Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
159results about How to "Avoid sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
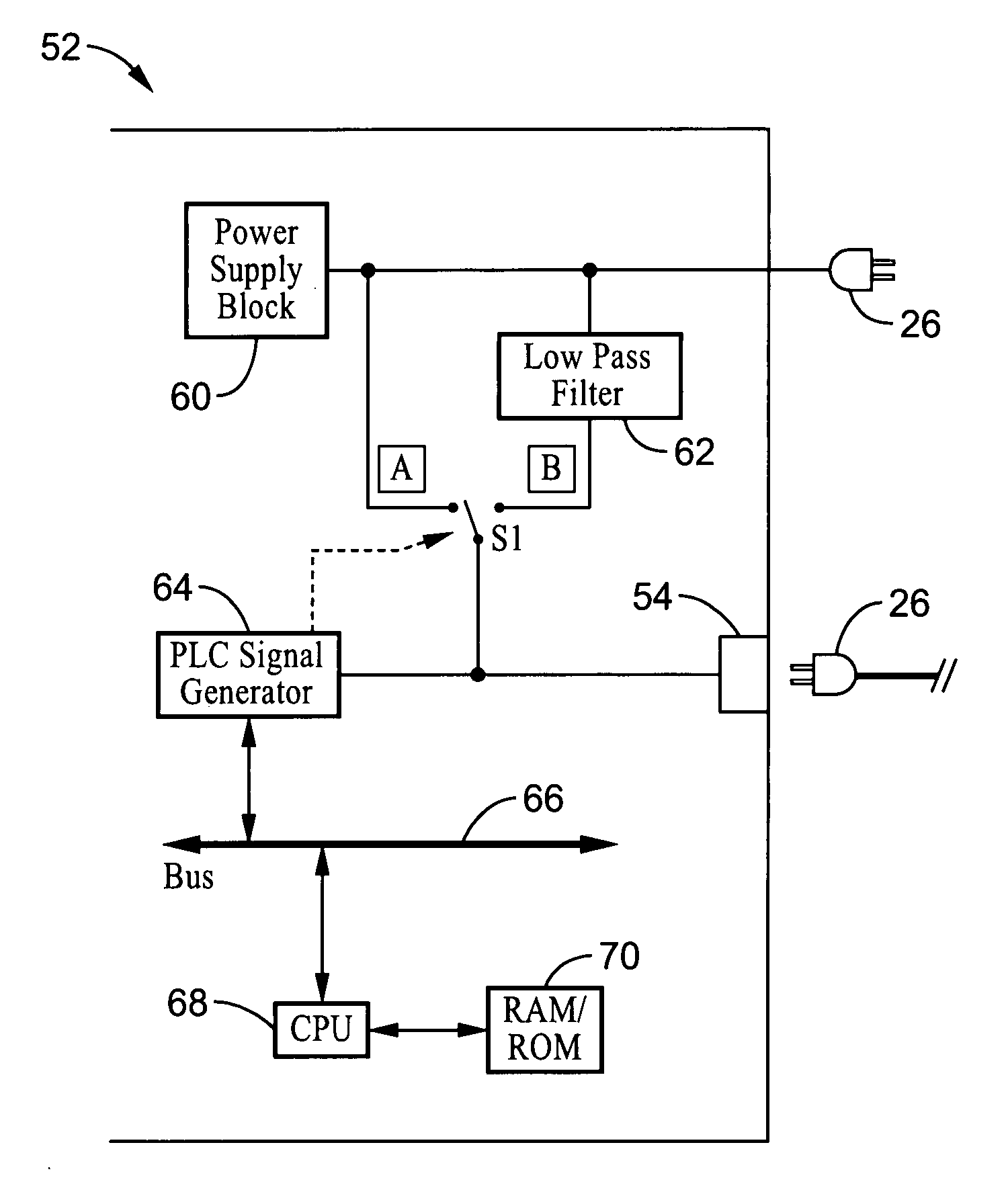
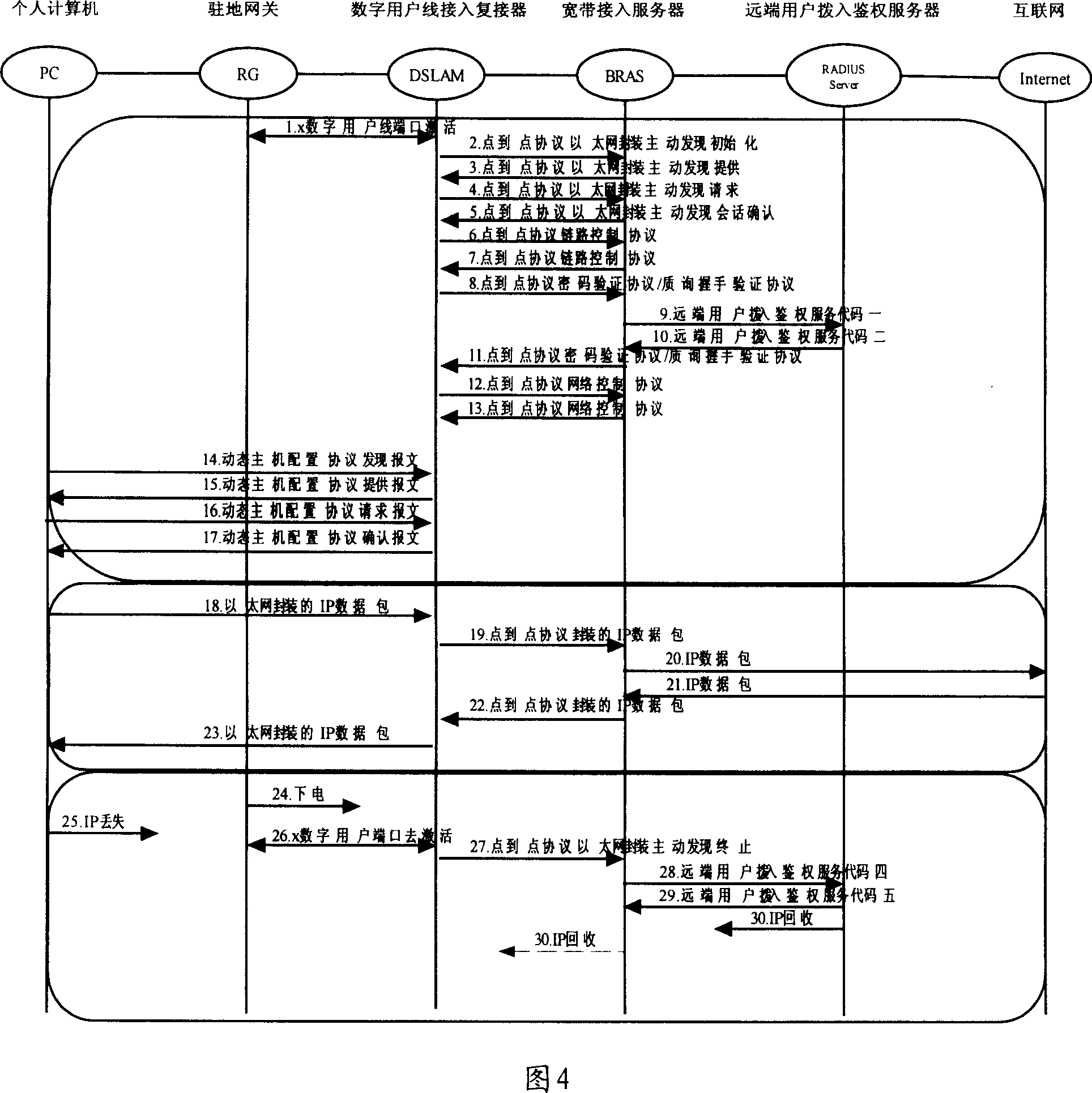
System and method for authenticating/registering network device in power line communication (PLC)
ActiveUS20060038660A1Avoid sharingProvide securitySystems using filtering and bypassingPower distribution line transmissionNetwork keyElectric power
A method and apparatus for protecting privacy in power line communication (PLC) networks. Data transmitted on a PLC network is encrypted according to a network key and can be properly received only by registered devices that have the proper network ID and network key value so that proper decryption can be performed. According to the invention a streaming media device is provided with a compatible network ID and network key during a registration process facilitated by coupling the device (applicant) to a direct power line connection associated with another device (administrator). The network key, and optionally network ID, are then shared over the direct connection without being distributed over the PLC network at large. By way of example, the data is prevented from being distributed across the PLC network in response to using selectable filtering of PLC data, and preferably a secure data communication mechanism, such as public-private key encoding.
Owner:SONY CORP +1
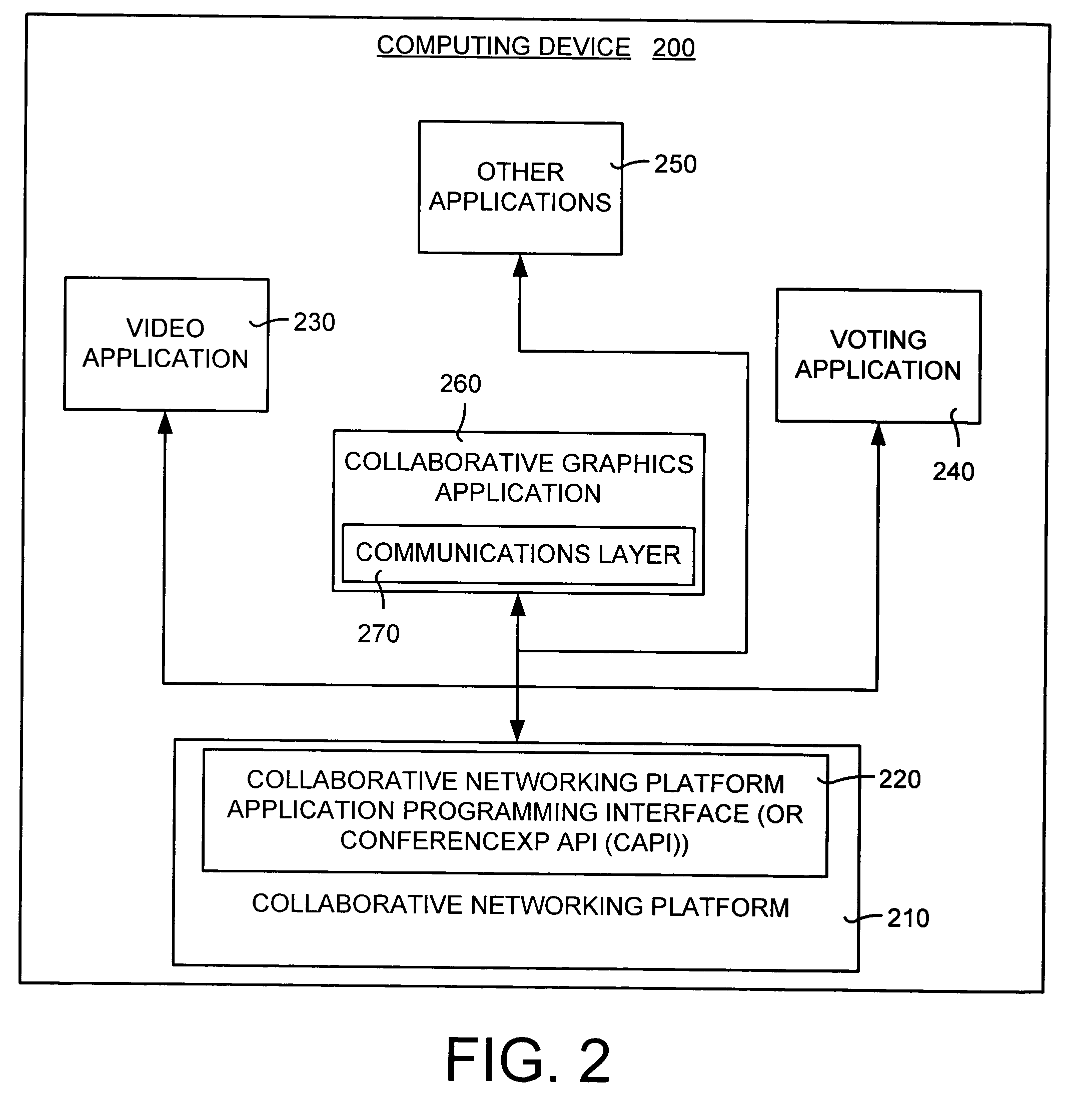
Real-time collaborative graphics application and method for use on a computer network having a collaborative networking platform
InactiveUS20060059431A1Facilitates real-time collaborationEasy to changeTelevision conference systemsTwo-way working systemsGraphicsPersonalization
A real-time collaborative graphics application and method (such as Microsoft® Visio®) that runs on top of a collaborative networking platform (such as Microsoft® ConferenceXP) and provides real-time collaboration. The real-time collaborative graphics application and method personalizes local objects created by a local to readily distinguish them from remote objects created by remote users. Identifiers are used to allow the authorship of an object to be easily determined by all users. Local objects, remote objects, and a combination of the two can be moved and manipulated by any users. A local user may avoid sharing his local objects with remote users. Moreover, a local user can decide to hide remote objects created by remote users. If at a later time the local user decides to once again view the hidden remote objects, all updates since the remote shapes were hidden are automatically updated at the local user's document.
Owner:MICROSOFT TECH LICENSING LLC
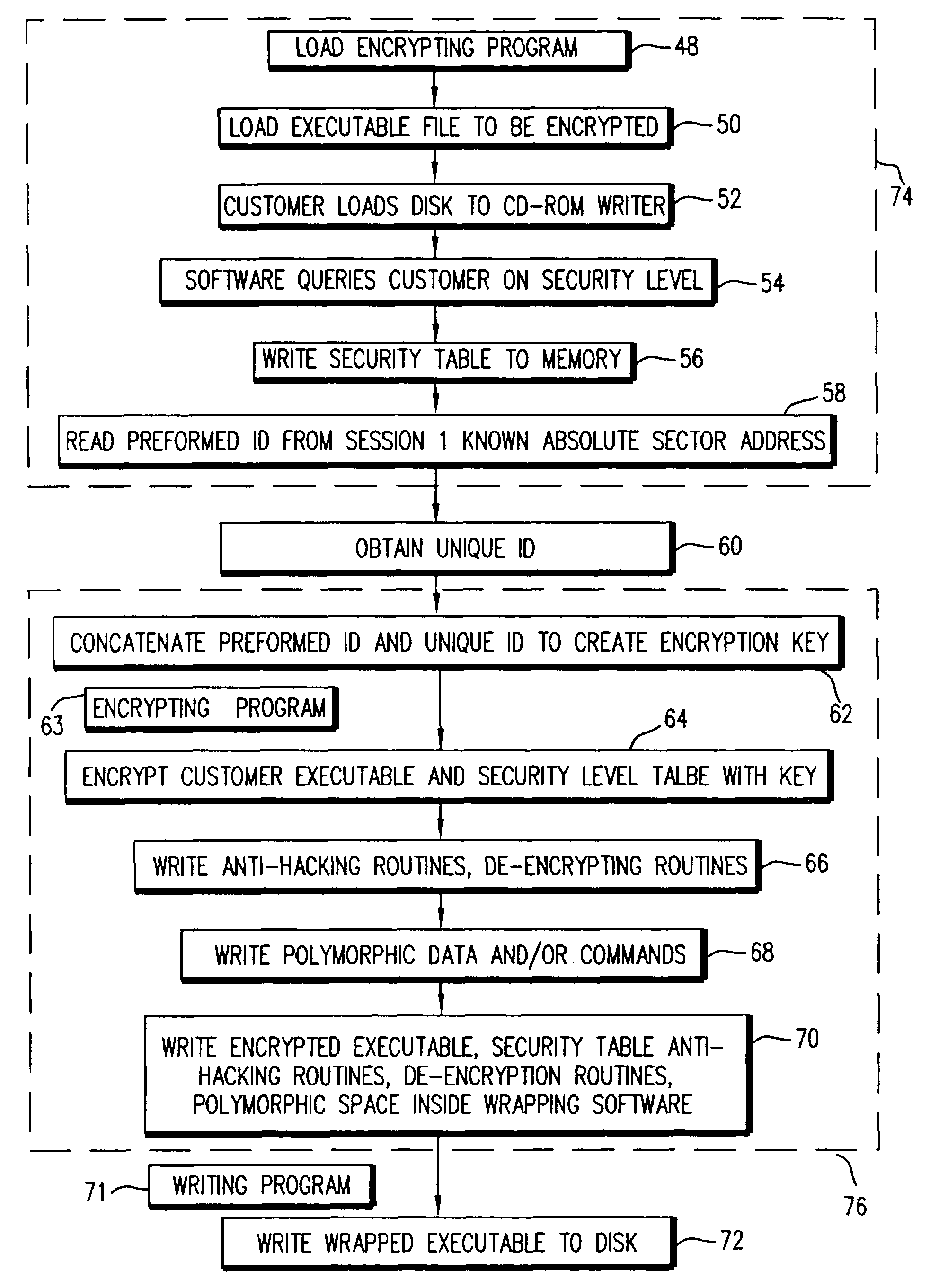
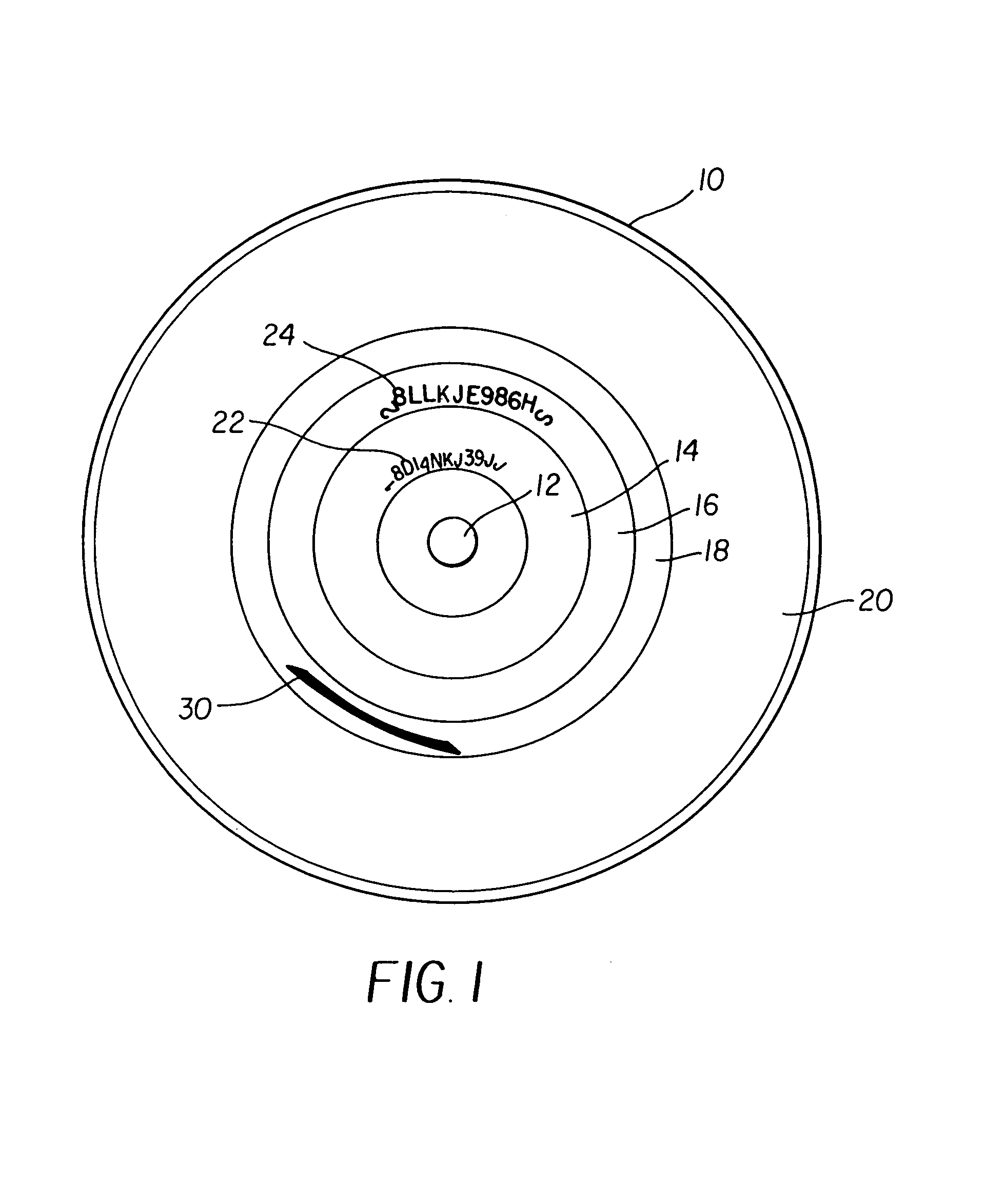
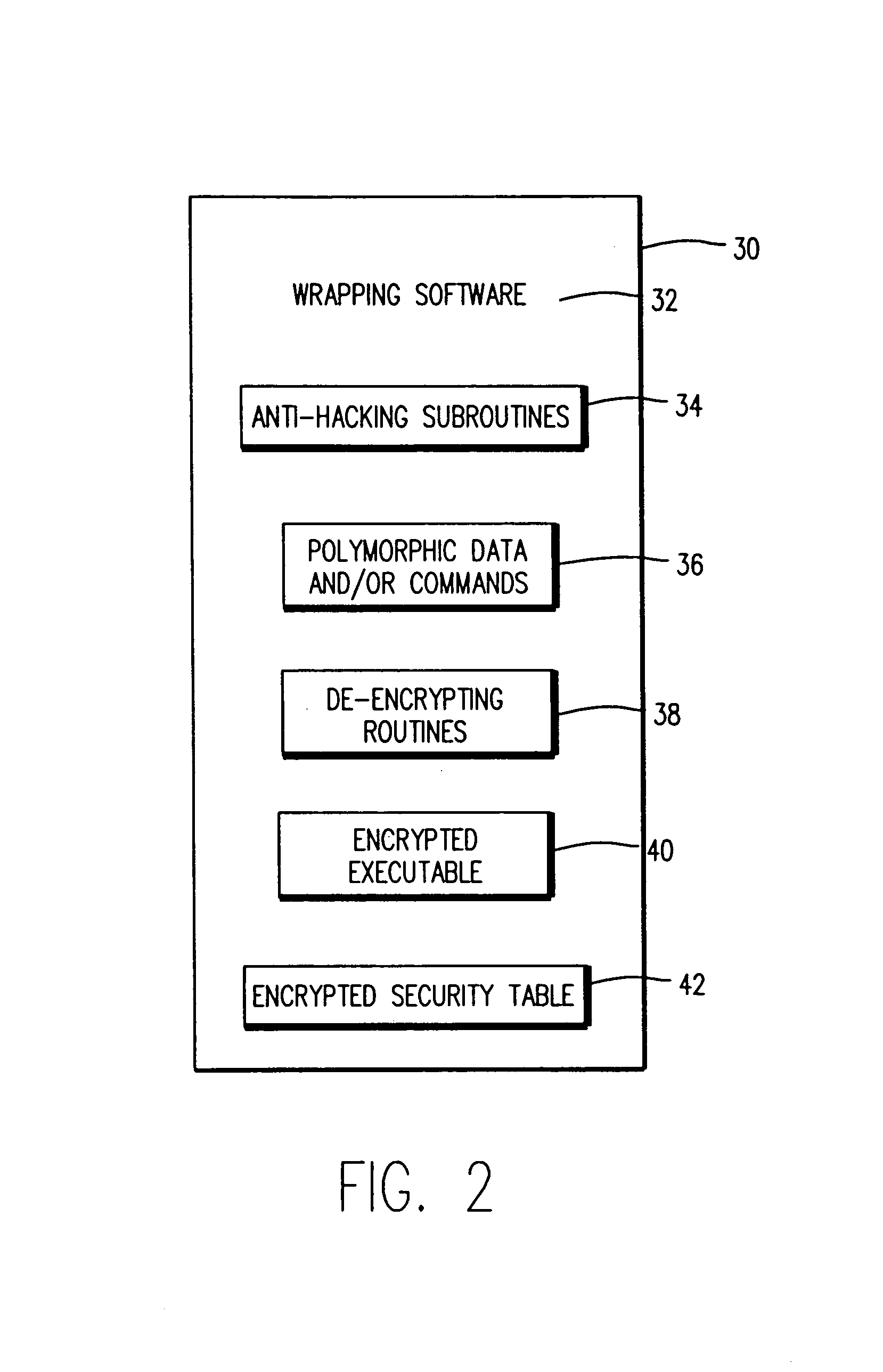
Copy protection using multiple security levels on a programmable CD-ROM
InactiveUS7057993B2Easy to copyNumber of EliminationsTelevision system detailsRecord information storageComputer hardwareCompact Disc manufacturing
A copy-protected optical disc, including a preformed identification number (ID) in the ATIP signal and the subcode which is impressed upon the optical disc and a number of other optical discs during optical disc manufacture, a unique identification number for the optical disc which was written on the optical disc after it is manufactured; and an encrypted program written onto the optical disc wherein the encryption of such program is based upon the preformed ID and the unique ID and includes two or more selectable security levels.
