Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
187 results about "Behavioral modeling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The behavioral approach to systems theory and control theory was initiated in the late-1970s by J. C. Willems as a result of resolving inconsistencies present in classical approaches based on state-space, transfer function, and convolution representations. This approach is also motivated by the aim of obtaining a general framework for system analysis and control that respects the underlying physics.
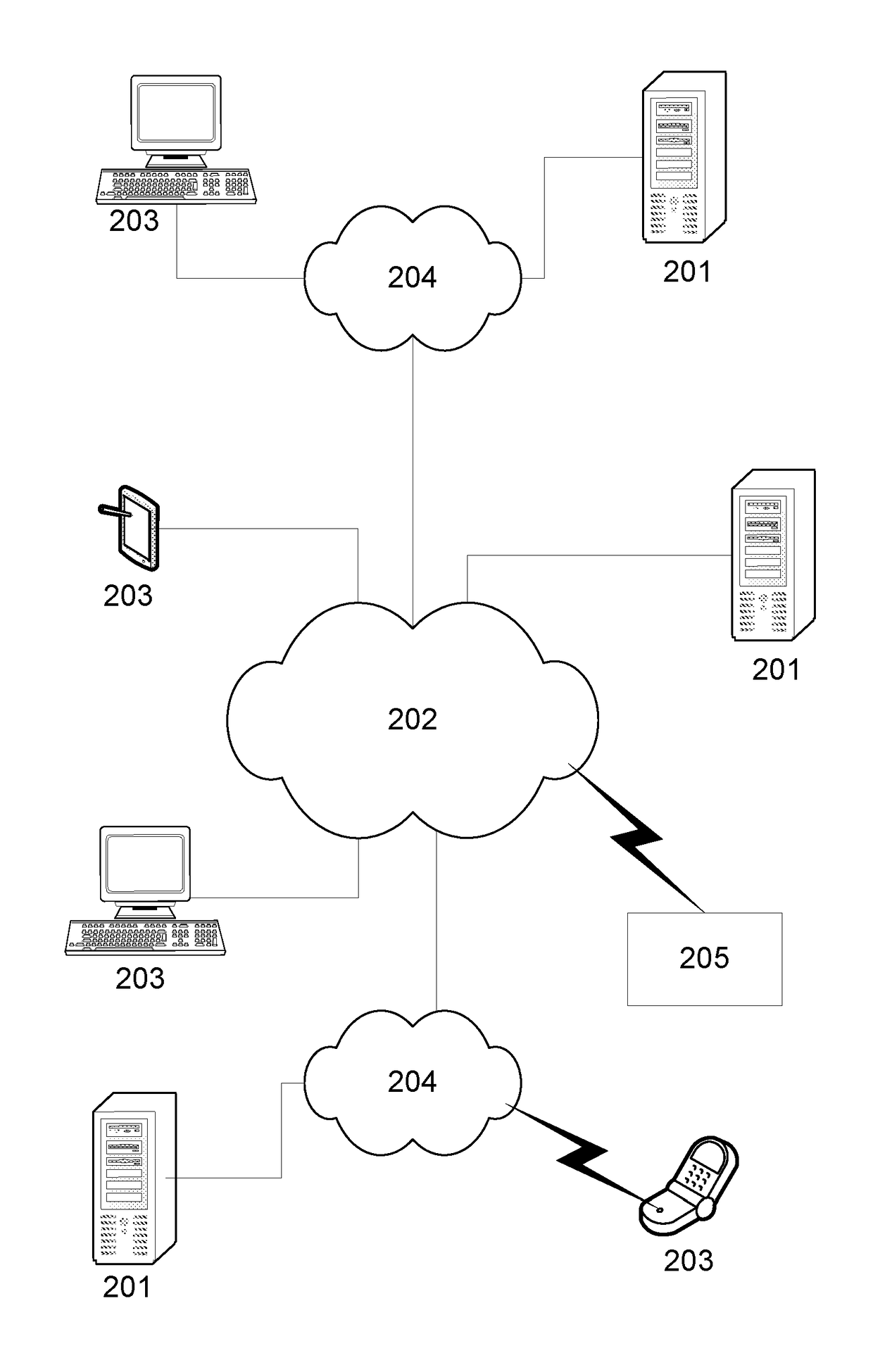
A System and Method for Modelling System Behaviour
ActiveUS20170147722A1Reduce the impactReduce impactMedical simulationDesign optimisation/simulationCollective modelModel system
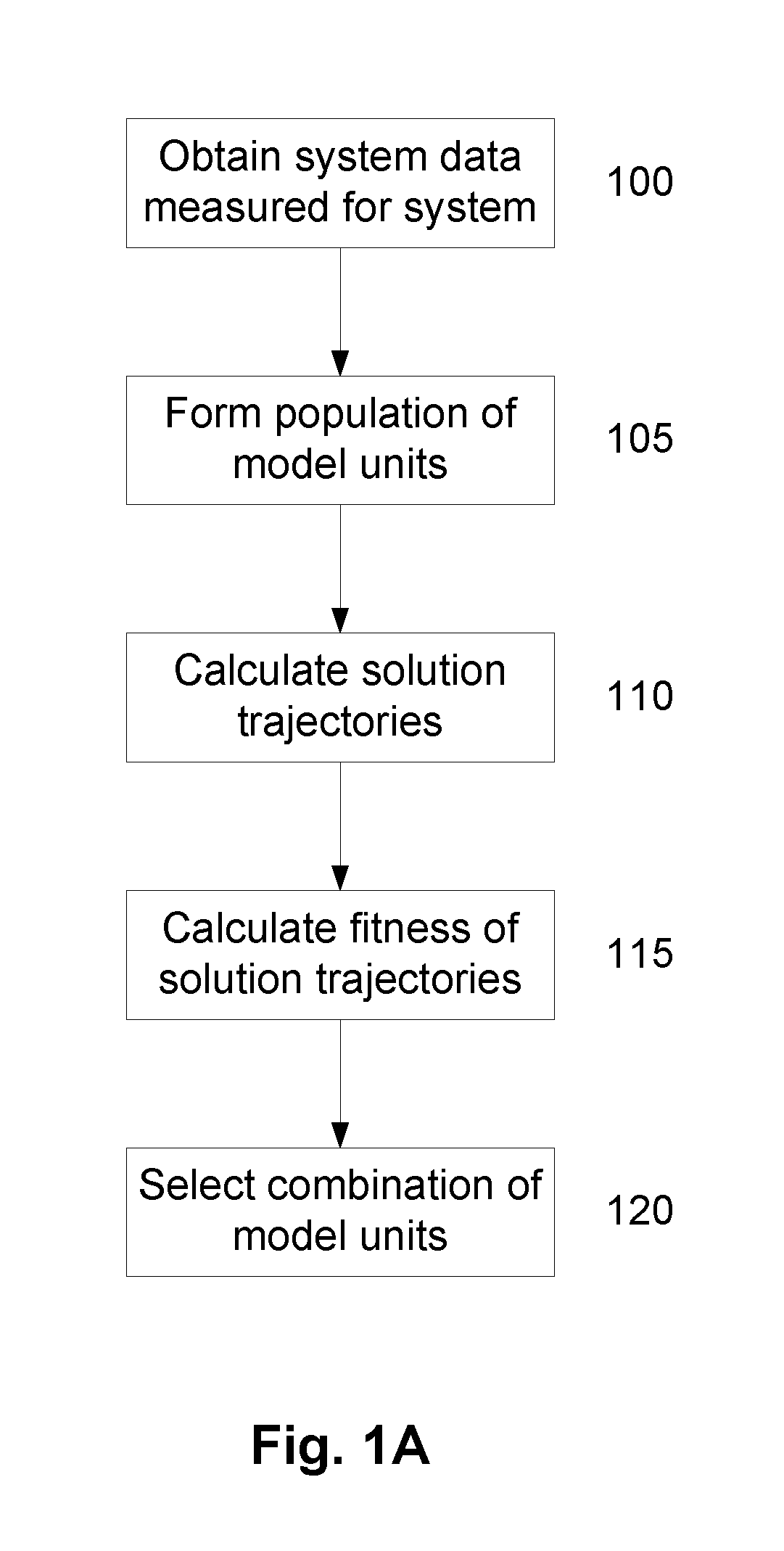
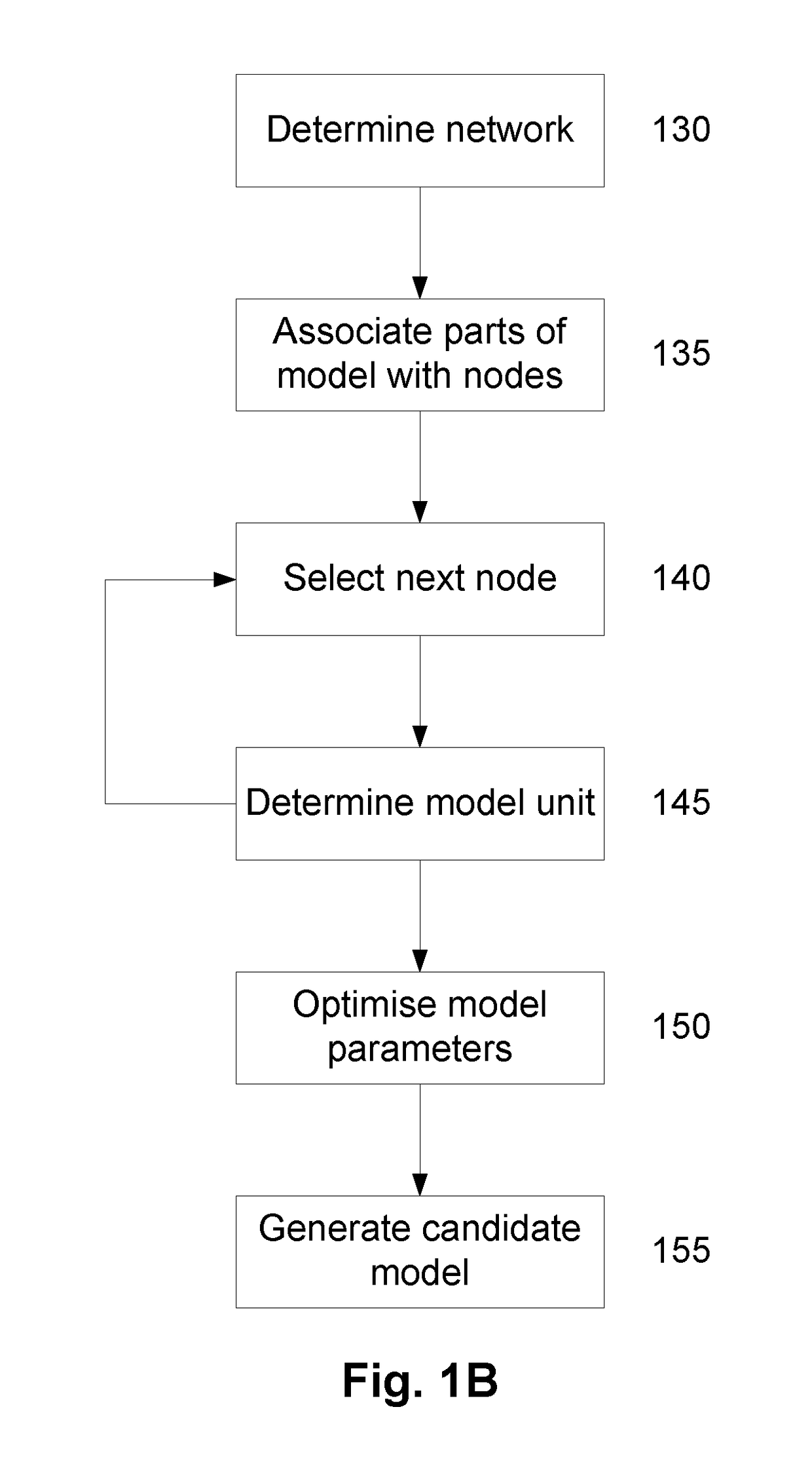
A method of modelling system behaviour of a physical system, the method including, in one or more electronic processing devices obtaining quantified system data measured for the physical system, the quantified system data being at least partially indicative of the system behaviour for at least a time period, forming at least one population of model units, each model unit including model parameters and at least part of a model, the model parameters being at least partially based on the quantified system data, each model including one or more mathematical equations for modelling system behaviour, for each model unit calculating at least one solution trajectory for at least part of the at least one time period; determining a fitness value based at least in part on the at least one solution trajectory; and, selecting a combination of model units using the fitness values of each model unit, the combination of model units representing a collective model that models the system behaviour.
Owner:EVOLVING MACHINE INTELLIGENCE
Circuit and method for modeling I/O
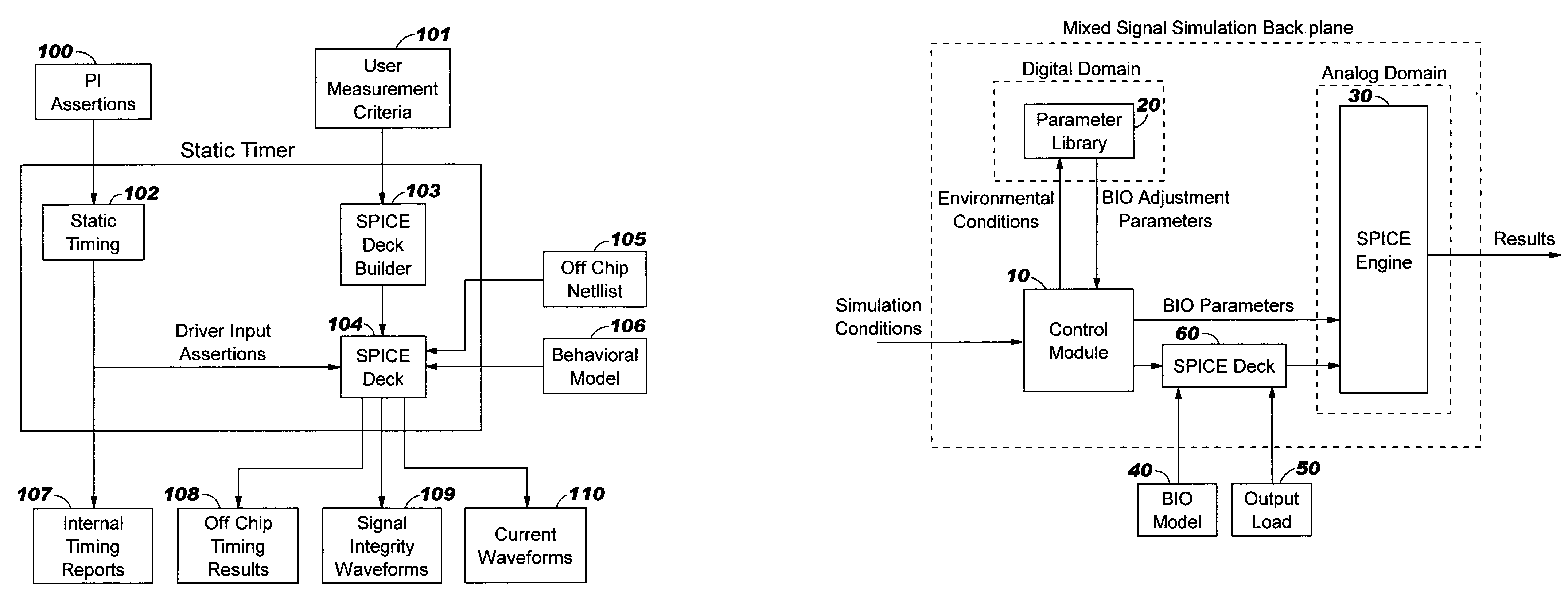
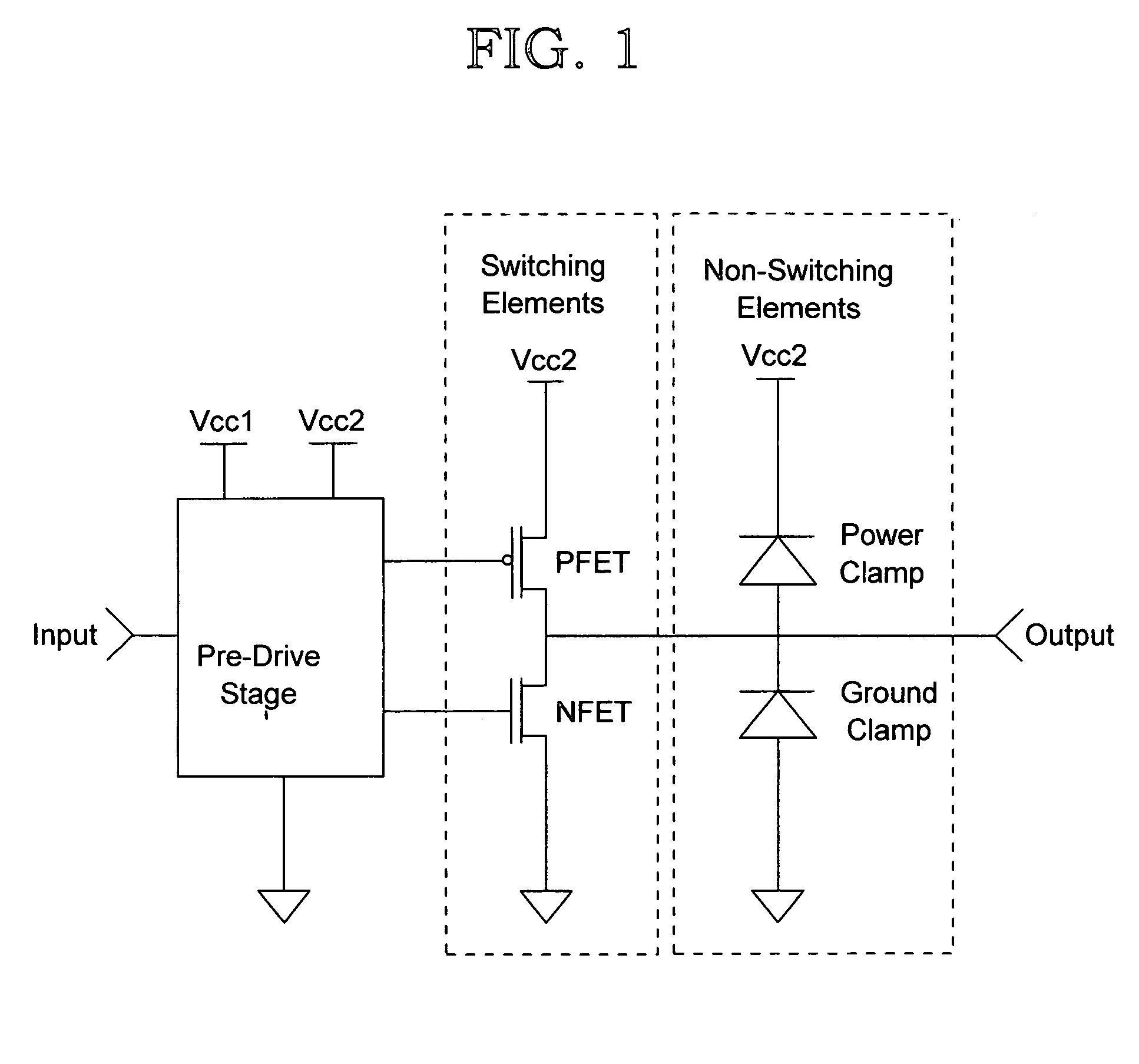
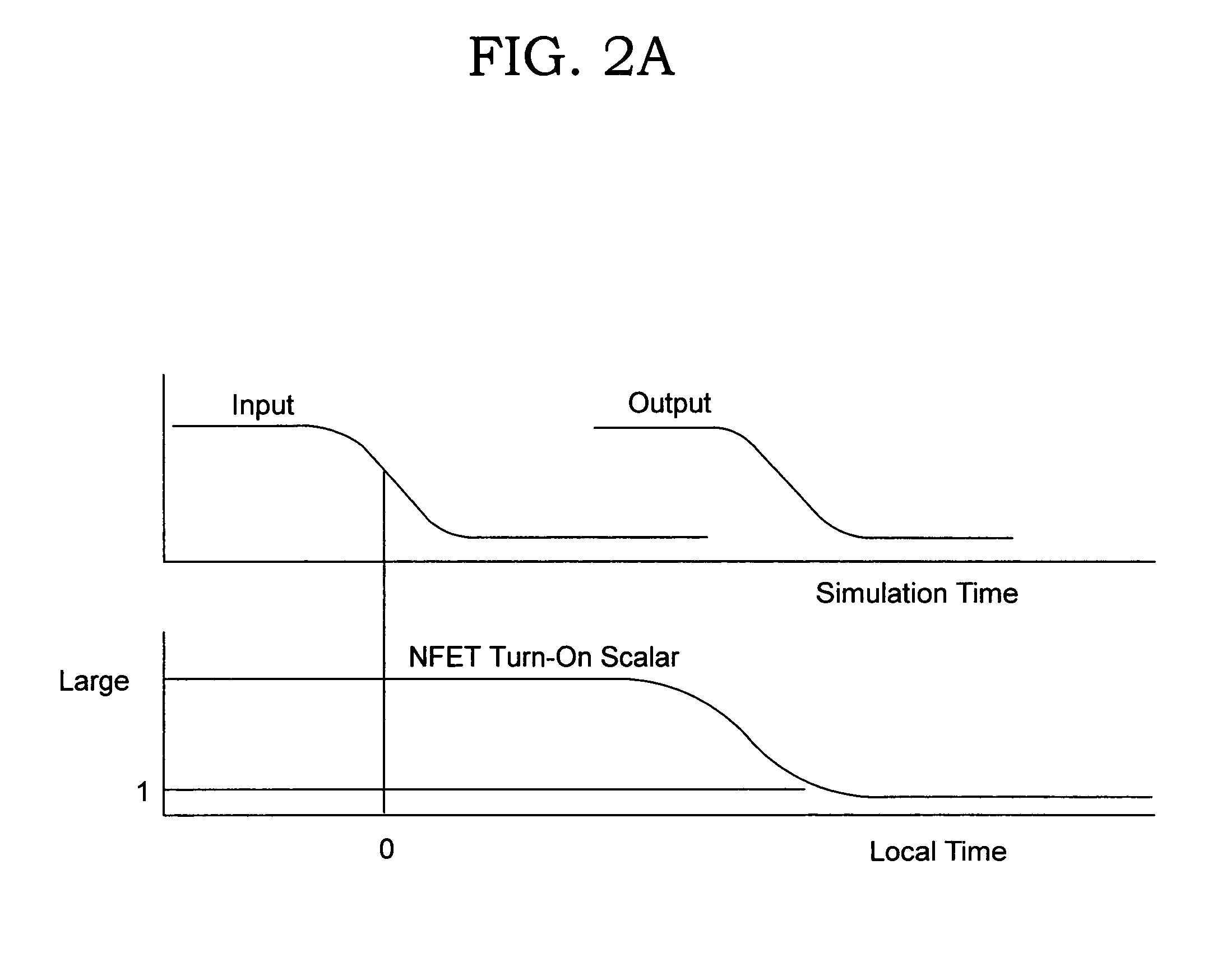
InactiveUS6983432B2Reduction in size of cross sectionReadily availableComputation using non-denominational number representationComputer aided designBehavioral modelingTime control
A behavioral modeling technique that captures driver delay. The output characteristics of a typical driver are represented by two basic element types: switching and non-switching. Switching elements are functions of both time-varying and non-time-varying parameters, and non-switching elements are functions of non-time-varying parameters only. The outputs of these elements are characterized and tabulated by applying a DC voltage on the output of the driver and measuring the current through each element. The time-varying switching element are represent by time-controlled resistors. The invention provides a methodology to account for variations in input transition rate, supply voltage(s) or temperature.
