Authentication system based on biological characteristics and identification authentication method thereof
A biometric and biometric authentication technology, applied in the field of security authentication systems, can solve problems such as personal privacy troubles, biometric authentication server downtime, and biometric authentication server idle
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
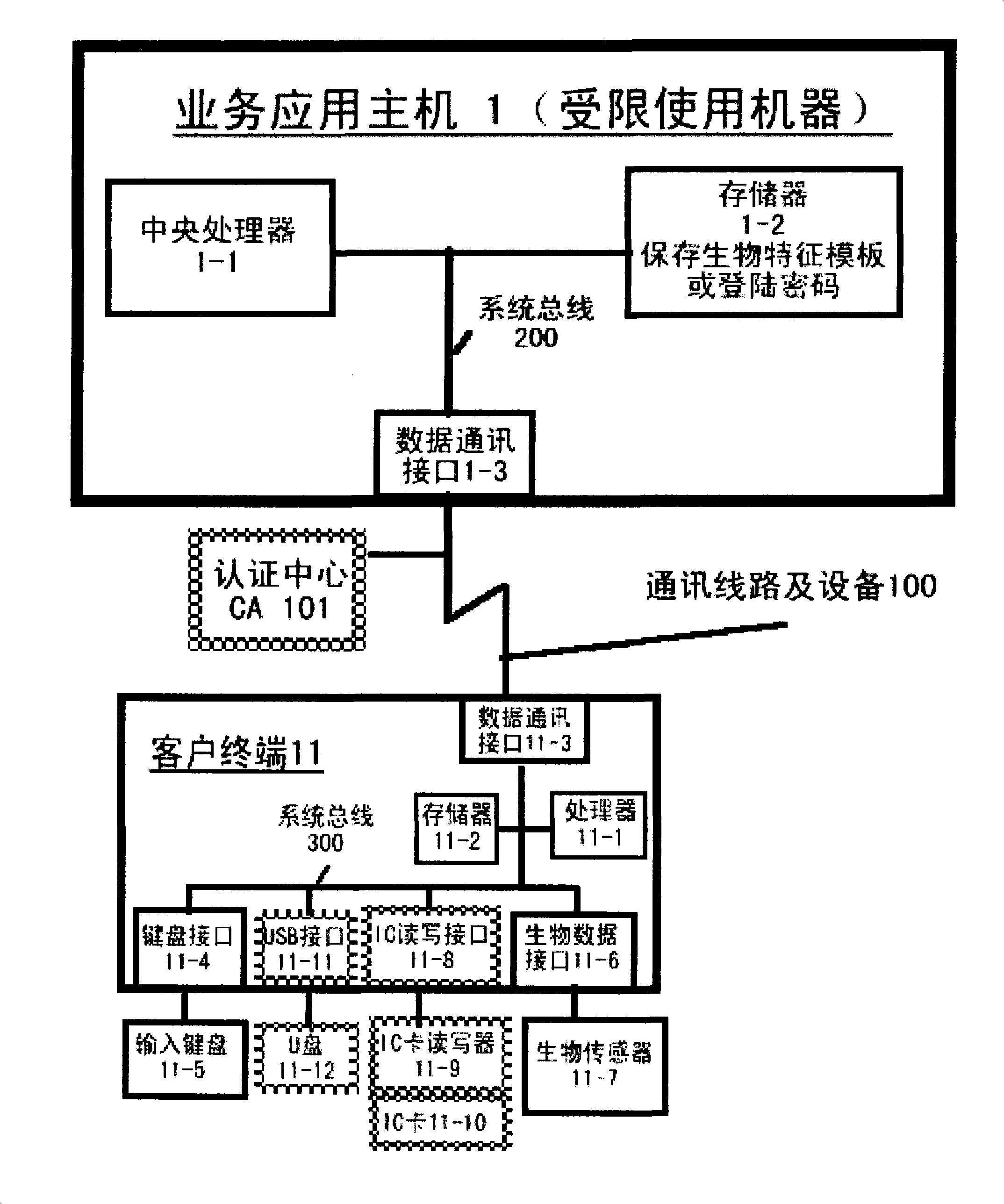
[0115] combine figure 2 A biometric authentication system illustrating one embodiment of the invention:
[0116] The user uses the biometric authentication system based on the palmprint biosensor 11-7 and the keyboard alphanumeric input device 11-5 held in the personal computer terminal 11; the biometric authentication system includes,
[0117] (1) A limited-use machine with a domain name URL (for example, www.EMBbiz.net) based on palmprint biometrics, i.e. an e-commerce server 1, at least with a memory 1-2, an authentication module 1-4 and an encryption / decryption module 1-7; where,
[0118] Memory 1-2, used to store the ID identification number of each user, and the mobile phone number of the smart phone 2 that is bound to each user ID identification number one-to-one, for example, Table 1 represents www.EMBbiz.net Detailed data stored on the memory of the e-commerce server 1;
[0119] ID number for each user
The mobile phone number of the smart phone 2 ...
