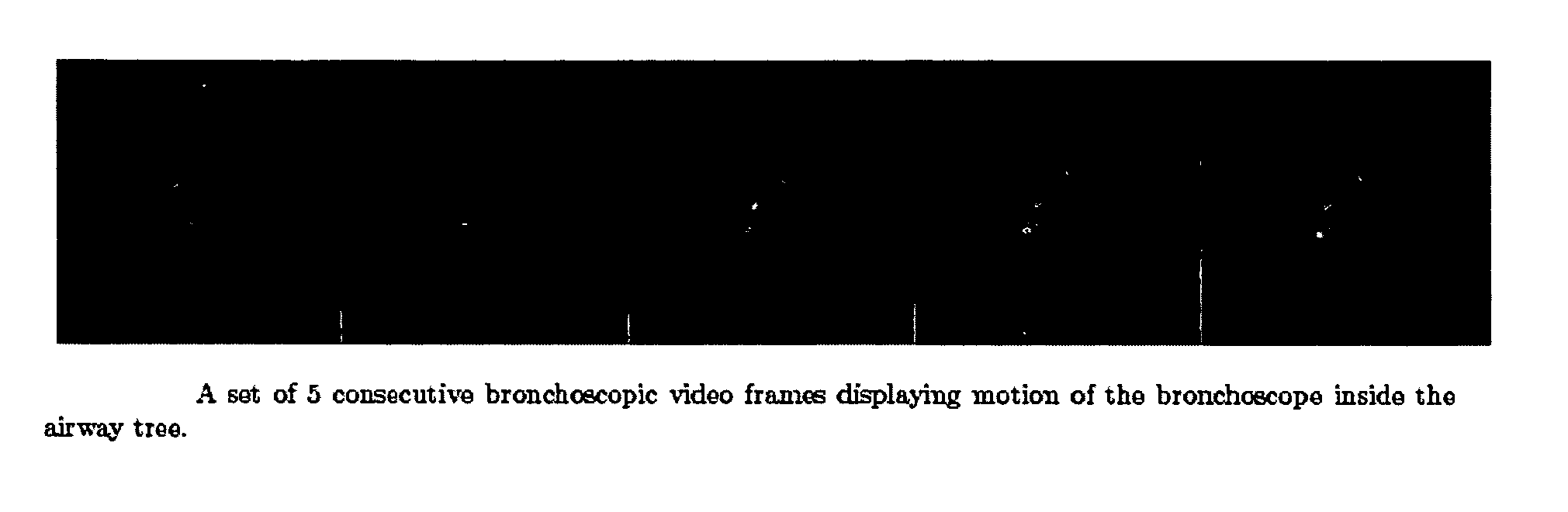Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Maximizing cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
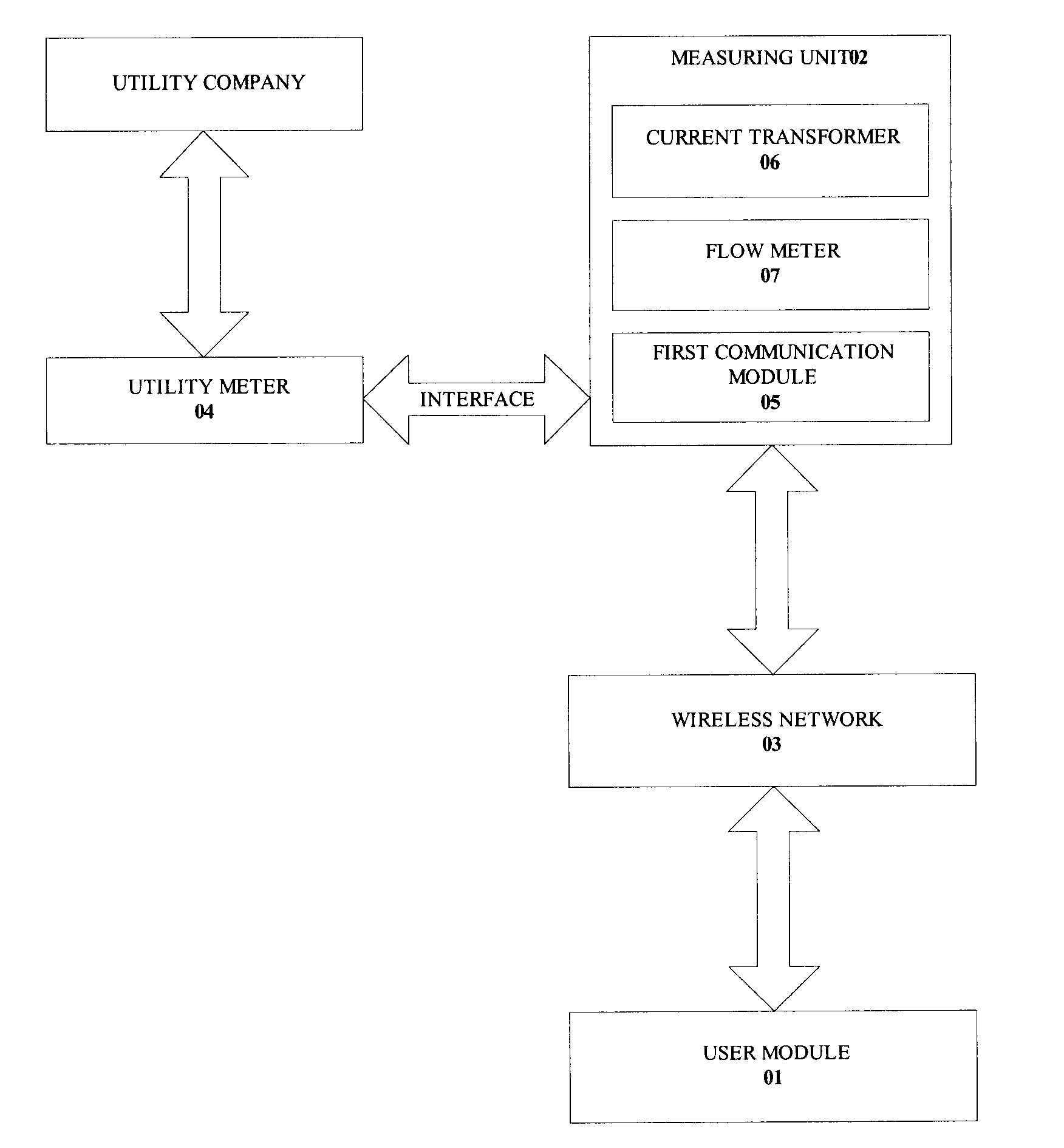
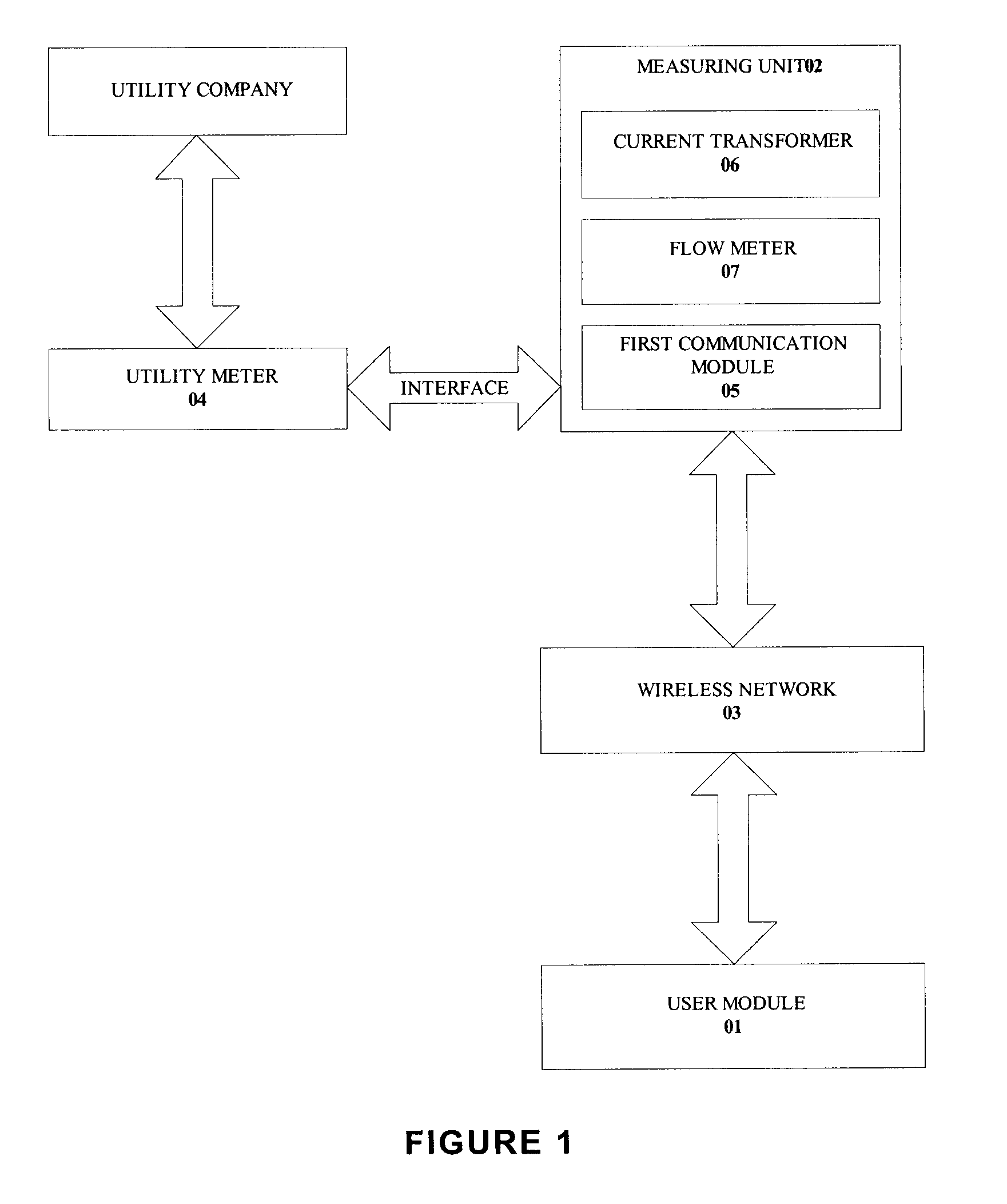
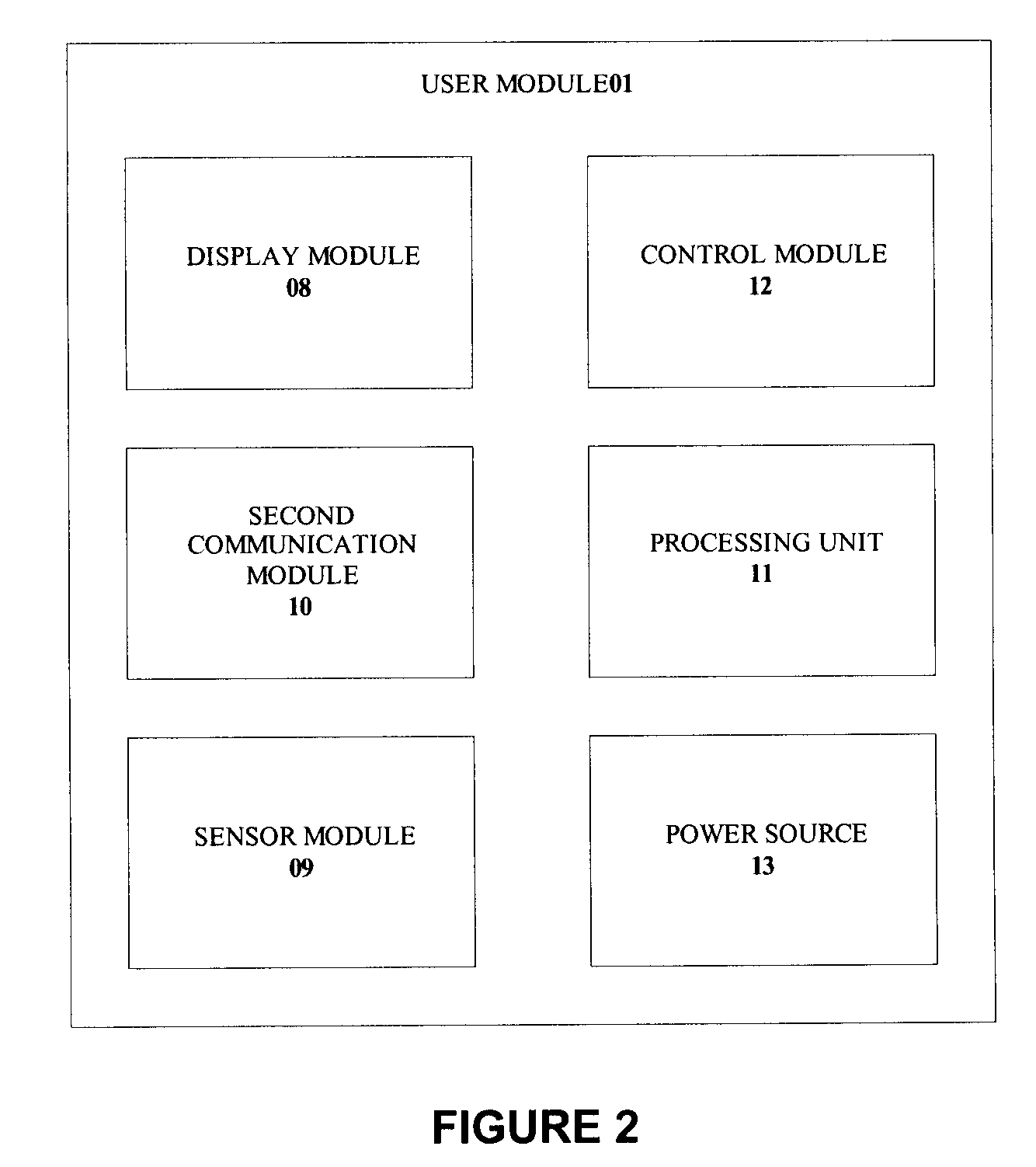
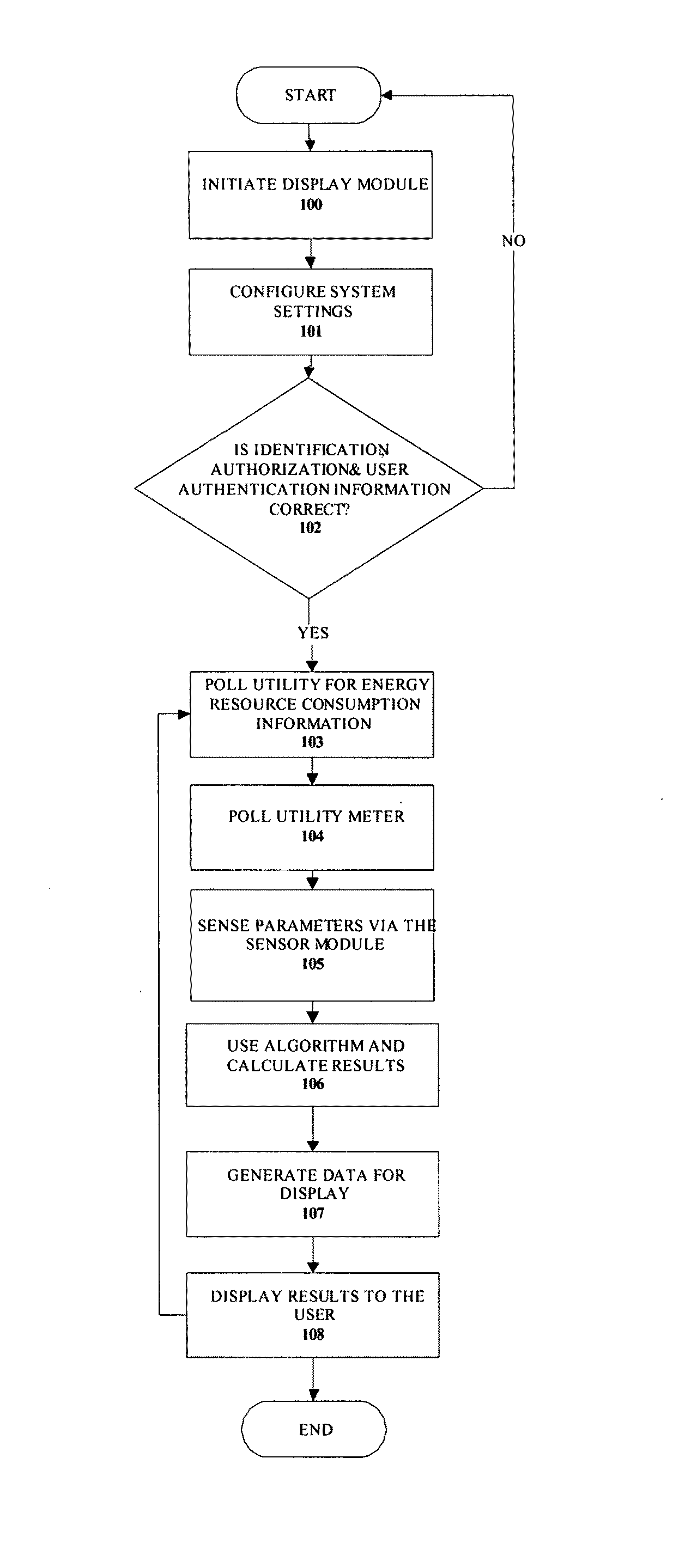
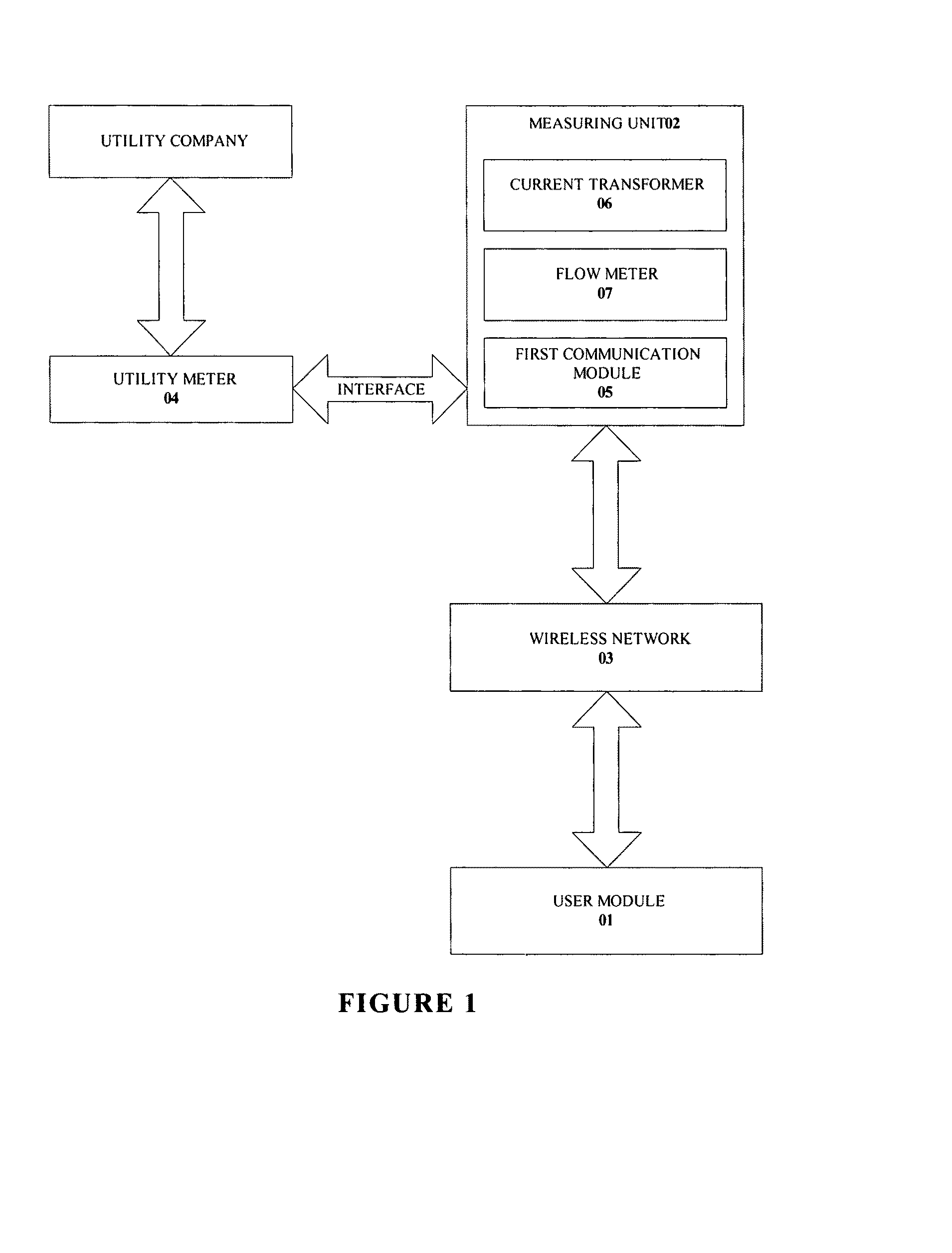
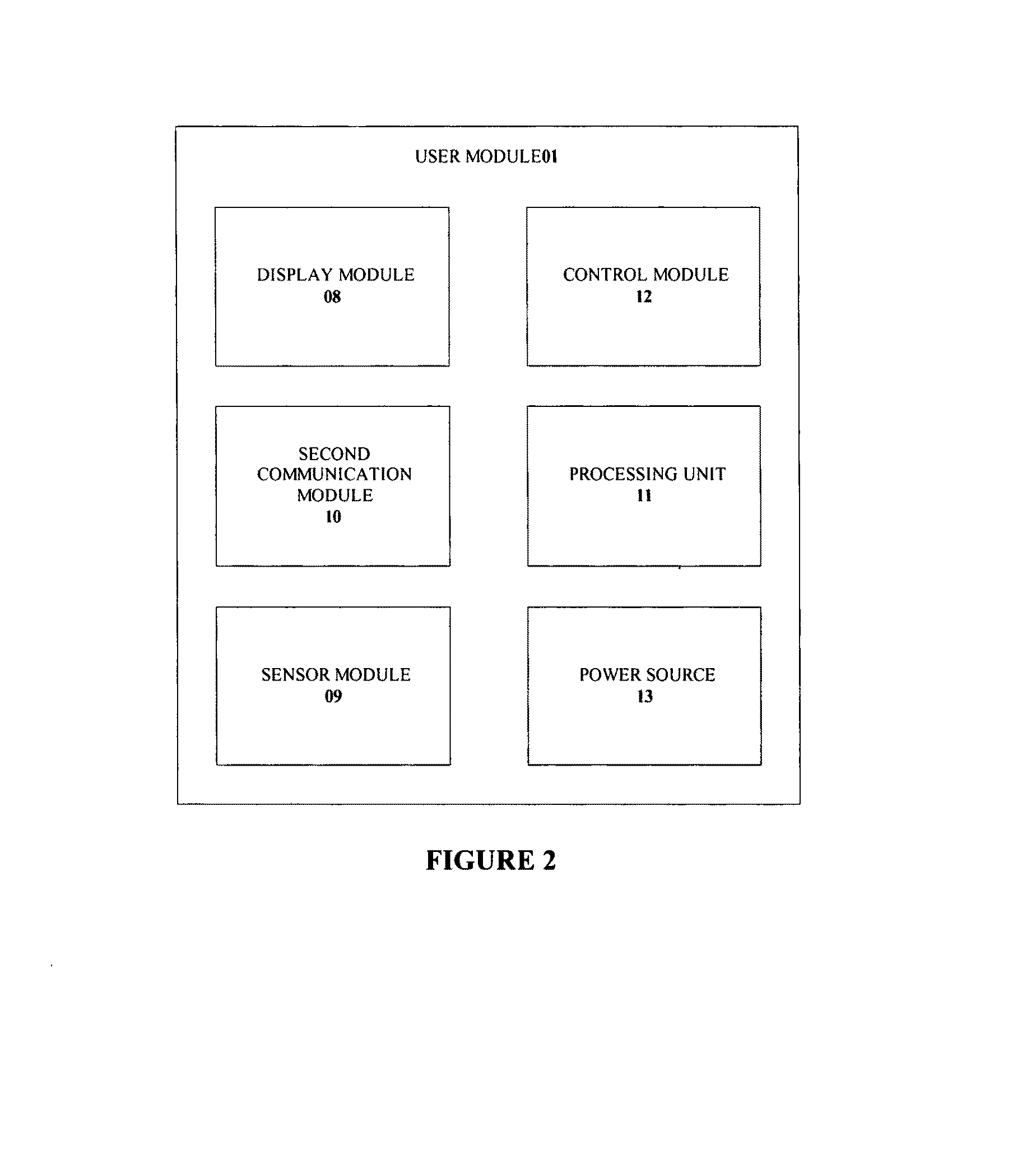
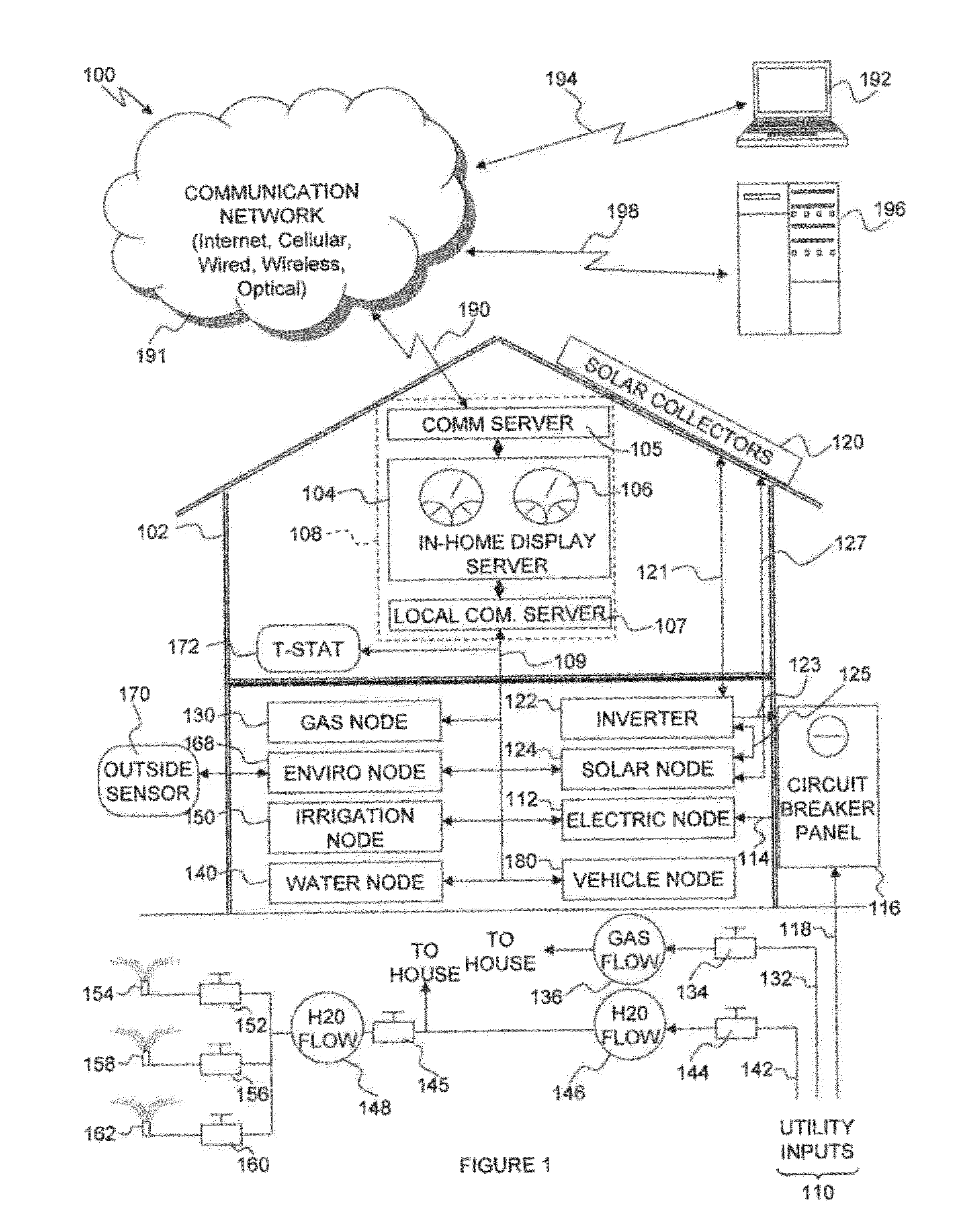
System and method for monitoring and estimating energy resource consumption
ActiveUS20080224892A1Good estimateEasy to understandEnergy efficient ICTElectric signal transmission systemsElectricityEngineering
The present invention discloses a system for monitoring and estimating the consumption of energy resources in real-time. The system includes an interactive user module, a measuring unit and a wireless network. The measuring unit is interfaced to a utility meter. Optionally, the measuring unit can also function as a stand alone device. The measuring unit is further connected to the interactive user module via the wireless network. The system monitors energy resource consumption such as electricity, gas or water consumption in real-time, generates and displays graphs of energy resource consumption over user selected time periods and enables communication with at least one utility company. The system increases the users' awareness of their energy consumption and aids users in dynamic or deregulated pricing environments to shed load when the energy resource is most expensive. With knowledge of their energy use, the users can take proactive steps to control their energy consumption and save money. A method of estimating the energy resource consumption over a period of time is also provided.
