Format-preserving encryption method and decryption method based on message authentication code algorithm
A technology of format-preserving encryption and message authentication code, which is applied in the field of information security, can solve the problems of slow execution efficiency of FPE algorithm, decreased execution efficiency, and difficult implementation of FPE algorithm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
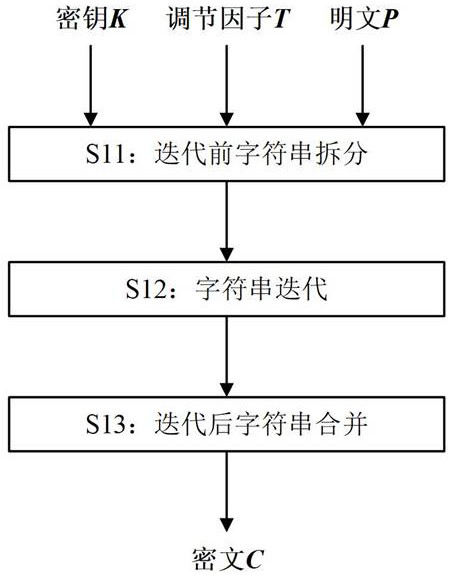
[0152] Such as figure 2 As shown, the present embodiment proposes a format-preserving encryption method based on the message authentication code algorithm, and the encryption method is expressed as GMFPE - Enc ( K , T , P ), including the following steps:
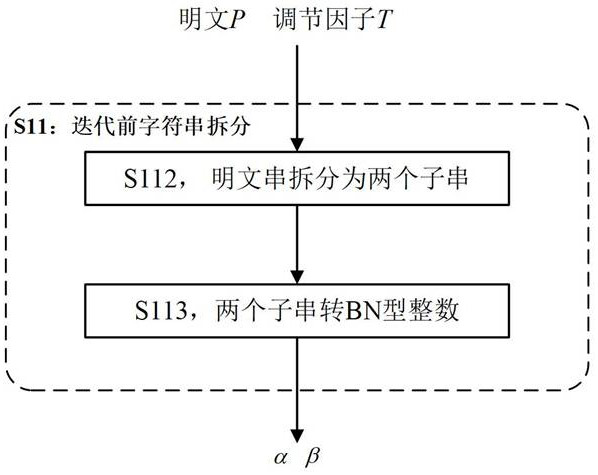
[0153] S11, such as image 3 As shown, string splitting: the input plaintext to be encrypted P Split into two substrings and convert them to BN-type integers:
[0154] specifically:
[0155] S111, input:
[0156] key K , the key in this example K Be a byte string of not less than 16 bytes;
[0157] An adjustment factor of length 7 bytes T ;
[0158] and the plaintext to be encrypted P ; The plaintext to be encrypted P is the length of n The character string; in this example, n satisfy , radix Satisfy 2≤ radix ≤65536;
[0159] S112, take INT type integer respectively , v ← n - u , the symbol ← stands for assignment, that is, assigned to u , n - u assigned to v ; the plaintext string P spl...
Embodiment 2
[0224] This embodiment provides a format-retaining decryption method based on a message authentication code algorithm, and the decryption method is used for the ciphertext obtained by the encryption method described in Embodiment 1 C Decryption, that is, the inverse operation of the encryption method of embodiment 1; as Figure 6 As shown, remember that the encryption method is expressed as GMFPE - December ( K , T , P ), including the following steps:
[0225] S21, string splitting: the input ciphertext to be decrypted P Split into two substrings and convert them into BN-type integers;
[0226] specifically:
[0227] S211, enter the key K , an adjustment factor of length 7 bytes T , and the ciphertext to be decrypted C ; The plaintext to be encrypted C is the length of n String, n satisfy , radix Satisfy 2≤ radix ≤65536; K , T Consistent with embodiment 1;
[0228] S212, take INT type integer respectively , v ← n - u , the symbol ← stands for assign...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com