Owner:IBM CORP
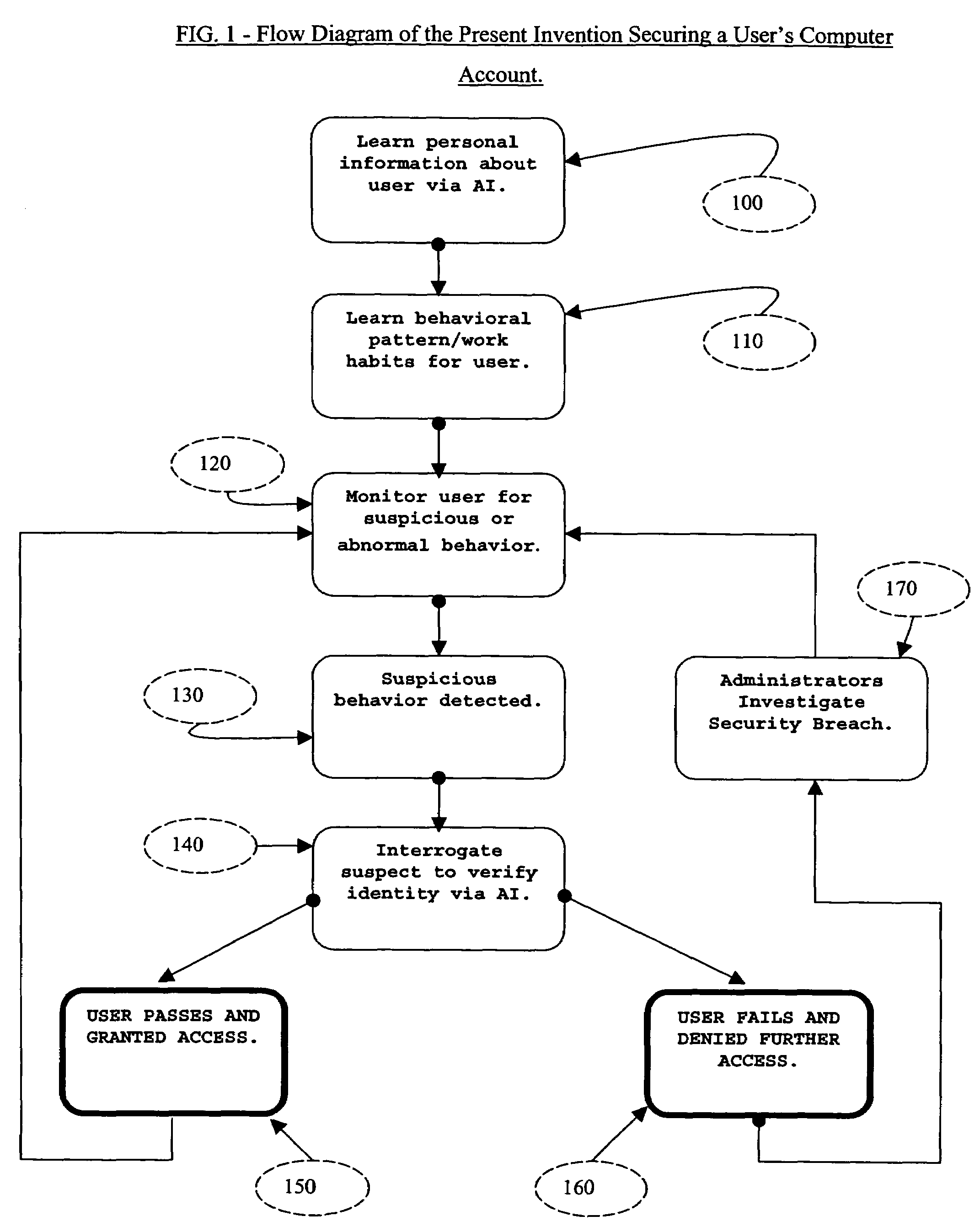
System and method for securing computer system against unauthorized access
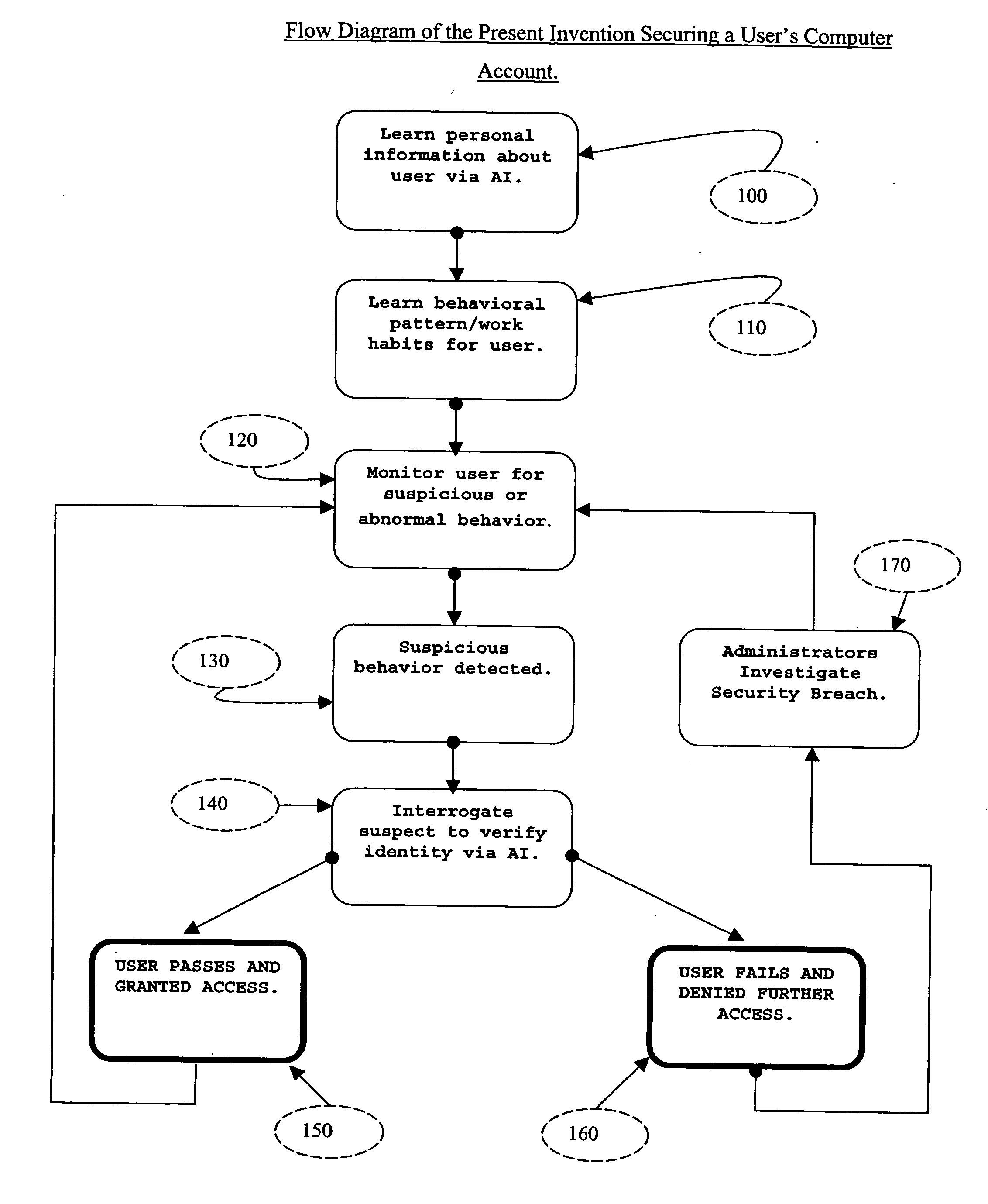
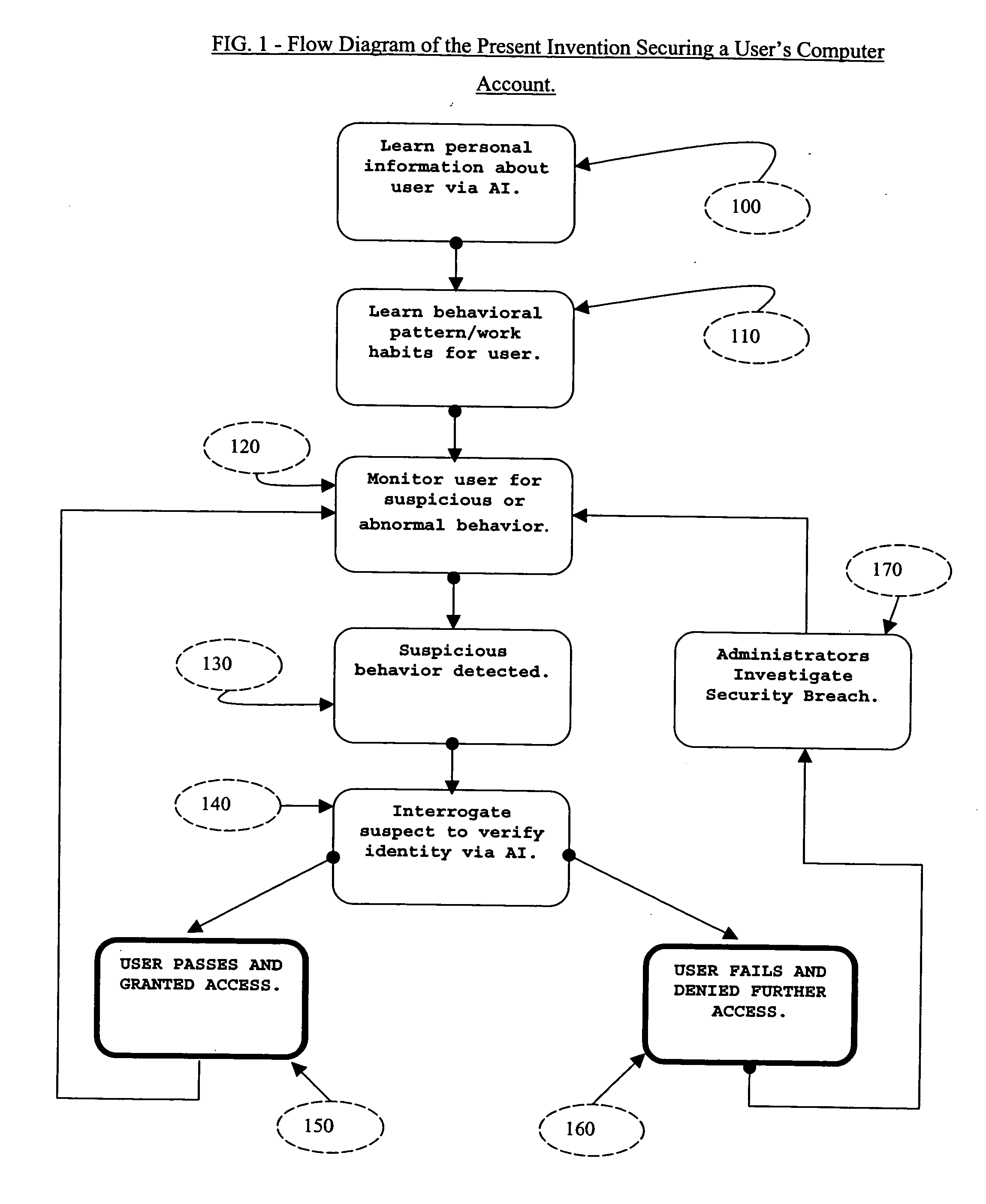
ActiveUS20050097364A1Defeat computer security breachSecurity breachMemory loss protectionDigital data processing detailsComputer usersIdentity theft
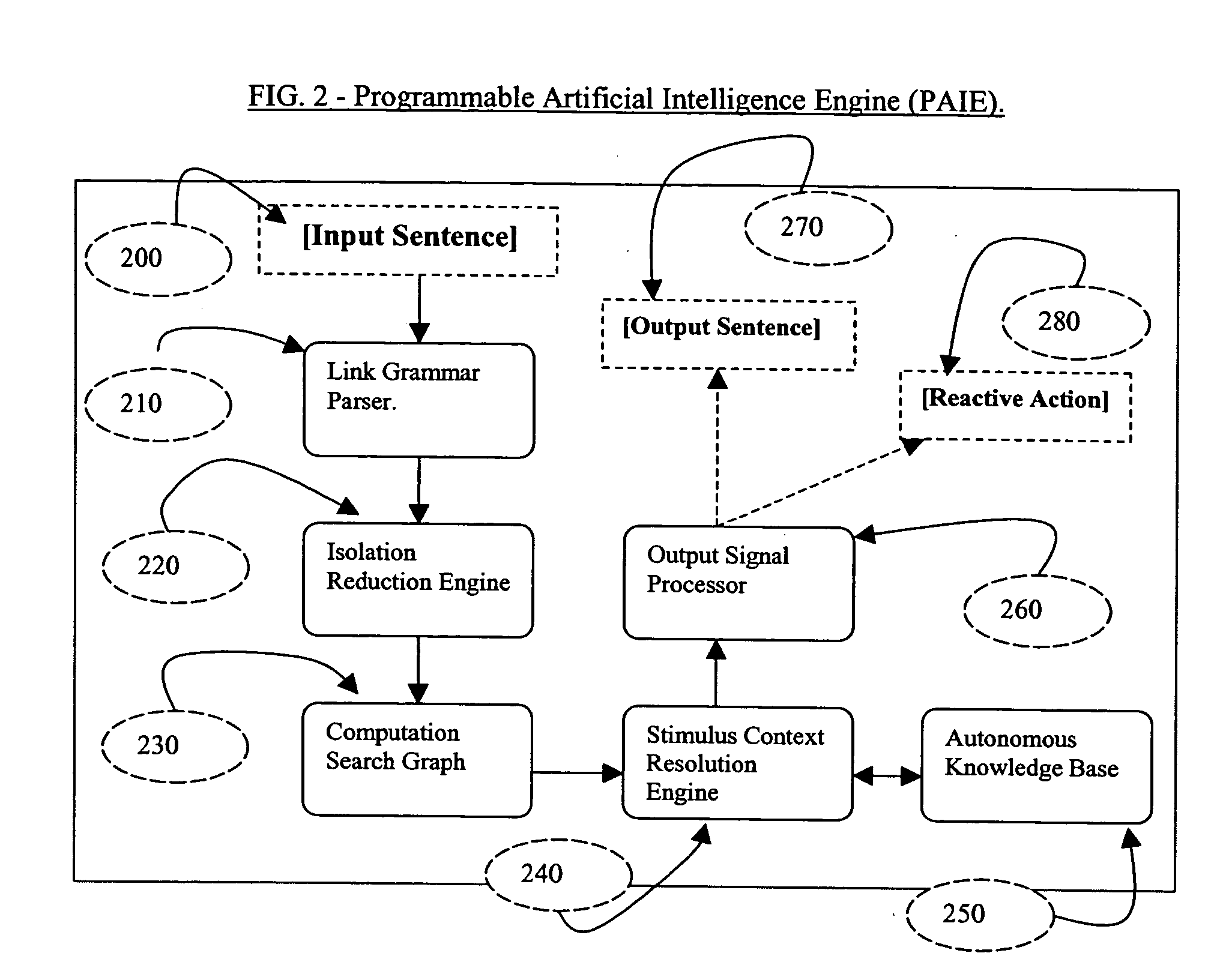
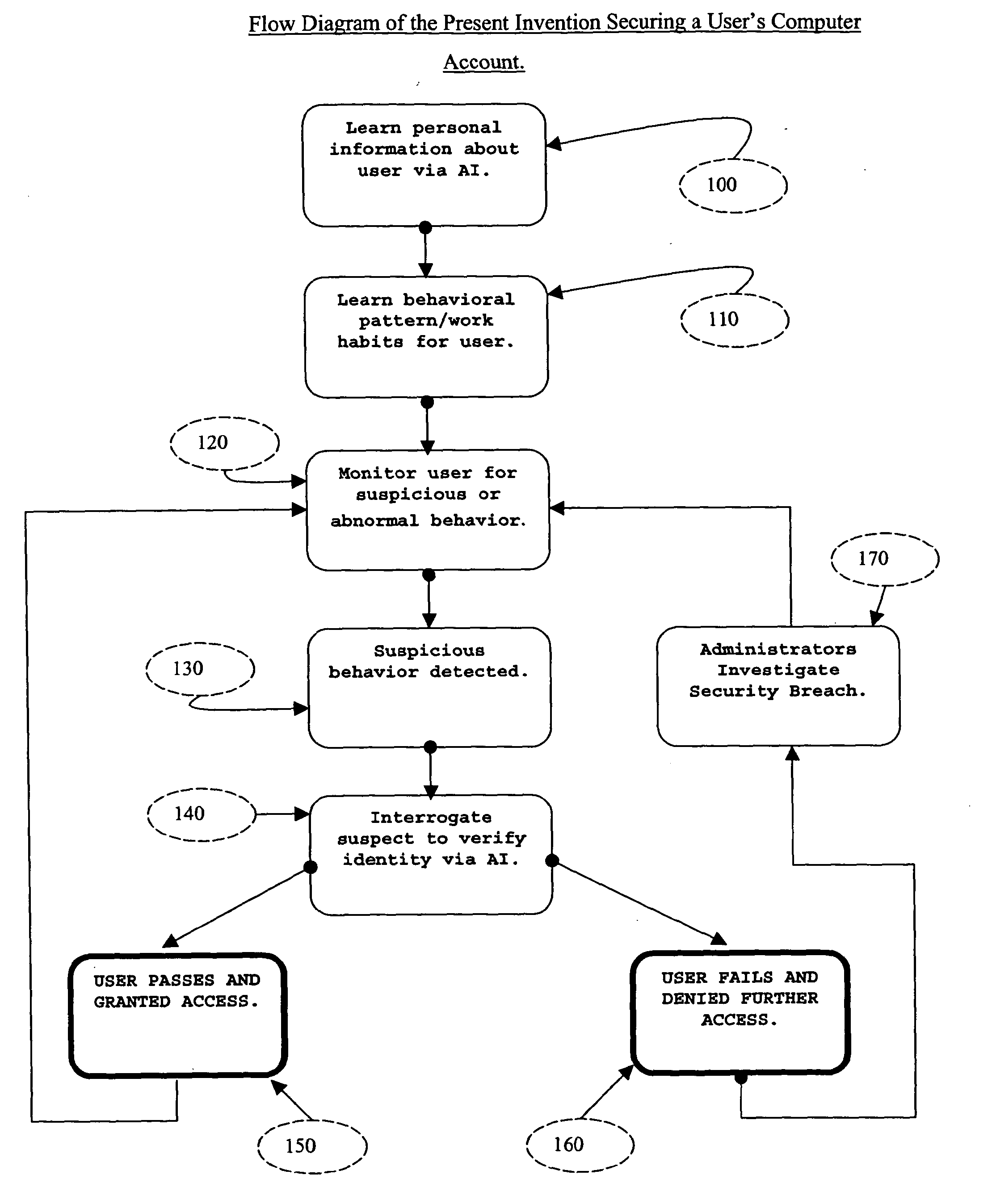
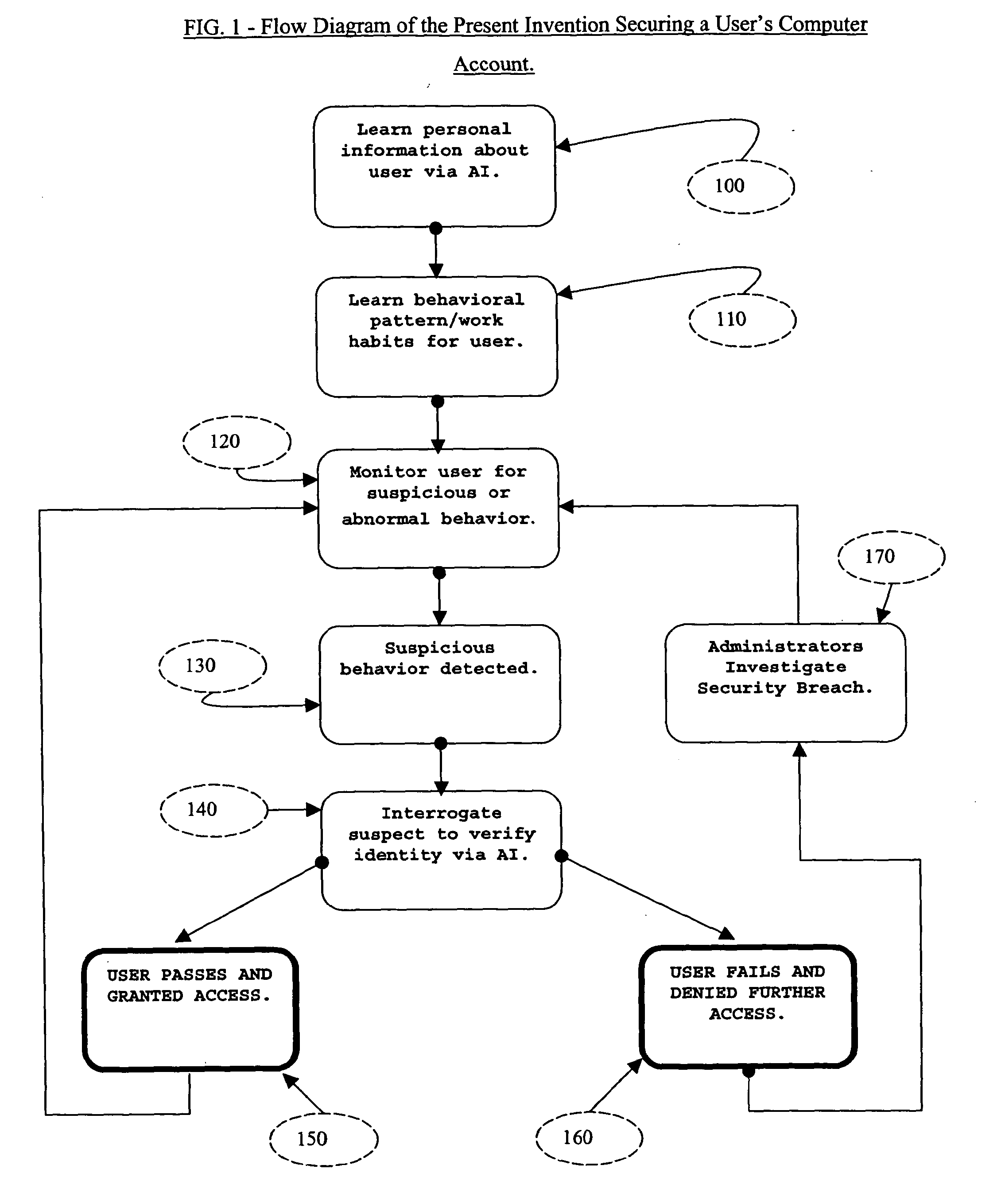
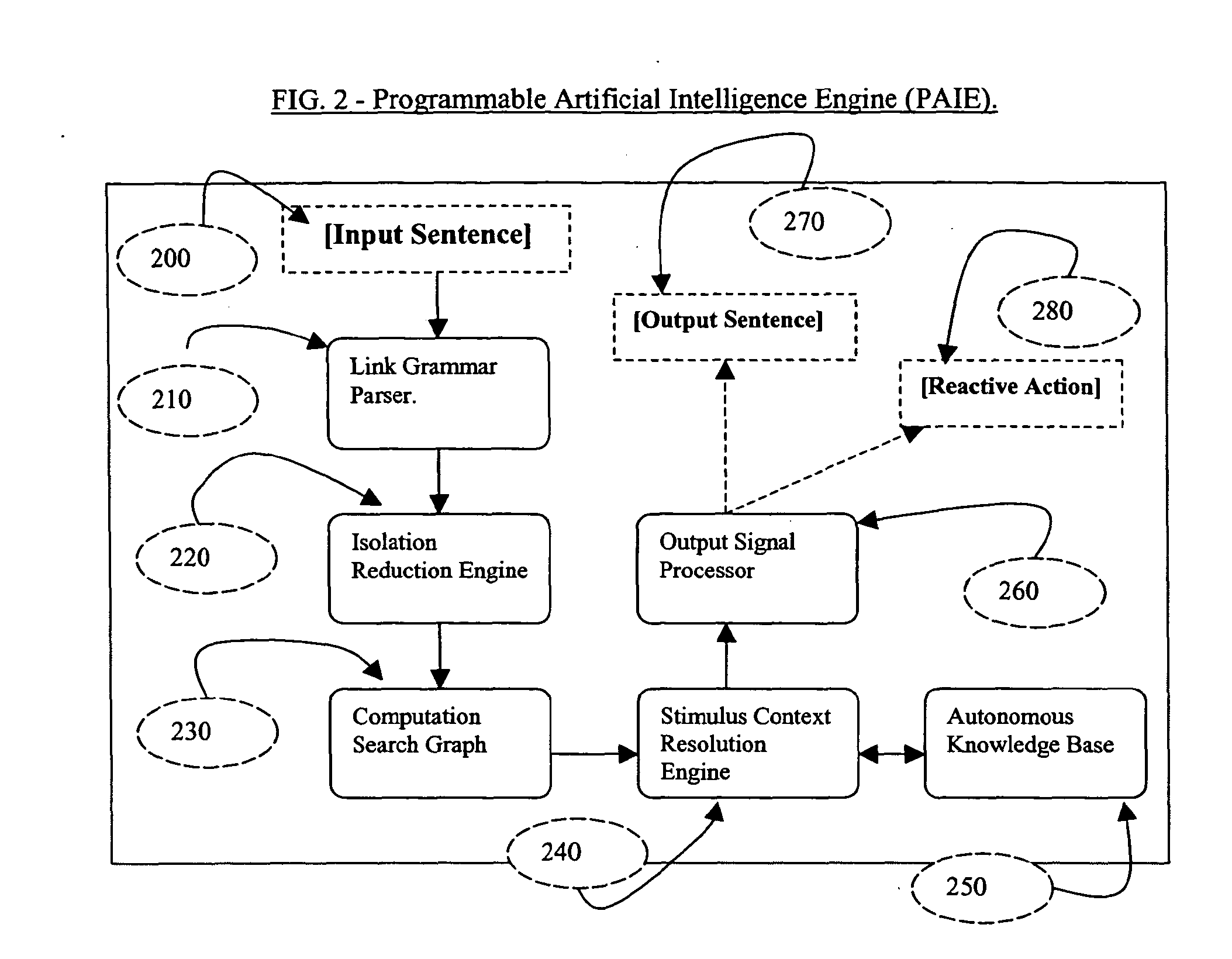
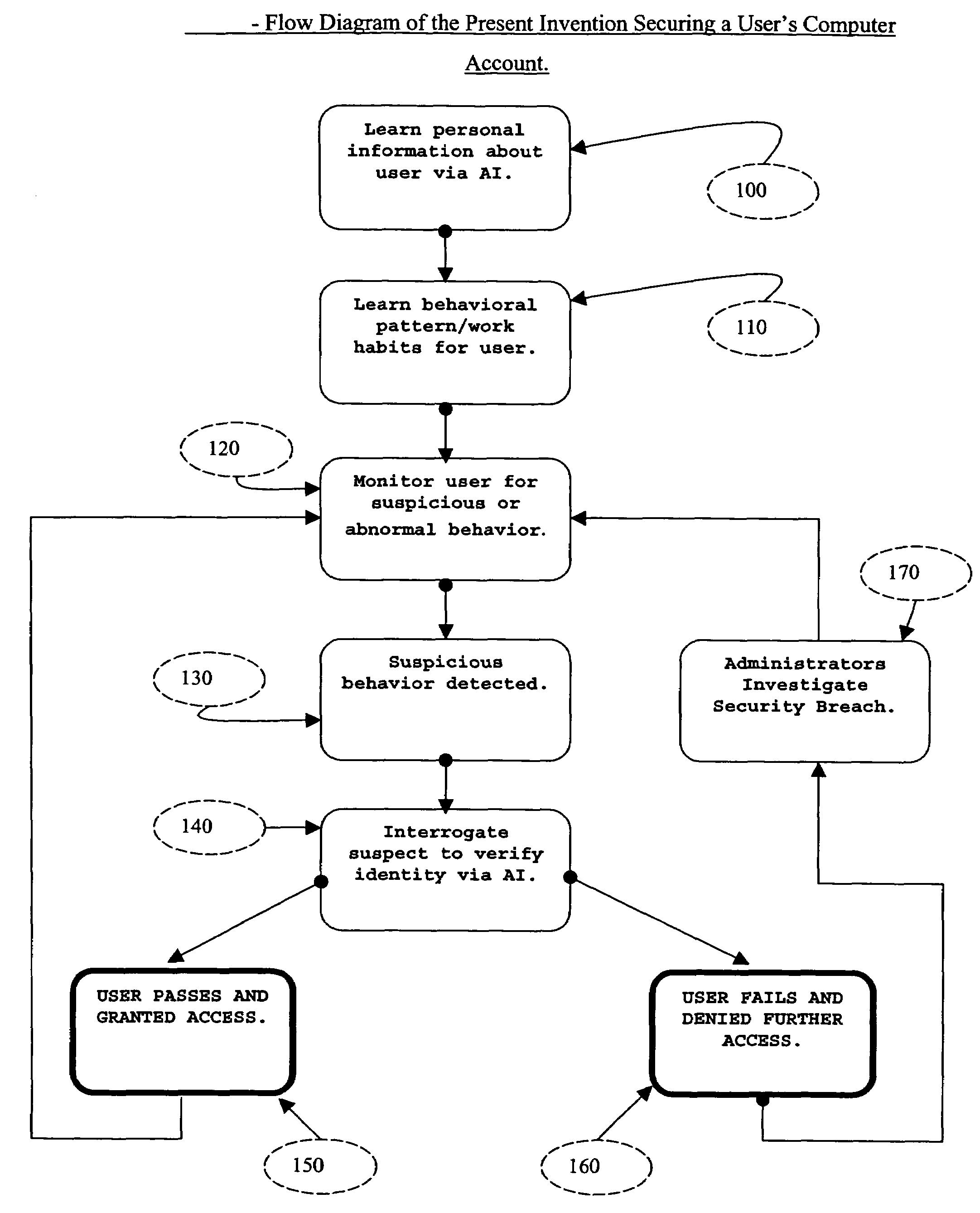
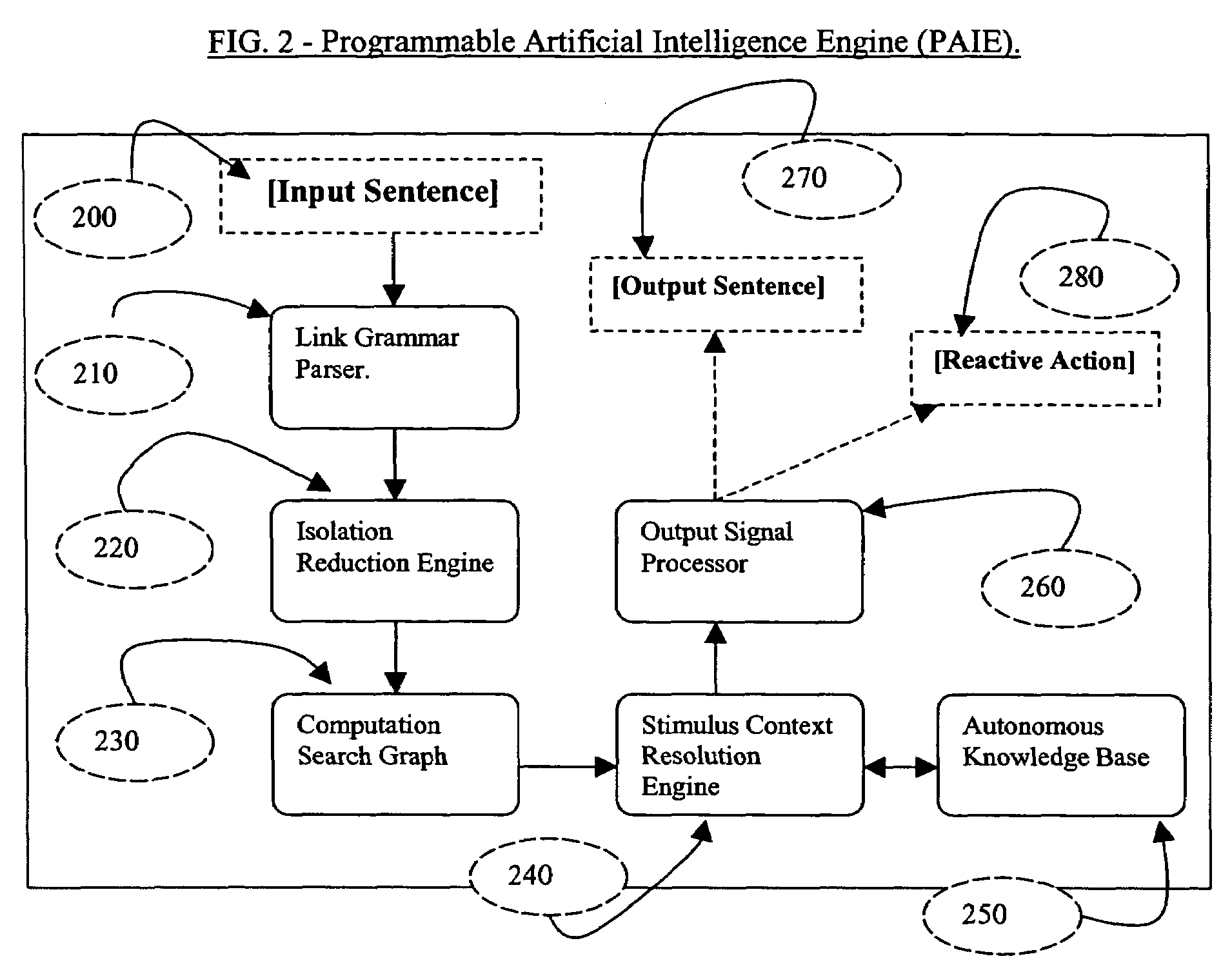
The present invention described secures a computer account against unauthorized access caused as a result of identity-theft, and insider-espionage using artificial intelligence and behavioral modeling methods. The present invention has the ability to detect intruders or impersonators by observing “suspicious” activity under a computer account. When it sees such suspicious behavior, it uses artificial intelligence to authenticate the suspect by interrogation. The present invention asks the suspect questions that only the legitimate computer account owner can verify correctly. If the suspect fails the interrogation, that proves that he / she is an impersonator and therefore further access to the computer account is denied immediately. On the other hand if the suspect passes, access to the computer account is restored. The present invention uses a Programmable Artificial Intelligence Engine (PAIE) to interact with computer users in human natural language. The PAIE can also be programmed to suit other applications where natural language interaction with humans is helpful.
Owner:EDEKI OMON AYODELE +2
Apparatus and method for prioritized grouping of data representing events
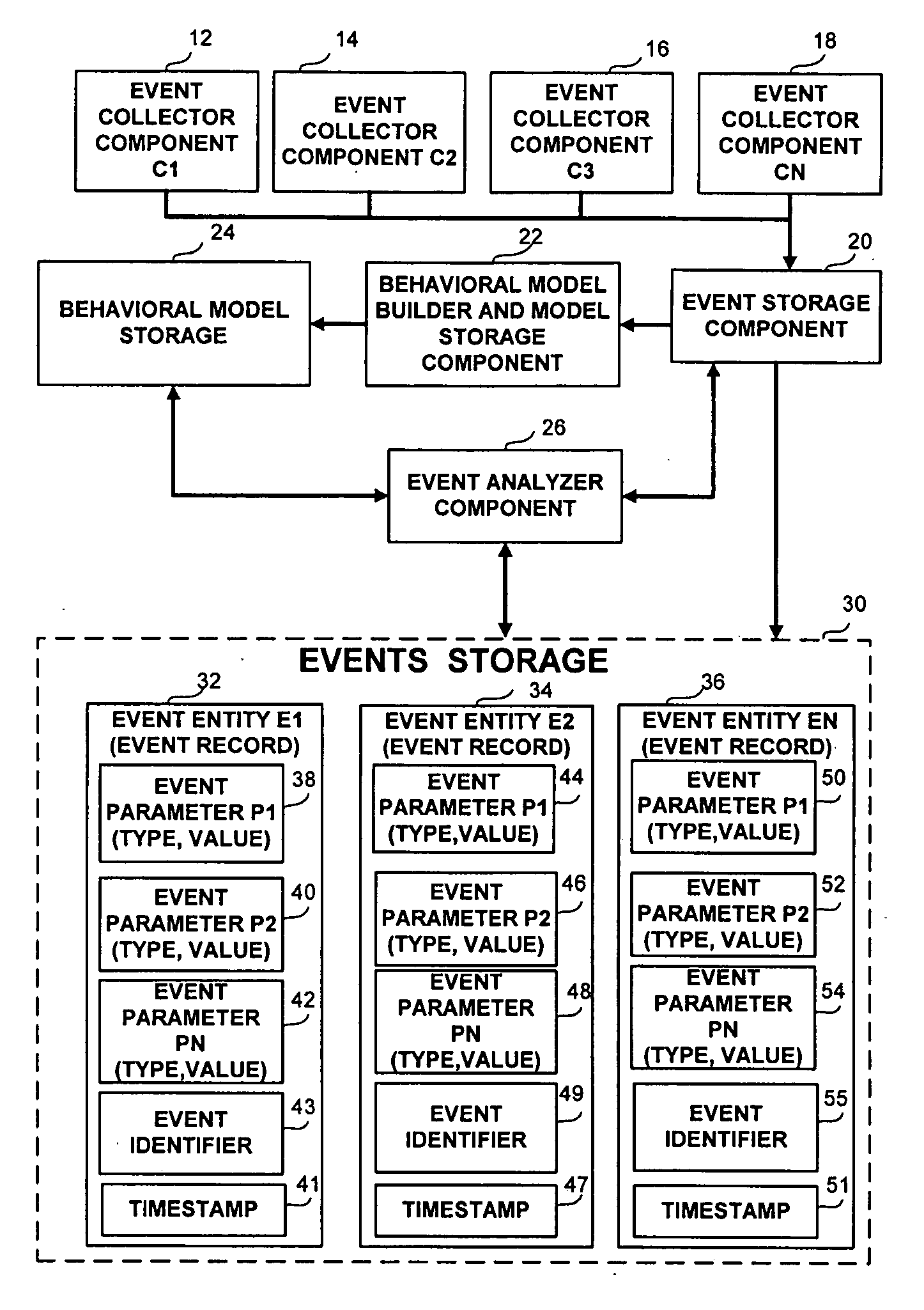
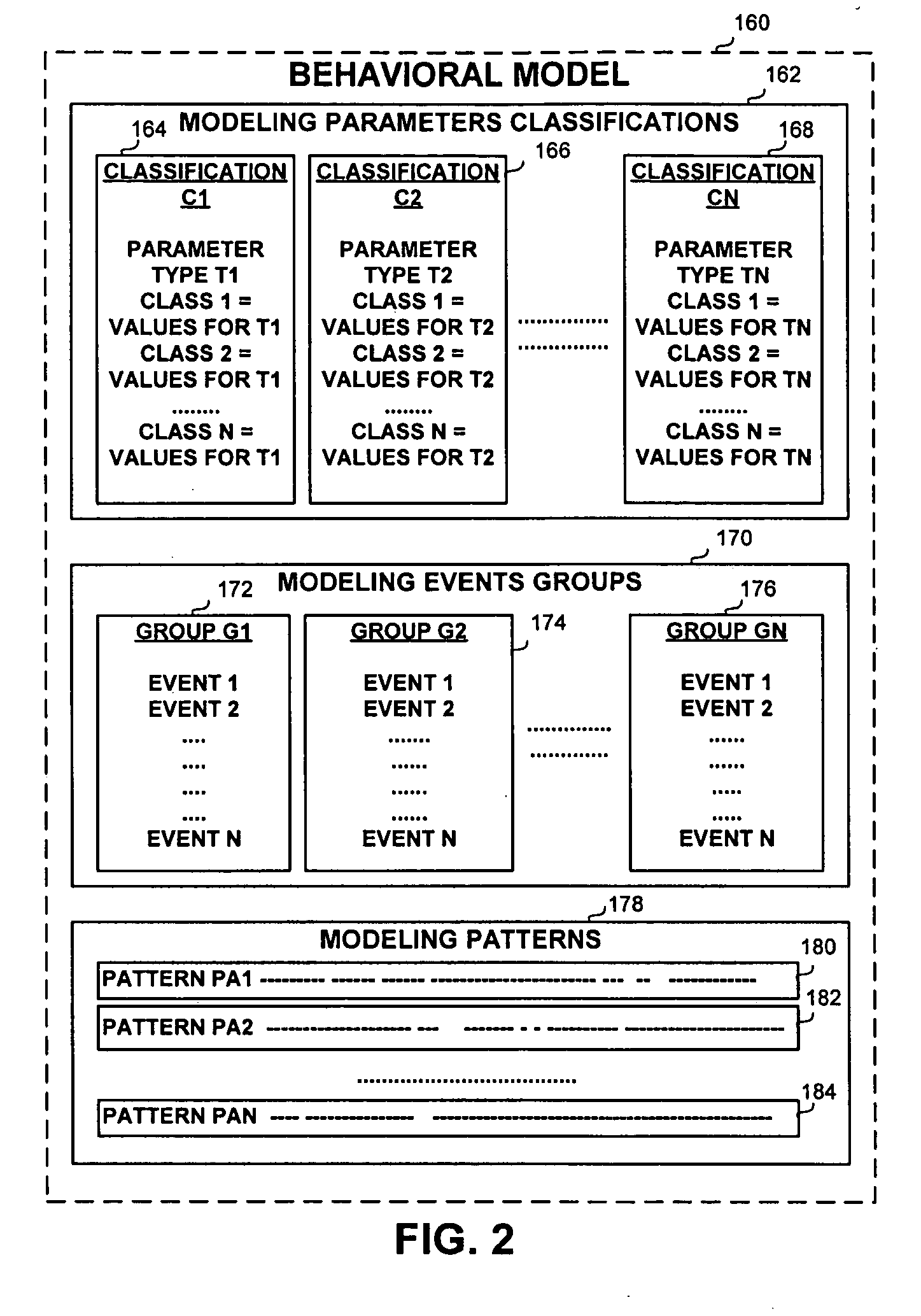
An apparatus and method for the grouping and prioritization of data events using behavioral modeling. The number of events to be analyzed is reduced by generating a behavioral model comprising modeling events groups, by grouping similar events into event groups, by calculating and assigning priority indicators based on the characteristics of the event groups and the behavioral model.