Owner:ITRON NETWORKED SOLUTIONS INC
System and method for monitoring and estimating energy resource consumption
ActiveUS7541941B2Good estimateEasy to understandEnergy efficient ICTElectric signal transmission systemsElectricityEngineering
The present invention discloses a system for monitoring and estimating the consumption of energy resources in real-time. The system includes an interactive user module, a measuring unit and a wireless network. The measuring unit is interfaced to a utility meter. Optionally, the measuring unit can also function as a stand alone device. The measuring unit is further connected to the interactive user module via the wireless network. The system monitors energy resource consumption such as electricity, gas or water consumption in real-time, generates and displays graphs of energy resource consumption over user selected time periods and enables communication with at least one utility company. The system increases the users' awareness of their energy consumption and aids users in dynamic or deregulated pricing environments to shed load when the energy resource is most expensive. With knowledge of their energy use, the users can take proactive steps to control their energy consumption and save money. A method of estimating the energy resource consumption over a period of time is also provided.
Owner:ITRON NETWORKED SOLUTIONS INC
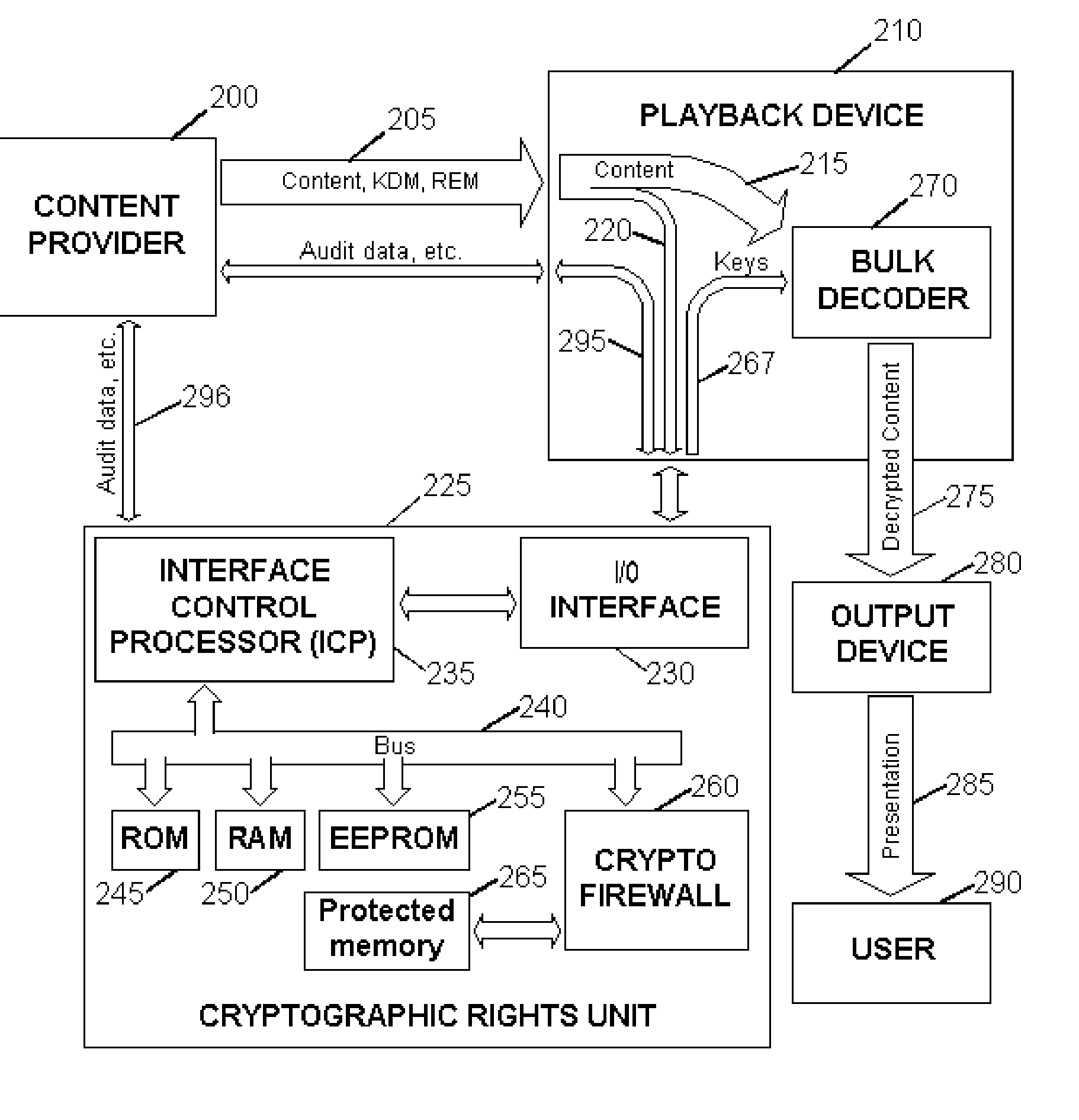
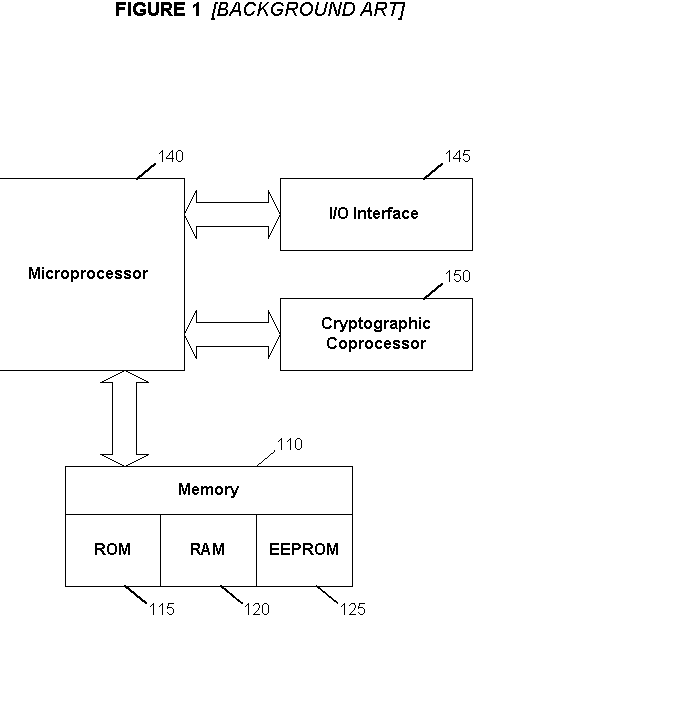
Digital Content Protection Method and Apparatus
InactiveUS20020099948A1Improve securityMinimizes probabilityKey distribution for secure communicationDigital data processing detailsDigital signatureDigital content
<heading lvl="0">Abstract of Disclosure< / heading> Before use, a population of tamper-resistant cryptographic enforcement devices is partitioned into groups and issued one or more group keys. Each tamper-resistant device contains multiple computational units to control access to digital content. One of the computational units within each tamper-resistant device communicates with another of the computational units acting as an interface control processor, and serves to protect the contents of a nonvolatile memory from unauthorized access or modification by other portions of the tamper-resistant device, while performing cryptographic computations using the memory contents. Content providers enforce viewing privileges by transmitting encrypted rights keys to a large number of recipient devices. These recipient devices process received messages using the protected processing environment and memory space of the secure unit. The processing result depends on whether the recipient device was specified by the content provider as authorized to view some encrypted digital content. Authorized recipient devices can use the processing result in decrypting the content, while unauthorized devices cannot decrypt the content. A related aspect of the invention provides for securing computational units and controlling attacks. For example, updates to the nonvolatile memory, including program updates, are supported and protected via a cryptographic unlocking and validation process in the secure unit, which can include digital signature verification.
Owner:CRYPTOGRAPHY RESEARCH
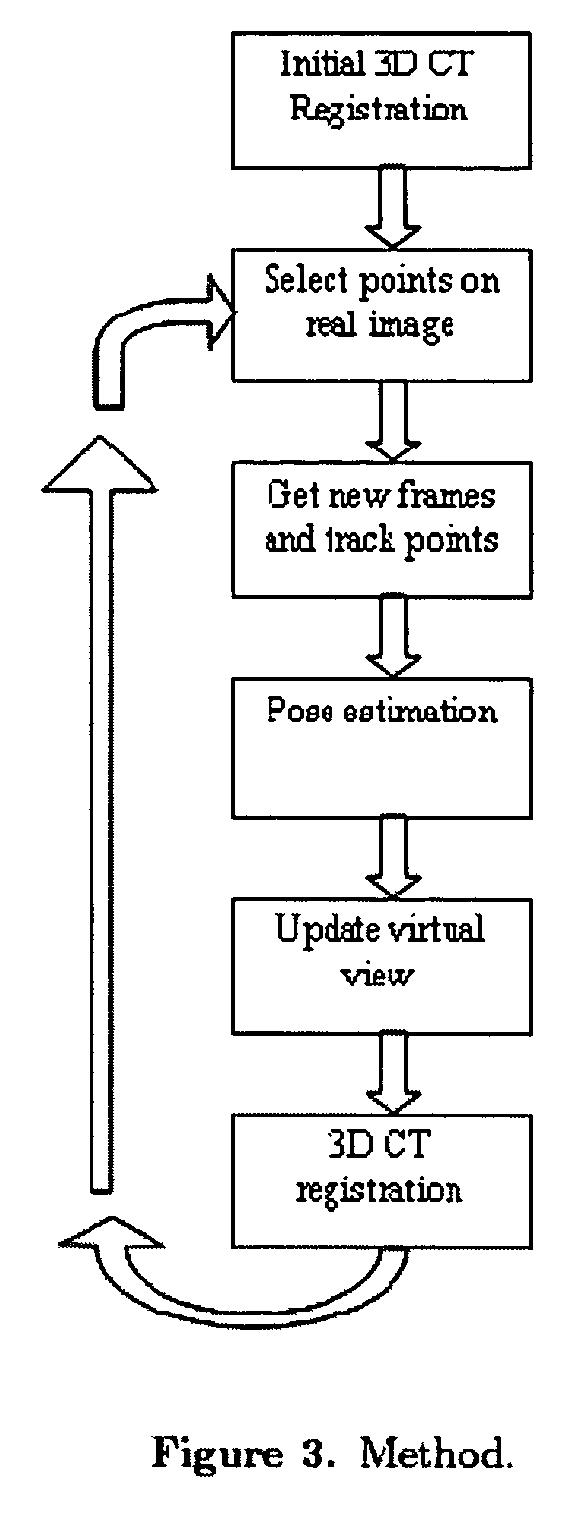
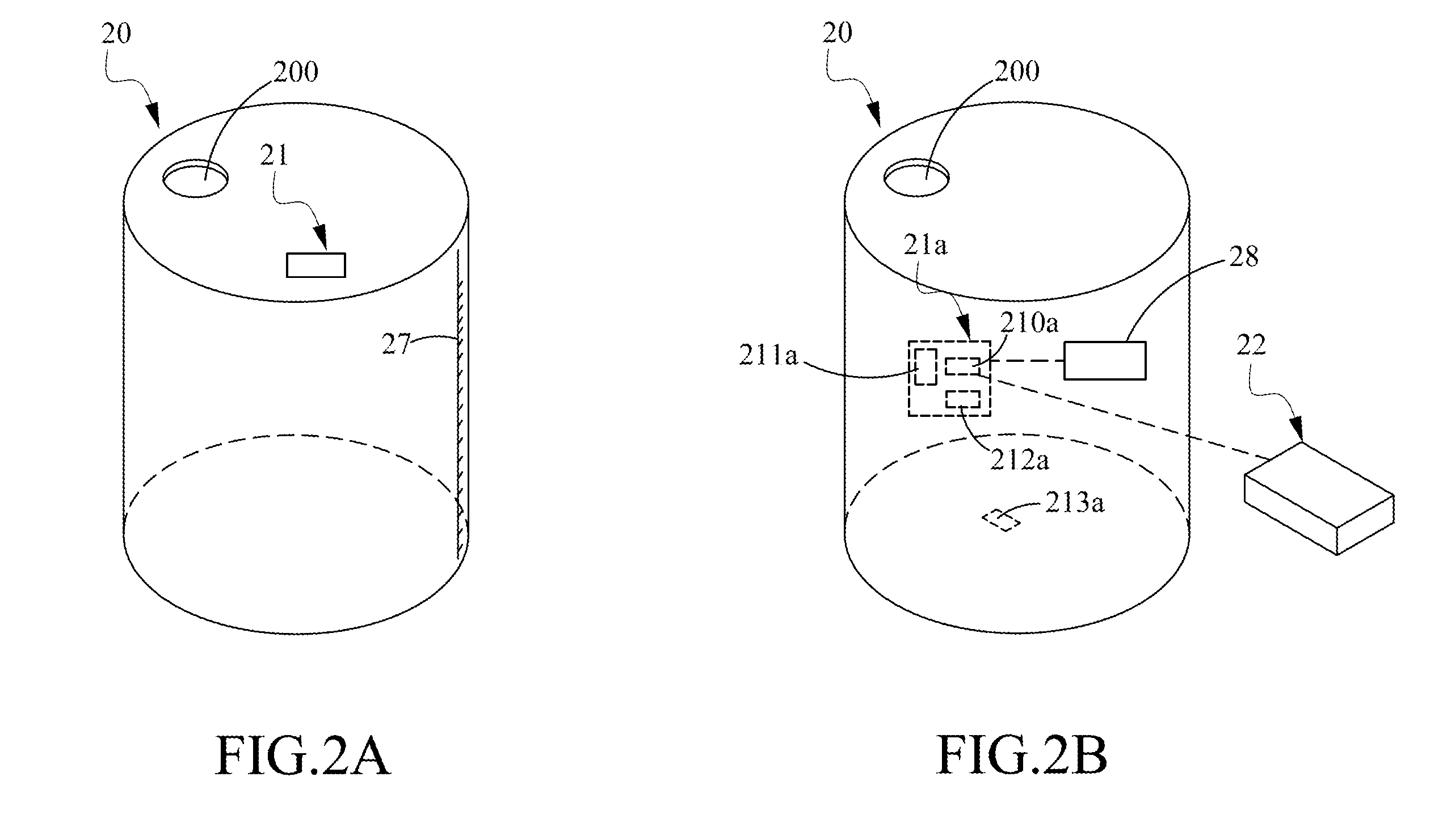
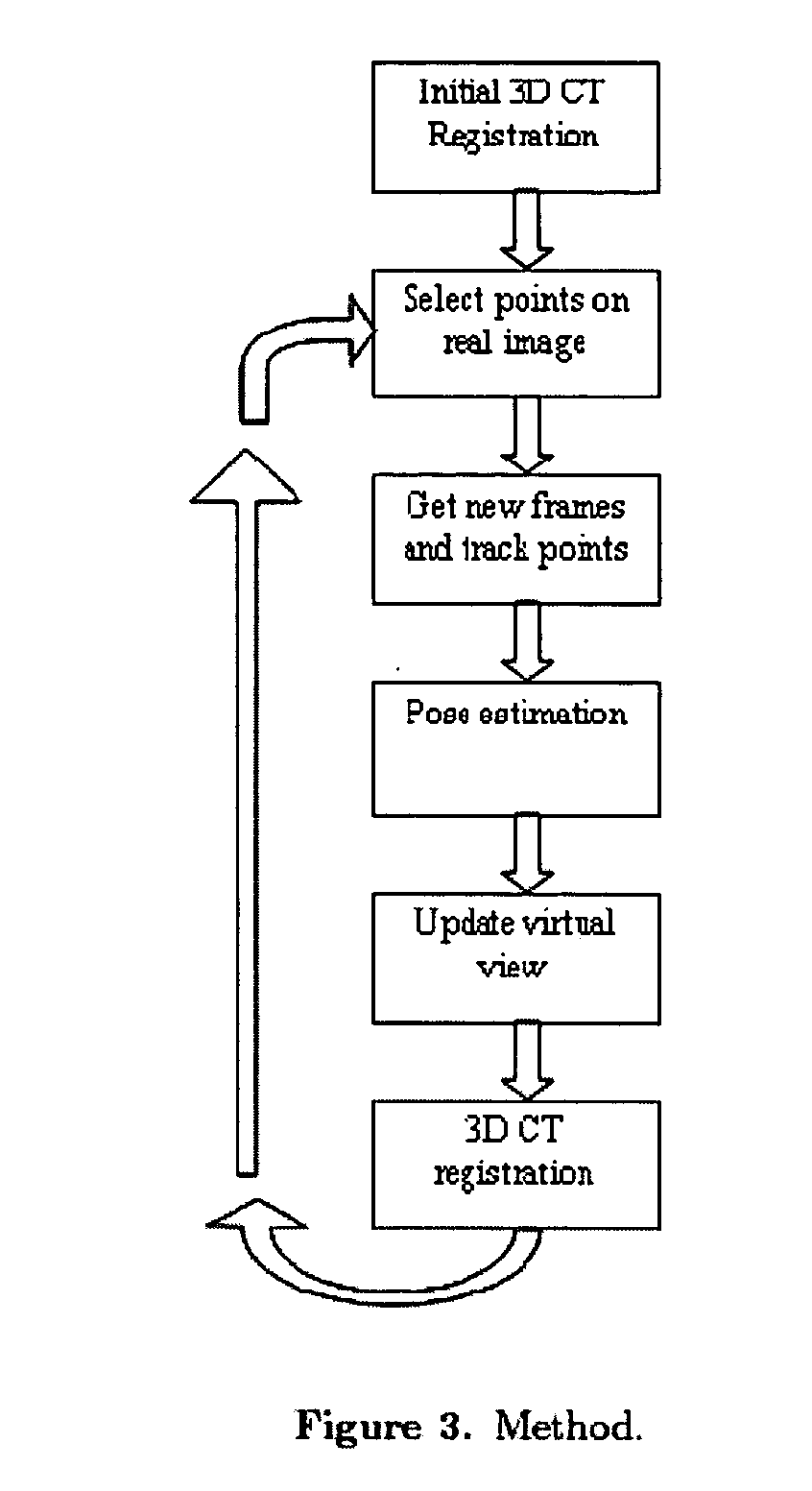
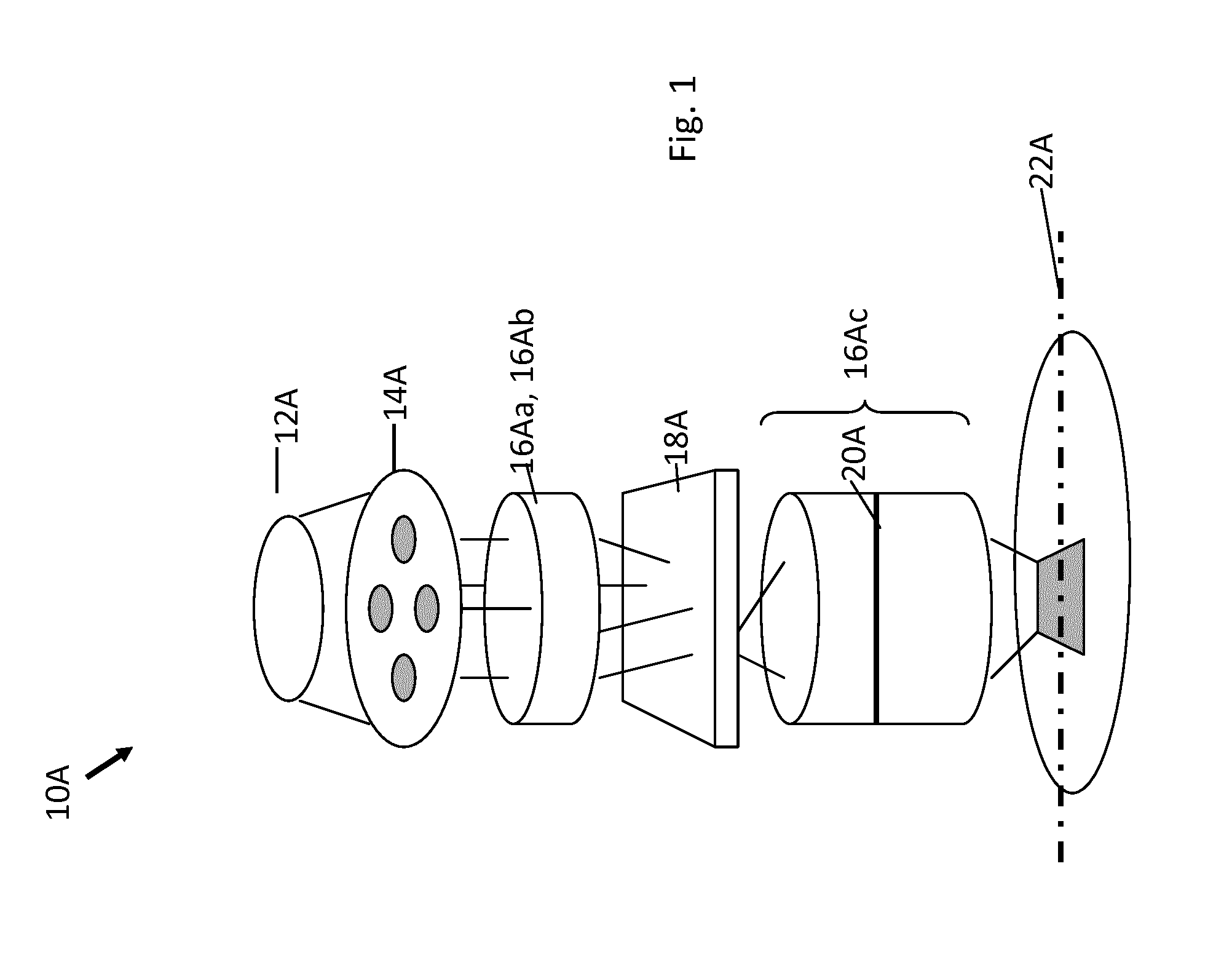
Guidance method based on 3D-2D pose estimation and 3D-CT registration with application to live bronchoscopy
ActiveUS7756563B2Maximizing costEasy to useRadiation diagnostic clinical applicationsSurgical navigation systemsGauss newton methodEndoscopic Procedure
A method provides guidance to the physician during a live bronchoscopy or other endoscopic procedures. The 3D motion of the bronchoscope is estimated using a fast coarse tracking step followed by a fine registration step. The tracking is based on finding a set of corresponding feature points across a plurality of consecutive bronchoscopic video frames, then estimating for the new pose of the bronchoscope. In the preferred embodiment the pose estimation is based on linearization of the rotation matrix. By giving a set of corresponding points across the current bronchoscopic video image, and the CT-based virtual image as an input, the same method can also be used for manual registration. The fine registration step is preferably a gradient-based Gauss-Newton method that maximizes the correlation between the bronchoscopic video image and the CT-based virtual image. The continuous guidance is provided by estimating the 3D motion of the bronchoscope in a loop. Since depth-map information is available, tracking can be done by solving a 3D-2D pose estimation problem. A 3D-2D pose estimation problem is more constrained than a 2D-2D pose estimation problem and does not suffer from the limitations associated with computing an essential matrix. The use of correlation-based cost, instead of mutual information as a registration cost, makes it simpler to use gradient-based methods for registration.
