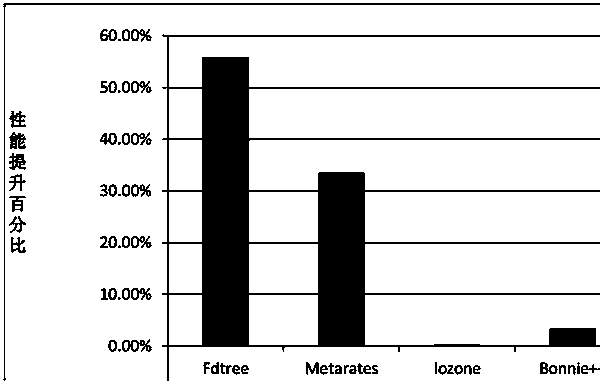
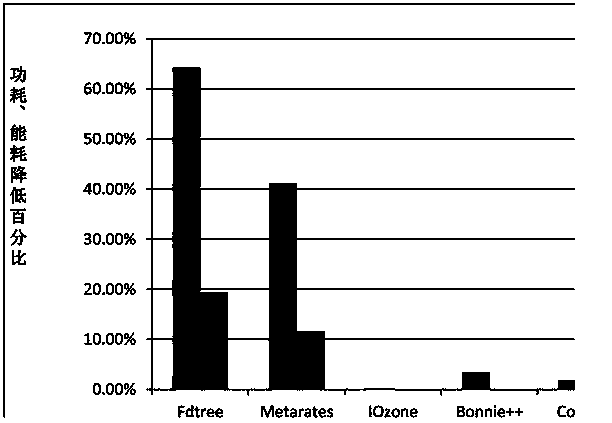
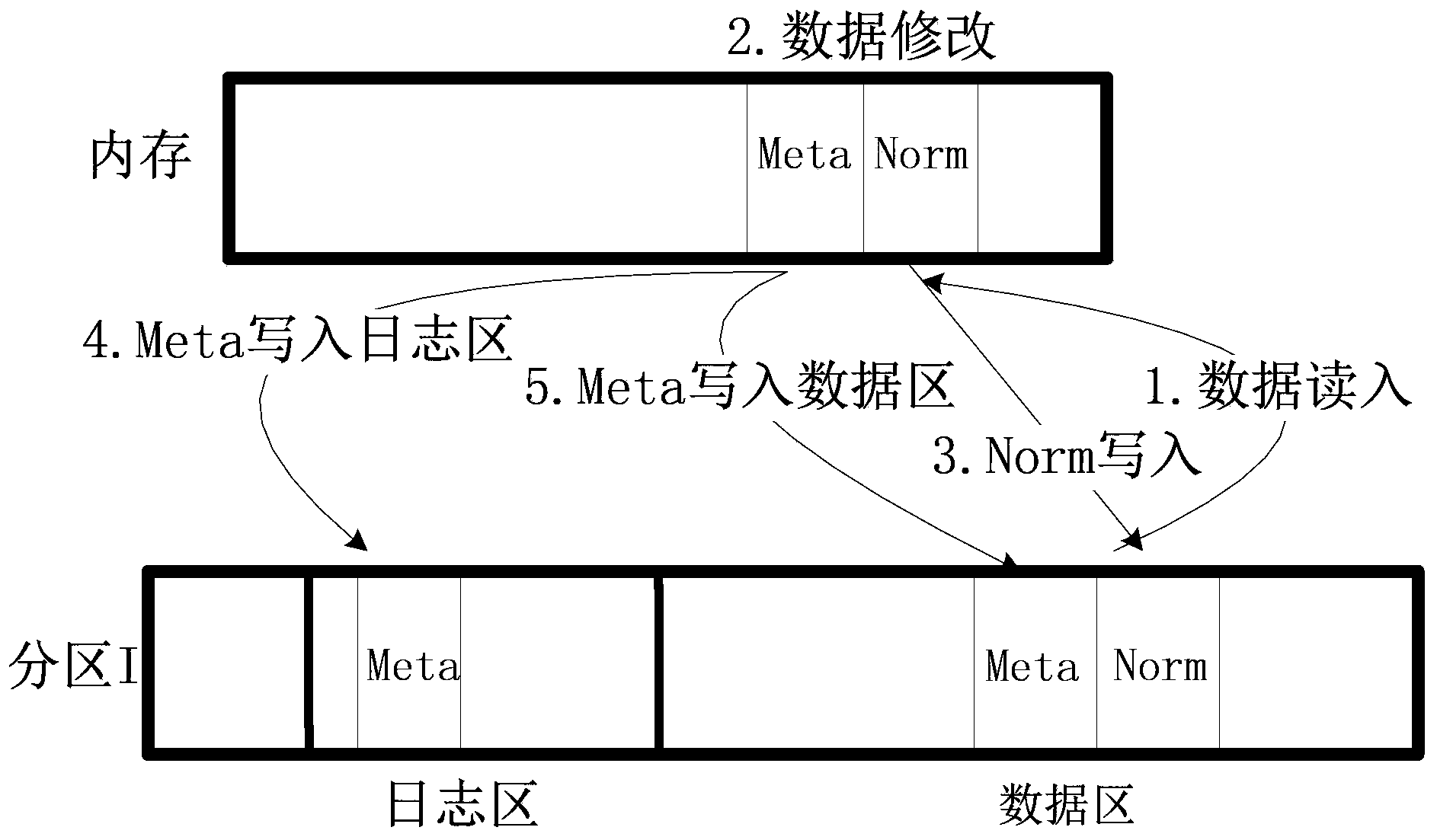
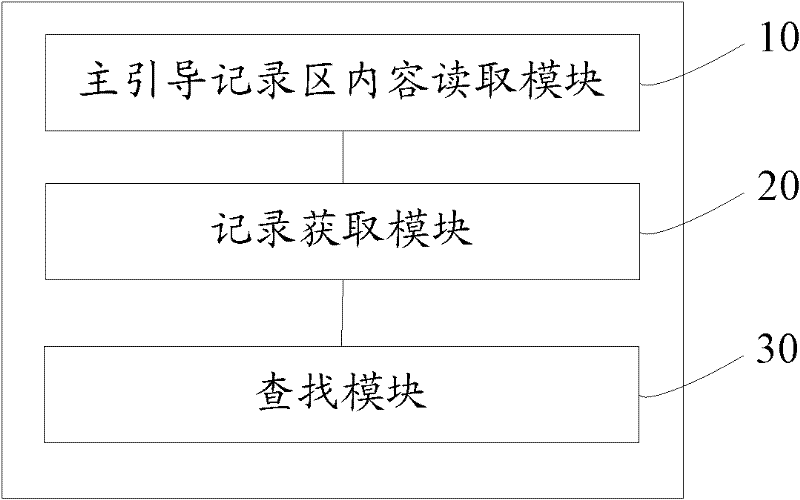
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
115 results about "Disk partitioning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Disk partitioning or disk slicing is the creation of one or more regions on secondary storage, so that each region can be managed separately. These regions are called partitions. It is typically the first step of preparing a newly installed disk, before any file system is created. The disk stores the information about the partitions' locations and sizes in an area known as the partition table that the operating system reads before any other part of the disk. Each partition then appears to the operating system as a distinct "logical" disk that uses part of the actual disk. System administrators use a program called a partition editor to create, resize, delete, and manipulate the partitions.. Partitioning allows the use of different filesystems to be installed for different kinds of files. Separating user data from system data can prevent the system partition from becoming full and rendering the system unusable. Partitioning can also make backing up easier. A disadvantage is that it can be difficult to properly size partitions resulting in having one partition with much free space and another nearly totally allocated.
Method and system for protecting data associated with a replaced image file during a re-provisioning event
InactiveUS20050182796A1Input/output to record carriersSpecial data processing applicationsOperational systemNetwork operating system
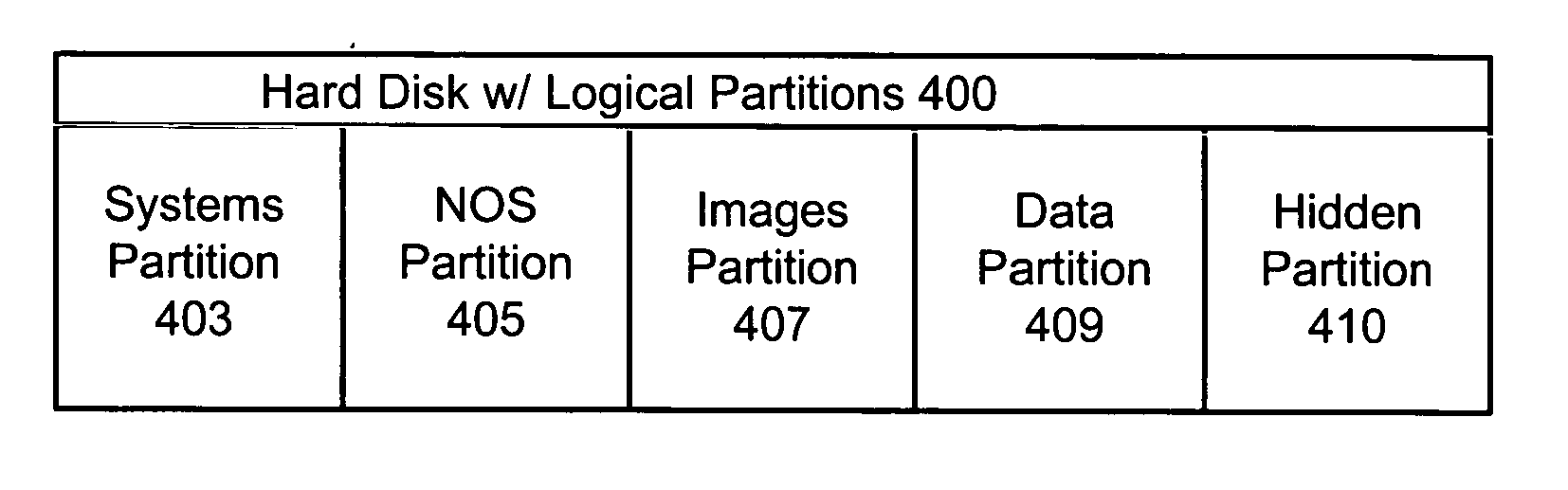
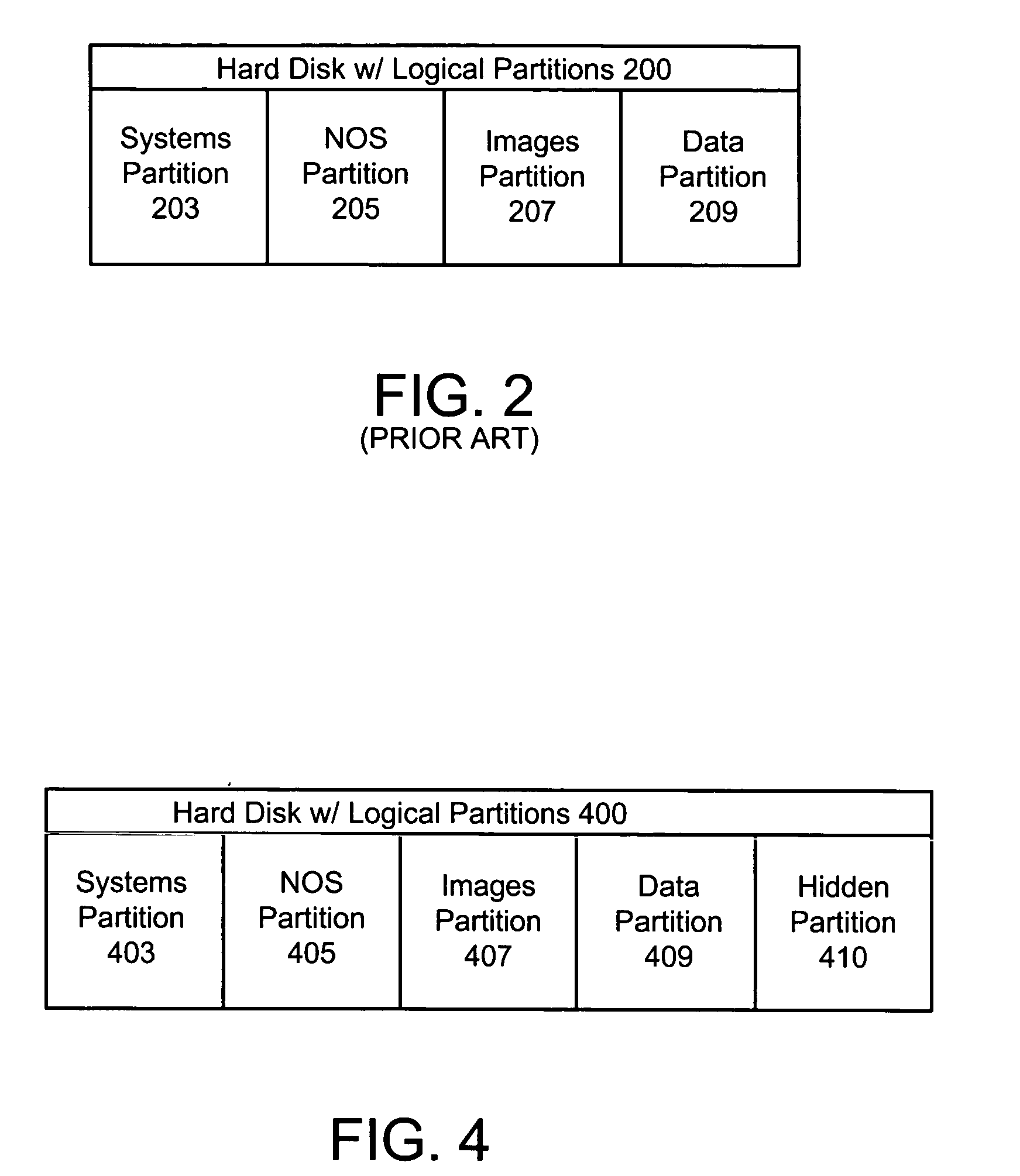
The present invention discloses a method and hard disk configuration for protecting data associated with a first image file in an appliance server after the first image file has been replaced with a second image file. In a first aspect, the method of the invention includes partitioning a hard disk of the appliance server into a plurality of partitions, wherein at least one of the plurality of partitions is a hidden partition and copying the data associated with the first image file to the hidden partition, wherein the data in the hidden partition is invisible to a network operating system during normal server operation. In another aspect, the hard disk of the invention includes a first partition for storing an image file, wherein the first partition stores one image file at one time, a second partition for storing data associated with the image file, wherein the second partition is visible to a network operating system in the first partition, a hidden partition, wherein the hidden partition is invisible to the network operating system in the first partition, means for replacing a first image file in the first partition with a second image file, and means for copying the data associated with the first image file from the second partition to the hidden partition when the first image file in the first partition is replaced with the second image file.
Owner:IBM CORP
Systems and methods for controlling access to data on a computer with a secure boot process
ActiveUS20060161790A1Improve efficiencyAvoid accessVolume/mass flow measurementUnauthorized memory use protectionProcess systemsDisk partitioning
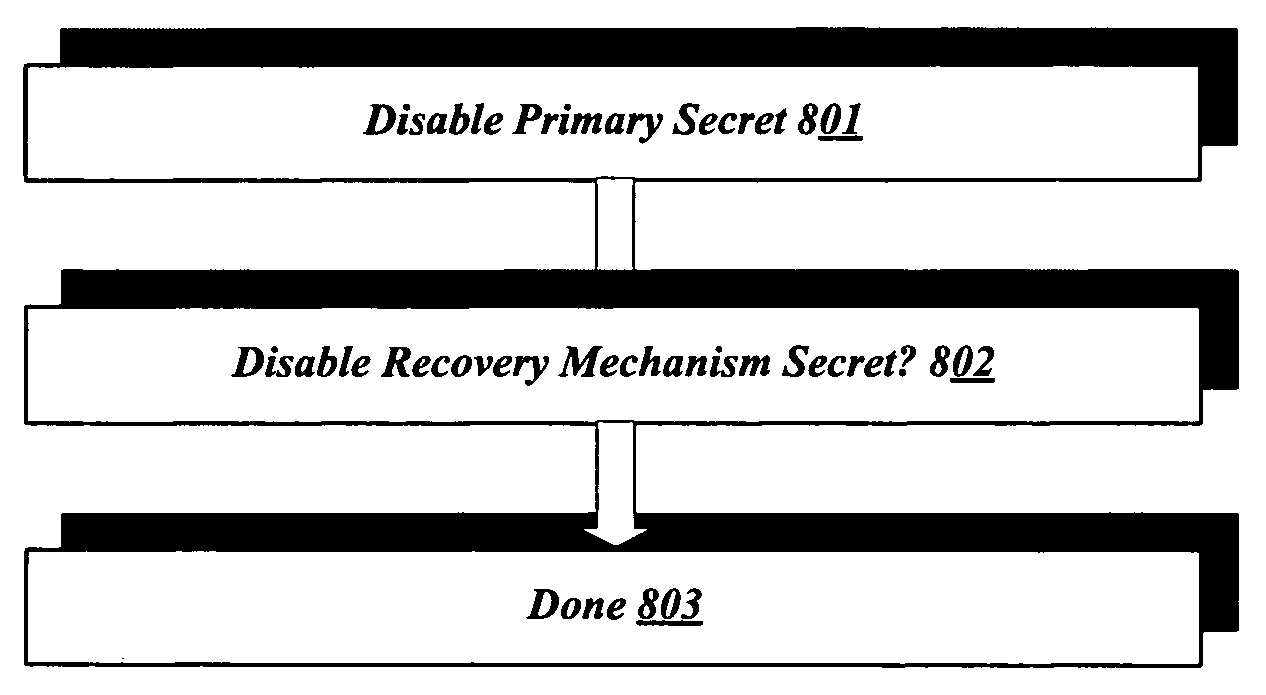
Systems and methods for controlling access to data on a computer with a secure boot process can provide a highly efficient mechanism for preventing future access to encrypted digital resources. This may be advantageous in a range of scenarios, for example where a computer is sold and assurance is desired that no stray private data remains on the hard disk. Data resources, for example all data associated with one or more particular hard disk partitions, may be encrypted. The decryption key may be available through a secure boot process. By erasing, altering, or otherwise disabling a secret, such as a decryption key or a process that obtains a decryption key, the data formerly accessible using such secret becomes inaccessible.
Owner:MICROSOFT TECH LICENSING LLC
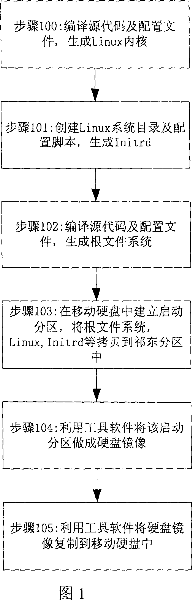
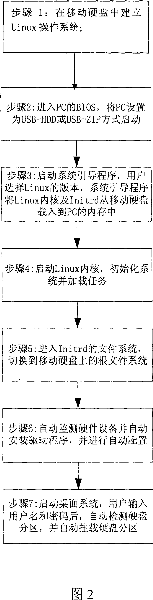
Method for implementing the start of Linux operation system in mobile hard disk
The invention relates to a method for realizing starting of Linux operation system on a hard drive when the hard drive is inserted into the USB interface of PC, which is carried out by the steps of: building up a Linux operation system in a hard drive, entering the BIOS of PC, setting the start mode as USB-HDD or USB-ZIP, starting the system bootstrap routine, selecting the Linux edition, and downloading the Linux internal kernel and Initrd to the internal memory of PC from mobile hard drive, starting the internal kernel of Linux, initializing the system and loading task, entering the file system of Initrd, switching to the root file system of the mobile hard drive, detecting the hardware equipment and installing the drive program automatically and implementing the automatic configuration, starting the desk system, and after the user enters the user name and cipher, detecting and mounting the hard disk partition.