Owner:SECURIMINE SOFTWARE
Mobile terminal and method for providing life observations and a related server arrangement and method with data analysis, distribution and terminal guiding
InactiveUS20110099142A1Mitigate such drawbackMore modular, smarter and flexibleDigital data processing detailsSubstation equipmentTransceiverWireless transceiver
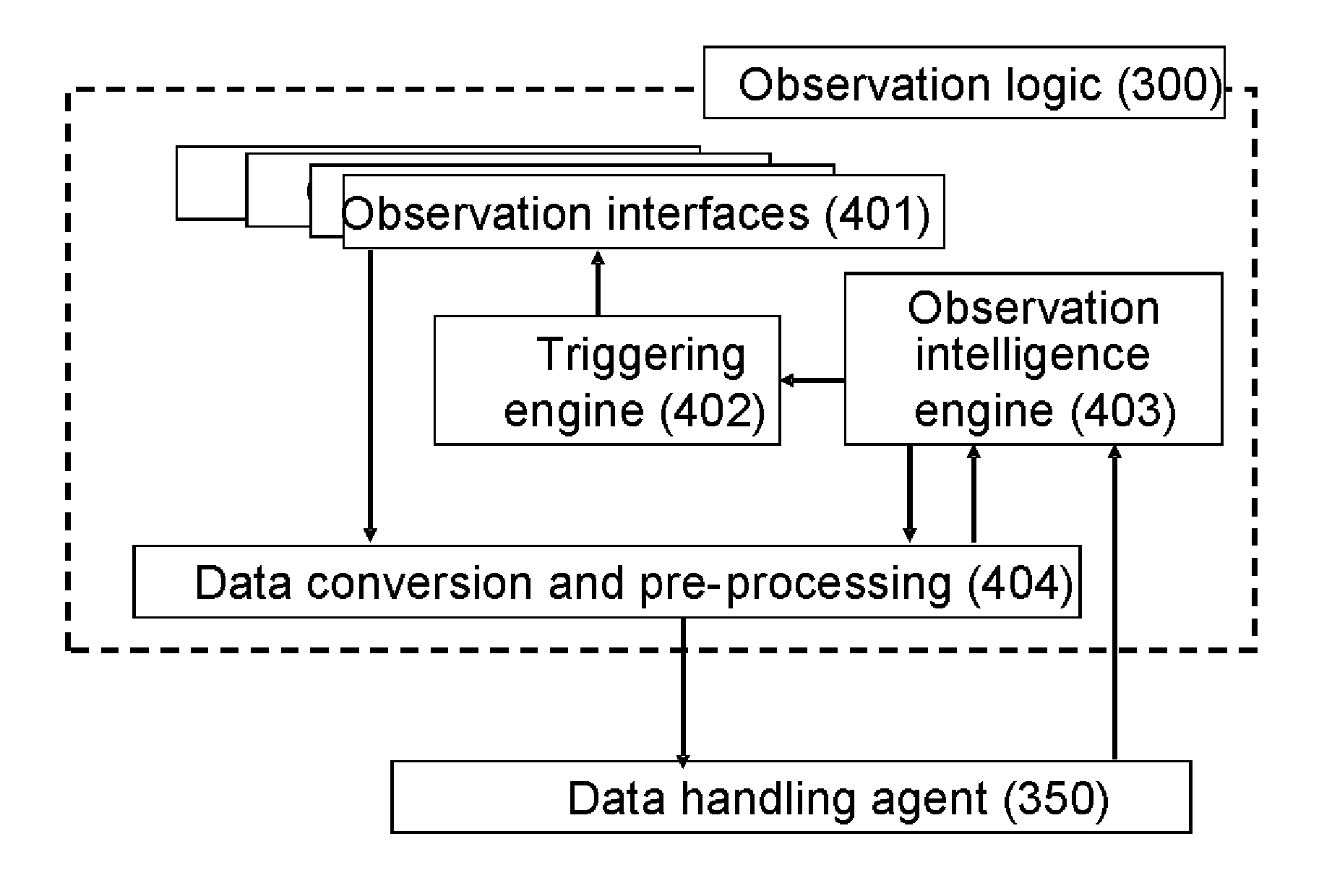
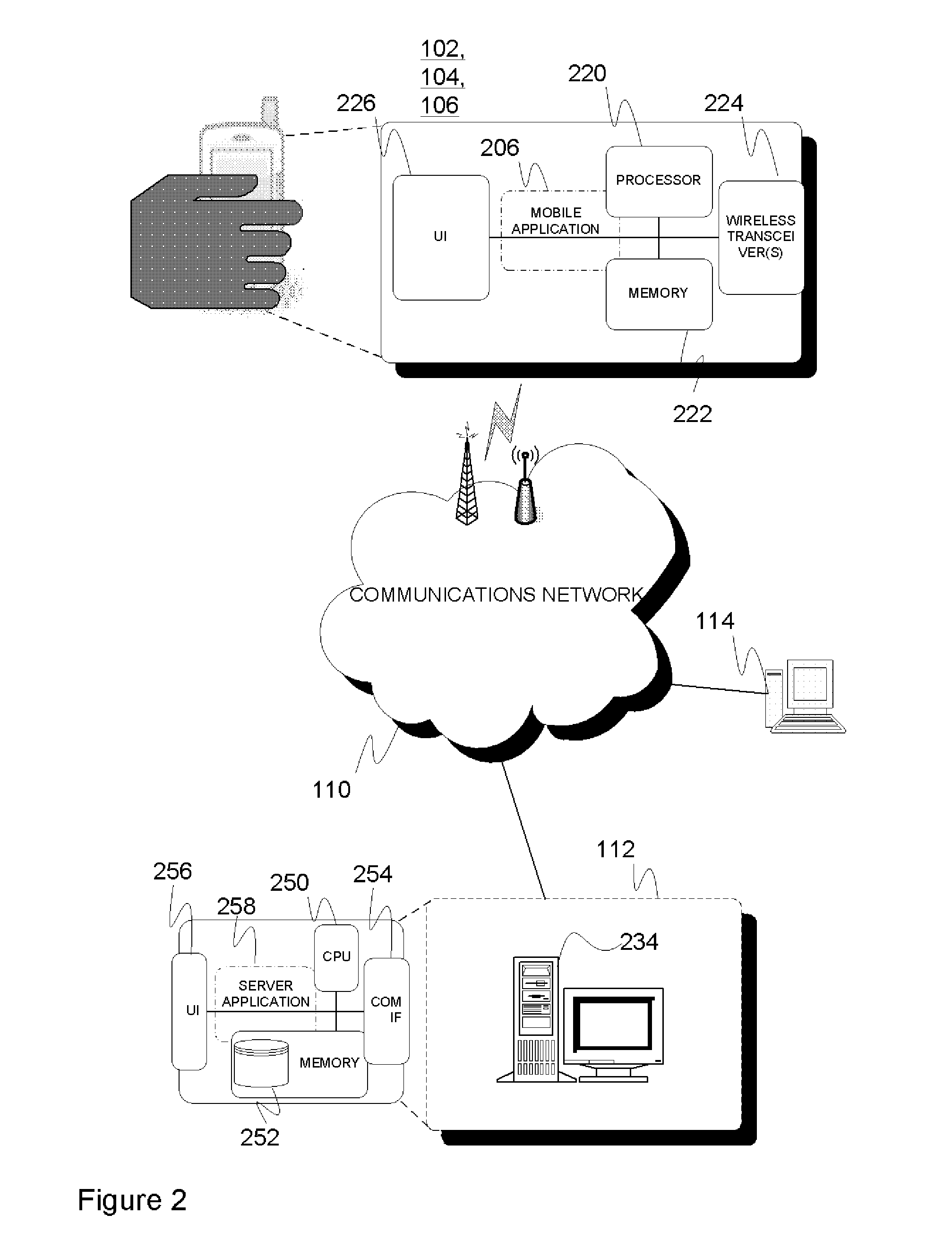
A mobile terminal for providing life observations including: a processing entity, memory, a wireless transceiver for wirelessly transmitting and receiving data relative to external entities, an observation logic conducting active and passive observations detectable relative the mobile terminal in response to active and passive triggers, respectively, each active trigger being associated with a triggering rule for conducting a related observation, each passive trigger being associated with a change in the observation environment, the occurrence of which in the mobile terminal triggers conducting the observation linked to the passive trigger, and a data handling logic for storing, analyzing, and aggregating observation data points of the gathered observation data to timed observation data transmissions via the wireless transceiver towards an external entity. A server arrangement for analyzing context and behavior modelling using observations from plural mobile terminals and guiding the mobile terminals for future observations is also presented, with corresponding methods.
Owner:THE NIELSEN CO (US) LLC
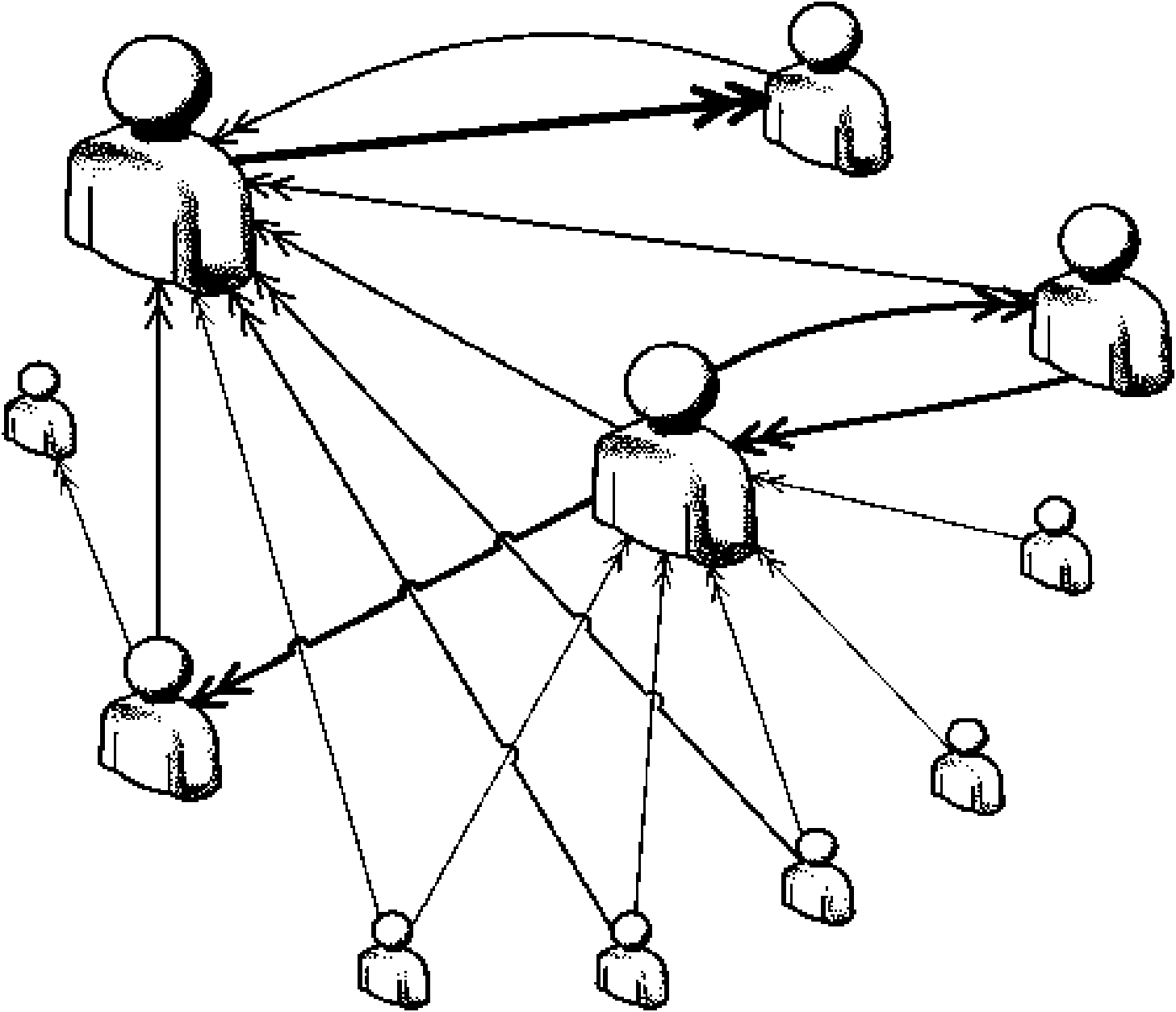
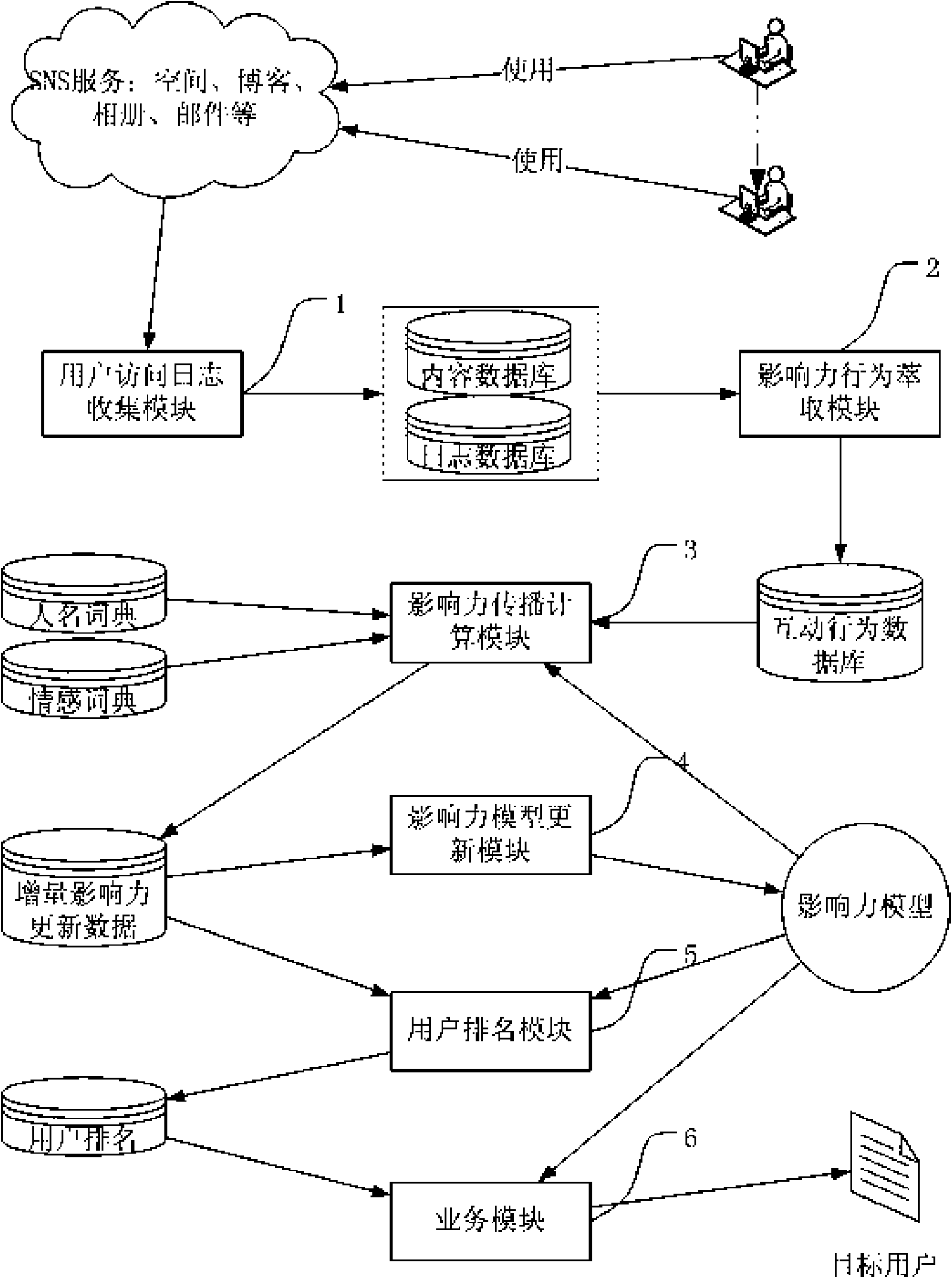
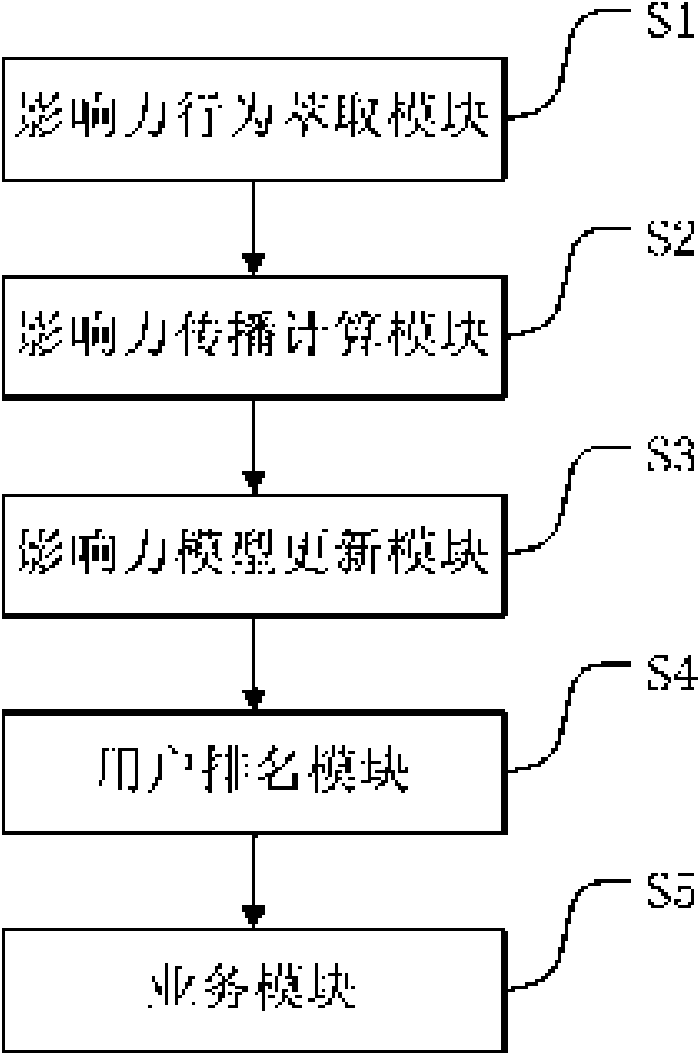
Method and system for calculating user influence in social network
InactiveCN101770487AAccurate descriptionIncrease influenceSpecial data processing applicationsWeb siteBehavioral modeling
The invention relates to the field of a social network and is applied to a network system with social elements. The invention discloses a method and a system for calculating user influence in a social network, and in the method, the behaviors of users are analyzed so that a model of the behavior of influence spread among users is established and the mold is used for identifying the most influential people in the social network. The system records user access logs in real time. The method comprises the following steps that: (1) an influence behavior extracting module filters the interactive behaviors in the logs; (2) an influence spread calculating module determines the influence of the current behavior spread according to the type and the actor of the behavior and the emotion tendentiousness analysis of the relative content; (3) an influence updating module mergers the data generated through the increment; (4) a user ranking module incrementally calculates the most influential people; and (5) a service module appoints a target user range and sequences the target users according to the influence. The method and the system can dynamically reflect the change condition of the user influence according to the interactive behaviors of the users in the social network.
Owner:聚友空间网络技术有限公司 +1
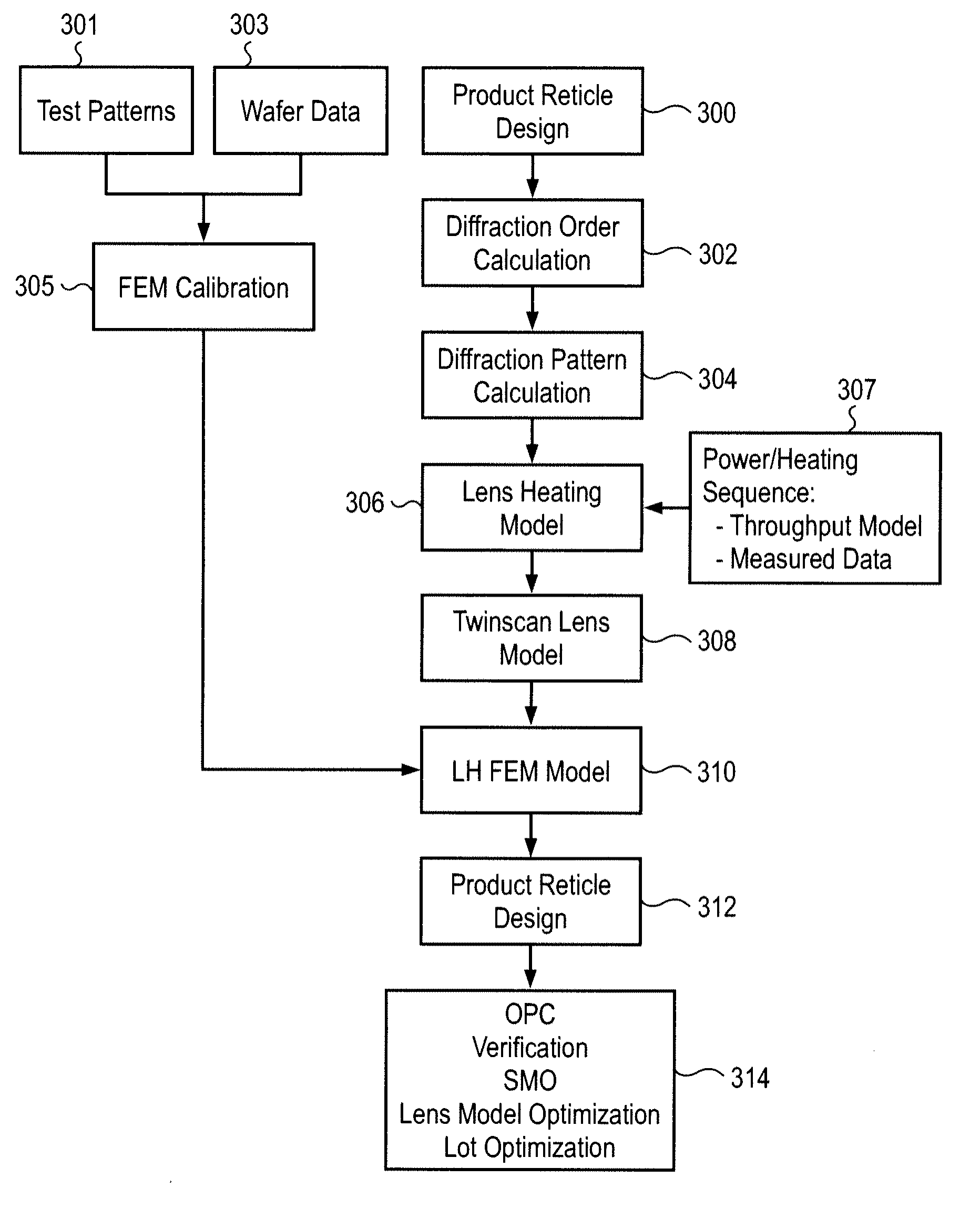
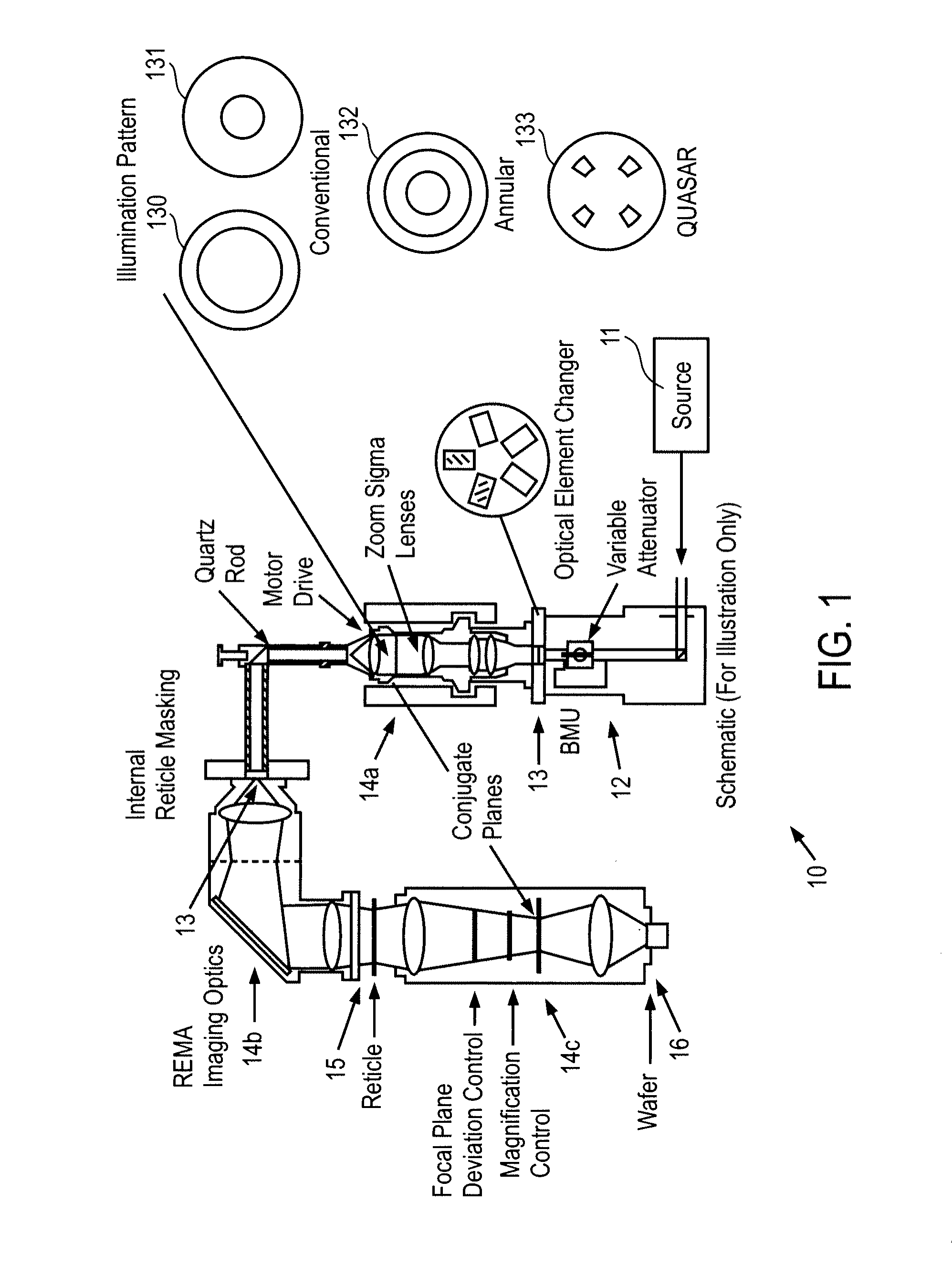
Lens heating compensation systems and methods
ActiveUS20090296055A1Improve accuracyIncrease speedPhotomechanical apparatusOriginals for photomechanical treatmentCamera lensProcess engineering
Methods for calibrating a photolithographic system are disclosed. A cold lens contour for a reticle design and at least one hot lens contour for the reticle design are generated from which a process window is defined. Aberrations induced by a lens manipulator are characterized in a manipulator model and the process window is optimized using the manipulator model. Aberrations are characterized by identifying variations in critical dimensions caused by lens manipulation for a plurality of manipulator settings and by modeling behavior of the manipulator as a relationship between manipulator settings and aberrations. The process window may be optimized by minimizing a cost function for a set of critical locations.
Owner:ASML NETHERLANDS BV
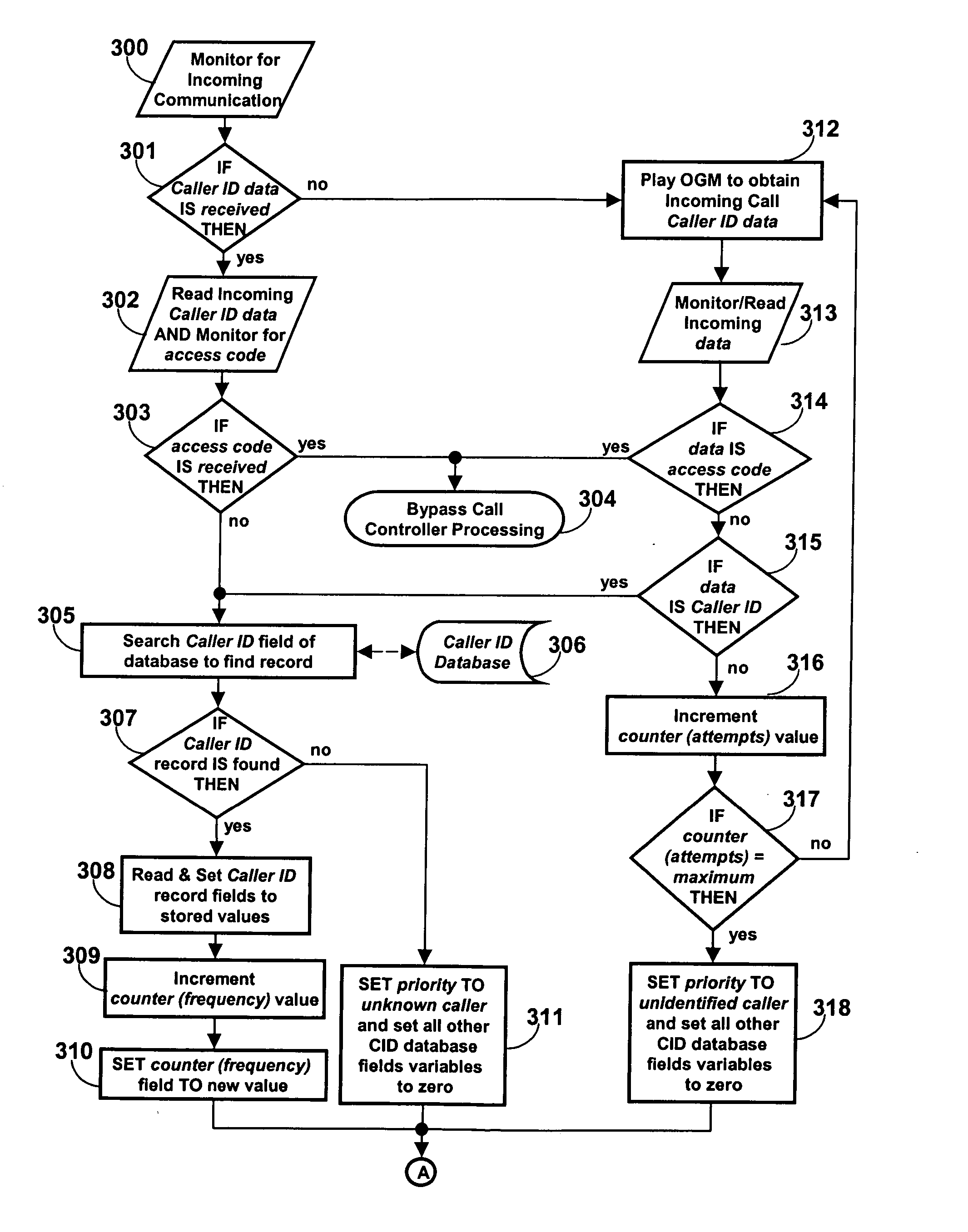
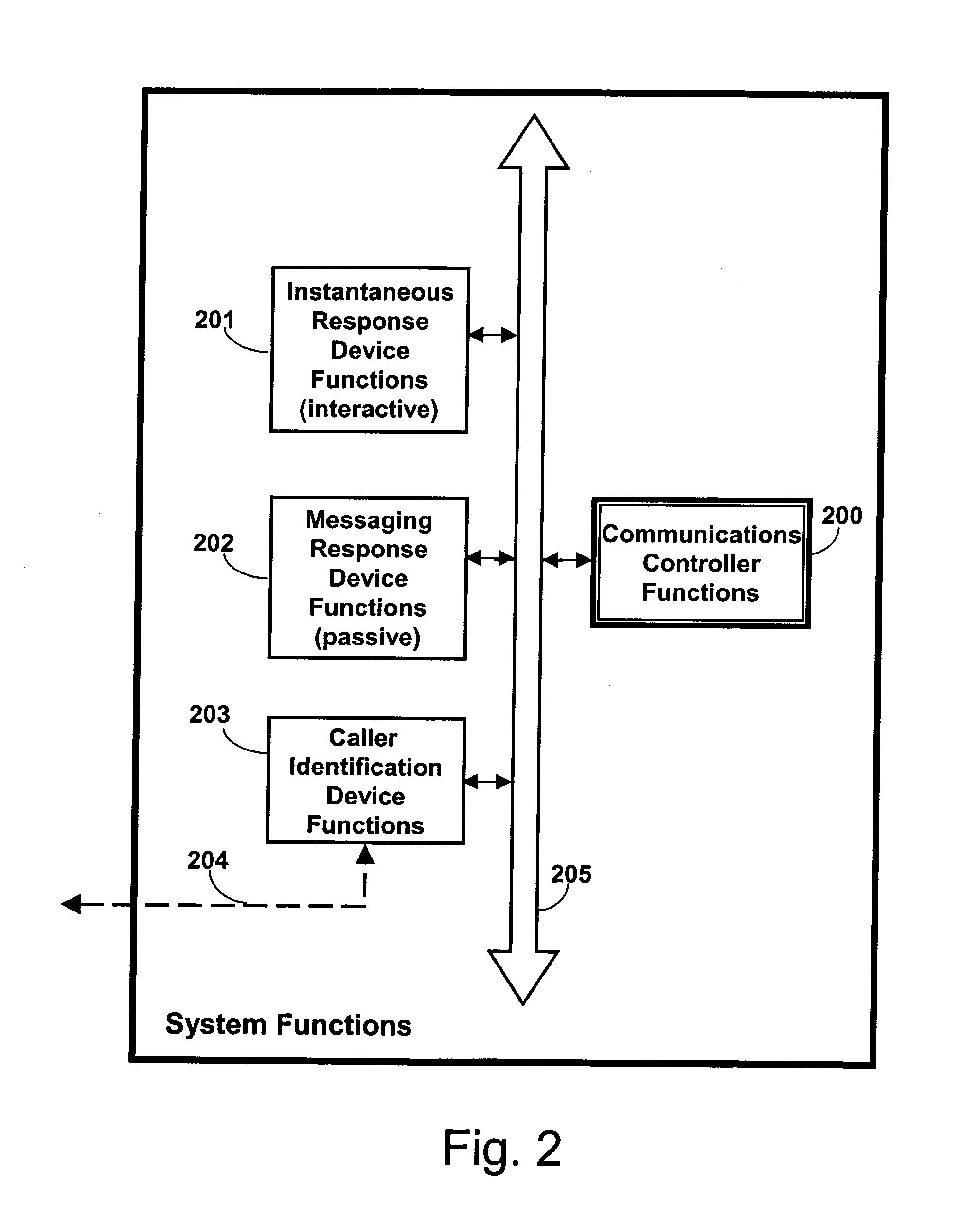
Communications control method and apparatus
InactiveUS20060094404A1Exposure was also limitedSpecial service for subscribersPower supply for data processingBehavioral modelingCommunication control
A communications controller is provided for empowering the user of a communications device, such as a telephone or other device, to assume control over incoming communications. This communications controller is based on artificial intelligence and behavior modeling techniques. Each communication is identified by unique identification information associated with an incoming communication. The user selects one of a plurality of different priority rating levels for a particular communication. The user also selects or infers block time intervals for each priority to indicate times during which incoming communication is not desired. Dynamic communications control is achieved by also determining the mood of the user or mode of the device. Undesirable communications will be “blocked”. For example, when that particular caller places a call to the user, the user's communication controller determines the caller's identification information and recalls the priority and corresponding blocking time interval for that particular caller. The user's mood or the mode of the communications device is determined. The call is accordingly passed to the communication device or blocked.
