Abnormal login detecting method and device
A technology of abnormal login and detection method, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as low safety factor, login data verification account password, etc., to reduce workload, make accurate judgments, and improve work efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the object, technical solution and advantages of the present invention clearer, the embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
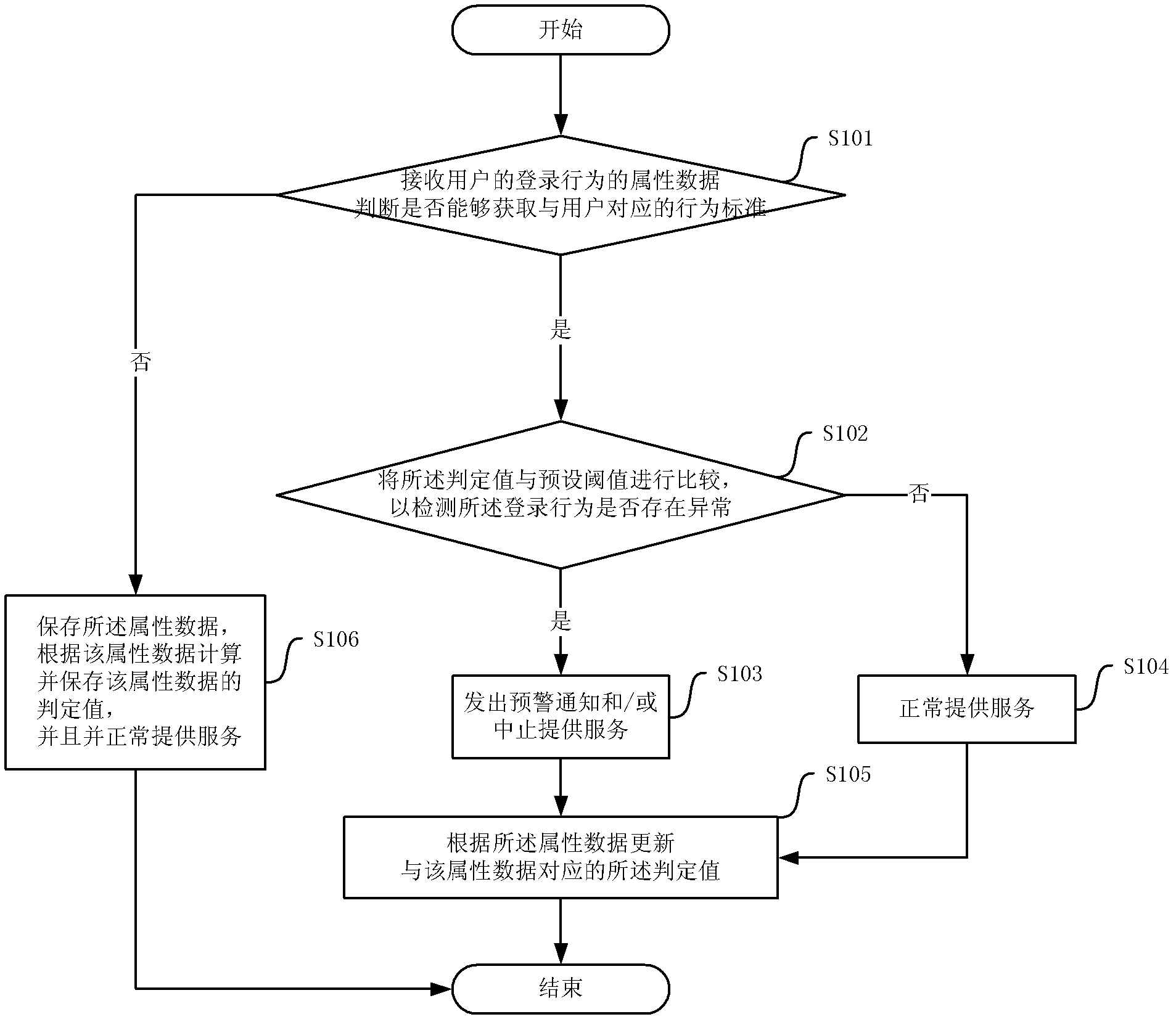
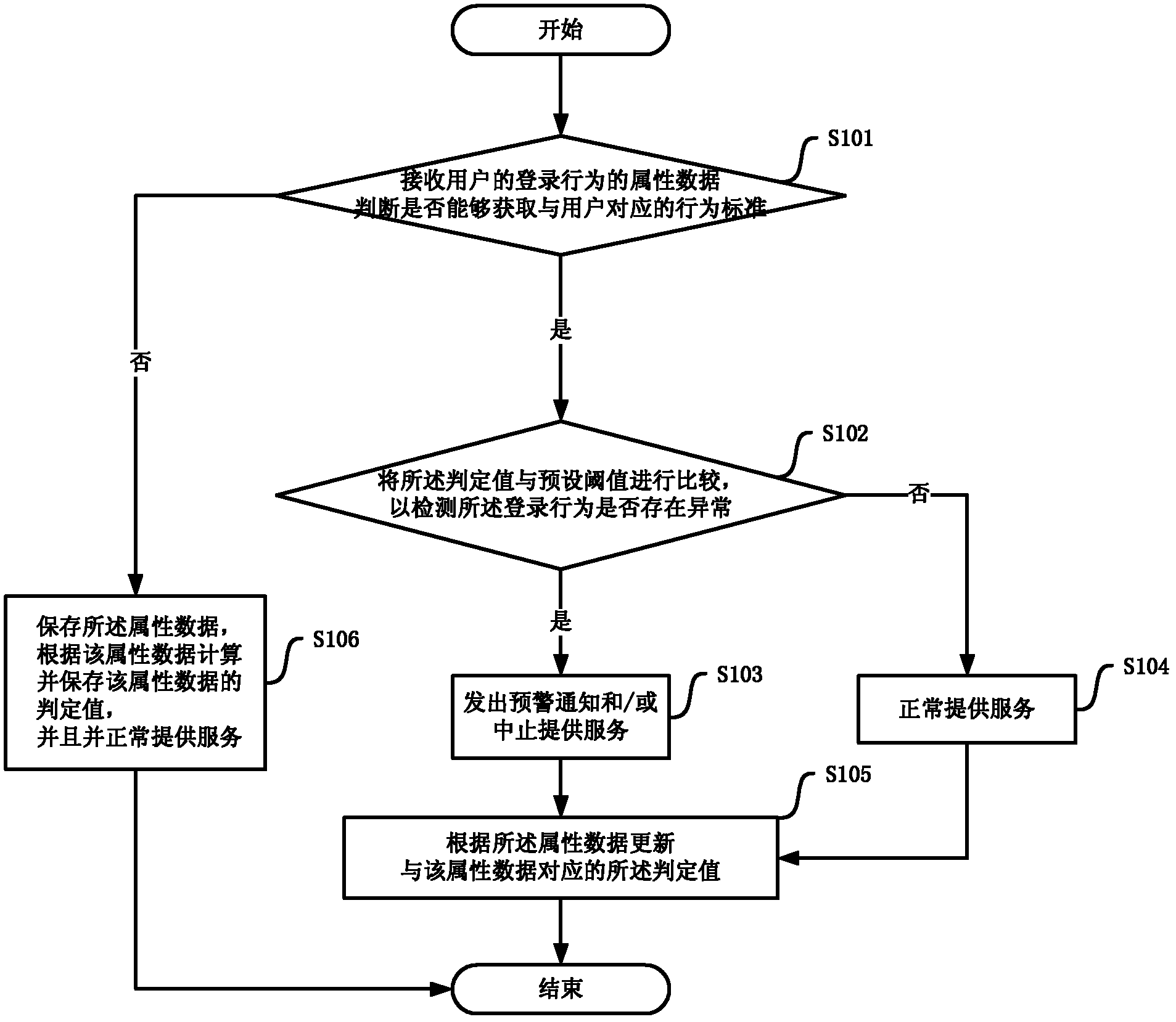
[0019] First please refer to figure 1 , figure 1 It is a flow chart of a specific embodiment of the method for detecting abnormal login based on self-learning according to the present invention, and the method includes the following steps:
[0020] Step S101, receiving the attribute data of the user's login behavior, and judging whether the behavior standard corresponding to the user can be obtained. If the behavior standard corresponding to the user can be acquired, execute step S102; otherwise, execute step S106. Specifically, the behavior standard records at least one set of historical attribute data of login behavior, and records the judgment value generated according to the statistical results of the at least one set of historical login behavior da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com