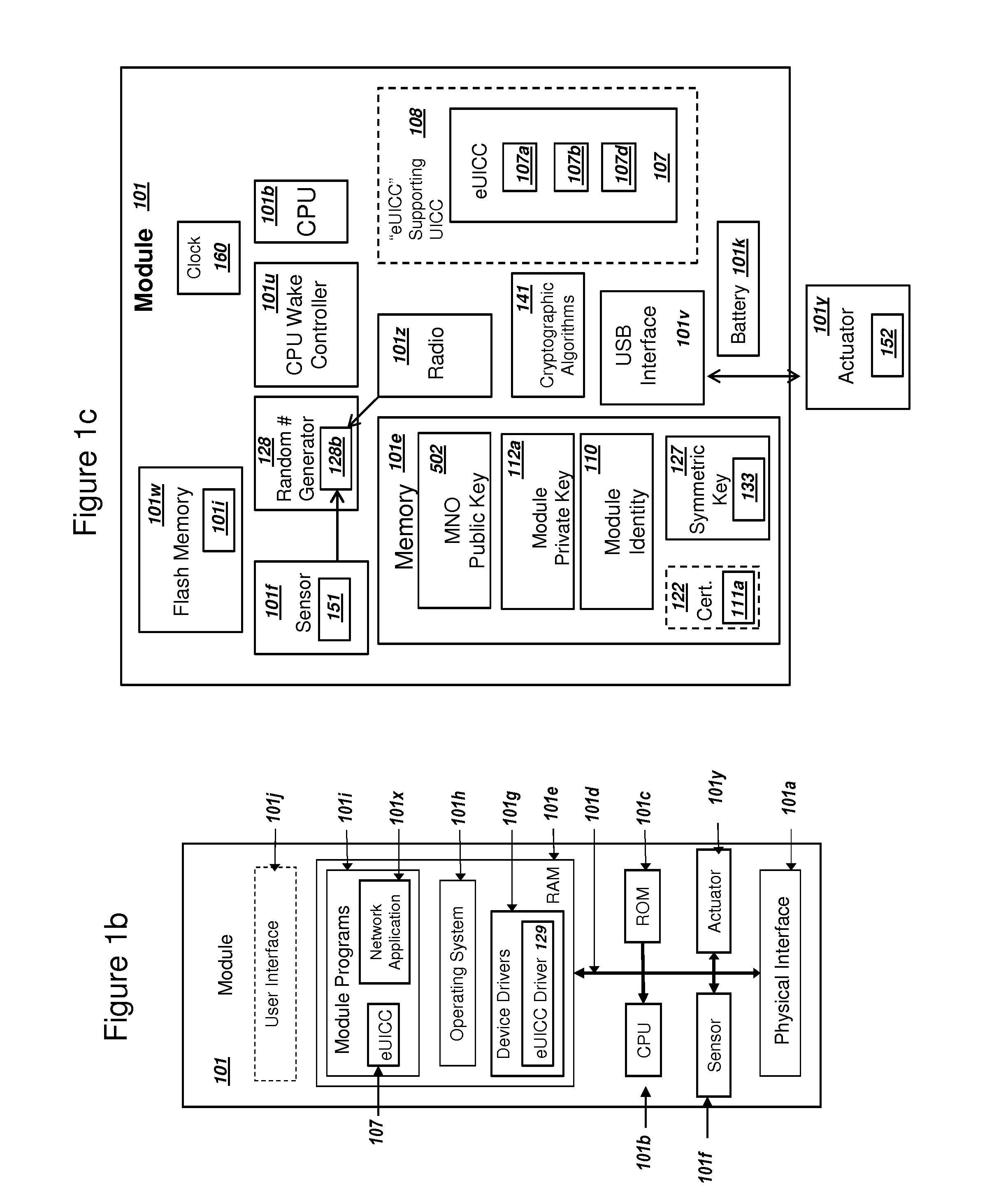
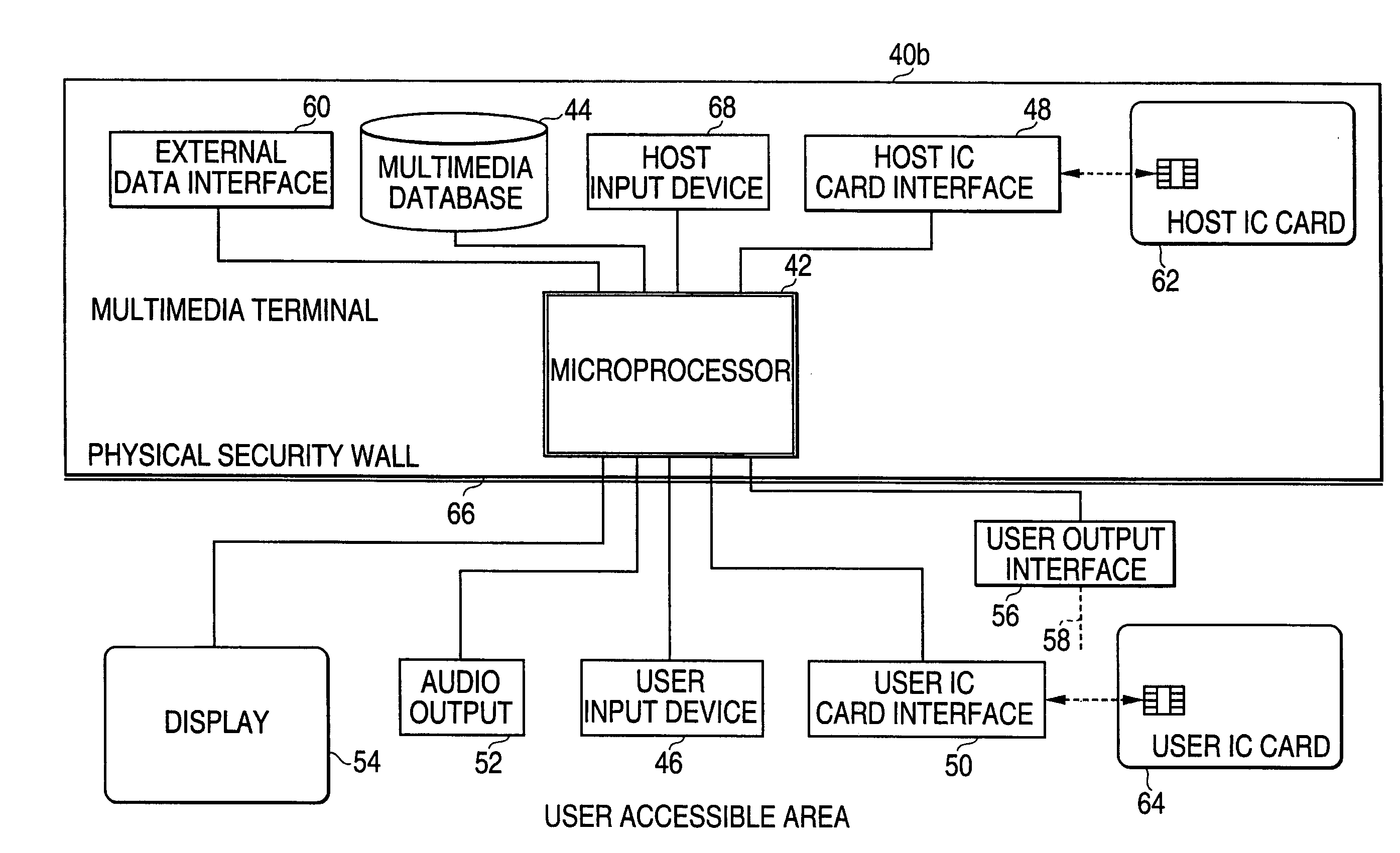
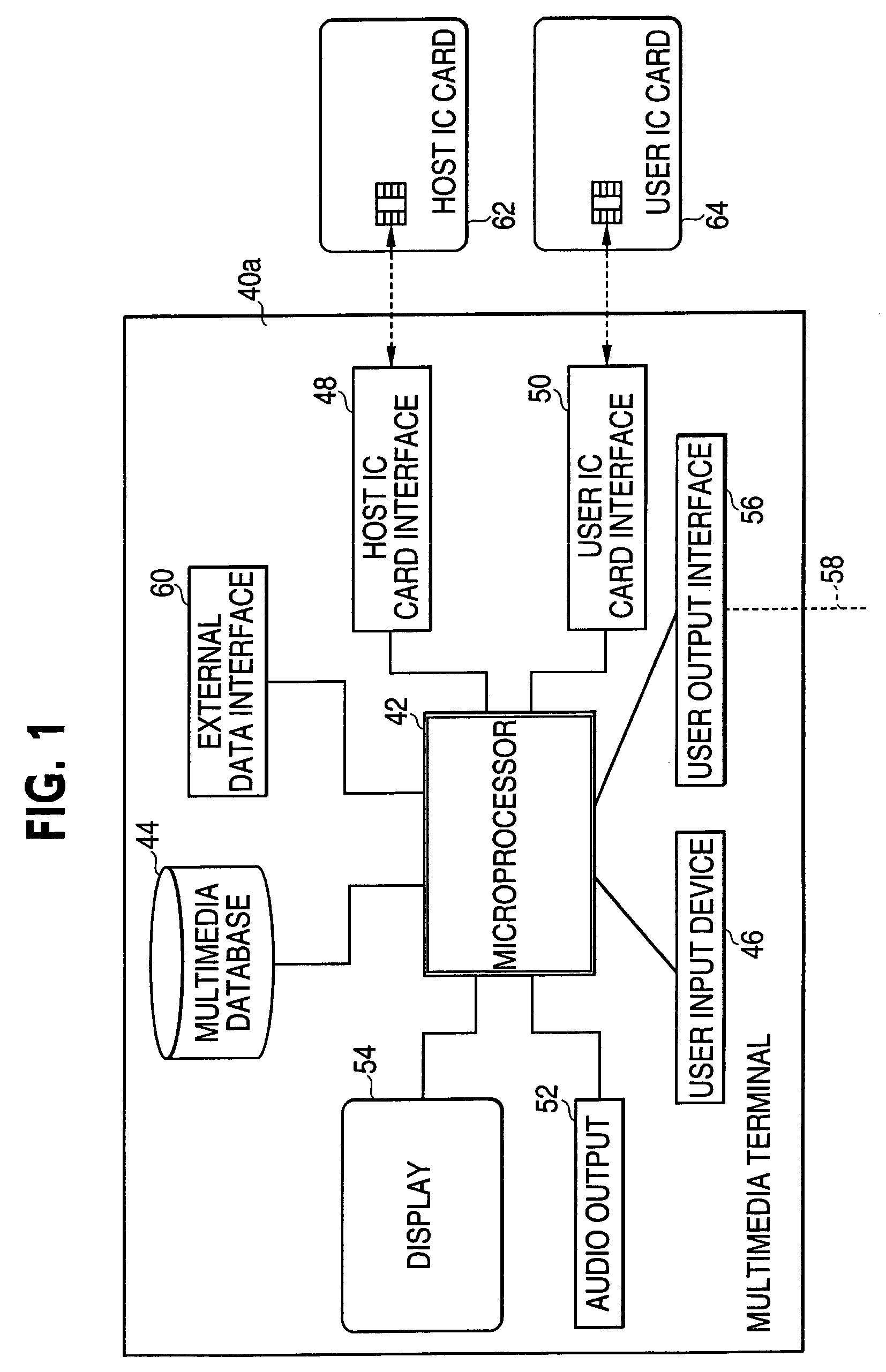
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
560 results about "Integrated circuit card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
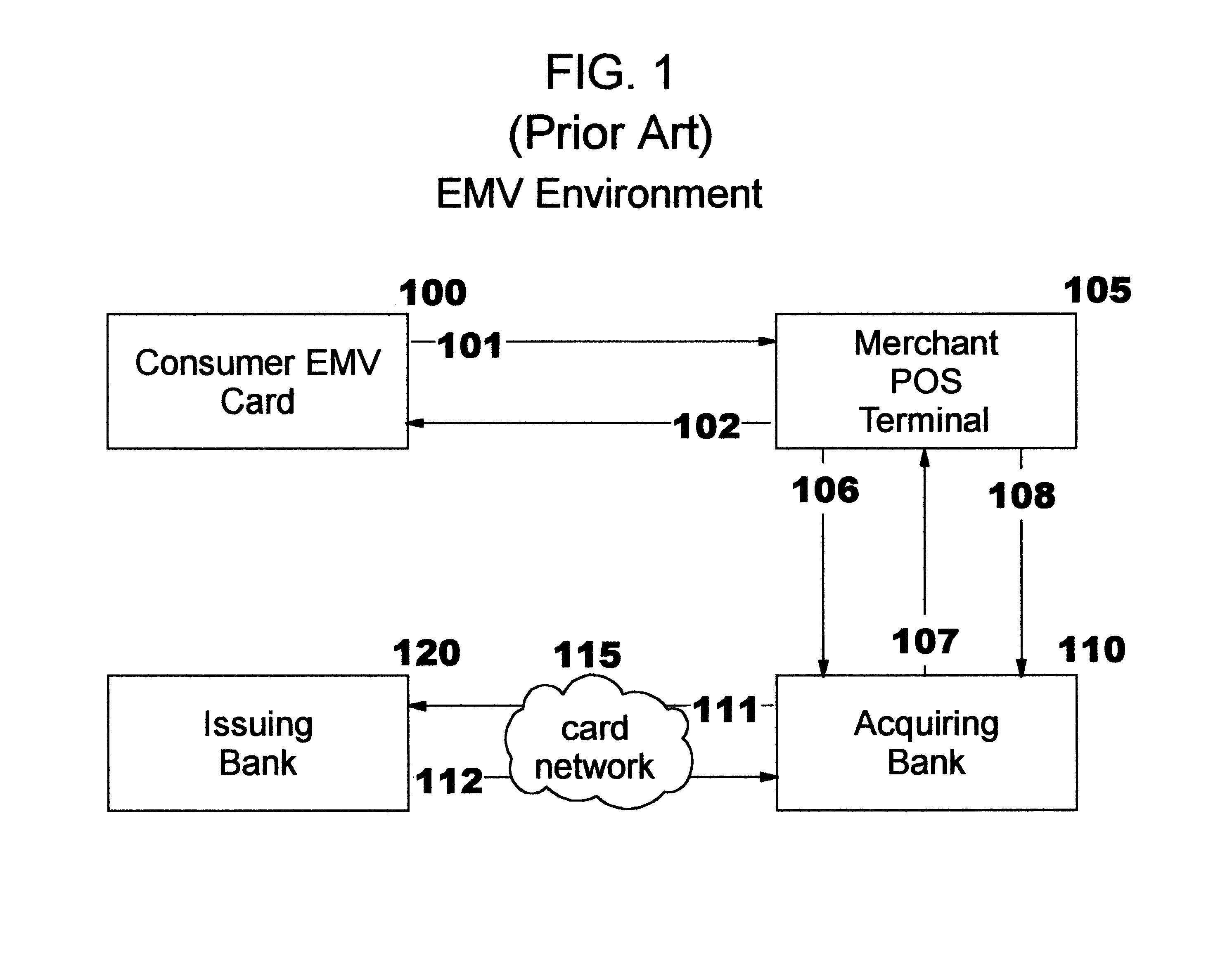
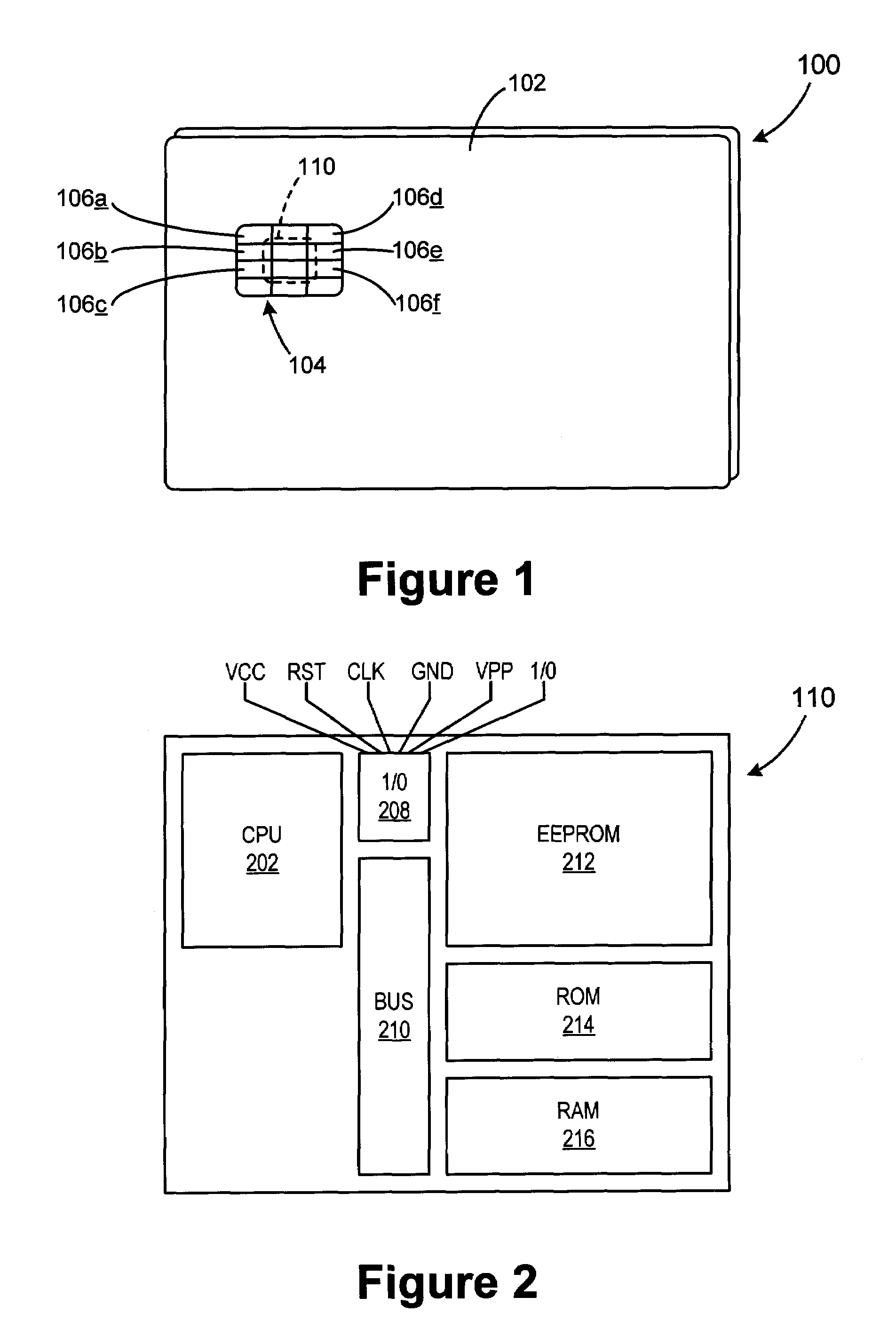
An integrated circuit card is a type of payment or identification card that