Owner:NANJING UNIV +1
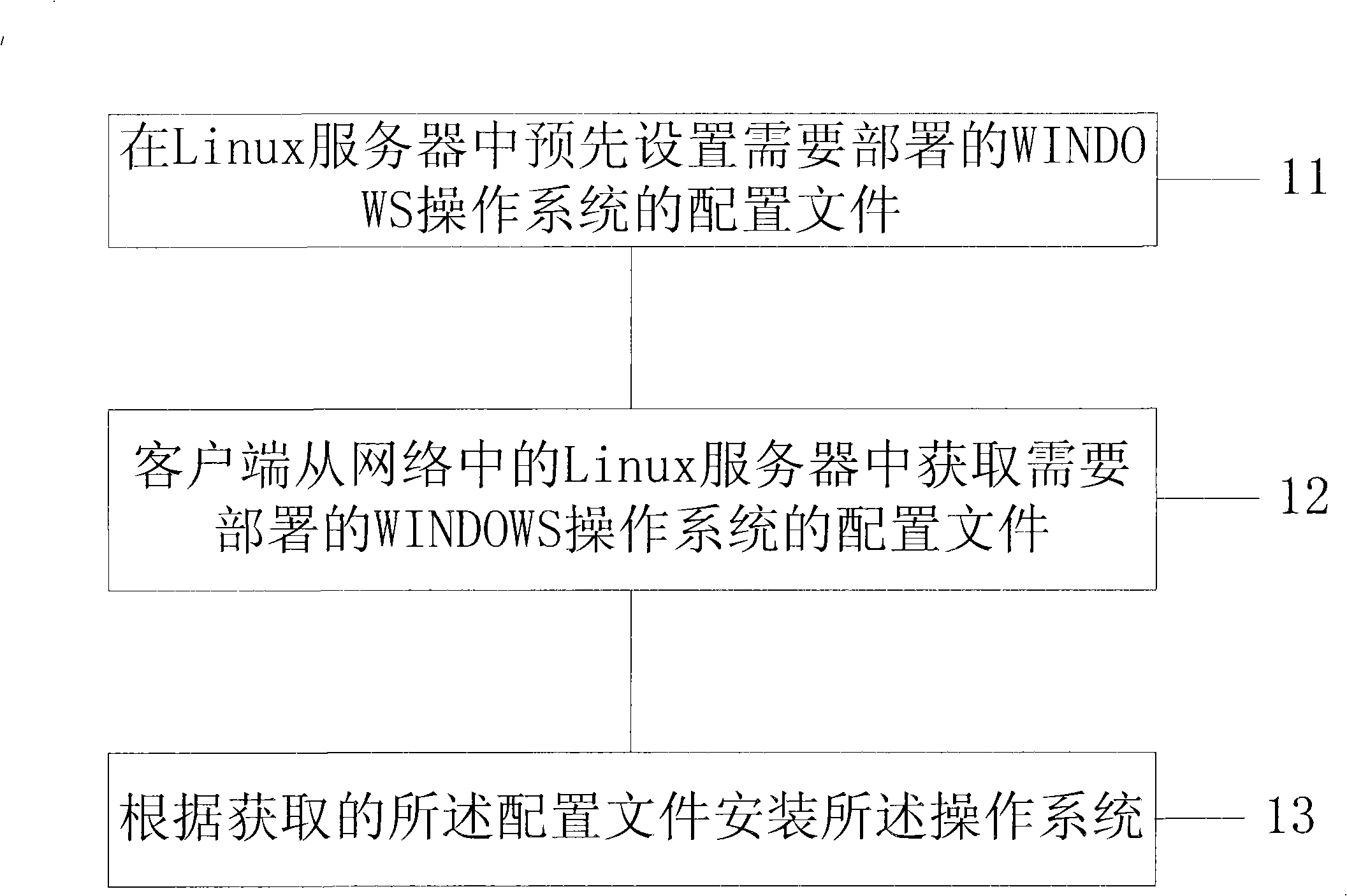
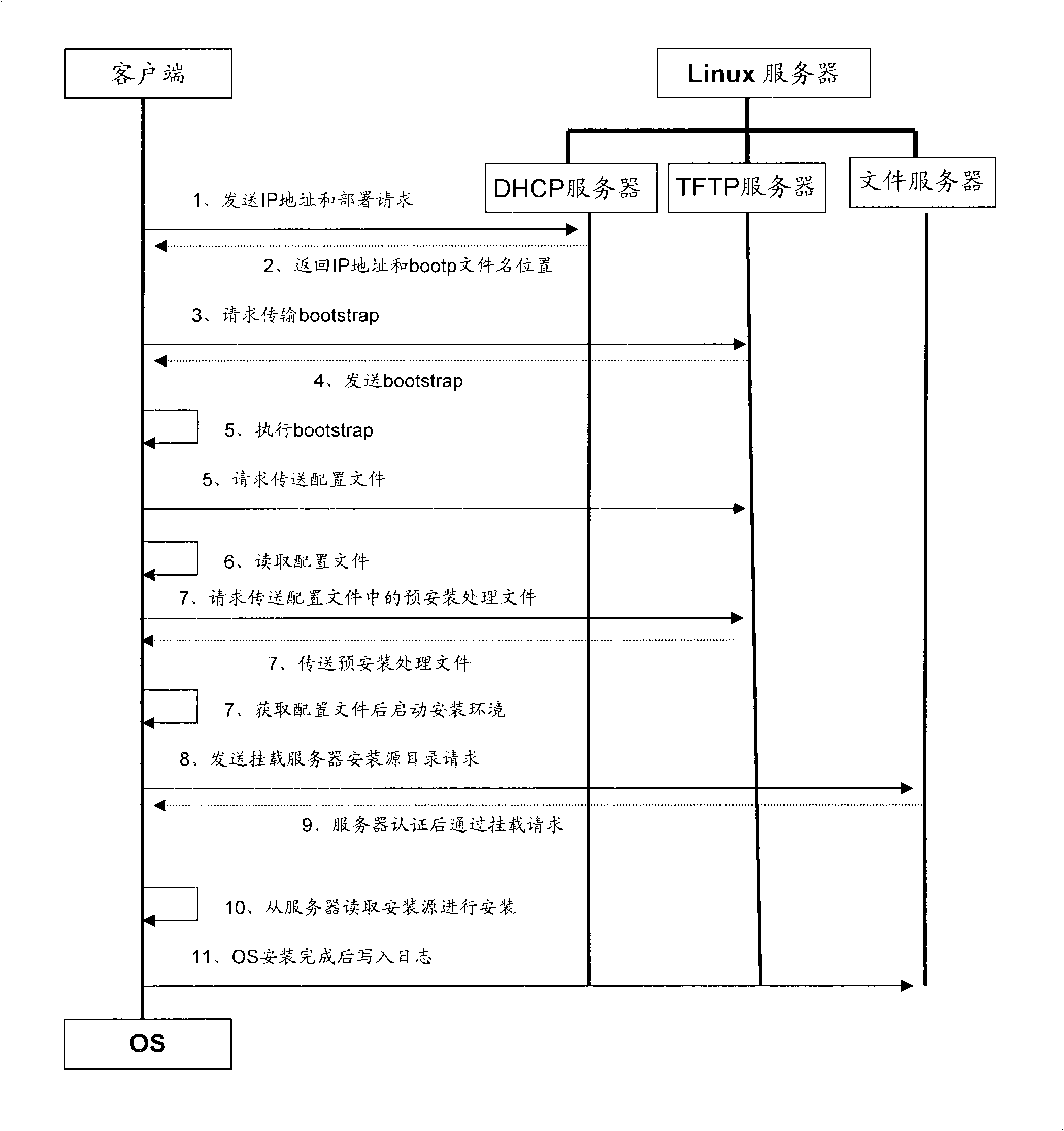
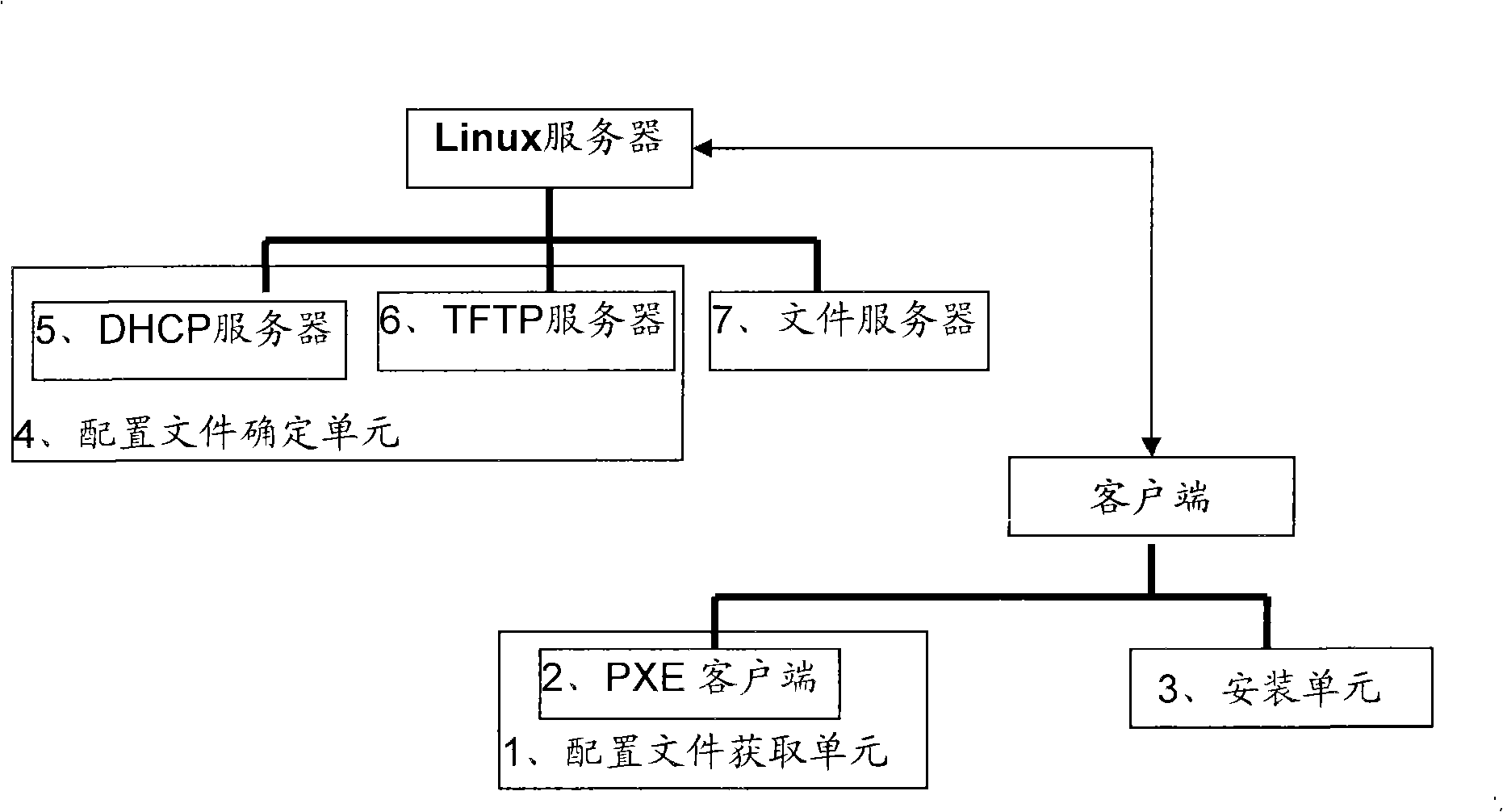
Method, device and system for allocating WINDOWS enterprise edition operating system
InactiveCN101344852AImprove individual needsRealize differential customizationProgram loading/initiatingTransmissionOperational systemDisk partitioning
The invention provides a method, a device and a system for deploying WINDOWS enterprise operation systems. The method comprises: a client acquires configuration files of the WINDOWS operation system to be deployed by the client from a Linux server in the network, wherein, the configuration files contain installation information of the operation system to be deployed by the client so that the client can install the operation system according to the installation information in the configuration files. One installation server of the embodiment of the invention can support concurrent installation of a plurality of Windows systems of different editions; therefore, the invention can greatly improve the support to individual requirements of users on the operation systems, maximize installation deployment of compatible service operation platforms and realize different customization of hard disc division.
Owner:HUAWEI TECH CO LTD
Plug and play cluster deployment
InactiveUS20070041386A1Digital computer detailsData switching by path configurationComputer hardwareBroadcasting
In a method of configuring a plurality of computer systems coupled through a network, each computer system comprises a bootable hard disk partition and the method comprises the steps of: automatically assigning an IP node address to each computer system coupled with the network; establishing a master node and creating a re-deployment image partition; synchronizing all computer systems which should receive the re-deployment image partition; broadcasting the re-deployment image partition from the master node; receiving the re-deployment image partition at each computer system; re-booting each computer system from their respective hard disk partition.
Owner:DELL PROD LP
Method and device for encrypting hard disk partition
InactiveCN102508791ARealize dynamic reading and writing encryption and decryptionGuaranteed real-timeKey distribution for secure communicationUnauthorized memory use protectionThird partyOperational system
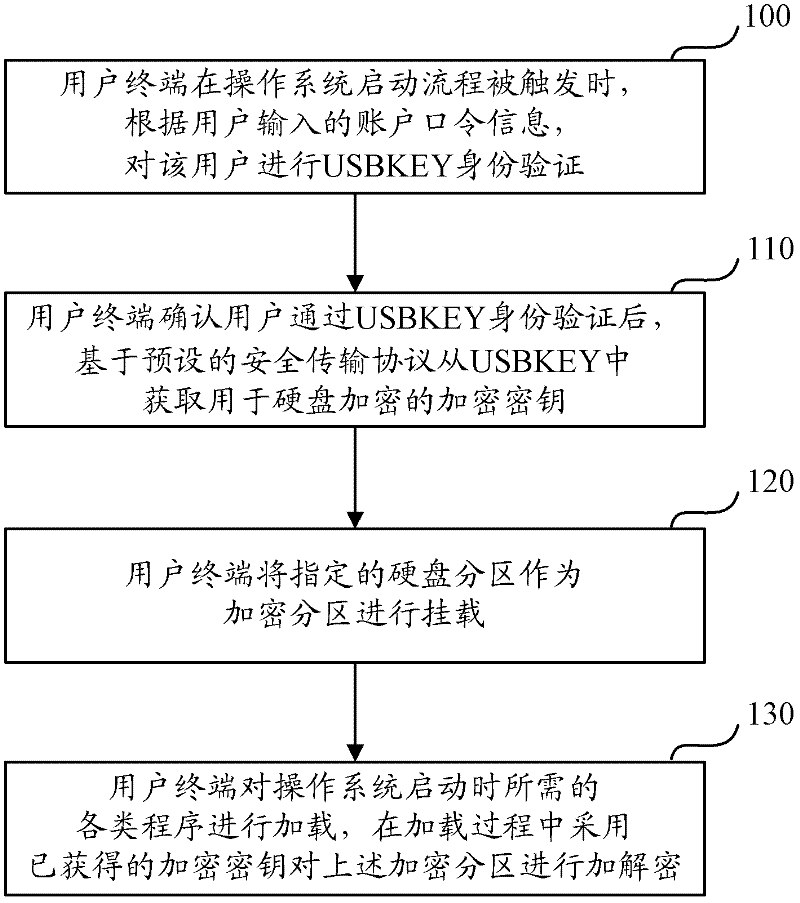
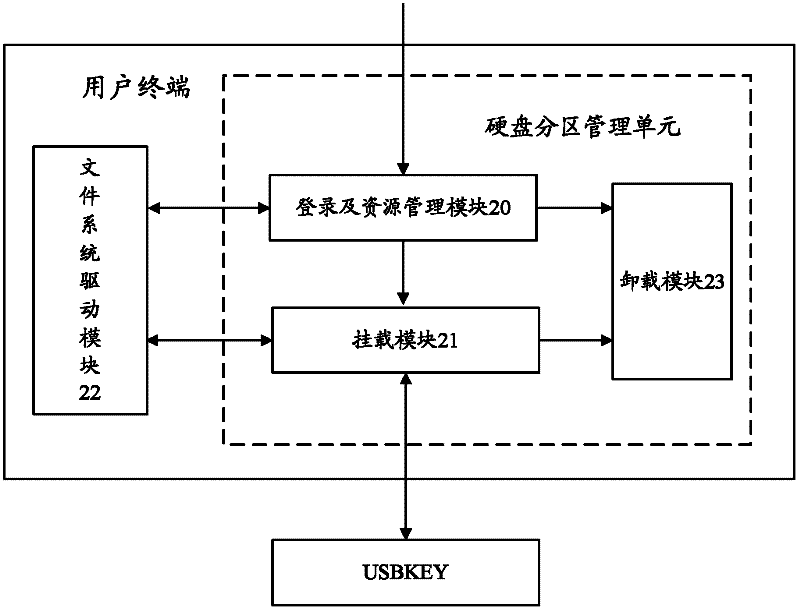
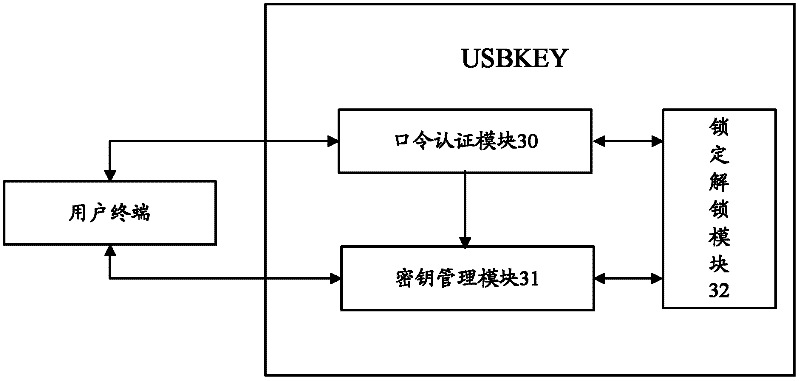
The invention relates to the field of computers and discloses a method and device for encrypting a hard disk partition. The method and the device are used for preventing data leakage of a hard disk and increasing data safety of the hard disk. The method comprises the following steps: when a starting process of an operation system on a user terminal is triggered, after being subjected to USBKEY authentication, an encryption key can be guided into the operation system to be stored temporarily according to a pre-set safety transmission mechanism; after obtaining the encryption key, the user terminal takes an appointed hard disk partition as an encryption partition to mount; and read-write operation of the encryption partition is encrypted and decrypted according to the obtained encryption key, therefore, data dynamic read-write encryption and decryption are realized in a driving layer; by means of driving of an independent file system, hook hijacking of the original file system of the operation system by a third party is stopped, so that the data safety is effectively increased; furthermore, mounting of the encryption partition and seamless integration of the starting process of the operation system are realized, and the execution efficiency of a hard disk encryption process is increased.
Owner:LIAOYUAN HUANYU JIAXUN COMM TECH
Systems and methods for controlling access to data on a computer with a secure boot process
ActiveUS7565553B2Improve efficiencyAvoid accessVolume/mass flow measurementUnauthorized memory use protectionProcess systemsDisk partitioning
Systems and methods for controlling access to data on a computer with a secure boot process can provide a highly efficient mechanism for preventing future access to encrypted digital resources. This may be advantageous in a range of scenarios, for example where a computer is sold and assurance is desired that no stray private data remains on the hard disk. Data resources, for example all data associated with one or more particular hard disk partitions, may be encrypted. The decryption key may be available through a secure boot process. By erasing, altering, or otherwise disabling a secret, such as a decryption key or a process that obtains a decryption key, the data formerly accessible using such secret becomes inaccessible.
Owner:MICROSOFT TECH LICENSING LLC
Internal storage log file system and achieving method thereof
ActiveCN103514260AEnsure consistencyReduce power consumptionInput/output to record carriersPower supply for data processingFile systemAccess time
The invention discloses an internal storage log file system based on an EXT 4 file system. The internal storage log file system is characterized by comprising an internal storage log area establishing module, a log file refreshing module and a log area write-back module, wherein the internal storage log area establishing module is used for establishing an internal storage log area for mapping an internal storage log area of a hard disk partition EXT4 file system log area in the internal storage. The log file refreshing module is used for reading a log area file in a hard disk partition into the internal storage log area when the hard disk partition is mounted, and the log file refreshing module is used for writing the internal storage log area as the log area file into a hard disk when the hard disk partition is dismounted. The log area write-back module is used for writing the internal storage log area for mapping a hard disk partition EXT4 file system into the other hard disk partition log area after the hard disk partition is dismounted. The power consumption of the hard disk is reduced by reducing the access times of the hard disk, and meanwhile due to the fact that the speed of the internal storage is far higher than that of the hard disk, the performance of the whole can be improved through the internal storage log system.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
File or folder search method and device
InactiveCN102289451AAvoid occupyingQuick responseFile access structuresSpecial data processing applicationsComputer resourcesInternal memory
A method for finding files or folders, including the following steps: acquiring a hard disk partition format; acquiring the recording addresses of all the file or folder attributes in the hard disk according to the hard disk partition format, and reading all the file or folder attributes into an internal memory according to the recording addresses of the file or folder attributes; and traversing and finding all or part of the files or folders in all the file or folder attributes read into the internal memory.Also provided is a device for finding files or folders for realizing the method above.The method and device for finding files or folders in the present invention can find files or folders rapidly, and reduce occupied computer resources.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
Data multi-duplicate hybrid storage method and system
ActiveCN103440301AImprove processing efficiencyReduce data reliabilityTransmissionRedundant operation error correctionOriginal dataDependability
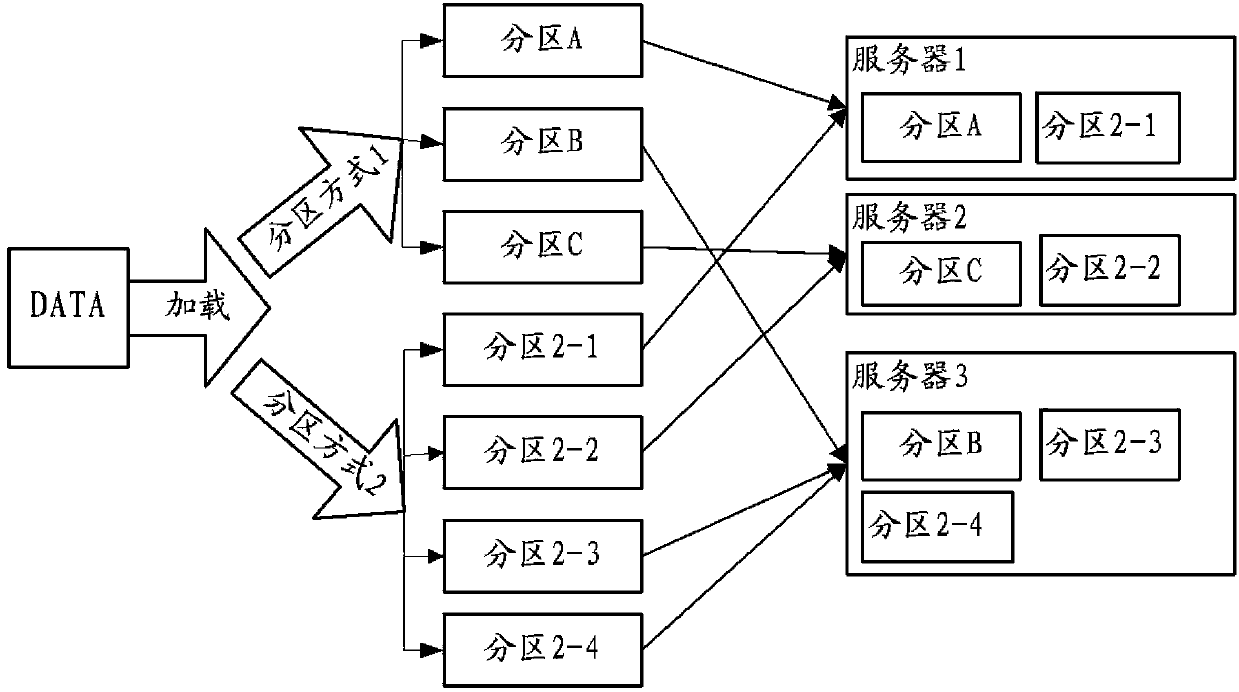
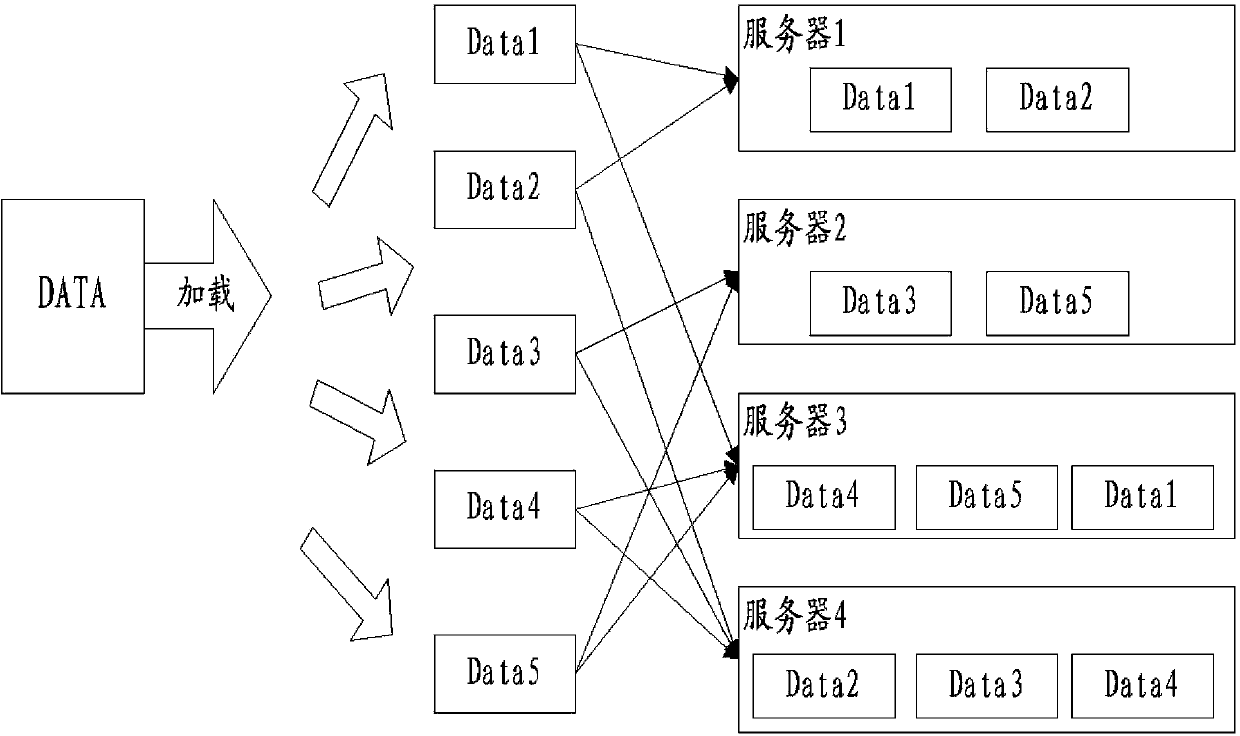
The invention provides a data multi-duplicate hybrid storage method and system. In a data loading stage, original data are partitioned repeatedly, different partitioning modes are adopted for each time of partitioning, and partition data obtained through each time of partitioning are stored in a plurality of servers. The invention further provides a data processing method mainly for large-scale data on-line analysis. According to the data multi-duplicate hybrid storage method and system, on the premises that disk space occupied by data storage is not increased and data reliability is not reduced, the variety of data partitioning is increased, therefore, data processing of the same type of more scenes conducted in groups can be subjected to parallel execution according to partitions, the expenditure for data query and processing under more scenes is reduced, and the problem that in the prior art, a single partitioning mode of duplicates causes low efficiency of some scenes under which data processing is conducted in groups.
