Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
66results about How to "Storage requirements is greatly reduced" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
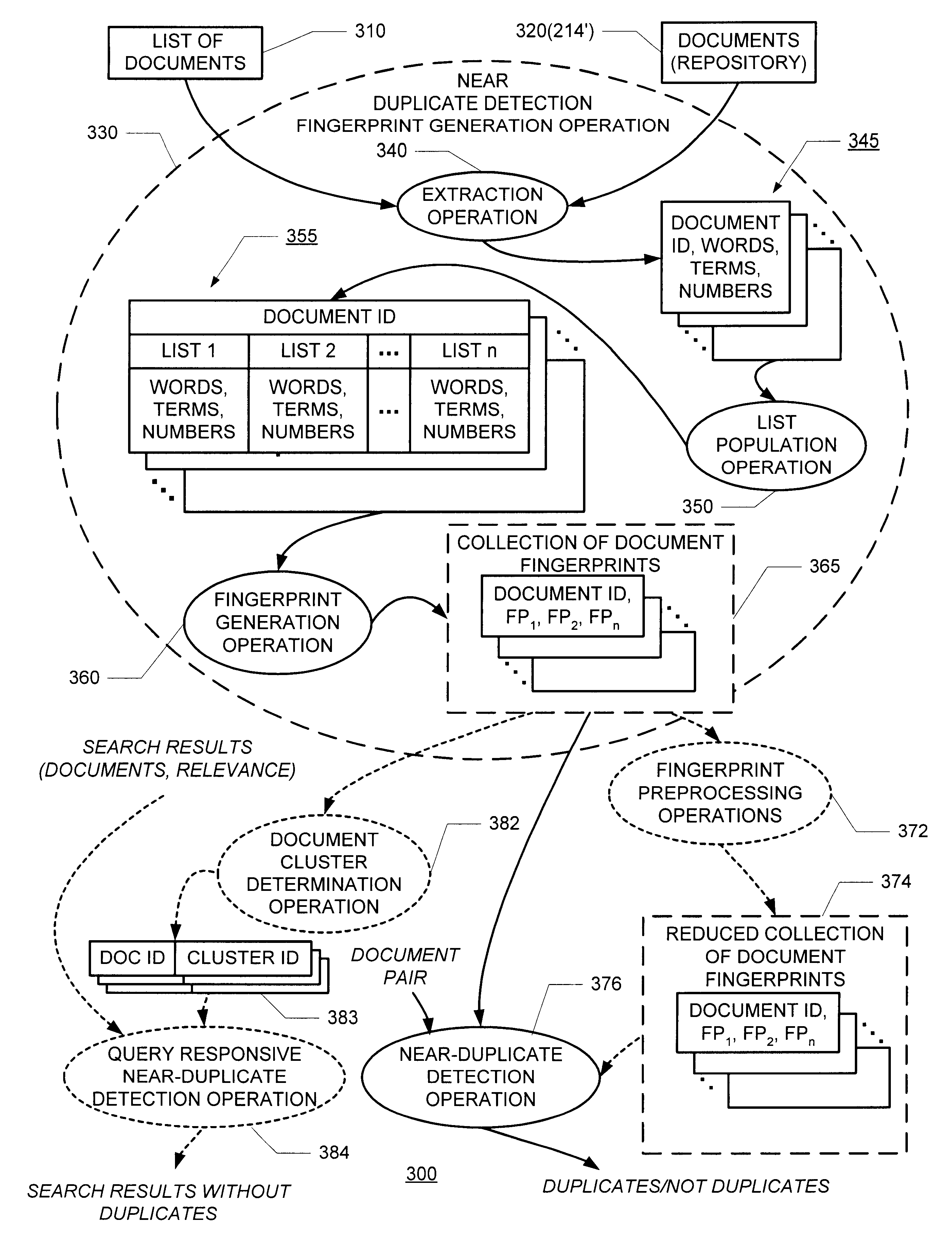
Detecting duplicate and near-duplicate files
InactiveUS6658423B1Save bandwidthStorage requirement be greatly reduceData processing applicationsWeb data indexingDocument preparationFingerprint
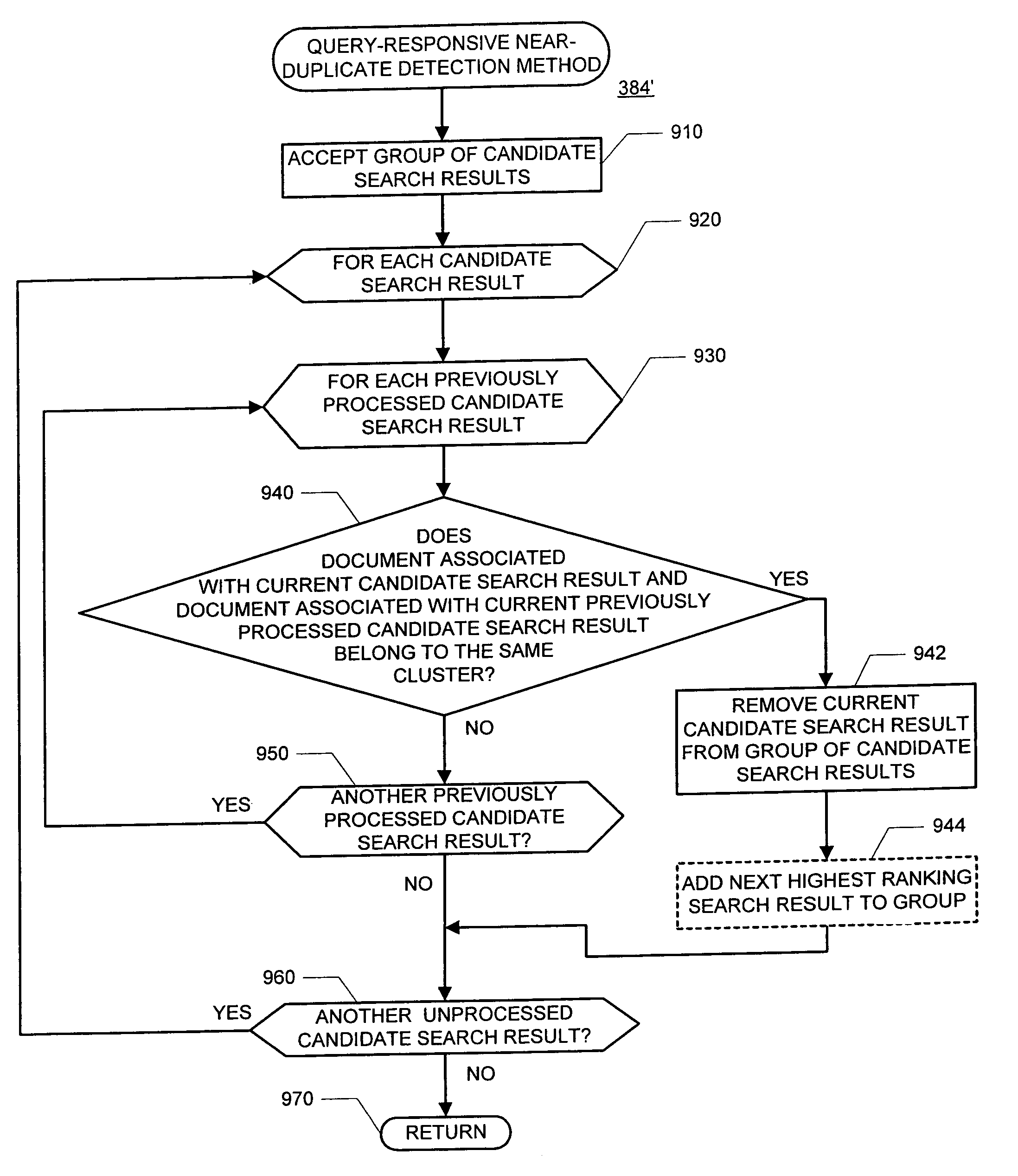
Improved duplicate and near-duplicate detection techniques may assign a number of fingerprints to a given document by (i) extracting parts from the document, (ii) assigning the extracted parts to one or more of a predetermined number of lists, and (iii) generating a fingerprint from each of the populated lists. Two documents may be considered to be near-duplicates if any one of their fingerprints match.
Owner:GOOGLE LLC
Monitoring fitness using a mobile device
ActiveUS20120116550A1Reduce storage requirementsStorage requirements is greatly reducedPhysical therapies and activitiesDigital data processing detailsTerrainExercise performance
Athletic performance monitoring and tracking may provide multiple ways in which to track athletic movement and activity. In one example, an athletic monitoring device may include or be associated with multiple types of movement sensors and switch between the sensors or use both depending on various factors including type of workout. Workouts may also be tagged with various parameters including mood, weather, terrain, athletic equipment used and the like. In one or more examples, the parameters may be automatically determined based on location. User workouts and accomplishments may also be celebrated through messages from celebrities, family, friends and other users. In some cases, the messages may be triggered by various conditions. Coaching may also be provided to the user to help improve workouts and overall athletic performance. Running routes may also be automatically tracked, stored and shared.
Owner:NIKE INC
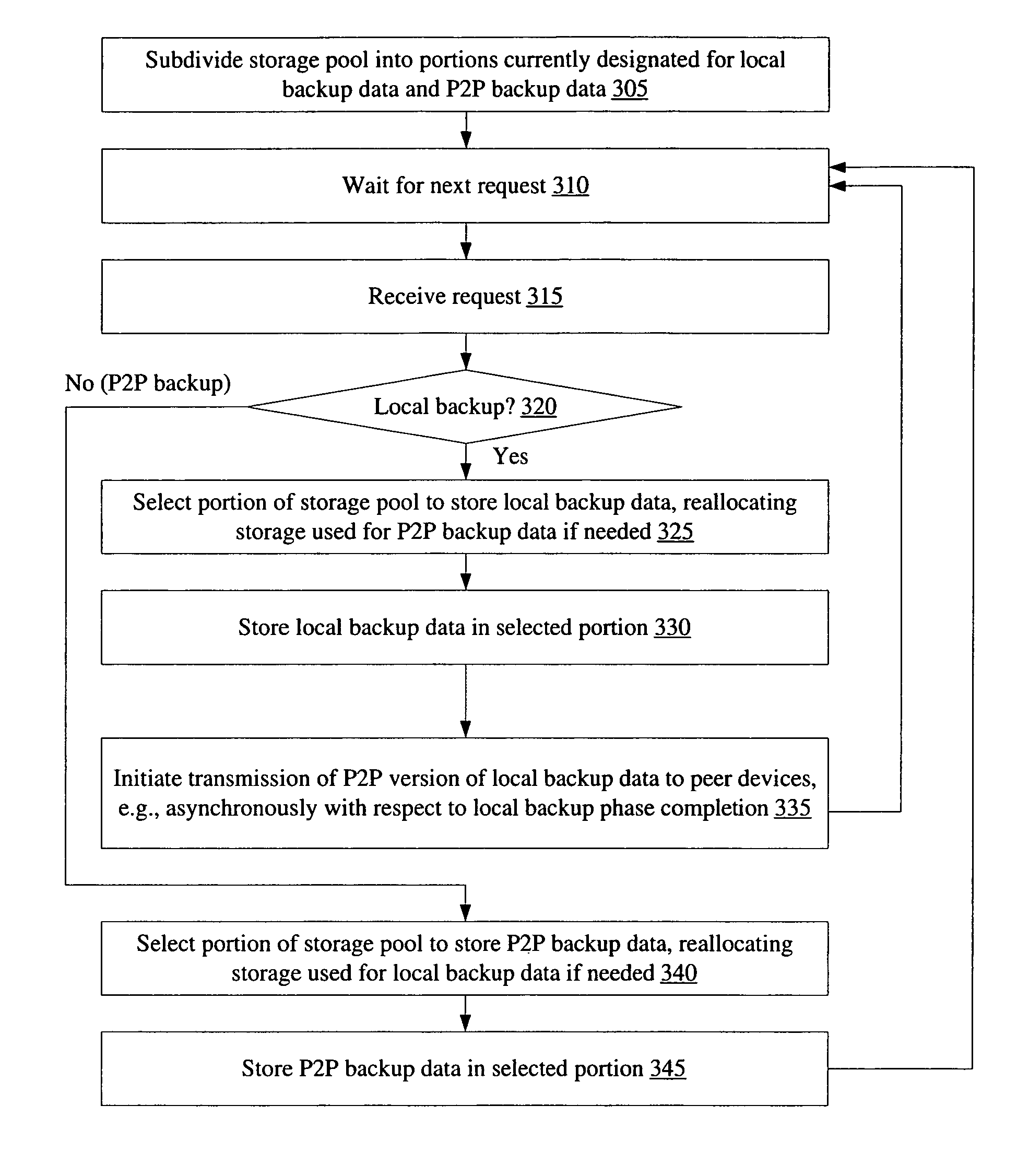
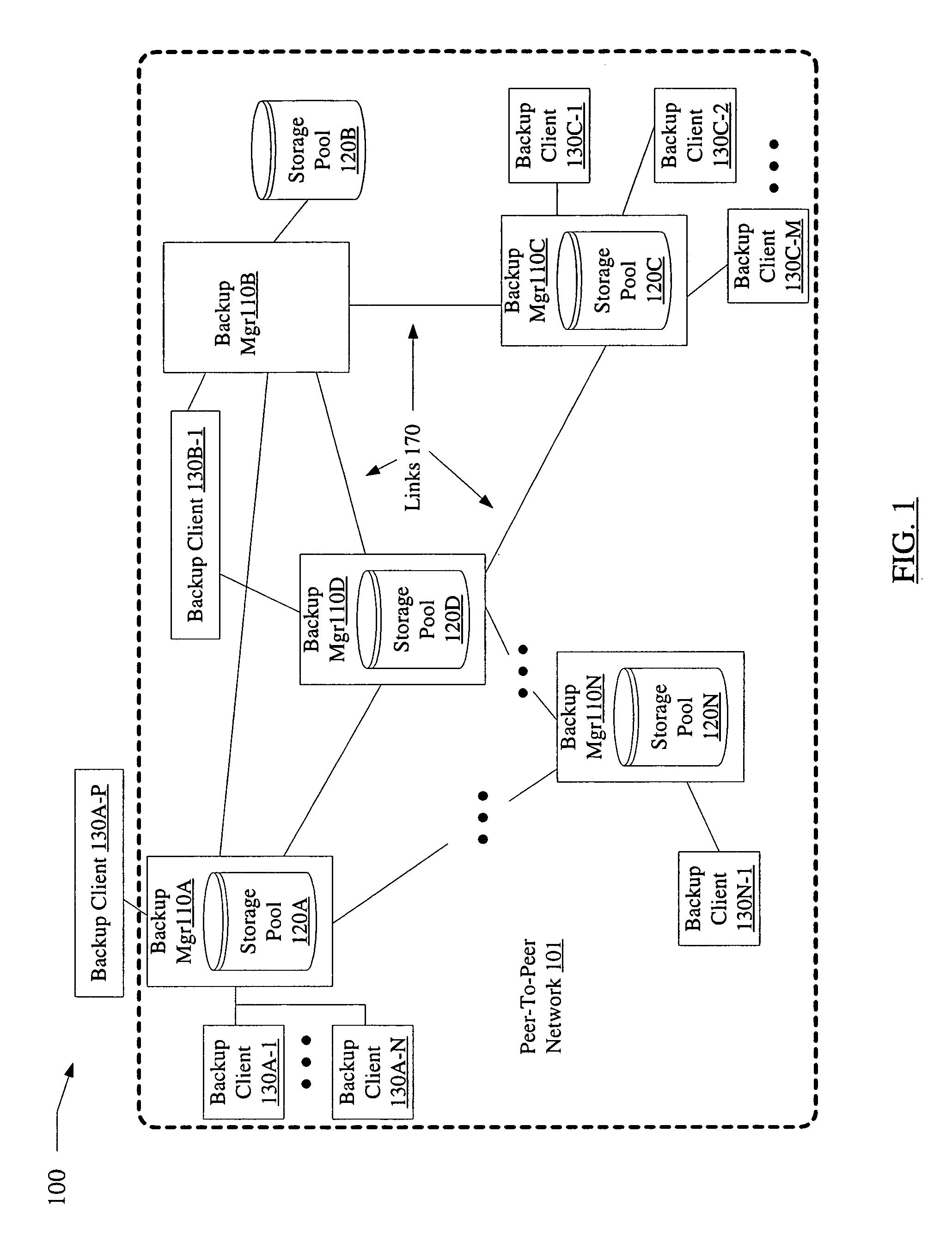
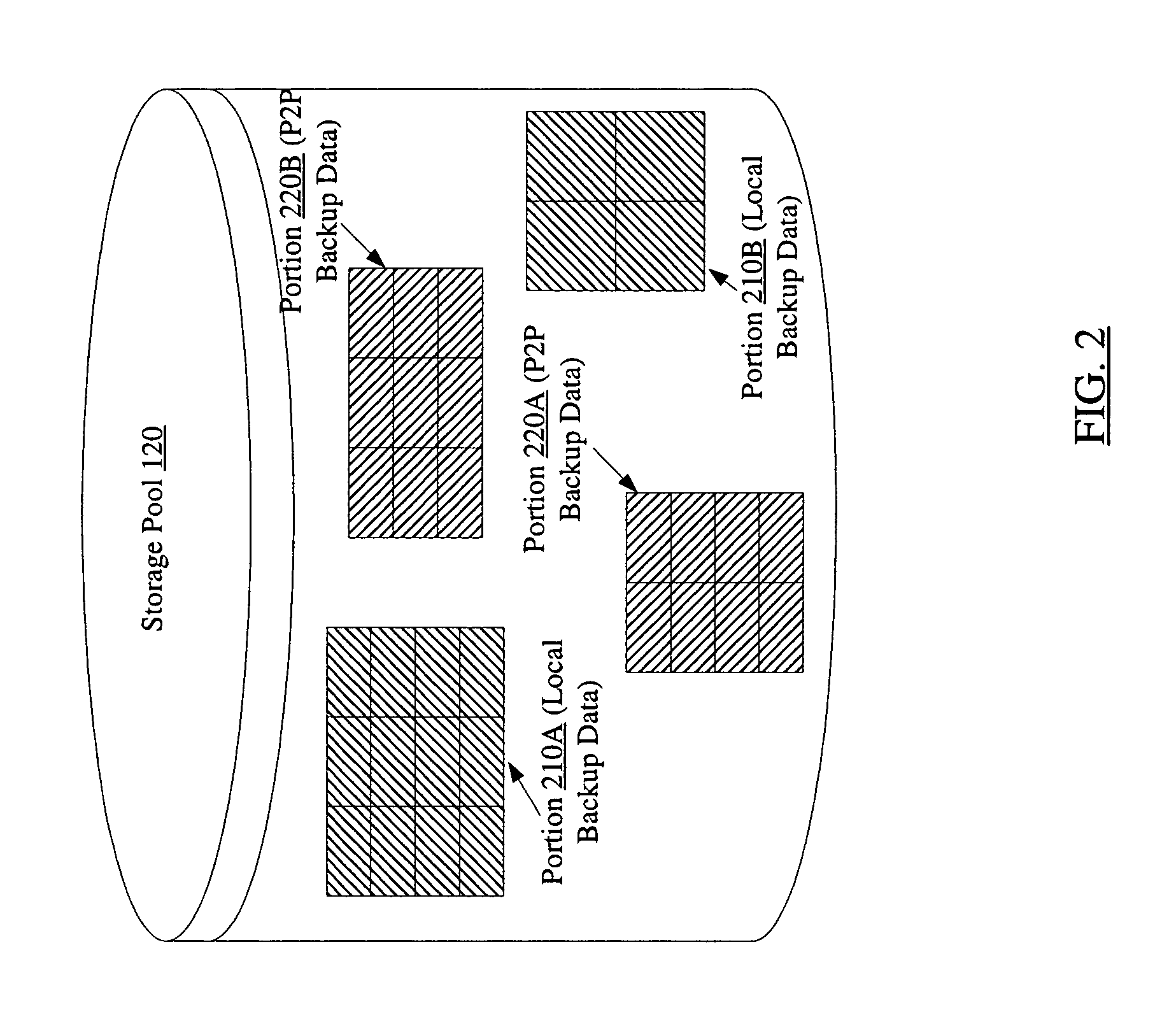
Efficient backups using dynamically shared storage pools in peer-to-peer networks
InactiveUS7529785B1Reduce storage requirementsEfficient backupError detection/correctionSpecial data processing applicationsClient-sideData store
A system for efficient backups using dynamically shared storage pools in peer-to-peer networks comprises one or more processors and memory coupled to the processors. The memory stores instructions executable by the processors to implement a backup manager configured to dynamically subdivide a storage pool into one or more portions of storage currently designated for local backup data and one or more portions of storage currently designated for peer-to-peer (P2P) backup data. In response to local backup data received from a backup client, the backup manager may store the local backup data in a portion of the storage pool that is currently designated for local backup data. The backup manager may then generate a P2P version of the local backup data, e.g., by encrypting and / or redundancy encoding the local backup data, and transmit parts of the P2P version to each of one or more peer devices in the P2P network.
Owner:SYMANTEC OPERATING CORP
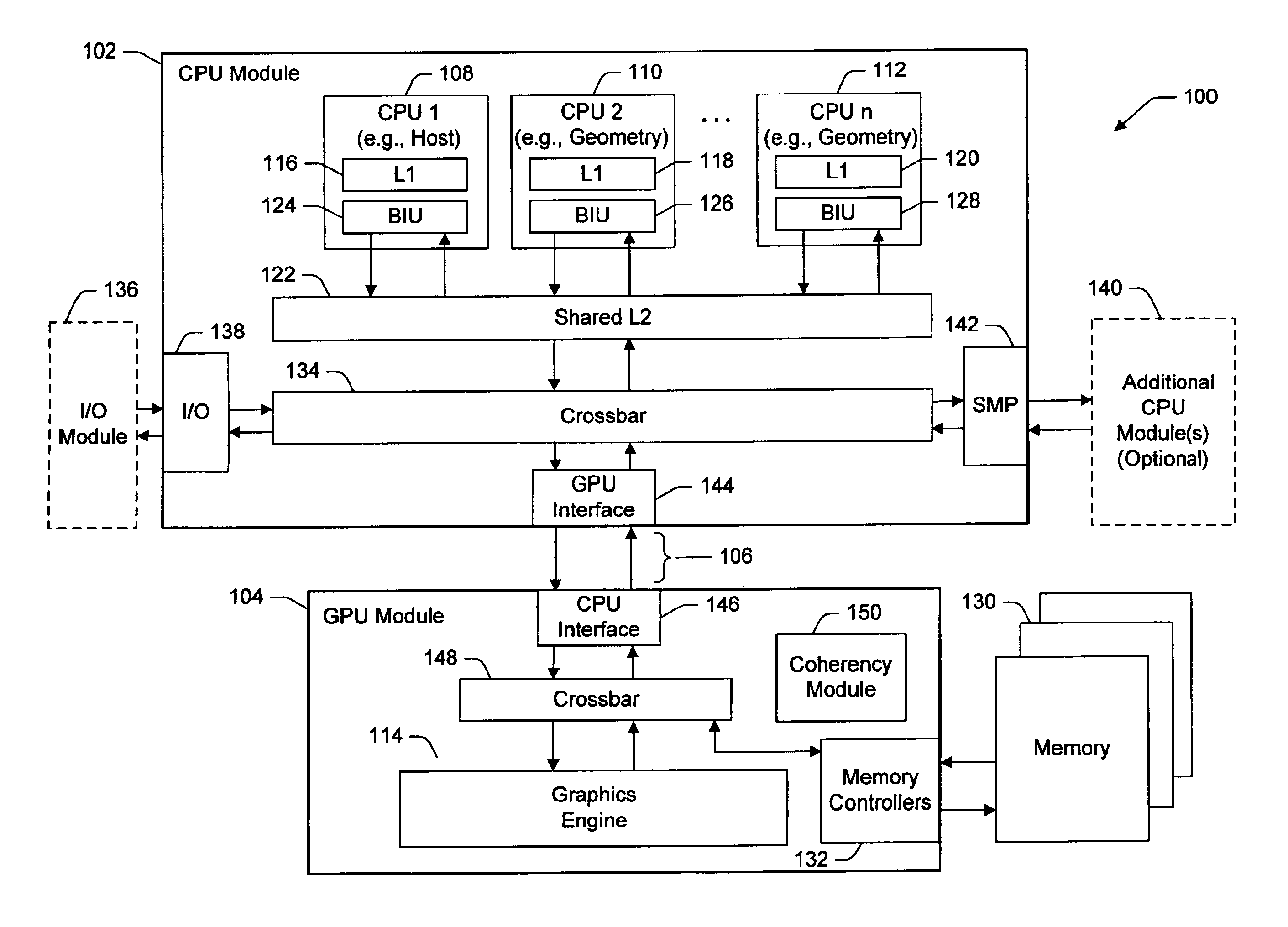
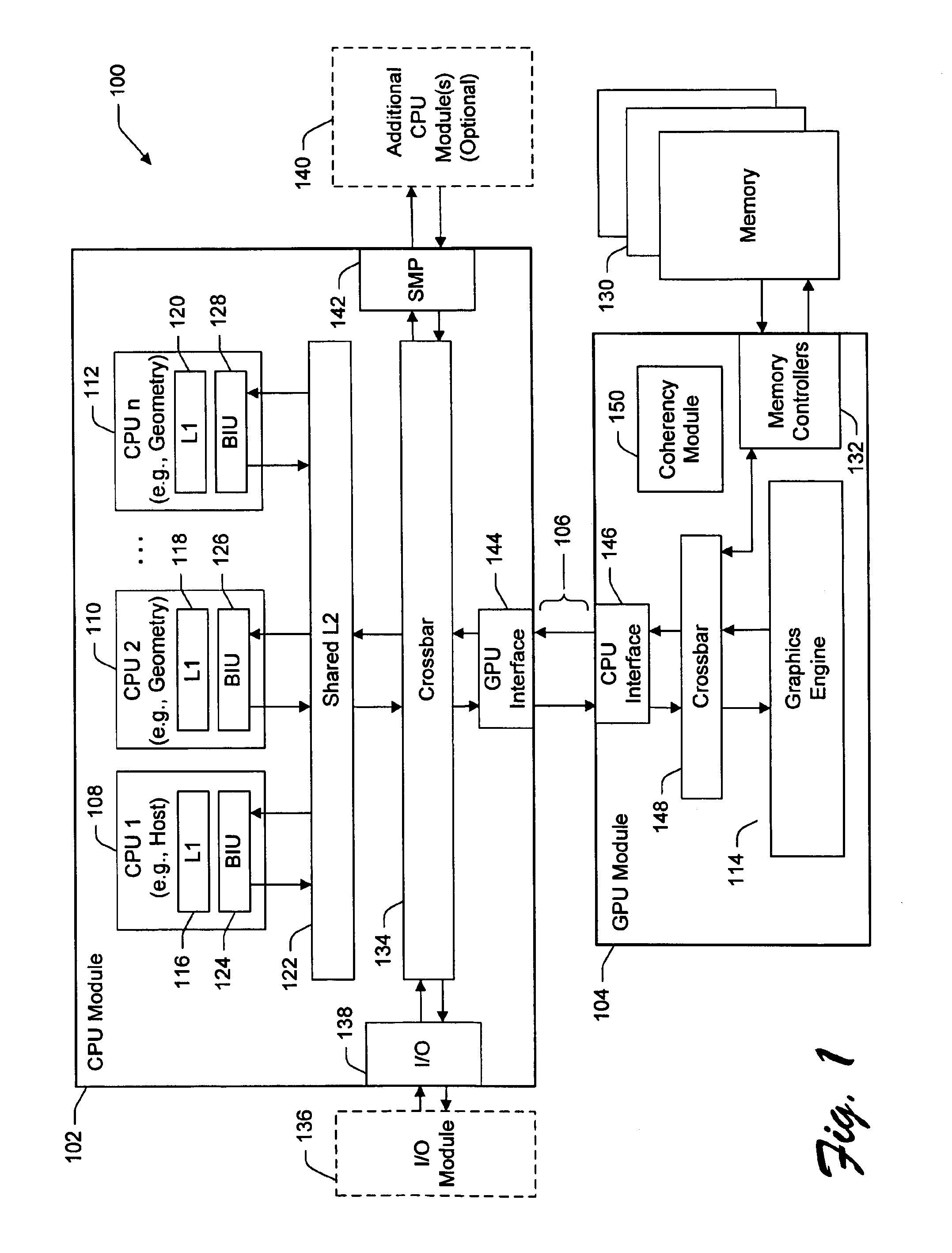
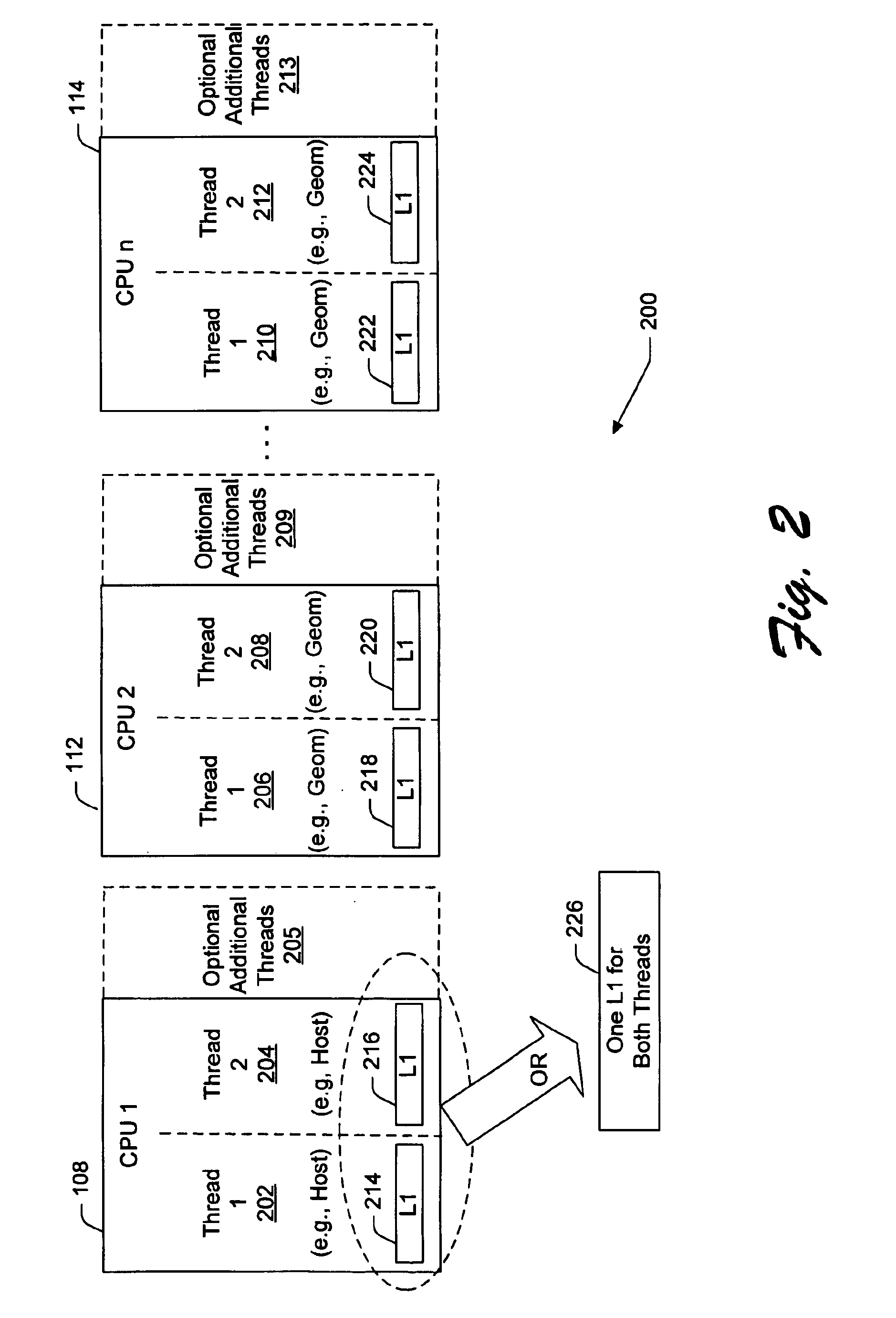
System and method for parallel execution of data generation tasks
InactiveUS6862027B2Reduce storage requirementsReduces deleterious bandwidth restrictionResource allocationMemory adressing/allocation/relocationGraphicsParallel computing
A CPU module includes a host element configured to perform a high-level host-related task, and one or more data-generating processing elements configured to perform a data-generating task associated with the high-level host-related task. Each data-generating processing element includes logic configured to receive input data, and logic configured to process the input data to produce output data. The amount of output data is greater than an amount of input data, and the ratio of the amount of input data to the amount of output data defines a decompression ratio. In one implementation, the high-level host-related task performed by the host element pertains to a high-level graphics processing task, and the data-generating task pertains to the generation of geometry data (such as triangle vertices) for use within the high-level graphics processing task. The CPU module can transfer the output data to a GPU module via at least one locked set of a cache memory. The GPU retrieves the output data from the locked set, and periodically forwards a tail pointer to a cacheable location within the data-generating elements that informs the data-generating elements of its progress in retrieving the output data.
