Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
328 results about "Digital resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Content Metadata Directory Services
ActiveUS20070156726A1Improve interoperabilityIncrease the number ofMultimedia data indexingDigital data processing detailsContent IdentifierSystems management
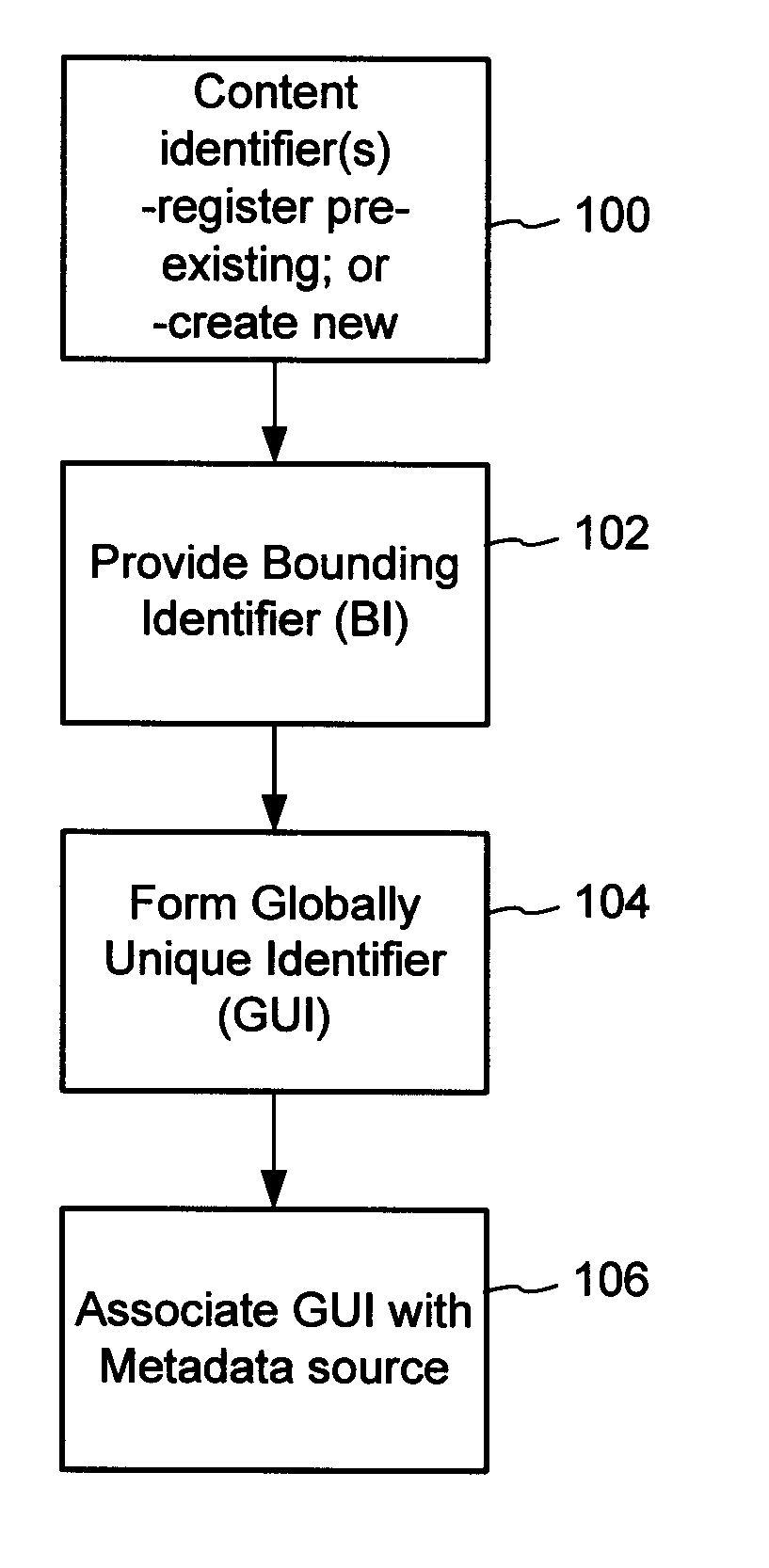
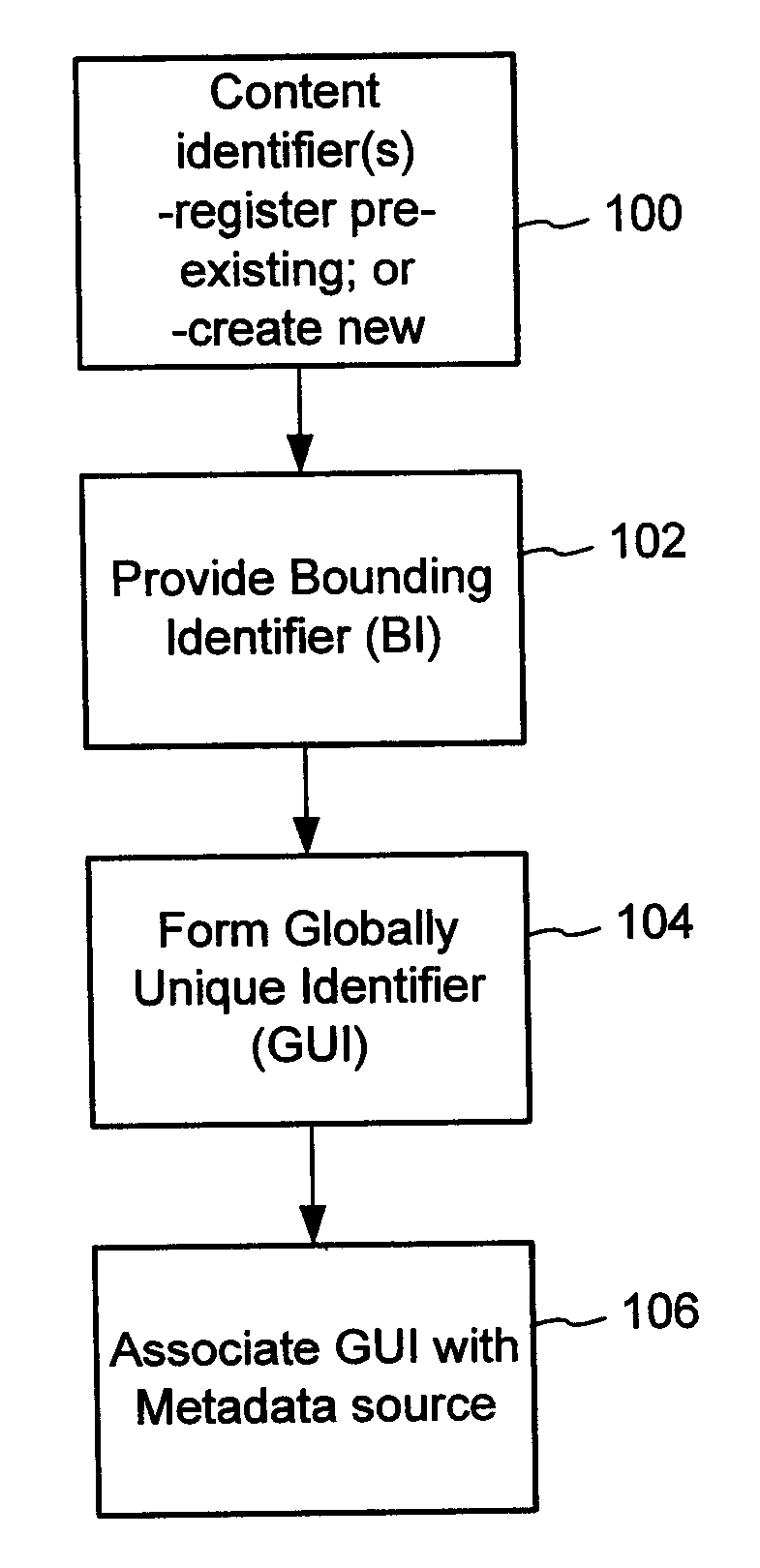
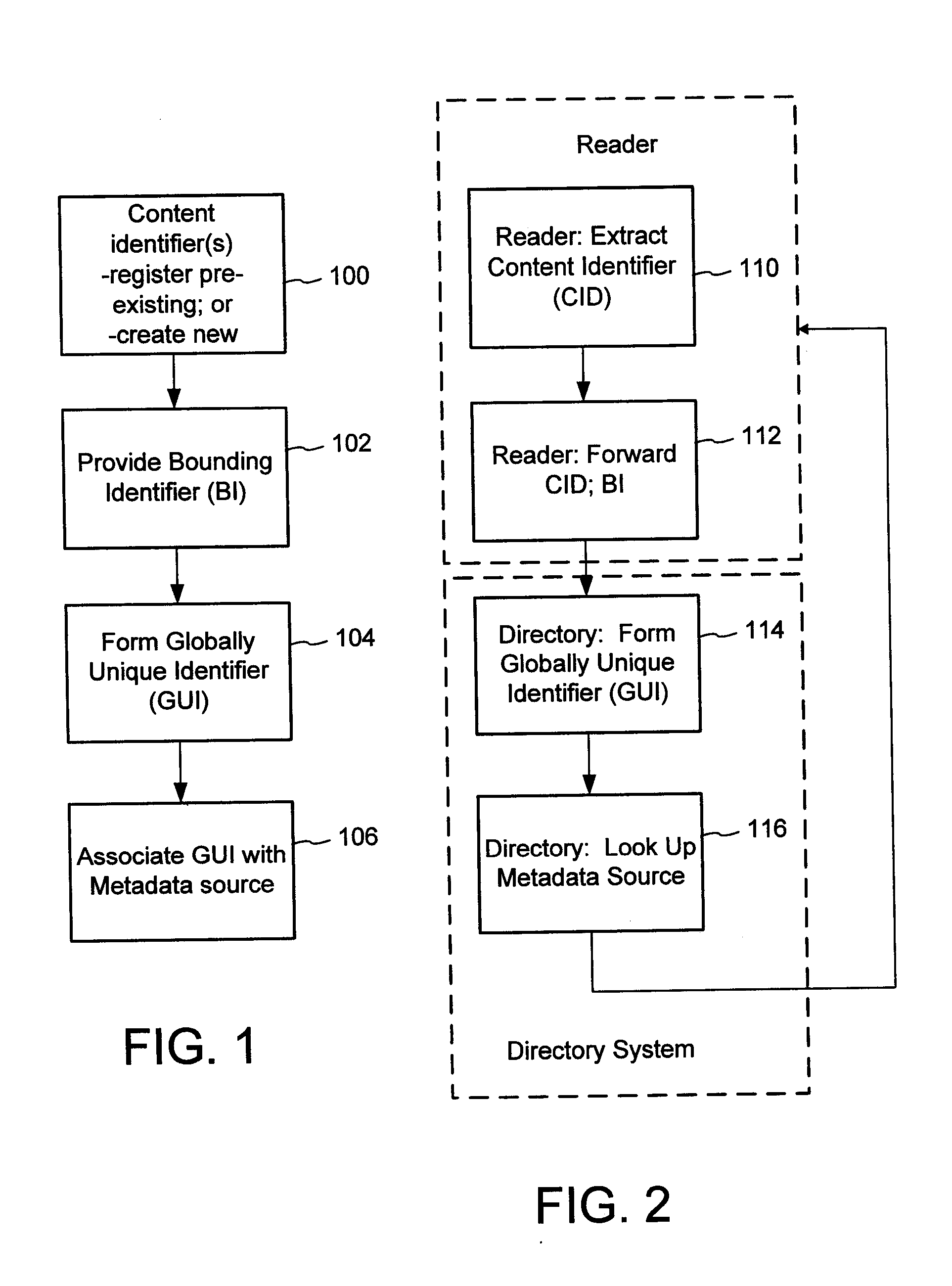
The content metadata directory system connects consumers of identified content to managed metadata databases and other digital resources. The system manages links between identifiers in content objects and metadata sources. It supports a variety of different type of content identifiers and allows for overlap among different content identification schemes. One method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers and provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source.
Owner:DIGIMARC CORP
Content Metadata Directory Services
ActiveUS20070192352A1Increase the number ofComplicate to identifyMultimedia data indexingDigital data processing detailsContent IdentifierWeb site
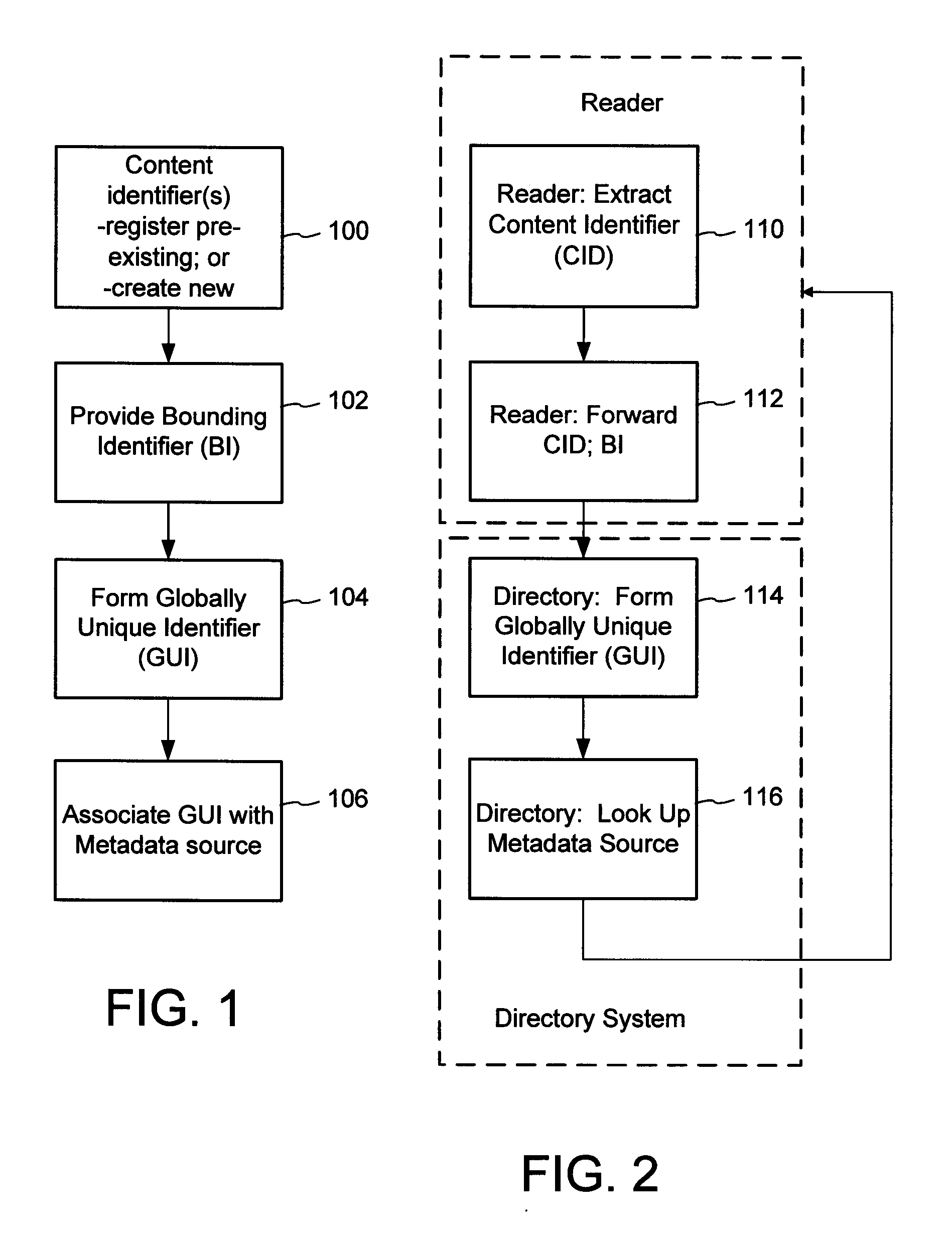
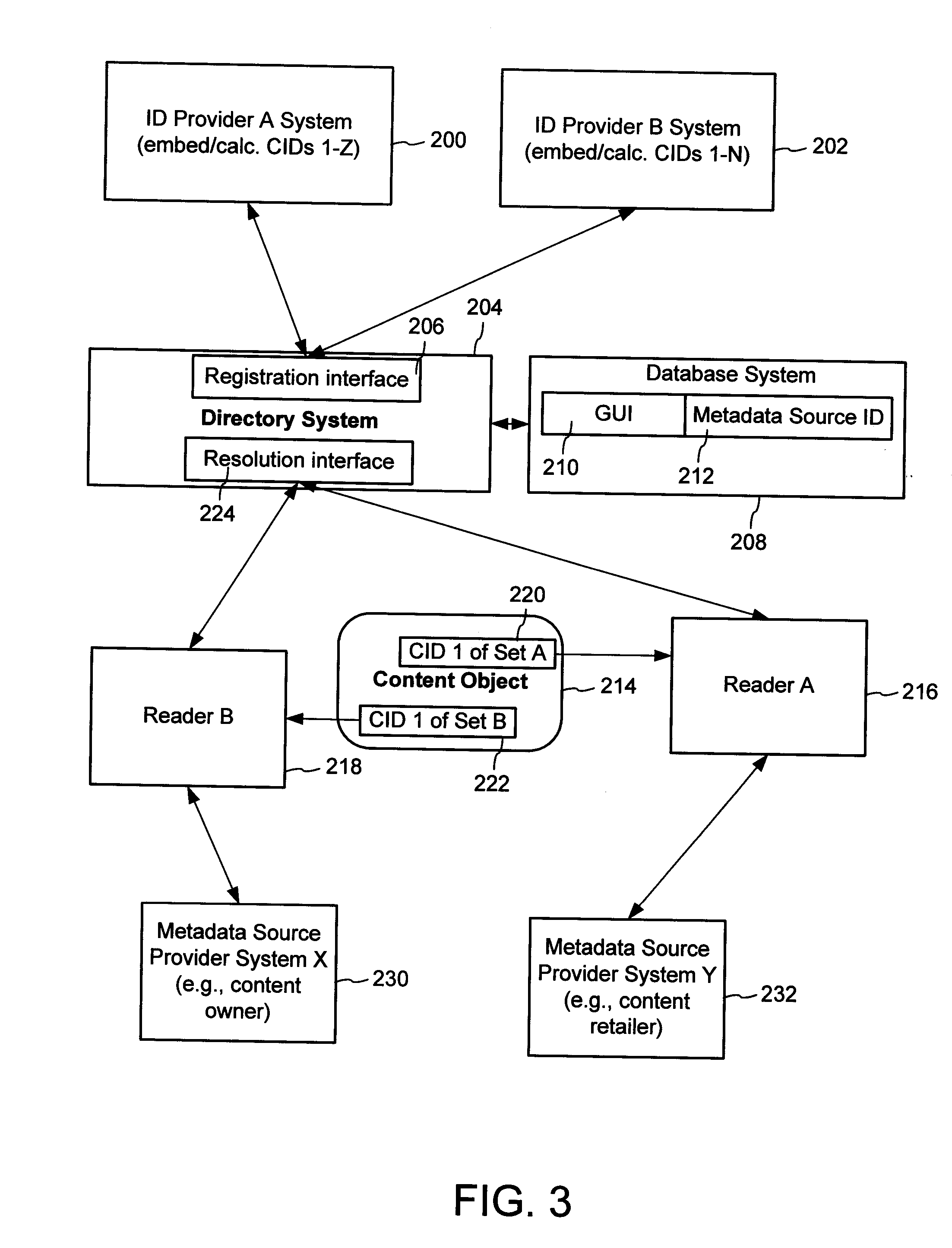
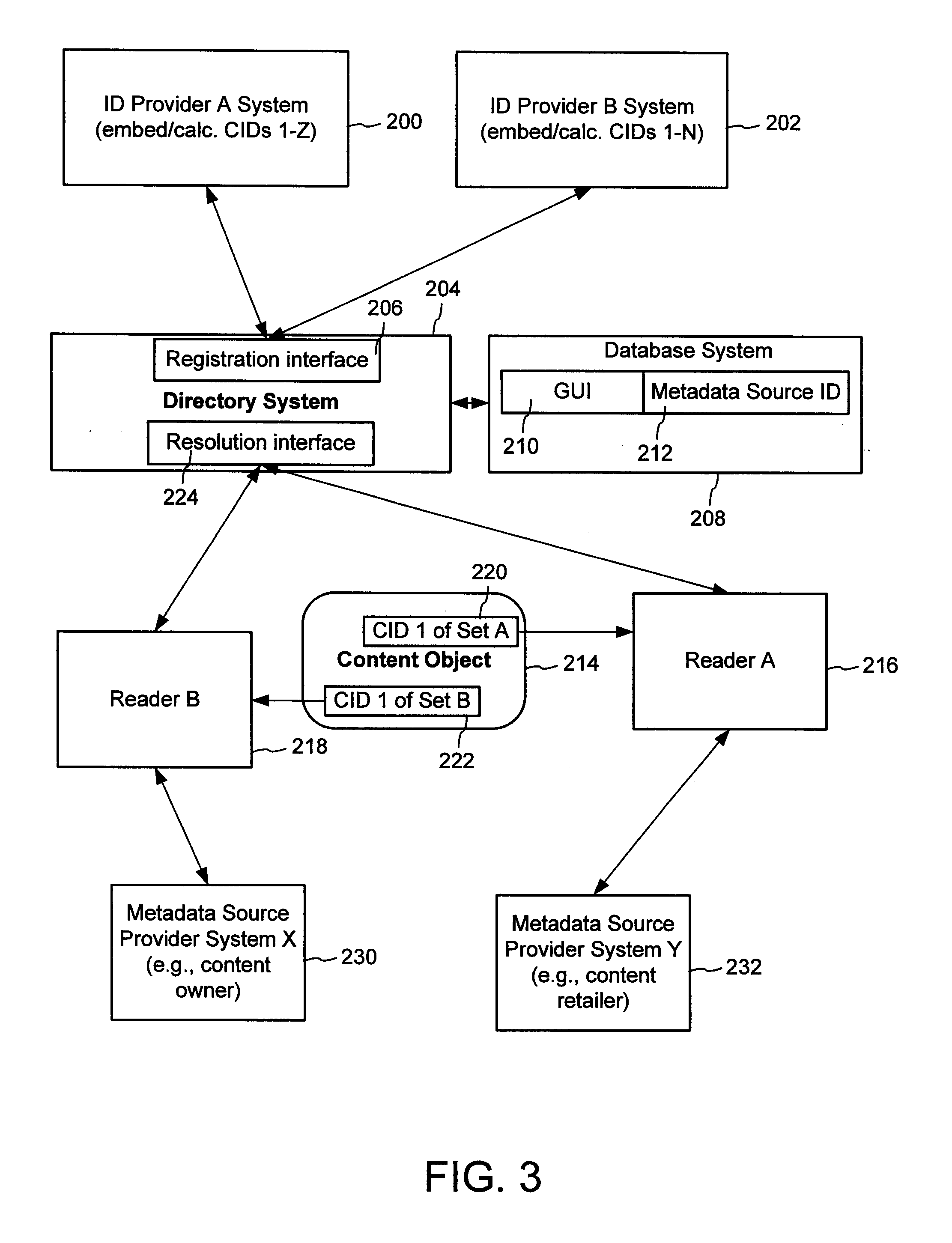
A method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers. It provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source. Another novel method addresses content objects with two or more content identifiers, potentially referencing different metadata sources. This method registers different globally unique identifiers for a content object. These globally unique identifiers each comprise a content identifier provided with the content object and a bounding identifier identifying a set of content identifiers of which the content identifier is a member. For each of the globally unique identifiers, information is maintained about a metadata source. The method receives a first content identifier for the content object, and uses a bounding identifier associated with the set of the first content identifier to determine the globally unique identifier for the first content identifier. The user is routed to the metadata source associated with globally unique identifier. This document describes a novel system that enables multiple identity providers (ID Providers) to register and use the system. The ID Provider registers with a metadata directory system, receives a unique bounding identifier, and uses this bounding ID (e.g., an ID provider ID) with subsequent interactions with the metadata directory system. Separately, metadata source providers register metadata sources with the metadata directory system. This enables many different participants to associate content objects with metadata sources using one or more identify providers. Examples of metadata source providers include content providers, like content owners or retailers that have the flexibility of working with different ID providers to associate content objects with metadata. Both content providers and ID providers can register and use the system. The metadata source is the system or device that provides the metadata, like a web site. The directory system uses an identifier for the metadata source, which enables it to maintain an association between a content object and its corresponding metadata source. For example, in some embodiments, a URL serves to identify the location of the source. The Content Metadata Directory Services (CMDS) is a global trusted directory service that connects consumers of identified content to content-provider authorized and managed metadata databases and other digital resources. It includes mostly links to metadata, forms globally unique IDs based upon overlapping content identifiers and unique bounding identifiers, enables multiple content identifiers within a content object, and enables multiple content identity technology providers, even when they are using different technology.