Owner:SUGON INFORMATION IND
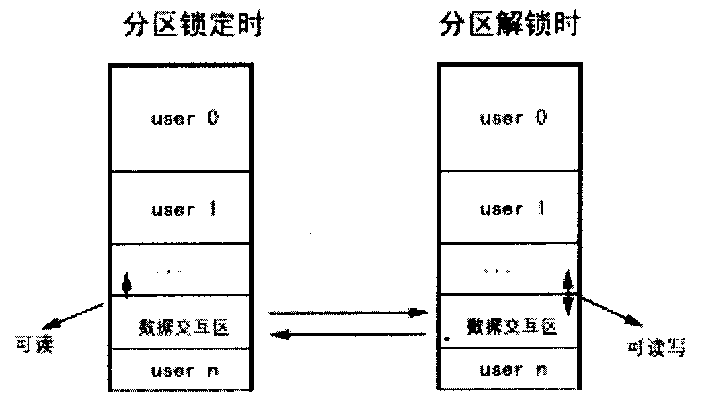
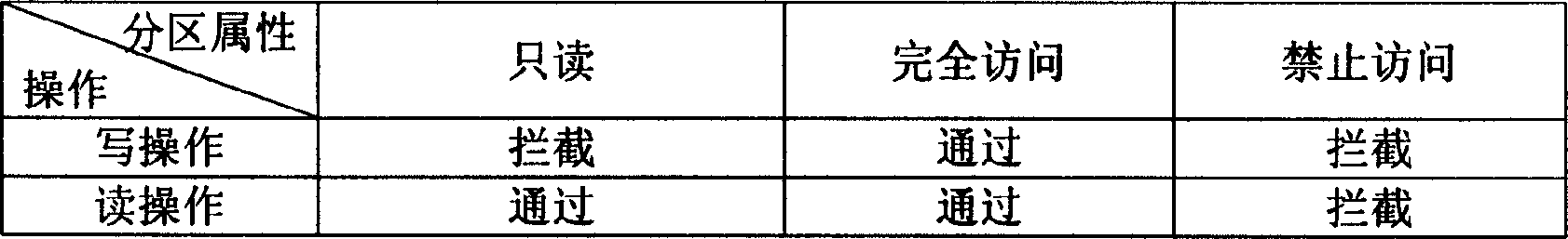
A method for locking hard disk partition safely
InactiveCN1595517AImprove securityLow costUnauthorized memory use protectionDigital recordingComputer compatibilityNetwork isolation
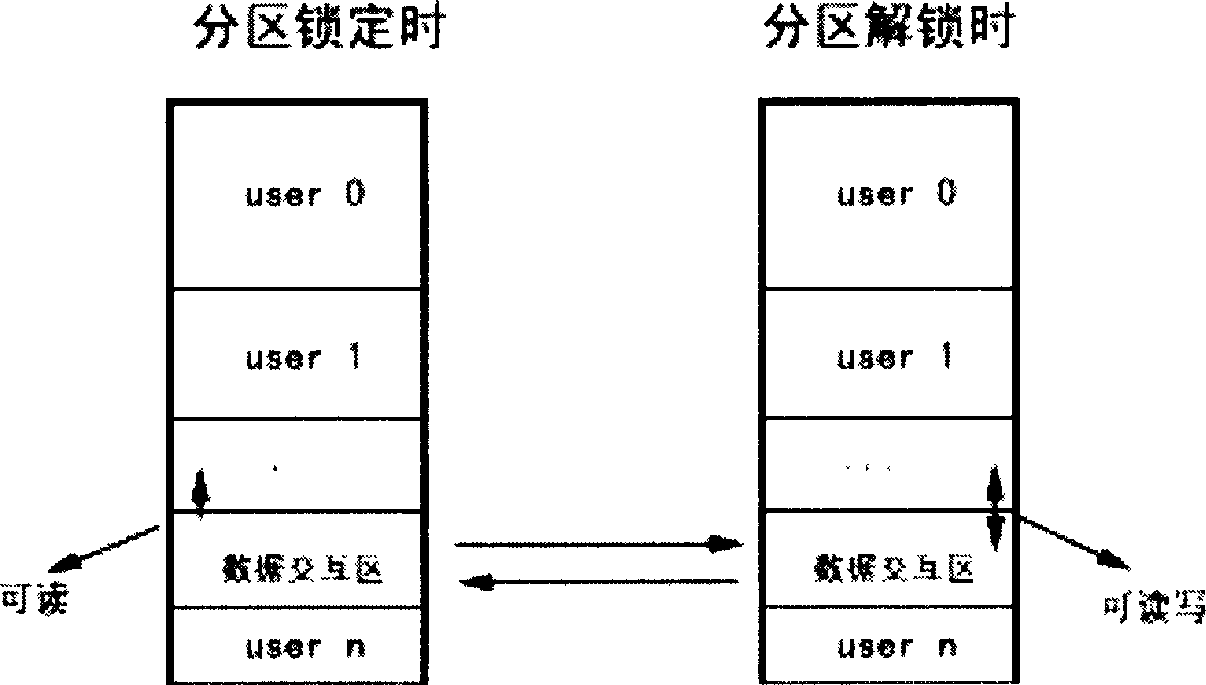
The invention relates to a method, which is used to lock the disc partition safely through BIOS layer and OS layer. The invention separates a disc into many working partitions with self-defining locking through the read-write control technique of the disc magnetic track. Data of different users in these partitions is kept secret on the one hand, but provides good interactivity within a permission range on the other hand. That is to say, many persons may share one computer safely, and one PC is visualized to be many PCs by physical means. Thus the multi-users state of the workstation is realized, and the network isolation card function is implemented with software. Regardless of the disc type, with perfect compatibility, the invention controls the disc partition data effectively, without influence of the reading-writing speed. The locking function is implemented costively.
Owner:西安三茗科技股份有限公司
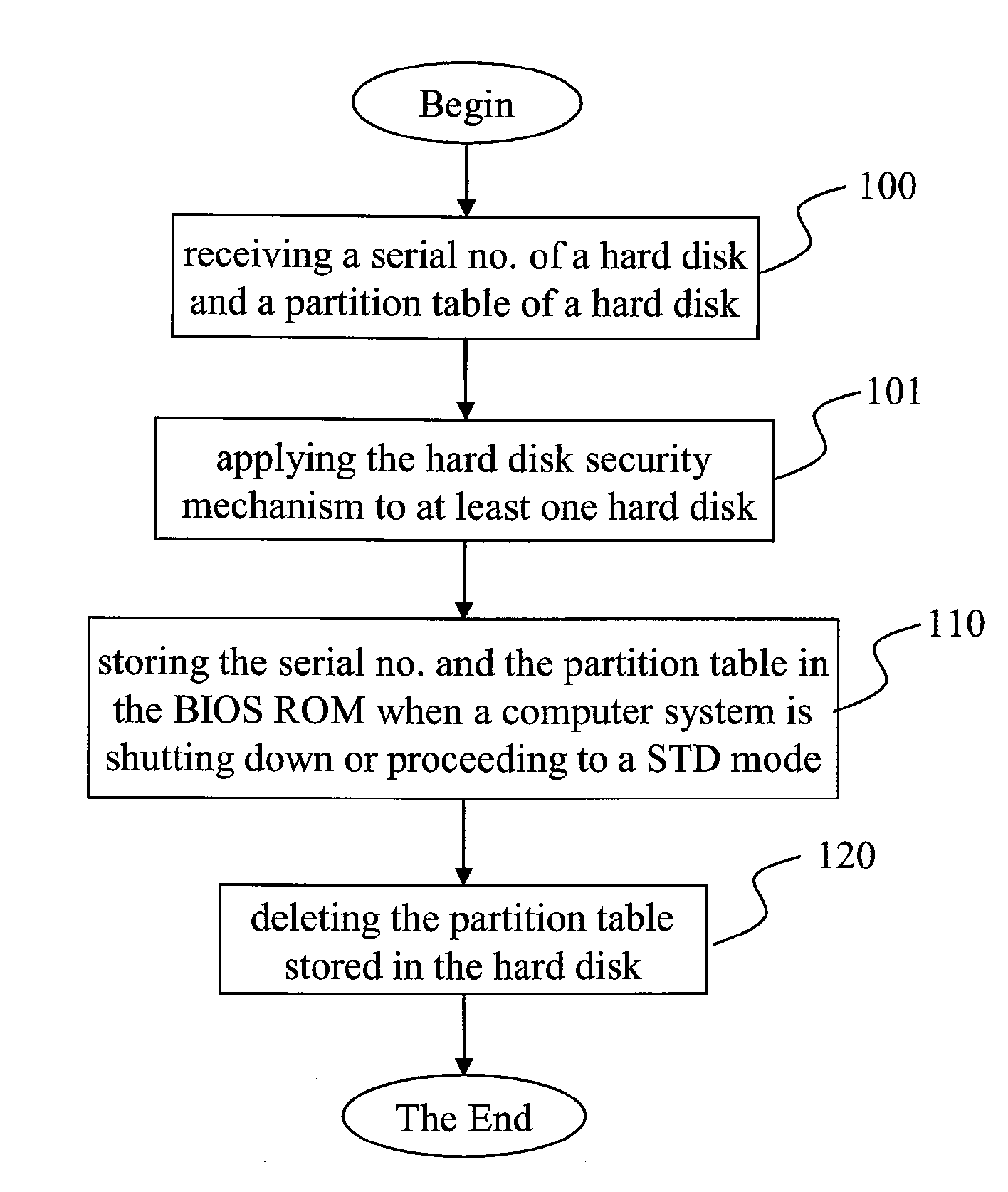
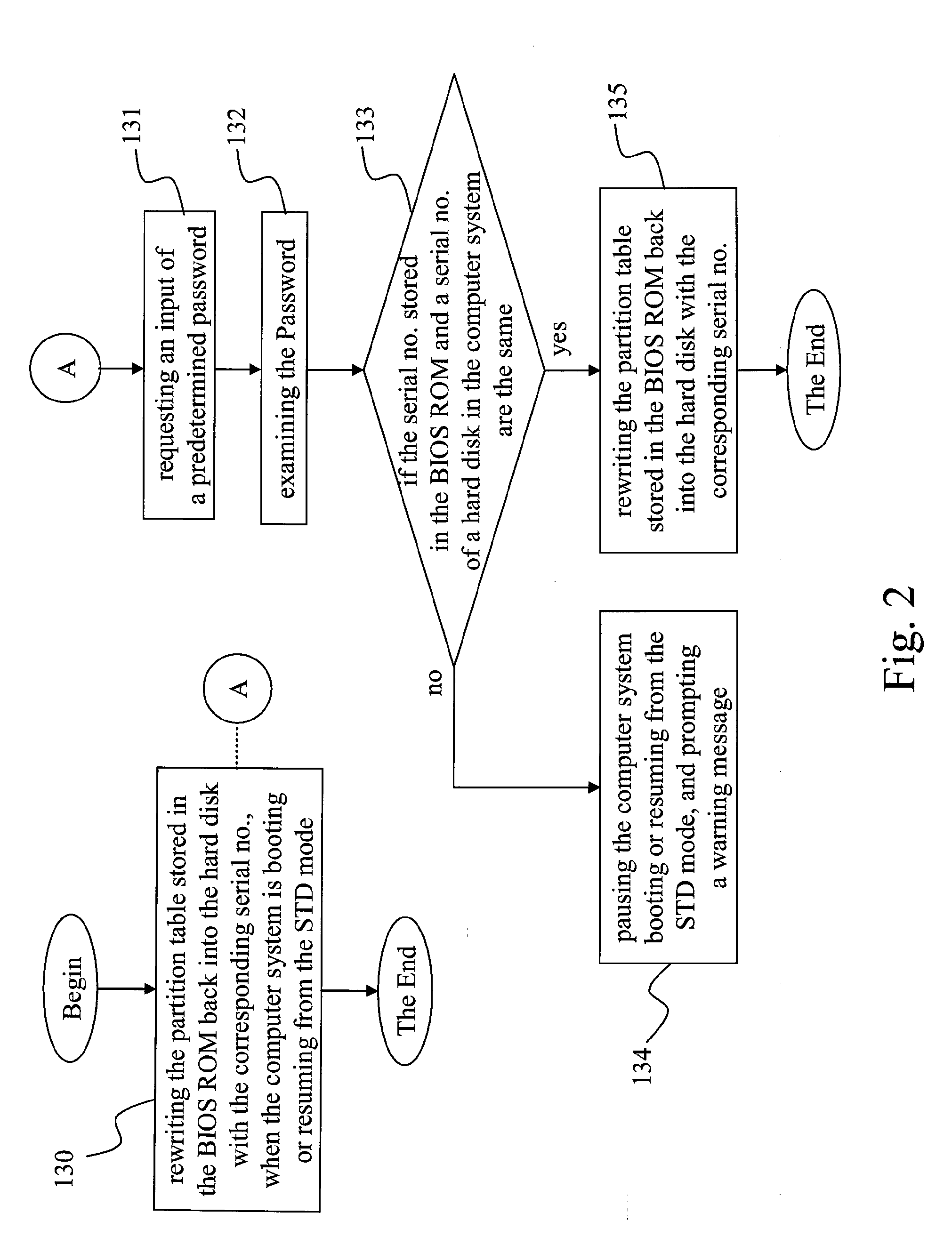
Hard Disk Security Method in a Computer System
InactiveUS20090037720A1Easy to useDigital data processing detailsDigital computer detailsPasswordComputerized system
This invention presented a hard disk security method in a computer system, which provides a hard disk security mechanism combining with the power-on password function for the storage data in a hard disk by restoring the partition table into the BIOS ROM in advance, and deleting the partition table of the hard disk to secure the hard disk.