Owner:EASTMAN KODAK CO
Storage device and system and control method
ActiveCN111361908AEasy to understand implementationEasy to understandStorage devicesControl engineeringMechanical engineering
The embodiment of the invention provides a storage device and system and a control method. The storage device comprises multiple goods shelves, a first robot channel and a second robot channel. Each goods shelf comprises at least one temporary storage laminate, at least one storage laminate and multiple stand columns arranged in the horizontal direction at intervals. The storage laminates and thetemporary storage laminates are arranged in the vertical direction at intervals through the stand columns. The temporary storage laminates are used for providing multiple temporary storage stations, and the storage laminates are used for providing multiple storage stations. The first robot channel is used for allowing a first robot to run, and the first robot is used for storing goods on the temporary storage laminates. The second robot channel is used for allowing a second robot to run, and the second robot is used for carrying goods between the temporary storage laminates and the storage laminates. By means of the technical scheme, the efficiency of putting cargoes in and out of warehouses can be improved.
Owner:SHANGHAI QUICKTRON INTELLIGENT TECH CO LTD
Security certification method and security certification system
InactiveCN104506542AAchieve sharingImprove securityDigital data authenticationTransmissionIn-memory databaseApplication software
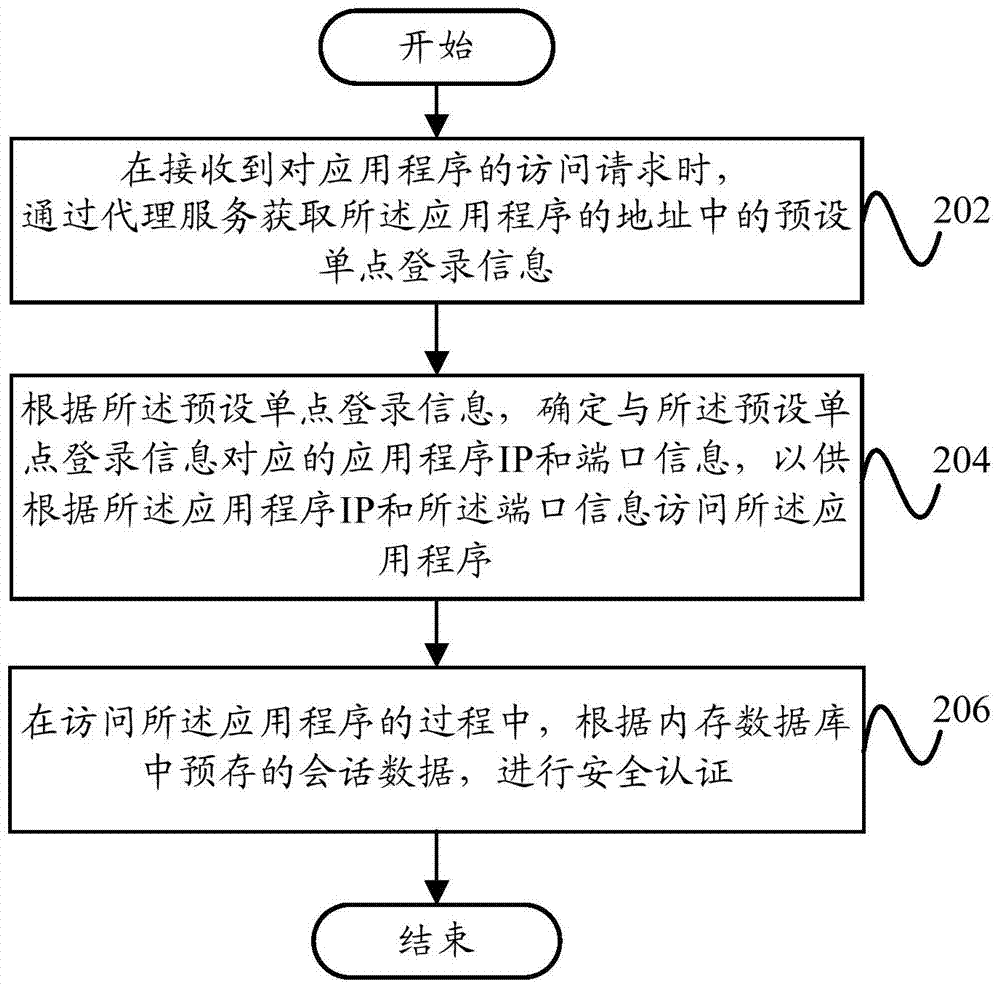
The invention provides a security certification method and a security certification system. The method includes: on receiving an access request from an application, acquiring preset single sign-on information in an address of the application; according to the preset single sign-on information, determining an application IP (internet protocol) and port information corresponding to the preset single sign-on information to allow the access to the application through the application IP and port information; during the access to the application, allowing security certification according to preset session data in a memory database. The security certification method and the security certification system have the advantages that service agency is achieved, the security of the system is better, and the system is imparted the functions of log auditing and permission controlling; session sharing is achieved so that the problem of non-uniformity in session information caused by the access to different servers is effectively avoided.
Owner:ZICT TECH CO LTD
Information sharing method and information sharing device
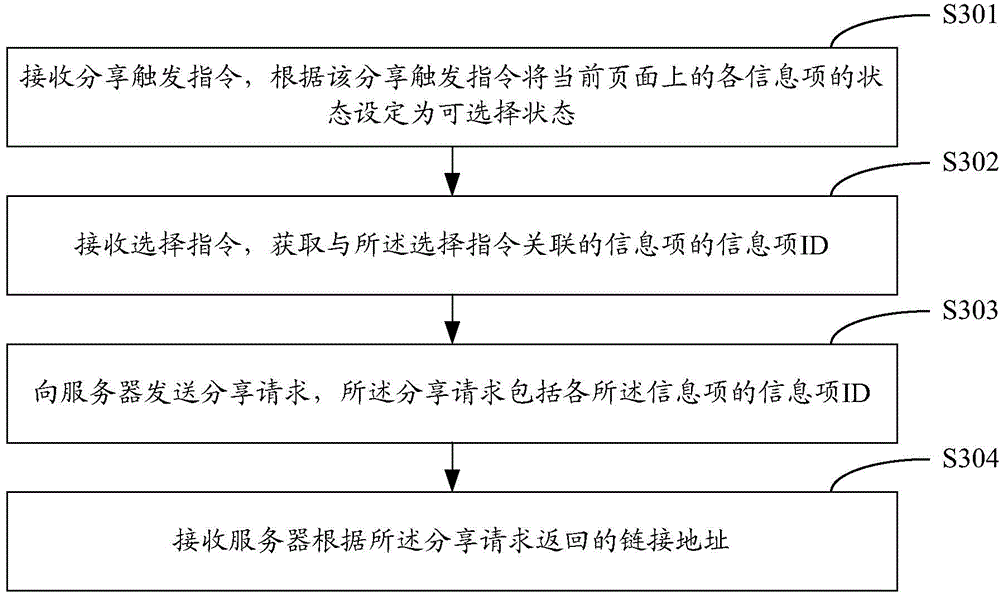
ActiveCN104702665AImprove accuracyAvoid sharingTransmissionSpecial data processing applicationsInformation sharing
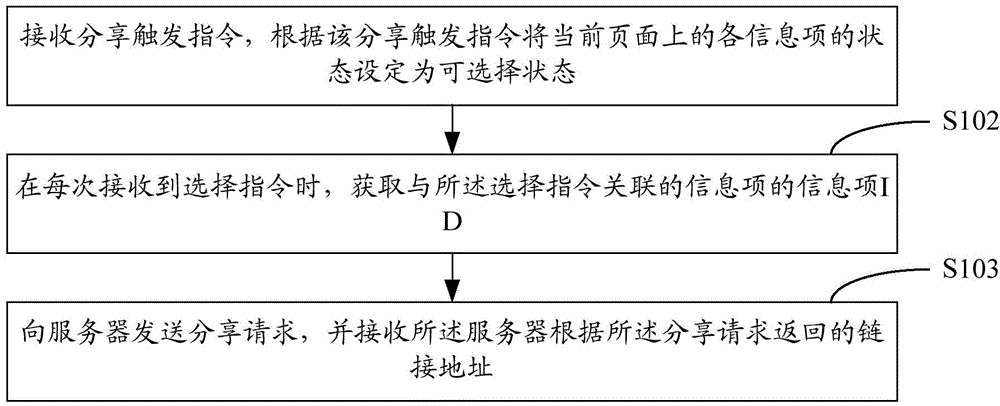
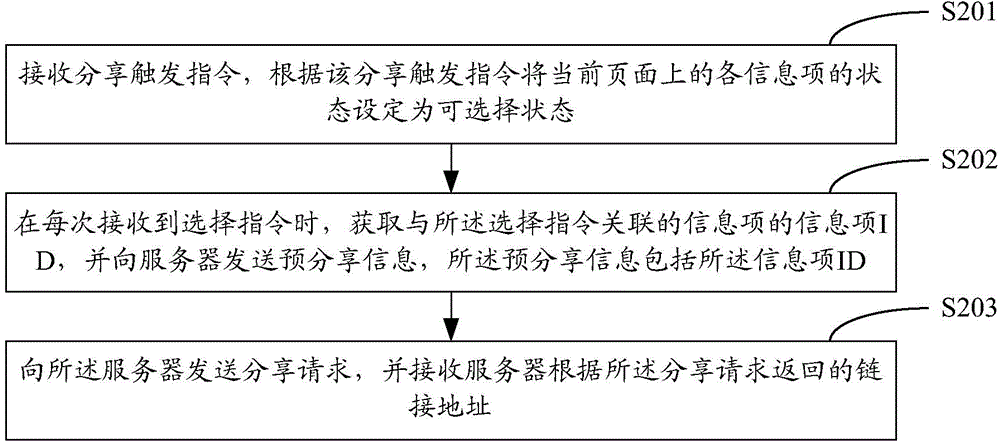
The invention discloses an information sharing method and device. The information sharing method comprises the steps of receiving a share triggering instruction and setting states of all information items on a current page as optional states according to the share triggering instruction, obtaining information item ID of the information items associated with the optional states when a selection instruction is received each time, sending a share request to a server and receiving a linkage address returned by the server according to the share request. By means of the scheme, unnecessary share of the information items which are not needed to be shared is avoided, the information sharing accuracy is improved, and the information is convenient and quick to share.
Owner:GUANGZHOU PINWEI SOFTWARE
Peer-to-peer network based digital copyright protection method
InactiveCN102143232AGuaranteed to be trueGuaranteed non-repudiationUser identity/authority verificationFile sharingDistributed computing
Owner:NANJING UNIV OF POSTS & TELECOMM
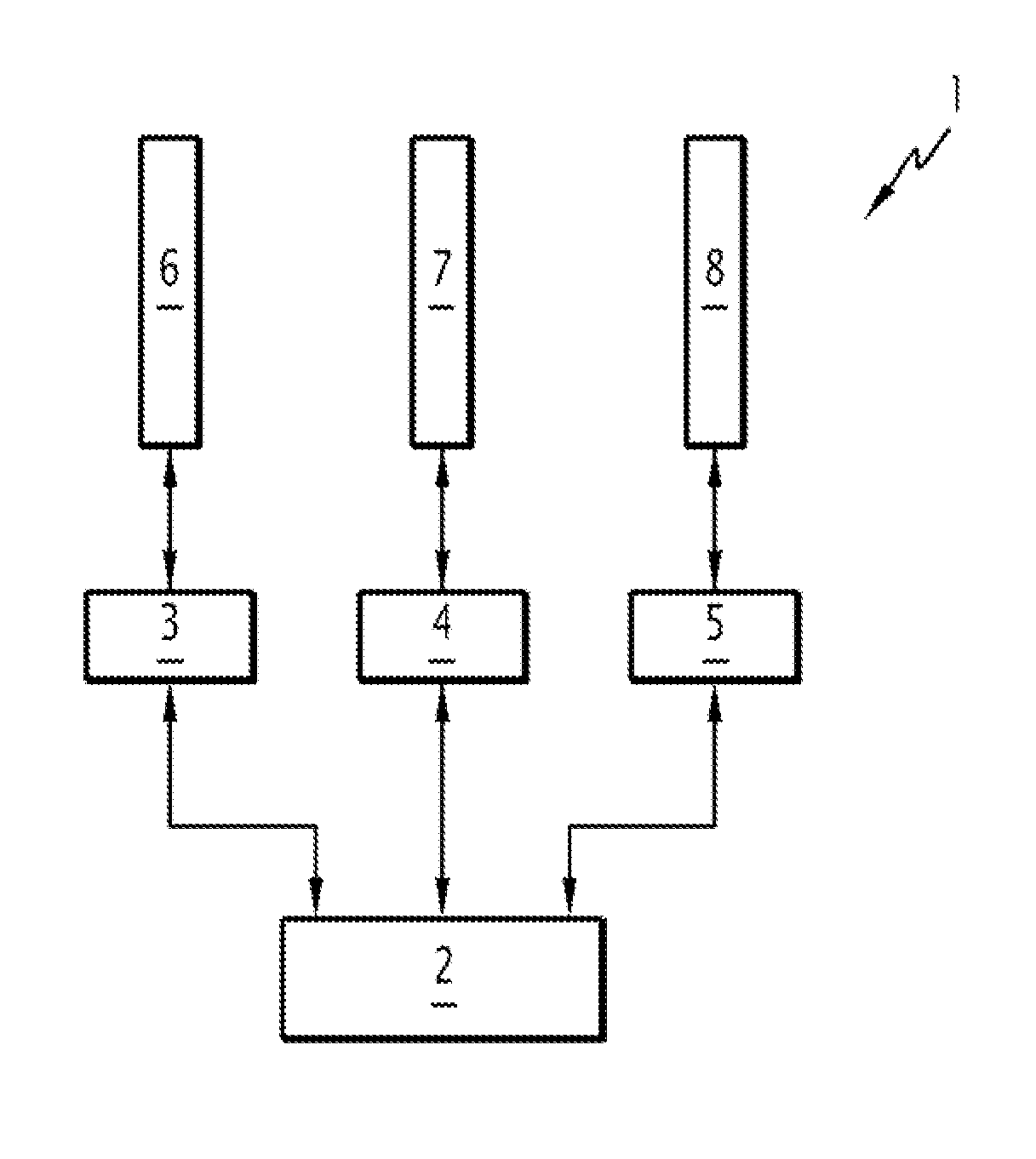
Transceiver Station for Forming a Telecommunications Network Node and Associated Telecommunications Method
InactiveUS20130064233A1Improve end-to-end efficiency of networkReinforce operating independenceNetwork topologiesConnection managementTelecommunications networkTransceiver
A transceiver station is provided for forming a telecommunications network node. The station includes at least two transceiver radio modules and a control module. Each transceiver module is adapted to operate alternatingly as a subscriber station and as a base station, as a function of commands from the control module. The control module is adapted to determine a modification of the state of the network and to dynamically control at least one change in the operation of at least one transceiver module, from subscriber station to base station or vice versa, as a function of at least the determined modification. The control module is adapted so that the number of subscriber stations connected to a base station is at most equal to 1.
