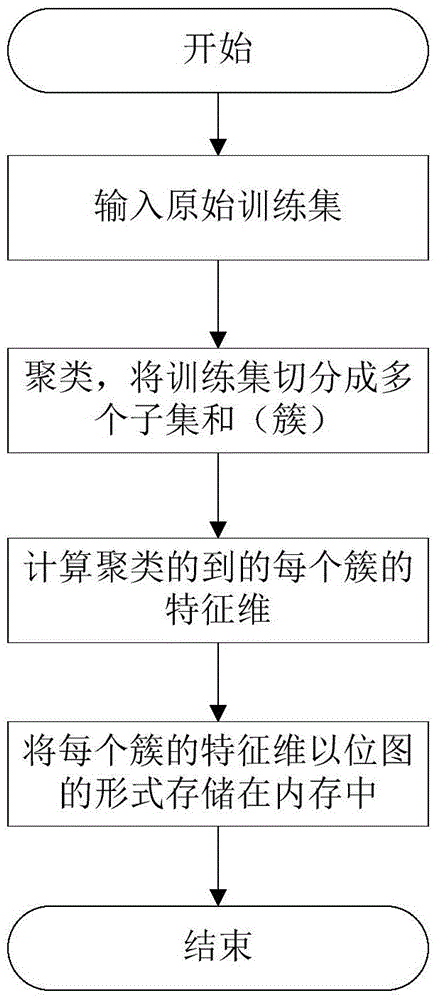
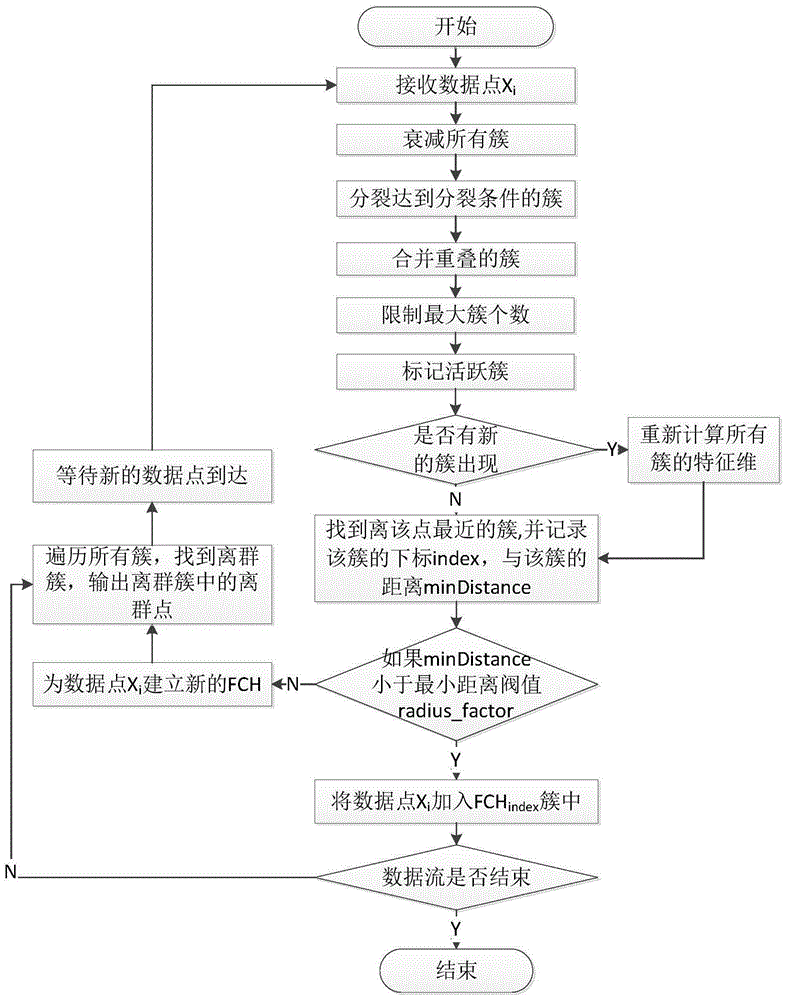
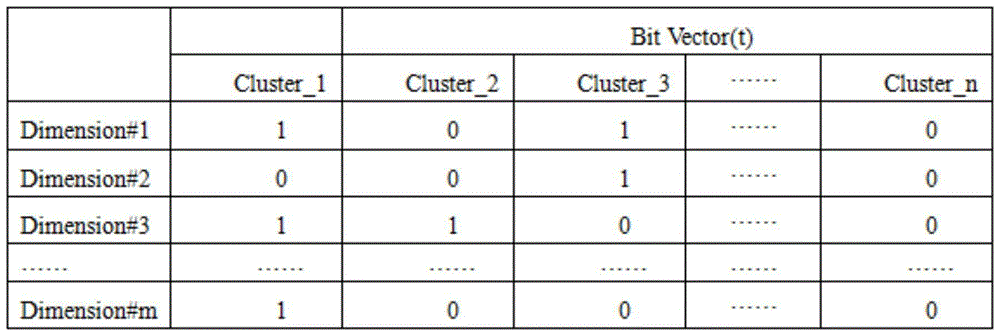
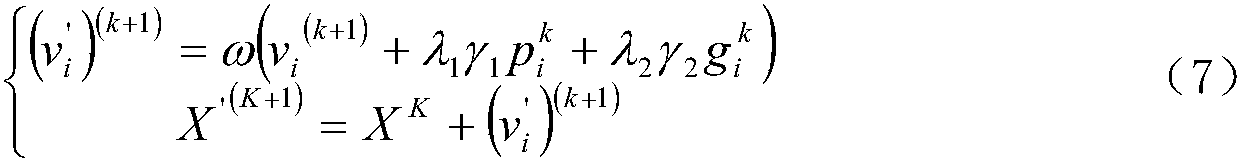Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71results about How to "Optimize execution efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Device and method for identifying and evaluating emergency hot topic
InactiveCN102937960AReduce complexityImprove operational efficiencySpecial data processing applicationsComputation complexityUnexpected events
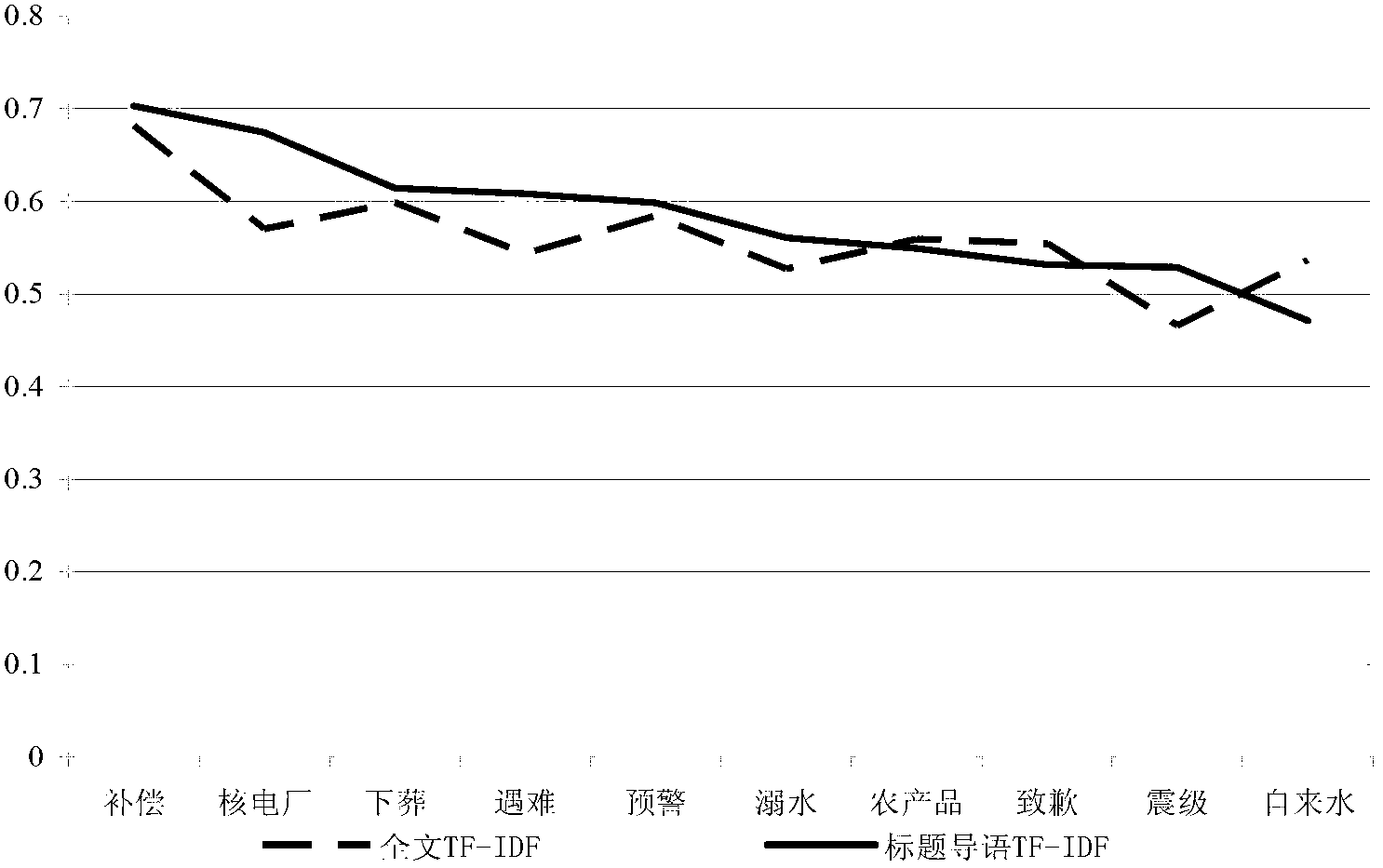
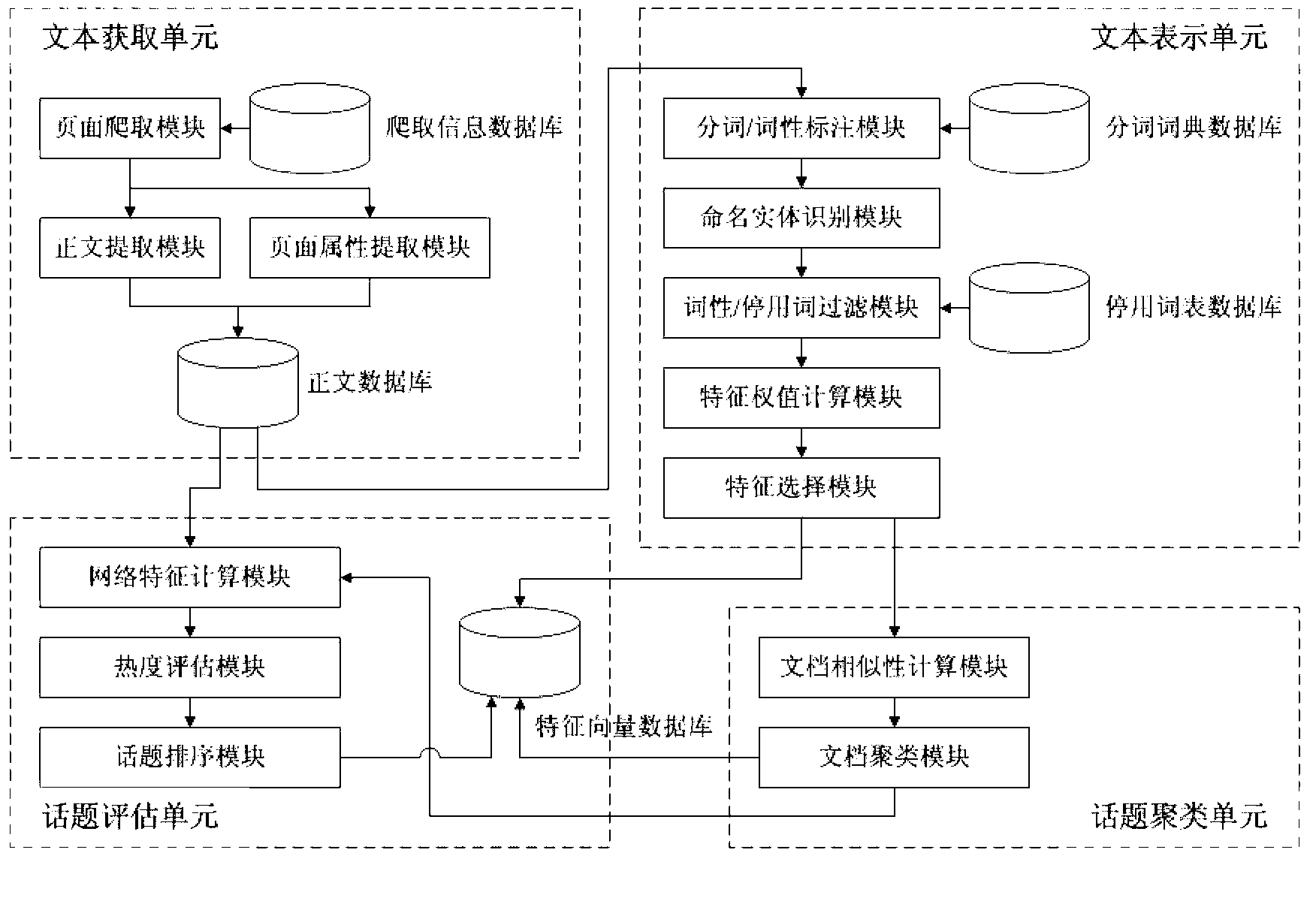
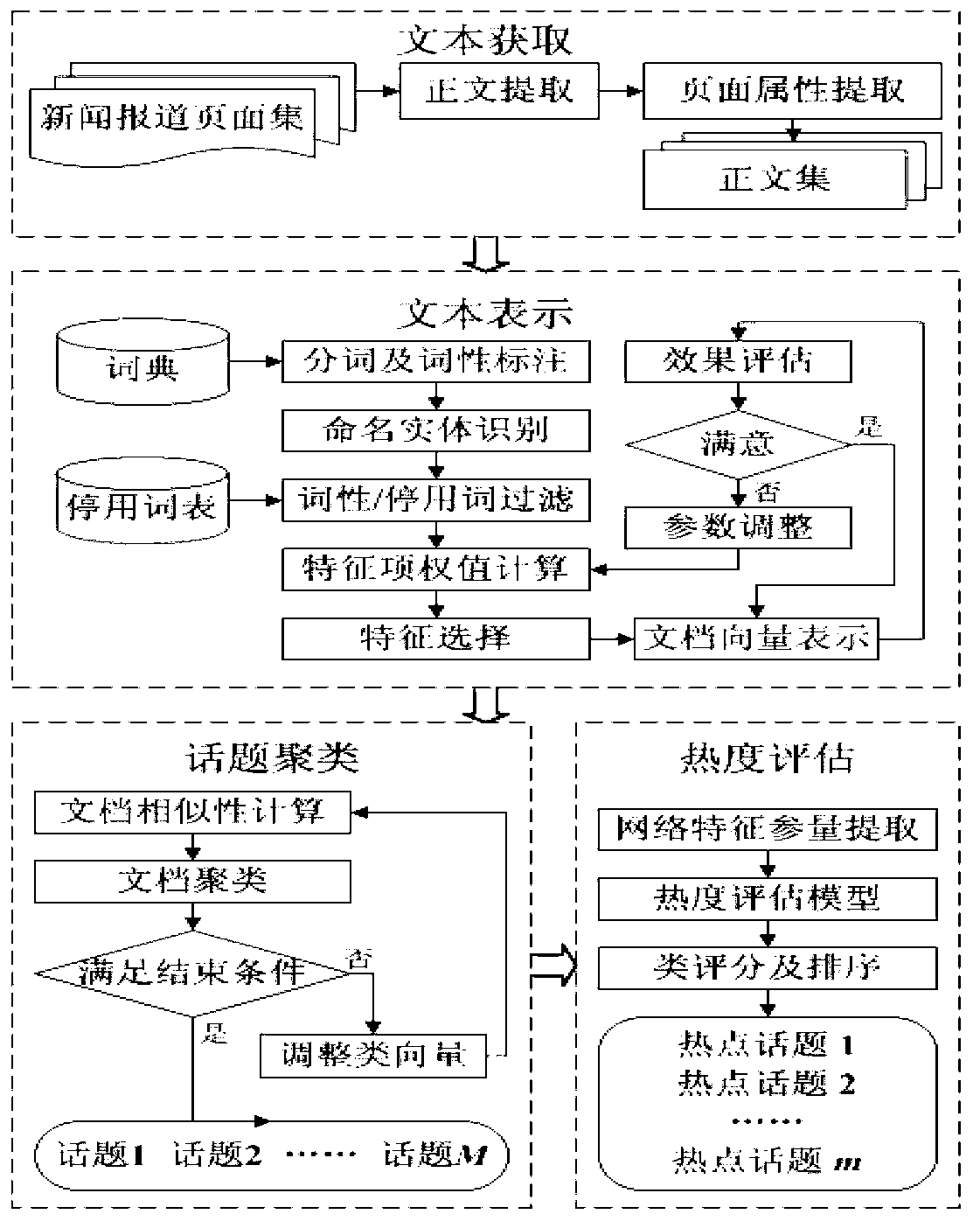
The invention relates to a device and a method for identifying and evaluating an emergency hot topic. The device is provided with four component parts including a text acquisition unit, a text expression unit, a topic clustering unit and a topic evaluation unit. The device and the method are characterized in that only a title, introduction, relevant features and other information of a text of a news report are extracted and regarded as an effective sample set identified by the hot topic. Compared with the existing full text extraction, the experiment result shows that the result of the existing full text extraction is similar to the result of the partial text extraction, but the operation of the device and the method is greatly simplified. Compared with a classical model, an improved feature weight calculation model is good in execution efficiency and strong in adaptability of text representation capability. The model is used for evaluating the hot value of clustered topics, and the calculated hot topic accords with the expected effect and is adaptive to the features of the emergency news report. In a word, in the process of processing the text of the emergency news report, the device and the method have good performance in aspects of calculation complexity, result accuracy and timeliness.
