
The invention discloses a secure transaction system based on a block chain. The system comprises a block chain secure transaction system. The block chain secure transaction system comprises a client mobile terminal, a transaction background system and a block chain service system. The client mobile terminal supports two architecture modes of C / S and B / S. A common user completes a digital asset transaction through a mobile phone APP. The transaction background system is used for processing the user request, extracting a core service to a block chain server for processing, and completing non-core service processing. The block chain service system is mainly used for processing the core service and calling an intelligent contract to execute a transaction, packaging a transaction result into blocks, and writing the blocks into a block chain account book after consensus. A block chain service system is deployed in each mechanism, and the block chain service systems are mutually connected toform a distributed block chain service system network. The secure transaction system has the advantage of secure transaction.
Owner:陕西医链区块链集团有限公司
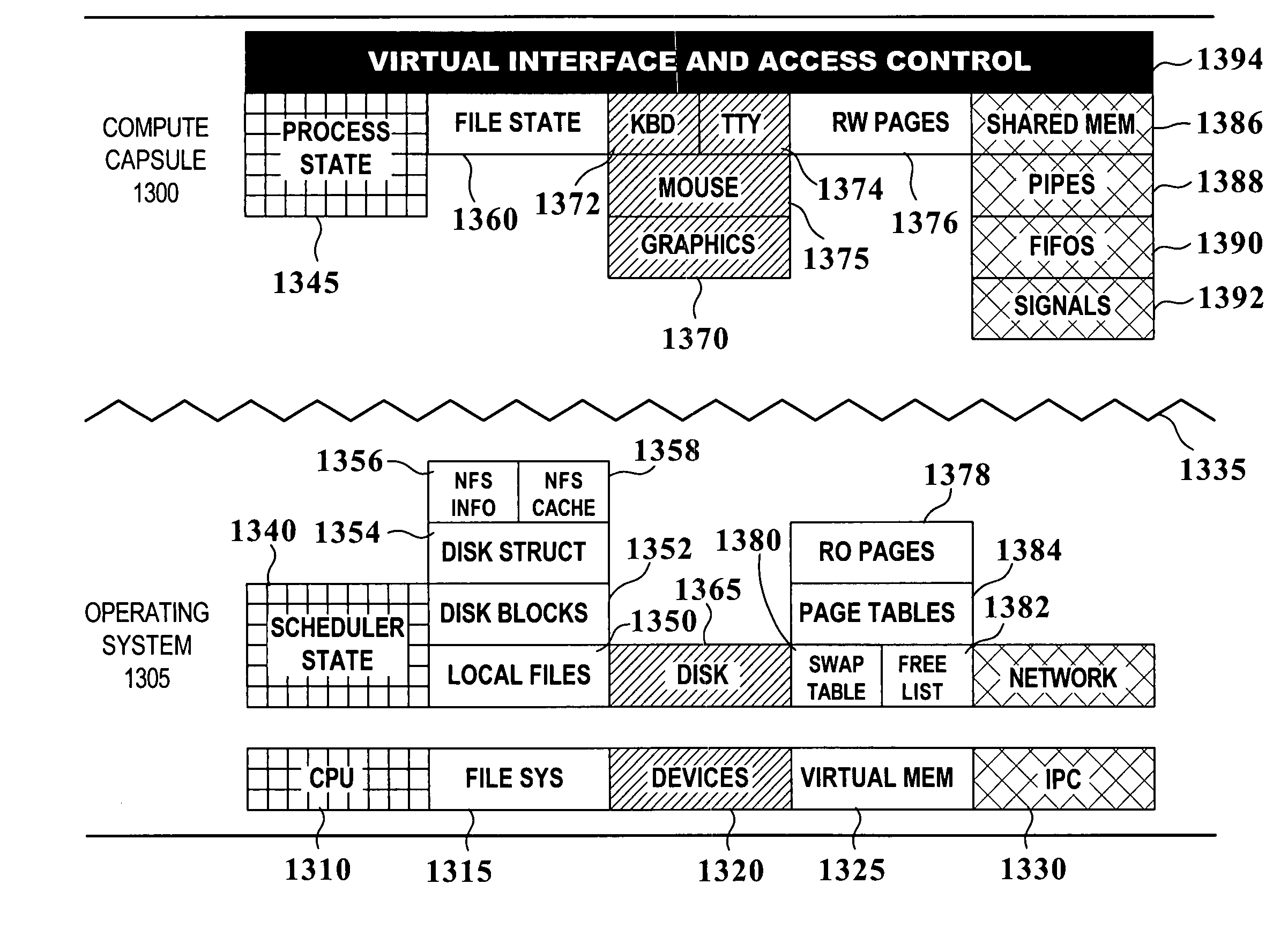
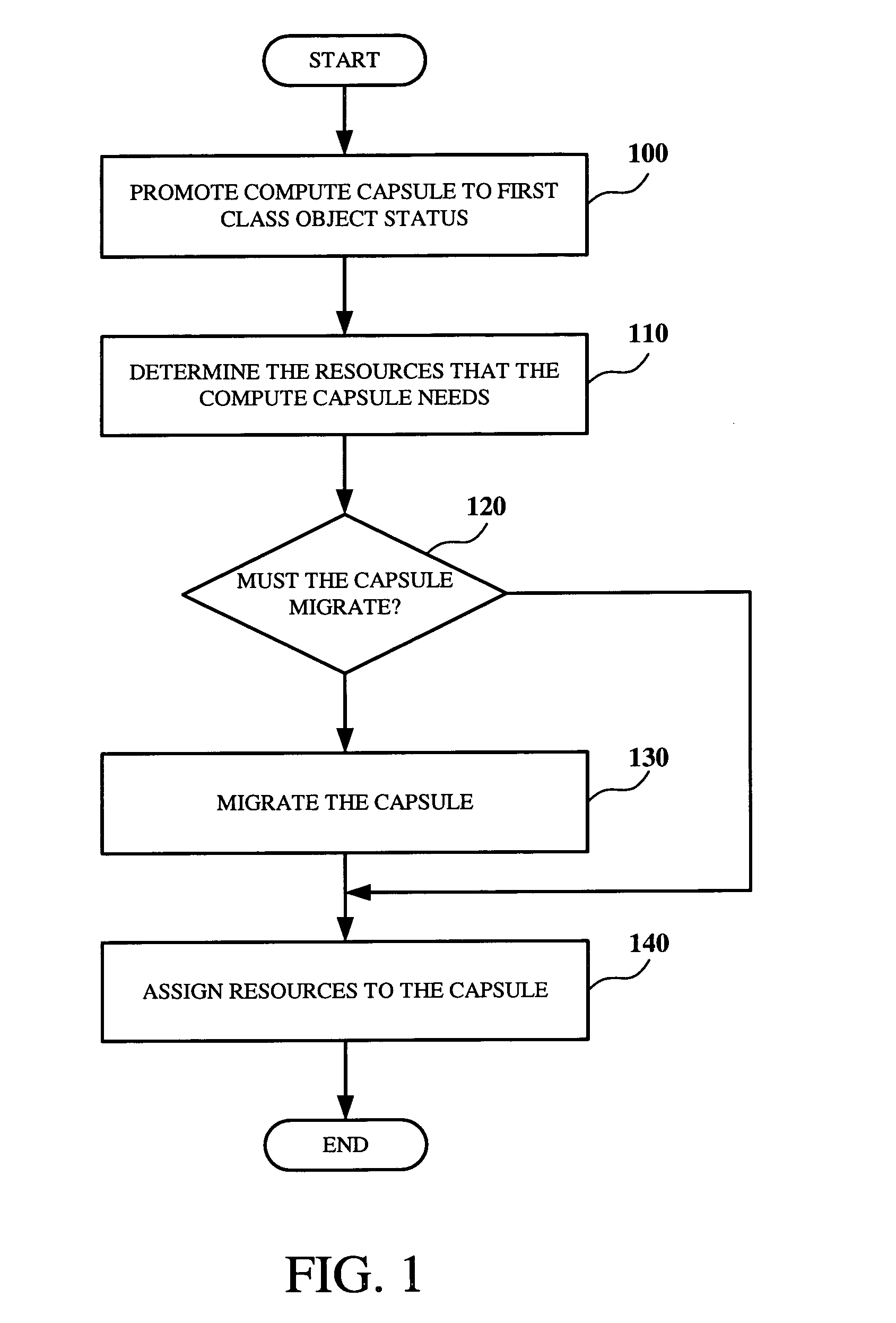
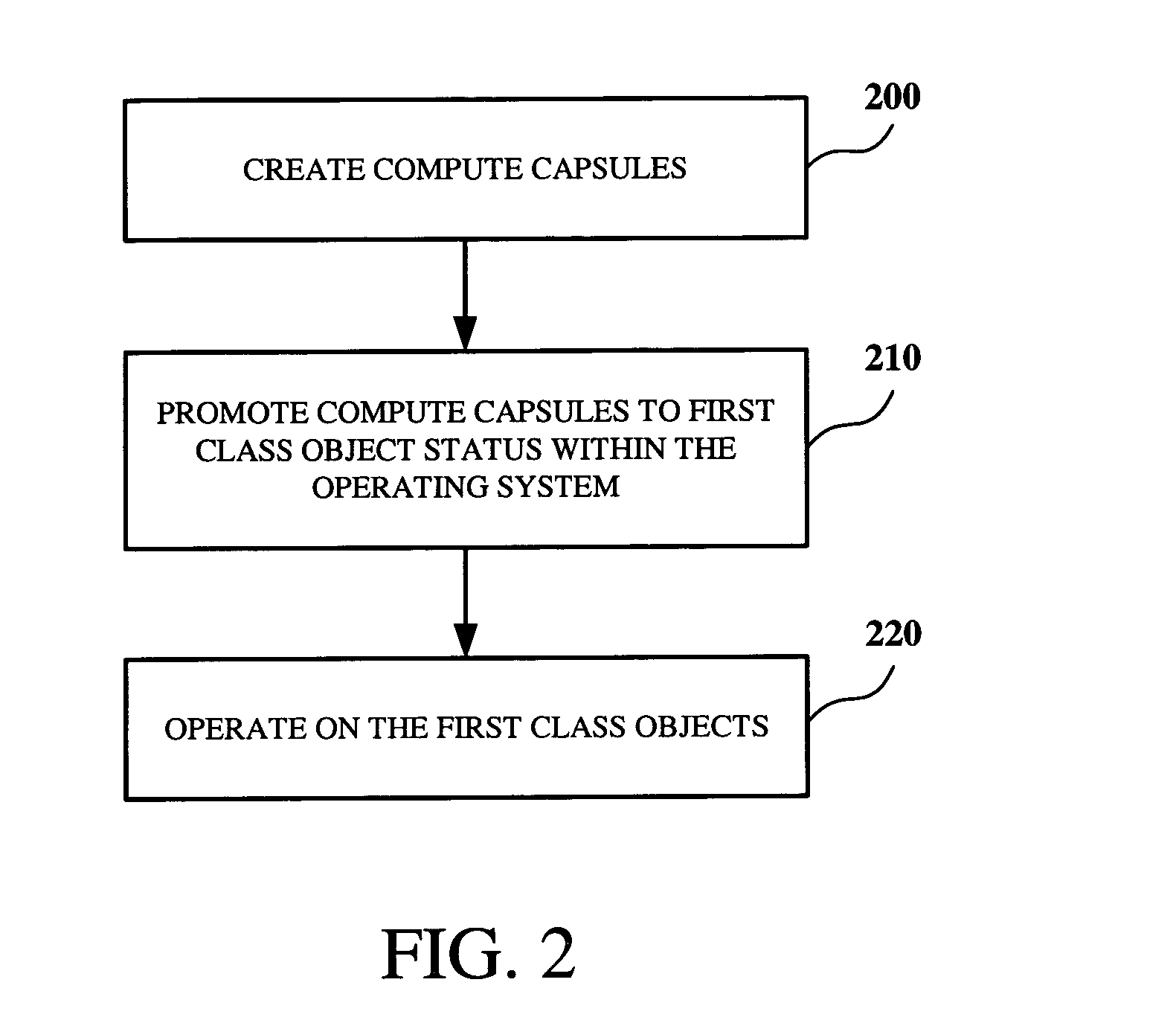
Method and apparatus for aggregate resource management of active computing environments
InactiveUS7162719B2Isolation performanceGuaranteed sharingEnergy efficient ICTResource allocationOperational systemFile system
The present invention is for aggregate resource management of active computing environments. According to one or more embodiments of the present invention a compute capsule is provided. A capsule encapsulates an active computing environment. An active computing environment comprises one or more processes and the complete state necessary for the execution of those processes. Within the operating system, compute capsules are promoted to first class objects. Once promoted to first class object status, the compute capsule can be assigned resources, subjected to auditing constraints, and subjected to security policies. In one embodiment, resource management algorithms are applied to the promoted compute capsules. In another embodiment, a compute capsule that encapsulates a user's computing session can be assigned a guaranteed share of computing resources. In another embodiment, compute capsules are restricted from accessing the network or certain portions of the file system.
Owner:ORACLE INT CORP
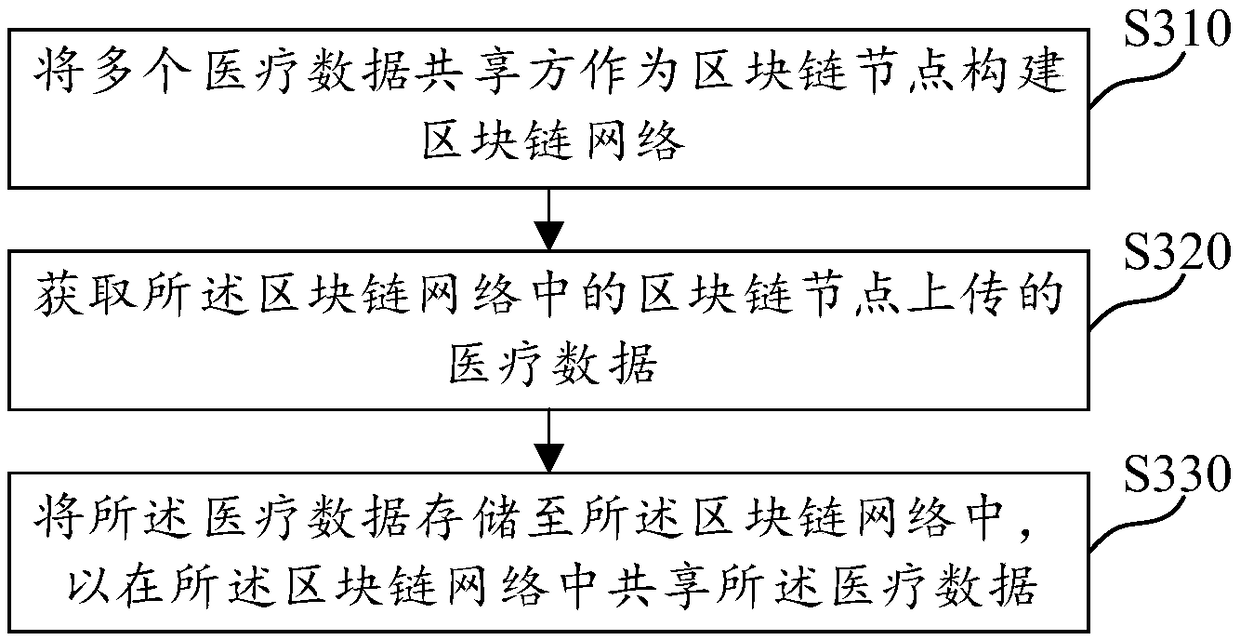
Medical data sharing method and apparatus, computer-readable medium and electronic device
Embodiments of the present invention provide a block chain-based medical data sharing method and apparatus, a computer-readable medium, and an electronic device. The medical data sharing method comprises the following steps: taking a plurality of medical data sharing parties as a block link node to construct a block link network; acquiring medical data uploaded by a block chain node in the block chain network; storing the medical data into the block chain network to share the medical data in the block chain network. The technical scheme of the embodiment of the invention ensures that a plurality of medical data sharing parties can realize the sharing of the medical data through the block chain network, and at the same time, due to the decentralized storage characteristic of the block chainnetwork, the safety of the medical data released to the block chain network can be ensured, thereby realizing the safety and controllability of the medical data.