Owner:MICROSOFT TECH LICENSING LLC
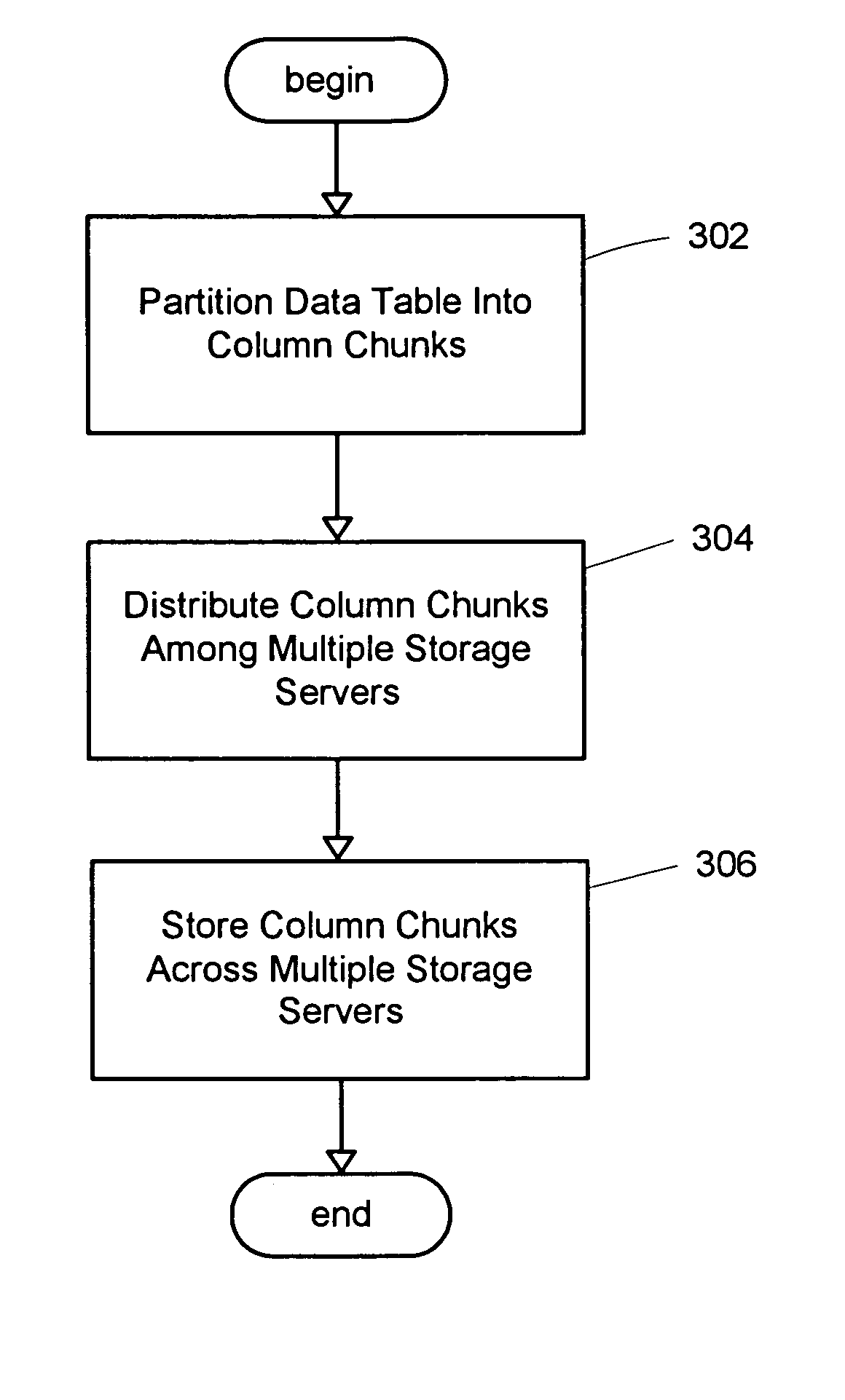
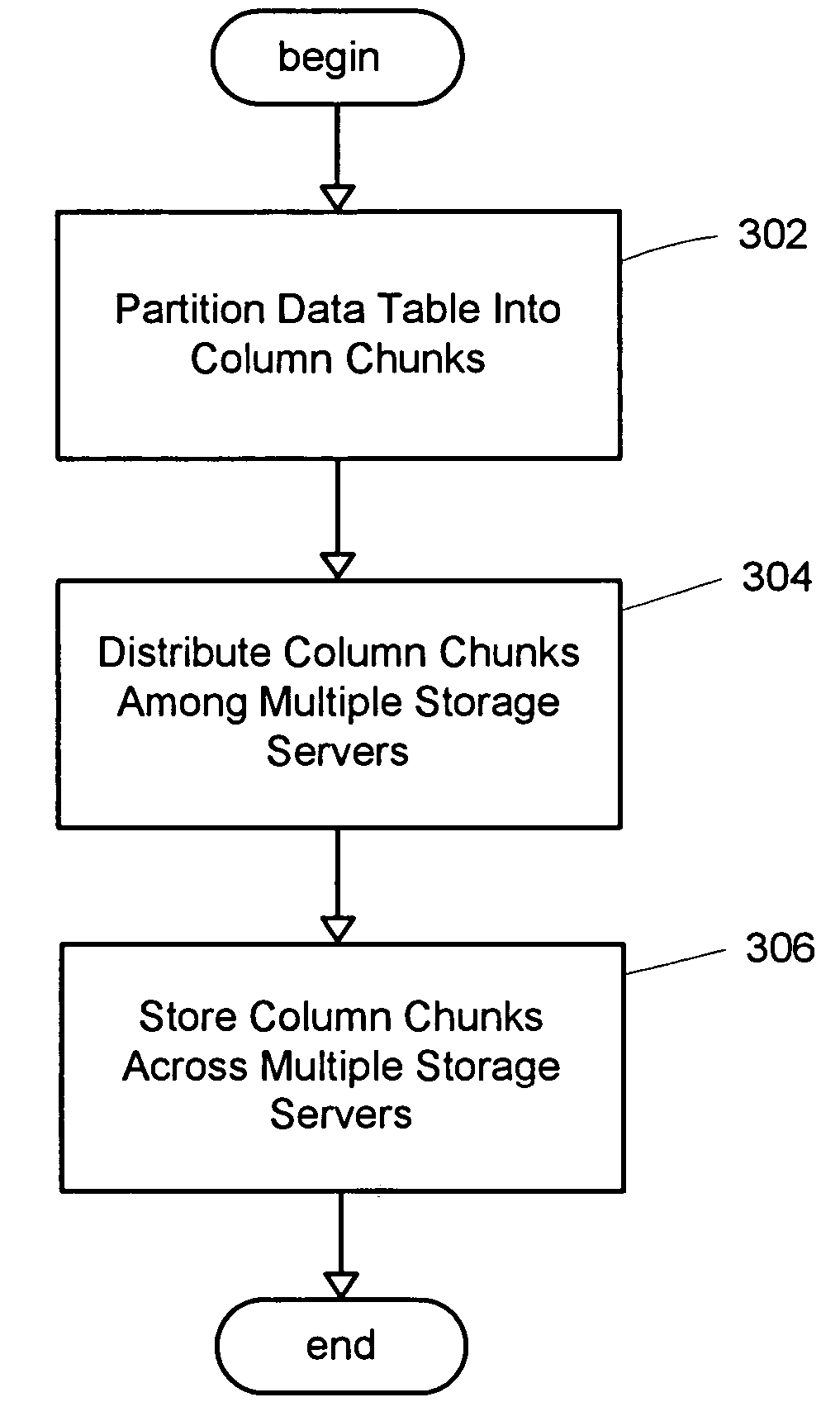
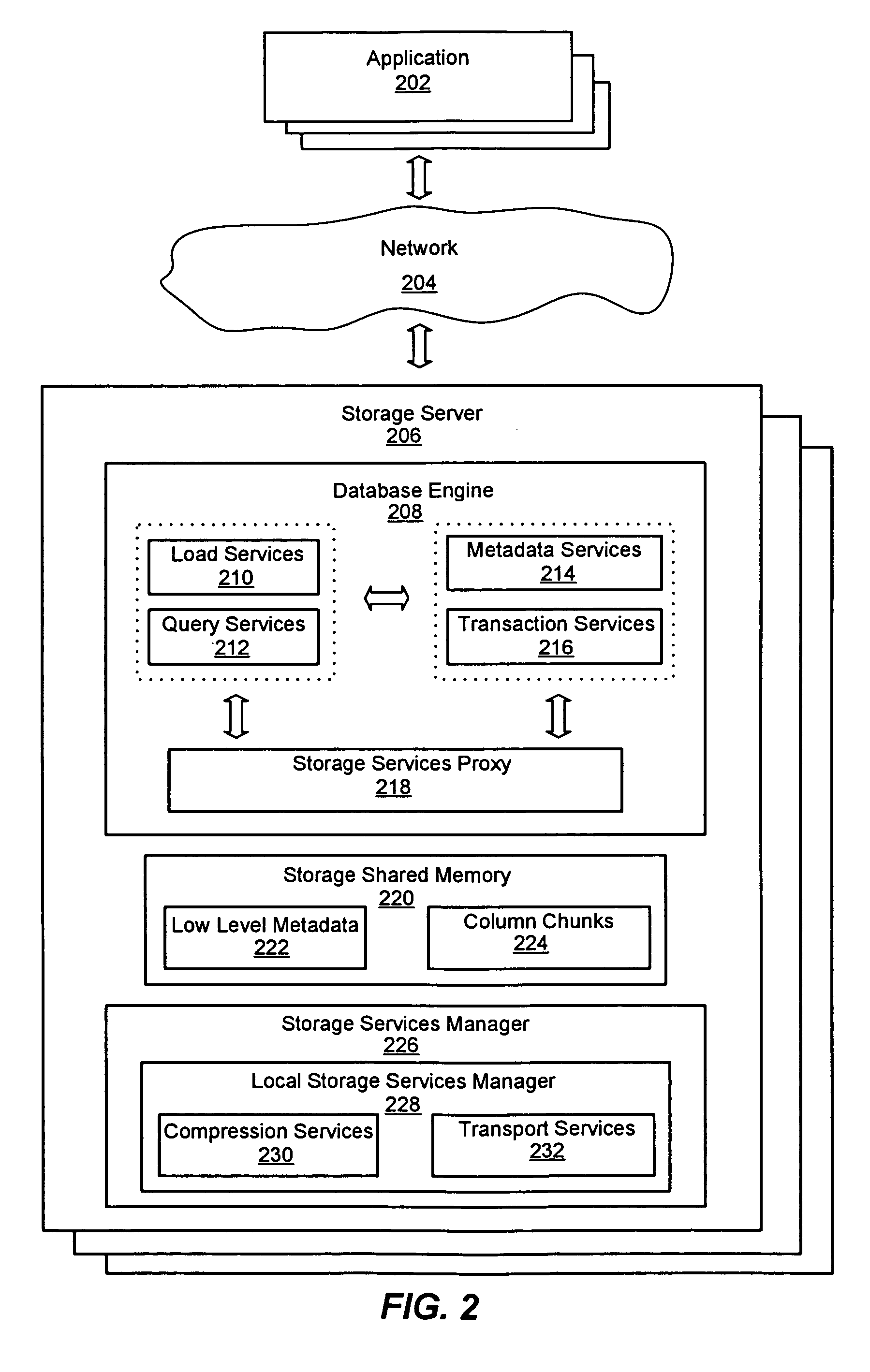
System for a distributed column chunk data store
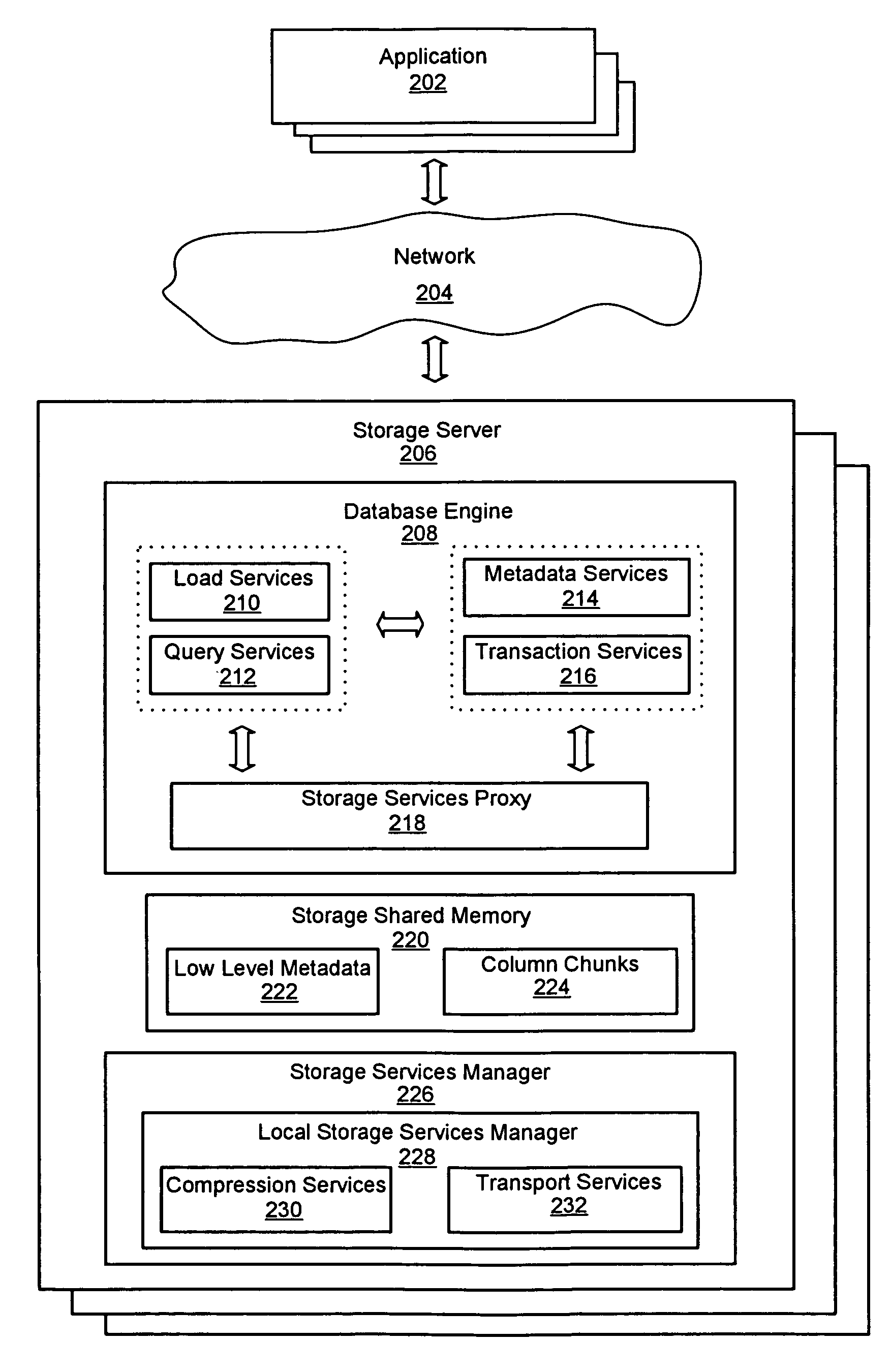
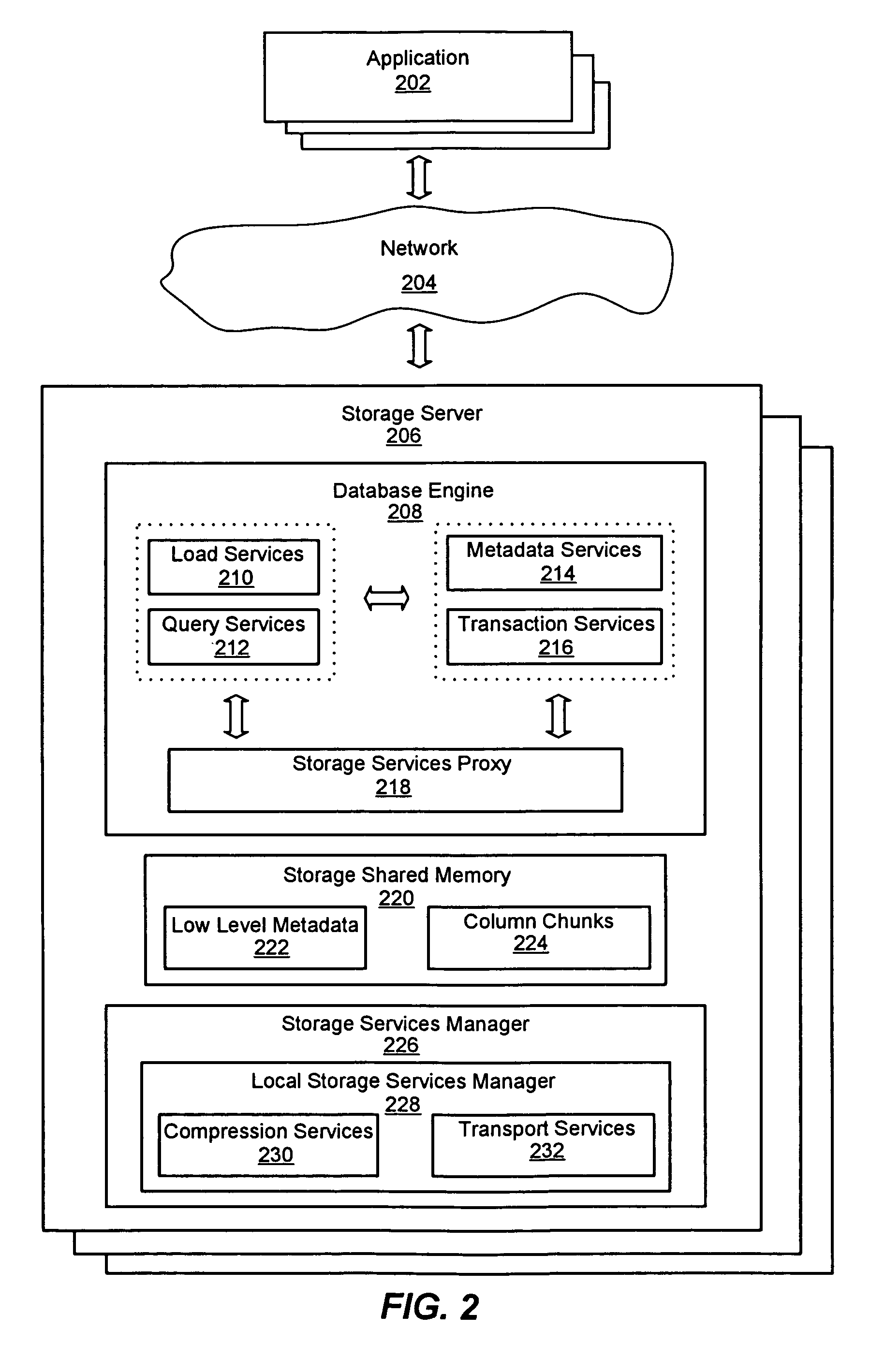
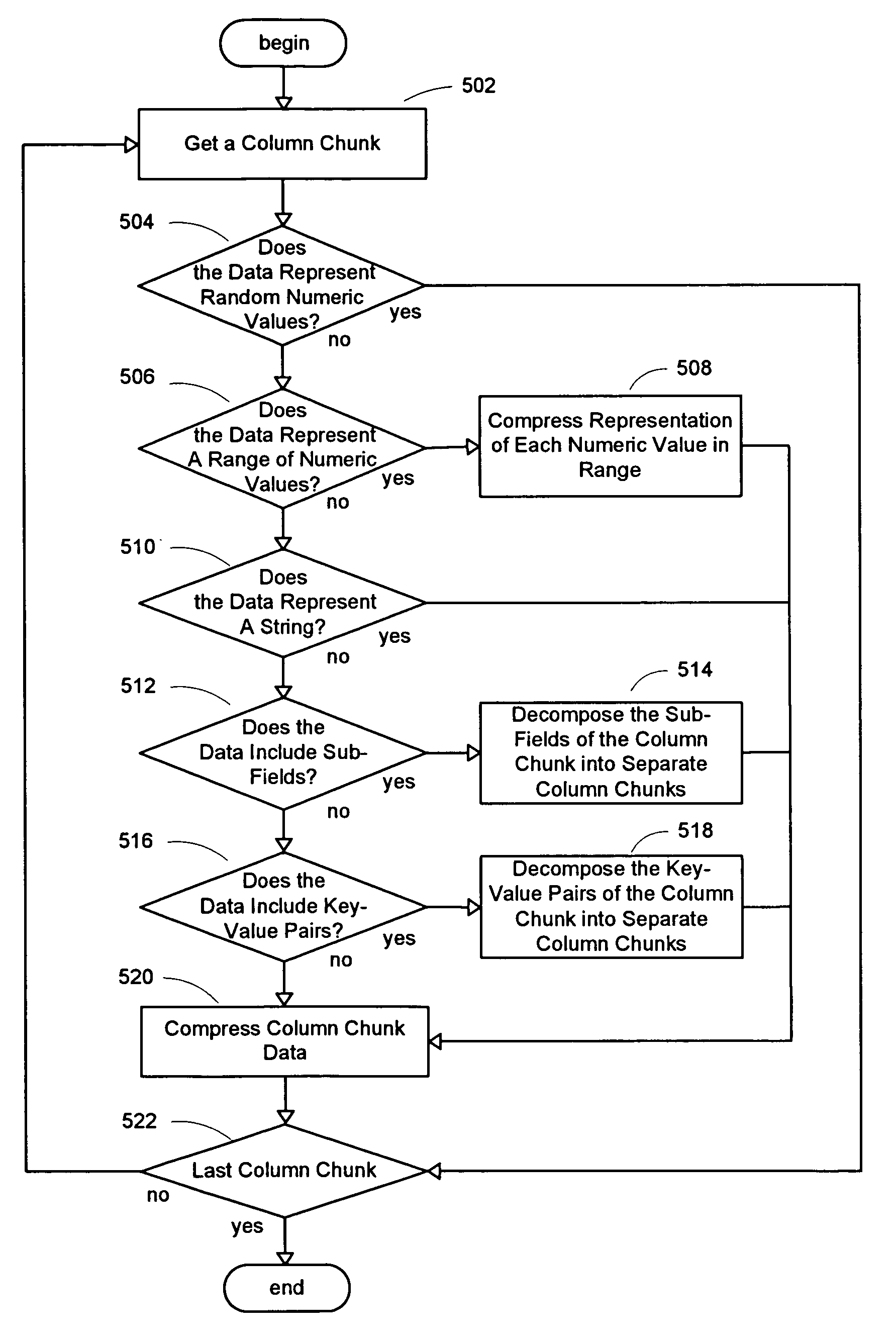
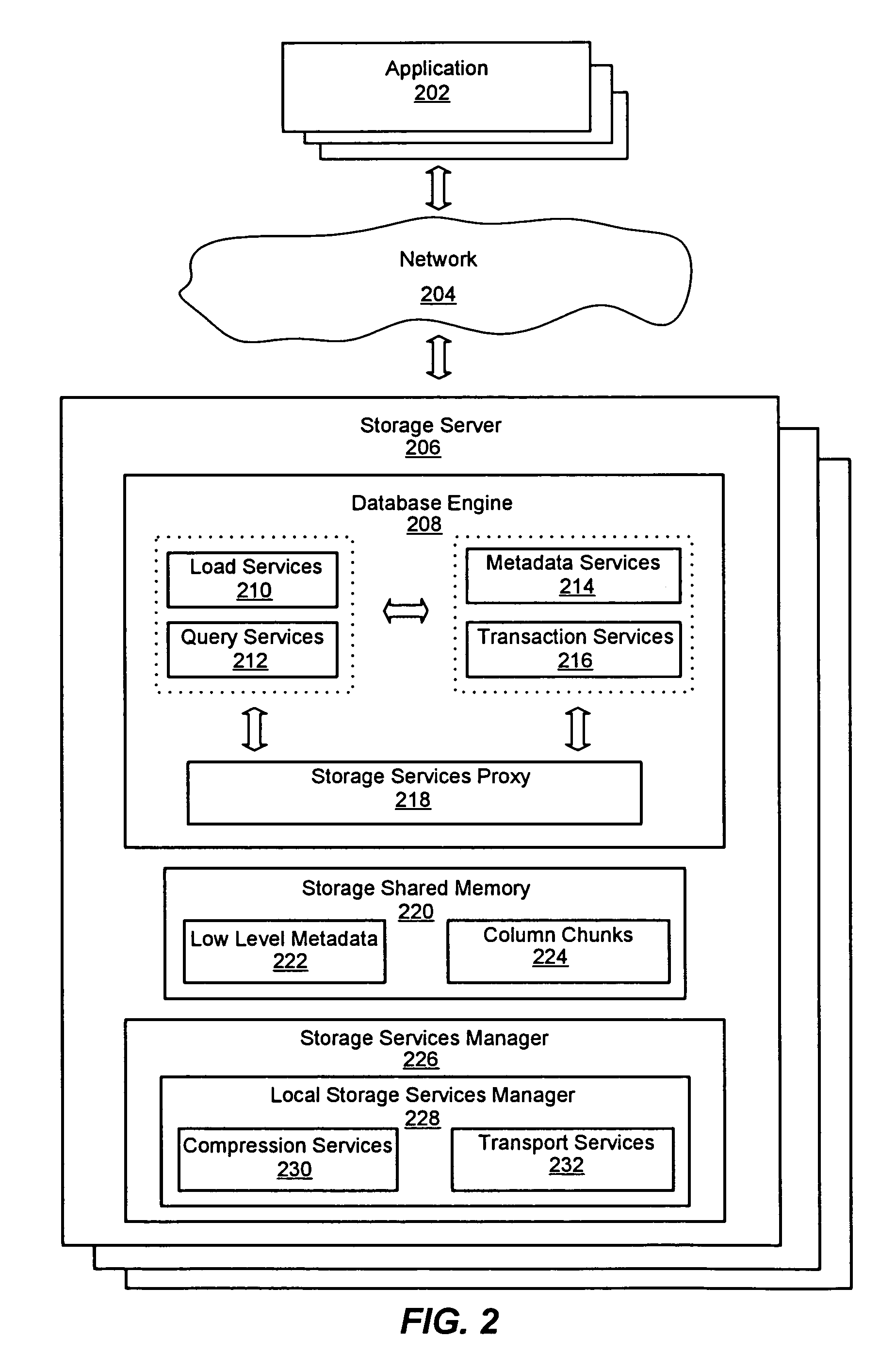
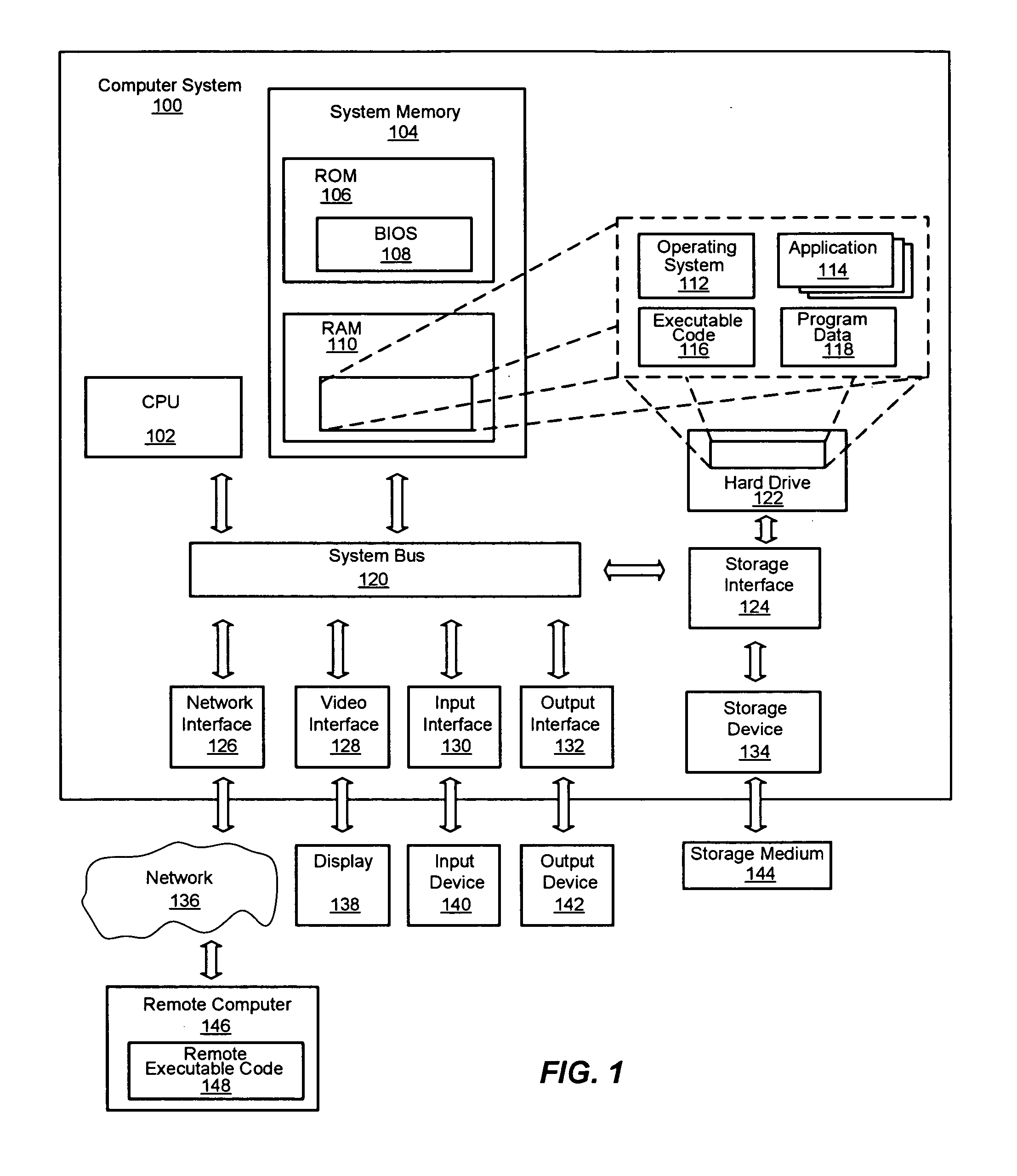
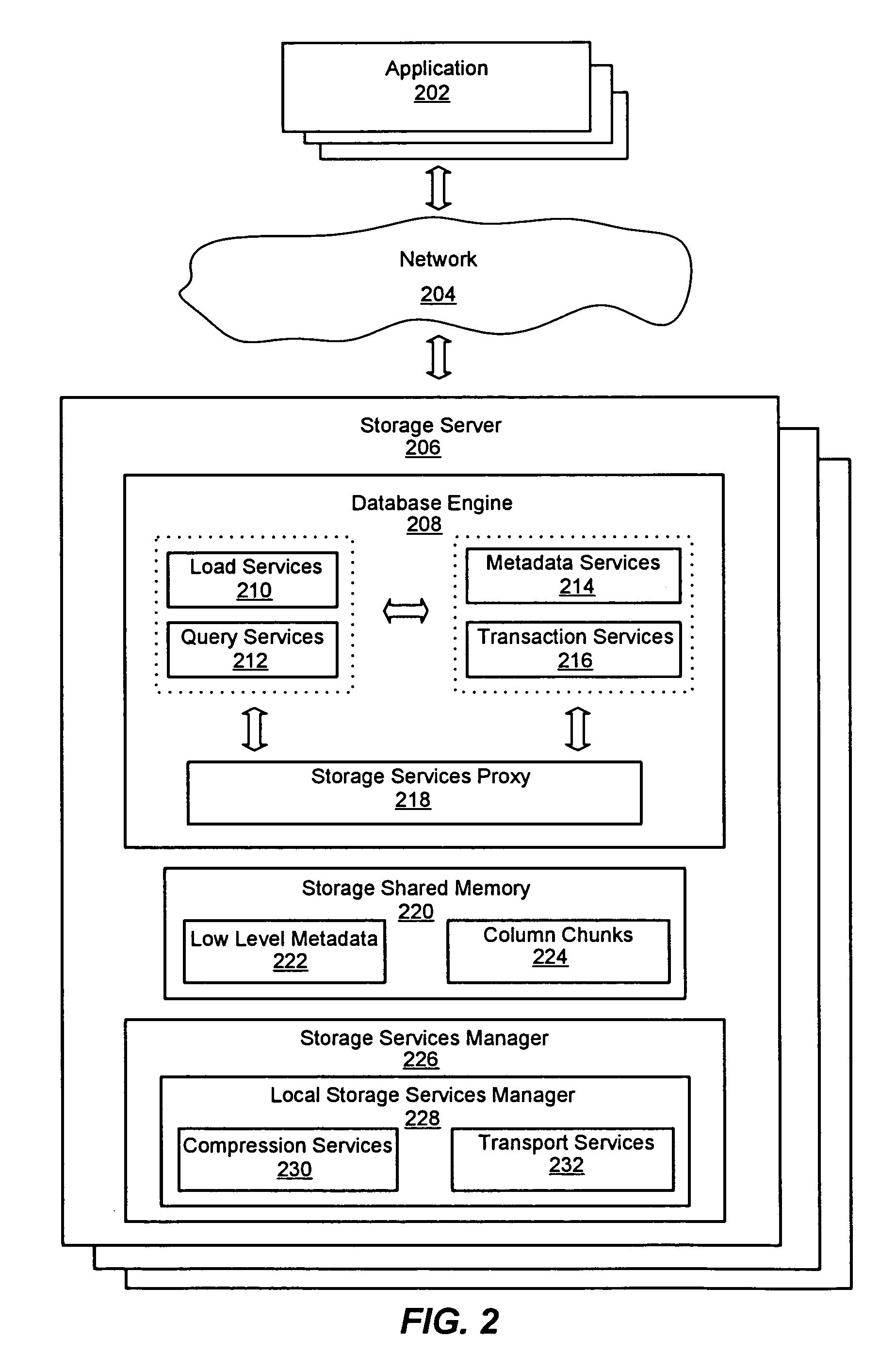
ActiveUS7447839B2Storage requirements is greatly reducedReduce transfer timeError detection/correctionMemory adressing/allocation/relocationServer allocationDatabase engine
An improved system and method for a distributed column chunk data store is provided. A distributed column chunk data store may be provided by multiple storage servers operably coupled to a network. A storage server may include a database engine for partitioning a data table into the column chunks for distributing across multiple storage servers, a storage shared memory for storing the column chunks during processing of semantic operations performed on the column chunks, and a storage services manager for striping column chunks of a partitioned data table across multiple storage servers. Any data table may be flexibly partitioned into column chunks using one or more columns as a key with various partitioning methods. There may also be a storage policy for specifying how to partition a data table for distributing column chunks across multiple servers and for specifying a level of redundancy for recovery from failure of storage servers.