Owner:BEIJING UNIV OF POSTS & TELECOMM
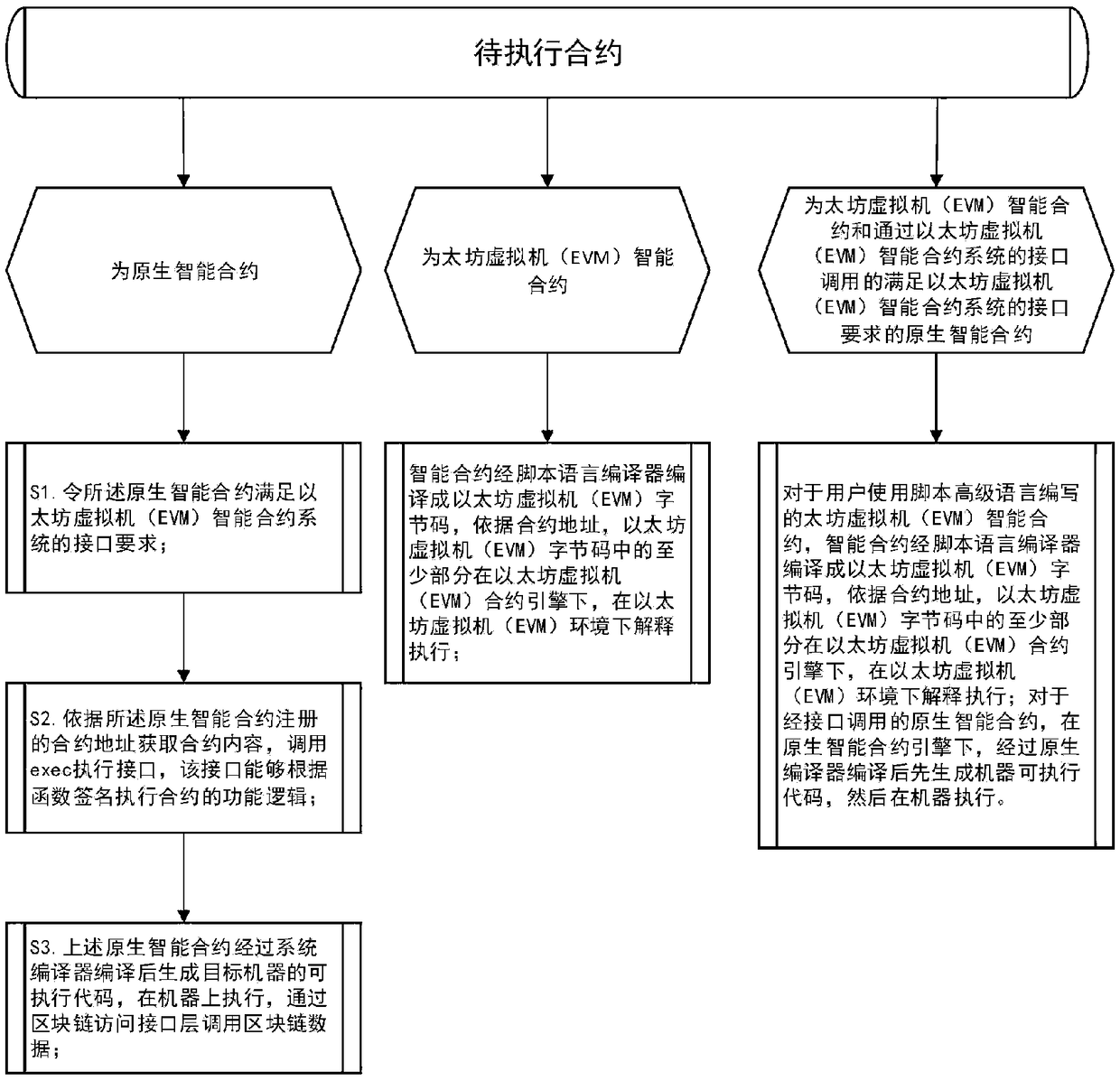
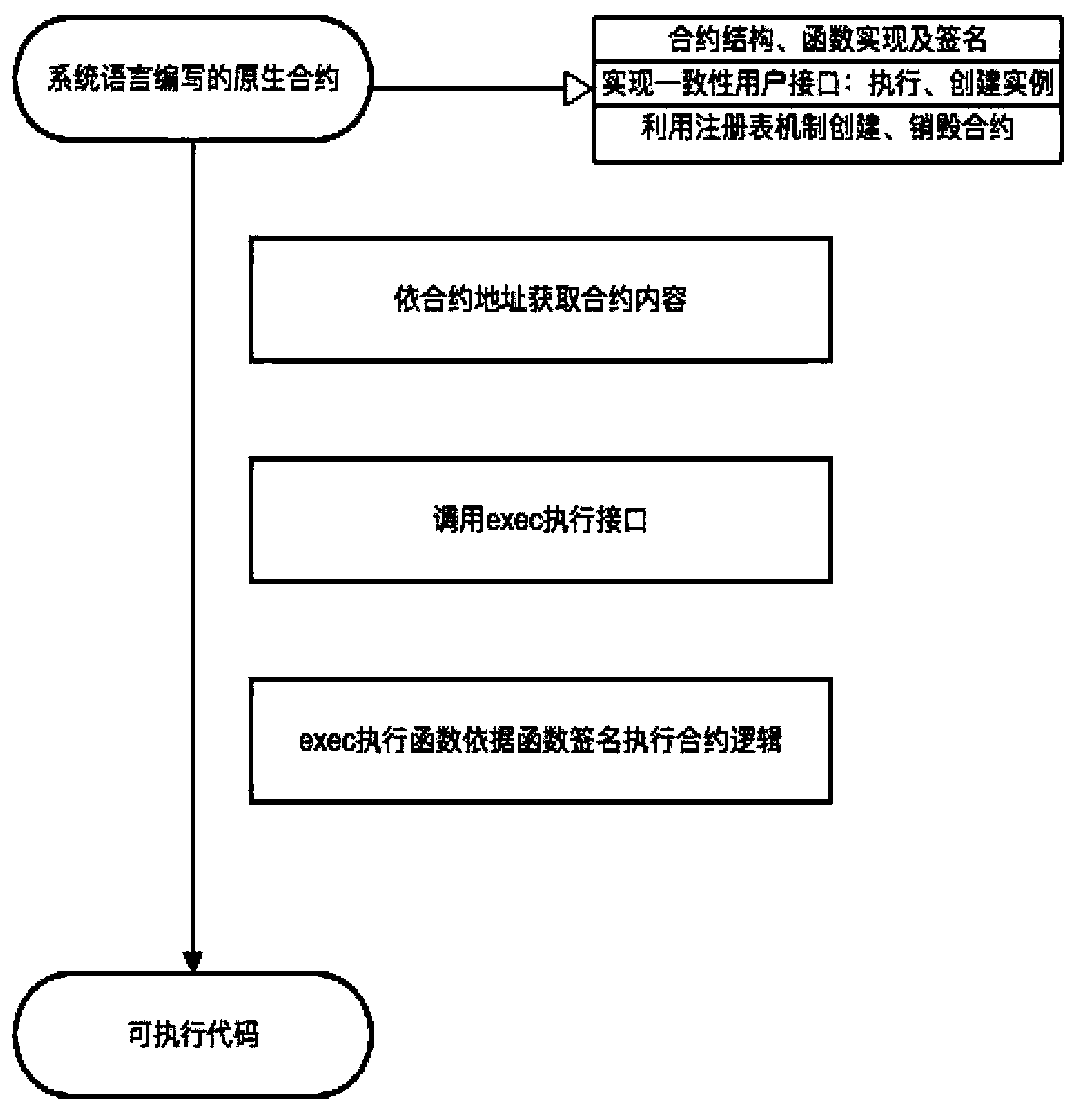
Intelligent contract engine system based on block chain and contract execution method
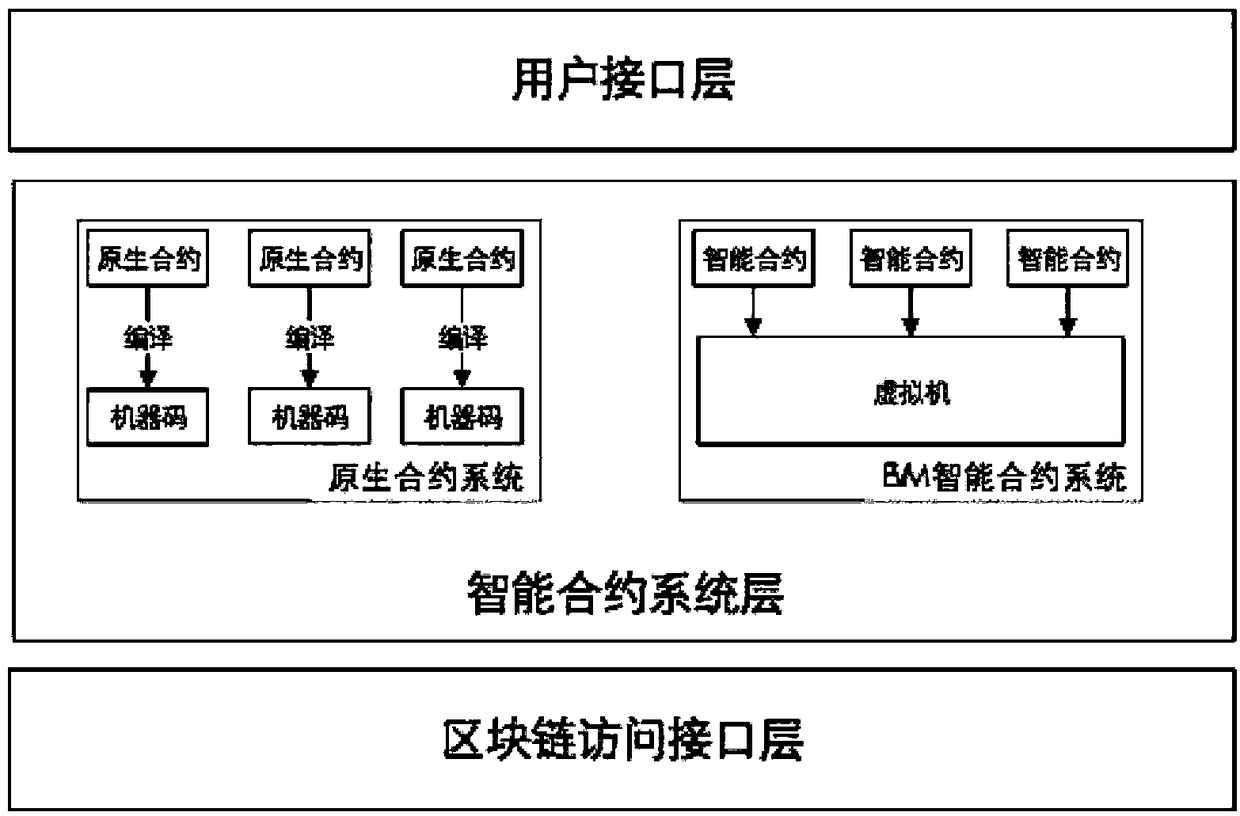
The invention discloses an intelligent contract engine system based on a block chain and a contract execution method. The intelligent contract engine system based on a block chain includes a user interface layer, an intelligent contract system layer and a block chain access interface layer; the user interface layer is used for providing a unified interface to users, and through the unified interface, the users can interact with an intelligent contract in the intelligent contract system layer in an identical data interaction manner; the intelligent contract system layer is used for executing the intelligent contract; and the block chain access interface layer is used for providing a unified interface for accessing block chain data for the intelligent contract in the intelligent contract system layer. The intelligent contract engine system based on a block chain can overcome the defects of restricted performance due to slow execution speed and restricted expandability due to limited expression ability caused by adoption of an EVM mode in an existing contract engine system; and at the same time, the system can also overcome the defect that the overall efficiency is affected due to long starting time caused by adoption of a Docker mode.
Owner:HANGZHOU RIVTOWER TECH CO LTD
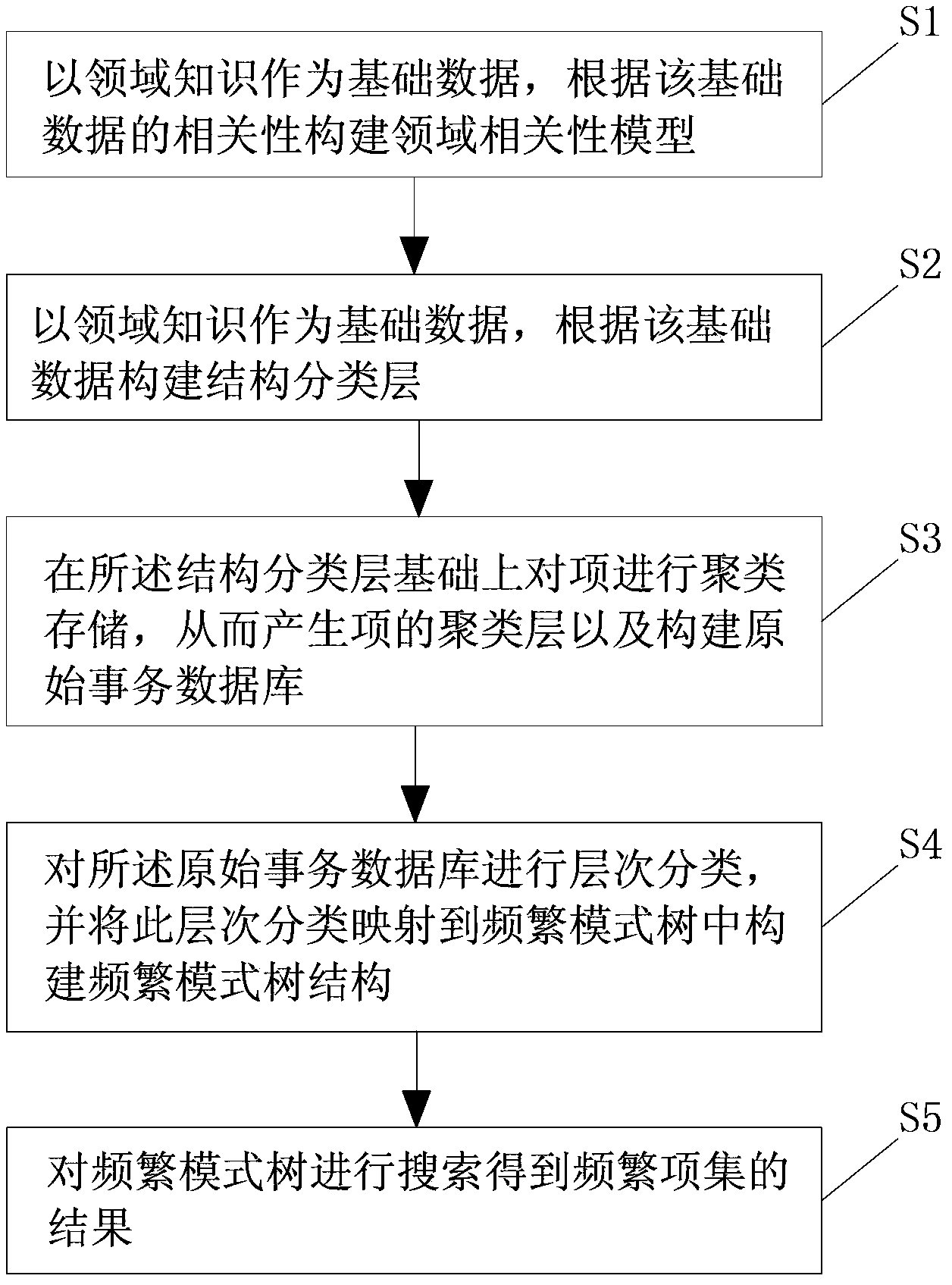
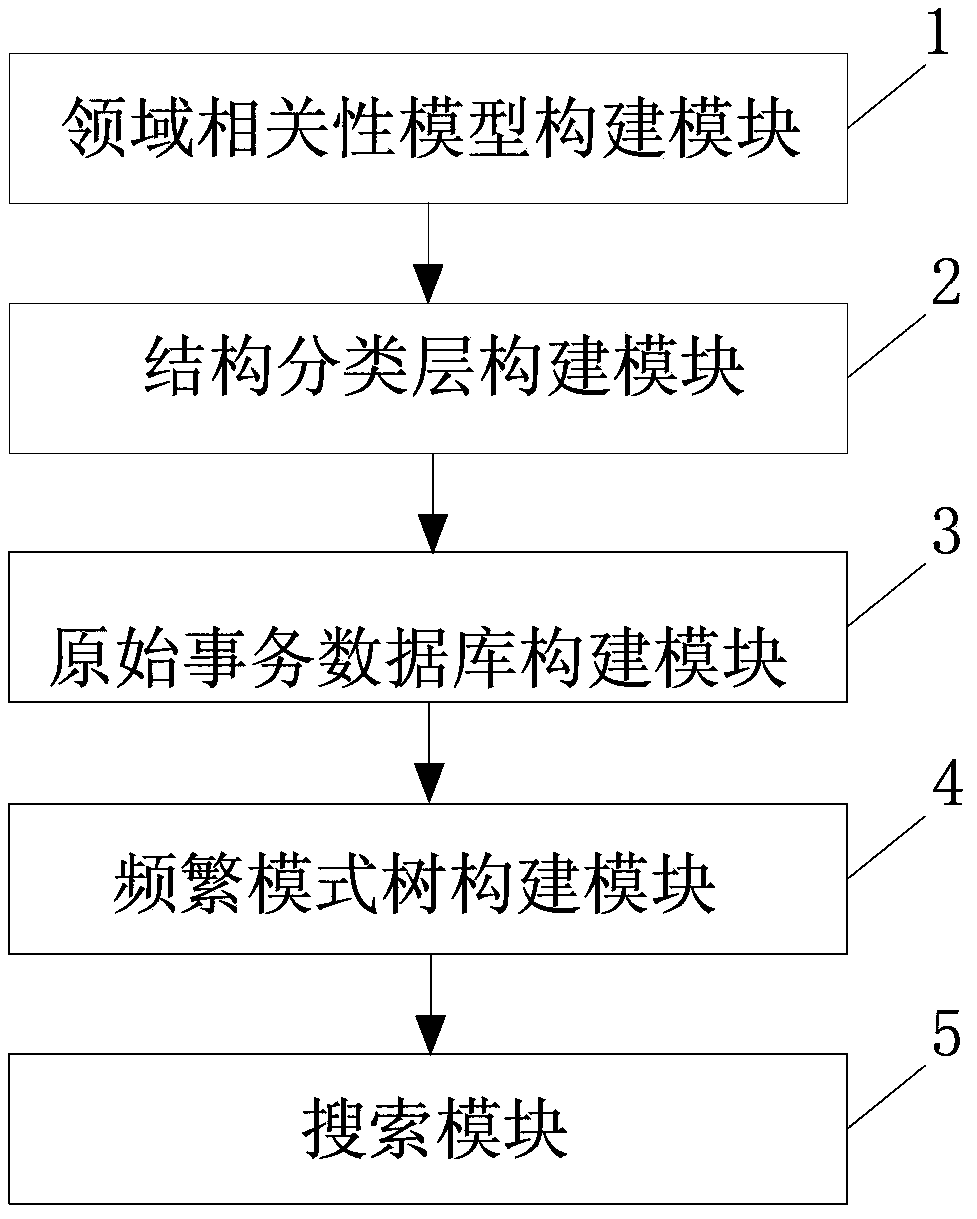
Domain knowledge-based multilayer association rules mining method and system
InactiveCN104281617AEnsuring Completeness and CorrectnessGood execution efficiency and scalabilitySpecial data processing applicationsRule miningA domain
The invention belongs to the technical field of data mining and specifically discloses a domain knowledge-based multilayer association rules mining method and system. The method comprises the following steps: taking the domain knowledge as basic data and constructing a domain correlation model according to the correlation of the basic data; taking the domain knowledge as the basic data and constructing a structure classification layer according to the basic data; performing clustering storage on the items on the basis of the structure classification layer, thereby generating an item clustering layer and constructing an original transactional database; performing layer classification on the original transactional database and mapping the layer classification into a frequent pattern tree for constructing a frequent pattern tree structure; searching the frequent pattern tree, thereby acquiring a result of a frequent item set. According to the invention, the correctness and completeness of the mining result of the frequent item set are ensured, and the method, compared with the present similar latest mining algorithm, has better executing efficiency and expansibility.