Owner:DIGIMARC CORP
System, method, and computer program product for managing rights of media in collaborative environments
InactiveUS20080133551A1Easy to understandEasily and efficiently share both content and editorial inputProgram/content distribution protectionSpecial data processing applicationsDigital rights managementRights management
A system, method, computer program product, and propagated signal of this collaborative system are adapted to track metadata relating to an online digital asset that captures each user's or group's interest in the asset and thus, in the aggregate, defines a collective interest in the asset and self-selects a relevant market based upon the nature of the asset, the distribution, and the collective group. Further, the system, method, computer program product, and propagated signal implement a rights manager to provide for digital rights management in collaborative systems. The system includes a plurality of communication clients, inter-communicated by a network, each for initiating a collaborative concurrent processing of a resource file; and a rights manager, coupled to each the plurality of communications clients, for authorizing the processing of the resource file responsive to a rights management tag associated with the resource file, the rights manager securing the rights management tag with the resource file to produce a digital resource and the rights manager decrypting the digital resource to produce the resource file and the rights management tag. The method includes initiating a collaborative concurrent processing of a resource file by a particular one communication client of a plurality of communication clients, inter-communicated by a network; and authorizing the processing of the resource file by a rights manager, the authorizing responsive to a rights management tag associated with the resource file, the rights manager securing the rights management tag with the resource file to produce a digital resource and the rights manager decrypting the digital resource to produce the resource file and the rights management tag.
Owner:APEER
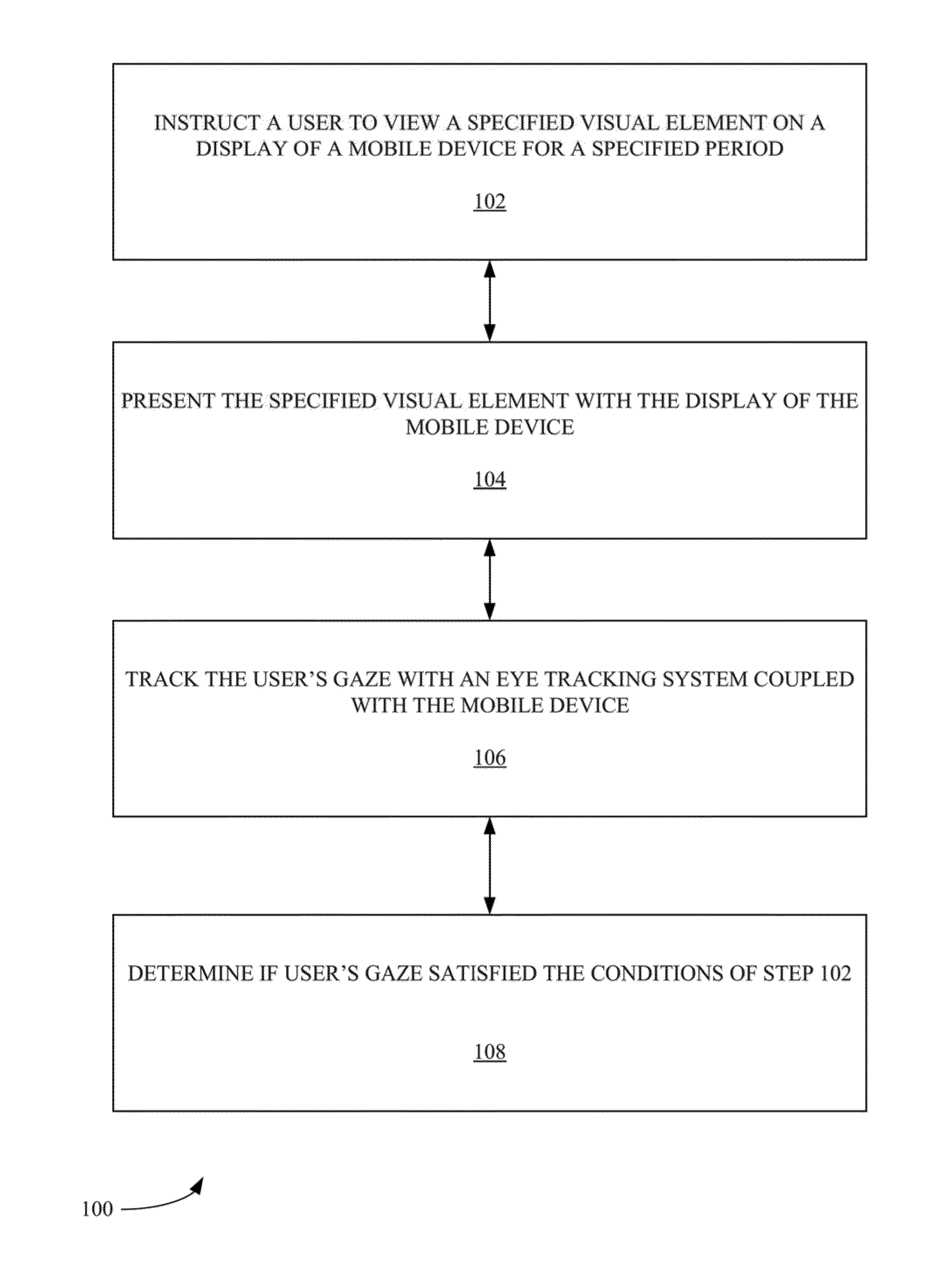
Method and system of user authentication with bioresponse data
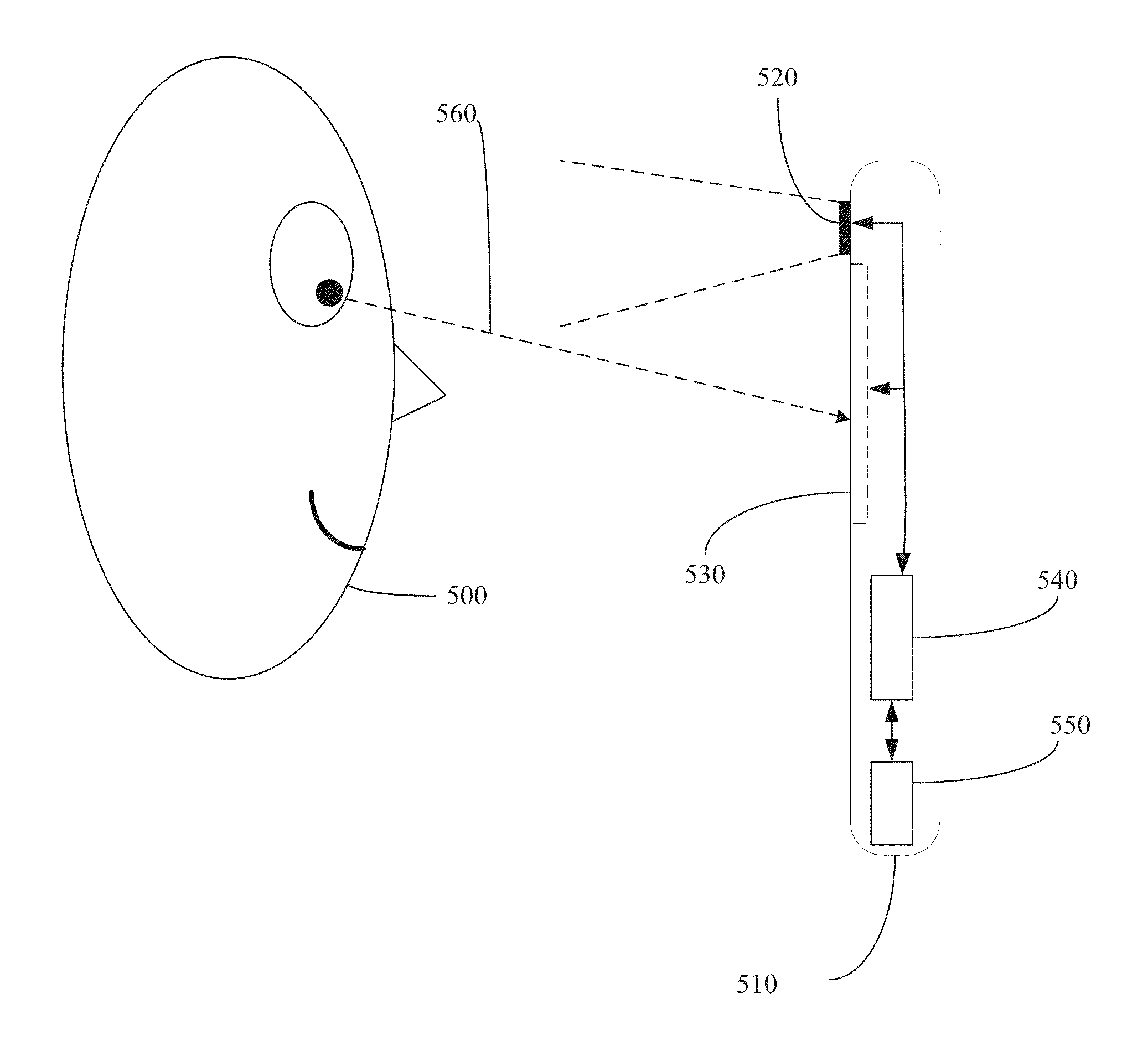
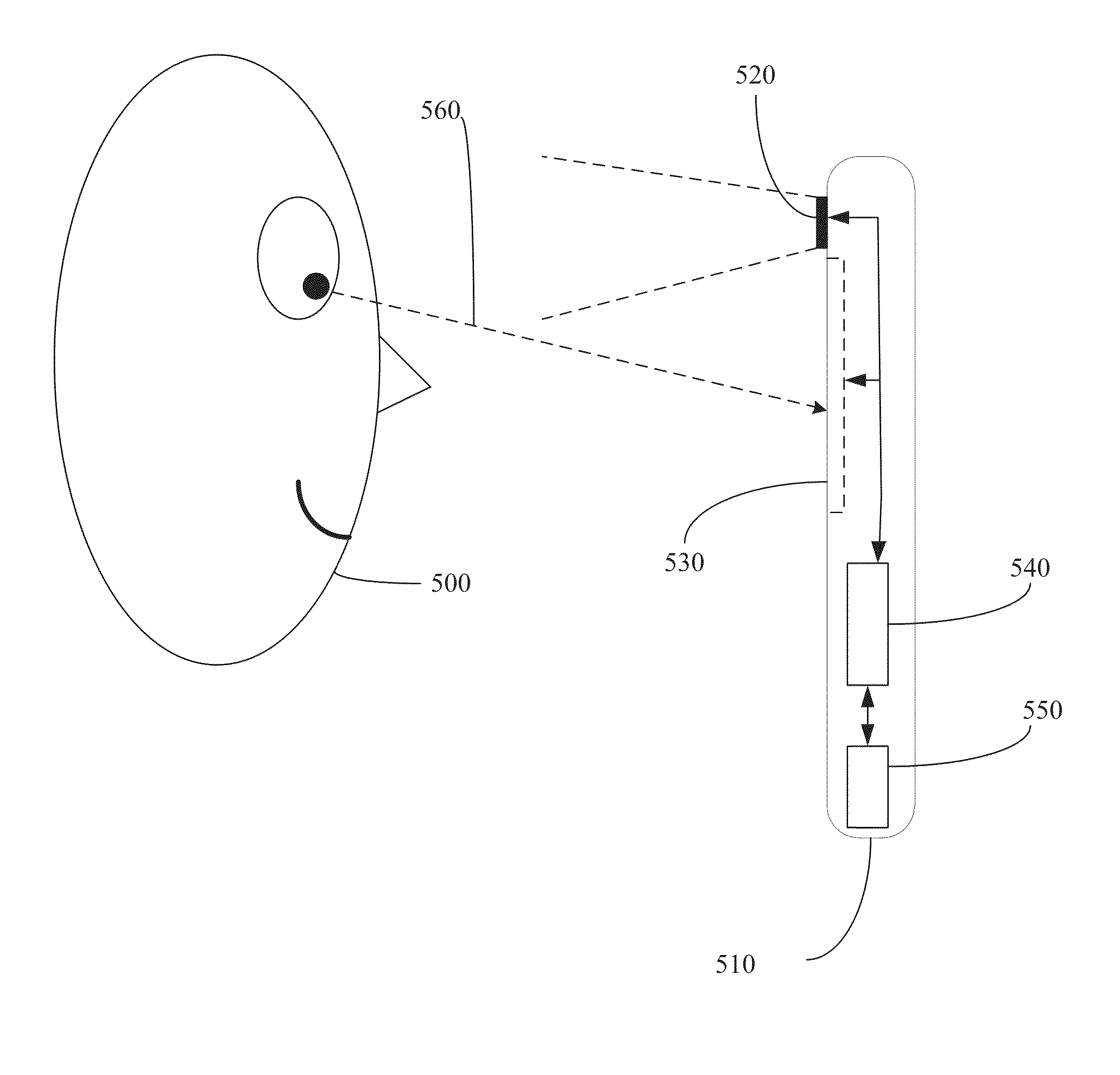
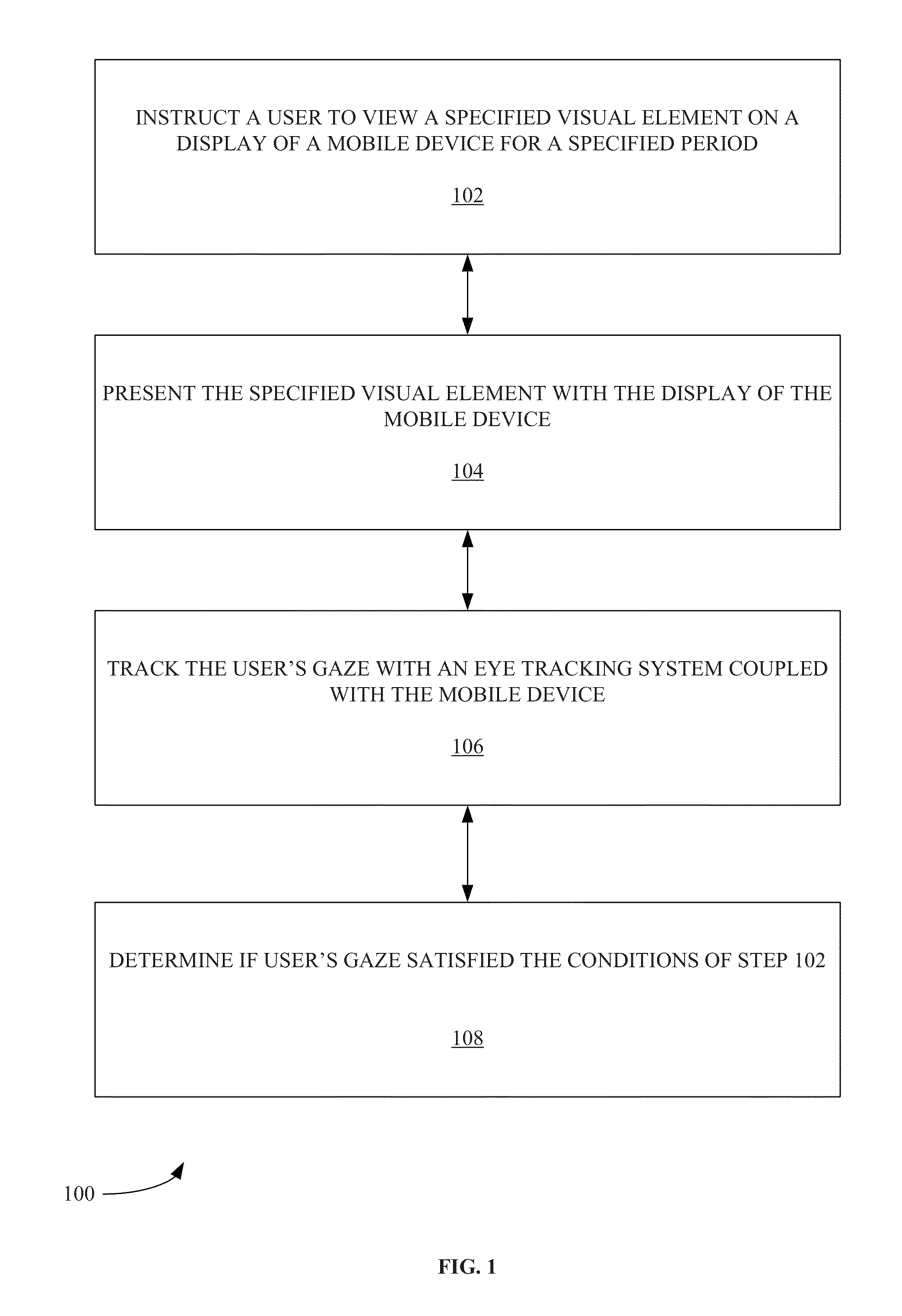
InactiveUS20130044055A1Acquiring/recognising eyesCathode-ray tube indicatorsUser authenticationEye tracking system
In one exemplary embodiment, a computer-implemented method includes the step of providing an image to a user. The image is provided with a computer display, An eye-tracking data is obtained from the user when the user views the image. The eye-tracking data is obtained with an eye-tracking system. A user attribute is determined based on the eye-tracking data. The user is enabled to access a digital resource when the user attribute is associated with a permission to access the digital resource. The user attribute can be a personhood state. The digital resource can be a web page document. An instruction can be provided to the user regarding a pattern of viewing the image. The pattern of viewing the image can include instructing the user to gaze on a specified sequence of image elements.