Owner:THALES SA
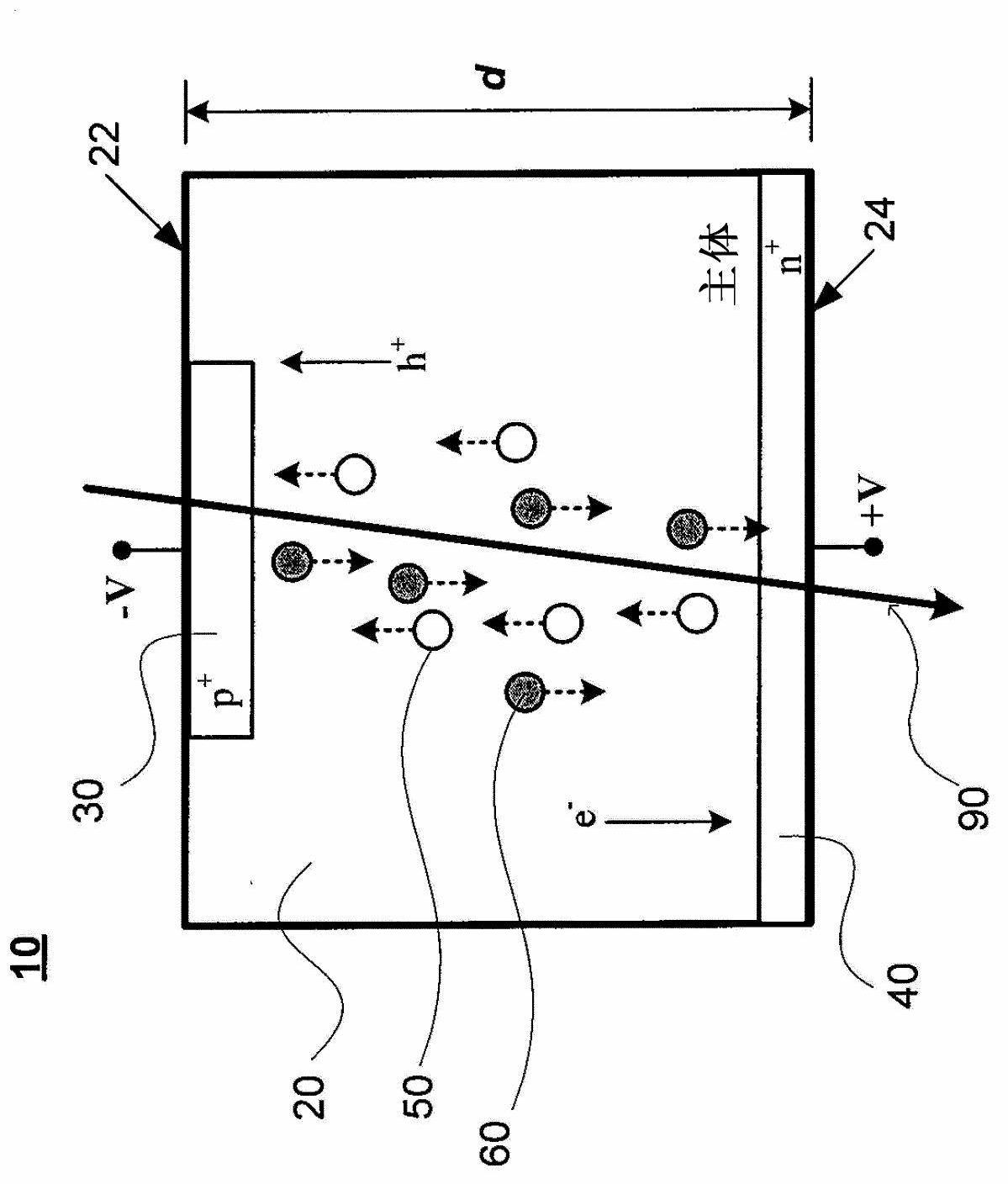
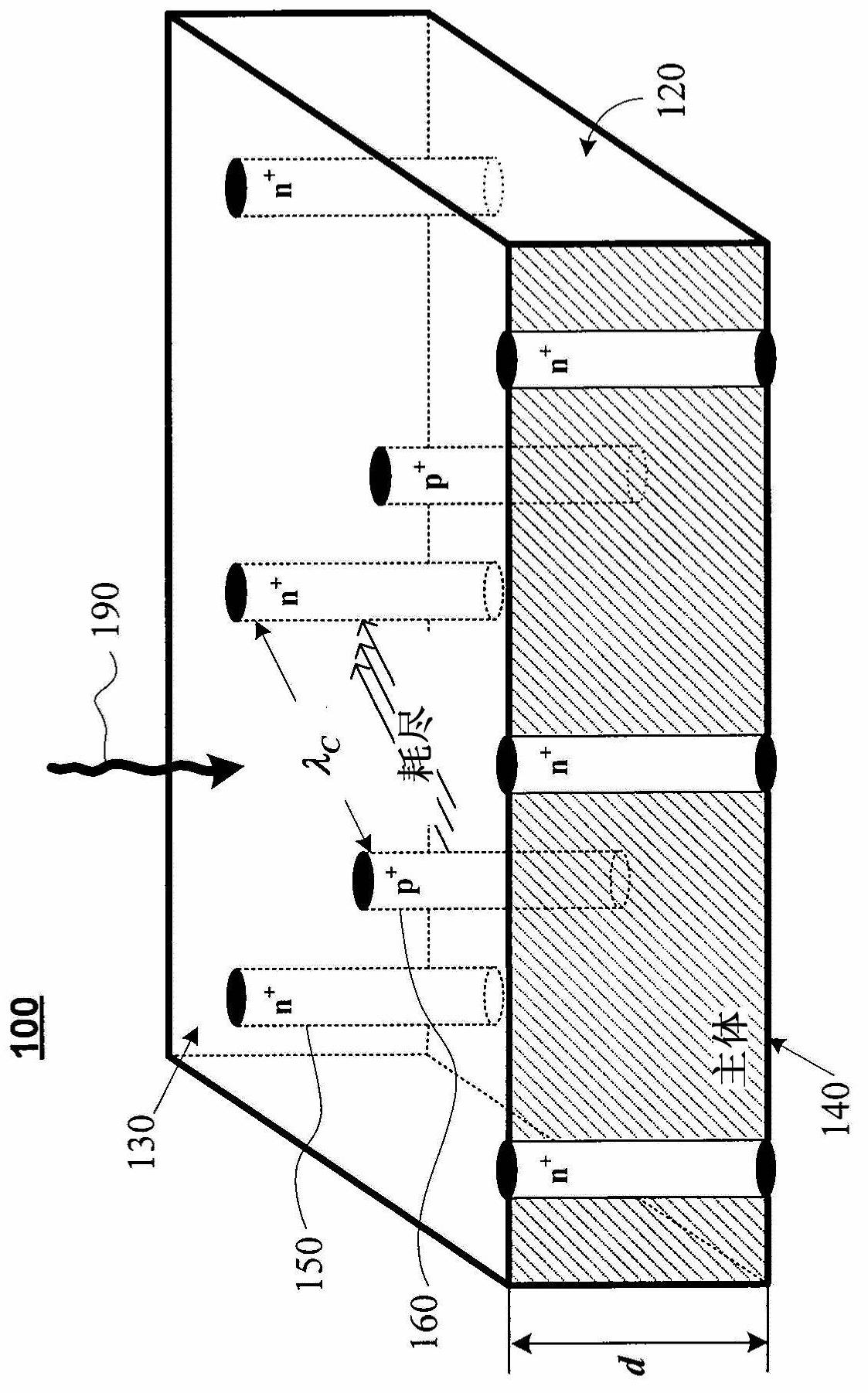
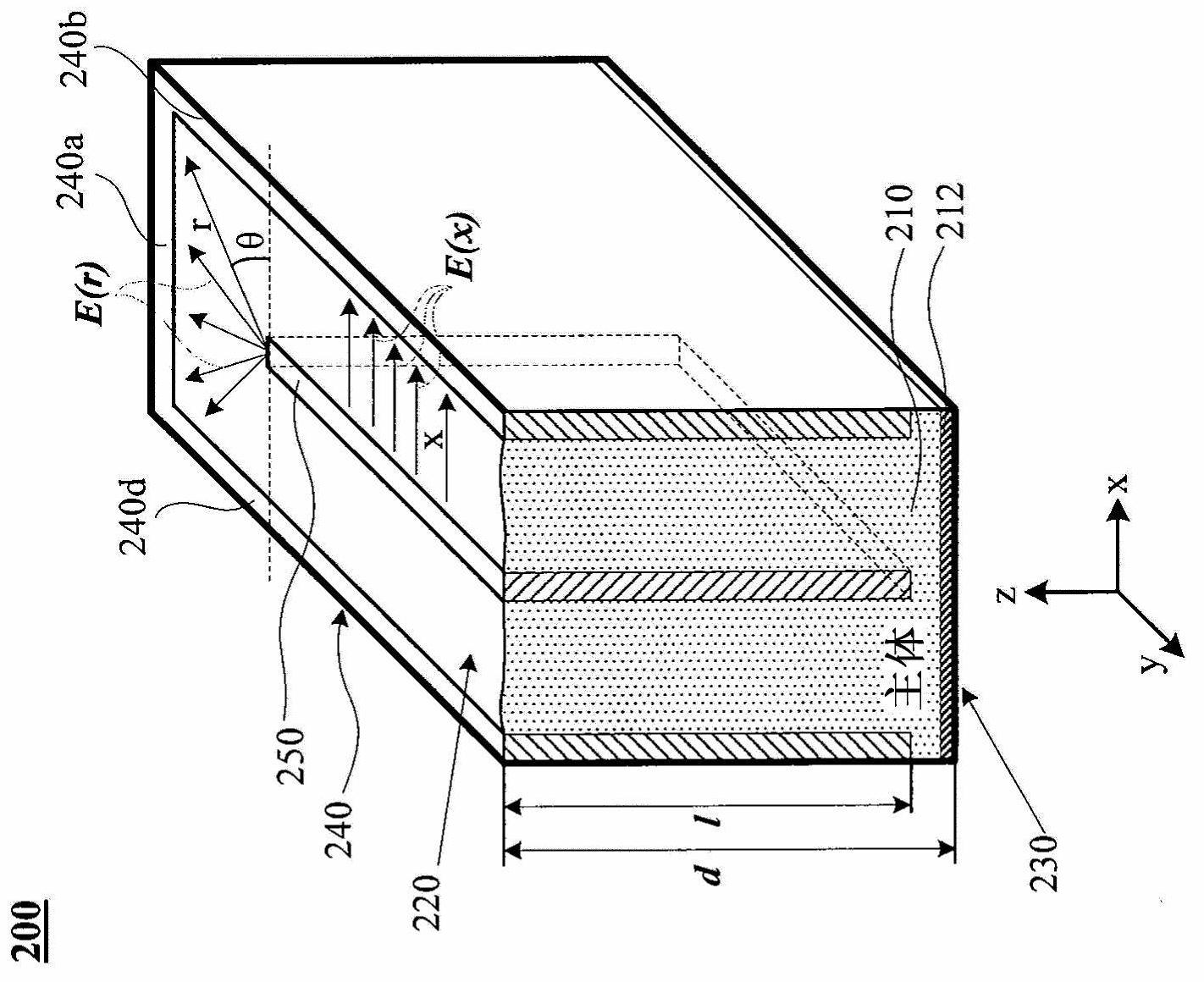
3D-trench electrode detectors
InactiveCN102695967ASolve problems caused by sharingAvoid sharingSolid-state devicesSemiconductor/solid-state device manufacturingSemiconductor materialsAtomic physics
A three-dimensional (3D) Trench detector and a method for fabricating the detector are disclosed. The 3D-Trench detector includes a bulk of semiconductor material that has first and second surfaces separated from each other by a bulk thickness, a first electrode in the form of a 3D-Trench, and a second electrode in the form of a 3D column. The first and second electrodes extend into the bulk along the bulk thickness. The first and second electrodes are separated from each other by a predetermined electrode distance, and the first electrode completely surrounds the second electrode along essentially the entire distance that the two electrodes extend into the bulk such that the two electrodes are substantially concentric to each other. The fabrication method includes doping a first narrow and deep region around the periphery of the bulk to form the first electrode, and doping a second narrow and deep region in the center of the bulk to form the second electrode.
Owner:BROOKHAVEN SCI ASSOCS
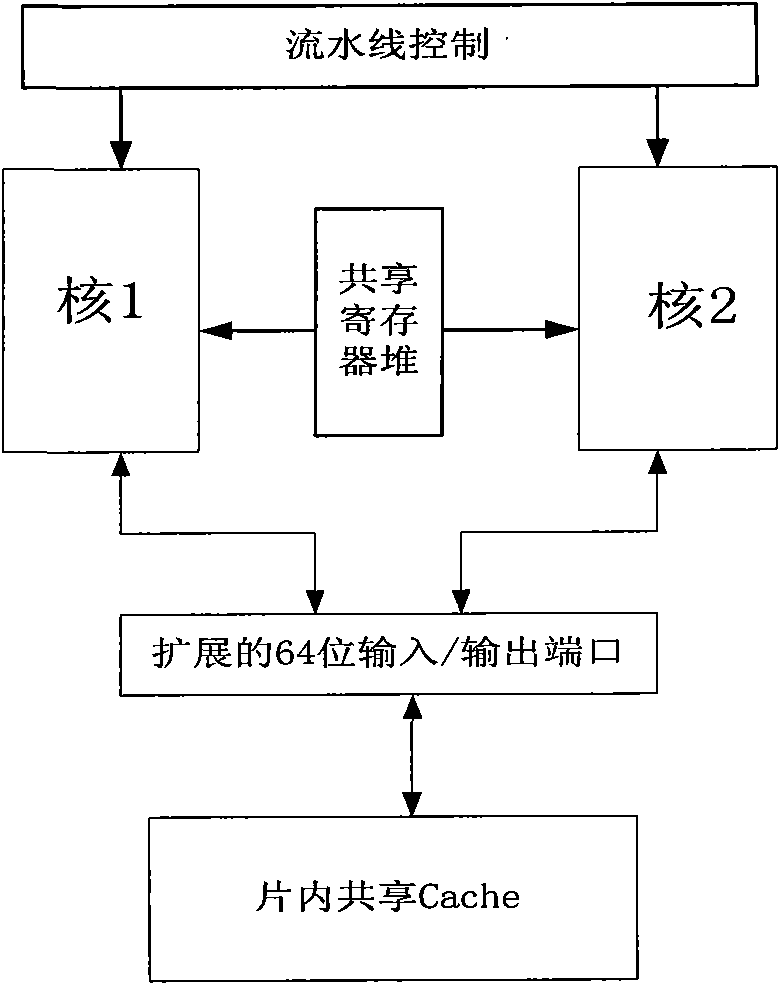
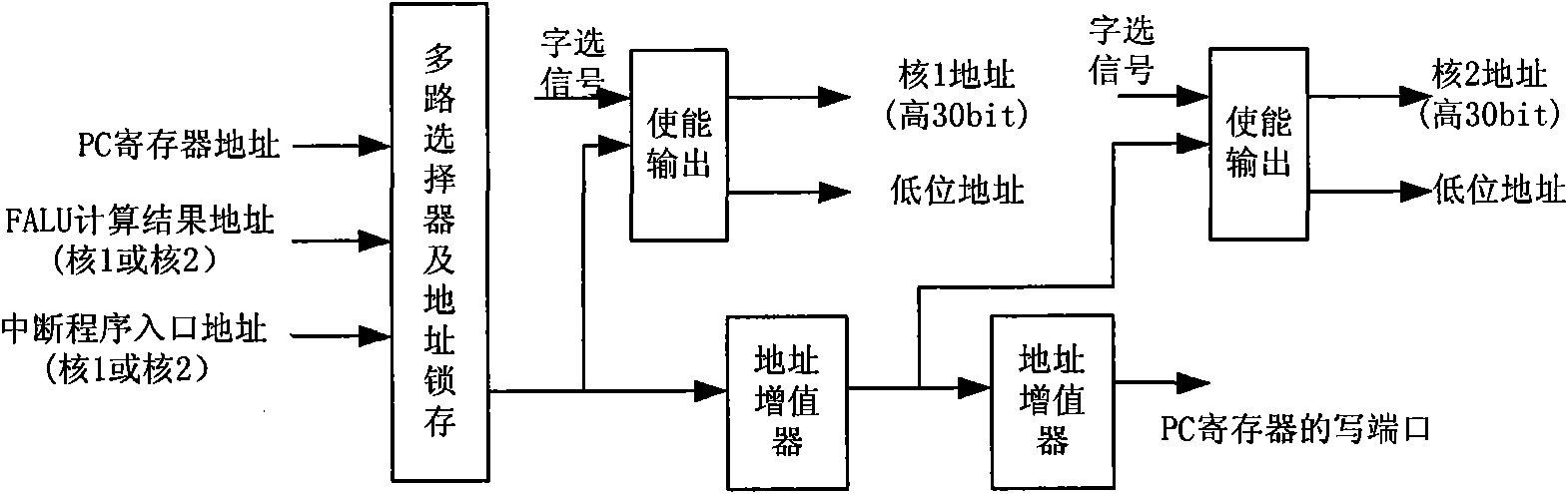
Method for designing embedded, isomorphic, symmetric and dual-core microprocessor
InactiveCN101593097AAvoid duplicationAvoid missesConcurrent instruction executionMicro structureComputer architecture
The invention discloses a method for designing an embedded, isomorphic, symmetric and dual-core microprocessor, which forms inner core units by module division according to the relative independency of an instruction fetch unit, a decoding unit, a control unit and a data path internal logistic module, designs a 32-bit dual-core RISC micro structure by using internal modules of a 32-bit RISC micro structure as an IP and expanding functions according to requirements, realizes the synchronization in terms of dual-core instruction fetch and avoids repeated instruction fetch of the two cores or instruction fetch omission by adopting a common PC register proposal, simplifies design by using a policy of sequential emission, namely executing according to the instruction fetch sequences of the two cores, designs a shared register file proposal according to data exchange between the two cores to allow the two cores to share resources, improve data exchange flexibility, avoid realizing data sharing by expanding an instruction set and reduce design period, and adopts a policy of assembly line control combination to realize unified management of two assembly lines and operational coordination of the two assembly lines.
Owner:XI AN JIAOTONG UNIV
Free radical and cation hybridized trigger for optical solidification and its preparing process and application
Owner:XIANGTAN UNIV
Human HLA-B*5801 gene polymorphism detection kit
InactiveCN106929591AAccurate detectionHigh sensitivityMicrobiological testing/measurementInternal standardHLA-B
The invention relates to a human HLA-B*5801 gene polymorphism detection kit. The human HLA-B*5801 gene polymorphism detection kit comprises PCR damping liquid, a specific primer, a specific probe, an interior label system, a Taq enzyme, a UNG enzyme, a weakly-positive control group and a blank control group, and also comprises a blood treating agent; a blood sample is simply treated and can be directly subjected to PCR amplification, the DNA extracting process is omitted, and operating time is saved. According to the human HLA-B*5801 gene polymorphism detection kit, the SNP probe is used in cooperation with the technology of the ARMS primer, and it is achieved that two different gene types are detected in one pipe; meanwhile, the interior label system is designed and used for monitoring the quality of the sample, and the weakly-positive control group and the blank control group are designed and used for monitoring the quality of the kit. The human HLA-B*5801 gene polymorphism detection kit for detecting HLA-B*5801 alleles has the advantages of being high in specificity and sensitivity, rapid and easy to operate, safe, objective in result interpretation and the like when being used for detecting HLA-B*5801 alleles.
Owner:WUHAN YZY MEDICAL SCI & TECH
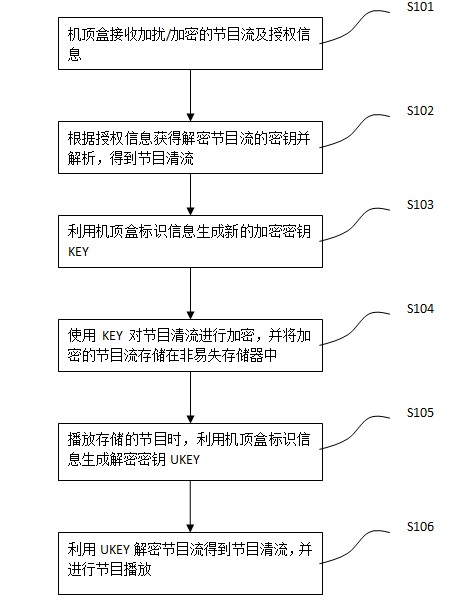
Method for preventing VOD (Video-On-Demand) programs from being illegally spread and shared
ActiveCN102427561ACopyright protectionAvoid distributingSelective content distributionAuthorizationVideo on demand
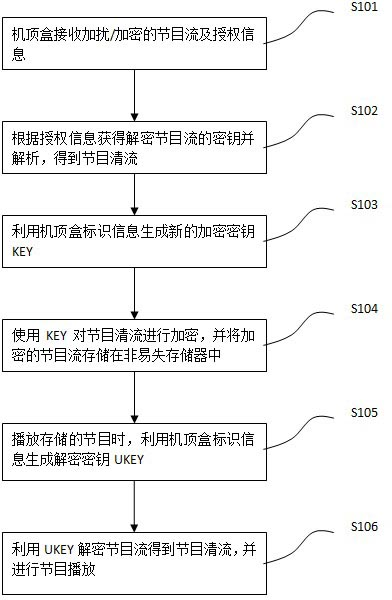
The invention discloses a method for preventing VOD (Video-On-Demand) programs from being illegally spread and shared. The method comprises the following steps of: S101: receiving a scrambled / encrypted program stream and an authorization message by a set top box; S102: acquiring a key for descrambling / decrypting according to the authorization message for decrypting the scrambled / encrypted programstream to obtain a program clear stream; S103: generating a new encrypting KEY by using identification information of the set top box; S104: encrypting the program clear stream by using the encrypting KEY and storing the encrypted program stream on a nonvolatile-memory connected with the set top box; S105: when the programs on the nonvolatile-memory are played, generating a decrypting UKEY corresponding to the encrypting KEY by using the identification information of the set top box; and S106: decrypting the program stream by using the UKEY and playing the decrypted program stream. Accordingto the method disclosed by the invention, the downloaded program data can be effectively prevented from being illegally copied, distributed and shared, the copyright of the programs is guaranteed andhigh safety is obtained.