Owner:GUANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI
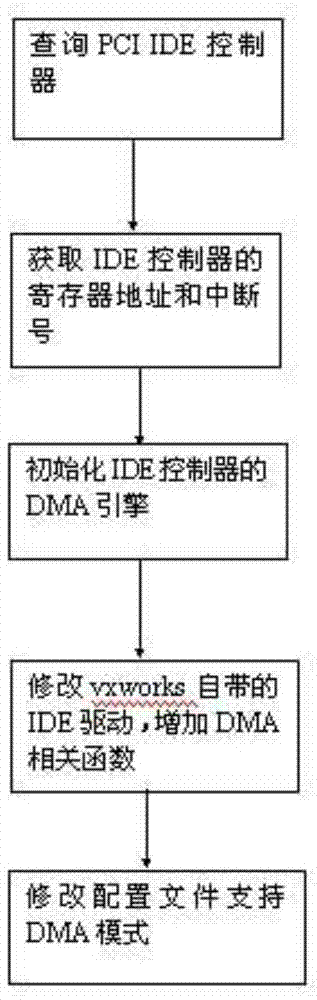
Quick starting optimizing method based on X86 platform Vxworks operation system
ActiveCN103942069AReduce startup timeOptimize execution efficiencyProgram loading/initiatingMemory addressOperational system
The invention discloses a quick starting optimizing method based on an X86 platform Vxworks operation system. The method comprises the following steps of (1) BIOS execution and (2) Vxworks loading and starting. According to the step of BIOS execution, after a computer is powered on and started, POST, initialization setting, execution of resident programs are carried out in sequence, a bootstrap program is started by calling an INT19 file in the system, a Vxworks file in the system is read directly and is analyzed after the bootstrap program is started, then an computer operation mode is switched to a protection mode from a real mode, and data and codes after analysis of the file are uploaded to assigned memory addresses respectively. According to the steps of Vxworks loading and starting, after uploading of the data and uploading of the codes are finished, the data and the codes skip to the position of a memory address e_entry corresponding to an ELF format file header to begin to be executed, the operation system is uploaded and started directly, and application programs are executed. According to the quick starting optimizing method based on the X86 platform Vxworks operation system, the method of uploading the system through bootrom in the prior art is changed, and the starting time is shortened to 3 seconds from original 20 seconds to 30 seconds.
Owner:XIAN RITRONTEK ELECTRONICS TECH
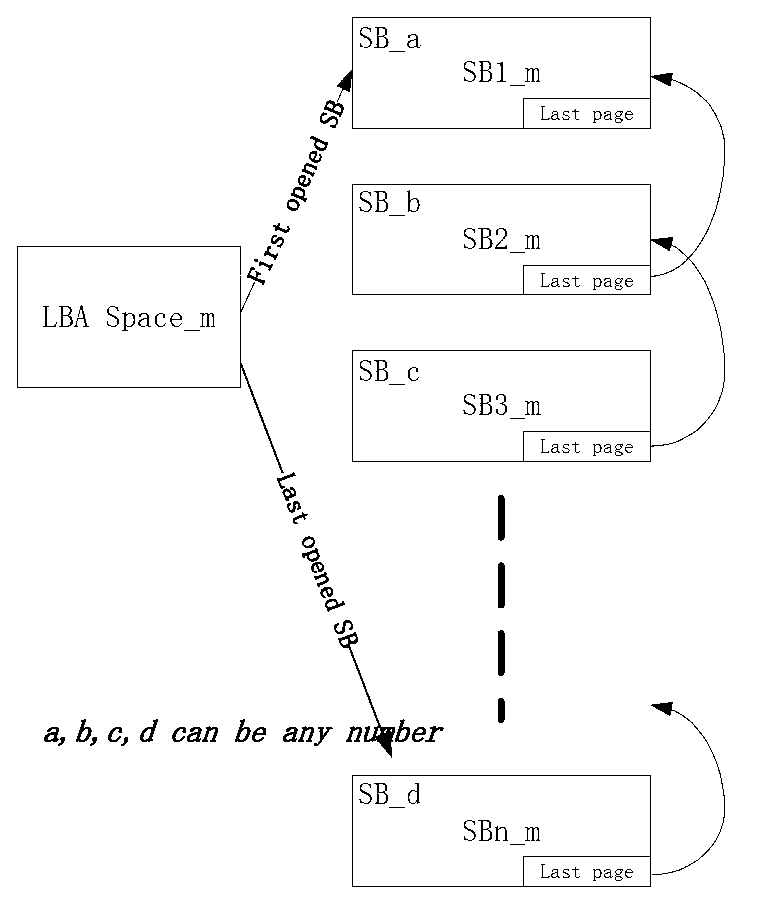
Address translation method of flash FTL (Flash Translation Layer)
InactiveCN102819496AImprove conversion efficiencyReduce conversionMemory adressing/allocation/relocationBlock numberAddress space
The invention discloses an address translation method of a flash FTL (Flash Translation Layer). The address translation method comprises the following steps of: acquiring a corresponding logic block number and a logic cluster number in the block according a logic address; searching a mapping table from logic block address spaces to super block groups according to the logic block number to obtain a corresponding physical block number and physical page number; and searching a mapping table from logic clusters to physical pages according to the physical block number and the logic cluster number in the block to obtain a corresponding physical address. According to the address translation method, addresses of physical pages corresponding to all logic clusters in the logic block can be found by only recording the physical block number and the physical page number mapped by each logic block for the final time for each logic block. Thus, the address translation speed of the FTL can be obviously increased, less hardware resource is occupied, and the address translation method has extremely high execution efficiency for reading and writing of continuous data and random data and has high flexibility.
Owner:常州新超电子科技有限公司
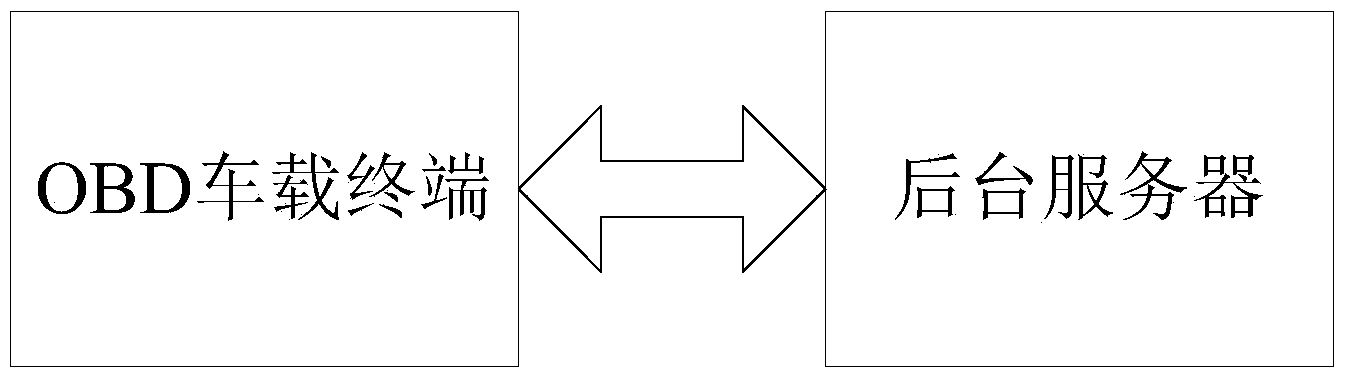
Calibrating system and method applied to vehicle monitoring terminal
InactiveCN103969469AImprove calibration accuracy and efficiencyImprove reliabilityTesting/calibration of speed/acceleration/shock measurement devicesSpeed measurementCalibration result
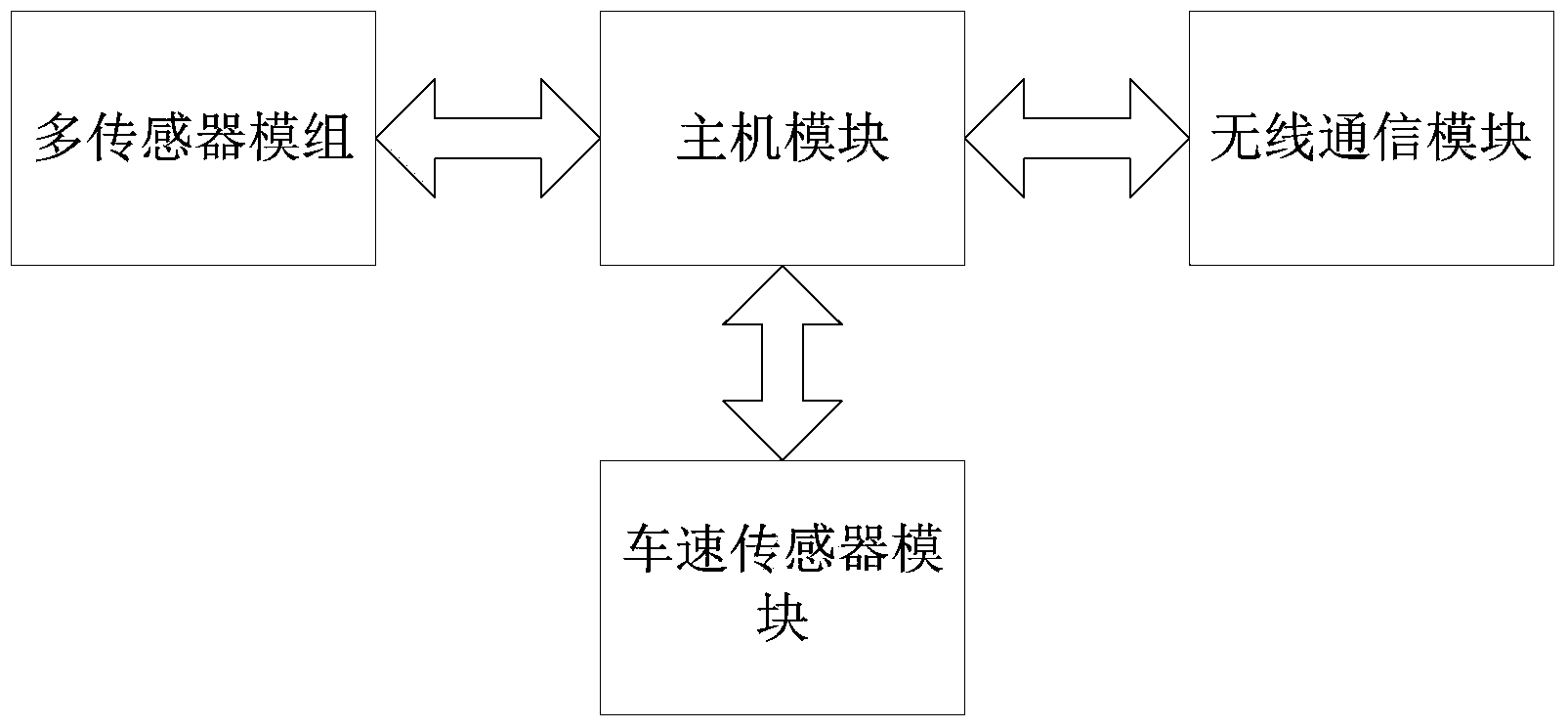
The invention relates to a calibrating system and method applied to a vehicle monitoring terminal. The calibrating system comprises an OBD vehicle-mounted terminal and a background server. The OBD vehicle-mounted terminal comprises a host module, a multi-sensor module, a wireless communication module and a vehicle speed measurement interface module. The wireless communication module is used for conducting wireless data communication with the background server, the multi-sensor module is used for measuring and obtaining G-sensor tri-axial acceleration speed information, tri-axial angular speed information, geomagnetic information, pressure information and temperature information of a vehicle, the vehicle speed measurement module is used for measuring and obtaining driving speed information of the vehicle and the host module is used for packaging the data and transmitting the data to the background server. The background server is used for calculating the received calibration parameter information, and calibration result information obtained after processing is transmitted to the OBD vehicle-mounted terminal. The calibrating system and method obviously improve the calibration precision and efficiency of the vehicle monitoring terminal and have the advantages of being good in user experience and the like.
Owner:SHENZHEN MESADA TECH
Taxi passenger-carrying trajectory clustering algorithm Tr-OPTICS
InactiveCN107392245AImprove accuracyOptimize execution efficiencyData processing applicationsCharacter and pattern recognitionCluster algorithmComputation complexity
The invention discloses a taxi passenger-carrying trajectory clustering algorithm Tr-OPTICS. A research object of the algorithm is passenger-carrying trajectories; reachable distance of trajectories, concepts of core trajectories and search neighborhood scopes of the core trajectories are redefined. For passenger-carrying trajectories of large data volumes, an adjacency list is used for replacing a spatial index in the algorithm, and therefore calculation complexity of the algorithm can be lowered. Algorithm execution efficiency and accuracy of clustering results can be improved via the Tr-OPTICS algorithm put forward in the invention. Stability can be maintained despite different sample sizes, and a frequent pattern of passenger-carrying sub-trajectories can be effectively found based on clustering results via the algorithm disclosed in the invention.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
MapReduce-based FP-Growth load balance parallel computing method
InactiveCN104731925AGood load balancing ability and execution efficiencyResolve uneven load situationsSpecial data processing applicationsDatabase transactionMultiple node
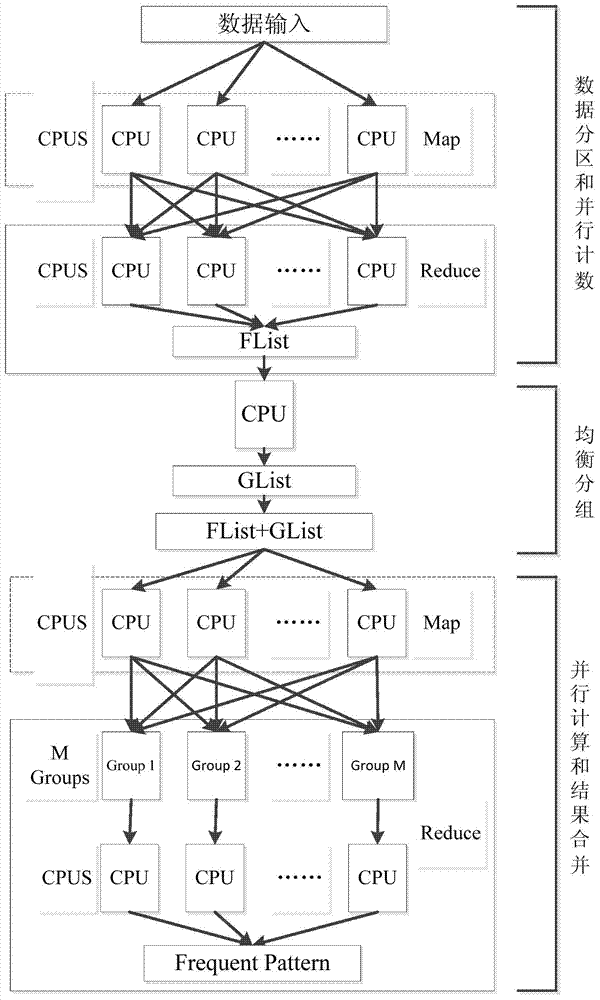
The invention relates to a MapReduce-based FP-Growth load balance parallel computing method. The method comprises the steps that 1, a database transaction set D is divided into different continuous partitions, and a sub-transaction set are stored on multiple nodes; 2, parallel computing is conducted on support counts to obtain all the frequent one-item sets FList; 3, items of the frequent one-item sets are divided into M groups according to a load balancing method to obtain a new list GList; 4, the database transaction set D is also divided into M groups according to the new list GList, a local FP-Tree of each transaction set DB is created when the division of the database transaction set D is finished, and a corresponding GList[gidi] is mined according to each local FP-Tree to obtain the frequent patterns of all the items in the frequent one-item set; 5, the frequent patterns of all the items in the frequent one-item set obtained on each node are aggregately output. The MapReduce-based FP-Growth load balance parallel computing method has good load balancing capacity and execution efficiency.
Owner:JIANGSU CAS JUNSHINE TECH
Clustering model based high-dimensional data stream outlier detection method
InactiveCN105868266AIncrease processing rateImprove accuracyRelational databasesSpecial data processing applicationsData stream processingMachine learning
The present invention belongs to application of a data mining algorithm in the field of high-dimensional data stream processing, and in particular, relates to a clustering model based high-dimensional data stream outlier detection method. According to the method, clustering is performed on sample data streams firstly; next, a feature dimension of each cluster in a clustering result is analyzed; when calculating which cluster a testing data set belongs to, only an attribute relates to the feature dimension of the cluster is calculated but calculation of a redundancy attribute is omitted, which thus effectively reduces a calculation amount; and if it is discovered that a certain data point does not belong to any cluster, the point forms a new cluster, and if a certain cluster does not attract a new data point for a long time and the number of data points of the cluster is small, then the cluster is a cluster that contains an outlier. The method provided by the present invention has the technical effect that the efficiency and accuracy of the method is both higher than the conventional outlier detection algorithm based on a sliding window when perform high-dimensional data stream outlier detection.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
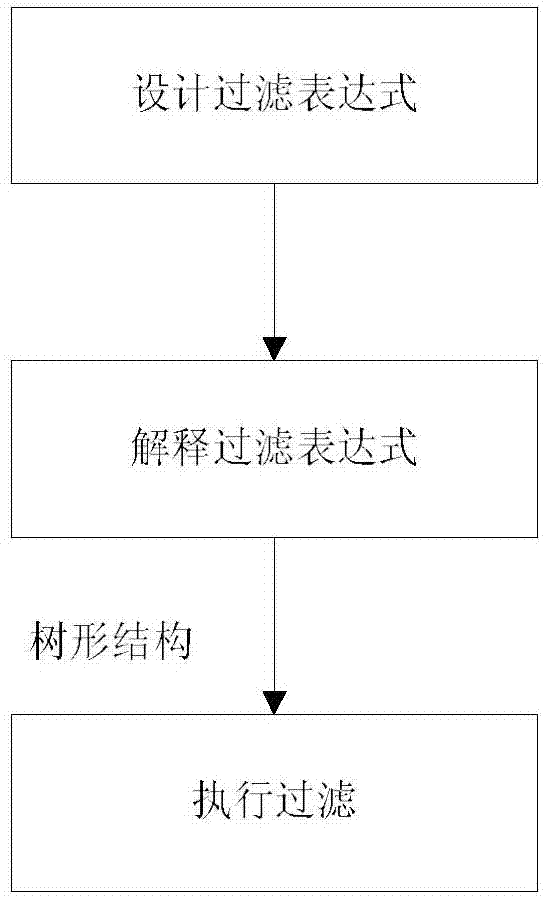
Instruction filtering method and device for specifications of ARINC661
ActiveCN104331278AFlexible configurationOptimize execution efficiencySpecific program execution arrangementsSpecial data processing applicationsFiltering rulesTree shaped
The invention discloses an instruction filtering method and device for specifications of ARINC661. The instruction filtering method comprises the following steps of designing a filtering expression; explaining the filtering expression; executing filtering. According to the instruction filtering method, characteristic attributes of ARINC661 instruction blocks are extracted as key words for designing filtering rules, and the filtering expression is designed to combine the filtering rules. On the method for executing filtering, according to the method, a tree-shaped structure is designed for storing the filtering rules, a method for calculating a filtering result is designed based on the tree-shaped structure, and good executing efficiency is realized. The device provided by the embodiment of the invention comprises a filtering-condition configuration module, a filtering-rule-base module, a filtering-expression interpretive module and a filtering execution module, wherein the filtering-condition configuration module is used for assisting a user to design out the filtering expression flexibly; the filtering-rule-base module is used for storing the historical filtering expression; and the filtering-expression explaining module and the filtering execution module are used for executing interpretation of the filtering expression and executing the filtering method.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method for asynchronous updating based on buffer area
ActiveCN104376096AGood execution efficiencyImprove update efficiencyDatabase updatingSpecial data processing applicationsDistributed computingDistributed cache
The invention discloses a method for asynchronous updating based on a buffer area. The method includes the steps that an updating request is submitted; whether a queue is empty or not is judged; if the queue is not empty, queue elements are extracted, and an updating request is ready to be processed; a latest upgrading threshold value is calculated, and the updating request is updated to the local; whether upgrading triggers an upgrading strategy or not is checked; if the updating strategy is trigged, distributed catch or a database is upgraded.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Height histogram segmentation-based method for identifying depth defect of refractory brick
InactiveCN108596873AExtended service lifeAvoid Penetrating Corrosion PhenomenaImage enhancementImage analysisBrickData graph
The invention discloses a height histogram segmentation-based method for identifying the depth defect of a refractory brick. The method comprises the steps of obtaining a segmented refractory brick grayscale image; performing plane fitting on the image point cloud of the refractory brick by using a least square method to obtain a zero plane, obtaining the size parameter of the original image of the refractory brick, and generating a corresponding reference plane image according to the size parameter and the zero plane of the original image of the refractory brick; performing difference betweenthe original image of the refractory brick and the reference plane image, and obtaining a point cloud data graph after the inclination correction process; carrying out filtering segmentation on the height histogram of the point cloud after the inclination correction process to obtain the point cloud information with a preset depth; marking communicated areas according to the point cloud information of the preset depth through adopting the double scanning method, calculating the area of the communicated areas at each depth, and obtaining defect data. According to the invention, the identification method for identifying the depth defect of the refractory brick is provided.