Owner:PENN STATE RES FOUND
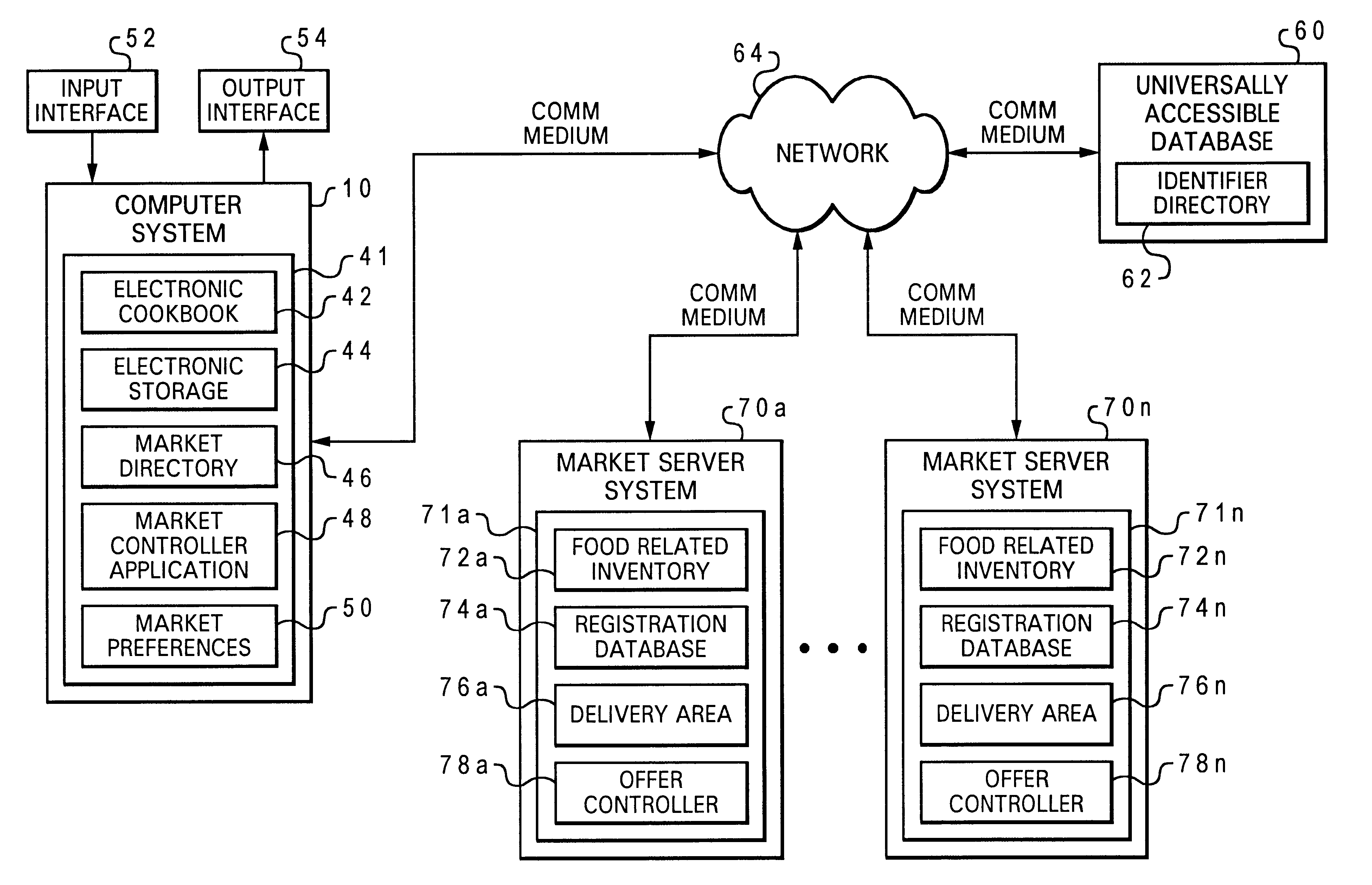
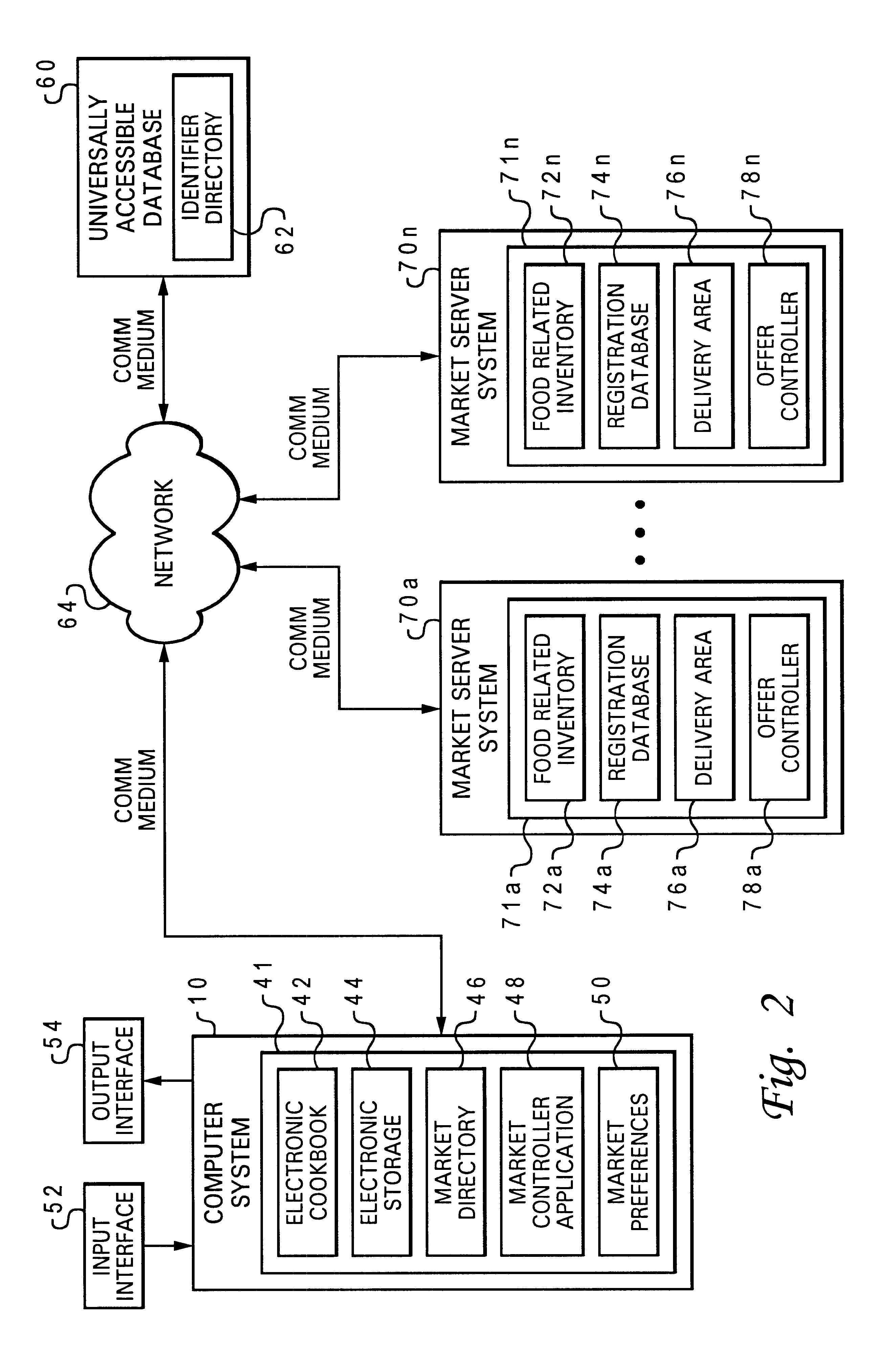
Managing inventory purchases
InactiveUS6430541B1Easy to manageMaximizing costAnimal feeding devicesBuying/selling/leasing transactionsComputerized systemDatabase
In accordance with the present invention, absent items from an intended inventory are monitored at a computer system. Search requests for the absent items are automatically transmitted from the computer system to multiple independent product databases each respectively associated with one of multiple retailers. Offers are returned from multiple retailers to the computer system, such that inventory purchases for the particular household are managed by the computer system.
Owner:IBM CORP
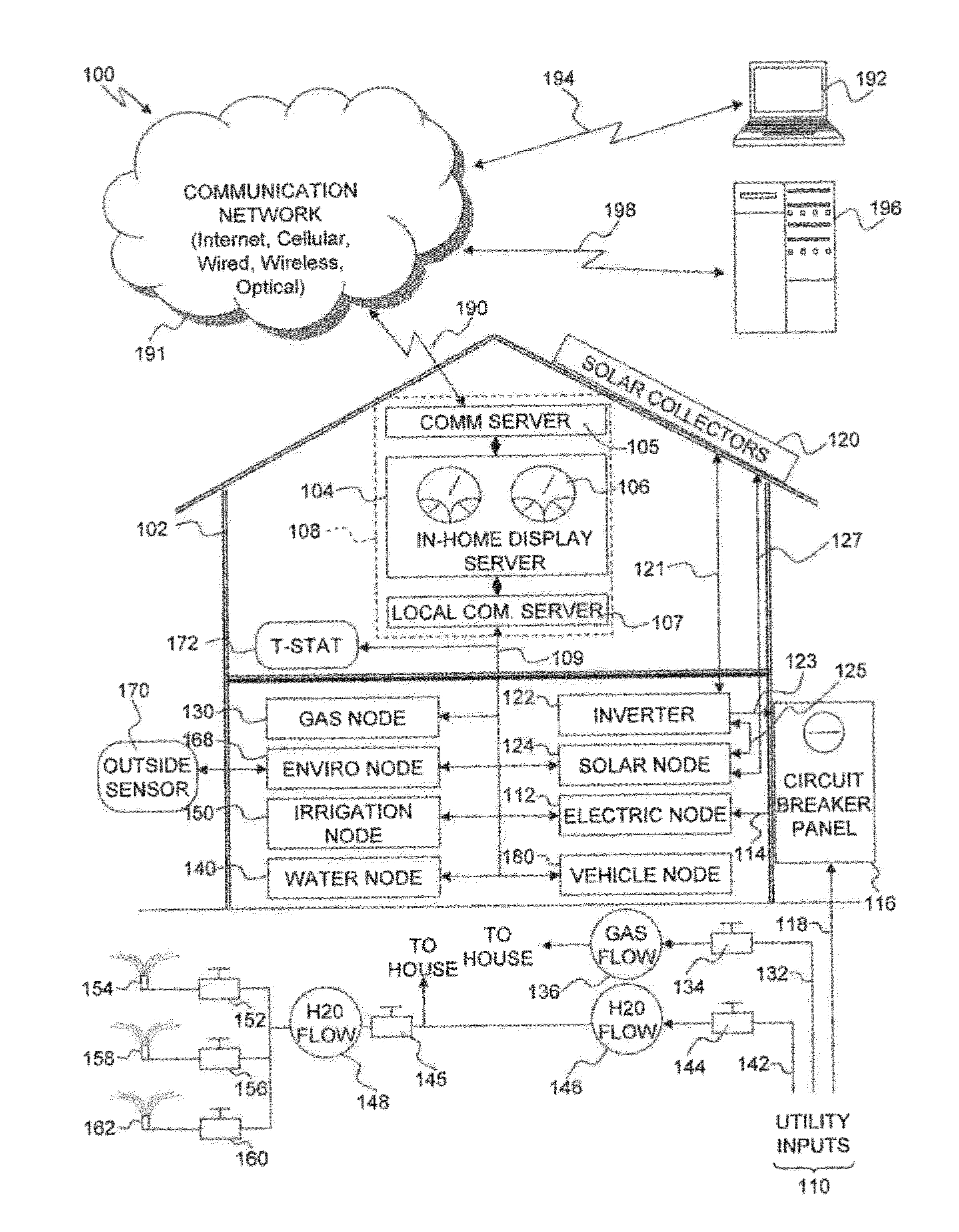
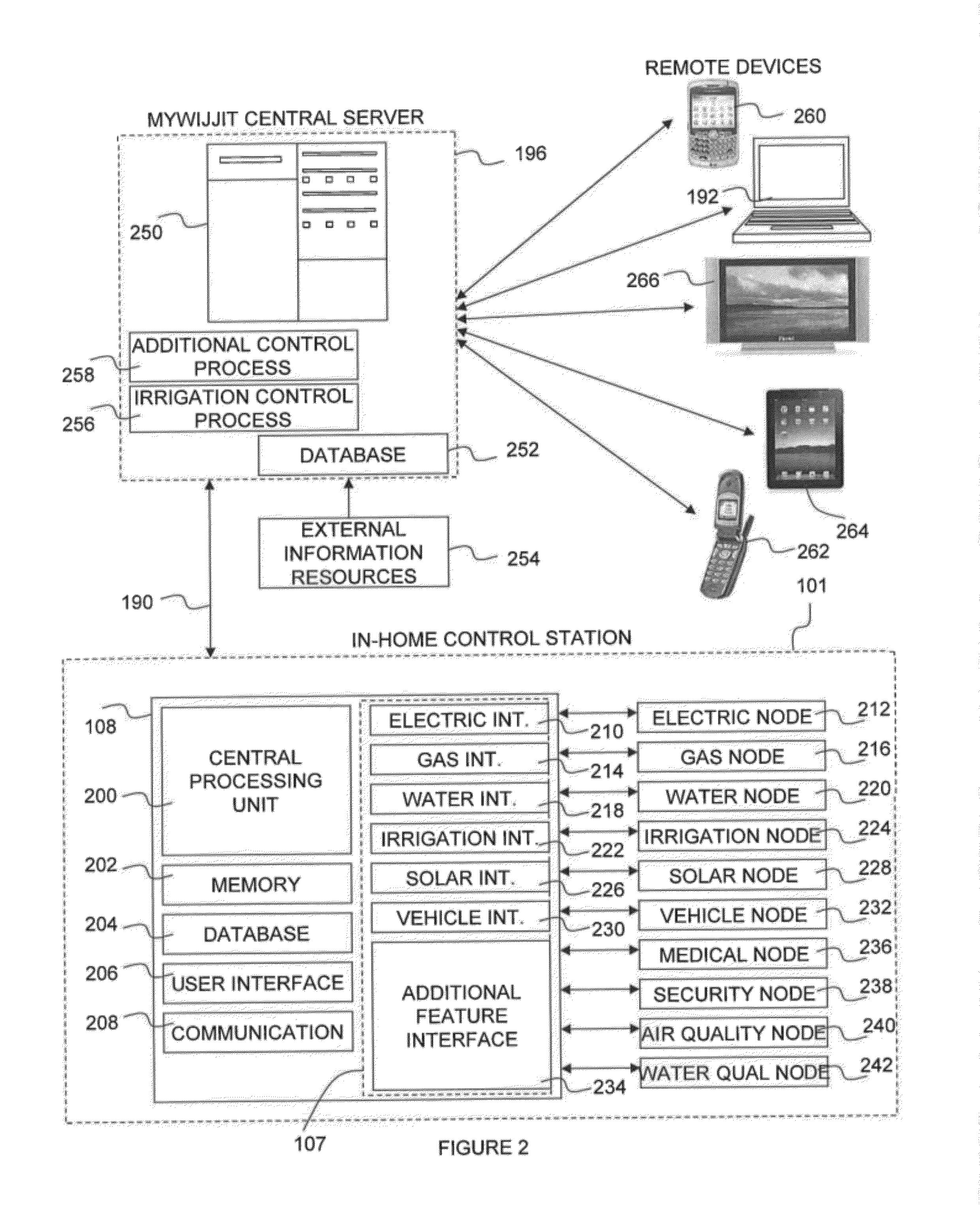
Resource management and control system
InactiveUS20120054125A1Easy to useSave effortProgramme controlData processing applicationsWater useService-level agreement
A resource management and control system includes real-time visibility to energy and water consumption. The resource management platform is flexible and allows users to create a system to suit their individual needs, and to make changes to that platform as their needs change and new needs arise. The resource management and control system monitors electricity and gas consumption, solar production, and water use in real time. The control system includes a number of wireless access nodes for interfacing with the various systems within a property, and also includes monitoring, diagnostic and alerting capabilities. Billing system integration provides historical data for the cost of resource usage and production relative to time, geography and consumer service level agreements and allows the user the ability to directly correlate consumption behaviors with cost implications. Autonomously operating control processes are incorporated to automatically configure and control devices for optimal resource consumption and application.
Owner:CELEVATORON ERIC DOUGLASS +1
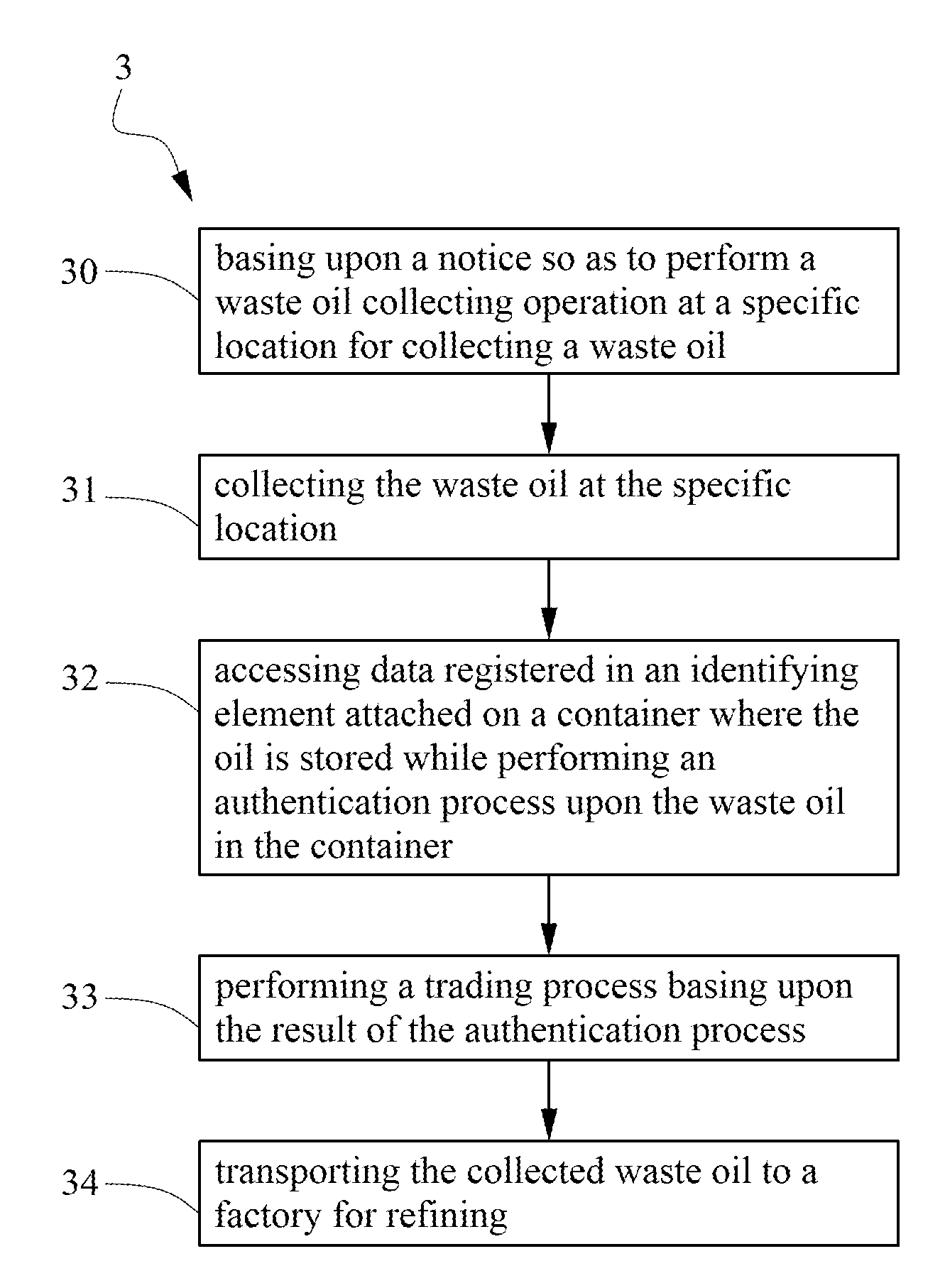
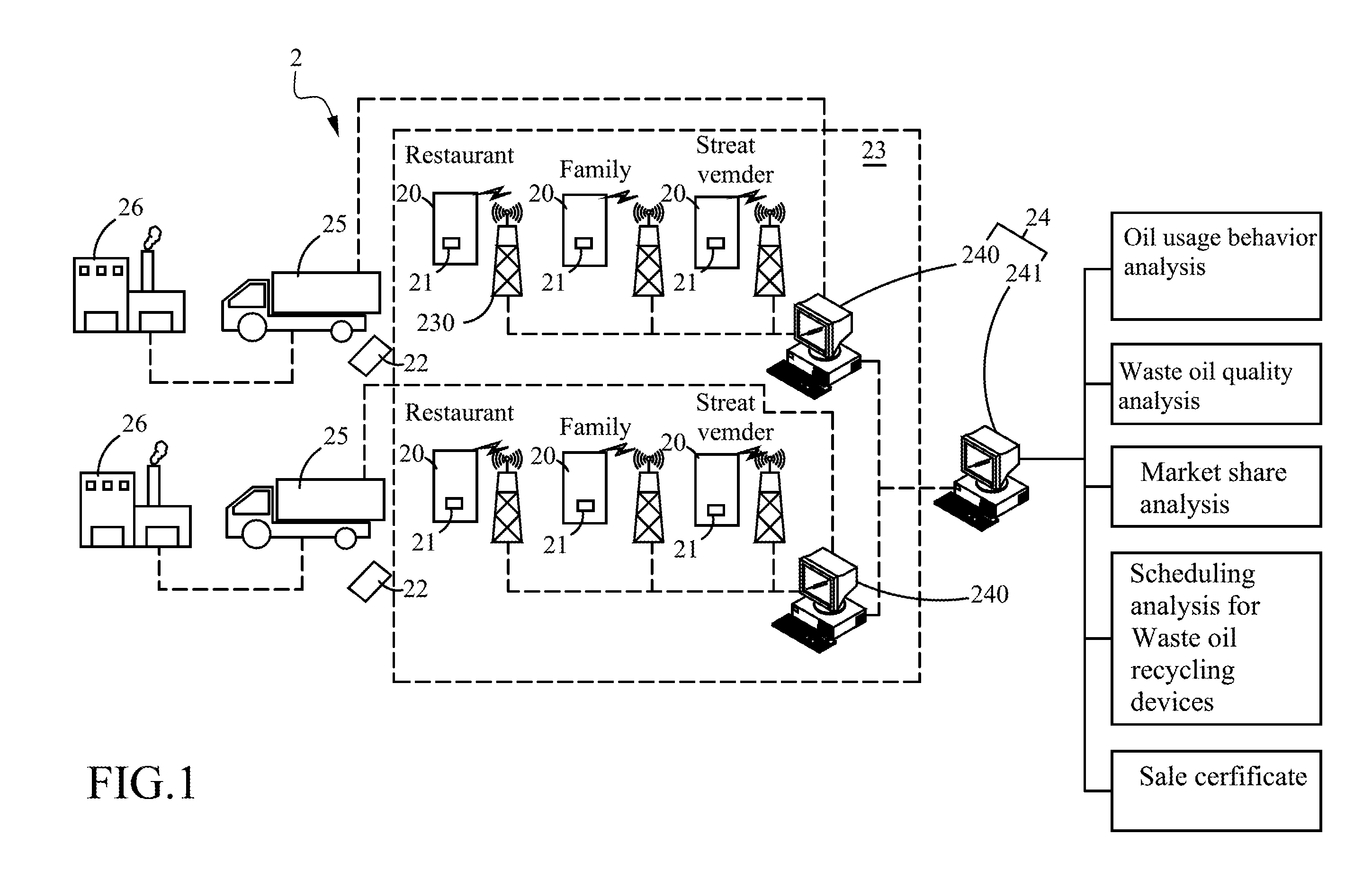
System and method for managing waste oil
InactiveUS20100312601A1Promote productionMaximizing costElectric signal transmission systemsDigital data processing detailsEngineeringWaste oil
The present invention provides a system for managing waste oil, which comprises at least one container wherein each container has an identifying element disposed thereon for recording information with respect to the waste oil provider, container, and quality of the waste oil. By means of the system, the present invention further provides a method for managing and trading the waste oil, which refers to a business method for implementing transaction such as sale of waste oil or exchange between waste oil and daily necessaries according to the information of the identifying element whereby the business center can control the logistics, cash flow and information flow easily and efficiently so that the waste oil provider can have service of transaction easily.