Owner:GOOGLE LLC
Method and system for multimedia tags
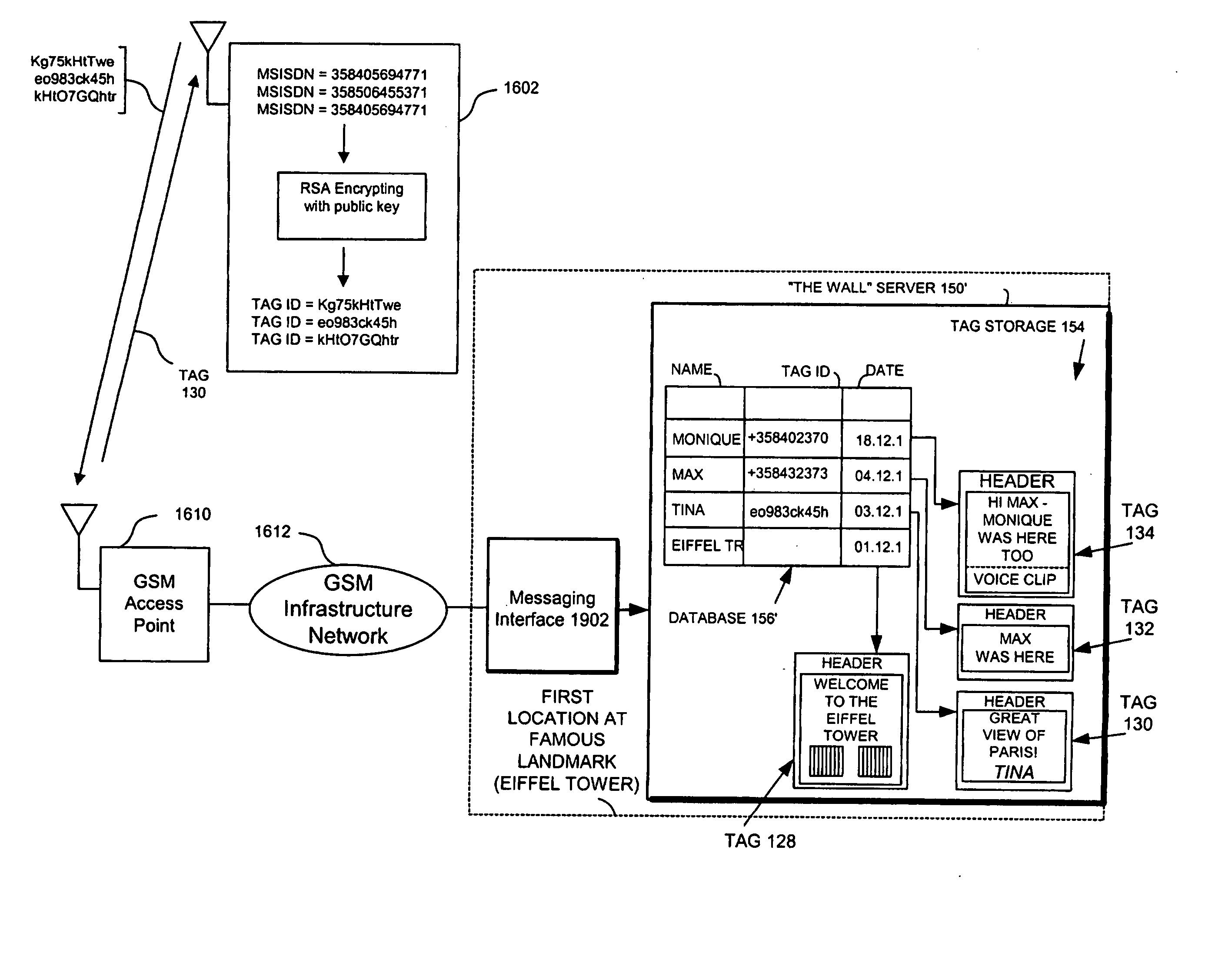
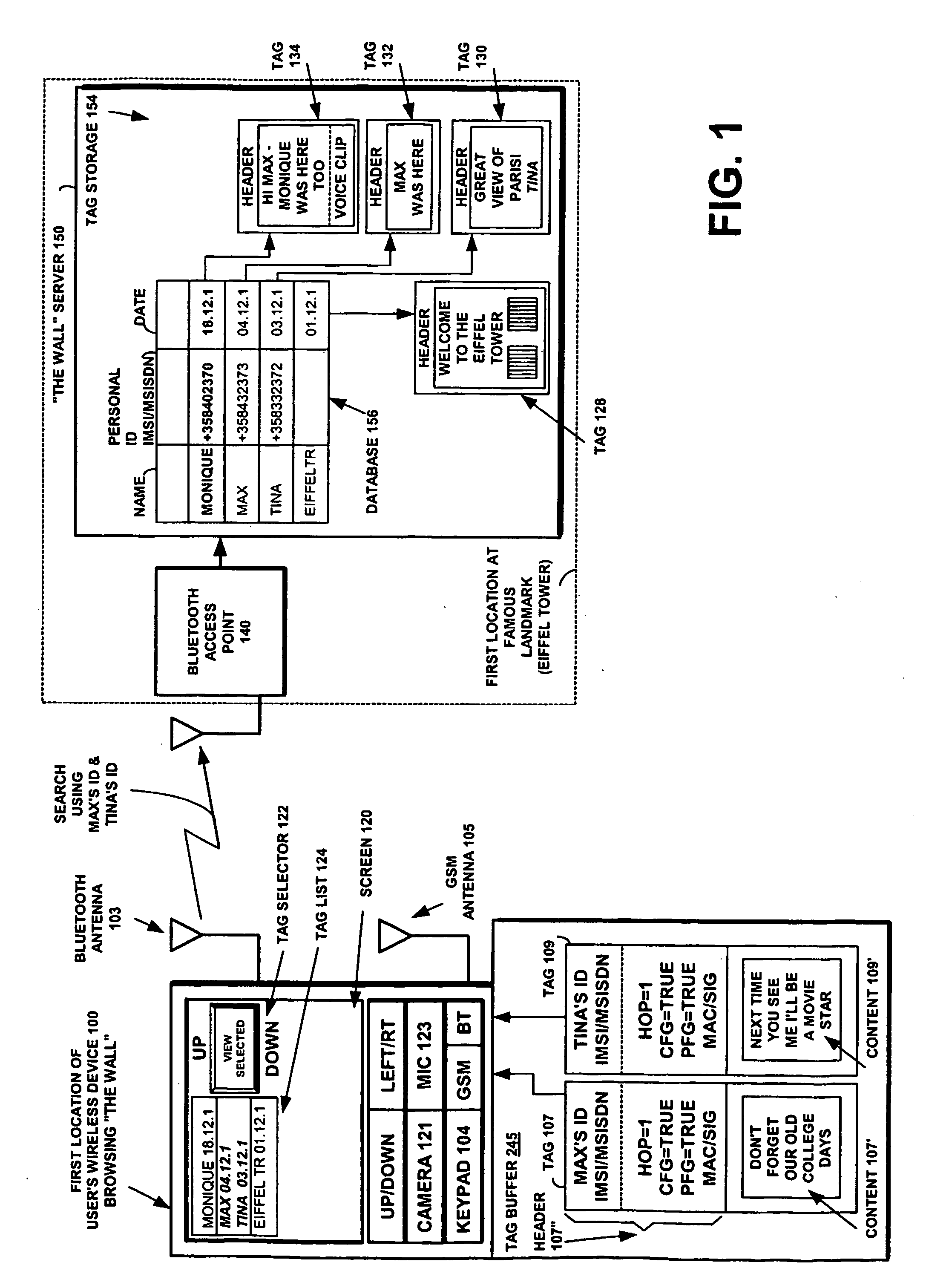
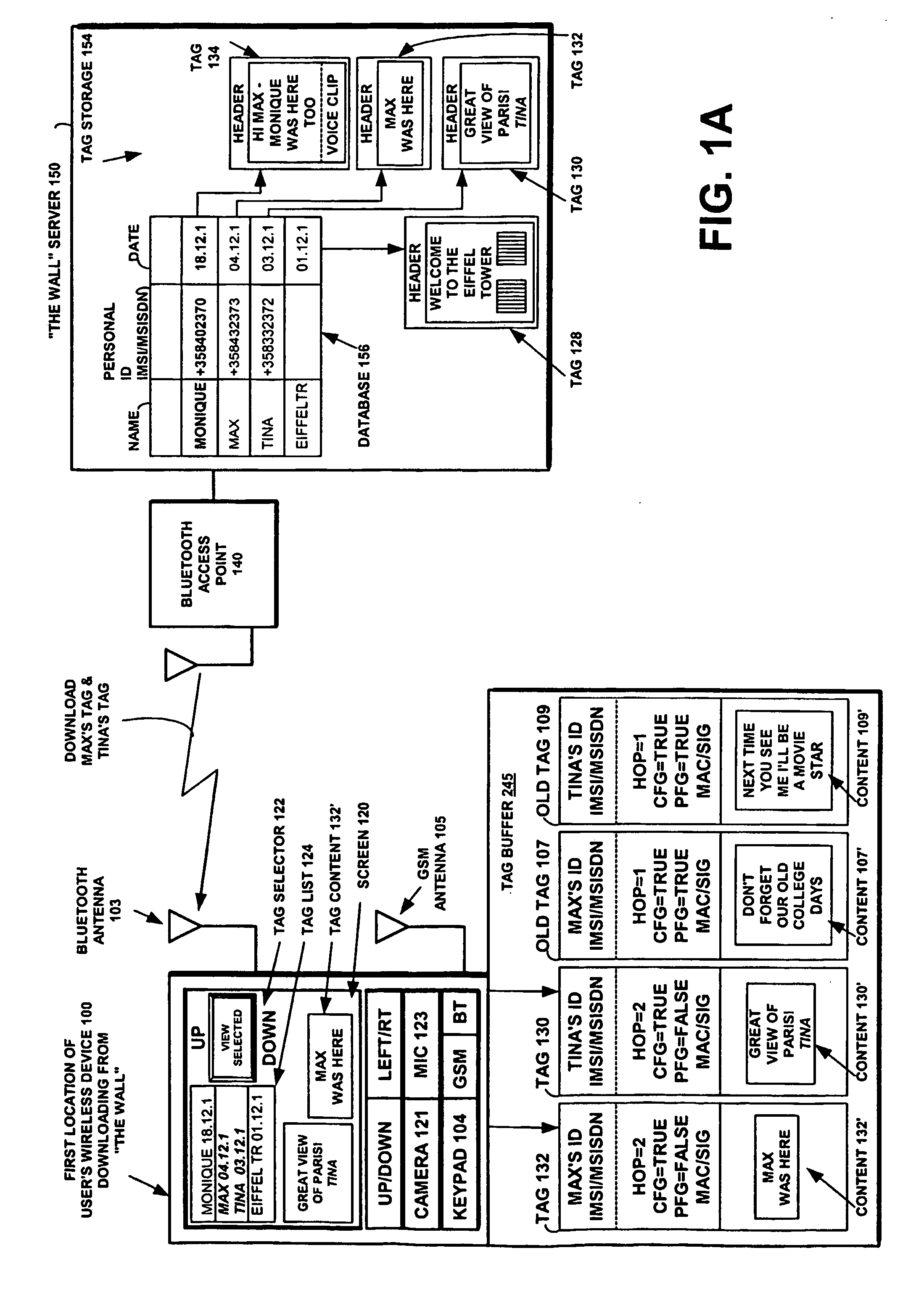
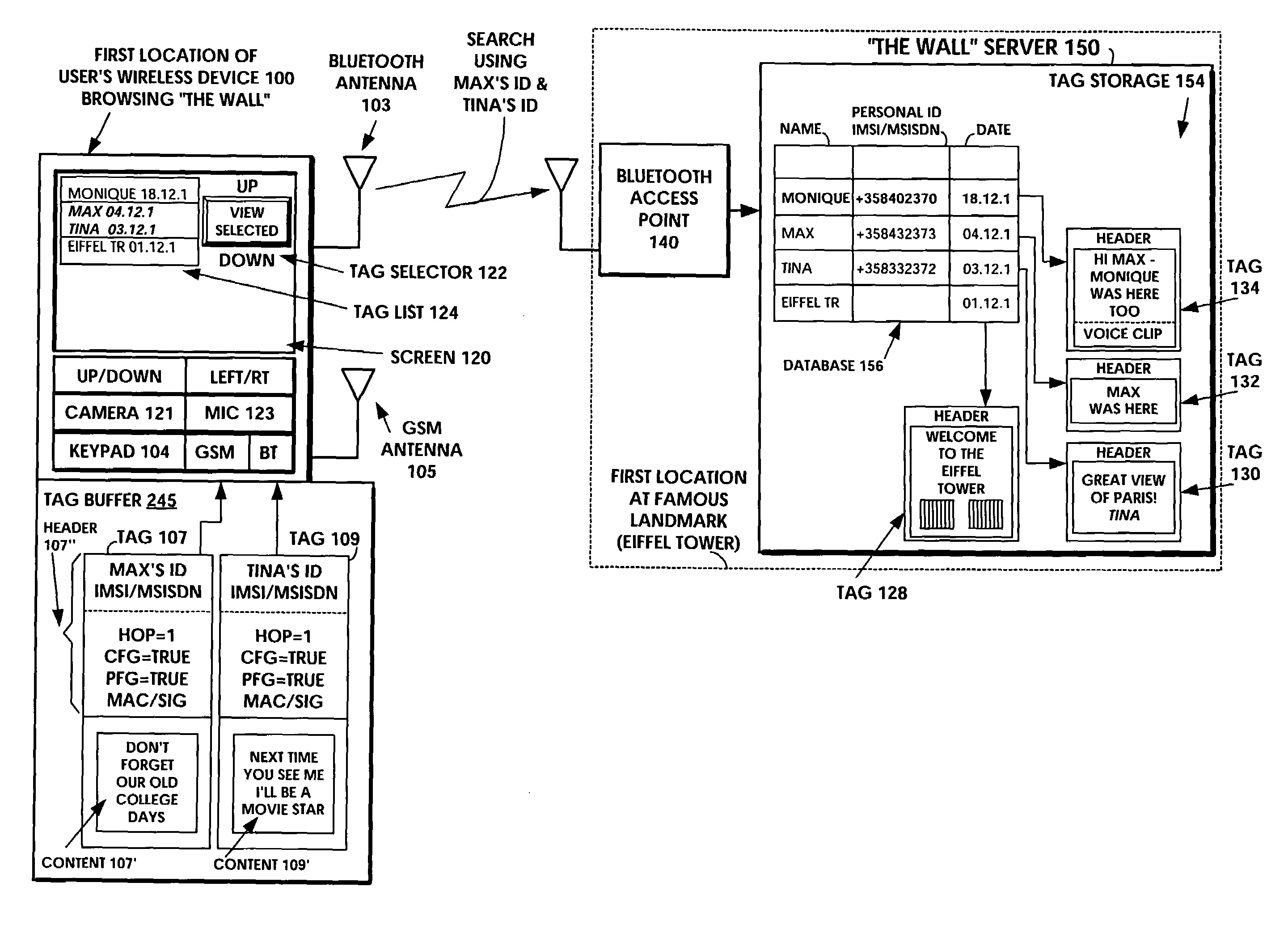
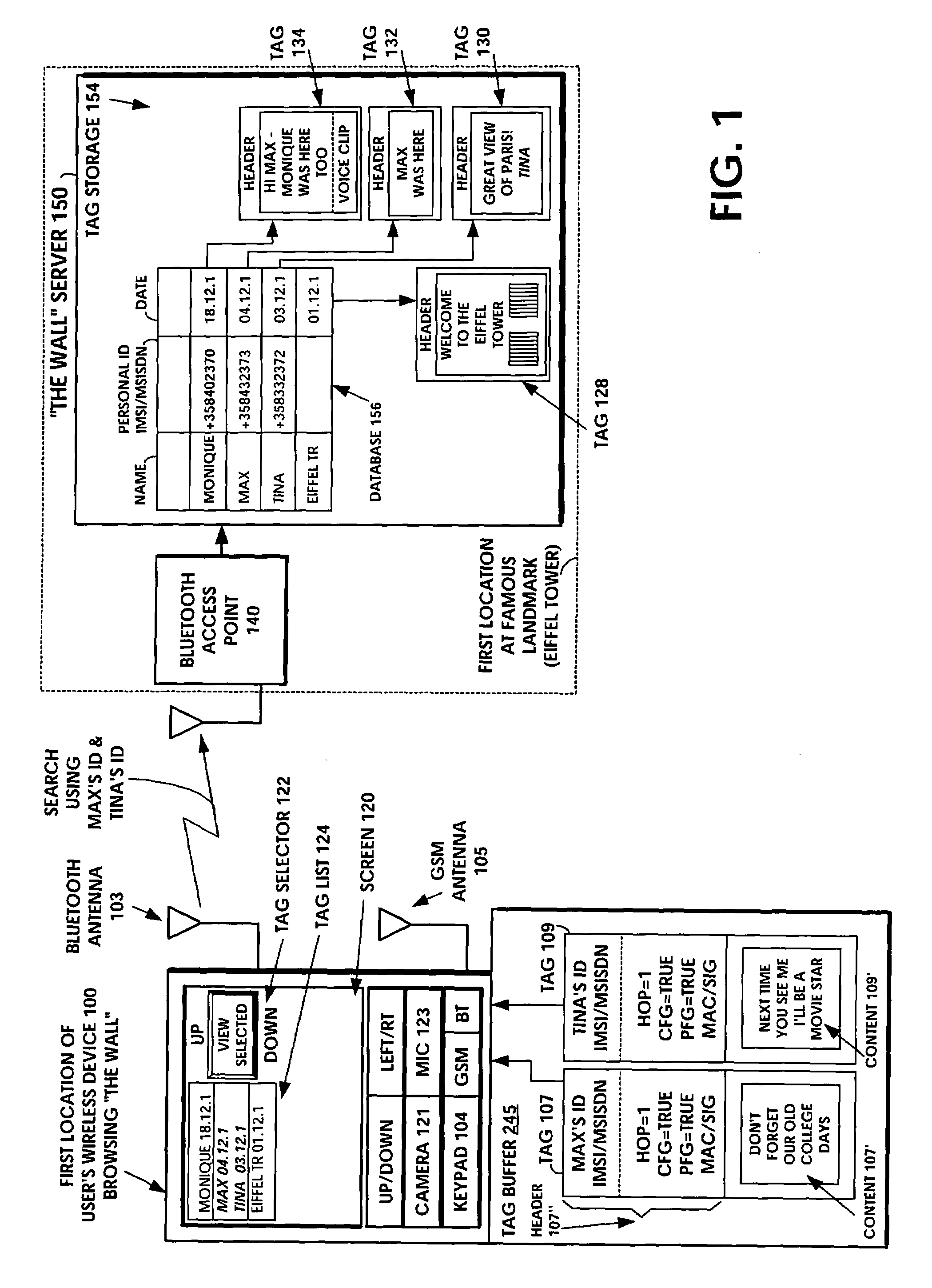
ActiveUS20050113066A1Storage requirements is greatly reducedAvoid receivingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareEncryption
A multimedia data construct called a tag may be stored and transferred. A user can use multimedia content, to create a the content portion of a tag. The multimedia file is then incorporated into the tag or it can be referenced by a pointer in the tag. The multimedia file is artistic expression of the user and the tag uniquely associates the user's identity with the multimedia file by prohibiting alteration of the content after the user completes its creation. The tag includes at least one dynamic indicator that may be changed based on one or more predefined rules upon transmission. The tag may include an ID, that may be based on subscriber information. Encryption techniques may be employed to protect privacy concerns so that such subscriber information is not freely available.
Owner:NOKIA TECHNOLOGLES OY
Short-range wireless system and method for multimedia tags
InactiveUS7340214B1Storage requirements is greatly reducedAvoid receivingError preventionFrequency-division multiplex detailsComputer hardwareHiperLAN
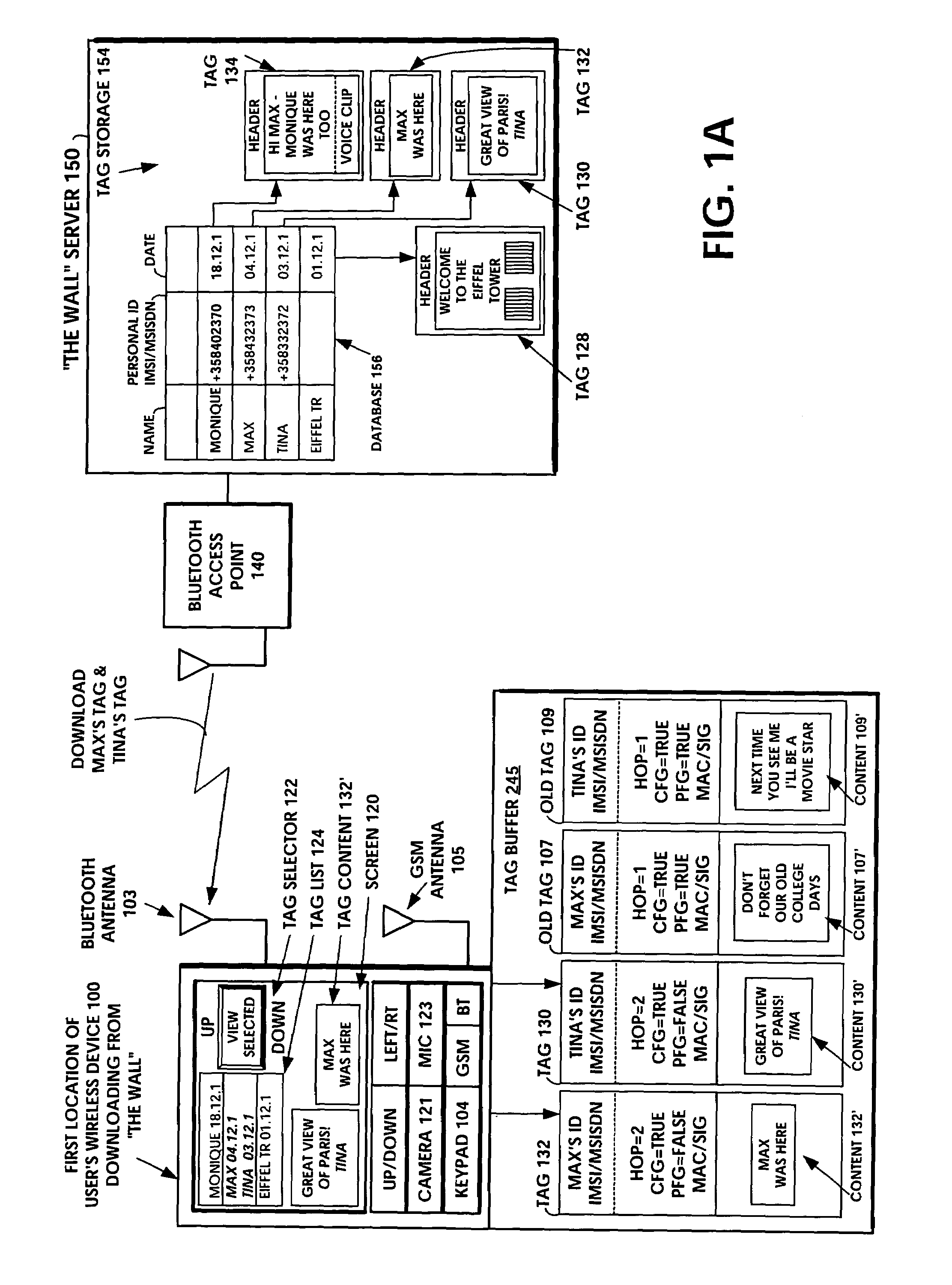
A short-range wireless system and method is disclosed to store and transfer a new type of multimedia data construct called a tag. A user can write text, create a voice clip and append it to the text, take a digital picture and append it to the text, to create a multimedia file as the content of a tag. The creation or modifying of the multimedia file can be done in the user's mobile wireless device or off line and then stored in the mobile device. The multimedia file is then incorporated into the tag or it can be referenced by a pointer in the tag. The multimedia file is artistic expression of the user and the tag uniquely associates the user's identity with the multimedia file by prohibiting alteration of the content after the user completes its creation. A content-originator flag (CFG) value in the tag is set to “false” during the period when the user is creating or modifying the tag's content. When the user completes editing the content of the tag, the content-originator flag (CFG) value is set to true, thereby freezing the content. The tag includes the user's ID, such as his / her international mobile subscriber identity (IMSI) or mobile station ISDN number (MSISDN). Subsequent viewers of the content can make a copy of the content and can then modify it, but they cannot authentically attribute the modified copy to the original user. The system can be implemented as a wireless personal area network (PAN) such as provided in the Bluetooth Standard or a wireless local area network (LAN) such as provided in the IEEE 802.11 Wireless LAN Standard and the HIPERLAN Standard.
Owner:NOKIA TECH OY
Detecting duplicate and near-duplicate files
InactiveUS7366718B1Eliminate duplicate documentsStorage requirements is greatly reducedData processing applicationsWeb data indexingDocument preparationDocumentation
Owner:GOOGLE LLC
System and method for compression in a distributed column chunk data store
ActiveUS7447865B2Storage requirements is greatly reducedReduce transfer timeDigital data information retrievalMemory adressing/allocation/relocationDatabase engineData storing
An improved system and method for compression in a distributed column chunk data store is provided. A distributed column chunk data store may be provided by multiple storage servers operably coupled to a network. A storage server provided may include a database engine for partitioning a data table into the column chunks for distributing across multiple storage servers, a storage shared memory for storing the column chunks during processing of semantic operations performed on the column chunks, and a storage services manager for striping column chunks of a partitioned data table across multiple storage servers. Any data table may be flexibly partitioned into column chunks using one or more columns with various partitioning methods. Domain specific compression may be applied to a column chunk to reduce storage requirements of column chunks and increase transmission speeds for sending column chunks between storage servers.
Owner:GOOGLE LLC
Providing VCR functionality for data-centered video multicast
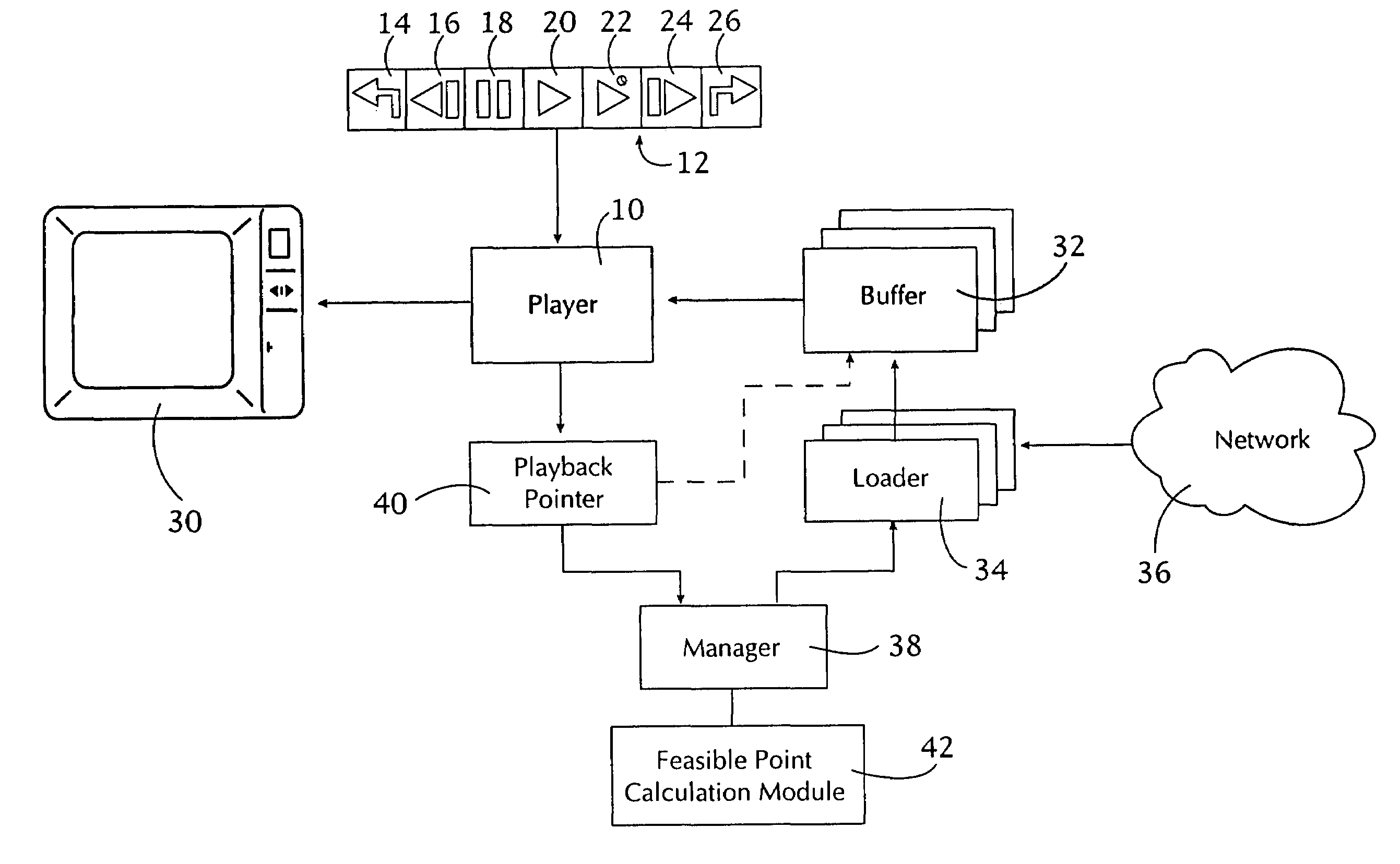
InactiveUS6993787B1Reduce storage requirementsHigh speedTwo-way working systemsSelective content distributionComputer hardwareBroadcast channels
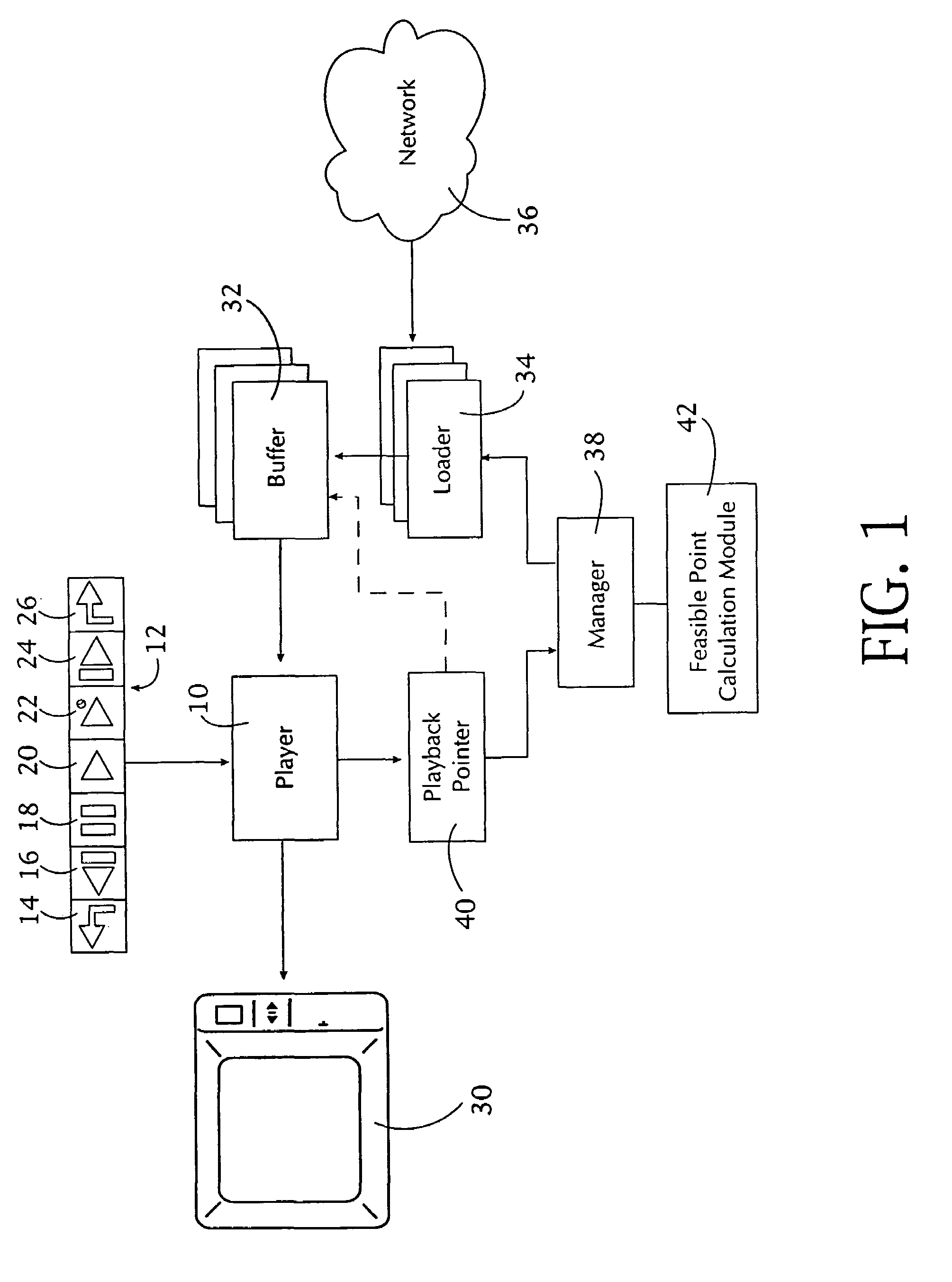
The client application provides VCR functionality in a data-centered video multicast network (36) through active prefetching of the fragments from broadcast channels. The player (10) has a user interface (12) that supports a plurality of VCR functions (14–26). Plural buffers (32) and their associated loaders (34) download video data under control of a manager module (38). The manager module accesses the playback pointer (40) and employs feasible point calculation module (42) to cause the loaders to selectively download segments so that VCR functions can be supported while maintaining continuous playback after the VCR function is performed.