Owner:BURGESS SHELIA JEAN
Method and apparatus for neuropsychological modeling of human experience and purchasing behavior
InactiveUS20120101966A1Easy accessLimited amountDigital computer detailsDigital dataNeuropsychological testData stream
A system for accurately modeling of buyer / purchaser psychology and ranking of content objects within a channel for user initiated browsing and presentation contains a neuropsychological modeling engine, a ranking application, and a behavior modeler which communicate with each other and a presentation system over communication networks. The neuropsychological modeling engine utilizes metafiles associated with content objects, a purchaser / viewer model and a channel model to derive a value ψ representing an individual's mood and a value m representing an individual's motivational strength to select a content object. If the value ψ is within an acceptable predetermined range, the value m is used to determine a ranking for the content object relative to other content objects associated with the channel model. Also disclosed are a system and technique for simultaneously presenting multiple, s content object data streams on the user interface in a manner which encourages multidimensional browsing using traditional navigation commands.
Owner:HOLYBRAIN
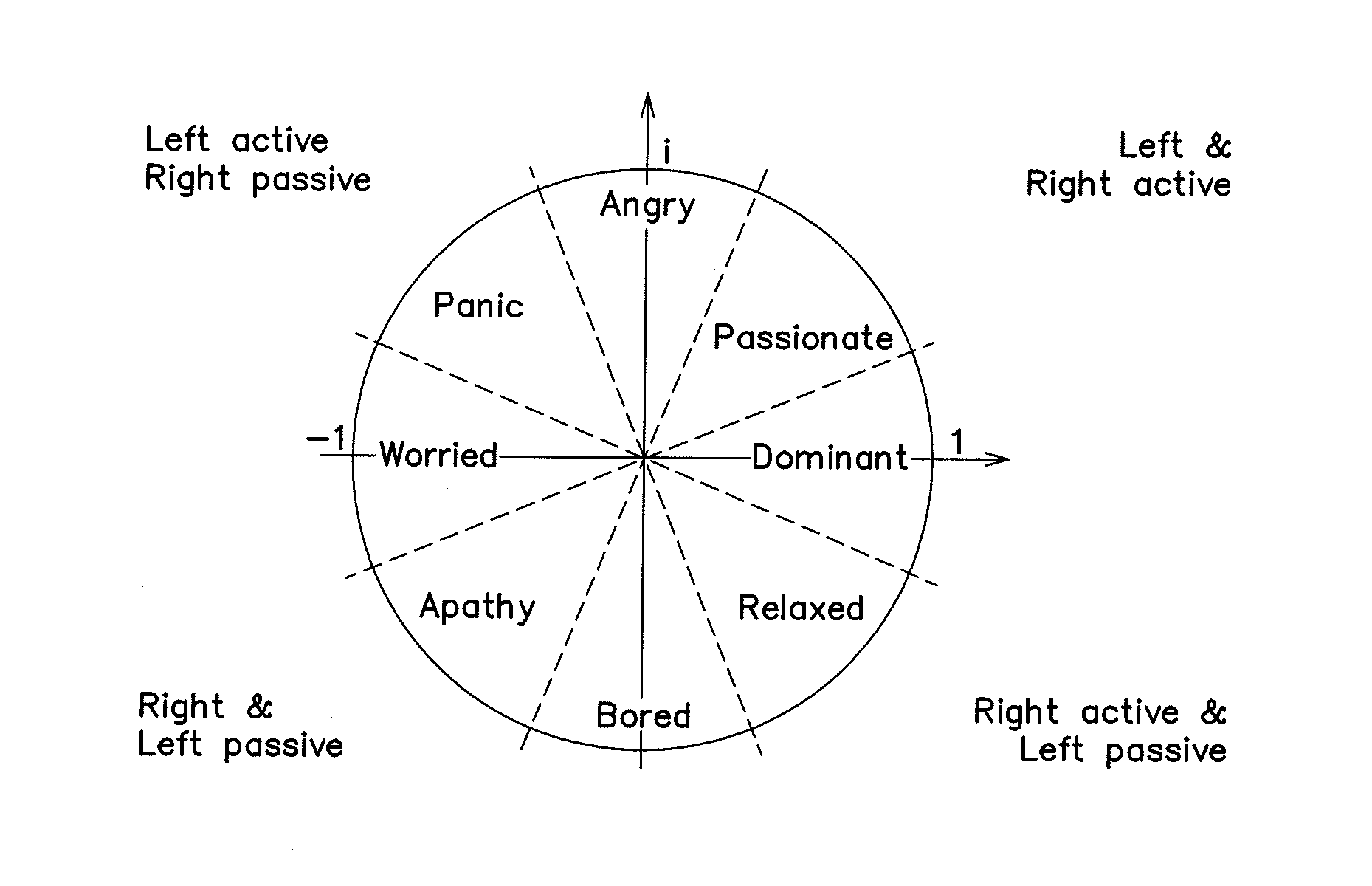
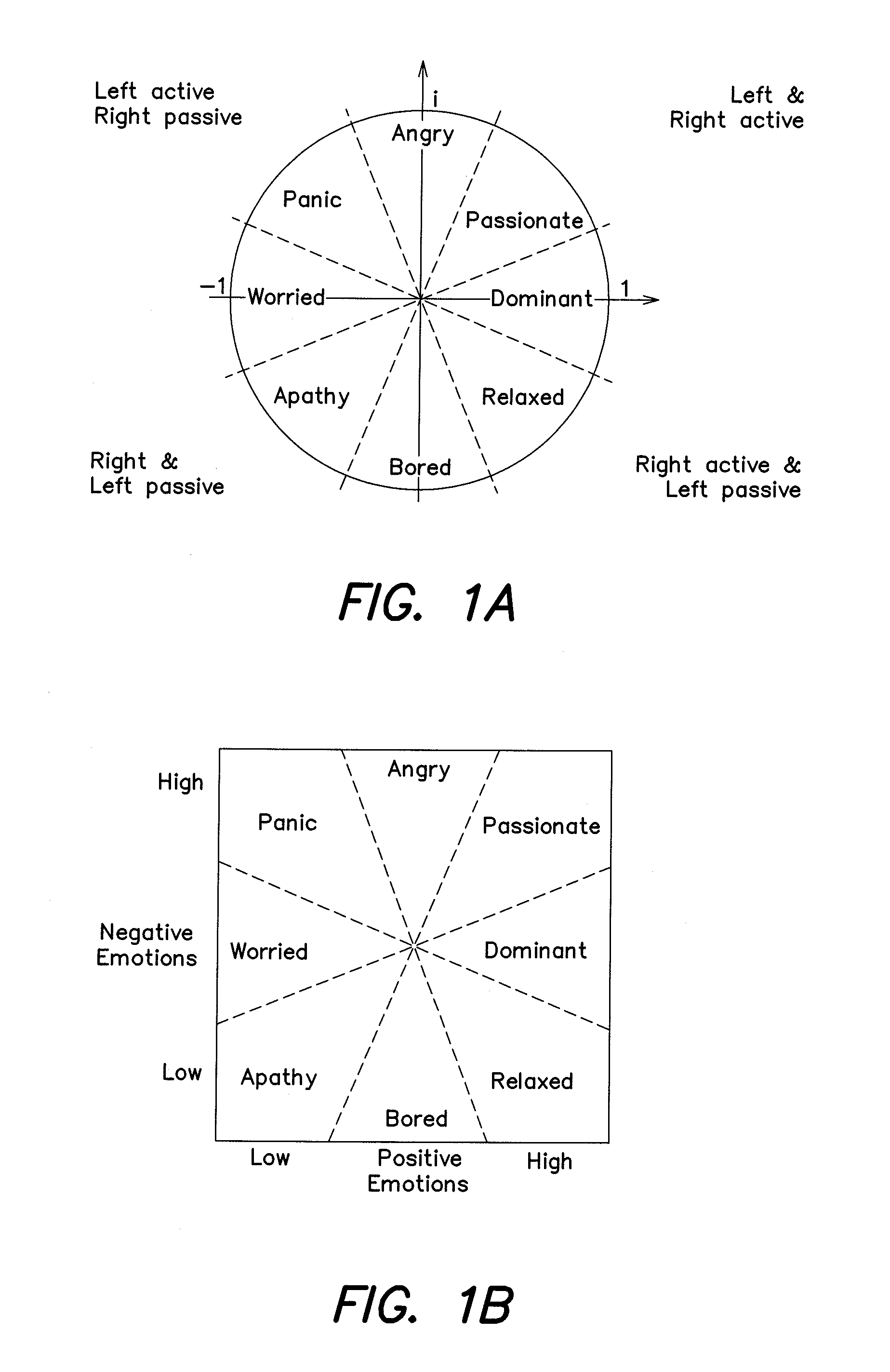
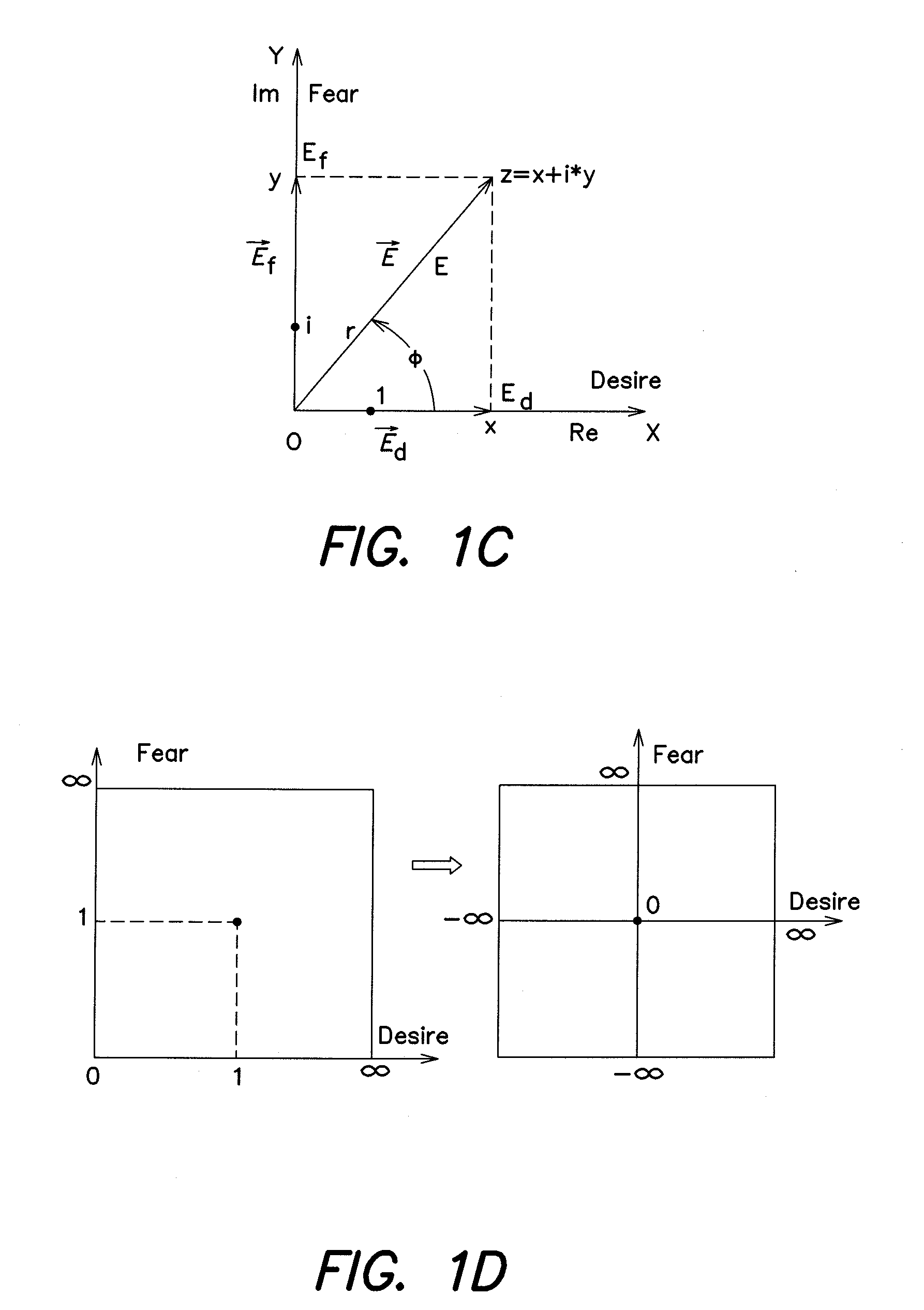
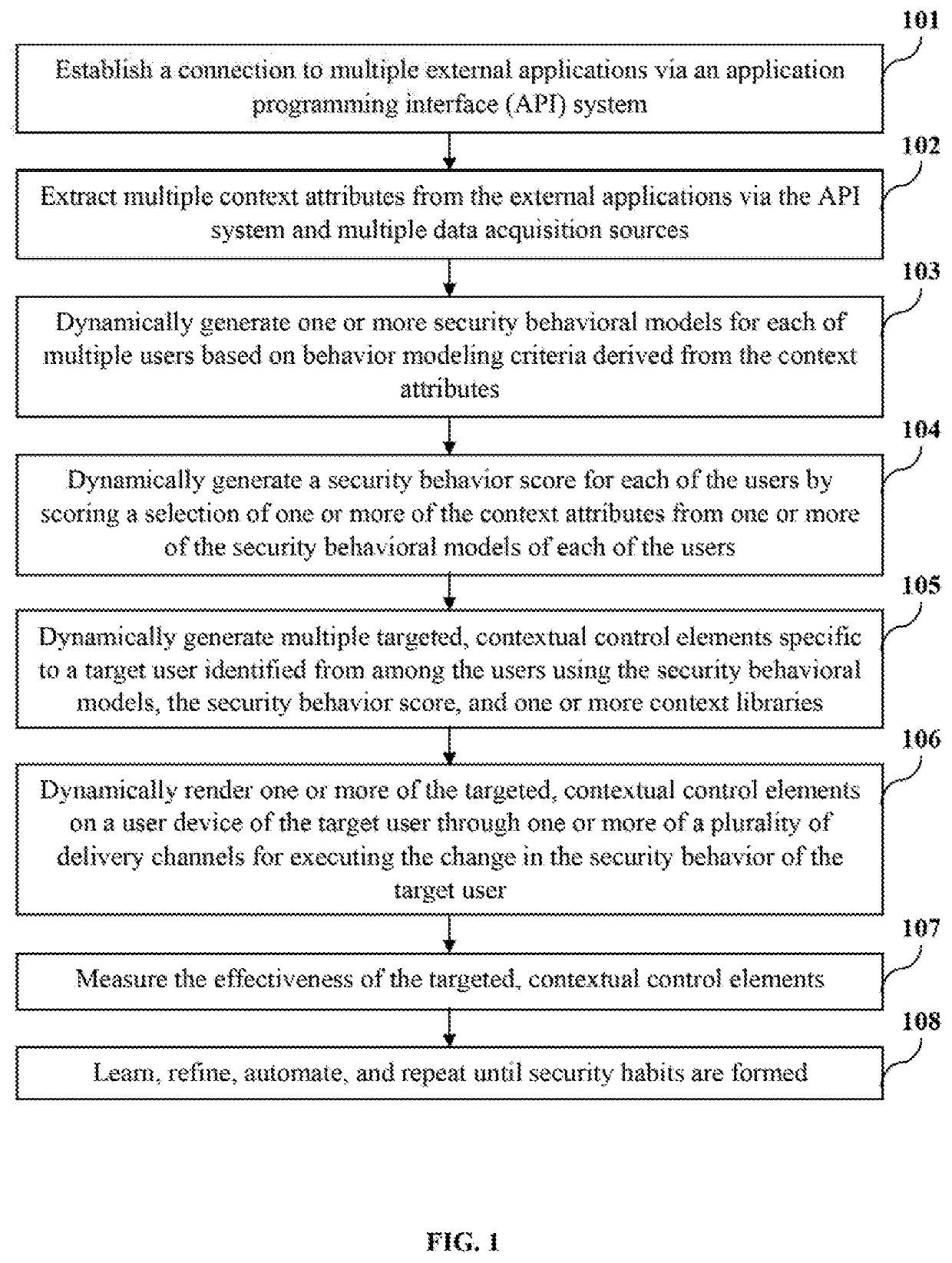
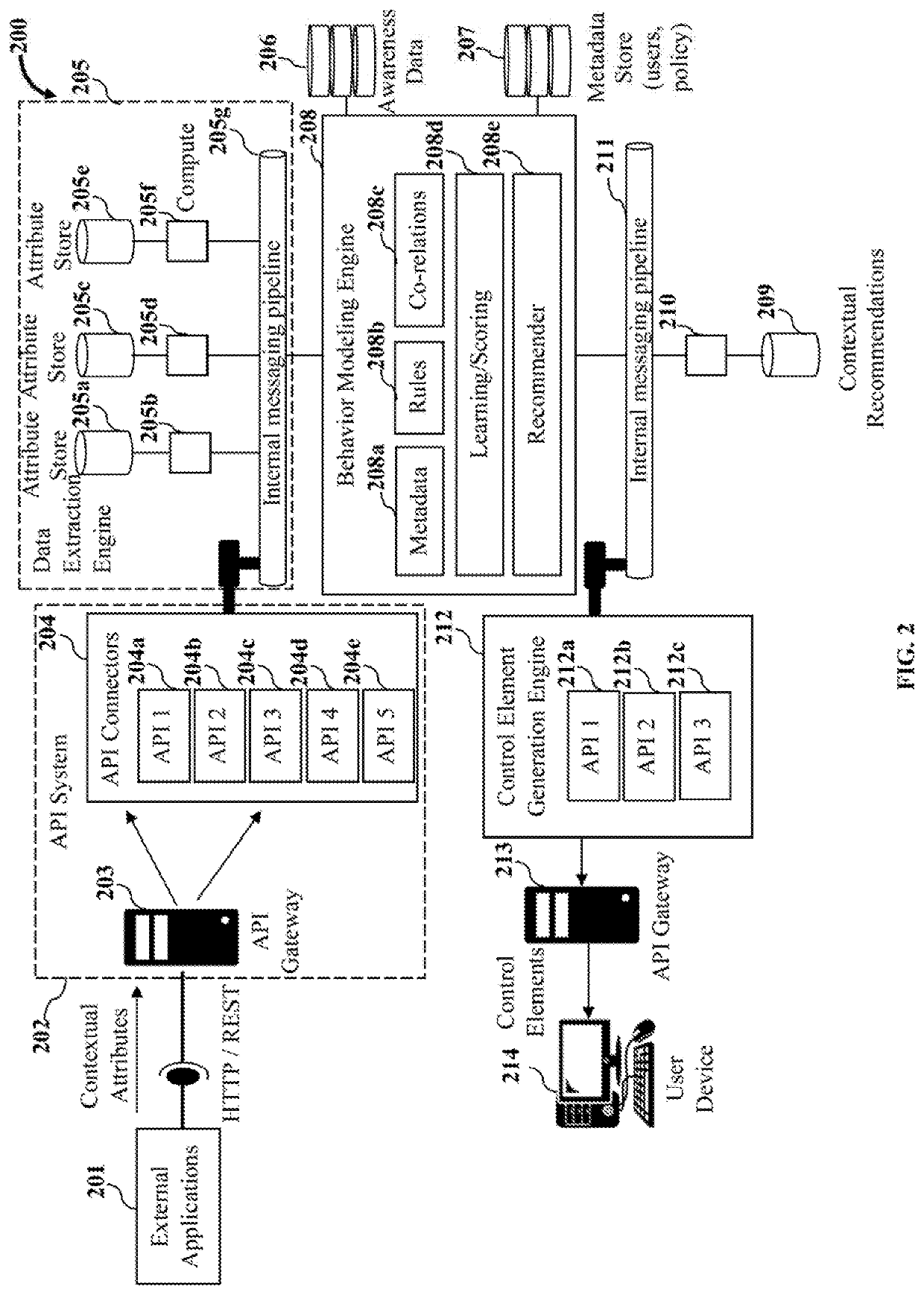
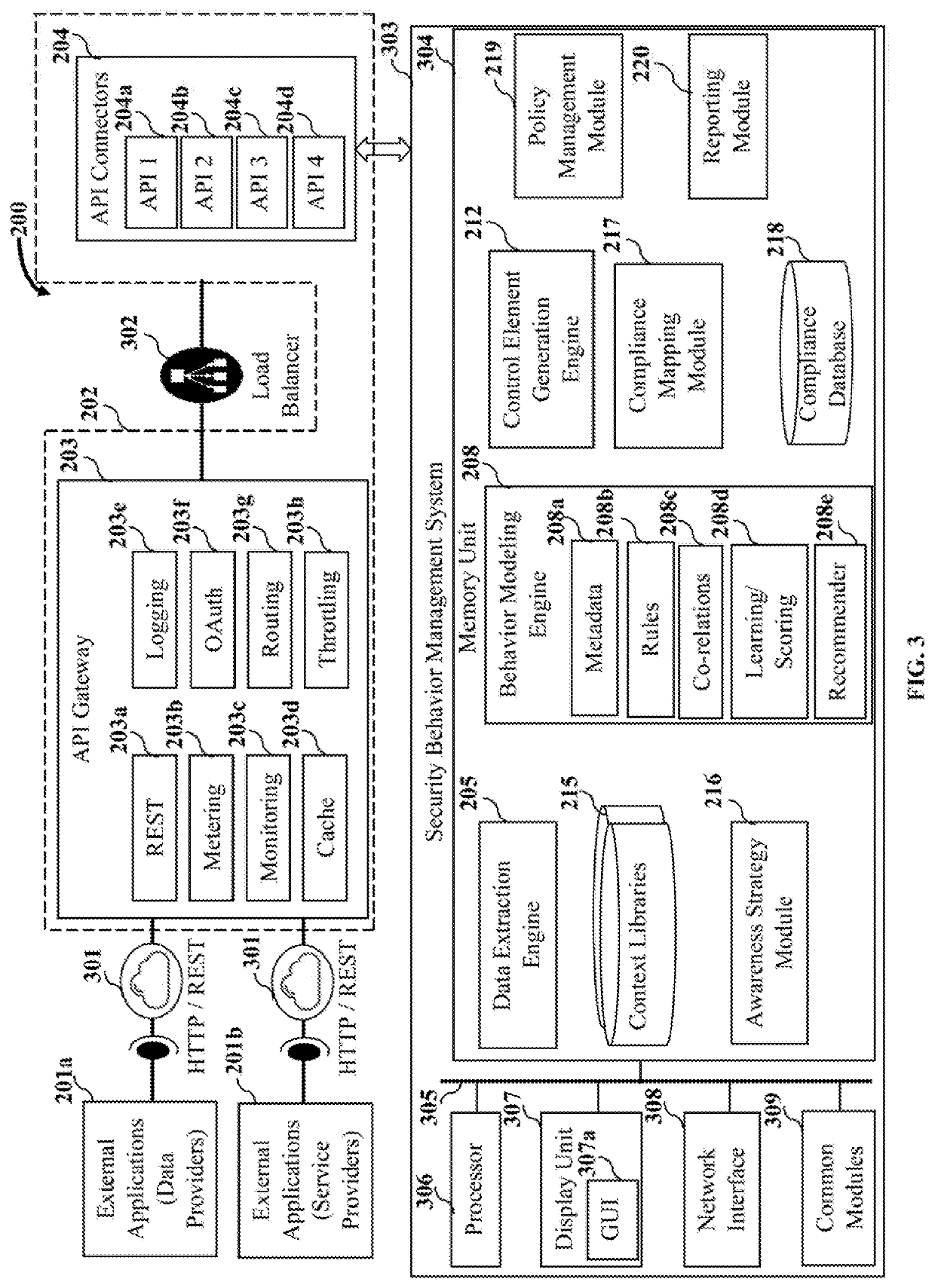
Contextual security behavior management and change execution
ActiveUS20200021620A1Shorten the timeEasy to implementMachine learningTransmissionMultiple contextUser device
A method and a system for contextually managing and executing a change in security behavior of a target user are provided. The system extracts multiple context attributes including activity telemetry, skill, etc., from multiple external applications. The system dynamically generates one or more security behavioral models for each user based on behavior modeling criteria. The system dynamically generates a security behavior score for each user by scoring a selection of the context attributes from their security behavioral models. The system dynamically generates targeted, contextual control elements specific to a target user identified from among the users using the security behavioral models, the security behavior score, and one or more context libraries. The system dynamically renders one or more of the targeted, contextual control elements on a user device of the target user through one or more delivery channels for executing a change in the security behavior of the target user.
Owner:KNOWBE4 INC
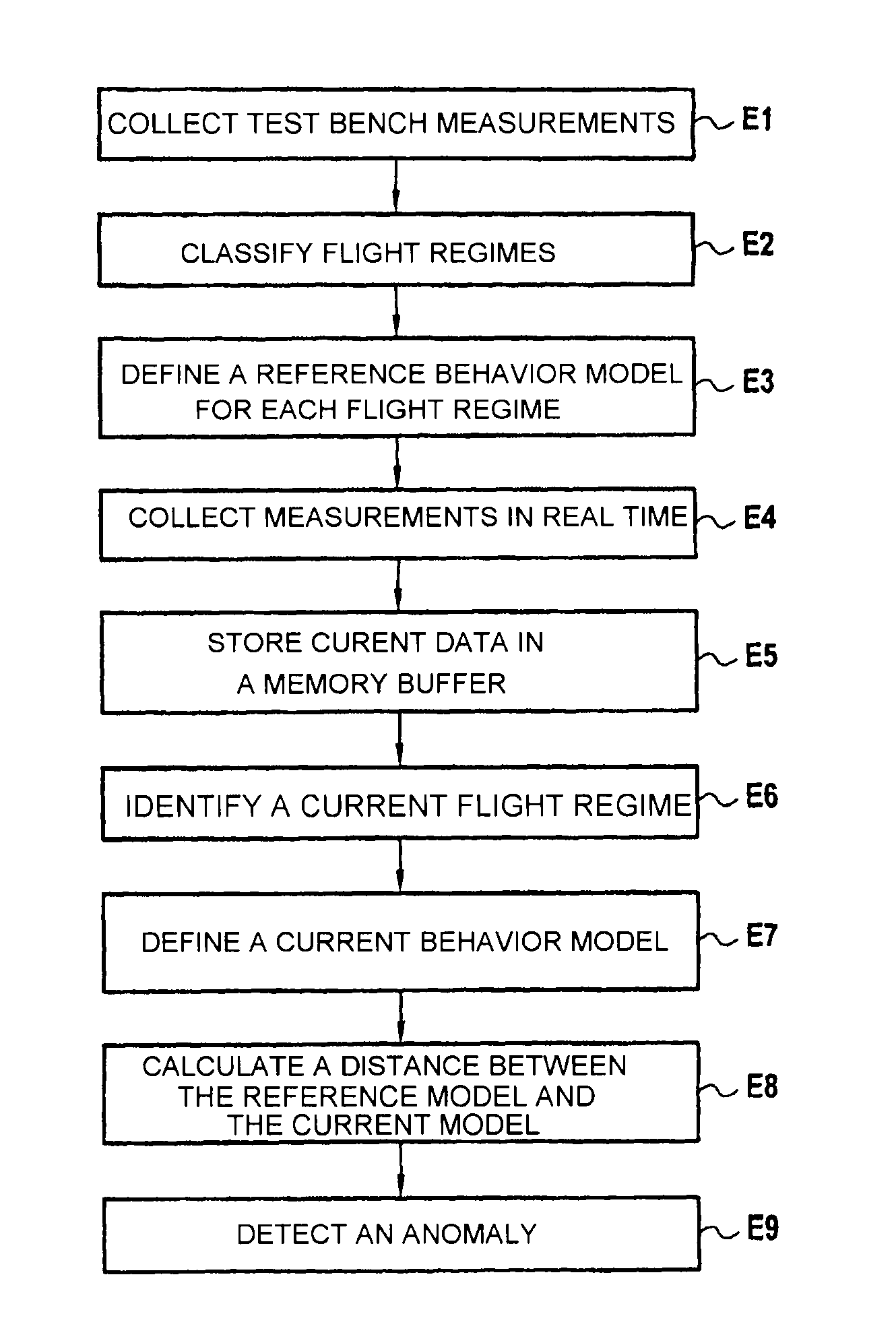
Detection of anomalies in an aircraft engine
ActiveUS20110288836A1Optimize calculation timeTesting/monitoring control systemsMachines/enginesAviationData set
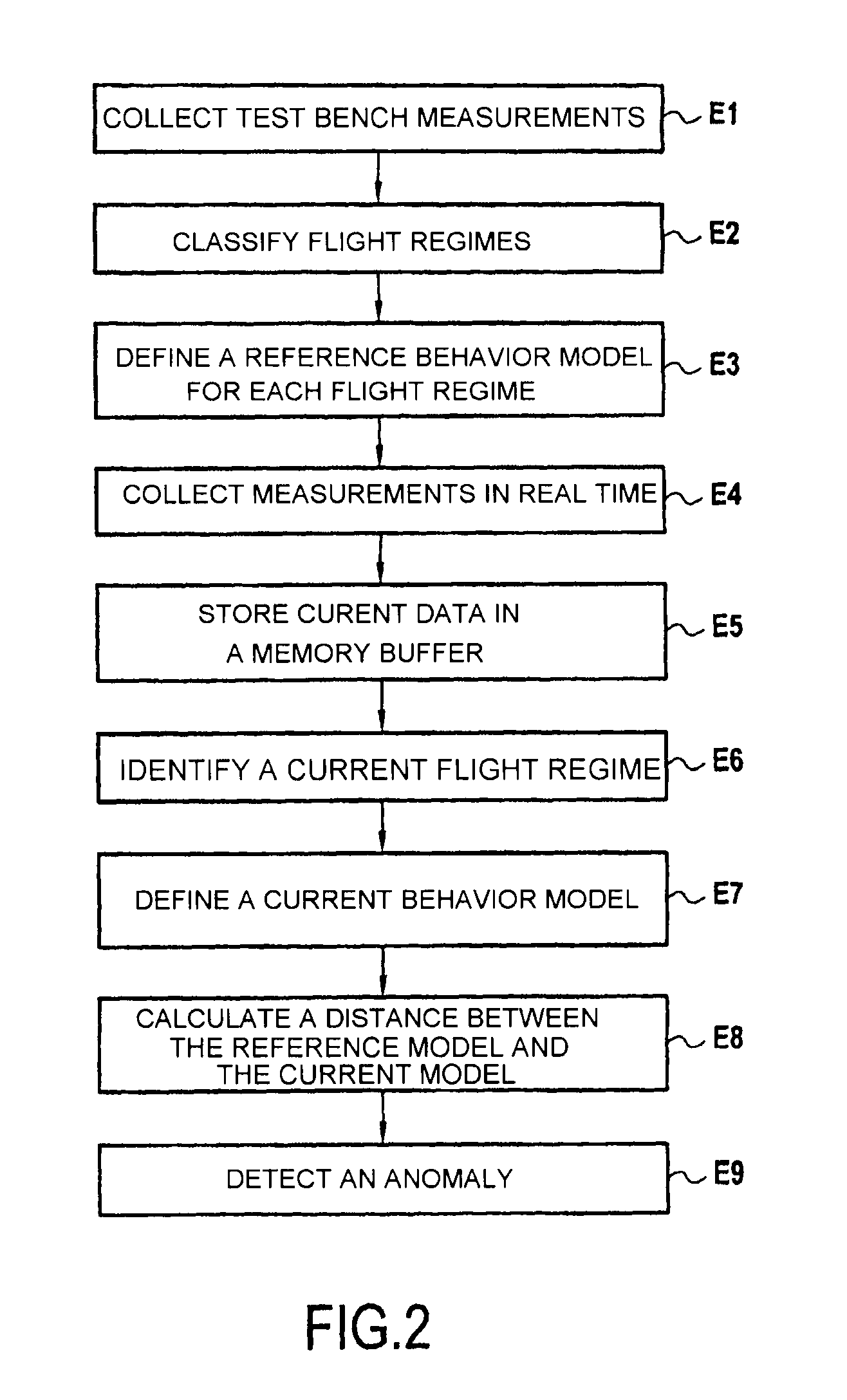
A method and system for detecting anomalies in an aeroengine. The method and system define a behavior model of a controller of the aeroengine using a time regression modeling the behavior of the controller as a function of a data set relating to the controller and including measurements of past behaviors and command and state measurements of the controller; continuously recalculate the behavior model for each new data set; and monitor statistical variation of the behavior model to detect a behavior anomaly of the controller representing an operating anomaly of the engine.