Owner:TENCENT TECH (SHENZHEN) CO LTD
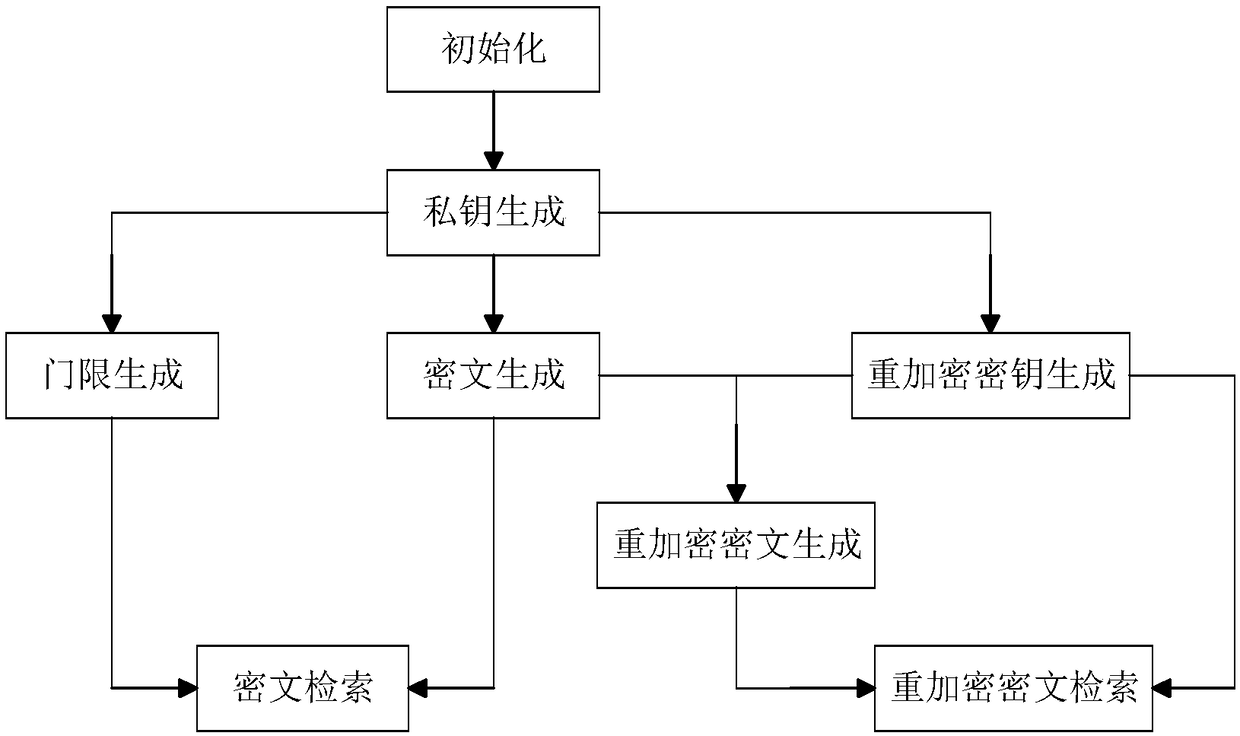
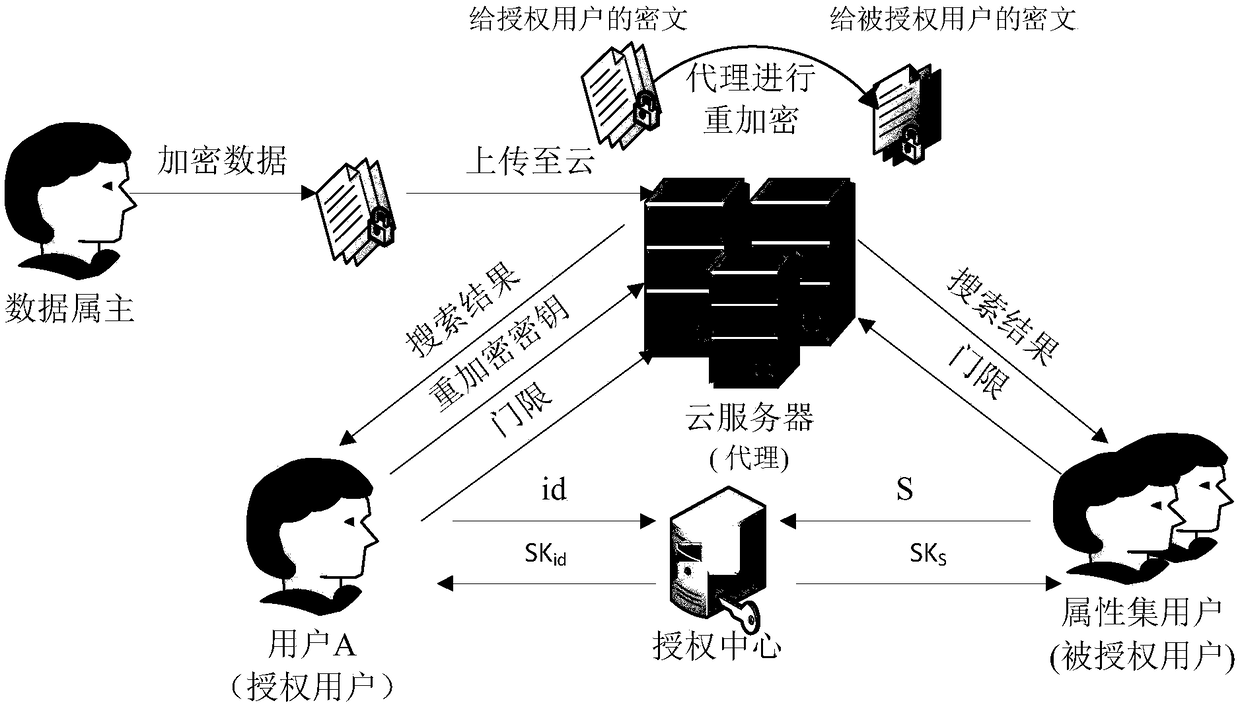
Attribute-based ciphertext searching system and method in support of proxy re-encryption
ActiveCN108418681AImplement fine-grained descriptionPrivacy protectionKey distribution for secure communicationAccess structureConfidentiality
The invention discloses an attribute-based ciphertext searching system and method in support of proxy re-encryption. According to the method, two functions that a user securely carries out searching and effectively shares searching authority in a cloud environment are realized at the same time. According to the method, through adoption of an LSSS linear secret sharing scheme, an attribute of an access user can be described in fine granularity, and the relatively high computing efficiency is achieved. In a threshold generation phase, a blind technology is carried out on a user key through utilization of a random value, and then the user key is submitted to a cloud server, so the confidentiality and security of the user key are ensured. A searching authority entrusting problem when an authorization user is offline in practical application is taken into consideration. A proxy re-encryption technology is imported, and the cloud server converts a ciphertext, so the encryption / decryption pressure of a data owner is migrated, and the system efficiency is greatly improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
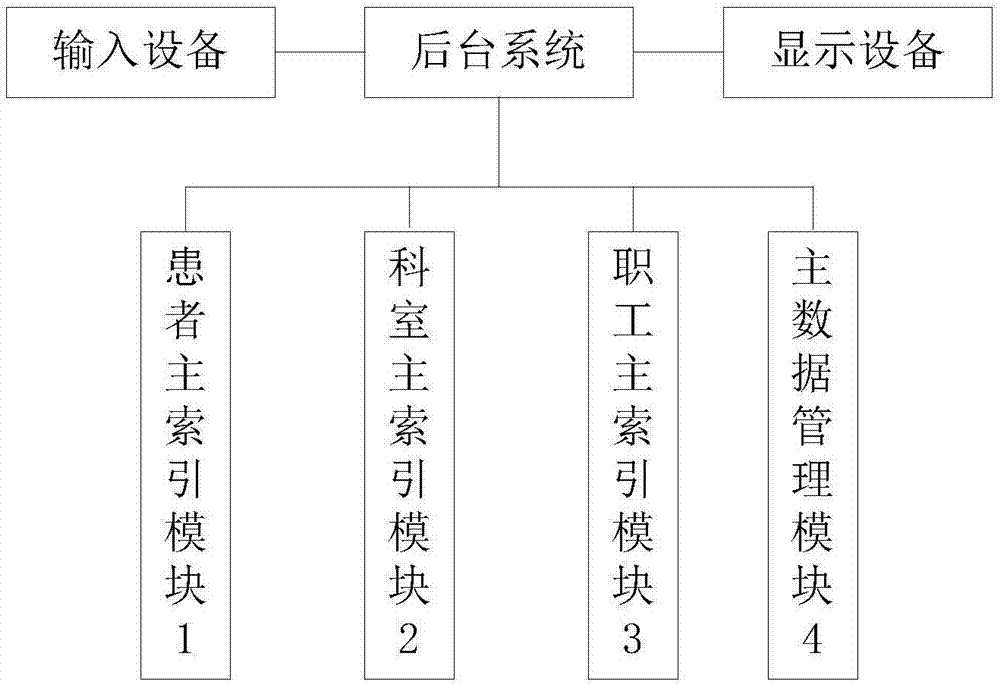
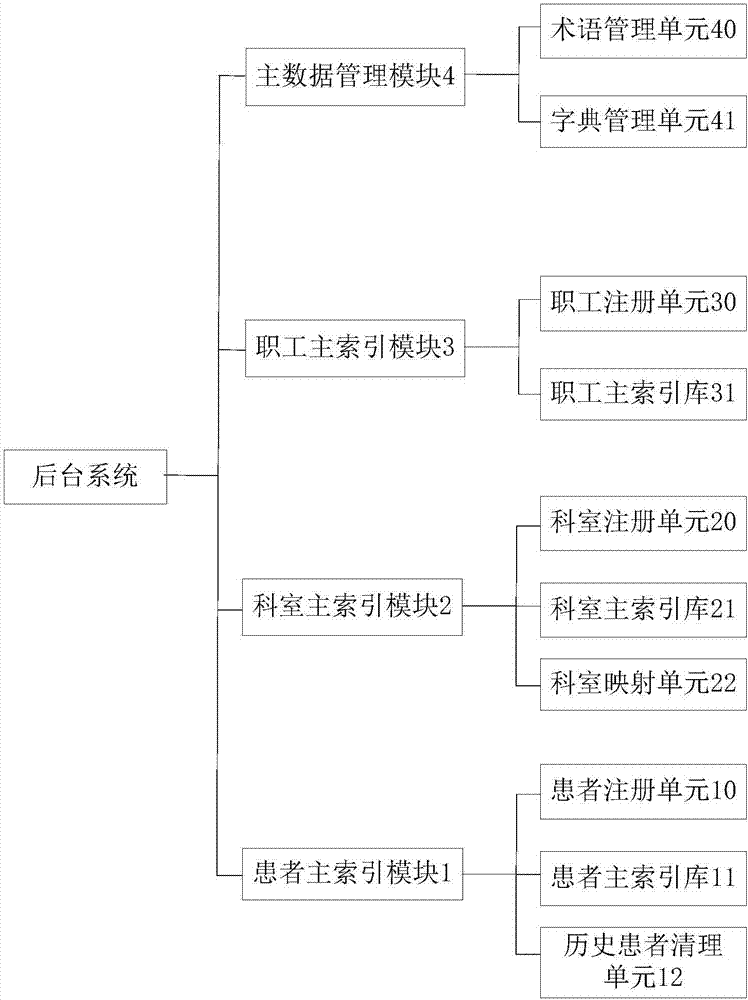
Doctor and patient data management system and method
InactiveCN107194167AAchieve uniqueThe only guaranteeSpecial data processing applicationsInformation sharingPatient data
The invention provides a doctor and patient data management system and method. The system comprises a patient main index module, a department main index module, a staff main index module and a main data management module, wherein the patient main index module generates patient main index information according to patient information and provides query and subscription services of the patient main index information; the department main index module generates department main index information according to department information and provides query and subscription services of the department main index information; the staff main index module generates staff main index information according to medical personnel information and provides query and subscription services of the staff main index information; and the main data management module obtains and stores standard business terms and standard business dictionaries, and provides query and subscription services of the standard business terms and the standard business dictionaries. According to the system and the method, unique patient main index, department main index and staff main index are realized among medical information systems, so that unique business terms and business dictionaries among the systems are ensured, and system connection and information sharing can be realized.
Owner:EWELL TEHCNOLOGY CO LTD
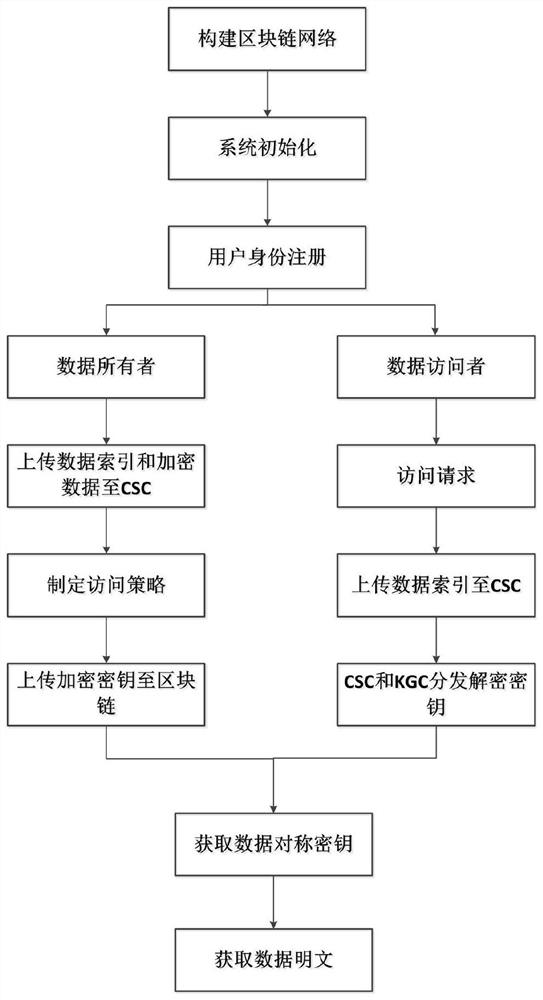
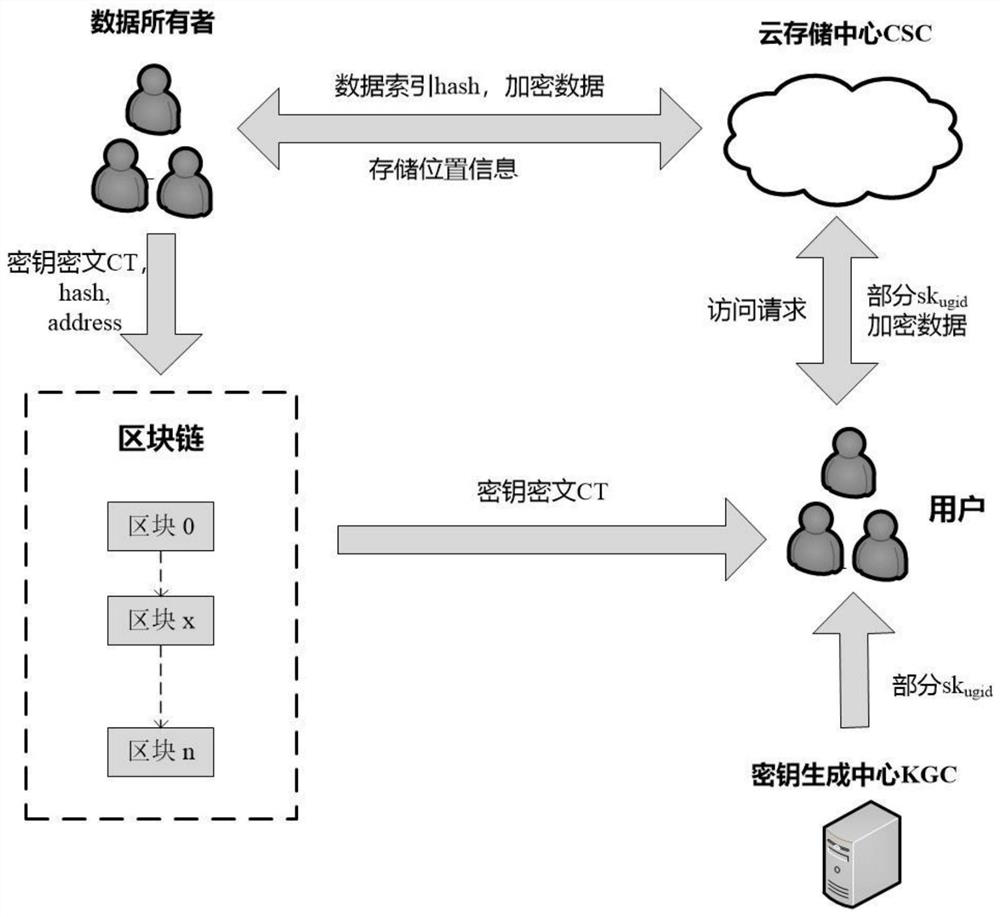
Cloud data sharing method based on block chain
ActiveCN112019591AGuaranteed storage securityGuaranteed sharingKey distribution for secure communicationUser identity/authority verificationBlockchainCloud storage
The invention discloses a cloud data sharing method based on a block chain, and the method comprises the steps: the block chain is constructed, an initialization generator is accessed, and the systeminitialization is performed; the user performs identity registration and joins the blockchain network to obtain an identity ID; the data owner uploads the data index and the encrypted data to the CSC;after successful uploading, the cloud storage center CSC stores the encrypted data and the index list; after the shared data is uploaded successfully, the data owner formulates an access strategy, encrypts an owner key, generates a new block in the block chain, and records data uploading information and an encryption key; the user sends an access request to a cloud storage center CSC and uploadsa data index needing to be accessed; the user submits attributes to the KGC and the CSC, and the KGC and the CSC jointly generate and issue a key to the user according to the attributes; and the useracquires the symmetric key ciphertext and decrypts the symmetric key ciphertext. According to the invention, the encryption key of the data owner is managed through the blockchain, an effective key management mechanism is provided, and the problem of secure sharing of cloud data is solved.
Owner:NANJING UNIV OF POSTS & TELECOMM
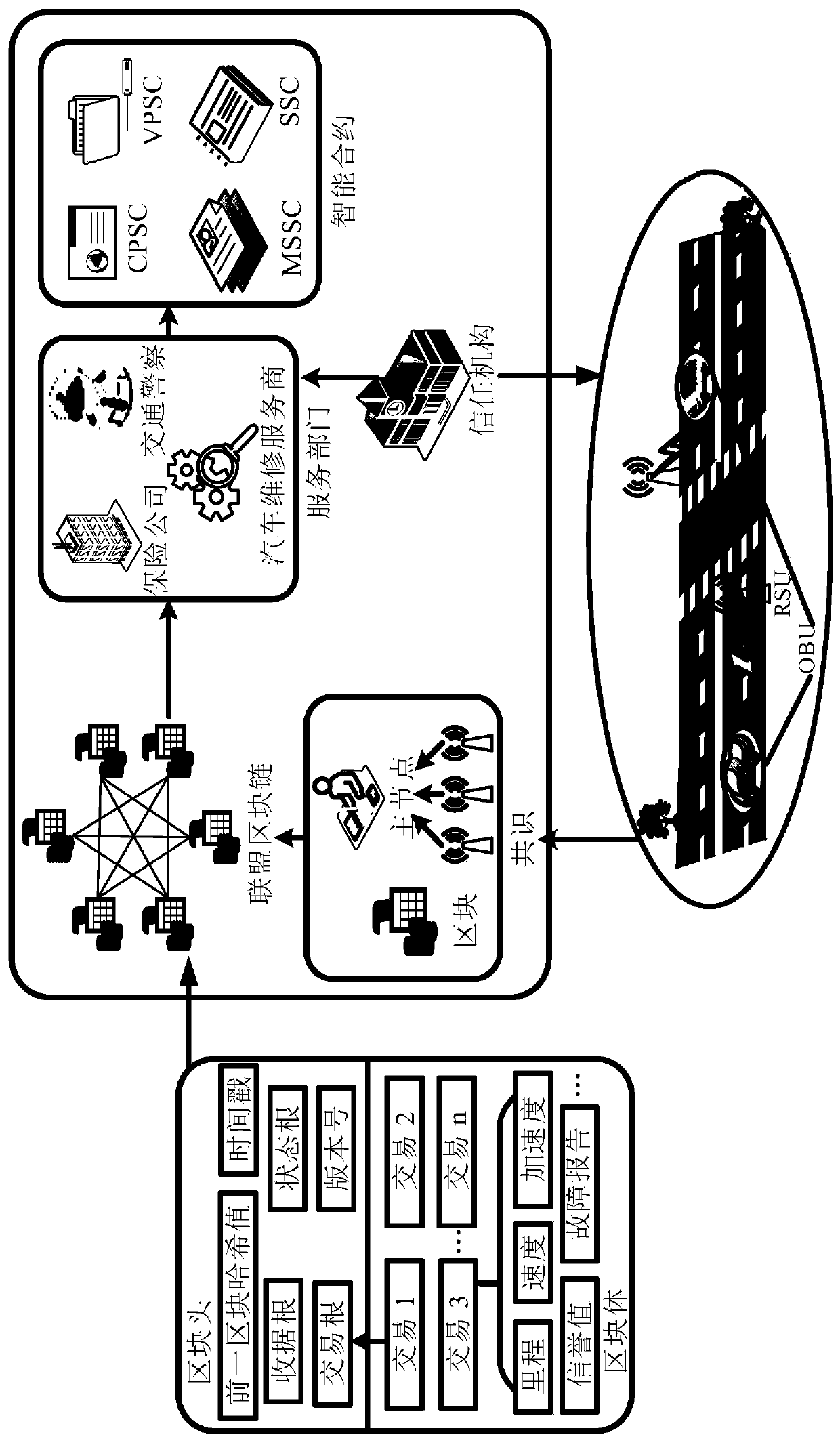
Intelligent traffic data safety sharing method based on alliance block chain
ActiveCN111050317AEnsure safetyGuaranteed confidentialityDigital data information retrievalParticular environment based servicesService departmentIn vehicle
An intelligent traffic data safety sharing method based on an alliance block chain comprises a trust institution, a vehicle-mounted unit, a roadside unit and a service department, and the service department is composed of an vehicle maintenance service provider, a traffic police and an insurance company. The vehicle-mounted unit encrypts the traffic data to generate a ciphertext and sends the ciphertext to the roadside unit; the roadside unit main node packages the ciphertext to generate a block, and then connects the block to a block chain; and the service department obtains the correspondingciphertext from the blockchain according to the attribute set and the keyword, and provides customized service for the vehicle-mounted unit by utilizing the decrypted information. According to the method, a data centralized management mode of traditional intelligent transportation is overturned, single-point crash and data monopoly are prevented, collusion attacks are effectively avoided, the integrity and confidentiality of data are guaranteed, safe sharing of the data is achieved, and the method has more advantages in the aspects of communication expenditure and calculation expenditure.