Owner:PANASONIC CORP
Apparatus and method for dynamically controlling the frame rate of video streams
InactiveUS6850564B1Meet growth requirementsReduce storage requirementsColor television with pulse code modulationColor television with bandwidth reductionHigh frame rateMotion vector
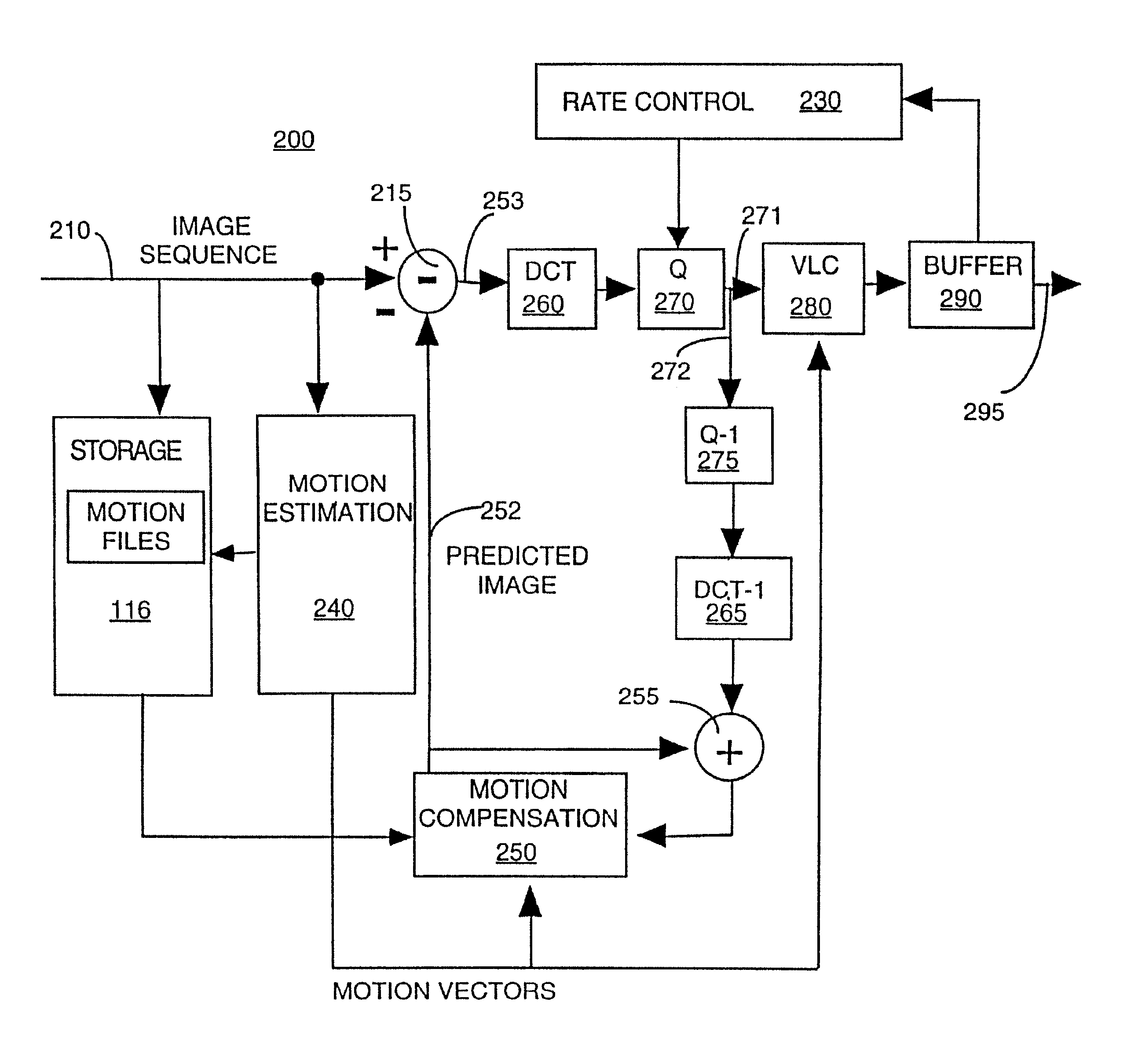
An apparatus and method for dynamically varying the frame rate of an image sequence is disclosed. In one embodiment, the image sequence is encoded and stored at different frame rates (e.g., 30, 25, 20 fps and so on). Alternatively, only the motion information, e.g., motion vectors, for the other frame rates are stored.
Owner:SARNOFF CORP
LDPC decoder, corresponding method, system and computer program
ActiveUS20050138519A1Reduce storage requirementsReduce computational complexityError detection/correctionError correction/detection using multiple parity bitsTheoretical computer scienceBelief propagation
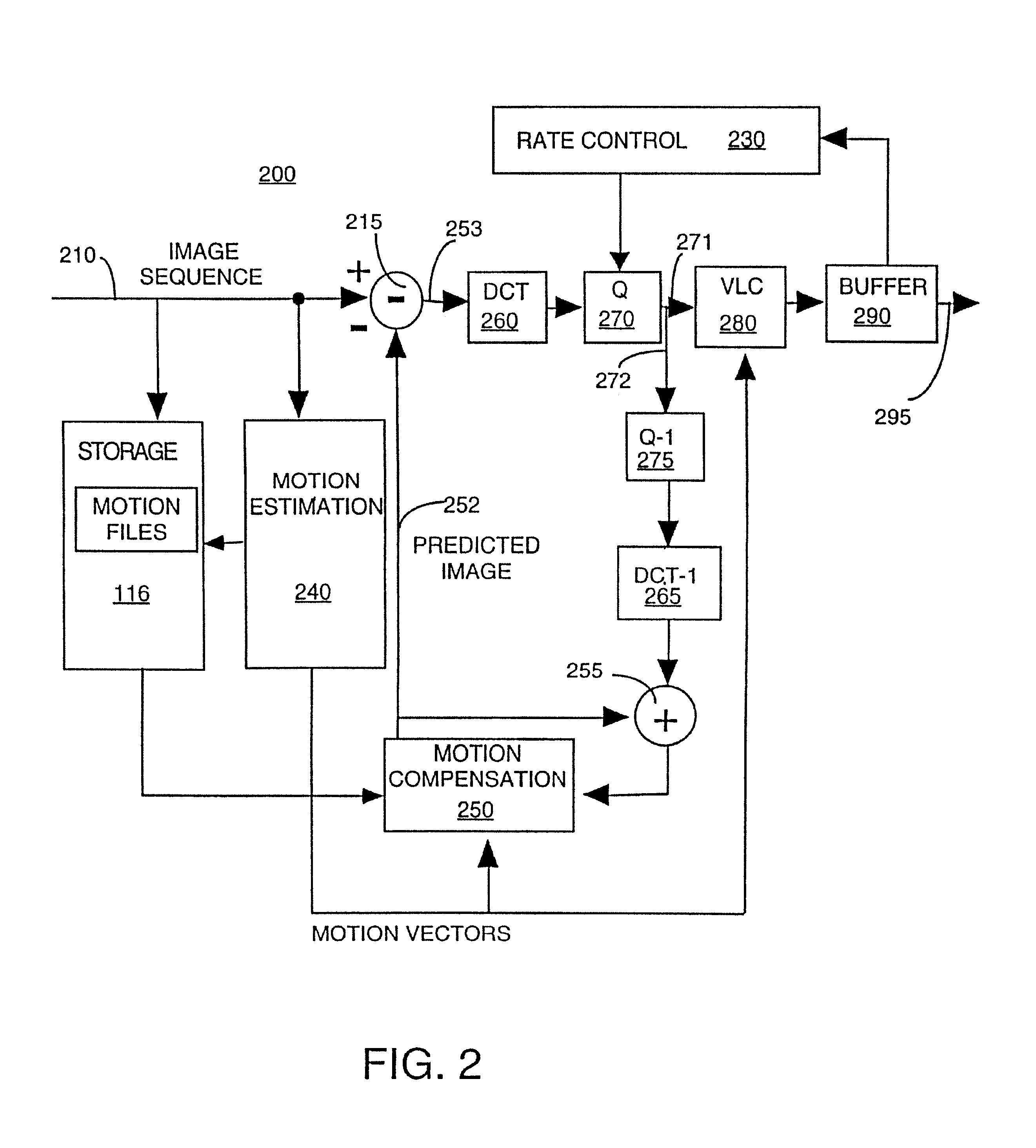
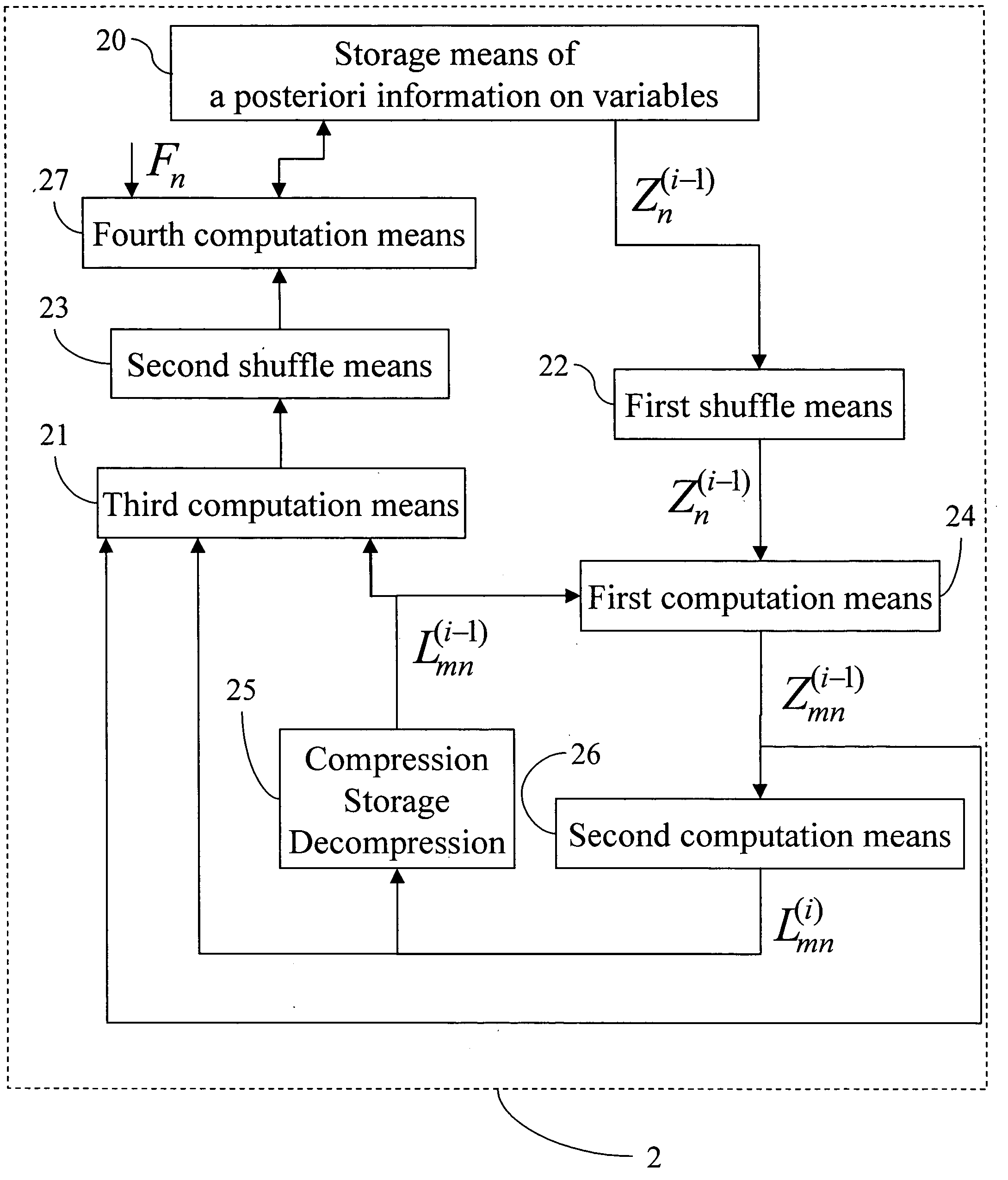
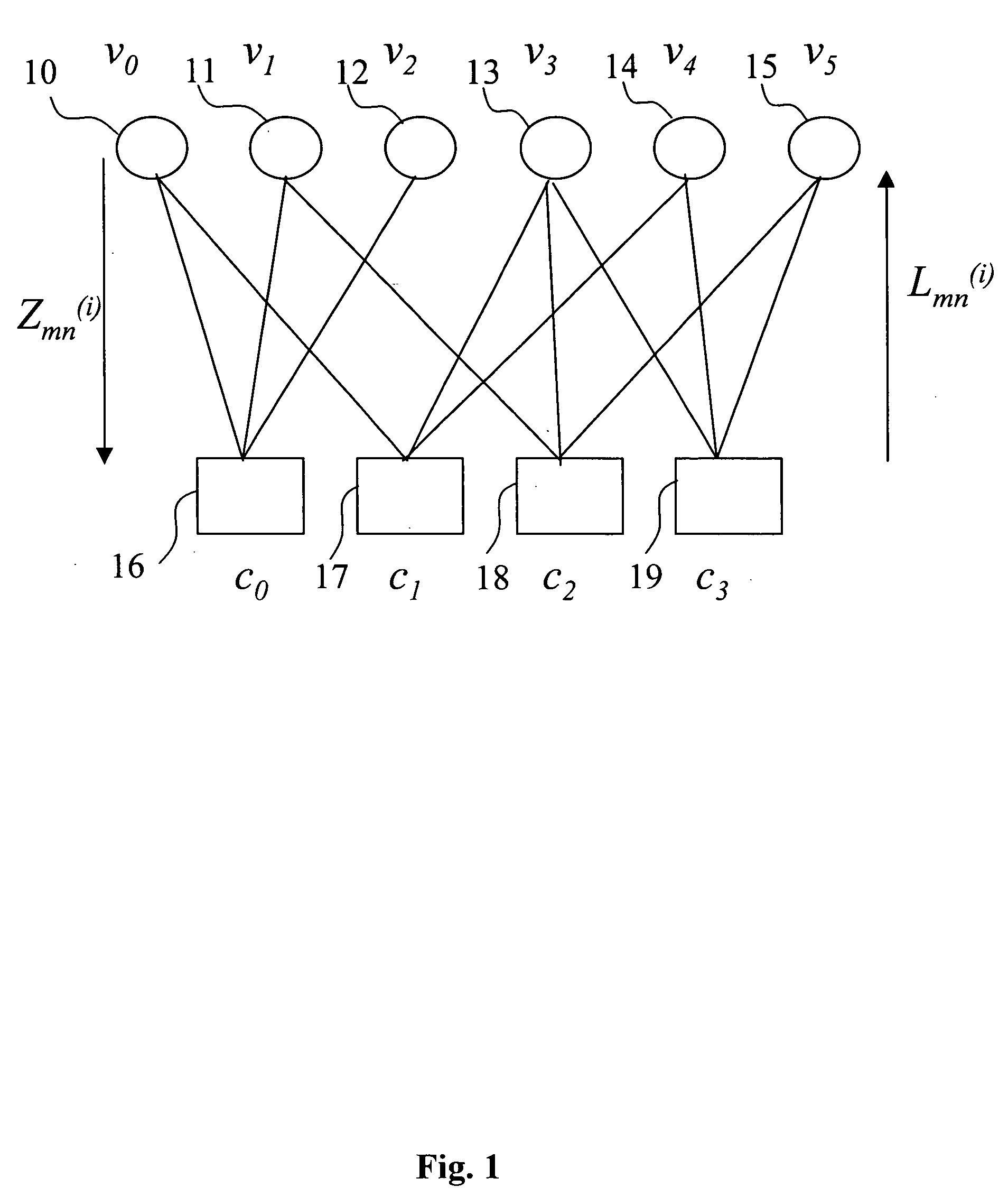
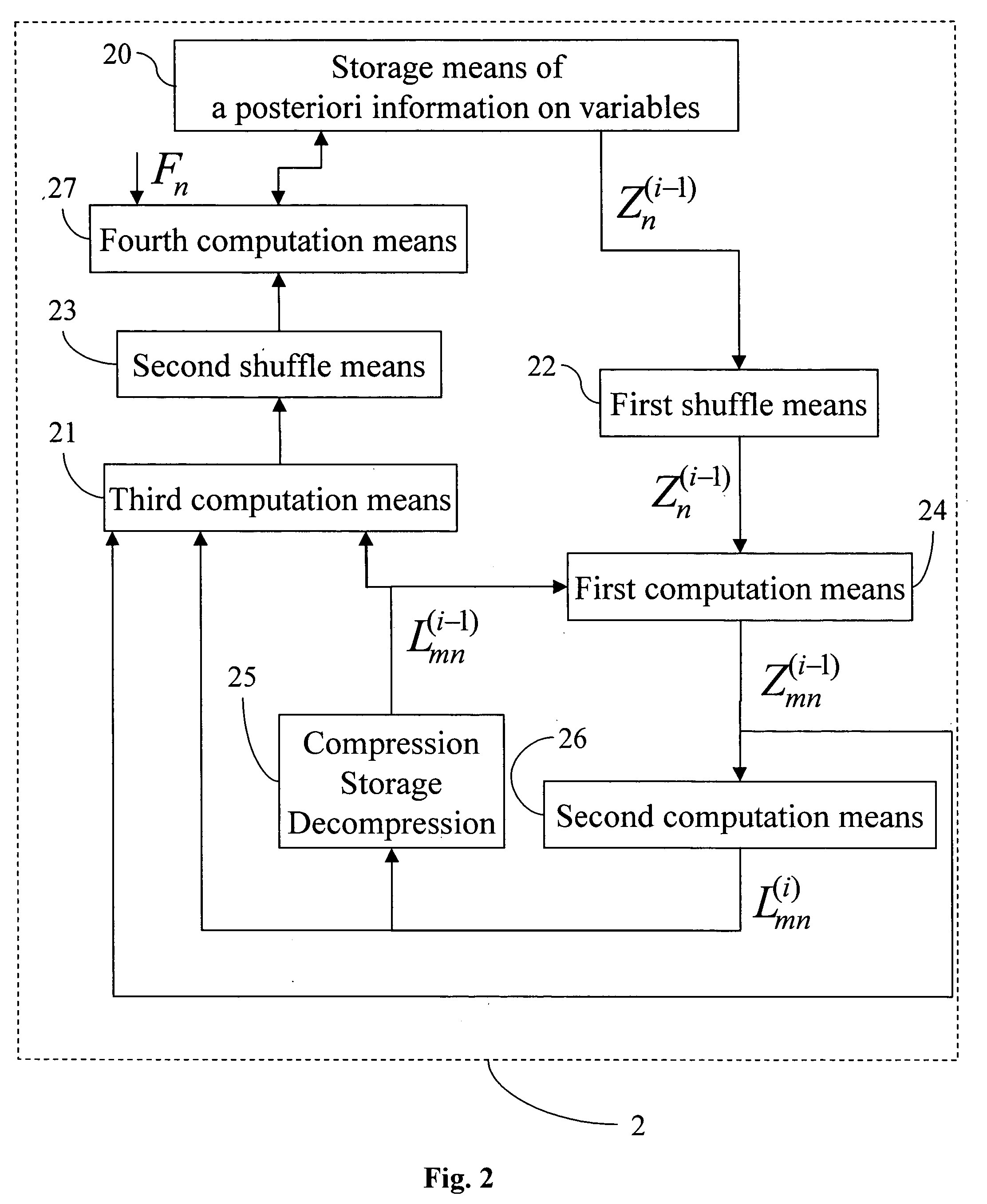
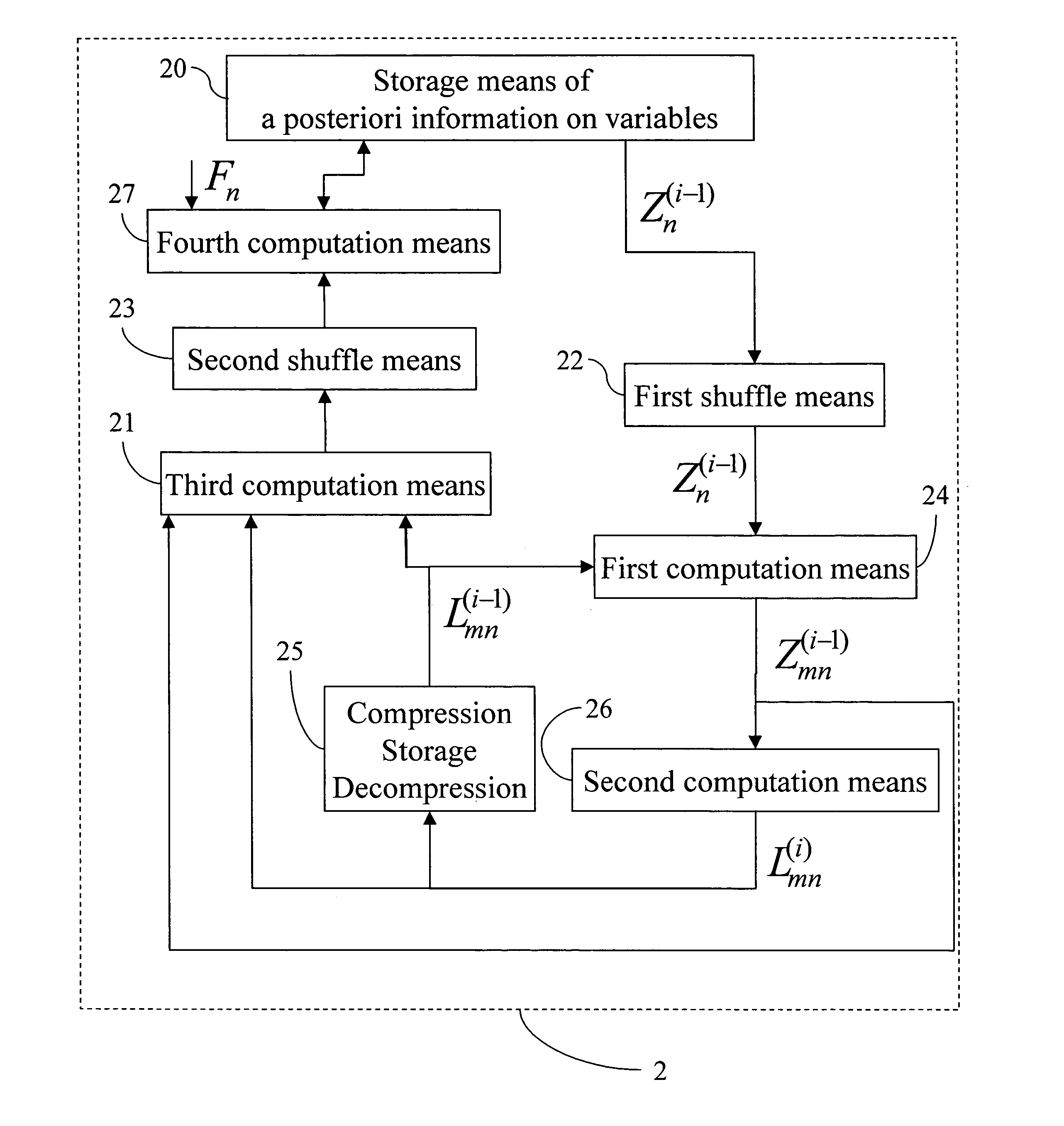
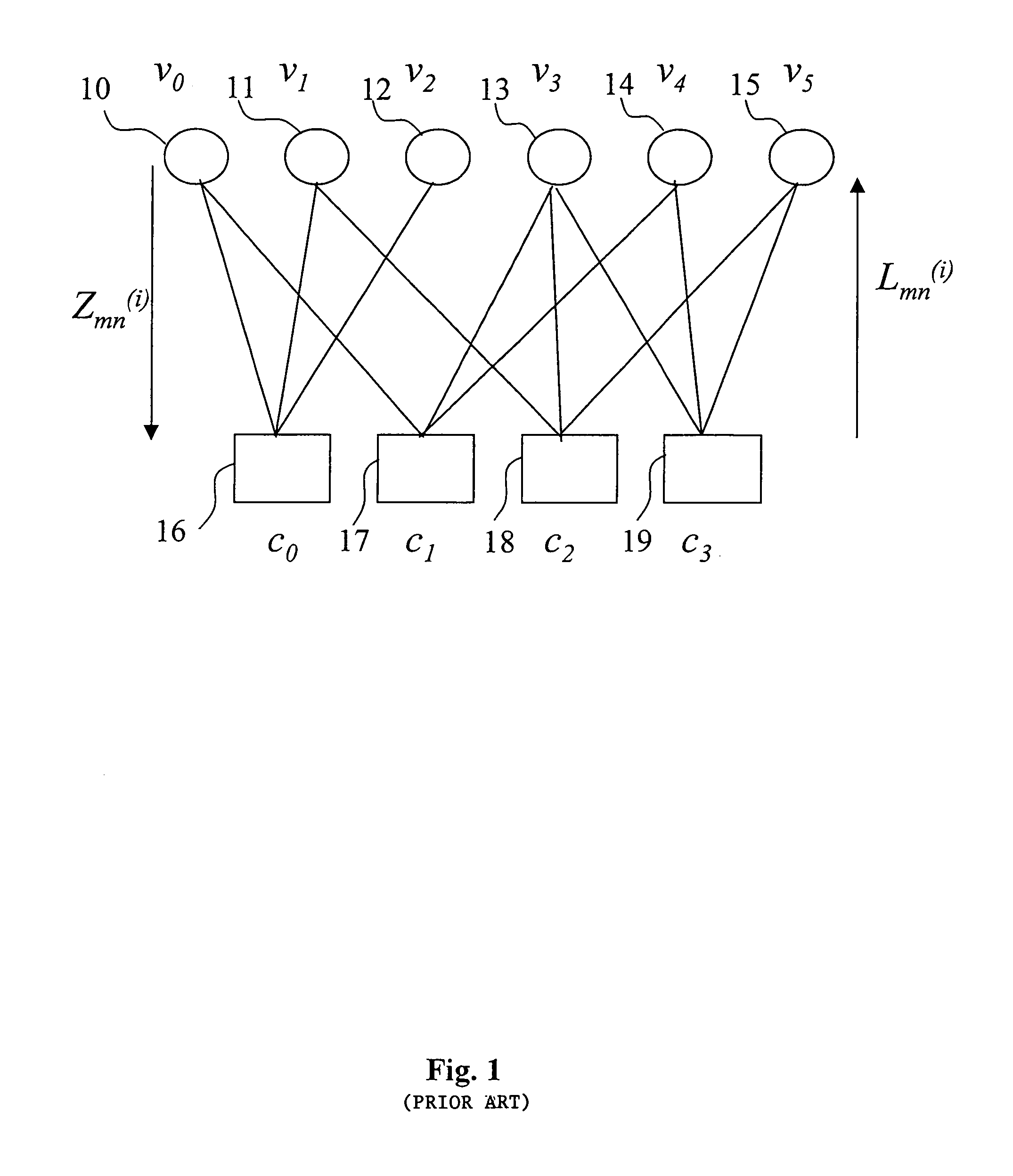
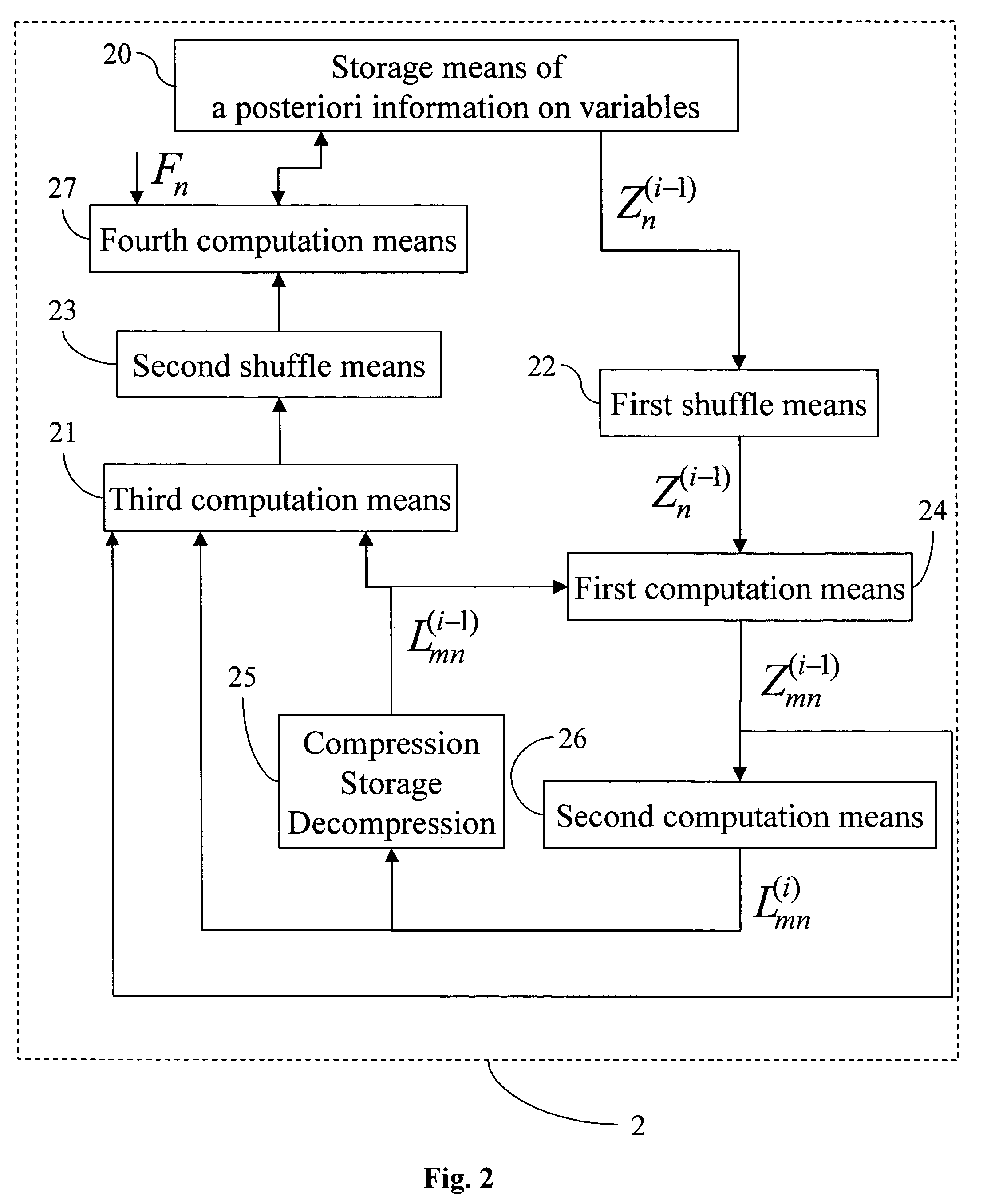
A decoder of LDPC codewords on GF(rq), using the iterative belief propagation algorithm comprises at least storing means to store a posteriori information on variables. Updating means updates the a posteriori information on variables, and computation means computes variables to constrain messages from a posteriori information on variables and variable to constraint messages from previous iteration. Computation means computes a constraint to variable messages from variable to constraint messages computed by the first computation means. Computation means updates the a posteriori information on variables. Shuffle means transfers the a posteriori information on variables to the first computation means, and shuffle means transfers information from the second computation means to the storing means. Compression-storage-decompression means constraint to variable messages. In one form, the invention concerns also corresponding method, computer program and system.