Owner:GITEN ENERGY MFG
Guidance method based on 3D-2D pose estimation and 3D-CT registration with application to live bronchoscopy
ActiveUS20070015997A1Maximizing costEasy to useRadiation diagnostic clinical applicationsSurgical navigation systemsGauss newton methodEndoscopic Procedure
A method provides guidance to the physician during a live bronchoscopy or other endoscopic procedures. The 3D motion of the bronchoscope is estimated using a fast coarse tracking step followed by a fine registration step. The tracking is based on finding a set of corresponding feature points across a plurality of consecutive bronchoscopic video frames, then estimating for the new pose of the bronchoscope. In the preferred embodiment the pose estimation is based on linearization of the rotation matrix. By giving a set of corresponding points across the current bronchoscopic video image, and the CT-based virtual image as an input, the same method can also be used for manual registration. The fine registration step is preferably a gradient-based Gauss-Newton method that maximizes the correlation between the bronchoscopic video image and the CT-based virtual image. The continuous guidance is provided by estimating the 3D motion of the bronchoscope in a loop. Since depth-map information is available, tracking can be done by solving a 3D-2D pose estimation problem. A 3D-2D pose estimation problem is more constrained than a 2D-2D pose estimation problem and does not suffer from the limitations associated with computing an essential matrix. The use of correlation-based cost, instead of mutual information as a registration cost, makes it simpler to use gradient-based methods for registration.
Owner:PENN STATE RES FOUND
Model for calculating a stochastic variation in an arbitrary pattern
ActiveUS20170010538A1Maximizing costMinimize timePhotomechanical exposure apparatusCAD circuit designSpatial imageComputer science
A method of determining a relationship between a stochastic variation of a characteristic of an aerial image or a resist image and one or more design variables, the method including: measuring values of the characteristic from a plurality of aerial images and / or resist images for each of a plurality of sets of values of the one or more design variables; determining a value of the stochastic variation, for each of the plurality of sets of values of the one or more design variables, from a distribution of the values of the characteristic for that set of values of the one or more design variables; and determining the relationship by fitting one or more parameters from the values of the stochastic variation and the plurality of sets of values of the one or more design variables.
Owner:ASML NETHERLANDS BV
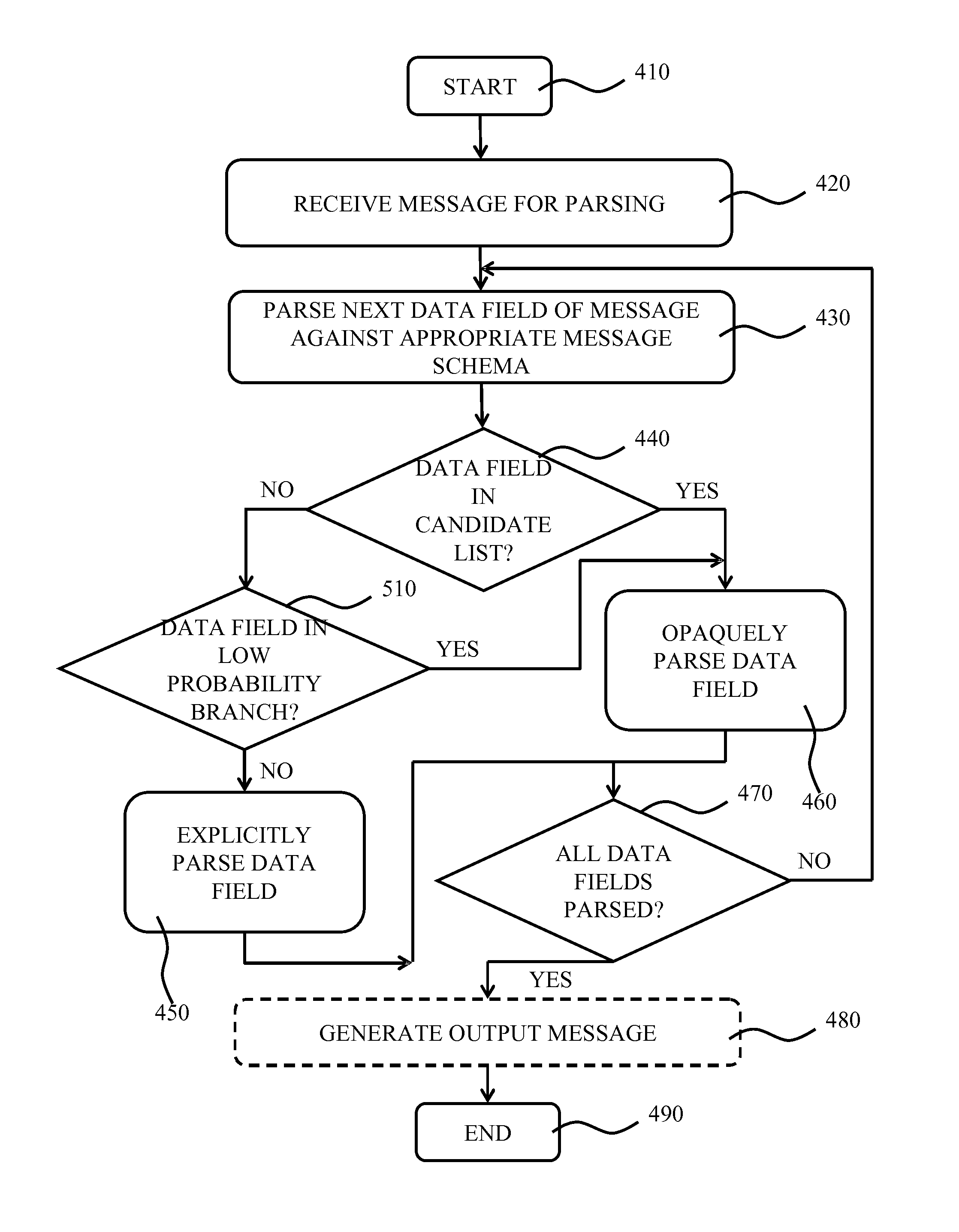
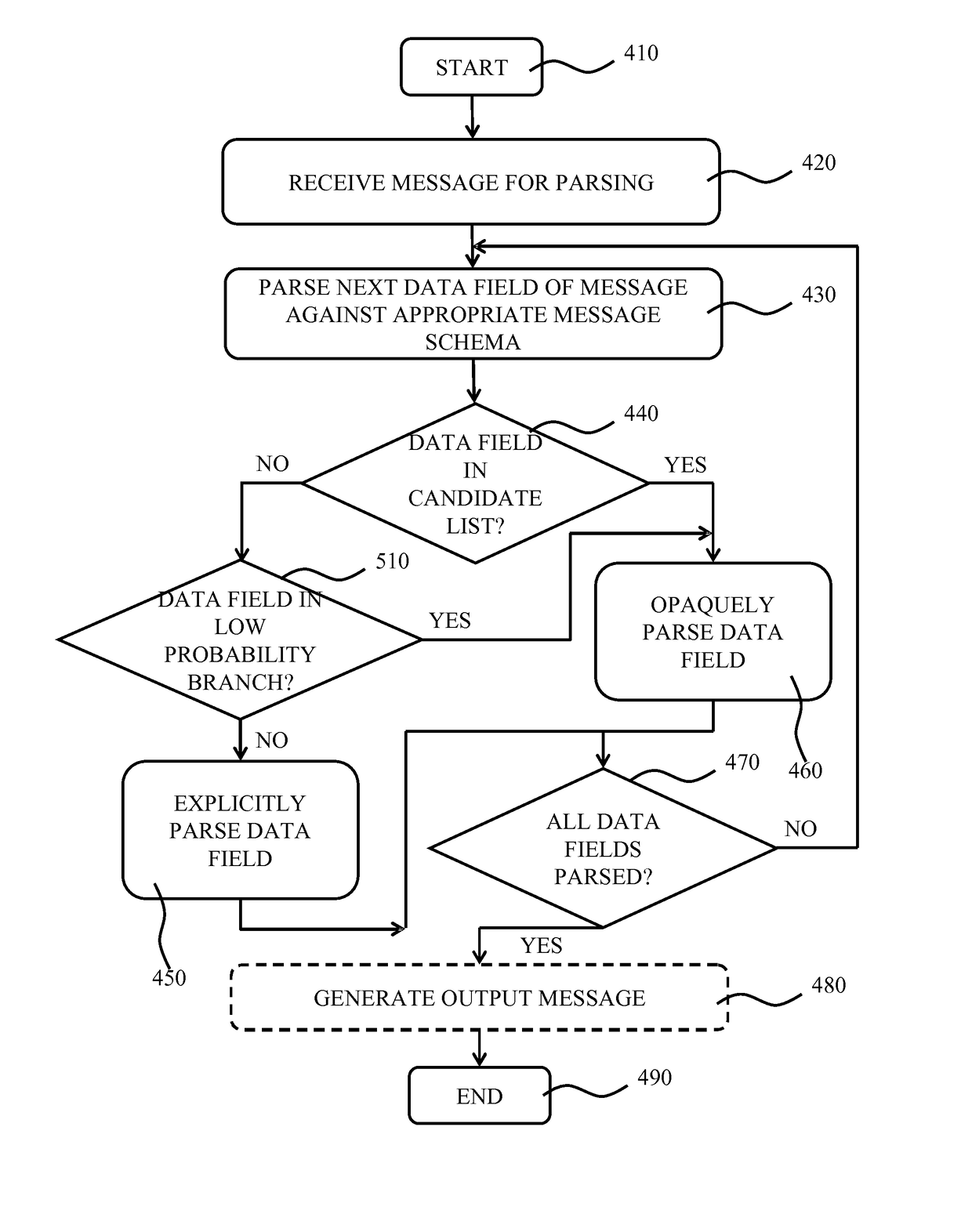
Opaque Message Parsing
ActiveUS20150161098A1Improved parsing cost reductionReduce riskDigital data processing detailsNatural language data processingData processing systemData field
A computer-implemented method of parsing a message comprising a sequence of data fields, the method comprising evaluating program code for processing the parsed message to identify a first set of data fields of the message that are referenced in said program code; identifying the boundaries of the data fields in a schema defining the format of said message; identifying a second set of data fields in said schema related to the first set of data fields by reference, said second set further including the first set; and sequentially parsing the message using the identified data field boundaries, wherein said parsing step comprises skipping data fields in said sequence that precede the first data field belonging to the second set. A computer program product comprising program code for implementing this method and a data processing system adapted to implement this method are also disclosed.
Owner:IBM CORP
Image log slope (ILS) optimization
ActiveUS20180011407A1Reducing characteristic variationReduce variationPhotomechanical exposure apparatusMicrolithography exposure apparatusResistAlgorithm
A method to improve a lithographic process of imaging a portion of a design layout onto a substrate using a lithographic projection apparatus, the method including: computing a multi-variable cost function, the multi-variable cost function being a function of a stochastic variation of a characteristic of an aerial image or a resist image, or a function of a variable that is a function of the stochastic variation or that affects the stochastic variation, the stochastic variation being a function of a plurality of design variables that represent characteristics of the lithographic process; and reconfiguring one or more of the characteristics of the lithographic process by adjusting one or more of the design variables until a certain termination condition is satisfied.
Owner:ASML NETHERLANDS BV
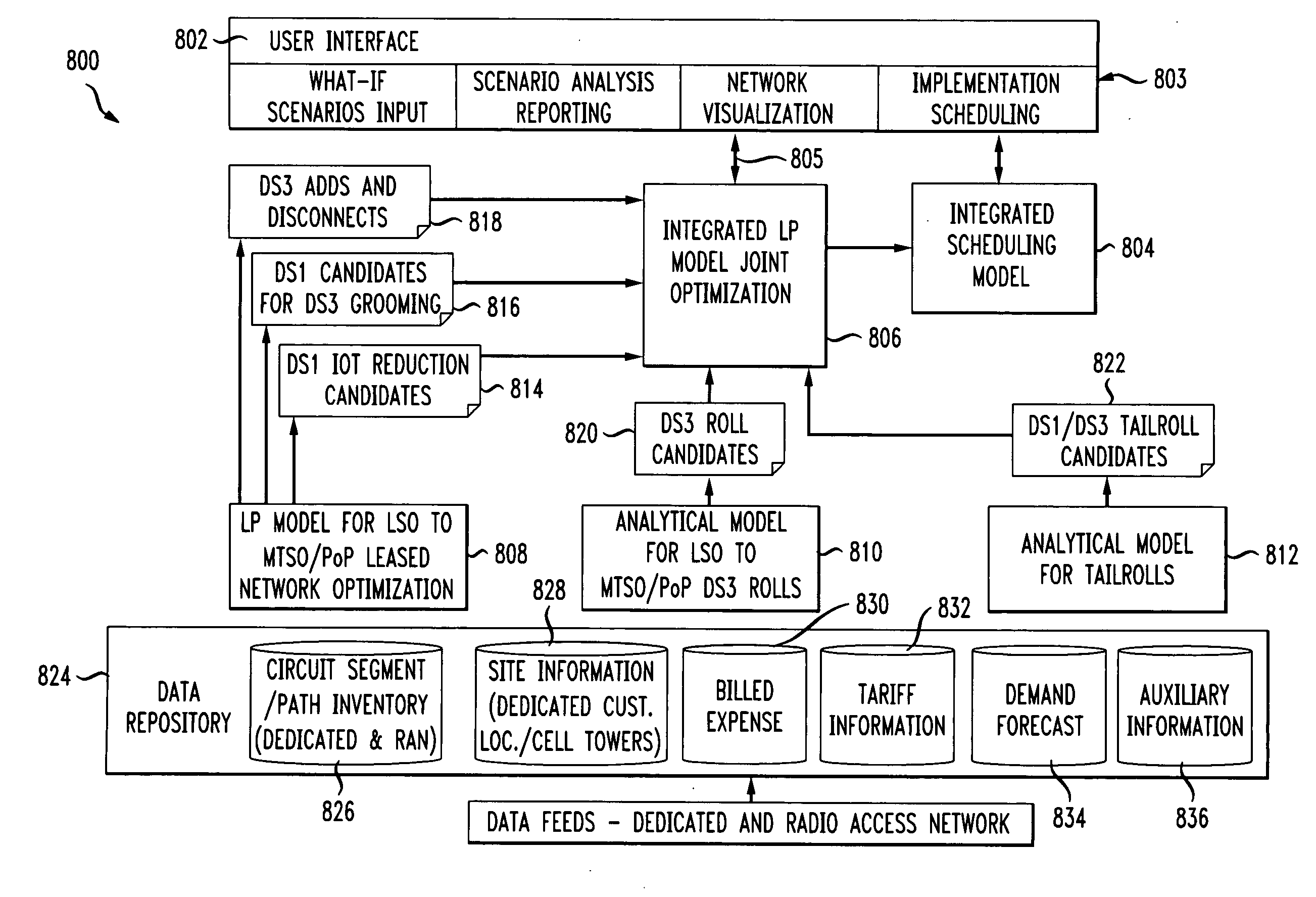
Method and apparatus for joint optimization of dedicatedand radio access networks
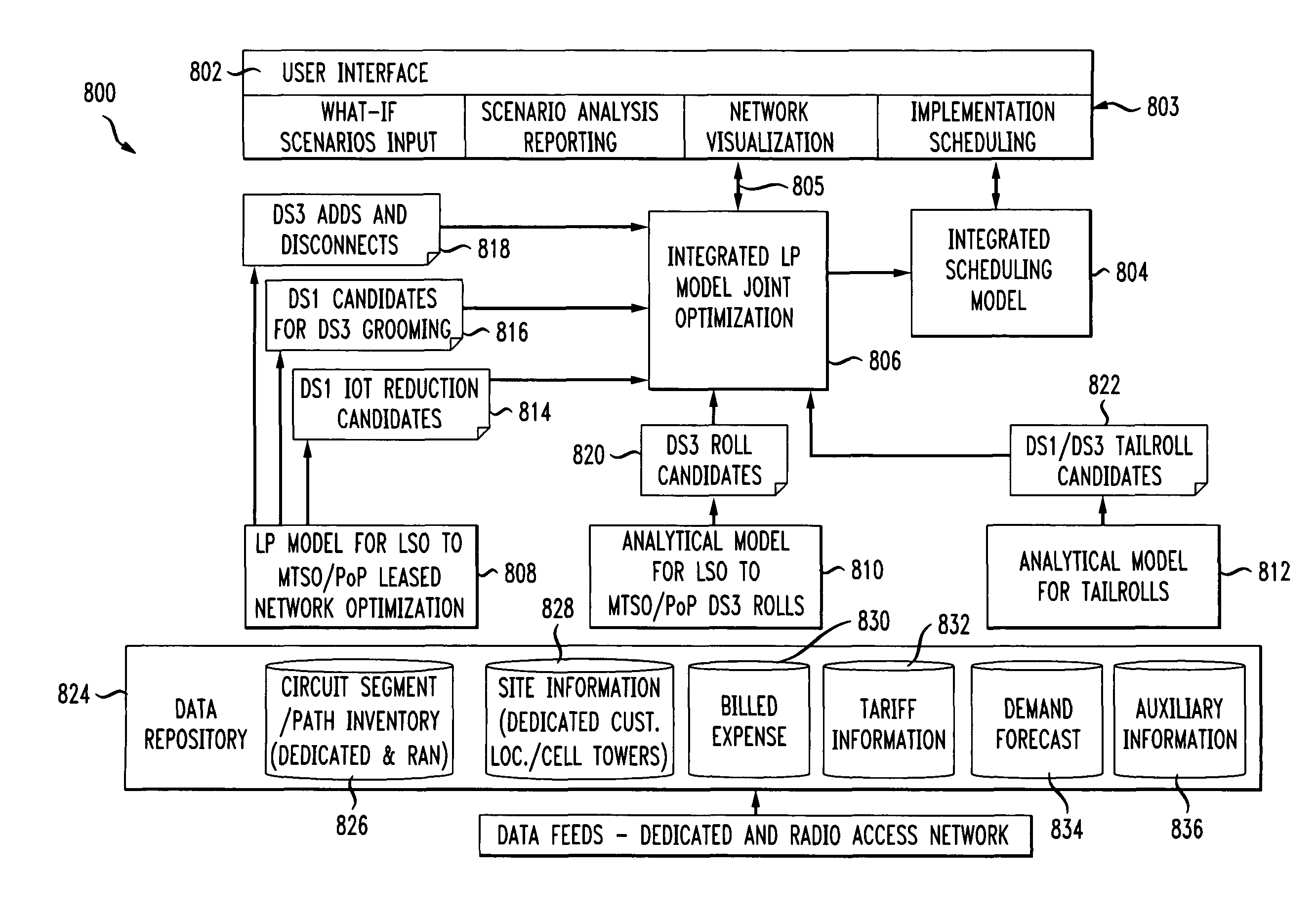
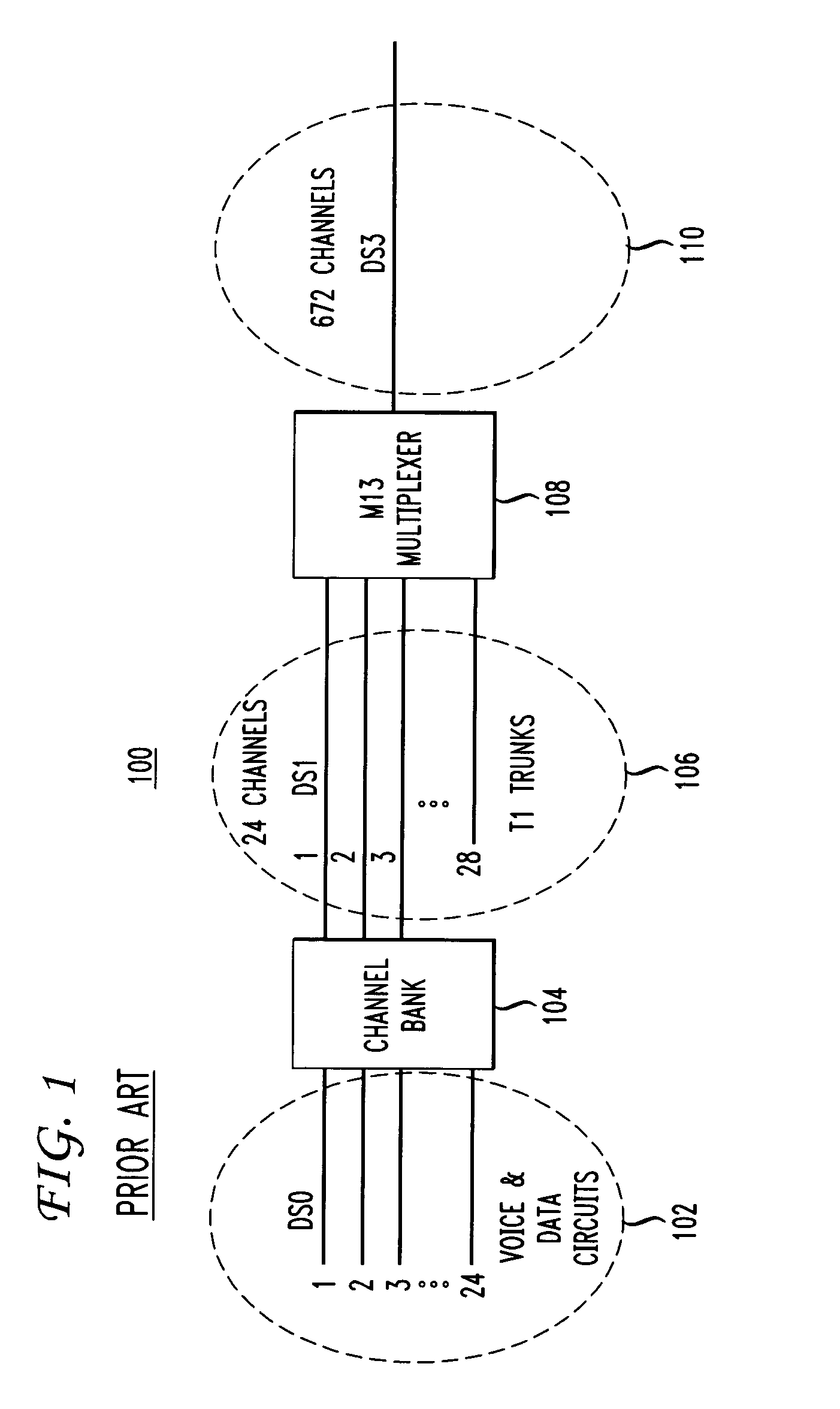
InactiveUS20100120440A1Maximizes cost savingMinimize resource requirementNetwork planningAccess networkRadio access network
A computerized method and system for integrated access network business planning for a telecommunications carrier. The invention enables a user to input a set of network business planning parameters that are utilized by a linear programming model to jointly optimize a carrier's dedicated and radio access network by executing a plurality of network optimization models and determine network configuration changes for the dedicated and radio access networks as a constrained optimization based on the set of business planning parameters.
Owner:AT&T INTPROP I L P
Systems and methods for reducing stranded inventory
InactiveUS20070220047A1Reduce amountMaximizing cost savingResourcesSpecial data processing applicationsEngineeringCost savings
Determining a particular product mix of old and new products to either minimize stranded inventory of old unique sub-components composing the old product or to minimize cost savings by phasing out the old unique sub-components of the old product is described. When a new product costs the same or more than the old product, a product mix which minimizes stranded inventory is determined. To this end, a liability on inventory of old unique sub-components at a number of build out quantities including the total number of product units to produce is determined. Additionally, a number of old products to produce is selected to correspond to a point where the liability on inventory of old unique sub-components is constant between consecutive build out quantities in order to reduce stranded inventory. When a new product costs less than the old product, a product mix which maximizes cost savings is determined. To this end, a liability on inventory of old unique sub-components at a number of build out quantities including the total number of product units to produce is determined. An economic buildout plan which indicates cost savings resulting from replacing the old product with the cheaper new product at the number of build out quantities including the total number of product units to produce is also determined. A number of old products to produce is selected to correspond to the maximum cost savings as indicated by the largest value in the economic buildout plan.