Owner:SHANDONG TAIXIN ELECTRONICS CO LTD
System, terminal equipment and method for managing secret key based on security chip
ActiveCN102595198ASimple requirementsPrevent leakageSelective content distributionCiphertextTerminal equipment
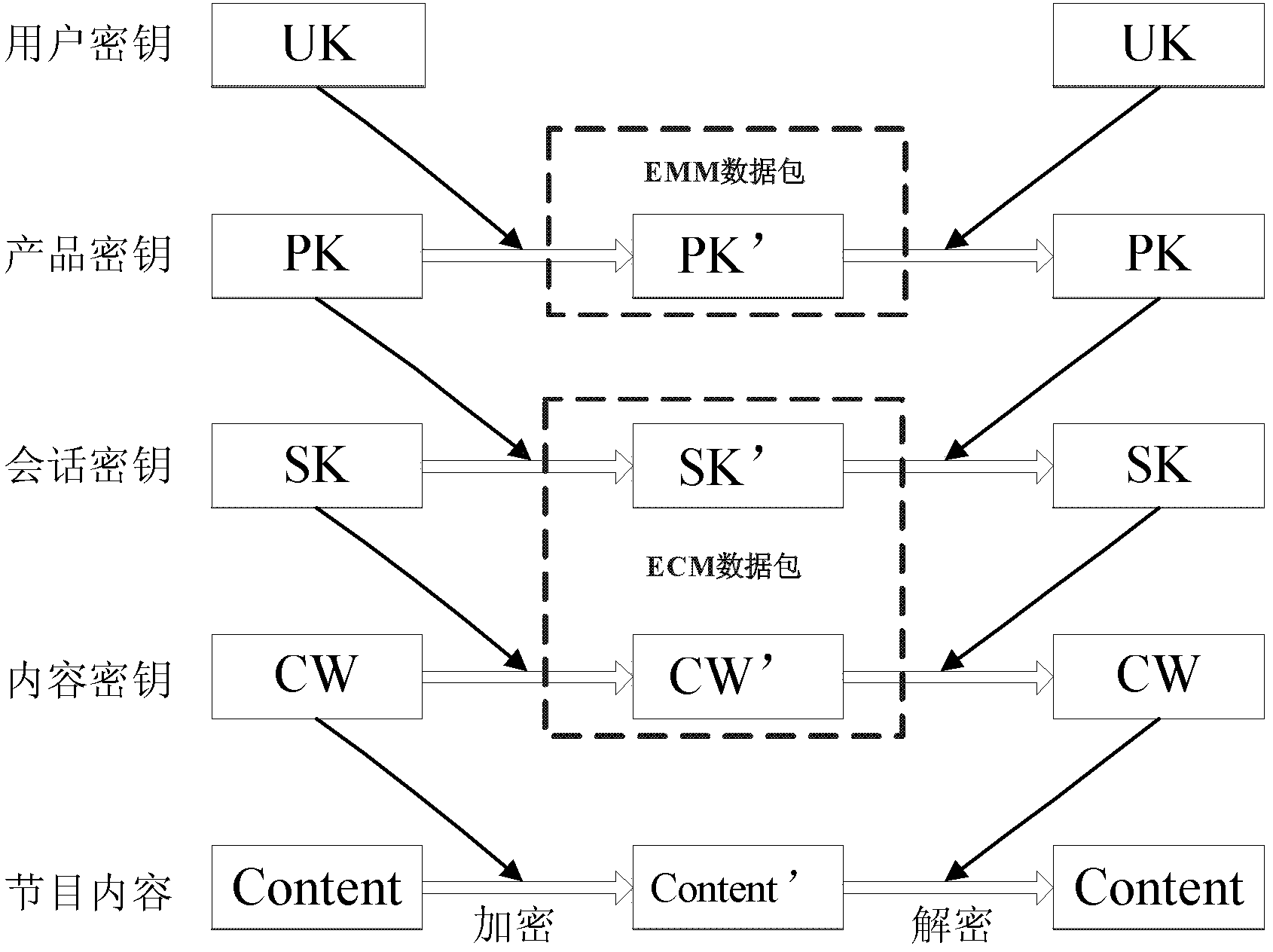
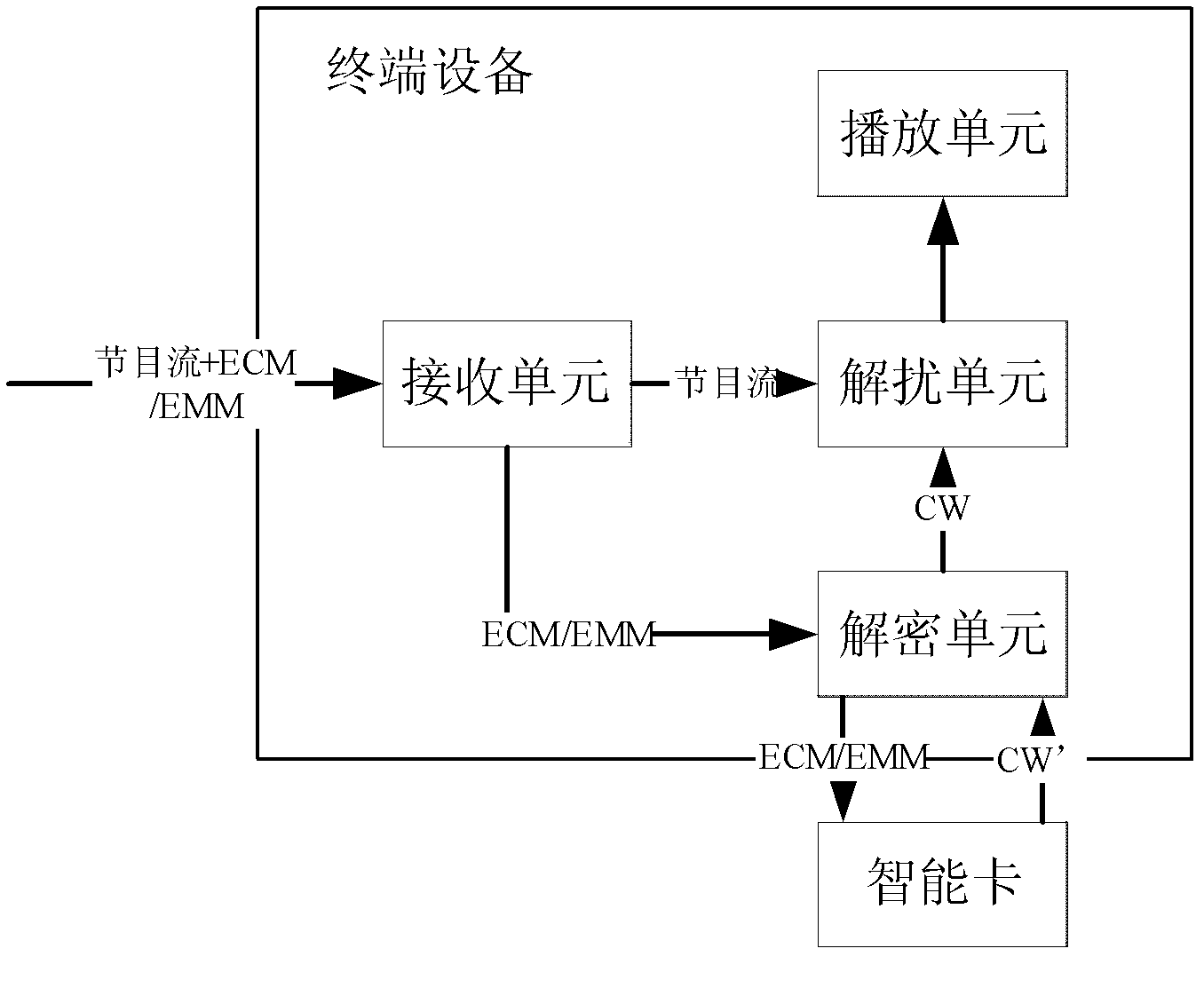
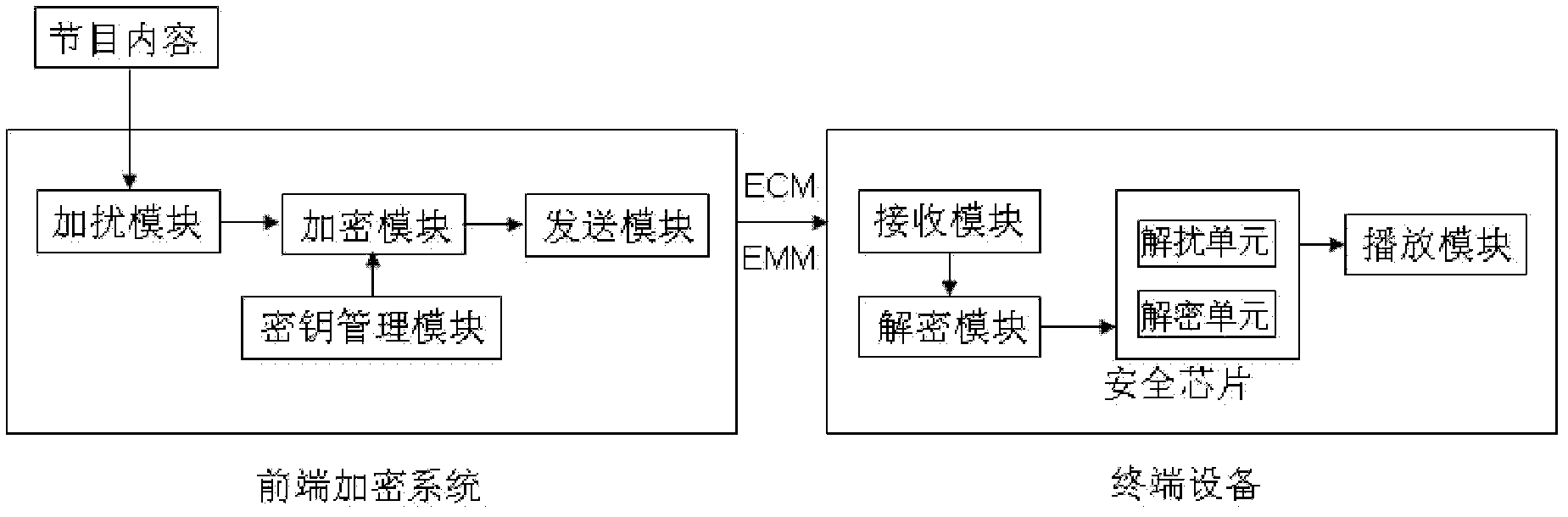
The invention discloses a system, terminal equipment and a method for managing a secret key based on a security chip. The system comprises a front-end encryption system and the terminal equipment, wherein the front-end encryption system comprises a scrambling module, an encrypting module, a secret key management module and a transmitting module; the scrambling module is used for generating a content secret key and scrambling program content; the secret key management module is used for managing a hierarchical secret key; the encrypting module is used for performing hierarchical secret key encryption on the scrambling data to form ciphertext data; the ciphertext data is transmitted to the terminal equipment through the transmitting module; the terminal equipment comprises a receiving module, a decrypting module, a security chip and a playing module; the receiving module is used for receiving the ciphertext data; the decrypting module is used for decrypting the ciphertext data primarily to obtain an encrypted content secret key; the encrypted content secret key is decrypted and descrambled in the security chip to obtain the program content; and the program content is played by the playing module. The content secret key is prevented from being leaked and shared, and the safety and the reliability of the system are improved.
Owner:北京视博数字电视科技有限公司
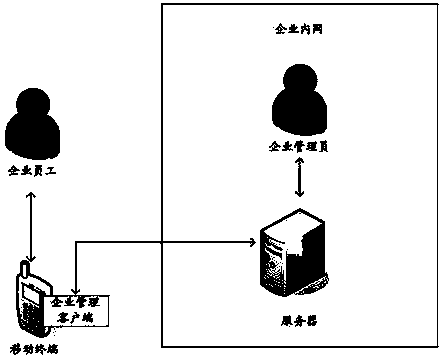
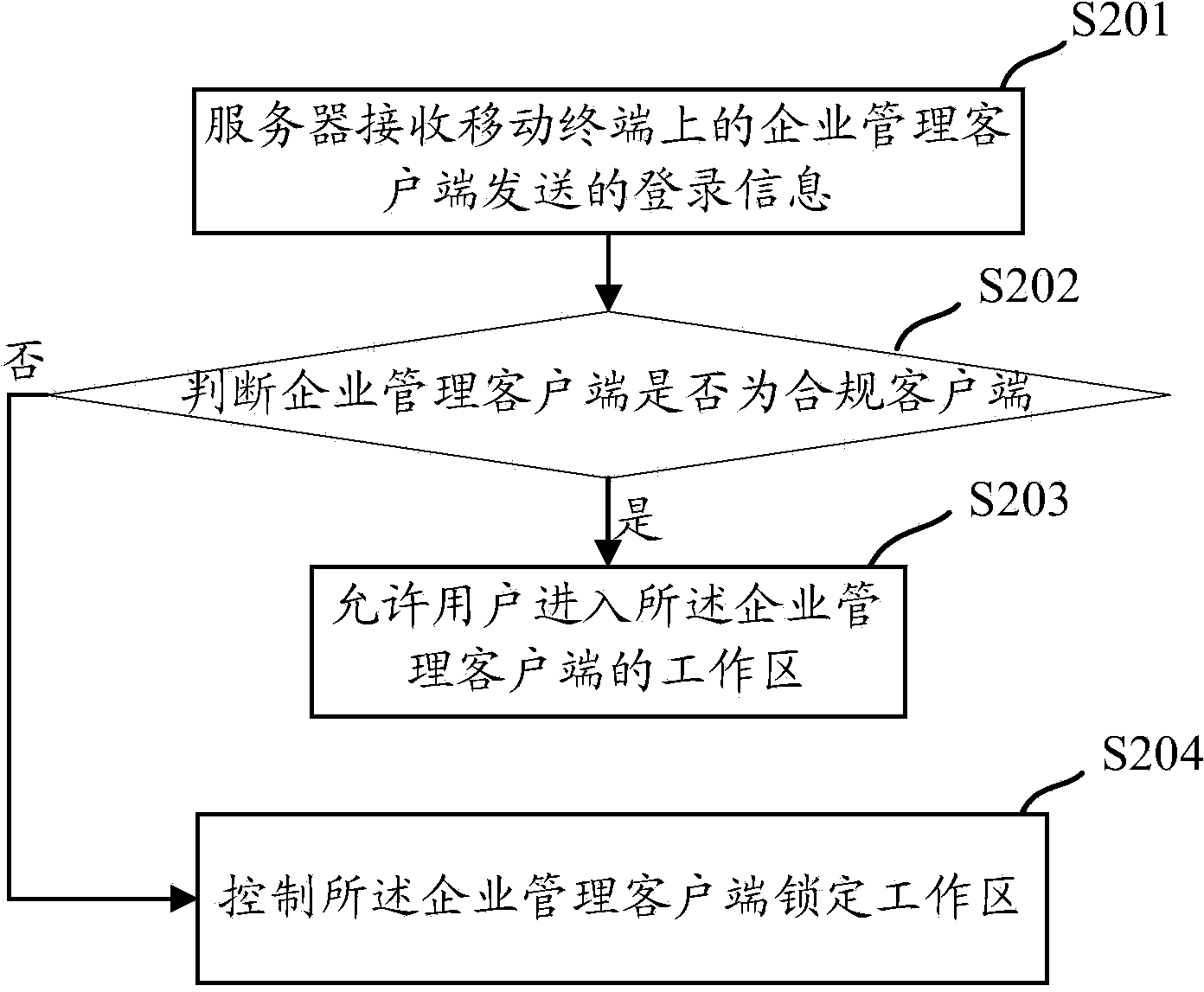
Method, system and device for locking working region of mobile terminal
InactiveCN103646198AAvoid uploadingProtection securityDigital data authenticationTransmissionComputer terminalClient-side
The invention provides a method for locking a working region of a mobile terminal, which is used for guaranteeing the information safety of the working region. According to the method, a server determines whether an enterprise management client is a compliant client according to a compliance detection rule stored by the server after receiving login information transmitted by the enterprise management client on the mobile terminal, and controls the enterprise management client to lock the working region when determining that the enterprise management client is non-compliant client. The embodiment of the invention also provides a corresponding device and system. In the embodiment of the invention, when the enterprise management client logins in every time, the server detects whether the enterprise management client is the compliant client, so that illegal users can be prohibited from entering the working region, uploading, sharing and leakage of data of the working region under the illegal condition can be avoided, and the safety of enterprise information is effectively protected.
Owner:BEIJING QIHOO TECH CO LTD +1
Information leakage testing control method, device and system and information channel safety certification device
ActiveCN103490893ALow costGuaranteed confidentialityUser identity/authority verificationTimestampApplication server
The invention provides an information leakage testing control method, device and system and an information channel safety certification device. The method comprises the steps of sending an information channel safety certification service request to a service information testing control processing server through a front-end processor, receiving information with the information source recognition function and a timestamp to send a dynamic electronic license, receiving user data information of POS equipment, conducting automatic recognition and checking on information source recognition characteristic parameter values, transmission information formats and content characteristic parameter values of the user data information, memorizing POS information source identification and information encoding in the user data information, reestablishing a retrieval tag, sending user upper-sending server processing data information to a short-micro message processing server in a split-channel mode, receiving short-micro messages fed back by the service information testing control processing server to conduct analyzing and splitting, converting information source equipment characteristics in the short-micro messages in a reversed mode to be transformed into original information source equipment characteristics in the user data information, and reassembling the short-micro messages to be fed back to a user application server.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Antenna and mobile terminal
ActiveCN106953176AAvoid sharingImprove antenna performanceSimultaneous aerial operationsAntenna equipments with additional functionsBand widthFeed point
The embodiment of the invention provides an antenna which comprises a metal shell and at least one feed source. The antenna further comprises a low-frequency matching circuit, a high-frequency matching circuit, a low-frequency feed point and a high-frequency feed point; a gap is formed on the metal shell, the gap divides the metal shell into an antenna radiation arm and main reference ground, one side edge of the metal shell is provided with a fracture, and the gap is communicated with the fracture; one end of the low-frequency matching circuit is connected with the other end of the feed source, the other end of the low-frequency matching circuit is connected with the low-frequency feed point, and the low-frequency feed point is positioned in the gap or at the position of the antenna radiation arm; and one end of the high-frequency matching circuit is connected with the other end of the feed source, the other end of the high-frequency matching circuit is connected with the high-frequency feed point, and the high-frequency feed point is positioned at the position of the antenna radiation arm. By separating the low-frequency matching circuit and the high-frequency matching circuit of the antenna excellent antenna performance in a wide frequency band can be achieved, and the antenna is excellent in both bandwidth and efficiency.
Owner:VIVO MOBILE COMM CO LTD
Micro valve capable of controlling liquid flowing and micro flow control chip
ActiveCN108443579AAvoid sharingAvoid mutual contaminationValve arrangementsLaboratory glasswaresPollutionBiomedical engineering
The invention relates to a micro valve capable of controlling liquid flowing. The micro valve comprises a valve body. The valve body comprises at least two flow guiding channels which are not in communication. The invention further relates to a micro flow control chip. The micro flow control chip comprises a substrate and a cover sheet, and the micro valve capable of controlling liquid flowing anda micro valve inserting hole used for receiving the micro valve are further included. The substrate is provided with a liquid storage groove and a micro channel, and the liquid storage groove and themicro channel are covered with the cover sheet and sealed. The micro channel is connected with the micro valve inserting hole. The micro flow control chip design and the micro flow control micro valve have the beneficial effects that the structure is simple, assembling is convenient, and repeated usage can be achieved; and the structure can be used for long-term effective sealing of a detection reagent in a testing sheet. Meanwhile, due to the flow guiding channels on the micro valve and the micro channel design on the substrate, the situation of flow guiding channel sharing can be avoided, and accordingly, the possibility of mutual pollution between fluid can be avoided.
Owner:LEADWAY HK
Automobile temperature regulating system
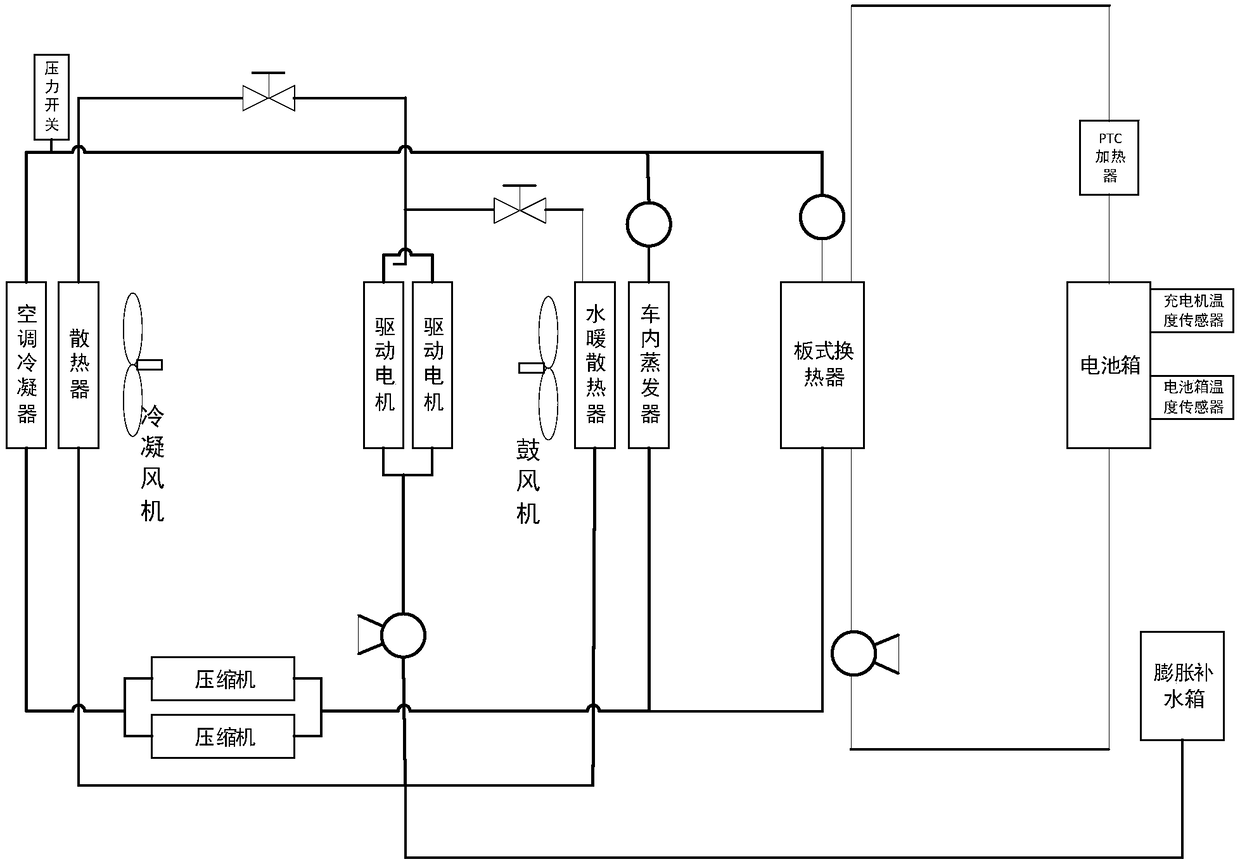
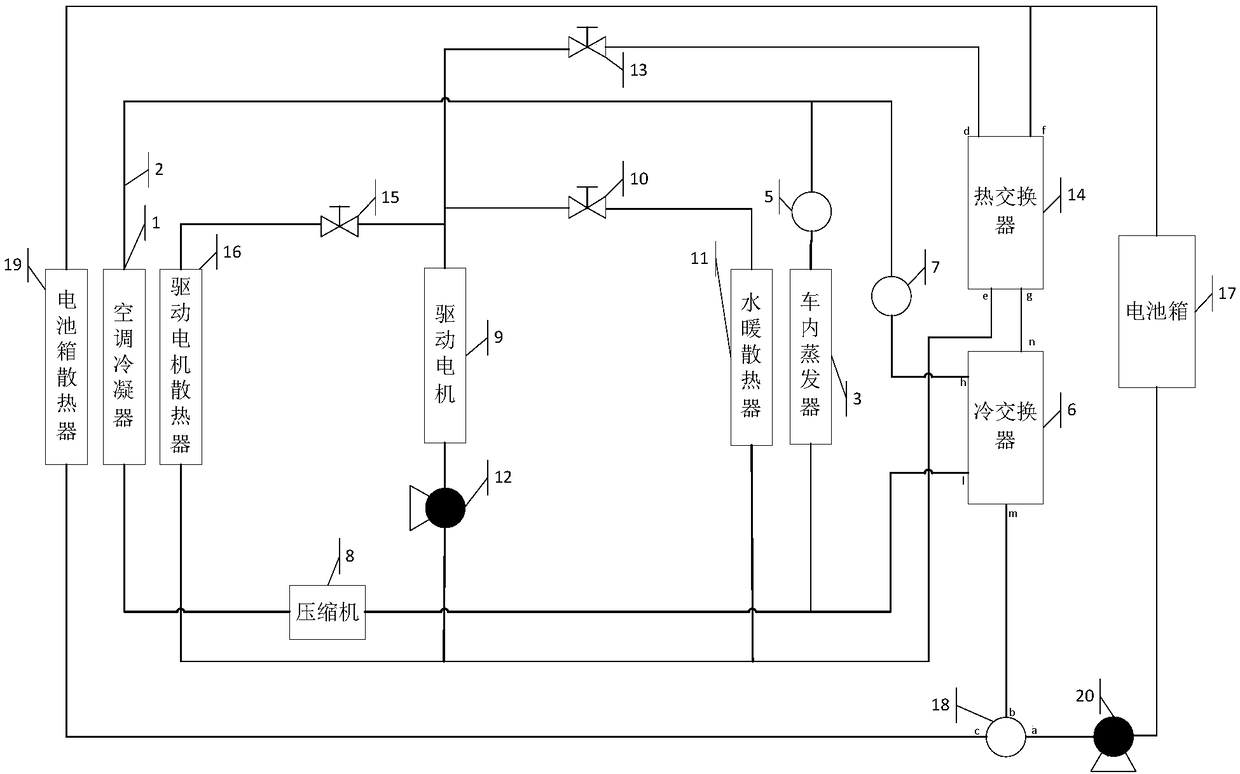
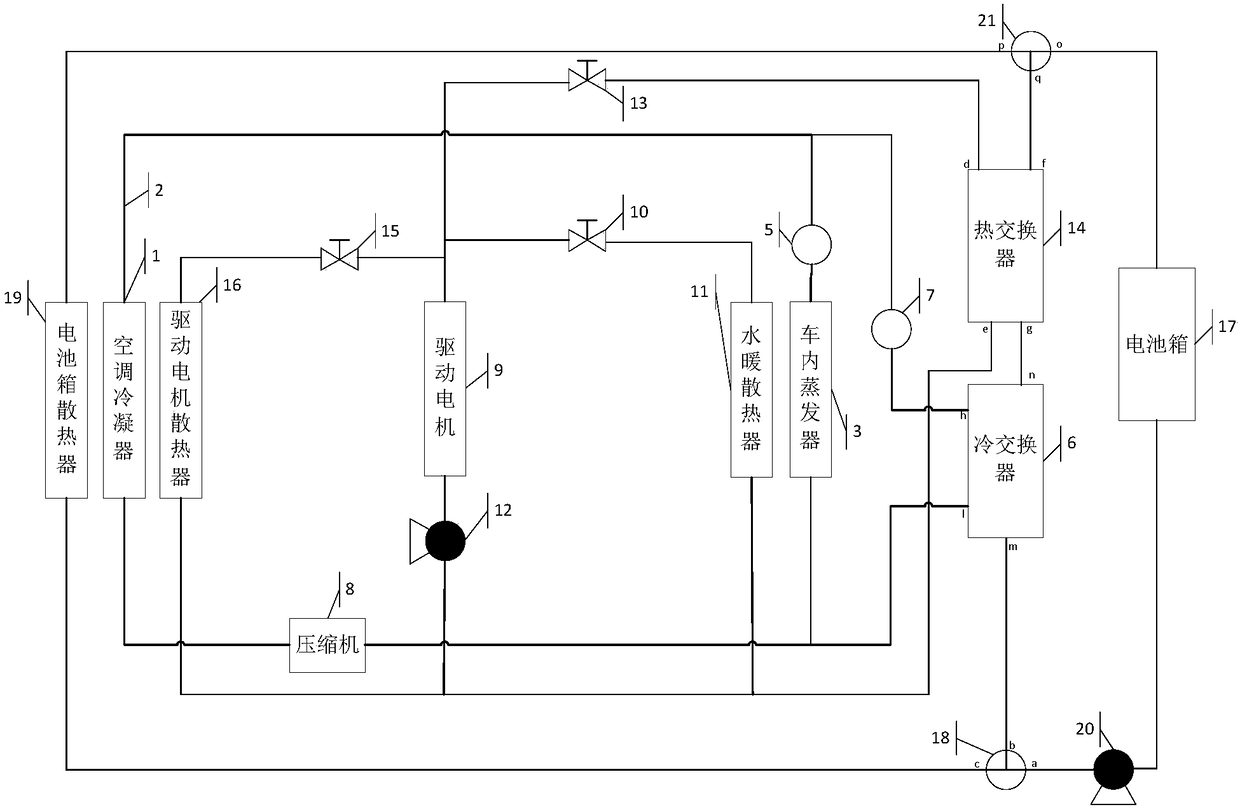
PendingCN108357328AImprove cooling efficiencyAvoid sharingAir-treating devicesSecondary cellsElectricityResource utilization
The invention discloses an automobile temperature regulating system. A heat exchanger and a cold exchanger are arranged in the automobile temperature regulating system. When a battery box needs to beheated, the heat produced by a driving motor can be utilized to heat the battery box by indirectly introducing heat in the driving motor into the battery box through the heat exchanger, so that consumption of electricity produced during heating based on PTC is avoided, the electricity of a system is saved, and resource utilization rate is improved.