Owner:TURBOCONCEPT SARL +1
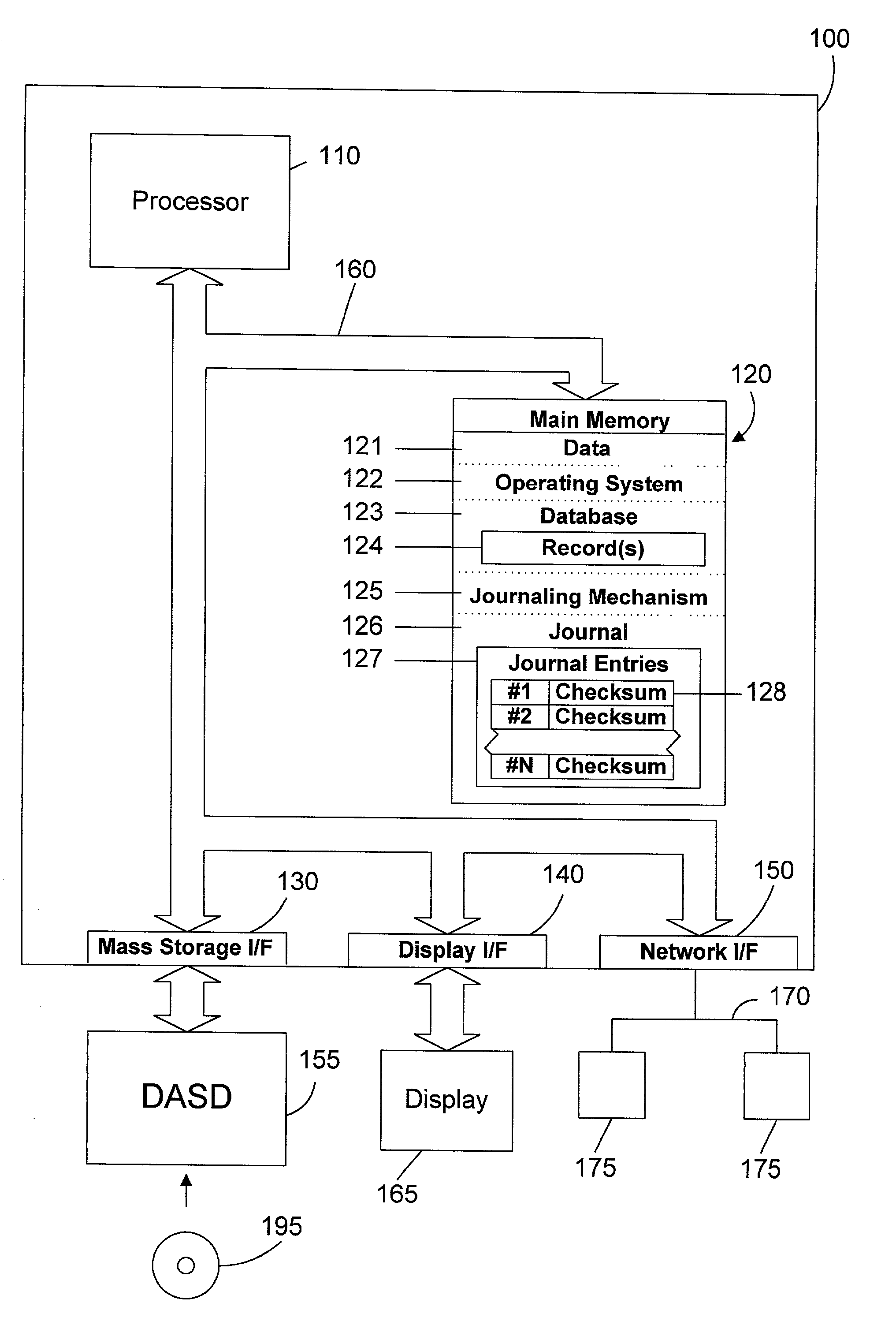
Apparatus and method for validating a database record before applying journal data
ActiveUS20030217031A1Minimizing dataPotential problemData processing applicationsDigital data information retrievalDatabaseRaw data
An apparatus and method includes a database journal that records journal entries. Each journal entry includes a validation value that is computed from the data and metadata for the record before it is changed. In this manner, journal entries may be applied with confidence to a record in a database. This is especially useful when minimized data journal entries are used. If the validation value of the journal entry matches the validation value computed from the data and metadata of the record that the journal entry is to be applied to, then the record before applying the journal entry is identical to the record in the original database, and the journal data may be applied to the database record. If the validation value of the journal entry does not match the validation value computed from the data and metadata of the record that the journal entry is to be applied to, the record is not the same as in the original database when the journal entry was generated. As a result, an error message is generated to indicate that an error was encountered when applying the journal entry. In this manner, the apparatus and method of the preferred embodiments automatically validate a database record before applying journal data to the record.
Owner:IBM CORP
System and method for compression in a distributed column chunk data store
ActiveUS20070061544A1Reduce storage requirementsReduce transfer timeDigital data information retrievalSpecial data processing applicationsDatabase engineData storing
An improved system and method for compression in a distributed column chunk data store is provided. A distributed column chunk data store may be provided by multiple storage servers operably coupled to a network. A storage server provided may include a database engine for partitioning a data table into the column chunks for distributing across multiple storage servers, a storage shared memory for storing the column chunks during processing of semantic operations performed on the column chunks, and a storage services manager for striping column chunks of a partitioned data table across multiple storage servers. Any data table may be flexibly partitioned into column chunks using one or more columns with various partitioning methods. Domain specific compression may be applied to a column chunk to reduce storage requirements of column chunks and increase transmission speeds for sending column chunks between storage servers.
Owner:GOOGLE LLC
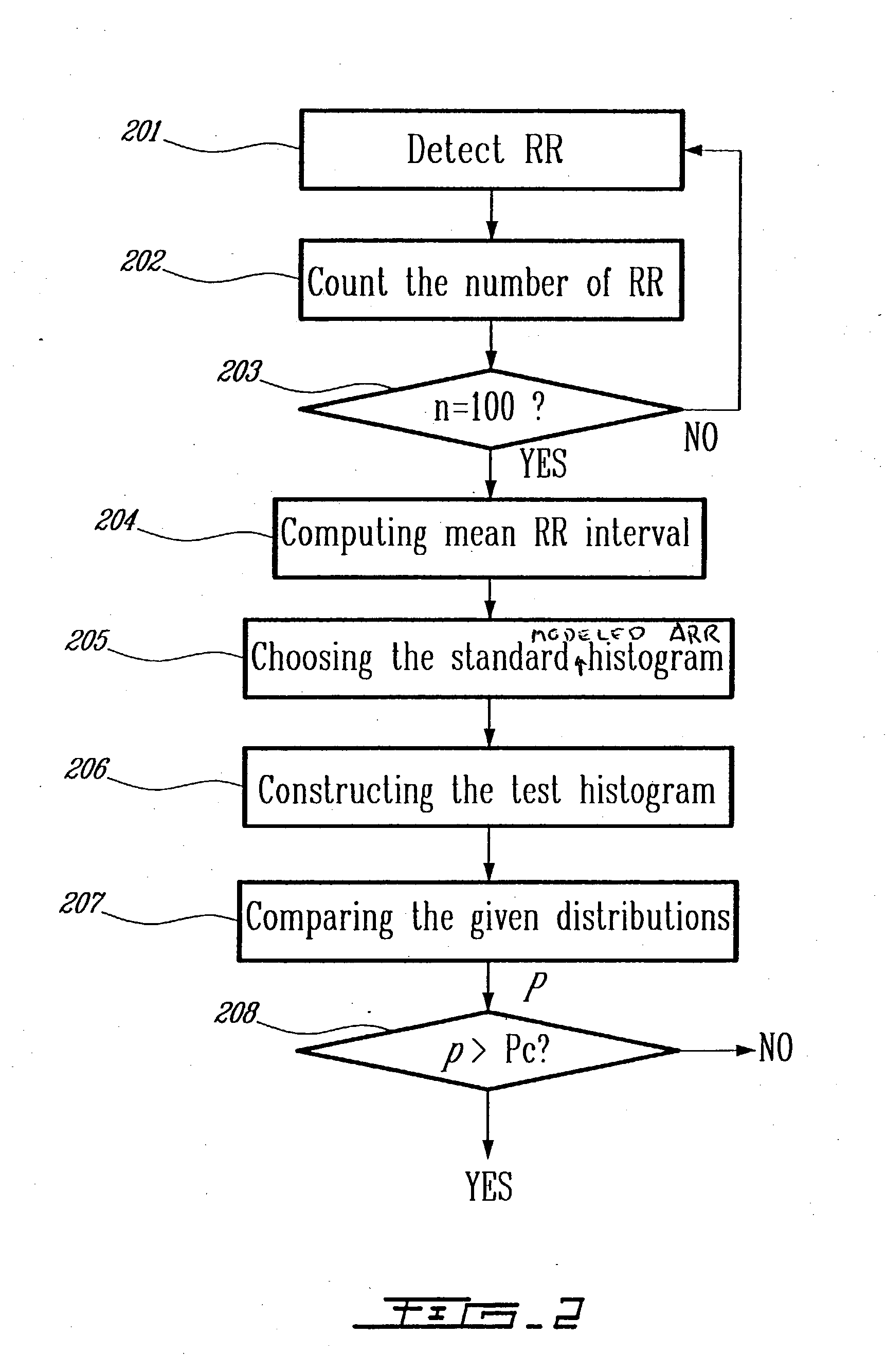
Detection of cardiac arrhythmia using mathematical representation of standard deltaRR probability density histograms
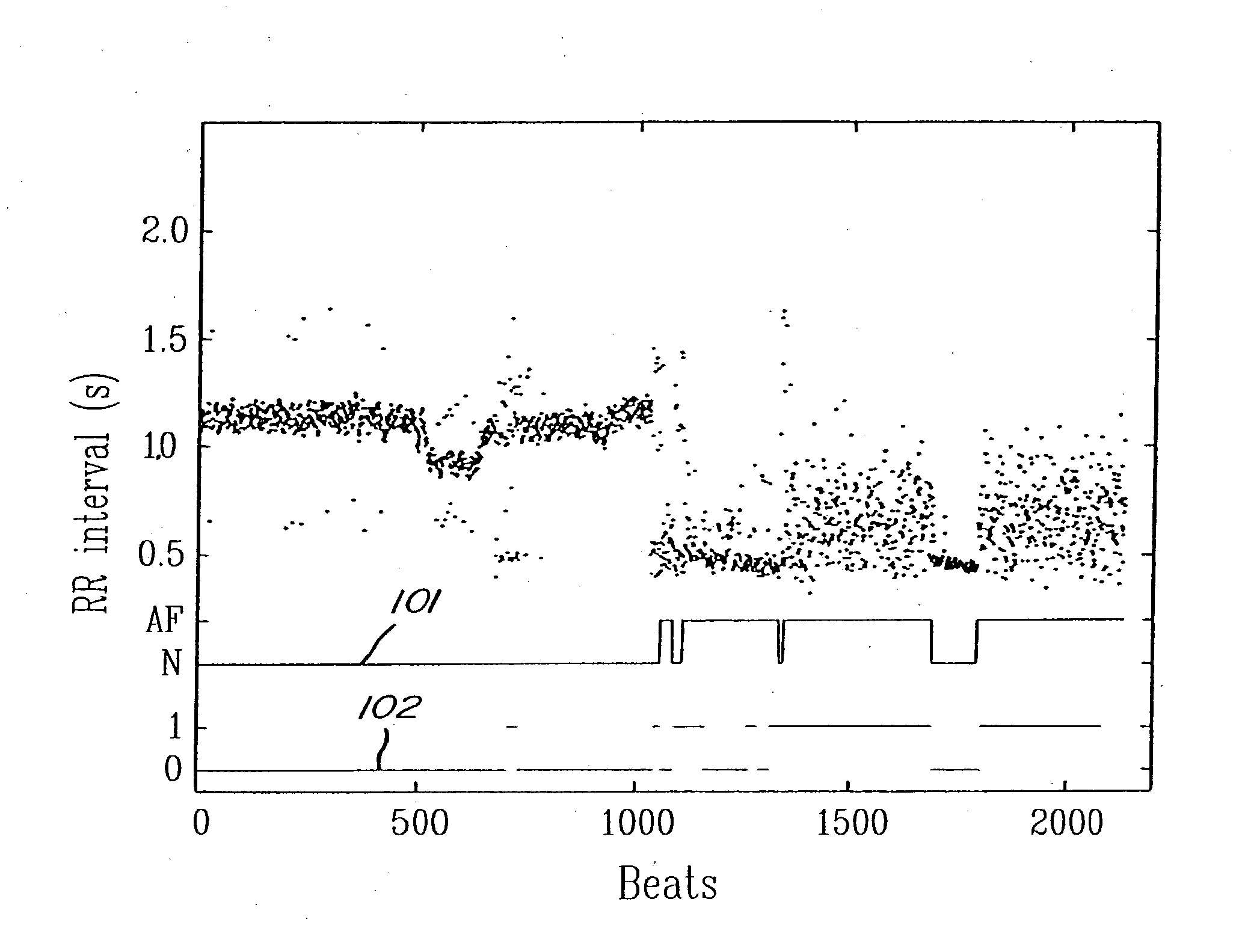
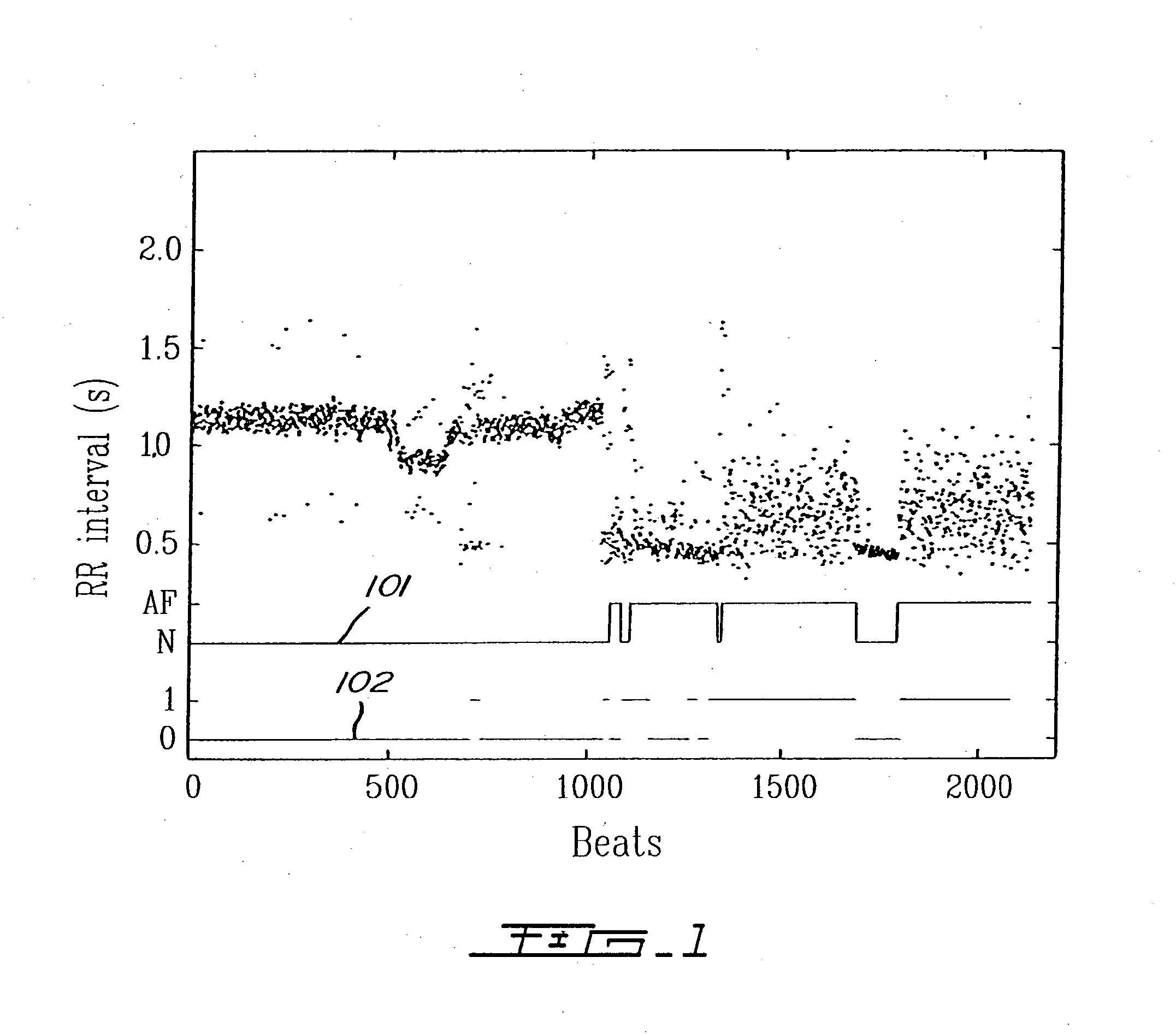
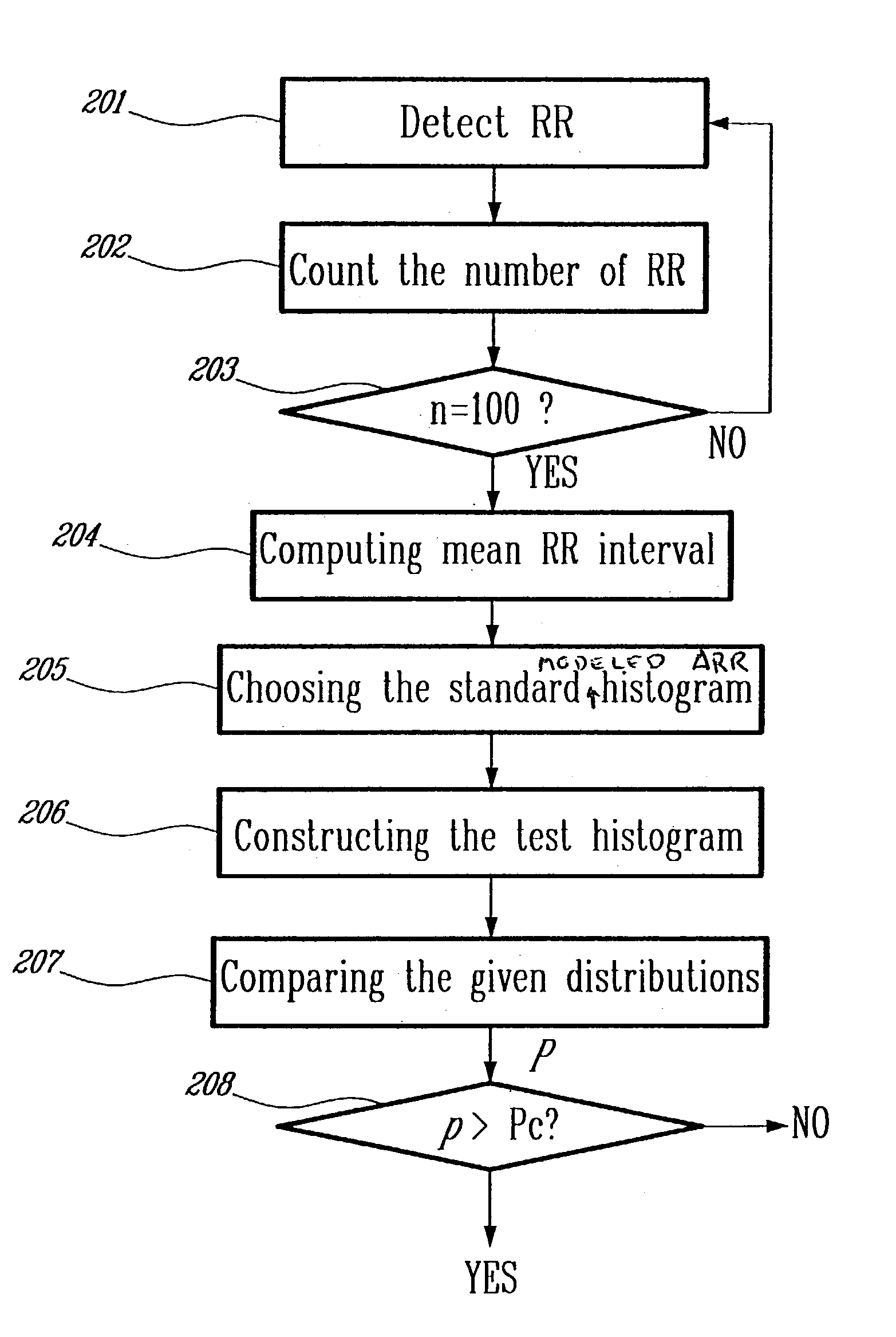
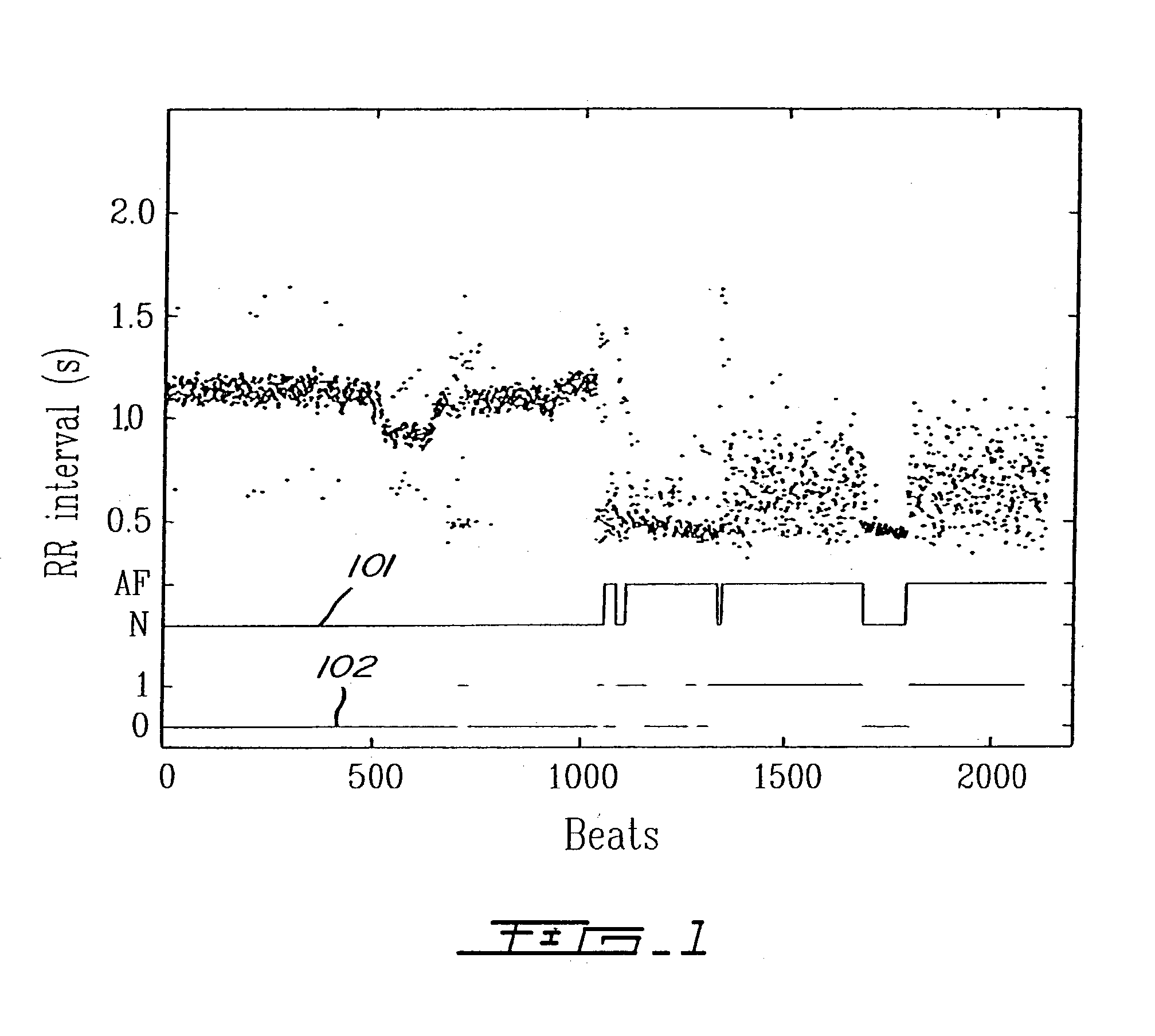
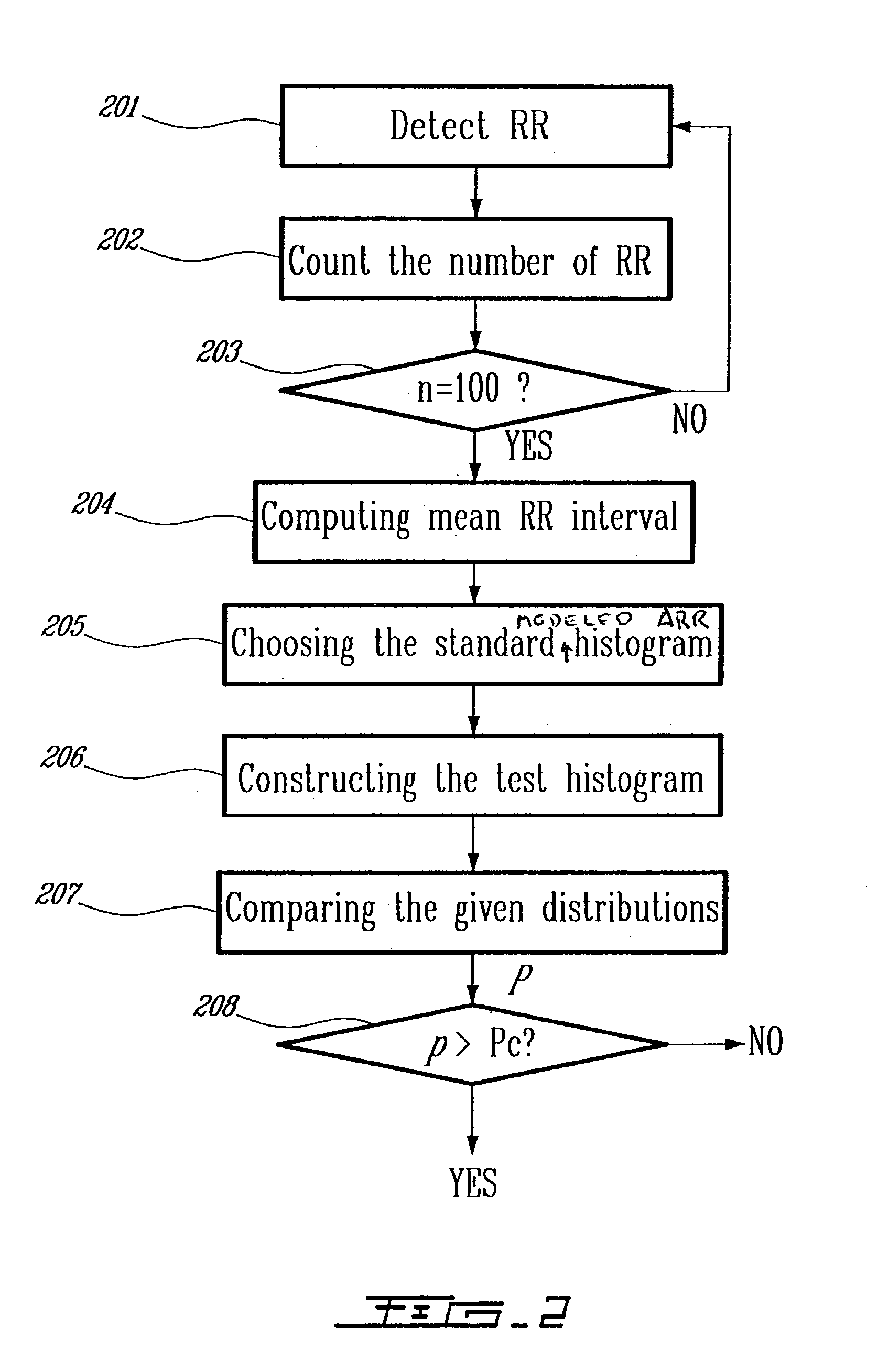
ActiveUS20050004486A1Improve accuracyReduce storage requirementsElectrocardiographySensorsRR intervalMedicine
A method and a system for detecting cardiac arrhythmias that includes detecting RR intervals of the patient wherein each RR interval is an interval between two heart beats, and simulating standard probability density histograms of ΔRRs by means of a suitable probability distribution calculated through at least one mathematical formulae, wherein ΔRR is a difference between two successive RR intervals. Test probability density histograms of ΔRRs of the patient are constructed from the detected RR intervals. Finally, the standard and test histograms are compared to detect whether the patient suffers from cardiac arrhythmia. As non limiting examples, the standard probability density histograms of ΔRRs are modeled by a mathematical equation selected from the group consisting of: the Lorentzian distribution, the Gaussian distribution, the Student's t-distribution, and a probability distribution including a linear combination of the Lorentzian and Gaussian distribution.
