Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85 results about "Virtual machine introspection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
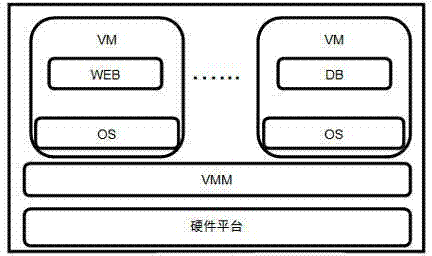
In computing, virtual machine introspection (VMI) is a technique "for monitoring the runtime state of a system-level virtual machine (VM)", which is helpful for debugging or forensic analysis. The term introspection in application to the virtual machines was introduced by Garfinkel and Rosenblum. They invented an approach for "protecting a security application from attack by malicious software" and called it VMI. Now VMI is a common term for different virtual machine forensics and analysis methods. VMI-based approaches are widely used for security applications, software debugging, and systems management.
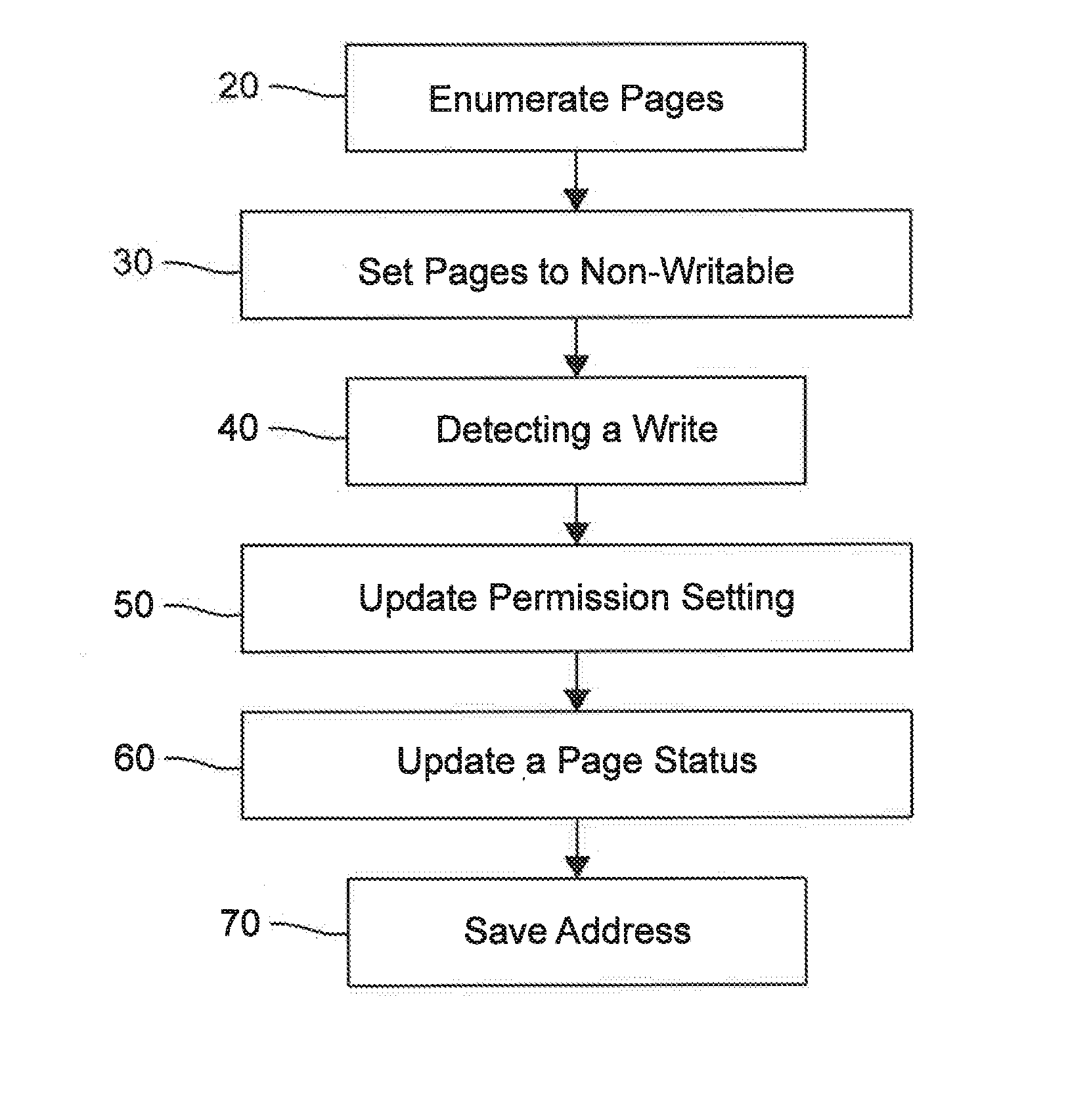
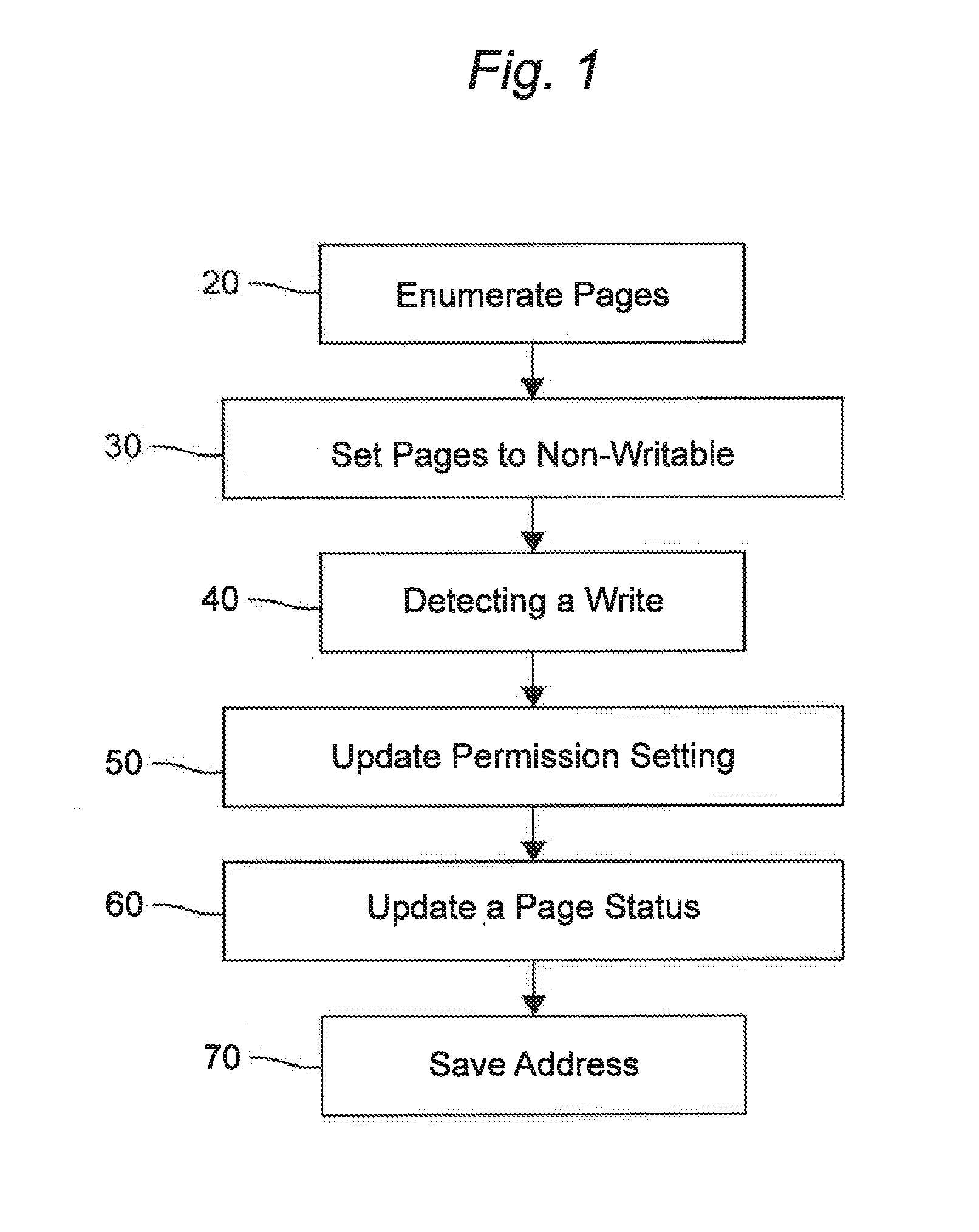
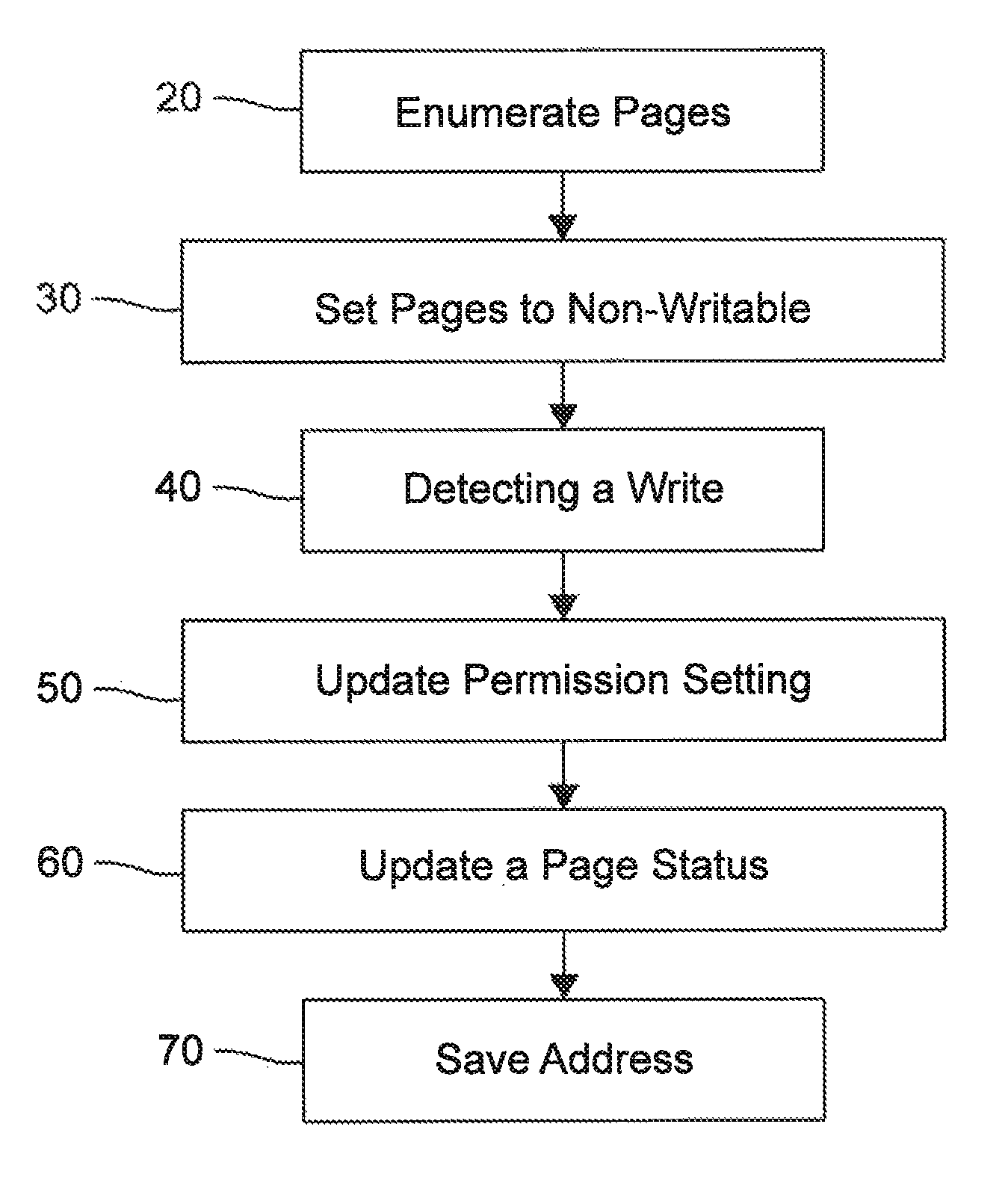
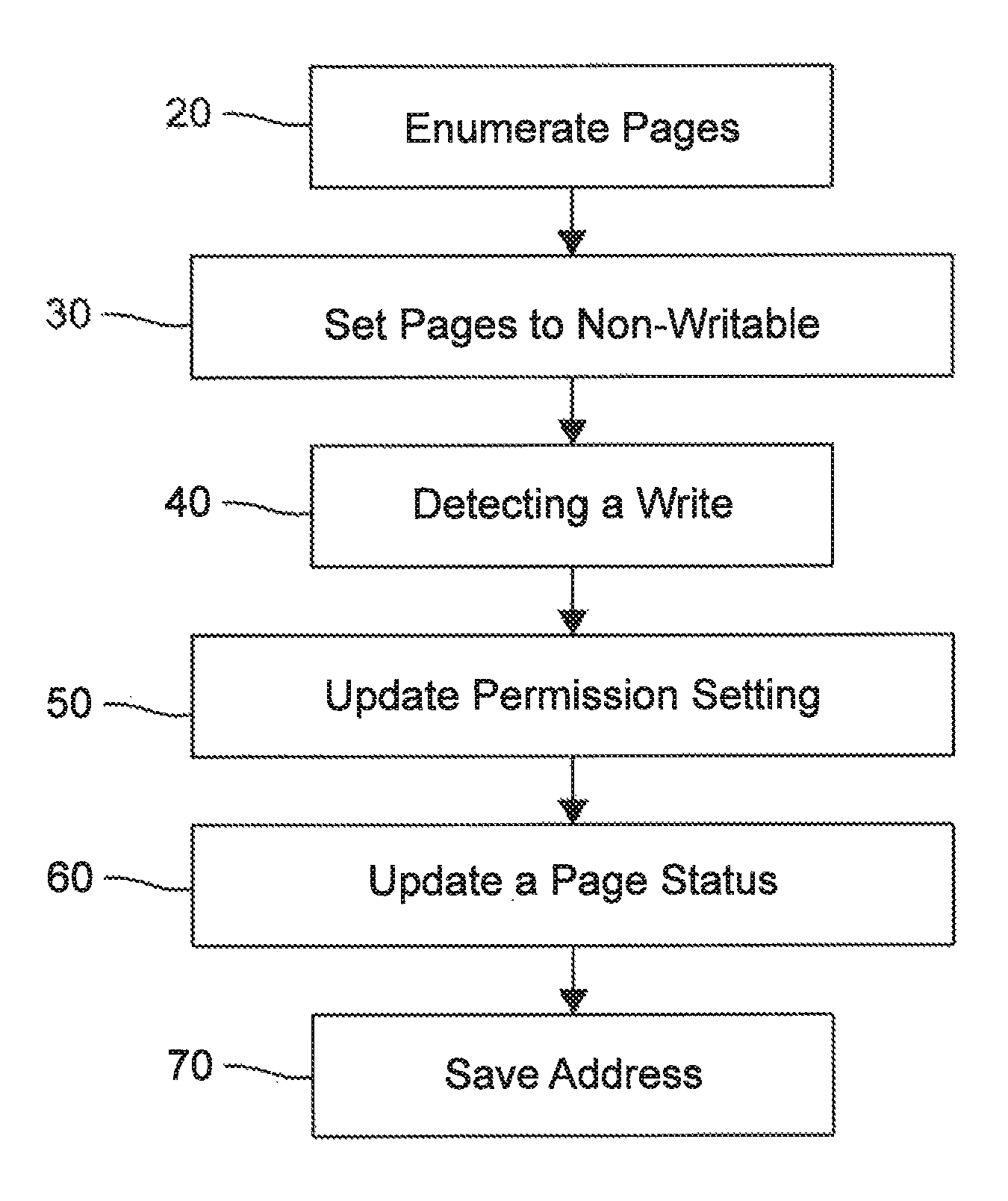
System and method for the programmatic runtime de-obfuscation of obfuscated software utilizing virtual machine introspection and manipulation of virtual machine guest memory permissions
ActiveUS20140189882A1Digital data processing detailsAnalogue secracy/subscription systemsObfuscationVirtual machine introspection
A system and method operable to programmatically perform runtime de-obfuscation of obfuscated software via virtual machine introspection and manipulation of virtual machine guest memory permissions.