has an embedded circuit, such as a computer chip. Integrated circuit cards are made of plastic or a similar material and are most often associated with specific credit cards known as EMV cards.
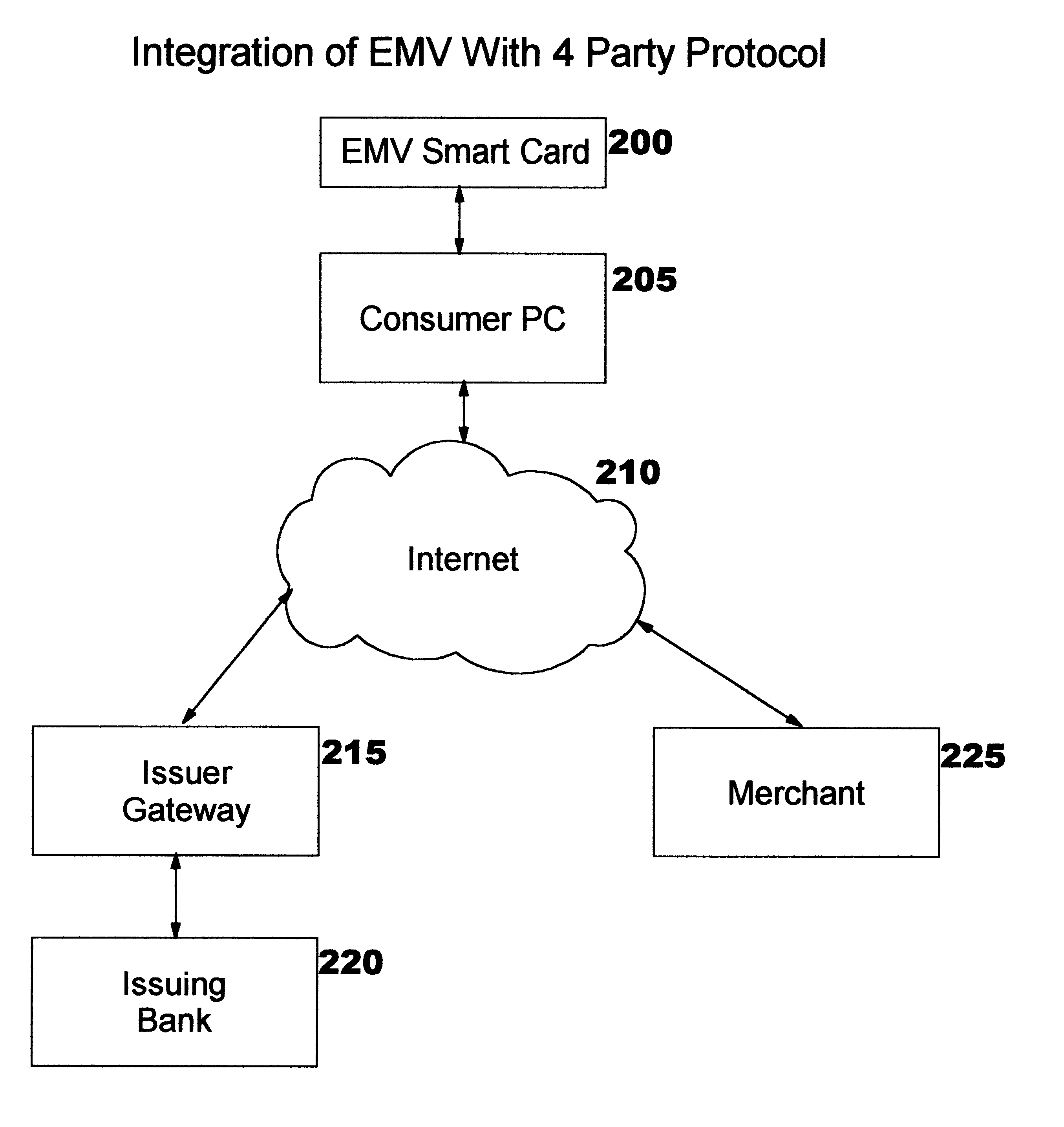
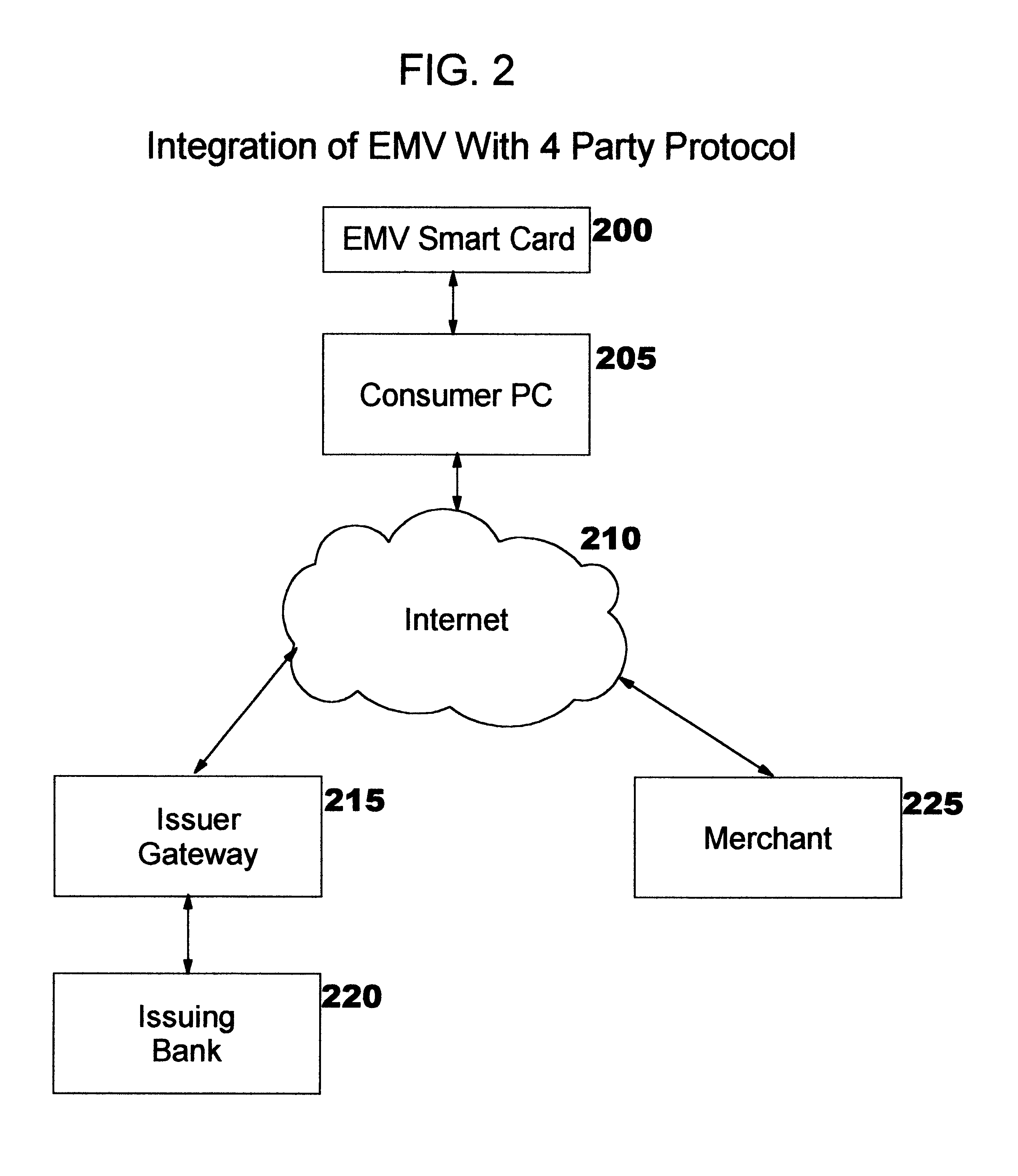
Enabling use of smart cards by consumer devices for internet commerce
A method, system, and computer readable code for enabling use of smart cards by