Owner:JIANGXI UNIV OF SCI & TECH
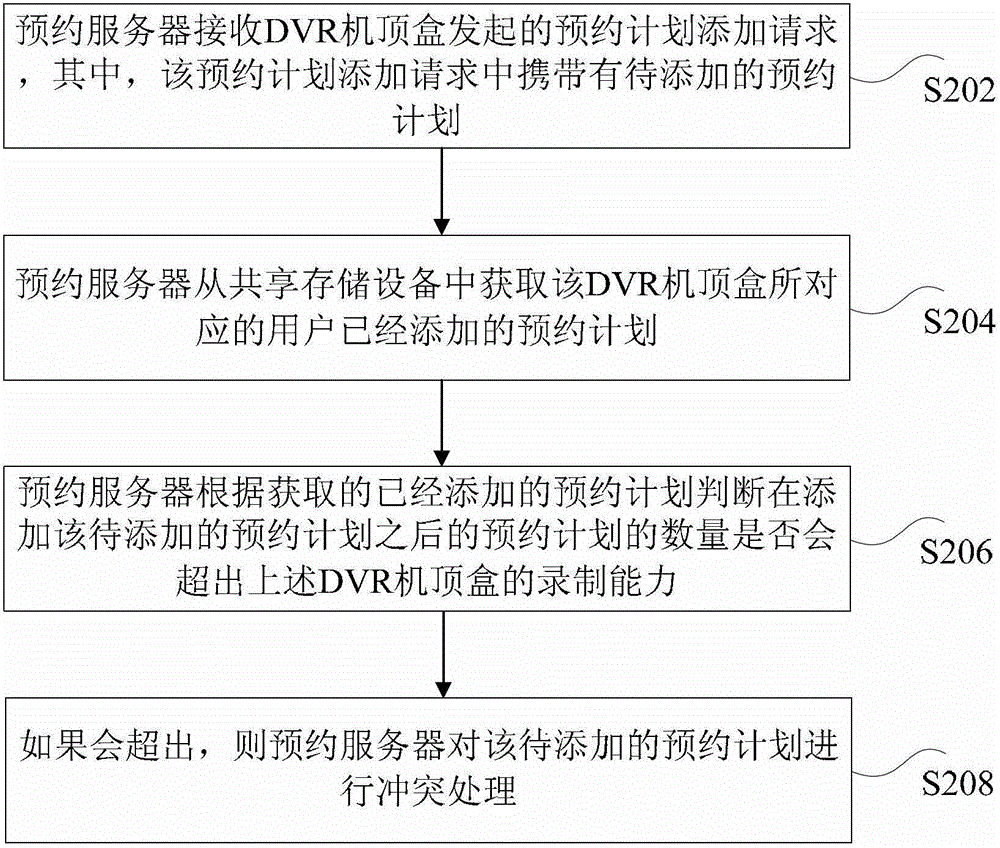
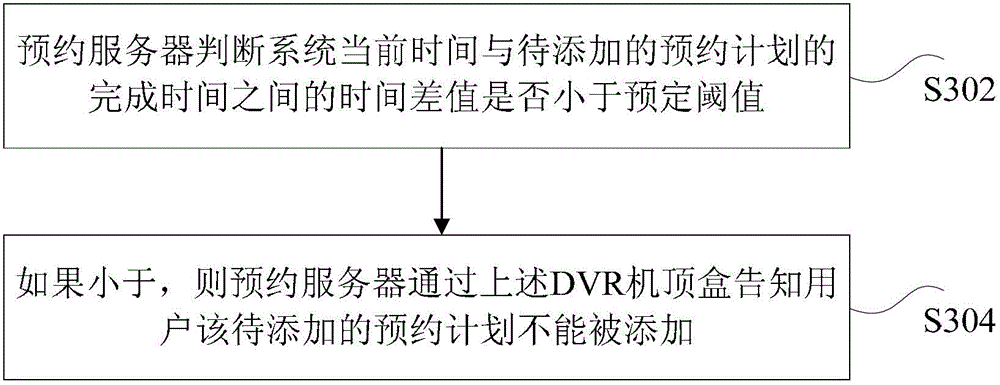
IPTV reservation system and reservation plan adding method based on same
ActiveCN102917249AGuaranteed efficient processingEasy loadingSelective content distributionReservation systemSet top box
The invention discloses an IPTV reservation system and a reservation plan adding method based on the same. The method comprises the following steps: a reservation server receives a reservation plan adding request generated by a DVR set-top box, wherein the reservation plan adding request contains reservation plans to be added; the reservation server acquires the reservation plans added by a user from share storage equipment Dcache, which is corresponding to the DVR set-top box; and the reservation server judges whether the number of the reservation plans added with the reservation plans to be added is over the recording capacity of the DVR set-top box according to the added reservation plans, if so, the reservation server carries out interference process for the reservation plans to be added. According to the invention, the technical problems of the prior art that the load of the reservation server is over large and the fault processing capacity of the system is lower, and technical effects of reduction of the load of the reservation server and improvement on fault processing capacity are obtained.
Owner:ZTE CORP
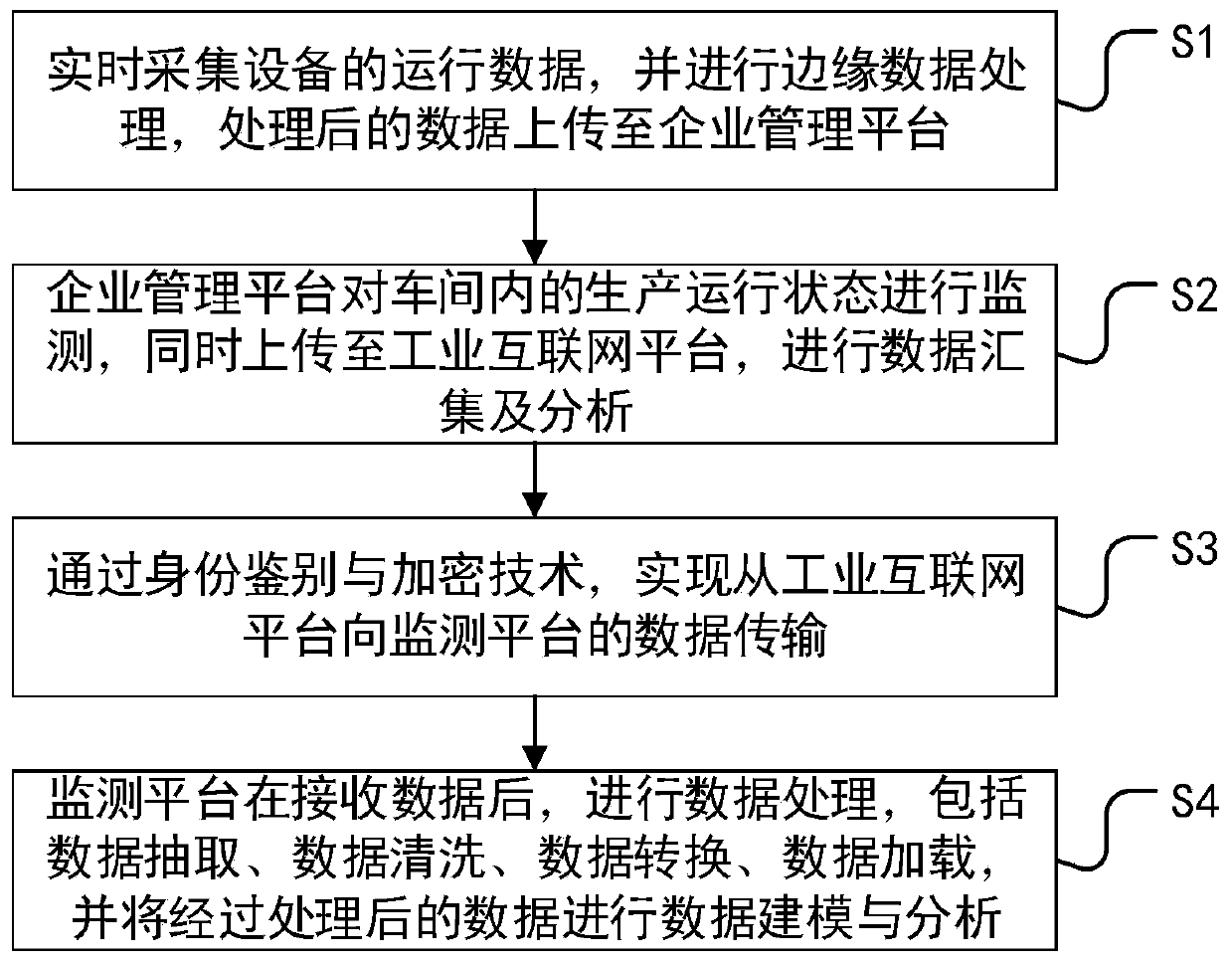
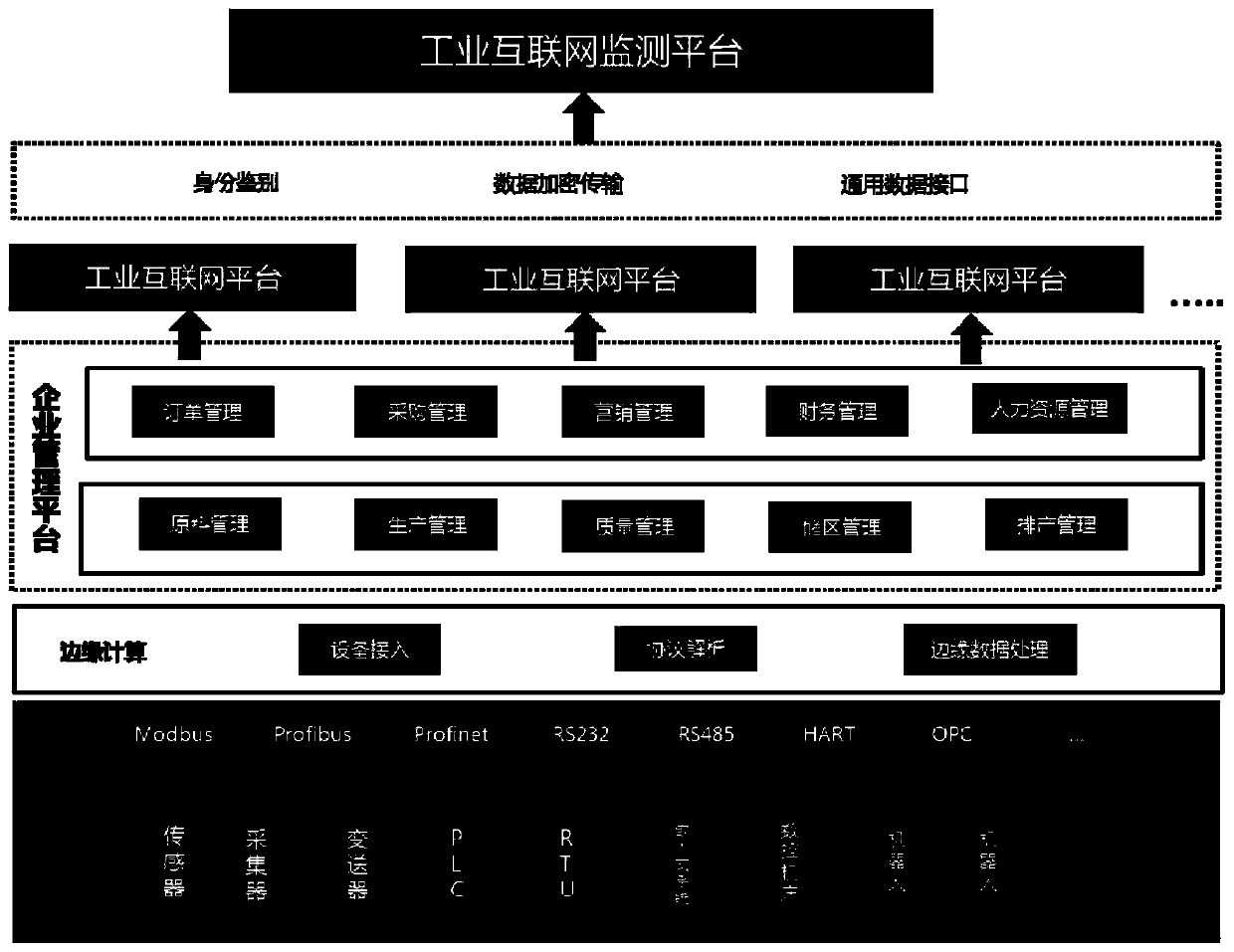
Industrial Internet platform monitoring data transmission and exchange method and system
InactiveCN109857732AEnsuring Integrity and ConfidentialityGuarantee normativeDatabase management systemsTransmissionData conversionData transmission
The invention provides an industrial Internet platform monitoring data transmission and exchange method and system, and the method comprises the steps: the operation data of equipment is collected inreal time, the edge data processing is carried out, and the processed data is uploaded to an enterprise management platform; the enterprise management platform monitors the production operation statein the workshop and uploads the production operation state to the industrial Internet platform for data collection and analysis; data transmission from the industrial Internet platform to the monitoring platform is realized through an identity authentication and encryption technology; and the monitoring platform performs data processing after receiving the data, and performs data modeling and analysis on the processed data. According to the invention, the collection of heterogeneous data of various data sources is realized, and the standardization, openness and shareability of monitoring platform data are ensured by setting a data conversion standard, so that the modeling and analysis of the data are facilitated, the problem that industrial data cannot be shared in the prior art is solved,the data sharing is realized, and the utilization rate of information resources is improved.
Owner:SHANDONG ELECTRONICS INFORMATION PROD INSPECTION INST
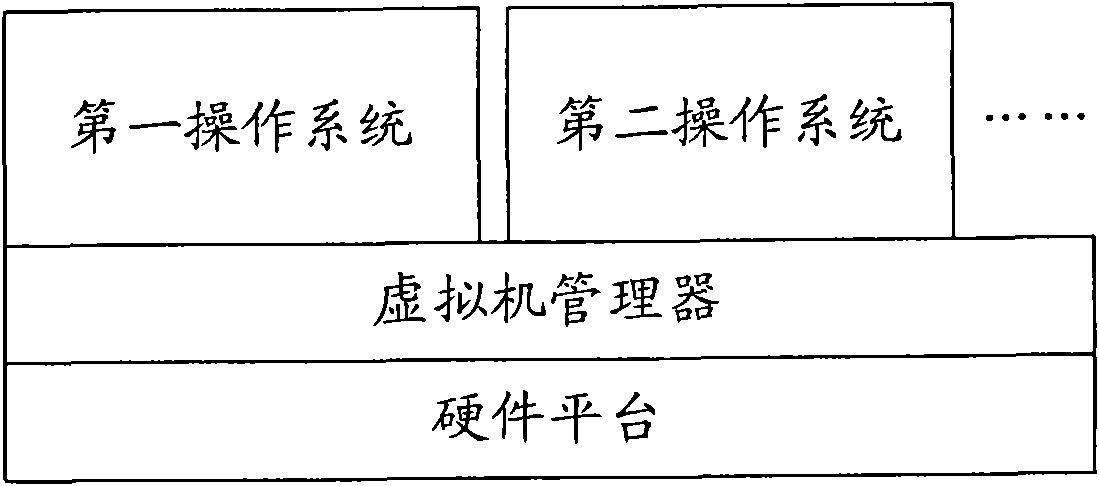
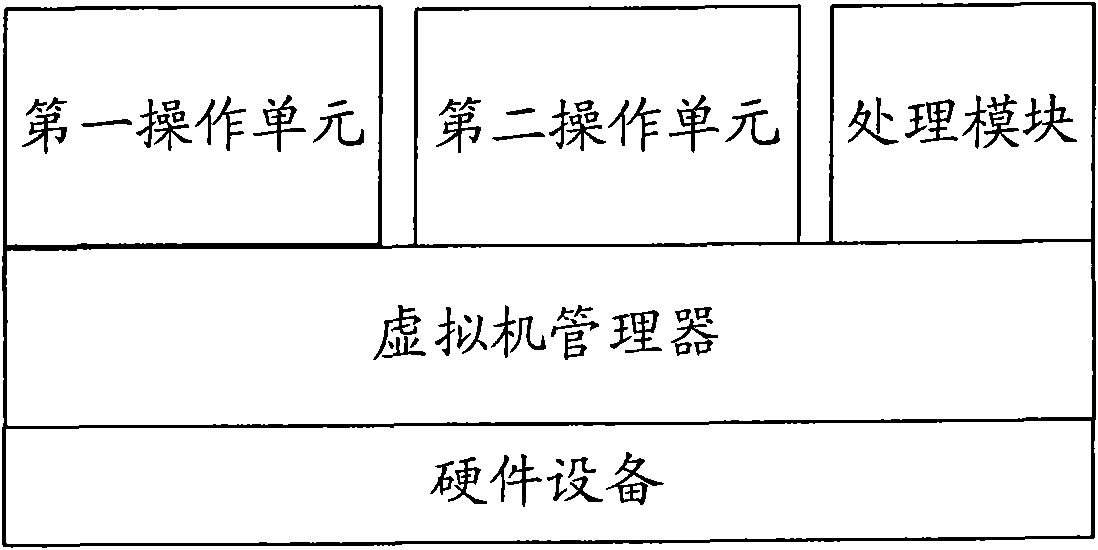
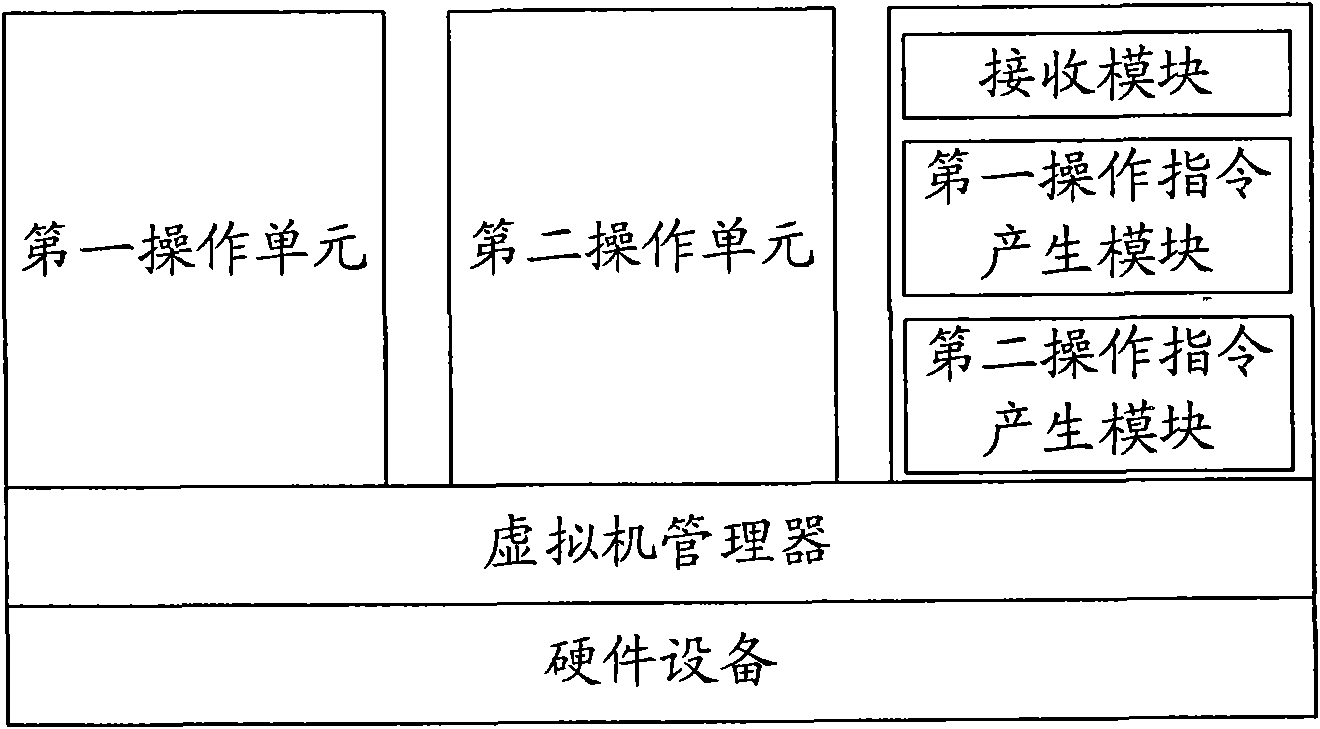
Computer and method for dynamically switching equipment in virtual environment
ActiveCN101685404AGuaranteed performanceGuaranteed sharingProgram initiation/switchingSoftware simulation/interpretation/emulationComputer hardwareOperational system
The invention provides a device dynamically switching equipment in a virtual environment and a method, wherein the equipment comprises a processing module which is used for receiving a moving-out command of a hardware equipment to be moved out, and simulating some moving-out or insertion events for the hardware equipment at a bottom layer through a virtual machine manager according to the moving-out command, or moving the hardware equipment from a first operating system to a second operating system through moving-out or insertion operation to the hardware equipment in each operation system through application programs, so that the hardware equipment can be used only by the second operating system. Due to the adoption of the technical scheme, all the operating systems of the computer can share the hardware equipment independently, thus the performance and the sharing property of the hardware equipment are ensured, and the hardware equipment can be switched among different operating systems.