Owner:FIREEYE SECURITY HLDG US LLC
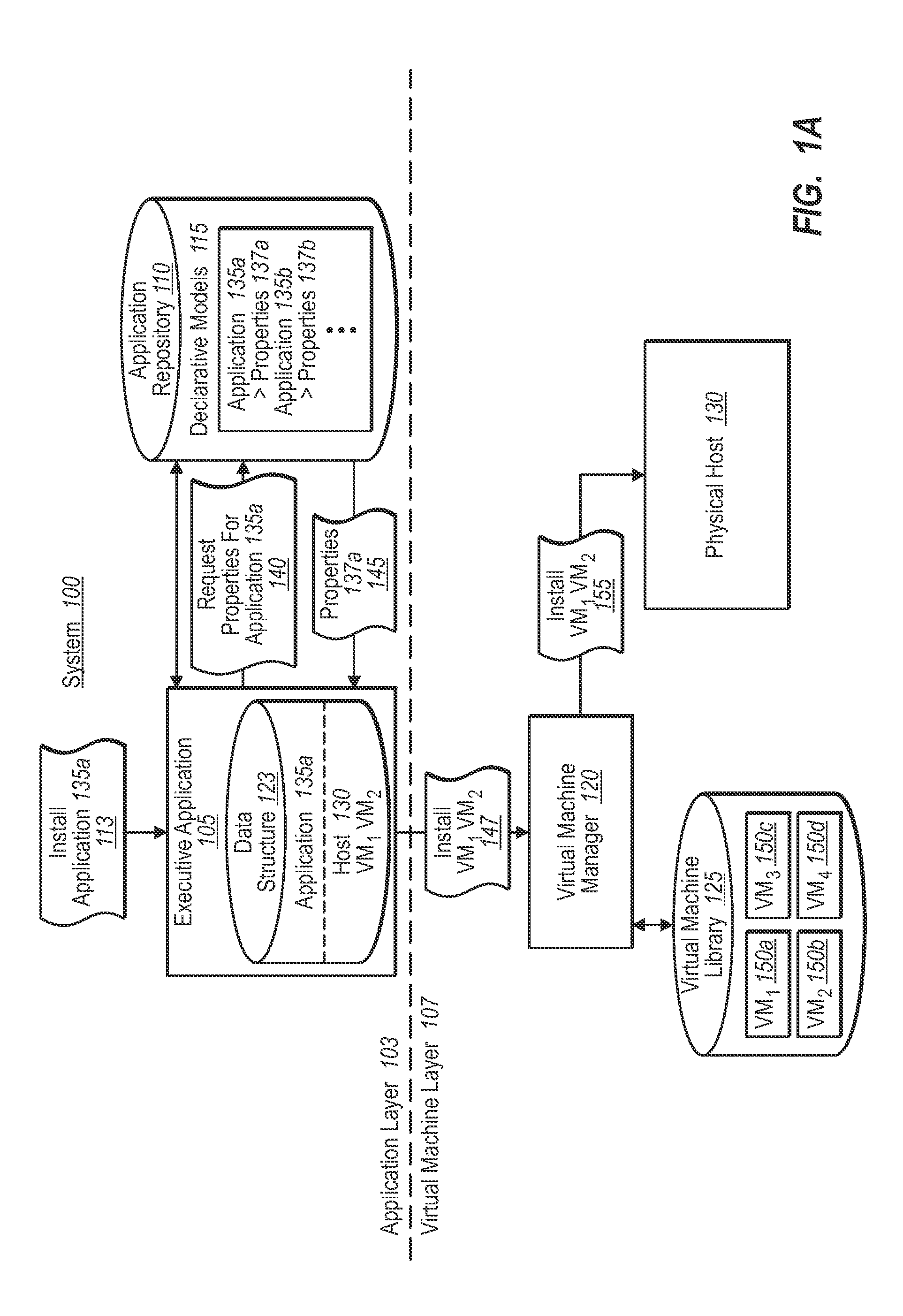
Optimized virtual machine specification for provisioning application specific runtime environment
ActiveUS8219987B1Resource allocationProgram loading/initiatingVirtual machine introspectionApplication software
Systems and methods of executing an application in an application specific runtime environment are disclosed. The application specific runtime environment is defined by an application environment specification to include a minimal or reduced set of software resources required for execution of the application. The application environment is generated by determining software resource dependencies and is optionally used to provision the application specific runtime environment in real-time in response to a request to execute the application. Use of the application specific runtime environment allows the application to be executed using fewer computing resources, e.g., memory. The application specific runtime environment is optionally disposed within a virtual machine. The virtual machine may be created in response to the request to run the executable application and the virtual machine may be automatically provisioned using an associated application environment specification.
Owner:VMWARE INC
System and method for the programmatic runtime de-obfuscation of obfuscated software utilizing virtual machine introspection and manipulation of virtual machine guest memory permissions
ActiveUS9459901B2Platform integrity maintainanceProgram/content distribution protectionObfuscationVirtual machine introspection
A system and method operable to programmatically perform runtime de-obfuscation of obfuscated software via virtual machine introspection and manipulation of virtual machine guest memory permissions.
Owner:FIREEYE SECURITY HLDG US LLC
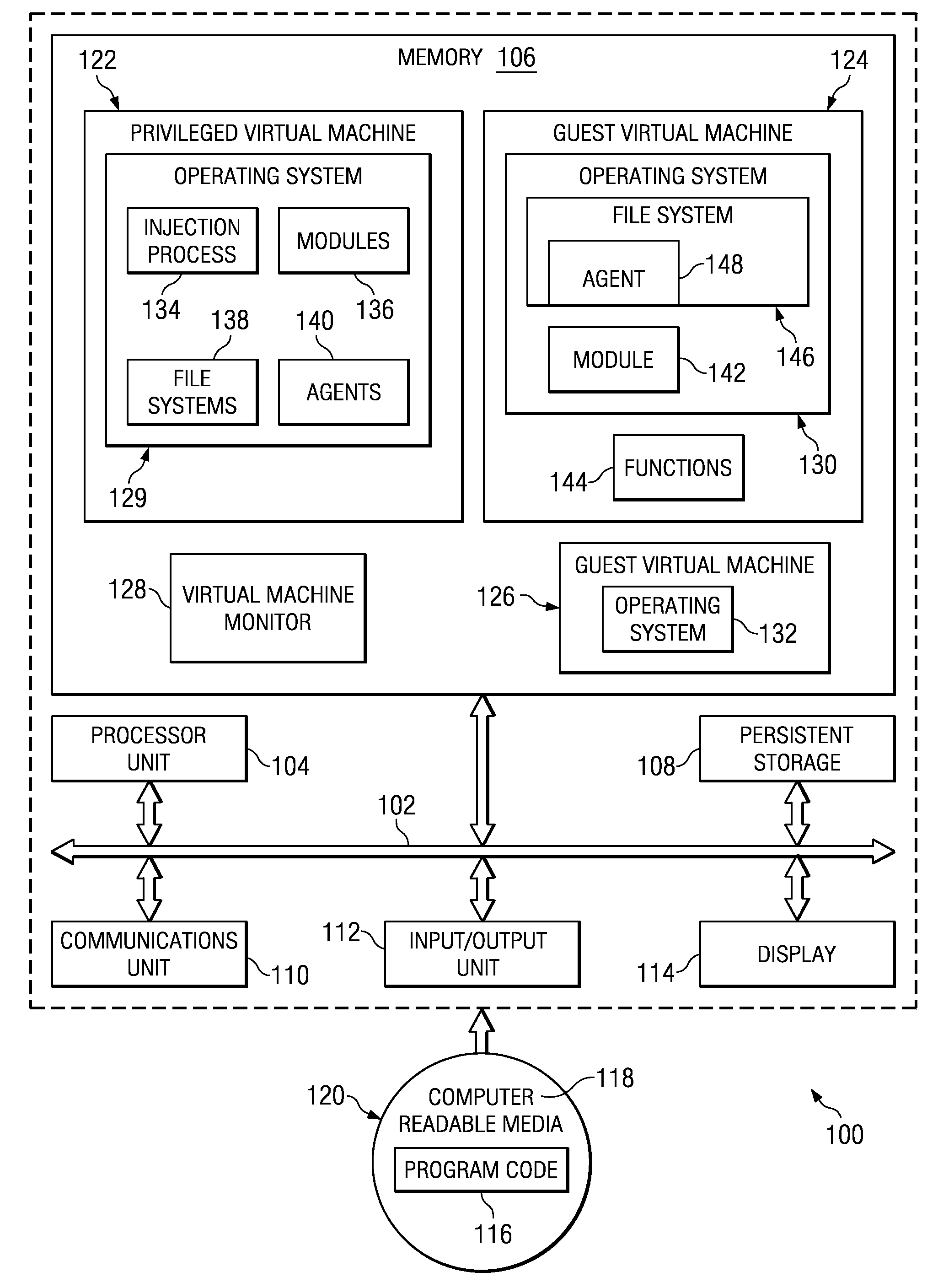
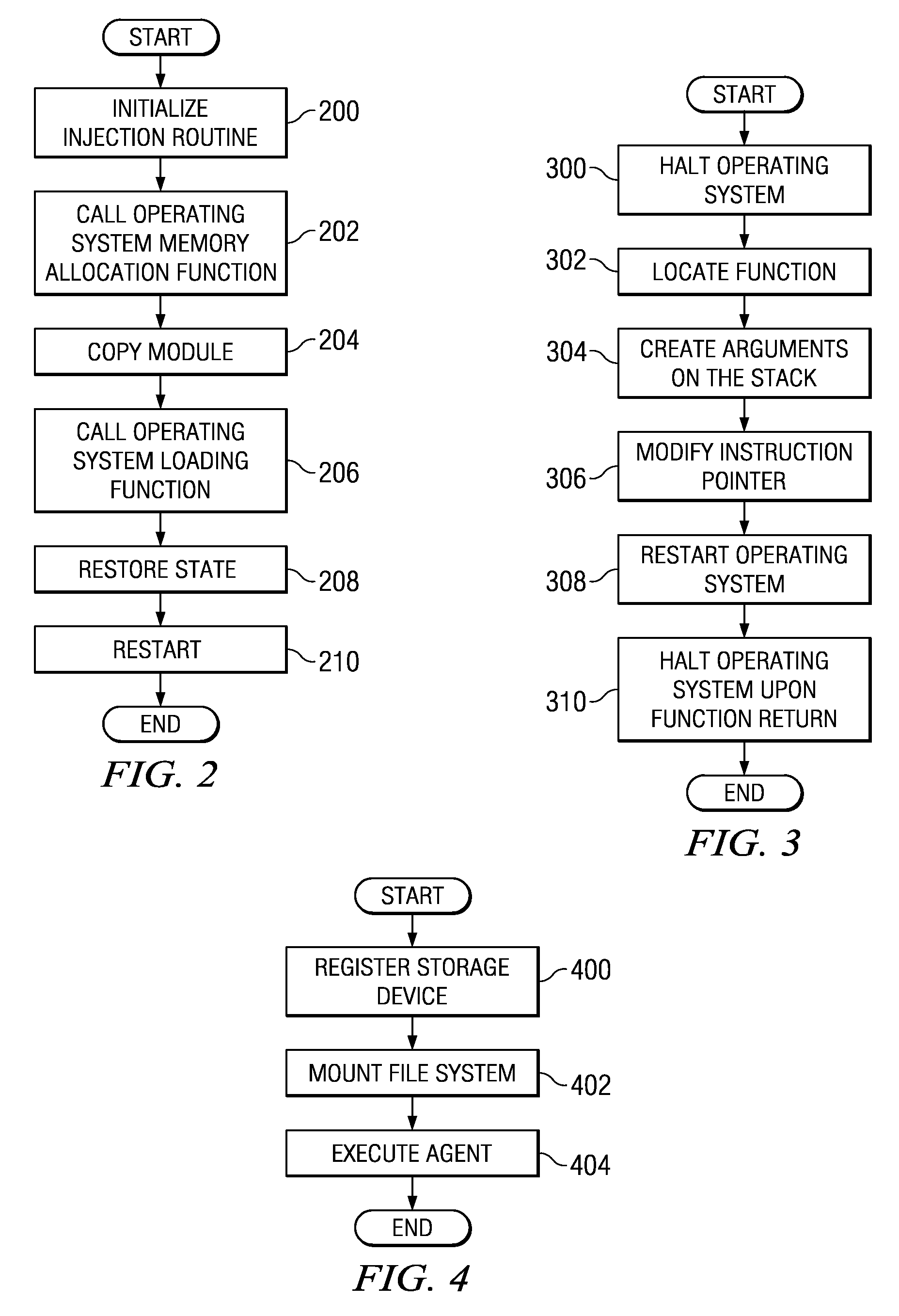
Context Agent Injection Using Virtual Machine Introspection
A computer implemented method, apparatus, and computer usable program code for executing a process within a virtual machine. A module is injected into an operating system for the virtual machine to form an injected module. The injected module is executed to load an agent process within an application space within the virtual machine. Execution of the agent process is initiated by the injected module.