Owner:WISTRON CORP
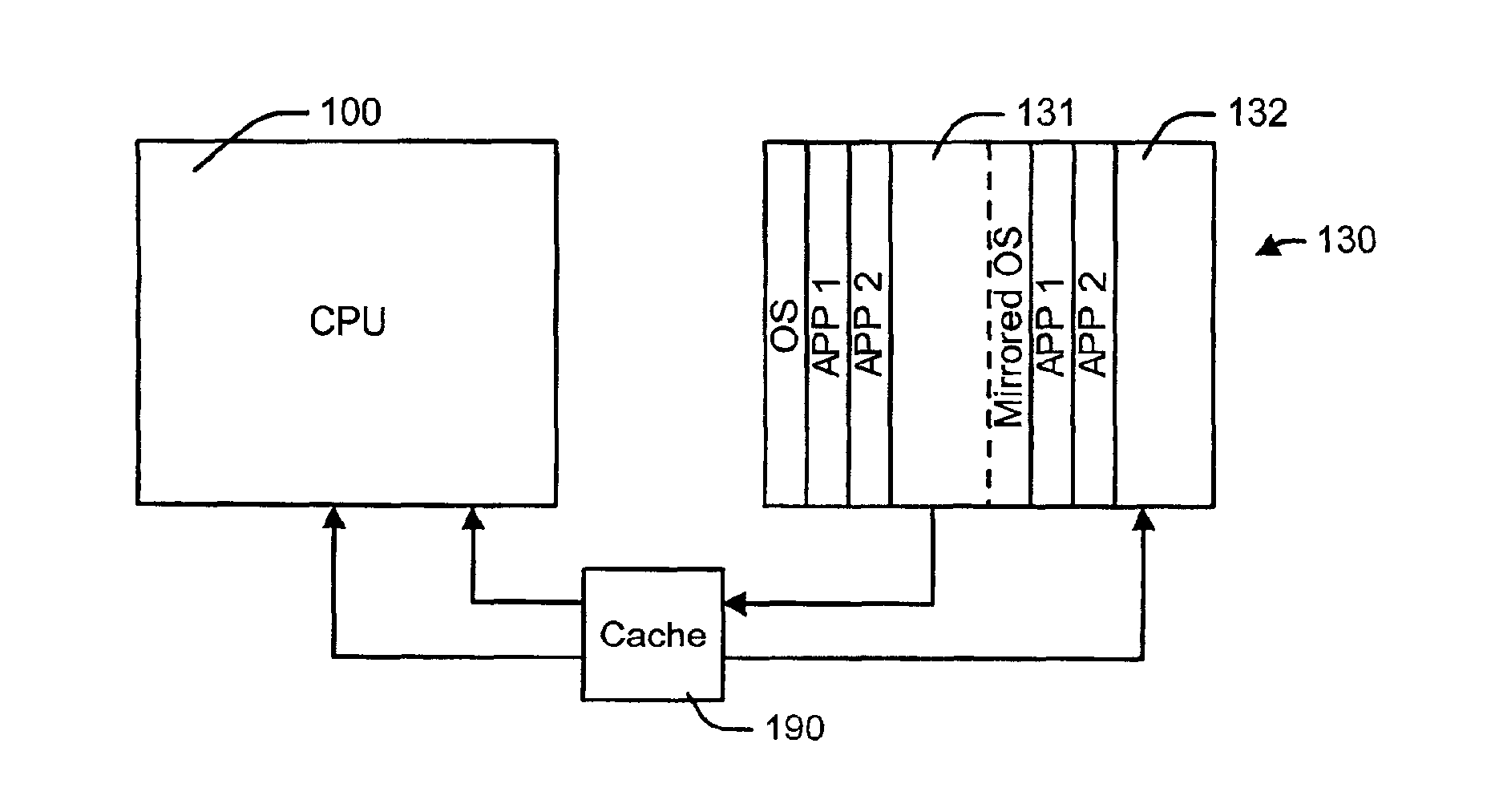
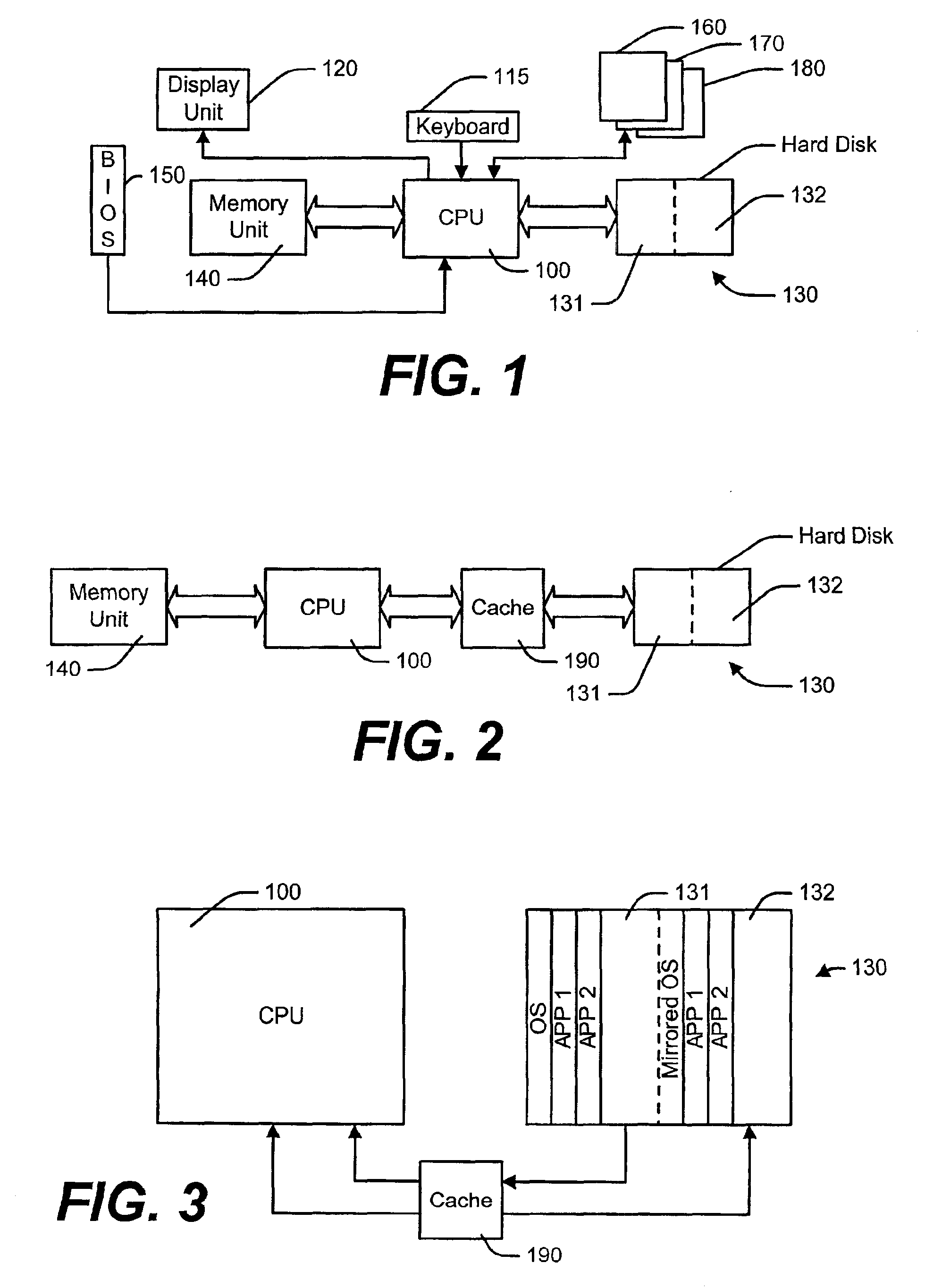
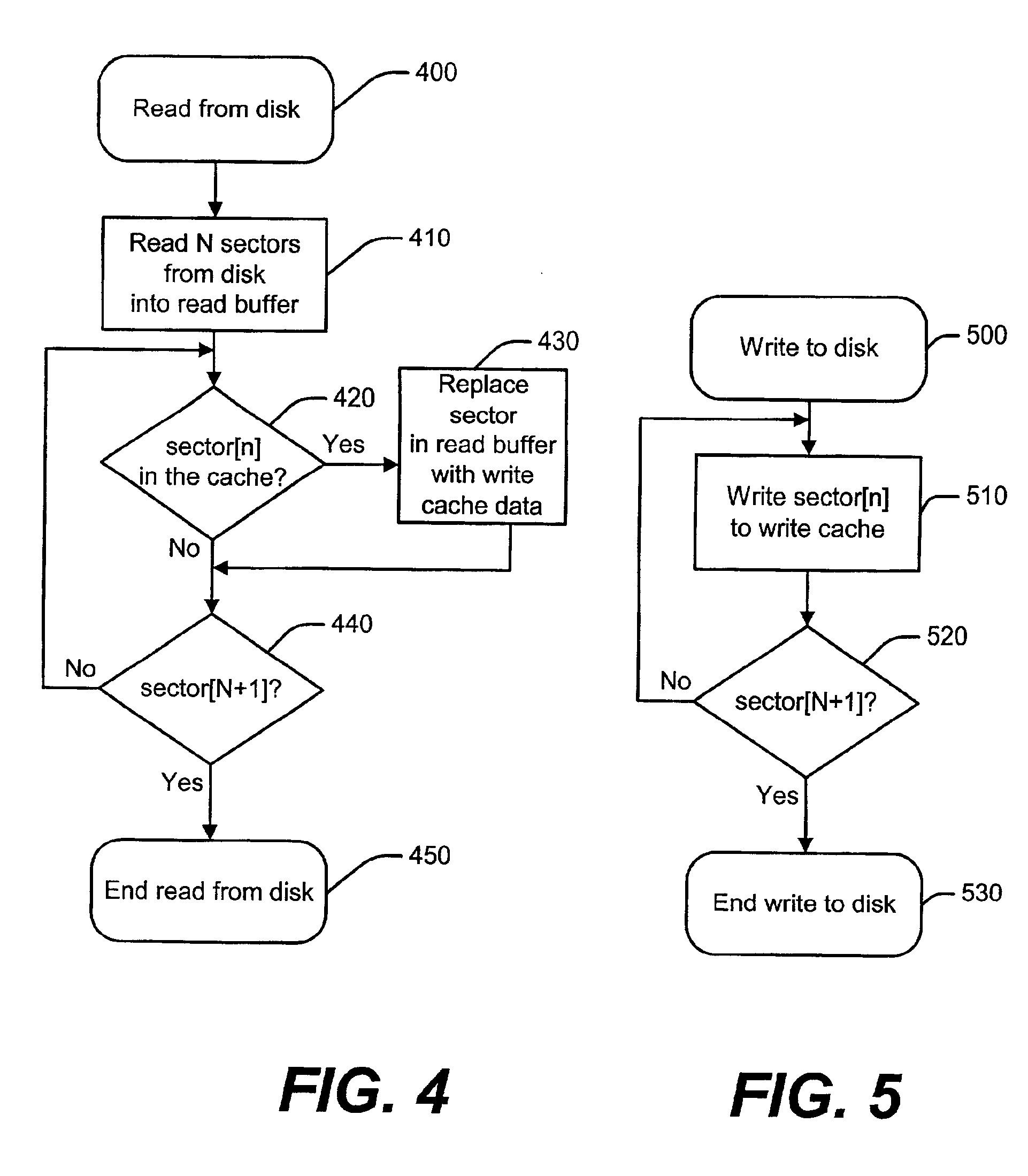
Computer system with improved write cache and method therefor
InactiveUS6904496B2Readily apparentInput/output to record carriersMemory adressing/allocation/relocationWrite protectionComputerized system
Method of operating a computer system with a central processing unit and a hard disk system coupled with the central processor, the method comprising the steps of:partitioning the hard disk into at least a bootable partition and a second partition;determining a write protection for the bootable partition;using the second partition as a write cache thereby maintaining the bootable partition;if a write protection is not set, then flushing the write cache to the bootable partition during a shutdown procedure.
Owner:DELL PROD LP
Computer security locks having separate key pairs
ActiveUS20170373851A1SpeedKeep data safeMultiple keys/algorithms usagePublic key for secure communicationComputer security modelDisk partitioning
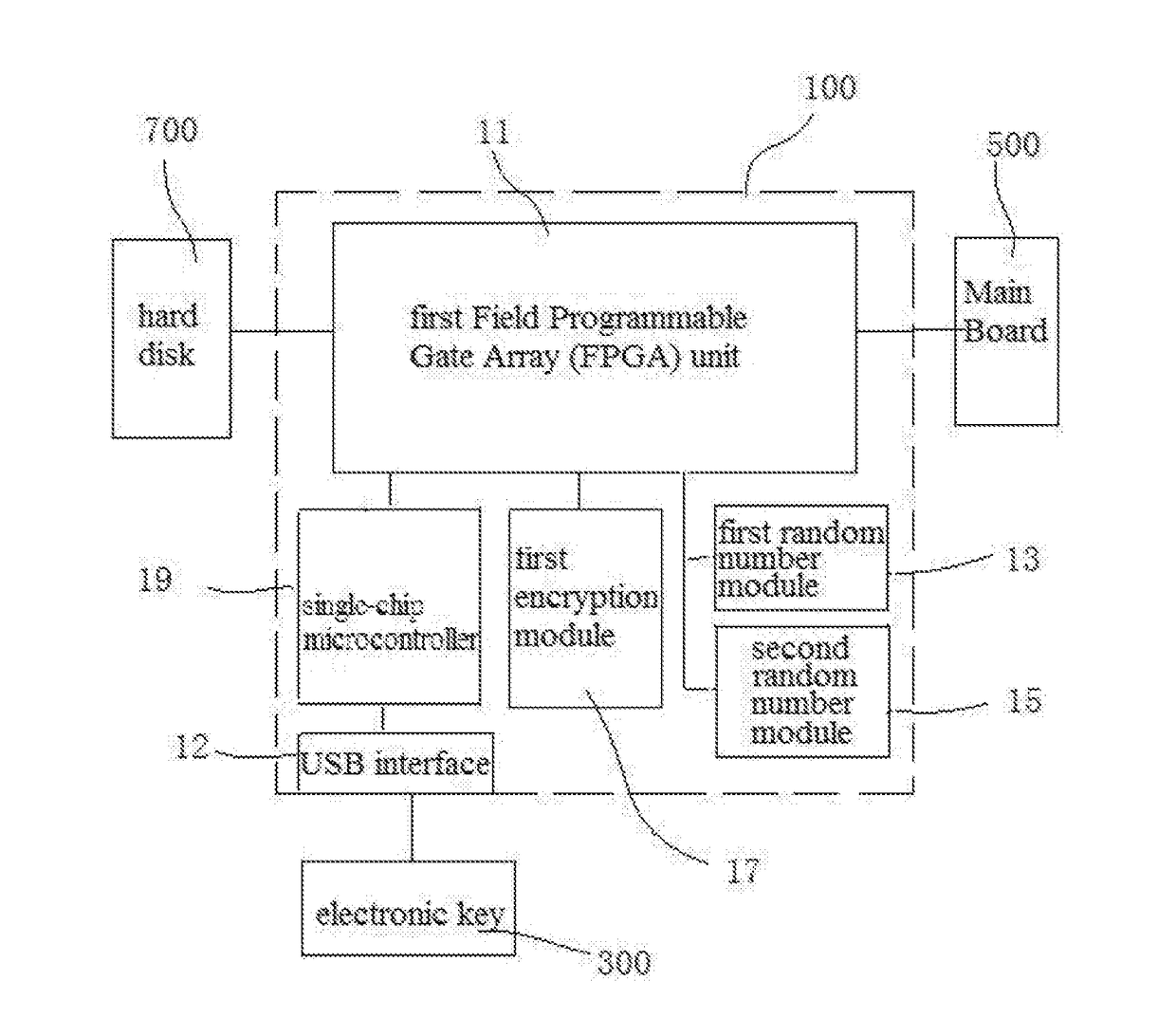
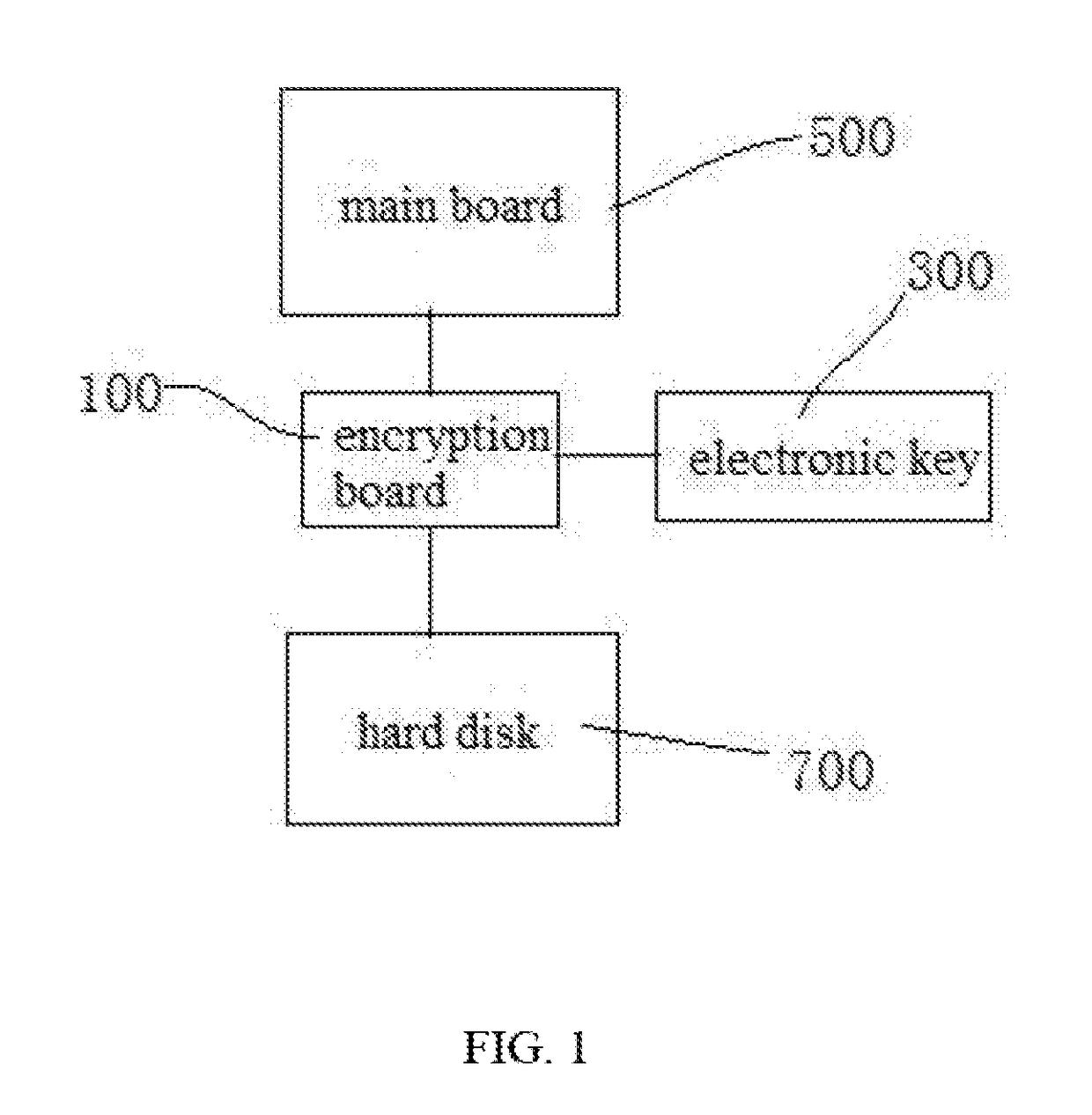
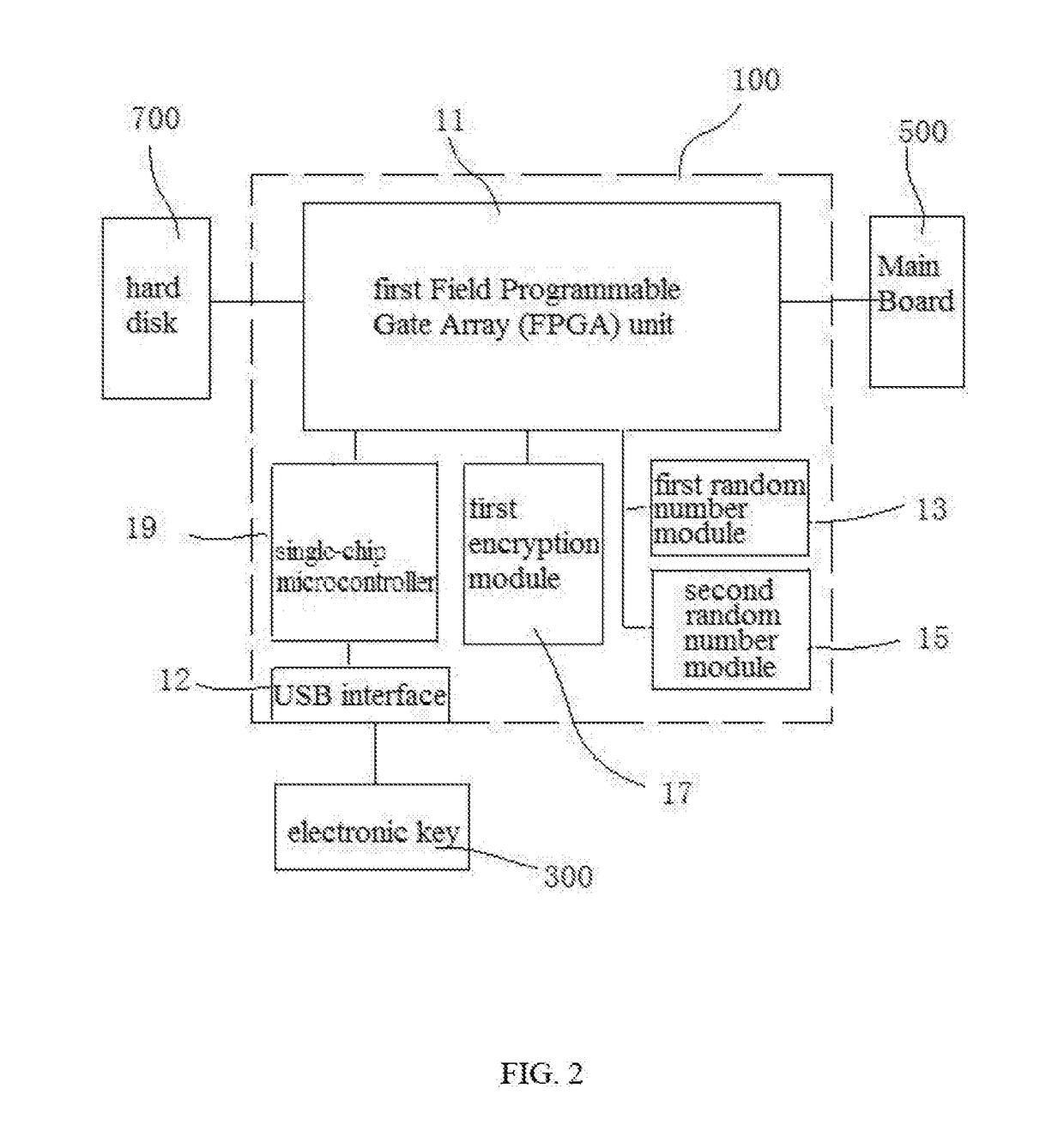
A computer security lock having separate key pairs includes an encryption board inserted between a main board and a hard disk, and an encryption board being inserted into the encryption board to perform a real-time authentication process. The electronic key and the encryption board performs the real-time authentication process and hardware anti-copy self-testing process, and encrypt the data communicated between the encryption board and the electronic key. After passing the authentication process and the hardware anti-copy self-testing process, the electronic key combines an internally stored key list with the key list on the encryption board, and selects a user key to encrypt / decrypt the data on the disk according to the partition of the hard disk where the encrypted data is written to. The computer security lock can assure the safety of the data, and the hardware is prevented from being copied.