Owner:BUCKYBALL MOBILE
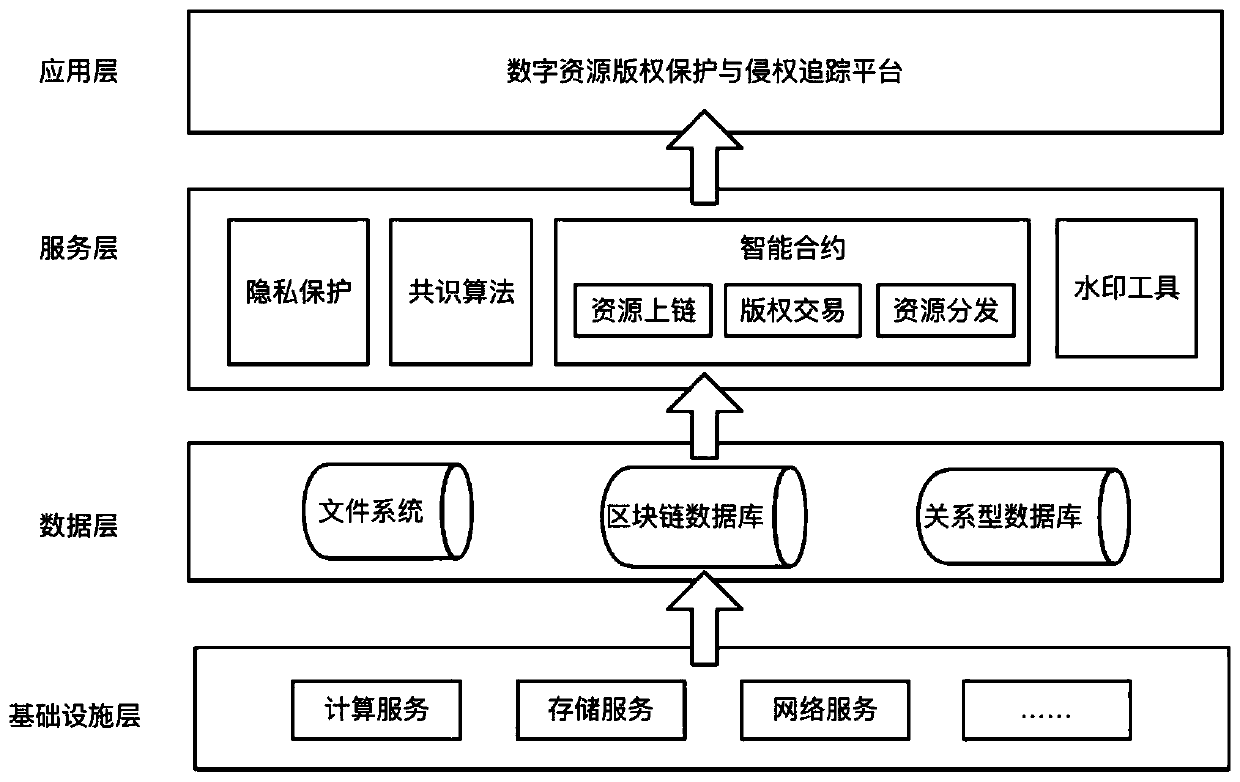
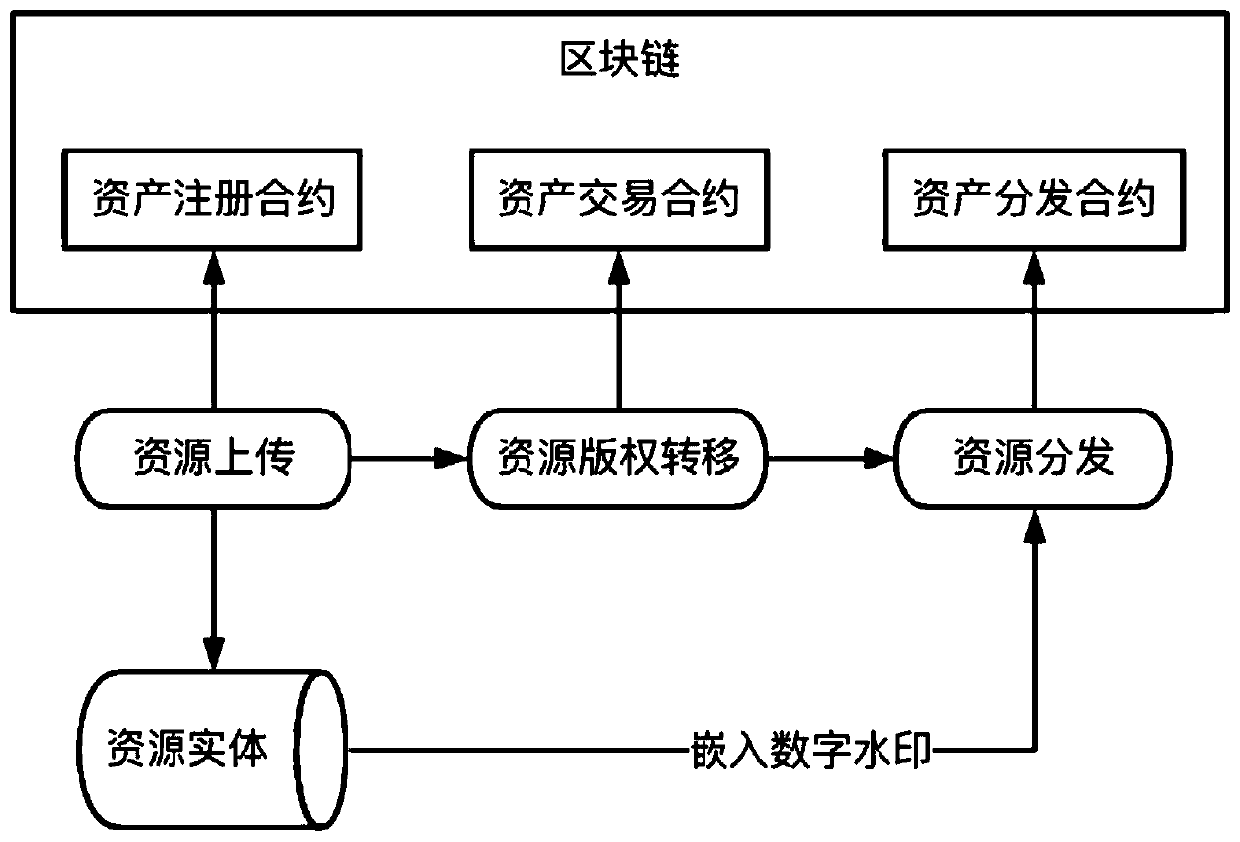
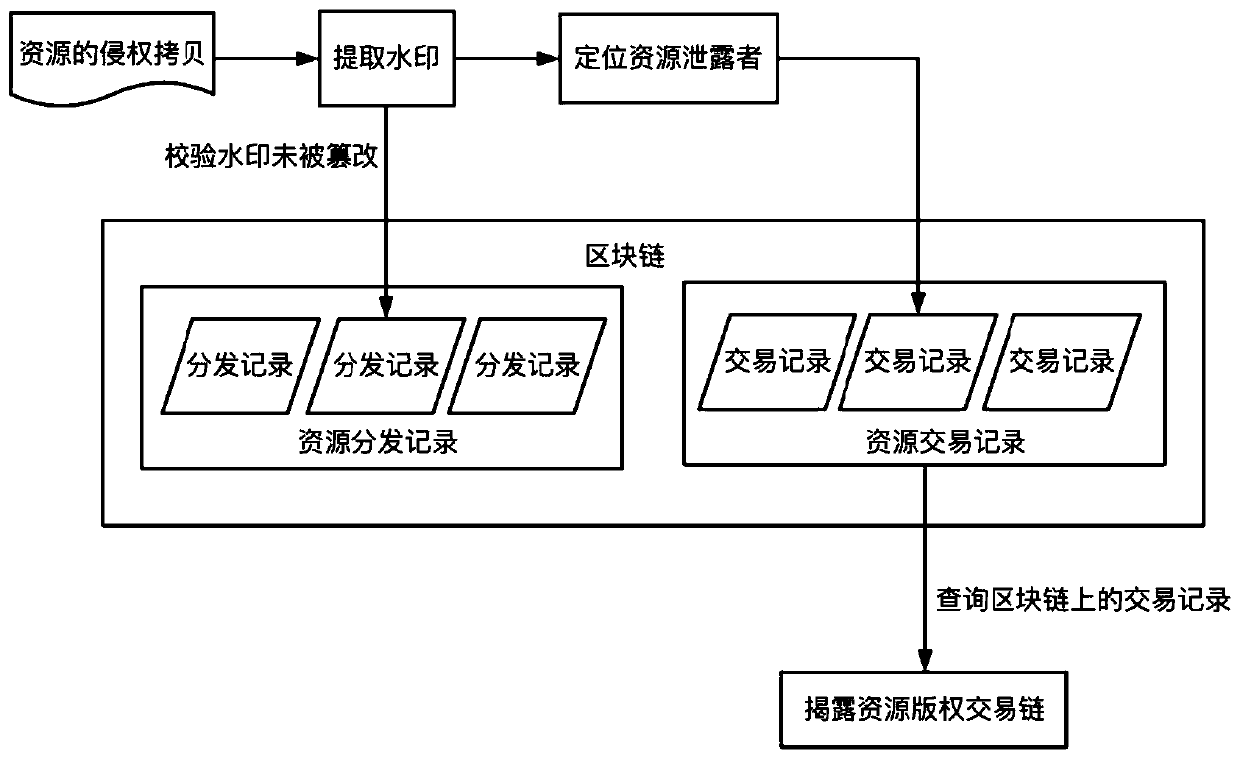
A digital resource infringement tracking method and system based on block chain digital watermarking
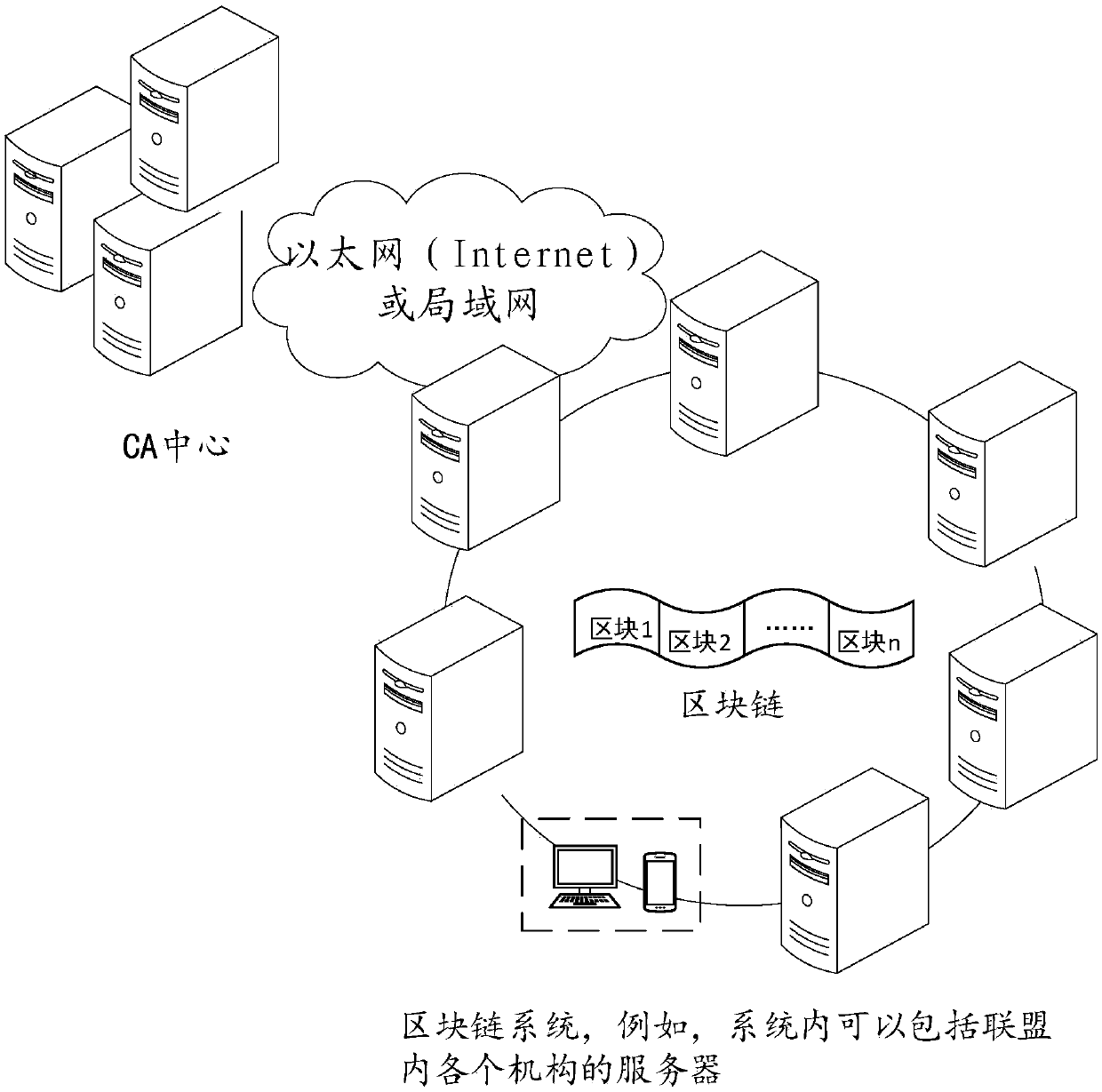
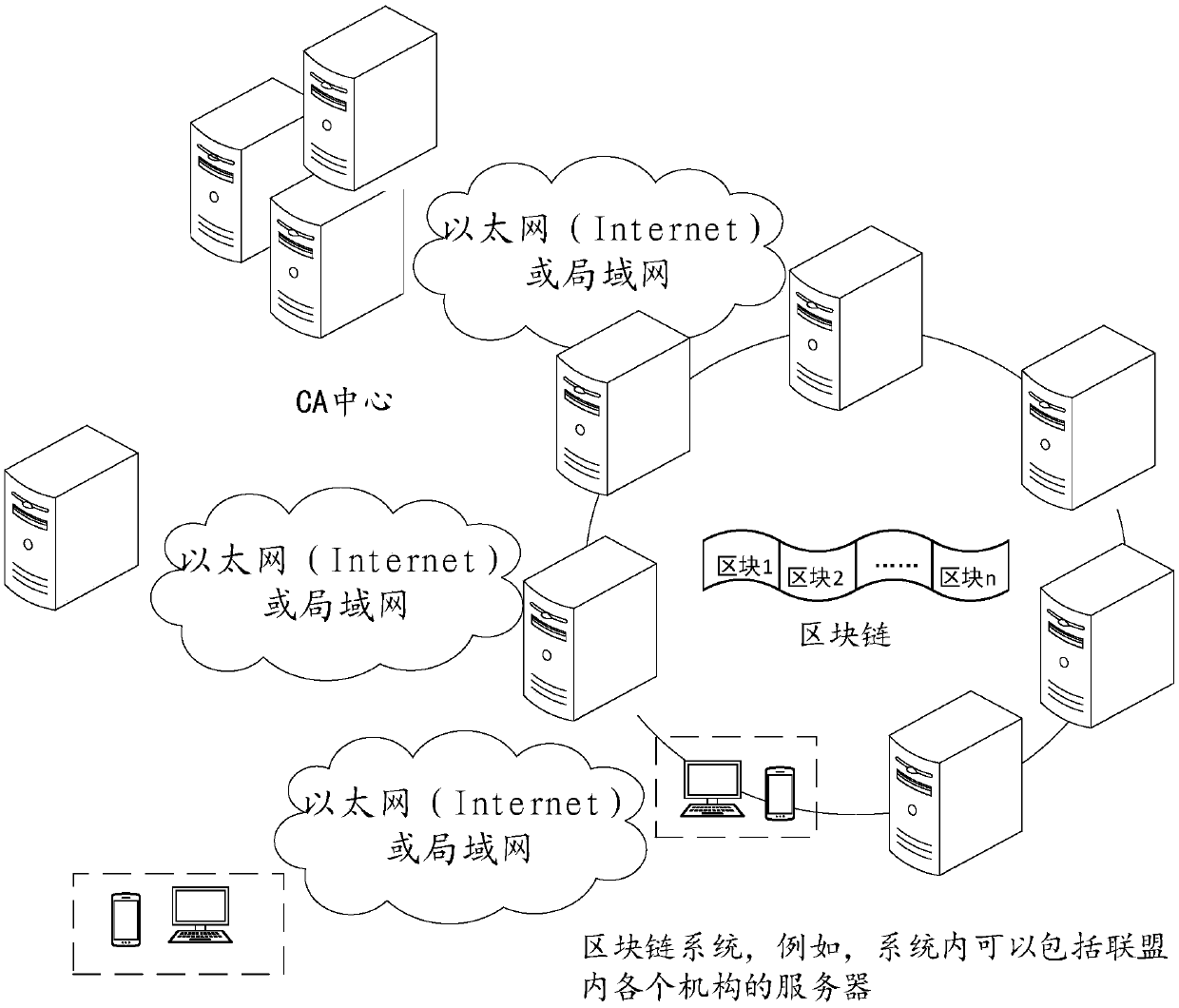
InactiveCN109711120ASolve pain pointsGuaranteed to be authenticFinanceDigital data protectionChronological timeChain system
The invention relates to the technical field of block chain application. The invention discloses a block chain digital watermark-based digital resource infringement tracking method and system, and themethod comprises the steps: packaging digital resource uploading, transaction and distribution information into a block, and recording the block in a block chain according to a time sequence, and comprises the steps: generating a block on the block chain when a user uploads digital resources, and recording copyright information; when the copyright of the digital resource is transferred, a block is generated on the block chain, and corresponding transaction information is recorded; when the digital resources are distributed, a block is generated on the block chain, corresponding distribution information is recorded, and a digital watermark is embedded into the digital resource entity; when infringement copying of digital resources occurs on the market, infringement tracking is carried outby combining the digital watermarks in the infringement copying of the digital resources with the transaction records of the digital resources on the block chain system. According to the method, the digital watermark is combined with the block chain, so that the digital watermark information can not be tampered with a chain, and infringement tracking information is guaranteed to be real and credible.
Owner:ZHEJIANG UNIV
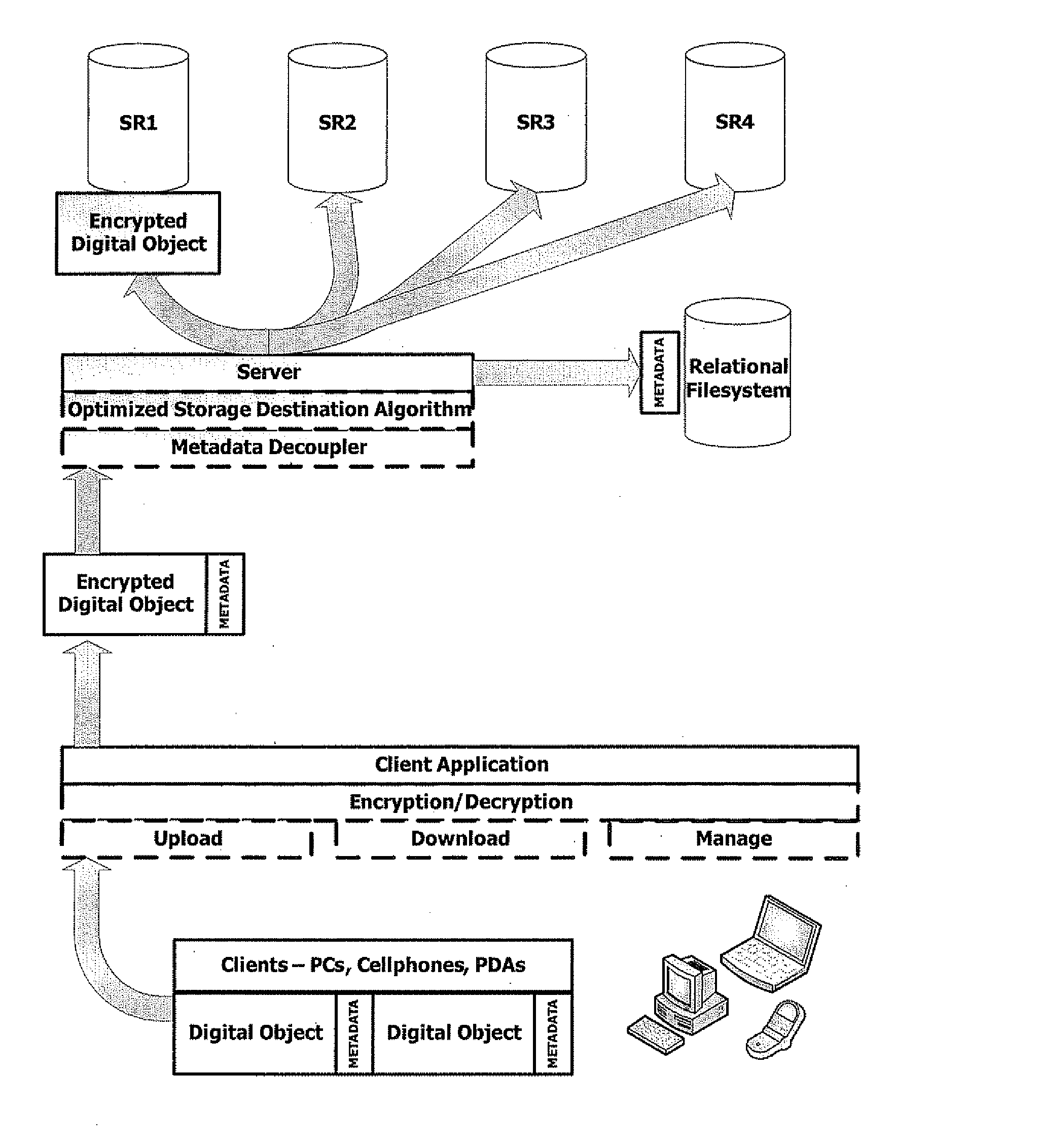
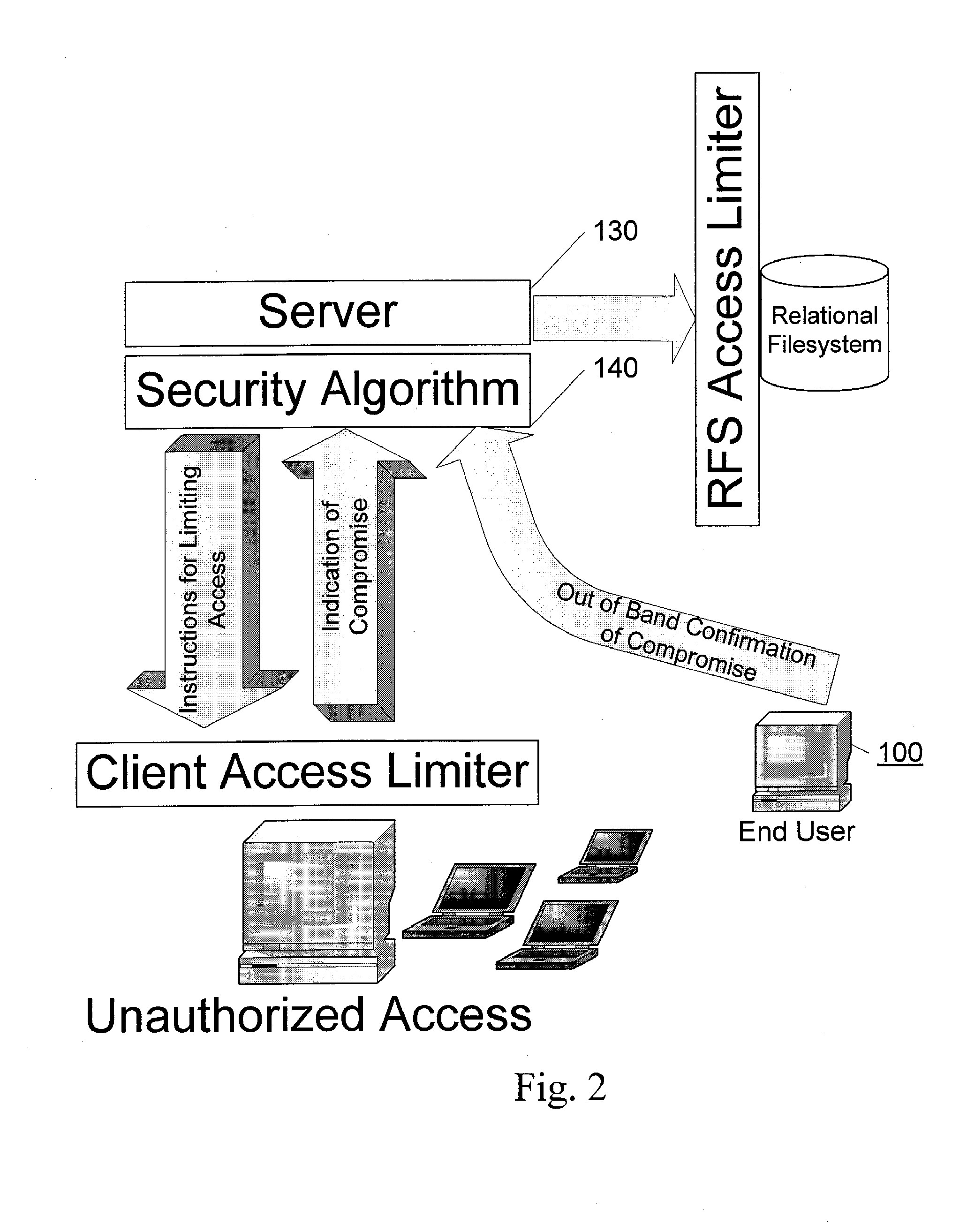
Abstracted and optimized online backup and digital asset management service
InactiveUS20080052328A1Overcome deficienciesLow costDigital data information retrievalDigital data processing detailsRelational databaseAccess frequency
A system and method for providing online storage and security. Digital assets are sent from client applications to server applications. The server implements an algorithm that optimizes the storage of digital assets. The server extracts the meta-data from digital assets and stores the meta-data in a relational database. The storage of digital assets will depend on analyzing the meta-data; factors such as file type, frequency of usage, and frequency of access are considered by the storage destination optimizing algorithm. The server also implements an algorithm that protects the digital assets from unauthorized network access. Upon detection of network intrusion by the security algorithm, the digital assets of the compromised users will be frozen, then either be destroyed or render unreadable by the unauthorized user. The security algorithm may then send an instance of the digitals assets to the compromised user to ensure that the digital assets remain accessible.