Owner:KYNDRYL INC
Microprocessor system for virtual machine execution
ActiveUS20120079479A1Software simulation/interpretation/emulationMemory systemsVirtualizationMode control
A processor includes guest mode control registers supporting guest mode operating behavior defined by guest context specified in the guest mode control registers. Root mode control registers support root mode operating behavior defined by root context specified in the root mode control registers. The guest context and the root context are simultaneously active to support virtualization of hardware resources such that multiple operating systems supporting multiple applications are executed by the hardware resources.
Owner:MIPS TECH INC
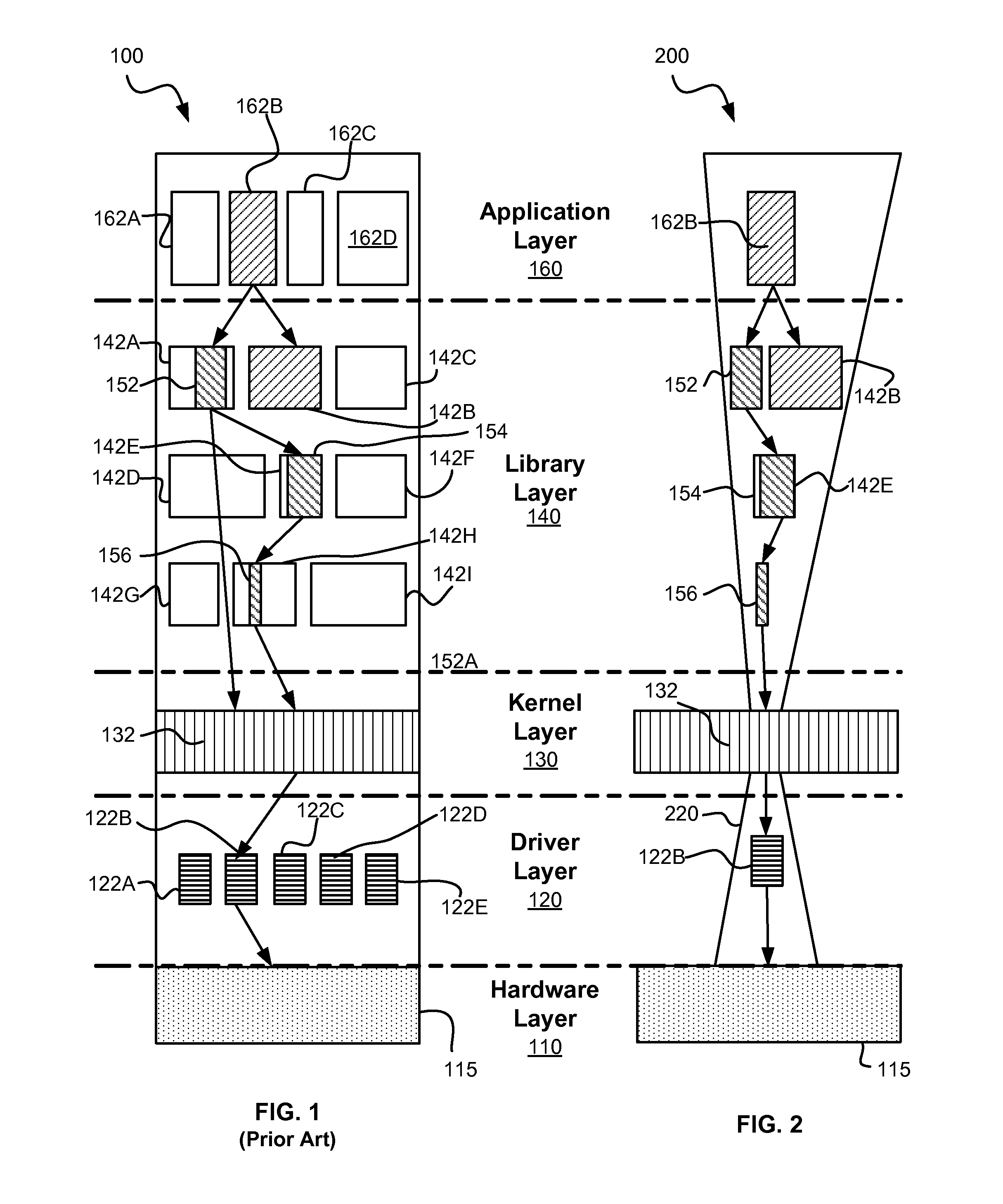
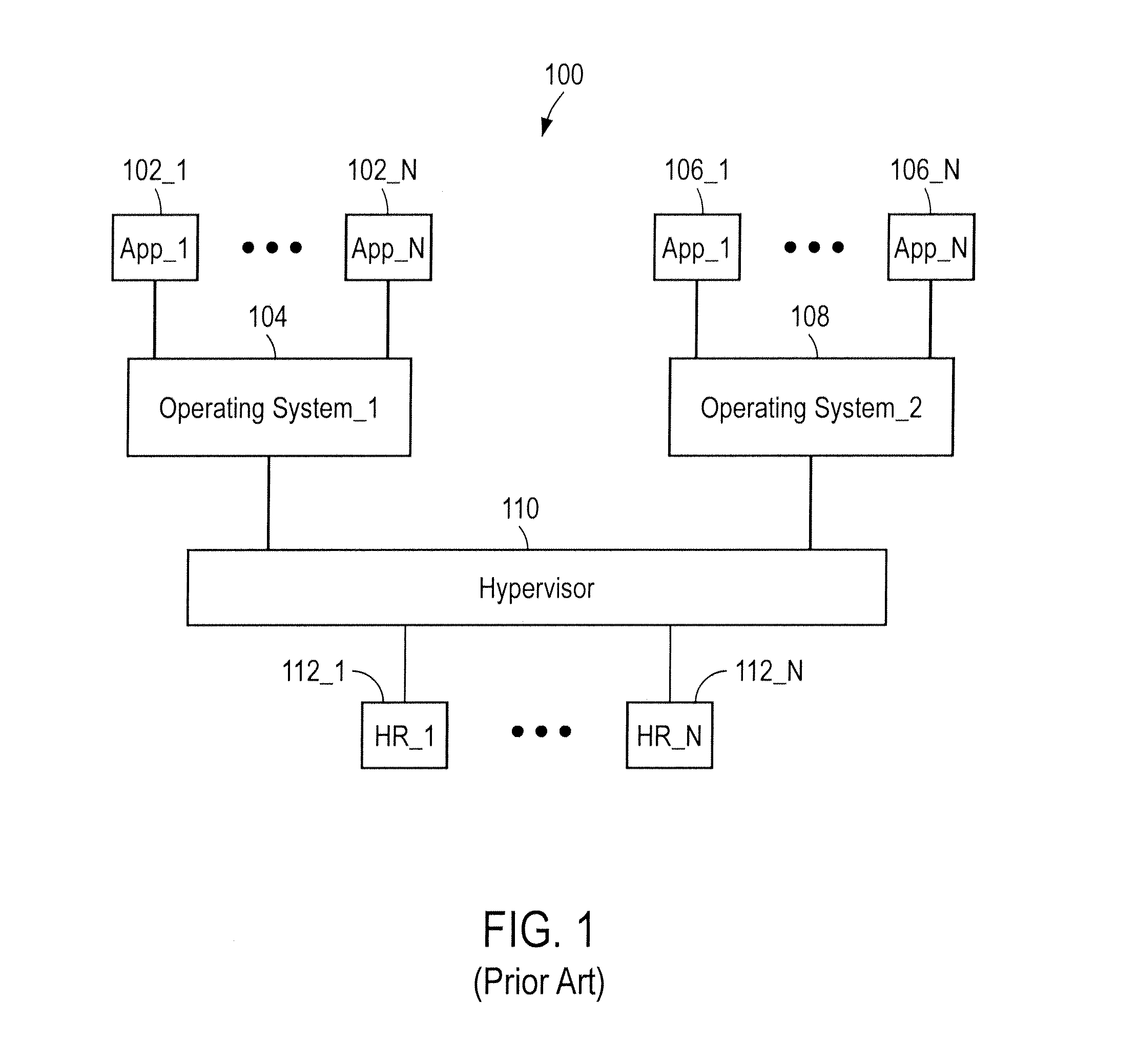
Synchronizing virtual machine and application life cycles
ActiveUS8161479B2Create efficientlyGuaranteed uptimeProgram loading/initiatingSoftware simulation/interpretation/emulationVirtual machine introspectionProtocol Application
A virtual environment can be configured to coordinate life cycles of virtual machines and application programs executing therein. In one implementation, the virtual environment includes an application layer and a virtual machine layer. The application layer communicates with the virtual machine layer to coordinate and directs virtual machine creation and deletion in a coordinated fashion with application programs. For example, the application layer receives a request to initiate an application program. The application layer determines from associated application properties the type and / or number of virtual machines to be created. The application layer then directs creation of the appropriate virtual machines (through the virtual machine layer), and further directs installation of the requested application programs therein. When detecting removal of the application program from the created virtual machines, the application layer can automatically direct removal or decommissioning of the corresponding virtual machine.
Owner:MICROSOFT TECH LICENSING LLC
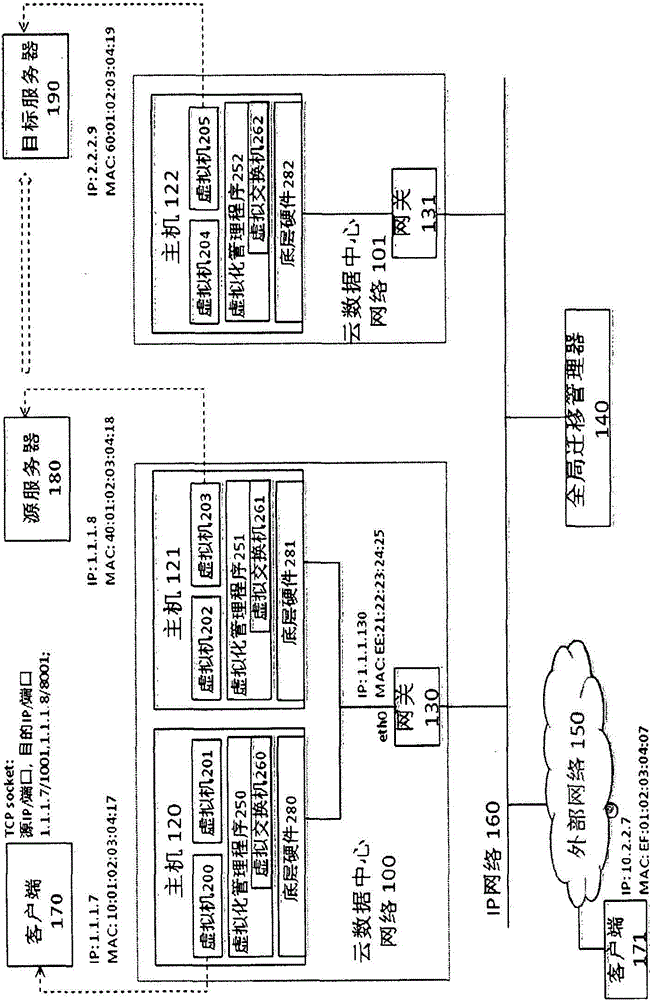
Global migration manager, gateway, virtual machine migration system and method thereof
InactiveCN105208048AGuaranteed continuityGuaranteed service qualityData switching networksGlobal migrationNetwork addressing
The invention provides a global migration manager, a gateway, a virtual machine migration system and a method thereof. The business continuity and the cloud service quality are ensured in the migration among different subnets. The global migration manager comprises a memory used for storing a virtual machine information management table of global unique virtual machine identification information; a virtual machine migration controller which is used for receiving a virtual machine migration request and notifying a source subnet to migrate a virtual machine in the source subnet to a target subnet and is further used for receiving a virtual machine migration completion notification, updating the virtual machine information management table and generating a virtual machine destination address transition request according to the global unique virtual machine identification information, a network address of the virtual machine before the migration and a network address of the virtual machine after the migration; and a gateway controller used for sending the generated virtual machine destination address transition request to each gateway and sending a false ARP update request message to the gateway of the source subnet. By adopting the technical scheme, the business continuity and the cloud service quality are ensured.