Owner:SHANDONG IND TECH RES INST OF ZHEJIANG UNIV
Method for processing acquisition index dynamic image
InactiveCN101706717AImprove experienceFully integratedSpecific program execution arrangementsData displayControl layer
The invention relates to a method for processing an acquisition index dynamic image. The technologies of Flash, favaScript and XML are integratively used to construct a model-view-control (MVC) data display model, wherein the Flash is used as a view layer, the JavaScript is used as a control layer, and the XML is used as a model layer. The invention adopts the well developed Flash technology, the XML technology and the Ext technology, wherein the Ext is the latest JavaScript class library. The method for processing the acquisition index dynamic image is constructed and formed through the MVC; and by adopting the method, the most reasonable integration mode is found, the advantages of the technologies are fully fused, an attractive interface is displayed, data can be acquired dynamically in real time without refreshing a page, and good user experience is achieved.
Owner:LINKAGE SYST INTEGRATION
White-box software implementation method of commercial code SM4 algorithm in standard ciphertext output format
ActiveCN107070636AEffective protectionImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
The invention provides a white-box software implementation method of a commercial code SM4 algorithm in a standard ciphertext output format. In the method provided by the invention, 36 times of operation are needed, each operation is divided into three layer, each layer utilizes input or output conversion to mix, input / output conversion parts between the layers are counteracted, operation of the layer including a secret key is achieved by a lookup table, the secret key appears in the algorithm non-explicitly, and the secrete key cannot be acquired by analyzing intermediate data. According to theSM4 white-box algorithm designed by the invention, the secret key is hidden in the lookup tale, the lookup table is mixed by using linear conversion, combined analysis of the lookup table is resisted by using the composition of linear conversion, and thus the purpose of effectively protecting the secret key is achieved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
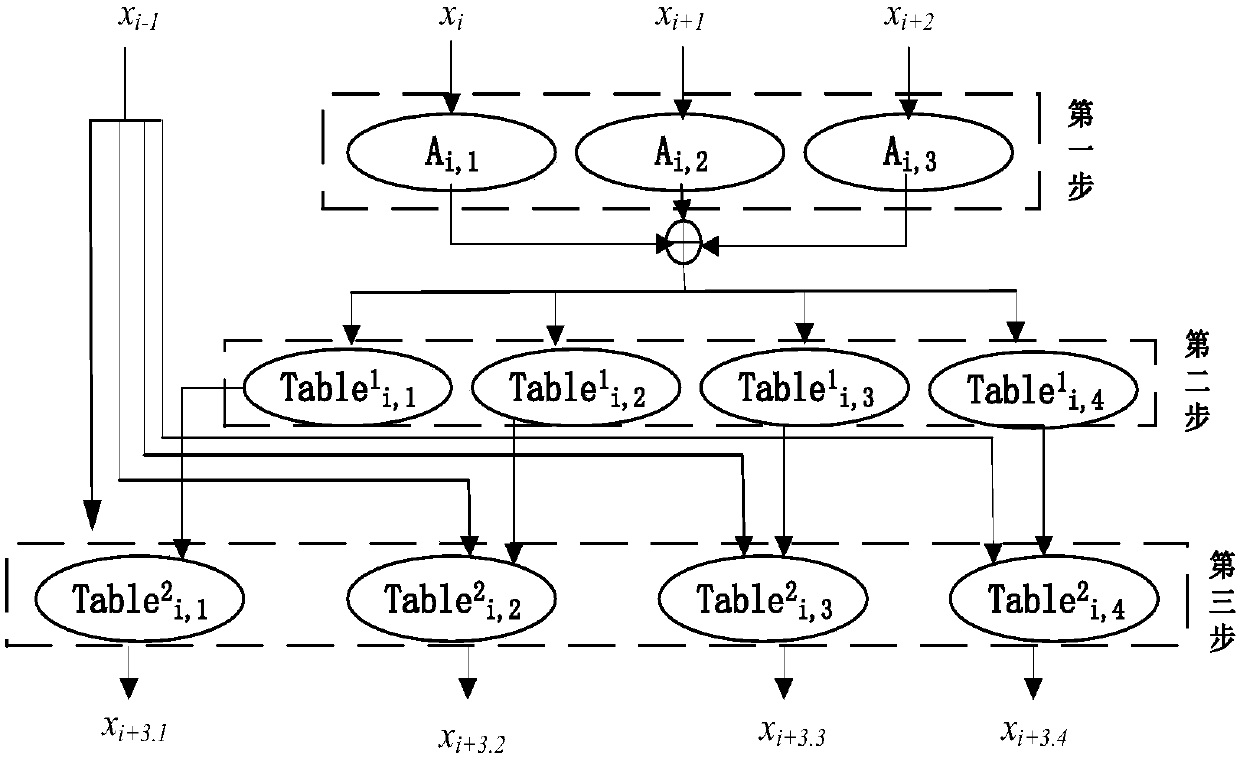
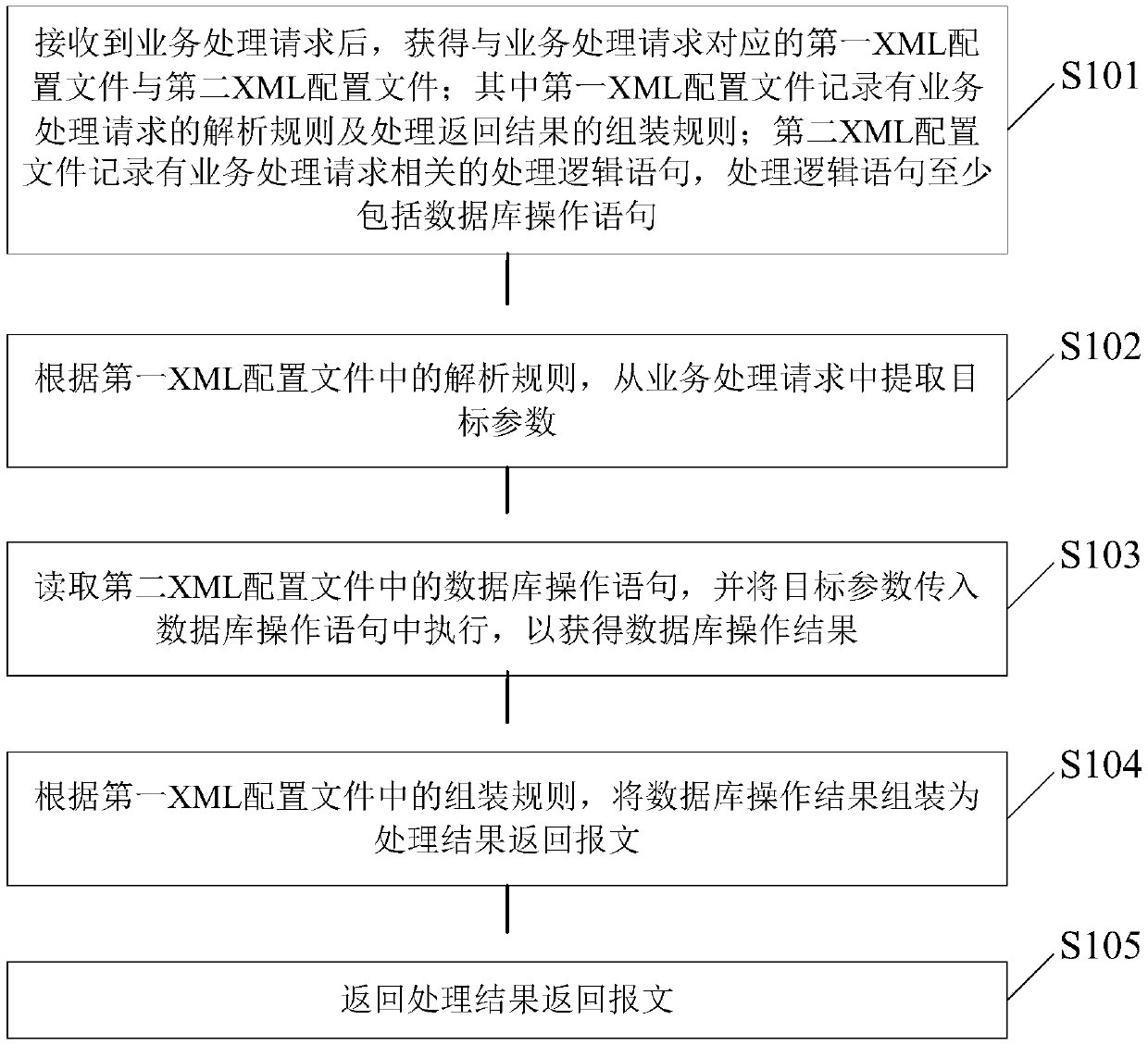
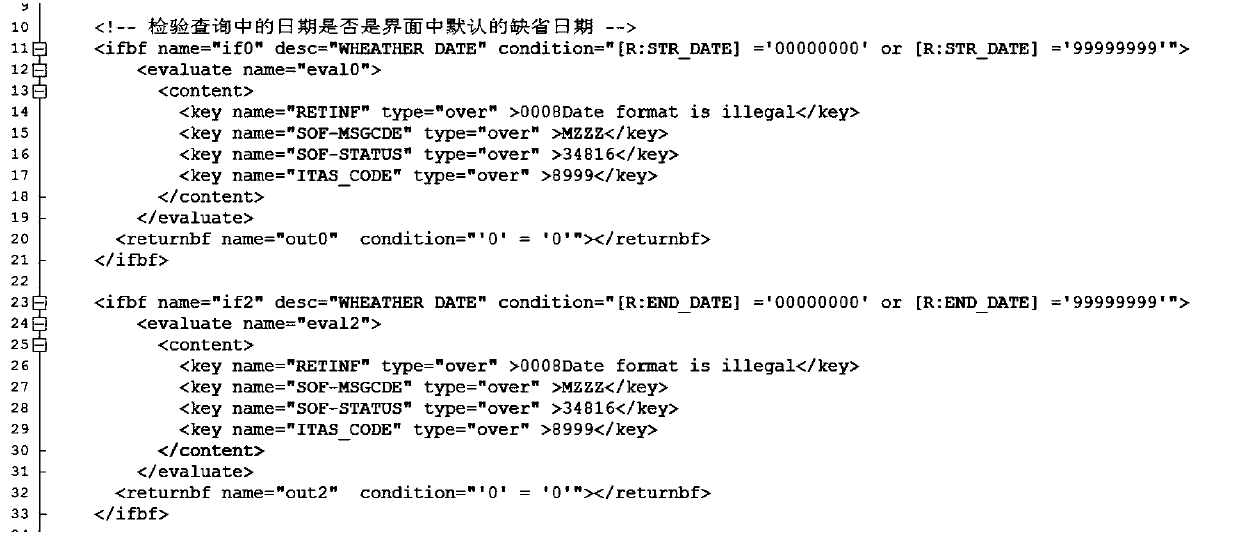
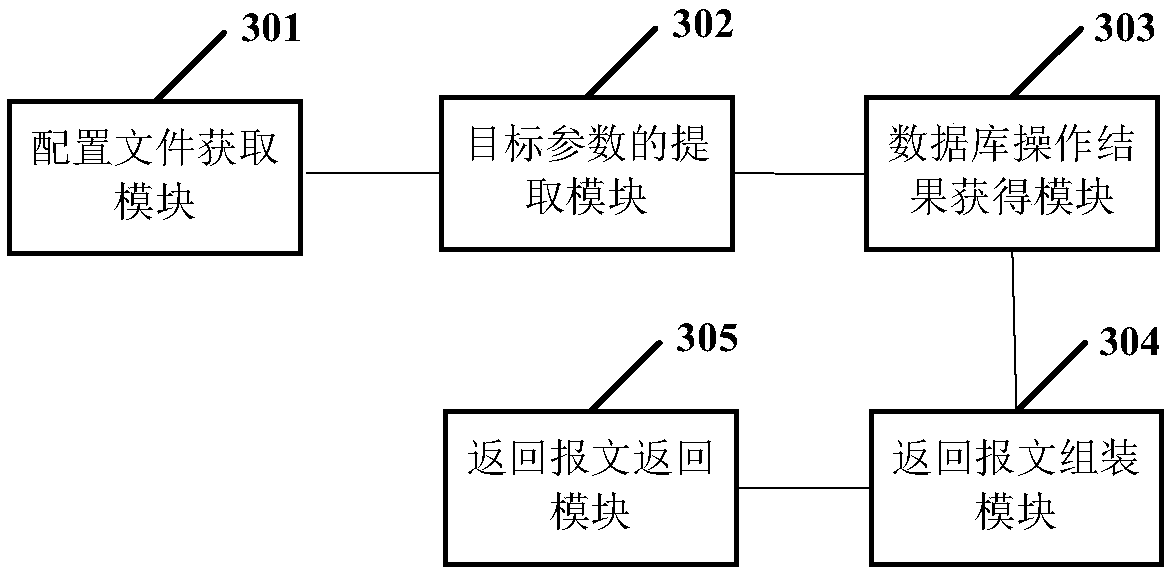
A service request processing method and device
ActiveCN109670081AOptimize execution efficiencyImprove execution efficiencySemi-structured data queryingOperation modeXML
The invention provides a method for operating a database. The method comprises the following steps of receiving a service processing request; and then obtaining a first XML configuration file and a second XML configuration file corresponding to the service processing request, and extracting a target parameter from the service processing request by using the first XML configuration file, reading and executing a database operation statement in the second XML configuration file to obtain a database operation result, assembling the database operation result into a processing result return messageaccording to the first XML configuration file, and returning the processing result return message. Compared with an existing mode of performing database operation by using a JAVA file, and according to the method and the device, the JAVA file is not used, the database operation statement is recorded in the second XML configuration file, and due to the fact that the execution efficiency of the second XML configuration file is superior to that of the JAVA file, the execution efficiency of the method and the device is higher than that of an existing database operation mode.