consumer devices for Internet commerce. This is achieved by integrating an existing “Integrated Circuit Card Specification for Application Payment Systems” standard (commonly known as the “EMV” standard) with an augmented version of the Four-Party Credit / Debit Payment Protocol which was disclosed in U.S. Pat. No. 6,327,578. The result of the integration allows a consumer to use a smart card from a personal computer system for credit or debit transactions, while preserving the level of security and other features required by the credit card associations and banks. No modifications are required to the existing EMV standard or existing EMV smart cards.
Owner:IBM CORP
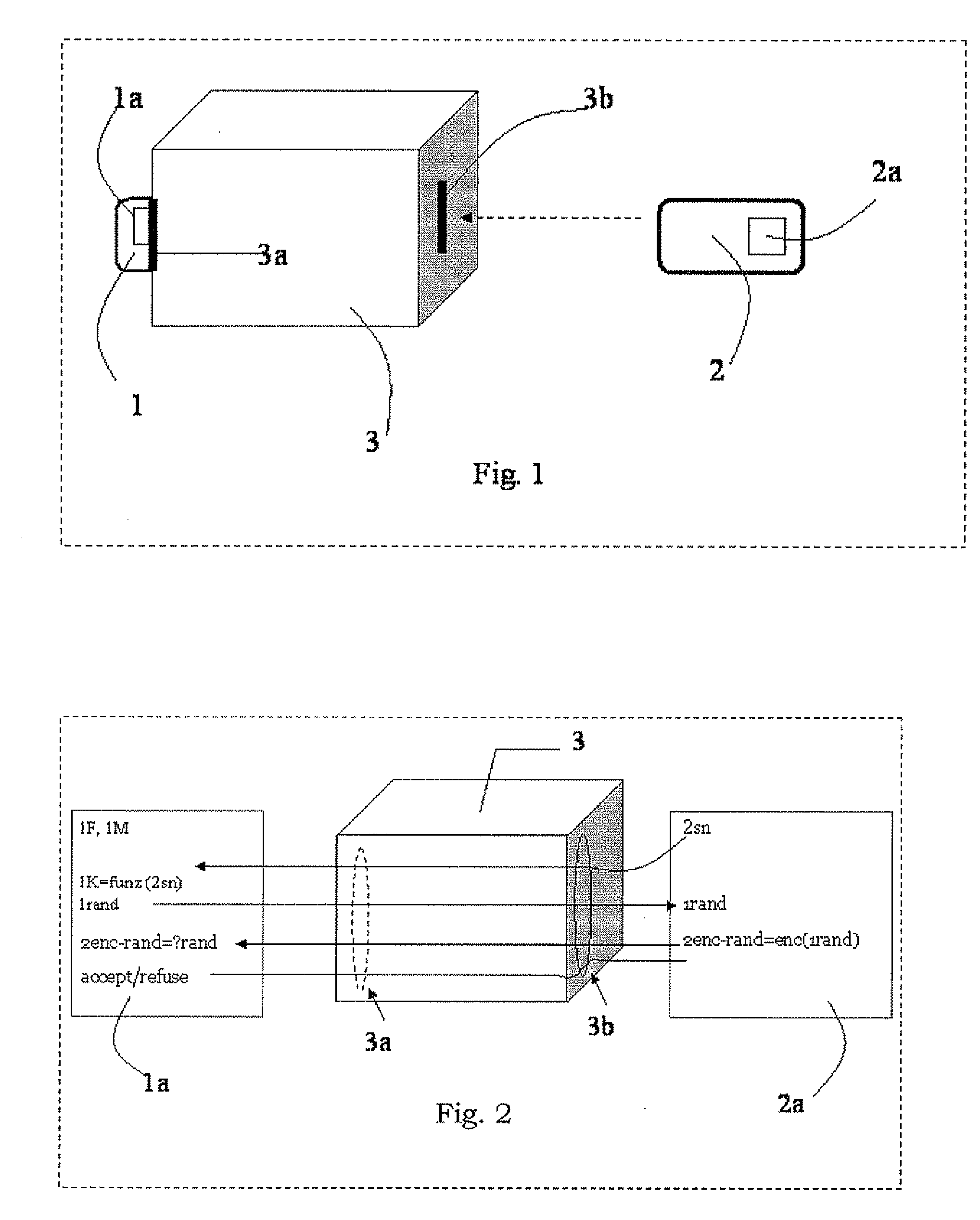
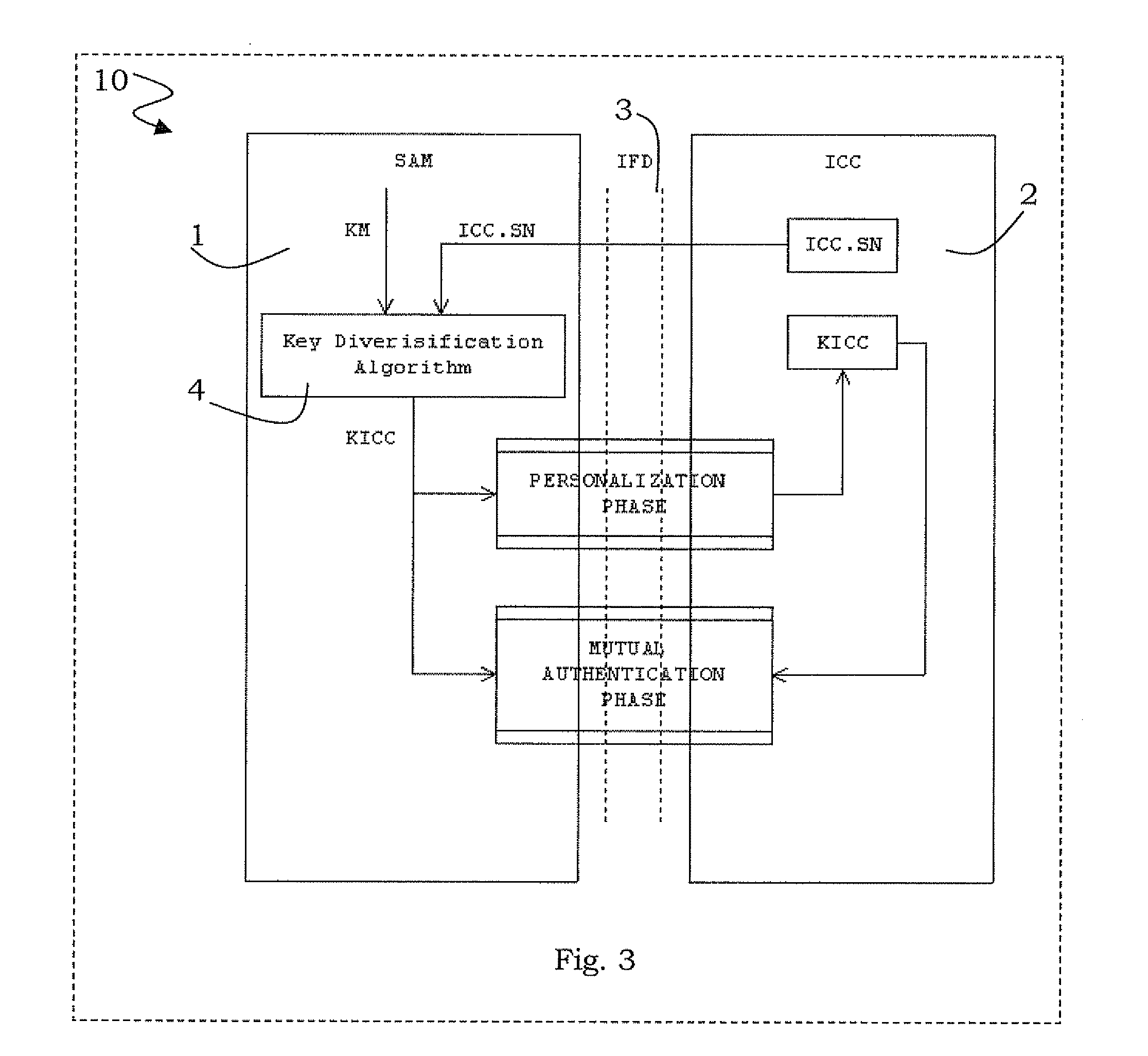
Method for key diversification on an IC card
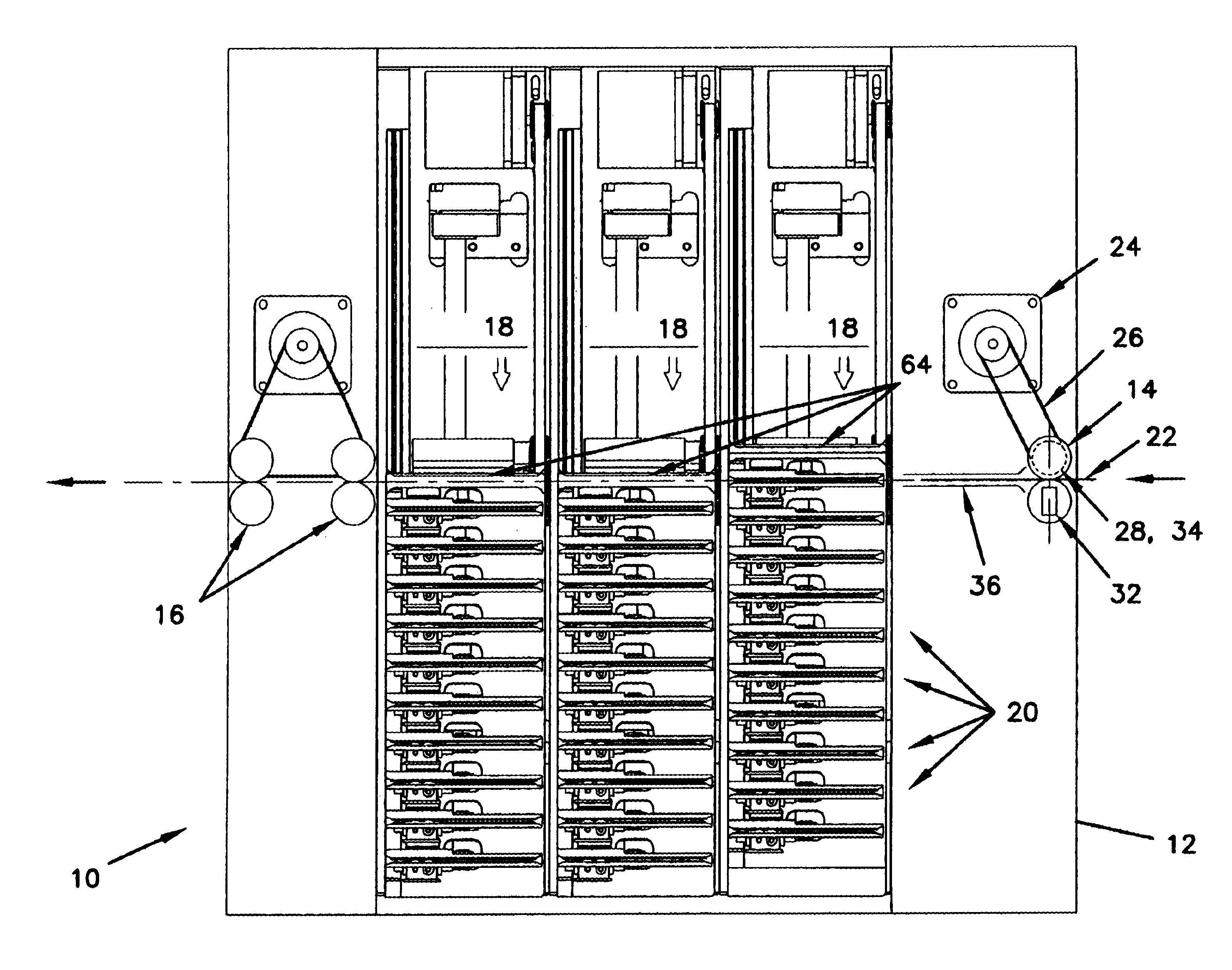
