A wireless security authentication method based on block chain technology
A wireless security and authentication method technology, applied in the field of information security, can solve the problems of large amount of Hash calculation, inability to resist replay attacks, and inability to resist internal attacks, etc., to achieve the effect of reducing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
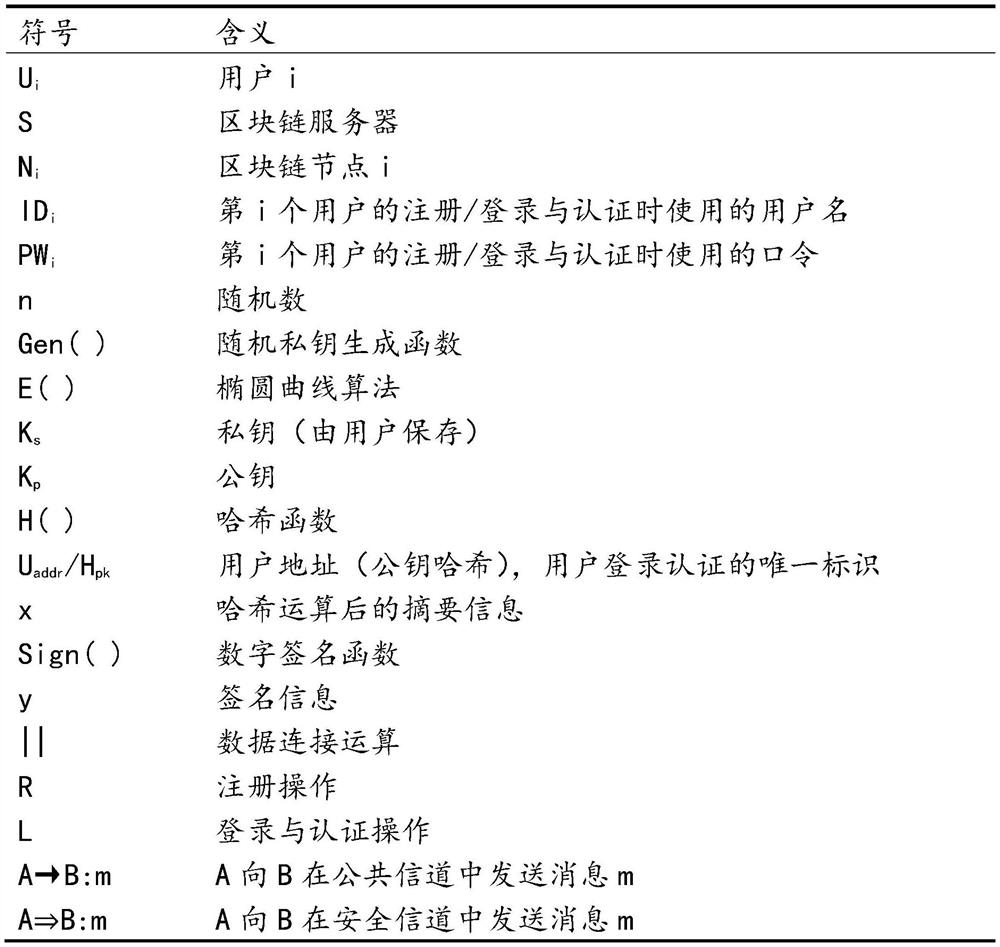
[0029] Table 1 Scheme symbol meaning
[0030]
[0031] The present invention will be described in further detail below in conjunction with the accompanying drawings.
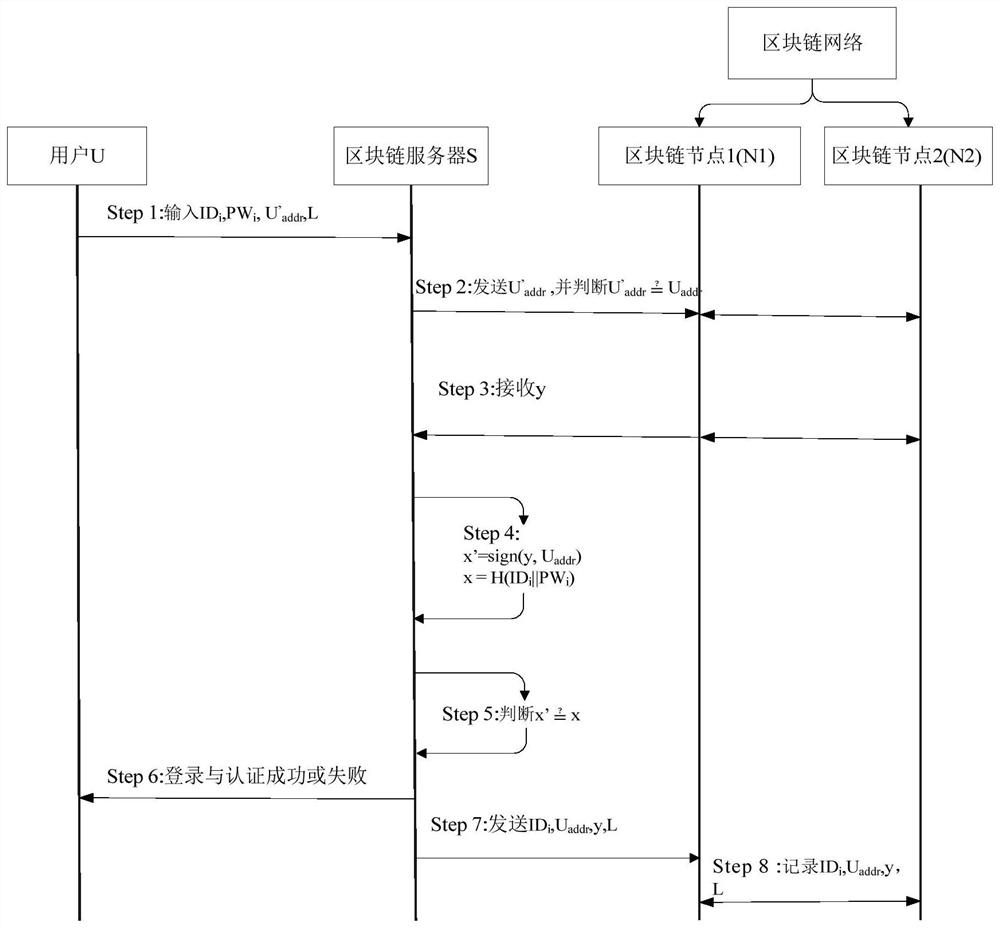
[0032] A wireless security authentication method based on blockchain technology, including a registration stage and a login authentication stage.