Owner:BANK OF CHINA
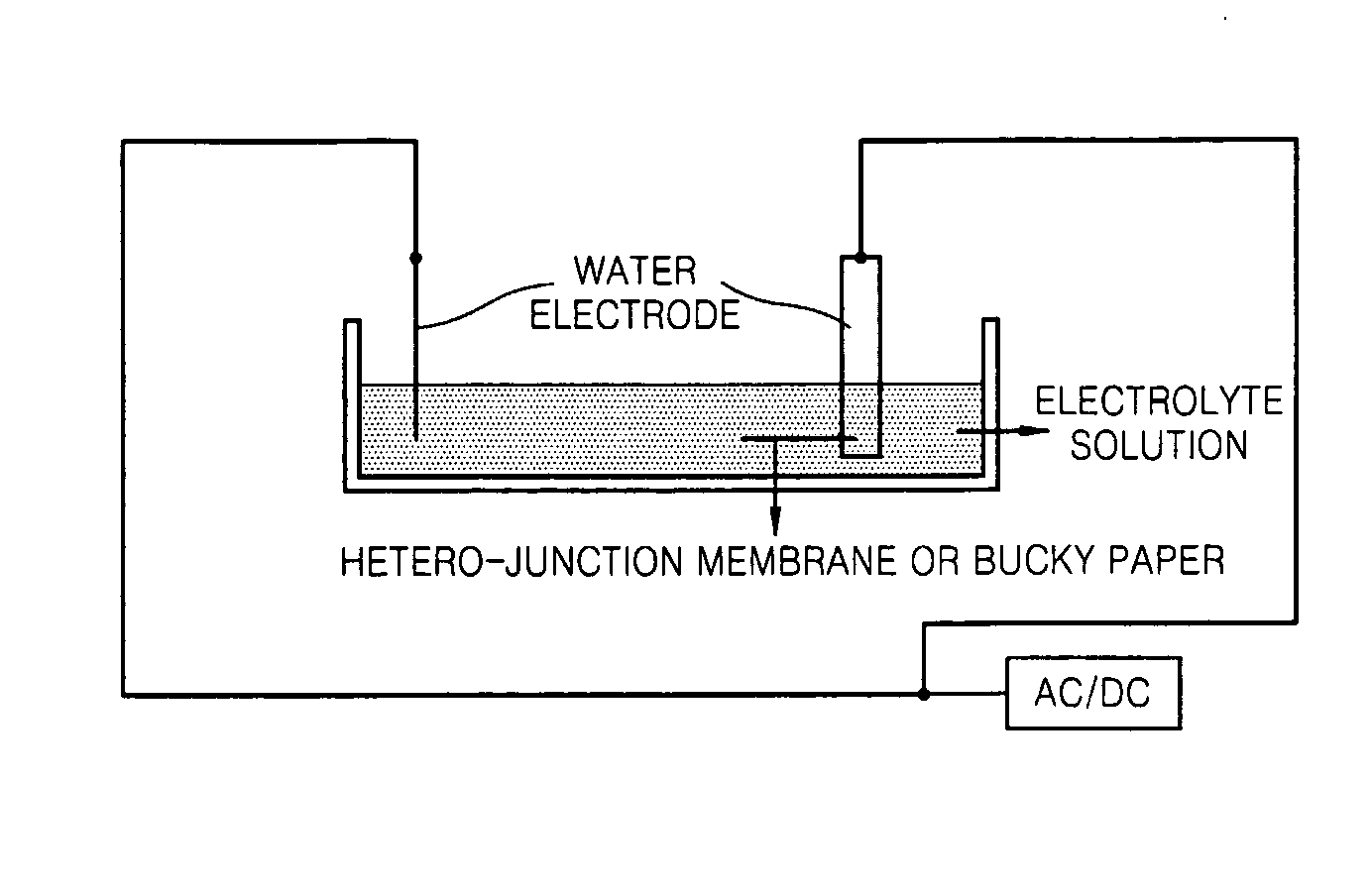
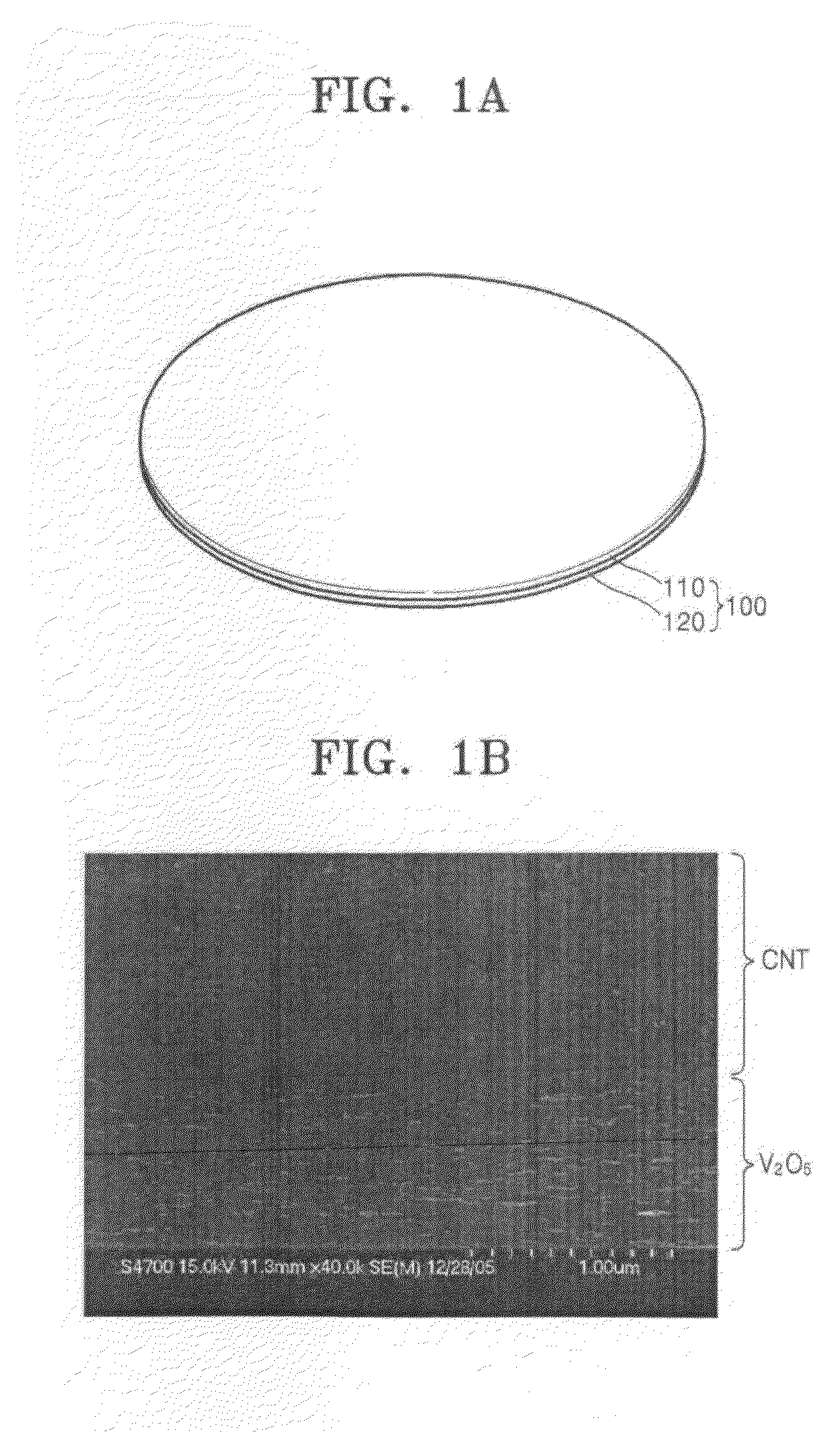
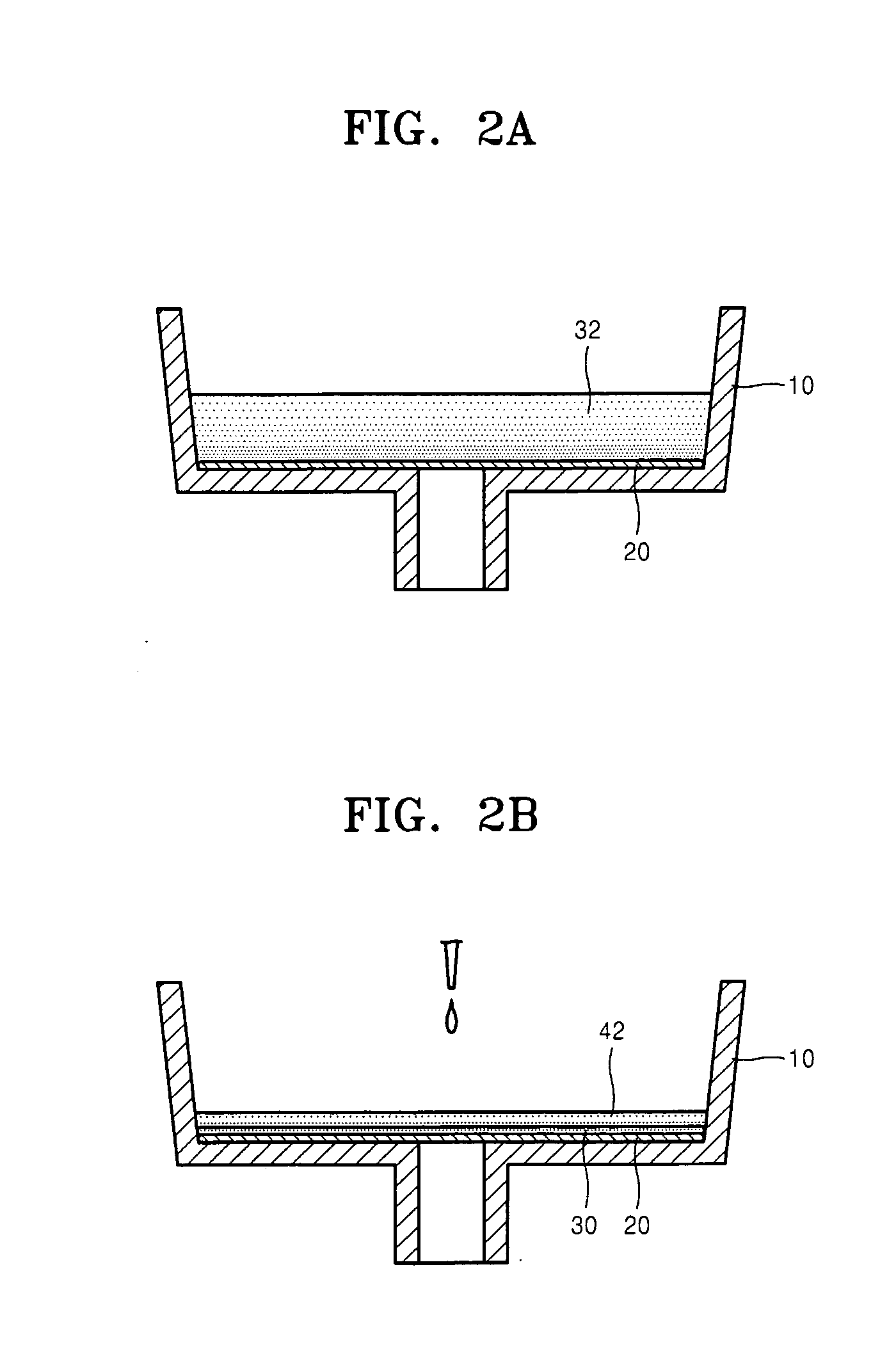
Hetero-junction membrane and method of producing the same
InactiveUS20080213567A1Improve efficiencyEasy to prepareLiquid surface applicatorsLayered productsNanoparticleEngineering
Owner:ELECTRONICS & TELECOMM RES INST
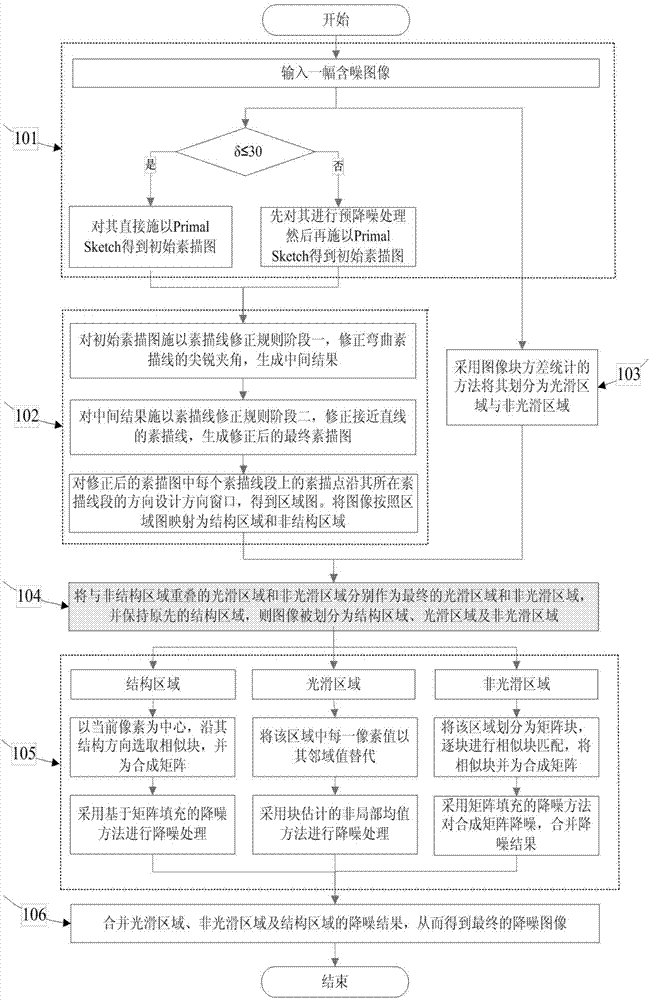
Image noise reduction method based on Primal Sketch correction and matrix filling
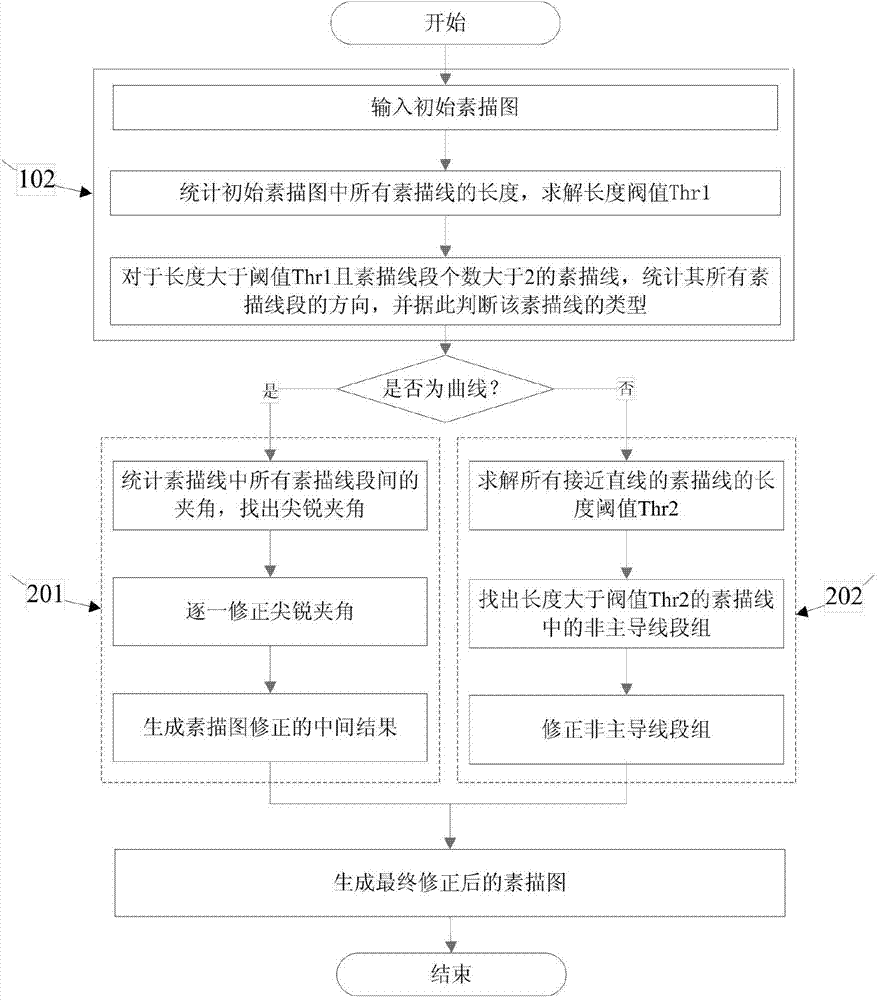
The invention relates to an image noise reduction method based on Primal Sketch correction and matrix filling. The image noise reduction method comprises, at least, step 101, adopting a Primal Sketch model to obtain a sketch map P of a noise adding image I1; step 102, providing a two-stage sketch line correction rule and a corrected sketch map P and designing a direction window for a pixel point on each sketch line segment in the corrected sketch map P in the direction of the sketch line segment to obtain a region map, mapping the image I1 into a structural region E1 and a non-structural region E2 according to the region map; step 103, simultaneously utilizing an image block variance statistic method to divide the image I1 into a smooth region E3 and a non-smooth region E4; step 104, respectively marking the smooth region and the non-smooth region overlapped with the non-structural region as a smooth region E23 and a non-smooth region E24; step 105, adopting the image noise reduction method based on the matrix filling to perform noise reduction on the E1 and the E24 and adopting a non-local average method to perform noise reduction on the E23; step 106, merging noise reduction results of the E1, the E23 and the E24 to obtain a final noise reduction result map of the image I1.