Owner:CHINA ZHENHUA GRP SCI & TECH +1
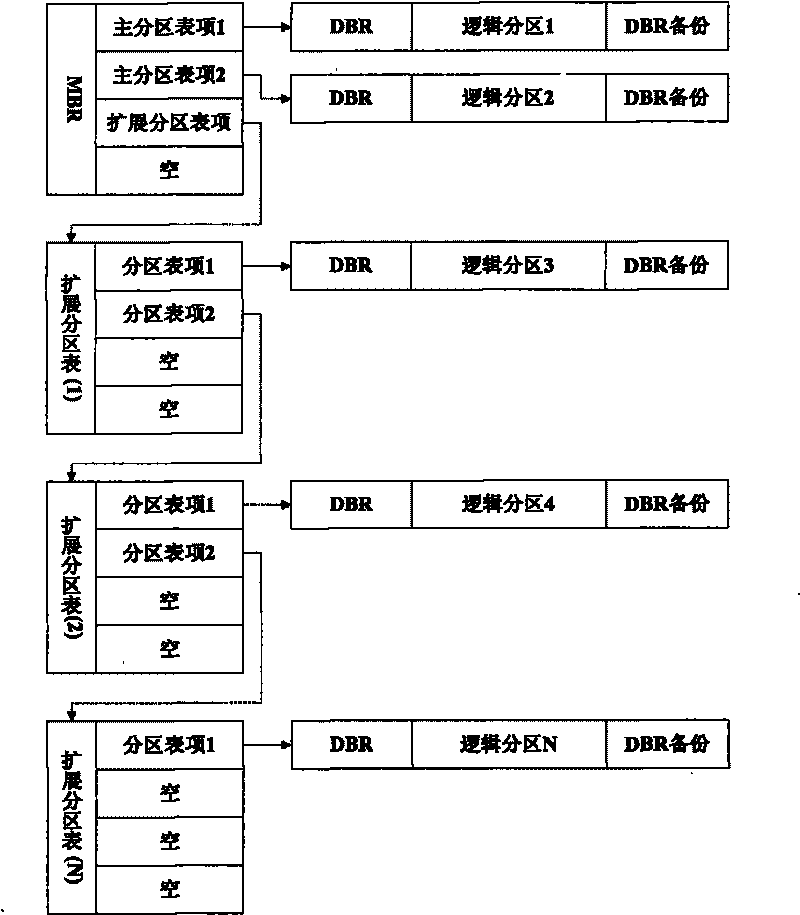
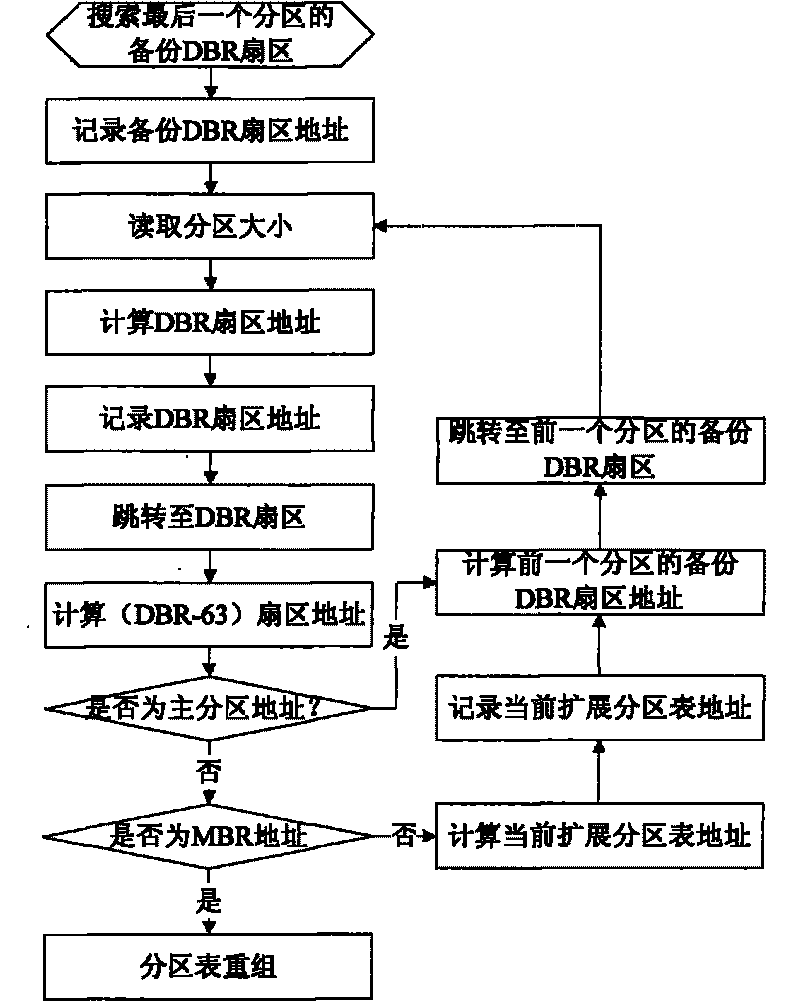
Fast reverse search restructuring and recovery method of hard disk partition table
ActiveCN101763296ANormal access dataAchieve data recoveryRedundant operation error correctionRecovery methodRestoration method
The invention discloses a fast reverse search restructuring and recovery method of a hard disk partition table. A destroyed main partition table is restored by adopting an NTFS partition table chain reverse search restructuring algorithm based on a back-up DBR, therefore, the data recovery of a hard disk is realized. The method comprises two processes of partitional and reverse scanning of an NTFS system and main partition table restructuring. The invention has fast recovery speed, simple operation and high recovery success ratio, and realizes the restructuring and the recovery of the whole main partition table.
Owner:江苏航天龙梦信息技术有限公司
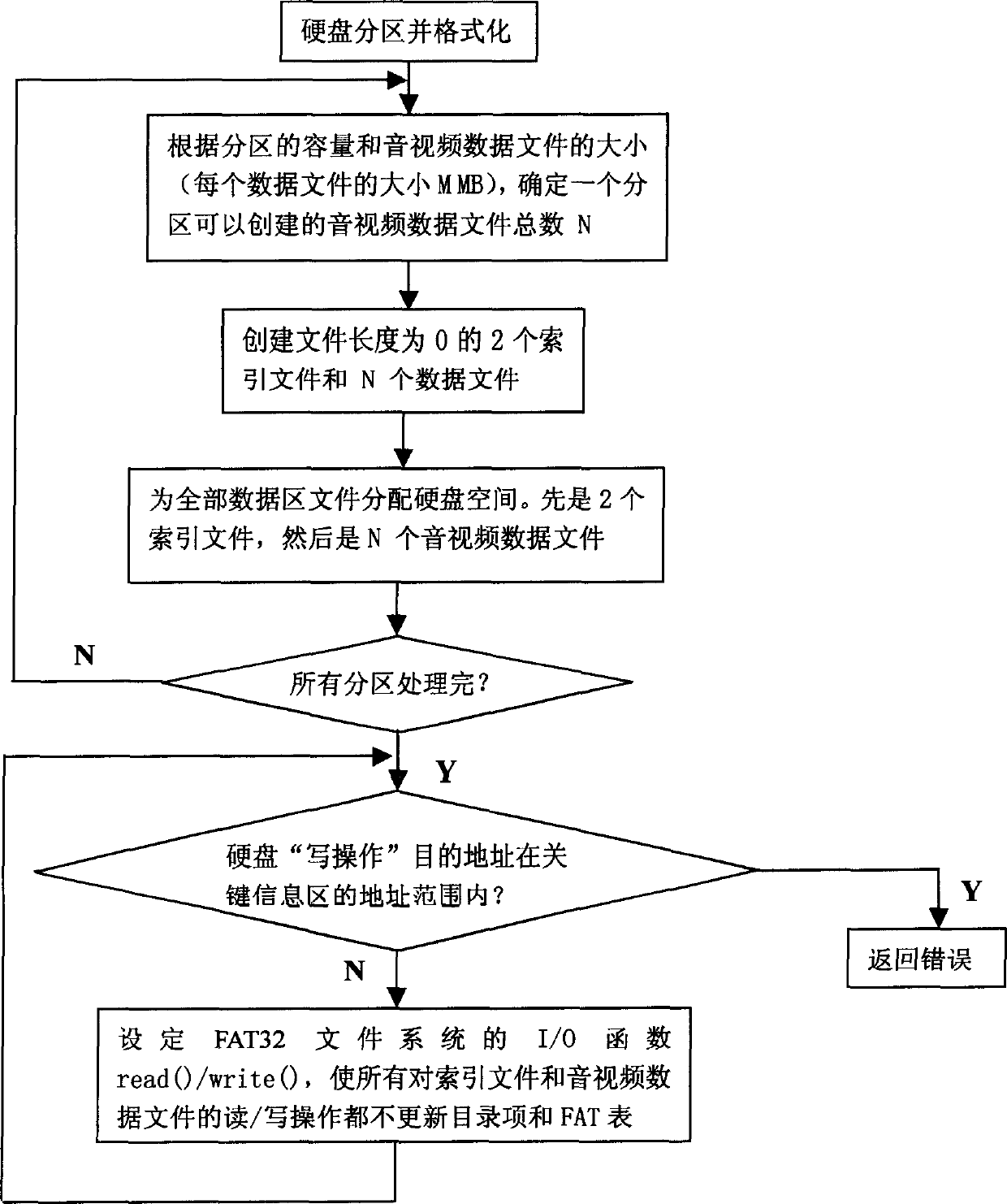
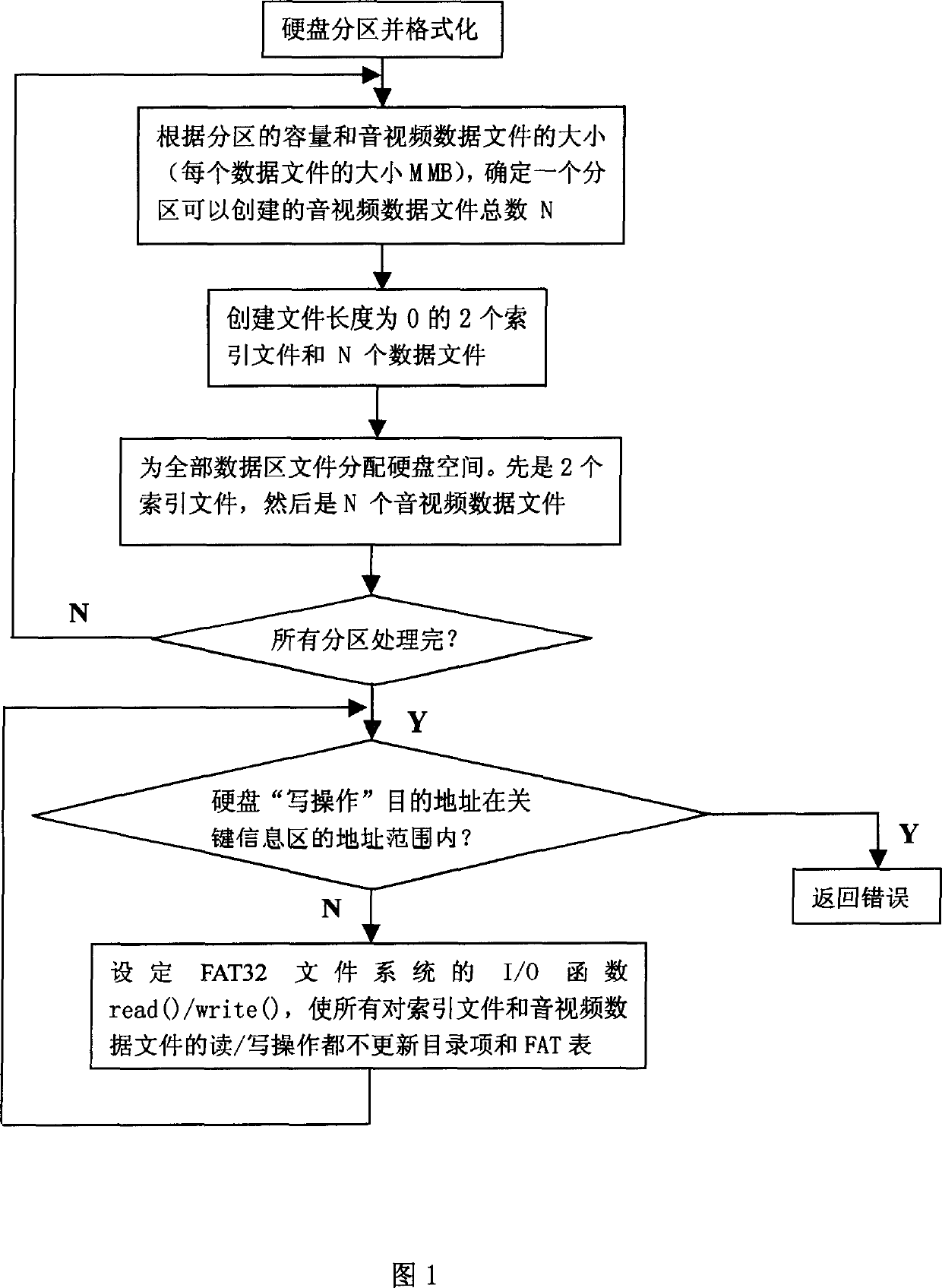
Method for protecting hardware key information area in embedded device
ActiveCN1822174AReduce maintenanceImprove reliabilityTelevision system detailsColor television detailsElectricityDisk partitioning
This invention relates to a protection method for hard disk key information region in an inserted device including the following steps: 1, partitioning a disk and formatting, 2, pre-setting up files, setting up index files and N audio and video data files, the lengths of the files are 0 bytes and the length of the index files is corrected, 3, freezing and protecting the key information region of the disk when recording, 31, when writing every disk, comparing the destination address of the disk and the address sphere of a key information region, if it is in the sphere, then the disk drive program returns back the mistake directly, 32, all read / write operations to the index files and audio and video data files will not refresh the directory entry and FAT table.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Method for switching operating system by hot key
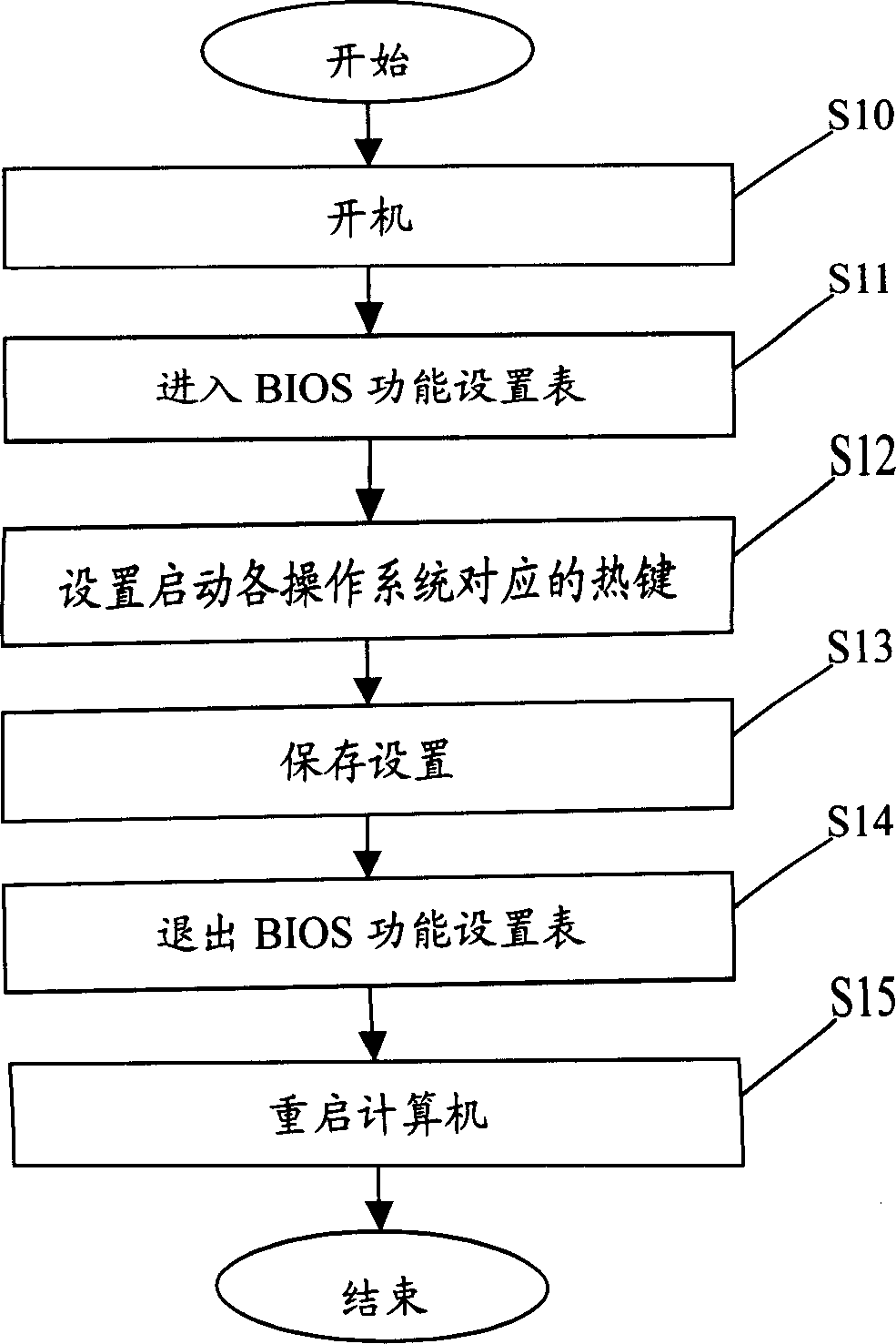
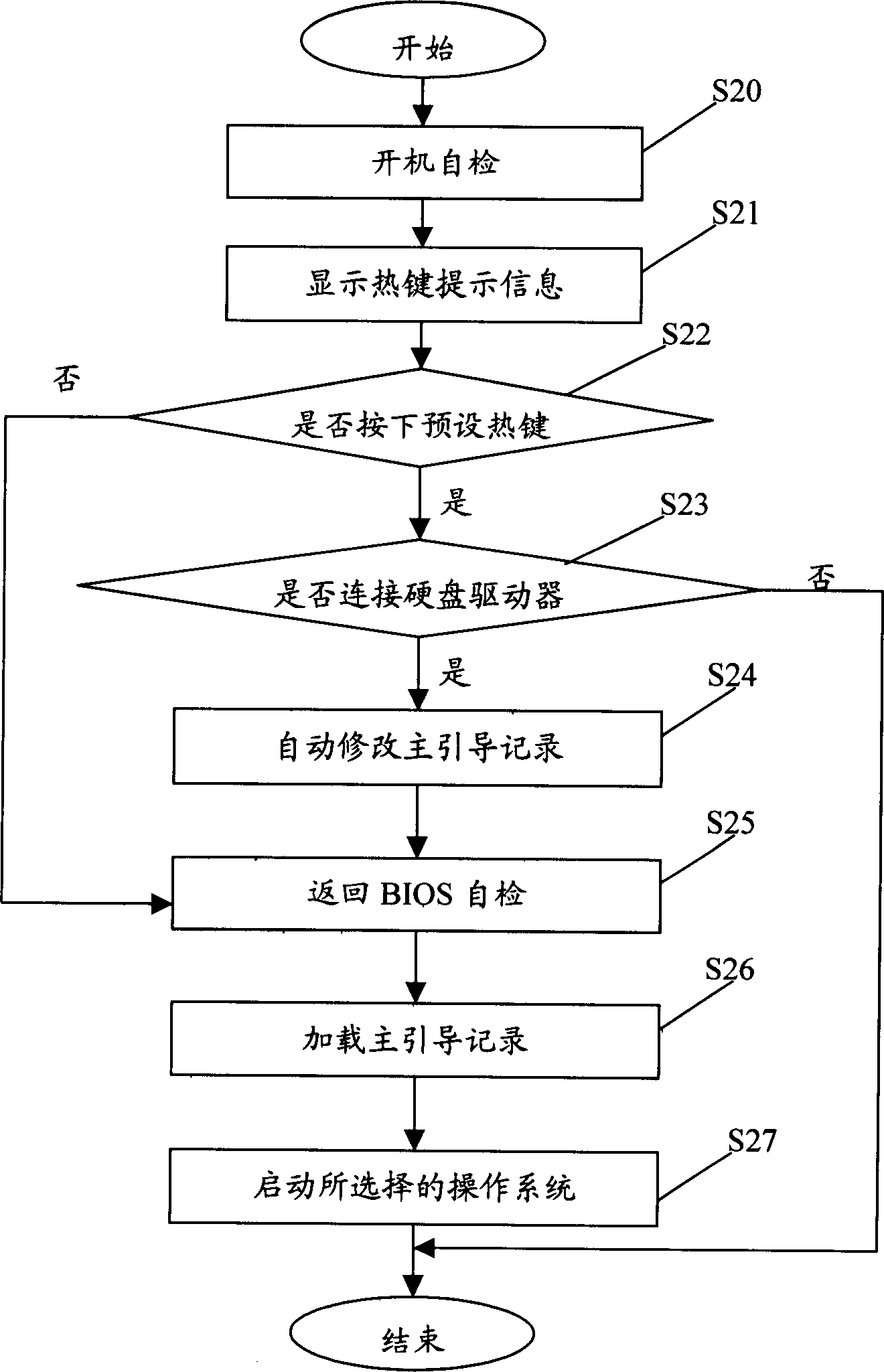
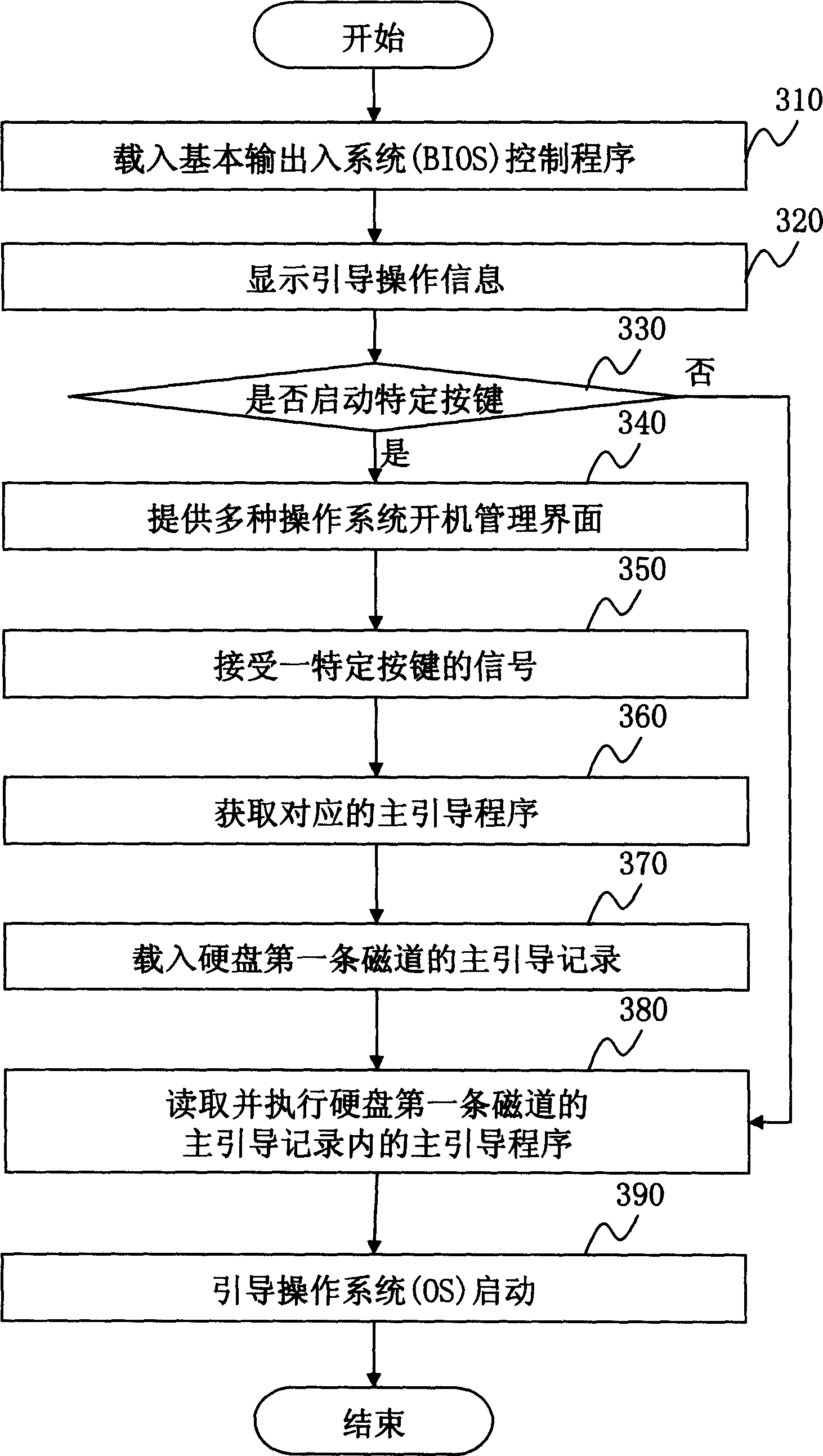
InactiveCN1841323AQuick switchBootstrappingProgram loading/initiatingHard disc driveOperational system
The method to switch OS by hotkey comprises: self checking by BIOS once startup; displaying all custom of default prompt information of hot key; deciding whether user presses set hot key; if yes, checking whether connects to the HD, if yes, auto modifying the HD partition table in MBR, namely modifying the partition parameter with corresponding OS; returning to the BIOS self check; loading the MBR; by the modified parameter, searching OS by HD bootstrap for startup.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Multiple user data storage service system
This invention discloses a multi-user data storage service system including a communication module undertaking communication tasks of TCP / IP network to guarantee the compute and order transmission of data on the communication layer, a user module discriminating the access requirement of the customer end, an ISCSI protocol module transforming ISCSI and standard SCSI instructions, a multi-user document system module setting up an independent disk for every user based on the user access ways and converting the block data operation request of each user to the access to file data directly and a management module managing the above mentioned modules to coordinate their operation.