Owner:HITACHI LTD
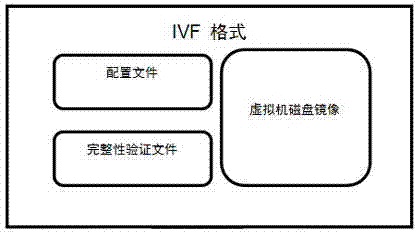
Virtual machine template IVF storage method
InactiveCN103970908AAvoid repetitionEasy to storeSoftware simulation/interpretation/emulationSpecial data processing applicationsOperational systemWeb service
The invention provides a virtual machine template IVF storage method. Different application types of virtual machines, such as WEB service, database service and load balance, are mounted on an established virtual platform according to a requirement, and a virtual machine operating system, an application program, a configuration environment and the like are mounted. After an environment is established, a function demand of a user in a certain aspect, such as website construction, is basically met. A system comprises a virtual machine template configuration file (1), a completeness checking file (2) and a virtual machine magnetic disk mirror image file (3). If the user still needs to deploy a similar environment, the user only needs to configure the current virtual machine into a use template so as to avoid repeated operation of the previous work, and then a virtual machine is established according to the template, so that the similar environment can be established quickly.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
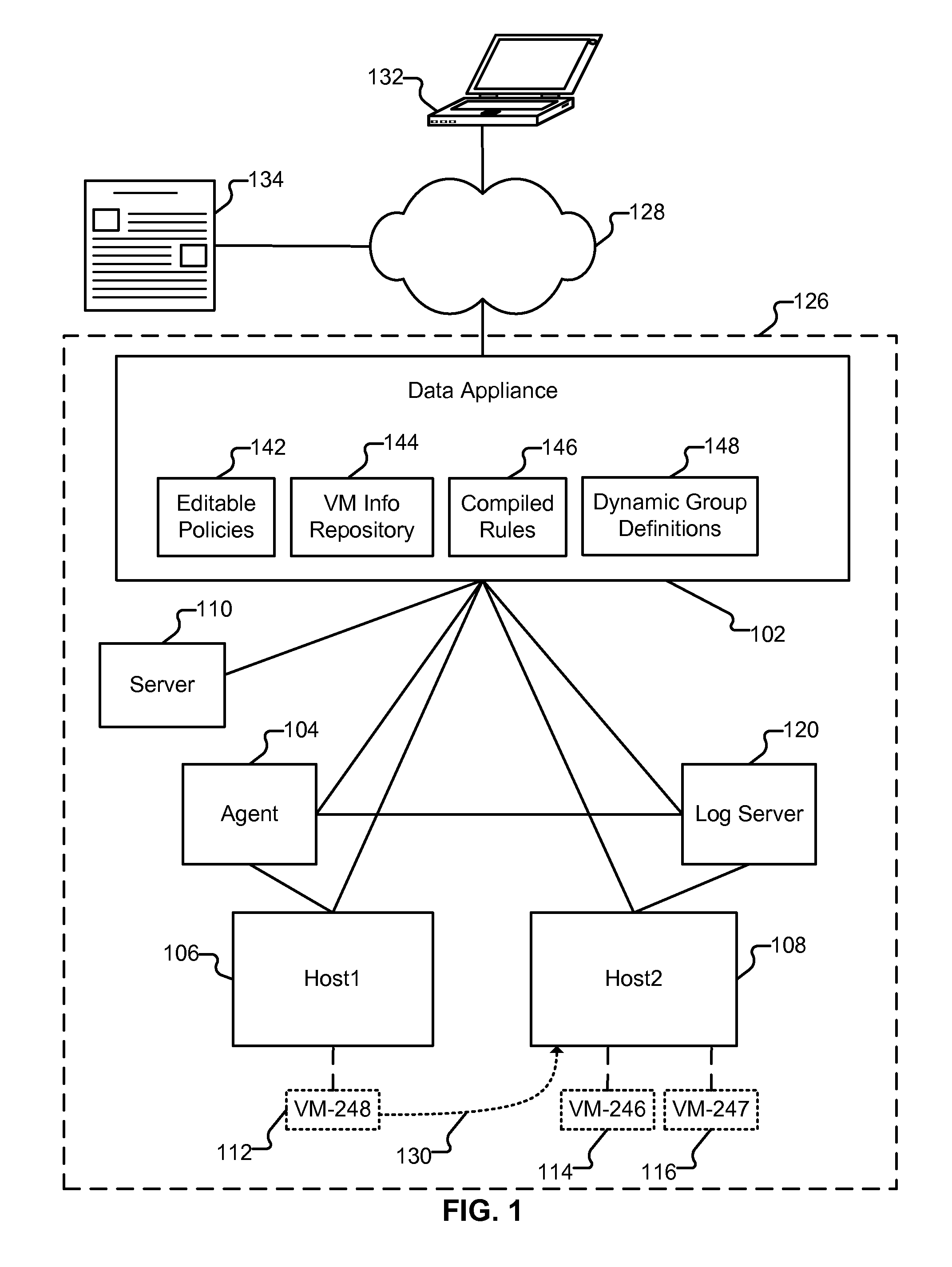
Policy enforcement in virtualized environment
ActiveUS9047109B1Multiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationVirtual machine introspection
Policy enforcement in an environment that includes virtualized systems is disclosed. Virtual machine information associated with a first virtual machine instance executing on a host machine is received. The information can be received from a variety of sources, including an agent, a log server, and a management infrastructure associated with the host machine. A policy is applied based at least in part on the received virtual machine information.
Owner:PALO ALTO NETWORKS INC
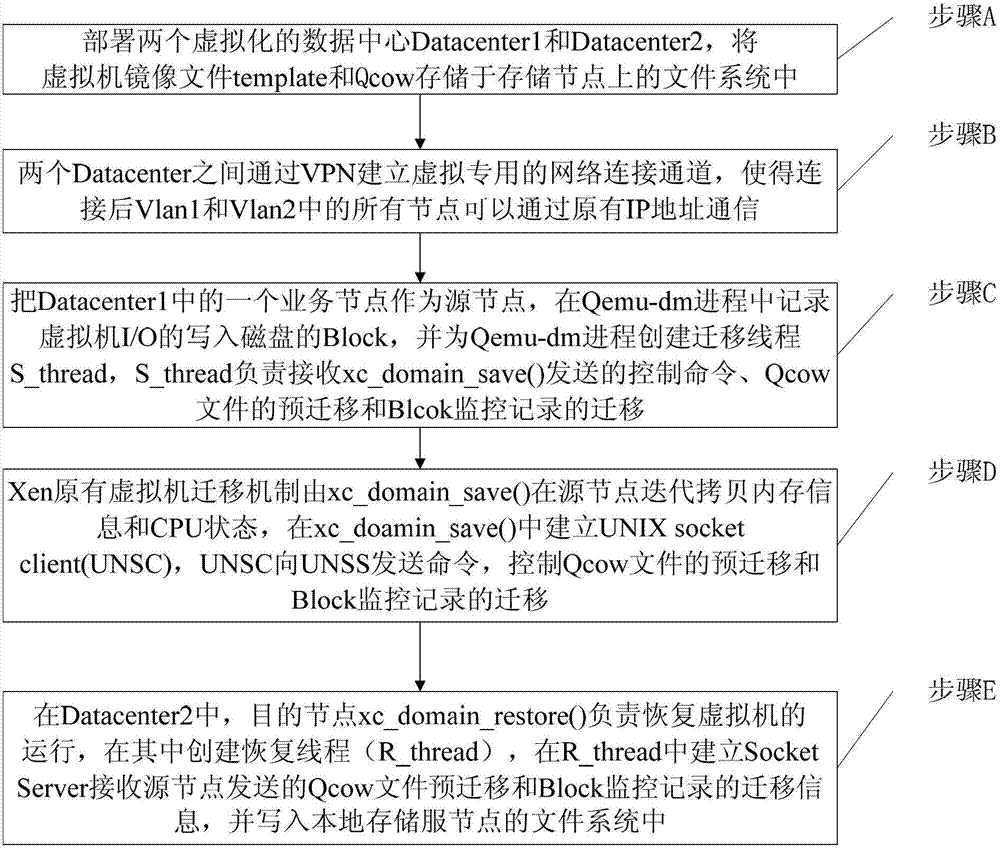
Virtual machine on-line transfer method across virtualization data centers
InactiveCN103095834ARealize online migrationReduce data volumeNetworks interconnectionSoftware simulation/interpretation/emulationVirtualizationBridge pattern
The invention provides a virtual machine on-line transfer method across virtualization data centers. The method includes that step 1, a plurality of virtualization data centers are deployed on a wide area network (WAN), and each virtual machine mirror file is divided into a template and user private data files, step 2, the virtualization data centers are connected through a virtual private network (VPN) of a two-tier bridge pattern, step 3, dirty blocks written into a disk every time are monitored in a virtual machine input / output (I / O) drive course on a source node, a transfer thread is created for the drive course, and the transfer thread pre-transfers the user private data files and transfers monitoring records of the dirty blocks, step 4, a transfer course of a virtual machine on the source node controls the pre-transfer and the transfer of the monitoring record, and step 5, the execution sequence of a destination node recovery course of the virtual machine is changed, a recovery thread is created for the recovery course, and the recovery thread receives information about the pre-transfer and the transfer of the monitoring records and writes the information into a storage node. The virtual machine on-line transfer method across the virtualization data centers can achieve dynamic mapping of virtual machines and resources among the plurality of virtualization data centers.
Owner:SHANGHAI YINGLIAN SOMATOSENSORY INTELLIGENT TECH CO LTD
Virtual machine migration prediction method based on SLA
InactiveCN105607948ANo shortage of resourcesProgram initiation/switchingResource allocationService-level agreementPrediction algorithms
The invention relates to the technical field of cloud computing, in particular to a virtual machine migration prediction method based on an SLA (Service Level Agreement). According to the method, firstly, the resource use condition of each virtual machine is monitored once every a period of time; then, after the curve fitting by a mathematical method on the basis of monitoring data, an equation of the curve is obtained; then, the resource quantity used by the virtual machines at the next time interval can be predicted; next, the resource use quantity at the next time interval is compared to the threshold value specified in the SLA; if the resource use quantity at the next time interval exceeds the threshold value, the virtual machine is likely to be about to overload; otherwise, the coming of the next monitoring time interval is waited; and finally, if the overload condition occurs, the virtual machine is migrated to an idle host. The virtual machine migration prediction method based on the SLA provided by the invention has the advantages that an active virtual machine migration strategy is realized through actively predicting the resource use trend of the virtual machine; the problem that the SLA cannot be met after the migration by a conventional migration strategy is solved; and the method can be used for virtual machine migration.
Owner:G CLOUD TECH
Virtualization implementing method for Power server
ActiveCN102981888ASimplify the deployment processSimplify configuration workSoftware simulation/interpretation/emulationVirtualizationOperational system
A virtualization implementing method for a Power server includes the steps of enabling virtualization management software to be directly installed in a virtual machine input / output (I / O) server; enabling at least one integrated virtualization manager (IVM) to be used as a platform and then to be registered to virtualization management software (Power Director); using commands supplied by the virtual machine I / O server and each IVM to create a virtual machine; enabling a preset installing module to automatically install in the created virtual machine through an image management function according to demands of a user and enabling a configuration file, an operating system, a network information configuration of the virtual machine to be completed. The virtualization implementing method for the Power server does not need to singly be supplied with another host machine or the virtualization management software so as to save host machine source and largely simplify deployment and configuration of the virtualization management software, and improve working efficiency of managers.
Owner:BEIJING TEAMSUN TECH
Hypervisor and virtual machine protection
ActiveUS20170200000A1Digital data authenticationPlatform integrity maintainanceDigital signatureComputerized system
A computer-implemented method, according to one embodiment, includes receiving a request for a hypervisor to run a virtual machine; determining, using a processor, whether the virtual machine is authorized to run using a data structure having metadata about properties of the virtual machine; determining, using the processor, whether the hypervisor is authorized to run the virtual machine using a digital signature of the data structure; and running the virtual machine on a computer system using the hypervisor in response to determining that the virtual machine is authorized to be run and that the hypervisor is authorized to run the virtual machine. Other systems, methods, and computer program products are described in additional embodiments.
Owner:INT BUSINESS MASCH CORP
Monitoring system and method in virtual machine environment
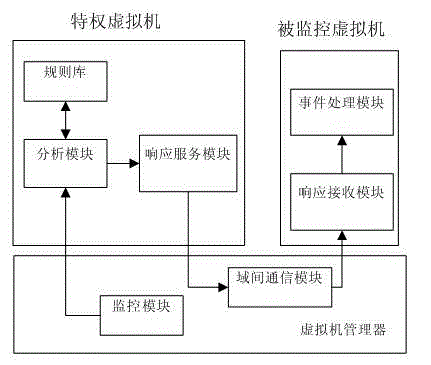
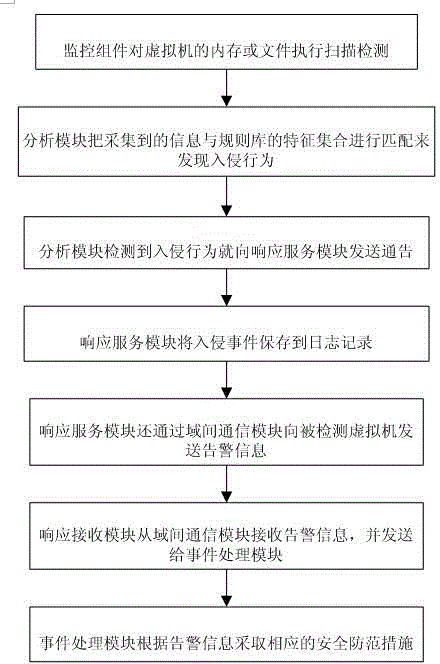
InactiveCN104866407AManage and control resourcesEfficient detectionHardware monitoringPlatform integrity maintainanceMonitoring systemVirtual machine introspection
The invention provides a monitoring system and method in a virtual machine environment. The system comprises a monitoring module, an inter-domain communication module, a rule base, an analyzing module, a response service module, a response accepting module, an event processing module and the like. The monitoring system and method in the virtual machine environment is used for security protection of the virtual machine running environments of users, can manage and control resources used by virtual machines or even monitor processes inside the virtual machines, and also, can correct content of virtual machine disks of the virtual machines, thereby ensuring the monitoring reliability when the monitoring module is deployed inside a virtual machine manager; meanwhile, combined with the virtual machine introspection technology, the monitoring system and method in virtual machine environment can effectively detect the kernel space of monitored virtual machine and further avoid intrusion.