Owner:ELEPHANTDRIVE
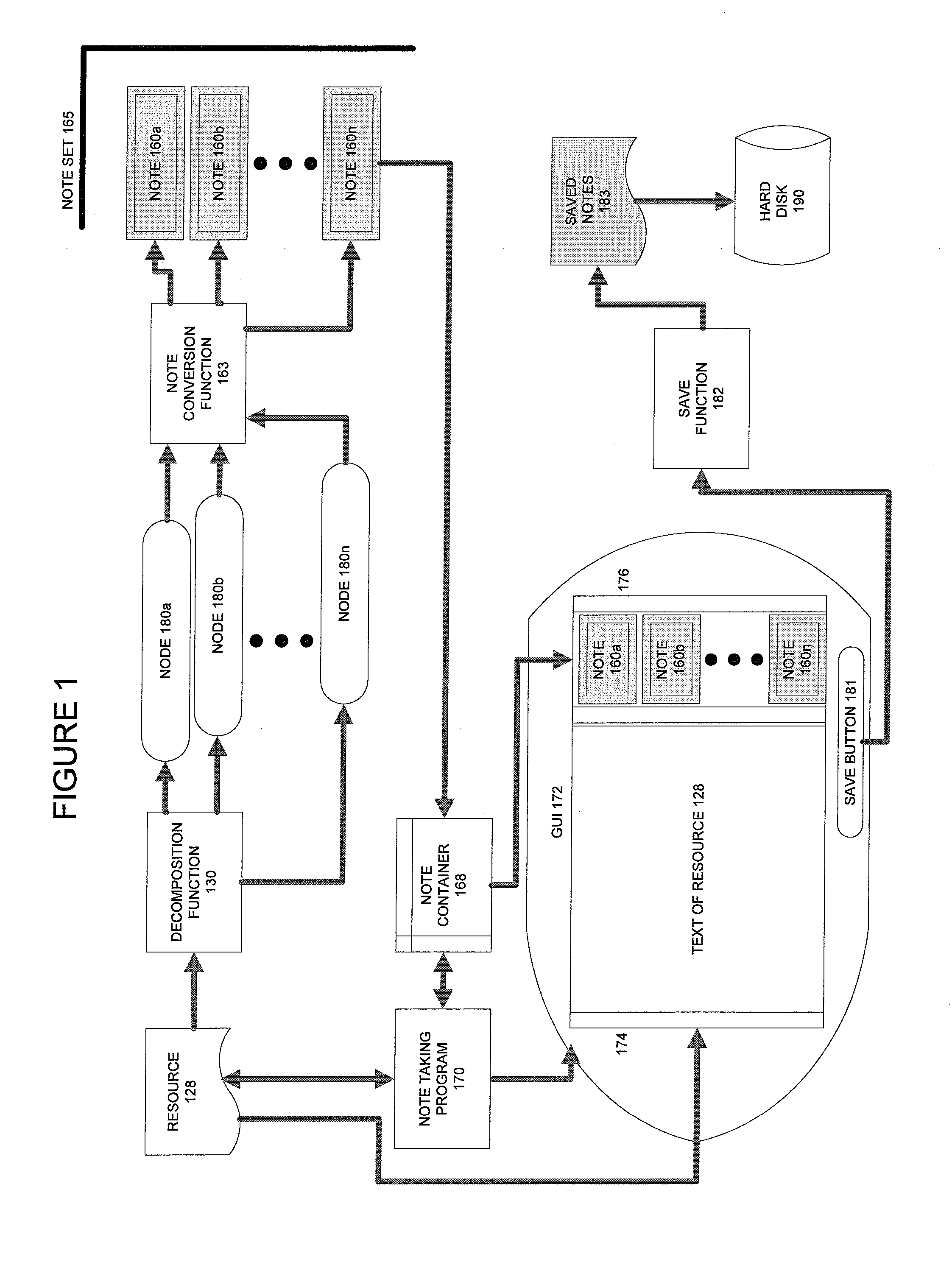
Techniques for Creating Computer Generated Notes
ActiveUS20080021701A1Facilitate knowledge acquisitionFacilitate utilizationNatural language analysisWeb data indexingInformation resourceRelational database
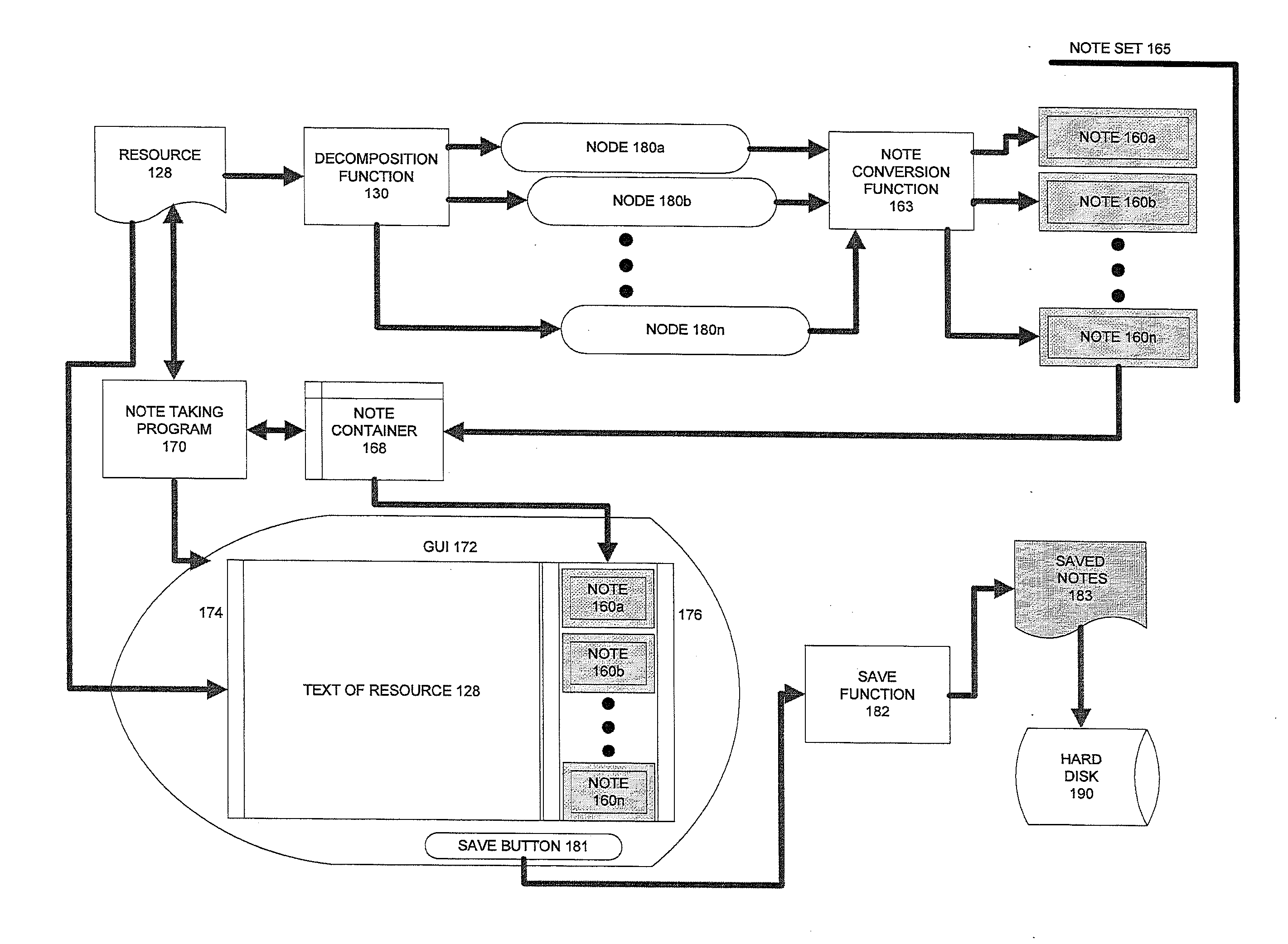
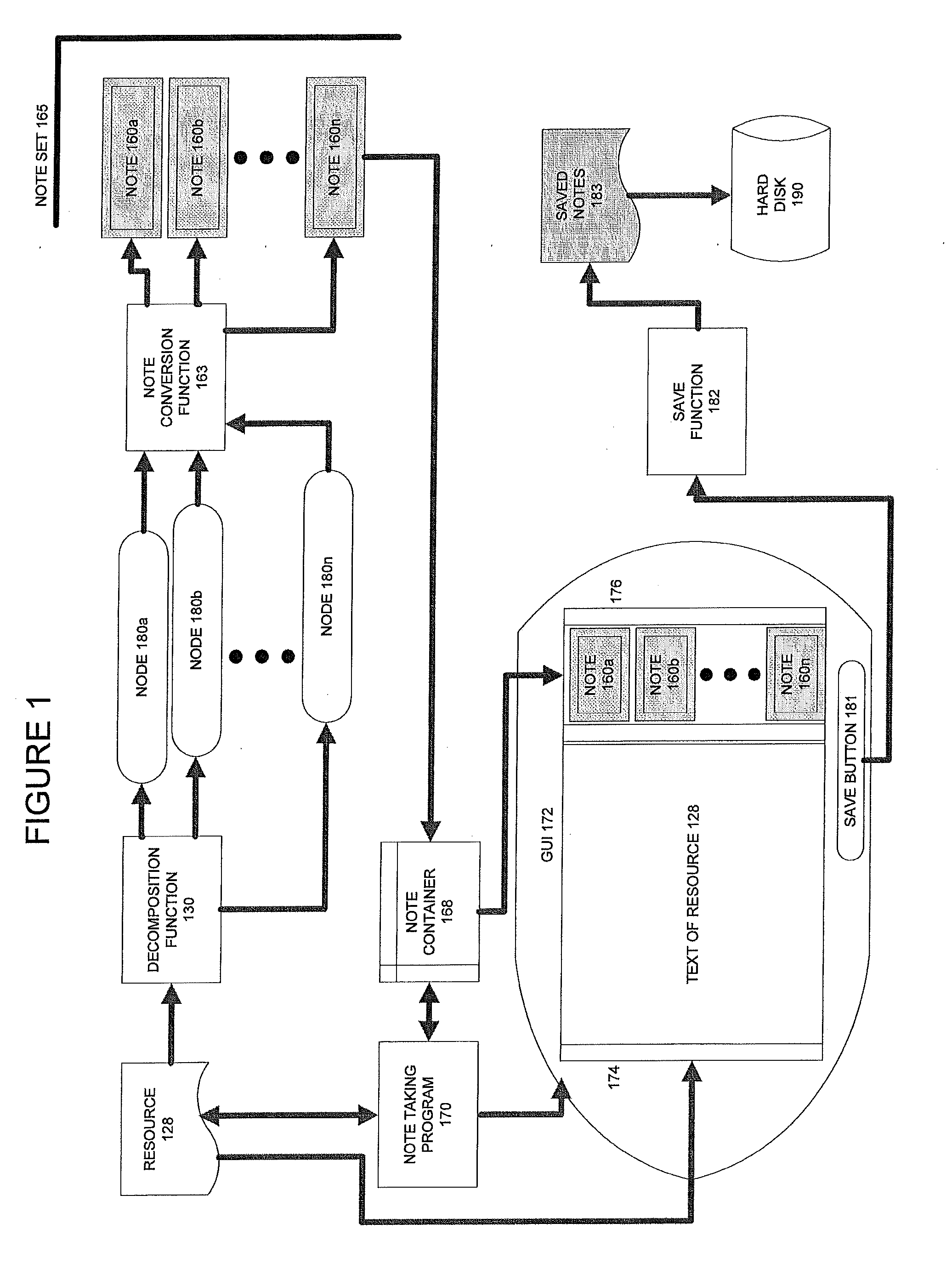
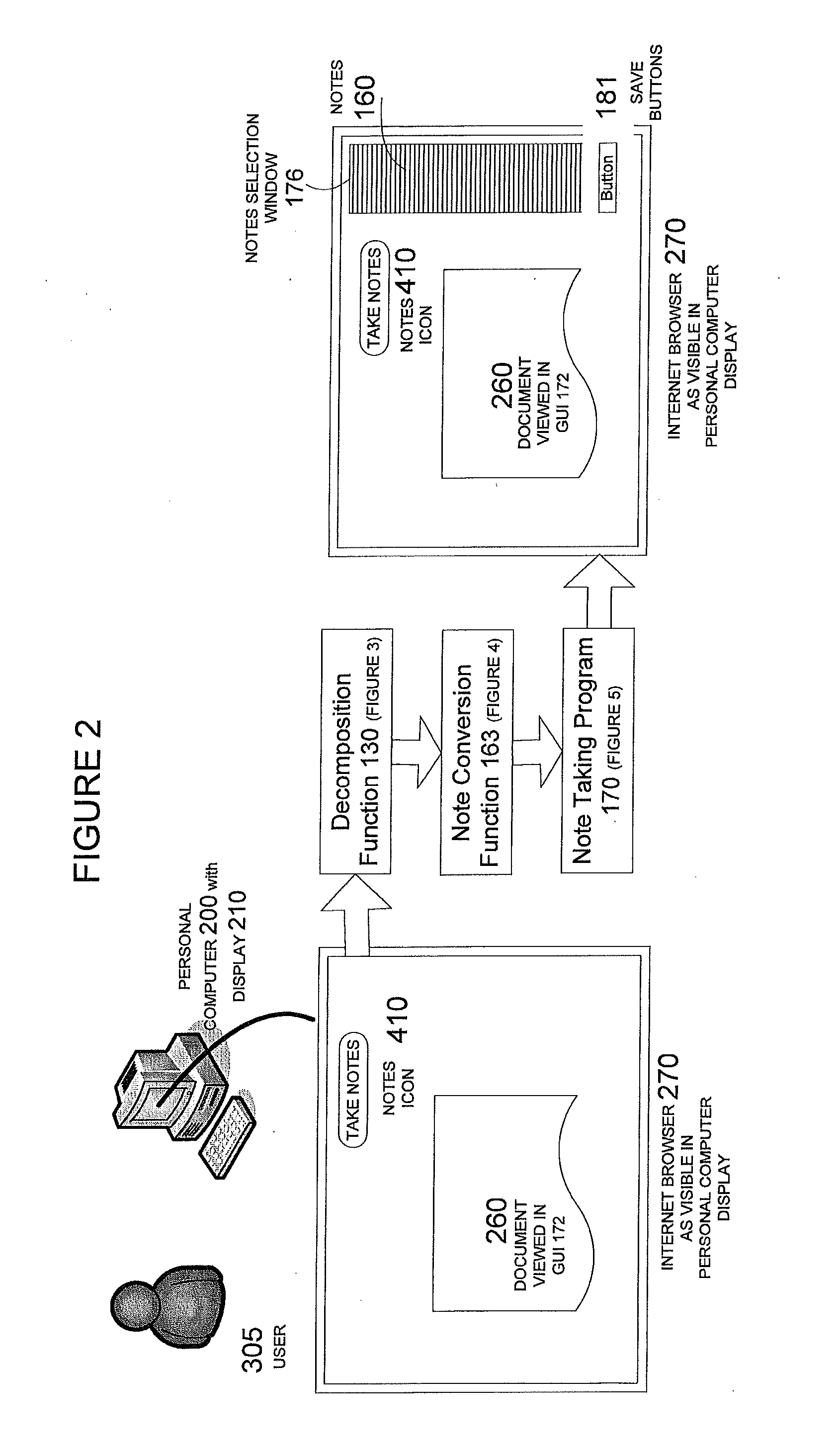
Text is extracted from and information resource such as documents, emails, relational database tables and other digitized information sources. The extracted text is processed using a decomposition function to create. Nodes are a particular data structure that stores elemental units of information. The nodes can convey meaning because they relate a subject term or phrase to an attribute term or phrase. Removed from the node data structure, the node contents are or can become a text fragment which conveys meaning, i.e., a note. The notes generated from each digital resource are associated with the digital resource from which they are captured. The notes are then stored, organized and presented in several ways which facilitate knowledge acquisition and utilization by a user.
Owner:MAKE SENCE
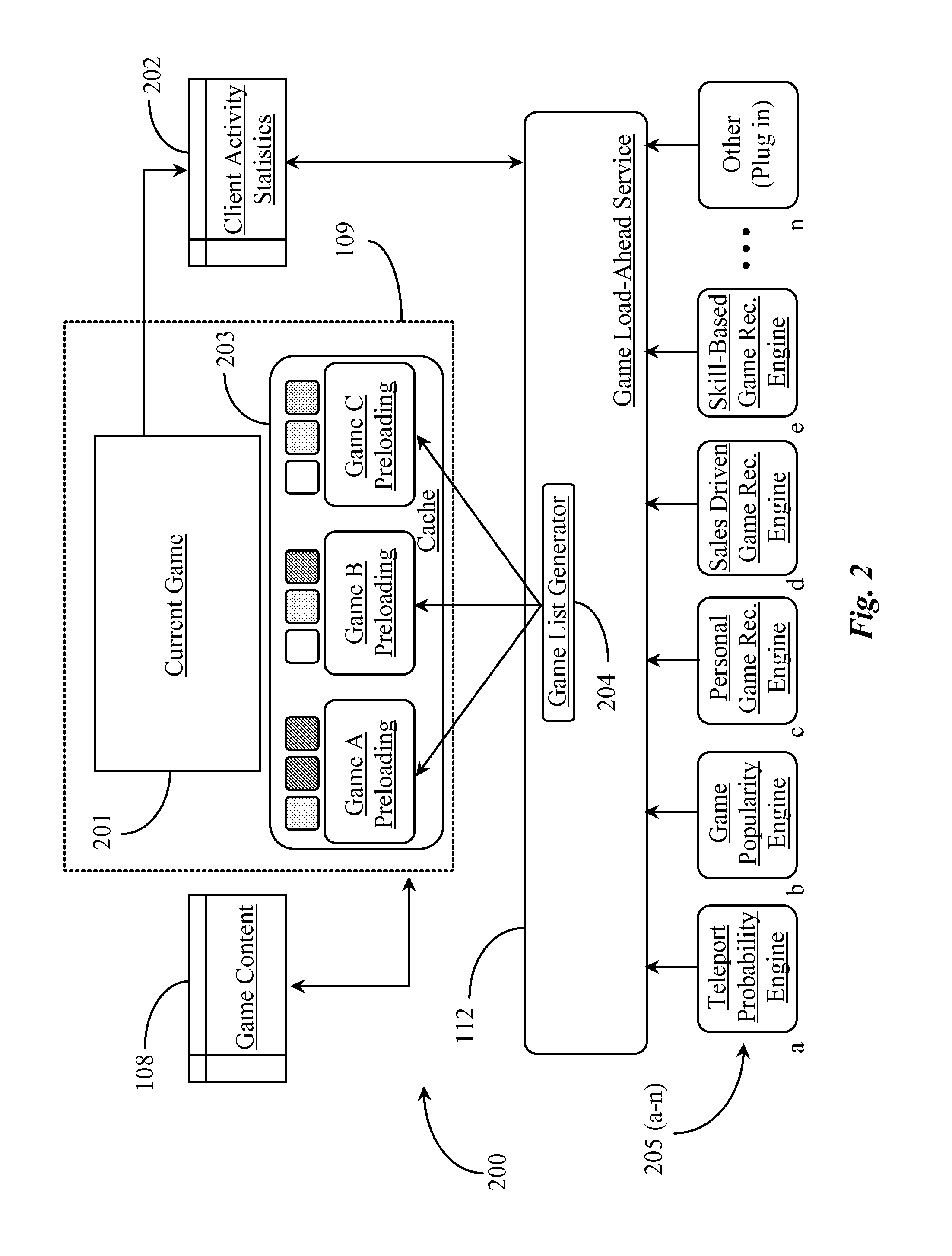
System for Pre-Caching Game Content Based on Game Selection Probability
InactiveUS20130137518A1Faster game loadingImprove loading timeVideo gamesTransmissionThe InternetDigital resources
A system for serving digital games to clients has an Internet-connected server, a digital data repository coupled to the Internet-connected server, the data repository storing digital resources for playing a plurality of games on a computerized appliance; and software executing on the Internet-connected server from a non-transitory physical medium, the software providing a first function determining for a specific client a list of games by probability of subsequent client selection, a second function causing transmission of resources for the list of games determined by the first function, directed to a computerized appliance associated with client, beginning with the most probable game in the list.