Owner:NETAK TECH KO LTD
Backup and recovery of systems including boot configuration data in an extension firmware interface partition
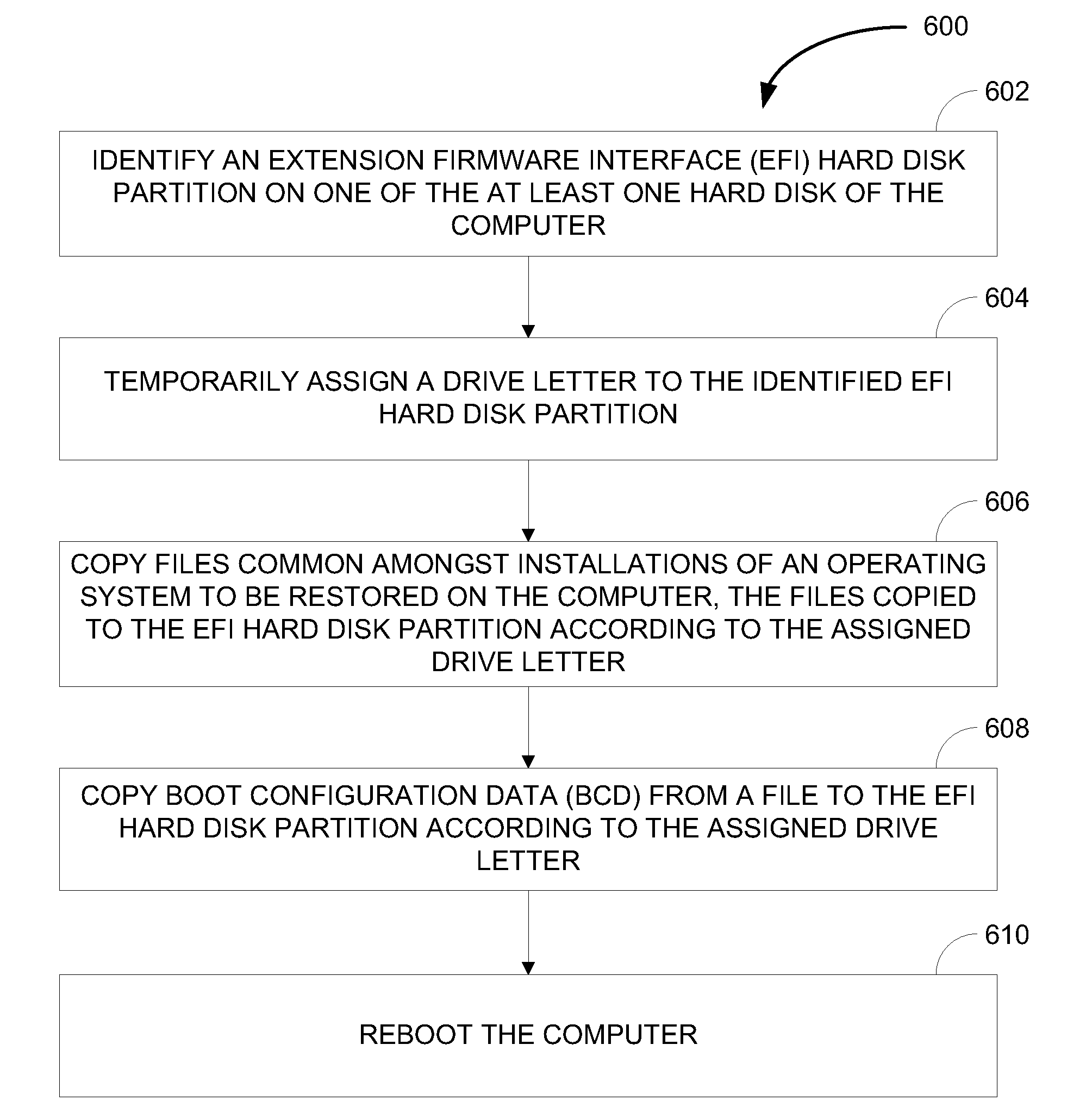
InactiveUS20110047129A1Memory loss protectionError detection/correctionOperational systemSystem recovery
Various embodiments includes at least one of systems, methods, and software for backup and recovery of systems including boot configuration data in an extension firmware interface partition. Generating a backup, in some embodiments, includes copying Boot Configuration Data (BCD) from a registry of an operating system executing on a computer into a file and storing the file. These and other embodiments may include a system restore process that consumes this file. Such a process may operate to identify an Extension Firmware Interface (EFI) hard disk partition on a hard disk of a system to be restored, temporarily assign a drive letter to the identified EFI hard disk partition, and copy files common amongst all installations an operating system to be restored on the system along with BCD data from the BCD file to the EFI hard disk partition according to the assigned drive letter. The system may then be rebooted.
Owner:CA TECH INC
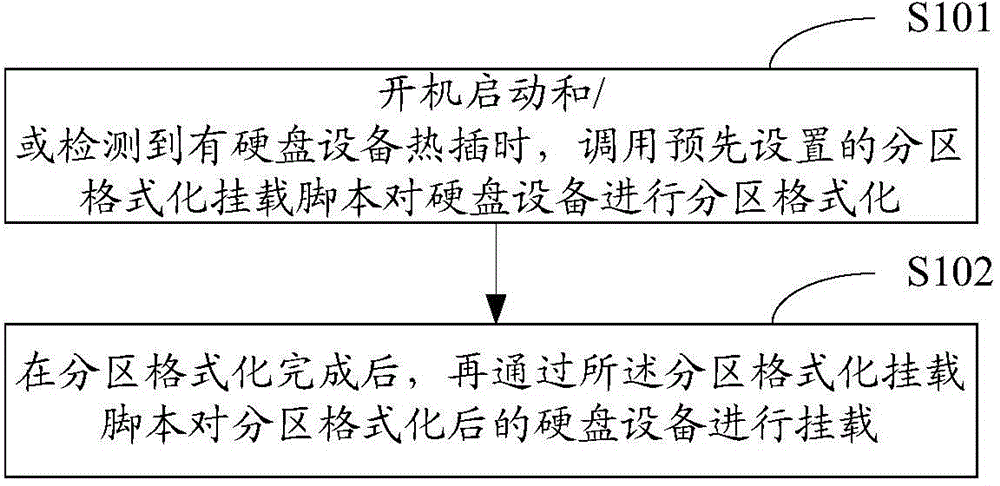
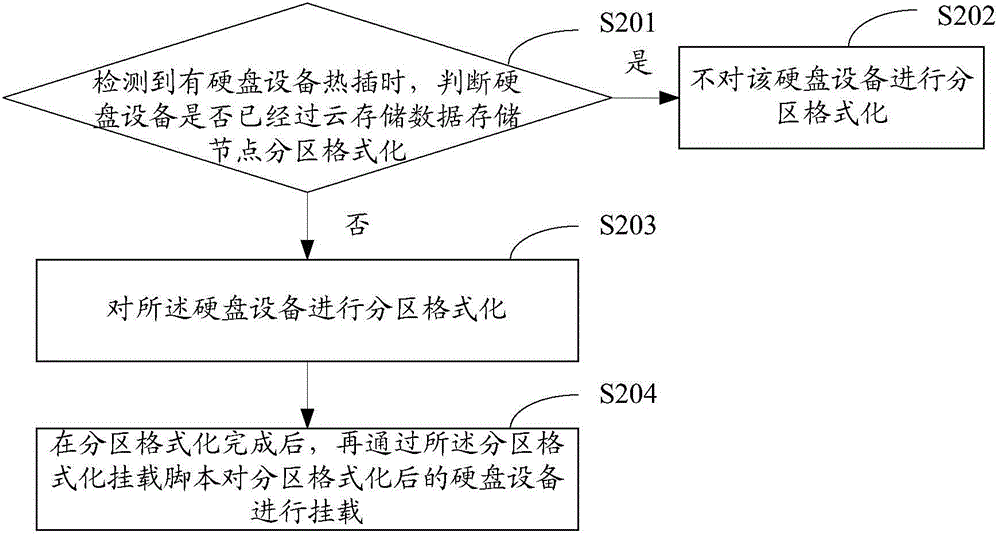
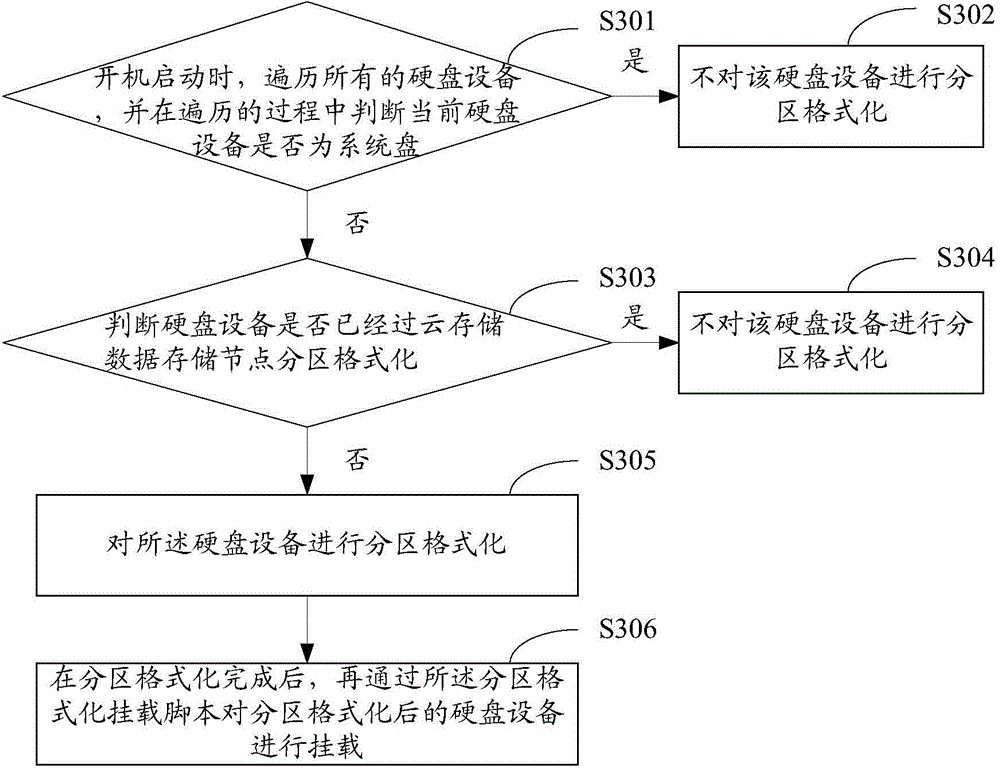
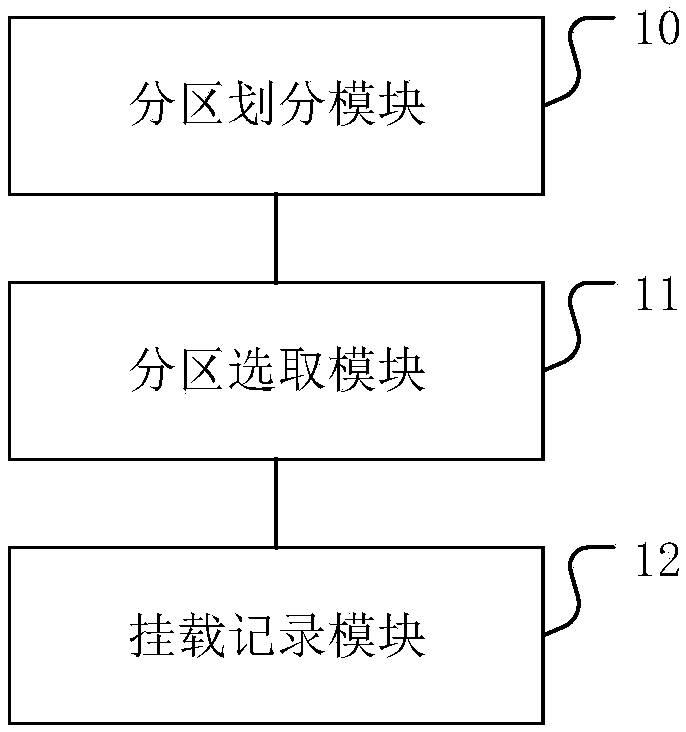
Method and device for conducting partition formatting and mounting on hard disk
InactiveCN104020960ASolve the cumbersome operationImplement automatic partition formattingInput/output to record carriersProgram loading/initiatingDisk partitioningComputer science
The invention is applicable to the field of security and protection monitoring, and provides a method and device for conducting partition formatting and mounting on a hard disk. The method comprises the steps that a partition formatting and mounting script set in advance is called to carry out partition formatting on the hard disk device when a computer is started and / or hot plugging of the hard disk device is detected; after partition formatting is completed, the partition formatting and mounting script is used for carrying out mounting on the hard disk device obtained after partition formatting. According to the method and device for conducting partition formatting and mounting on the hard disk, the partition formatting and mounting script is added, the function of calling the partition formatting and mounting script is set in a boot-up script and a script called when hot plugging of the hard disk device is detected, and therefore a system can automatically carry out partition formatting and mounting on the hard disk device when the computer is started and / or hot plugging of the hard disk device is detected.
Owner:SHENZHEN INFINOVA
Multiple operating system boot loading method
InactiveCN1570884AMemory adressing/allocation/relocationProgram loading/initiatingOperational systemEngineering
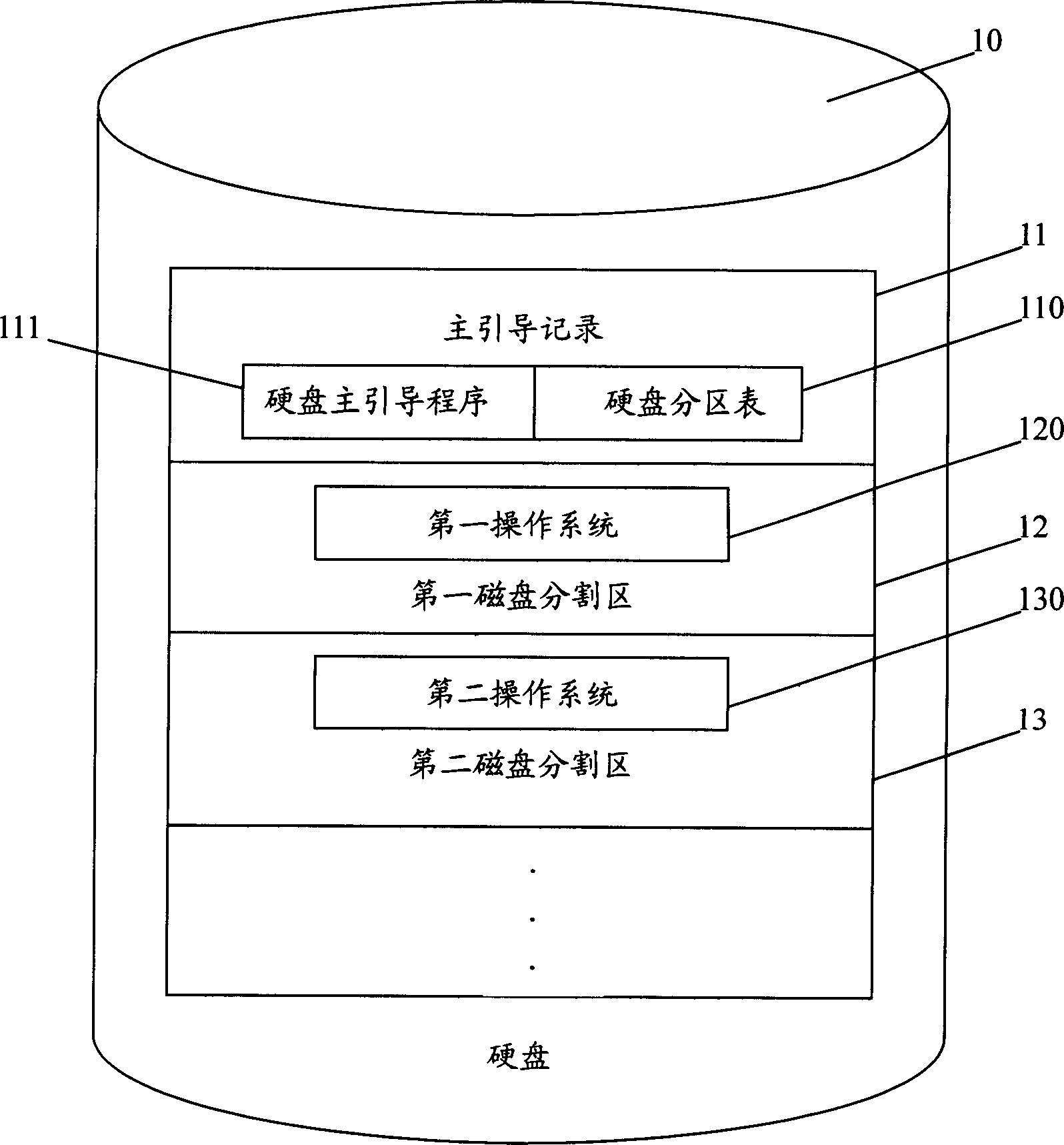
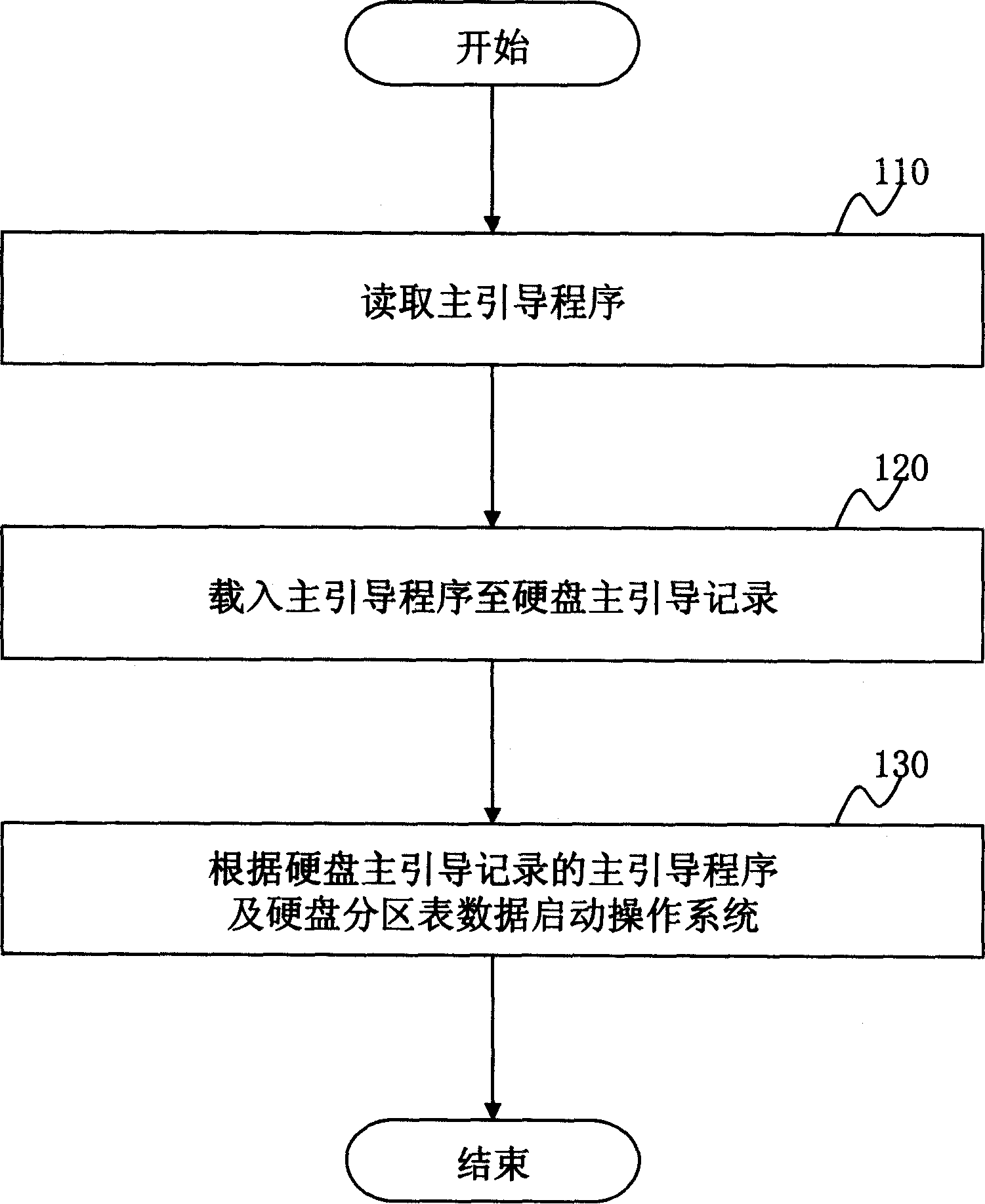
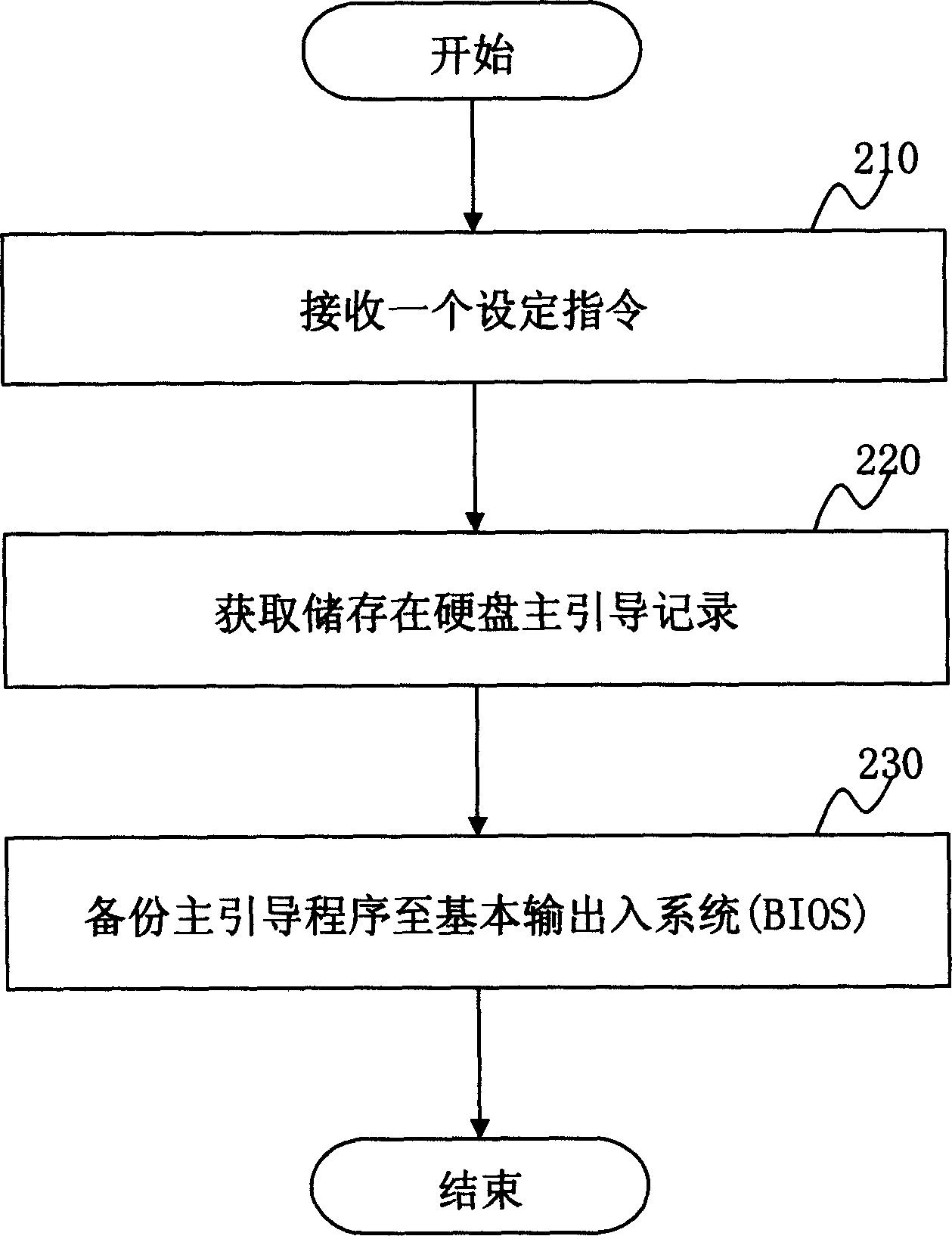
It is a kind of multiple operation system booting and loading method. It copys the main boot program that stored in the main boot record in hardware to the memory device that beyond the main boot record. During boot executing, it changes the main boot program of hardware main boot record by executing the function that defined in special key or operation that defined in special control interface. By reading the main boot program of hardware main boot record and hard disk partition table data when power on, it can boot multiple operation system.