Owner:XIDIAN UNIV
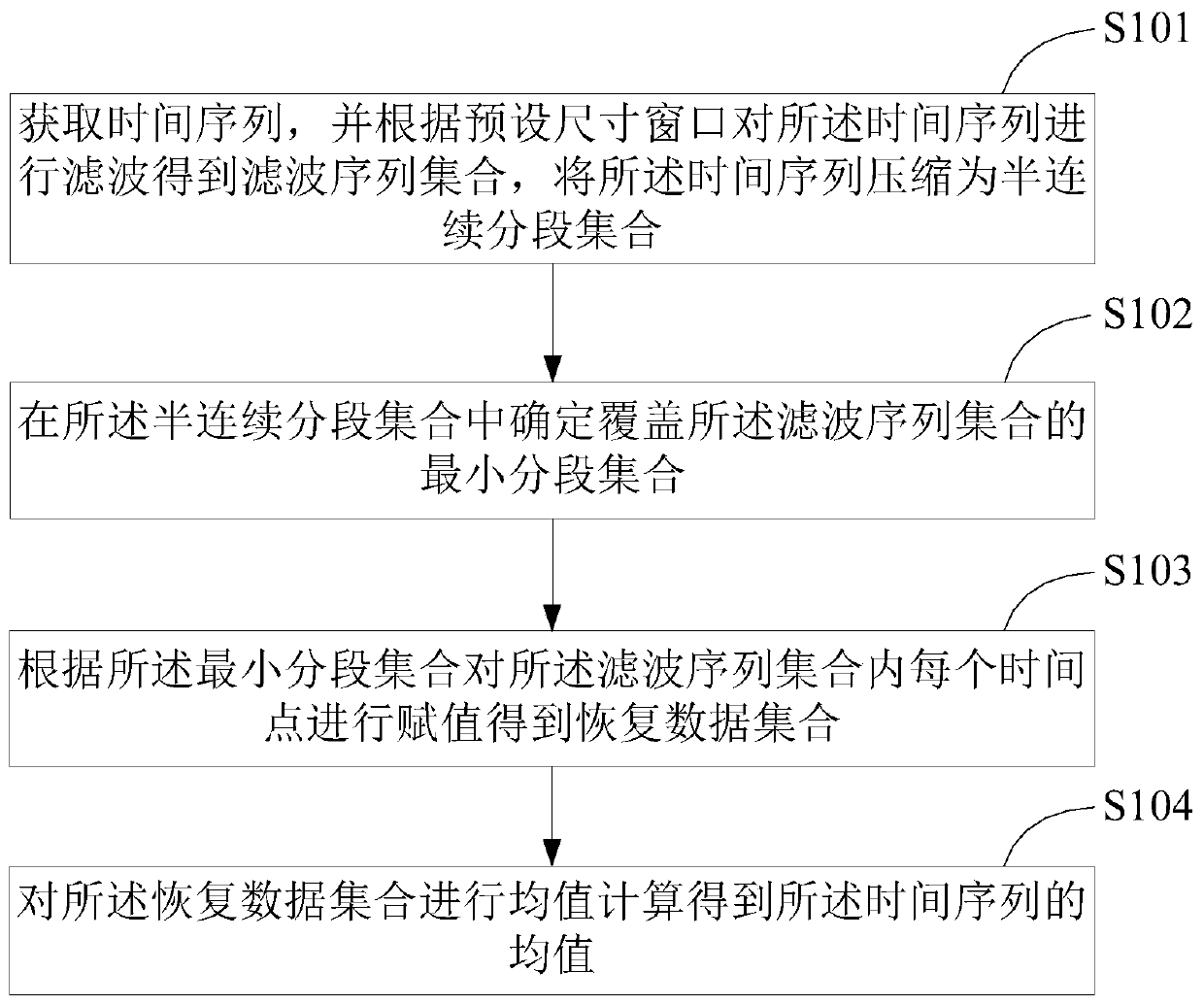
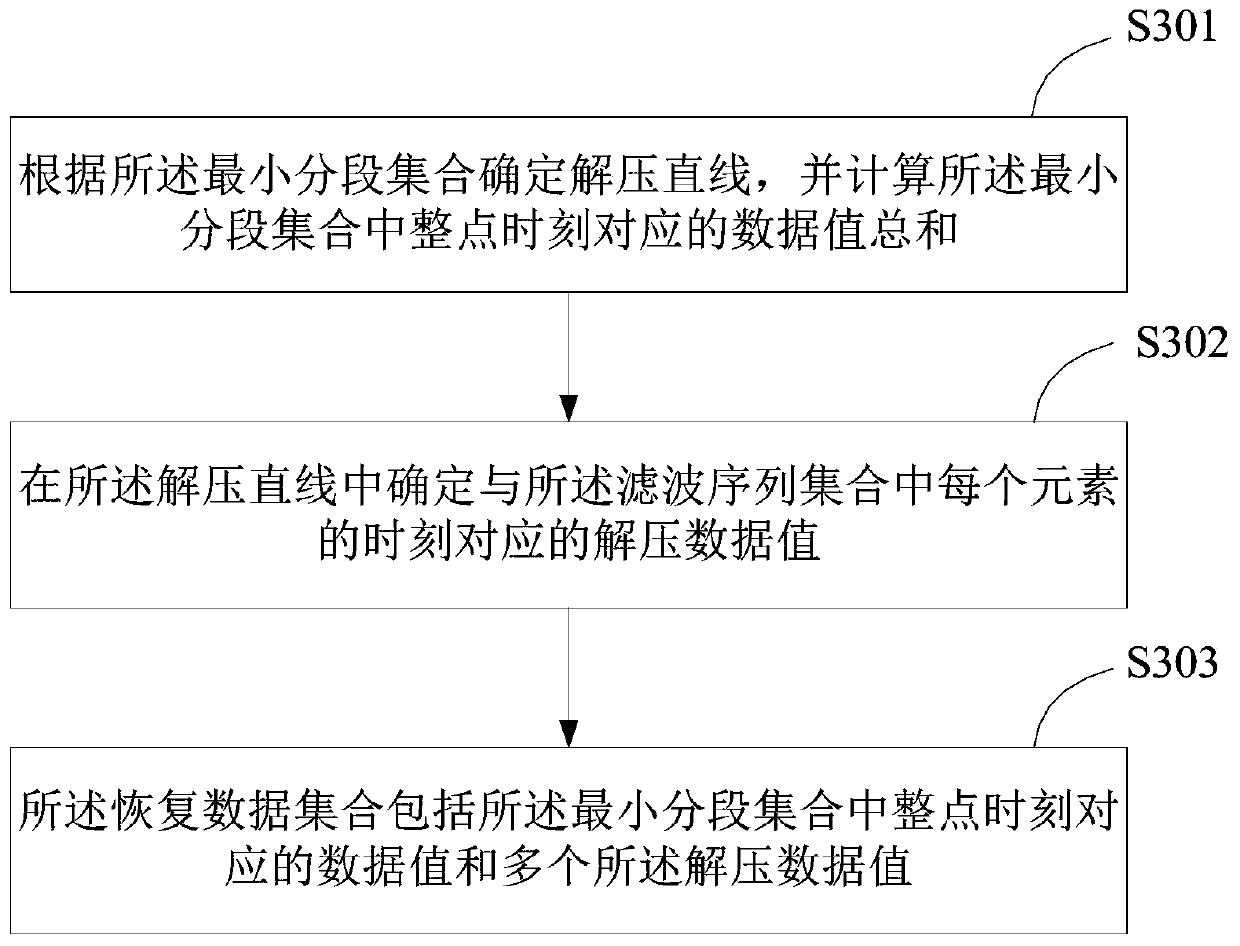
Mean value calculation method and device based on data compression and terminal equipment
InactiveCN110971239AOptimize execution efficiencyGuaranteed speedCode conversionData compressionData set
The invention is applicable to the technical field of data compression, and provides a mean value calculation method and device based on data compression and terminal equipment. The method comprises the following steps: acquiring a time sequence, filtering the time sequence according to a preset size window to obtain a filtering sequence set, and compressing the time sequence into a semi-continuous segment set; determining a minimum segment set covering the filtering sequence set in the semi-continuous segment set; assigning each time point in the filtering sequence set according to the minimum segment set to obtain a recovery data set, and performing mean value calculation on the recovery data set to obtain a mean value of the time sequence. Mean value calculation is carried out based onthe compressed data, the operation speed is high, the mean value error is controllable, the error condition is met, the mean value quality is ensured, and the execution efficiency is better.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
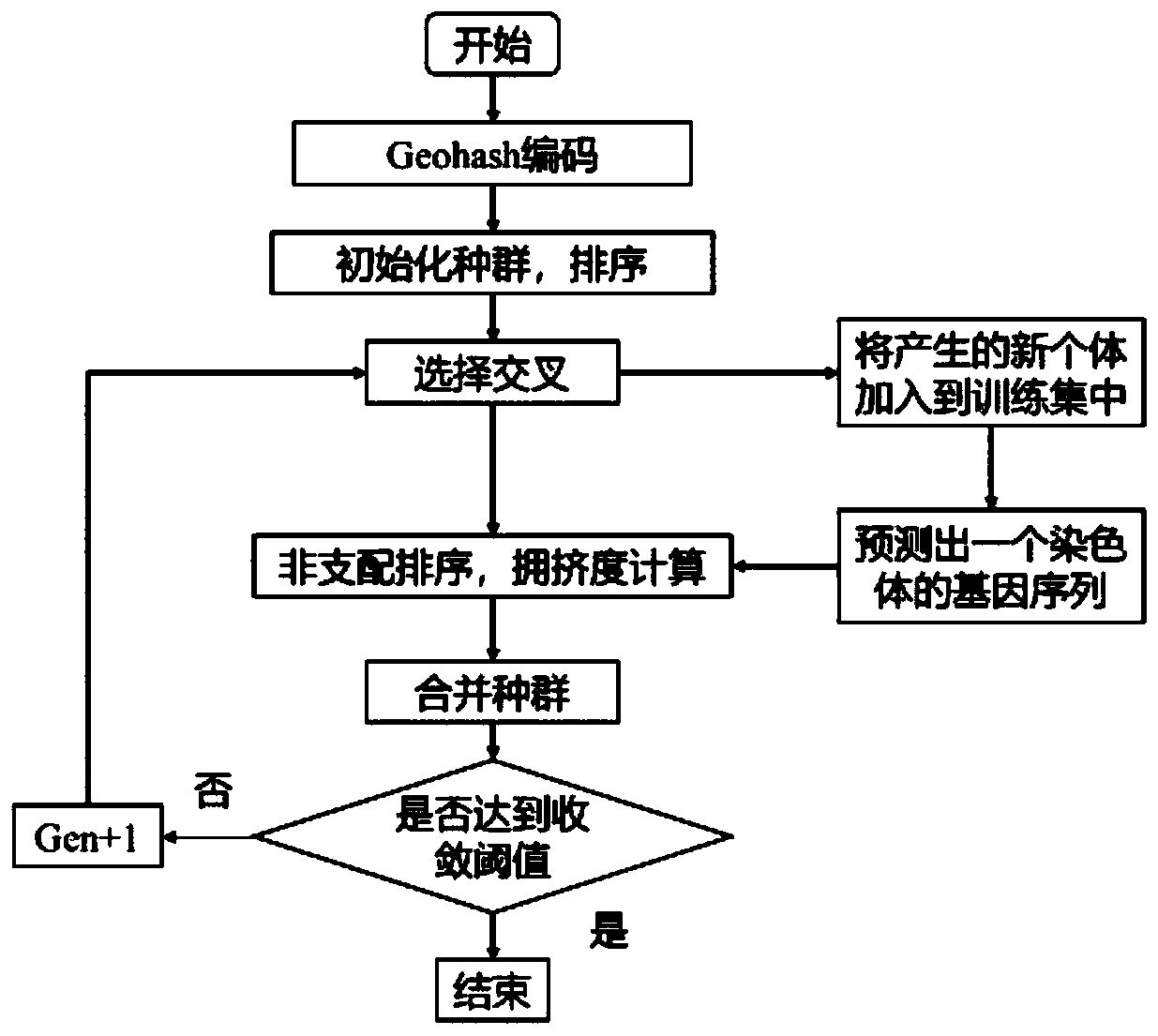
Shared bicycle parking point distribution method based on multi-objective genetic algorithm
ActiveCN111582552AOptimize execution efficiencyImprove executionInternal combustion piston enginesForecastingBicycle parkingAlgorithm
The invention relates to a shared bicycle parking point distribution method based on a multi-objective genetic algorithm. The method comprises the steps: S1, enabling a server to collect a plurality of current user request data within a certain time point; s2, after the server collects request data of the user, performing statistical analysis on coordinate information, destination information andnearby available parking point position information of the user; s3, selecting a competition algorithm as a selection operator, selecting selfing as a crossover operator, and selecting a double competition participation mode; s4, dividing the population into a plurality of levels by utilizing rapid non-dominated sorting, and calculating the crowding degree of the population; and s5, merging populations. The beneficial effects of the invention are that: according to the parking point distribution system based on the multi-objective genetic algorithm, the genetic algorithm and the regression algorithm are combined, the Hypervolume evaluation index is added, the improvement performance of the algorithm is discussed, the improvement performance is mainly represented by convergence and distributivity, and the execution efficiency and the execution effect of the algorithm are optimized to a certain extent.
Owner:ZHEJIANG UNIV CITY COLLEGE
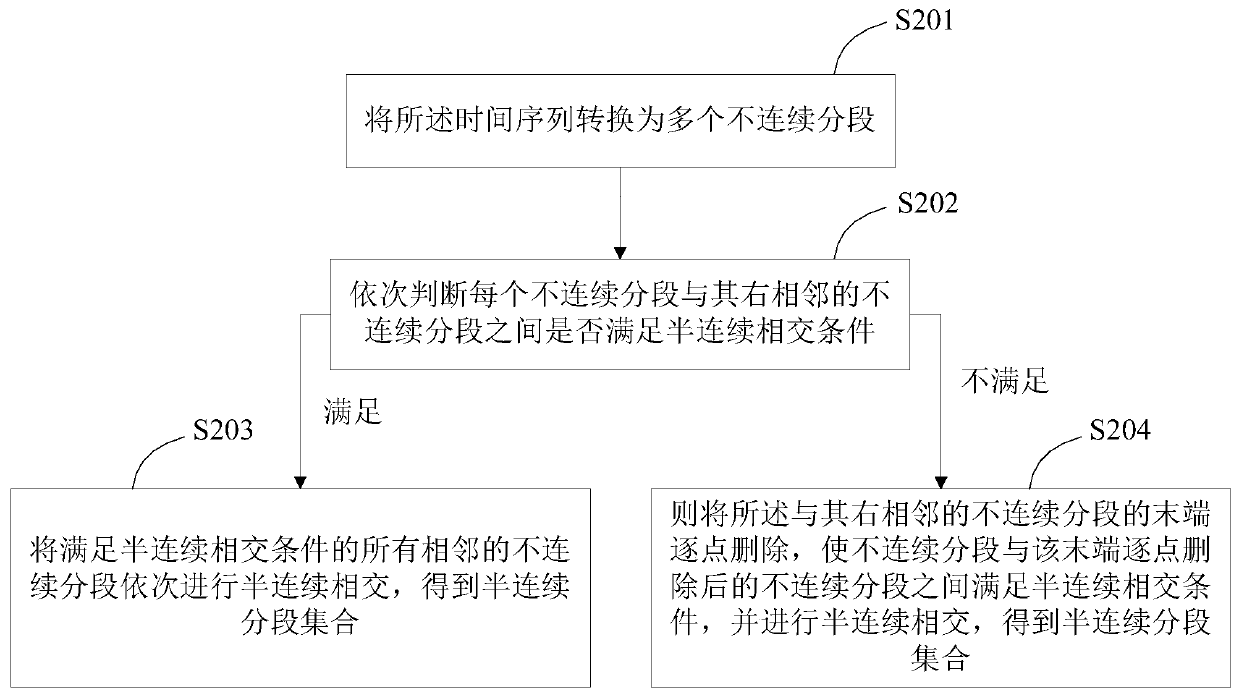
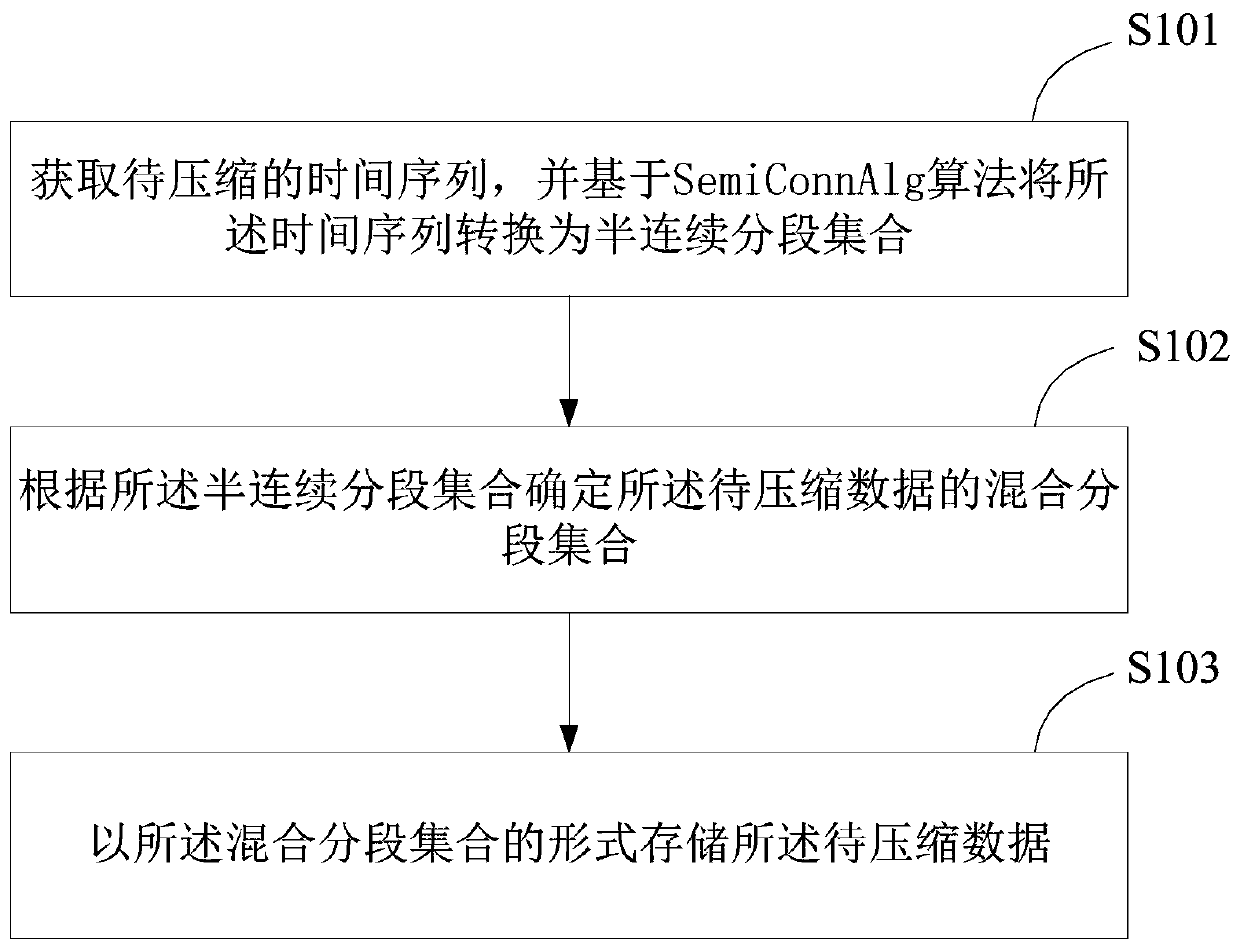
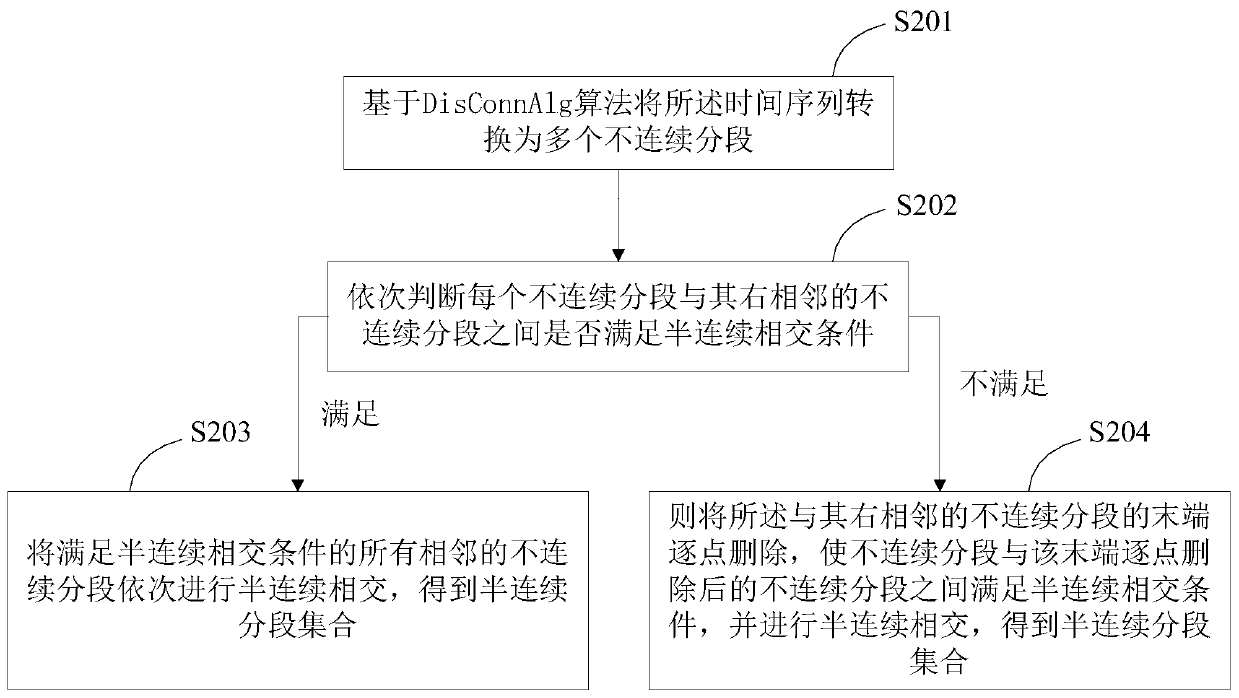
Data compression method and device and terminal equipment
ActiveCN110620586ASolving a piecewise linear approximation problemOptimize execution efficiencyCode conversionAlgorithmTerminal equipment
The invention is applicable to the technical field of data compression, and provides a data compression method and device and terminal equipment. The method comprises the following steps: acquiring atime sequence to be compressed, and converting the time sequence into a semi-continuous segment set based on a SemiConnAlg algorithm; determining a mixed segment set of the to-be-compressed data according to the semi-continuous segment set; and storing the to-be-compressed data in the form of the mixed segment set. According to the method, the optimal partwise linear approximation problem is solved, the linear time complexity is achieved, and the better execution efficiency is achieved while the optimal storage is guaranteed.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
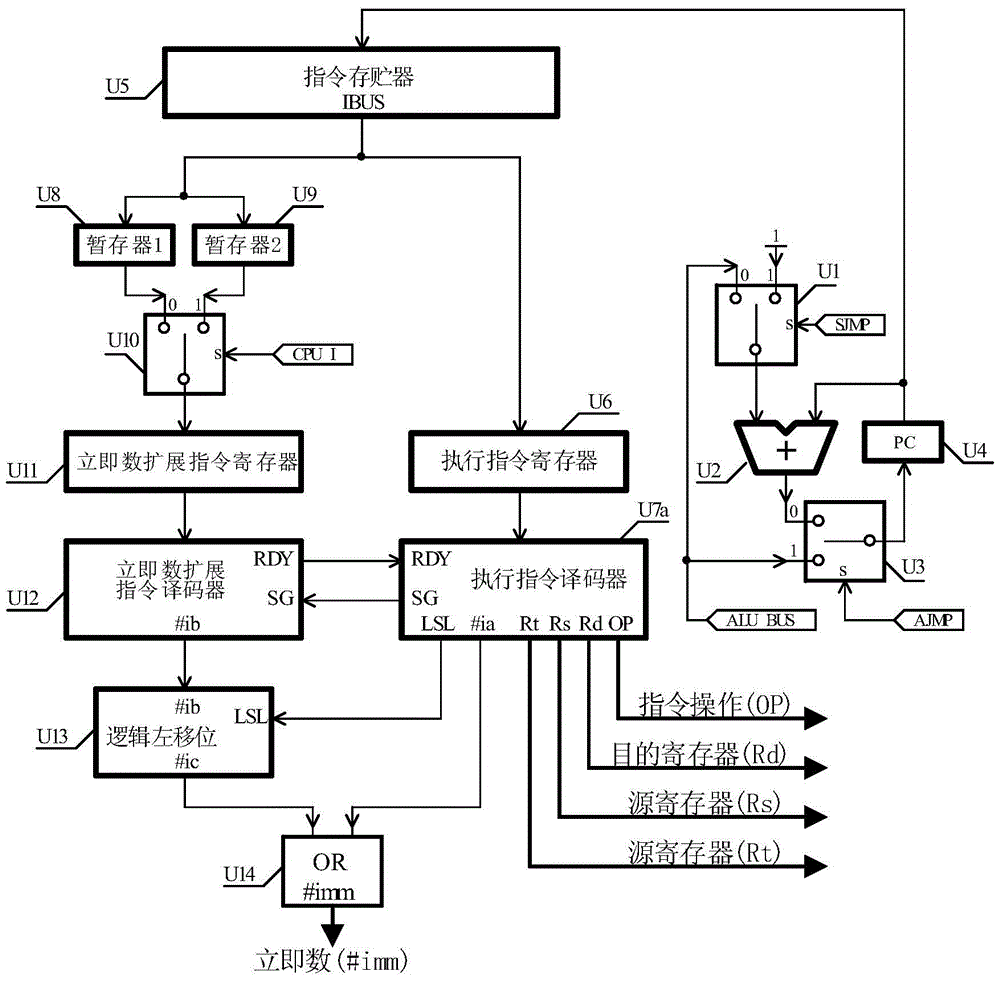
Method and device for extending immediate operand in computer instruction
ActiveCN105677298AOptimize execution efficiencyShorten the timeMachine execution arrangementsProgramming processLeft shifting
The invention discloses a method and device for extending an immediate operand in a computer instruction. At least one immediate operand extending instruction is newly increased in an RISC instruction system, during the programming process, an immediate operand the digit number of which is larger than the length of an immediate operand domain of an execution instruction is divided into a high-order immediate operand field and a low-order immediate operand field, the high-order immediate operand field is subjected to signed extension or unsigned extension and then is stored in the immediate operand domain of the immediate operand extending instruction, and the low-order immediate operand field just fills up the immediate operand domain of the execution instruction; during the instruction fetching process, the newly-increased immediate operand extending instruction and the execution instruction following closely are sent into respective decoders synchronously to carry out decoding; during the decoding process, the immediate operand output by the immediate operand extending instruction decoder is subjected to logical left shift and then is merged with the immediate operand output by the execution instruction decoder, after the merging process, the immediate operand the digit number of which is larger than the length of the immediate operand domain of the execution instruction is obtained. By employing the method for extending the immediate operand in the computer instruction, the program execution efficiency can be greatly improved, and time and space are saved.