Owner:ROBLOX CORP
Method and system of user authentication with eye-tracking data
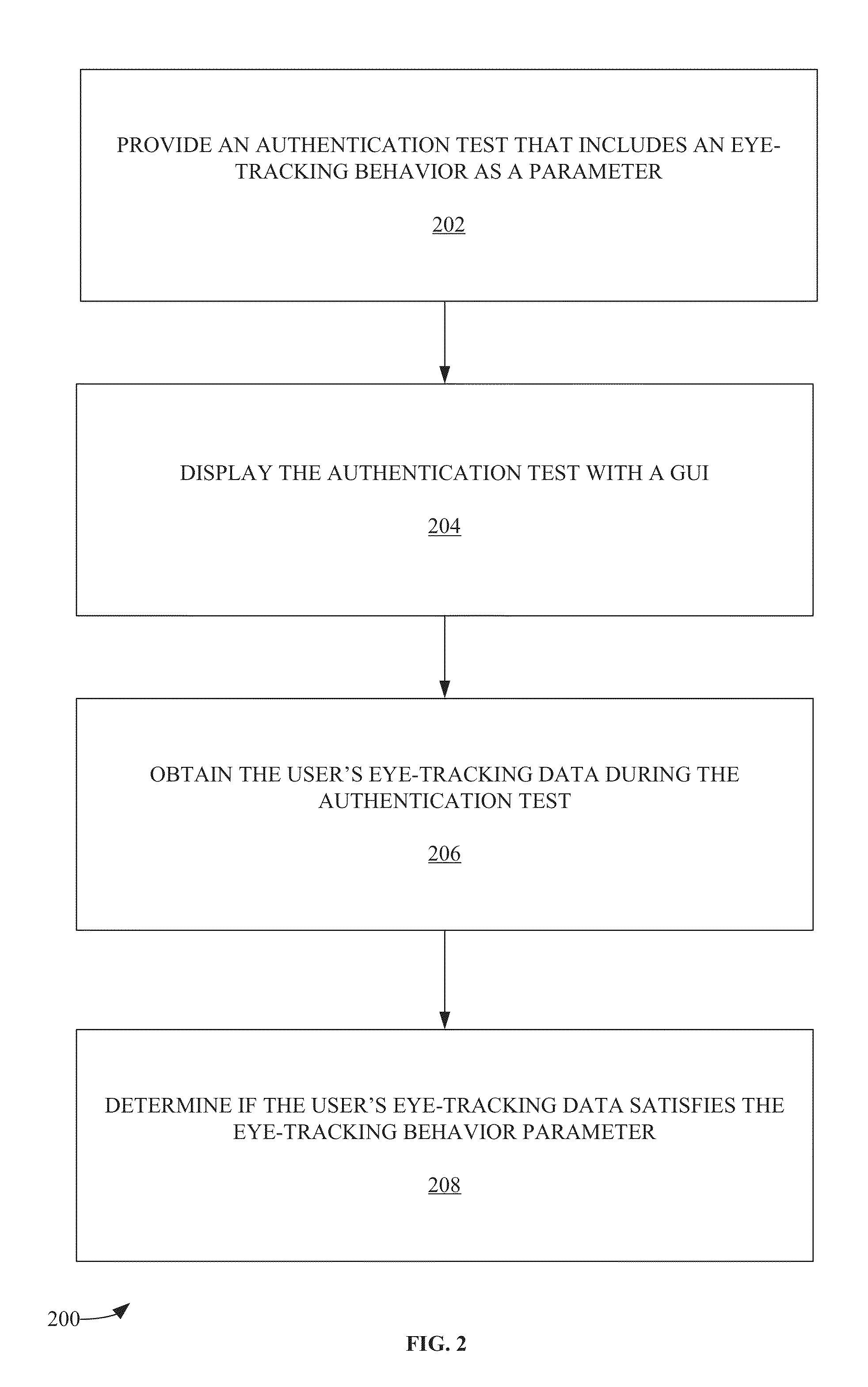
InactiveUS20150135309A1Input/output for user-computer interactionDigital data information retrievalUser authenticationEye tracking system
In one exemplary embodiment, a computer-implemented method includes the step of providing an image to a user. The image is provided with a computer display. An eye-tracking data is obtained from the user when the user views the image. The eye-tracking data is obtained with an eye-tracking system. A user attribute is determined based on the eye-tracking data. The user is enabled to access a digital resource when the user attribute is associated with a permission to access the digital resource. The user attribute can be a personhood state. The digital resource can be a web page document. An instruction can be provided to the user regarding a pattern of viewing the image. The pattern of viewing the image can include instructing the user to gaze on a specified sequence of image elements.
Owner:KARMARKAR AMIT VISHRAM +1
Common drawing model
InactiveUS20130321306A1Input/output for user-computer interactionCathode-ray tube indicatorsClient-sideHuman–computer interaction
An approach for sharing a master version of a drawing with multiple clients is provided, wherein an example embodiment comprises capturing a first gesture associated with a first digital resource at a first device, transmitting data representing the first gesture from the first device to a server, processing the data representing the first gesture at the server, storing the data representing the first gesture at the server, transmitting the data representing the first gesture to a second device, processing the data representing the first gesture at the second device, and rendering the first gesture on the second device.
Owner:DOOR NUMBER 3
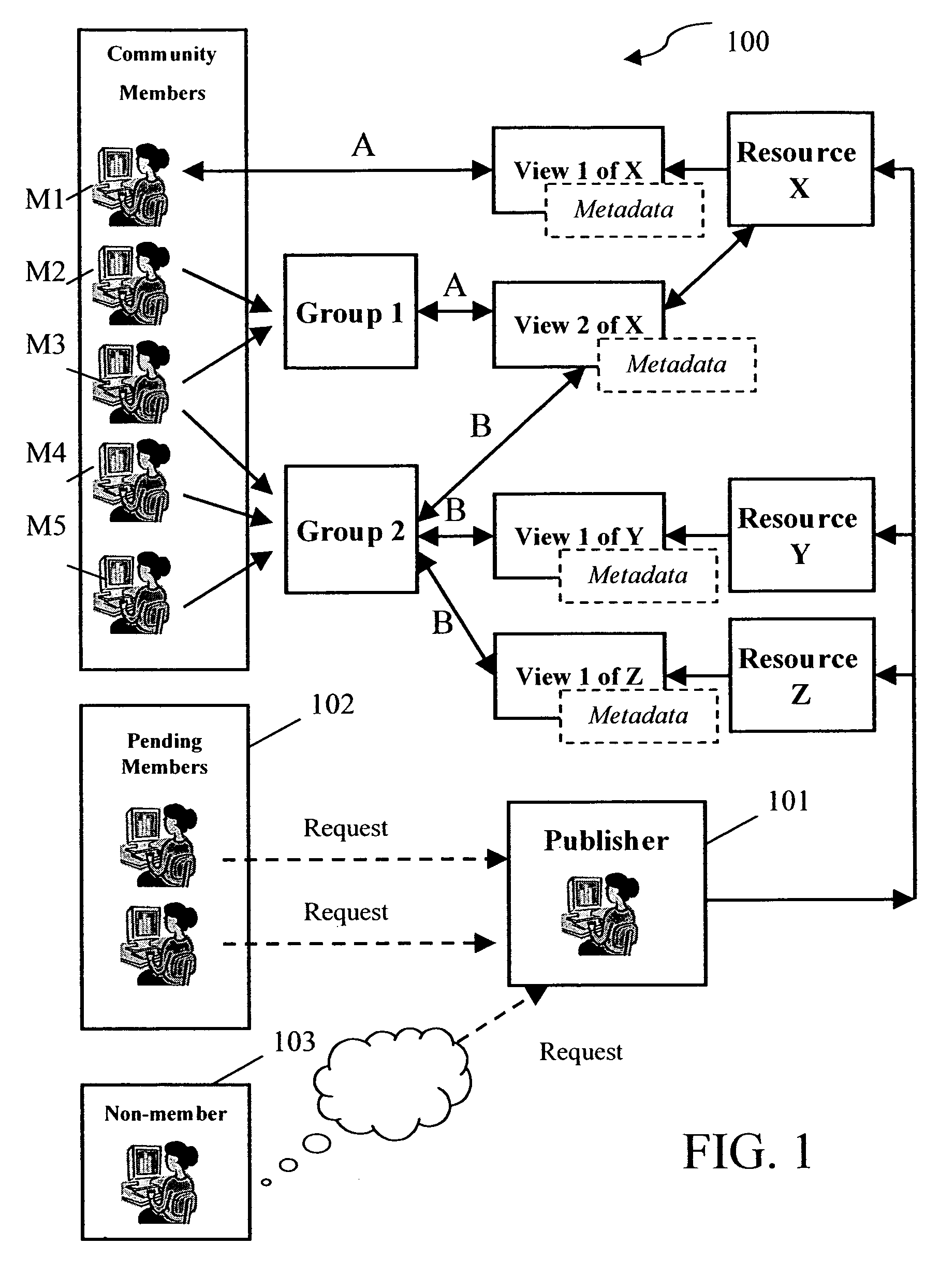
System and method for community centric resource sharing based on a publishing subscription model
InactiveUS7739602B2Good choiceReceives changeMultiple digital computer combinationsOffice automationWeb serviceShared resource
The invention provides a Web service which enables a publisher to share his digital resources such as an address card or a calendar with a number of subscribers based on different sharing relationships. The Web service includes a host-based interface called “My Community”, for example, with which the publisher manages the share-relationships with his community members. The community members are organized into different groups. Each group includes a number of community members who have a common sharing relationship with the publisher with respect to one or more views of the shared resources. A resource may have multiple views. Each of the views has Metadata describing sharing-styles, as well as version, creation date, size, and the like. Each sharing style corresponds to a specific sharing relationship between a community member and the publisher.
Owner:GOOGLE LLC
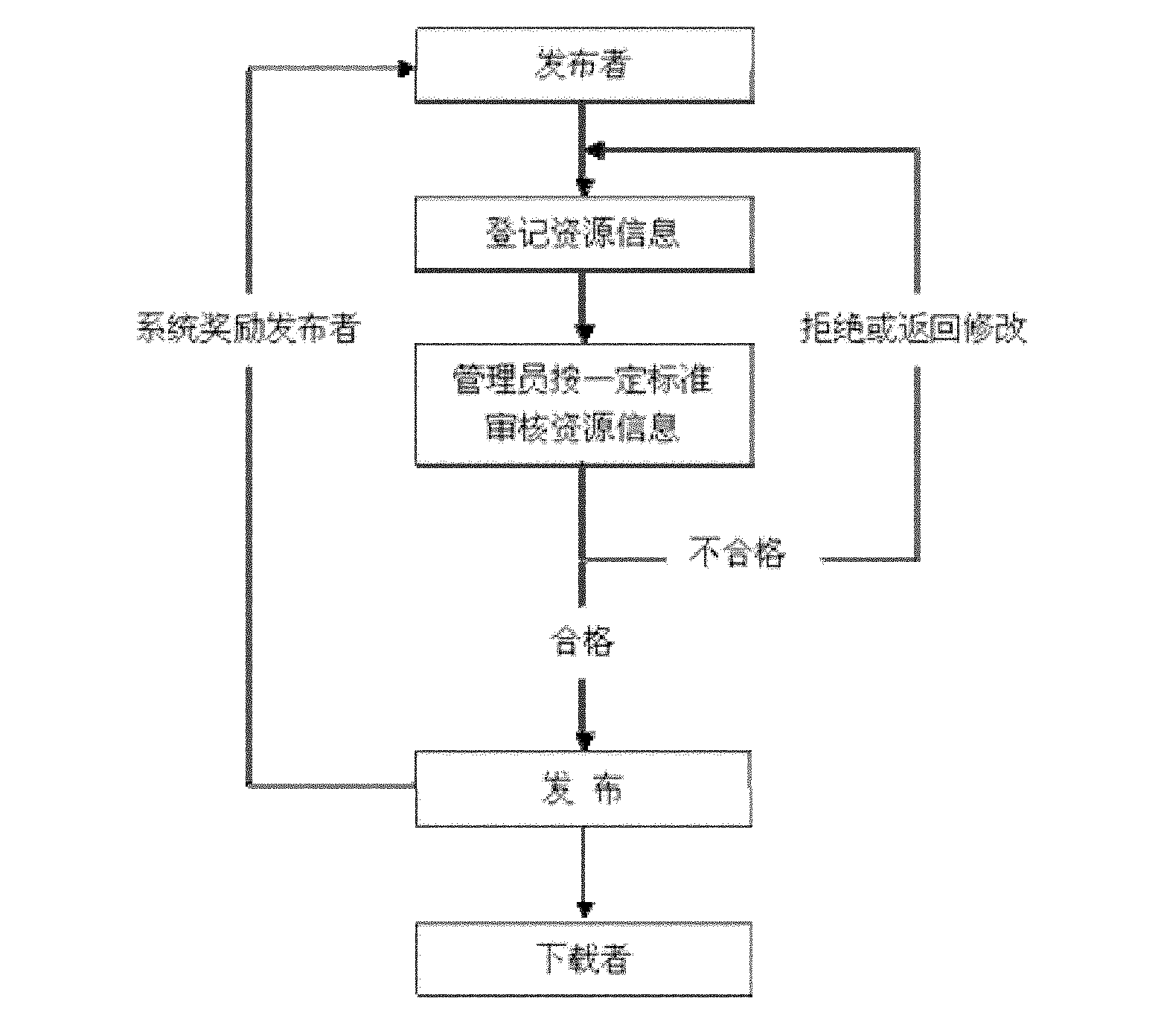
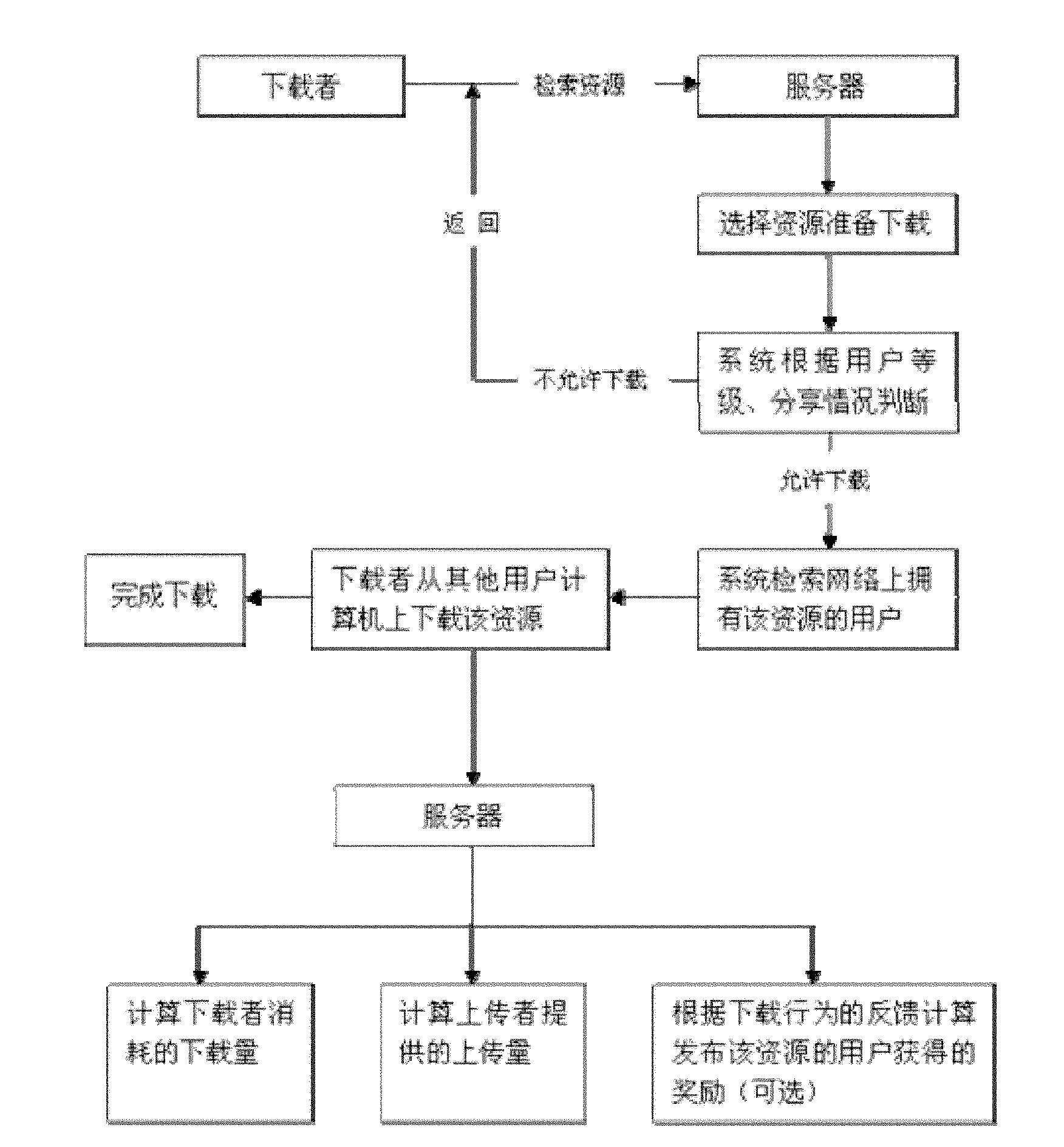
User contribution-based method and system for sharing personalized digital resources
The invention relates to a user contribution-based method and a user contribution-based system for sharing personalized digital resources. The method mainly comprises a user registration step, a resource releasing step and a resource downloading step, wherein a system manager examines and grades the resources, and a resource downloading mode adopts a peer-to-peer technology. The system based on the method mainly comprises a server for registering and calculating user contribution, the system manager for examining the resources and rewarding a user, a resource releasing party and a resource downloading party. The invention adopts an incentive policy of evaluating the user contribution and giving the user relevant rights and interests, so the user is promoted to make more contribution for the system, and the sustainable scale development of the system is promoted; meanwhile, the system adopts a combined manner of examining and grading by a network manager and peer-to-peer (P2P) download, so the server pressure is effectively reduced, and the network sharing of big-bytes personalized digital resources is realized.
Owner:肖智刚
Block chain based resource management
PendingUS20190139047A1Digital data information retrievalUser identity/authority verificationProcessing coreResource management
According to an example aspect of the present invention, there is provided an apparatus comprising a memory configured to store an identifier of a digital resource, at least one processing core configured to cause transmission of a request to receive the digital resource in the apparatus, the request comprising the identifier, and to verify, using a first distributed block chain ledger, that a user of the apparatus is authorized to access the digital resource.
Owner:NOKIA TECHNOLOGLES OY
Suspected target analyzing system and method by video investigation
ActiveCN102819578AImprove playbackAvoid latency effectsImage analysisSpecial data processing applicationsPattern recognitionTarget analysis
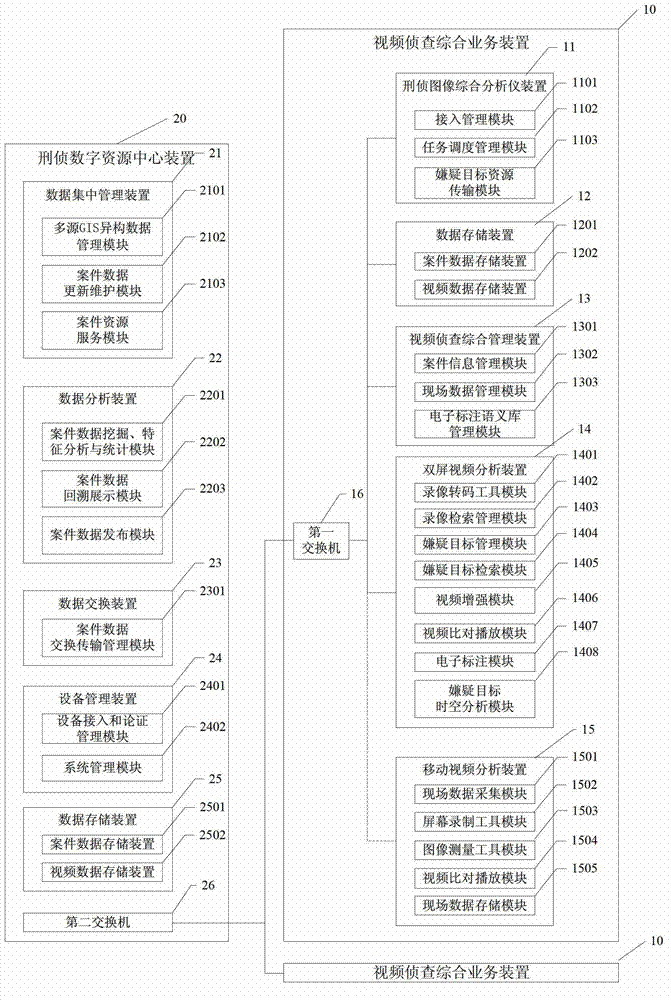
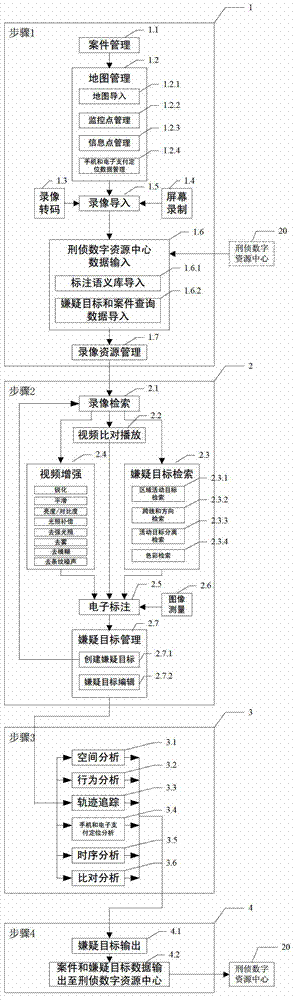
The invention discloses a suspected target analyzing system and a method by a video investigation, belonging to the field of a criminal investigation video analysis. The system comprises a video investigation comprehensive business device and a criminal investigation digital resource center device which are connected to each other through an exchanger. By using the system, the case field information is structured, various monitoring video formats are transcoded to an uniform format; each frame image of a fuzzy video including a suspected target is enhanced to form a video enhanced segment; a suspected target video segment is obtained through the suspected target index with zero loss and low false drop rate; the unified semantic electronic mark is carried out on the suspected target video segment; the suspected target is found, screened and tracked by performing the space analysis, action analysis, trajectory tracking, positioning trace analysis of telephone and electronic payments, time sequence analysis, feature contrasting and analysis; furthermore, the system and the method can be widely applied to the video investigation and case solution.