Owner:INVENTEC CORP
System partitioning hiding method
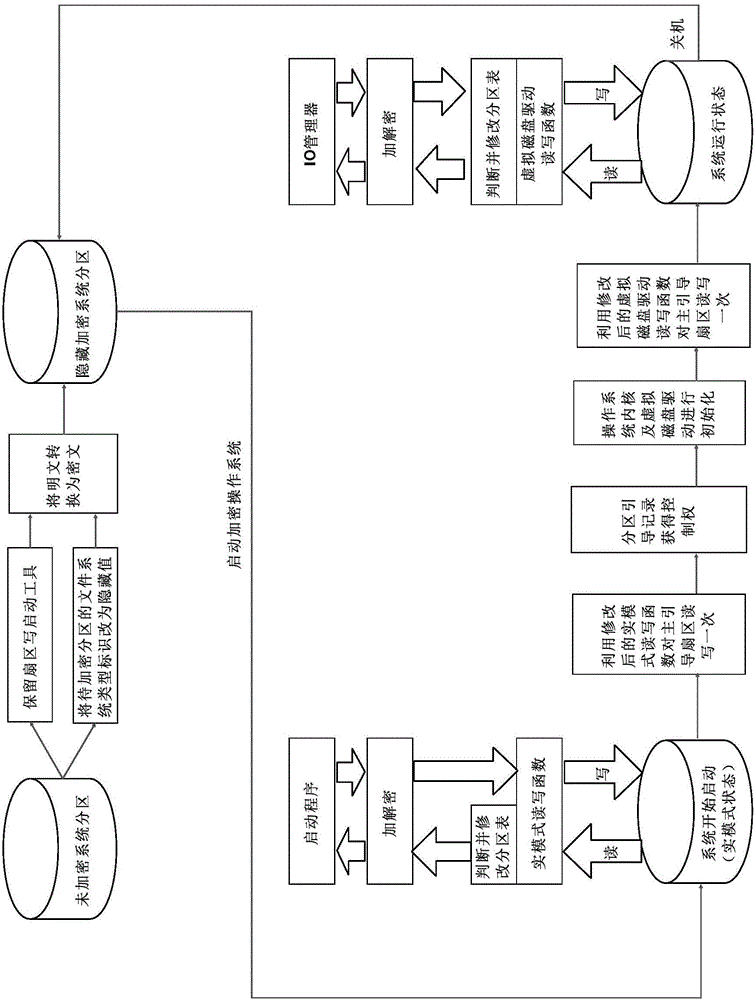
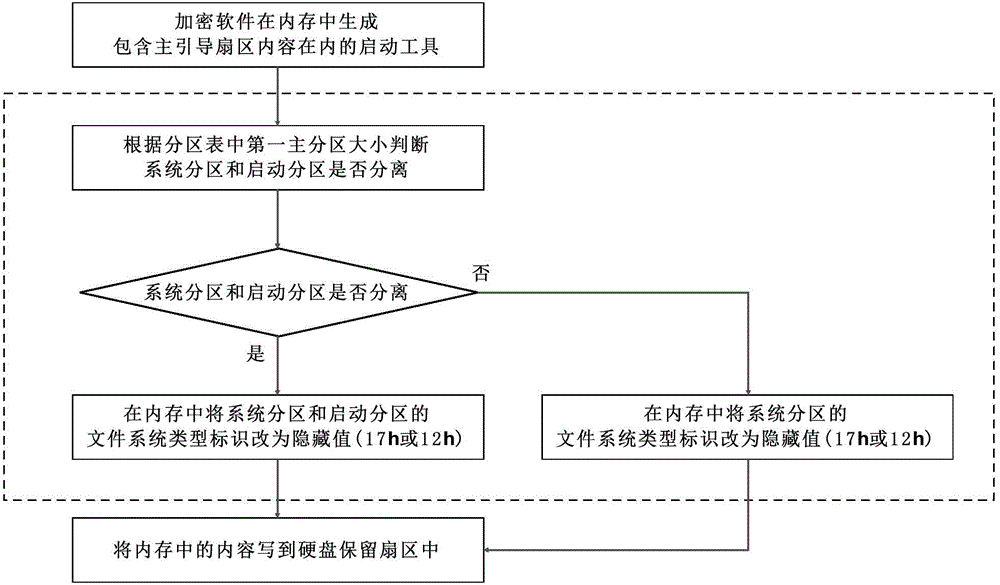
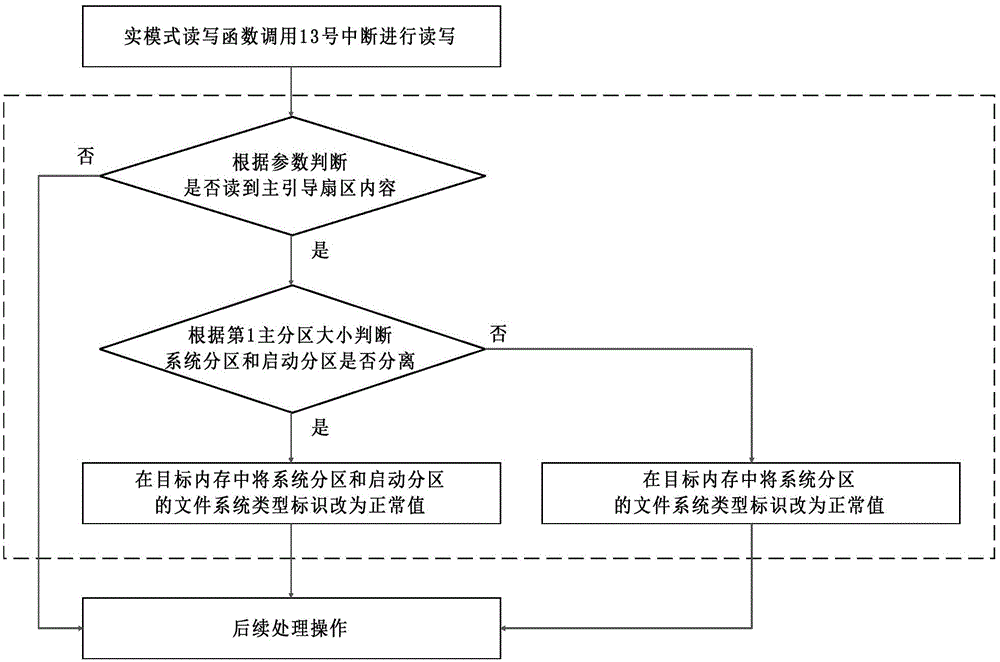
InactiveCN103984910AImprove concealmentImprove securityInternal/peripheral component protectionFile systemDisk partitioning
The invention discloses a system partition hiding method. A file system type identification of each encryption system partition on a hard disk is set into a hidden value; under the system operation state, the reading operation is carried out on a partition table of the hard disk, and the file system type identification of the corresponding encryption system partition in an internal storage buffering region is changed into a normal value and then is read; when the writing operation is carried out on the partition table of the hard disk, a section of internal storage space is applied for, data to be written is copied to the applied internal storage buffering region, the file system type identification of the corresponding encryption system partitioning in the internal storage buffering region is changed into a hidden value and then is written on the hard disk. According to the method, the incorrect formatting operation is effectively avoided, a drive does not need to be distributed for the encryption partition by a system, and the hidden property of the encryption partition is enhanced.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV +1
Installation method and system of operating systems
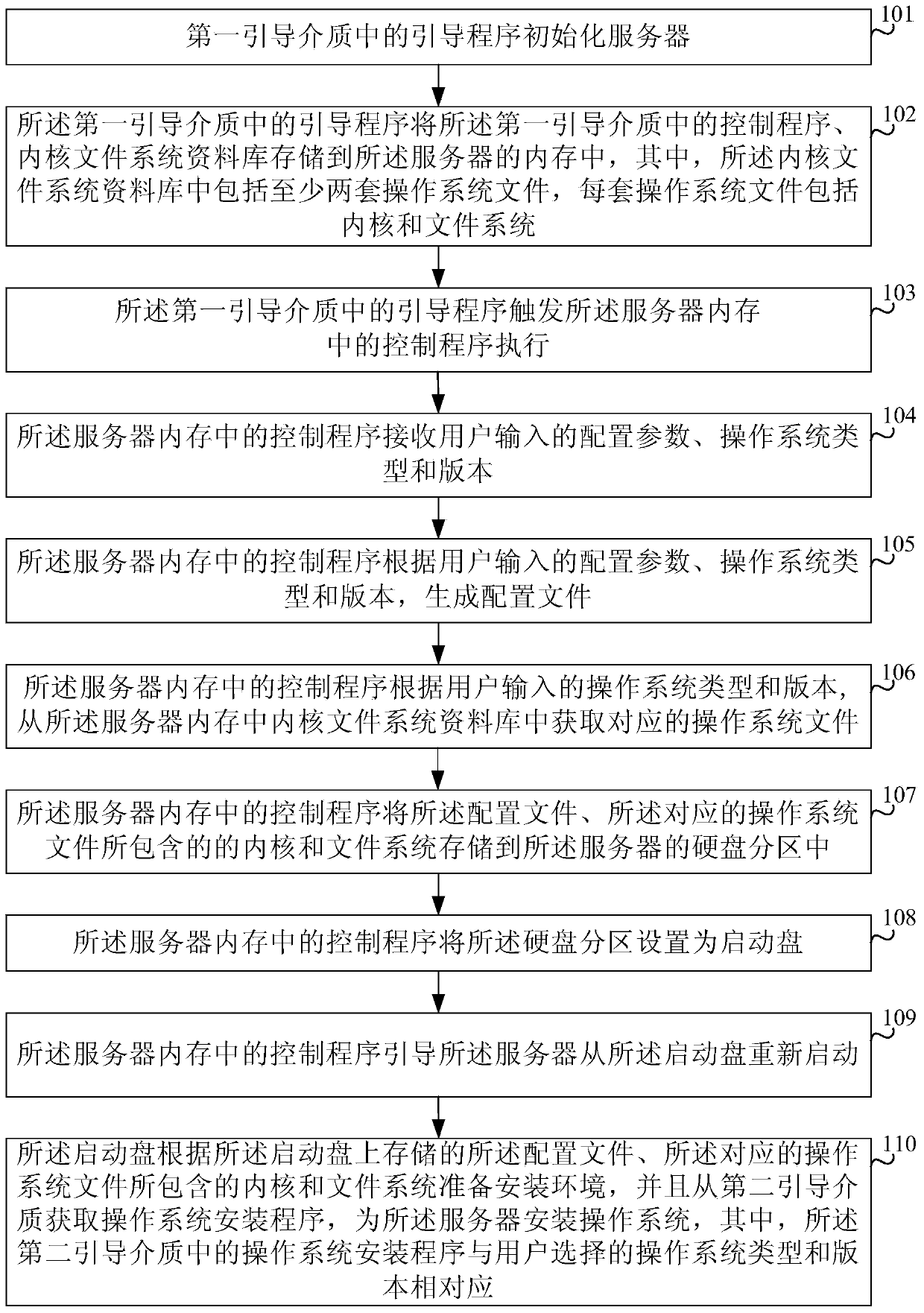
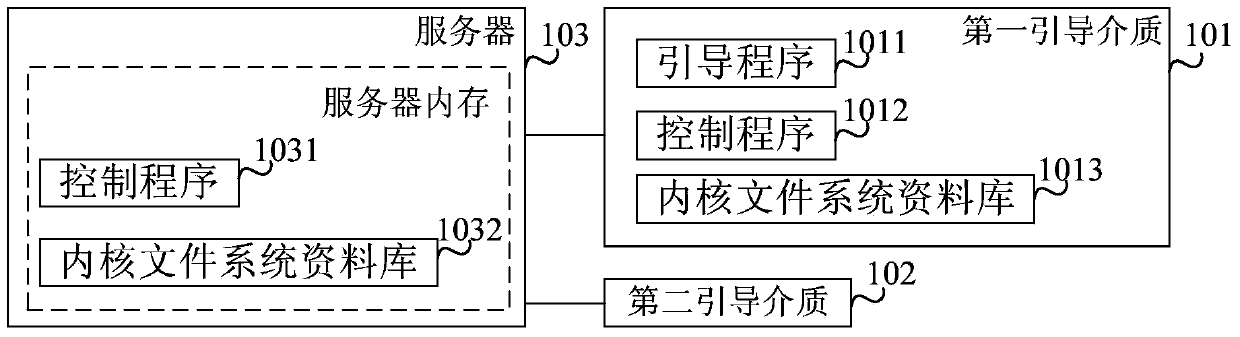
The invention provides an installation method and system of operating systems. The installation method includes: initializing a server by a boot loader in a first guide medium, storing a control program and a core file system database in the first guide medium, into the server, and triggering execution of the control program in a memory of the server; allowing the control program to receive configuration parameters, operating system type and version and to generate a configuration file according to the configuration parameters, operating system type and version, acquiring an operating system file, storing the configuration file and the operating system file into a hard disk partition of the server, setting the hard disk partition as a startup disk, and guiding the server to restart from the startup disk; allowing the startup disk to prepare an installation environment according to the configuration file and the operating system file, acquiring an operating system installer from a second guide medium, and installing an operating system for the server. The configuration file is dynamically generated according to the configuration parameters, operating system type and version, so that personal installation requirements are met.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
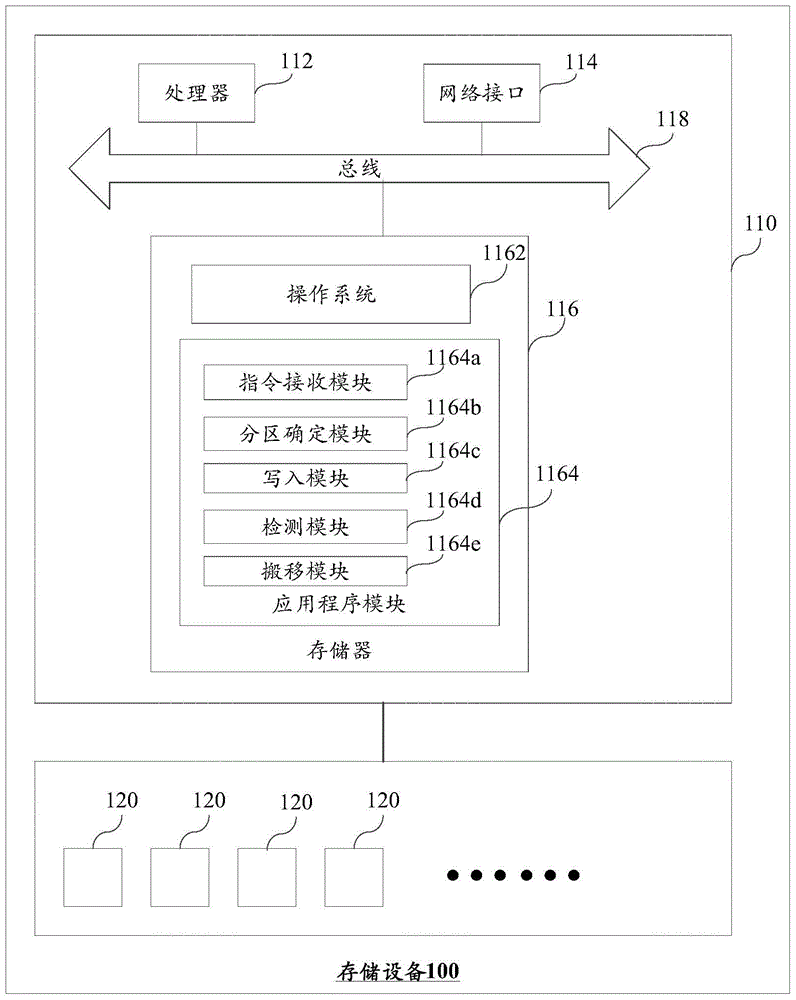
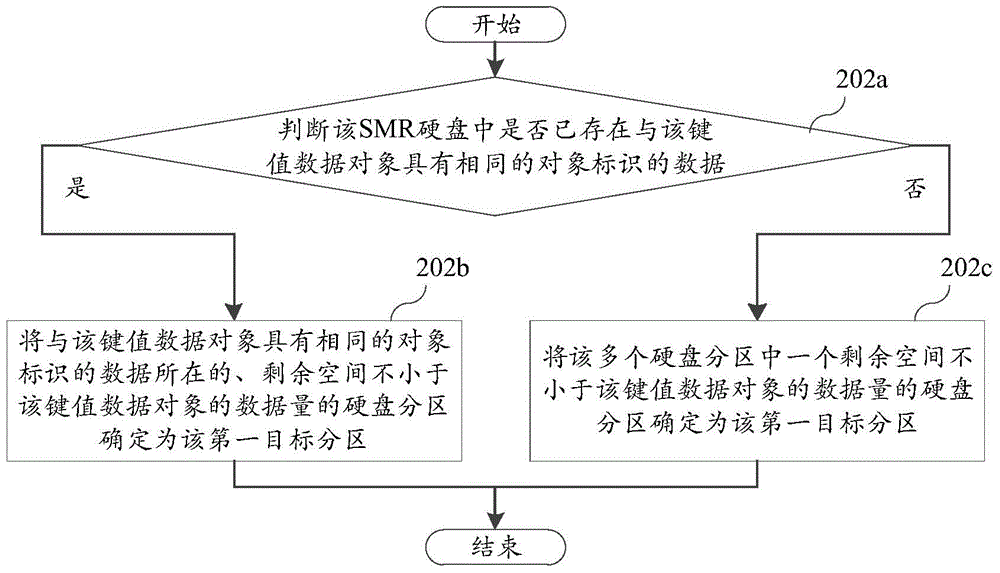
Data writing device and method
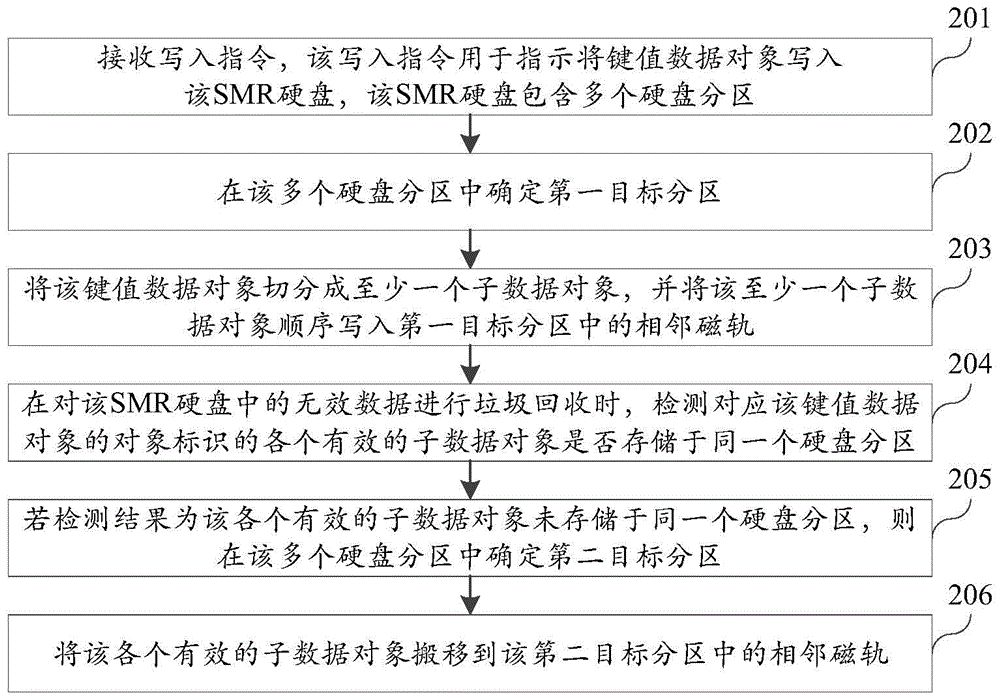
ActiveCN105677243AReduce fragmentationImprove recycling efficiencyInput/output to record carriersInvalid DataDisk partitioning
The invention discloses a data writing method, and belongs to the technical field of data storage. The method is used for a key value storage system which is built in an imbricated type magnetic recording SMR hard disk. The method comprises the steps that a writing instruction is received and used for giving an instruction for writing a key value data object into the SMR hard disk, and the SMR hard disk comprises multiple hard disk partitions; a first target partition is determined from the hard disk partitions; the key value data object is segmented into at least one sub data object, and the sub data objects are sequentially written in adjacent magnetic rails in the first target partition. Accordingly, formed invalid data is relatively concentrated when part or all of the sub data objects in the key value data object are deleted in the subsequent process, too many cavities cannot be caused on the SMR hard disk, the fragmentation degree of the SMR hard disk is relieved, and then the garbage recycling efficiency of the system is improved.