Owner:THE ROYAL INSTION FOR THE ADVANCEMENT OF LEARNING MCGILL UNIV A UNIV
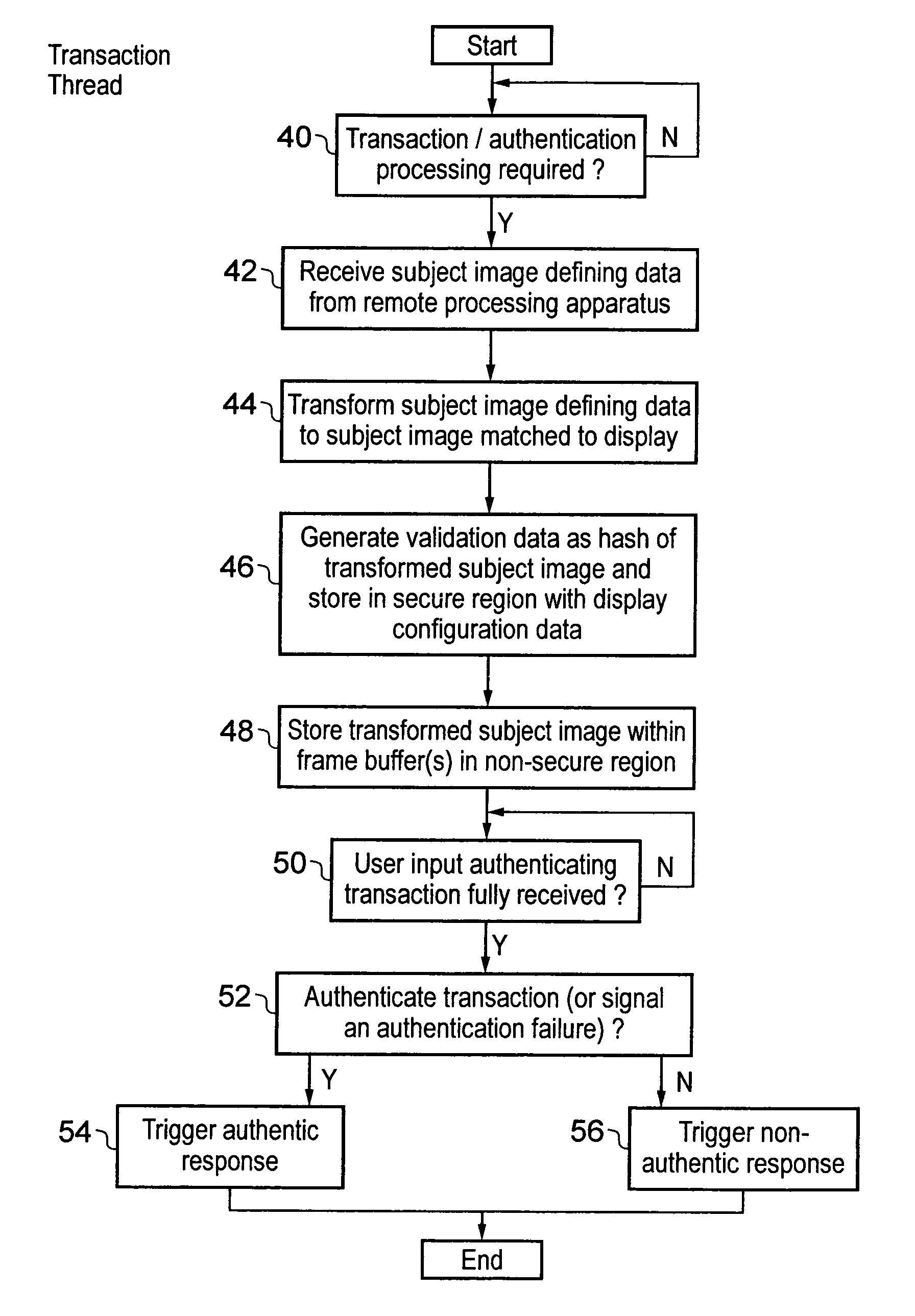
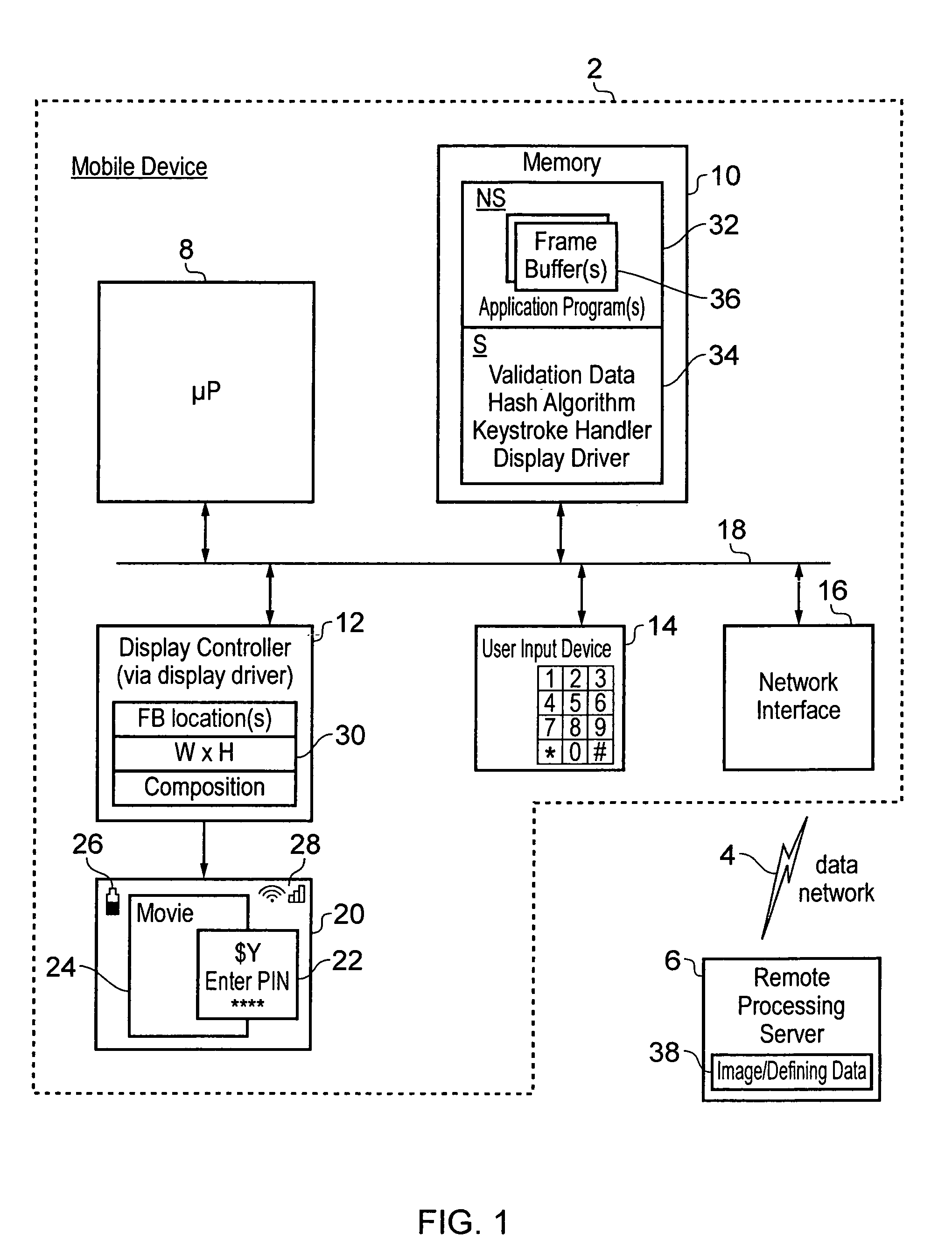
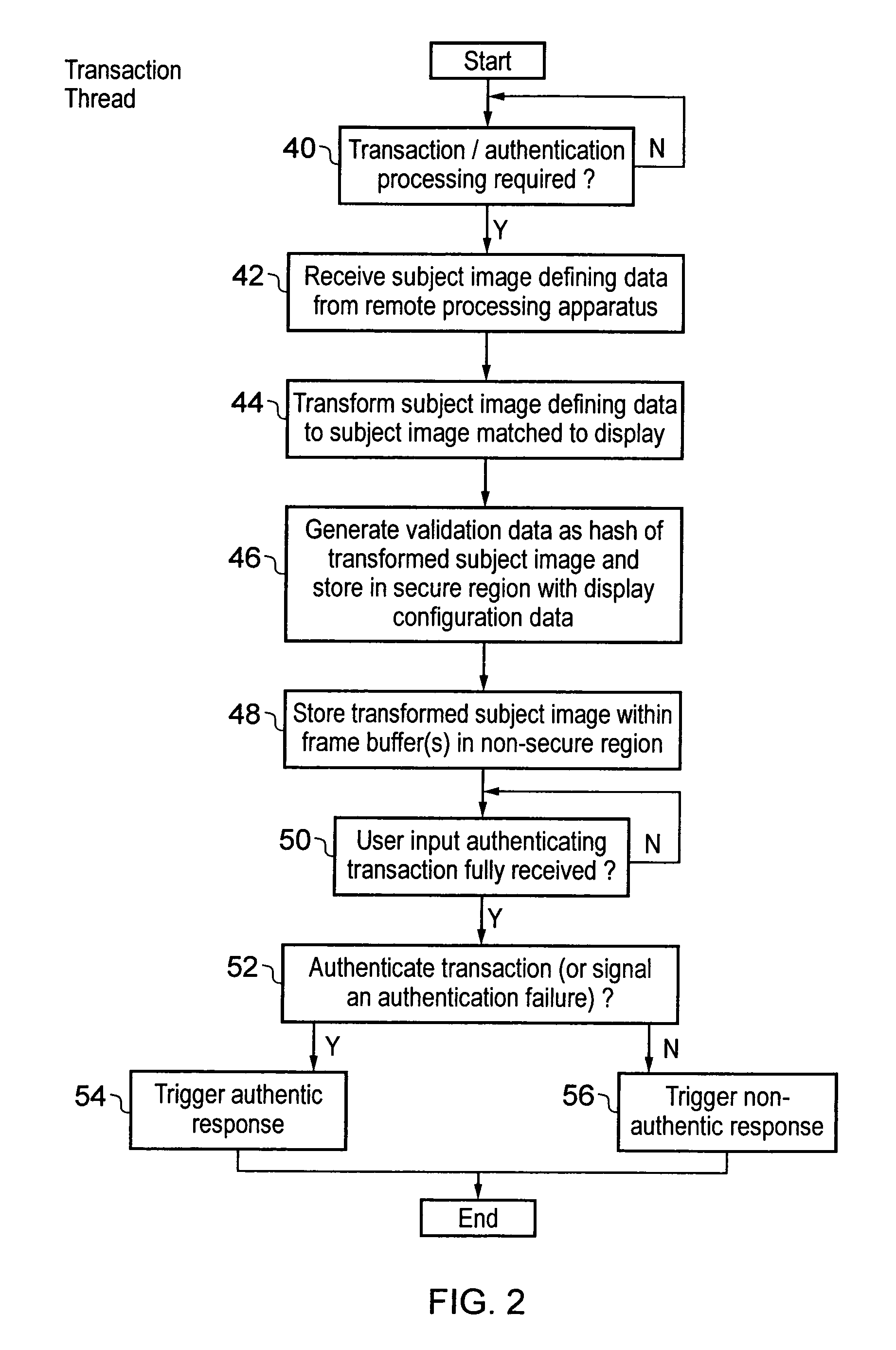
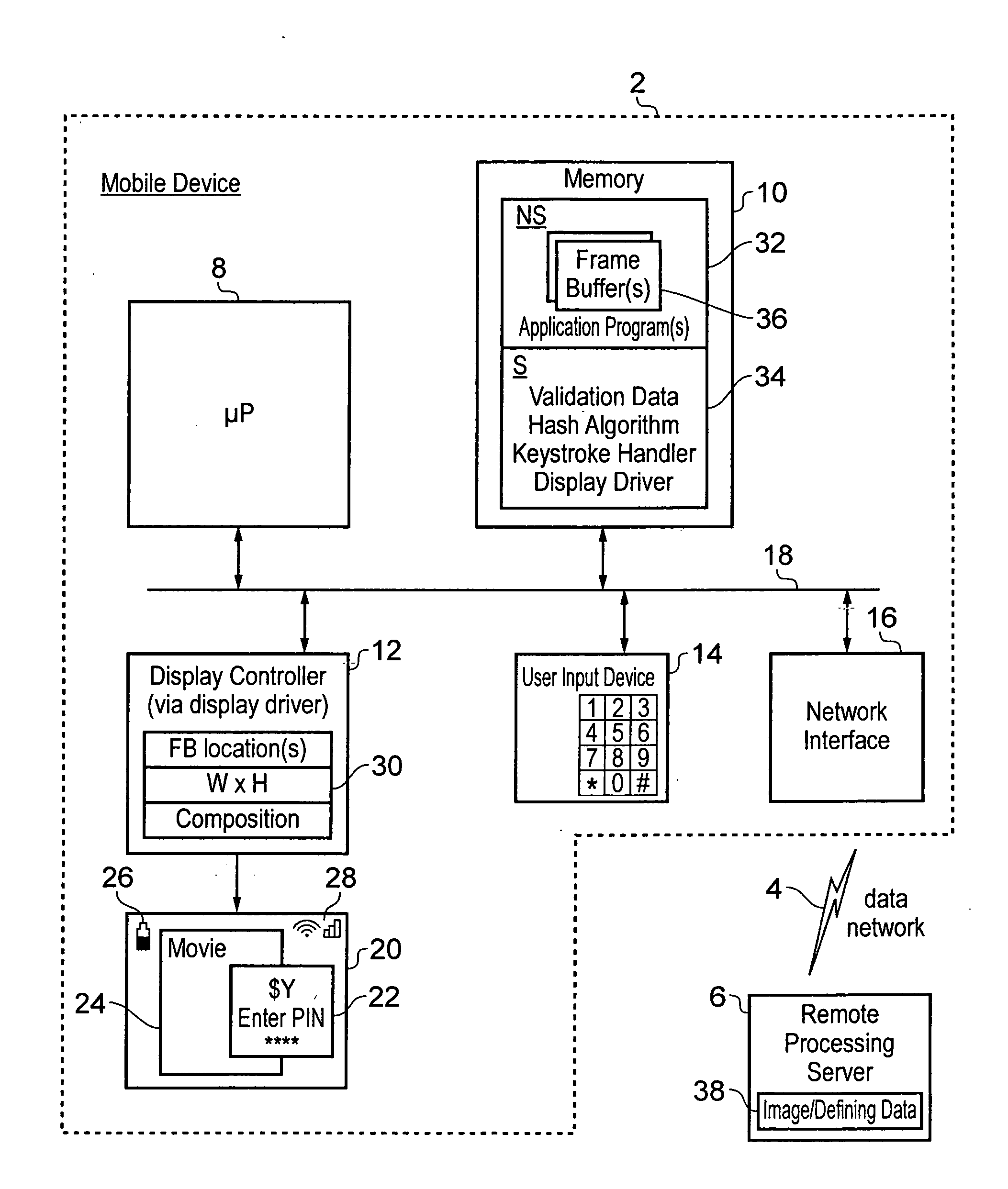
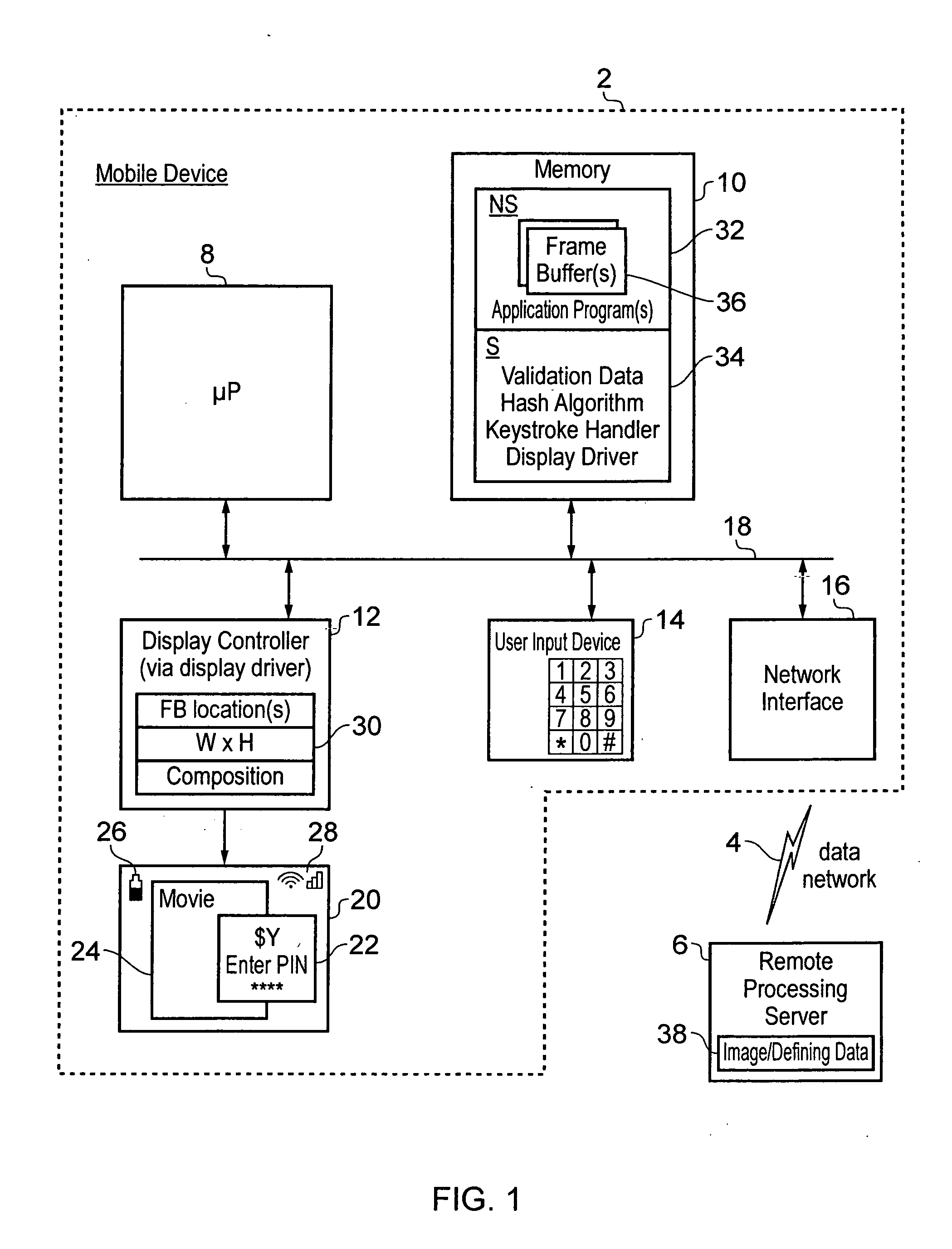
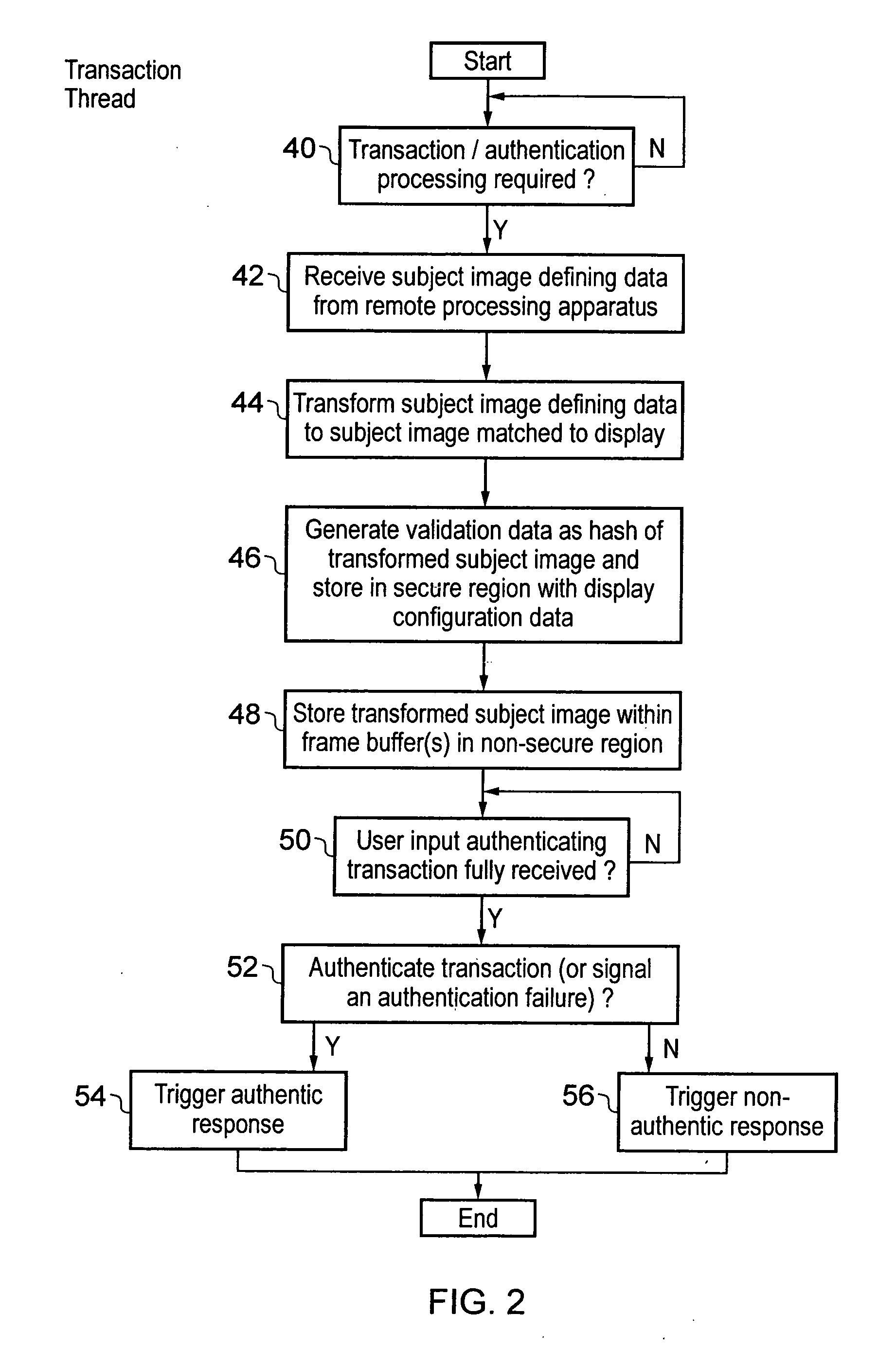
Security provision for a subject image displayed in a non-secure domain
ActiveUS8707056B2Storage requirements is greatly reducedImprove securityDigital data processing detailsAnalogue secracy/subscription systemsUser inputData treatment
A data processing device is provided with a processor core 8 that can operate in either a secure domain or a non-secure domain. Data stored within a secure region 34 of a memory 10 can only be accessed when the processor core 8 is executing in the secure domain. A frame buffer 36 for storing a display image 20 to be displayed is stored within a non-secure region of memory which can be accessed by the processor core 8 irrespective of whether it is in the secure domain or the non-secure domain as well as a display controller 12. When a subject image 22 is written to the frame buffer 36, validation data for the subject image 22 is stored within the secure region 34. When a user input is received the displayed data stored at a validated display area to which the subject image was written is read back and used to generate check data with is compared with the validation data before the user input is authenticated.
Owner:ARM LTD
LDPC decoder, corresponding method, system and computer program
ActiveUS7174495B2Storage requirements is greatly reducedError detection/correctionError correction/detection using multiple parity bitsTheoretical computer scienceBelief propagation
A decoder of LDPC codewords using the iterative belief propagation algorithm stores a posteriori information on variables. An updating device updates the a posteriori information on variables, and a first computation device computes variables to constrain messages from a posteriori information on variables and variable to constraint messages from previous iteration. A second computation device computes a constraint to variable messages from variable to constraint messages computed by the first computation device. A further computation device updates the a posteriori information on variables. A shuffle device transfers the a posteriori information on variables to the first computation device, and a further shuffle device transfers information from the second computation device to the storing device. The decoder further includes a device for compression-storage-decompression of the constraint to variable messages. The disclosure also relates to a corresponding method, computer program and system.
Owner:TURBOCONCEPT SARL +1
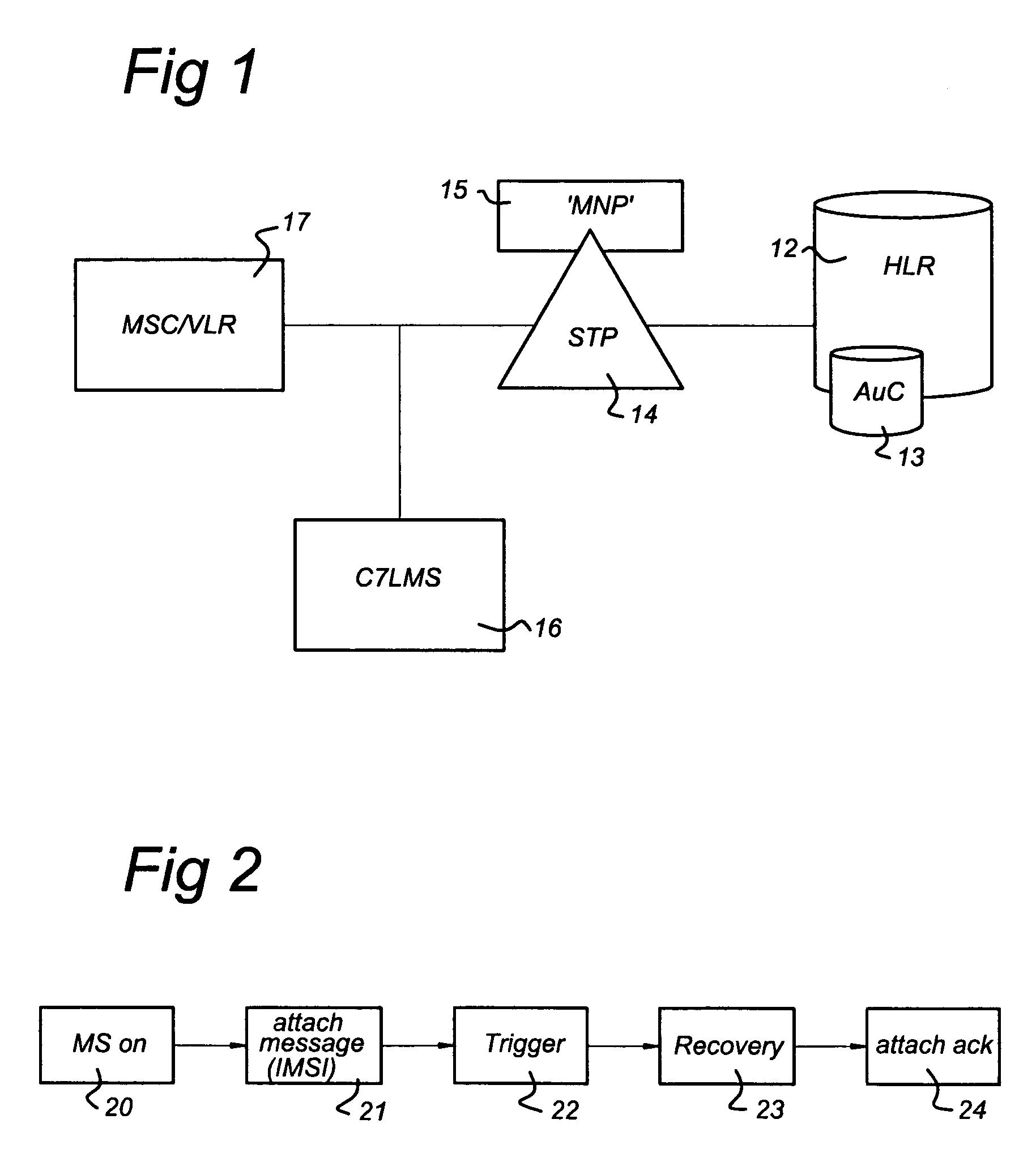
Method and System for Updating Home Location Register in Mobile Network
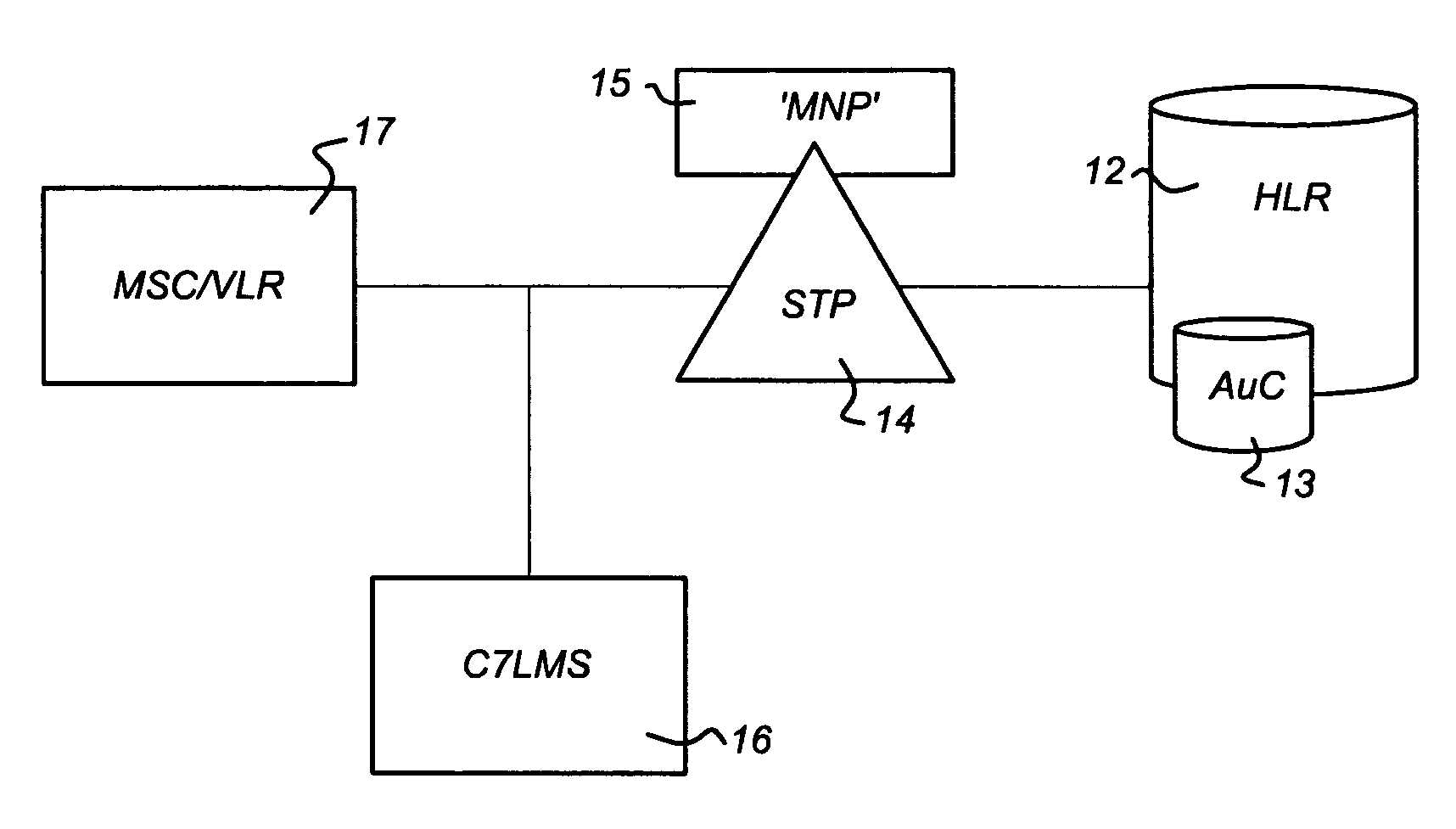
InactiveUS20090264122A1Efficient use of resourcesEasy to useWireless commuication servicesNetwork data managementTelecommunicationsProcessor register
Owner:KONINK KPN NV
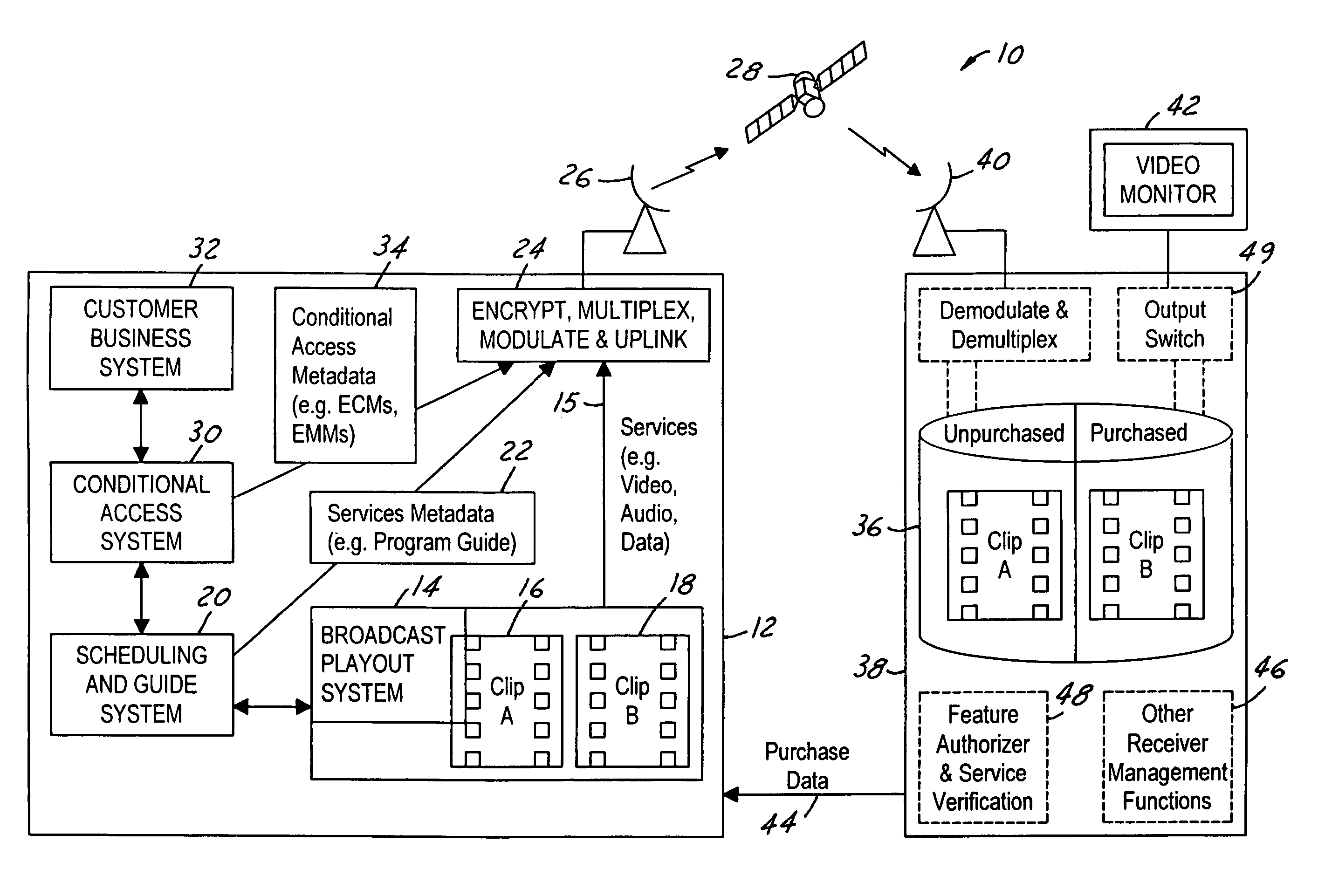
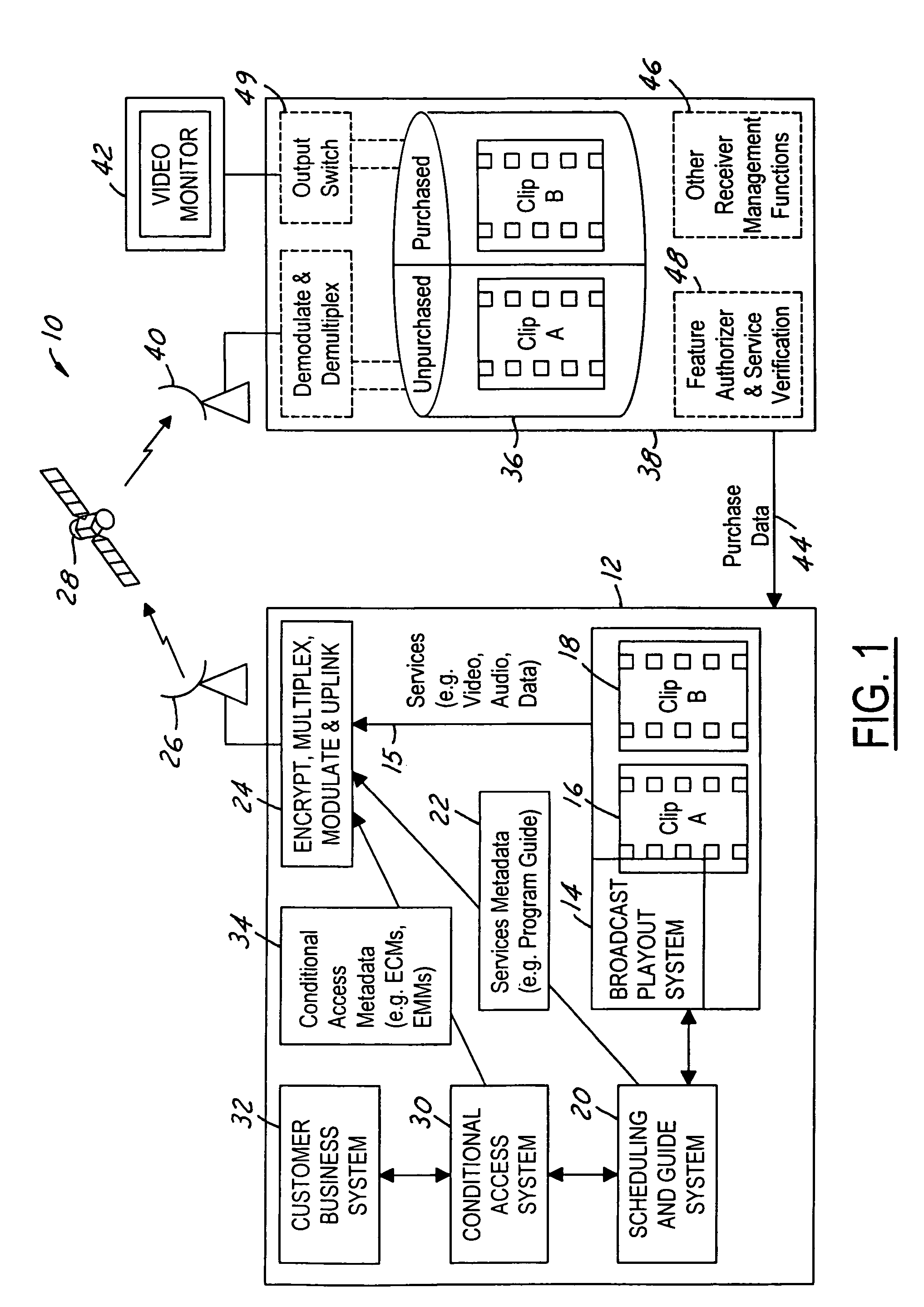
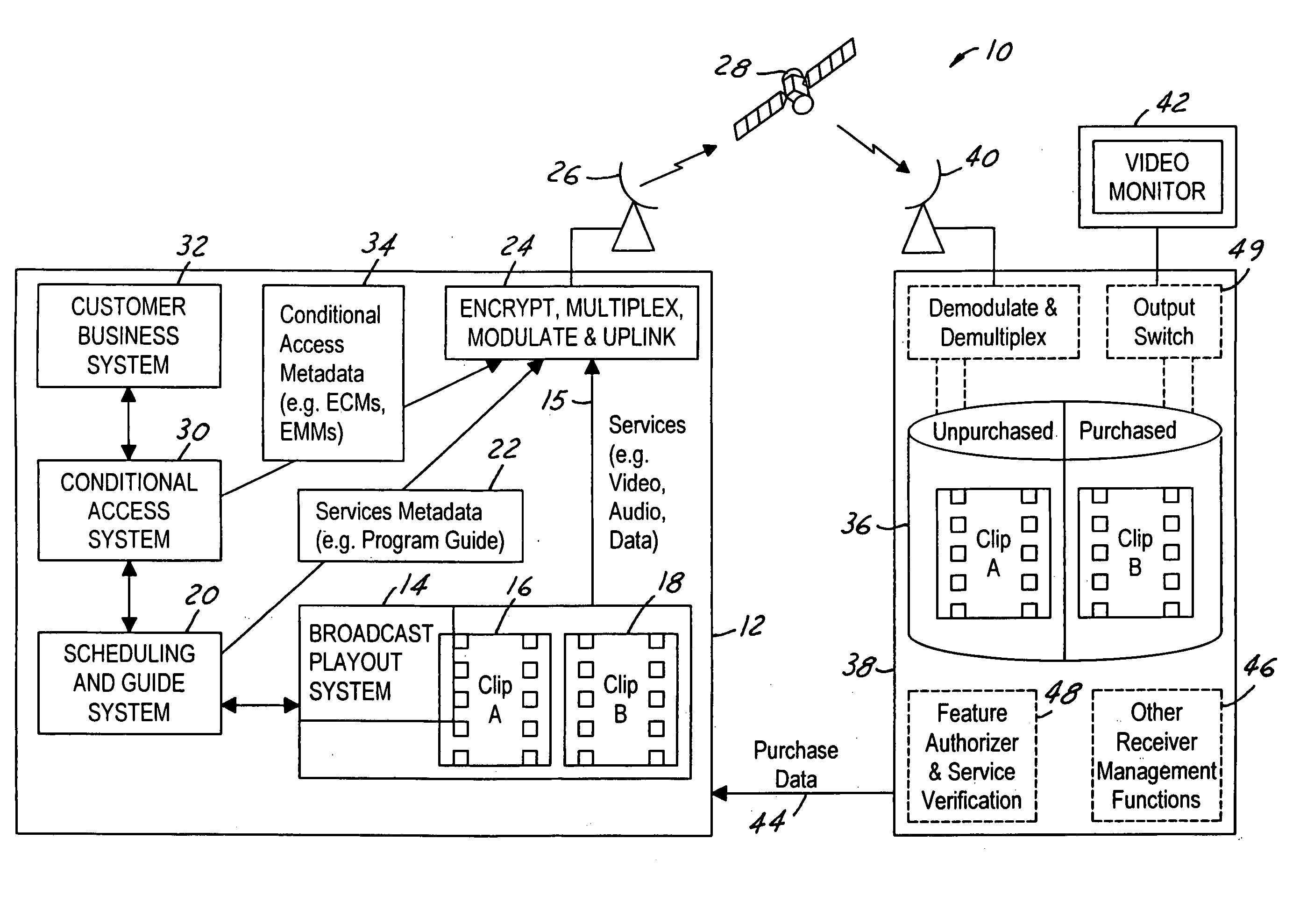
Video on demand in a broadcast network
ActiveUS7801303B2Storage requirements is greatly reducedLowering the risk that the program content may be accessedDigital data processing detailsAnalogue secracy/subscription systemsDigital videoNear video on demand
Owner:DIRECTV LLC
Detection of cardiac arrhythmia using mathematical representation of standard DeltaRR probability density histograms
ActiveUS7146206B2Improve accuracyStorage requirements is greatly reducedElectrocardiographySensorsRR intervalMedicine
Owner:THE ROYAL INSTION FOR THE ADVANCEMENT OF LEARNING MCGILL UNIV A UNIV
Data deduplication
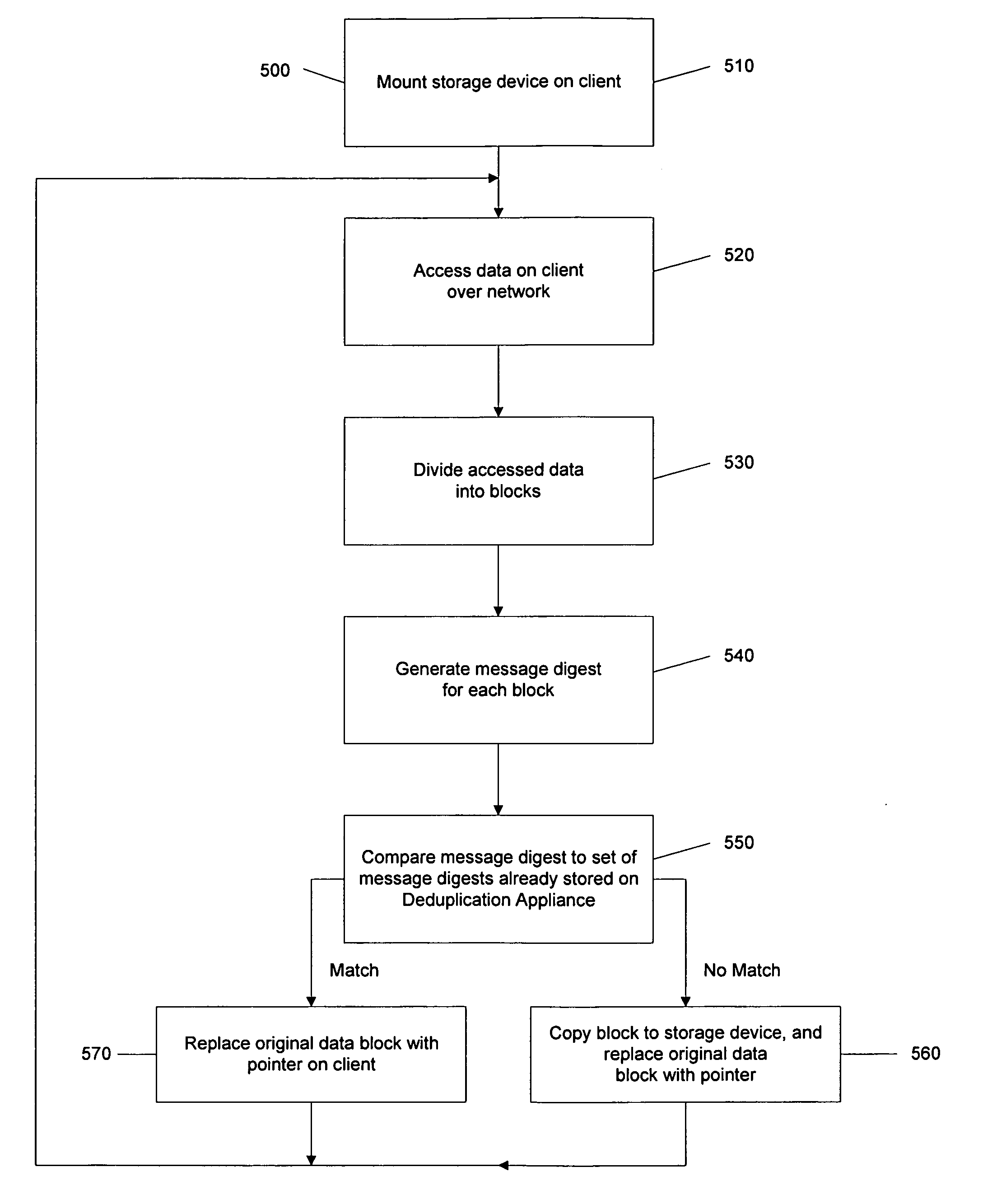
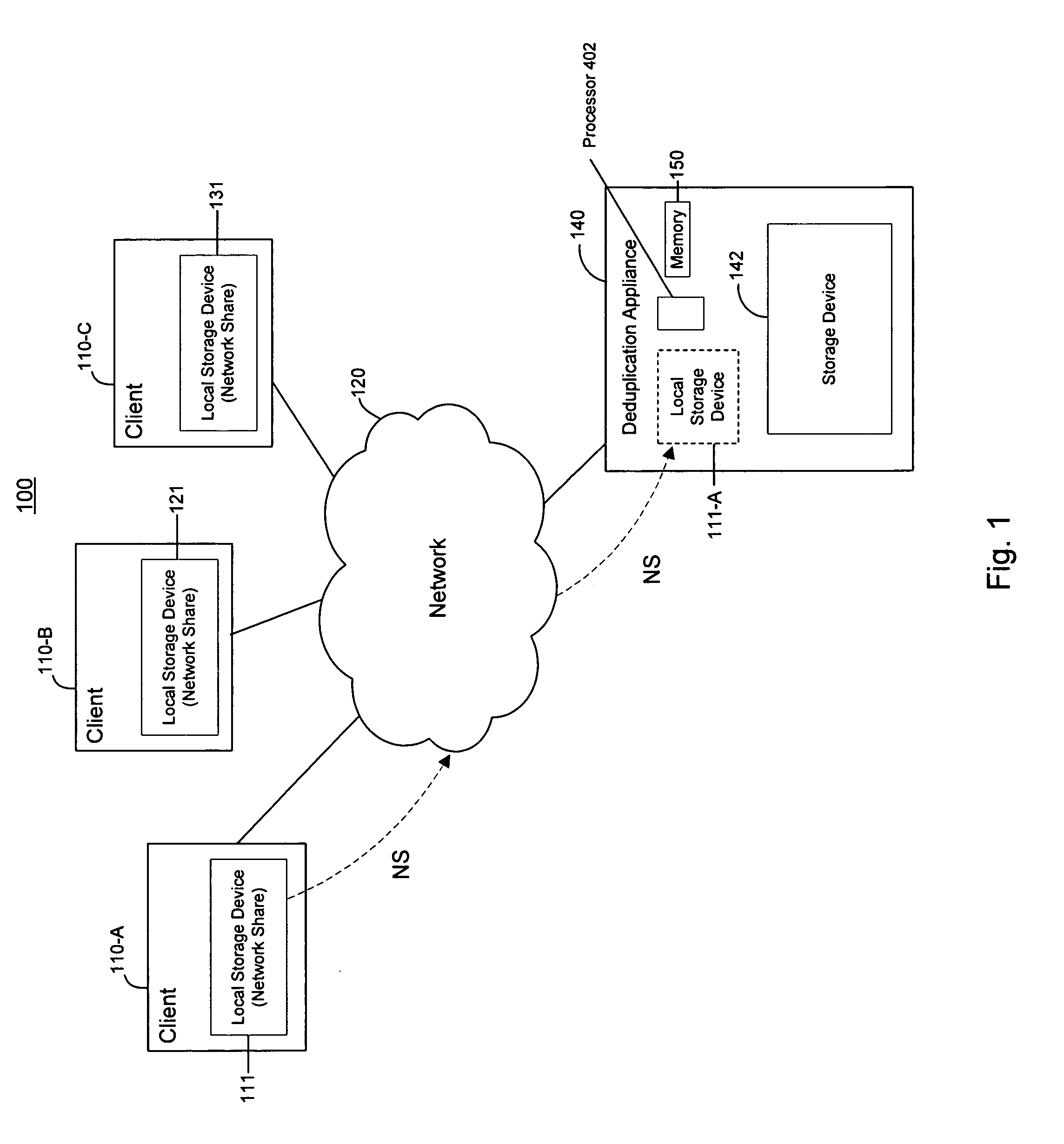
ActiveUS20120089578A1Reduce complexitySave network bandwidthDigital data information retrievalDigital data processing detailsData storingClient machine