Owner:WUHAN DAQIAN INFORMATION TECH
Systems and methods for controlling access to data on a computer with a secure boot process
ActiveUS20060161790A1Improve efficiencyAvoid accessVolume/mass flow measurementUnauthorized memory use protectionProcess systemsDisk partitioning
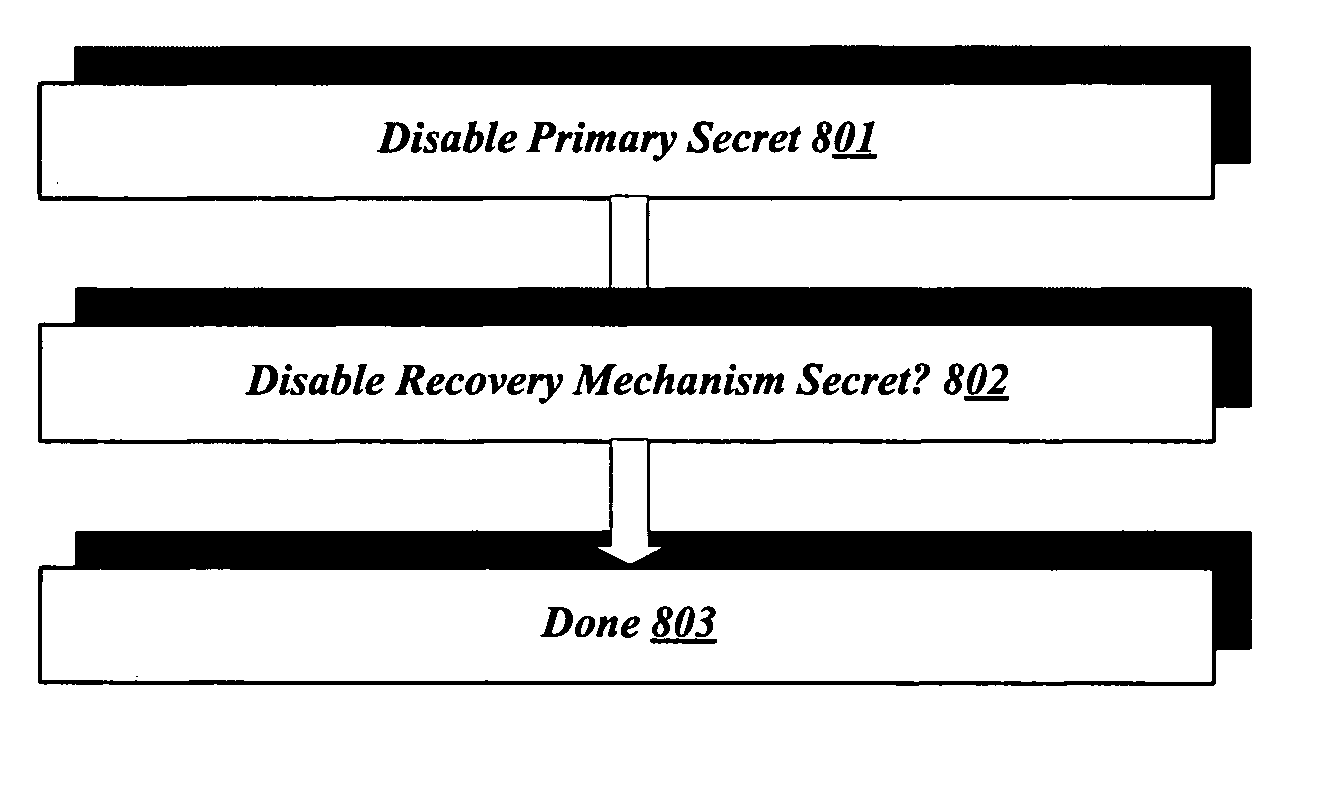
Systems and methods for controlling access to data on a computer with a secure boot process can provide a highly efficient mechanism for preventing future access to encrypted digital resources. This may be advantageous in a range of scenarios, for example where a computer is sold and assurance is desired that no stray private data remains on the hard disk. Data resources, for example all data associated with one or more particular hard disk partitions, may be encrypted. The decryption key may be available through a secure boot process. By erasing, altering, or otherwise disabling a secret, such as a decryption key or a process that obtains a decryption key, the data formerly accessible using such secret becomes inaccessible.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for notifying a server with cache information and for serving resources based on it
ActiveUS20130339472A1Reduce in quantityDigital computer detailsTransmissionCommunications systemResource based
The present invention relates to the notification of a server device with the availability of resources in cache memories of a client device and to the serving of digital resources in such a client-server communication system. The notifying method comprises: obtaining a first list of resources available in the cache memories of the client device; filtering the first list according to filtering criteria relating to a resource parameter, to obtain a filtered list of fewer resources available in the client device or splitting the first list according to splitting criteria relating to a resource parameter, to obtain a plurality of sub-lists of resources available in the client device; and notifying the server device with data structures representing the filtered list or sub-lists of resources.
Owner:CANON KK
Method and system of user authentication with bioresponse data
InactiveUS8988350B2Input/output for user-computer interactionAcquiring/recognising eyesUser authenticationEye tracking system
Owner:BUCKYBALL MOBILE
Method and device for accessing digital resources
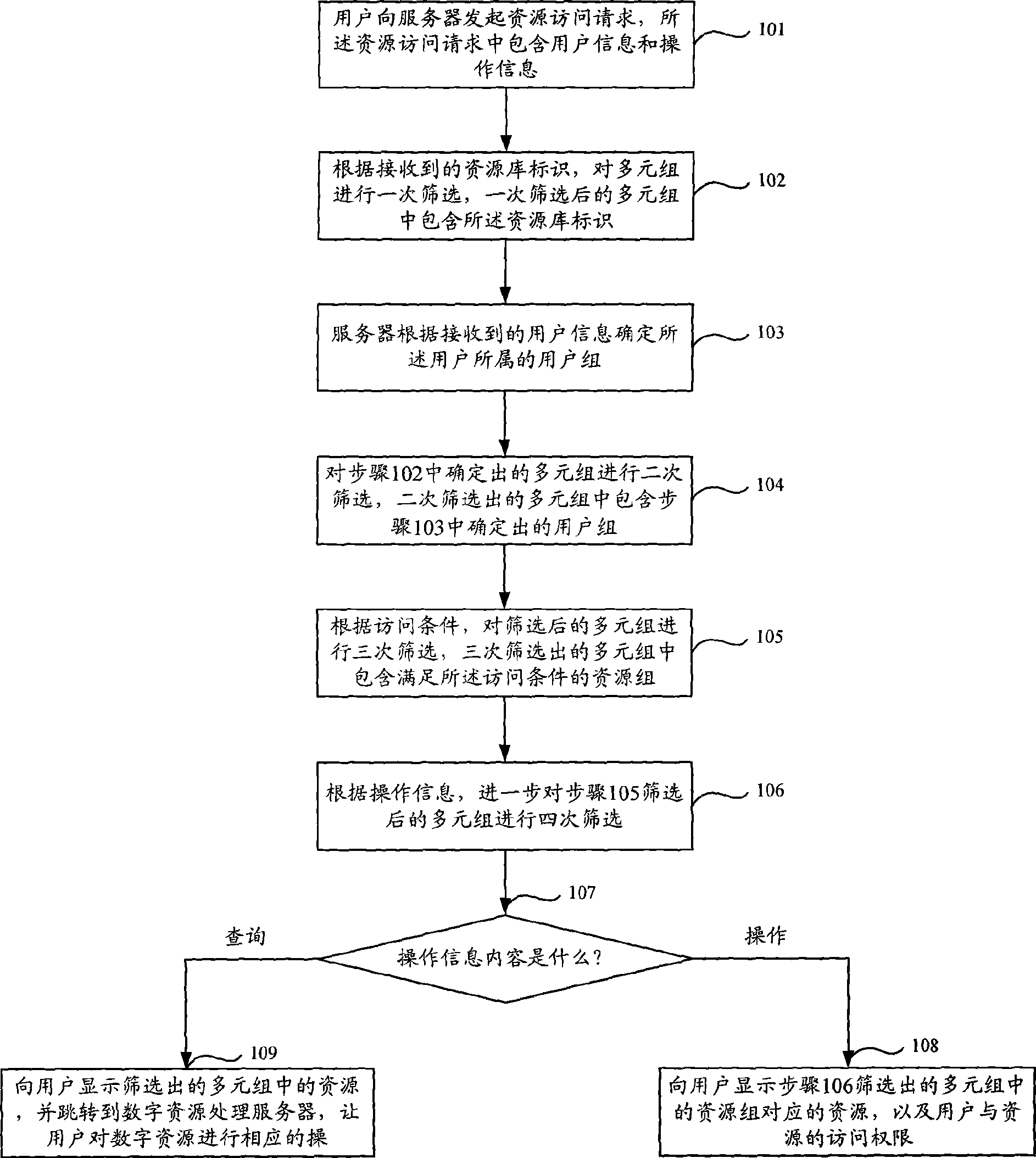
ActiveCN101448002AReduce in quantityAccess rights lookupData switching networksSpecial data processing applicationsAccess methodData resources
The invention discloses a method for accessing digital resources, which comprises steps as follows: multiple tuples are screened according to user information in the received resource accessing request, the screened multiple tuples comprises a user group including the user information; the screened multiple tuples are further selected according to the operation information in the resource accessing request, the relation between the user and the resources selected in the multiple tuples meets that of the user and the resources in the operation information, and the access authority of the user and the resources in the multiple tuples is matched with the operation required by the user in the operation information; and the selected multiple tuples including the resources corresponding to the resource group are outputted. By adopting the method for accessing digital resources, the quantity of the authority relation is reduced, and the access authority of the user for specific data resources can be quickly searched. In addition, the invention also discloses an accessing device for digital resources.
Owner:PEKING UNIV +2
Systems and methods for controlling access to data on a computer with a secure boot process
ActiveUS7565553B2Improve efficiencyAvoid accessVolume/mass flow measurementUnauthorized memory use protectionProcess systemsDisk partitioning
Systems and methods for controlling access to data on a computer with a secure boot process can provide a highly efficient mechanism for preventing future access to encrypted digital resources. This may be advantageous in a range of scenarios, for example where a computer is sold and assurance is desired that no stray private data remains on the hard disk. Data resources, for example all data associated with one or more particular hard disk partitions, may be encrypted. The decryption key may be available through a secure boot process. By erasing, altering, or otherwise disabling a secret, such as a decryption key or a process that obtains a decryption key, the data formerly accessible using such secret becomes inaccessible.
Owner:MICROSOFT TECH LICENSING LLC
Learning resource push method and system based on learning preferences of users
InactiveCN107800801AMeeting the Needs of Personalized LearningGood market prospects and social benefitsTransmissionSpecial data processing applicationsSocial benefitsPersonalization
The invention provides a learning resource push method based on learning preferences of users. The method includes the following steps: firstly, acquiring the learning preferences of different users,and establishing a user attribute library according to the different learning preferences; and then classifying various types of learning resources according to different attributes, and establishinga digital resource attribute library; and finally, establishing a recommendation model according to a corresponding relationship between the user attribute library and the digital resource attribute library, wherein the recommendation model automatically selects digital resources of the corresponding attribute to perform personalized learning resource pushing according to different user attributes. The invention also provides a learning resource push system based on the learning preferences of the users. According to the scheme of the invention, by adopting the learning resource push method based on the learning preferences of the users, the needs of learners for personalized learning can be met, the learning resources can be pushed rapidly and accurately in combination with learning activities of the learners, and the effect of resource recommendation services can be effectively improved. The scheme of the invention has relatively good application and promotion values, and also has relatively good market prospects and social benefits.
Owner:SHANGHAI DIANJI UNIV
Internet precision education tutoring system based on big data and artificial intelligence
InactiveCN110136037ATimely intervention in physical and mental healthClose communication and learningData processing applicationsPersonalizationThe Internet