Owner:LENOVO (BEIJING) LTD
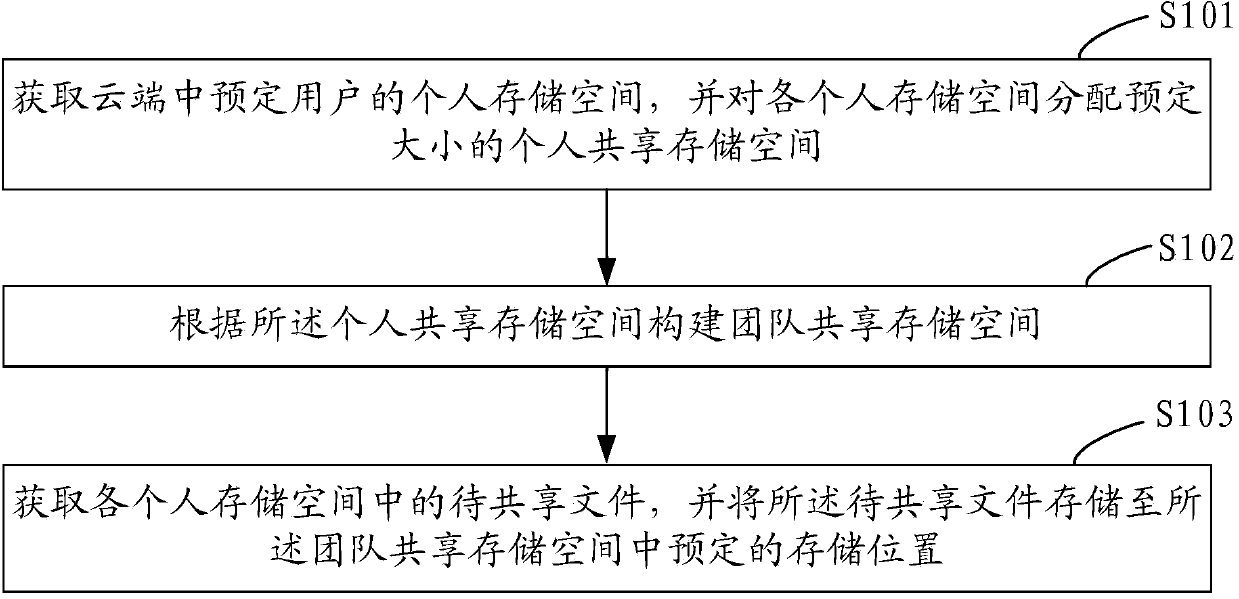
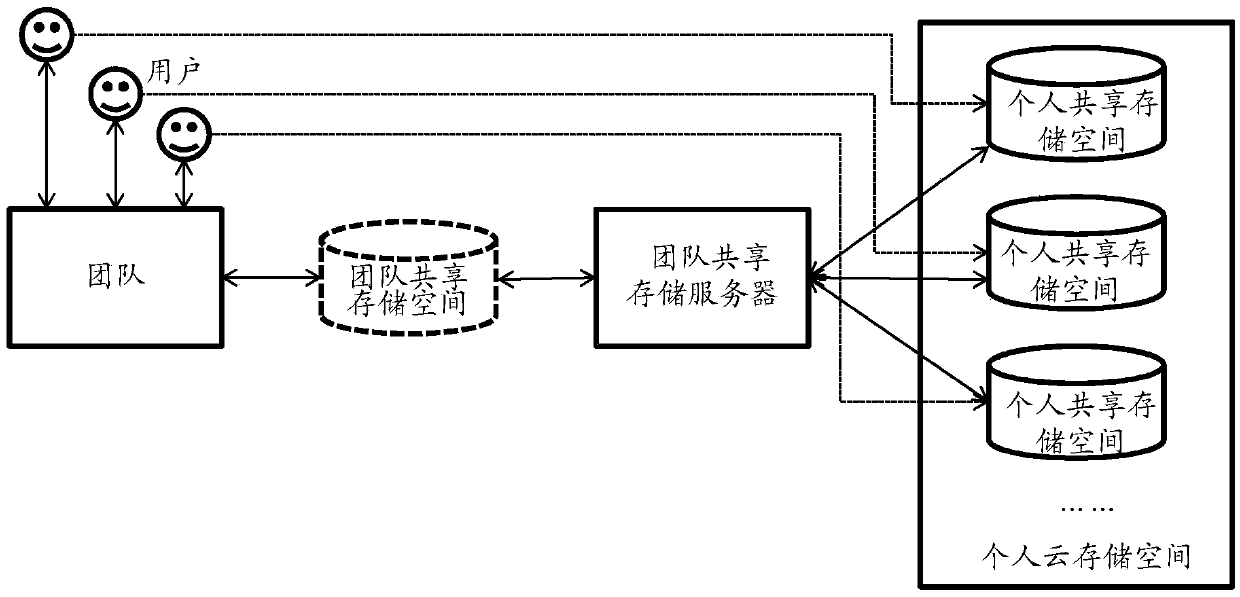
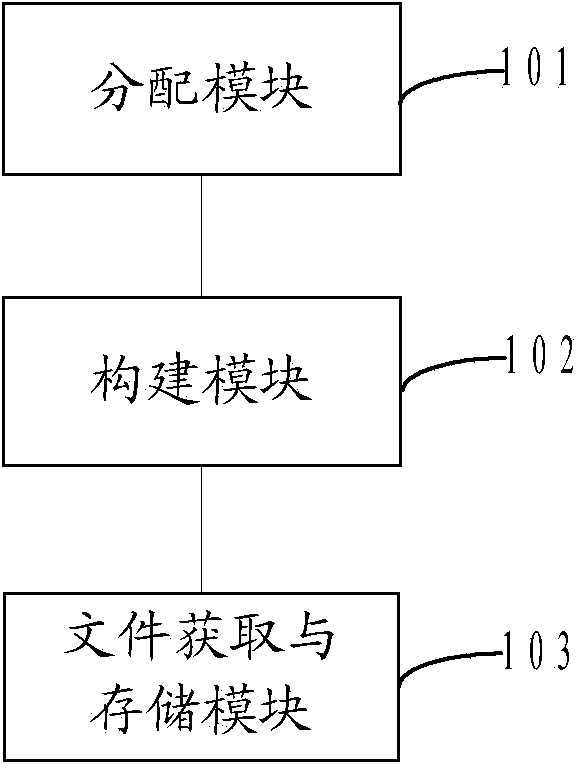
Method and system for achieving team shared storage
ActiveCN103744618ALow costAvoid public accessInput/output to record carriersTransmissionSpace allocationFile storage
The invention provides a method and a system for achieving team shared storage. The method includes the following steps: acquiring individual personal storage spaces of preset users in the cloud, distributing individual shared storage spaces with preset size for the individual storage spaces, constructing a team shared storage space according to the individual shared storage spaces, acquiring files to be shared in each individual storage spare and storing the files to be shared into the preset storage position in the team shared storage space. By means of the method and the system, team shared storage cost can be effectively reduced, the users share the files only among the users in a team, public assess of the files is avoided, and the team shared storage safety is effectively improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
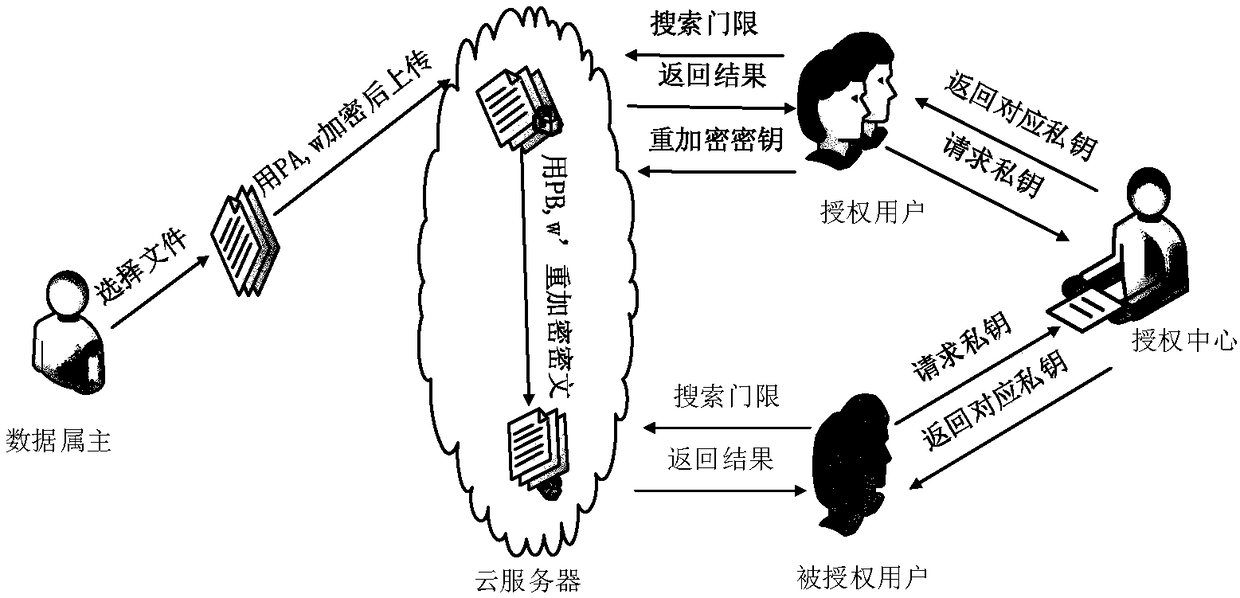
Ciphertext retrieval system and method for supporting proxy re-encryption in combination with identity and attribute
ActiveCN108400871AImprove efficiencySimple key generationPublic key for secure communicationDigital data protectionAccess structureSecret share
The invention discloses a ciphertext retrieval system and method for supporting proxy re-encryption in combination with identity and attribute. The method realizes sharing of a secure and efficient one-to-many user search authority in a cloud environment. The previous identity-based searchable encryption and proxy scheme combines identity-based proxy re-encryption with a searchable encryption scheme to implement agency for a one-to-one search authority. The scheme uses an identity-based encryption method in the initial ciphertext encryption, and adopts an LSSS linear secret shared matrix access structure in the re-encryption phase, which can authorize the ciphertext retrieval authority to other users who conform to the access structure. Therefore, the scheme supports the sharing of a moregranular user search authority and has higher computational efficiency. In the re-encryption threshold generation phase, the user key is blinded by the random value and submitted to a cloud server, ensuring the confidentiality and security of the user key.
Owner:NANJING UNIV OF POSTS & TELECOMM
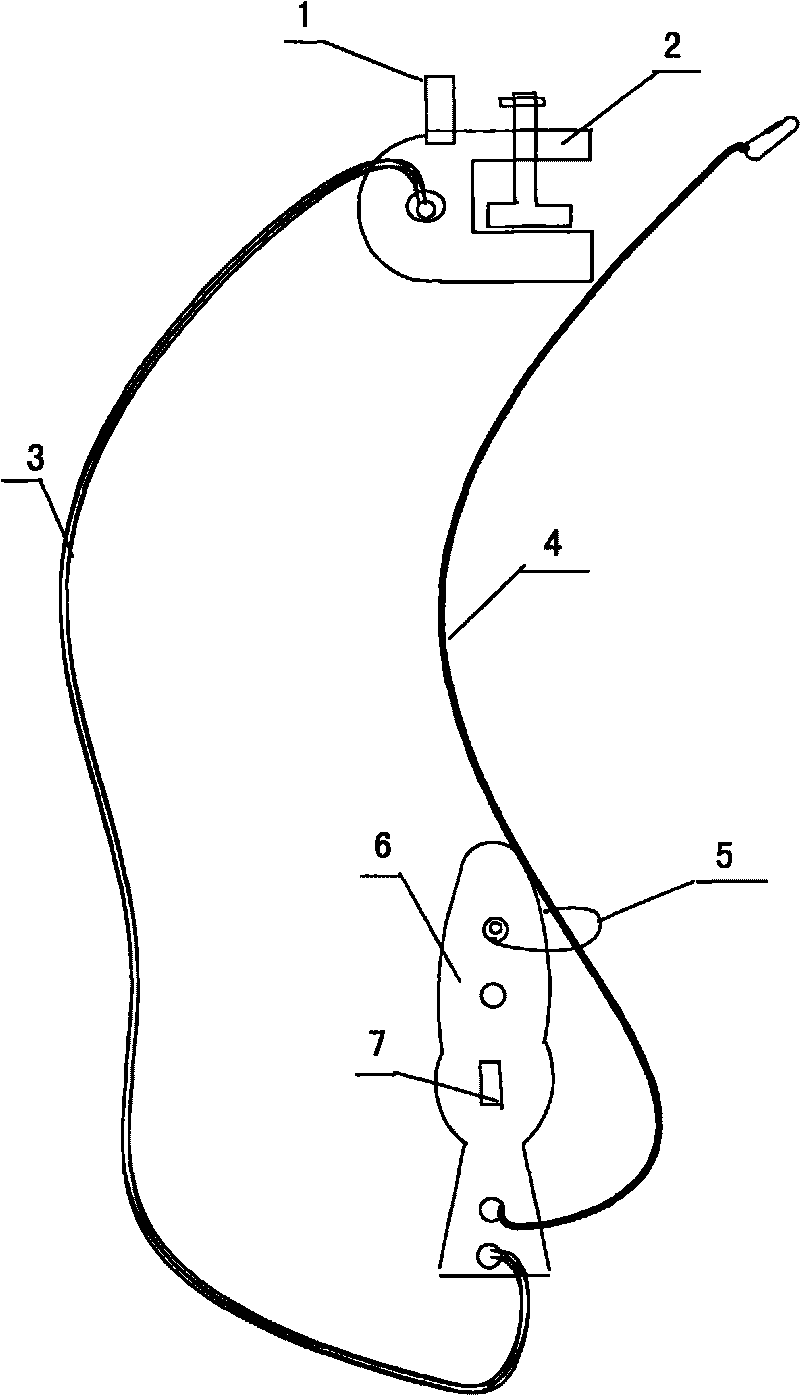
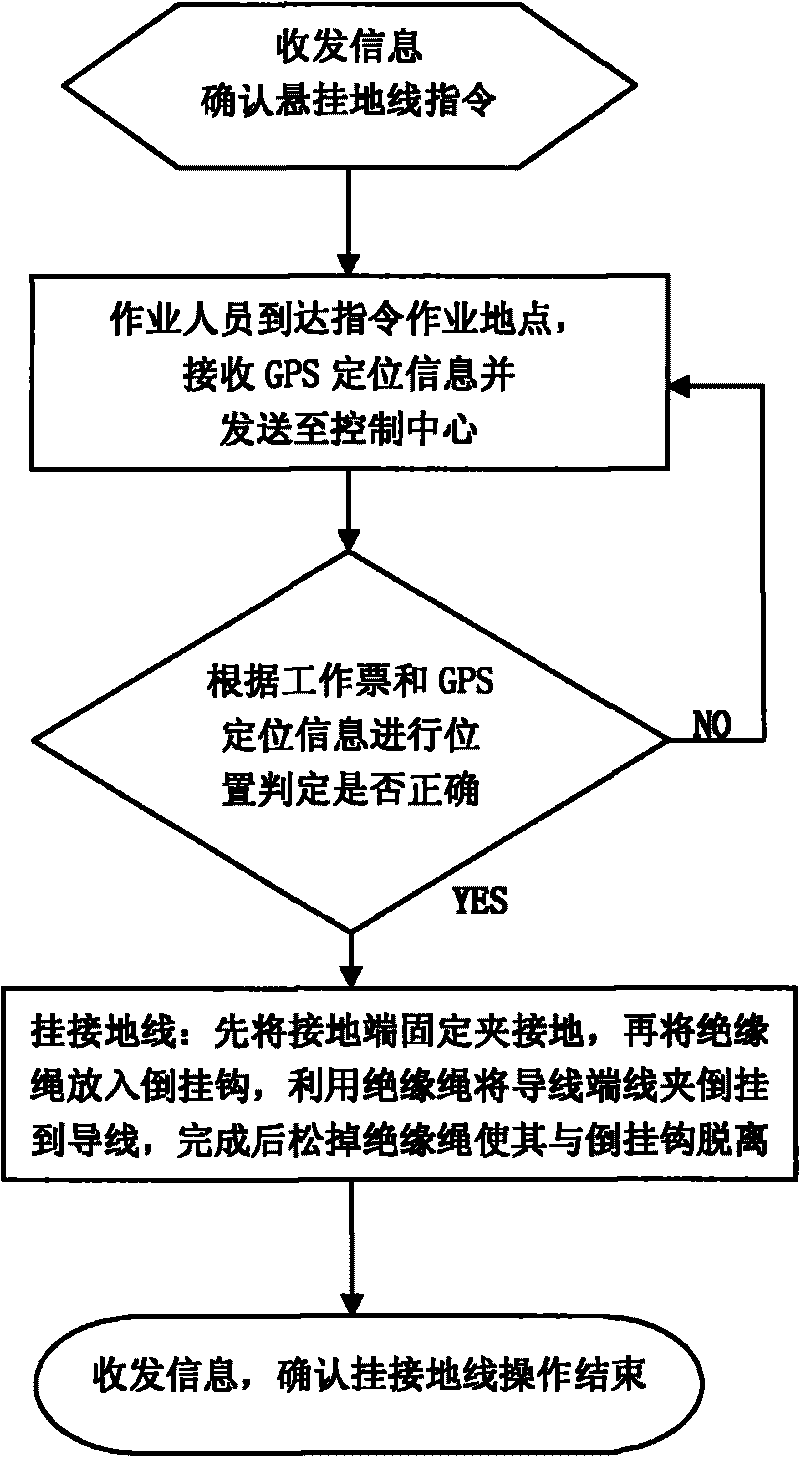
Earthing lines of power transmission lines overhauling and hooking method thereof
ActiveCN101692541AAdd information sourceGuaranteed to be correctProgramme controlComputer controlEngineeringHigh pressure
The invention provides earthing lines of power transmission lines overhauling and a hooking method thereof, and the earthing line comprises a wire end clip capable of hooking and dismantling with a power transmission line, an earth terminal fixed clamp capable of being fixedly connected with an earth terminal and an earth short-circuit line for connecting the wire end clip and the earth terminal fixed clamp. The wire end clip is also connected with an insulating rope for performing the operation of hooking and dismantling the wire end clip, a GPS information transceiver is arranged on the earth terminal fixed clamp, and the wire end clip is also provided with a reversed hook and a magnet sheet. The invention can realize GPS precise location for power transmission line overhauling positions, avoid easily-generated risks of malposition caused by false hooking and dismantling and the process of hanging earthing lines by maintenance personnel, lower work difficulty and be widely used in overhauling earthing protection of high-voltage power transmission line.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
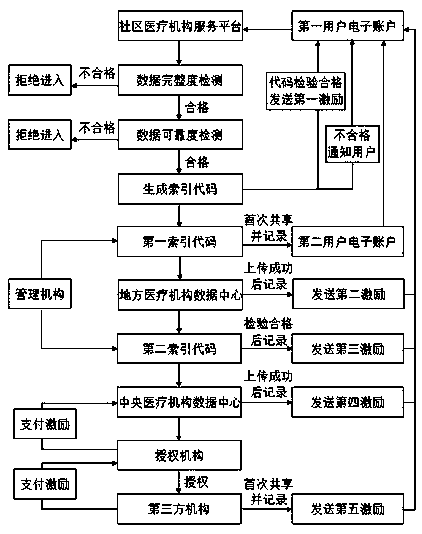
Personal health electronic medical record sharing and querying method based on block chain technology
InactiveCN109243559AAvoid identity verification workAvoid double entryPayment circuitsMarketingMedical recordData information
The invention relates to a personal health electronic medical record sharing and querying method based on the block chain technology. A first index code corresponding to a part of the non-privacy datainformation in the user's personal health data information in a one-to-one way is generated to avoid repeated input of data and the user's identity verification work and provide other users for sharing and querying so as to ensure the good publicity and advertising effect of the user's non-privacy information and play a very good demonstration and imitation effect. A second index code corresponding to all the data information of the user's personal health data information in a one-to-one way is generated to avoid repeated input of the data and the user's identity verification work without providing other users for sharing and querying and only ensure for sharing and querying of the user himself and the relevant medical institutions so as to avoid leakage of the user's private informationand facilitate querying of the user at any time and summary production of big data of the medical institutions.