Owner:SHANDONG ZHONGFU INFORMATION IND
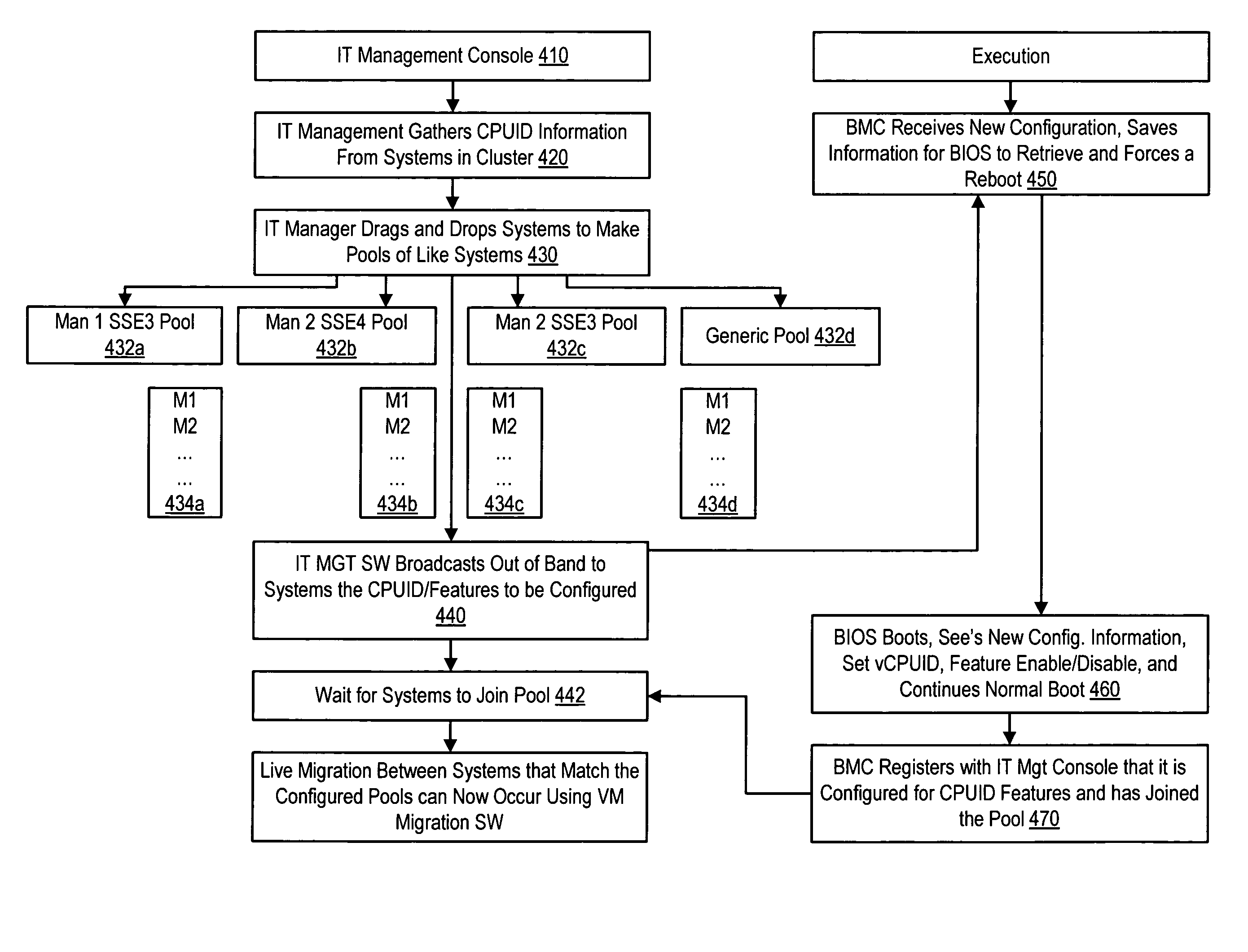
Virtual machine migration between processors having VM migration registers controlled by firmware to modify the reporting of common processor feature sets to support the migration
ActiveUS8127296B2General purpose stored program computerMultiprogramming arrangementsOperational systemFeature set
Owner:DELL PROD LP
Data wiping system in virtualization environment and method thereof
ActiveCN103996003ANo effect on operationOperation impactDigital data protectionPlatform integrity maintainanceVirtualizationUser privacy
The invention relates to a data wiping system in a virtualization environment and a method thereof, and belongs to the field of data safety and user privacy in cloud computing. Based on a Xen virtualization framework, the data wiping system comprises a process monitoring module, a control module, a virtual machine introspection module and a data wiping module. The control module, the virtual machine introspection module and the data wiping module are deployed in a management field, and the process monitoring module is deployed in a virtual machine manager, namely a VMM kernel. The data wiping system in the virtualization environment and the method thereof are used for reducing the threats to sensitive data stored in an internal storage when a user client operates, a time window which is attacked by the sensitive data is shortened at a possibly small cost, and the security of the sensitive data in the user client is guaranteed.
Owner:AVICIT CO LTD
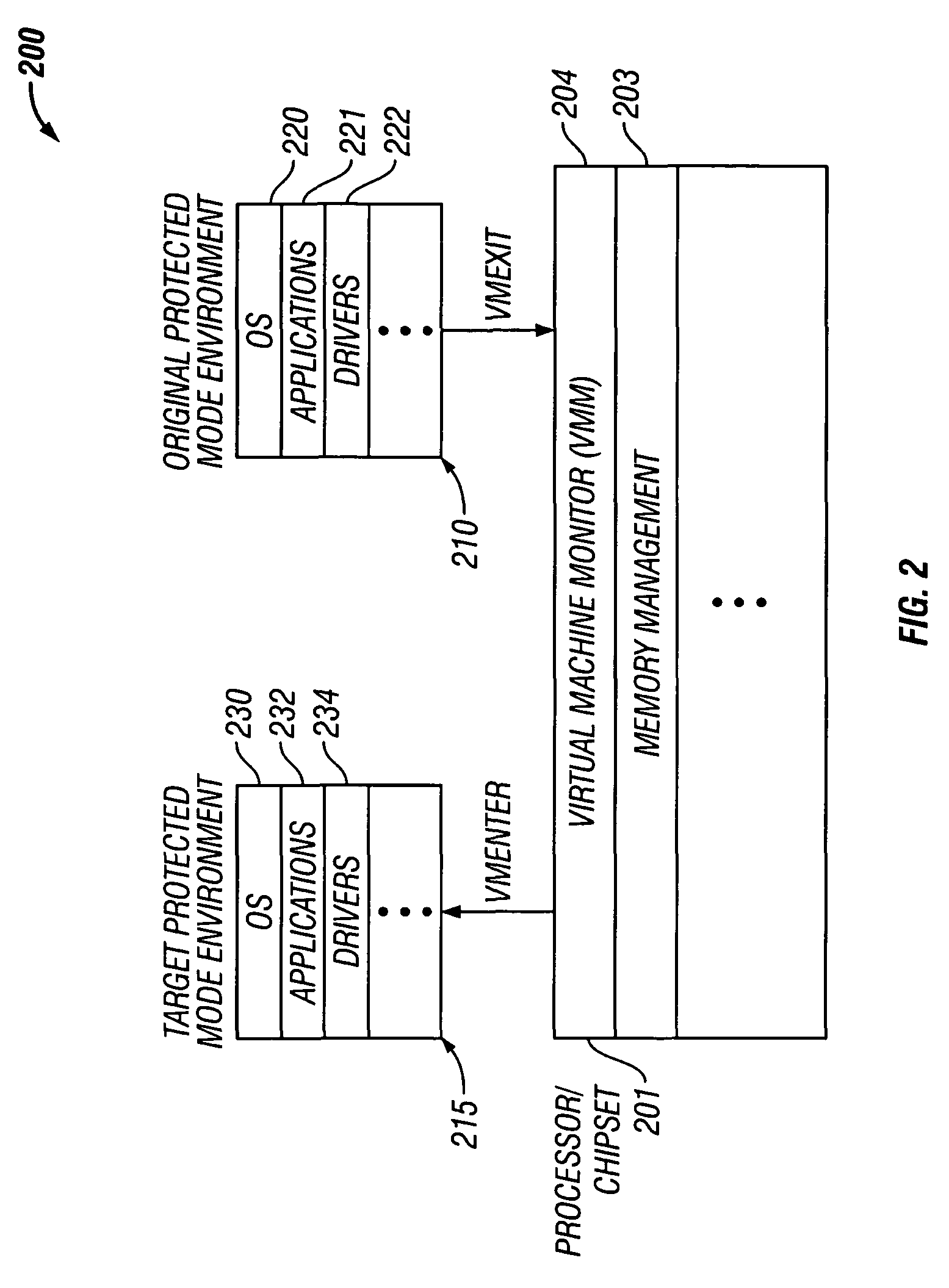
Switching between protected mode environments utilizing virtual machine functionality
InactiveUS8024730B2User identity/authority verificationMultiprogramming arrangementsVirtual machine introspectionProtected mode
Owner:INTEL CORP
Moving Target Defense for Distributed Systems
InactiveUS20180332073A1Maximizing costMinimizing probability of successfulProgram initiation/switchingTransmissionOperational systemRobin Sequence
An apparatus and method defends against computer attacks by destroying virtual machines on a schedule of destruction in which virtual machines are destroyed in either a random sequence or a round-robin sequence with wait times between the destruction of the virtual machines. Also, each virtual machine is assigned a lifetime and is destroyed at the end of its lifetime, if not earlier destroyed. Destroyed virtual machines are reincarnated by providing a substitute virtual machine and, if needed, transferring the state to the substitute virtual machine. User applications are migrated from the destroyed machine to the replacement machine. All virtual machines are monitored for an attack at a hypervisor level of cloud software using Virtual Machine Introspection, and if an attack is detected, the attacked virtual machine is destroyed and reincarnated ahead of schedule to create a new replacement machine on a different hardware platform using a different operating system.