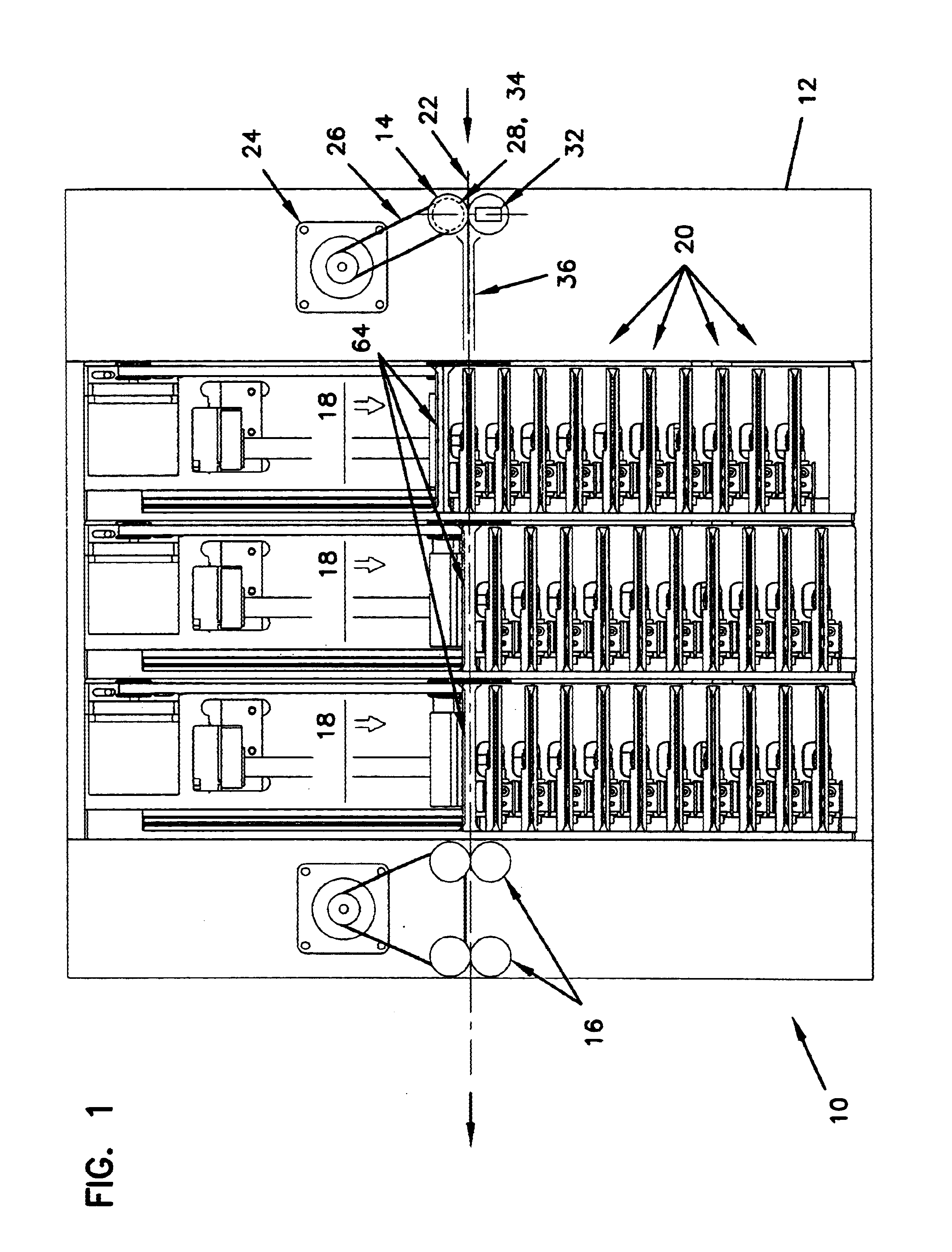
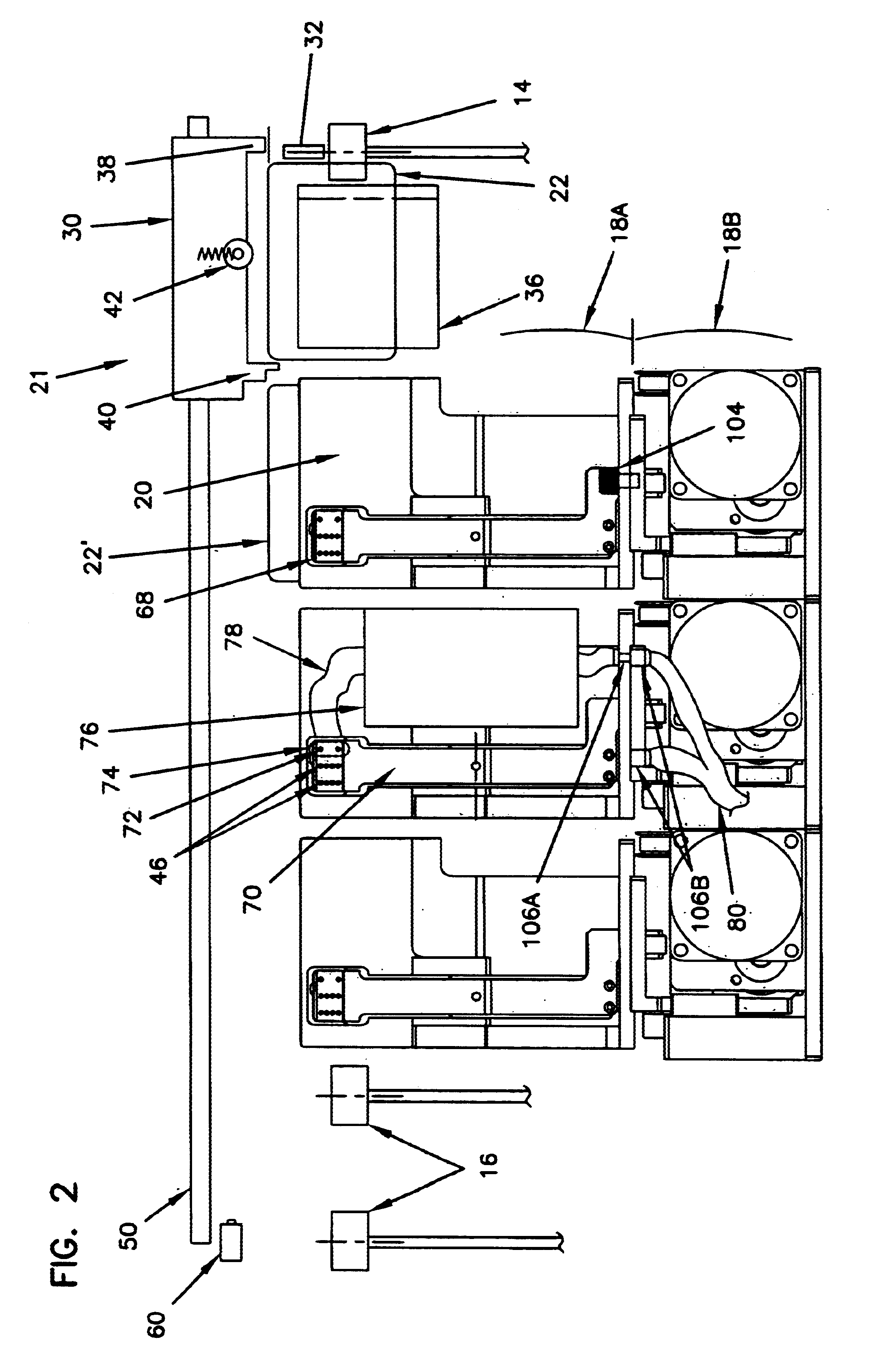
InactiveUS20080008315A1Shorten the timeNon-time consuming and non-computational intensive operationsAcutation objectsUser identity/authority verificationCommunication interfaceMaster key
Key diversification is performed during a mutual authentication between a SAM integrated circuit (IC) card storing a master key, and a user IC card storing an identification number. The user IC card is connected to the SAM IC card through a communications interface. The key diversification includes deriving sub keys from the master key, and computing ciphered strings through corresponding cryptographic computations on a string obtained by an elaboration on the identification number with the sub keys. A diversification key is generated by linking together a combination of bytes of the ciphered strings.