A method of deduplicating data is disclosed comprising mounting, by a deduplication appliance, network shared storage of a client machine, via a network, accessing data to be deduplicated on the network shared storage device, deduplicating the data, storing the deduplicated data on a second storage device, and replacing the data in the network shared storage device by at least one indicator of the location of the deduplicated data in the second storage device. A method is also disclosed for copying deduplicated data stored by a deduplication appliance, by a client machine, comprising receiving a request to copy data from a first location to a second location, by the client machine, by providing at least one second indicator to the third location on the deduplication appliance, at the second location, if the source and the destination are on the deduplication appliance. Systems are also disclosed.
Owner:FALCONSTOR
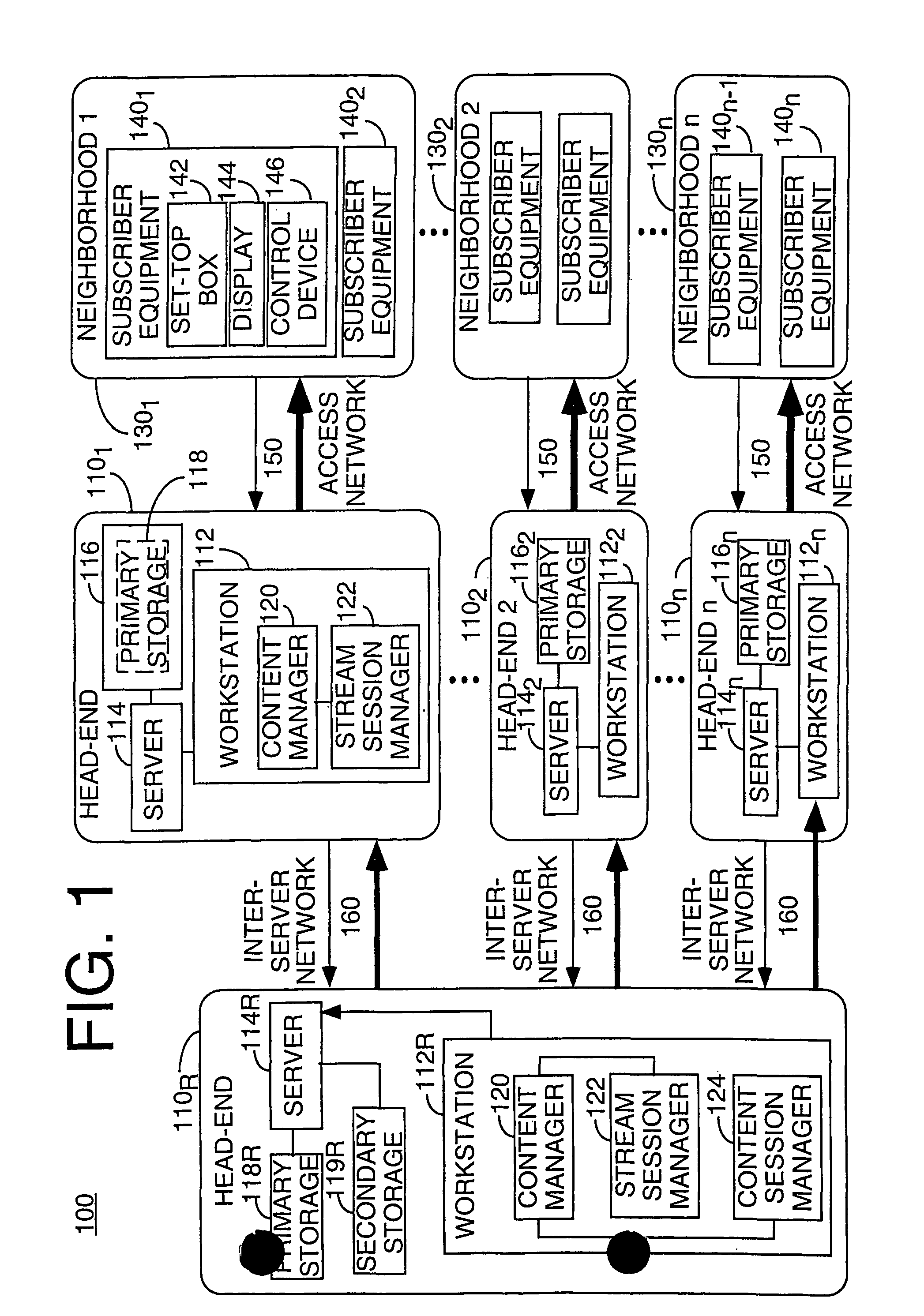
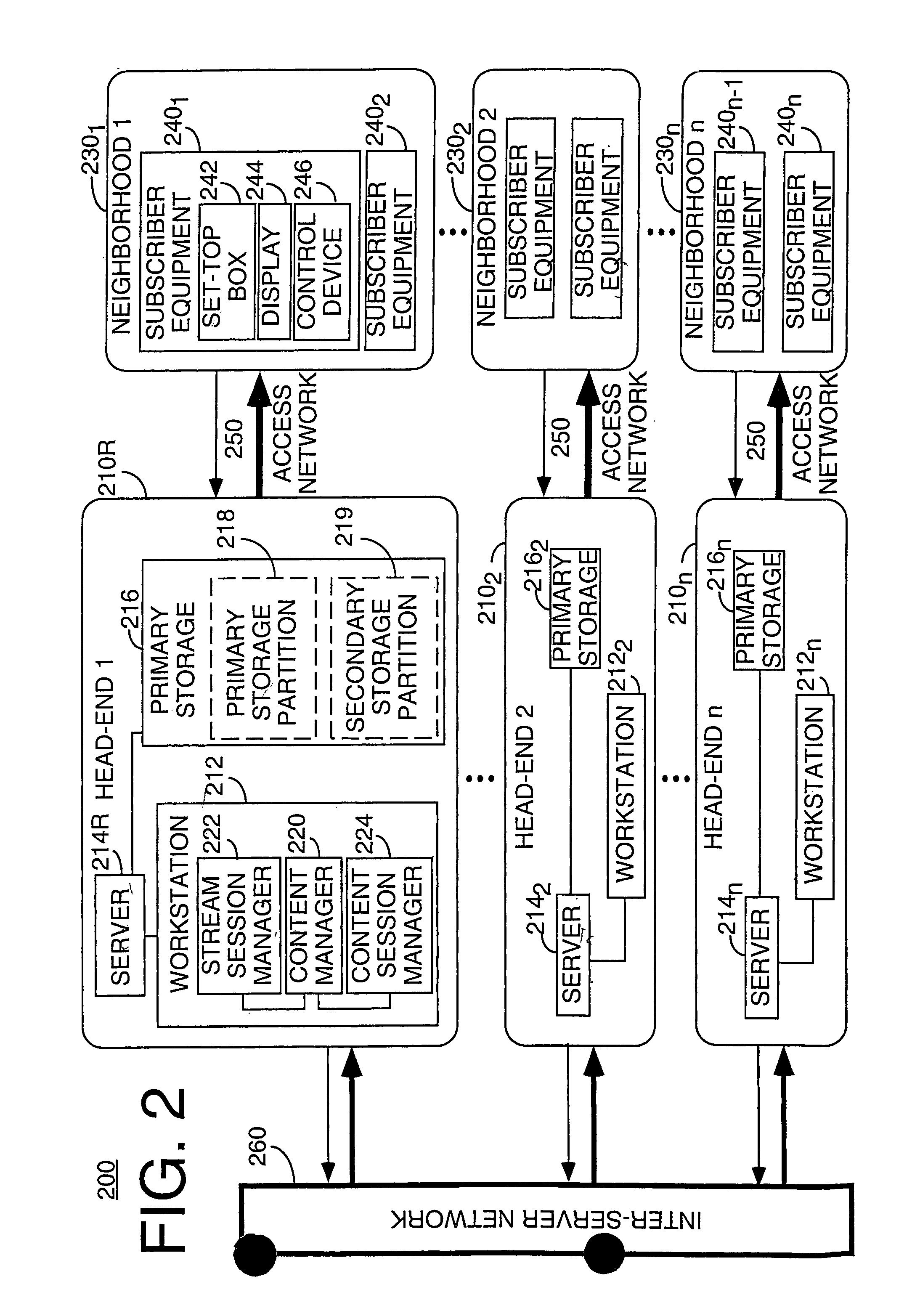
Method and apparatus for hierarchical distribution of video content for an interactive information distribution system
InactiveUS8191097B1Lower latencyHigh bit variable rateAnalogue secracy/subscription systemsMultiple digital computer combinationsUser deviceDistribution system
A method and apparatus for storing and distributing video information in an interactive information distribution system by storing video information on either a centralized or de-centralized secondary storage partition in a network of provider and subscriber equipment, and therein distributing the video information to a subscriber having made a request for such video information.
Owner:COMCAST IP HLDG I
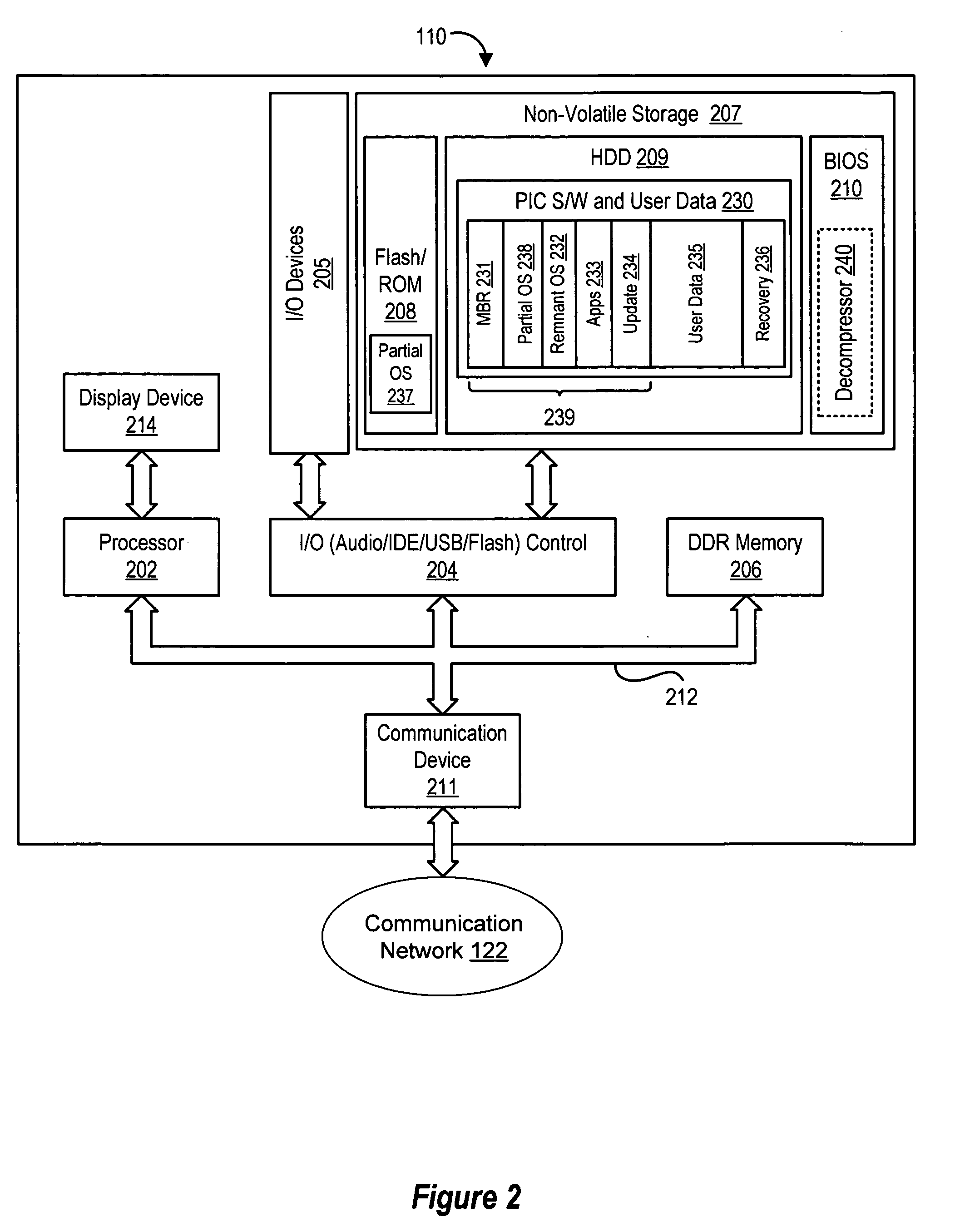
Boot performance optimization for hard drive for personal internet communicator
ActiveUS20070067679A1Efficient loadingReduce part sizeLink editingError detection/correctionInternet communicationOperational system
In a personal Internet communication device, an optimized operating system image (NK.bin) is constructed from the operating system component files required to provide a minimum threshold of operating system functionality. By reducing the size of the operating system image, the time required to load the operating system is reduced.
Owner:GLOBALFOUNDRIES US INC
System for a distributed column chunk data store
ActiveUS20070061542A1Reduce storage requirementsReduce transfer timeError detection/correctionMemory systemsServer allocationDatabase engine
An improved system and method for a distributed column chunk data store is provided. A distributed column chunk data store may be provided by multiple storage servers operably coupled to a network. A storage server may include a database engine for partitioning a data table into the column chunks for distributing across multiple storage servers, a storage shared memory for storing the column chunks during processing of semantic operations performed on the column chunks, and a storage services manager for striping column chunks of a partitioned data table across multiple storage servers. Any data table may be flexibly partitioned into column chunks using one or more columns as a key with various partitioning methods. There may also be a storage policy for specifying how to partition a data table for distributing column chunks across multiple servers and for specifying a level of redundancy for recovery from failure of storage servers.
Owner:GOOGLE LLC
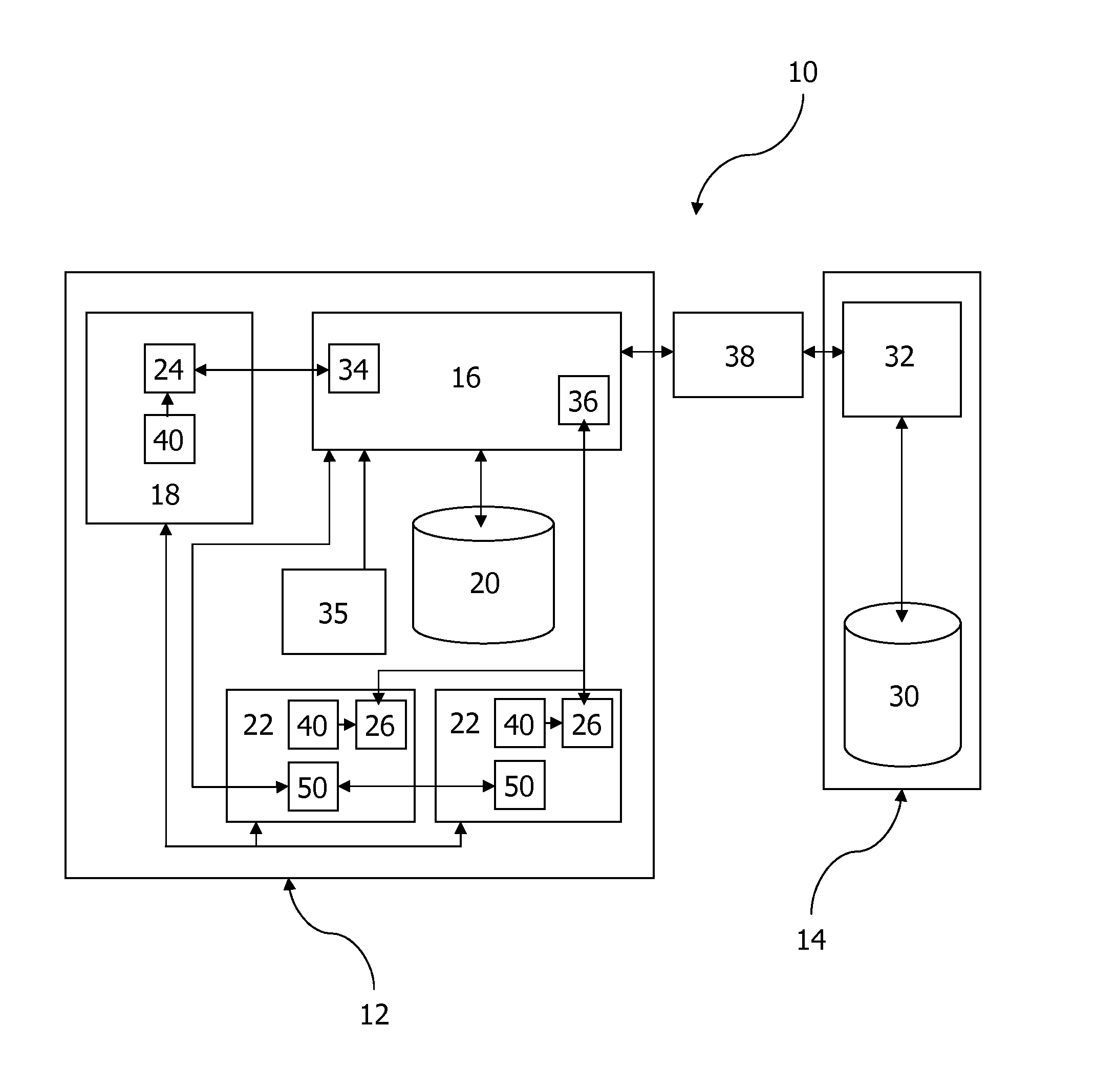
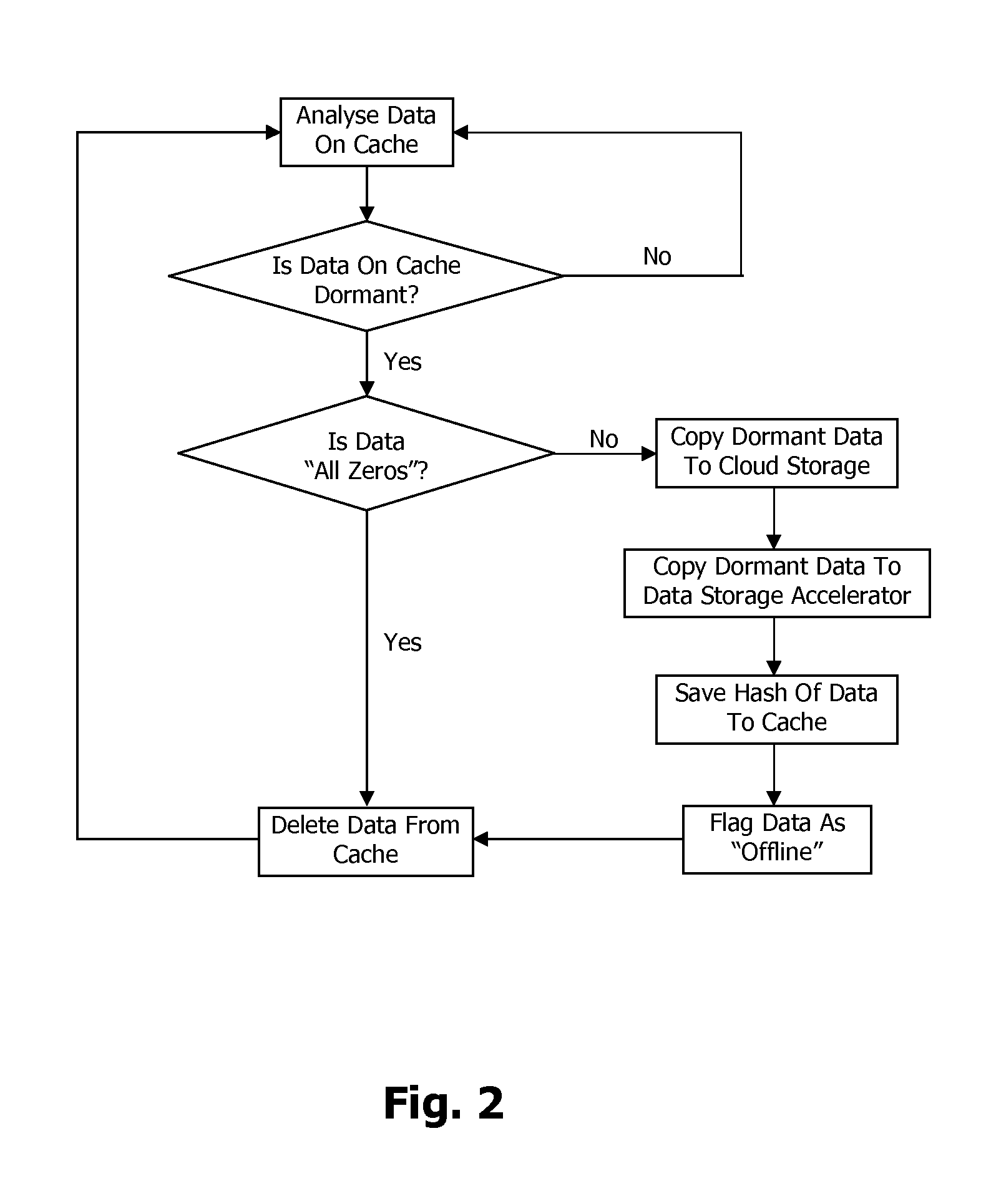
Data Storage System
InactiveUS20120042130A1Improve performanceStorage requirements is greatly reducedMemory architecture accessing/allocationMemory adressing/allocation/relocationThe InternetData management
A data storage system includes a host computing system having a data storage server and a local cache. The host computing system has access via an internet connection to a data account with a cloud data storage provider. A data management protocol is stored on, and adapted to be employed by, the host computing system. The protocol directs the data storage server to store current data in the local cache and dormant data in the data account of the cloud data storage provider.