Owner:GOVERNMENT OF THE UNITED STATES AS REPRESENTED BY THE SEC OF THE AIR FORCE
Agent-free client process protection method based on virtualization technology
ActiveCN106897121AGuaranteed concealmentHigh performance advantagePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationStructure of Management Information
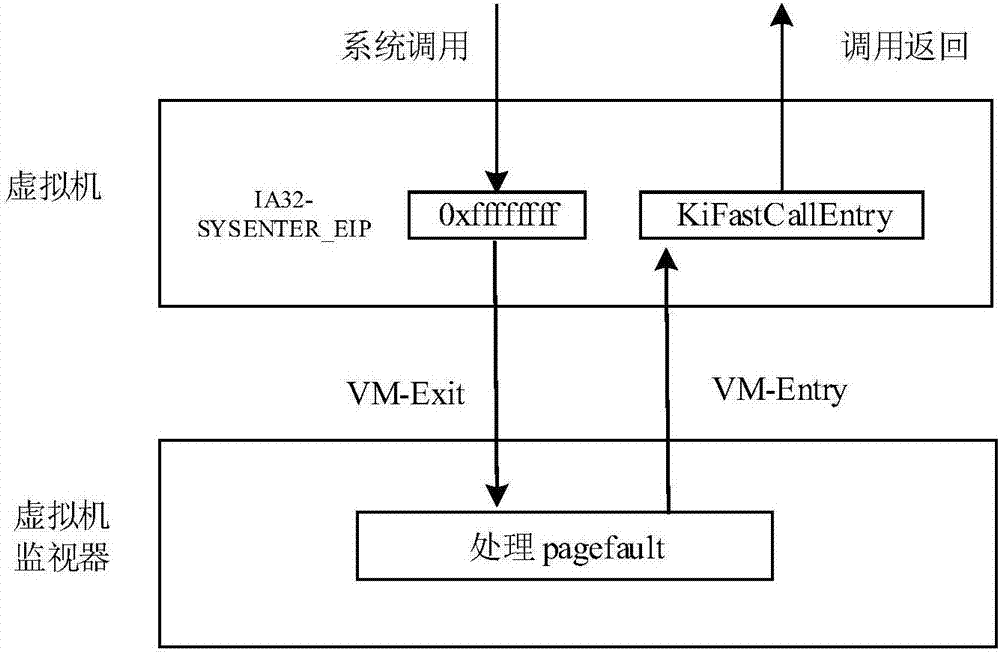
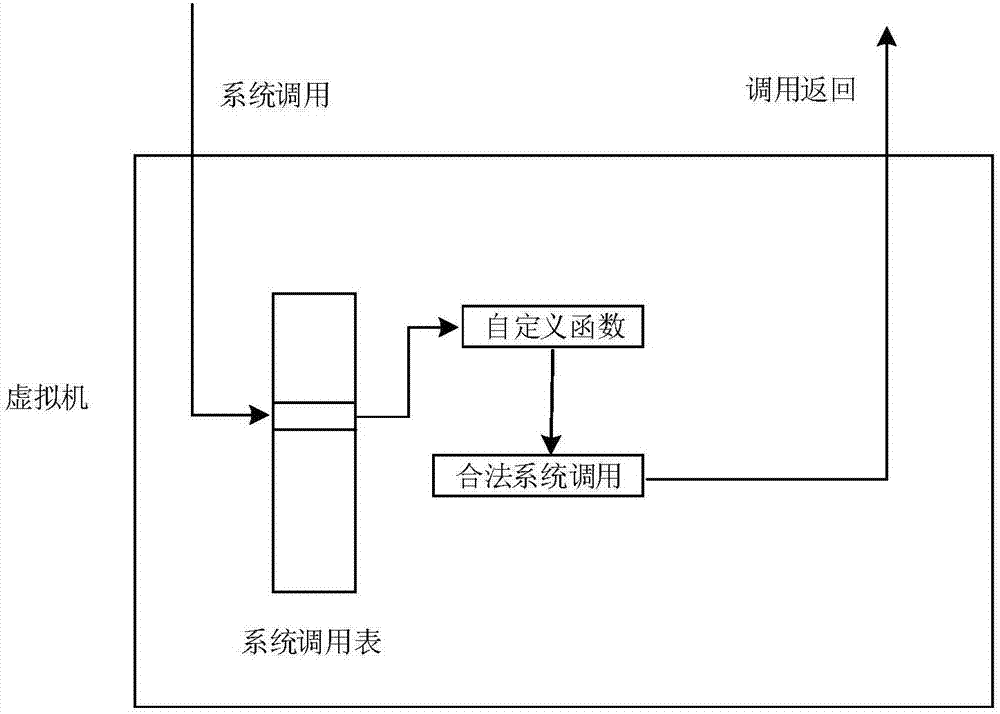
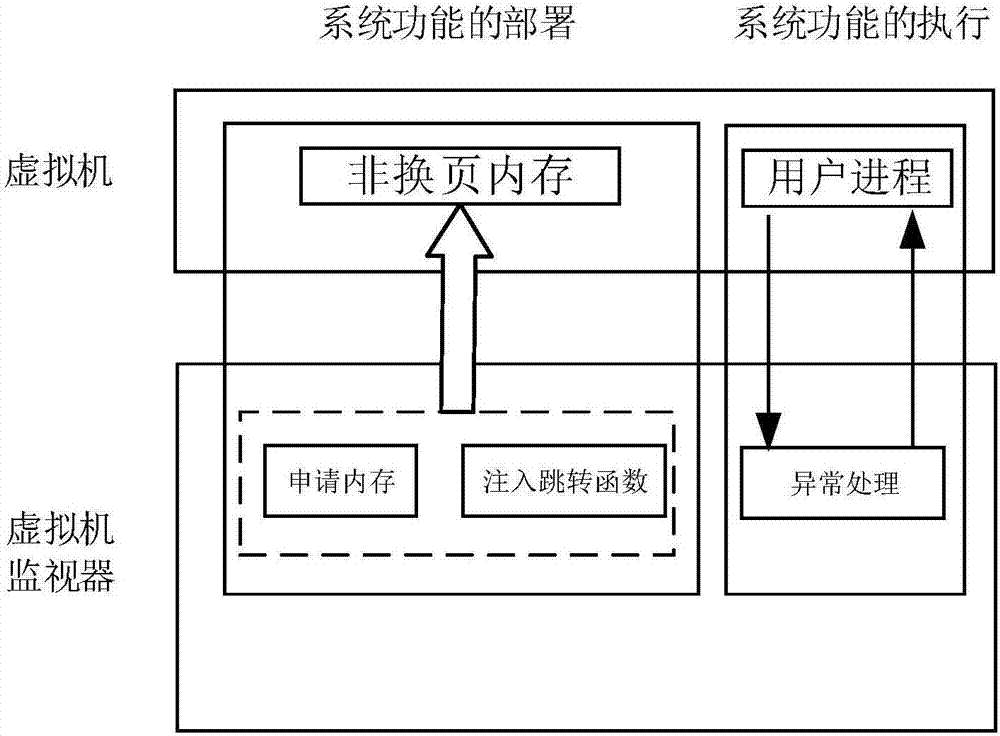
The invention discloses an agent-free client process protection method based on a virtualization technology. The method comprises the steps of transparently obtaining a windows non-paging memory page in a KVM, and recording an initial address of the memory page to a KVM structure body corresponding to a virtual machine; injecting virtual machine information; setting an IA32-SYSENTER-EIP register as a newly injected KiFastCallEntry function address, and conducting hook on a KiSystemService function; conducting clearing on original SSDT contents; setting VMCS structure relevant fields, and setting read-write sinking of the IA32-SYSENTER-EIP register and pagefault abnormal sinking of an instruction fetching type; intercepting instruction fetching pagefault abnormality of a client by a virtual machine monitor, analyzing a current operation, feeding a result back to the client, and finishing one-time accessing processing. According to the agent-free client process protection method based on the virtualization technology, the safe execution of system functions is ensured, there is no need to install an agent drive inside the client, there is no need to consider the security of the agent drive, and the influence on the performance of the virtual machine is reduced to the minimum.
Owner:SICHUAN UNIV
Software testing and evaluation method based on cloud computation technology
ActiveCN108255716AEnable continuous testingEasy to operate and maintainSoftware testing/debuggingVirtual machine introspectionSoftware deployment
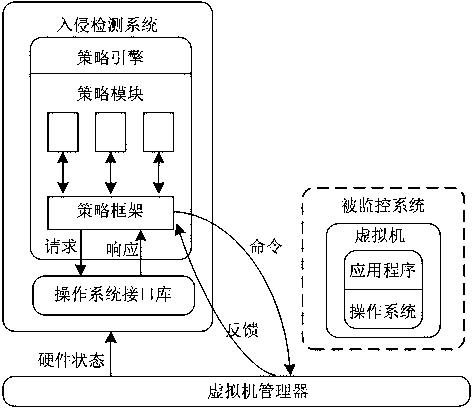
The invention relates to a software testing and evaluation method based on a cloud computation technology. The method comprises the steps that a testing cloud platform and an evaluation cloud platformare established; a lightweight cloud probe is deployed on the testing cloud platform; state data is collected by using the cloud probe and transmitted to the evaluation cloud platform through a network; analysis is conducted in the evaluation cloud platform, tested software is comprehensively established according to testing and evaluation standards, and a testing and evaluation report is generated. The software testing and evaluation method has the advantages that through the cloud computation technology, the utilization rate of equipment can be effectively increased, the required resourcesare dynamically adjusted according to service demands, the tested software is continuously tested, and the method helps to run and maintain a whole testing system. Through an introspection technologyof a virtual machine, the tested software is separated from a detection module. The tested software is deployed in the virtual machine, the detection module is deployed in a safer virtual machine monitor layer with a higher power level, and by integrating multiple advantages of the introspection technology of the virtual machine, the tested software is continuously, accurately and comprehensivelydetected.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
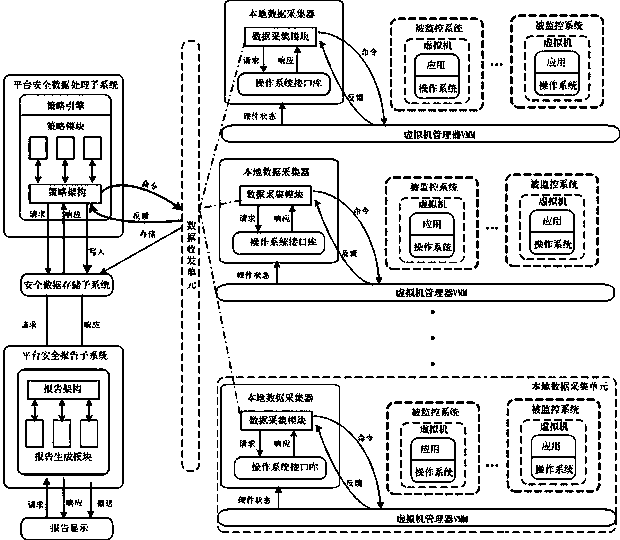
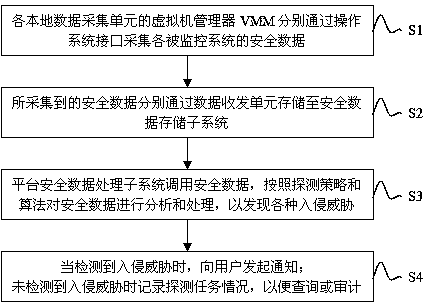
Cloud platform safe monitor system and method based on virtual machine introspection technology
ActiveCN103929502AKeep abreast of the detection statusTimely detection of joint attacksData switching networksData acquisitionVirtual machine introspection
The invention discloses a cloud platform safe monitor system and method based on a virtual machine introspection technology. The system comprises a local safety data collection subsystem, a platform safety data processing subsystem, a platform safety reporting subsystem and a safety data storage subsystem. The local safety data collection subsystem is used for collecting safety data of all monitored systems. The platform safety data processing subsystem is used for analyzing and processing the data, collected by the local safety data collection subsystem, of each monitored system according to detection strategies and an algorithm. The platform safety reporting subsystem is used for generating safety reports to a user. The safety data storage subsystem is used for storing the safety data collected by all local data collectors and original safety data. According to the system and method, a virtual machine can be monitored ceaselessly, and smooth transferring of monitoring data can be provided when the virtual machine migrates. The invaded and attacked virtual machine can be stopped fast, and more virtual machines can be prevented from being invaded and attacked.
Owner:CHENGDU GOLDTEL IND GROUP
Virtual machine introspection-based virus detection system and method
InactiveCN108762888AMonitor running statusImprove visibilityPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationProcess behavior
The invention provides a virtual machine introspection-based virus detection system and method, and aims at detecting external parts of virtual machines so as to improve the integral safety of virtualization systems. The virus detection system comprises a virus behavior feature library and a process behavior tracing data module on the basis of a virtual machine introspection tool, wherein the virus behavior feature library and the process behavior tracing data module are respectively connected with a process behavior analysis module so that comparison and detection can be carried out by the process behavior analysis module; and the virus behavior feature library is connected with the virus behavior analysis module which is used for automatically analyzing virus samples. According to the system and method, operation states in virtual machines can be monitored without modifying virtual machine systems or installing any software and tool, process behaviors in the virtual machines are utilized to judge whether virus programs are operated or not, and operations such as shutdown and the like can be carried out on the virtual machines with safety threats.
Owner:CHANGSHA WENDUN INFORMATION TECH
Virtual machine-based dynamic introspection function-level virtual machine kernel detection system and method
ActiveCN108469984AAnalytical integrityIntegrity checkSoftware simulation/interpretation/emulationControl flowVirtual machine introspection
The invention discloses a virtual machine-based dynamic introspection function-level virtual machine kernel detection system and method, and belongs to the field of cloud safety. The device compriseshardware which is used for providing hardware basis for a secure virtual machine, a target virtual machine and a virtual machine management layer; the secure virtual machine comprises a monitoring framework; the secure virtual machine interacts with the target virtual machine through the virtual machine management layer; the virtual machine management layer comprises a connection extraction module; and the extraction module is connected with each of the learning module and a monitoring module through page execution information. The method comprises the following steps of: starting a monitor, injecting a monitoring point to the target virtual machine by the extraction module, so as to ensure that the virtual machine management layer can monitor sub-functions in calling; carrying out staticanalysis by utilizing a static memory analysis method and dynamic tracking, so as to obtain subsequent sub-functions and carry out monitoring; and carrying out loop execution until system calling is returned. According to the system and method, execution information is modeled through three learning methods, so that integrity of kernel control flows is detected, and the kernel control flows are prevented from being detected and broken through by attackers.