Owner:南京旭颢信息科技有限公司
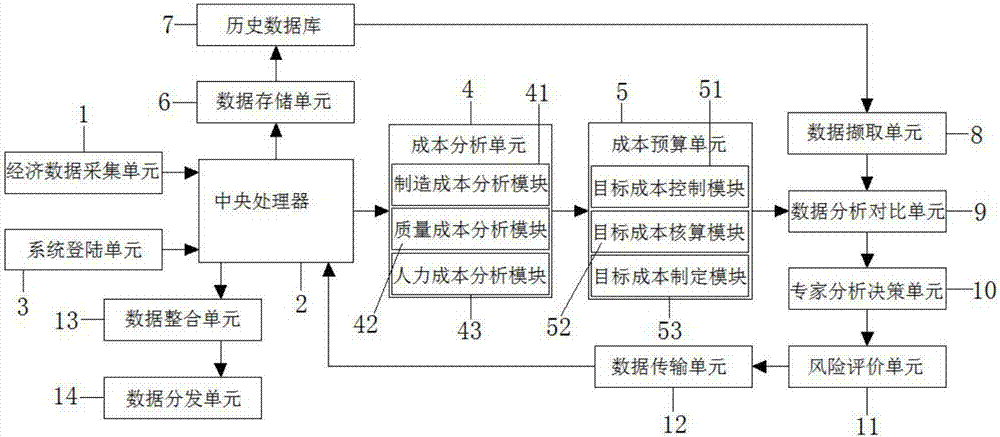
Enterprise inner economic management cost control system
The invention discloses an enterprise inner economic management cost control system in the field of economic cost control technology. The system comprises an economic data acquisition unit. The output end of the economic data acquisition unit is electrically connected with the input end of a central processing unit. The output end of a risk evaluation unit is electrically connected with the input end of a data transmission unit. The output end of the data transmission unit is electrically connected with the input end of the central processing unit. Through acquiring the economic data, comprehensive and systemic cost analysis is performed on the economic data; objective cost budget is performed through a cost budget unit; then a cost system is made through expert analysis and decision; and then risk evaluation is performed on the economic data, thereby ensuring high safety of the economic cost. The enterprise inner economic management cost control system further has advantages of realizing data combination and distribution, ensuring data sharing, realizing high data distribution safety, realizing economic data understanding by each layer of the enterprise, realizing high convenience in use, and improving working efficiency.
Owner:LIAONING UNIVERSITY OF PETROLEUM AND CHEMICAL TECHNOLOGY
Aviation service customization system and method based on federated learning technology platform
PendingCN111899076AGuaranteed sharingNo leakageDigital data information retrievalCharacter and pattern recognitionAviationRecommendation model
The invention discloses an aviation service customization system and method based on a federated learning technology platform. The system comprises a federated learning technology platform, a data source module, a data processing module, a local training module and a cloud module. The method comprises the following steps of establishing own local models for airlines and partners by utilizing own source data respectively; and then uploading parameters and gradients of the model to a federated learning technology platform, realizing fusion on the federated learning technology platform so as to establish a new virtual model, performing prediction and updating by utilizing the virtual model, and finally establishing a federated personalized recommendation model. The model established through the method can provide personalized and accurate product recommendation for aviation customers, meanwhile, the modeling process is achieved through a federated learning technology platform, and safetyand privacy of data are guaranteed.
Owner:科技谷(厦门)信息技术有限公司
Intelligent building management method and device, medium and electronic device
PendingCN110703619AGuaranteed sharingGuarantee managementComputer controlProgramme total factory controlVideo monitoringHealth safety
The embodiment of the invention relates to the technical field of information, and provides an intelligent building management method and device, a medium and an electronic device. The method comprises the steps: collecting the position information, health information and environment information of personnel in an intelligent building, and carrying out the video monitoring; comparing the health information of the personnel in the intelligent building with a preset health standard, and predicting whether a health safety risk exists or not; comparing the environment information of the intelligent building with a preset environment standard, and predicting whether an environment safety risk exists or not; analyzing abnormal behaviors in the intelligent building according to video monitoring;and when at least one of the health safety risk, the environment safety risk and the abnormal behavior exists, sending risk prompt information in combination with the position information. According to the embodiment of the invention, the position information, the health information and the environment information of the personnel in the intelligent building are compared with the standard, the health of the personnel and the safety risk existing in the environment are predicted, and early warning information is given in time according to the prediction result.
Owner:TAIKANG LIFE INSURANCE CO LTD
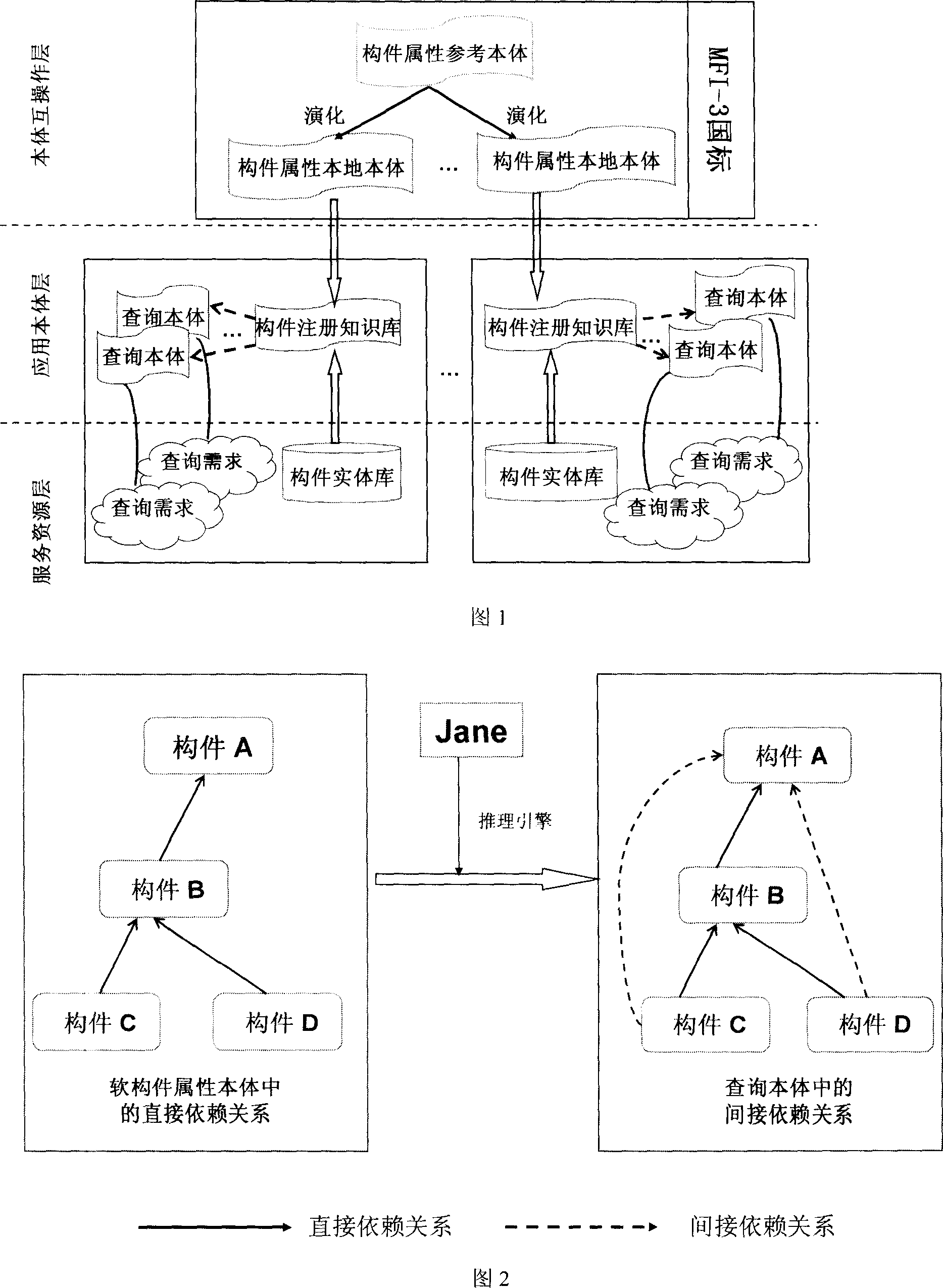
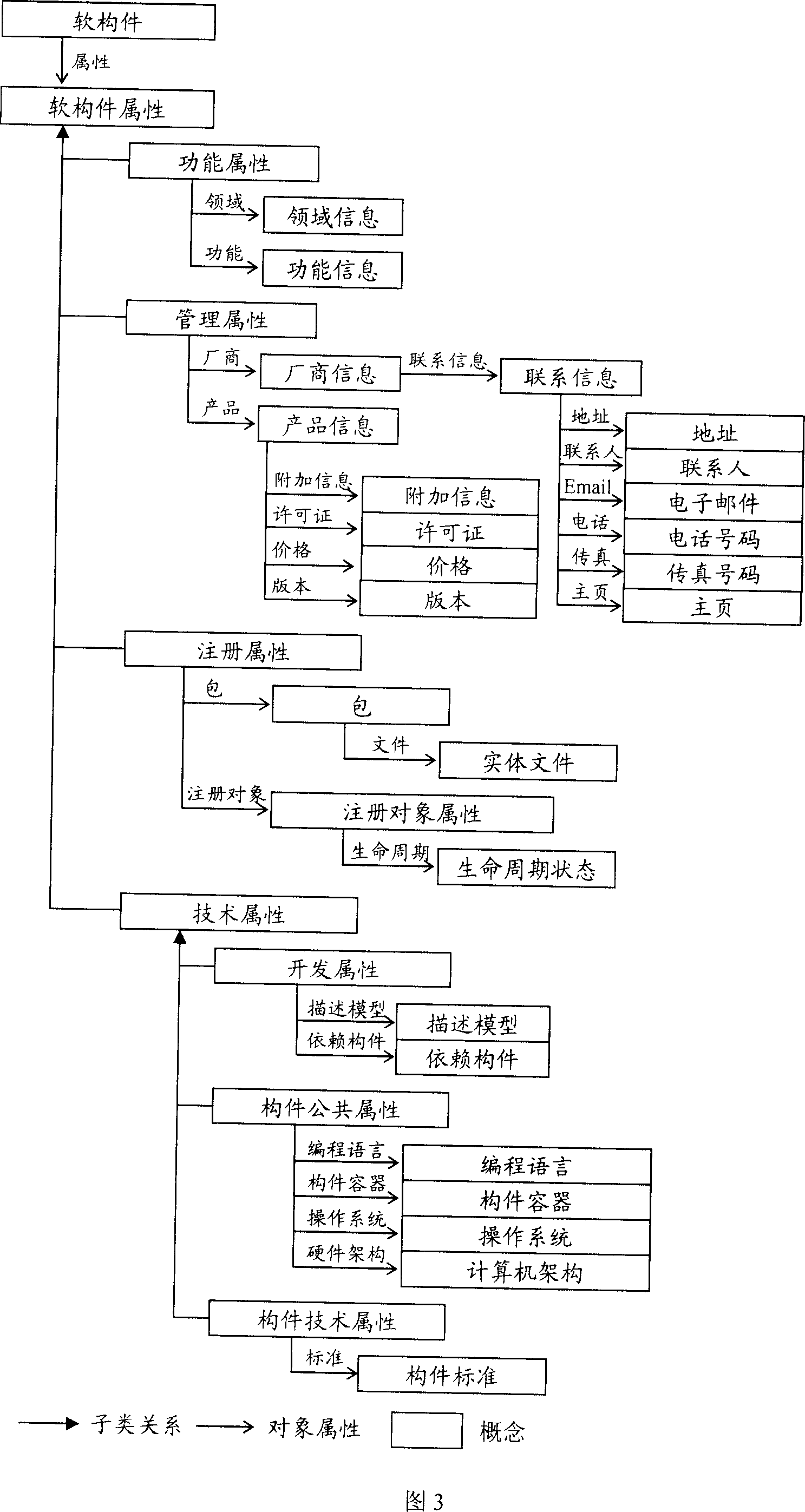
Management method of component library
InactiveCN101017432AStrong opennessImprove general performanceSpecific program execution arrangementsInformation resourceComputer compatibility
This invention relates to one form part management method, which comprises the following steps: a, forming part register knowledge concept module composed of register property and part application sort property; b, forming register knowledge sample module composed of register information concept module property; c, according to the meets to define the register knowledge meanings; d, getting inquire body by form register knowledge database; e, analyzing the information materials from inquire body as inquire and comprehension base to provide form inquire mechanism based on meaning induce.