Owner:LUCENT TECH INC
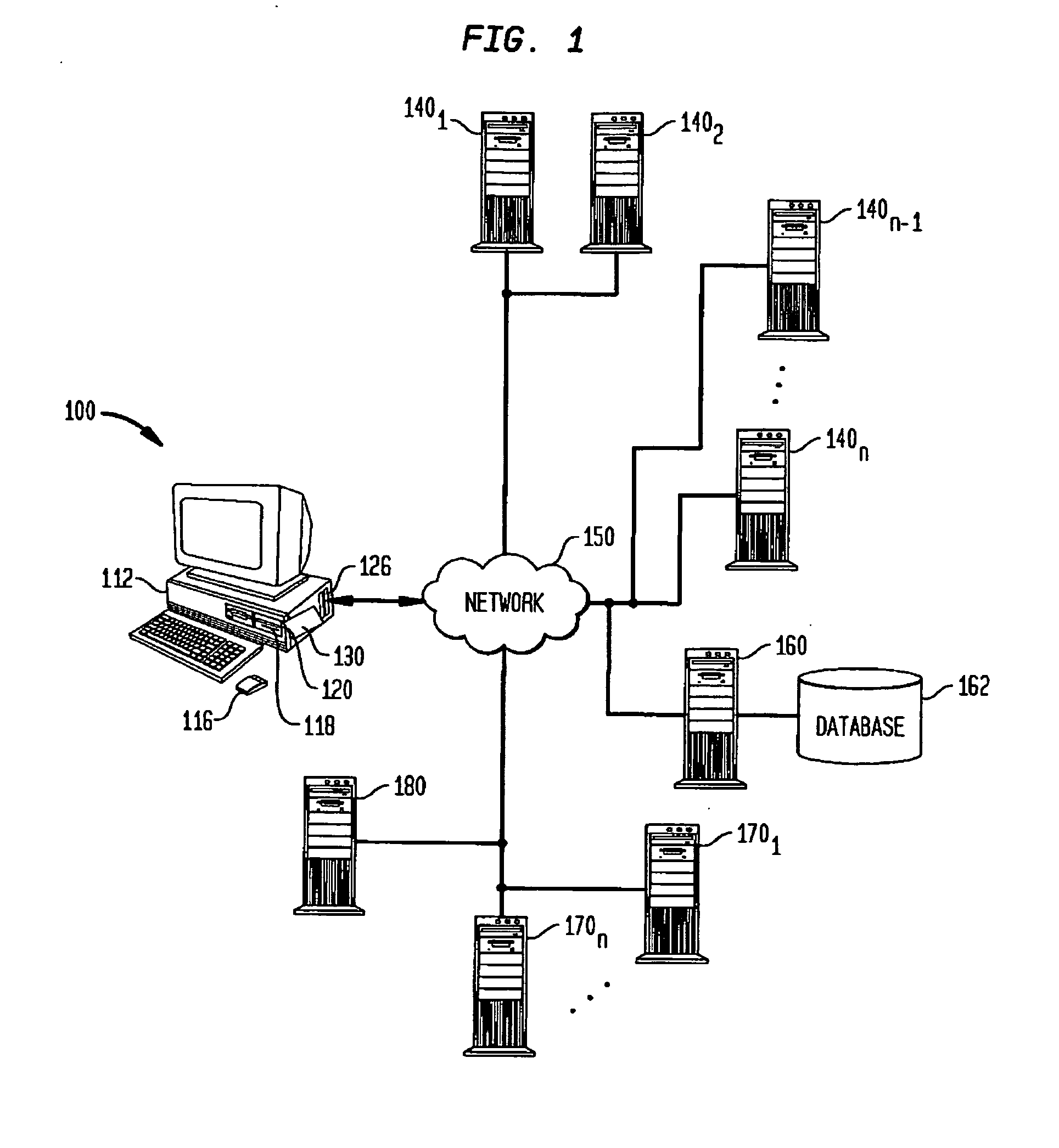
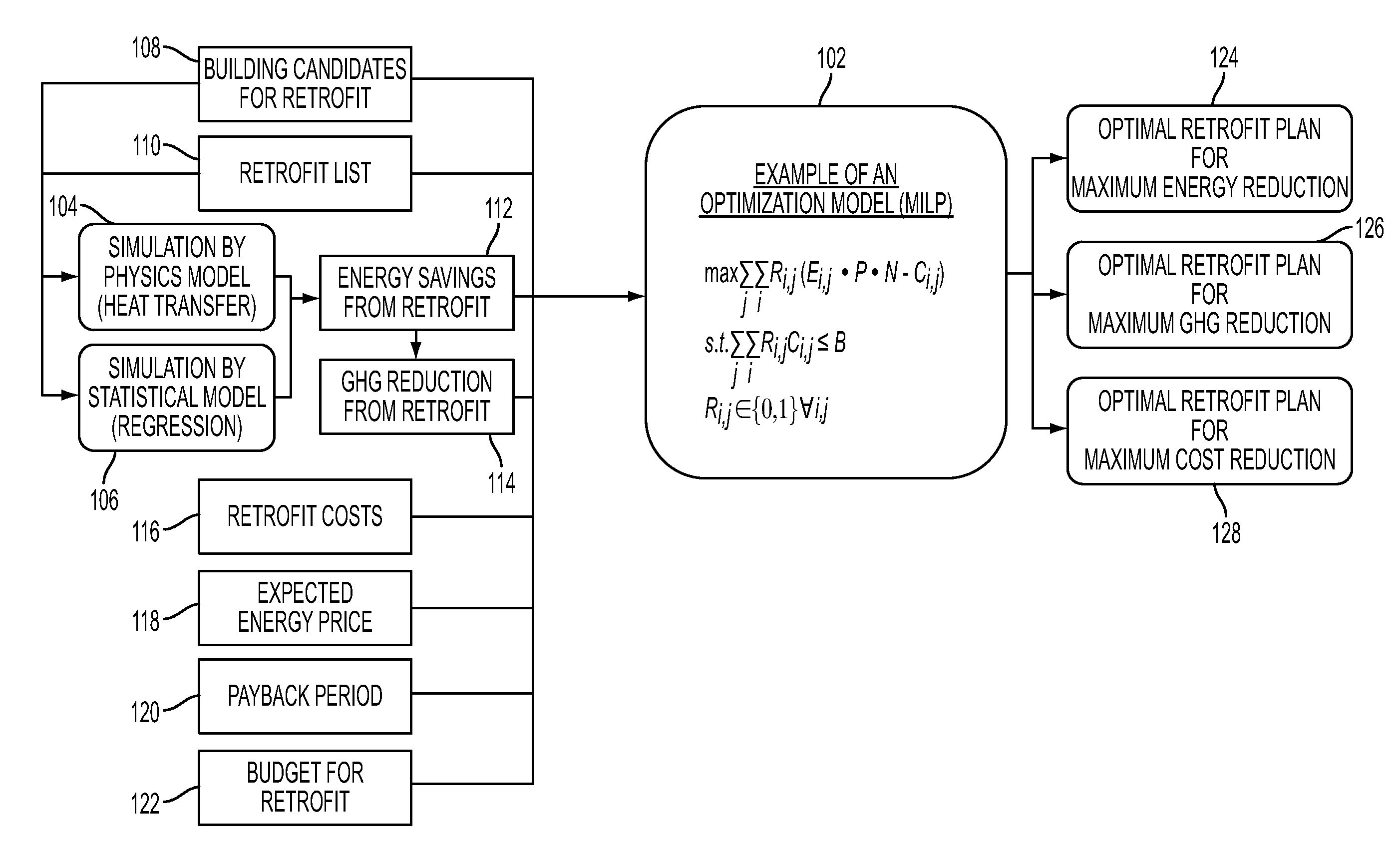
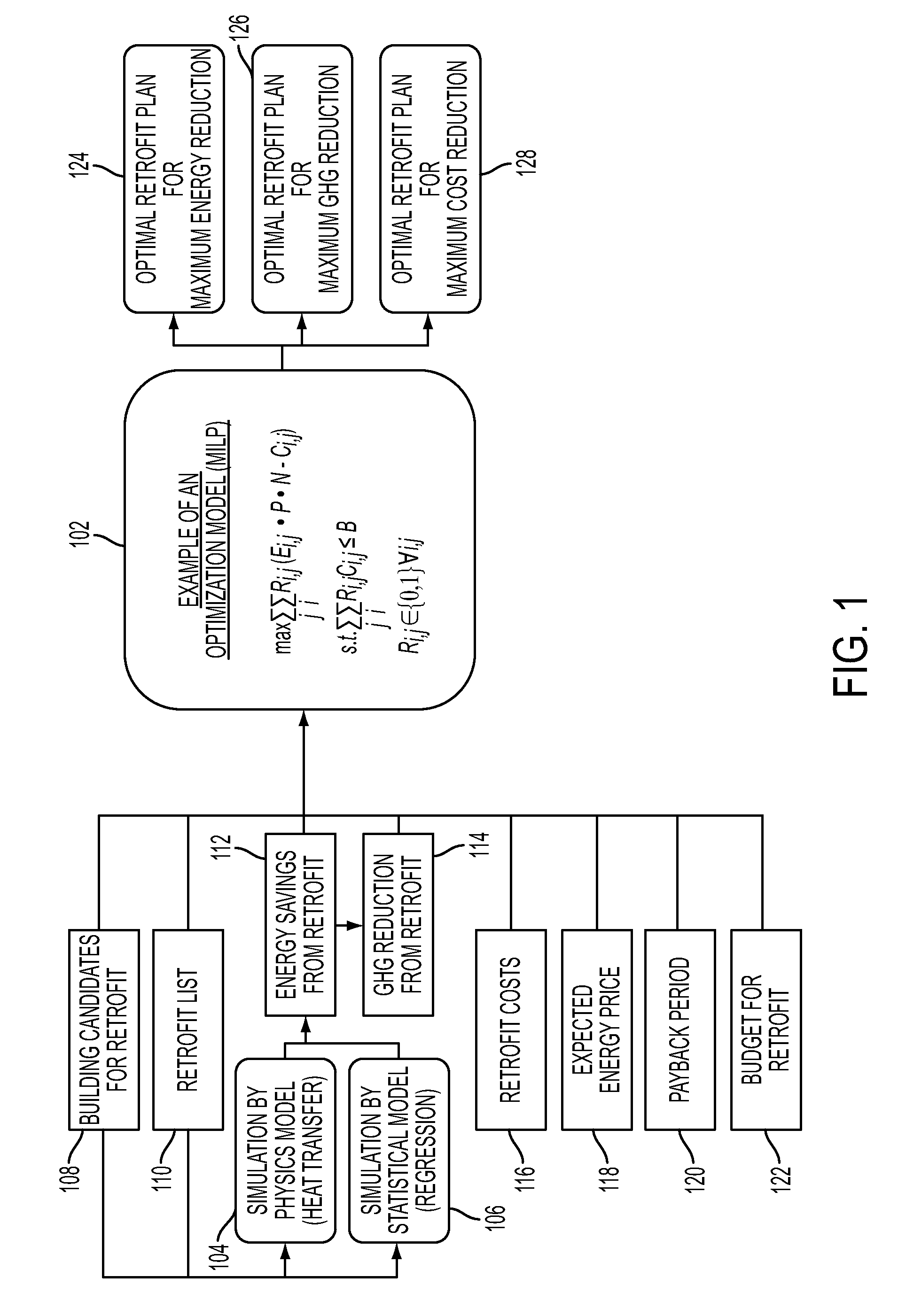
Optimal planning of building retrofit for a portfolio of buildings
InactiveUS20120310689A1Maximizing costSave energyForecastingEnergy reductionGreen house gas emission
Generating an optimal planning of building retrofit for a portfolio of buildings may include providing a plurality of objective functions that may be selected for maximizing cost reduction, maximizing green house gas emission reduction, or maximizing energy reduction, or combinations thereof. The objective function may be solved based on information including at least a retrofit cost for retrofitting a building, payback period specifying the length of time needed to recover the retrofit cost, a budget available for retrofitting the building, expected price of energy, estimated energy savings from retrofitting and estimated green house gas emission from retrofitting. The planning of building retrofit may be generated based on the solutions of one or more of the objective functions, which may provide for an optimal plan of building retrofit.
Owner:IBM CORP
Optimization of source and bandwidth for new and existing patterning devices
ActiveUS20180356734A1Improve image qualityIncreased latitudePhotomechanical exposure apparatusMicrolithography exposure apparatusPhotolithographyEngineering
A method to improve a lithographic process of imaging a portion of a design layout onto a substrate using a lithographic apparatus, the method including: computing a multi-variable cost function, the multi-variable cost function being a function a plurality of design variables that represent characteristics of the lithographic process; and reconfiguring one or more of the characteristics of the lithographic process by adjusting one or more of the design variables until a certain termination condition is satisfied; wherein a bandwidth of a radiation source of the lithographic apparatus is allowed to change during the reconfiguration.
Owner:ASML NETHERLANDS BV +1
Opaque message parsing
ActiveUS9882844B2Reduce riskMaximizing costNatural language data processingSemi-structured data mapping/conversionData processing systemData field
A computer-implemented method of parsing a message comprising a sequence of data fields, the method comprising evaluating program code for processing the parsed message to identify a first set of data fields of the message that are referenced in said program code; identifying the boundaries of the data fields in a schema defining the format of said message; identifying a second set of data fields in said schema related to the first set of data fields by reference, said second set further including the first set; and sequentially parsing the message using the identified data field boundaries, wherein said parsing step comprises skipping data fields in said sequence that precede the first data field belonging to the second set. A computer program product comprising program code for implementing this method and a data processing system adapted to implement this method are also disclosed.
Owner:INT BUSINESS MASCH CORP
Model for calculating a stochastic variation in an arbitrary pattern
ActiveUS10545411B2Maximizing costMinimize timePhotomechanical exposure apparatusCAD circuit designAlgorithmSpatial image
Owner:ASML NETHERLANDS BV
Method for separating blind signal and apparatus for performing the same
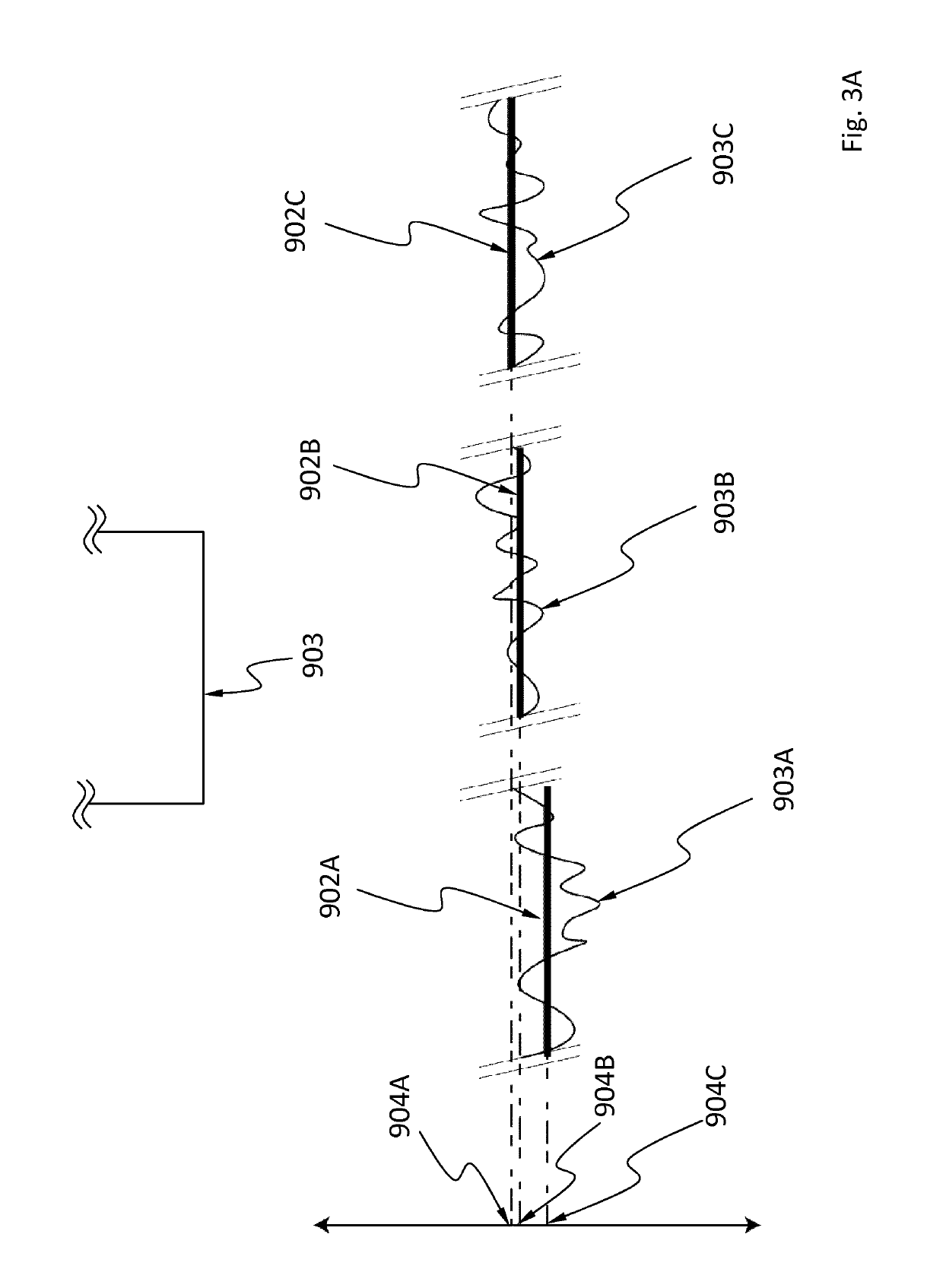
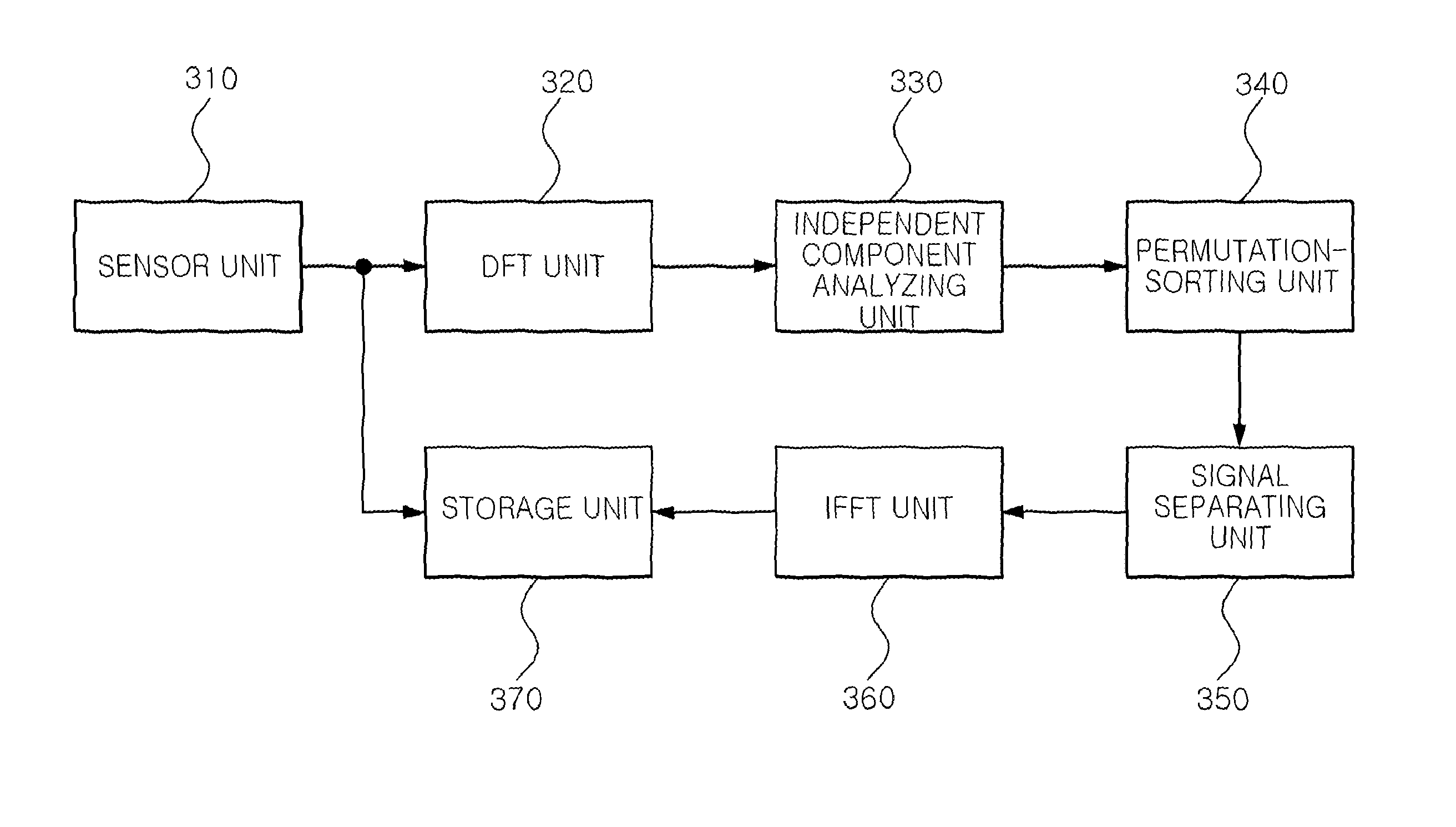
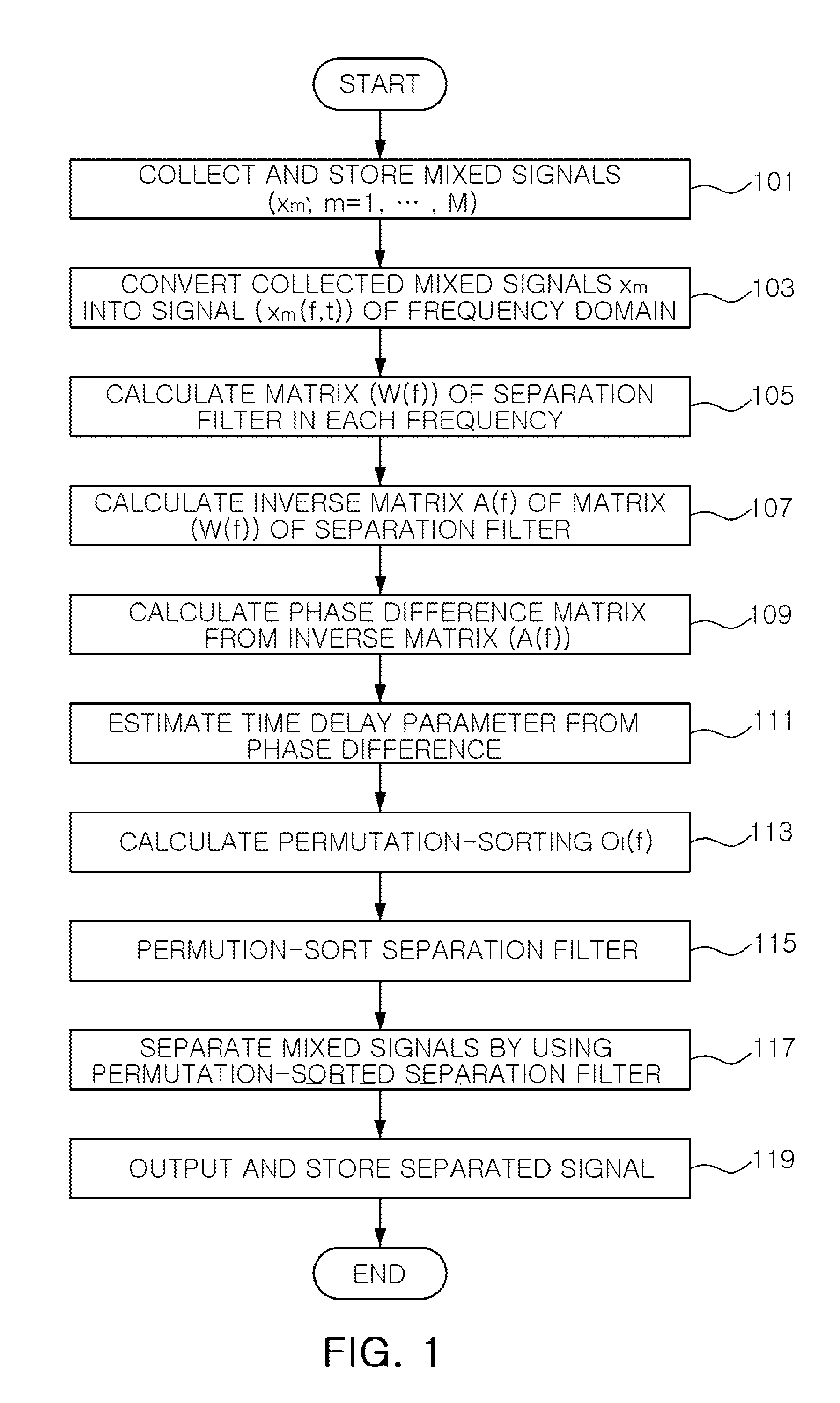
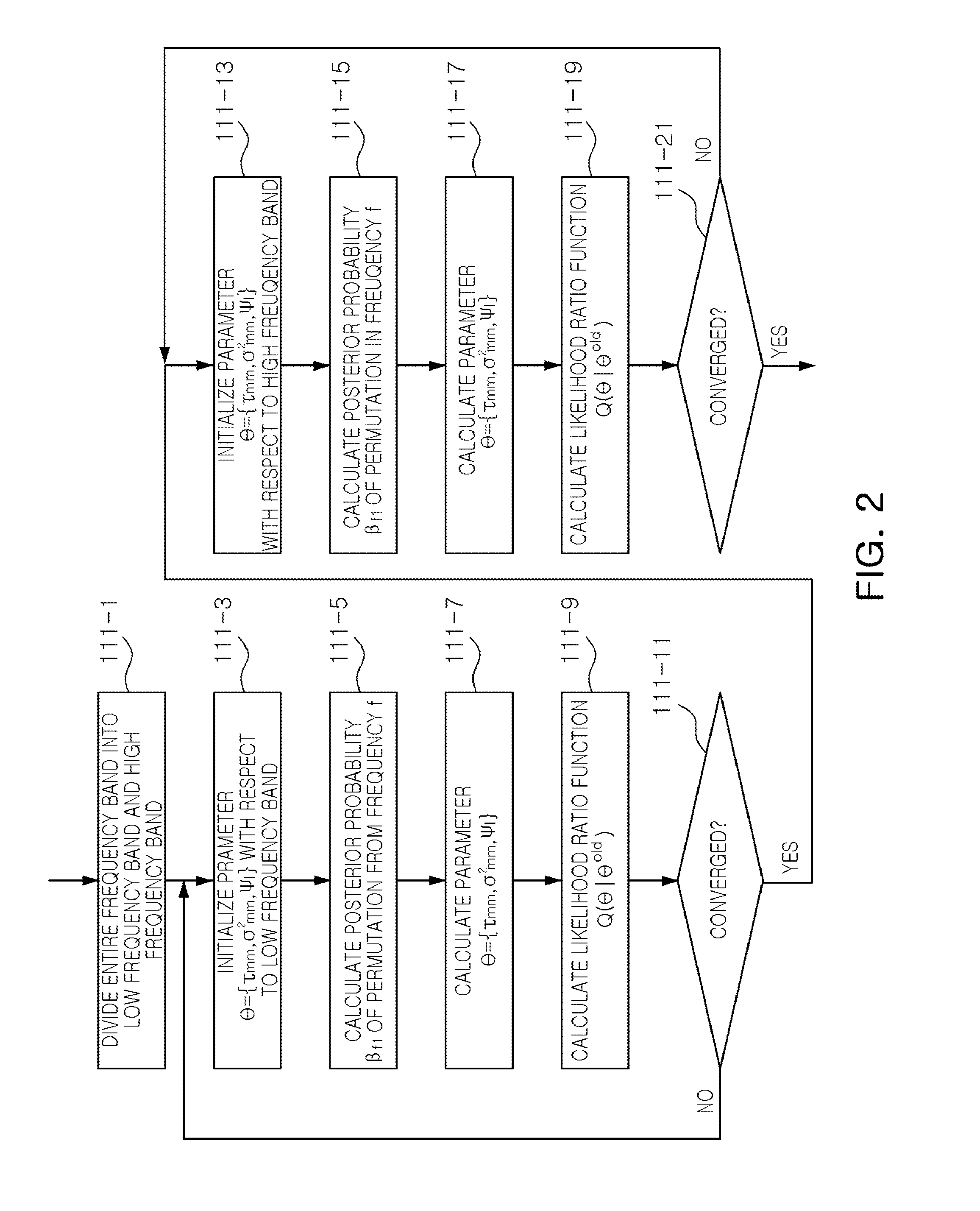
InactiveUS8521477B2Easy to separateMaximizing costAmplifier modifications to reduce noise influenceSpeech analysisTime domainPhase difference
A method for separating a blind signal includes: converting mixed signals of a time domain collected by using a plurality of sensors into mixed signals of a frequency domain; calculating a separation filter from the mixed signals which have been converted into those of the frequency domain; calculating an inverse filter of the separation filter; calculating the difference in phase between the respective sensors from the calculated inverse filter; permutation-sorting the separation filter by using the calculated phase difference; and separating the mixed signals of the frequency domain by using the permutation-sorted separation filter.