Owner:SN DETUDE & DE CONSTR DE MOTEURS DAVIATION S N E C M A
Apparatus and method for detecting abnormal behavior
InactiveUS20150199512A1Easy to detectMemory loss protectionError detection/correctionBehavioral analyticsProcess behavior
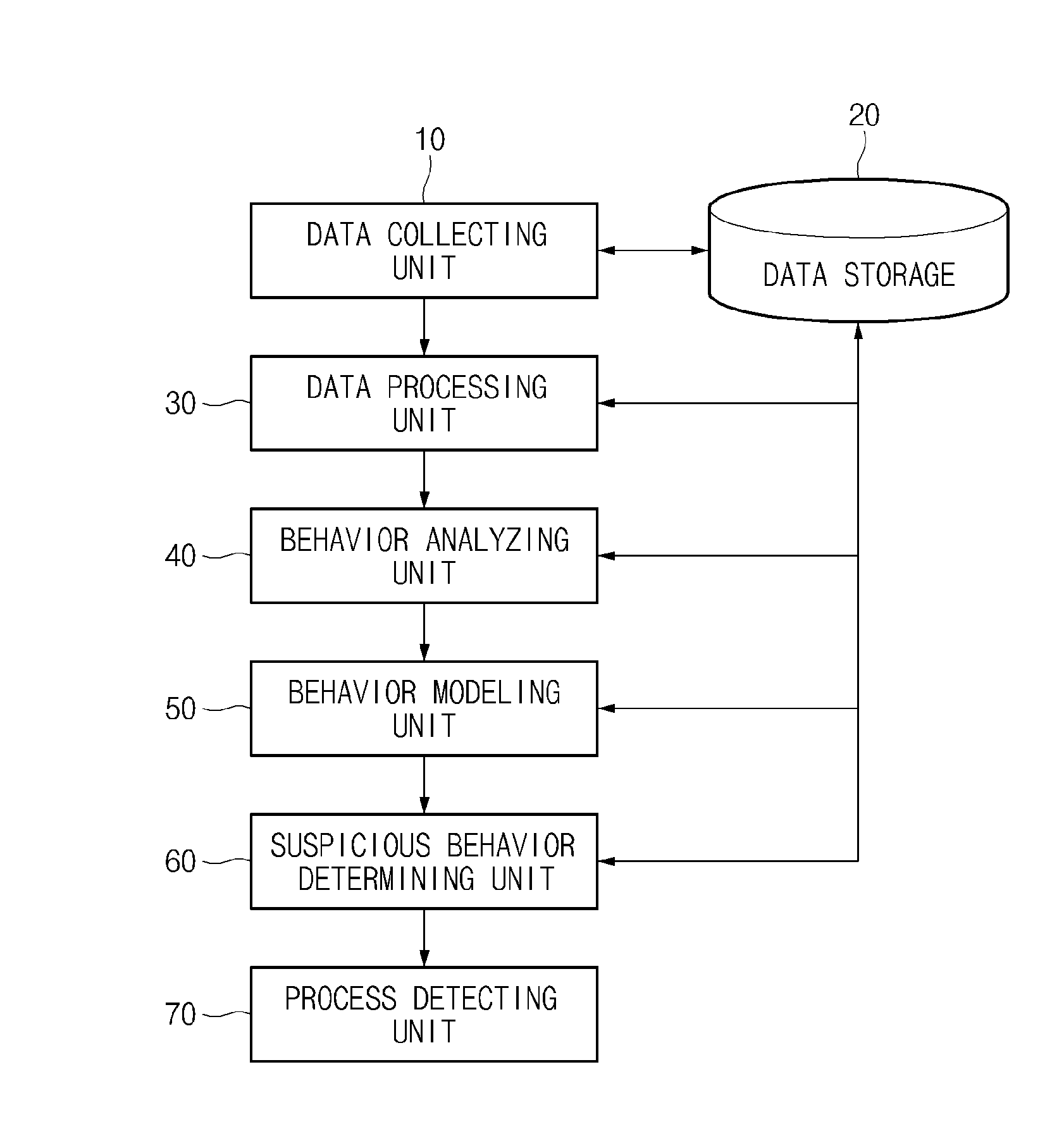
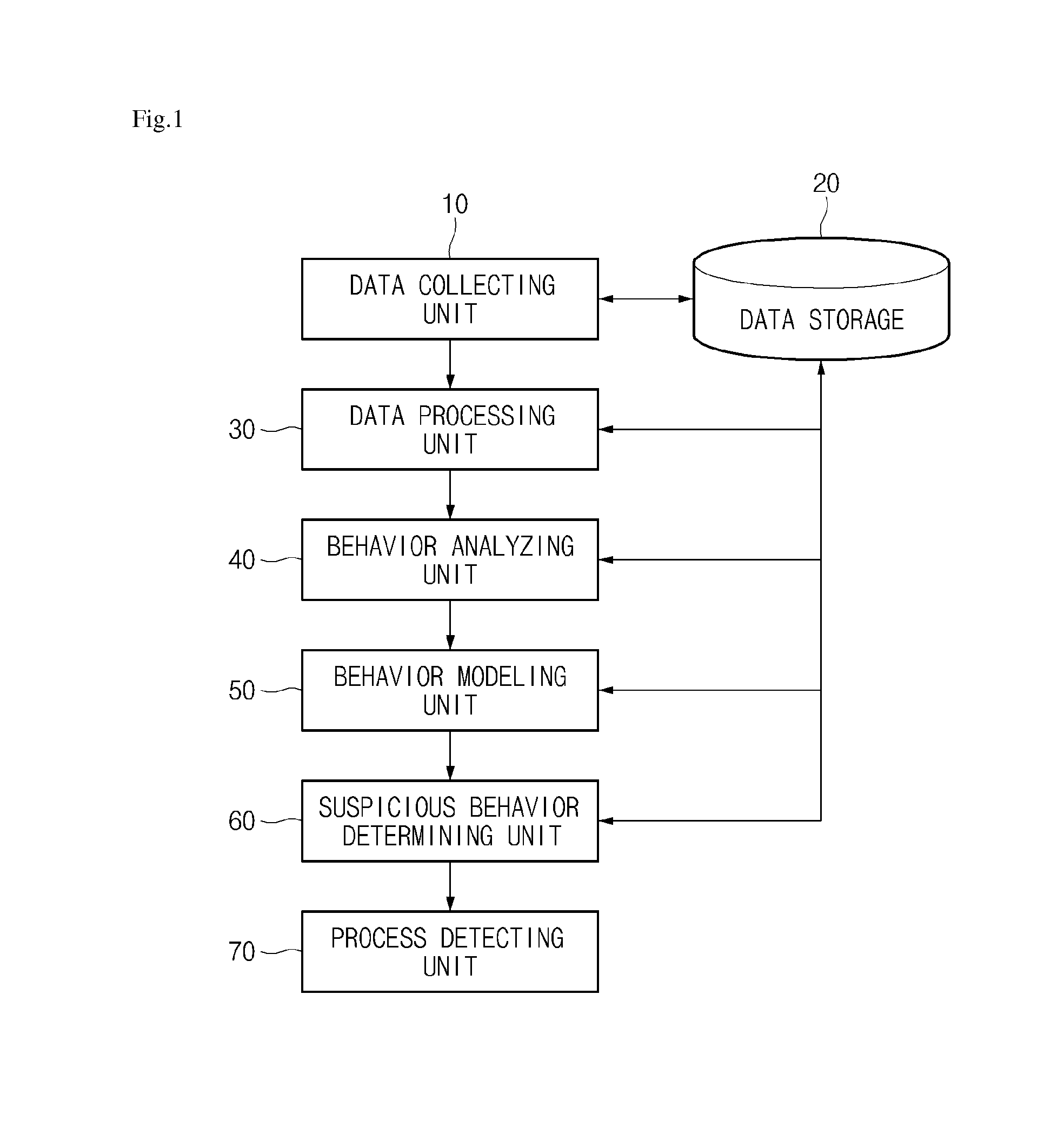
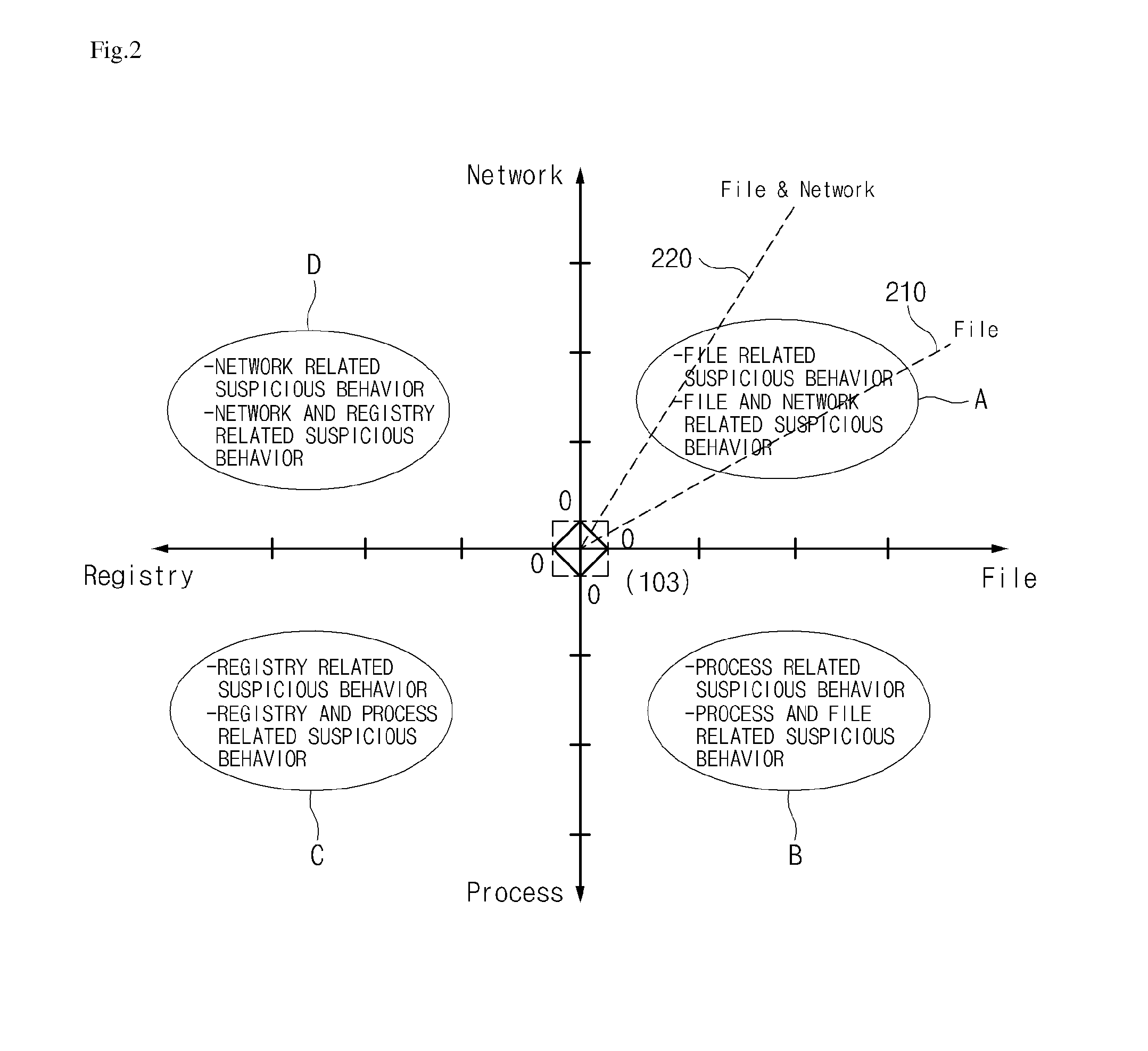
Provided are abnormal behavior detecting apparatus and method and the abnormal behavior detecting apparatus, includes: a behavior analyzing unit which analyzes a behavior which occurs for resources of a system based on data collected from a process while the process is executed on the system; a behavior modeling unit which models a behavior analysis result for the resources of the system on a coordinate which is generated based on the behavior for the resources of the system to create a process behavior model corresponding to the resources of the system; a suspicious behavior determining unit which determines a suspicious behavior of the process in accordance with the type of the process behavior model which is implemented on the coordinate; and a process detecting unit which detects a process in which the suspicious behavior occurs as an abnormal behavior process.
Owner:ELECTRONICS & TELECOMM RES INST
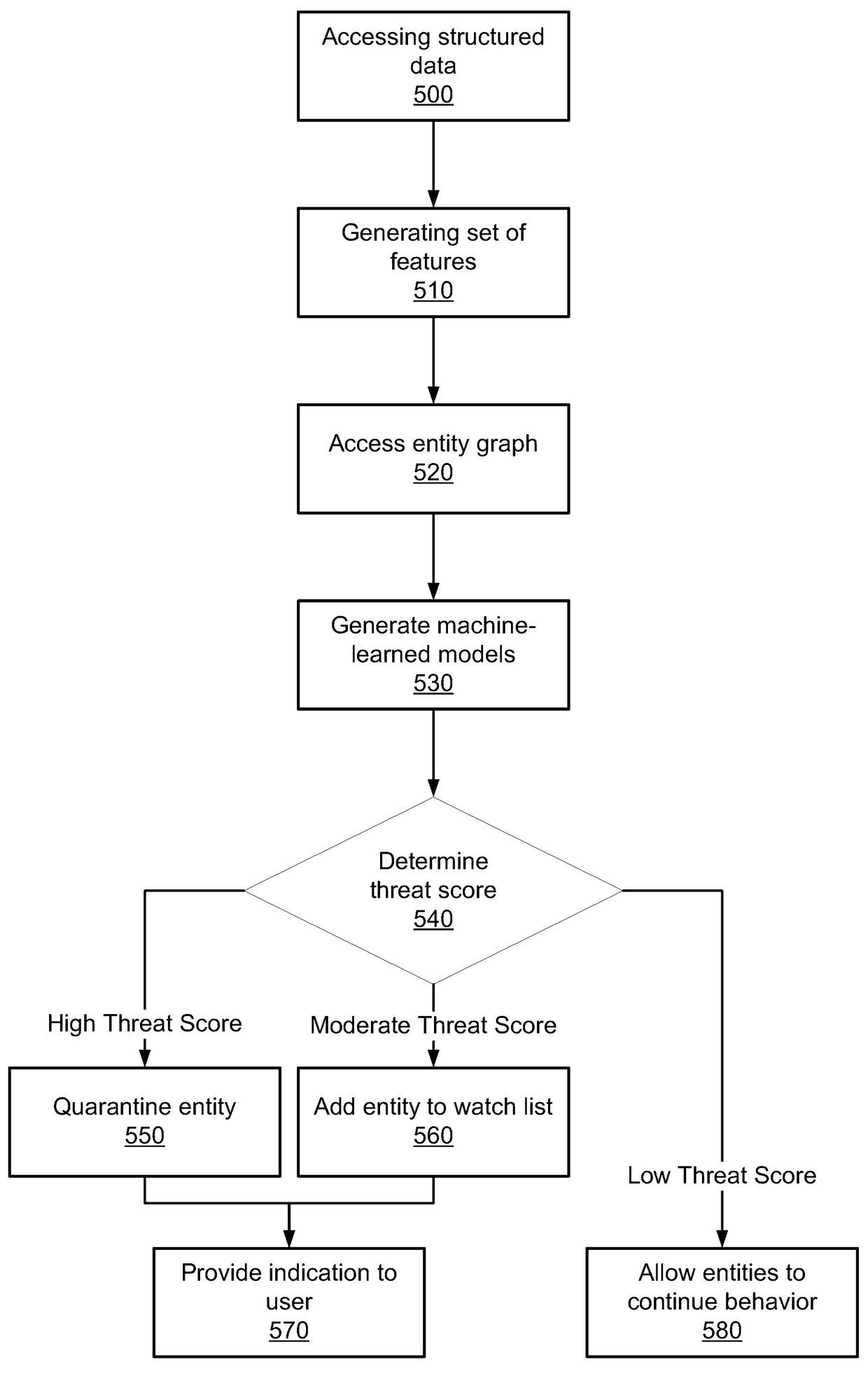
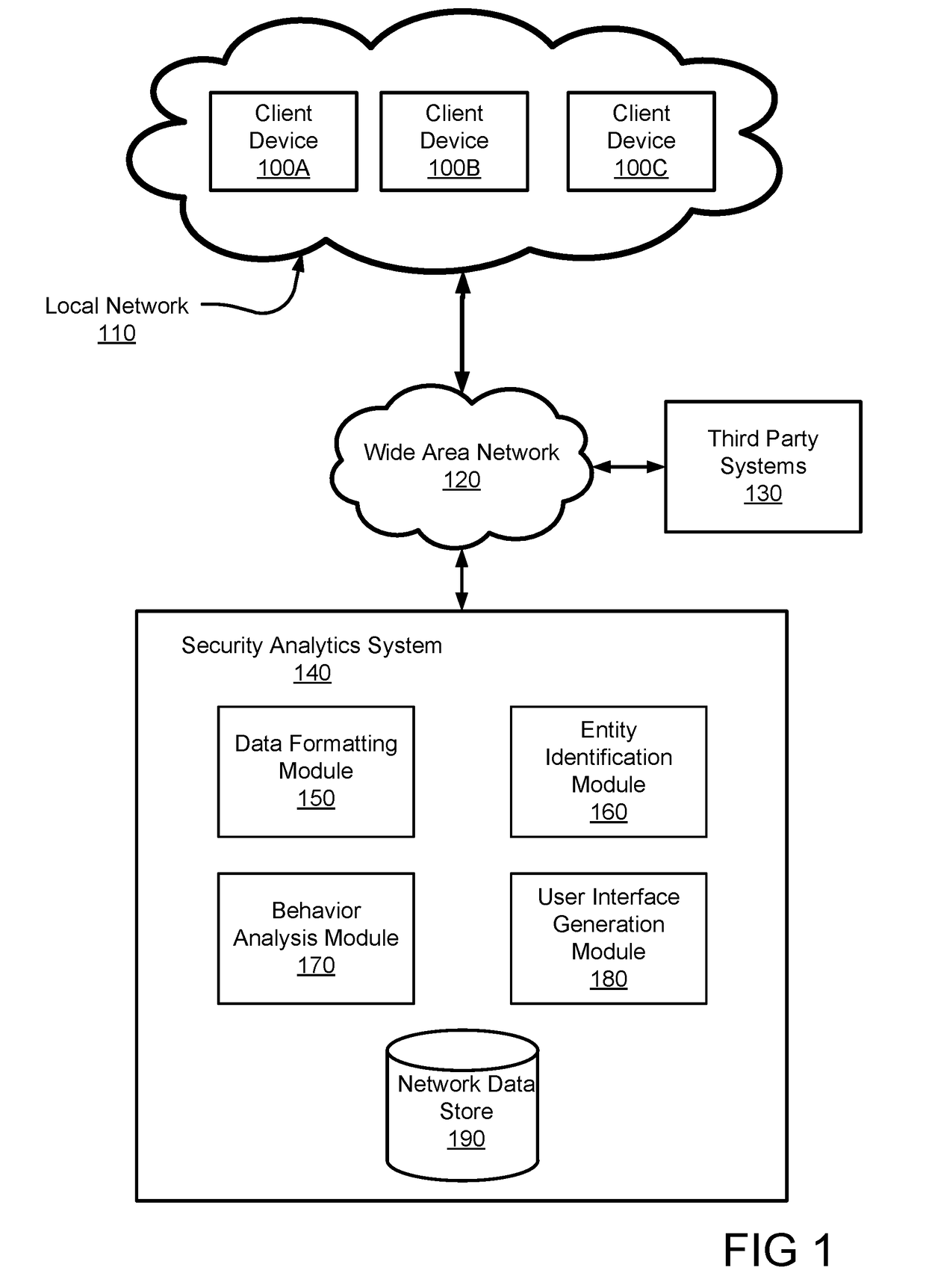
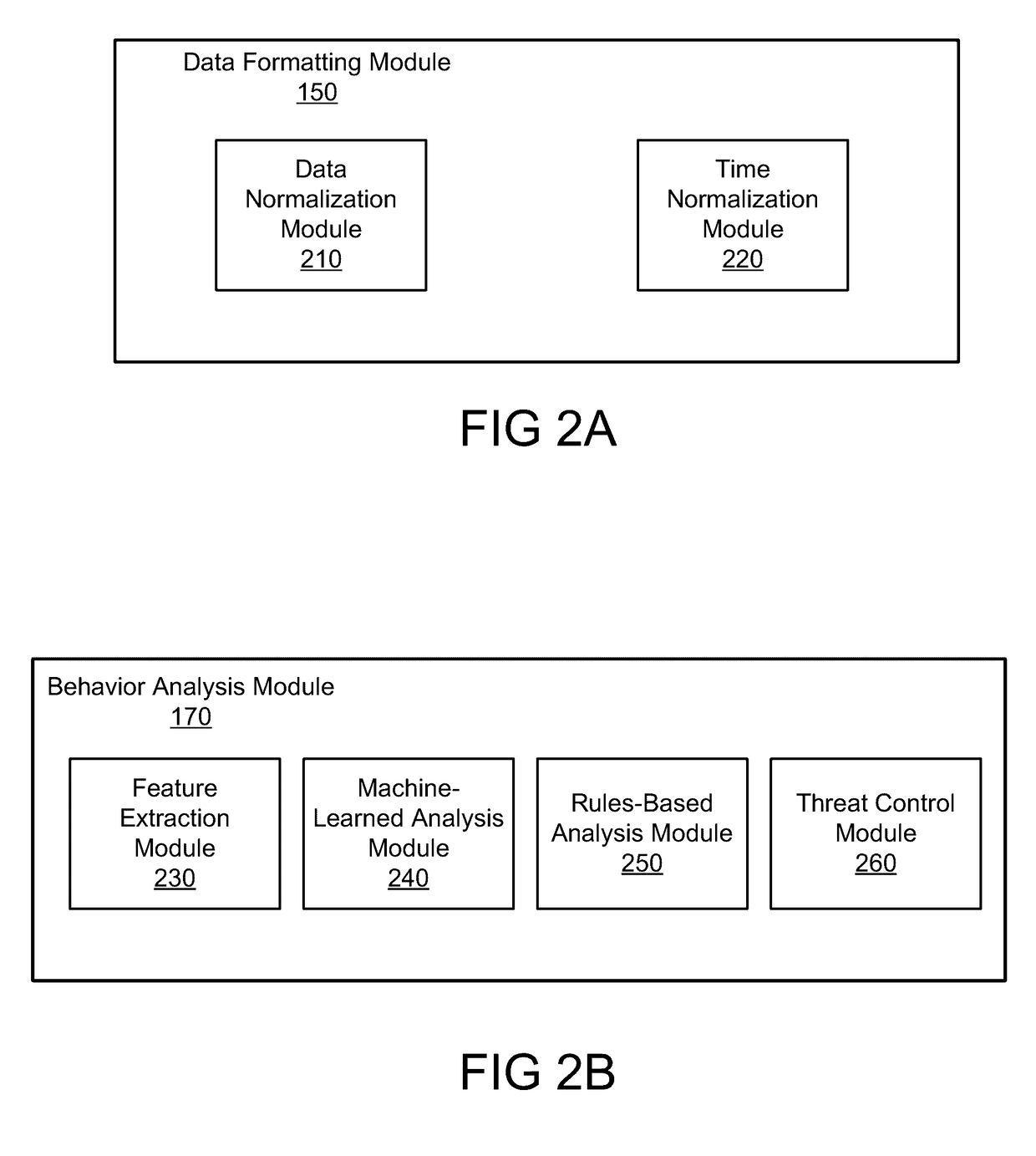
Modeling behavior in a network
Disclosed is a system for detecting security threats in a local network. A security analytics system collects data about entities in the local network. The raw data can be filtered to extract data fields from the raw data that are relevant to detecting security threats in the local network. The filtered data can be converted into structured data that formats the information in the filtered data. The structured data may be formatted based on a set of schema, and can be used to generate a set of features. The security analytics system can use the generated features to build machine-learned models of the behavior of entities in the local network. The security analytics system can use the machine-learned models to generate threat scores representing the likelihood a security threat is present. The security analytics system can provide an indication of the security threat to a user.
Owner:VMWARE INC
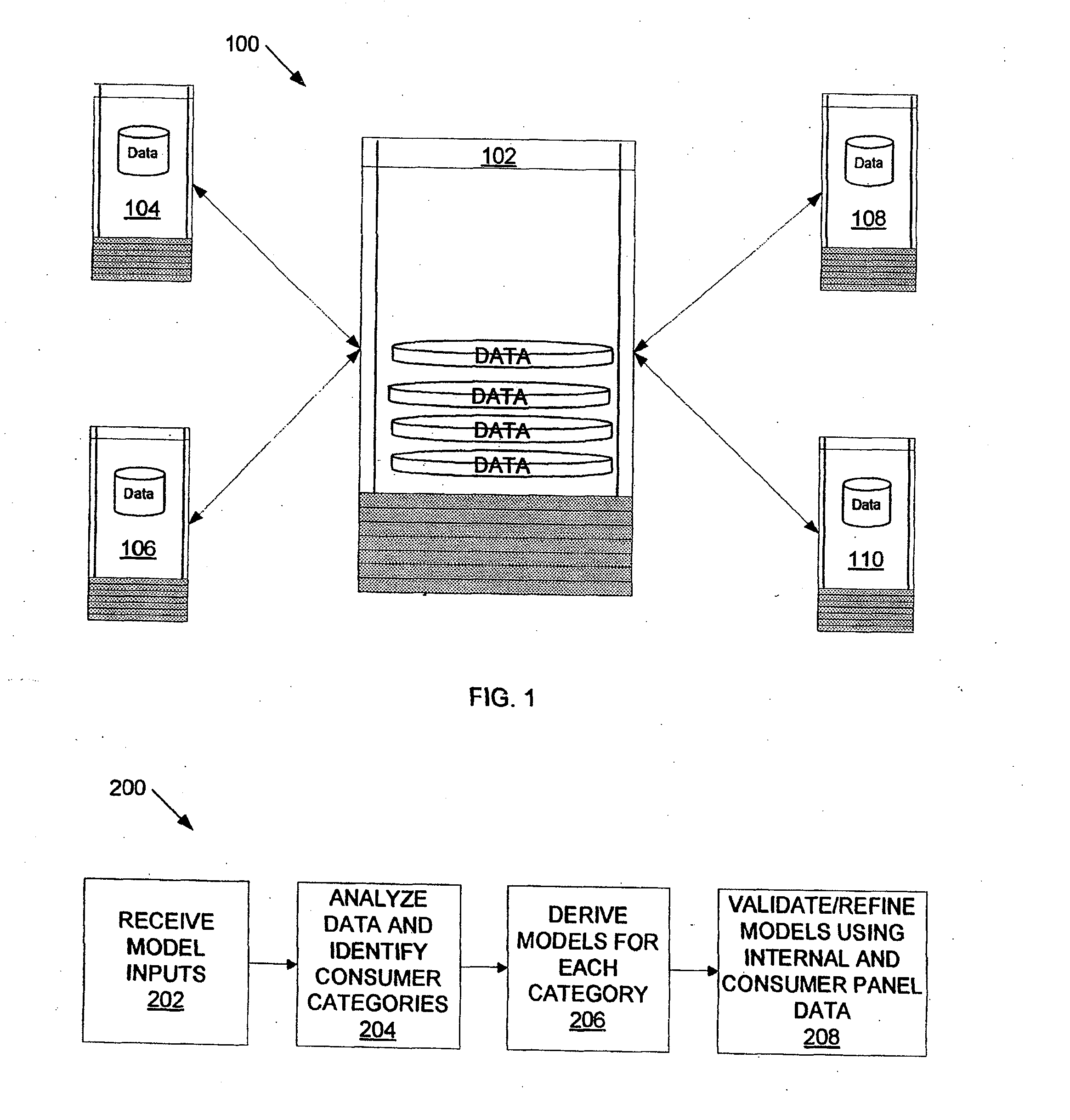
Computer-Based Modeling of Spending Behaviors of Entities
InactiveUS20100250469A1Efficient use ofEfficient managementFinancePayment architectureBehavioral modelingComputer science
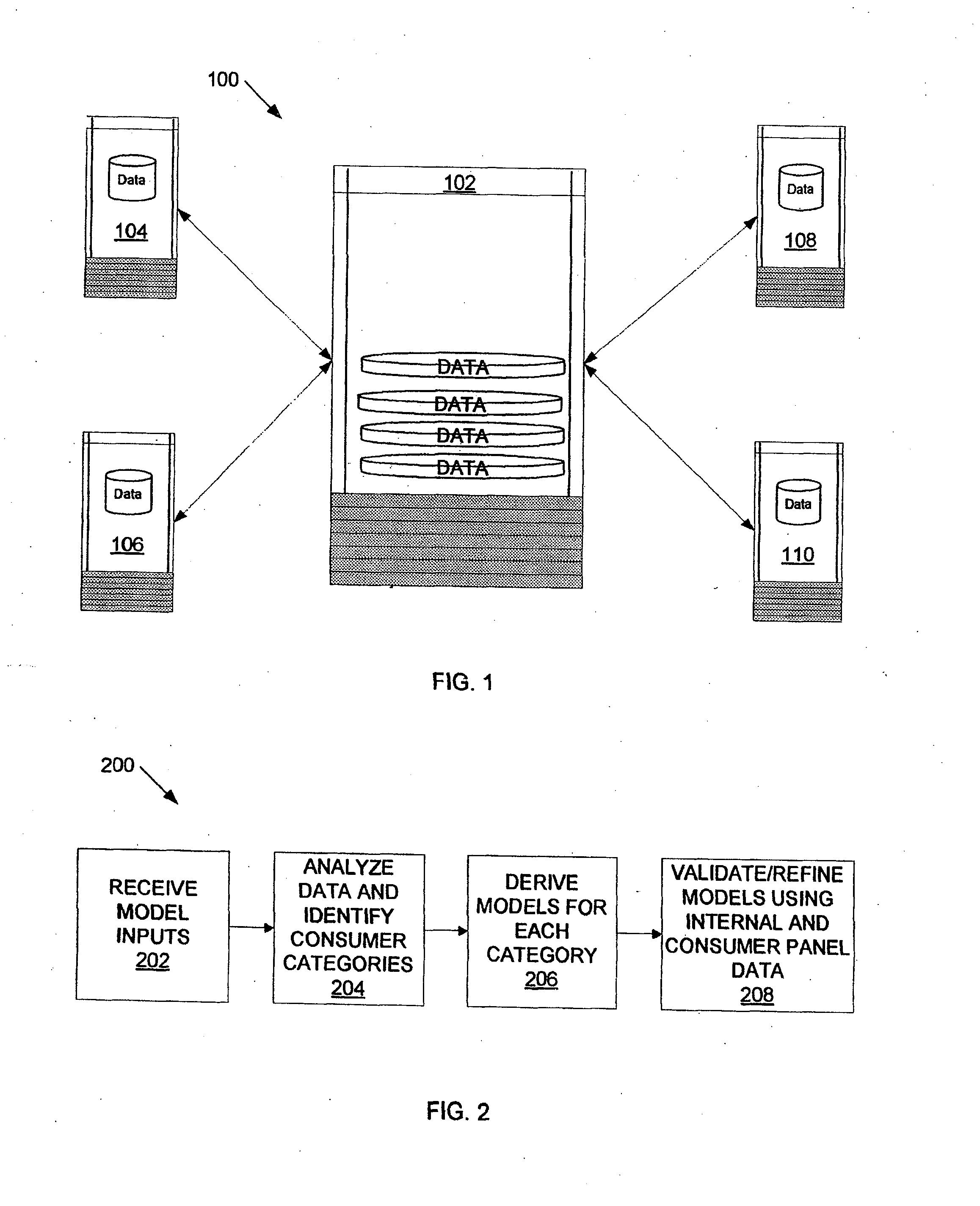
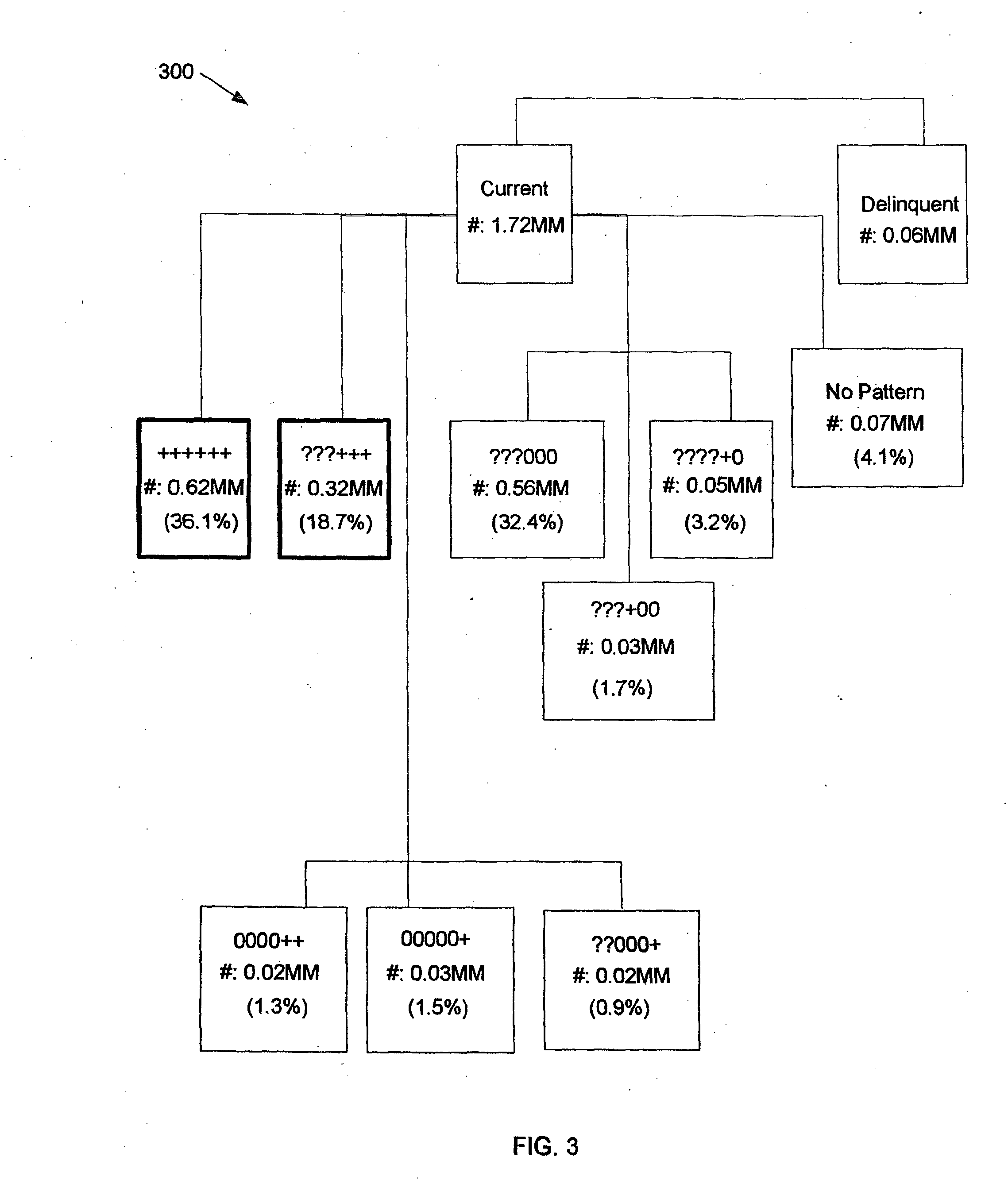
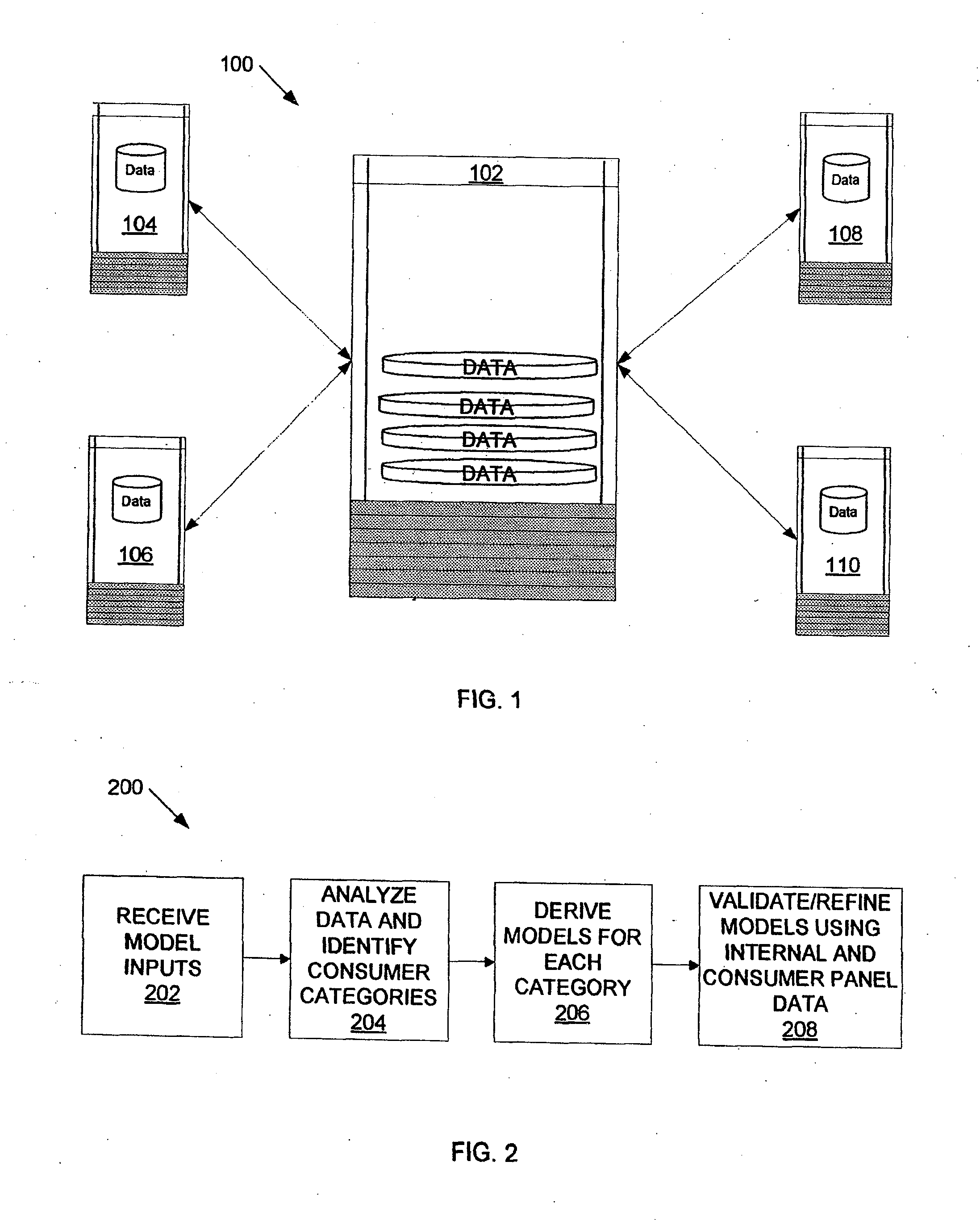
Time series consumer spending data, point-in-time balance information and consumer panel information provide input to a model for consumer spend behavior on plastic instruments or other financial accounts, from which approximations of spending ability and share of wallet may be reliably identified and utilized to promote additional consumer spending.