Owner:珠海长欣汽车智能系统有限公司
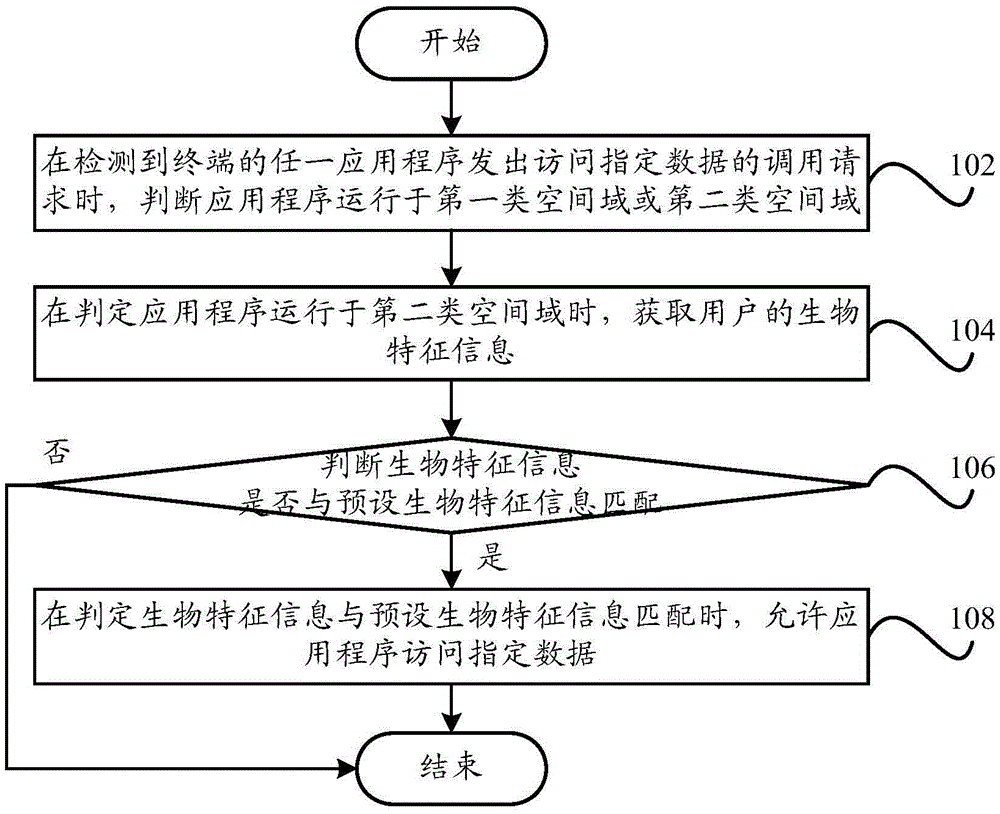
Data access method, data access system and terminal
InactiveCN105631293AAchieve sharingAvoid sharingDigital data protectionDigital data authenticationAccess methodData access
The invention provides a data access method, a data access system and a terminal. The data access method comprises the steps that when it is detected that any application program of the terminal sends out a call request for accessing designated data, whether the application program runs in the first-class space domain or the second-class space domain is judged; when it is determined that the application program runs in the second-class space domain, biological feature information of a user is obtained; whether the biological feature information is matched with preset biological feature information or not is judged; when it is determined that the biological feature information is matched with the preset biological feature information, the application program is allowed to access the designated data. According to the technical scheme, private data of the same application program in the different space domains can be stored in the safe domain (namely the first-class space domain), and the storage space of the terminal is saved; meanwhile, due to the matching of the user biological feature information and the preset biological feature information, the running efficiency of the application program is improved, and user private information is effectively protected.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
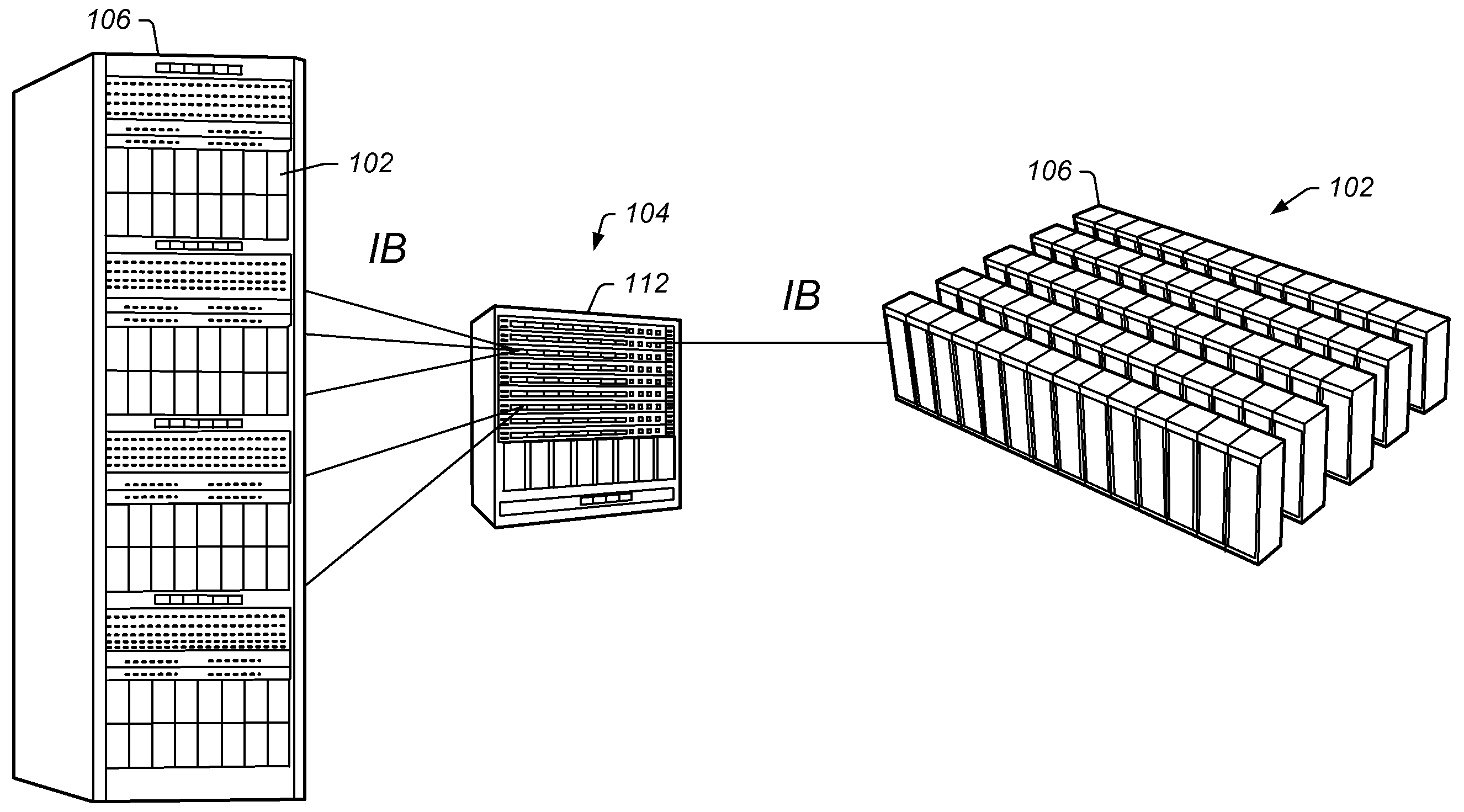
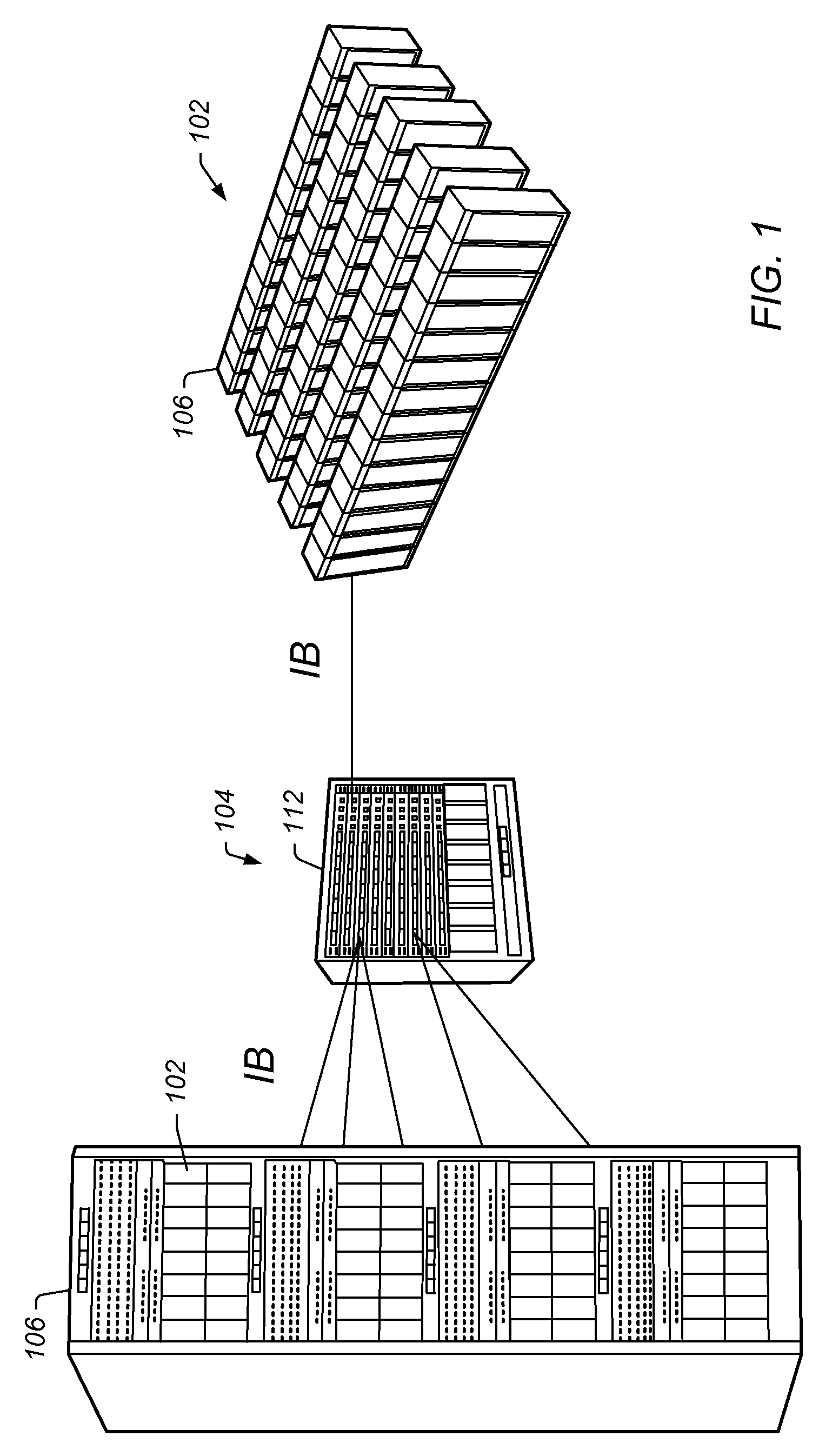
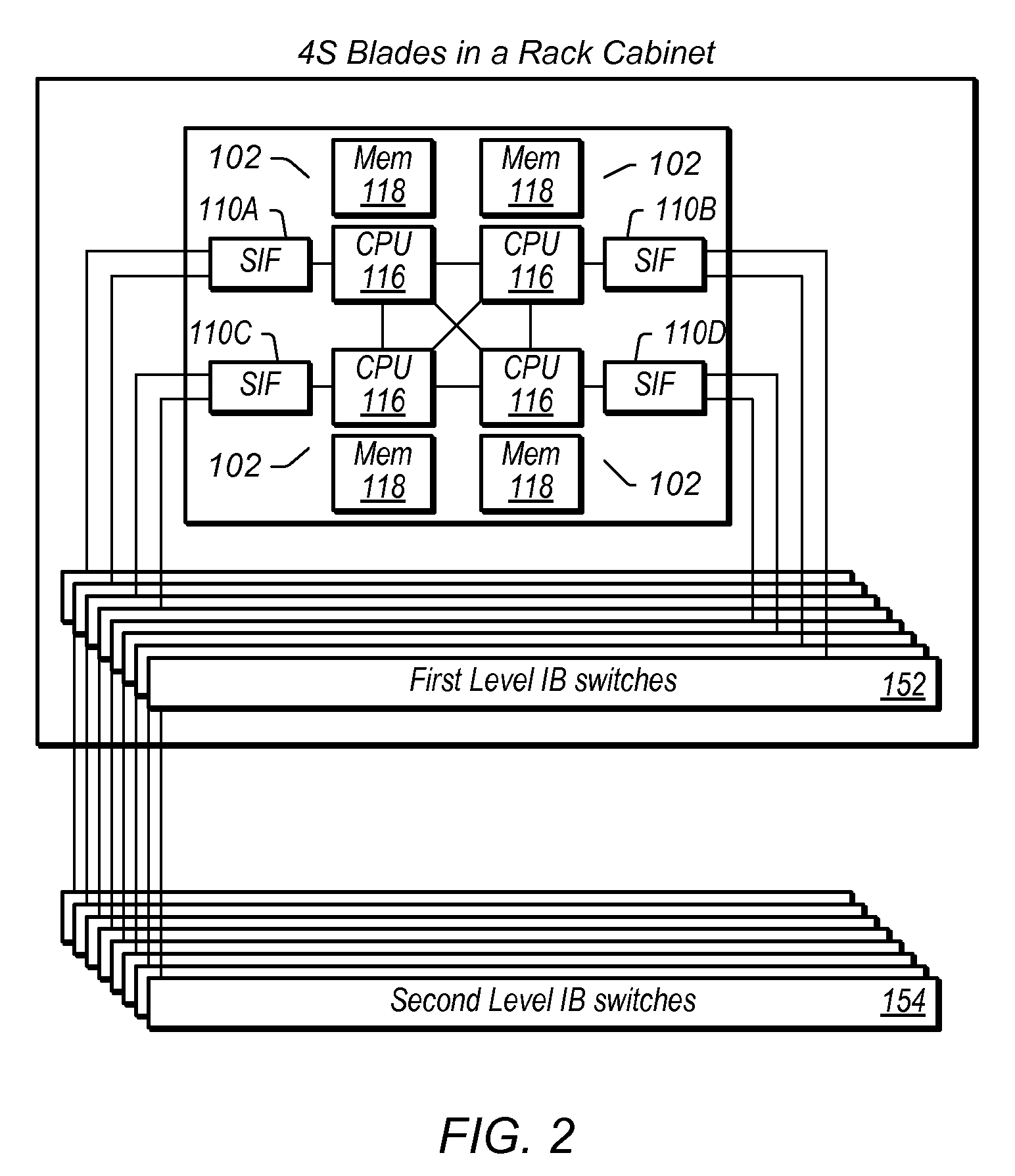
Multiple Processes Sharing a Single Infiniband Connection
ActiveUS20100329275A1Improve network performanceReduce system costData switching by path configurationRemote computingDistributed computing
A compute node with multiple transfer processes that share an Infiniband connection to send and receive messages across a network. Transfer processes are first associated with an Infiniband queue pair (QP) connection. Then send message commands associated with a transfer process are issued. This causes an Infiniband message to be generated and sent, via the QP connection, to a remote compute node corresponding to the QP. Send message commands associated with another process are also issued. This causes another Infiniband message to be generated and sent, via the same QP connection, to the same remote compute node. As mentioned, multiple processes may receive network messages received via a shared QP connection. A transfer process on a receiving compute node receives a network message through a QP connection using a receive queue. A second transfer process receives another message through the same QP connection using another receive queue.
Owner:ORACLE INT CORP
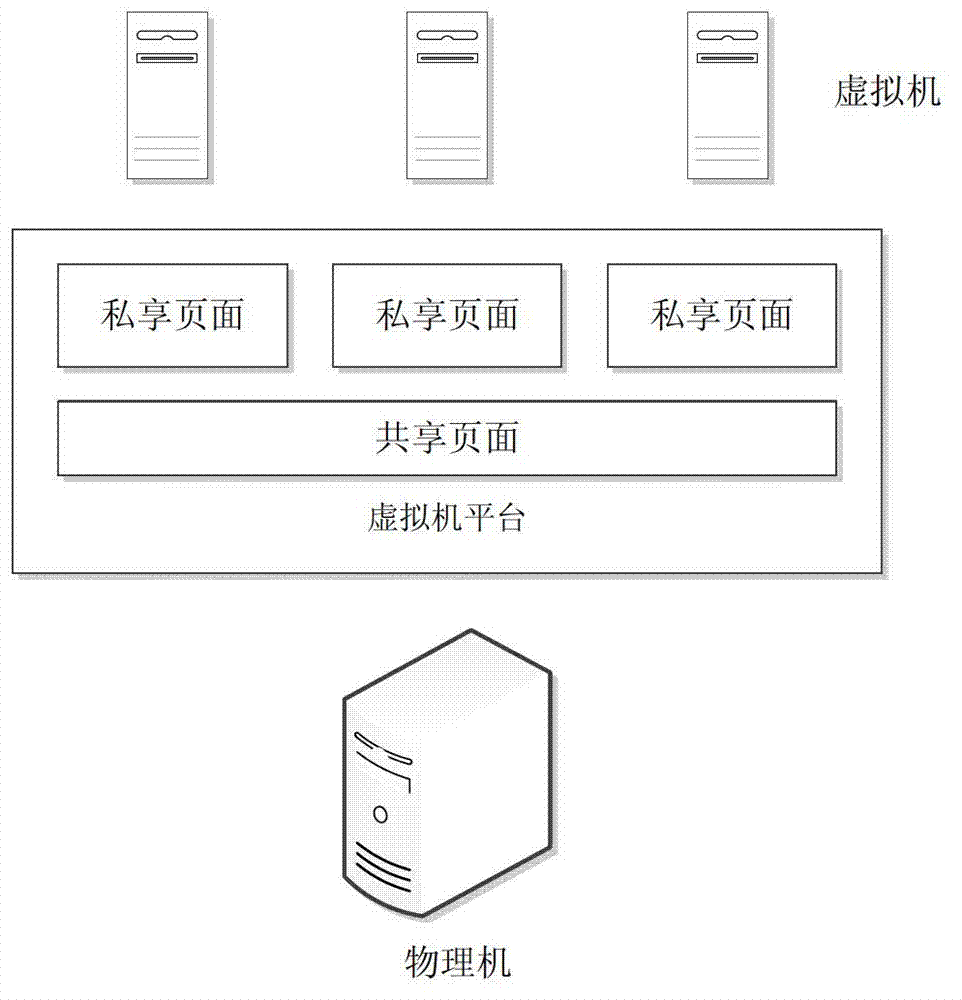
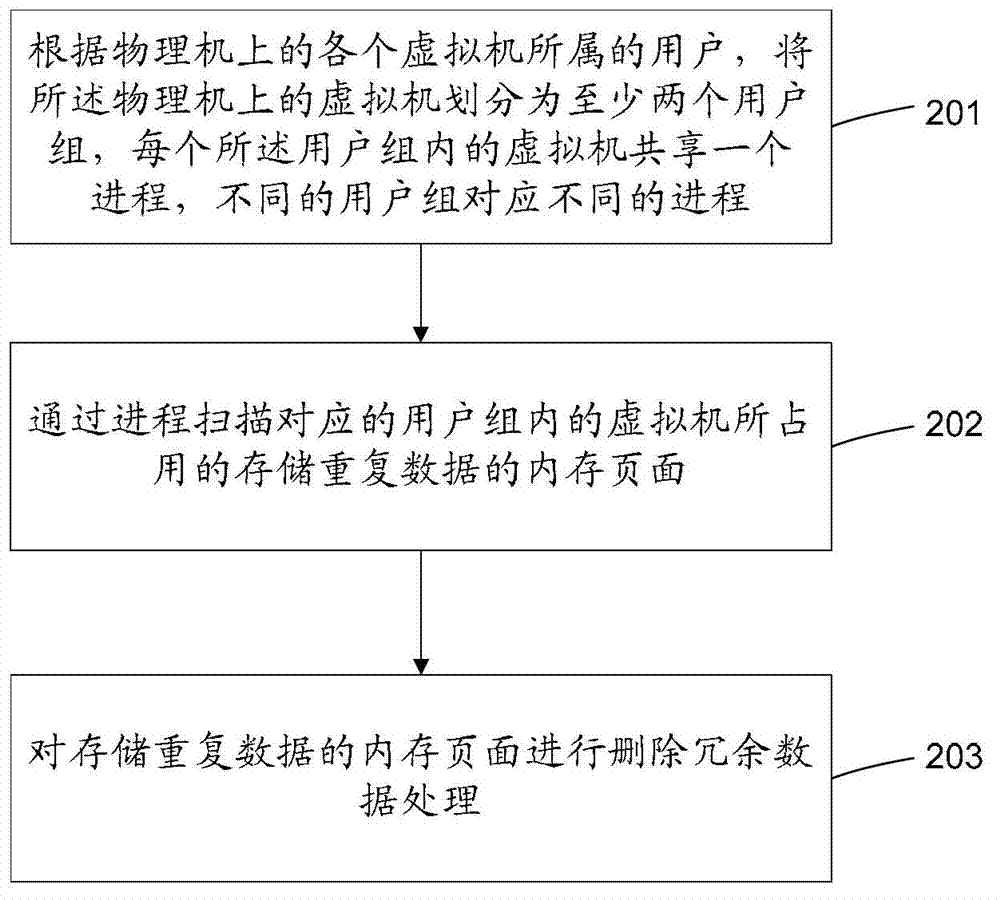
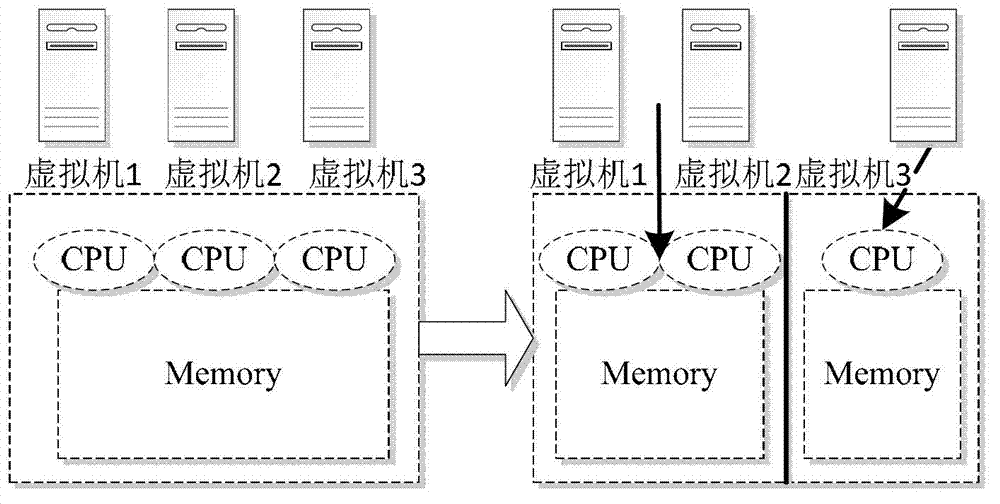
Memory sharing method and device for virtual machine
InactiveCN103034591AAvoid sharingMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationMemory sharingVirtual machine
The invention provides a memory sharing method and device for a virtual machine. The method comprises the steps of: dividing the virtual machine on a physical machine into at least two user groups according to the users to whom the virtual machines on the physical machine belong, wherein the virtual machine in each user group shares a progress, and different user groups correspond to different progresses; scanning a memory page occupied to store repeated data by the virtual machine in the corresponding user group according to the progress; deleting redundant data of the memory page where repeated data is stored; and further comprising: re-distributing the memory page released by deletion of redundant data to the virtual machines in corresponding user groups. According to the method and device provided by the invention, sensitive information of the user is prevented from being shared by other virtual machines when the virtual machines share the memory.