The invention discloses an internet precision education tutoring system based on big data and artificial intelligence. The system comprises a teacher client, a student client, a parent client, an education manager client and a server. The teacher client, the student client, the parent client and the education manager client are connected with the server. School teaching and management are assistedbased on big data analysis and an artificial intelligence technology so that the education burden of teachers, society and education managers in three aspects is reduced. By establishing a digital resource library and careful knowledge graphs, learning conditions of students are accurately collected, and personalized tutoring plans of the students are formulated in an assisted manner. By establishing an interest stimulation module and a personalized evaluation system, the learning achievement and exploration spirit of students are stimulated. According to the invention, a four-in-one system of'school + teacher + student + parent 'is established in combination with the Internet, and the functions of real-time communication, mutual communication and self-promotion are realized.
Owner:毕成
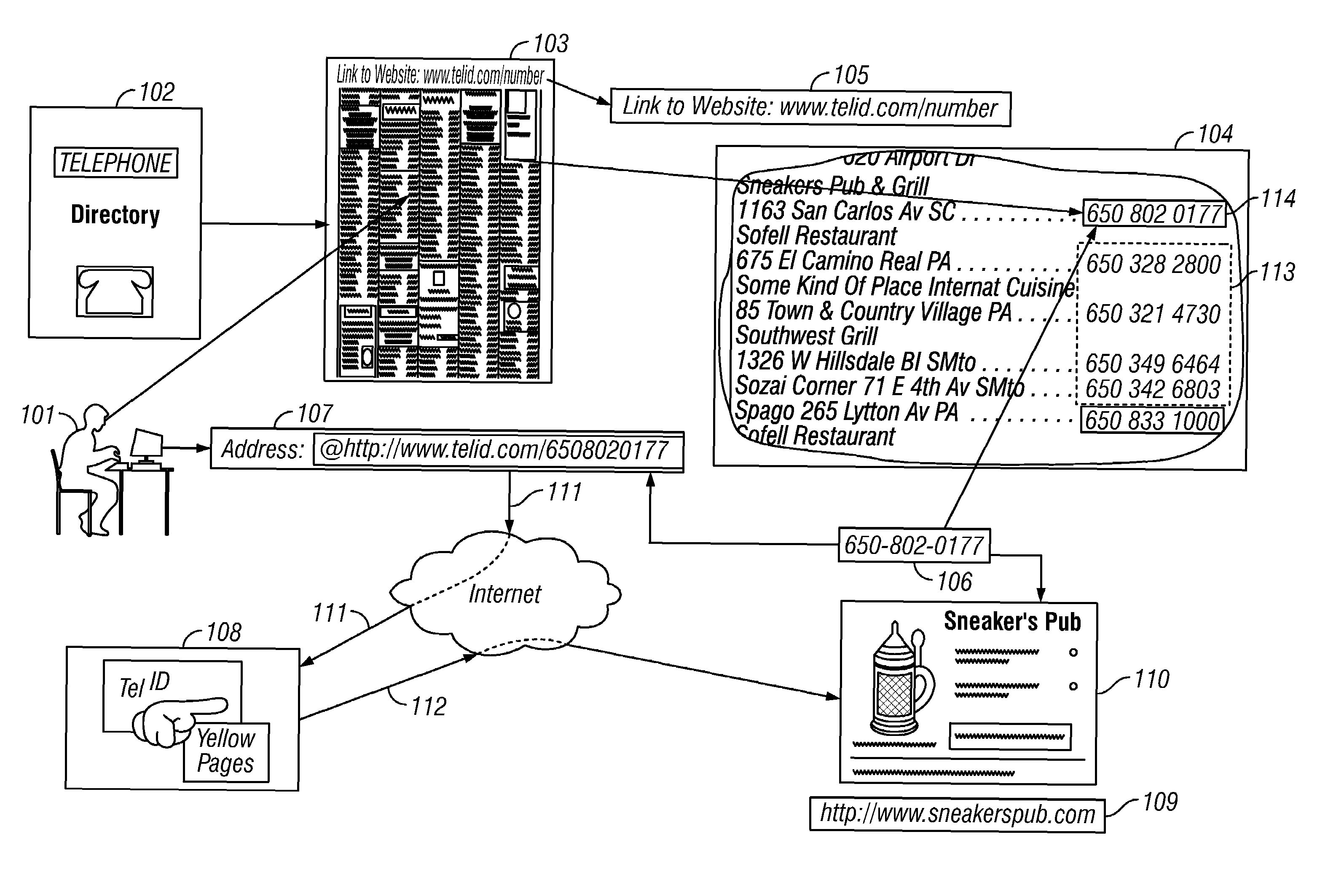
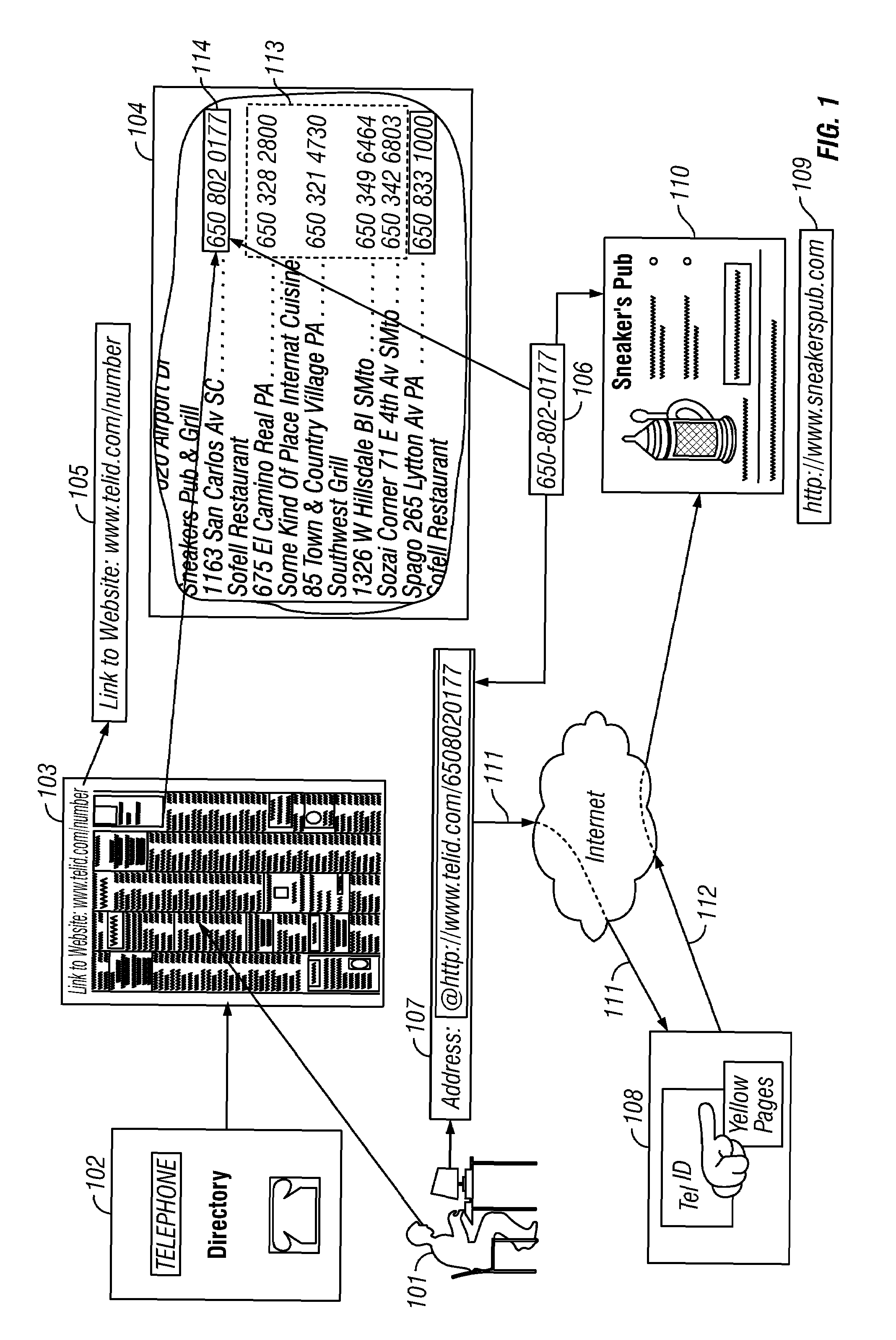
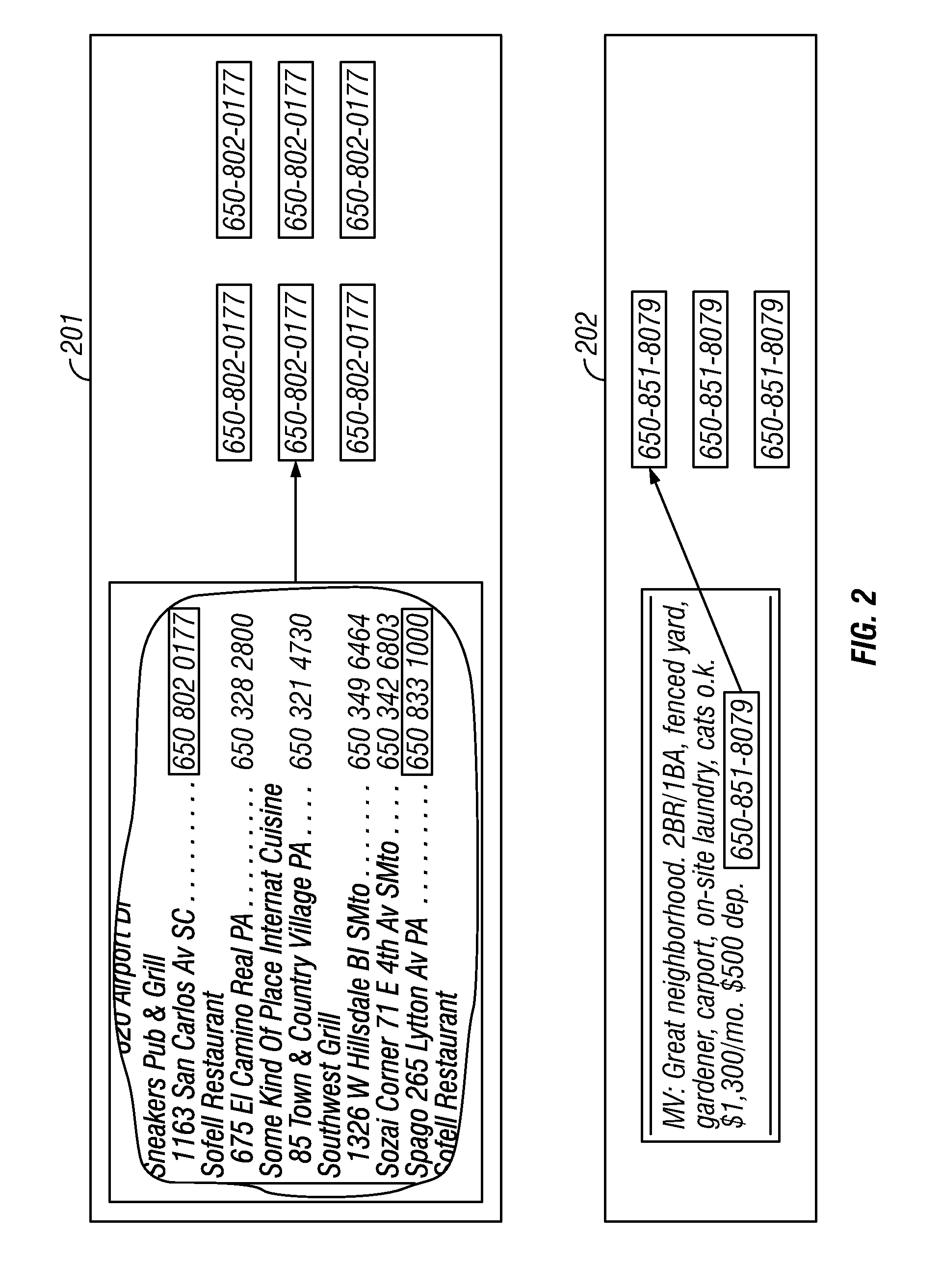
Linking method for printed telephone numbers identified by a non-indicia graphic delimiter
InactiveUS7310772B2Digital data processing detailsMultiple digital computer combinationsGraphicsInternet address
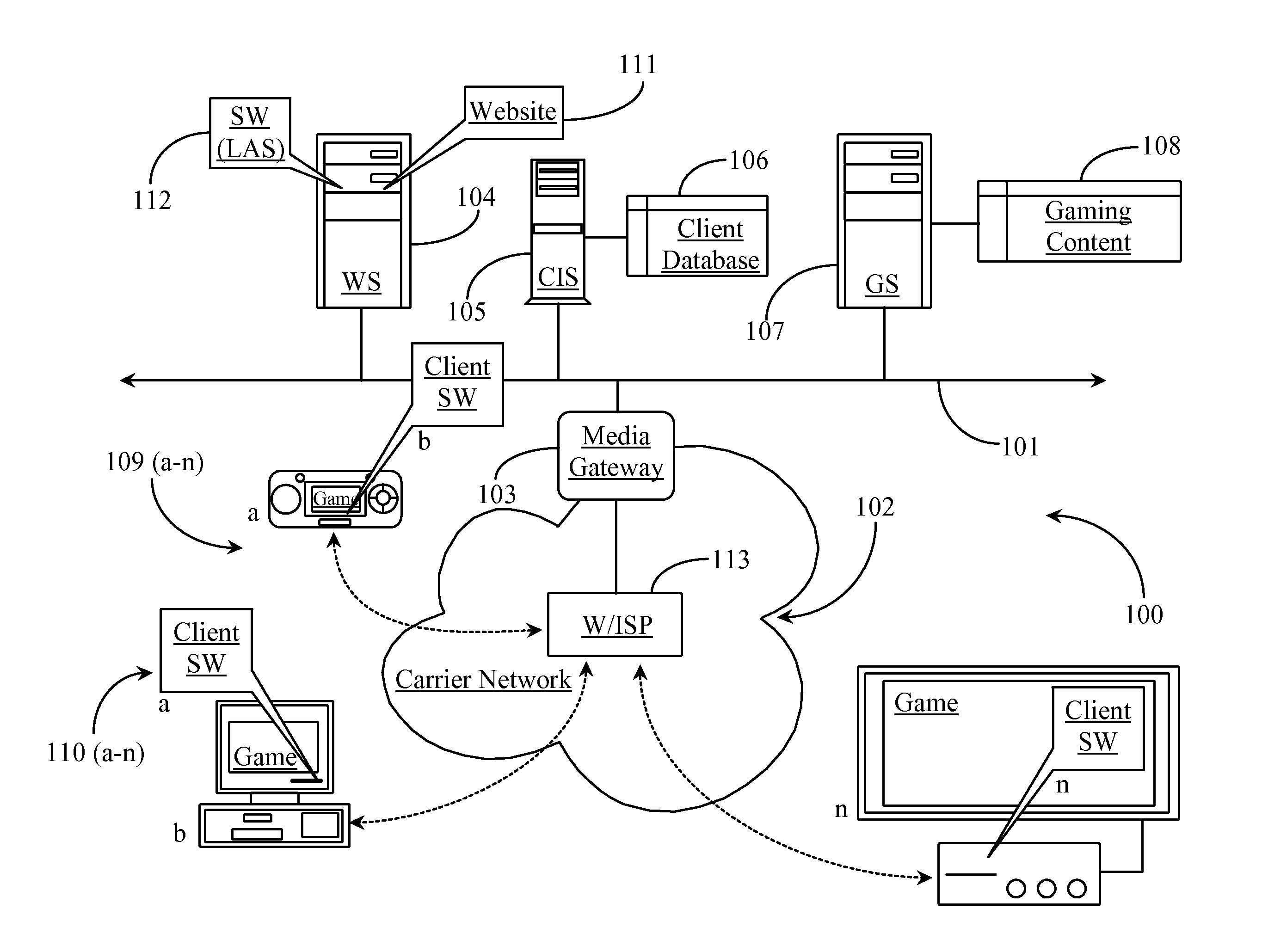
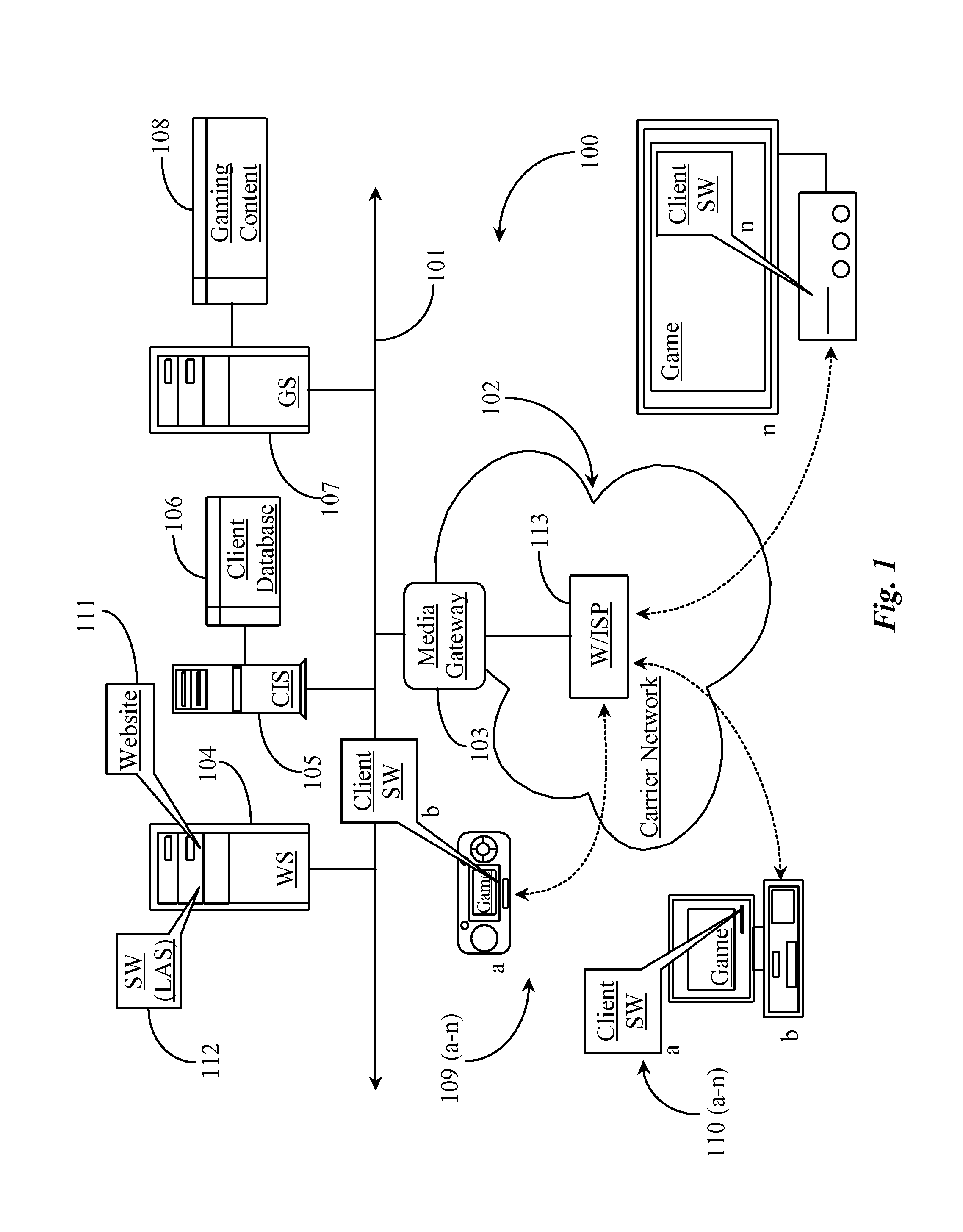
The invention comprises a graphic designation method for visually differentiating each number individually for a set of telephone numbers within a printed telephone directory. In a particular instance, the invention is applied in cases in which each said telephone number in the set has been established as a link element for linking to online digital resources associated with said telephone number. The invention also teaches a method for establishing a printed telephone number directory simultaneously as a directory for a telephone number directory service. The invention also teaches a method for displaying instructions for Internet addressing within a printed directory.
Owner:WHITFIELD HENRY
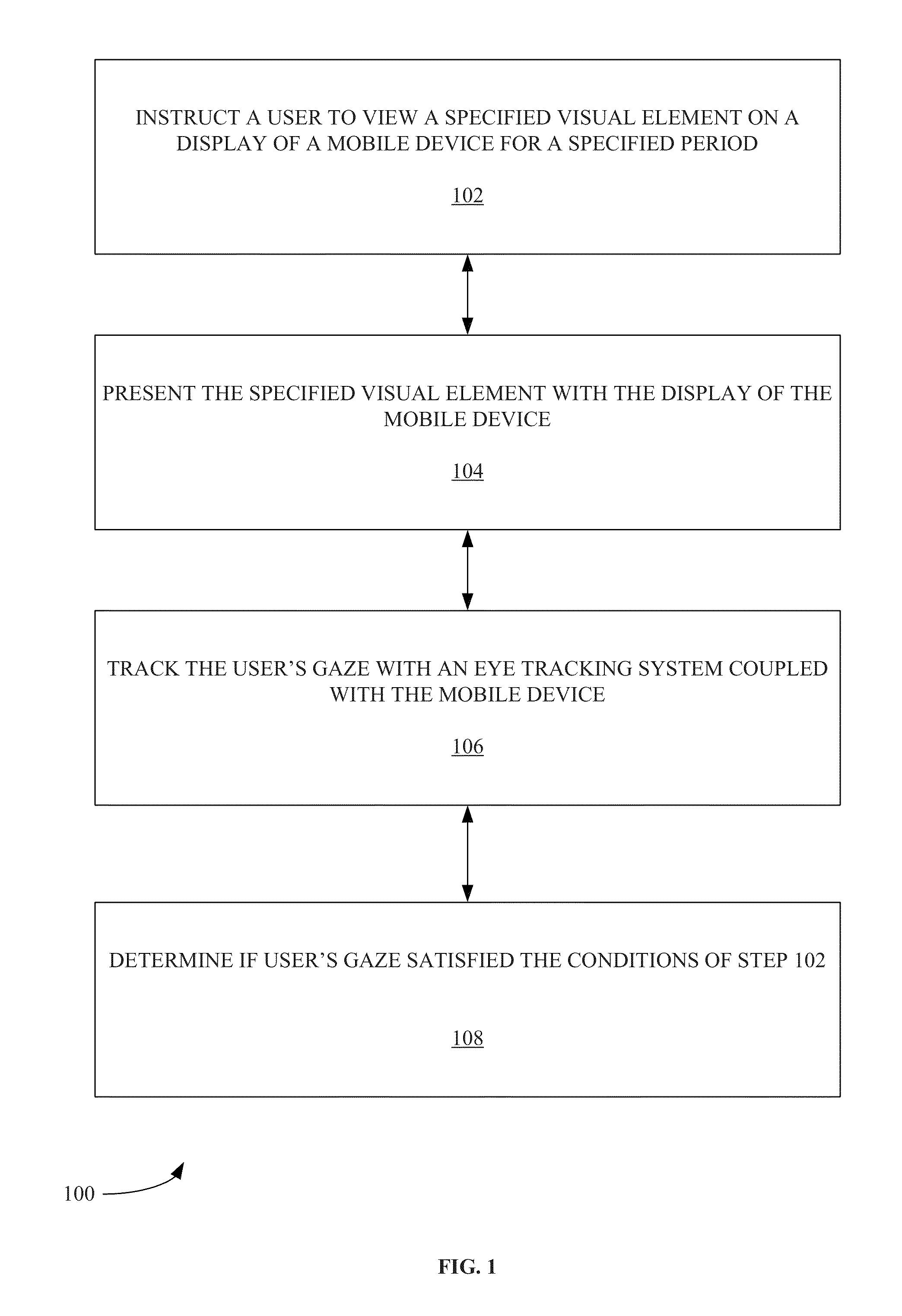
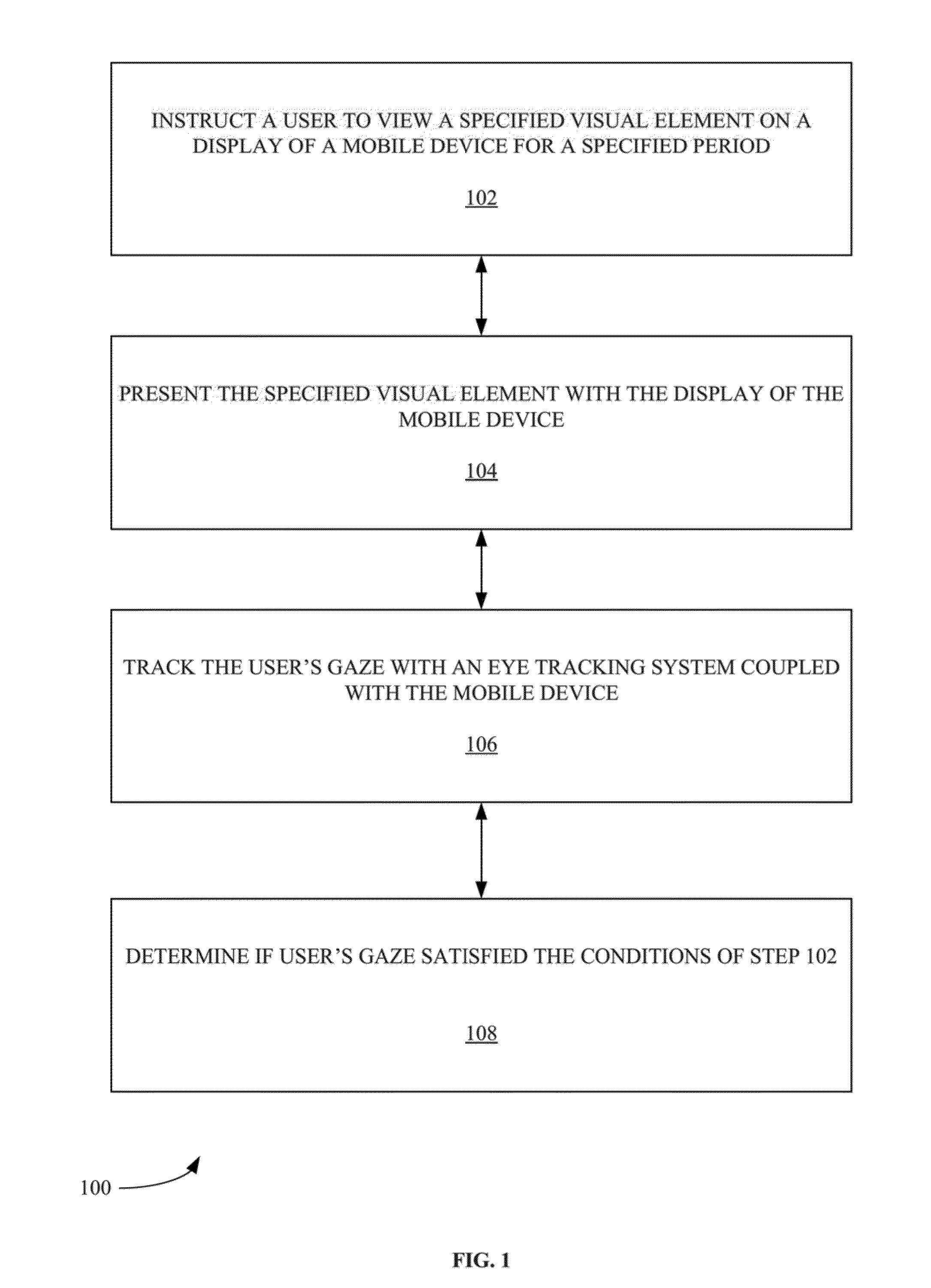
Resource transfer method and device, electronic equipment and storage medium
ActiveCN109615516AAddress the disconnectIntelligent processingFinancePayment architecturePaymentResource information
The invention discloses a resource transfer method and device, electronic equipment and a storage medium, and belongs to the technical field of block chains. The method comprises the following steps:receiving a first resource transfer request, wherein the first resource transfer request is used for requesting resource transfer associated with a target creditor's right certificate; verifying the first resource transfer request according to a target creditor's right voucher stored in the block chain system; and when the verification is passed, performing resource transfer associated with the target creditor's right certificate based on the first resource transfer request. According to the embodiment of the invention, the resource information on the chain can be obtained; the entity resourcetransfer request is verified; entity resource transfer is carried out when the verification is passed; according to the method and the system, the on-chain resource information is associated with theentity resource transfer, so that the transfer of the entity resources can be automatically realized, the disjunction phenomenon between the entity resource transfer and the on-chain digital resources in the payment process is effectively solved, the information such as the resource transfer does not need to be input, and the processing process of the resource transfer is intelligent and automatic.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Systems and methods for access control based on machine-learning
Example implementations are directed to a method of receiving information associated with an activity, analyze the information to identify a first pattern and a second pattern, generate a customized transition model for returning to the first pattern. In response to a detected trigger indicating a transition to the first pattern, the method assesses context factors to apply the customized transition to dynamically manage access to digital resources during the transition to the first pattern. In response to a determination that a transition to the first pattern satisfies a threshold, the method restores access to the digital resources.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Techniques for creating computer generated notes
ActiveUS20120004905A1Facilitate knowledge acquisition and utilizationNatural language analysisWeb data indexingRelational databaseInformation resource
Text is extracted from and information resource such as documents, emails, relational database tables and other digitized information sources. The extracted text is processed using a decomposition function to create. Nodes are a particular data structure that stores elemental units of information. The nodes can convey meaning because they relate a subject term or phrase to an attribute term or phrase. Removed from the node data structure, the node contents are or can become a text fragment which conveys meaning, i.e., a note. The notes generated from each digital resource are associated with the digital resource from which they are captured. The notes are then stored, organized and presented in several ways which facilitate knowledge acquisition and utilization by a user.
Owner:MAKE SENCE INC
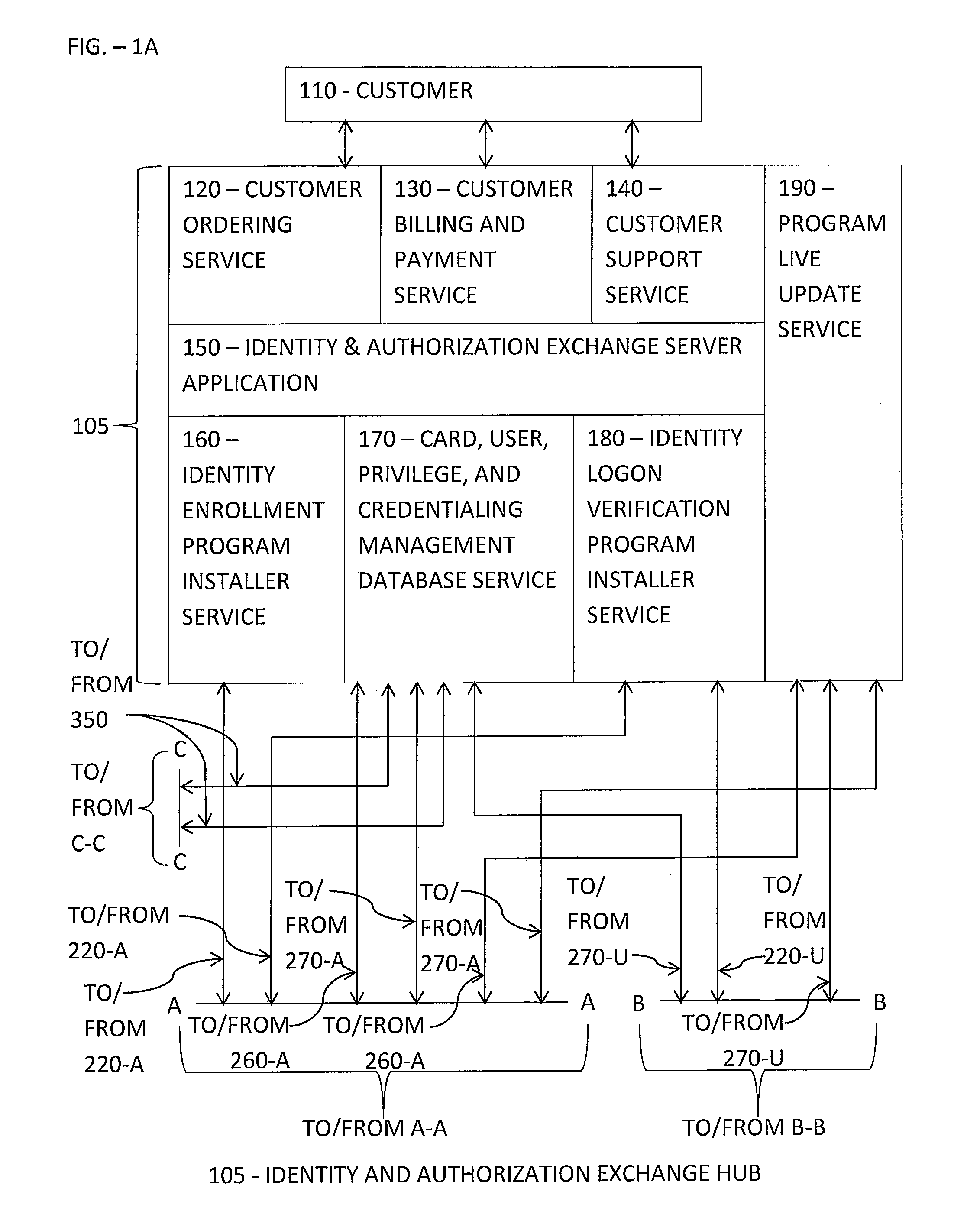
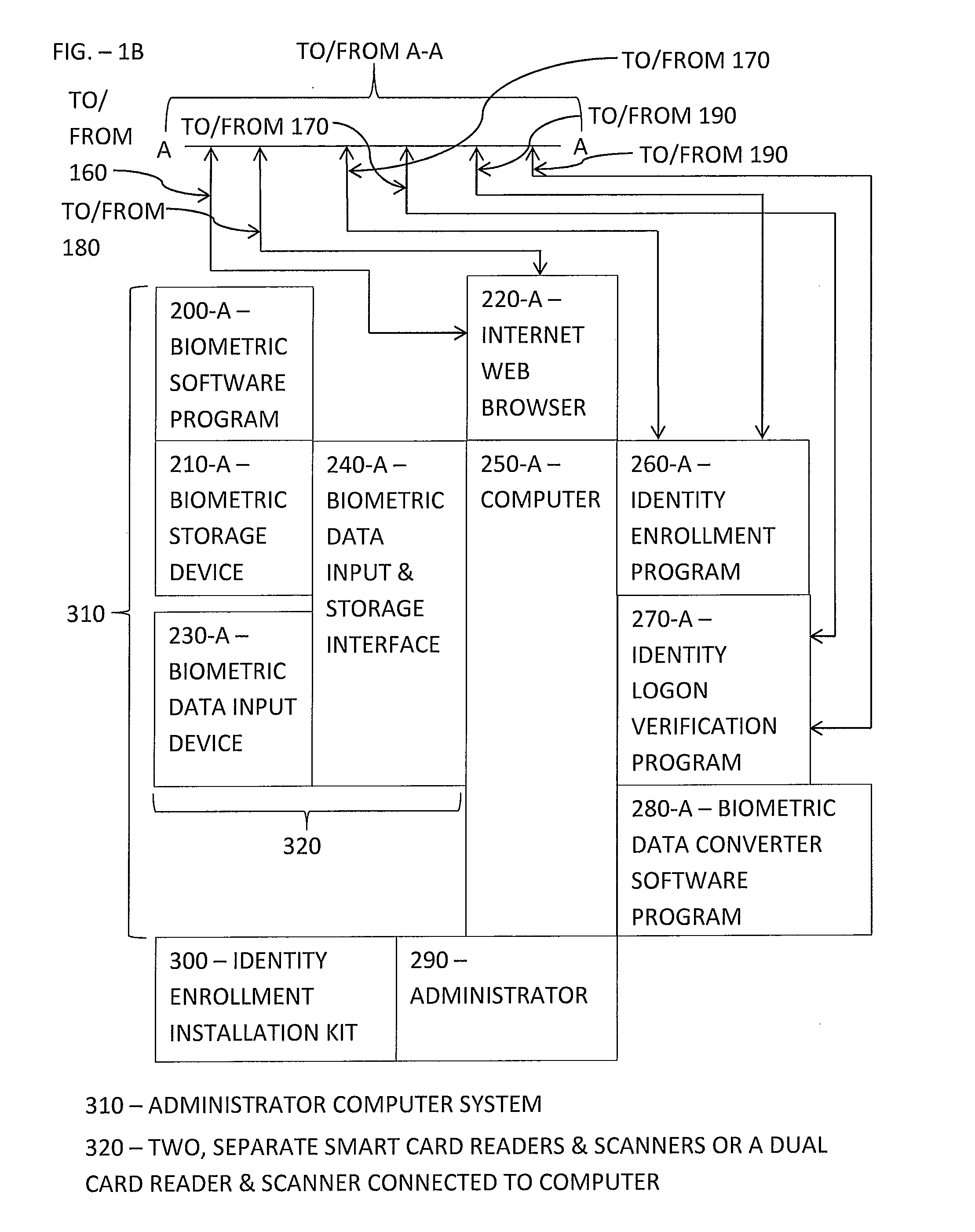
Automated Computer Biometric Identity Assurance
In a method of biometric identity assurance, biometric data based on a biometric modality is stored in a memory of a first computer. The biometric data is converted into a biometric template which is transferred from the first computer memory to a memory of a second computer. The second computer determines an encryption key based on a combination of the biometric template with a biometric-hash file of the user. Multiple credential files previously distributed among multiple remote computers are assembled into a single user credential file at the second computer. The first computer receives the encryption key and the user credential file from the second computer and accesses user credentials stored in the user credential file based on decryption of the user credential file using the encryption key. Via the thus accessed user credentials, the first computer uses or accesses one or more digital resources of the user.