Owner:EXPERIAN MARKETING SOLUTIONS
Computer-Based Modeling of Spending Behaviors of Entities
InactiveUS20100250434A1Efficient use ofEfficient managementFinancePayment architectureBehavioral modelingData science
Owner:MEGDAL MYLES G +2
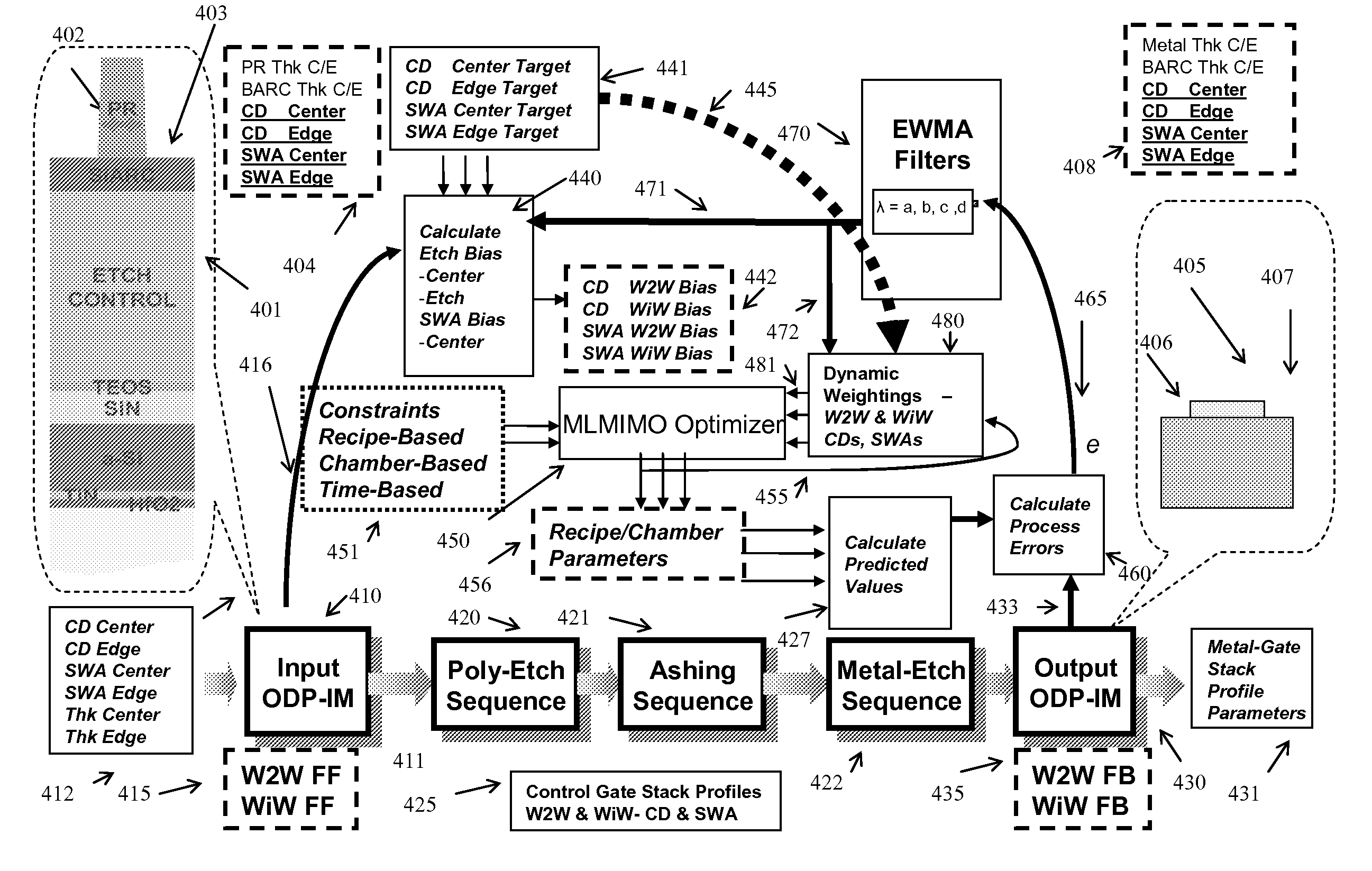
Using Multi-Layer/Multi-Input/Multi-Output (MLMIMO) Models for Metal-Gate Structures
InactiveUS20100036518A1Semiconductor/solid-state device testing/measurementSolid-state devicesMulti inputSequence processing
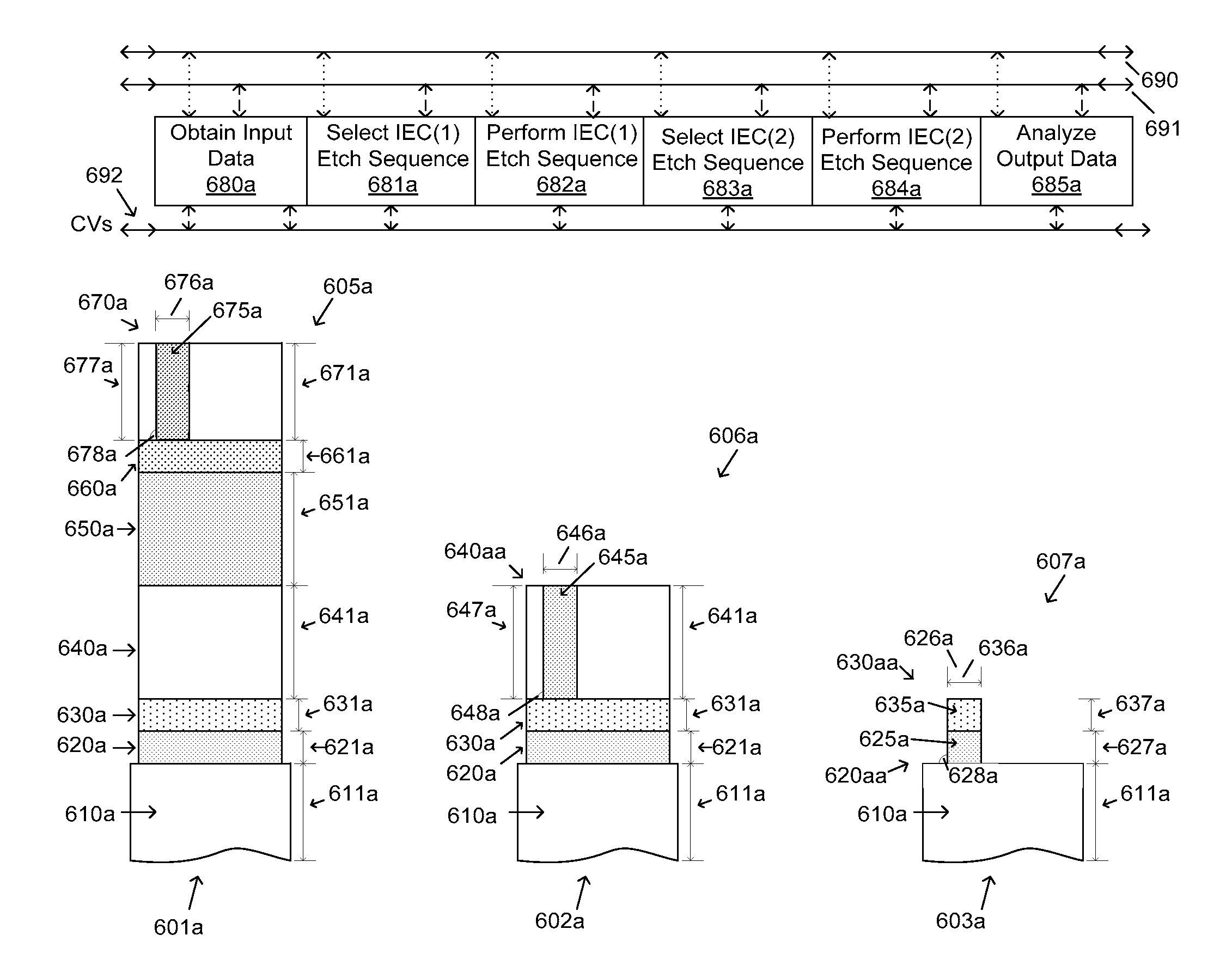
The invention provides a method of processing a wafer using multilayer processing sequences and Multi-Layer / Multi-Input / Multi-Output (MLMIMO) models and libraries that can include one or more measurement procedures, one or more Poly-Etch (P-E) sequences, and one or more metal-gate etch sequences. The MLMIMO process control uses dynamically interacting behavioral modeling between multiple layers and / or multiple process steps. The multiple layers and / or the multiple process steps can be associated with the creation of lines, trenches, vias, spacers, contacts, and gate structures that can be created using isotropic and / or anisotropic etch processes.
Owner:TOKYO ELECTRON LTD
System and method for securing computer system against unauthorized access
InactiveUS20100229230A1Security breachDigital data processing detailsUser identity/authority verificationComputer usersIdentity theft
The present invention described secures a computer account against unauthorized access caused as a result of identity-theft, and insider-espionage using artificial intelligence and behavioral modeling methods. The present invention has the ability to detect intruders or impersonators by observing “suspicious” activity under a computer account. When it sees such suspicious behavior, it uses artificial intelligence to authenticate the suspect by interrogation. The present invention asks the suspect questions that only the legitimate computer account owner can verify correctly. If the suspect fails the interrogation, that proves that he / she is an impersonator and therefore further access to the computer account is denied immediately. On the other hand if the suspect passes, access to the computer account is restored. The present invention uses a Programmable Artificial Intelligence Engine (PAIE) to interact with computer users in human natural language. The PAIE can also be programmed to suit other applications where natural language interaction with humans is helpful.
Owner:EDEKI OMON AYODELE +2
System and method for securing computer system against unauthorized access
ActiveUS7647645B2Security breachMemory loss protectionError detection/correctionComputer usersIdentity theft
Owner:EDEKI OMON AYODELE +2
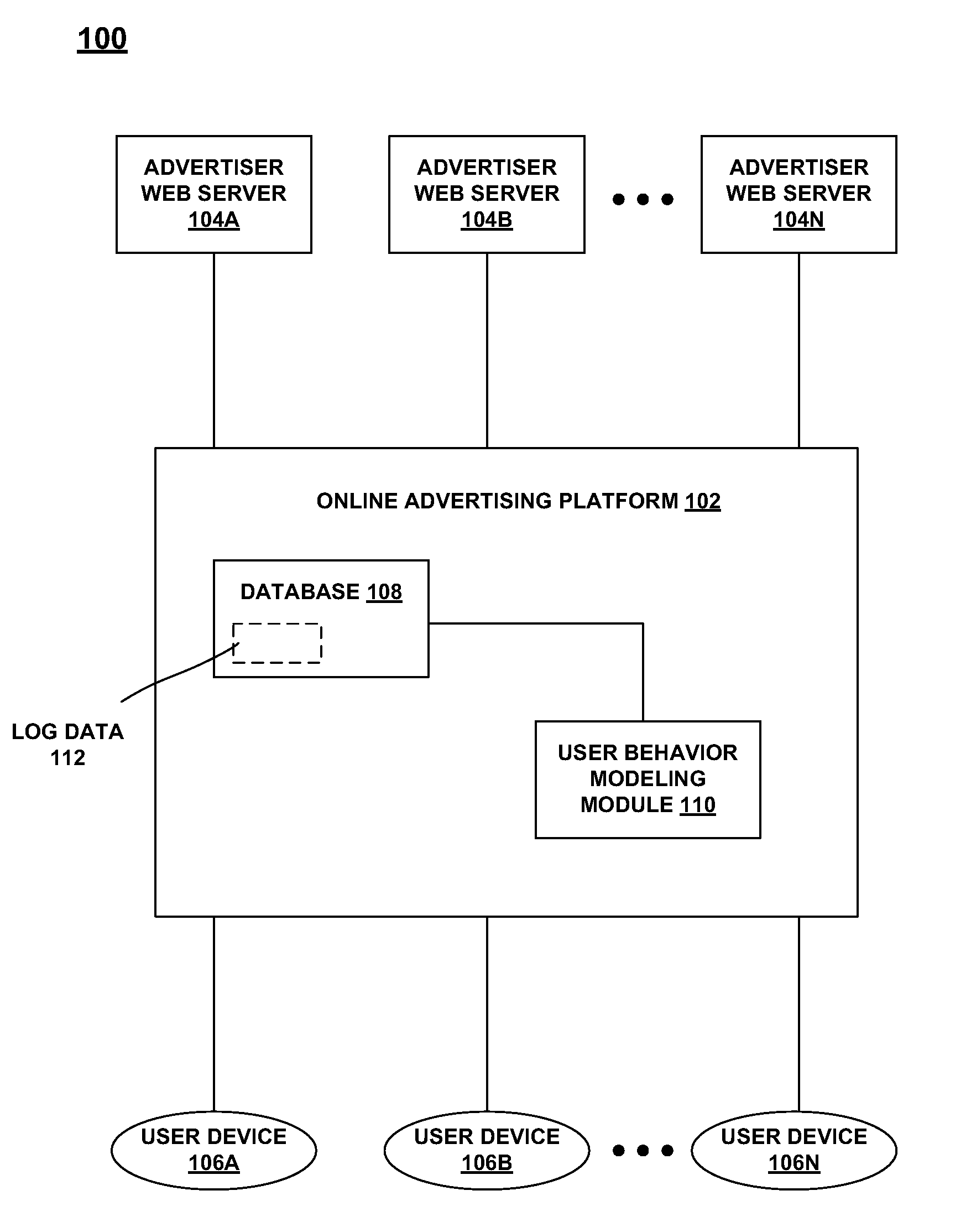
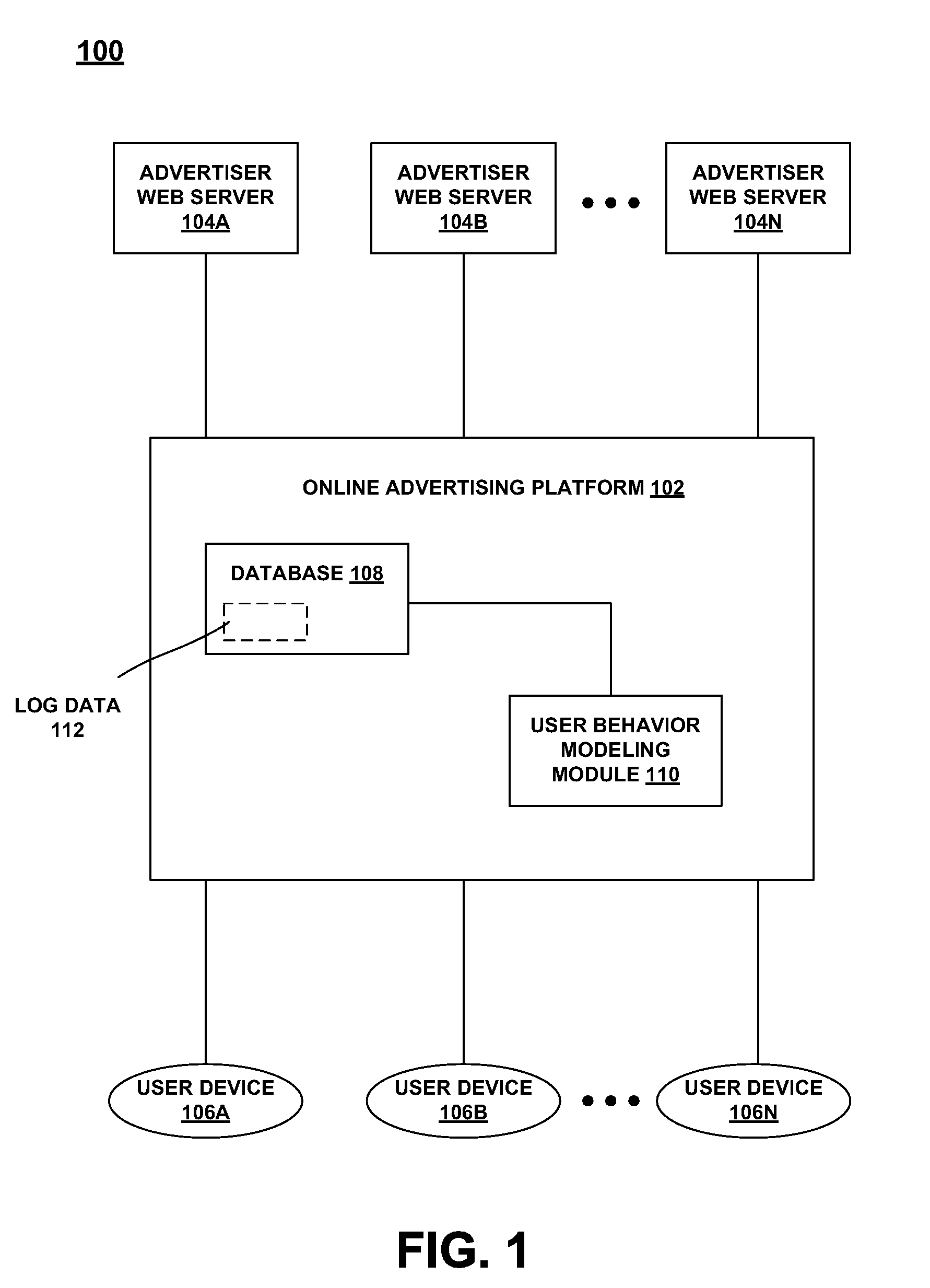
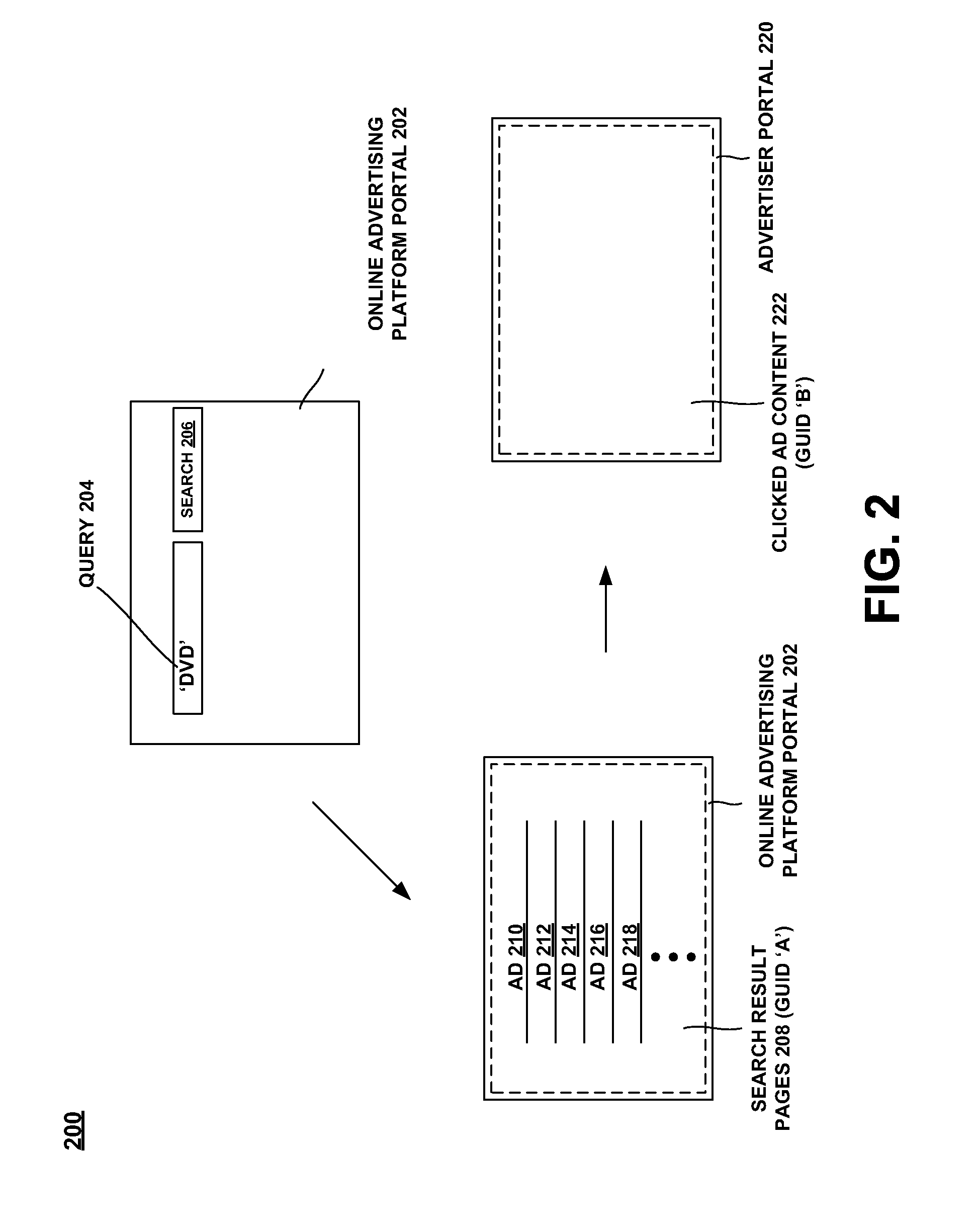
User advertisement click behavior modeling
ActiveUS20090299967A1Digital data processing detailsSpecial data processing applicationsOnline advertisingBehavioral modeling
Described herein is technology for, among other things, mining similar user clusters based on user advertisement click behaviors. The technology involves methods and systems for mining similar user clusters based on log data available on an online advertising platform. By building a user linkage representation based on one or more attributes from the log data, the similar user clusters can be harvested in more efficient manner.
Owner:ZHIGU HLDG
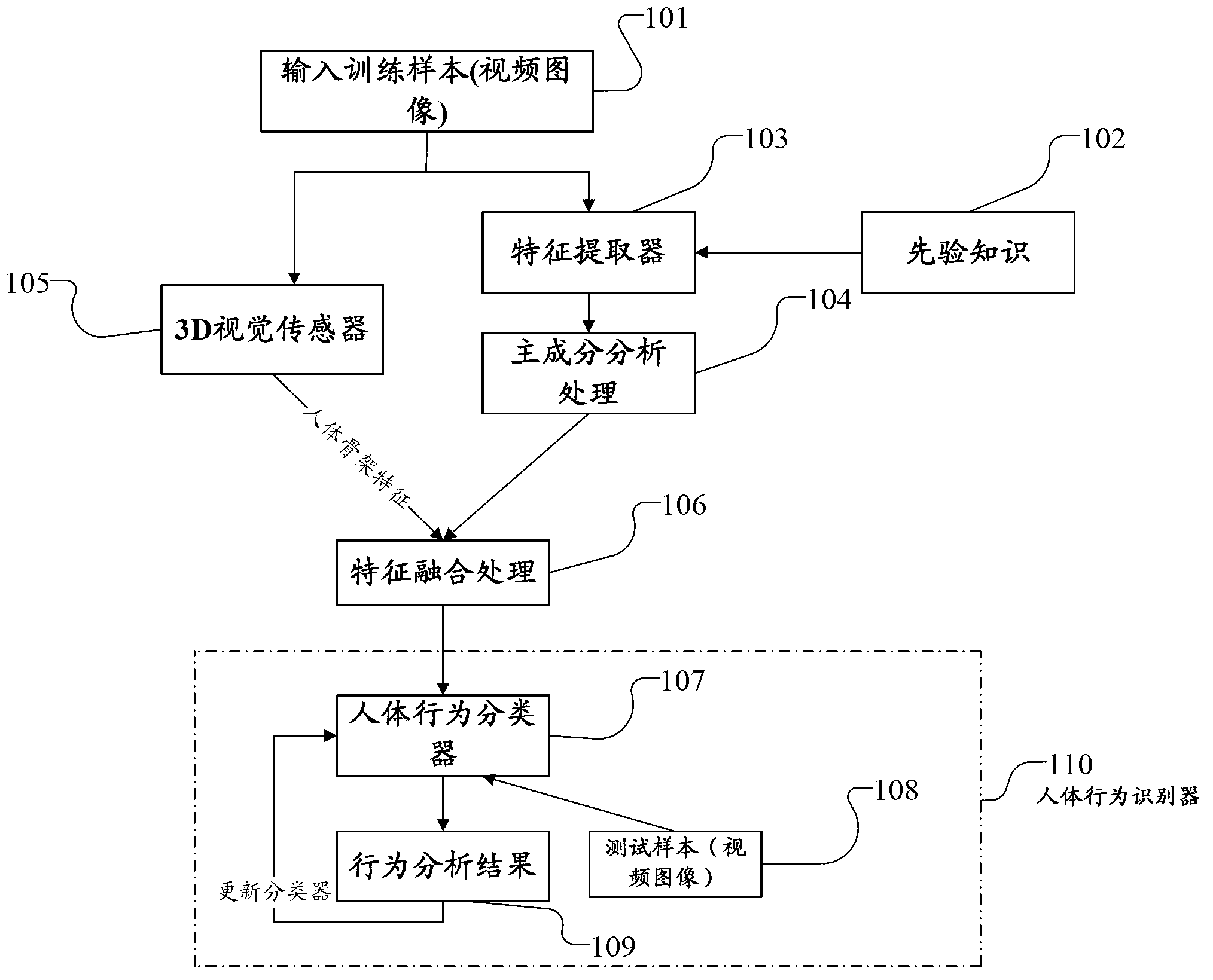
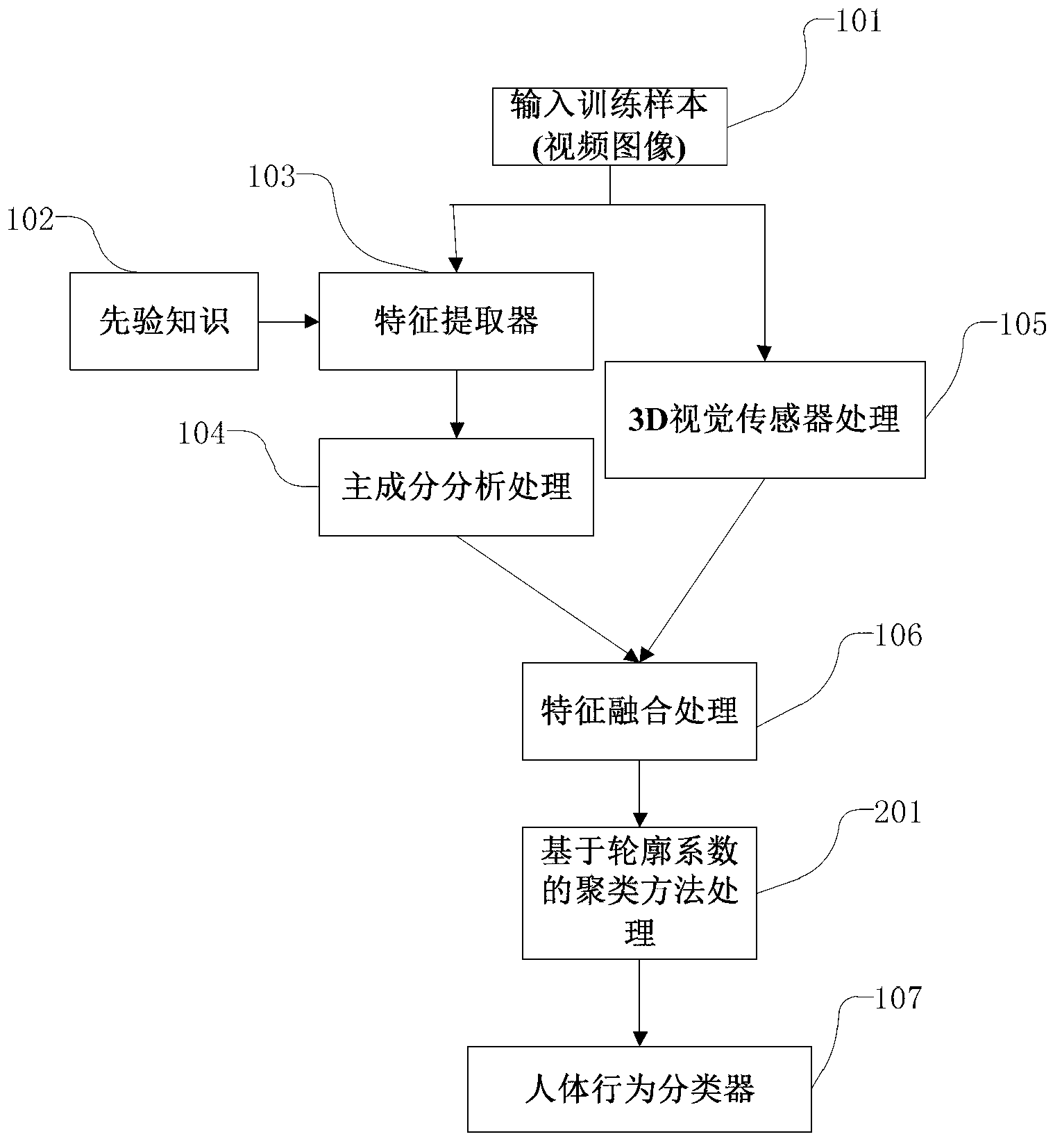
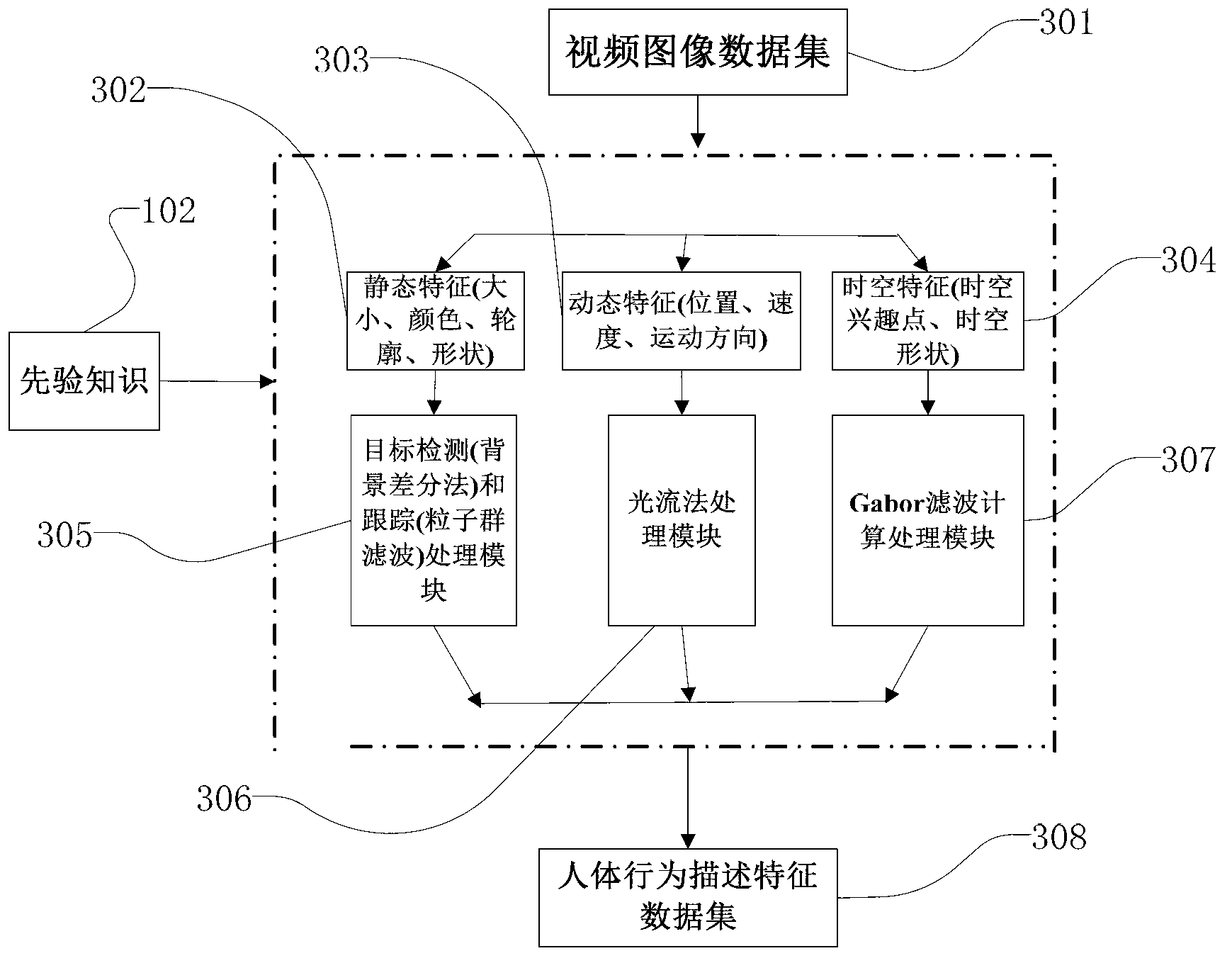
Human body behavioral modeling identification method based on priori knowledge cluster in computer system
ActiveCN103268495ASelf-learning abilityThe number of accurate classifiersCharacter and pattern recognitionHuman bodyPattern recognition
The invention relates to a human body behavioral modeling identification method based on a priori knowledge cluster in a computer system. The method comprises the steps of human body behavioral modeling processing and human body behavioral identification processing. By the adoption of human body behavioral modeling identification method based on the priori knowledge cluster in the computer system, a constructed modeling system has a self-learning capacity and can continuously perfect a classifier along with the classification of observed samples. In cluster distribution obtained in the process of human body behavioral modeling, if outliers exist, the outliers serve as an abnormal behavioral model. When the system is designed, precaution is given as required, the method has great realistic meanings, important influence of priori knowledge on a human body behavioral identification result is considered, an improved cluster method is adopted to model and identify the human body, and foundation can be laid for identifying abnormal behaviors. The method is simple and efficient, can accurately identify different behavioral modes, and has good expandability. Working performance is reliable and stable, and the application range is wide.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Identity authentication method based on Web user behavior model
ActiveCN102970289AGuarantee property securityImprove accuracyTransmissionDirected graphWeb page clustering
An identity authentication method based on a Web user behavior model comprises performing behavior modeling by collecting Web user web page browsing records on a client-side and depicting behavior characteristics of a user within a certain time period; performing web page clustering with web page contents and time series of the Web user accessing Web pages as the standard, and enabling formed classes to serve as behavior model nodes; enabling Web pages skip links among the nodes (the Web page classes) to be directed edges, and enabling linking number to be edge weight; building a directed graph with an edge weight value to serve as a behavior model graph of the Web user, and converting to a markov model. The identity authentication method can be combined with an existing Web user identity authentication mode, user identity is authenticated from two aspects, the authentication accuracy rate is improved, and property safety of the Web user is guaranteed.