Owner:BEIHANG UNIV
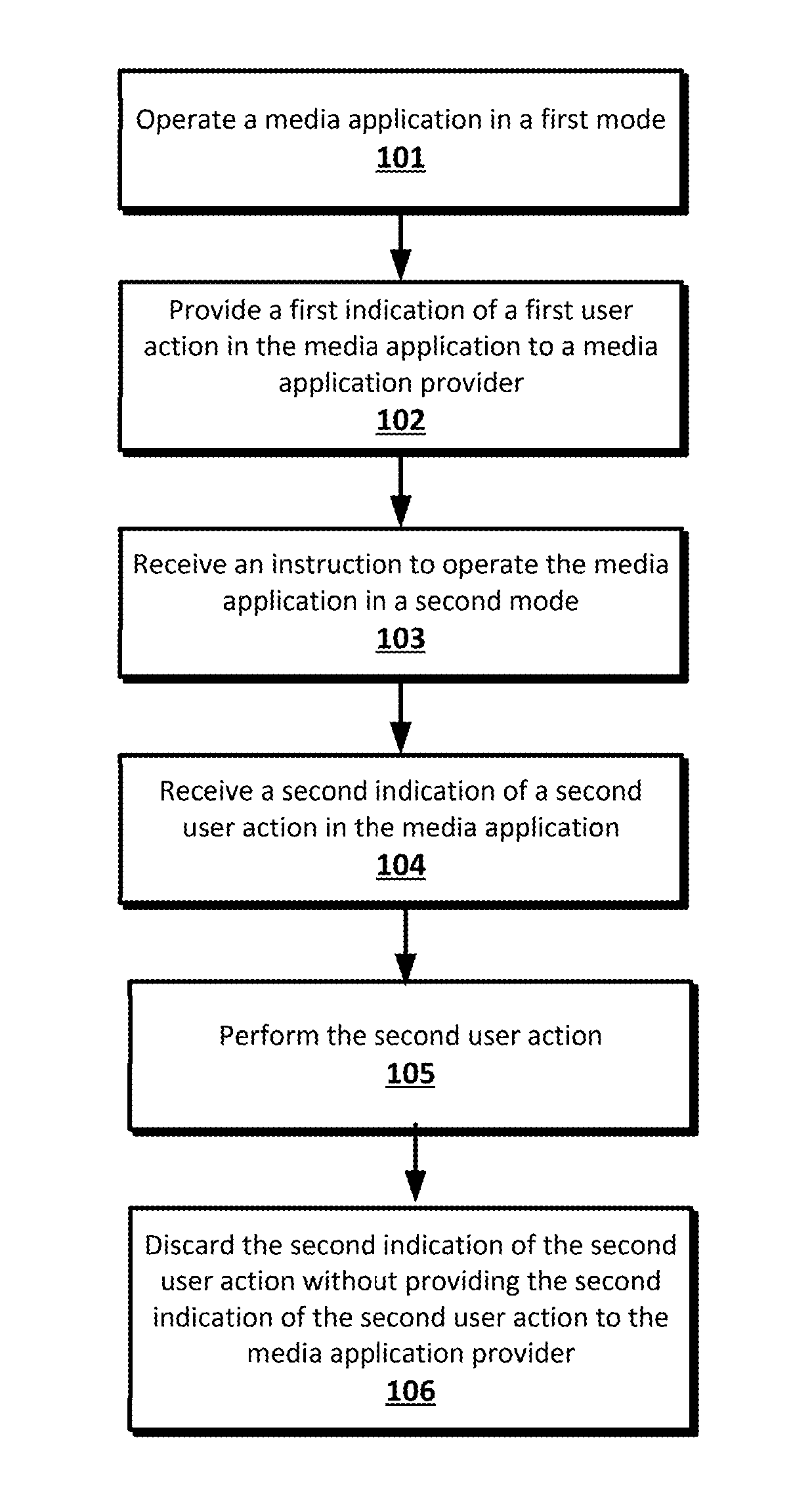
Incognito Mode in a Media Application
Implementations of the disclosed subject matter provide techniques for operating a media application in an incognito mode. A method may include operating a media application in a first mode and providing a first indication of a first user action in the media application to a media application provider. Next, an instruction may be received to operate the media application in a second mode. A second indication of a second user action may be received in the media application and the second user action may be performed. Then, the second indication of the second user action may be discarded without providing the second indication of the second user action to the media application provider.
Owner:GOOGLE LLC
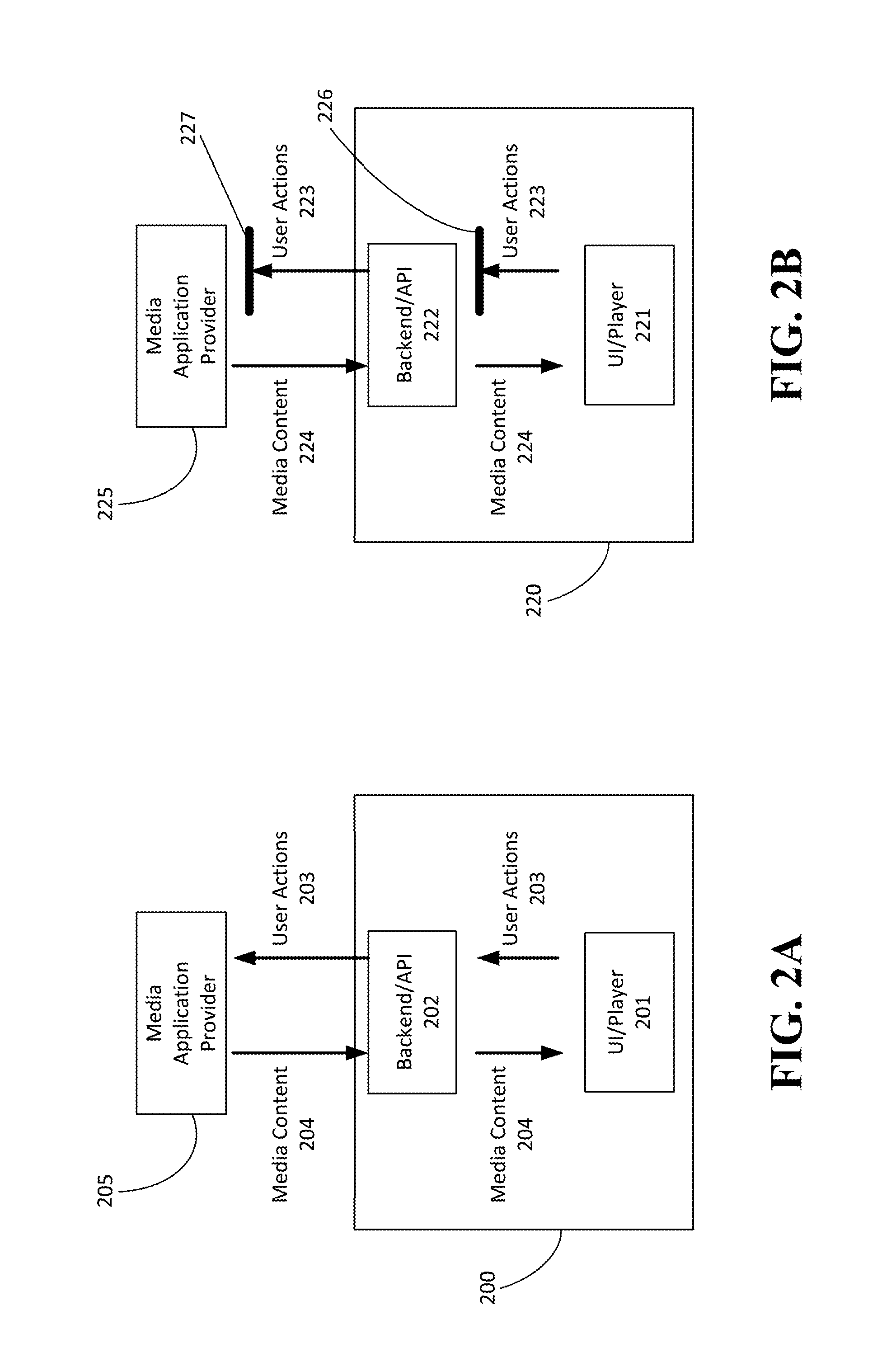
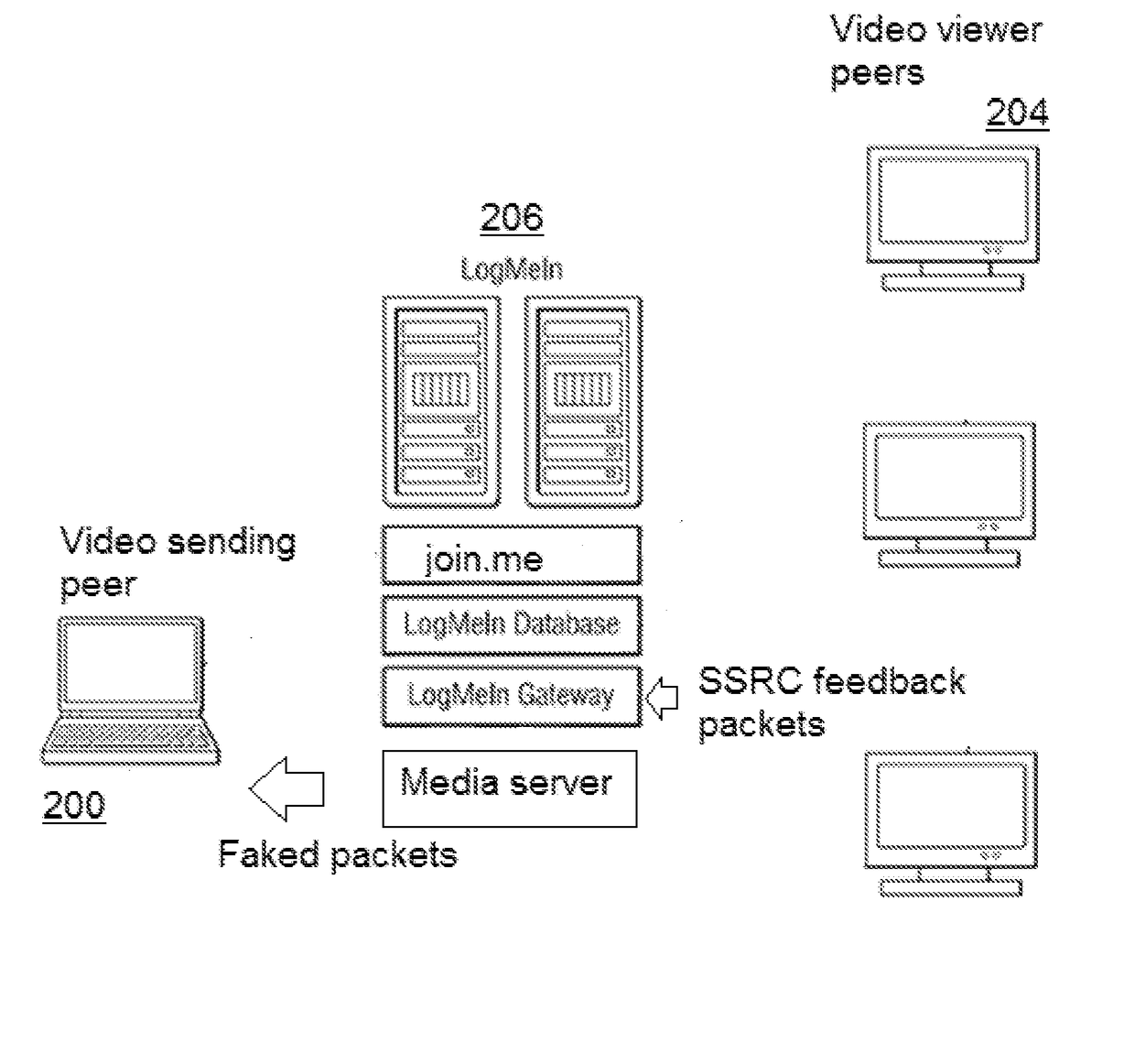
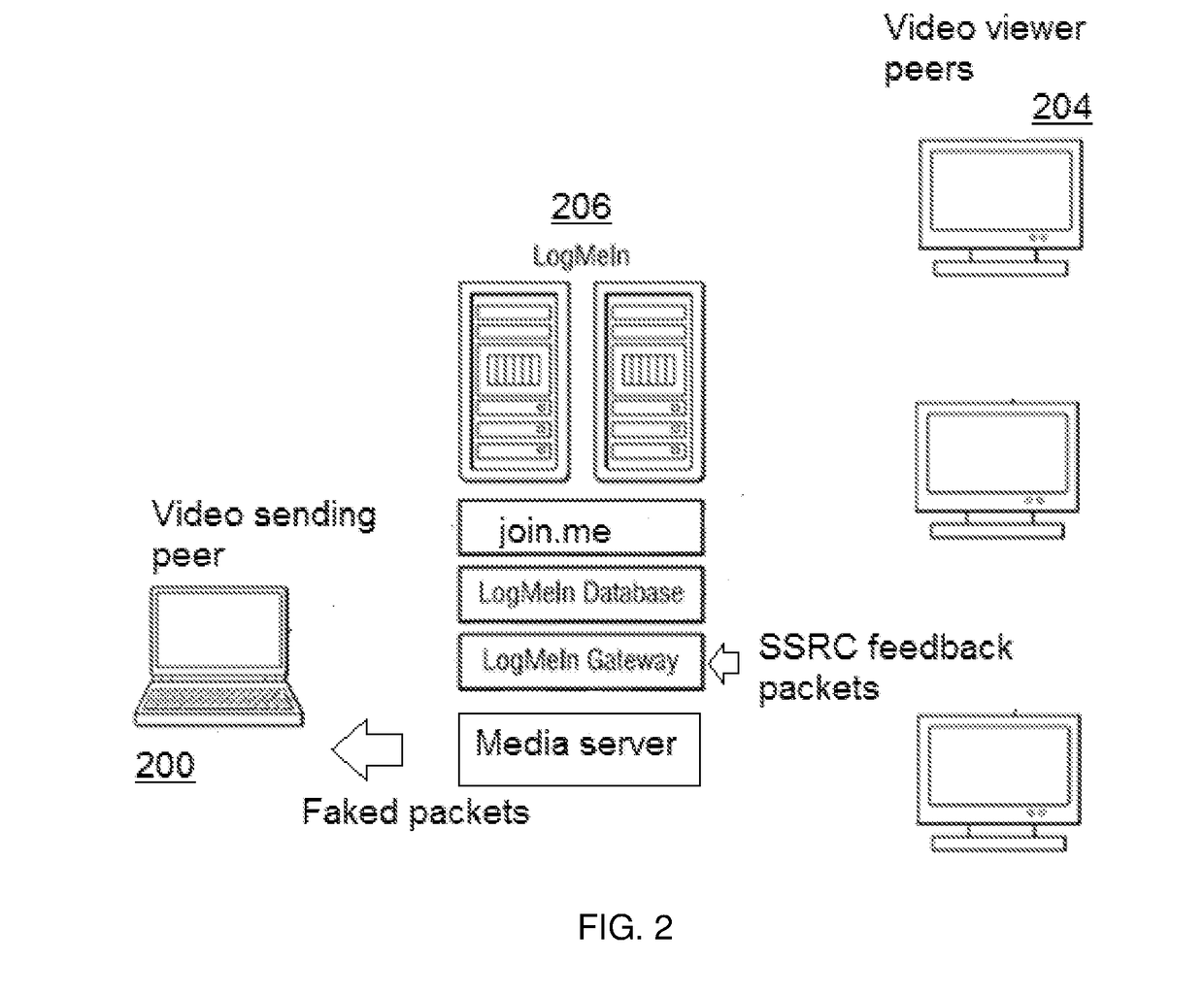
Scalable real-time videoconferencing over WebRTC
InactiveUS20170359187A1Avoids sharing SSRCsMinimize the numberSpecial service provision for substationTelevision conference systemsVideo senderMedia server
A WebRTC-compliant media server avoids sharing the SSRCs of passive participants (namely, the video viewers who do not send video) by intercepting feedback packets (issued from the viewers) on the server side, modifying those packets, and then transmitting the modified packets back to the sender such that, when the sender receives these feedback packets, the sender treats the packets as if they were sent by a known SSRC. Preferably, the known SSRC is one that is associated with a single SSRC (e.g., a dummy or surrogate SSRC, or a technical SSRC, in either event that was previously shared with the video sender). The sender knows how to handle these packets and can then send the desired answer to the viewer(s) to maintain the conference stable and operational even as the number of participants grows and exceeds the SSRC peer limitations.