Owner:STMICROELECTRONICS INT NV
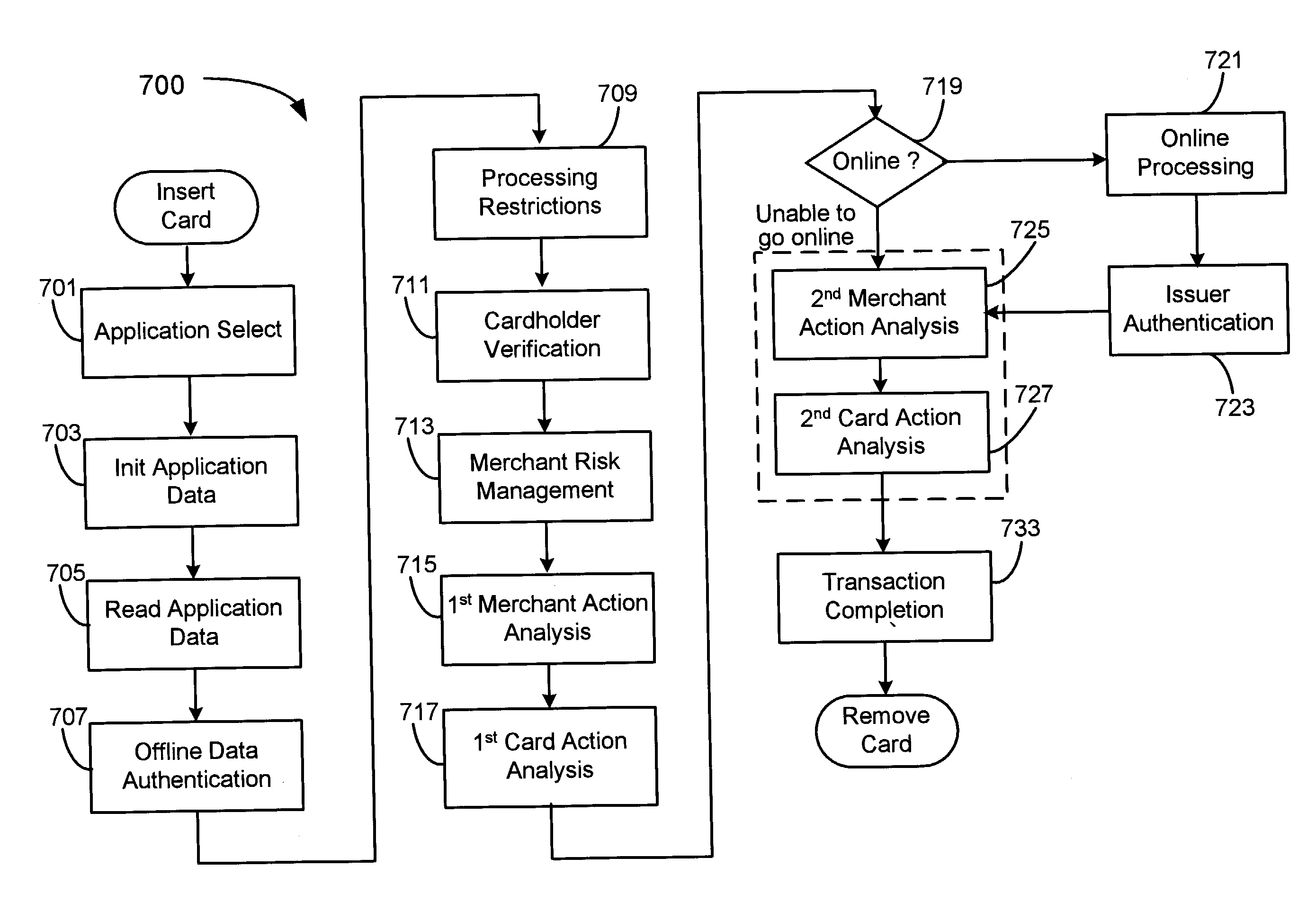
Methods and apparatus for a secure proximity integrated circuit card transactions
ActiveUS20050033688A1Digital data processing detailsAnalogue secracy/subscription systemsSystem parametersRisk factor
Methods and apparatus for a smartcard system are provided which securely and conveniently provides for secure transaction completion in a contact or contactless environment. The invention utilizes selection of processing applications based on the account issuer parameters and risk factors (stored on a smartcard) and merchant system