Integrity verification method and device, terminal equipment and verification server
A technology for integrity verification and terminal equipment, applied in the direction of digital data protection, etc., can solve problems such as large amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
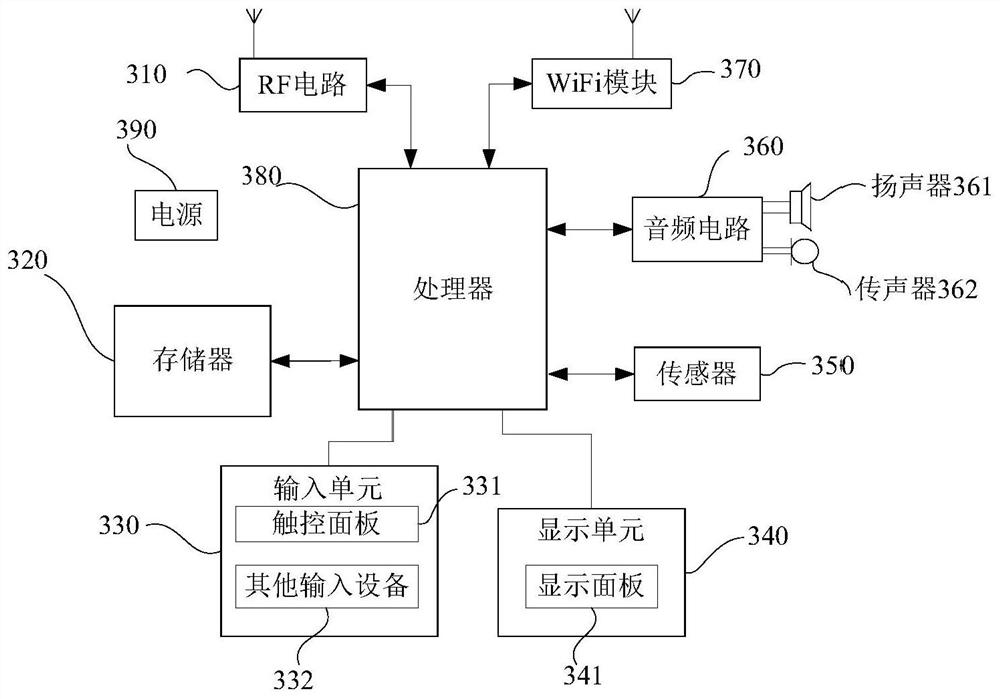
[0167] The integrity verification method provided by Embodiment 1 can be implemented on a mobile phone with the above-mentioned hardware structure / software structure, so as to perform integrity verification on the downloaded files of the mobile phone, that is, after the mobile phone downloads the file from the file server, it can be used in the application The integrity of the file is verified by the integrity verification method provided in this embodiment before, to ensure that the file downloaded by the mobile phone is a file that has not been tampered with, has a legal version, and has a traceable source. The following will combine figure 1 The integrity verification system shown in this example describes the integrity verification method provided in this embodiment in detail.
[0168] Such as Figure 5 As shown, the integrity verification method provided in this embodiment may include:
[0169] S501. Obtain the file to be verified sent by the file server and the integri...
Embodiment 2
[0217] The integrity checking method provided by Embodiment 2 can be performed in such as figure 2 The integrity verification system shown in the verification server is implemented to perform integrity verification on each terminal device, that is, the integrity verification method for each terminal device can be used to perform integrity verification on the application files in each terminal device. Check to ensure that the application files in each terminal device are files that have not been tampered with and have legal versions. The following will combine figure 2 The integrity verification system shown in this example describes the integrity verification method provided in this embodiment in detail.
[0218] Such as Figure 6 As shown, the integrity verification method provided in this embodiment may include:
[0219] S601. Acquire the integrity verification information of each terminal device, where the integrity verification information includes the initial root no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com