Owner:BIOLUTION IDENTITY NETWORKS
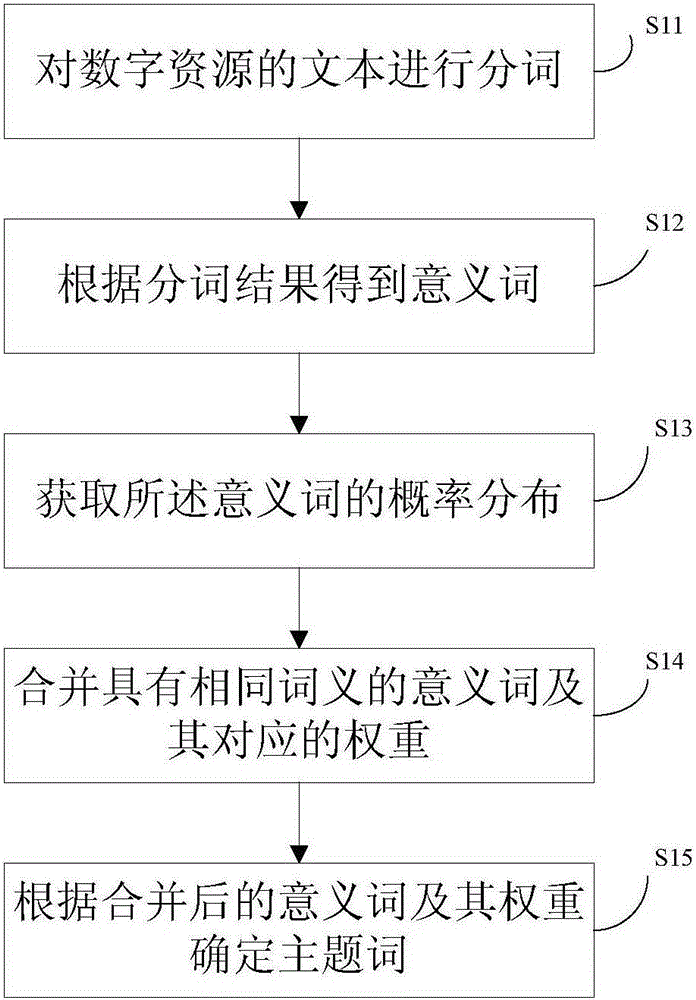
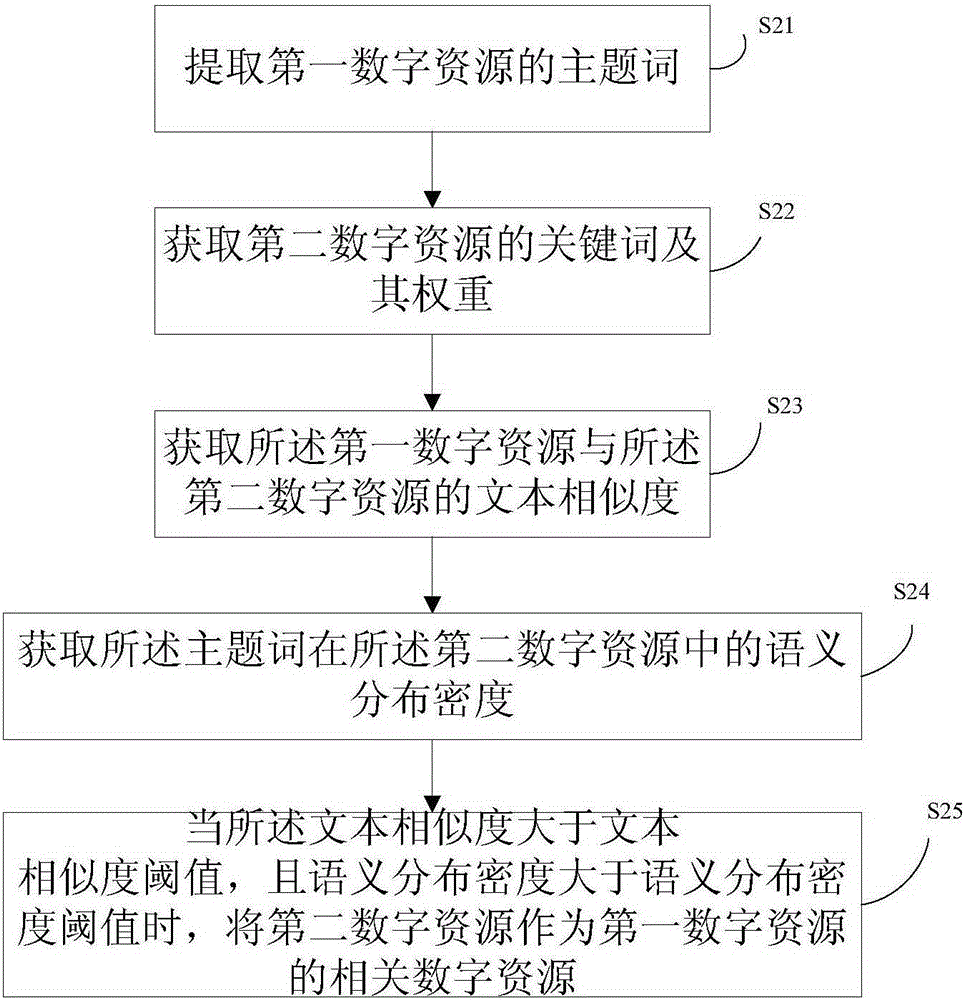
Theme word extraction method, and method and device for obtaining related digital resource by using same
ActiveCN105224521AAvoid interferenceImprove accuracySpecial data processing applicationsPersonalizationNamed-entity recognition
The invention provides a theme word extraction method, and a method and a device for obtaining related digital resources by using the same. The theme word extraction method comprises: firstly, performing word segmentation on a text of digital resource, and then obtaining content words according to a word segmentation result; aimed at each theme, obtaining probability distribution of the content words, the probability distribution comprising the content words and corresponding weight thereof; obtaining each meaning of the content words, combining the content words in the same meaning and combining the corresponding weight; and according to the combined content words and the weight thereof, determining the theme words. The scheme views from an angle of the meaning of a word, and the words in the same meaning are combined, so as to prevent interference of polysemic words and synonyms on extraction of the theme words in the prior art, and improve accuracy of extraction of the theme words. The method eliminates dependence on selection of feature words and identity of named entities in the prior art, weakens interference of polysemic words and synonyms on extraction of the theme words, and a user oriented customized special subject organization and generation thereof are realized.
Owner:NEW FOUNDER HLDG DEV LLC +2
Attribute-based encryption access control system of cloud storage digit library, and access control method thereof
ActiveCN105681355AAchieve integrationSolve the repeatabilityTransmissionStorage securitySecure authentication
The invention discloses an attribute-based encryption access control system of a cloud storage digit library, and an access control method thereof. The access control system comprises five entities: an authority center, a key distribution center, a cloud server, an uploading center, and an access user. The access control method comprise the steps of: system initialization, uploading center encryption and accessing a digit library. In the access control system, the uploading center uploads book data in categories according to corresponding attributes of books, so that the system realizes data integration, and effectively solves the problems of digital resource repeated construction and low sharing degree; in the access control method, the attribute-based encryption technology is introduced, which guarantees data storage security on one hand, and realizes user access control on the other hand. Accordingly, the method realizes user safety certificate and fine grit access control.
Owner:XIDIAN UNIV
System and method for community centric resource sharing based on a publishing subscription model
InactiveUS20100299611A1Receives changeKept up-to-dateInput/output for user-computer interactionMultiple digital computer combinationsWeb serviceShared resource
The invention provides a Web service which enables a publisher to share his digital resources such as an address card or a calendar with a number of subscribers based on different sharing relationships. The Web service includes a host-based interface called “My Community”, for example, with which the publisher manages the share-relationships with his community members. The community members are organized into different groups. Each group includes a number of community members who have a common sharing relationship with the publisher with respect to one or more views of the shared resources. A resource may have multiple views. Each of the views has Metadata describing sharing-styles, as well as version, creation date, size, and the like. Each sharing style corresponds to a specific sharing relationship between a community member and the publisher.
Owner:SERIES 42 OF ALLIED SECURITY TRUST I
Vehicle state determination integrity
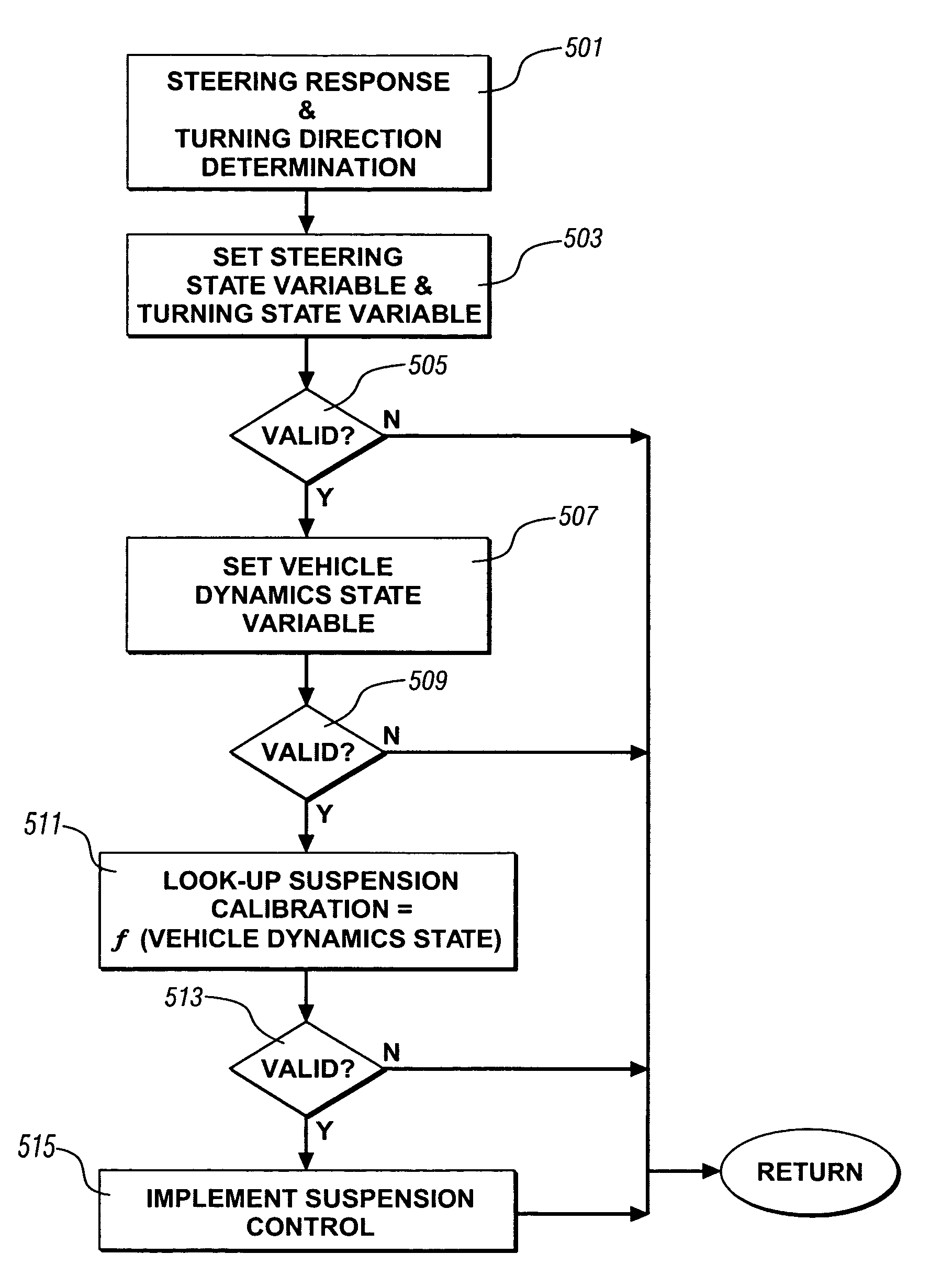
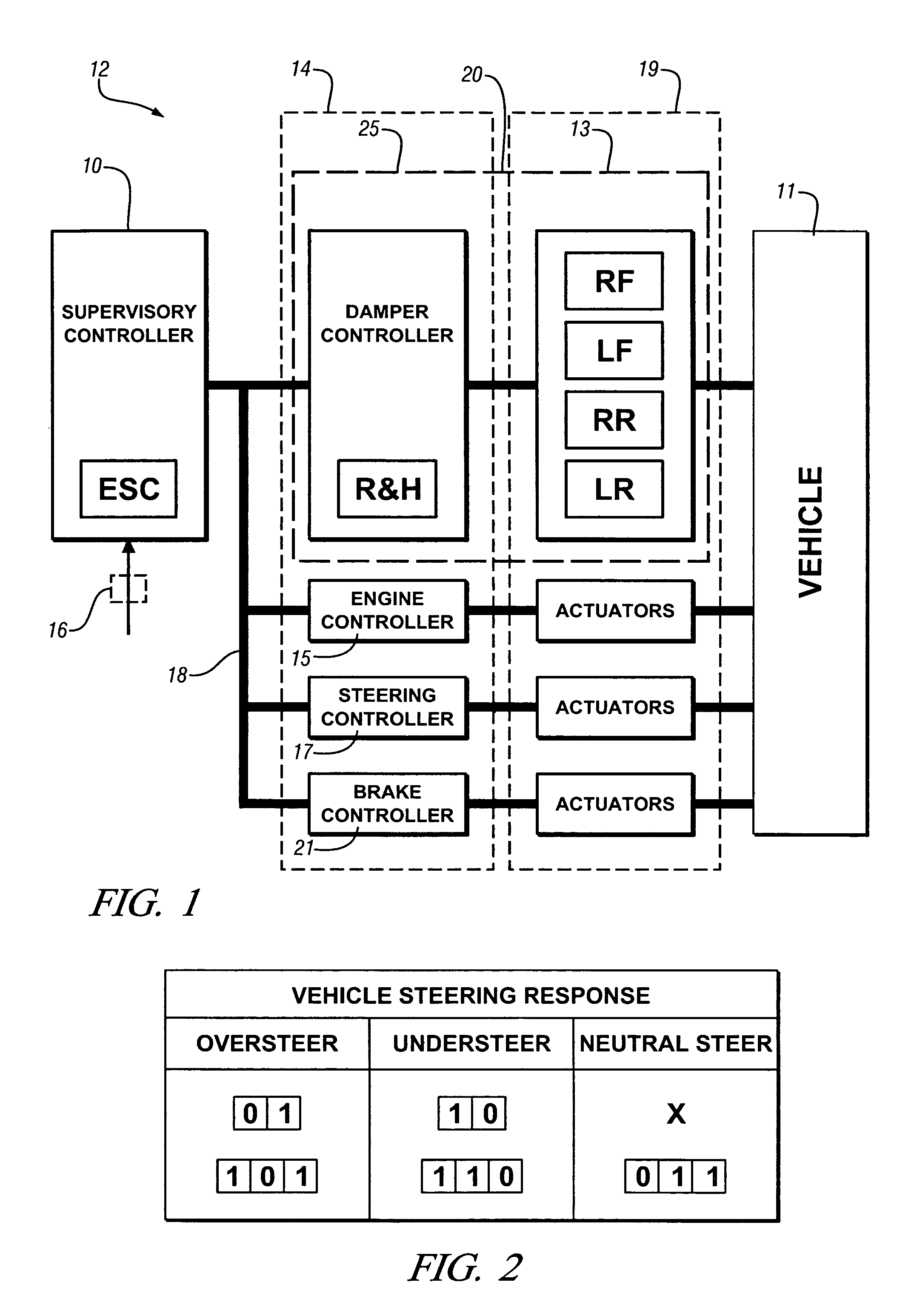
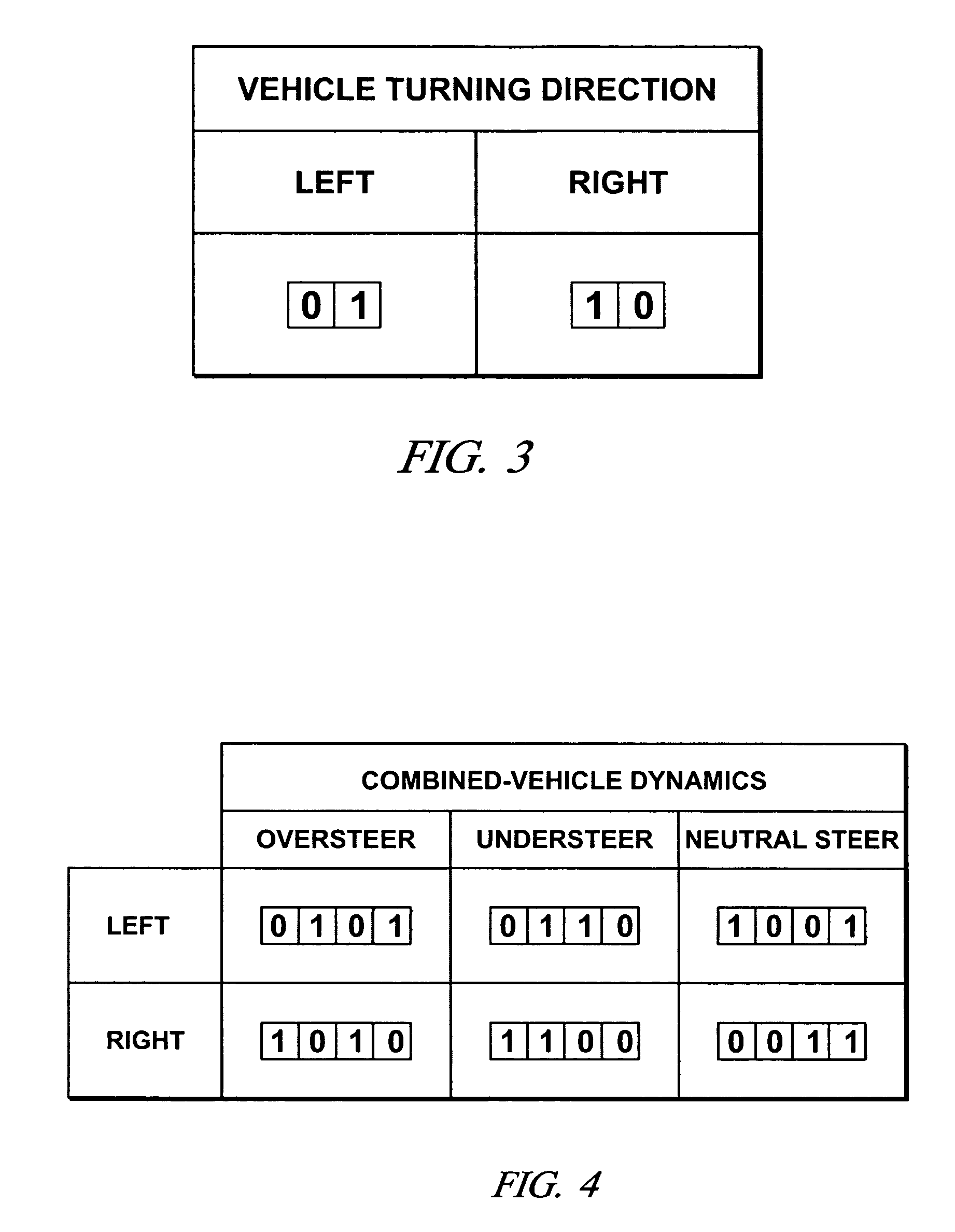
InactiveUS7747359B2Wheel based transmissionFrictional rollers based transmissionSemi activeVehicle dynamics
A vehicle includes a semi-active suspension including suspension dampers controllably adjustable in accordance with electronic stability control commands and ride and handling commands. Vehicle steering response states, turning direction states and vehicle dynamics states are binary coded in respective state variables and suspension control calibrations are binary coded in calibration words. Integrity and security of state variables and calibration words are ensured in efficient binary digit resource allocation schemes.
Owner:GM GLOBAL TECH OPERATIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com