Owner:HUAWEI TECH CO LTD
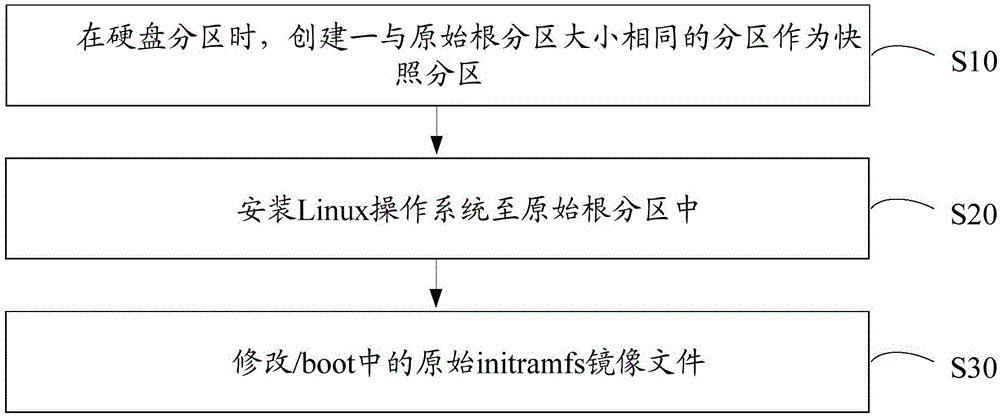
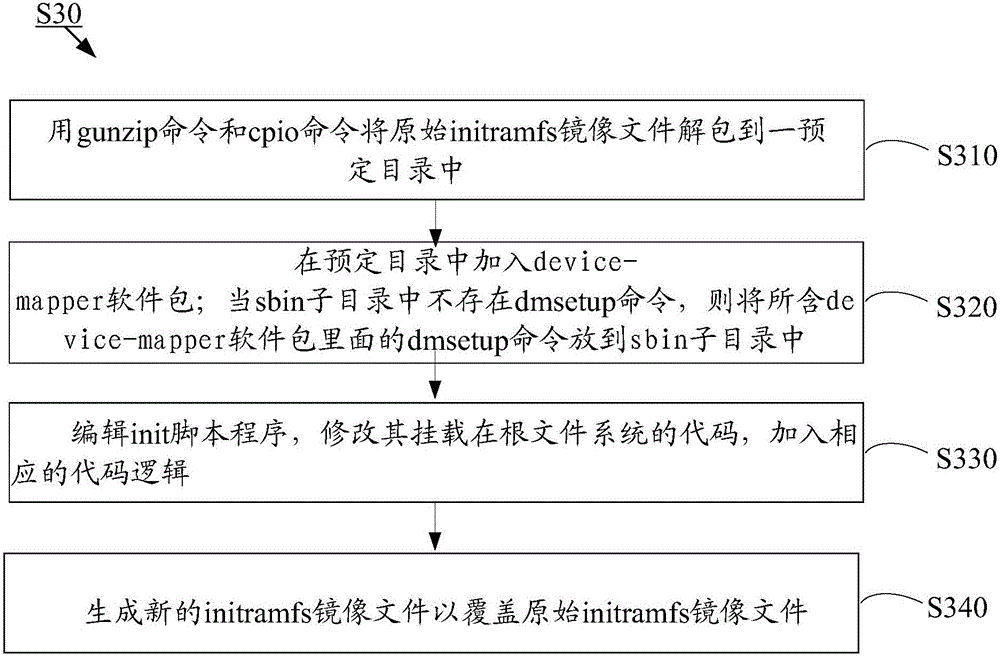
Method for ensuring normal start-up of Linux operating system
ActiveCN106776128AGuaranteed normal startupRedundant operation error correctionOperational systemGNU/Linux
The invention discloses a method for ensuring a normal start-up of a Linux operating system. The method comprises the following steps that during hard disk partition, a partition that is the same size as an original root partition is created as a snapshot partition; the Linux operating system is installed in the original root partition; an original initramfs mirror file in / boot is modified; the steps to modify the original initramfs mirror file in the / boot comprise: using a gunzip command and a cpio command to unpack the original initramfs mirror file to a predetermined catalog; adding a device-mapping software package to the predetermined catalog; when a dmsetup command does not exist in a sbin subcatalog, the dmsetup command in the device-mapper software package is put in the sbin subcatalog; editing an init script program, modifying a code of the init script program that mounts the root file system, and adding a corresponding code logic; generating a new initramfs mirror file to overwrite the original initramfs mirror file. By adopting the method, when a file system of the hard disk is damaged, the system can be automatically restored and be started up normally without manual participation, and normal start-up of the operating system is ensured.
Owner:BANGYAN TECH
Method for one-key backup and PC software system recovery
InactiveCN101403987AEasy to useWon't failProgram loading/initiatingSpecial data processing applicationsSoftware systemSystem recovery
The invention relates to a method for onekey backup and recovery of PC software system, which comprises the steps as follows: 1) PC hard disk partition is divided into at least two independent partitions which are FAT32 mode; 2) the relevant system adjustment and setting are conducted after the device driver and the common application software that PC needs are installed, then, boot.ini file is altered under the root directory in a main partition; 3) the files of GHOST compressed files, automatic batch commands, system configuration files, system backup batch commands and system recovery batch commands are copied under the root directory in the main partition; 4) an overall backup is carried out on the software system existing in PC; 5) a start up disk is made. The technician only needs to install, debug and protect the PC microcomputer software system according to the method of the invention; once the PC is turned over to the user, the technician does not need to drop in the user for on-site service. The method of the invention can be conveniently used by middle and old-aged users who have no computer professional maintenance knowledge.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
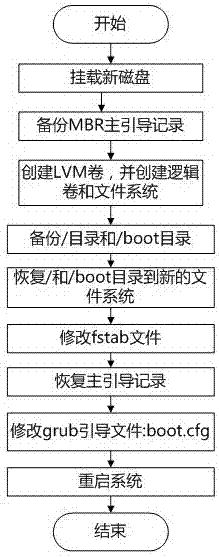
Method for realizing capacity expansion of root partitions of Kylin systems
The invention discloses a method for realizing capacity expansion of root partitions of Kylin systems, and relates to the field of system partition management. The method comprises the following steps of: mounting an external disk which has a capacity greater than a partition, which can be normally started, of a Kylin system under the system on the basis of the Kylin system, backing an MBR master boot record up to the external disk, and downloading the external disk; creating a new disk partition, a logical volume and a new file system, and creating a backup / catalog and a boot catalog to the new file system; and modifying a starting file, recovering the MRB master boot record to the logic volume and modifying a grub boot, and starting and booting the system to the new disk partition. By utilizing the method, by utilizing a logical volume management function of Linux, the external disk is utilized to start the system to carry out partition size adjustment without halt, so that the root partitions of the system are fundamentally adjusted and benefit is brought to manage stored files by the system.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
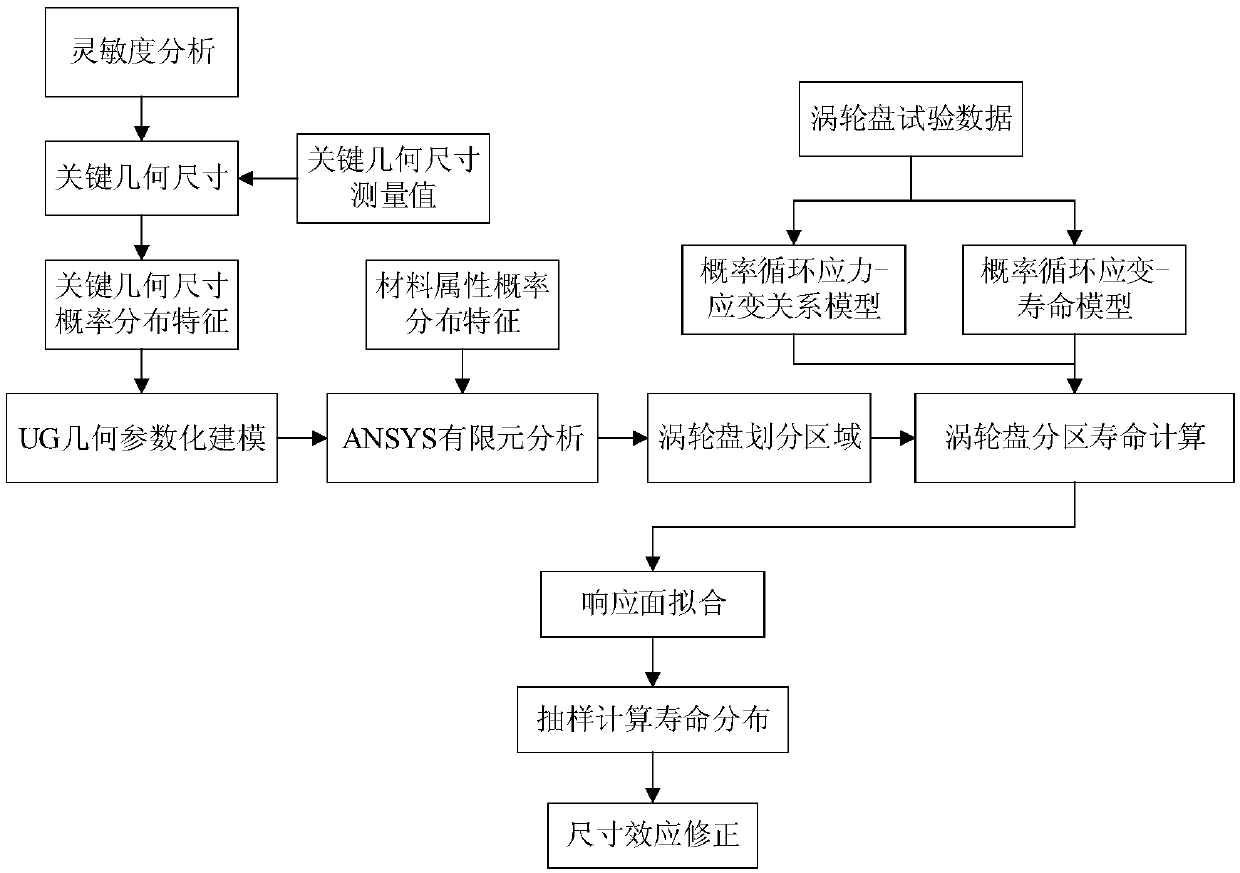
Turbine disk partitioning reliability analysis method based on size effect modification
ActiveCN108629092AAccurate lifeAccurate and reliableGeometric CADDesign optimisation/simulationRelational modelStress level
The invention relates to a turbine disk partitioning reliability analysis method based on size effect modification. The method includes the steps of firstly, simplifying a turbine disk model, analyzing the sensitivity to obtain the key geometrical size of a turbine disk, measuring the key geometrical size of the turbine disk to obtain a corresponding probability distribution feature; secondly, obtaining the material attributes of the turbine disk, and establishing a SWT probability cyclic stress-strain relation model and a strain-life model of the turbine disk; thirdly, conducting geometricalparameterization modeling on the turbine disk, analyzing finite elements, dividing areas according to the stress level and temperature distribution conditions of the turbine disk, conducting Latin hypercube sampling on the established SWT probability cyclic stress-strain relation model and the probability strain-life model to obtain the relation between random input variables and output service lives of all divided areas of the turbine disk and establish response face models, and sampling the response face models of all the divided areas through a Monte-Carlo sampling method to obtain the corresponding service life distribution and finally obtain the fatigue life and reliability of the turbine disk; fourthly, conducting size effect modification on the service life distribution of the turbine disk.
Owner:BEIHANG UNIV
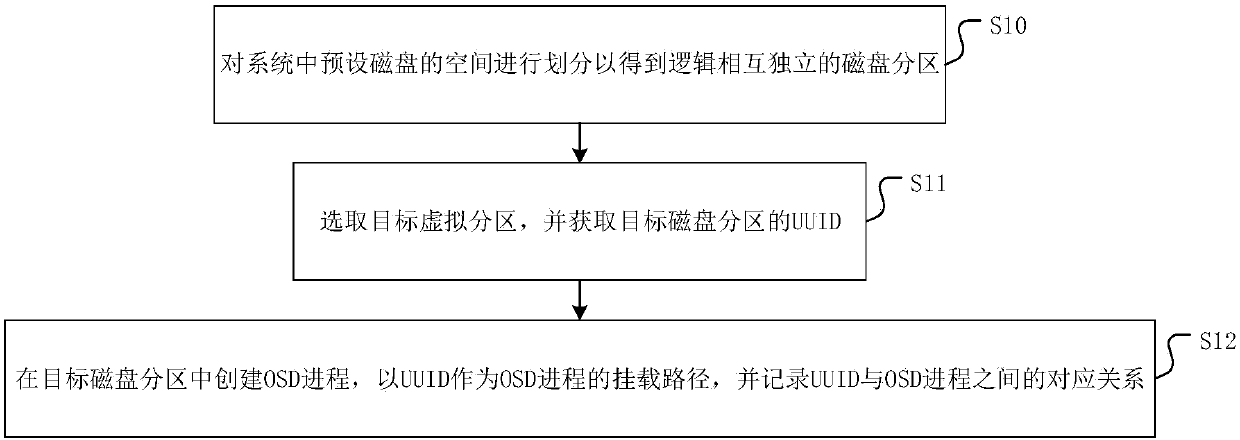
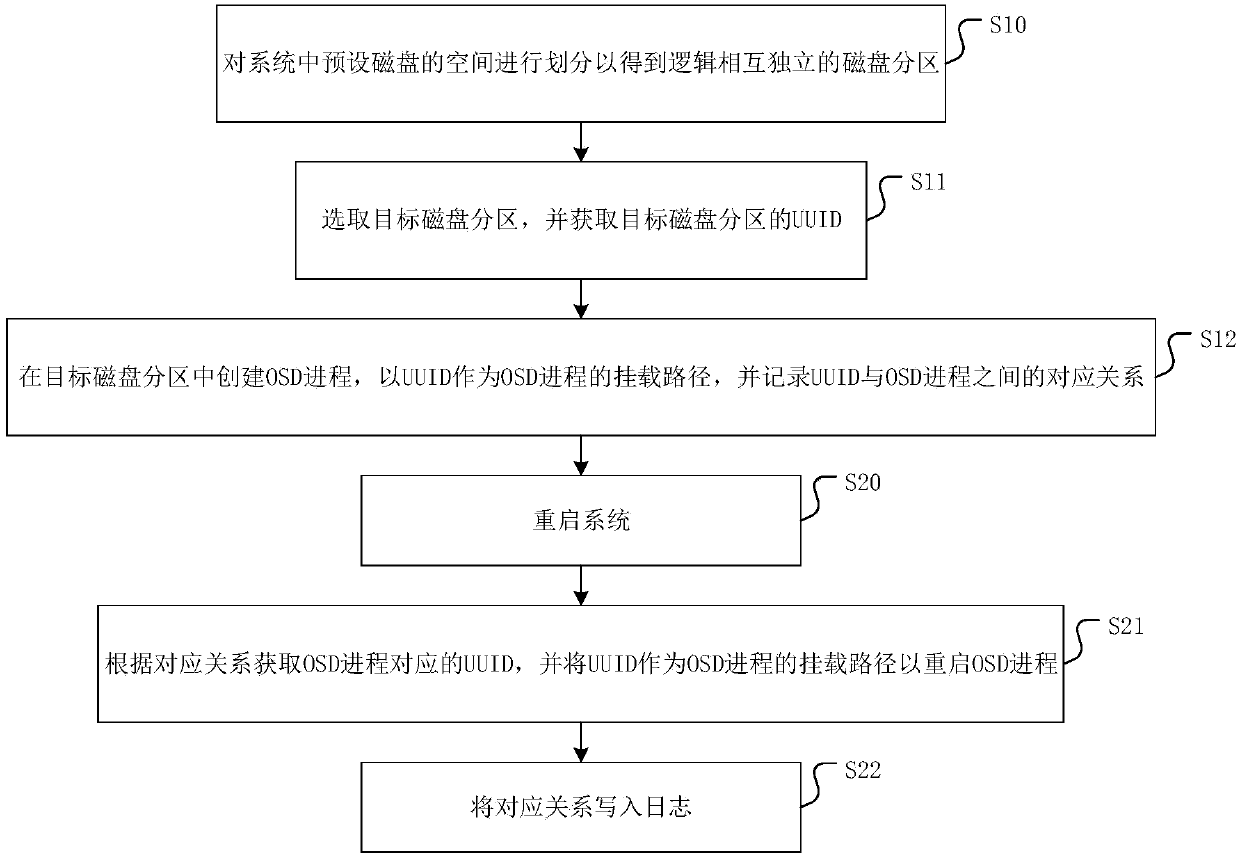
OSD process deployment method and device of distributed block storage system and medium
InactiveCN107861693AEnsure safetyGuarantee stabilityInput/output to record carriersUsabilityDisk partitioning
The invention discloses an OSD process deployment method and device of a distributed block storage system and a medium. The method comprises the steps that space of a preset disk in the system is divided to obtain disk partitions which are mutually independent logically; the target disk partition is selected, and a UUID of the target disk partition is obtained; an OSD process is built in the target disk partition, the UUID is regarded as a mount path of the OSD process, and the corresponding relationship between the UUID and the OSD process is recorded. The UUID is regarded as the mount path of the OSD process, so that a mount path of the target OSD process before system reboot is successfully found, then the stability and usability of the whole system are ensured, and security of data inthe system is guaranteed; moreover, the invention further provides the OSD process deployment device of the distributed block storage system and the medium which have the advantages.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method for backuping data through adopting dual-disk read-write operation
InactiveCN102841863ARun fastImprove robustnessMemory loss protectionRedundant operation error correctionDigital dataElectricity
The invention relates to the field of methods for processing electrical and digital data which are accessed, addressed or distributed in memory systems or architectures, and in particular relates to a method for backuping data through adopting dual-disk read-write operation. The method for backuping data through adopting dual-disk read-write operation comprises hard disk arrangement, and is characterized by further comprising the following steps of a, hard disk partition; b, master disk initiation; and c, standby disk initiation. The method has the advantages of high safety, strong reliability, quick operation speed, shortened system breakdown time and convenience in maintenance.
Owner:SHANGHAI DATATOM INFORMATION TECH CO LTD
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com