Owner:LOGMEIN INC
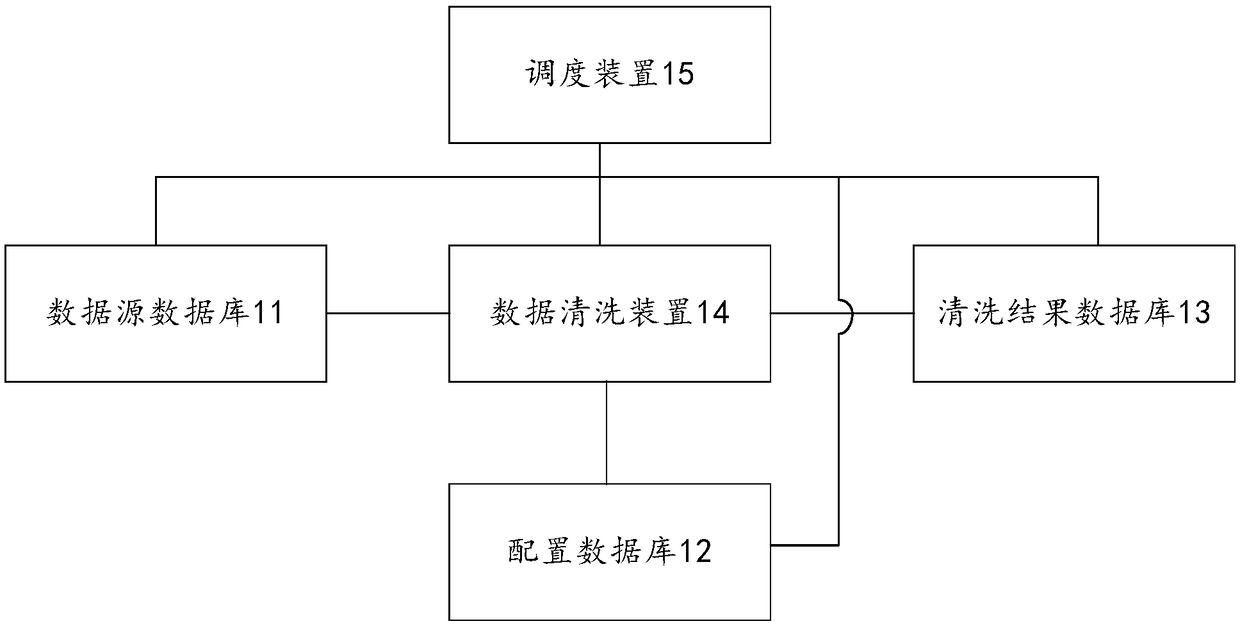
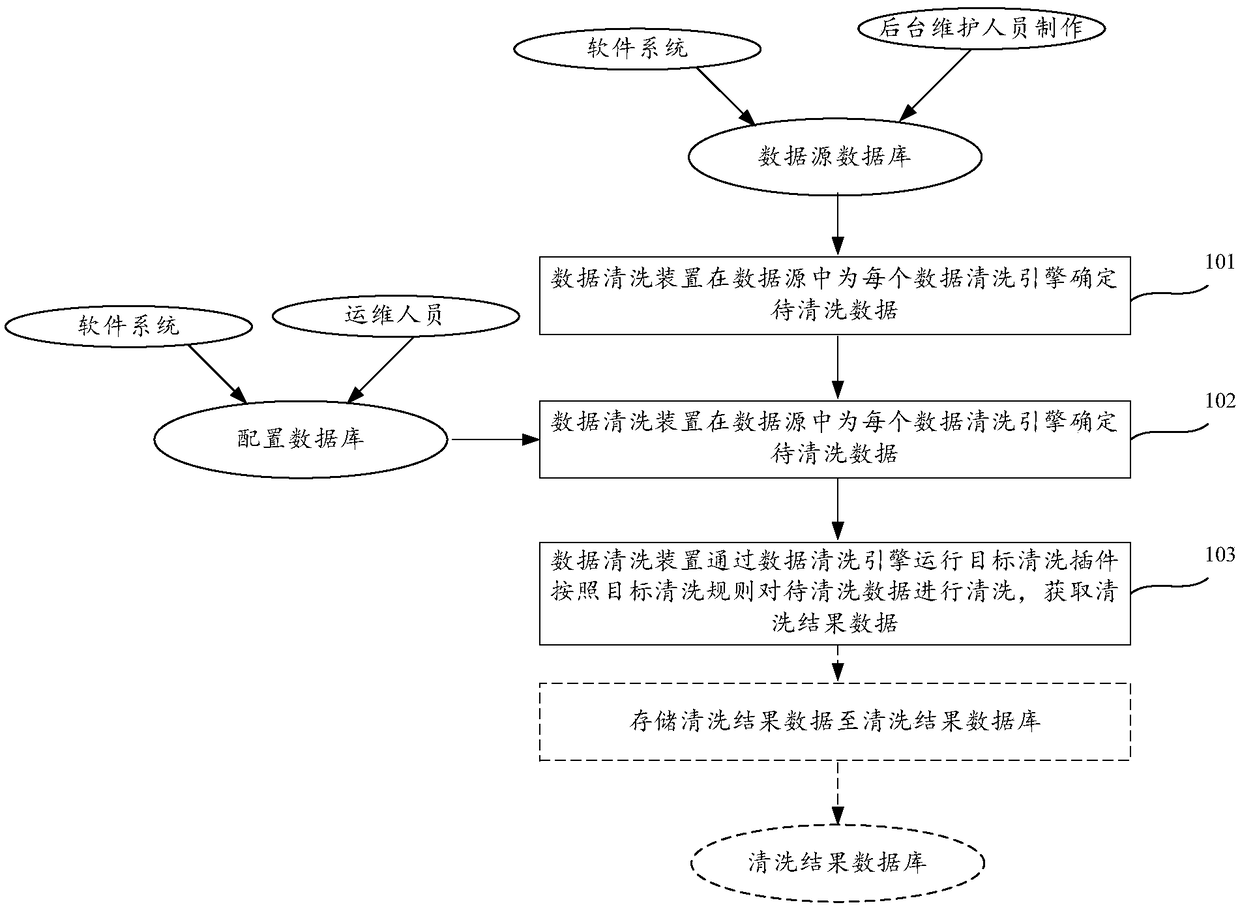
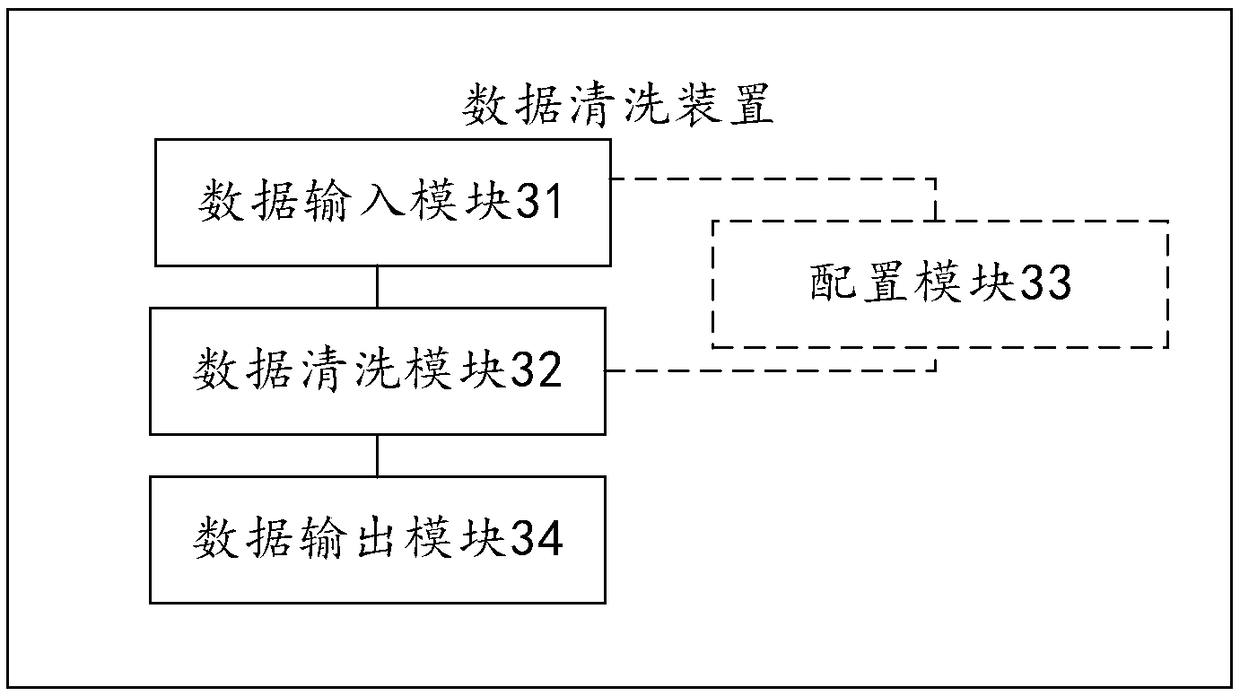
A data cleaning method and device
PendingCN109033274AAvoid sharingAchieve coordinationSpecial data processing applicationsData selectionData source
The embodiment of the invention discloses a data cleaning method and device, which relate to the data processing field and can realize dynamic data cleaning on a data cleaning engine. The method comprises the following steps of: determining data to be cleaned for each data cleaning engine in a data source; Selecting a target cleaning rule for the to-be-cleaned data in at least one pre-stored cleaning rule according to the type of the to-be-cleaned data; Invoking a target cleaning plug-in in at least one pre-stored cleaning plug-in according to the target cleaning rule; Wherein each of the cleaning rules corresponds to at least one cleaning plug-in; The target cleaning plug-in is operated by the data cleaning engine to clean the data to be cleaned according to the target cleaning rule to obtain the cleaning result data.
Owner:BANK OF CHINA
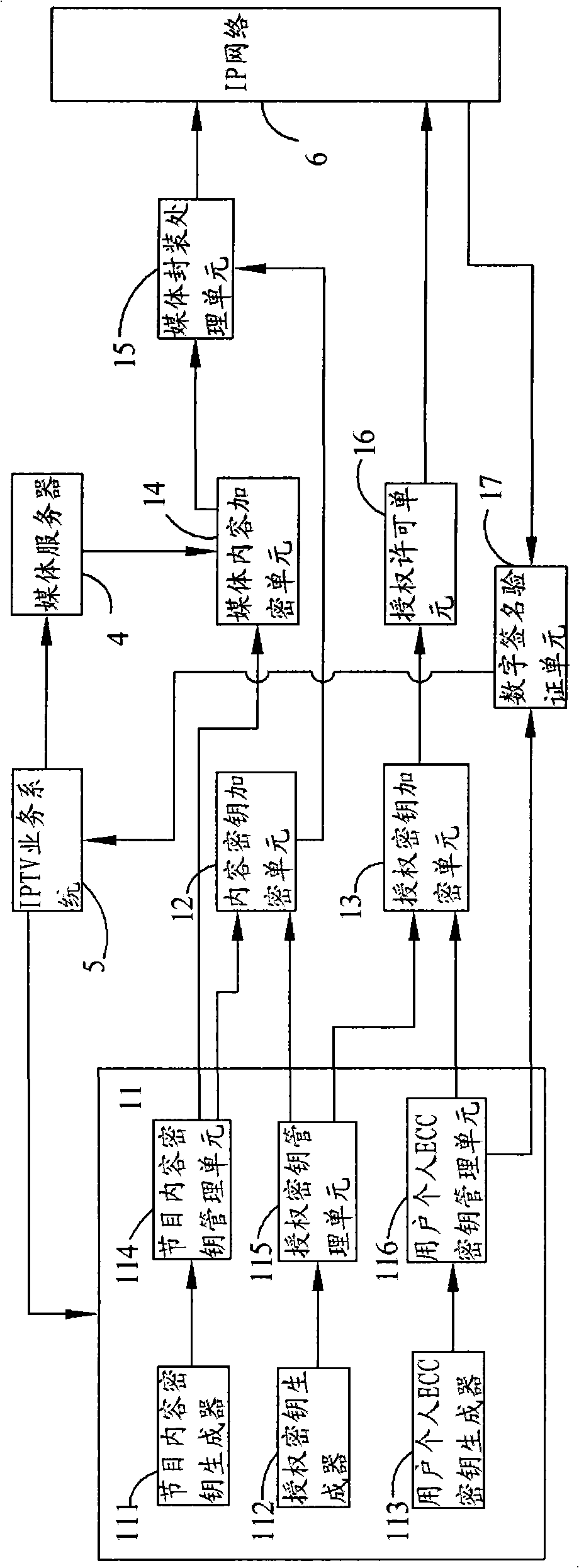
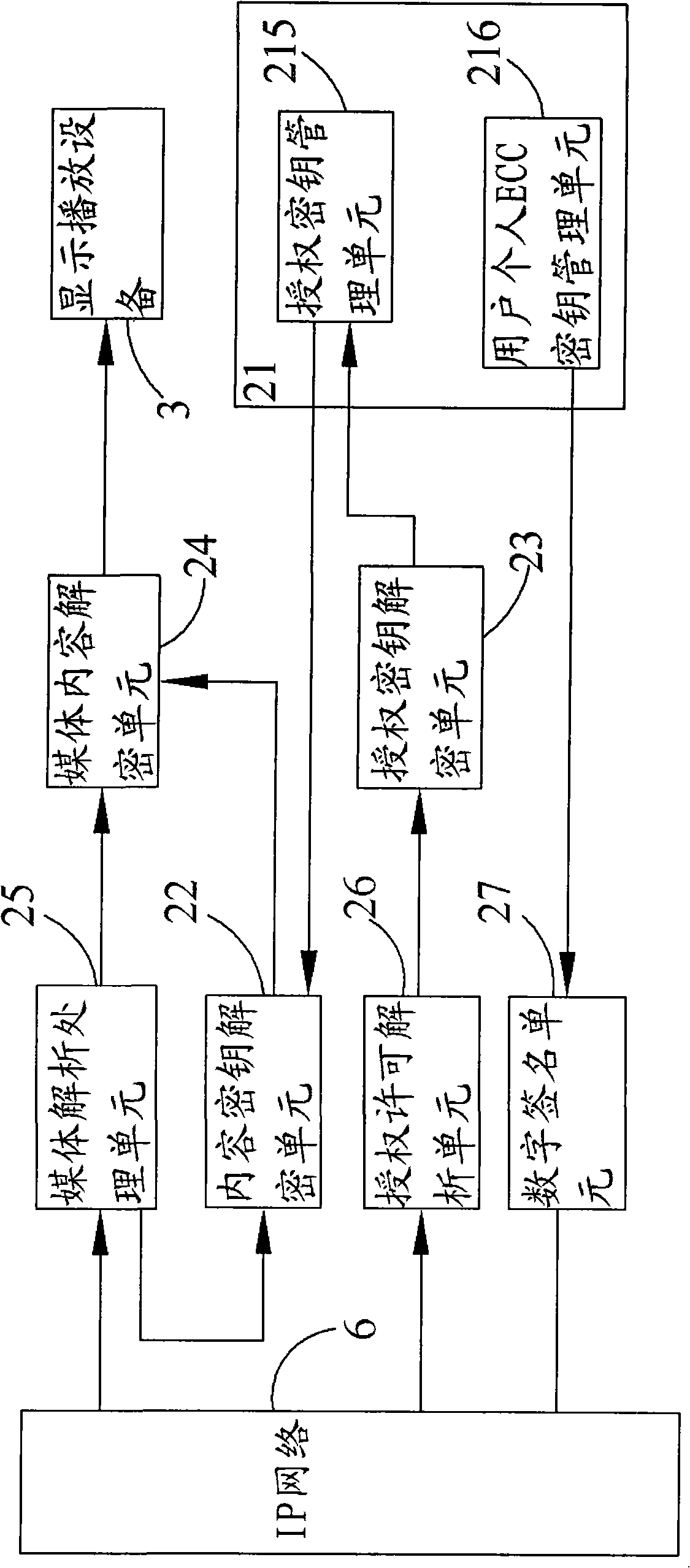
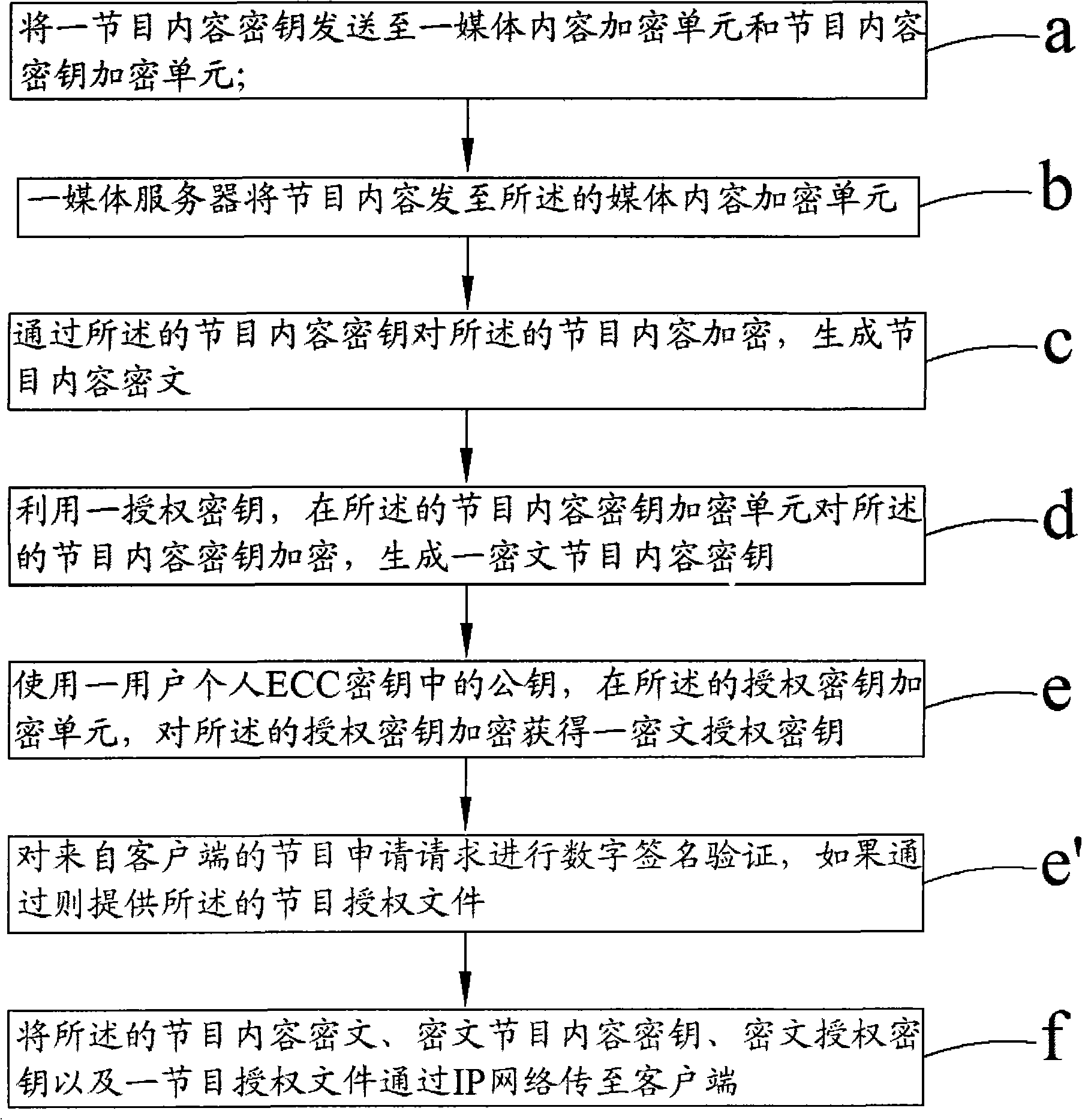
Encrypting/decrypting system and encrypting/decrypting method for interactive network television
ActiveCN101640785AAvoid sharingAvoid distributingAnalogue secracy/subscription systemsCryptogramBroadcast service
The invention discloses an encrypting / decrypting system and an encrypting / decrypting method for an interactive network television. By using a cryptographic algorithm approved by the national cryptogram management department, adopting a secure three-layer key system, namely a program content key, an authorized key and a user personal ECC key pair, and adopting a mature identity authentication technique, the security of a service system is protected, so the identity authentication problem of the system can be solved, and simultaneously the security protection for on-demand and living broadcast services also can be realized.
Owner:AEROSPACE INFORMATION
Window shield identification method for sharing application program
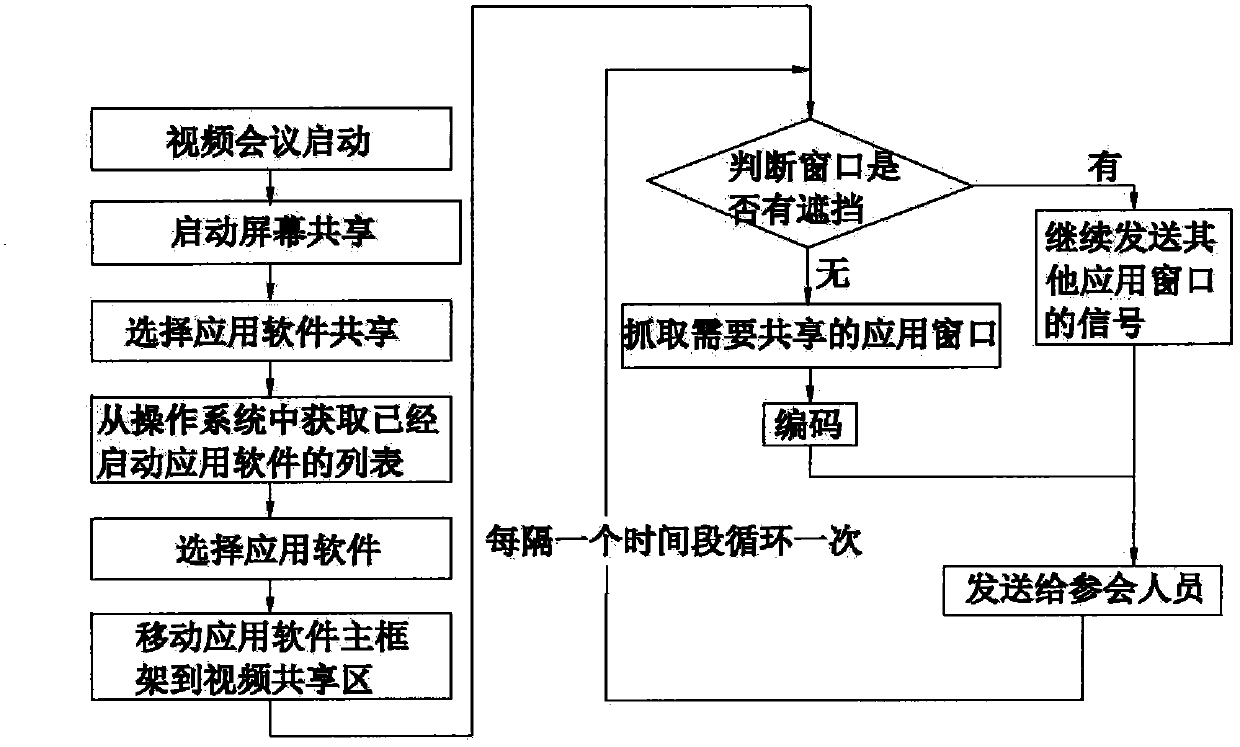
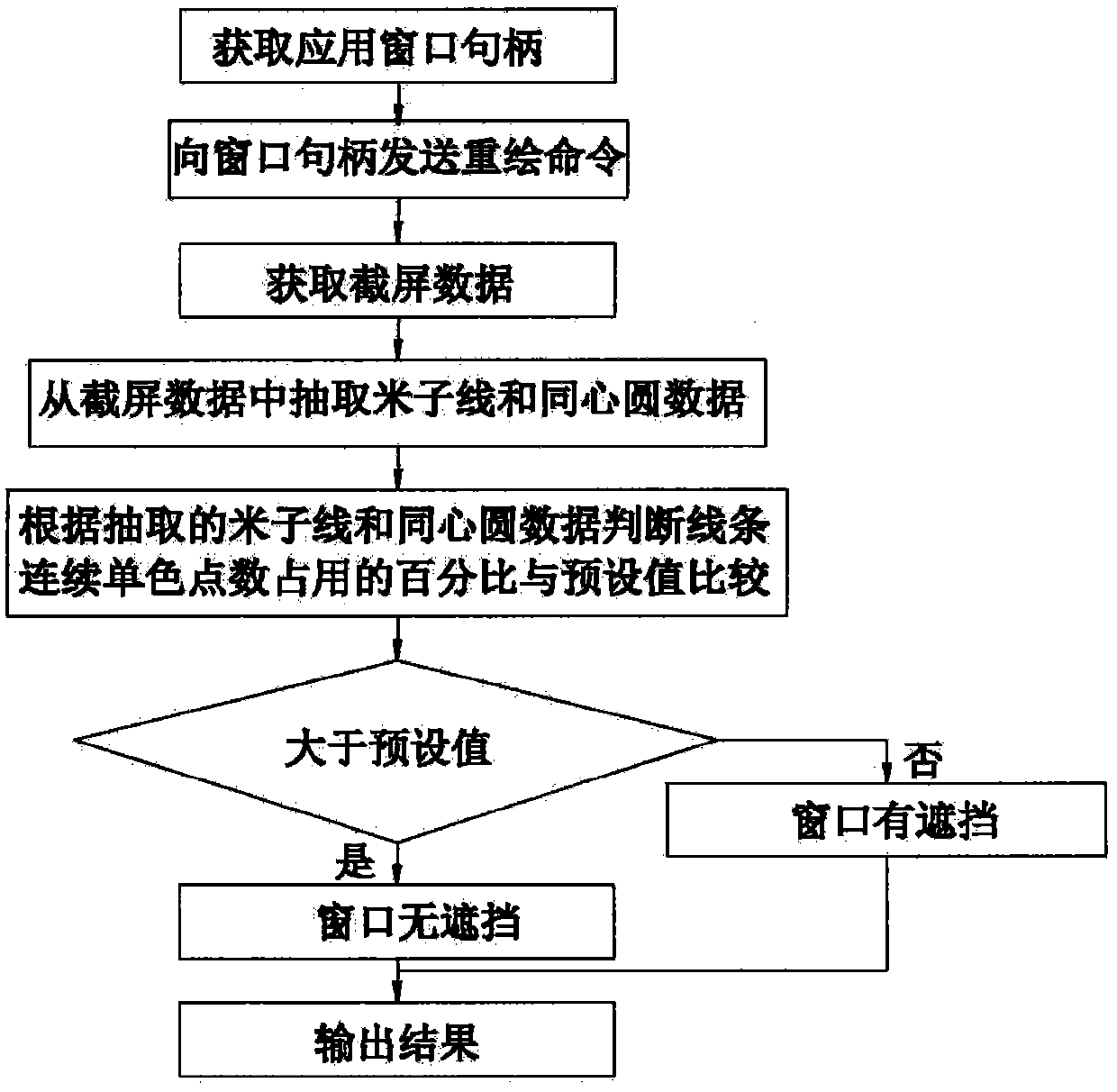
InactiveCN103475850AImprove smooth performanceAvoid sharingTelevision conference systemsTwo-way working systemsScreen sharingVideo sharing
The invention discloses a window shield identification method for sharing an application program. The method comprises the following steps: determining whether an application window needing to be shared is shielded by other application windows in a video sharing area; if so, continuously sending the signals of other conference application windows to conference participants and continuously ensuring that the application windows of the conference participants are not refreshed or don't contemporarily stop; and otherwise, sending the signals of the application window needing to be shared to the conference participants and enabling the application windows of the conference participants to be refreshed to the application window needing to be shared. According to the window shield identification method for sharing the application program, a specified application program window can be shared in conventional screen sharing so that network data fluency can be improved, personal information is prevented from being shared with the conference participants in case of maloperation, and the problem can be solved that a small black block occurs after a window is shielded when a specified window is shared.