Owner:PEAPELL AARON ANTONY
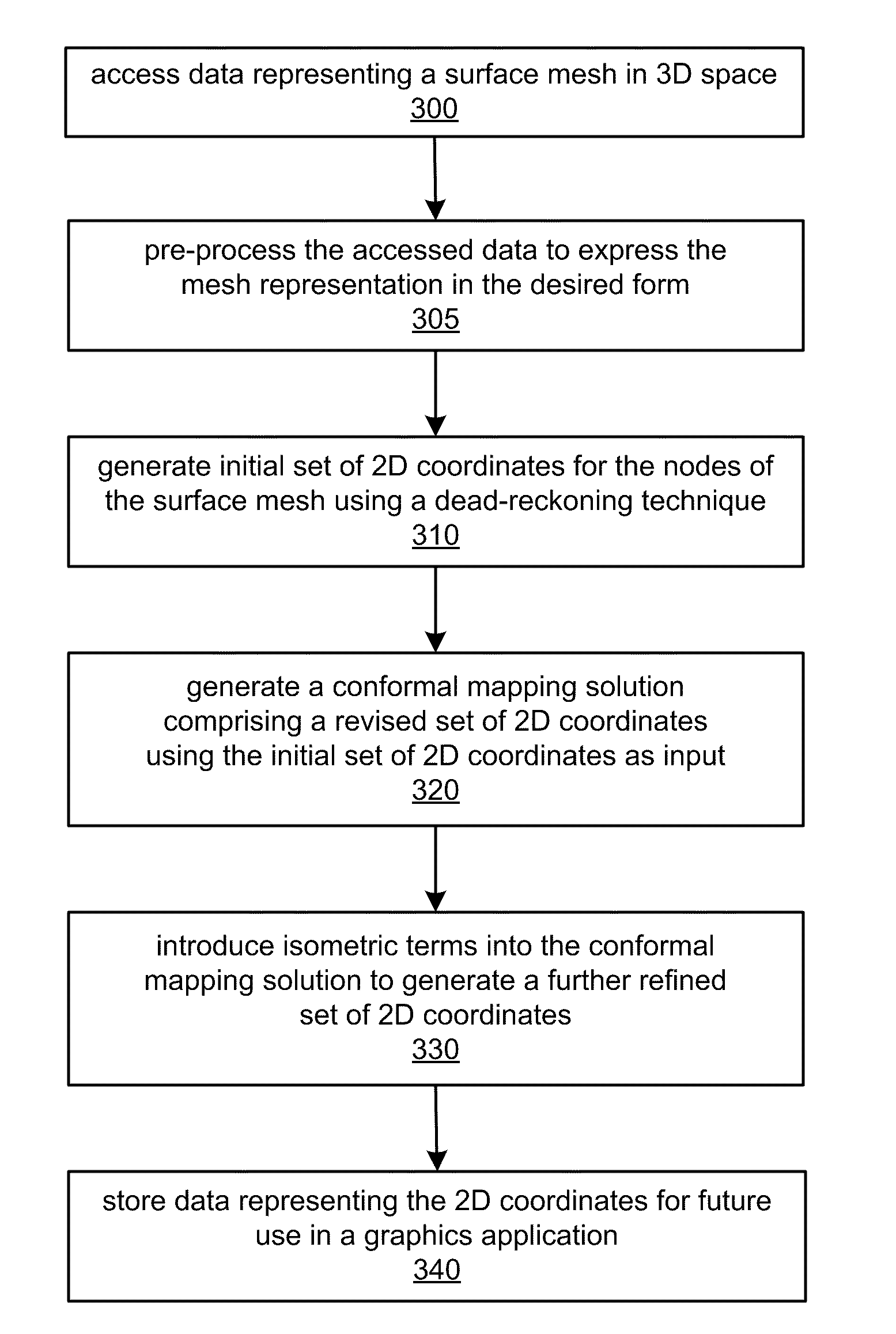
System and Method for Generating 2D Texture Coordinates for 3D Meshed Surfaces
ActiveUS20130328870A1Minimum edge-length distortionImprove accuracyCathode-ray tube indicators3D-image renderingGraphicsShortest distance
Systems and methods for generating 2D texture coordinates for 3D surfaces meshes may assign initial 2D texture coordinates to each node within a mesh using dead reckoning, compute a conformal mapping solution to revise the texture coordinates dependent on the initial mapping, and store the texture coordinates for subsequent use in a graphics application (e.g., applying a texture and / or re-meshing a surface). The methods may include designating one node as the origin, determining the shortest distance from each other node to the origin, and computing texture coordinates for each other node in order of increasing distance to the origin. The dead reckoning operation may compute texture coordinates of each node dependent on the distance and direction of a vector formed between the node and a neighbor node to which texture coordinates have already been assigned. Isometric terms reflecting stretching or compression may be introduced following convergence by the conformal mapping.
Owner:ADOBE INC
Method and Apparatus of Constrained Intra Block Copy for Coding Video
InactiveUS20160241875A1Reduce storage requirementsStorage requirements is greatly reducedDigital video signal modificationCoding blockAlgorithm
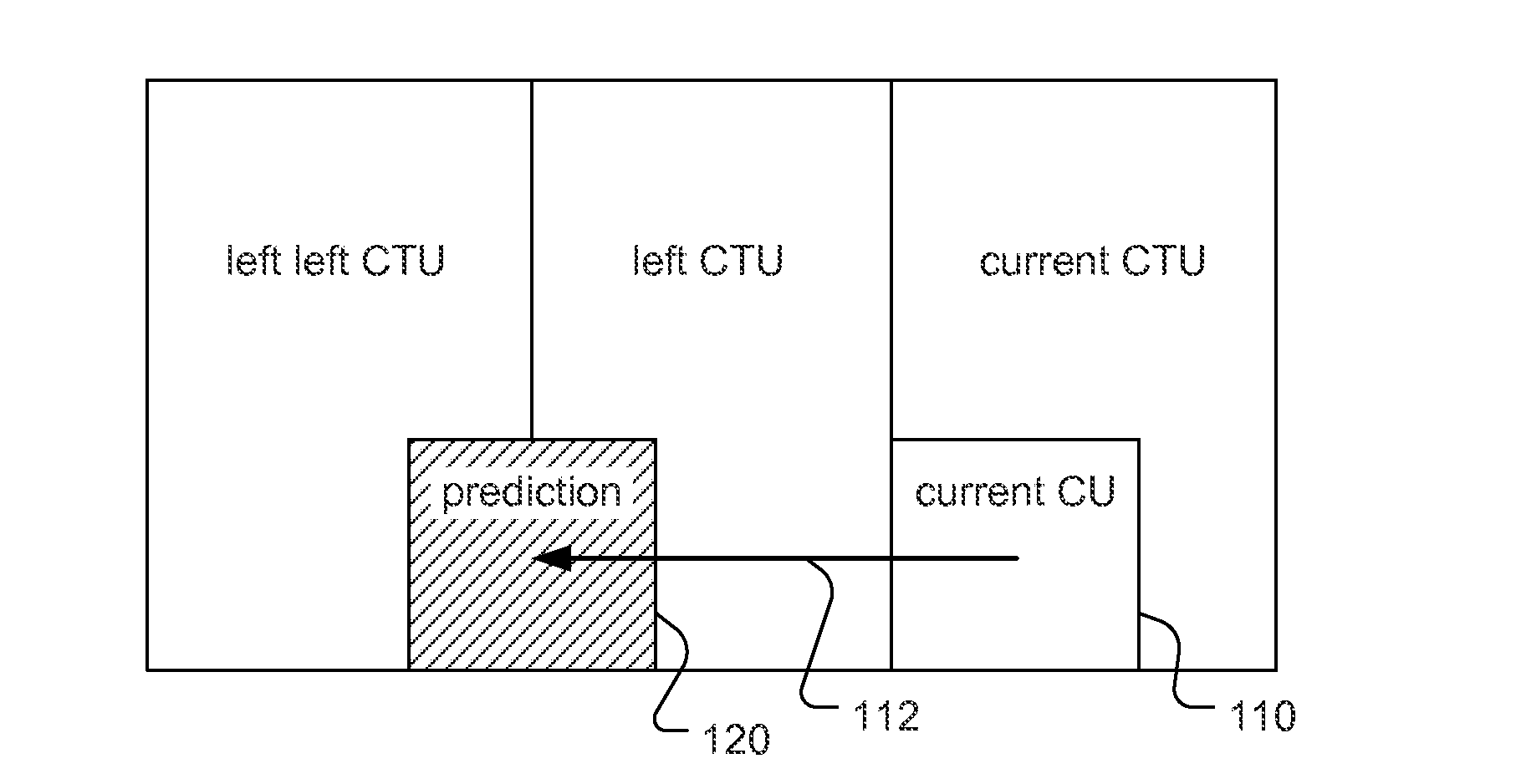
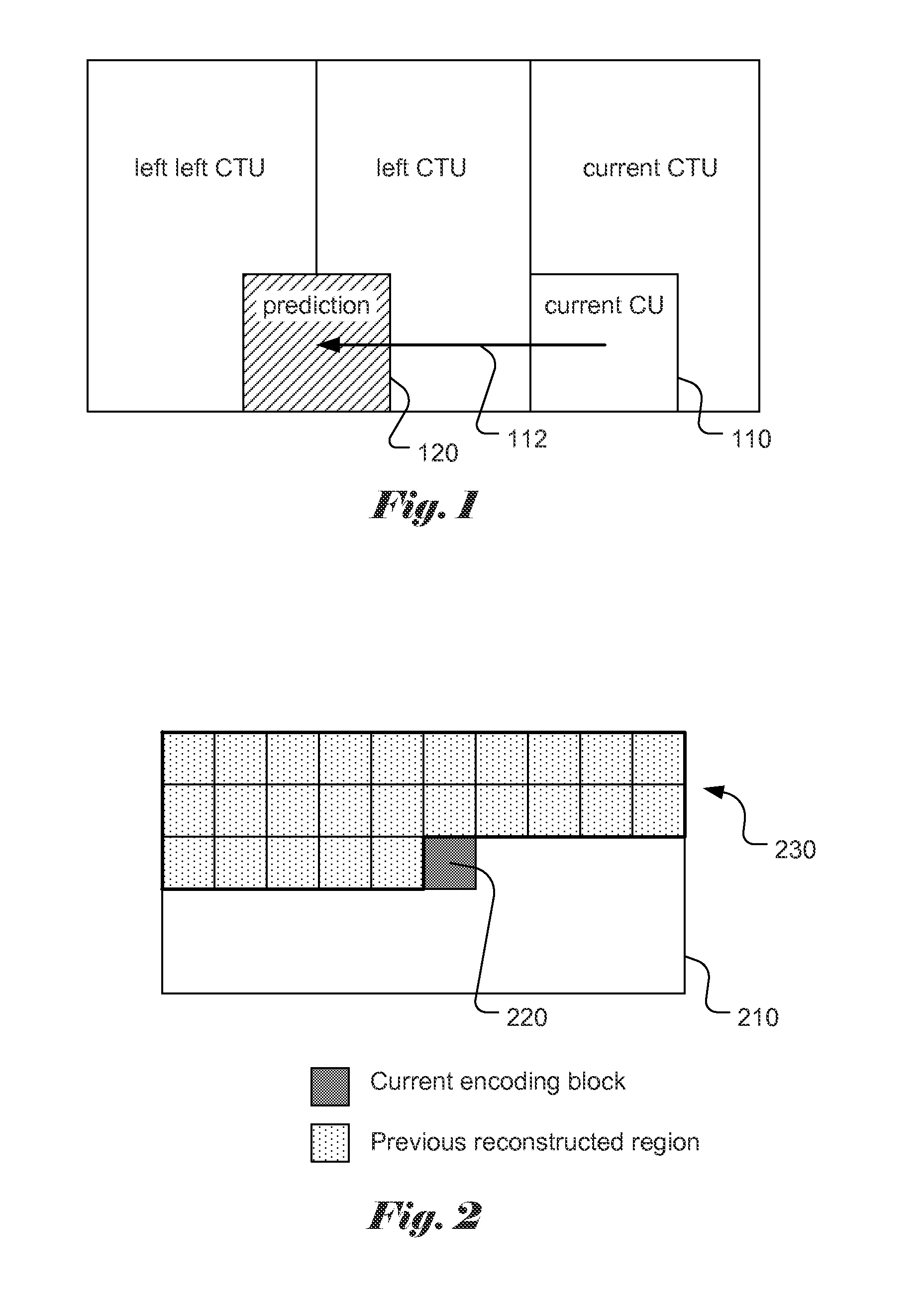
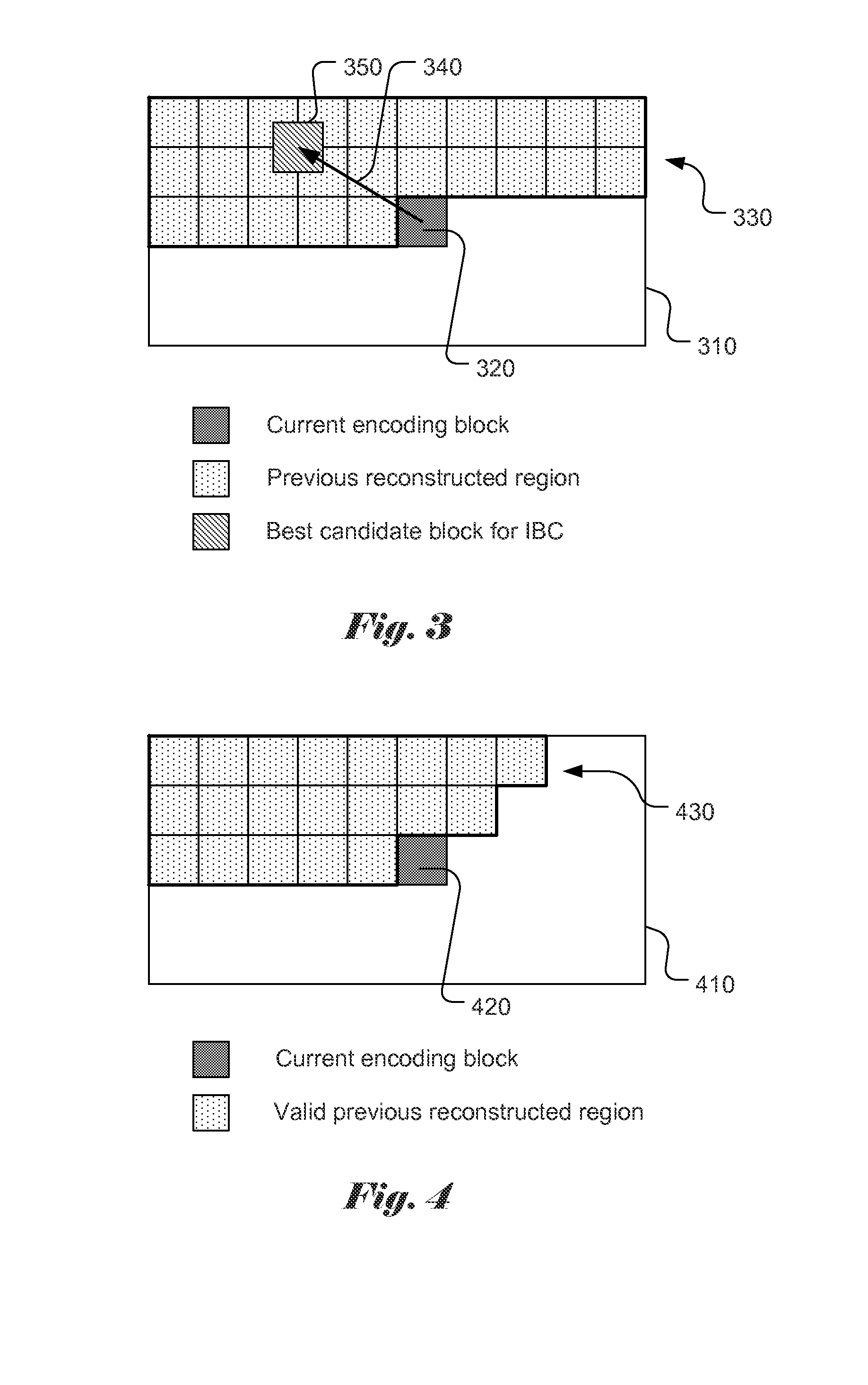
A method of IntraBC (Intra-block copy) coding for a coding region is disclosed. Embodiments of the present invention derive an IntraBC (Intra picture block copy) predictor from a constrained previous reconstructed region so as to reduce storage requirement for the previous reconstructed data. In one embodiment, a maximum absolute vertical BV (block vector) value, MaxV_BV is determined, where MaxV_BV is smaller than a full vertical search range for the coding region. A constrained previous reconstructed region corresponding to previous reconstructed samples processed before the current block is then determined, where the constrained previous reconstructed region includes at least MaxV_MV reconstructed samples in vertical direction above the current block and excludes at least one row of reconstructed samples for the current block with a vertical distance larger than MaxV_MV. Each coding block may correspond to a prediction unit (PU) or a coding unit (CU).
Owner:XUESHAN TECH INC
System and method for reducing storage requirements for content adaptive binary arithmetic coding
ActiveUS7595743B1Data storage requirement is reducedReduce storage requirementsCode conversionDigital video signal modificationComputer hardwareData stream
A system for reducing storage requirements for content-adaptive binary arithmetic coding (CABAC) is provided. The system includes a transcode engine performing CABAC on a video data stream. The transcode engine receives save data, stops CABAC, and converts the video data stream into sub-network abstraction layer (NAL) unit state data. An entropy state data storage system receiving the sub-NAL unit state data and stores the sub-NAL unit state data. The transcode engine subsequently receives restore data, extracts the sub-NAL unit state data from the entropy state data storage system, and re-starts CABAC on the video stream data.
Owner:AVAGO TECH INT SALES PTE LTD
Security provision for a subject image displayed in a non-secure domain
ActiveUS20120102557A1Storage requirements is greatly reducedImprove securityFinanceDigital data processing detailsUser inputData treatment
A data processing device is provided with a processor core 8 that can operate in either a secure domain or a non-secure domain. Data stored within a secure region 34 of a memory 10 can only be accessed when the processor core 8 is executing in the secure domain. A frame buffer 36 for storing a display image 20 to be displayed is stored within a non-secure region of memory which can be accessed by the processor core 8 irrespective of whether it is in the secure domain or the non-secure domain as well as a display controller 12. When a subject image 22 is written to the frame buffer 36, validation data for the subject image 22 is stored within the secure region 34. When a user input is received the displayed data stored at a validated display area to which the subject image was written is read back and used to generate check data with is compared with the validation data before the user input is authenticated.
Owner:ARM LTD
Video on demand in a broadcast network
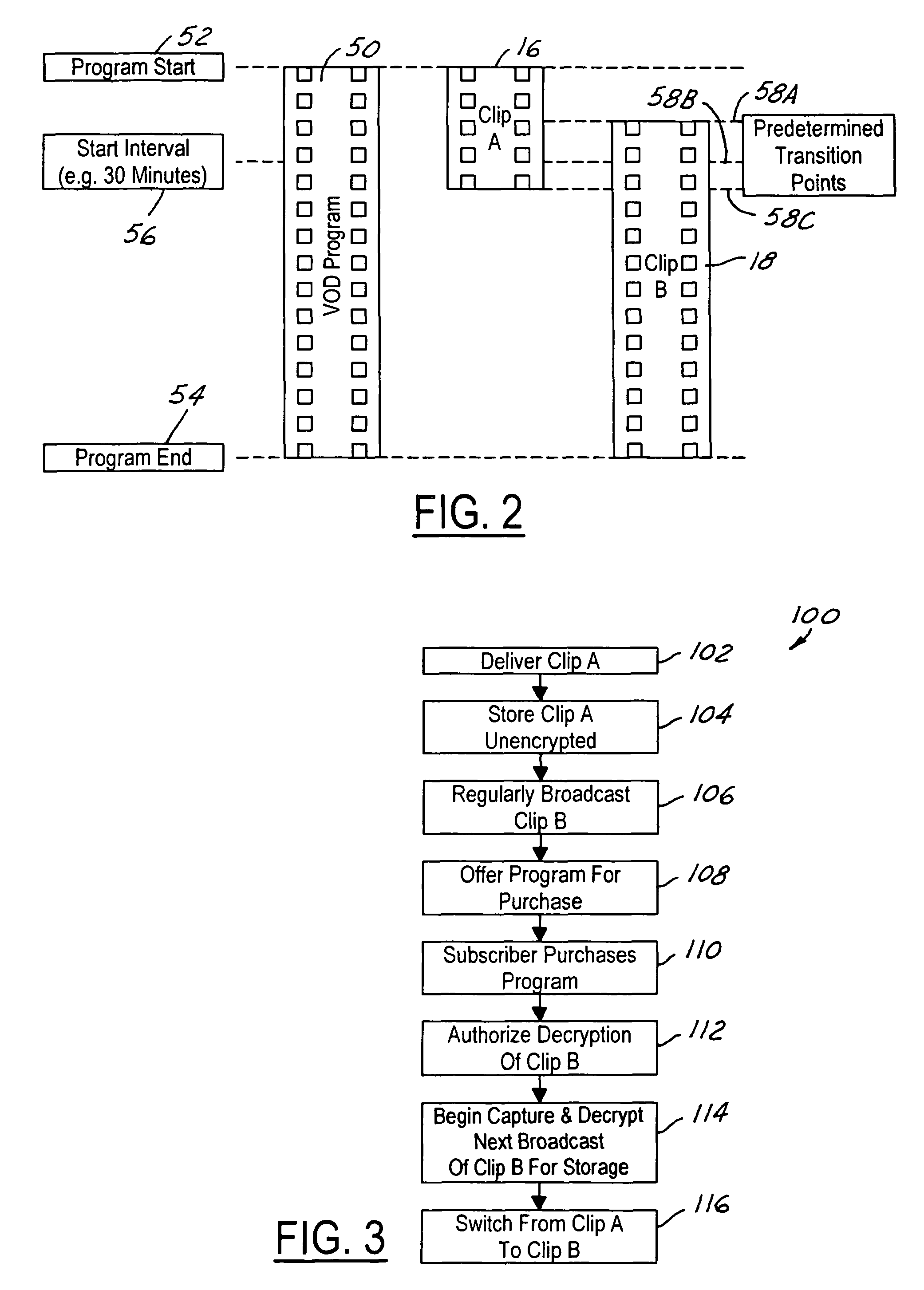
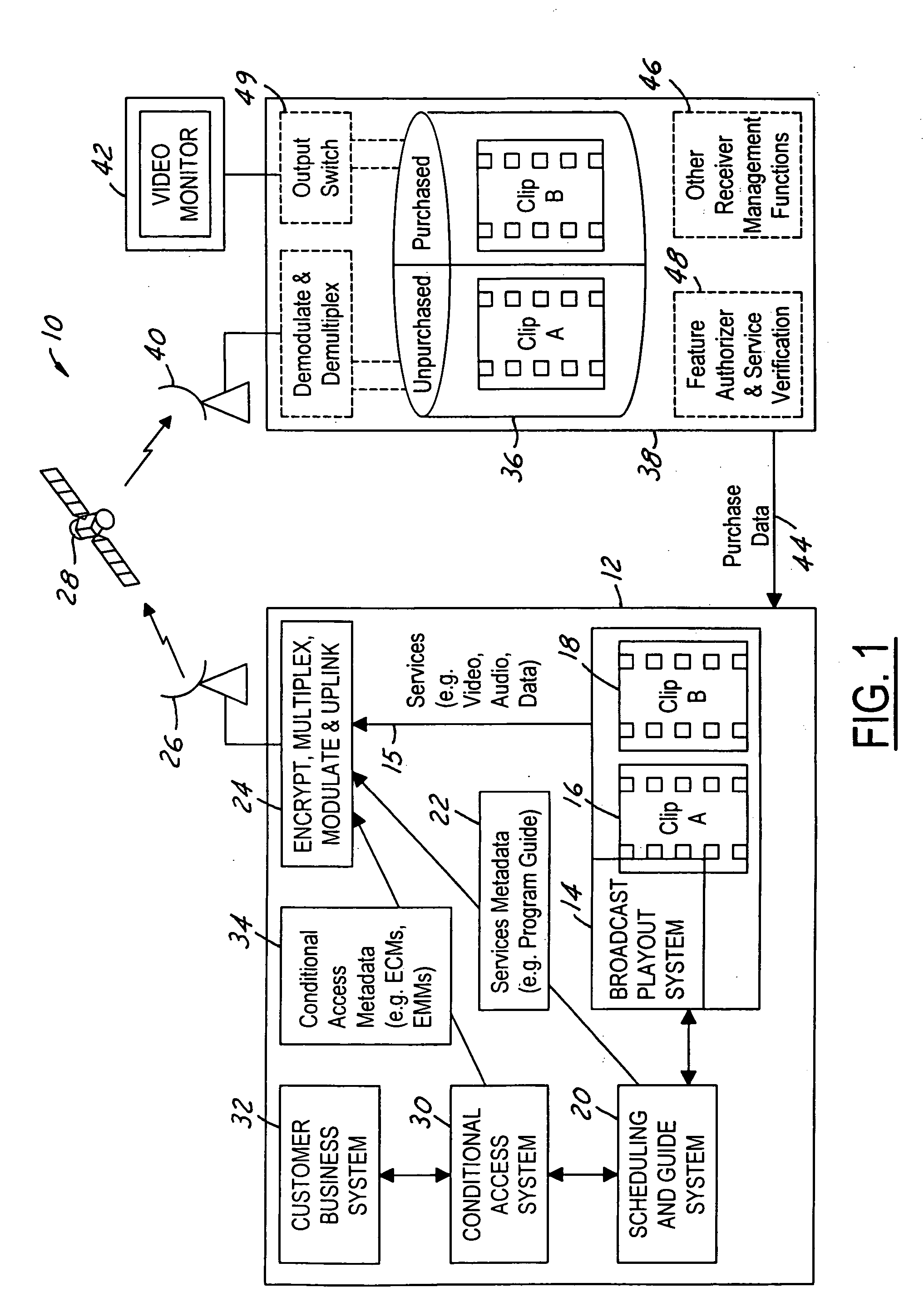
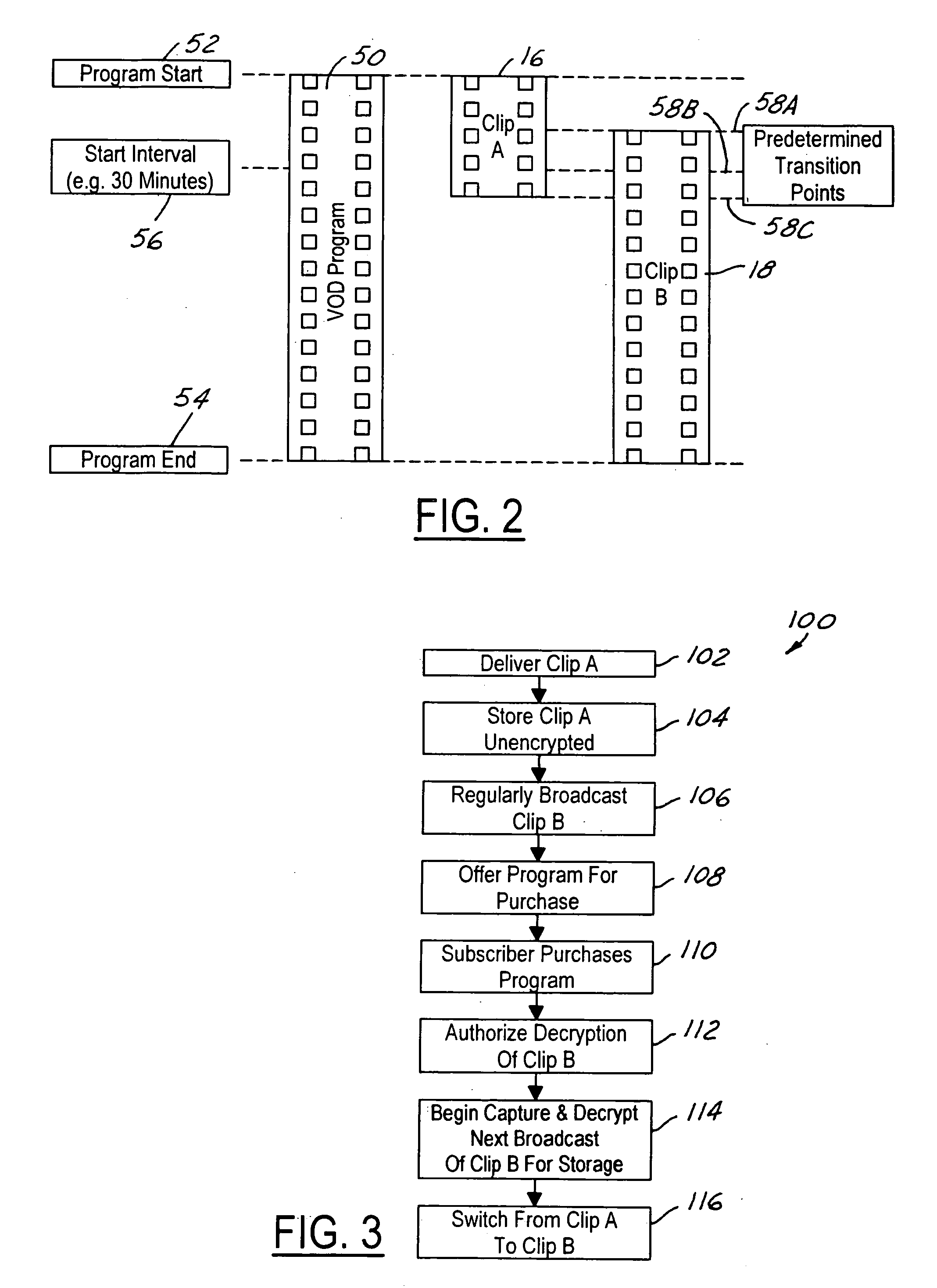
ActiveUS20050190947A1Lower requirementStorage requirements is greatly reducedDigital data processing detailsAnalogue secracy/subscription systemsNear video on demandStart time
The present invention is a video on demand service enabled from a near video on demand service. A desired program is split into portions, or clips. The first clip is delivered a priori to the customer's DVR using a hidden channel and it is made available for purchase on demand. The remaining portion is broadcast regularly using the start time of the NVOD service, for as long as the program is available for VOD purchase. Upon purchase, the remaining portion is authorized for capture by the DVR. The clips are spliced together upon playback to form a complete program.
Owner:DIRECTV LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com