Owner:ELECTRONICS & TELECOMM RES INST +1
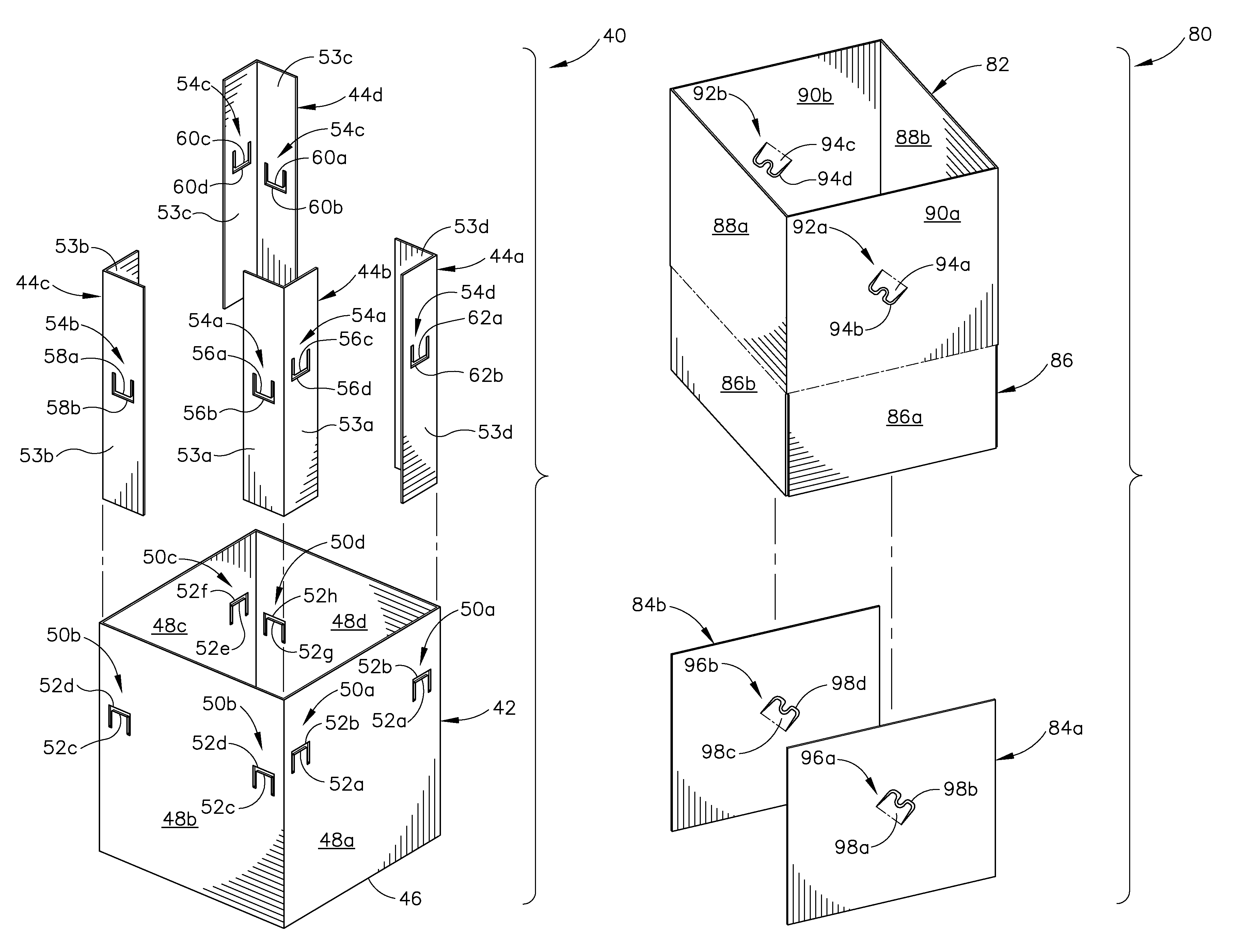
Self-Locking Support Panel For Corrugated Container
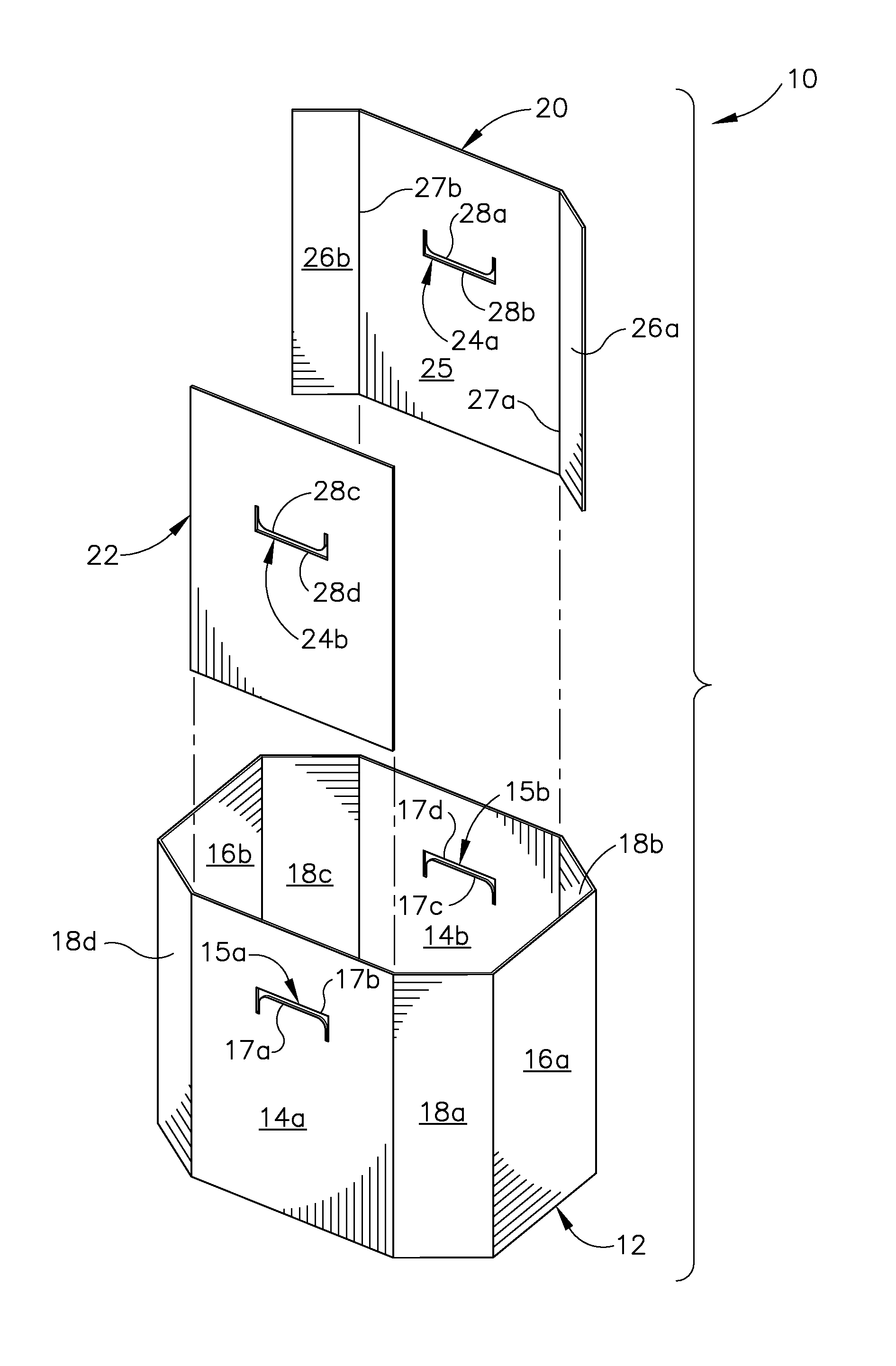
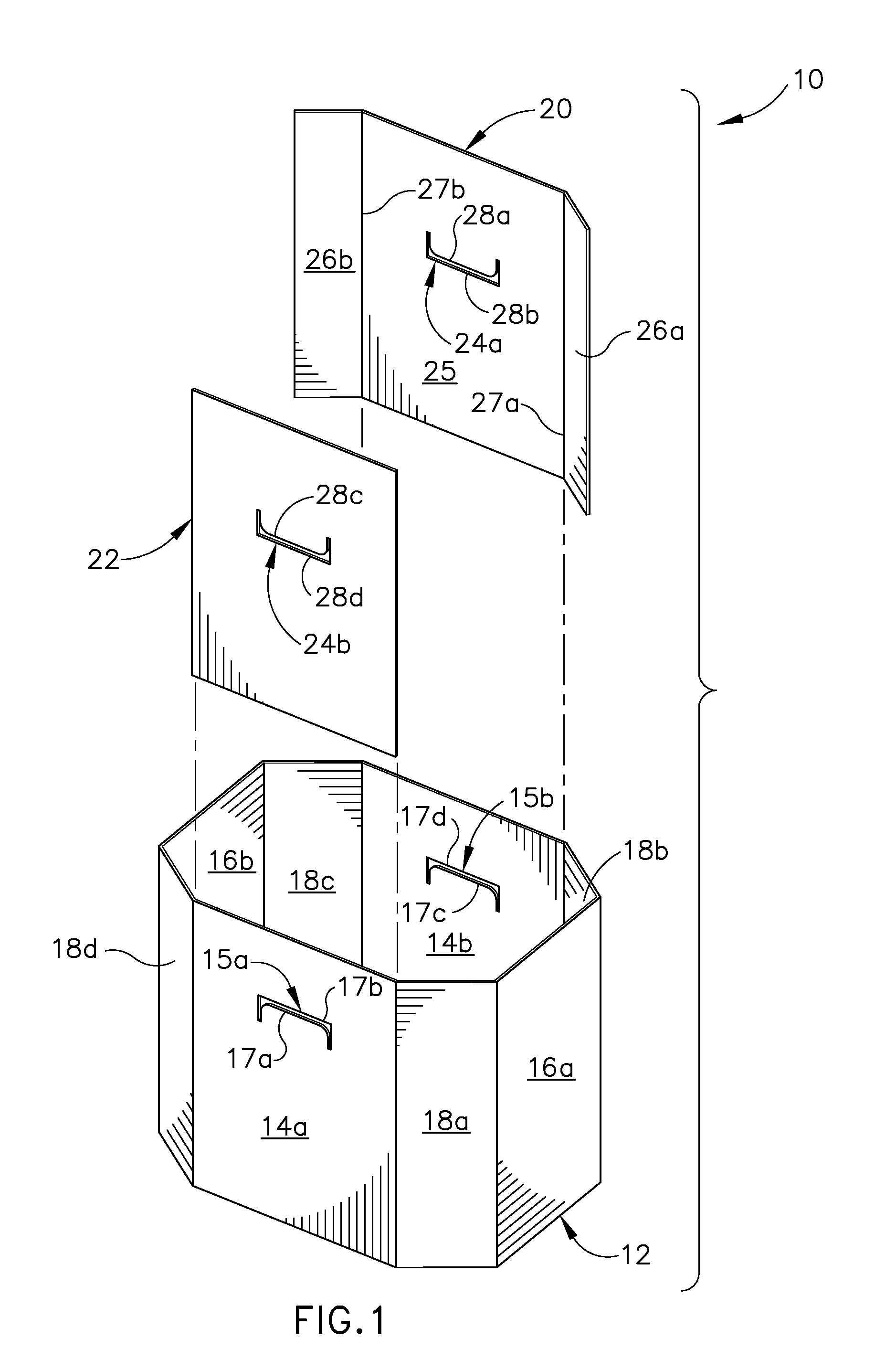
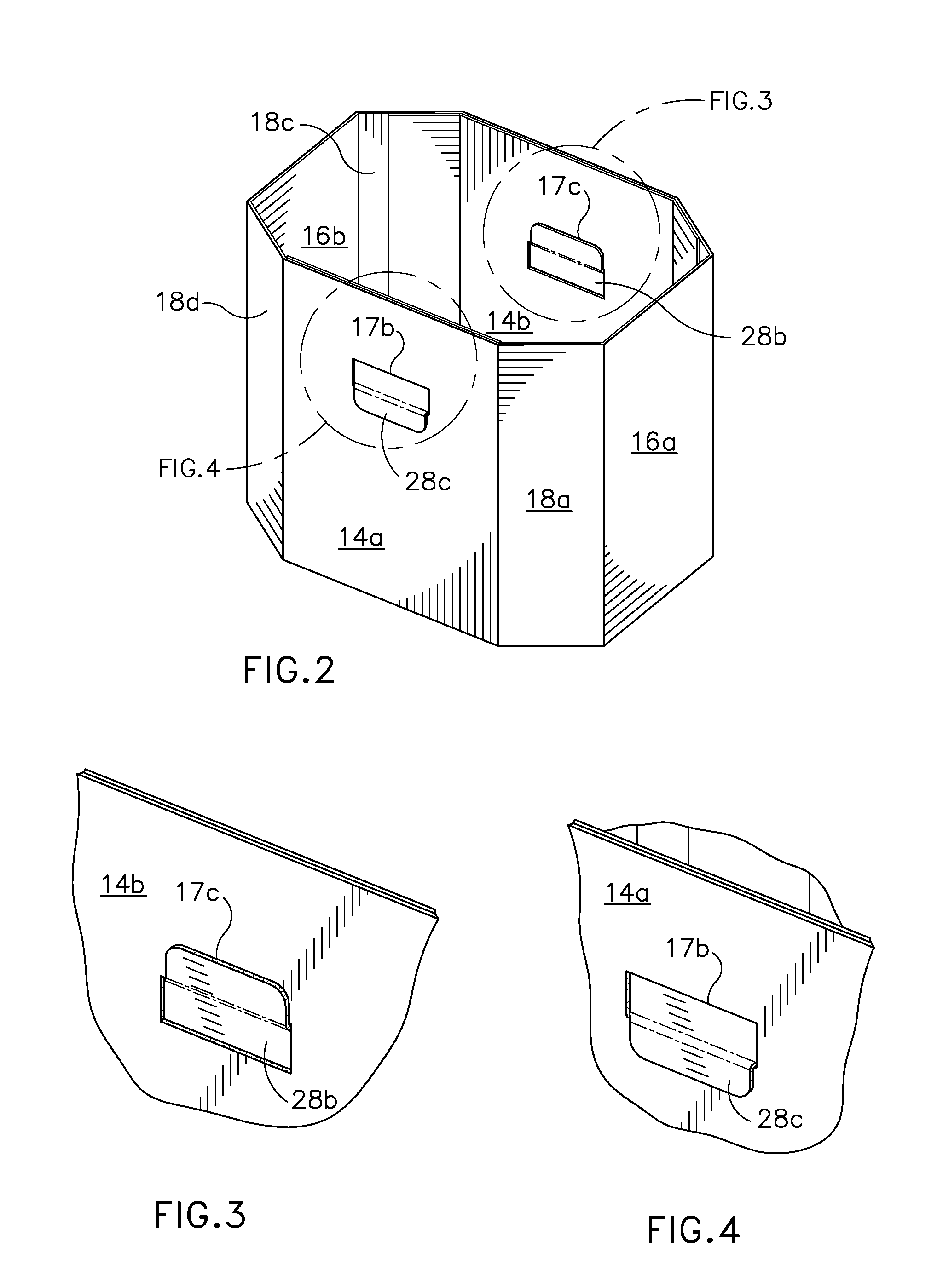
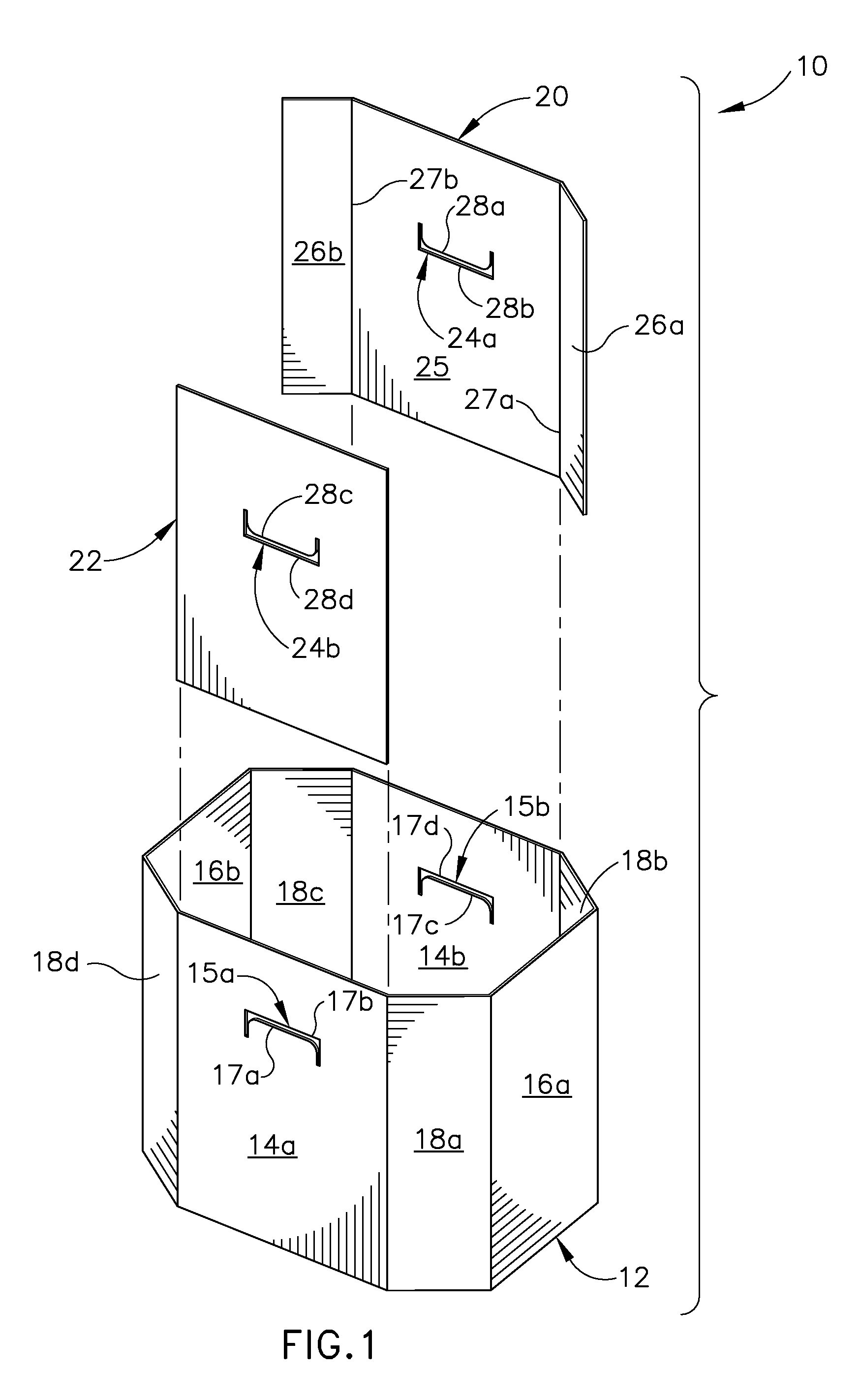
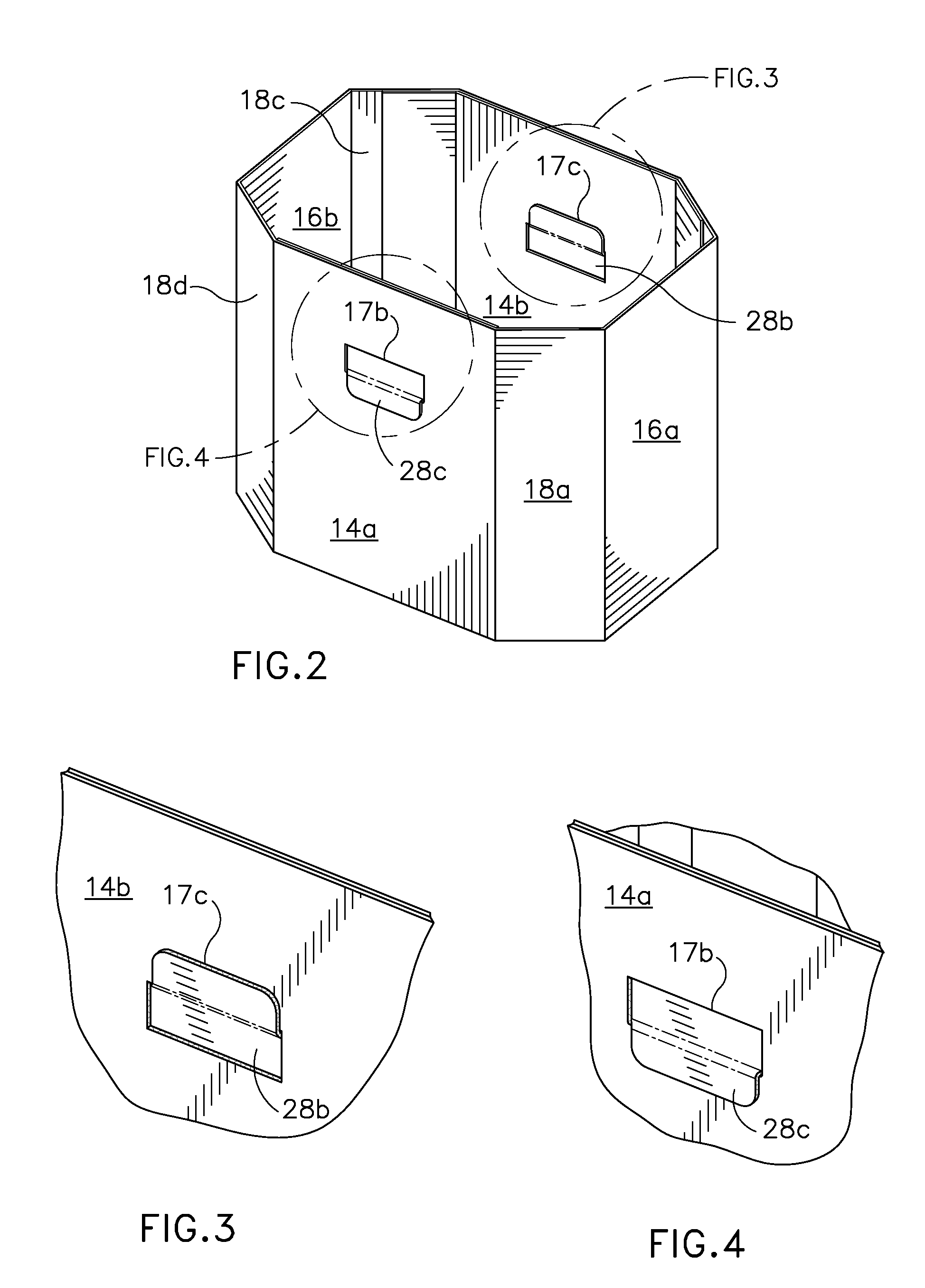
ActiveUS20130146651A1Increased flexural rigidityEnhance increased flexRigid containersSelf lockingEngineering
Owner:INT PAPER CO
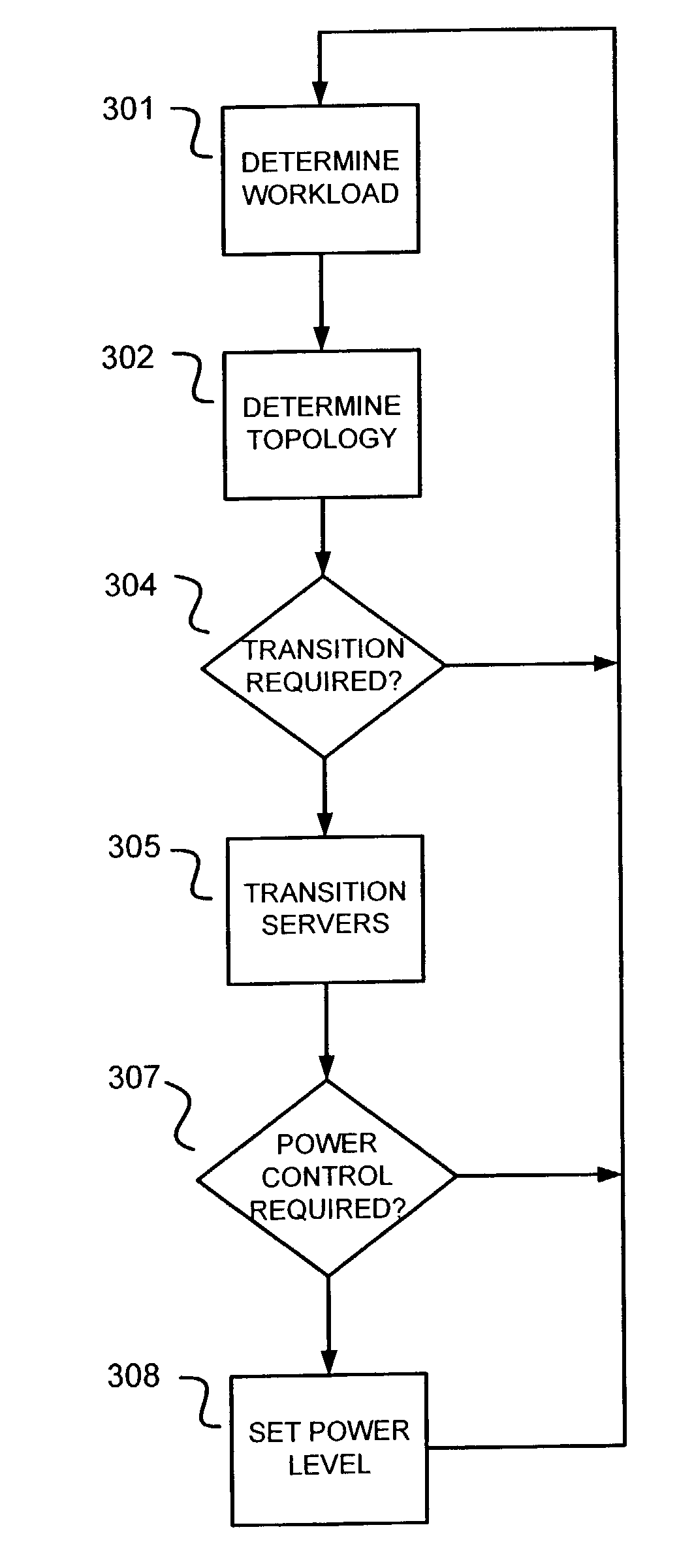
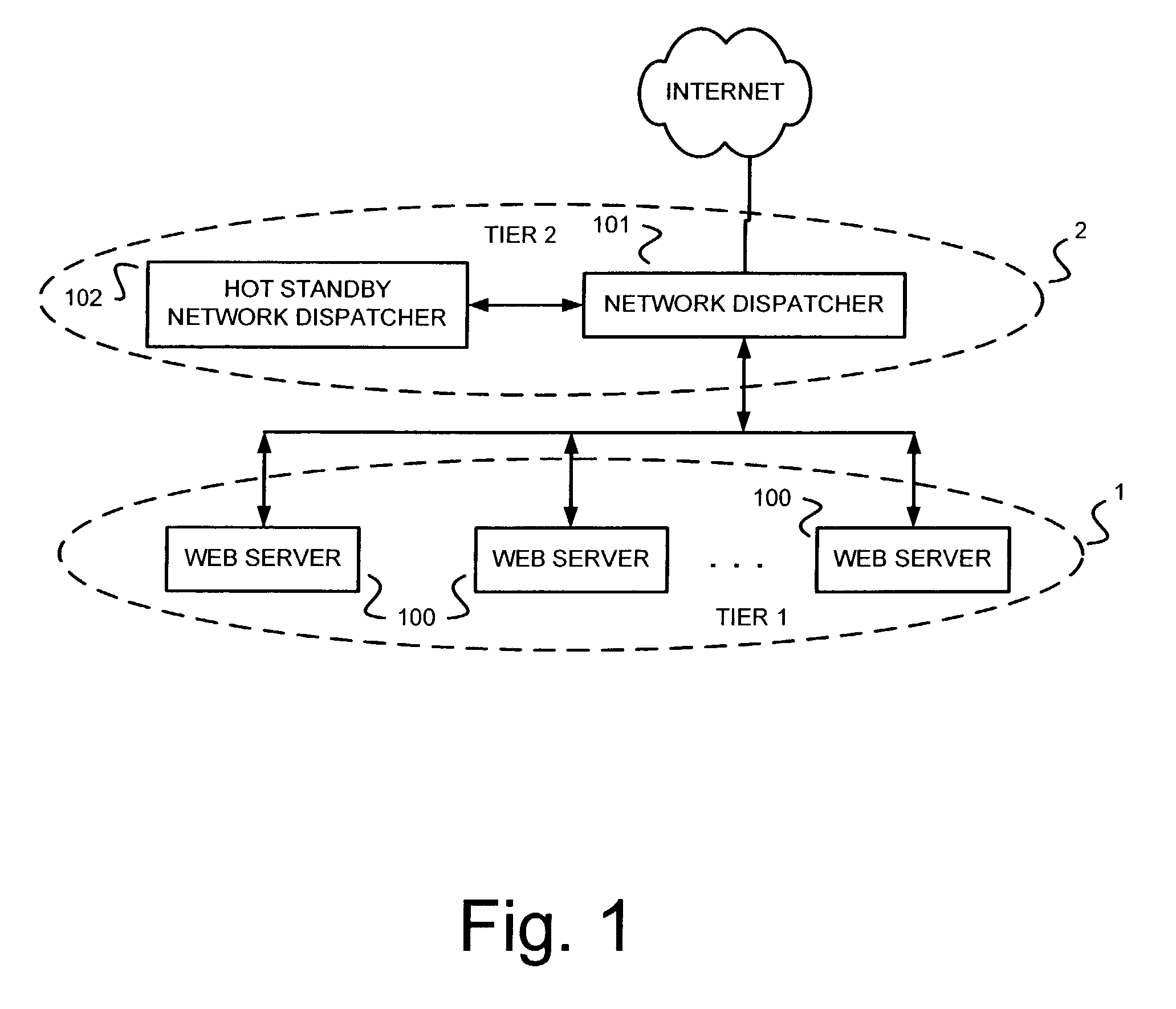
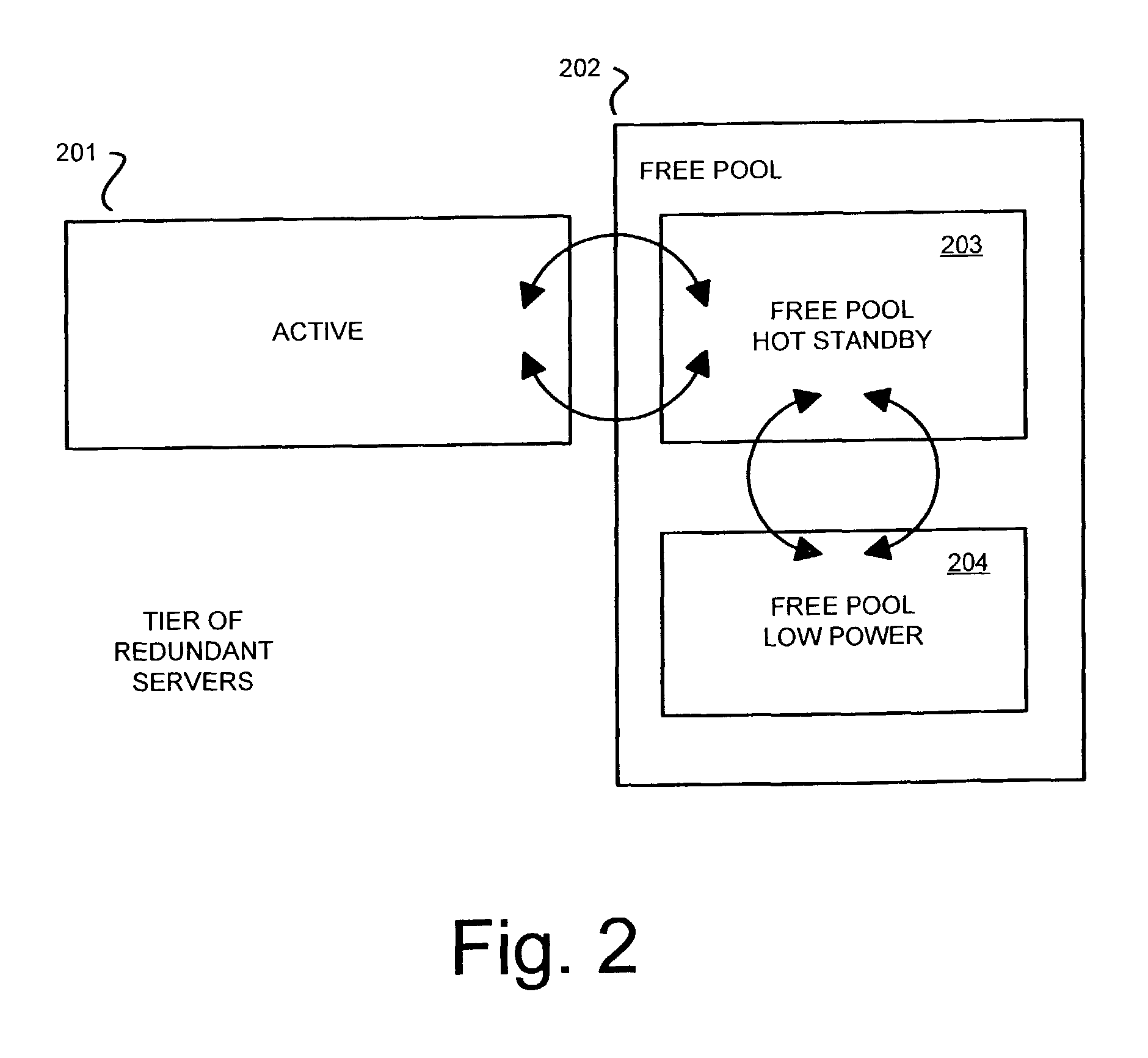
Automated power control policies based on application-specific redundancy characteristics
ActiveUS7870241B2Maximize cost savingMaximizing costEnergy efficient ICTResource allocationPower modeApplication specific
Power and redundancy management policies are applied individually to the tiers of redundant servers of an application service such that power is reduced while maintaining a high level of system availability. Servers which are determined to be relatively inactive are moved to a free pool. Certain servers of the free pool are maintained in a hot standby state, while others are powered-off or set to operate in a low power mode. During times of high load, the servers in the hot standby state can be provisioned quickly into the application service.
Owner:LENOVO GLOBAL TECH INT LTD
Image log slope (ILS) optimization
ActiveUS10394131B2Maximizing costMinimize timePhotomechanical exposure apparatusMicrolithography exposure apparatusResistAlgorithm