Owner:WUHAN UNIV
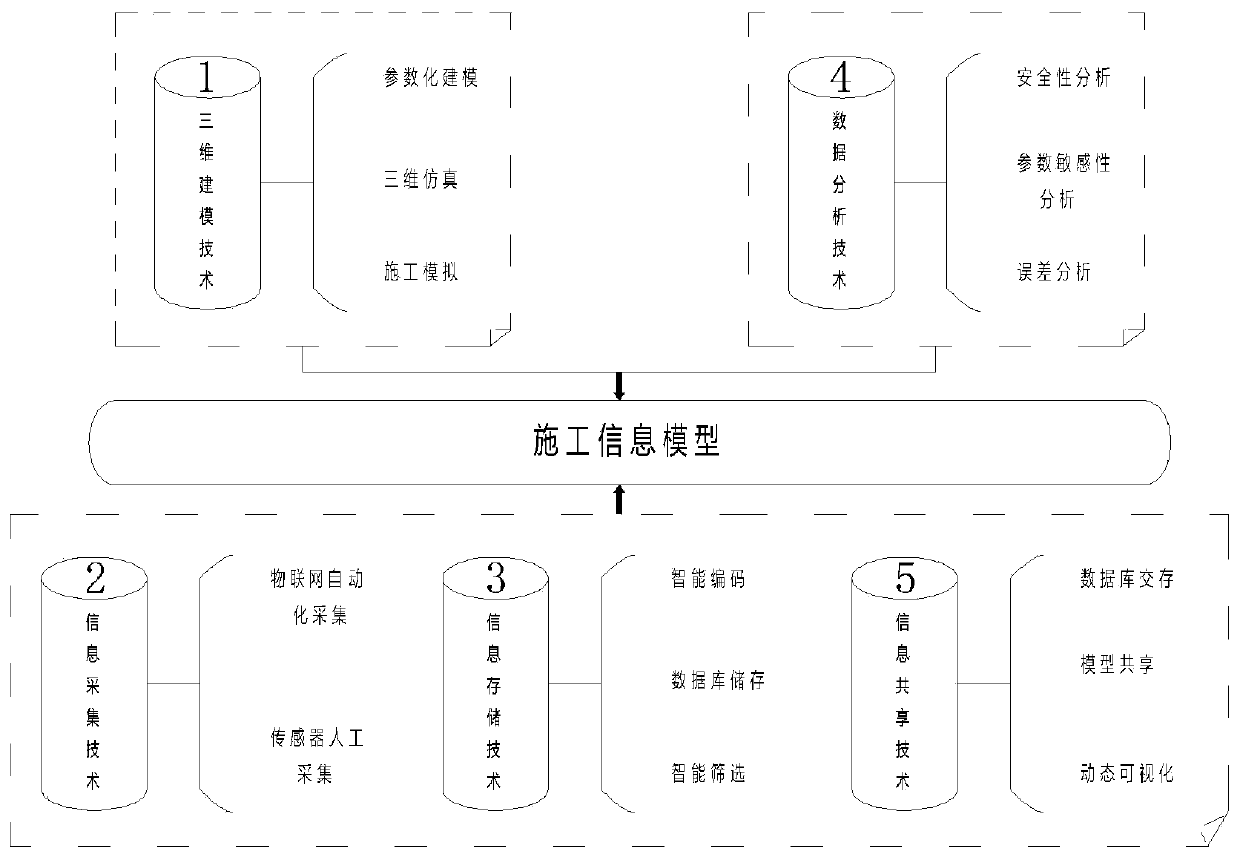
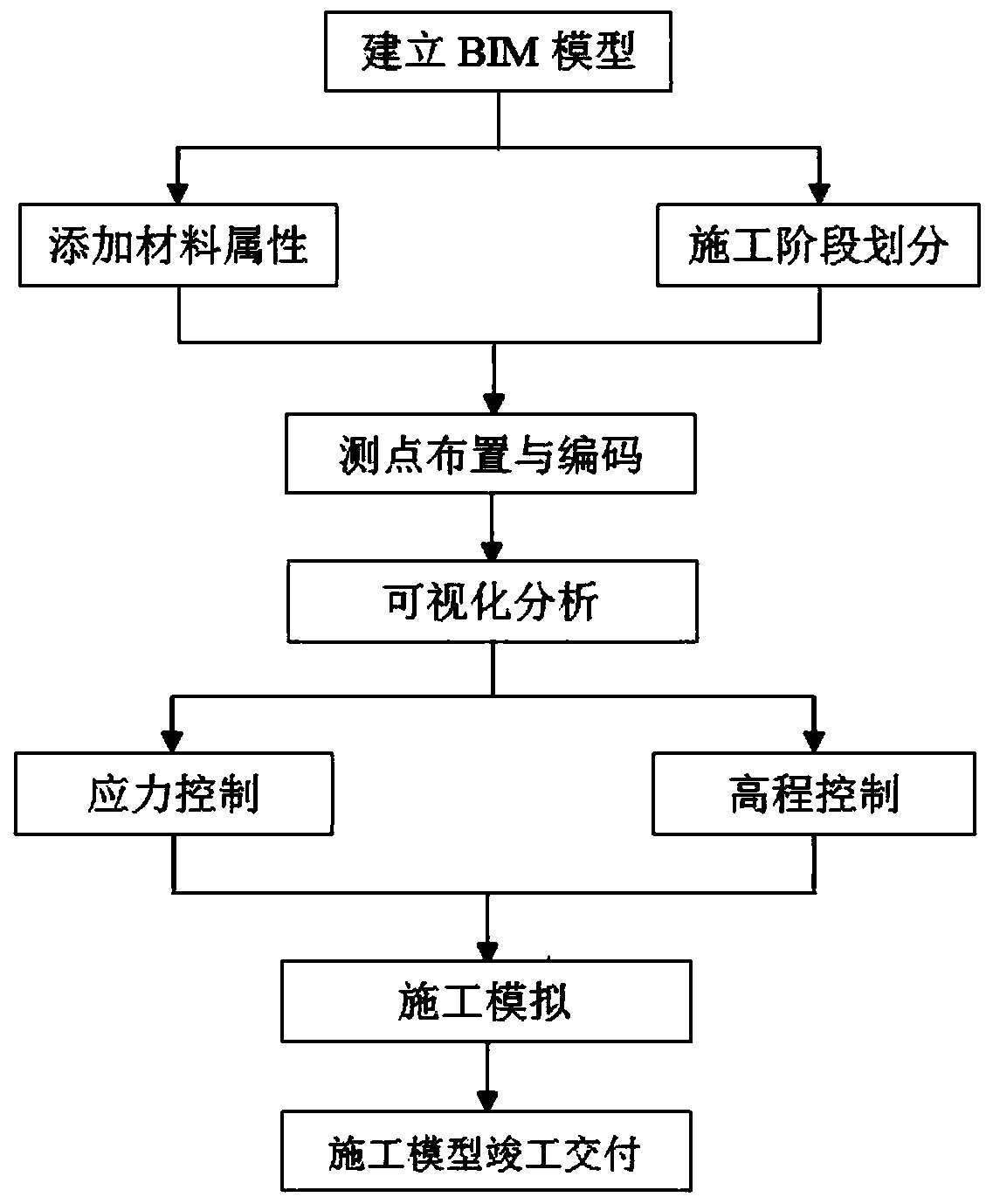
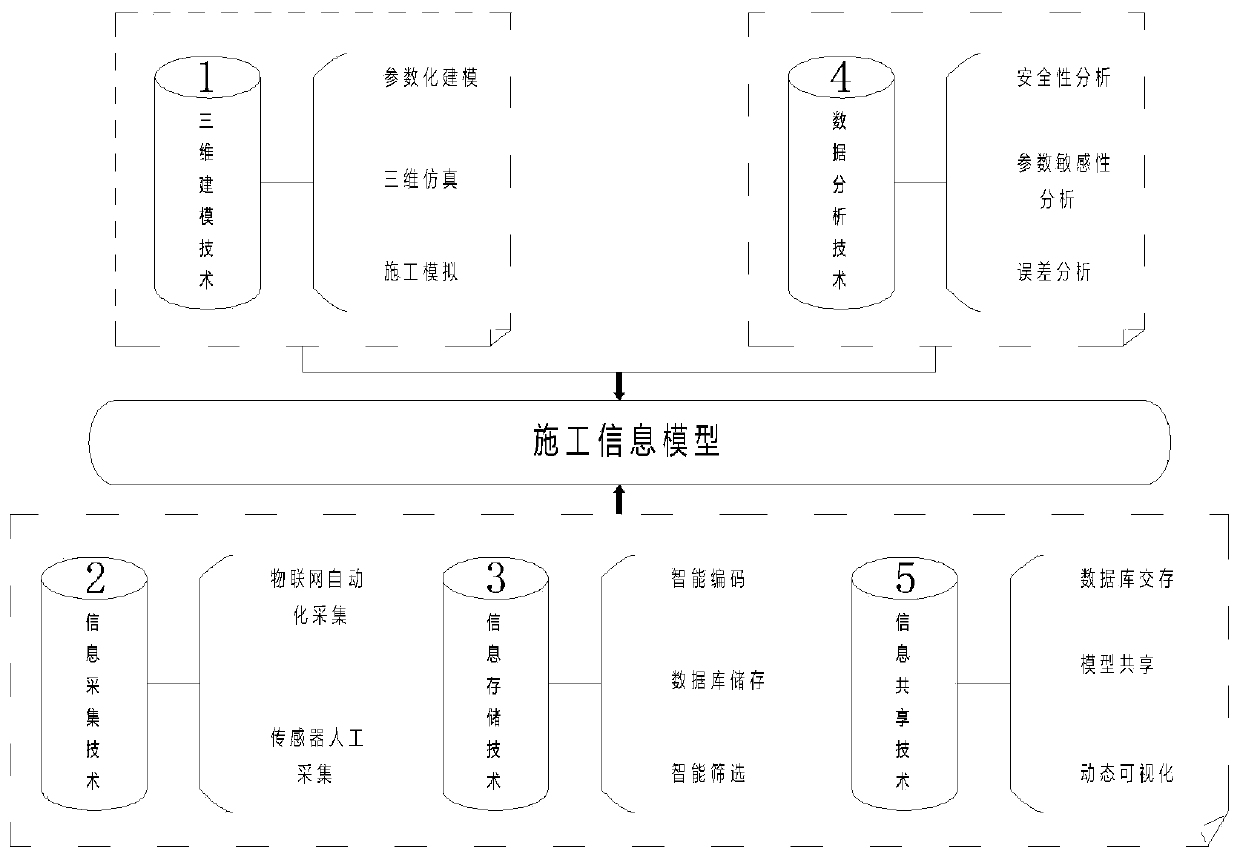
Continuous rigid frame bridge construction management control method based on BIM
ActiveCN110008591AReal-time inputImplement database storageGeometric CADDesign optimisation/simulationComplete dataConstruction management
The invention discloses a continuous rigid frame bridge construction management control method based on BIM, and belongs to the technical field of building construction. The method comprises the following steps: step 1, establishing a model; step 2, measuring point arrangement and coding; step 3, visual analysis; and step 4, construction simulation: carrying out whole-process construction simulation by utilizing the built continuous rigid frame bridge BIM model, visualizing disclosure, optimizing a construction scheme, and carrying out completion delivery on a full-information model. Accordingto the invention, real-time recording and database storage of Revit model information are realized; the integrity and the sharing of construction information are ensured, the efficiency of rigid frame bridge construction management control is improved, complete data support and visual check are provided for construction of the continuous rigid frame bridge, and the application of the BIM technology in the aspect of bridge construction monitoring is promoted.
Owner:CHINA MCC17 GRP
Method and device for synchronizing terminal and server
ActiveCN103312489ASave resourcesGuaranteed sharingSpecial data processing applicationsSynchronising arrangementComputer scienceDatabase
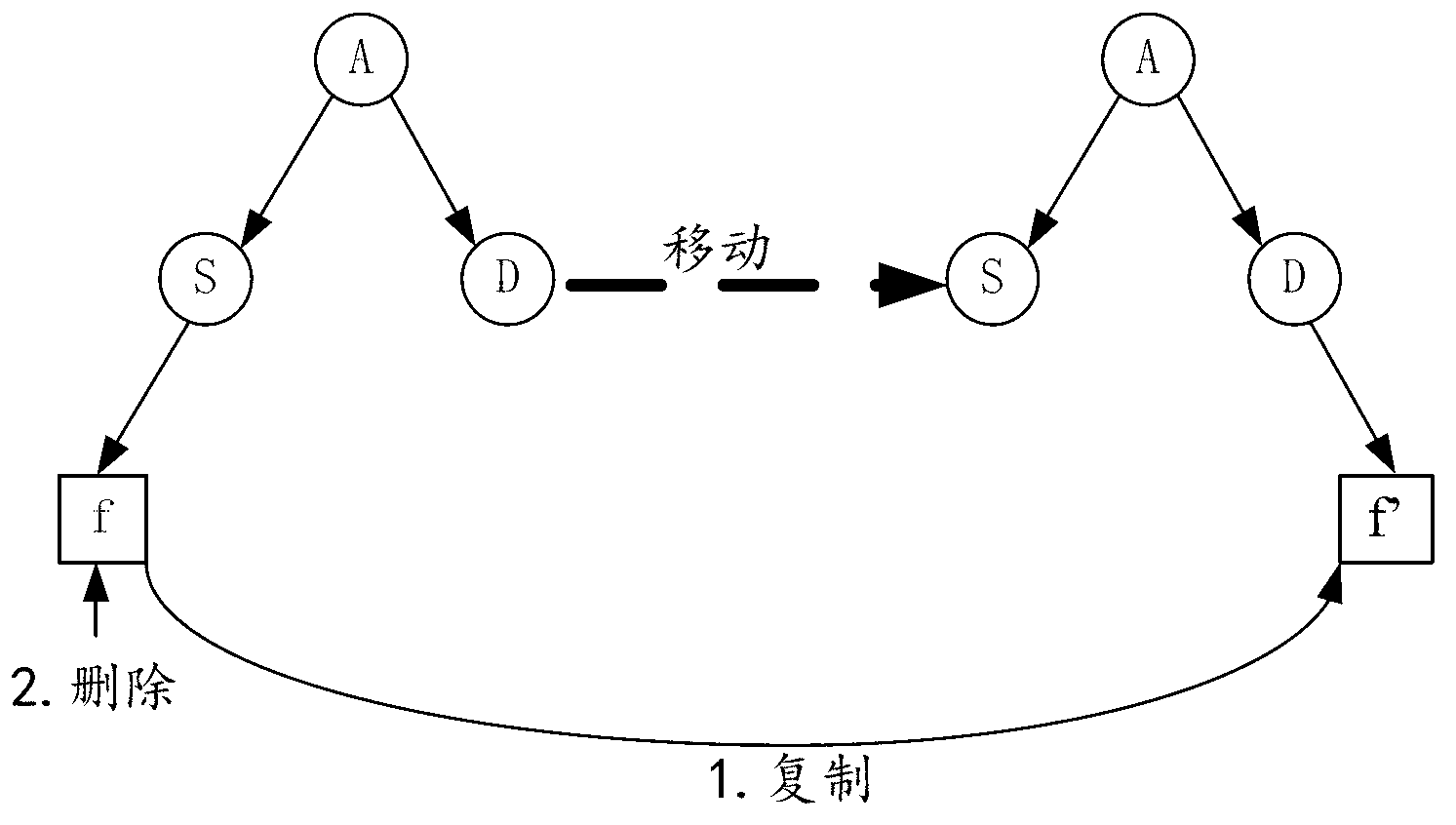
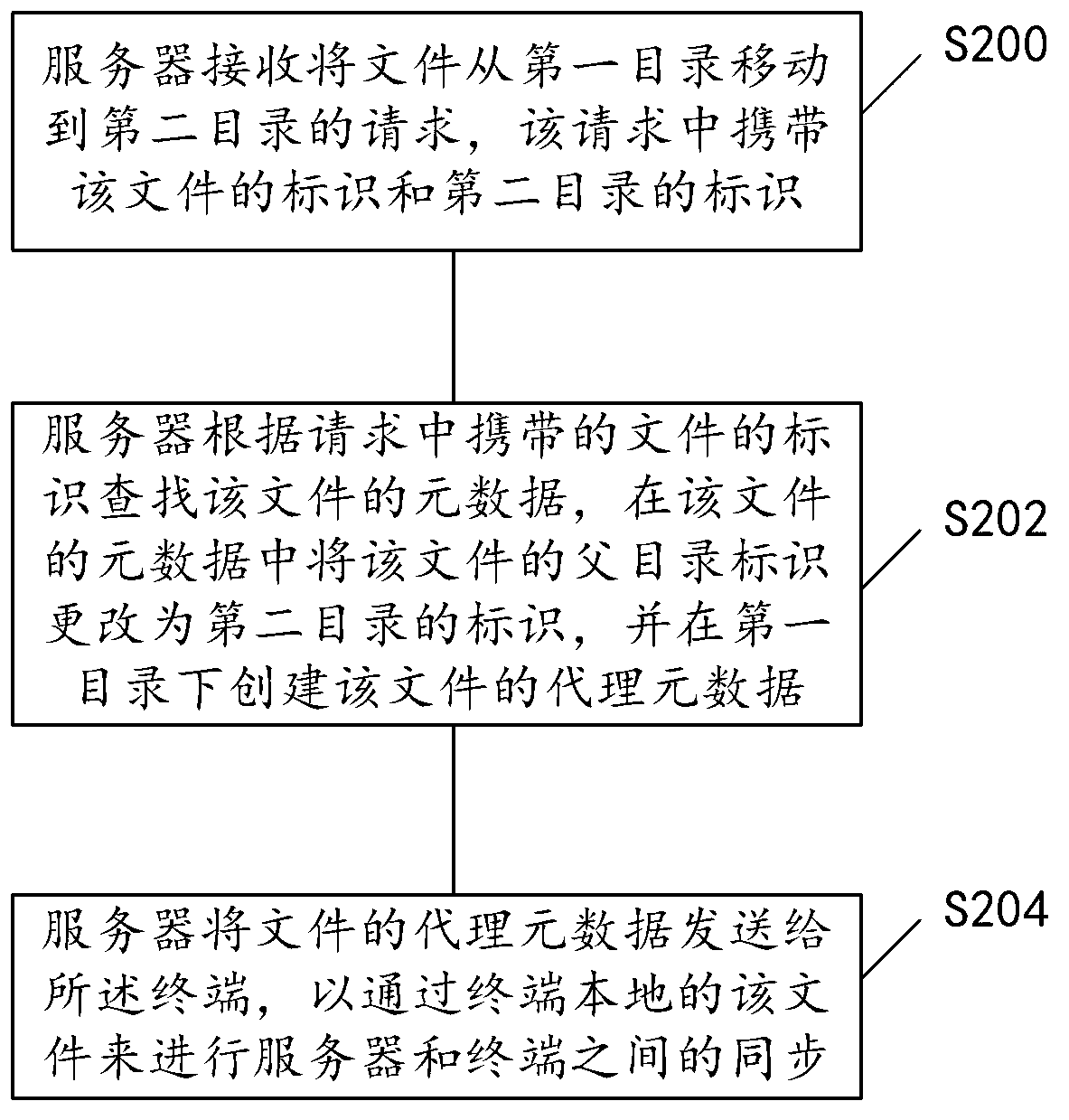
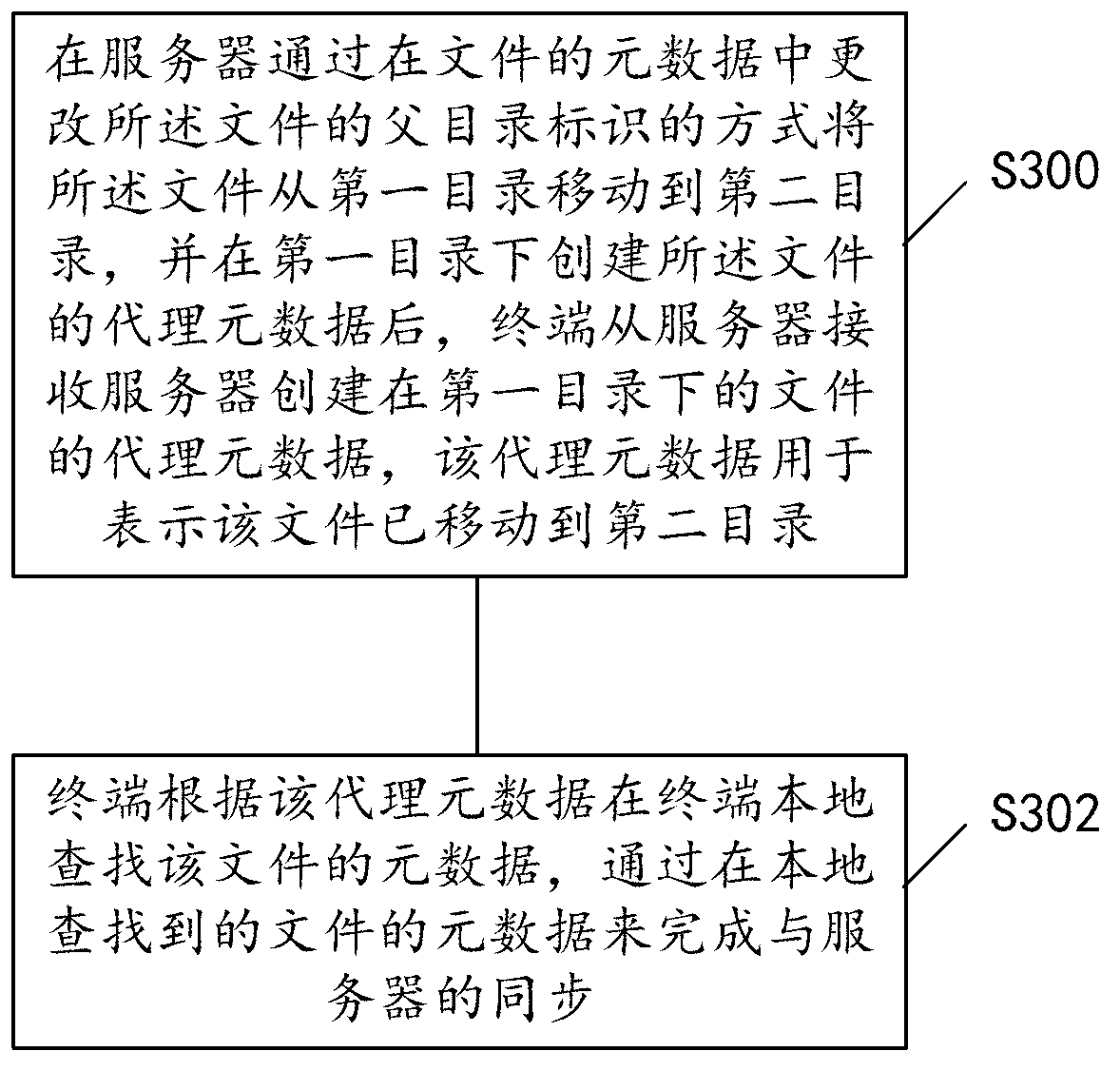
The invention discloses a method and a device for synchronization. The method includes that a server receives a request of moving a file from a first directory to a second directory, and the request carries an identity of the file and an identity of the second directory; the server searches metadata of the file according to the identity of the file, a parent directory identity of the file is changed to be the identity of the second directory in the metadata, and proxy metadata of the file are created under the first directory and used for expressing that the file is moved to the second directory; the server sends the proxy metadata of the file to a terminal to realize synchronization between the server and the terminal through the local file of the terminal. By the method and the device, bandwidth consumption is reduced and synchronization efficiency is improved.