Owner:李朝波
Coevolutionary algorithm optimized support vector machine wetland remote sensing remote sensing classification method
ActiveCN107067035AReduce diversityIncrease diversityScene recognitionSupport vector machineLocal optimum
Provided is a coevolutionary algorithm optimized support vector machine wetland remote sensing remote sensing classification method, belonging to the technical field of remote sensing. The method includes the following steps of 1. adopting an individual coding manner; 2. calculating the individual fitness function; and 3. performing PSO-GA coevolutionary algorithm: (1) initializing the population and parameters; (2) adopting a PSO evolution strategy; (3) adopting a GA evolution strategy; (4) selecting the filial generation; and (5) updating the selection probability of the strategies. The PSO-GA coevolutionary algorithm is adopted to carry out the optimization selection of the SVM model parameters, the algorithm combines the PSO and GA and takes the optimization parameters and the high-precision classification as the design scheme to perform the probability selection of the evolution strategies, and through the combination of the two evolution calculating modes, the global searching capability is guaranteed to prevent from local optimization and the evolution speed is improved.
Owner:HARBIN NORMAL UNIVERSITY
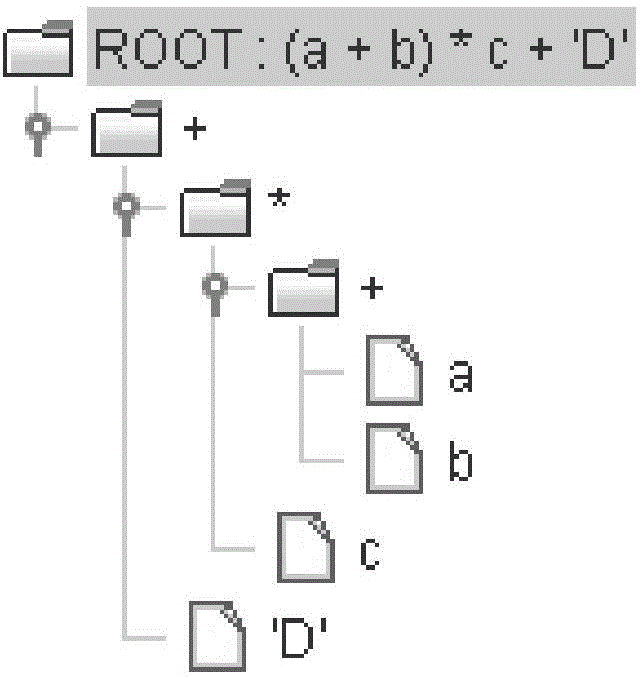
Scripting language execution method and device
InactiveCN105786465AReduce dependenceImprove execution efficiencySoftware simulation/interpretation/emulationScripting languageParsing
The embodiment of the invention provides a scripting language execution method, which comprises the following steps: (1) analyzing and explaining the code of a scripting language to generate an operation subset; (2) generating the operation subset into an operable code, and storing the code into a memory; and (3) executing the operable code. The invention also correspondingly provides a scripting language execution device. The scripting language execution method and device carries out a code curing operation on grammatical analysis and operation subset explanation exaction processes in an execution process of the scripting language through a precompiled way, so that the scripting language reduces the explanation exaction process in the execution process, meanwhile, dependence on a virtual machine in the execution process of the scripting language is lowered, and the execution efficiency of the scripting language is improved.
Owner:YGSOFT INC
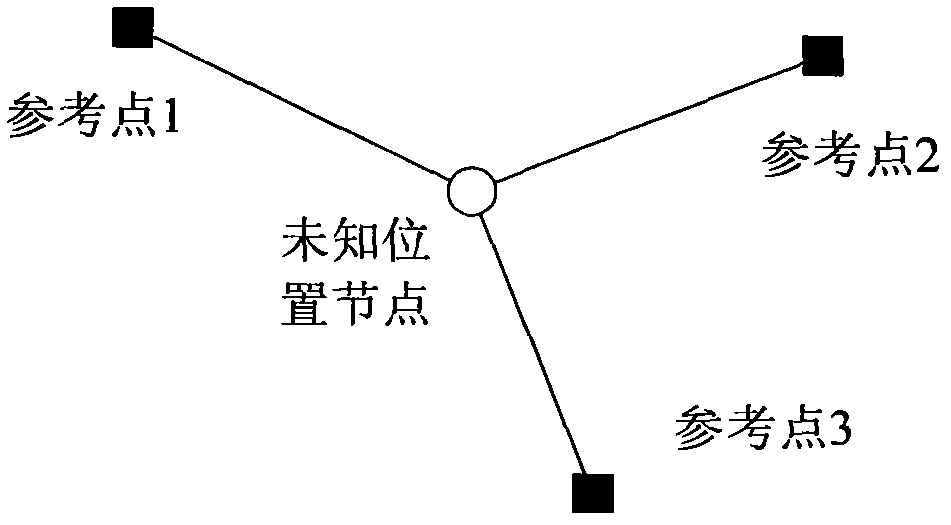
Locating method of wireless network terminal based on wheel-shaped diaphragms
ActiveCN102143580ANo uncertaintyAvoid overheadNetwork topologiesSelf-organizing networkComputer science
The invention discloses a locating method of a wireless network terminal based on wheel-shaped diaphragms, belonging to the field of a wireless self-organized network and a sensor network, and comprising the following steps of: (1) acquiring locatable nodes in the wireless network terminal as beacon nodes; (2) selecting unknown nodes around the beacon nodes, wherein the unknown nodes and the beacon nodes are in neighbour relation; (3) carrying out state information exchange among the beacon nodes and the unknown nodes and judging whether the unknown nodes can be located; (4) selecting the locatable unknown nodes and leading the unknown nodes and the beacon nodes to be in one wheel-shaped diaphragm; (5) recognizing and locating the unknown nodes, and simultaneously updating the node state to be beacon nodes; and (6) repeating the steps (1)-(5), till all the node information of the wireless network terminal is not updated. In the node locating method disclosed by the invention, more network nodes can be successfully positioned.
Owner:北京凯华信业科贸有限责任公司
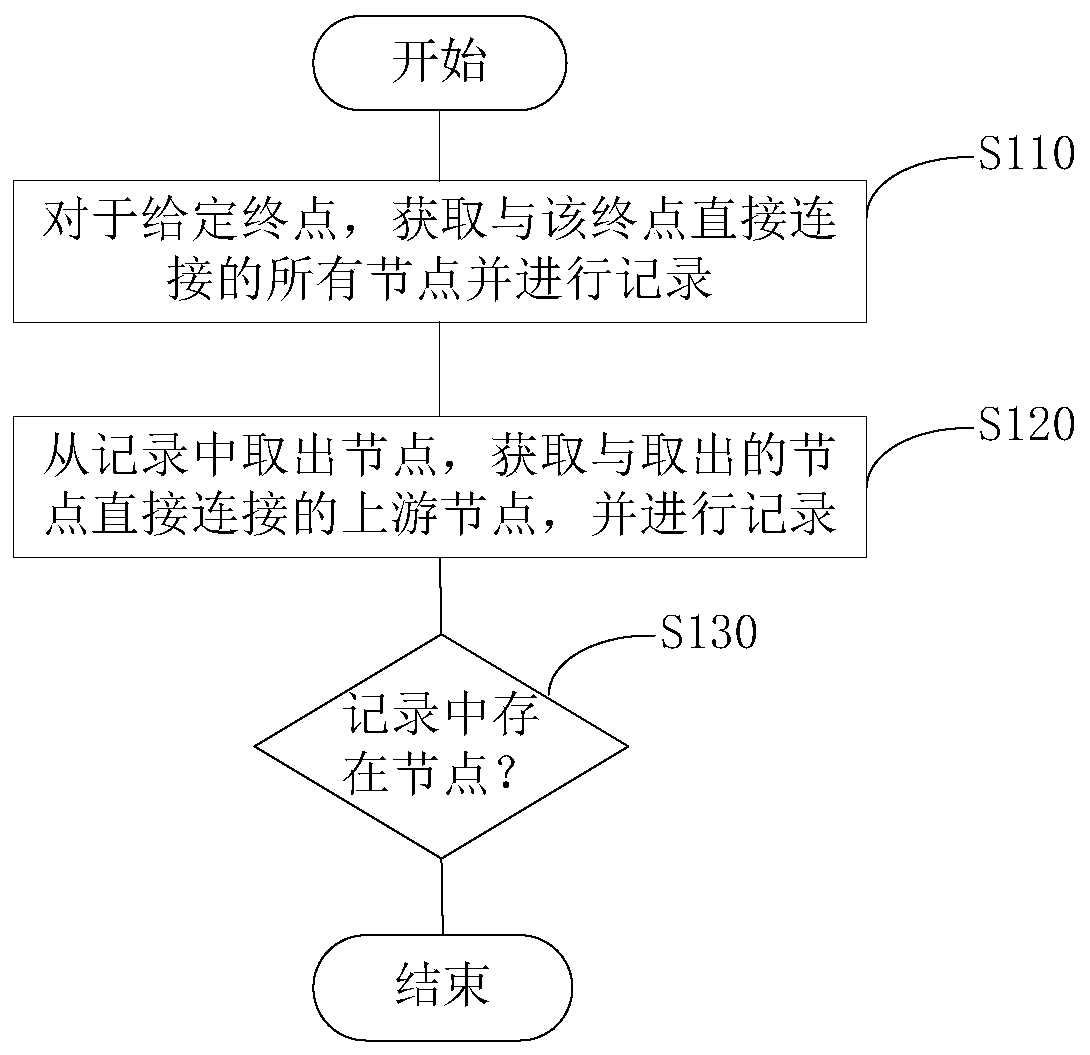
Time sequence processing method and device based on computational flow graph and storage medium
InactiveCN109740916AOptimize execution efficiencyImprove execution efficiencyResourcesTime sequenceAlgorithm
The invention provides a time sequence processing method and device based on a computational flow graph and a storage medium. The method comprises the following steps: carrying out sub-graph search based on a given end point node of a calculation flow graph to obtain a sub-graph required for calculating the end point node; Recording the degree of each node in the sub-graph, wherein the degree comprises an input degree; Traversing the subgraphs according to the recorded in-degree of the nodes, and determining a calculation execution sequence of the nodes; and performing calculation operation between the nodes based on the determined calculation execution sequence, and storing a calculation result. According to the embodiment of the invention, the execution efficiency of time sequence processing can be optimized.
Owner:YUSUR TECH CO LTD
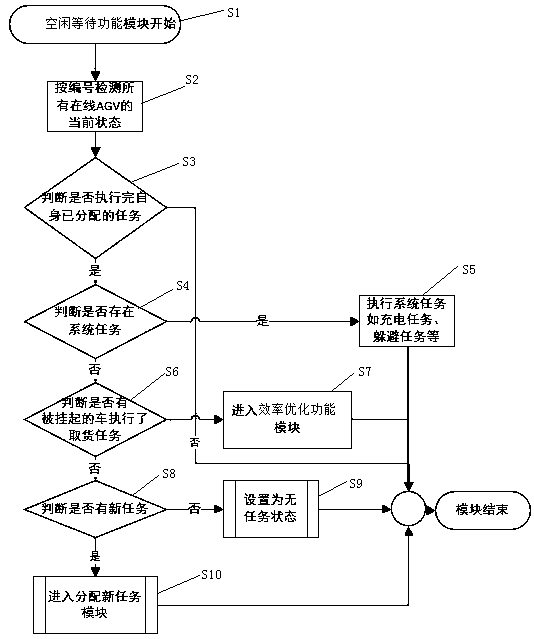
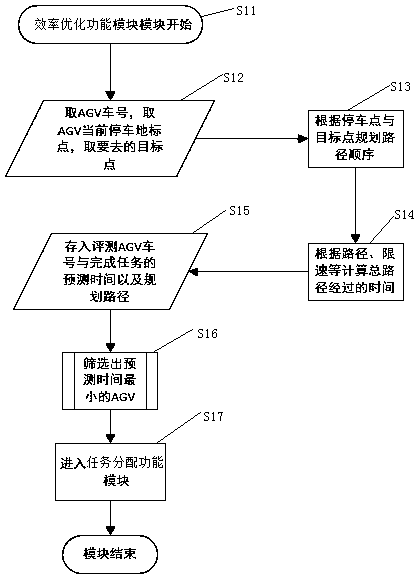
Implementation method for improving target executing efficiency of mobile robot
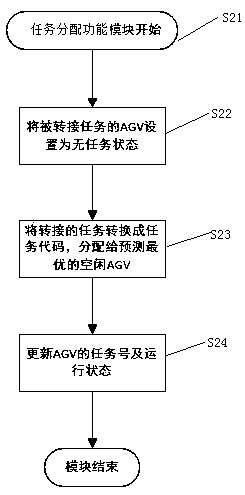
InactiveCN109254582AImprove efficiencyShorten the timePosition/course control in two dimensionsVehiclesMobile robotSoftware
The invention discloses an implementation method for improving the target executing efficiency of a mobile robot. Task distribution operation is executed, timely processing of tasks is achieved, and the tasks are transferred to more suitable AGVs so as to improve the target executing efficiency. The implementation method for improving the target executing efficiency of the mobile robot is an implementation method for a task transferring function of universal dispatching software and is used for optimizing the target executing efficiency; when the tasks are executed, blocked AGVs exist, and meanwhile, an idler and unblocked AGVs exist; and task distribution operation is re-executed through the implementation method, and timely processing of the tasks is achieved, so that the time is saved,the efficiency is improved, the automation degree of dispatching work of the AGVs is increased, and the manpower and time costs are saved.
