Automatic analysis method and system of malicious codes based on API (application program interface) HOOK
A malicious code, automatic analysis technology, applied in the field of malicious code, can solve the problem of slow analysis and detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
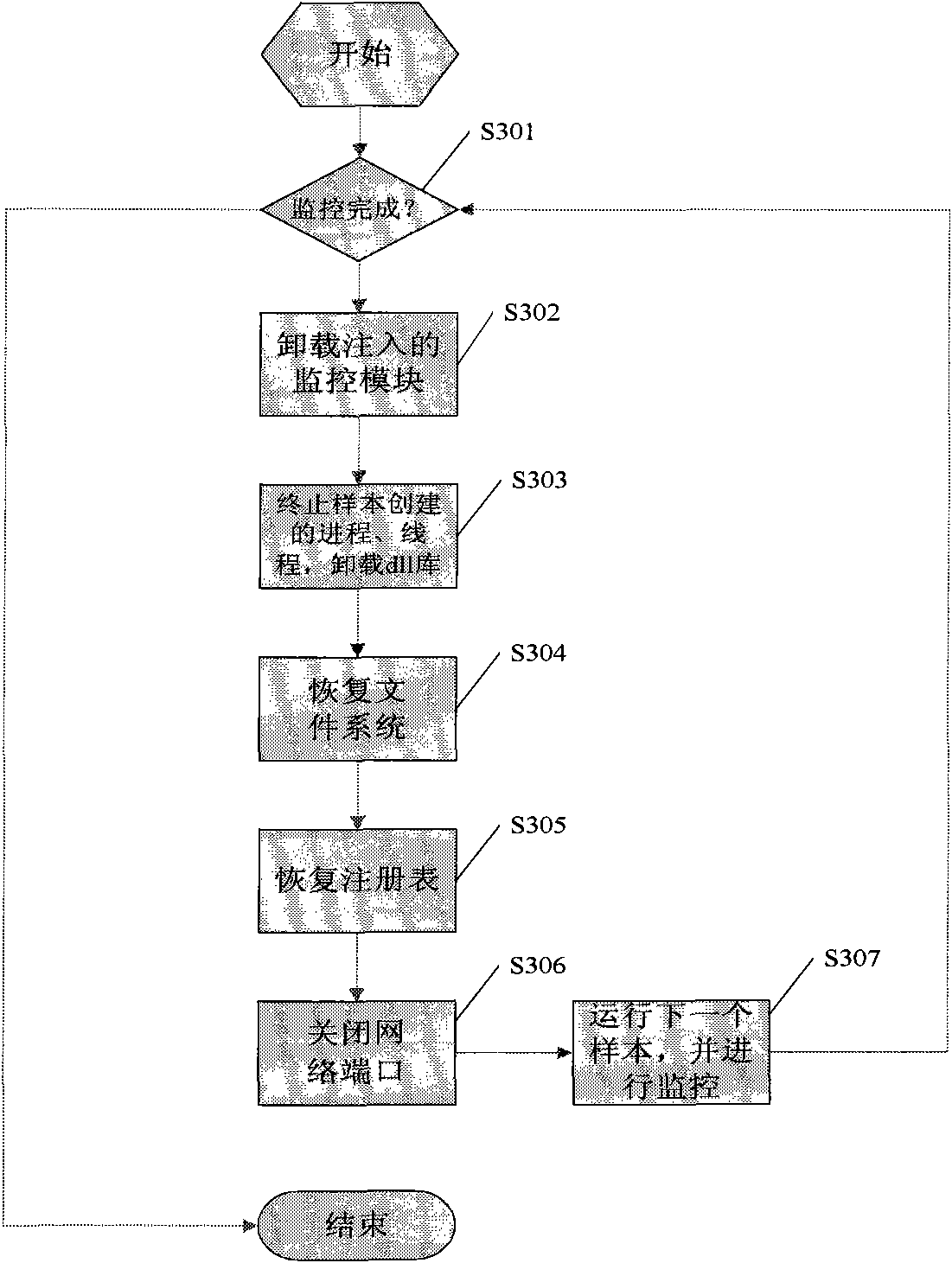
[0026] The technical scheme of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0027] figure 1 Show the step diagram of concrete implementation of the present invention, in order to describe the present invention clearly, describe a specific embodiment below, detailed figure 1 The steps are as follows:
[0028] S101 Enumerate system processes, find sample processes, start the malicious code monitoring system by means of remote thread injection, register and load each module
[0029] S102 When a sample is finished running, the log report is analyzed, and after the system is restored, check whether there are still samples in the sample set directory, and end if not
[0030] S103 Start the sample process in the suspend state. At this time, the sample process has been created, but it is not running
[0031] S104 Inject the file monitoring module, network monitoring module, registry monitoring module, and process monitorin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com