Embodiment 2
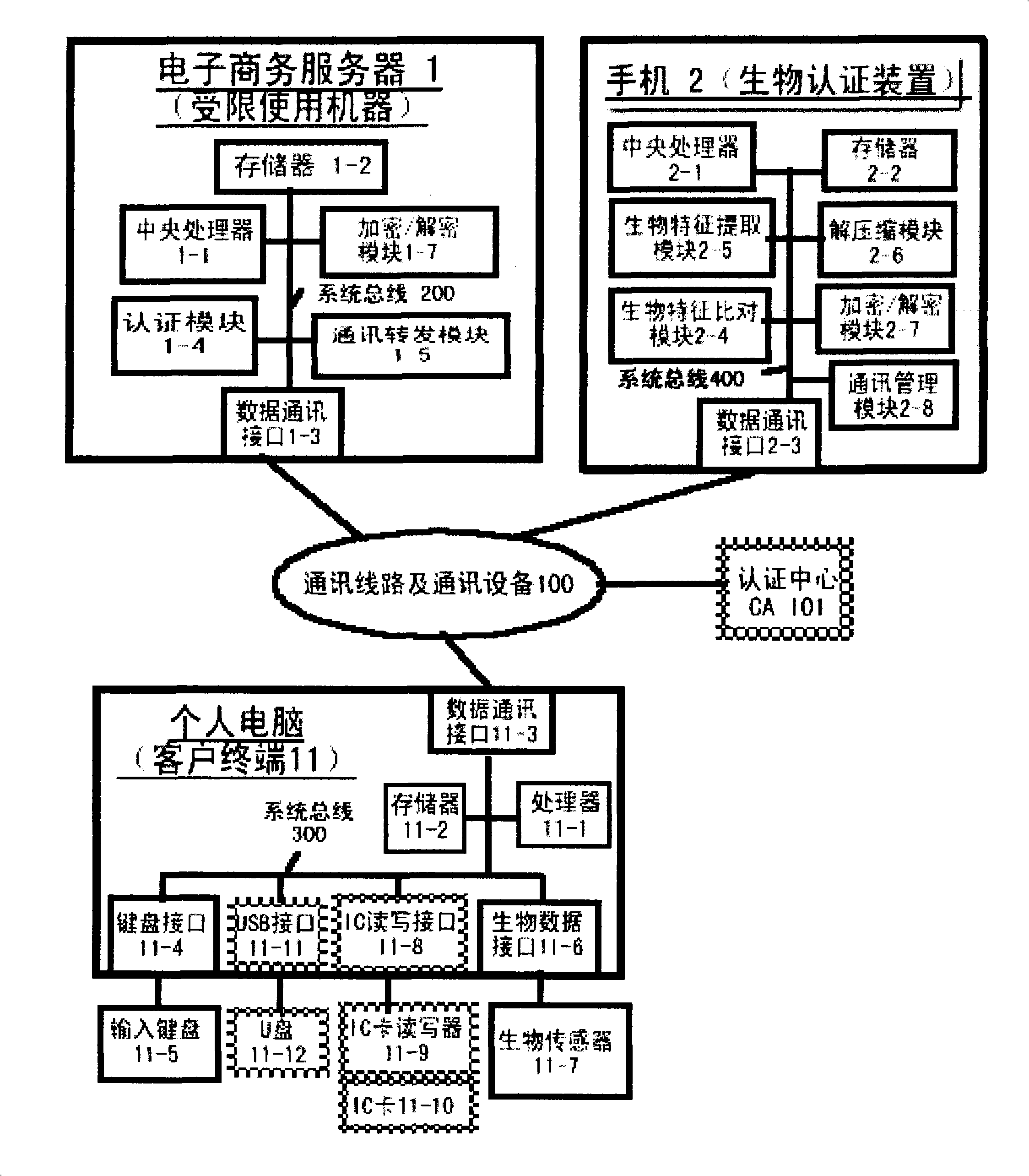
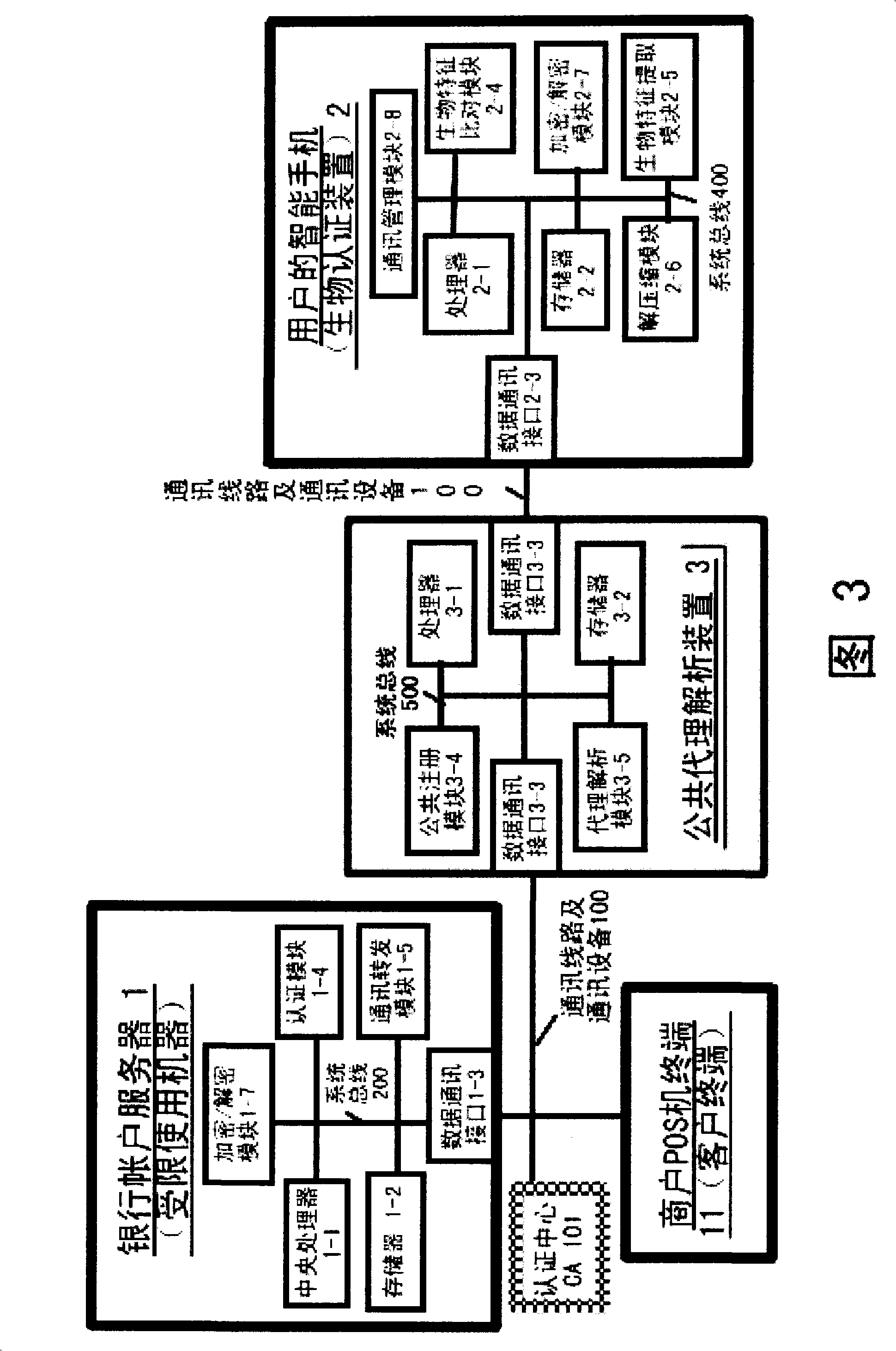
[0153] The biometric authentication system of another embodiment of the present invention is illustrated below in conjunction with Fig. 3:
[0154] The user uses the biometric authentication system based on the fingerprint sensor held by the POS machine terminal 11 of the merchant, the bank card reader, and the keyboard input device; it includes,
[0155] (1) Banks with domain name URLs (such as www.chinaunionpay.com) based on fingerprint characteristics
[0156] account server 1,
[0157] (2) Smartphone 2 and
[0158] (3) public proxy analysis device 3,
[0159] in,
[0160] (1) A bank account server (that is, a limited-use machine) 1 with a domain name URL based on fingerprint features, with a memory 1-2, an authentication module 1-4, a communication forwarding module 1-5, and an encryption / decryption module 1-7 ;in,
[0161] The memory 1-2 is used to pre-store the card number of each bank card of the user, and the mobile phone number of the smart phone 2 that is bound ...
Embodiment 3
[0198] An embodiment of the biometric authentication method of the present invention is described in conjunction with the steps in FIG. 4 .
[0199] (401a) From the frontier inspection client terminal computer 11 of the border inspection and law enforcement department equipped with iris sensors and keyboards, the foreign entry personnel to be authenticated input their visa numbers and collect the iris biometric data to be authenticated, and perform detailed feature points after preprocessing Extract, obtain the effective representation data of the iris biometric feature, send it to the visa server 1 with a fixed IP address (limited use machine) through the communication line or with the device 100, request authentication to log in to the visa server 1 with the fixed IP address or use its resources for specific authentication, such as records showing the visa information of the immigrant,
[0200] The above communication data are encrypted / digitally signed or decrypted / verified...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com