Owner:HUAWEI TECH CO LTD
DCF protocol fairness guarantee method suitable for multi-hop ad hoc network
InactiveCN101951612AGuaranteed sharingNetwork traffic/resource managementNetwork topologiesPower controlChannel resource
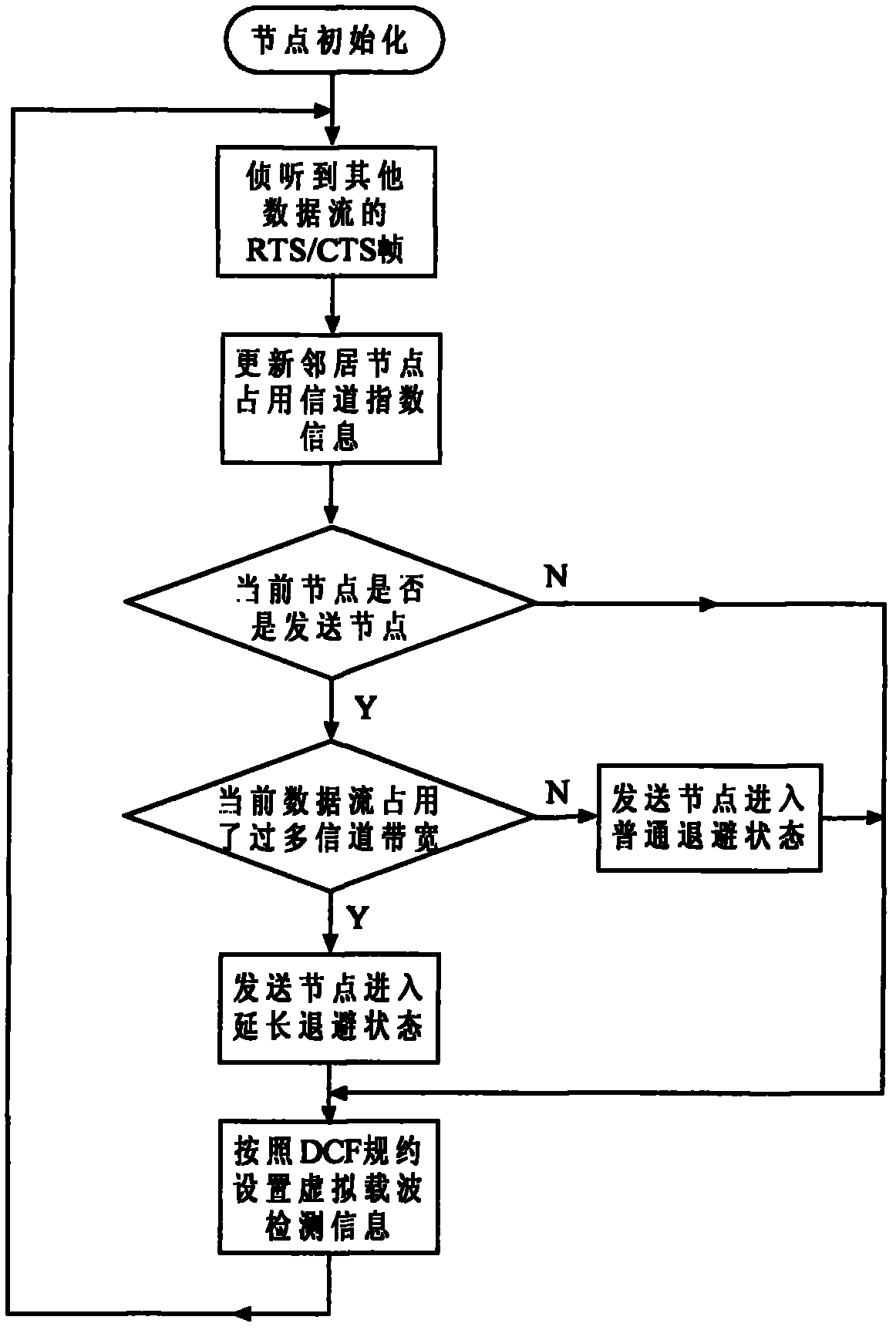
The invention discloses a DCF protocol fairness guarantee method suitable for multi-hop ad hoc network. The fairness problem of a DCF protocol means that, in a multi-hop wireless ad hoc network, the protocol fails to effectively guarantee that a plurality of data streams of equal status share network channel bandwidth fairly. Based on the actual network condition that the detection scope of physical carriers of nodes is wider than the transmission scope thereof, the invention provides a DCF protocol fairness guarantee method suitable for multi-hop ad hoc network. The method comprises the steps that: on the basis of adaptive power-controlled RTS / CTS handshake process, data flow-occupied channel indexes reflecting the occupancy of the current channel bandwidth by the data flows are transferred, sending nodes are then required to comprehensively judge whether the current data flows occupy excessive channel resource according to own and neighboring data flows, and finally, the fair sharing of the channel bandwidth by a plurality of data flows is implemented by adopting the method for contention window adjustment and backoff in combination with the sending nodes. The effectiveness of the method is proved by data of simulation experiments in wireless network stimulating environment GloMoSim.
Owner:SUZHOU HENGZHI ELECTRONICS TECH CO LTD
Adaptive video coding control system and method
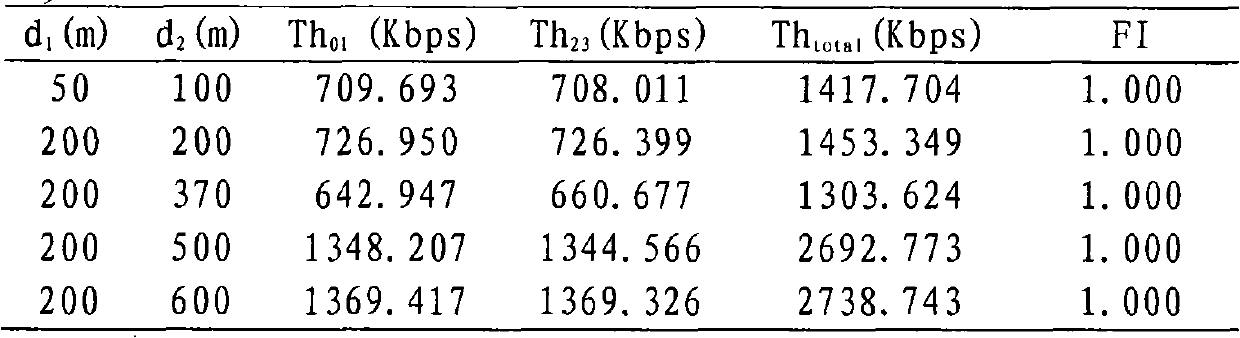
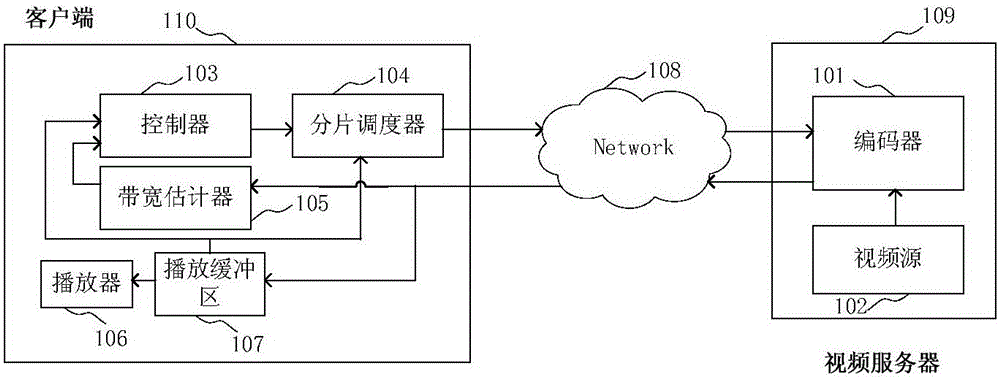
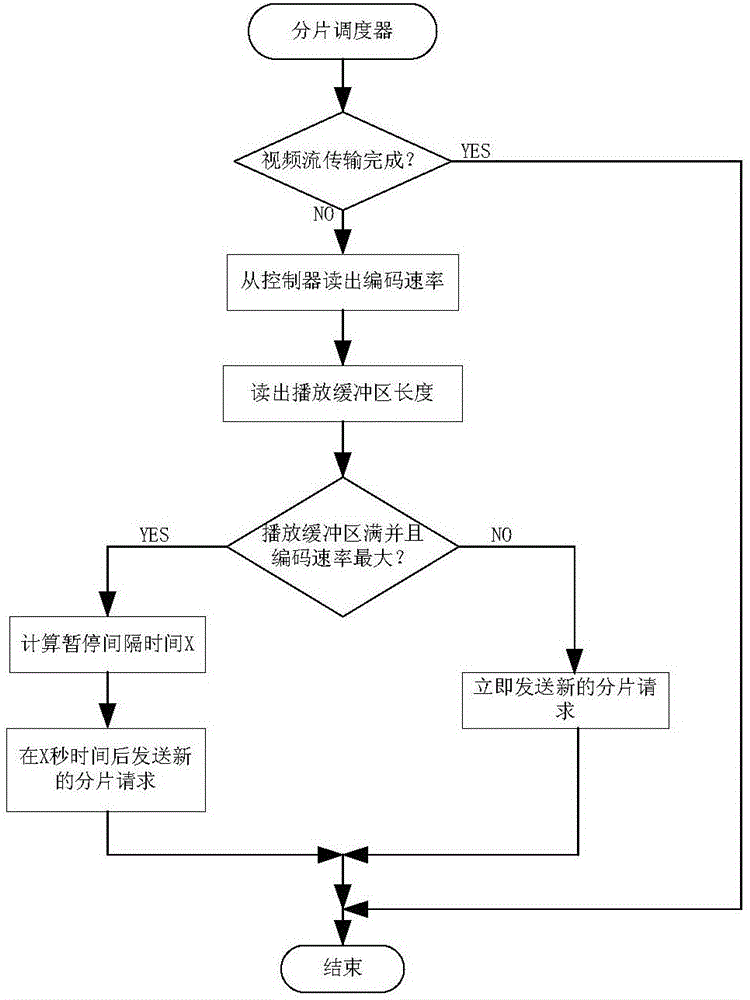
ActiveCN106791860AImprove video qualityGuaranteed sharingDigital video signal modificationControl systemVideo encoding
The invention provides an adaptive video coding control system and method, and belongs to the technical fields of video transmission and video coding. According to the adaptive video coding control system and method, the real-time coding rate of a video is calculated through the arrangement of a controller according to the length of a playing buffer zone and the estimated value of available bandwidth of network, and then, a fragmentation request is transmitted to a video server through a fragment dispatching and handling unit according to the real-time coding rate and the length of playing buffer zone to request next fragment to be transmitted and the video grade of the fragment to further control the coding rate of the next video fragment transmitted by the video server, so that end-to-end bandwidth given from the video server to a client end provides the maximum video quality for a user, and under the situation that a TCP flow exists, bandwidth can be fairly distributed to a plurality of video flows, and the phenomenon that the video flows can share one same bottleneck channel can be guaranteed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
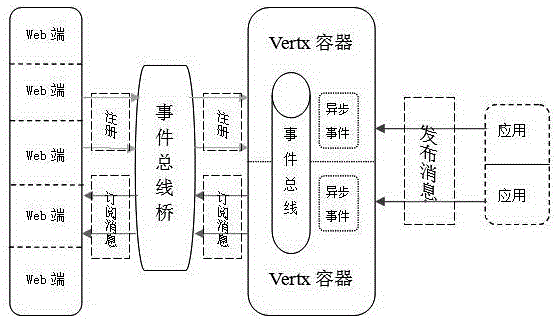
Web push method based on event bus
The invention discloses a web push method based on an event bus. The method comprises the following steps of S1, service container stack address binding; S2, asynchronous processing of messages; S3, releasing of application service messages; S4, web side message subscription; and S5, event bus pushing. The difficulty of upgrading and capacity expanding can be reduced by the technical scheme, and the workload of upgrading can be reduced so that message sending and receiving are enabled to be more timely; the services can be quickly deployed with increasing of the number of the registered users; the concurrency of the system can be enhanced through asynchronous processing; the TPS (transaction per second) of the system can be obviously enhanced; and service calling is safer.
Owner:YONYOU NETWORK TECH
Authorizable financial data privacy processing and sharing method on block chain
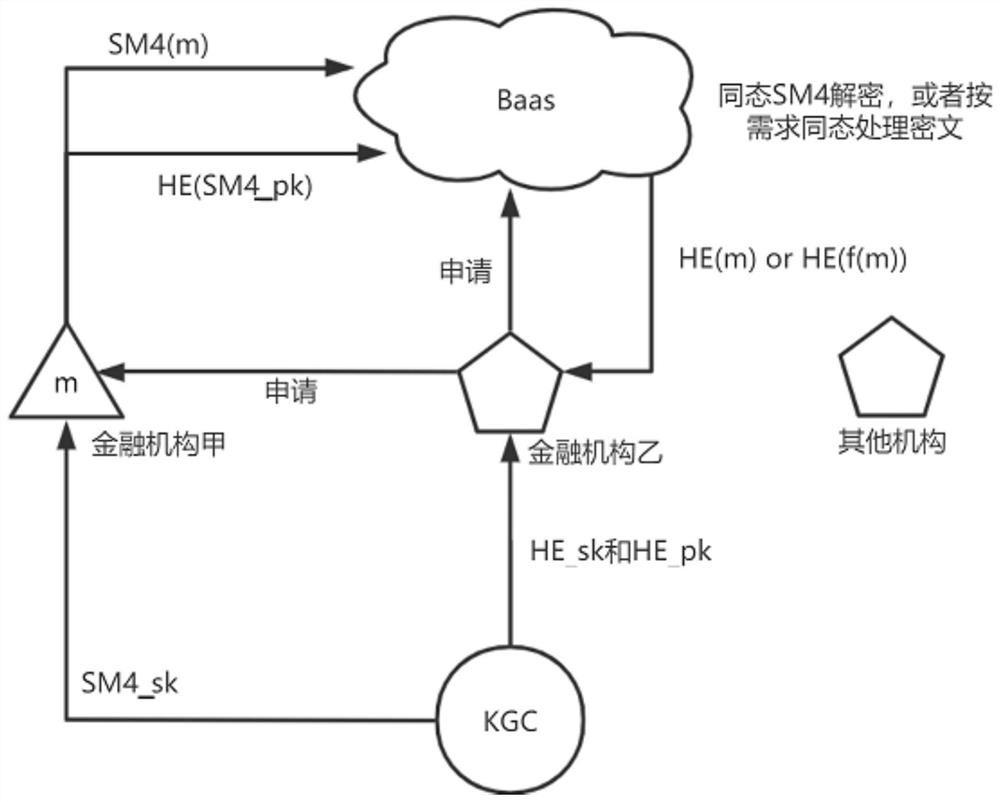
PendingCN112685760ASupport multi-level sharingGuaranteed treatment effectFinanceDatabase distribution/replicationCiphertextData needs
The invention discloses an authorizable financial data privacy processing and sharing method on a block chain, which comprises the following steps that financial data privacy processing and multi-party or multi-stage sharing on an alliance chain is achieved by combining a national cipher SM4 algorithm and BGV-based homomorphic encryption, anda financial institution performs multi-party or multi-stage data sharing on the alliance chain. A data owner performs encryption protection on written-in data by using a national cryptography SM4 algorithm, then packages and uplinks the data, and when ciphertext data needs to be shared and authorized to other cooperation or applicants, only an authorized financial institution can decrypt the data. According to the invention, the ciphertext encrypted by the authorizer SM4 is converted into the new ciphertext of the data applicant under the fully homomorphic encryption, so that the BaaS can be utilized to ensure the security processing and sharing of financial data and support the multi-level sharing of data at the same time.