Owner:SHENZHEN INPOR CLOUD COMPUTING CO LTD
A broadband access method and device
The related broadband access method and device comprise: the user broadband device obtains internet IP and DNS addresses based on PPPoE or PPPoA, and allocates all of the IP and DNS addresses, virtual mask and gateway to user terminal device through DHCP. This invention ensures one broadband channel only for one terminal device communicating with internet, and prevents multiple users sharing one broadband channel.
Owner:HUAWEI TECH CO LTD
Network platform system and management method
InactiveCN101872447AGuaranteed uniquenessEnsure consistencyMultimedia data retrievalBuying/selling/leasing transactionsData synchronizationLibrary science
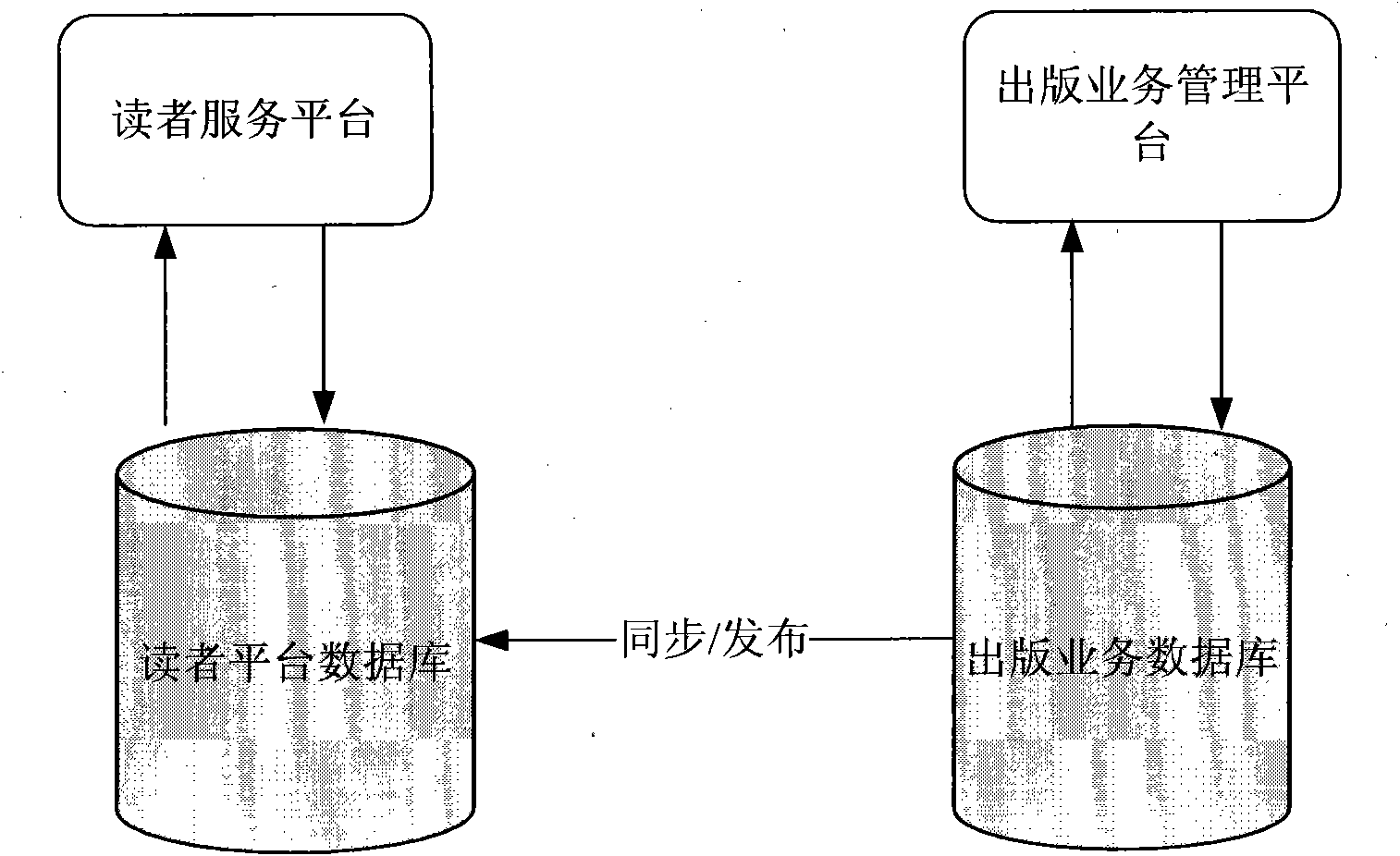
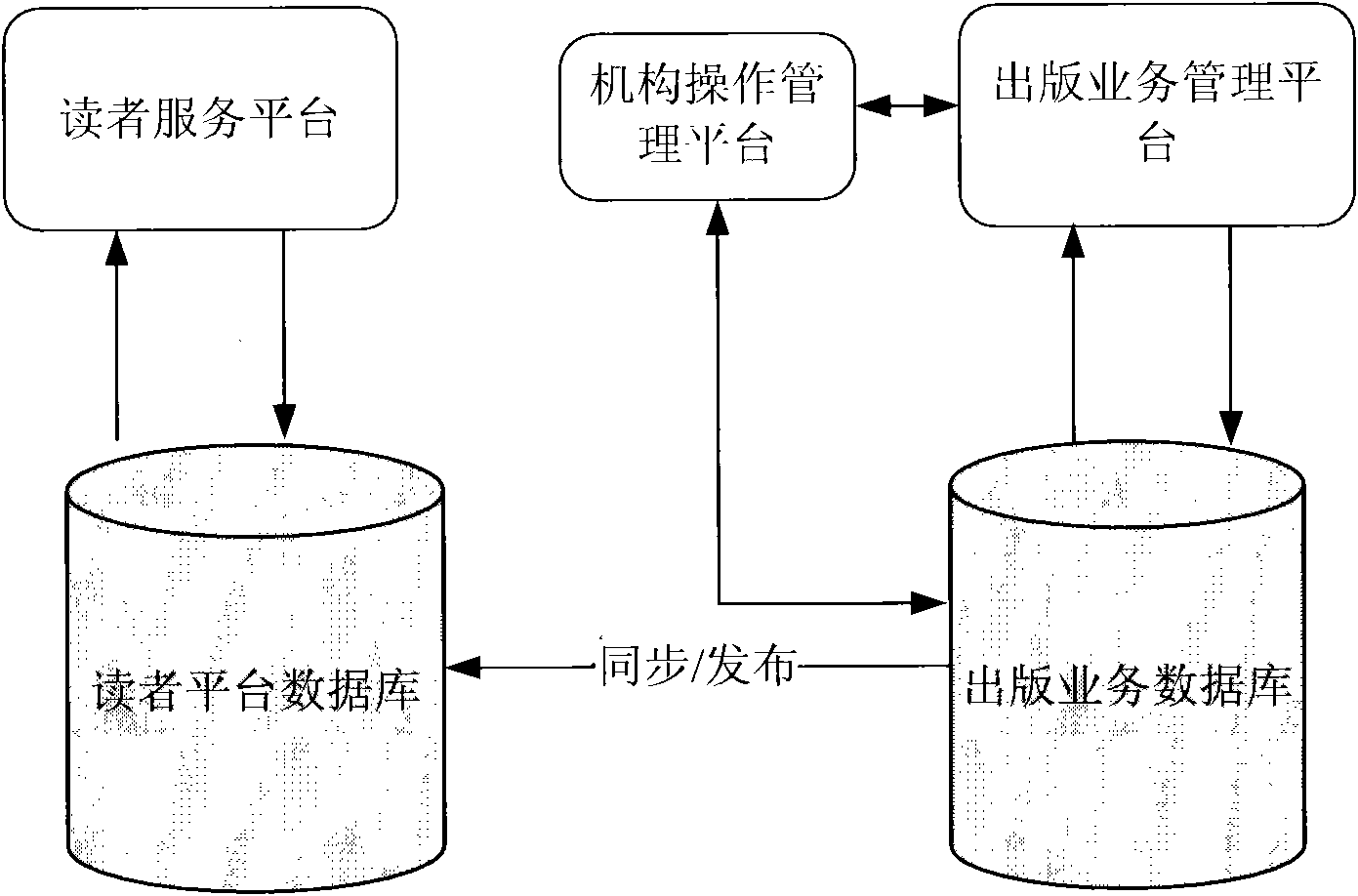
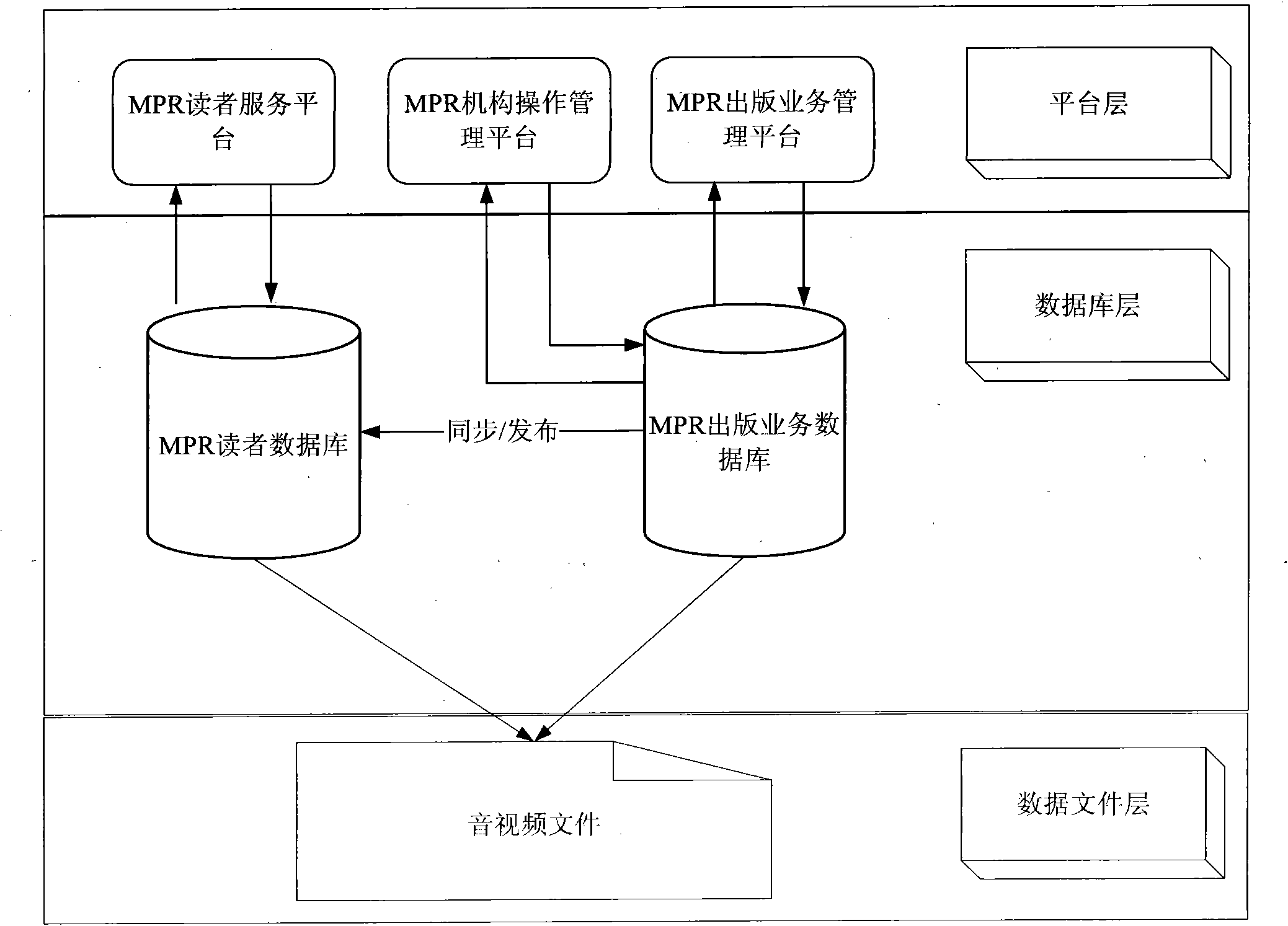
The embodiment of the invention provides a network platform system and a network platform management method. The network platform system performs unique coding management on a cross-media association of multimedia print reader to realize services aiming at publication and use of the multimedia print reader, and comprises a publication service management platform, a reader service platform, a publication service database and a reader platform database, wherein the publication service management platform is used for publishing a unique code of the cross-media association of the multimedia print reader to publishers, and is also used for synchronizing / publishing data in the publication service database to the reader platform database; and the reader platform is connected with the reader platform database, and is used for acquiring multimedia information from the reader platform database according to requests submitted by readers and providing the multimedia information for the readers. Through the network platform system and the network platform management method, the automation and unification of the services for the publication and use of the multimedia print reader can be realized, and the publishers are provided with a copyright protected digital publication service platform.
Owner:SHENZHEN MPR TECH CO LTD
Tracing copies of an implementation
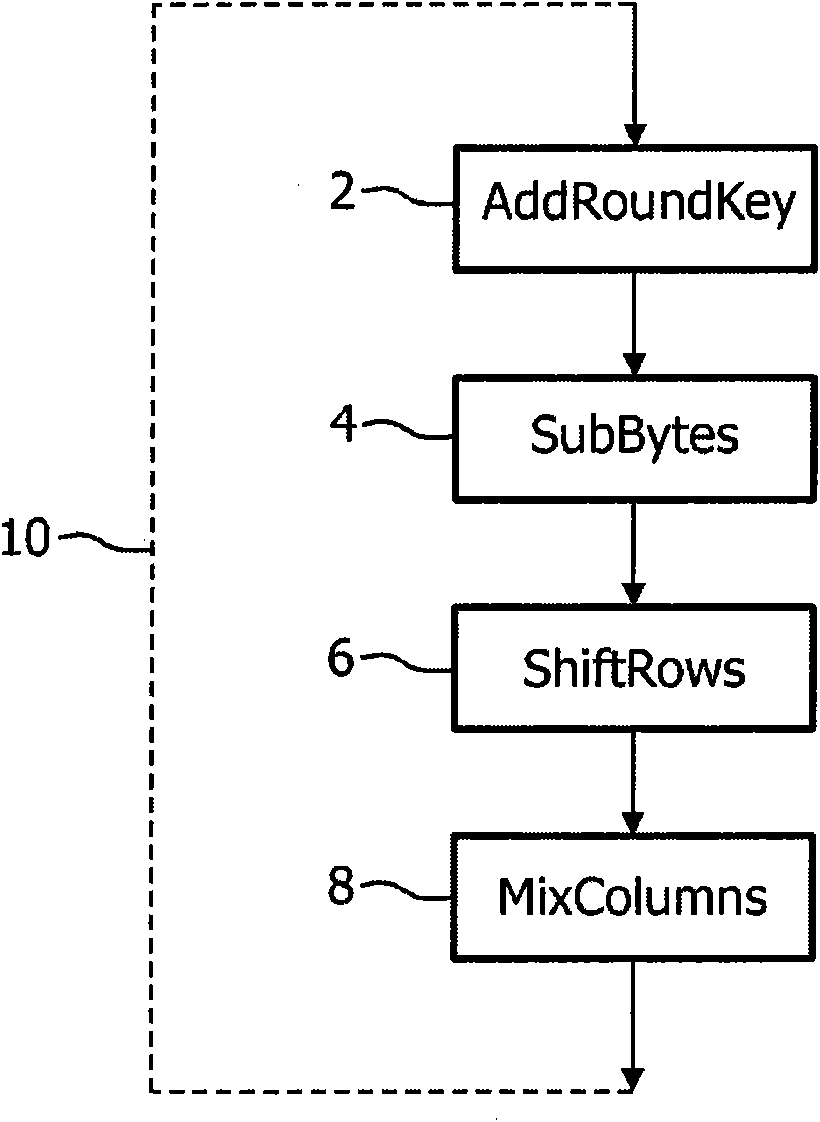
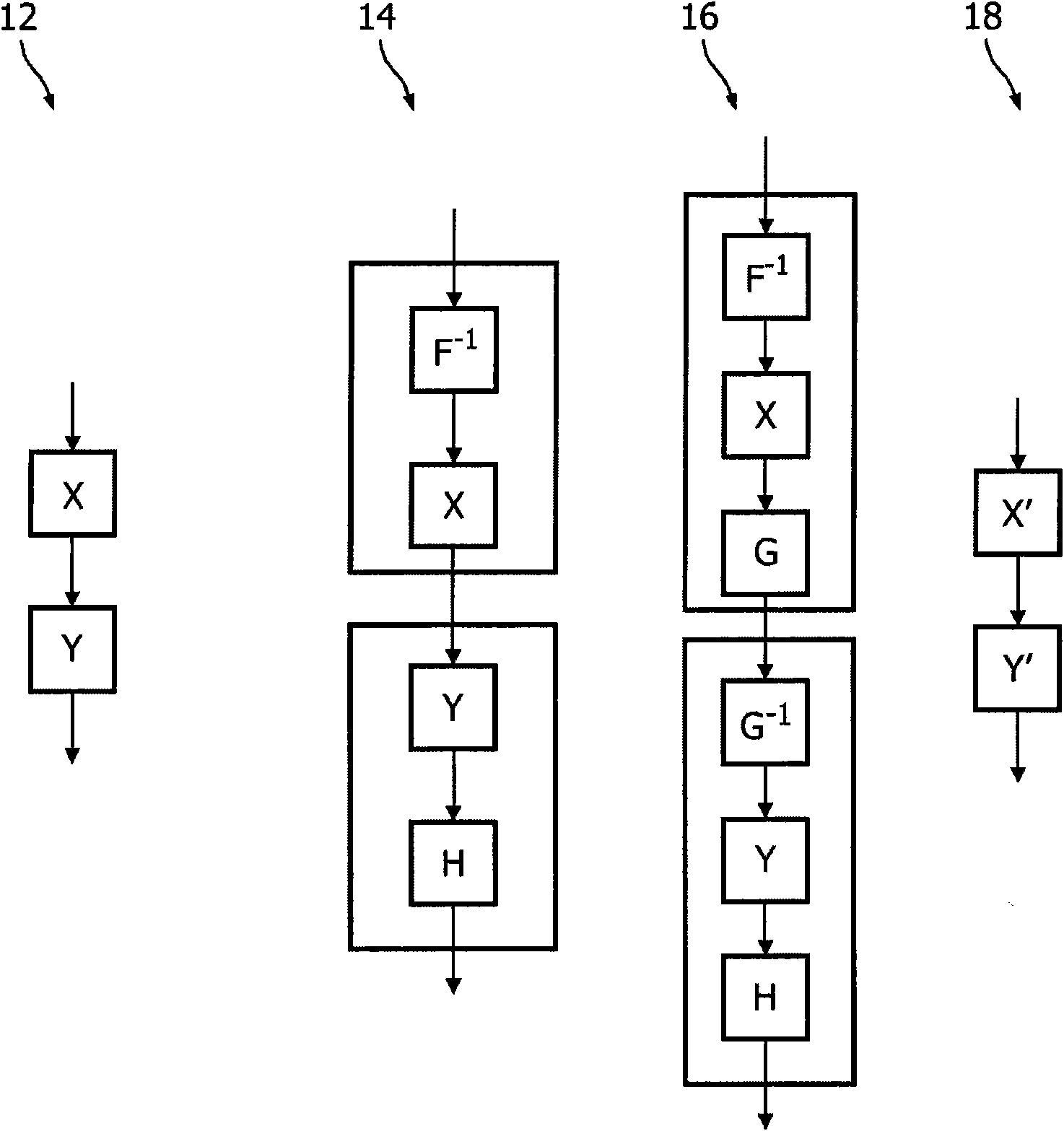
InactiveCN101578813AAvoid sharingEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresNetwork generationComputer science
A system (600) for facilitating tracing copies (634) of an implementation of a computational method (602). A network generator (604) for generating a network of look-up tables representing steps of the computational method (602), the network being formed by using an output value of a first look-up table as an input value of a different second look-up 5 table. A personalizer (606) for generating a plurality of different versions of the network of look-up tables by changing at least one value in the network of look-up tables, end results of the version corresponding to a relevant domain of input values being substantially the same for each version. An associator (608) for associating individual versions with individual stations (610) or users (632) of stations (610). The computational method (602) includes a 10 cryptographic scheme and a cryptographic key.
Owner:IRDETO BV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com