Owner:TONGJI UNIV
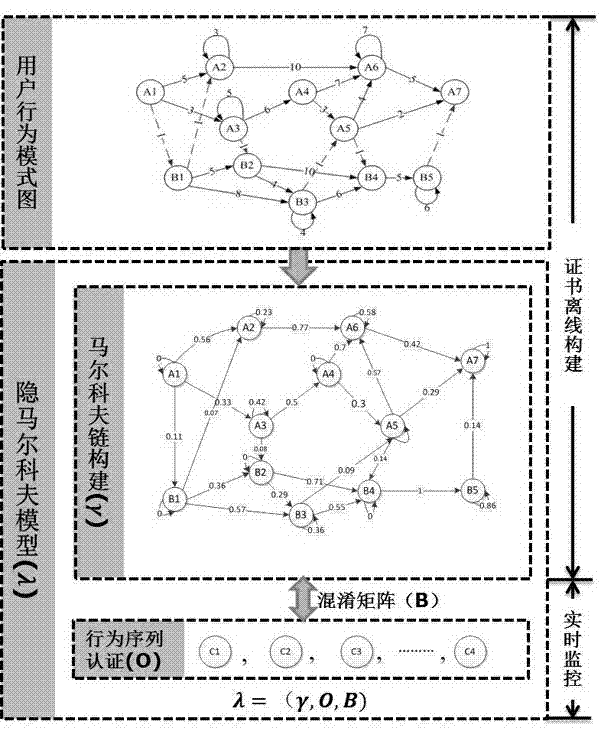
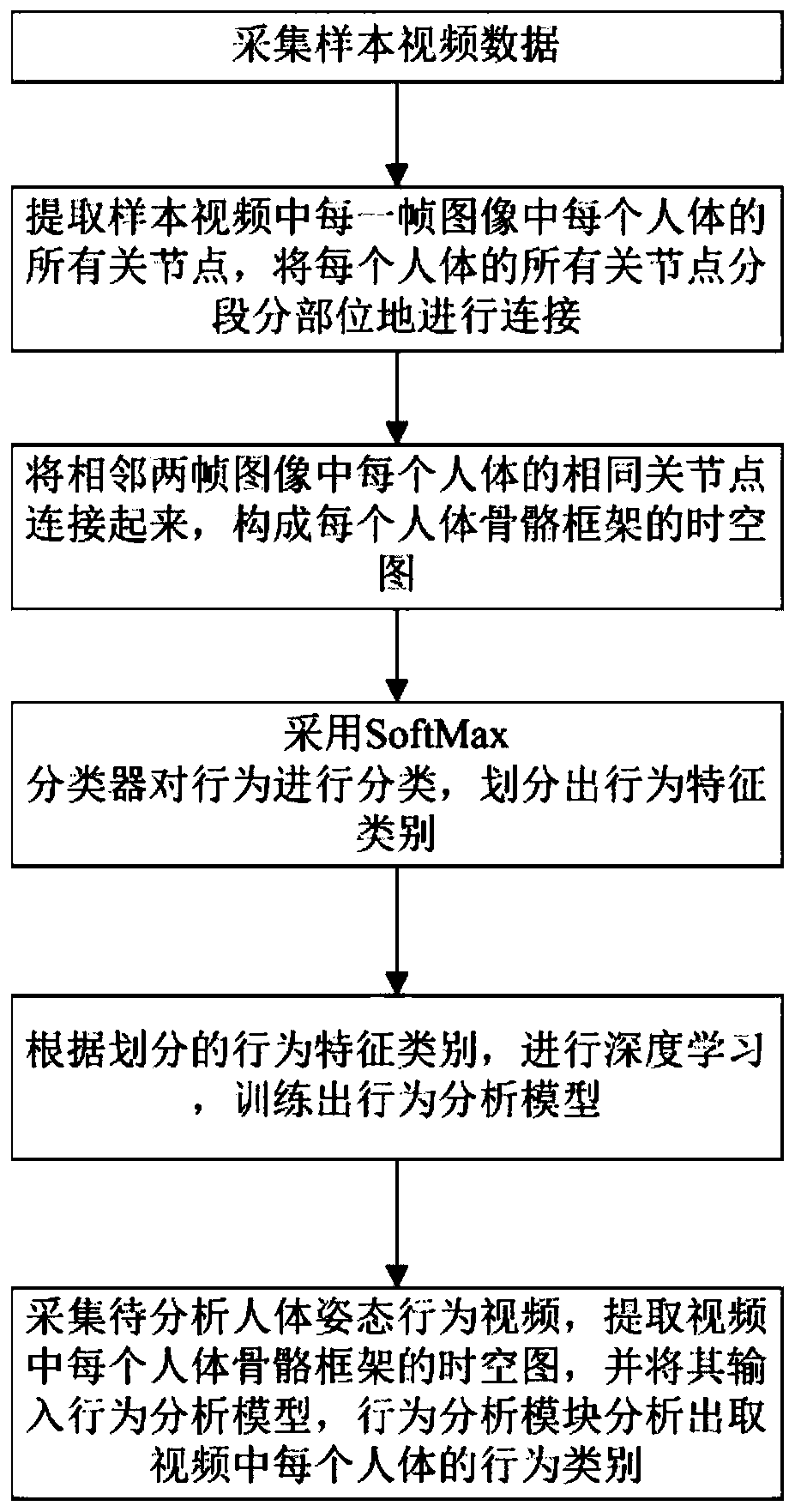
Human body posture behavior intelligent analysis and recognition method
The invention discloses a human body posture behavior intelligent analysis and recognition method. The method comprises the following steps: collecting sample video data; extracting all joint points of each human body in each frame of image in the sample video, and connecting all joint points of each human body in a segmented and partial manner; connecting the same joint point of each human body in two adjacent frames of images to form a space-time diagram of each human body skeleton framework; classifying the behaviors by adopting a SoftMax classifier, and dividing behavior feature categories; performing deep learning according to the divided behavior feature categories, and training a behavior analysis model; collecting a human body posture behavior video to be analyzed, extracting a space-time diagram of each human body skeleton framework in the video, inputting the space-time diagrams into the behavior analysis model, and analyzing the behavior category of each human body in the video by the behavior analysis module. Human body posture behaviors are analyzed and recognized through feature extraction, behavior modeling and behavior classification, and the accuracy is high.
Owner:哈工大机器人义乌人工智能研究院
Adaptive Recipe Selector
ActiveUS20120252141A1Semiconductor/solid-state device testing/measurementElectric discharge tubesMulti inputEngineering
The invention provides a method of processing a wafer using Ion Energy (IE)-related multilayer process sequences and Ion Energy Controlled Multi-Input / Multi-Output (IEC-MIMO) models and libraries that can include one or more measurement procedures, one or more IEC-etch sequences, and one or more Ion Energy Optimized (IEO) etch procedures. The IEC-MIMO process control uses dynamically interacting behavioral modeling between multiple layers and / or multiple IEC etch sequences. The multiple layers and / or the multiple IEC etch sequence can be associated with the creation of lines, trenches, vias, spacers, contacts, and gate structures that can be created using IEO etch procedures.
Owner:TOKYO ELECTRON LTD
Creating Multi-Layer/Multi-Input/Multi-Output (MLMIMO) Models for Metal-Gate Structures
ActiveUS20100036514A1Polycrystalline material growthSemiconductor/solid-state device testing/measurementMulti inputSequence processing
The invention provides a method of processing a wafer using multilayer processing sequences and Multi-Layer / Multi-Input / Multi-Output (MLMIMO) models and libraries that can include one or more measurement procedures, one or more Poly-Etch (P-E) sequences, and one or more metal-gate etch sequences. The MLMIMO process control uses dynamically interacting behavioral modeling between multiple layers and / or multiple process steps. The multiple layers and / or the multiple process steps can be associated with the creation of lines, trenches, vias, spacers, contacts, and gate structures that can be created using isotropic and / or anisotropic etch processes.
Owner:TOKYO ELECTRON LTD
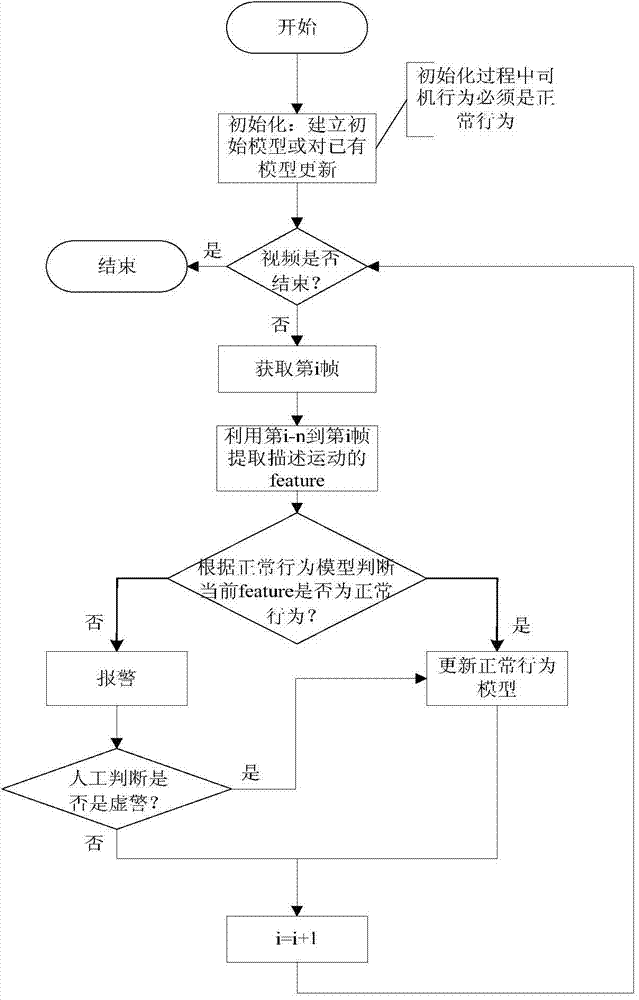
Detection method of driver's abnormal behavior modeled based on online behavior
InactiveCN104504400ALess error rateImprove stabilityCharacter and pattern recognitionFeature extractionBehavioral modeling
The invention relates to a detection method of a driver's abnormal behavior modeled based on an online behavior and belongs to the technical field of image identification and monitoring. The method is based on a video analysis technology, the driver's abnormal behavior is detected by modeling the driver's normal behavior, and the method mainly comprises the following steps of: firstly, initializing and creating an initial model or updating the existing model; secondly, extracting driver's behavior characteristics in a driving process; thirdly, judging whether the driver's behavior is normal according to the initial model and the driver's behavior characteristics; fourthly, updating the model. The detection method is characterized in that the abnormal behavior is detected by a novelty detection way, multiple normal and abnormal behaviors can be treated by adopting a multi-mode modeling method, and false alarms are eliminated by a manual labeling method, thus the steadiness of the solution is increased and the error rate of the solution is reduced.
Owner:CHONGQING INST OF GREEN & INTELLIGENT TECH CHINESE ACADEMY OF SCI
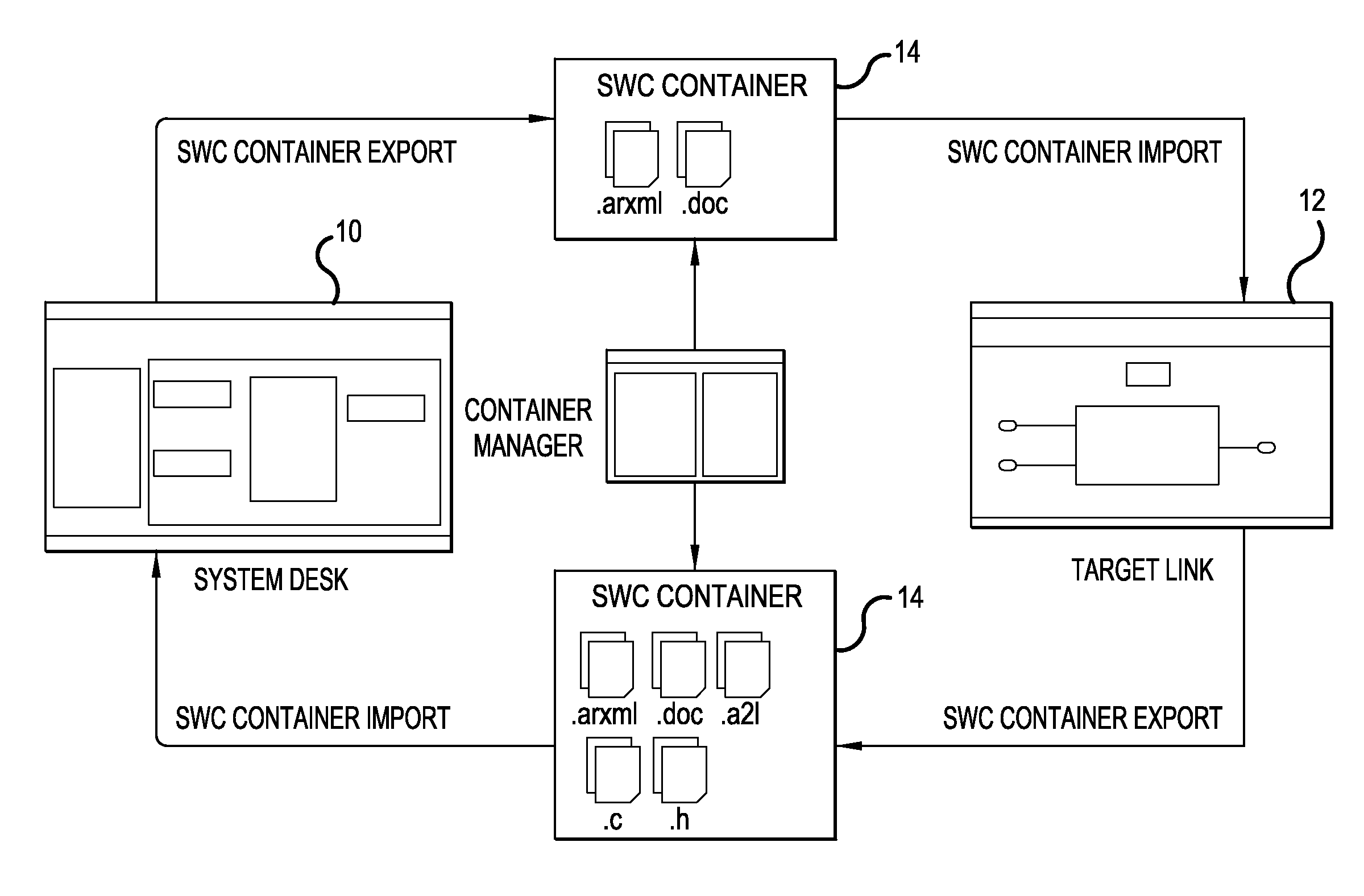
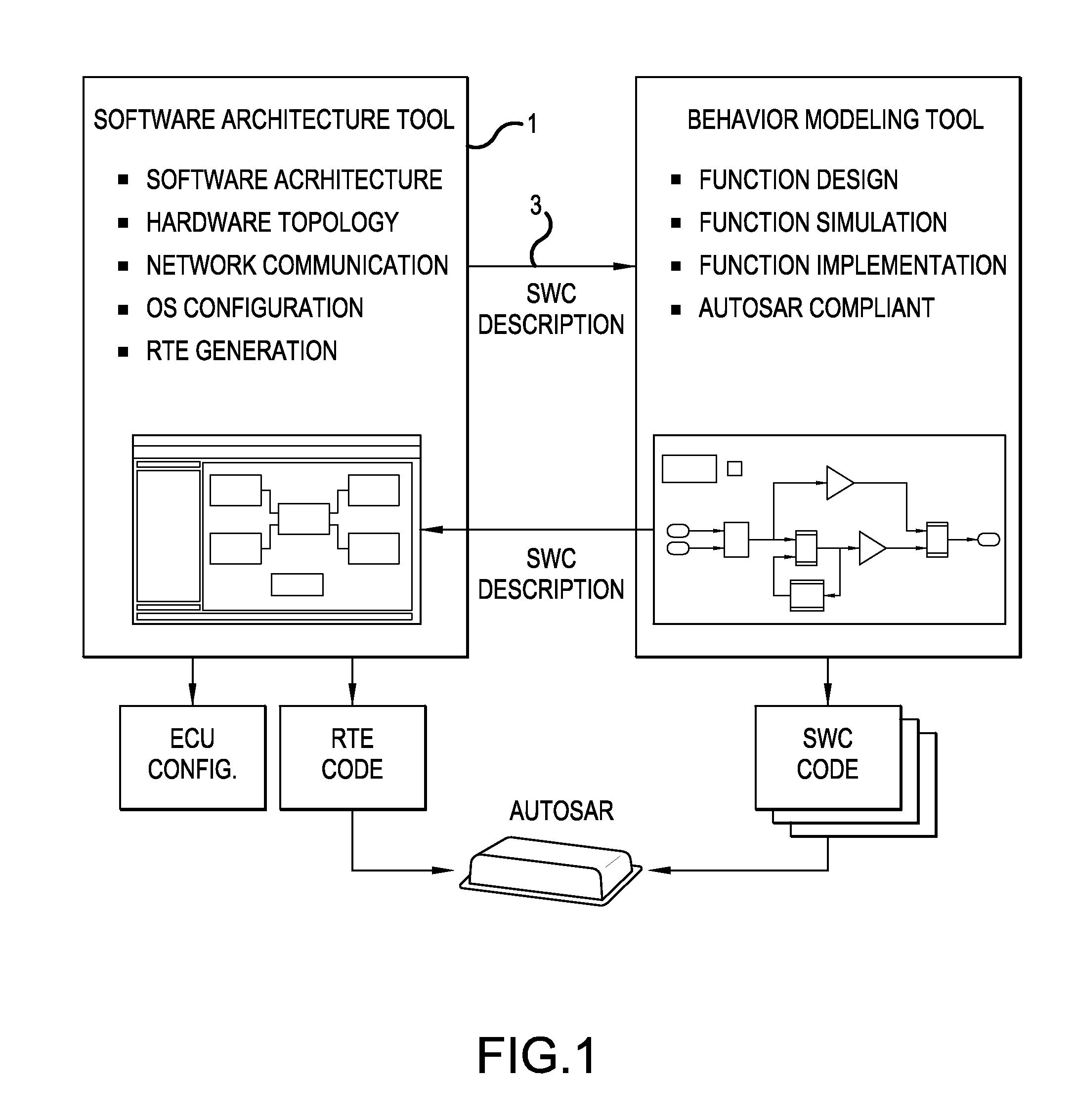
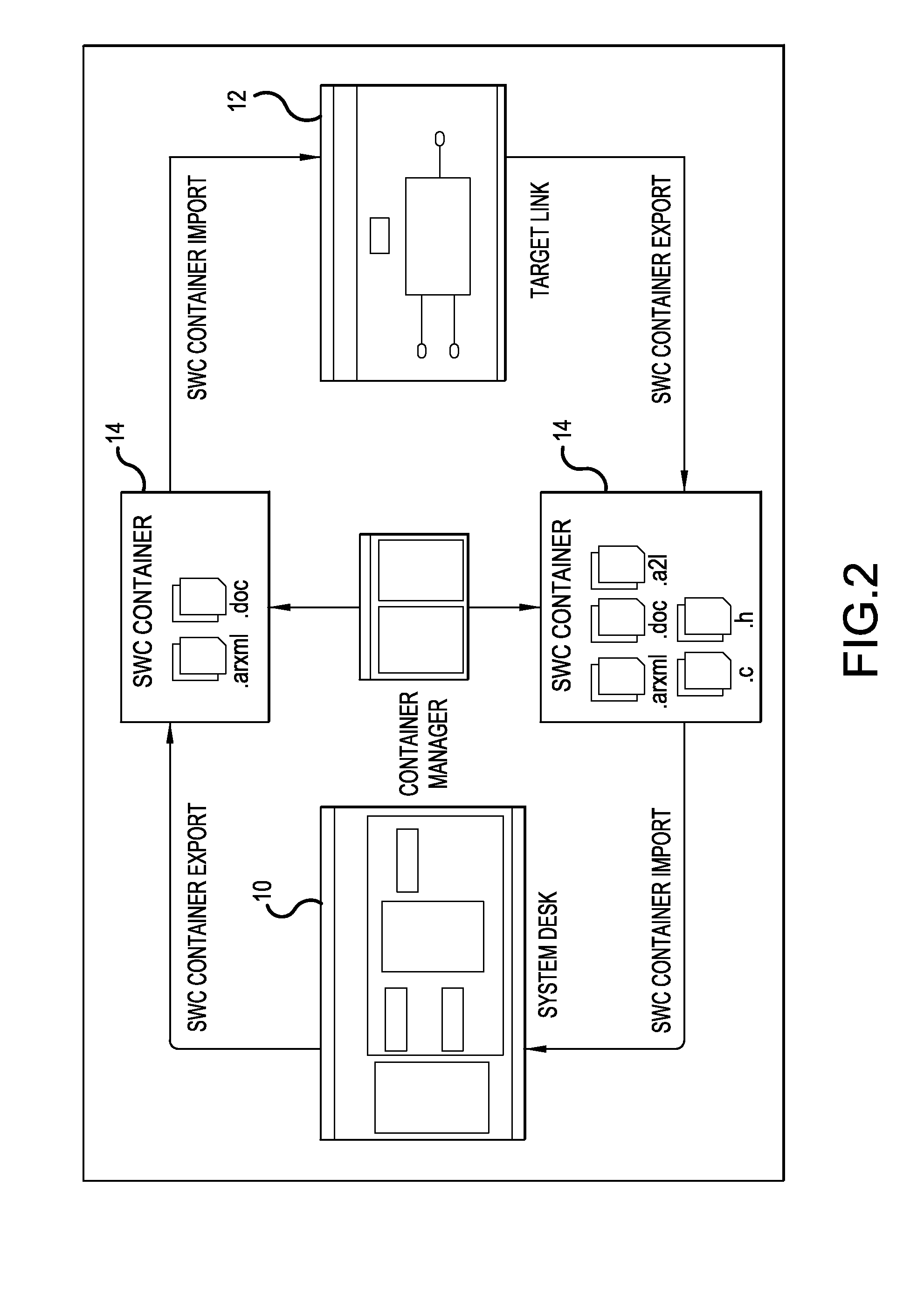
Exchange of files and meta-information between system design tools and behavior modeling tools and/or simulators for the creation of ECU software
ActiveUS20130073063A1Simplify management of fileSimplified managementComputer controlSimulator controlGraphicsSystems design
A computer project management system and method for the creation of an electronic control unit software is provided. The system has a software architecture tool configured to design a graphical model of an electronic control unit for a motor vehicle. A behavior model tool converts the graphical model into a computer readable production code. A software container has a file generated based on the electronic control unit. A container manager compares the software container with a prior software container during the importation or exportation of the software container to or from the software architecture tool or the behavior model tool, and a comparison list is generated indicating whether interface modifications for the electronic control unit were made. The comparison list is then displayed to a user on a display screen.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
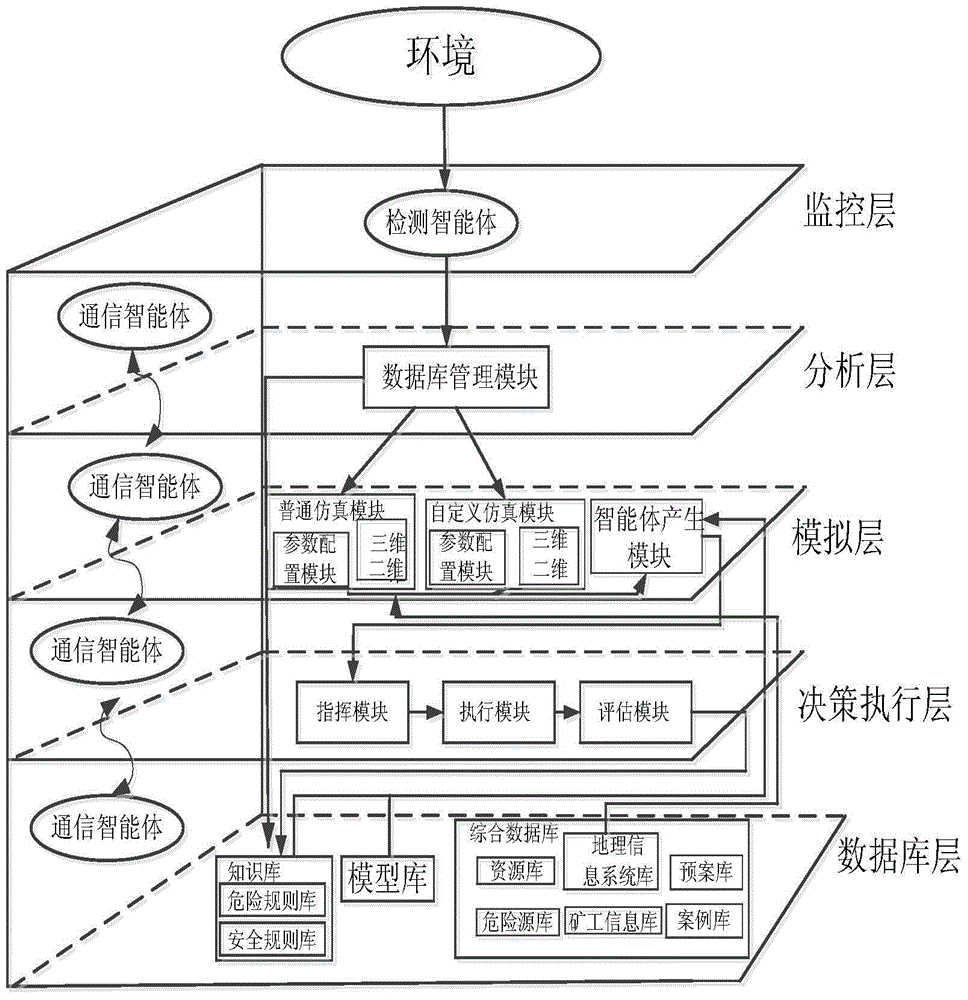
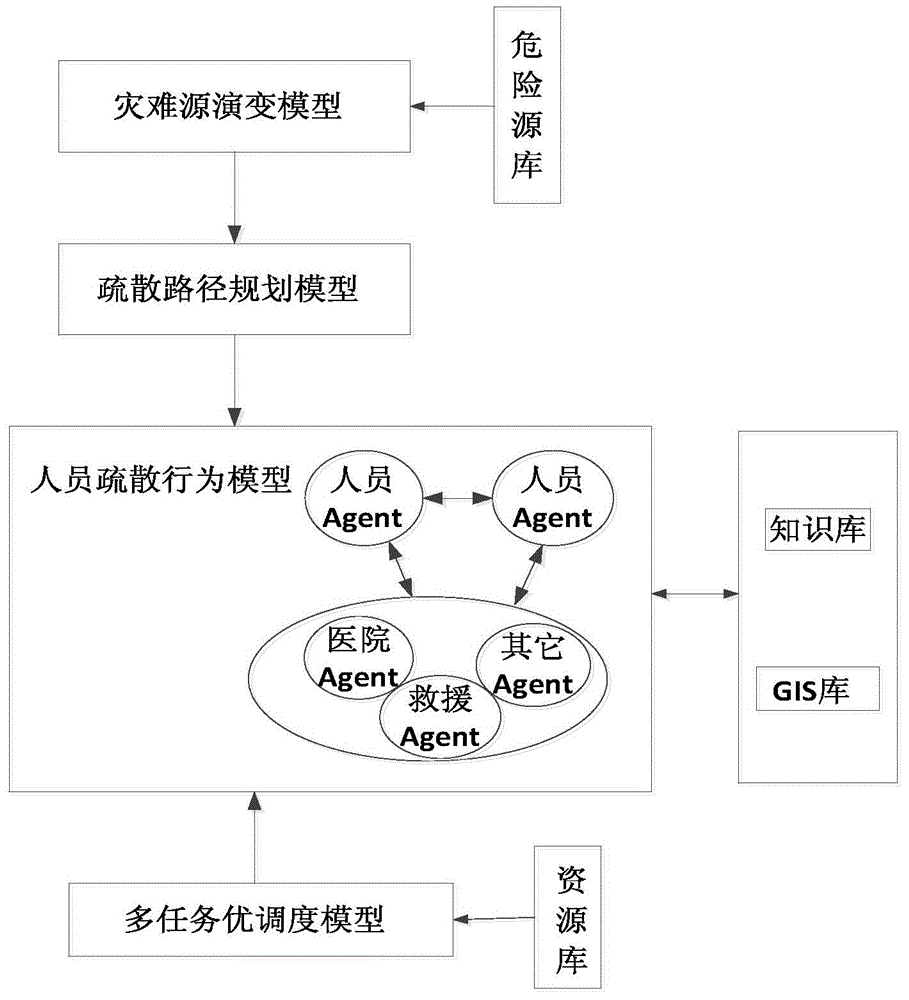
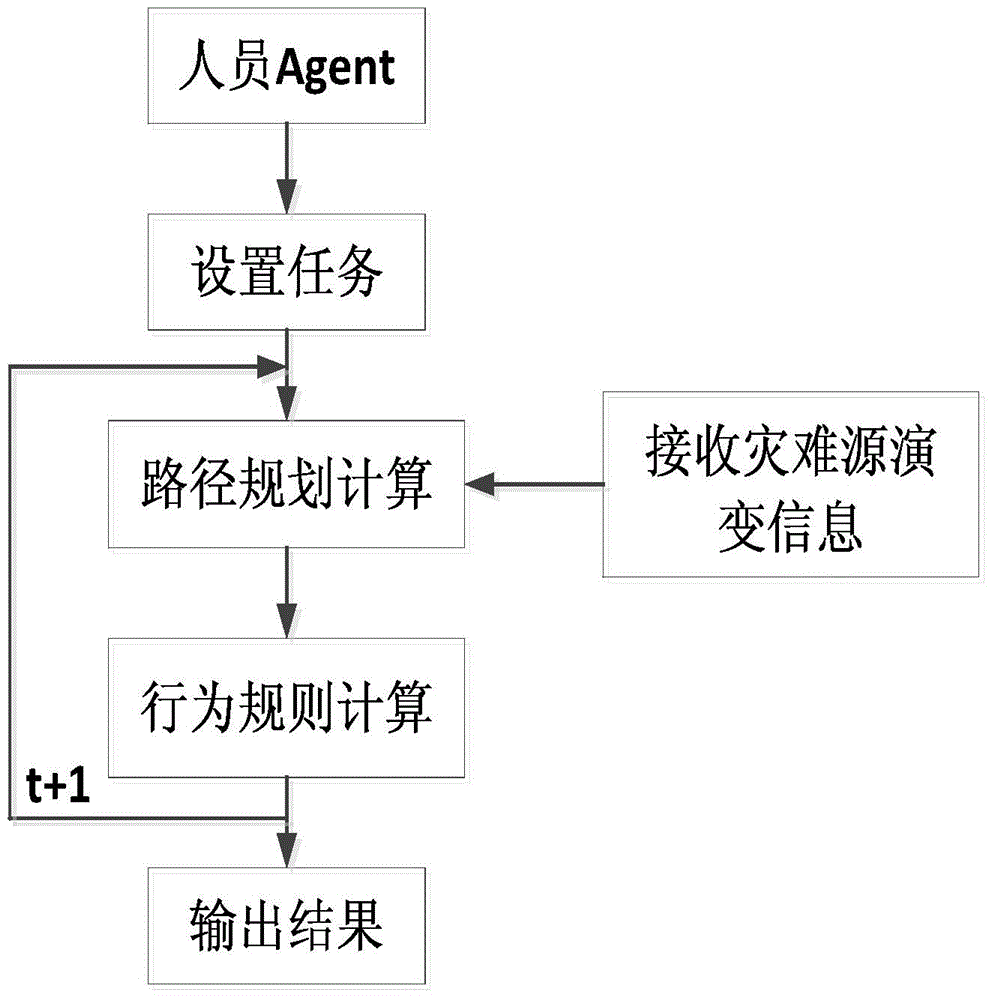
Multi-agent-based virtual miner safety behavior modeling and emergency simulation system
InactiveCN104317637AReduce distanceSafe escape routeSoftware simulation/interpretation/emulationIntegrated databaseBehavioral modeling
The invention discloses a multi-agent-based virtual miner safety behavior modeling and emergency simulation system. The system is characterized by comprising a monitoring layer, an analysis layer, a simulation layer, a decision enforcement layer and a database layer, wherein a communication agent is responsible for communication between every two layers; the monitoring layer consists of various detection agents; the analysis layer consists of a database management module; the simulation layer comprises an ordinary simulation module, a self-defined simulation module and an agent generation module; the decision enforcement layer comprises a commanding module, an enforcement module and an evaluation module; the database layer comprises an integrated database, a model base and a knowledge base. According to the system, an evolution trend during the occurrence of various disasters in a mine and evacuation behaviors of underground miners under a real condition can be simulated in a simulation environment, the system can be extended according to different environments of different mines in a self-defined way, a guiding basis is provided for the underground emergency evacuation of the mines in the real condition, and the safety production efficiency and the scientific management level of a mine environment are greatly improved.