A method to improve a lithographic process of imaging a portion of a design layout onto a substrate using a lithographic projection apparatus, the method including: computing a multi-variable cost function, the multi-variable cost function being a function of a stochastic variation of a characteristic of an aerial image or a resist image, or a function of a variable that is a function of the stochastic variation or that affects the stochastic variation, the stochastic variation being a function of a plurality of design variables that represent characteristics of the lithographic process; and reconfiguring one or more of the characteristics of the lithographic process by adjusting one or more of the design variables until a certain termination condition is satisfied.
Owner:ASML NETHERLANDS BV
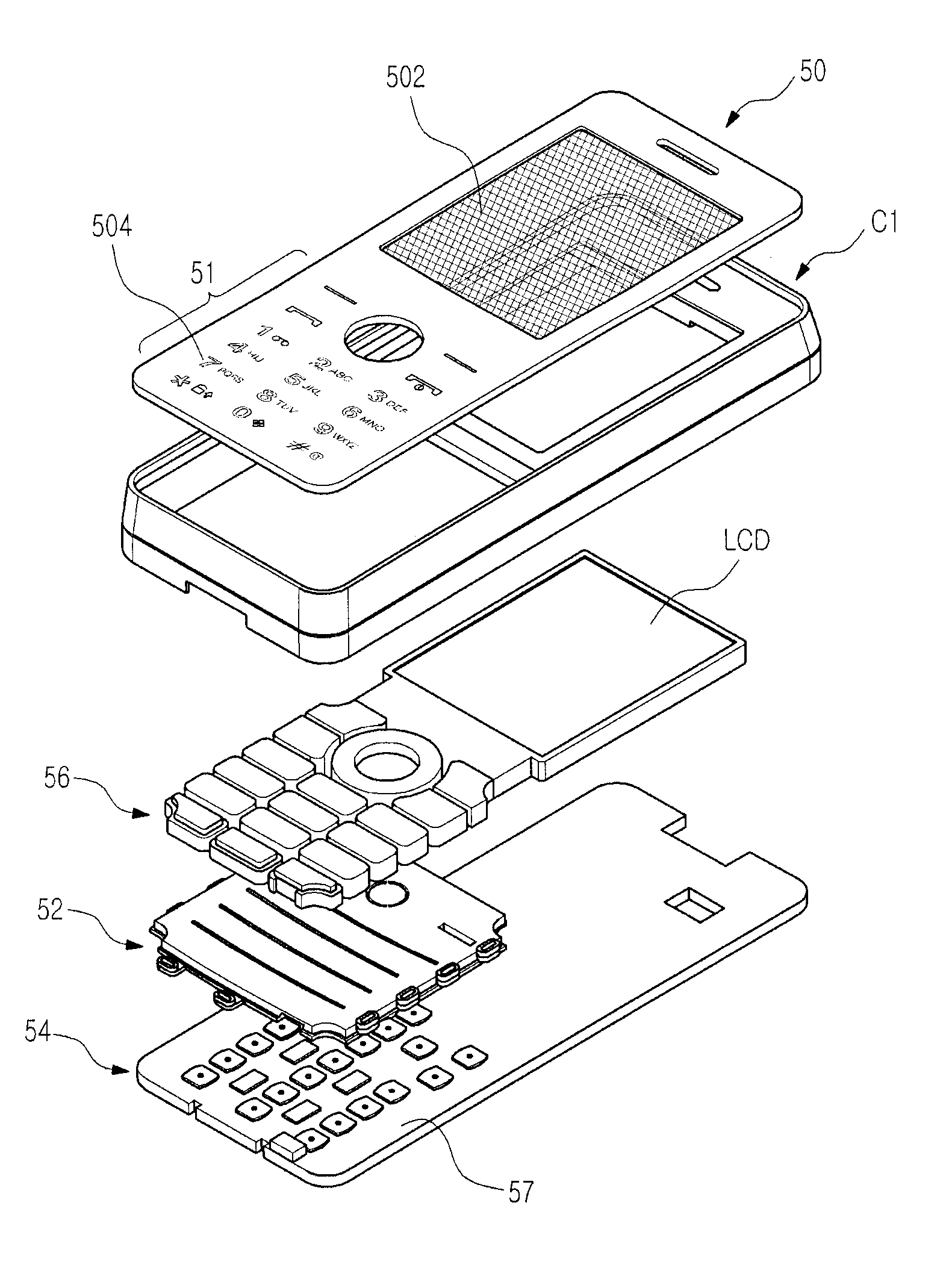
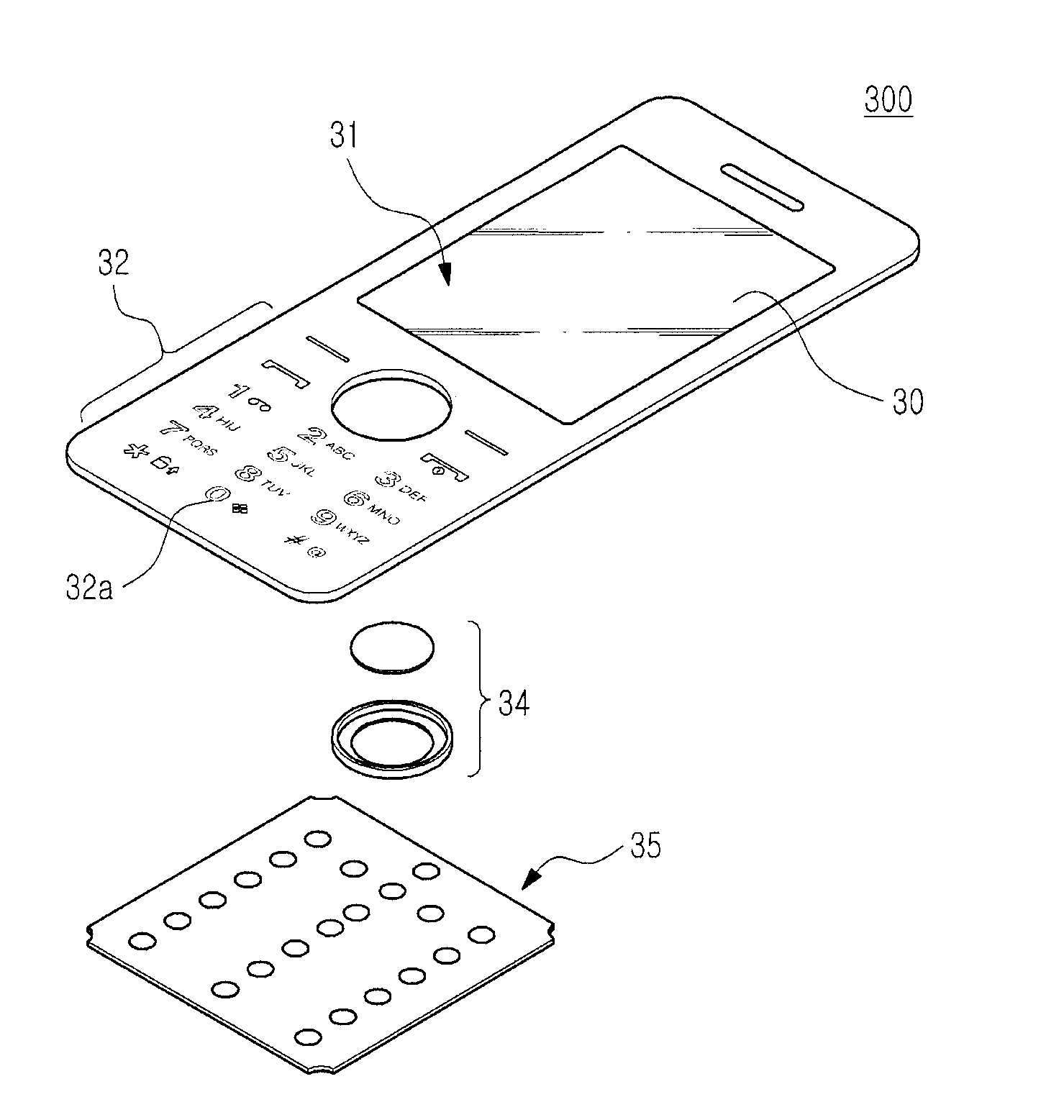
Keypad assembly for mobile phone
ActiveUS8227715B2Low costMaximizing costContact surface shape/structureEmergency casingsEmbedded systemMobile phone
A keypad assembly mounted in a portable terminal is disclosed. The keypad assembly has a window keypad including a display window disposed on a front face of the portable terminal. A keypad top is integrally molded with the display window and simultaneously assembled on the front face of the portable terminal, thereby providing an easier assembly than known heretofore, as two parts can be assembled at the same time and additionally provide an elegant exterior front face.