Owner:HARBIN INST OF TECH +1
Context agent injection using virtual machine introspection
Owner:KYNDRYL INC
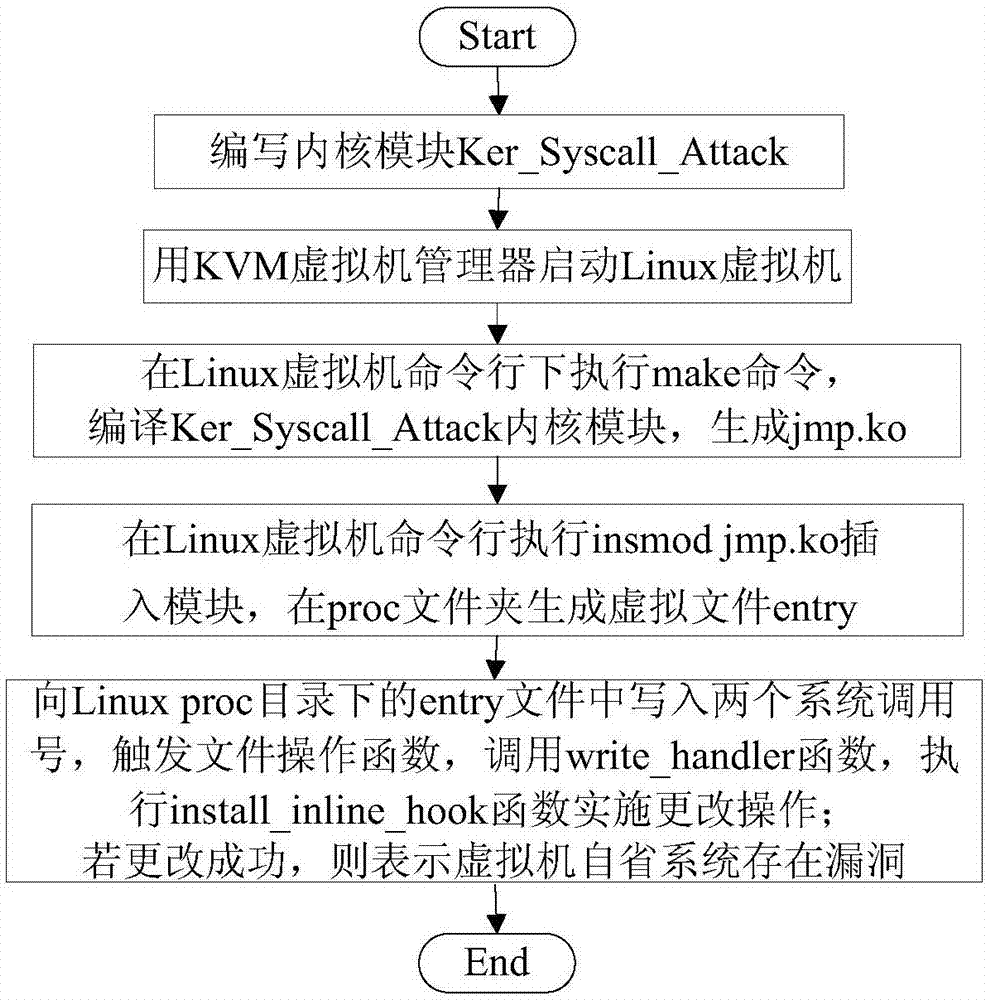
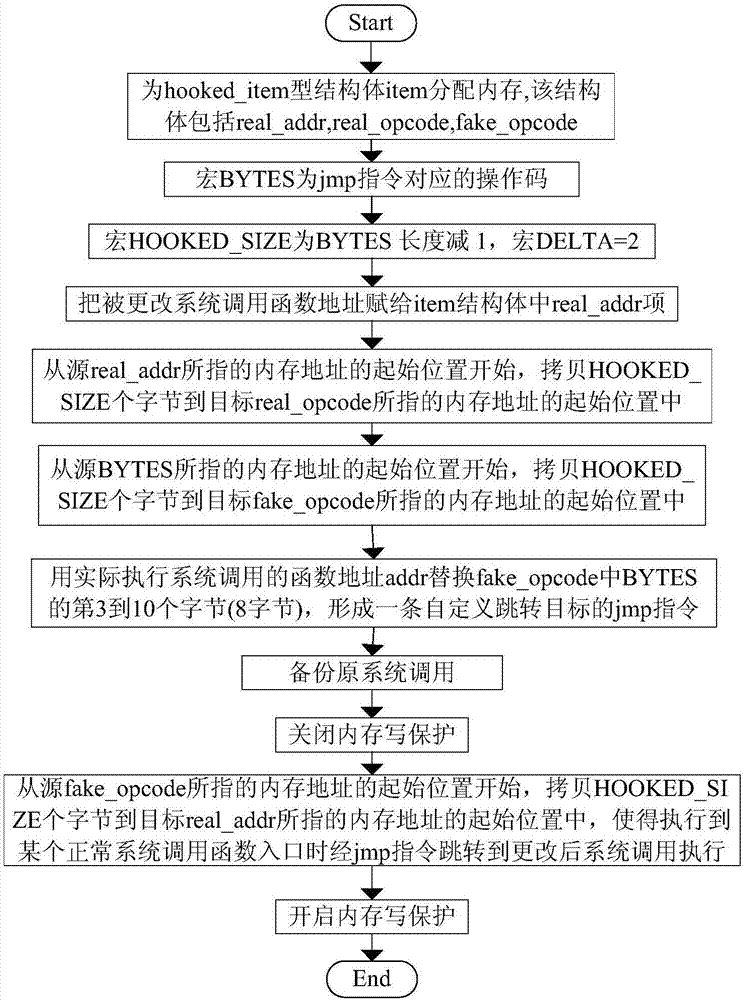
Method for discovering whether or not vulnerability exists in virtual machine introspection system
ActiveCN107450964APlatform integrity maintainanceSoftware simulation/interpretation/emulationDynamic monitoringVirtual machine introspection
The invention discloses a method for discovering whether or not a vulnerability exists in a virtual machine introspection system. A specific jmp instruction is inserted at a calling function entry address of a changed Linux virtual machine system, if the virtual machine introspection system can be modified, it means that the vulnerability exists in the virtual machine introspection system, and it indicates that a dynamic monitoring result of the virtual machine introspection system can be manually controlled to further disclose the vulnerability of the virtual machine introspection system, and important references are provided for follow-up relevant researchers to further improve the system.
Owner:XIDIAN UNIV
Openstack based physical machine remote maintenance method
InactiveCN105426243AGuaranteed uptimeAvoid lostProgram initiation/switchingMachine maintenanceGreedy algorithm
The invention relates to the technical field of physical machine power control and cloud computing virtual machine migration, in particular to an Openstack based physical machine remote maintenance method. The method comprises: firstly, establishing an Openstack cloud platform and setting an IPMI address, an IPMI login user name and a password of a physical machine; secondly, searching for an available physical node in a normal state according to a greedy algorithm at a control node of the Openstack cloud platform, sending an instruction of migrating a virtual machine to the available physical node to a target physical machine through a component, and after all virtual machines are migrated, sending a shutdown command to a baseboard management controller (BMC) of the target physical machine; and finally, executing a request by the BMC of the target physical machine, and returning an executive result. According to the method, the problems that the virtual machines need to be migrated before physical machine maintenance, a Juno version of the Openstack open source cloud platform cannot perform remote physical machine maintenance, an application cannot be ensured to be normally and continuously used, inconvenience is provided for the operation and maintenance personnel to maintain the physical machine, and the like are solved; and the method can be applied to physical machine maintenance and virtual machine migration of the cloud platform.
Owner:G CLOUD TECH
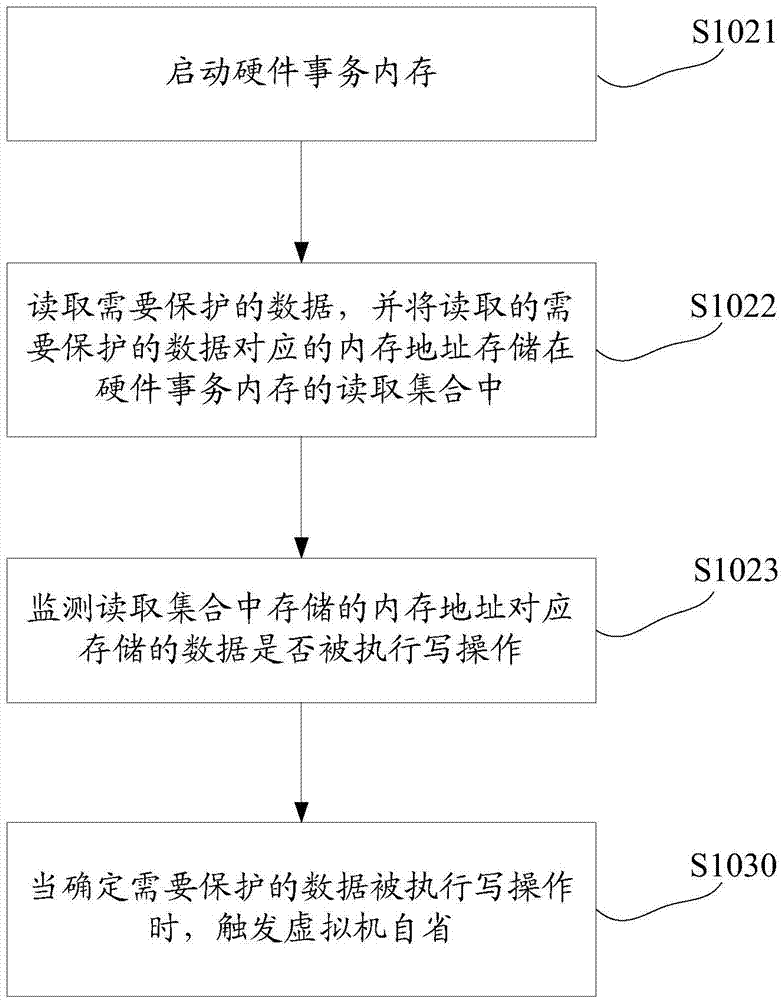
Method, device and system for triggering self-examination of virtual machine
ActiveCN104750534AIntrospection in timeAvoid lostError detection/correctionPlatform integrity maintainanceVirtual machine introspectionSecurity check
The present invention discloses a method, an apparatus, and a system for triggering virtual machine introspection, so as to provide a timely and effective security check triggering mechanism. In the present invention, data that needs to be protected is determined; the data that needs to be protected is monitored; and when it is determineed that the data that needs to be protected is modified, virtual machine introspection is triggered. The present invention avoids a performance loss and a security problem that are brought about by regularly starting a virtual machine introspection system to perform a security check, and therefore, the present invention is more applicable.
Owner:HUAWEI TECH CO LTD
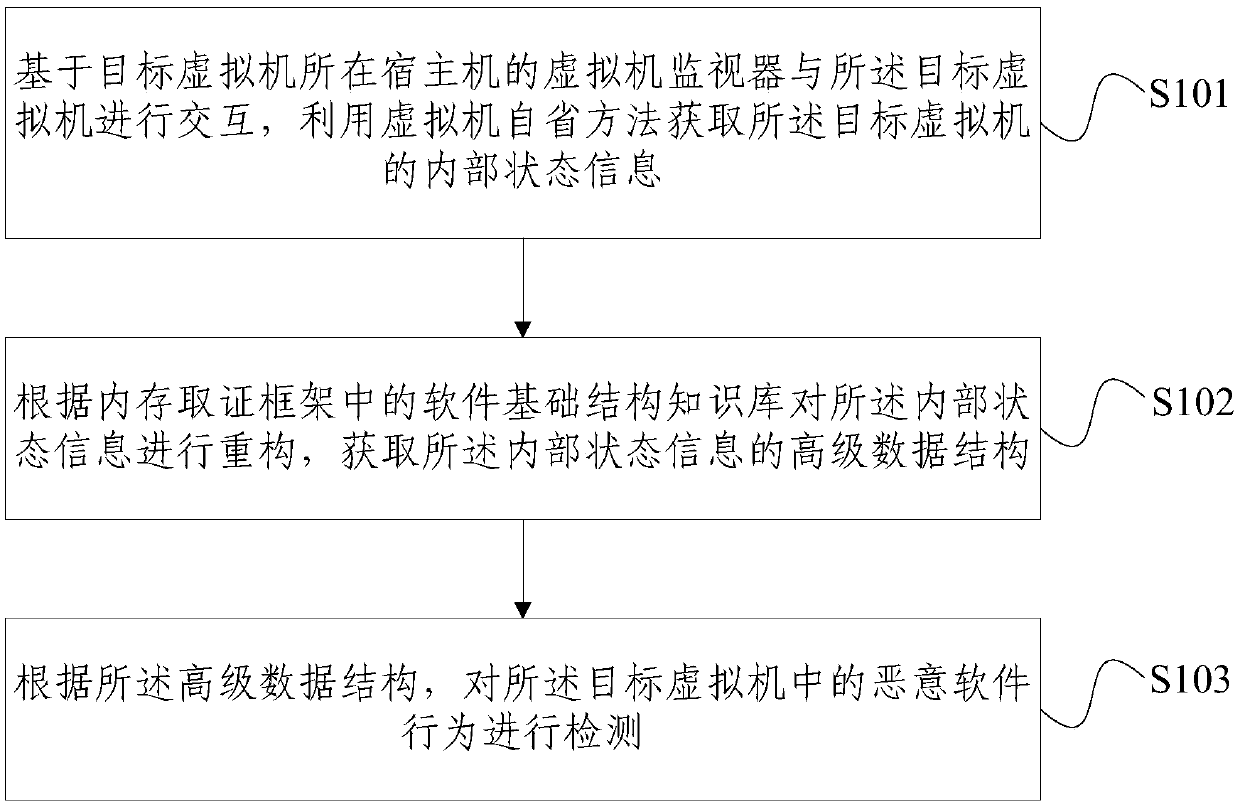
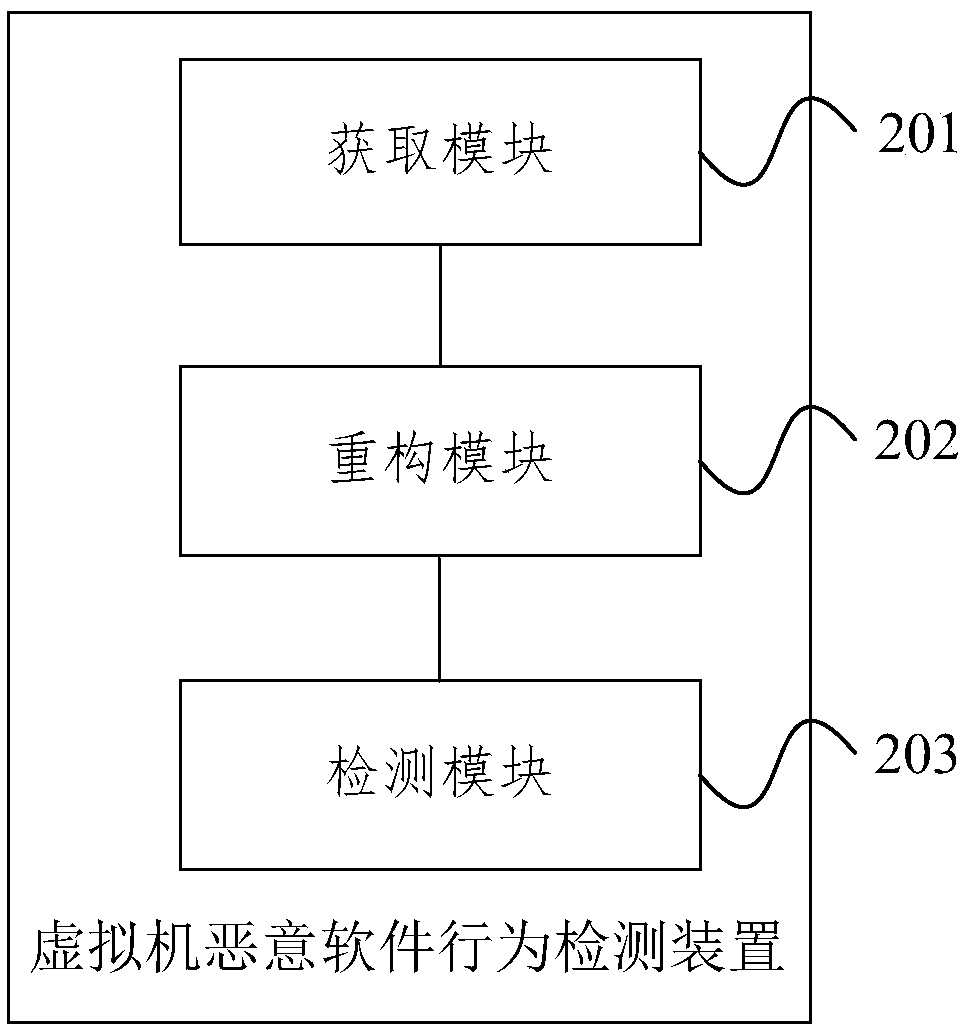
A virtual machine malicious software behavior detection method and system
ActiveCN109597675AEnsure safetyAccurate detectionPlatform integrity maintainanceSoftware simulation/interpretation/emulationMemory forensicsVirtual machine introspection
The embodiment of the invention provides a virtual machine malicious software behavior detection method and system, and the method comprises the steps: carrying out the interaction with a target virtual machine based on a virtual machine monitor of a host machine where the target virtual machine is located, and obtaining the internal state information of the target virtual machine through a virtual machine self-provincial method; Reconstructing the internal state information according to a software basic structure knowledge base in a memory evidence obtaining framework, and obtaining a high-level data structure of the internal state information; And according to the advanced data structure, detecting malicious software behaviors in the target virtual machine. According to the embodiment ofthe invention, the detection of the malicious software behavior is more accurate and comprehensive, the abnormal behavior can be processed in a targeted manner, the security of the target virtual machine is ensured, the influence on the performance of the virtual machine is greatly reduced, and the detection of the malicious software behavior is realized on the premise of no perception.