Owner:ANHUI UNIV OF SCI & TECH
Human driving behavior modeling system using machine learning
PendingUS20190164007A1Autonomous decision making processDetection of traffic movementPattern recognitionBehavioral modeling
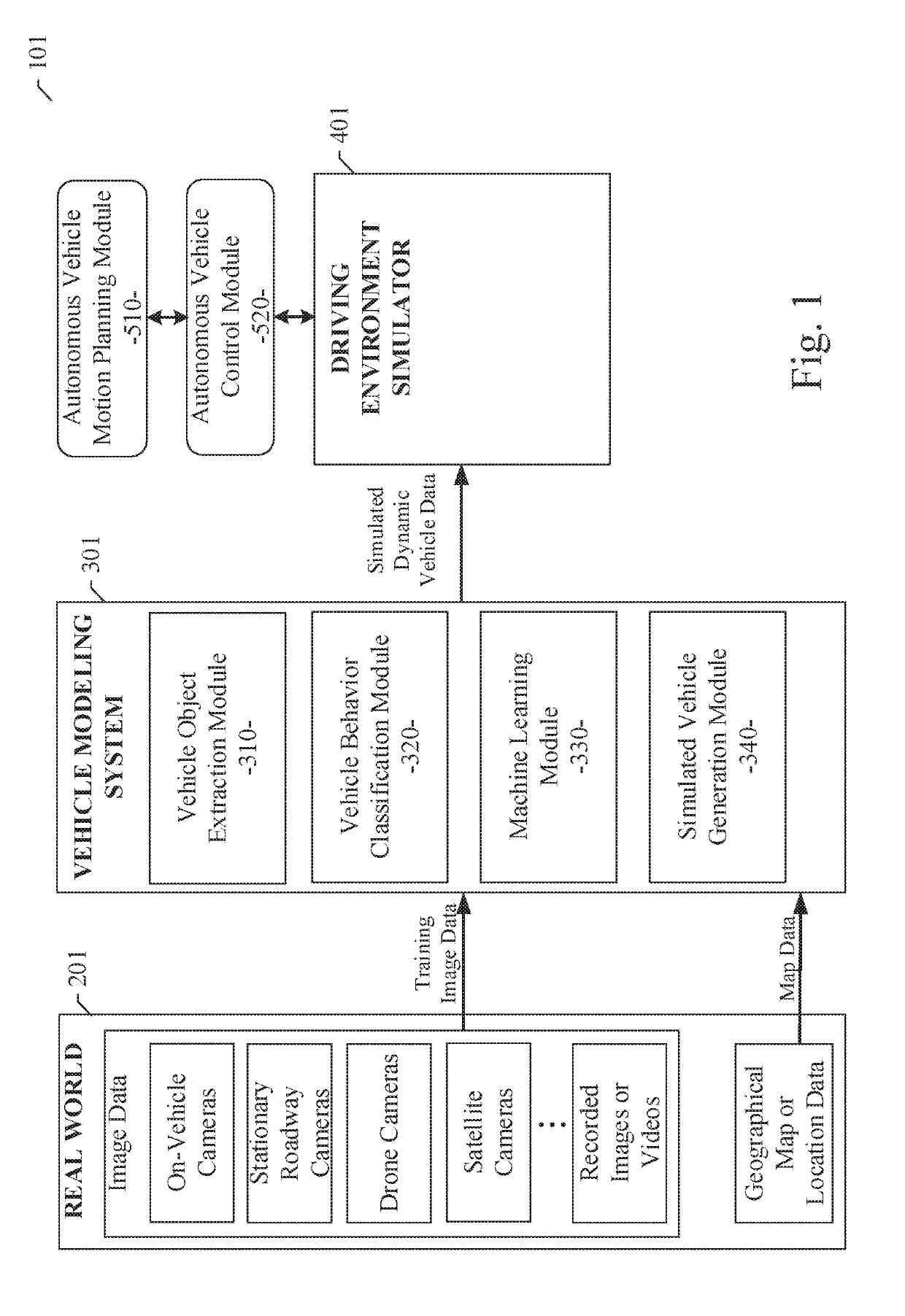
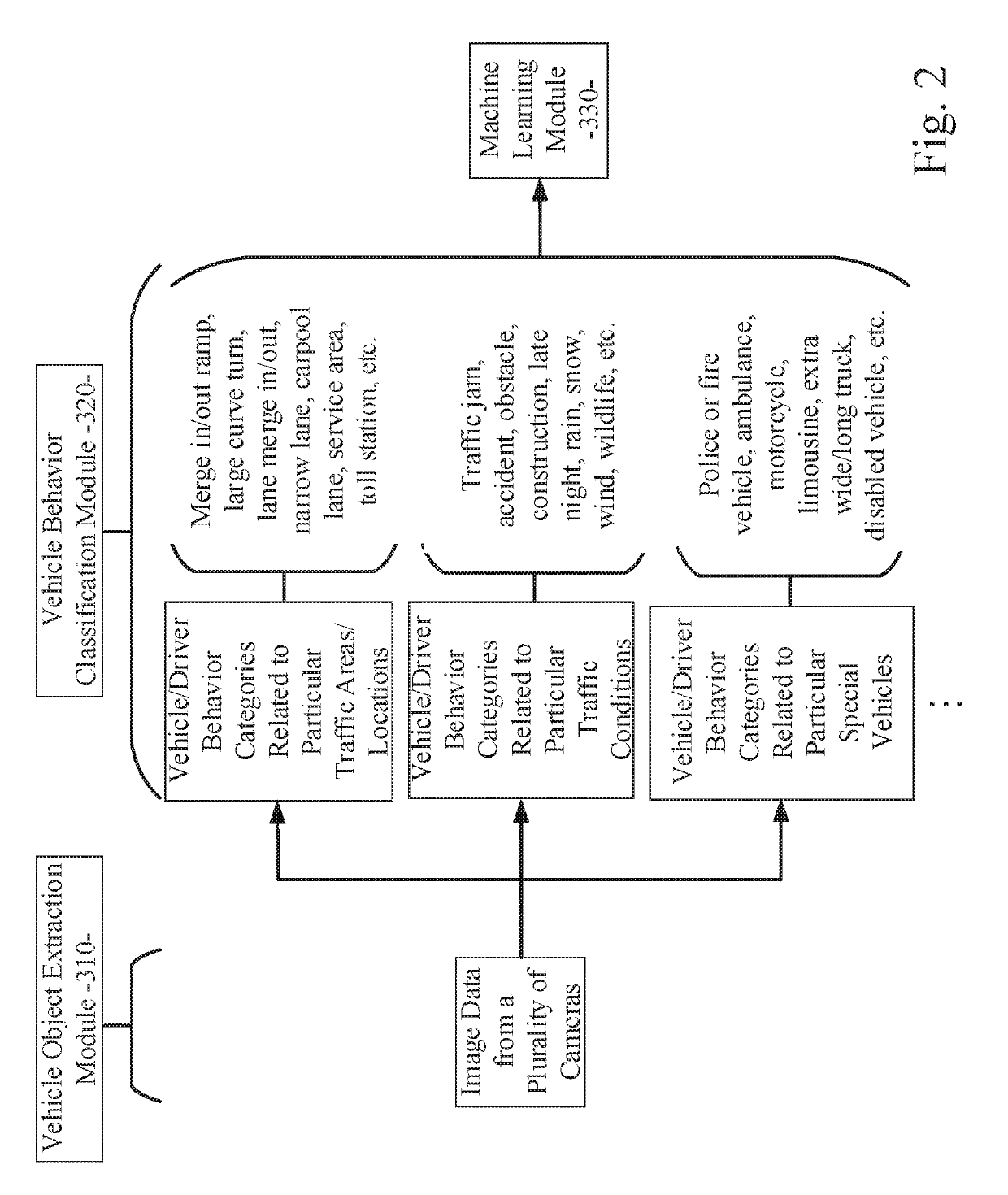
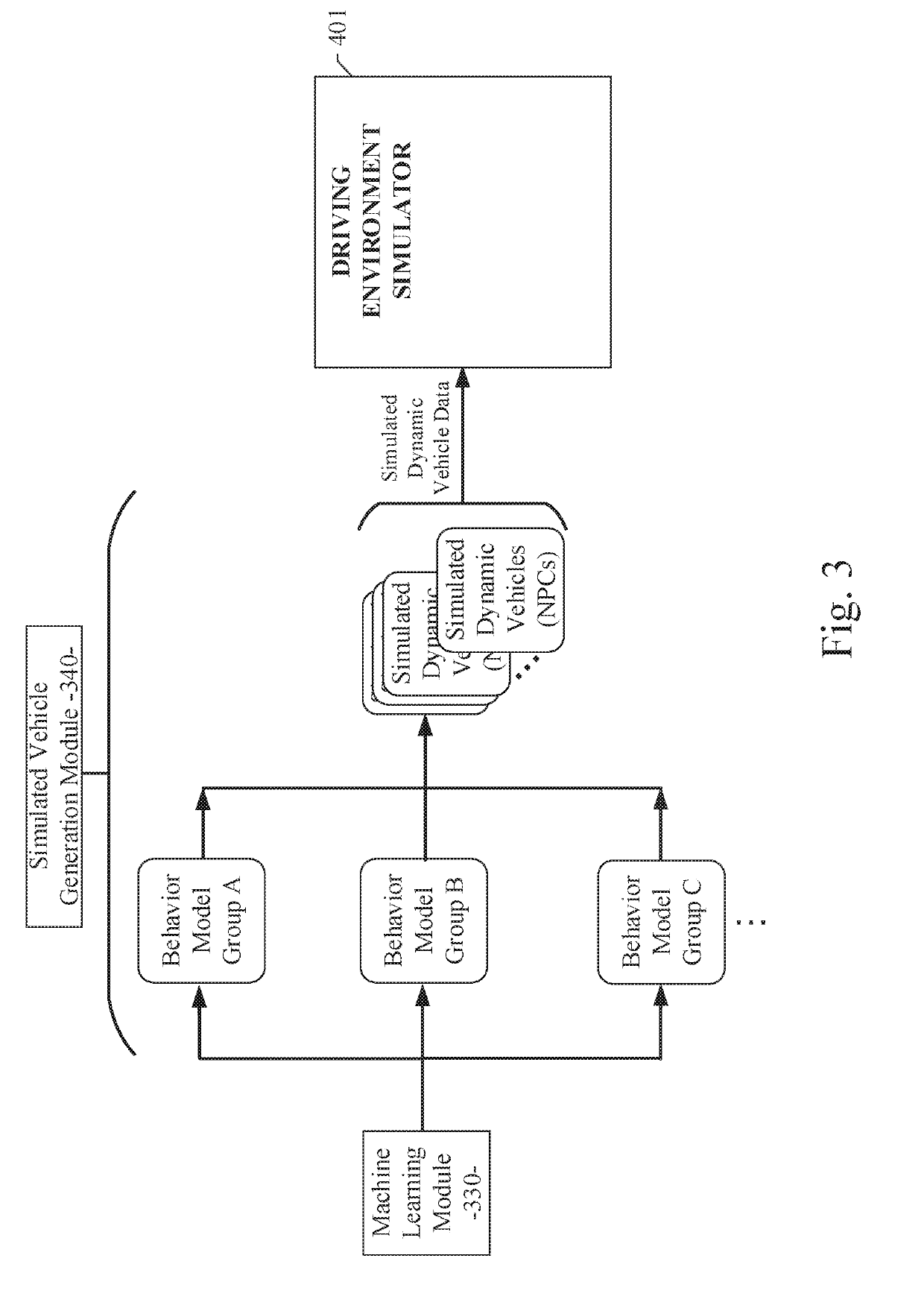
A human driving behavior modeling system using machine learning is disclosed. A particular embodiment can be configured to: obtain training image data from a plurality of real world image sources and perform object extraction on the training image data to detect a plurality of vehicle objects in the training image data; categorize the detected plurality of vehicle objects into behavior categories based on vehicle objects performing similar maneuvers at similar locations of interest; train a machine learning module to model particular human driving behaviors based on use of the training image data from one or more corresponding behavior categories; and generate a plurality of simulated dynamic vehicles that each model one or more of the particular human driving behaviors trained into the machine learning module based on the training image data.
Owner:TUSIMPLE INC
Apparatus, System and Method for Mobile Terminal Data Analysis and Distribution Utilizing Internal Proxies
InactiveUS20130183926A1Mitigate such drawbackEasy to convertServices signallingSubstation equipmentBehavioral modelingData type
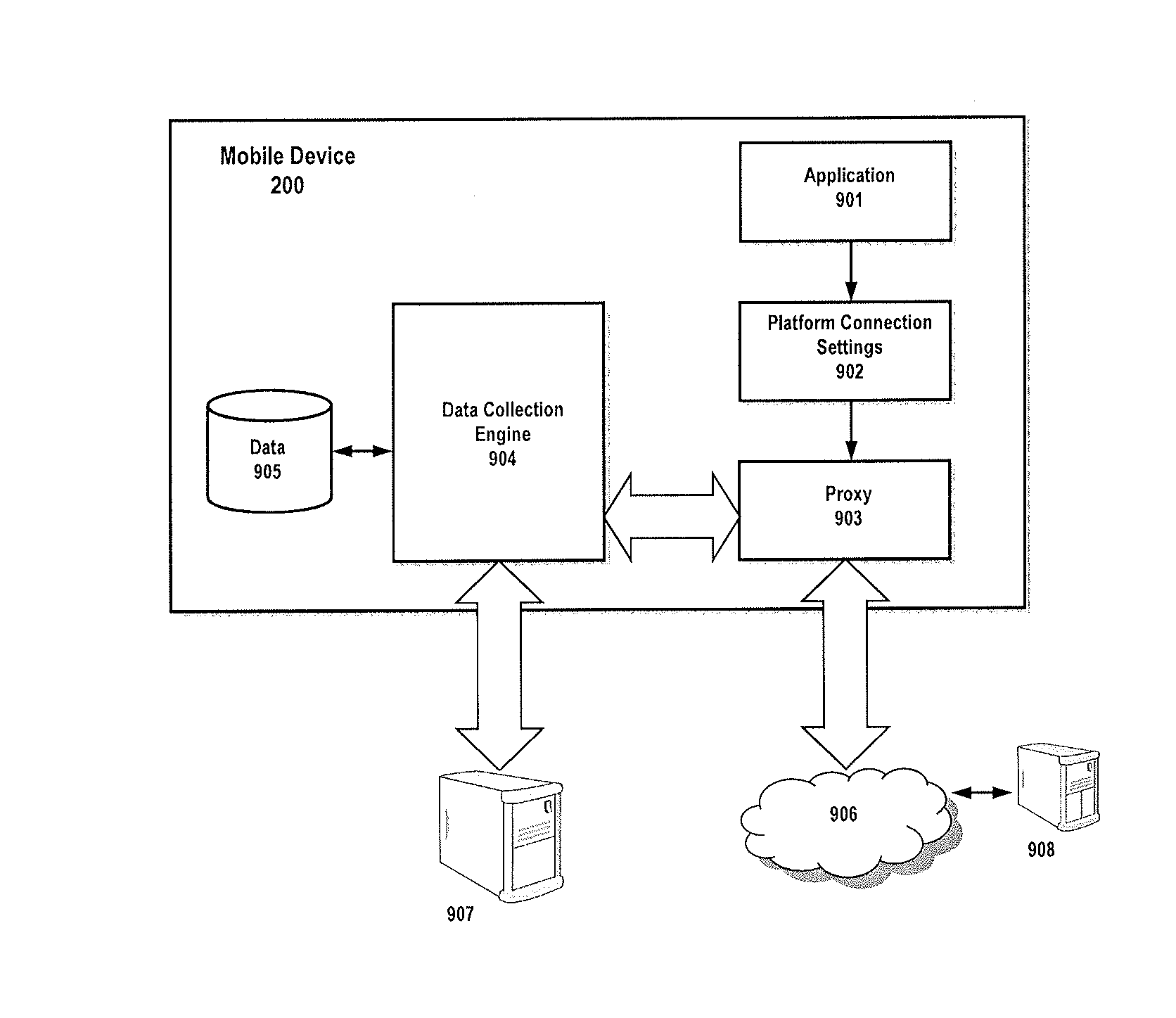
A mobile terminal for providing life observations by monitoring data being transmitted to / from the terminal. A mobile terminal proxy works in conjunction with a data collection engine and platform connection settings to detect at least on data object type and forward information relating to the data type to the data collection engine. Various observation logic and triggering rules may be implemented for the data collection. A server arrangement may further utilize context and behavior modeling using observations from plural mobile terminals and guiding the mobile terminals for future observations.
Owner:THE NIELSEN CO (US) LLC
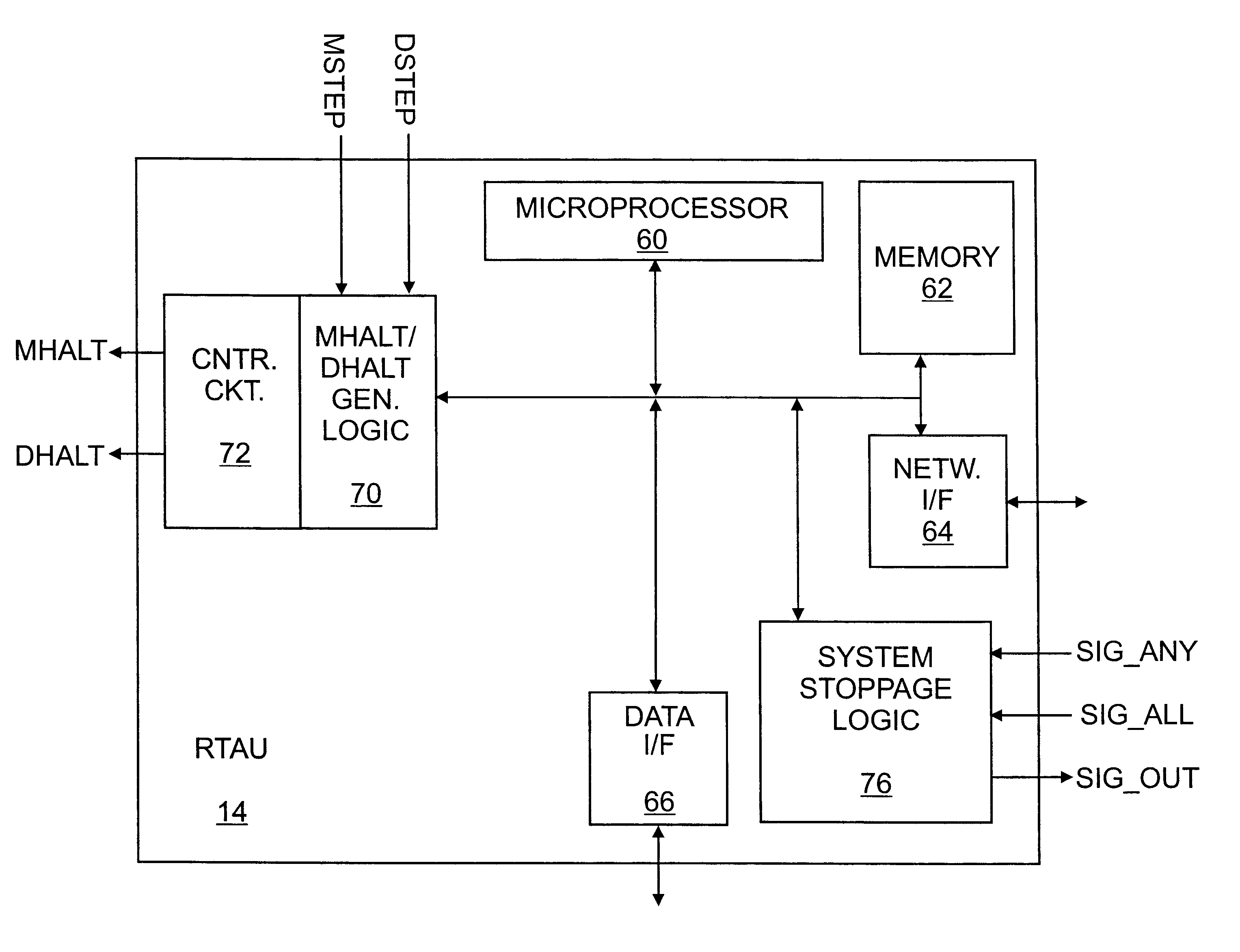
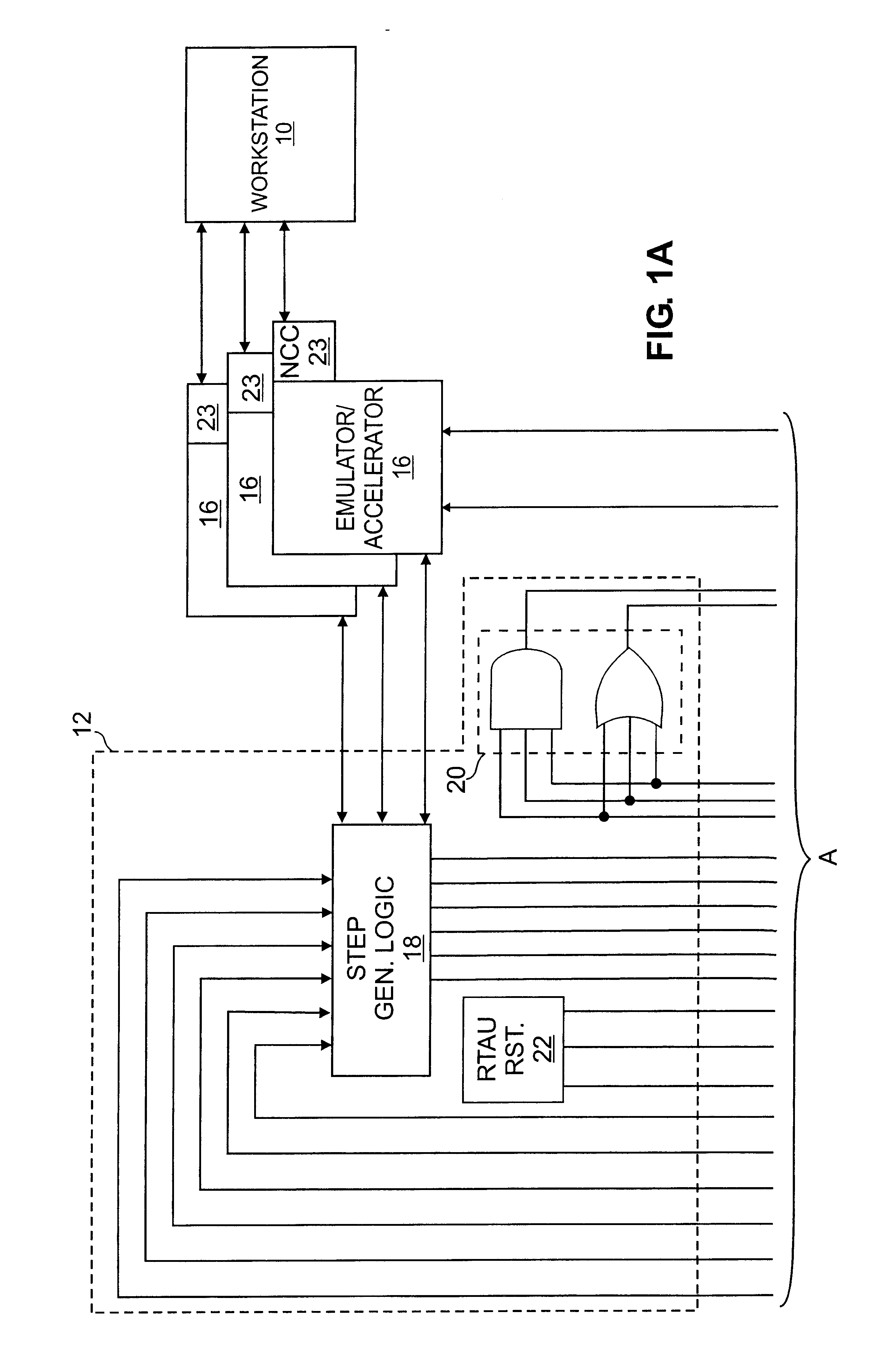
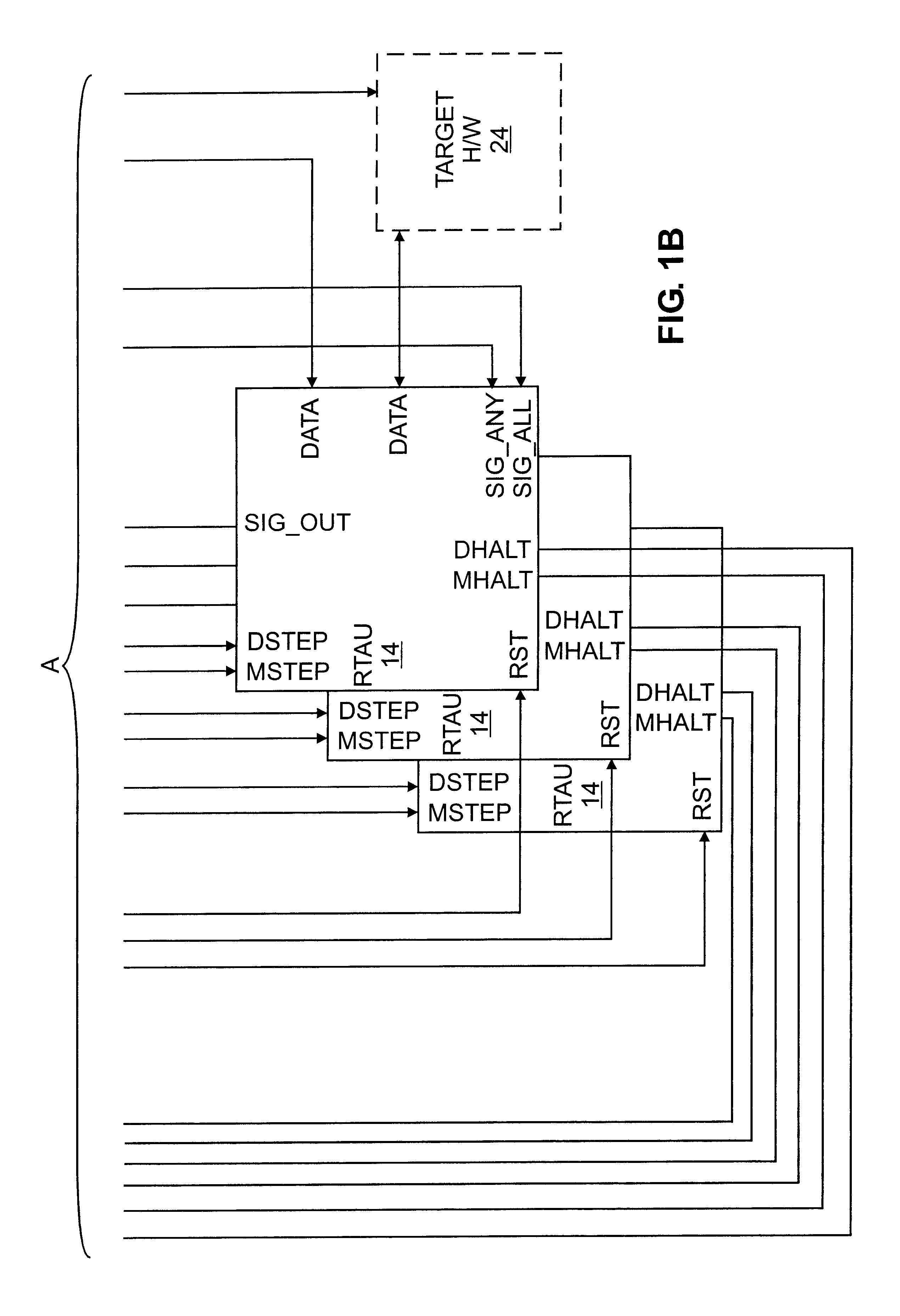
Apparatus for improving concurrent behavior modeling with emulation
InactiveUS6782355B1Improve versatilityVersatile interfaceComputer aided designSoftware simulation/interpretation/emulationBehavioral modelingA domain
A hardware design emulation system that includes one or more emulators and one or more associated run-time assist units (RTAUs). The emulator logic is a combination of user model logic, reflecting the hardware design, and non-user model logic. A handshaking controller produces a domain step signal and a model step signal. The domain step signal indicates that the emulator is entering a state for executing the next step of the logic with which it is programmed, be it user model logic or non-user model logic. The model step signal indicates that the emulator is entering a state for advancing the user model defined by the user model logic. This dual handshaking protocol enhances versatility by enabling a wide variety of RTAUs to be used, particularly in combination with one another. Also, a RTAU can, in accordance with its programming, "skip steps" (either model steps or domain steps) to enhance efficiency if there is a known relationship between cycles of the emulator logic and cycles of the user model. In addition, system stoppage logic efficiently alerts other RTAUs when one RTAU has caused the emulation to stop. Furthermore, the emulation system can be scaled to accommodate a greater number of RTAUs by cascading the master panels to which they are connected.
Owner:CADENCE DESIGN SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com