Owner:SAMSUNG ELECTRONICS CO LTD
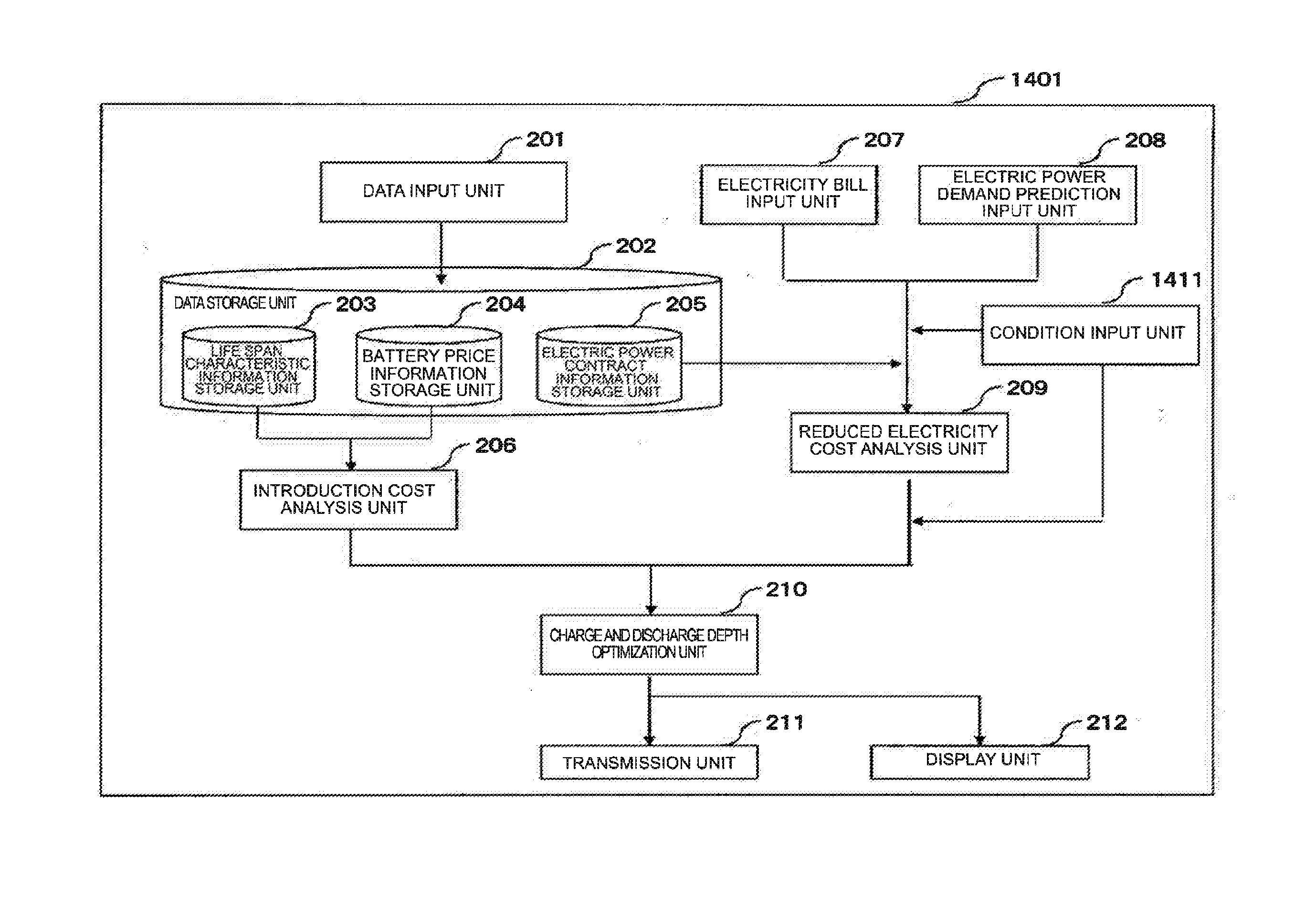
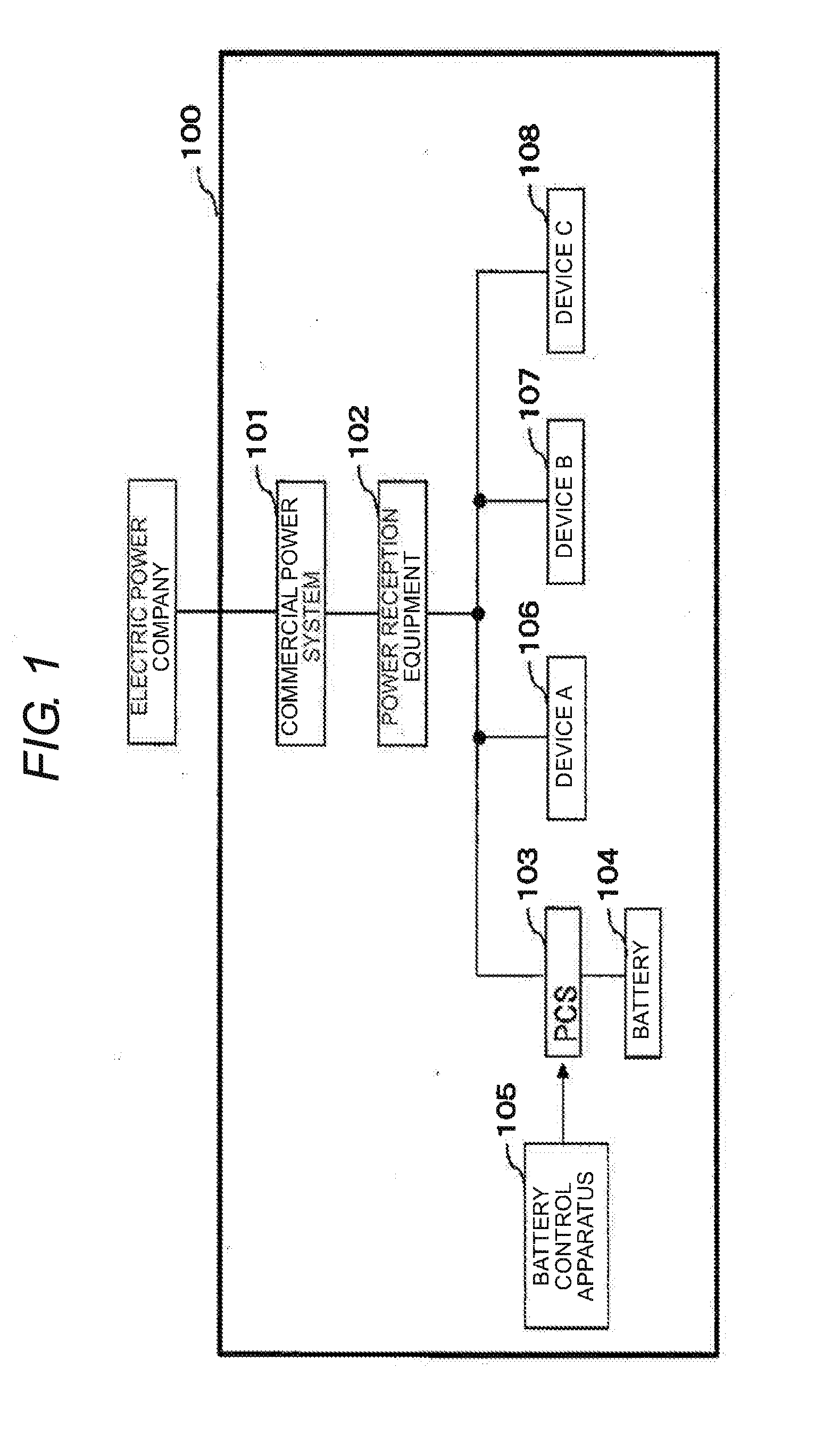
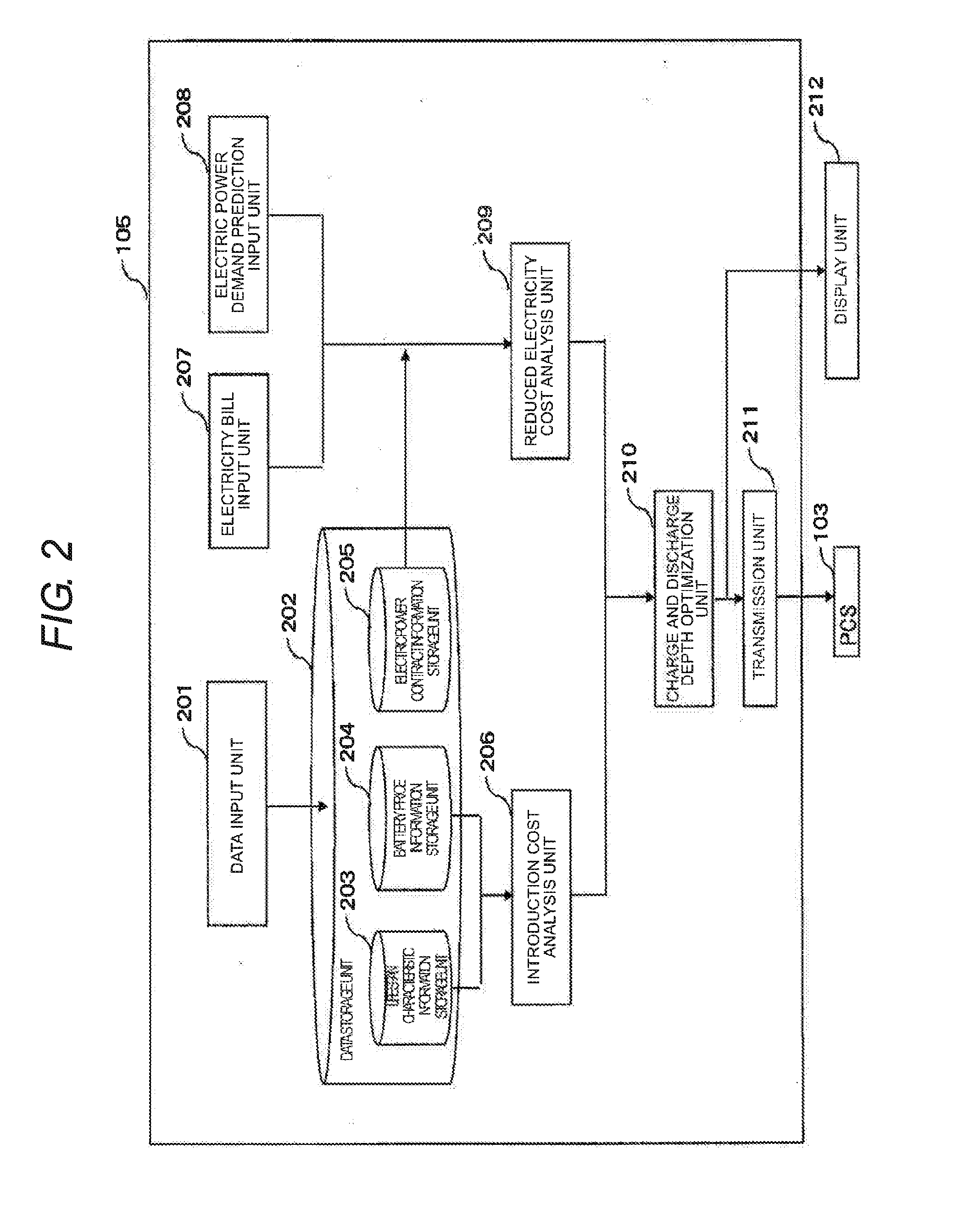
Battery Control Apparatus
ActiveUS20170005483A1Maximize cost benefitLower battery costsCircuit monitoring/indicationAc network load balancingCost analysisElectrical battery
A battery control apparatus includes a reduced electricity cost analysis unit that obtains a discharge electric power cost at a discharge time and a charge electric power cost at a charge time of a battery, based on a basic cost and a unit cost of an electricity bill, and obtains a reduced electricity cost in which the charge electric power cost is subtracted from the discharge electric power cost for every discharge depth of the battery; an introduction cost analysis unit that calculates an introduction cost of the battery for every discharge depth of the battery; and a charge and discharge depth optimization unit that obtains a difference of the reduced electricity cost and the introduction cost for every discharge depth of the battery, and determines a charge and discharge depth of the battery based. on the difference. The discharge of the battery is performed at the determined charge and discharge depth.
Owner:HITACHI LTD
Optimization of source and bandwidth for new and existing patterning devices
ActiveUS10416566B2Improve image qualityIncreased latitudePhotomechanical exposure apparatusMicrolithography exposure apparatusEngineeringPhotolithography
Owner:ASML NETHERLANDS BV +1
Procedure for seizing the beginning of an active signal section
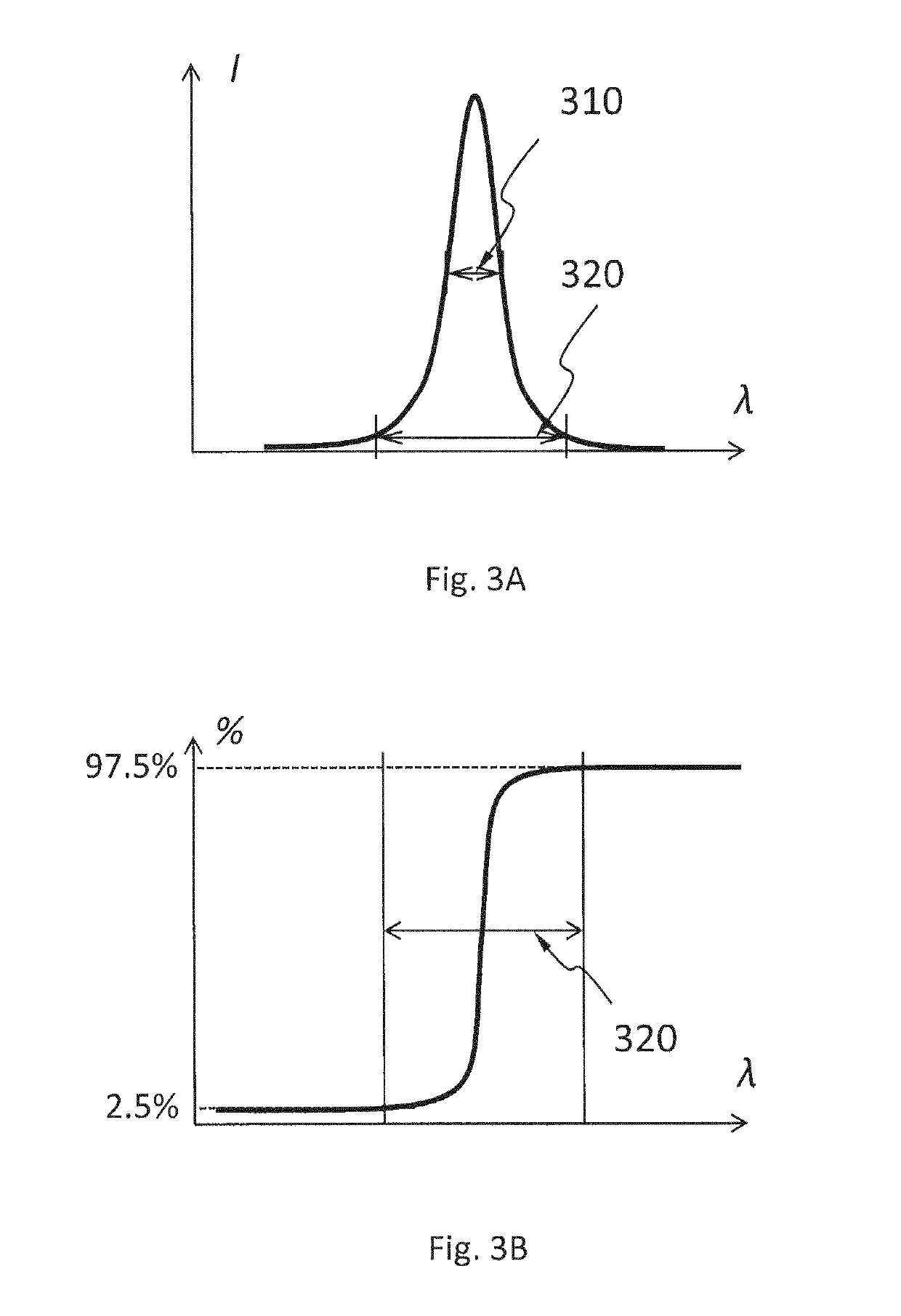
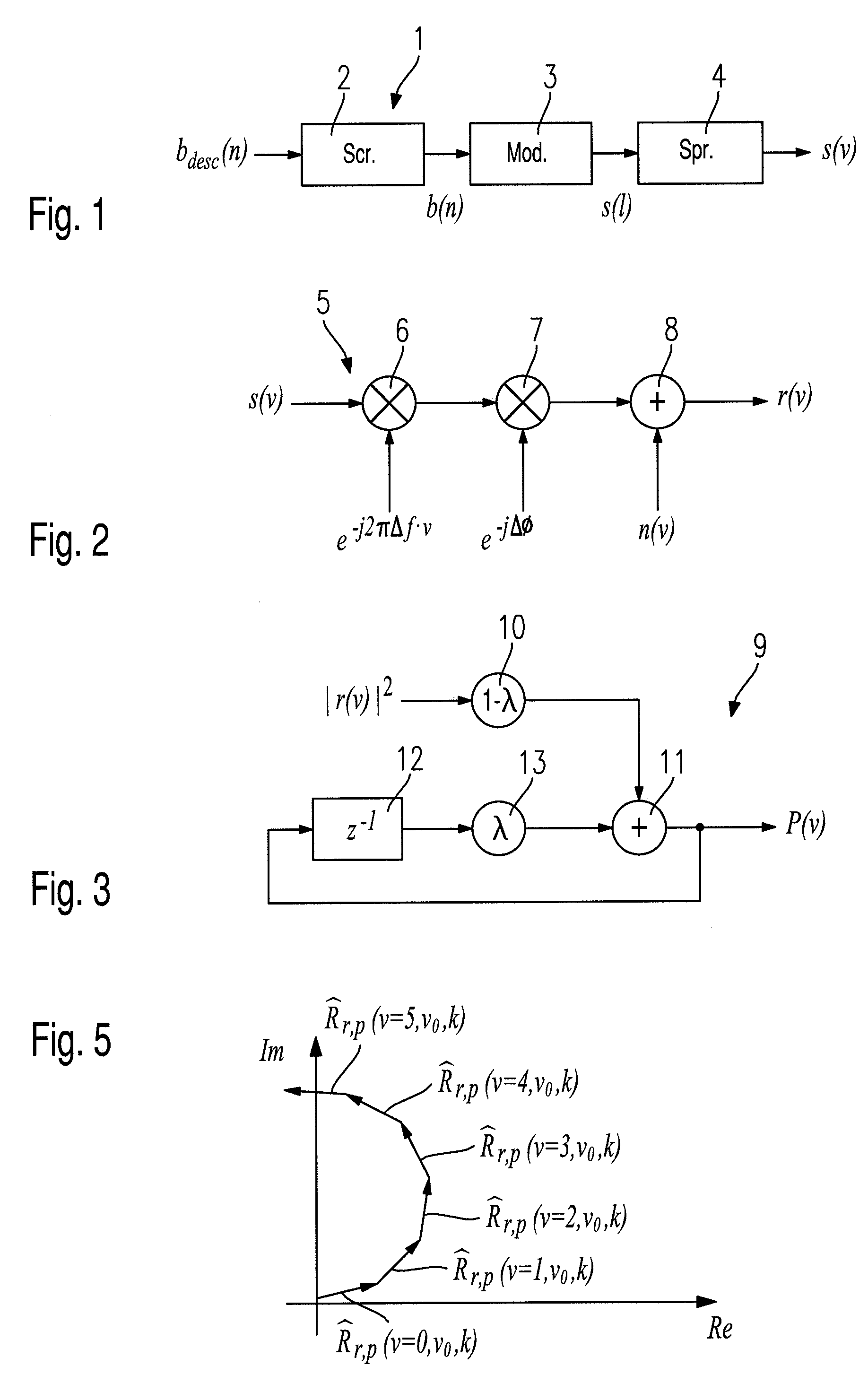
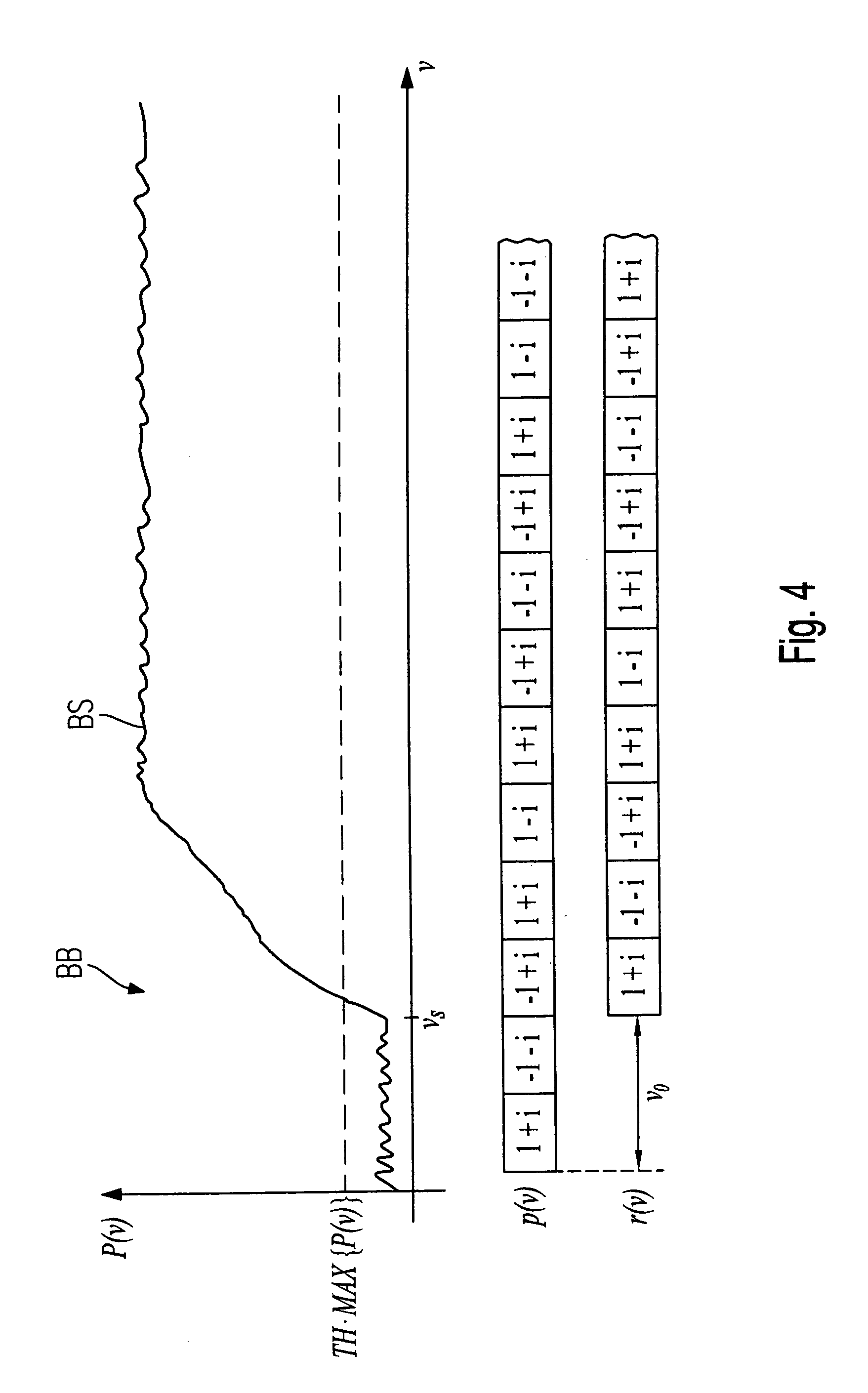
InactiveUS7283600B2Increase the lengthMaximizing costAmplitude-modulated carrier systemsSynchronisation signal speed/phase controlTime delaysCorrelation function
A process for detecting initiation (BB) of an active packet or burst in a digital received signal r(v) during use of a digital reference signal p(v) includes: (a) executing a correlation (S102, S103) by forming a cost function L(v0) with a correlation function within a correlation function interval dependent upon a time delay of the received signal r(v) relative to a bit offset or a chip offset v0 characterized by reference signal p(v), whereby the addends of the correlation function were multiplied with a frequency offset correction factor, namely e−j2πΔ{tilde over (f)}v, which factor was characterized with a frequency offset Δf of received signal r(v) relative to the reference signal p(v); and (b) seeking a maximum Max(L) of cost function L(v0) dependent upon the bit offset or the chip offset v0 and upon the approximate frequency offset Δ{tilde over (f)} whereby maximum Max(L), following a discrete Fourier Transform (FFT) is sought in the frequency space.
Owner:ROHDE & SCHWARZ GMBH & CO KG
Self-locking support panel for corrugated container
Owner:INT PAPER CO
Method and apparatus for joint optimization of dedicated and radio access networks
InactiveUS8224338B2Maximizing costMinimization requirementsNetwork planningAccess networkRadio access network
A computerized method and system for integrated access network business planning for a telecommunications carrier. The invention enables a user to input a set of network business planning parameters that are utilized by a linear programming model to jointly optimize a carrier's dedicated and radio access network by executing a plurality of network optimization models and determine network configuration changes for the dedicated and radio access networks as a constrained optimization based on the set of business planning parameters.
Owner:AT&T INTPROP I L P
Biodegradable container closure and resin therefor
PendingUS20220089862A1Maximize productivityMaximizing costFlexible coversWrappersPolymer sciencePolymer chemistry
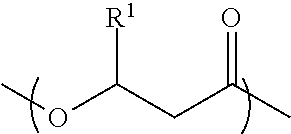
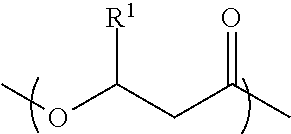
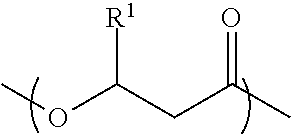
A biodegradable container closure and a method for making the container closure. The biodegradable container closure includes from about 40 to about 99 weight percent of a polymer derived from random monomeric repeating units having a structure ofwherein R1 is selected from the group consisting of CH3 and a C3 to C19 alkyl group. The monomeric units having R1═CH3 is about 75 to about 99 mol percent of the polymer. A resin adapted for forming the closure is also disclosed.
Owner:DANIMER IPCO LLC
Keypad assembly for mobile phone
ActiveUS20100200386A1Low costMaximizing costContact surface shape/structureEmergency casingsEmbedded systemMobile phone
A keypad assembly mounted in a portable terminal is disclosed. The keypad assembly has a window keypad including a display window disposed on a front face of the portable terminal. A keypad top is integrally molded with the display window and simultaneously assembled on the front face of the portable terminal, thereby providing an easier assembly than known heretofore, as two parts can be assembled at the same time and additionally provide an elegant exterior front face.
Owner:SAMSUNG ELECTRONICS CO LTD
Optimization of a lithographic projection apparatus accounting for an interlayer characteristic
ActiveUS20190137889A1Improve image qualityIncreased latitudePhotomechanical exposure apparatusMicrolithography exposure apparatusPhotolithographyEngineering
A method to improve a lithographic process of imaging a portion of a design layout onto a substrate using a lithographic apparatus, the method including computing a multi-variable cost function. The multi-variable cost function represents an interlayer characteristic, the interlayer characteristic being a function of a plurality of design variables that represent one or more characteristics of the lithographic process. The method further includes reconfiguring one or more of the characteristics of the lithographic process by adjusting one or more of the design variables and computing the multi-variable cost function with the adjusted one or more design variables, until a certain termination condition is satisfied.
Owner:ASML NETHERLANDS BV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com