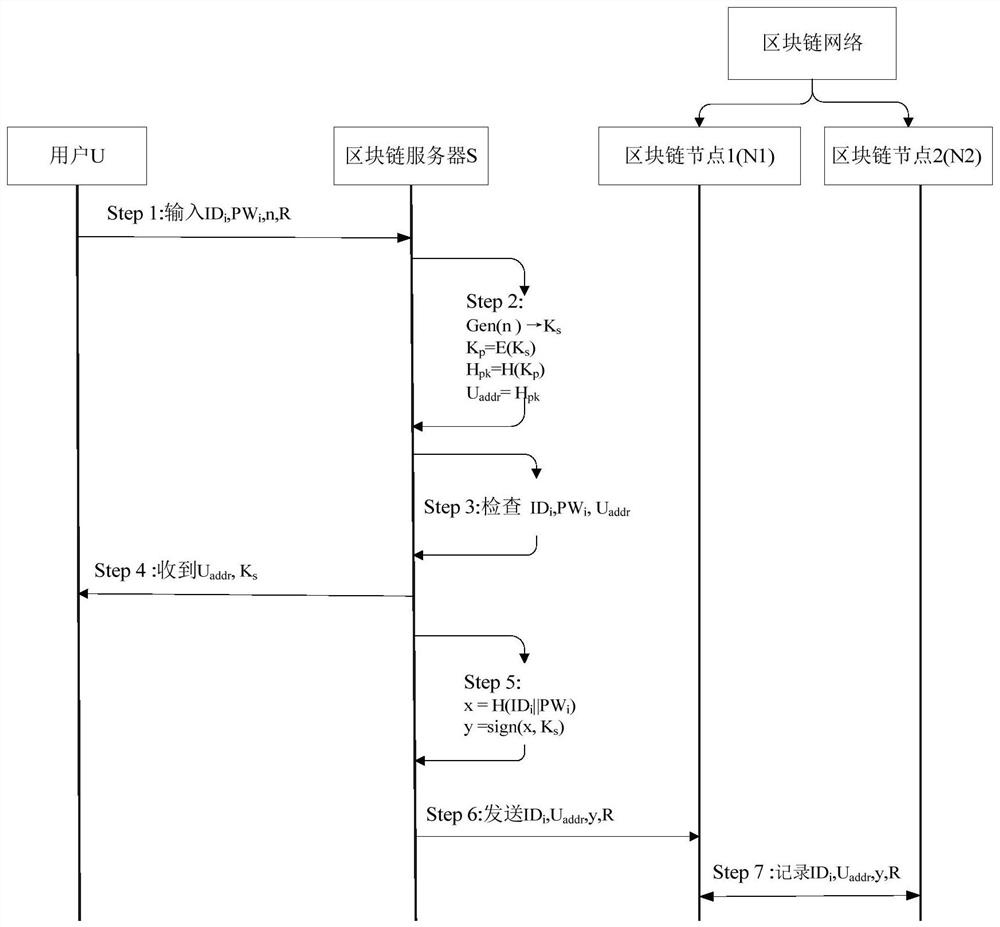
[0033] Such as figure 1 As shown, the specific steps of the user in the registration phase are as follows:
[0034] Step1: User U i Enter your username ID i , password PW iThe registration operation R is performed with the random number n (when the user performs the registration operation, the random number is automatically assigned), and is transmitted to the blockchain server S through a secure channel.
[0035]
[0036] Step2: The blockchain server S receives the information sent by the user, uses the random private key generation function Gen() to process the input random number, and generates the private key K s , use the private key to generate the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com