Owner:INST OF INFORMATION ENG CAS
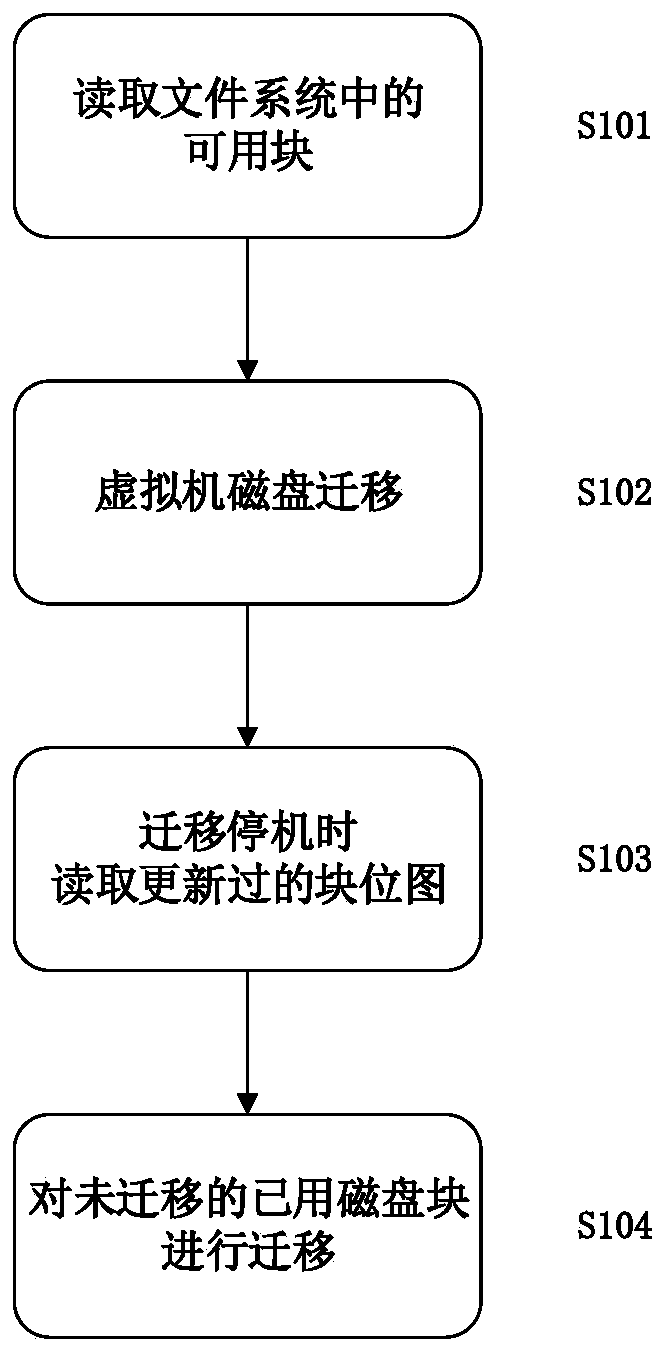
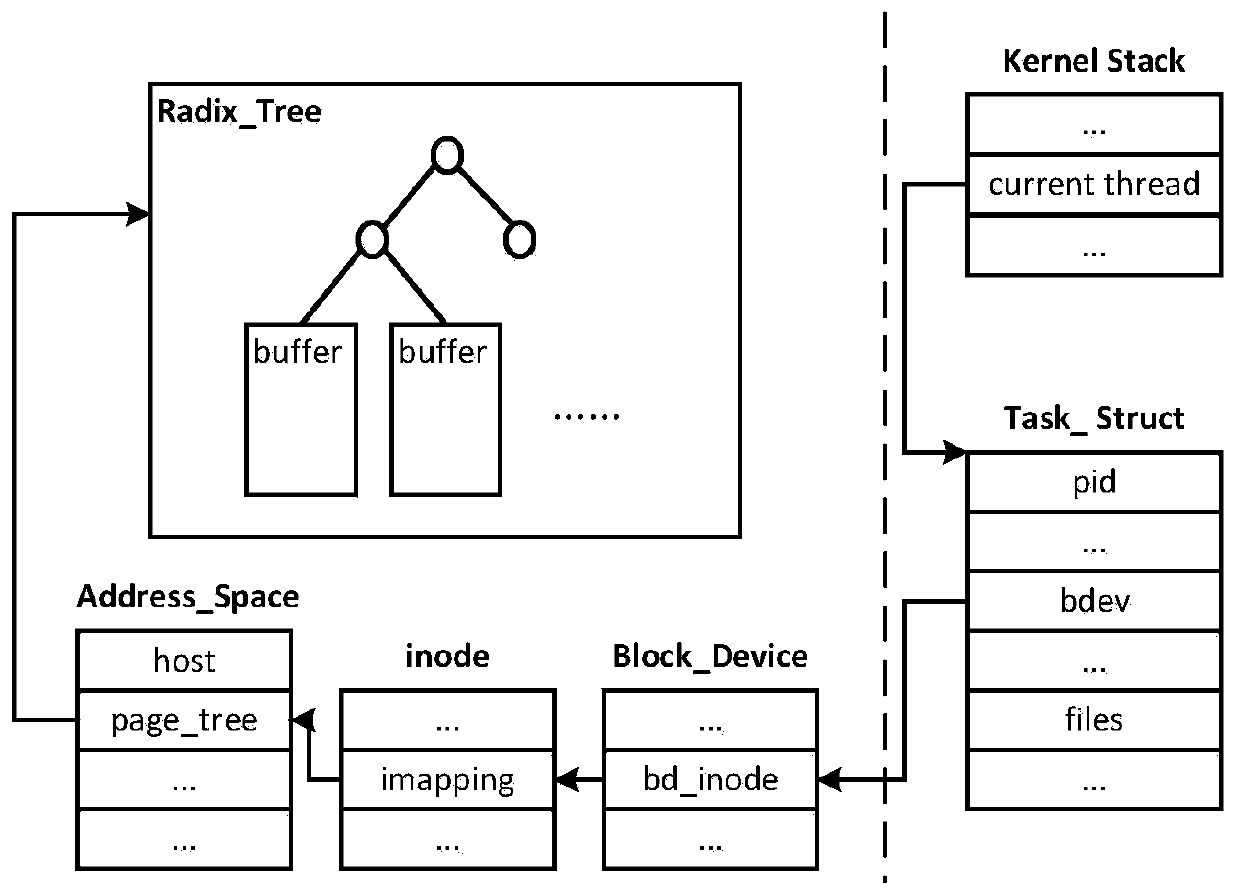
Online migration redundancy removal method for virtual machine disk
ActiveCN111580932ASave migration timeSave migration bandwidthDigital data information retrievalInput/output to record carriersComputer hardwareData compression
The invention discloses an online migration redundancy removal method for a virtual machine disk. The method comprises the following steps: firstly, reading a super block in a disk according to a filesystem organization mode, then reading a bitmap in each block group according to block group description information in the super block, determining whether each block in the bitmap record block group is used or available, and constructing a complete bitmap for the whole disk by utilizing the obtained bitmaps of all the block groups; secondly, in the virtual machine migration process, carrying out disk migration according to the obtained disk use information, and at the moment, only transmitting used disk blocks; and thirdly, extracting unused block bitmaps which are possibly updated from theoriginal memory data by using a virtual machine introspection technology, updating bitmap information by using the unused block bitmaps after obtaining caches of metadata of all block equipment in the memory, and migrating used disk blocks which are not migrated before to a destination end by using an existing method. According to the method, semantic information of the data is mainly used for data compression, so that very small overhead for upper-layer applications is introduced.
Owner:XI AN JIAOTONG UNIV
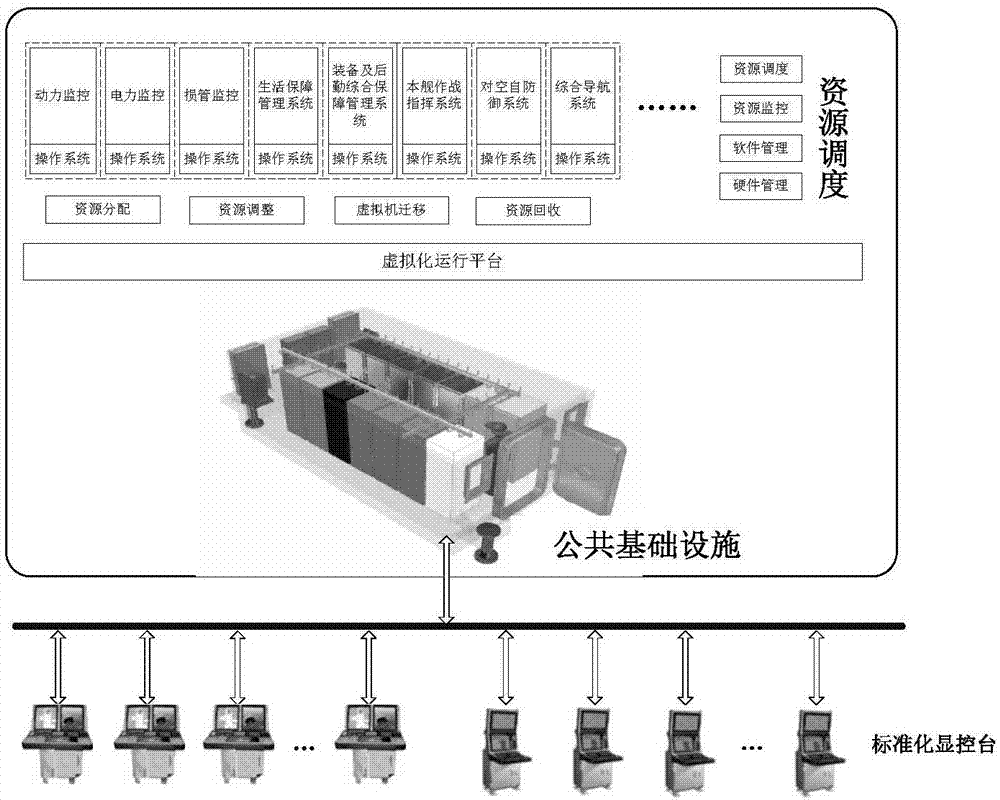
Public infrastructure resource scheduling method based on application priority
ActiveCN107122235AAchieve sharingRealize unified schedulingProgram initiation/switchingResource allocationVirtualizationInformation resource
The invention discloses a public infrastructure resource scheduling method based on an application priority. The method comprises the following steps that: (1) uniformly deploying an application system in different virtual machine, uniformly deploying the application system in the virtual machine, and configuring an operating environment on which the application system depends in the virtual machine, wherein only an independent application system is deployed in each virtual machine, and the virtual machine where the application system is positioned is taken as granularity for scheduling during scheduling; and (2) in a resource scheduling process, monitoring the resource use situation of the application system in real time, and according to the load situation of the application system, taking virtual machine migration as the resource scheduling method to dynamically deploy application system resources according to the priority of the application system. By use of the method, through a virtualization technology, full-ship information resources are integrated to realize the sharing and the uniform scheduling of the full-ship information resources, and the resource requirements of a combat and platform application system are subjected to overall consideration so as to perform a supporting function of the public information infrastructure to a maximum degree and improve the integral combat effectiveness.
Owner:CHINA SHIP DEV & DESIGN CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com