Owner:浙江泰科数联信息技术有限公司
Surface multi-beam forming method based on hybrid adaptive particle swarm optimization
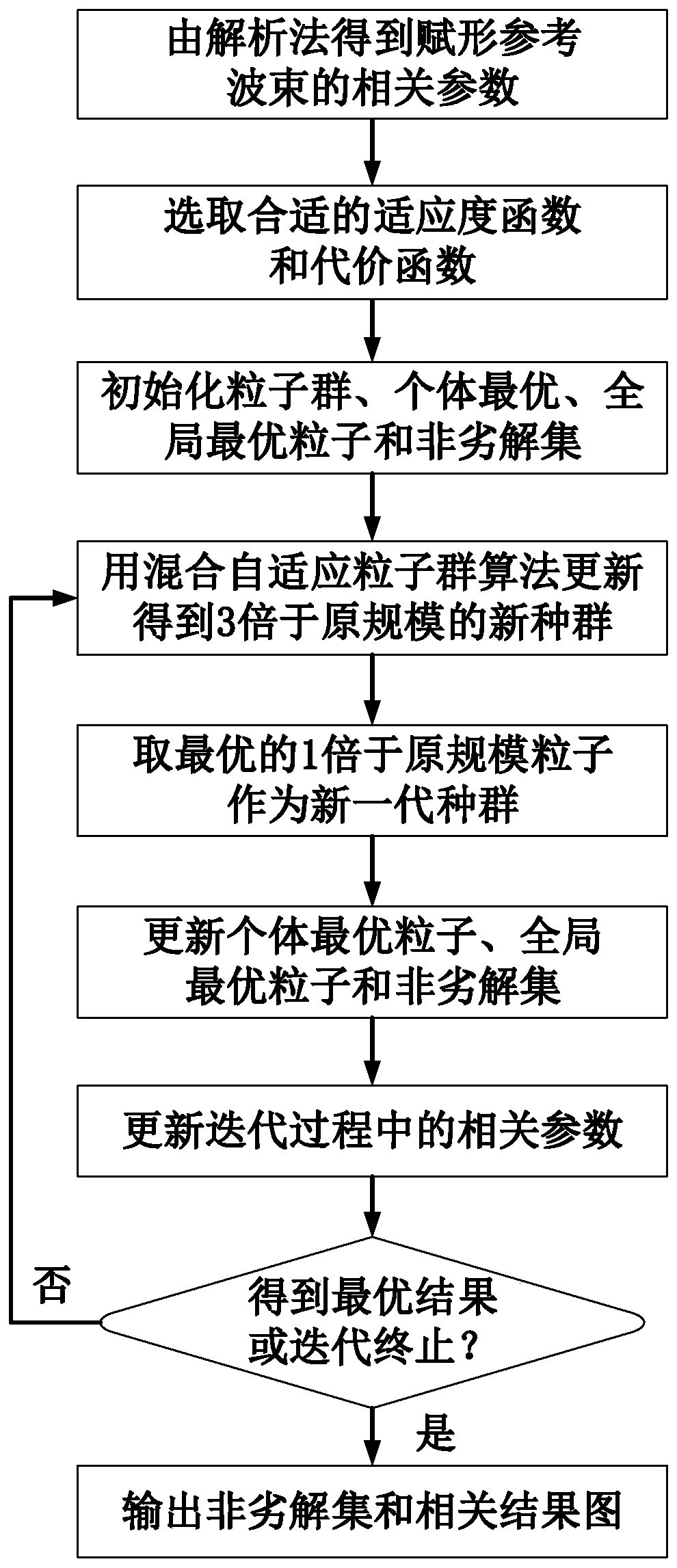
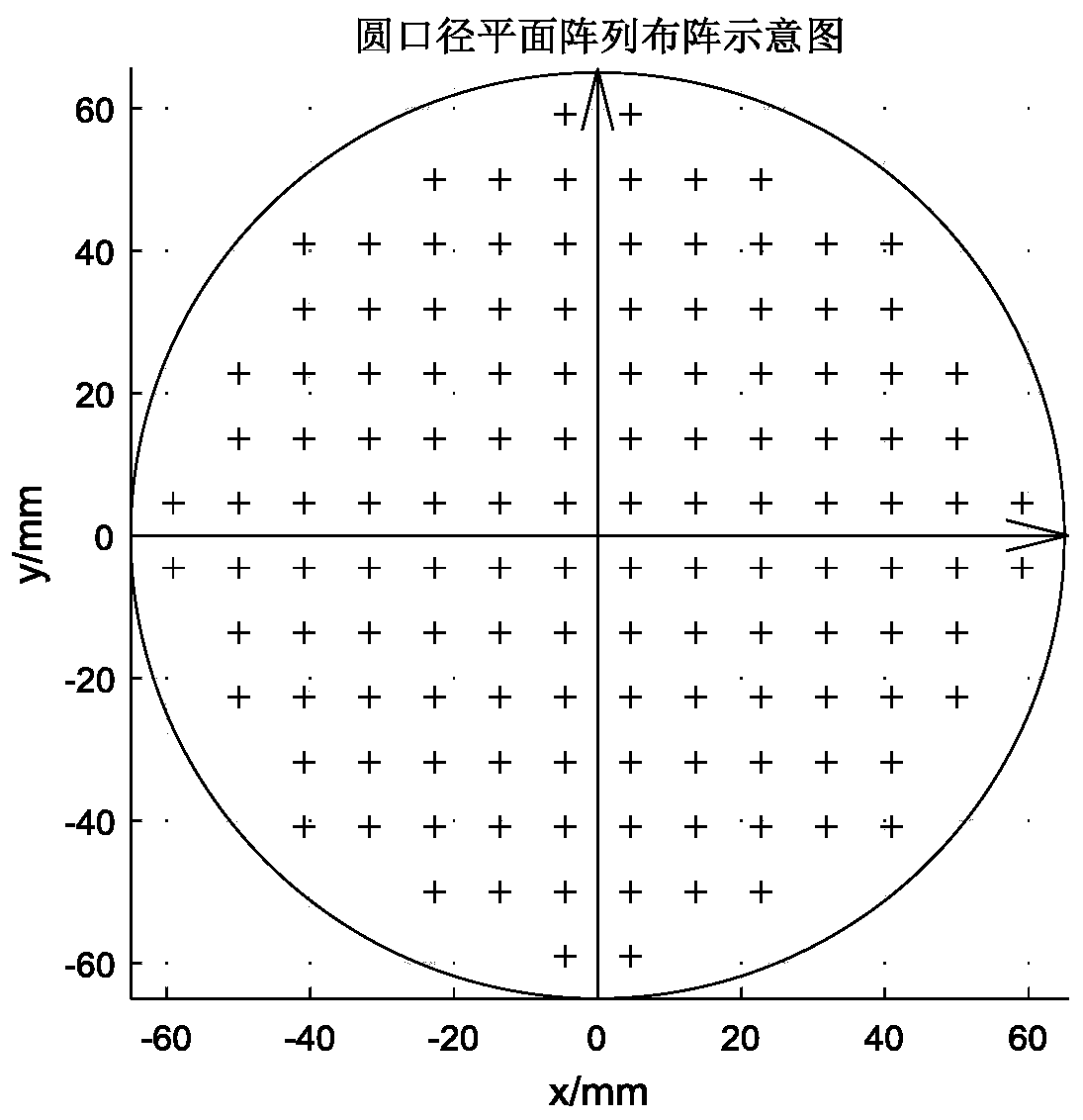
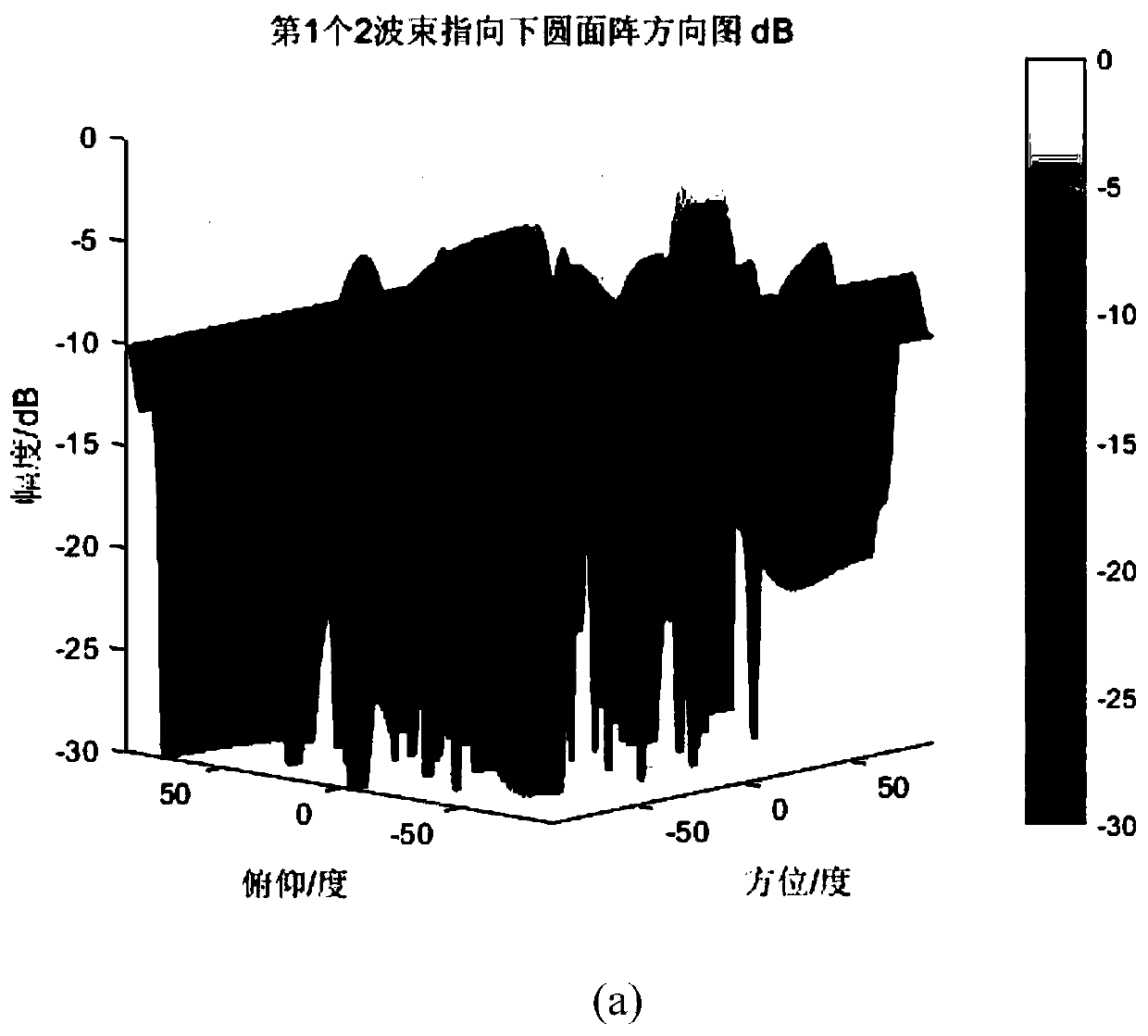
ActiveCN111224706AOptimize the targetIncrease diversitySpatial transmit diversityArtificial lifeEngineeringRadar signal processing
The invention belongs to the technical field of radar signal processing, and particularly relates to a surface multi-beam forming method based on hybrid adaptive particle swarm optimization, which comprises the following steps: obtaining related parameters of a forming reference beam by an analytical method; selecting an appropriate fitness function and an appropriate cost function; initializing aparticle swarm, an individual optimal particle, a global optimal particle and a non-inferior solution set; using hybrid adaptive particle swarm optimization for updating to obtain a new swarm of which the scale is three times of the original scale; taking the optimal particle which is 1 time of the original scale as a new generation of swarm; updating the individual optimal particle, the global optimal particle and the non-inferior solution set; updating related parameters in the iteration process; determining an optimal result or terminating iteration; and outputting the non-inferior solution set and a related result graph.
Owner:XIDIAN UNIV
Method, device and server for encrypted file management
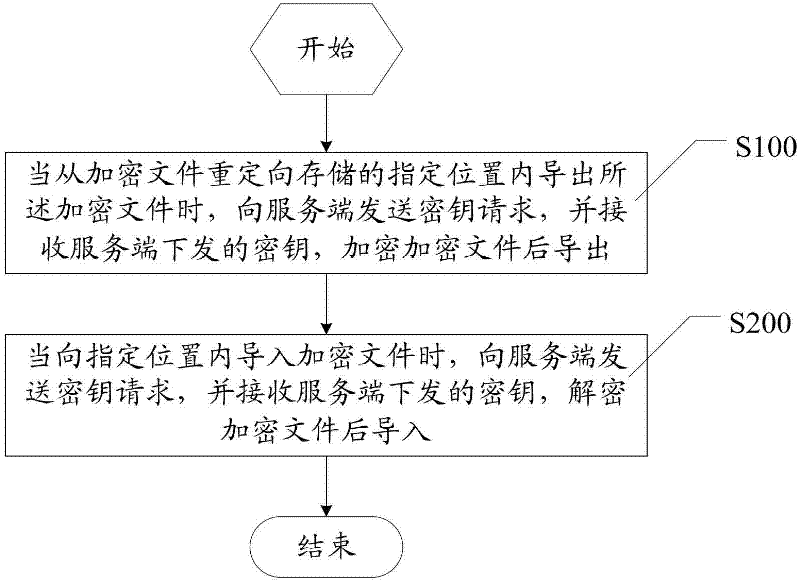
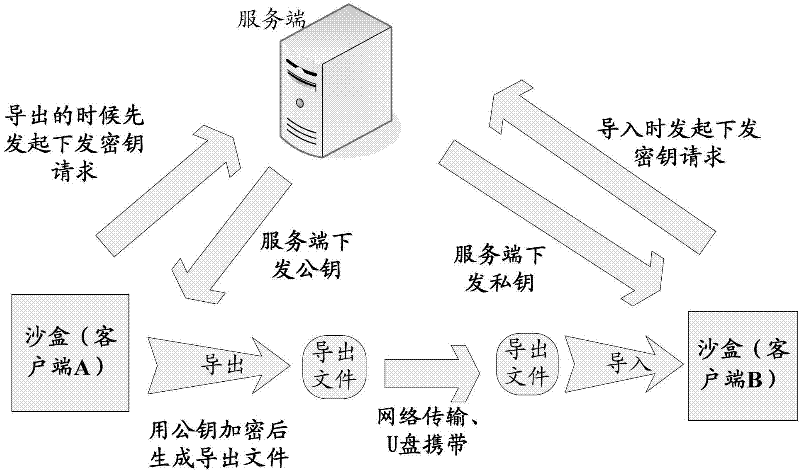
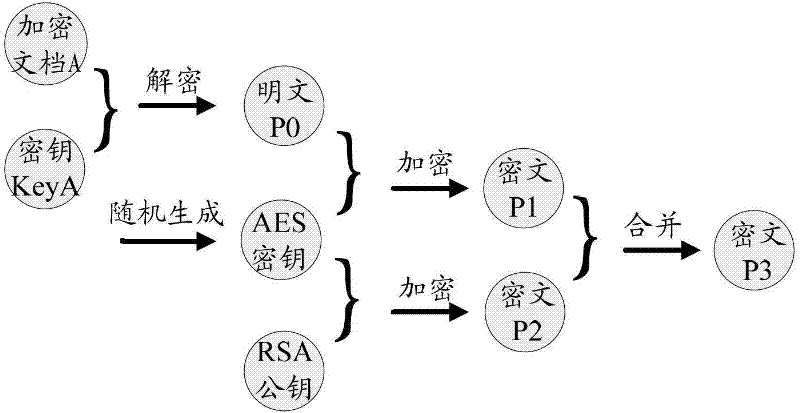
InactiveCN102694796AEnsure safetyGuaranteed sharingUser identity/authority verificationDigital data protectionComputer hardwareThird party
The invention relates to a method, a device and a server for encrypted file management. The method includes the steps: when encrypted files are led out from a designated position for redirected storage of the encrypted files, sending secret key requests to a server side, receiving secret keys sent by the server side and leading out the encrypted files after encrypting; and when the encrypted files are led into the designated position, sending secret key requests to the server side, receiving secret keys sent by the server side and leading in the encrypted files after decrypting. The encrypted files are redirected and stored in the designated position, and users are supposed to check and compile the encrypted files at the designated position. Special encryption and decryption algorithms are used for encrypting and decrypting files, so that a third party cannot check specific contents of the encrypted files even acquiring the encrypted files, and safety and sharing of confidential files are guaranteed.
Owner:SANGFOR TECH INC
Universal standing-wave ratio detection method for TDD-LTE RRU and FDD LTE RRU
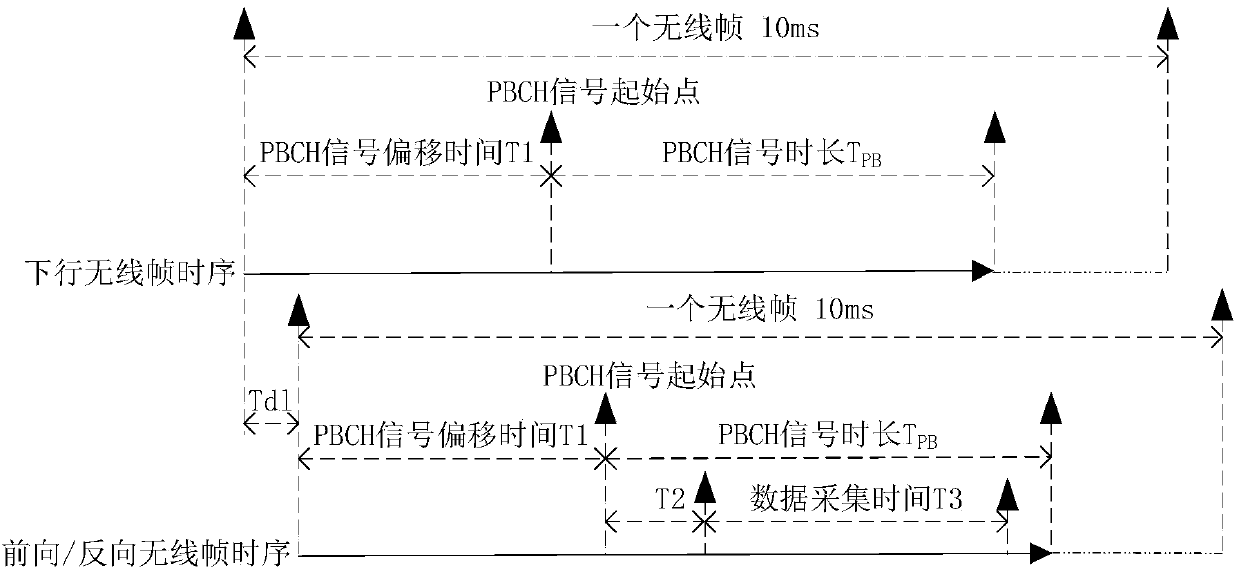
InactiveCN107809291AImprove accuracyDoes not affect signal qualityTransmitters monitoringWireless communicationStanding waveVIT signals
The invention belongs to the technical field of mobile communication, and discloses a universal standing-wave ratio detection method for a TDD-LTE RRU and an FDD LTE RRU. The method comprises the steps that the delay time of a downlink signal and forward and reverse link signals is acquired; configuration information of a cyclic prefix and the time of a PBCH signal are acquired; a CPU switches a switch of a feedback link to be in a forward direction; an FPGA acquires a forward signal; the FPGA truncates out the PBCH signal through a 1.08M-bandwidth digital filter at a signal center frequency point, reads the PBCH signal and converts the PBCH signal to obtain a forward power value; the CPU switches the switch of the feedback to be in a reverse direction; a reverse power value is obtained ina similar way; a return loss value is acquired; calibration is conducted according to a return loss calibration value to obtain an actual return loss value; and a standing-wave ratio detection resultis acquired. According to the method, standing-wave ratio detection on the TDD-LTE RRU and standing-wave ratio detection on the FDD LTE RRU FDD LTE RRU can be achieved simultaneously, and the detection accuracy can be guaranteed.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com