Owner:潍坊大世自动化装备有限公司
Dual gateway-based lightweight mobile payment protocol design method
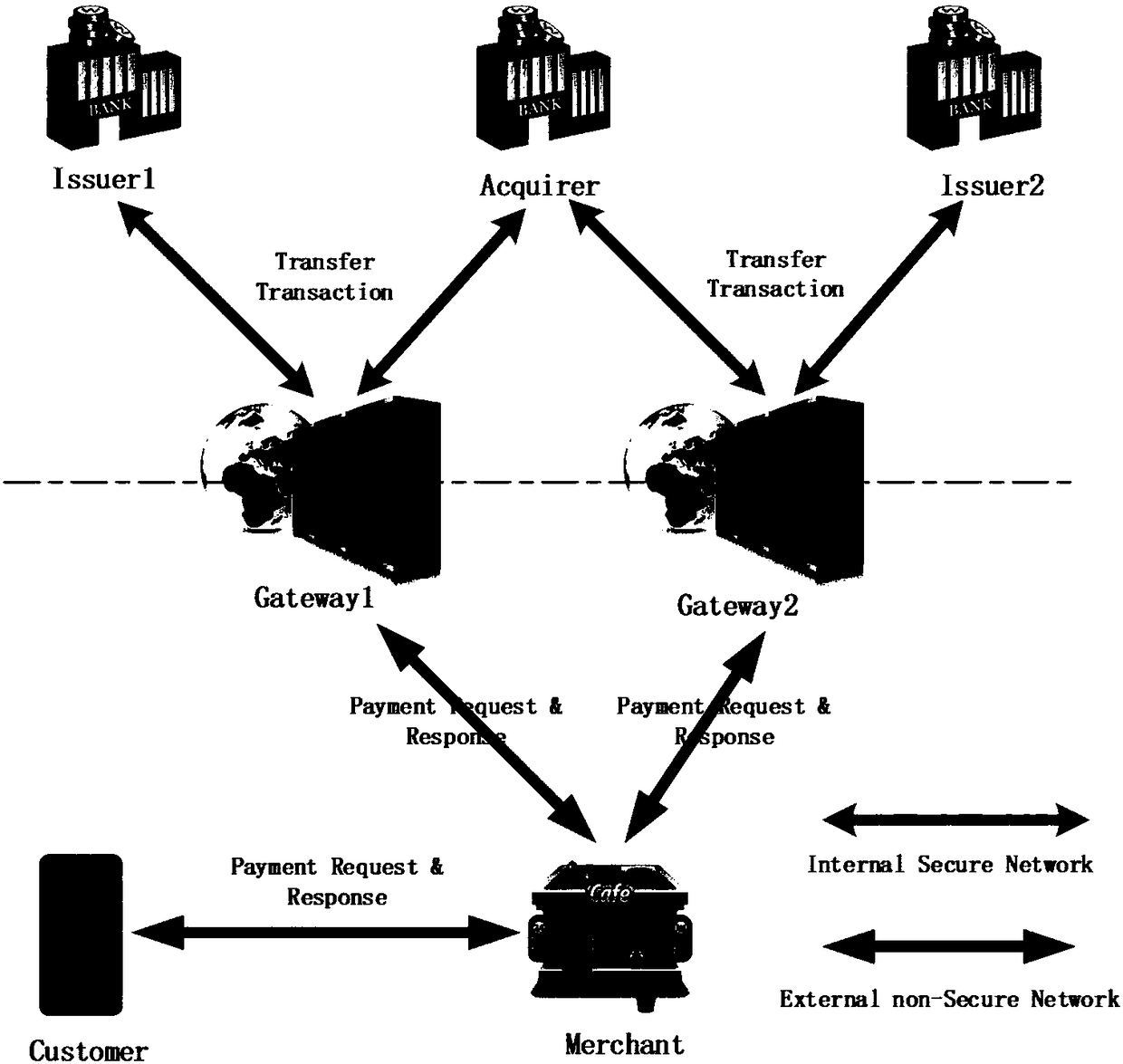
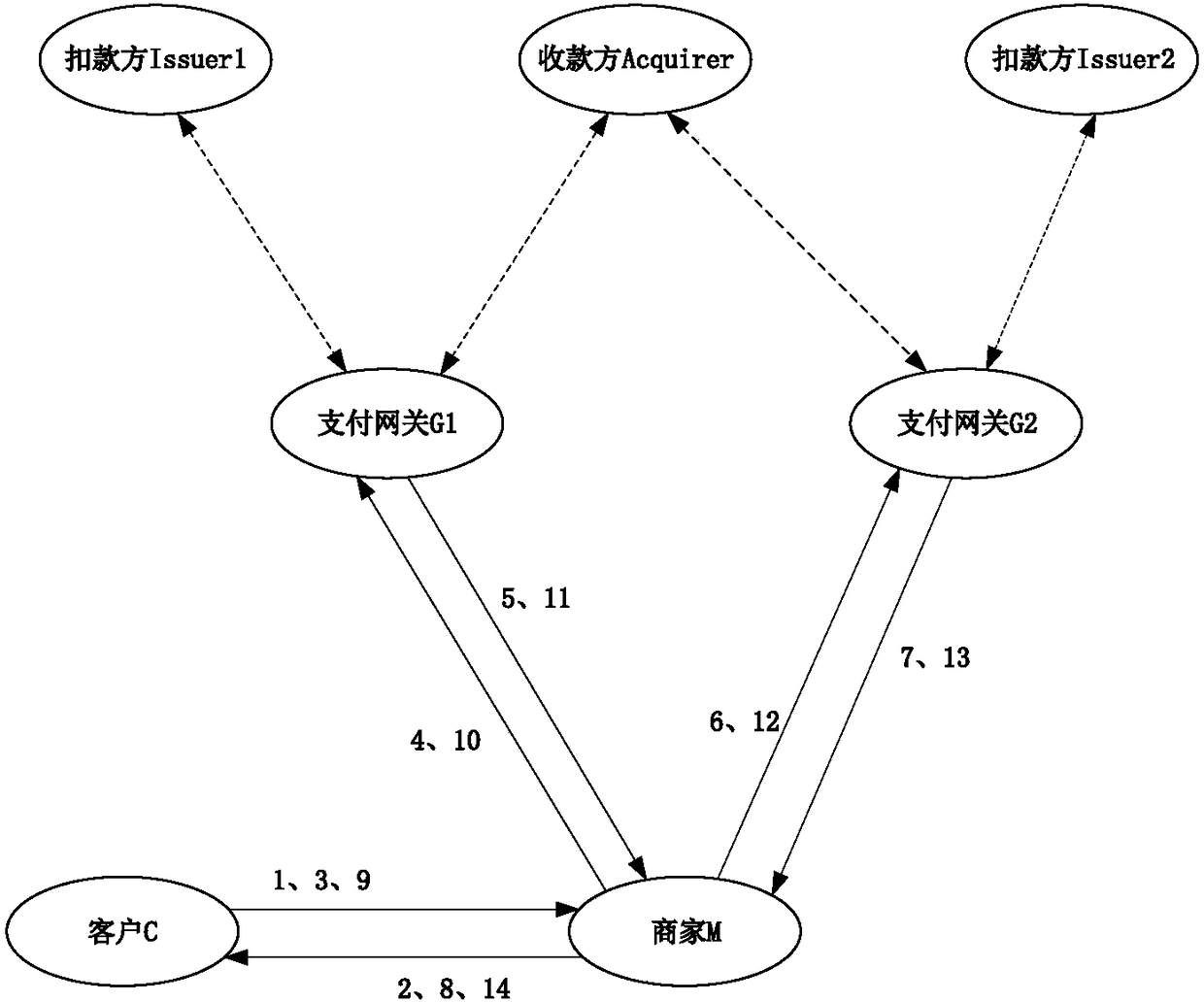
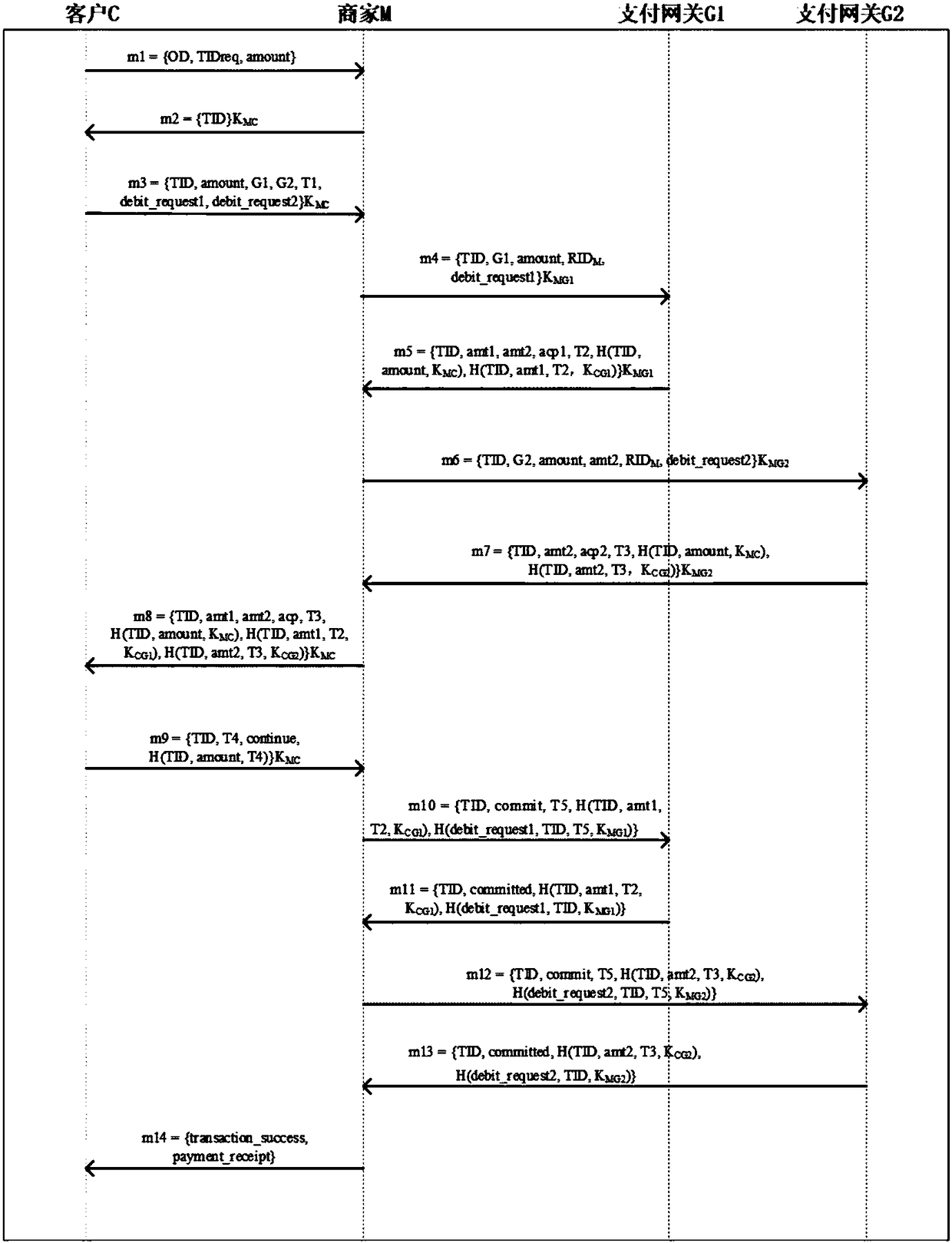
InactiveCN108449332AEnhanced anonymityReduce resource consumptionTransmissionProtocol authorisationProtocol designConfidentiality
The invention provides a dual gateway-based lightweight mobile payment protocol design method. According to a dual gateway-based secure payment protocol designed by the method, a user initiates a payment request, and a symmetric key system is used in a protocol process. The secure protocol provided by the invention meets a basic security requirement of the payment protocol, and comprises confidentiality, intactness, unforgeability and non-repudiation; meanwhile, in order to guarantee the privacies of the user and a merchant, the protocol is that the user and the merchant use dynamic IDs; and in each transaction process, a random pseudo ID is used, so that an anonymity of the user to the merchant and an anonymity of the merchant to an issuing bank of the user. The symmetric key system whichreduces the resource consumption of a mobile terminal in encrypting and decrypting processes is very light in weight and is applicable to a mobile payment system. In conclusion, the secure protocol provided by the invention provides all security attributes required by the mobile payment system, and is relatively high in execution efficiency.
Owner:SUN YAT SEN UNIV
Refractory brick surface scratch identification method based on frequency domain filtering enhancement
InactiveCN110288561AExtended service lifeAvoid Penetrating Corrosion PhenomenaImage enhancementImage analysisPattern recognitionColor image
Owner:SHANDONG IND TECH RES INST OF ZHEJIANG UNIV
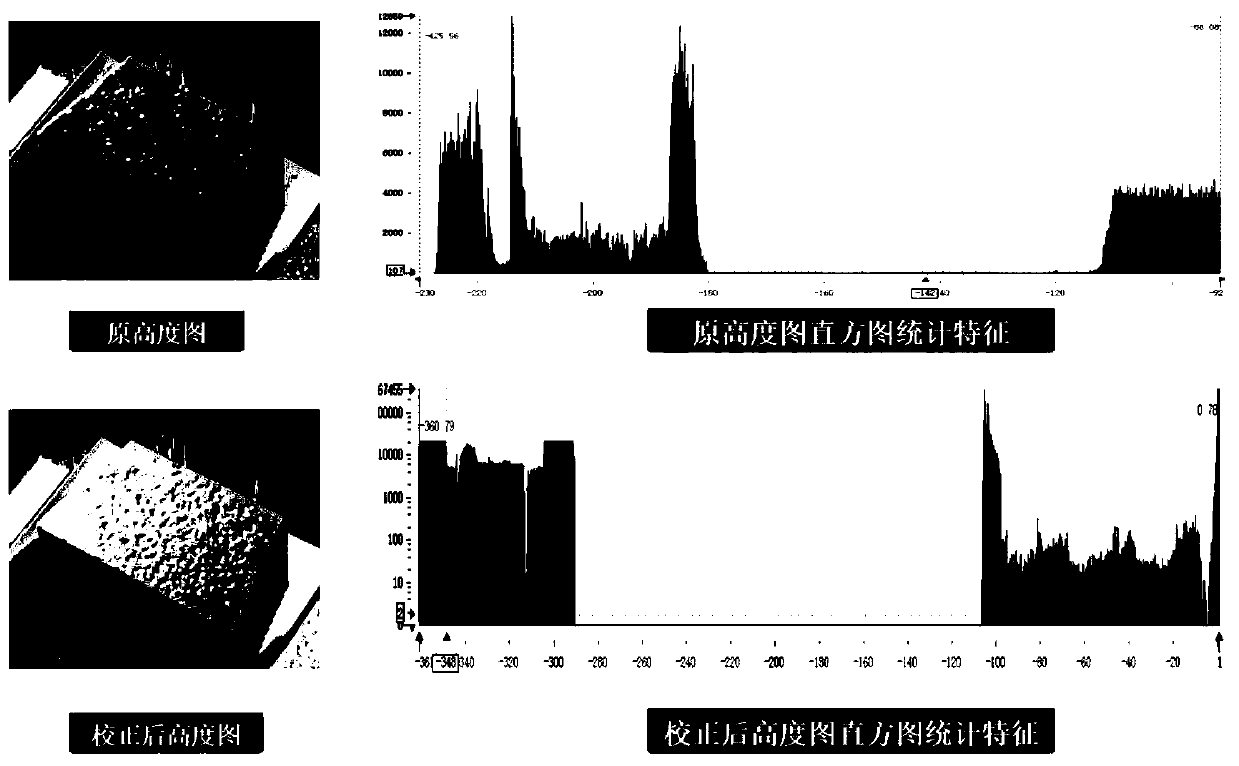
Refractory brick depth defect identification method based on height histogram segmentation
ActiveCN110223267AExtended service lifeAvoid Penetrating Corrosion PhenomenaImage enhancementImage analysisBrickHeight map
The invention discloses a refractory brick depth defect identification method based on height histogram segmentation. The method comprises the following steps: acquiring color point cloud data of refractory bricks by utilizing a structured light sensor, wherein the color point cloud data is formed by fusing image data and three-dimensional point cloud; carrying out plane fitting on the point cloudof the refractory brick image by using a least square method to obtain a zero plane; obtaining the height and width of the original refractory brick image; and according to the size parameters and the zero plane of the original refractory brick image, generating a corresponding reference plane image, subtracting the original refractory brick image from the reference plane image to obtain a pointcloud data graph after tilt correction, and carrying out filtering segmentation on a height histogram of the point cloud after tilt correction to obtain point cloud information with a set depth. The method can analyze the image height map on the basis of gray moment plane fitting to obtain the depth defect information of the refractory bricks, effectively avoids the permeation corrosion phenomenon, and prolongs the service life of the refractory bricks.
Owner:SHANDONG IND TECH RES INST OF ZHEJIANG UNIV
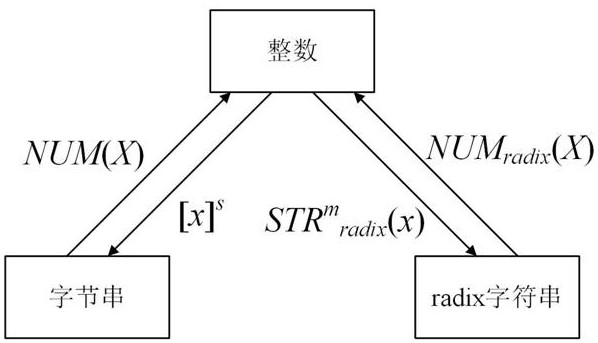
Format-preserving encryption method and decryption method based on message authentication code algorithm
ActiveCN112994874AOptimize execution efficiencyEnough securityEncryption apparatus with shift registers/memoriesAlgorithmTheoretical computer science
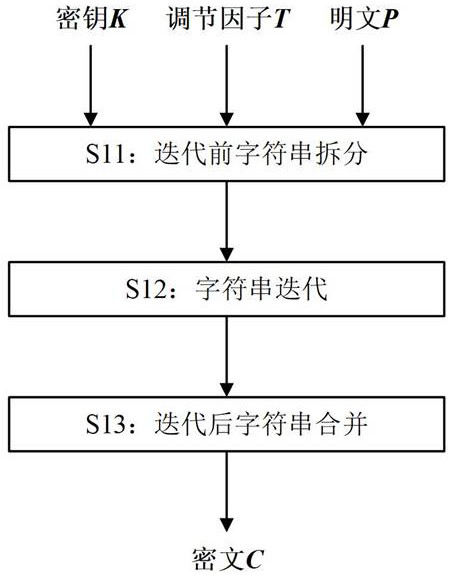
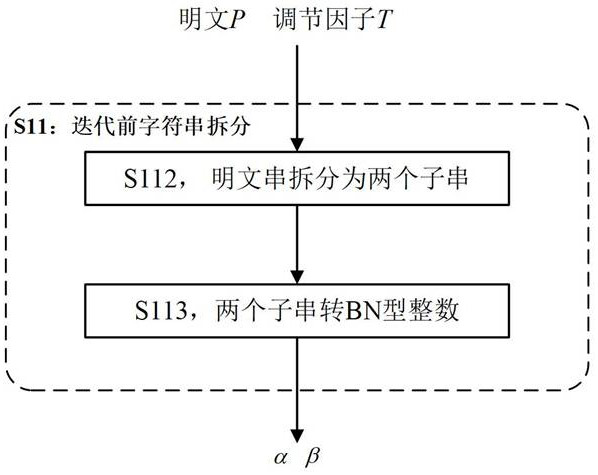
The invention provides a format-preserving encryption method and decryption method based on a message authentication code algorithm. The encryption method comprises the following steps: S11, character string splitting: splitting an input plaintext P to be encrypted into two sub-character strings, and respectively converting the two sub-character strings into BN type integers; s12, performing character string iteration: setting an iteration index number i to be equal to 0, 1, 2,..., 7, and performing eight rounds of iteration based on a Feistel structure and PRF conversion on the two BN type integers obtained in the step S11, wherein the PRF conversion is a pseudo-random digital node generation function based on a message authentication code algorithm HMAC-SM3; and S13, character string merging: respectively converting the two BN type integers obtained through iteration into character strings, then connecting the character strings in series and merging them into one character string, and obtaining a ciphertext C. The encryption method provided by the invention meets the requirements of localization and security and is relatively high in execution efficiency.
Owner:工业信息安全(四川)创新中心有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com