Method for discovering whether or not vulnerability exists in virtual machine introspection system
A virtual machine and vulnerability technology, applied in software simulation/interpretation/simulation, program control design, instruments, etc., can solve the problems of unrealized controllability of virtual machine introspection system dynamic monitoring results, lack of design ideas, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
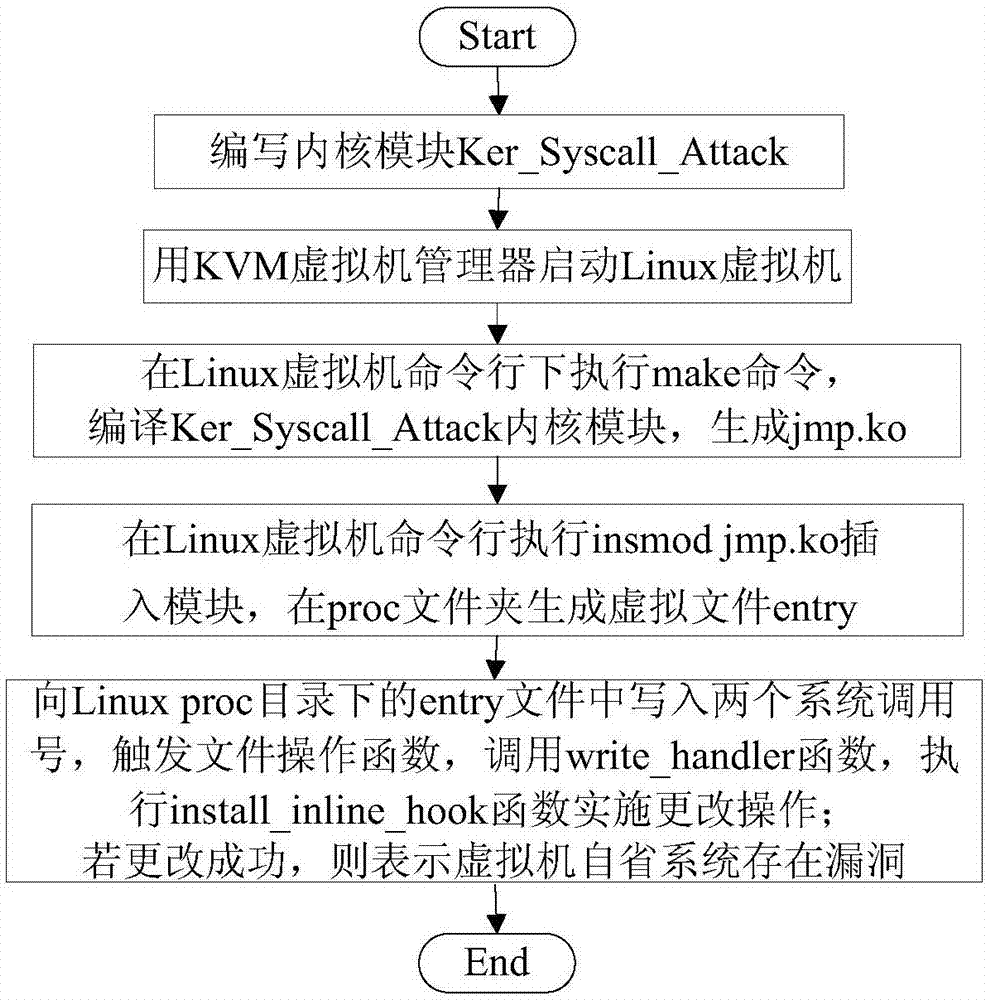
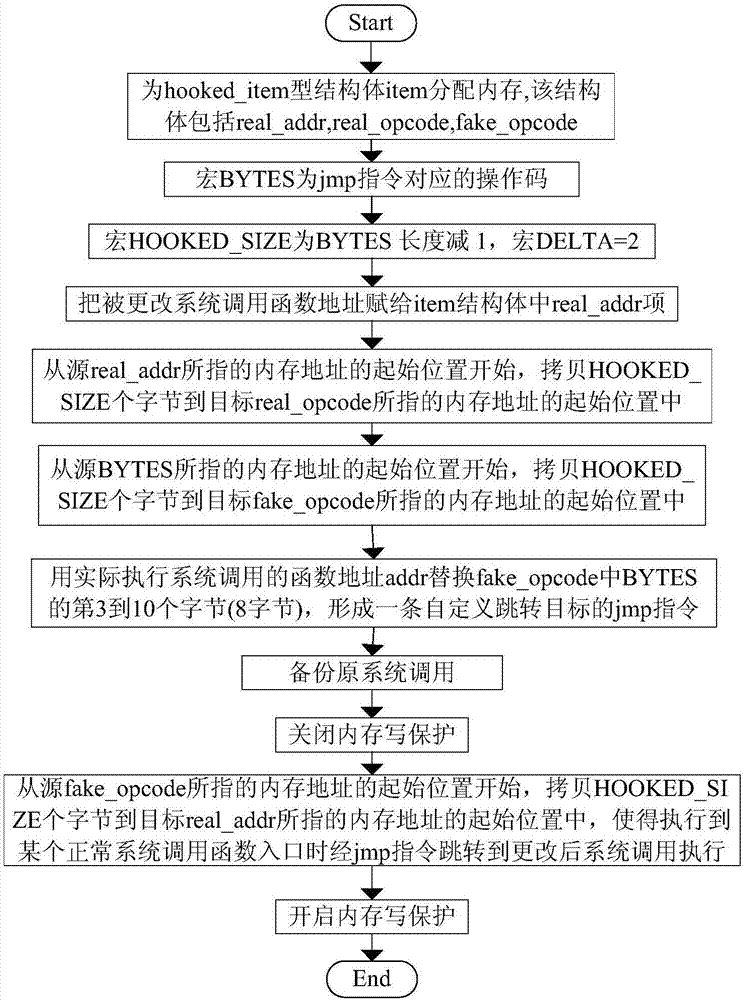
[0042] The present invention allows the system to jump to the changed system call code and execute it by inserting a specific jmp instruction at the entry address of the changed Linux virtual machine system call function, thereby misleading the VMI tool to obtain false system call monitoring information , to hide the system call operations actually executed by the experimenters in the virtual machine to achieve the purpose of the experiment. Assuming that the experiment can be successful, it shows that there are certain loopholes in the realization of the dynamic monitoring function of the virtual machine introspection system, which provides a basis for subsequent related researchers to further improve the system Important reference.
[0043] refer to figure 1 , the present invention comprises five steps, wherein needs to write Linux kernel module Ker_...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com