parameters and risk factors (stored on a merchant system database). The invention permits a merchant system and smartcard to exchange information useful for determining if particular transactions should be completed online or offline.
Owner:LIBERTY PEAK VENTURES LLC
Methods and apparatus for large scale distribution of electronic access clients
ActiveUS20130227646A1Large distributionDigital data processing detailsMultiple digital computer combinationsElectronic accessSecurity software
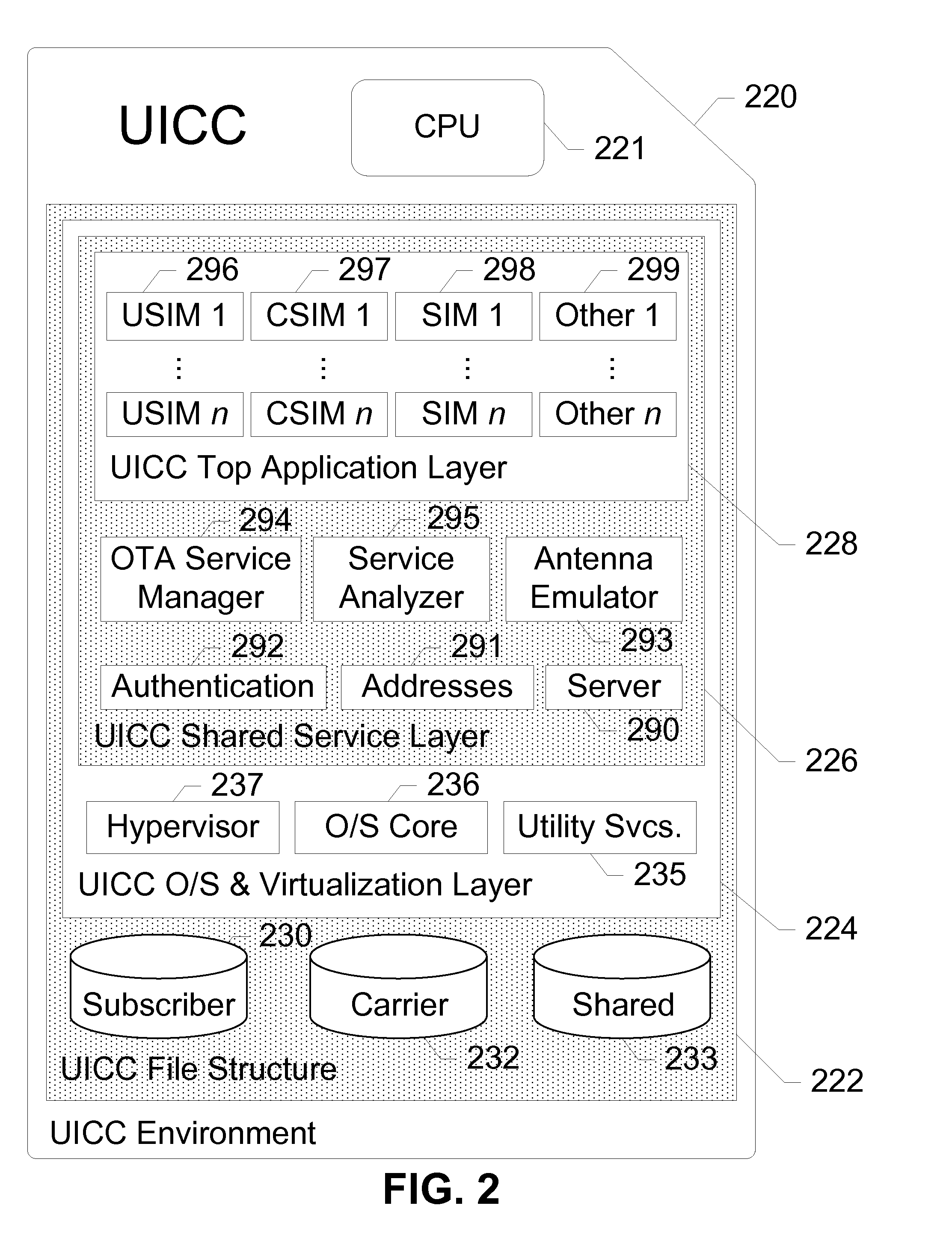
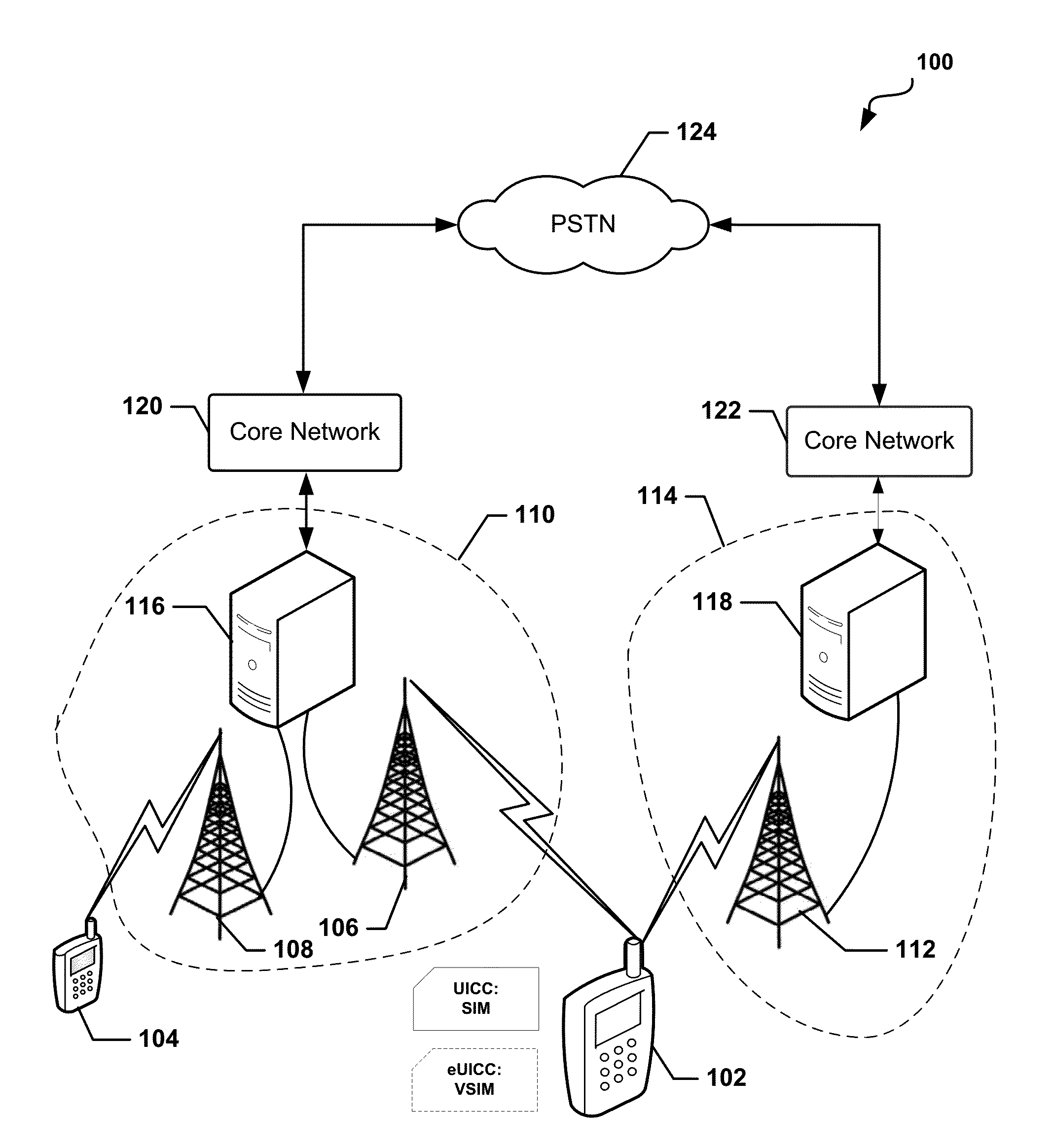
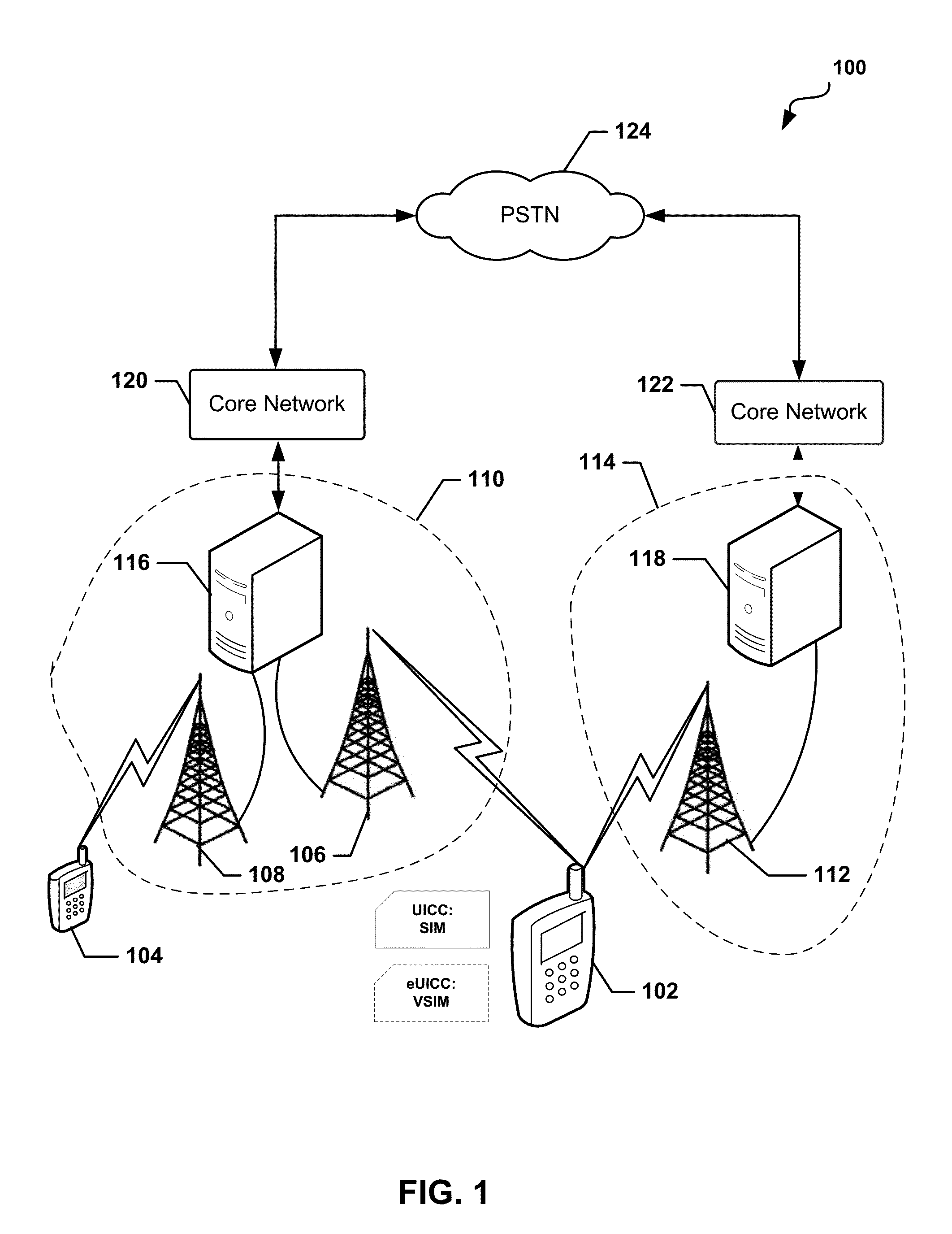
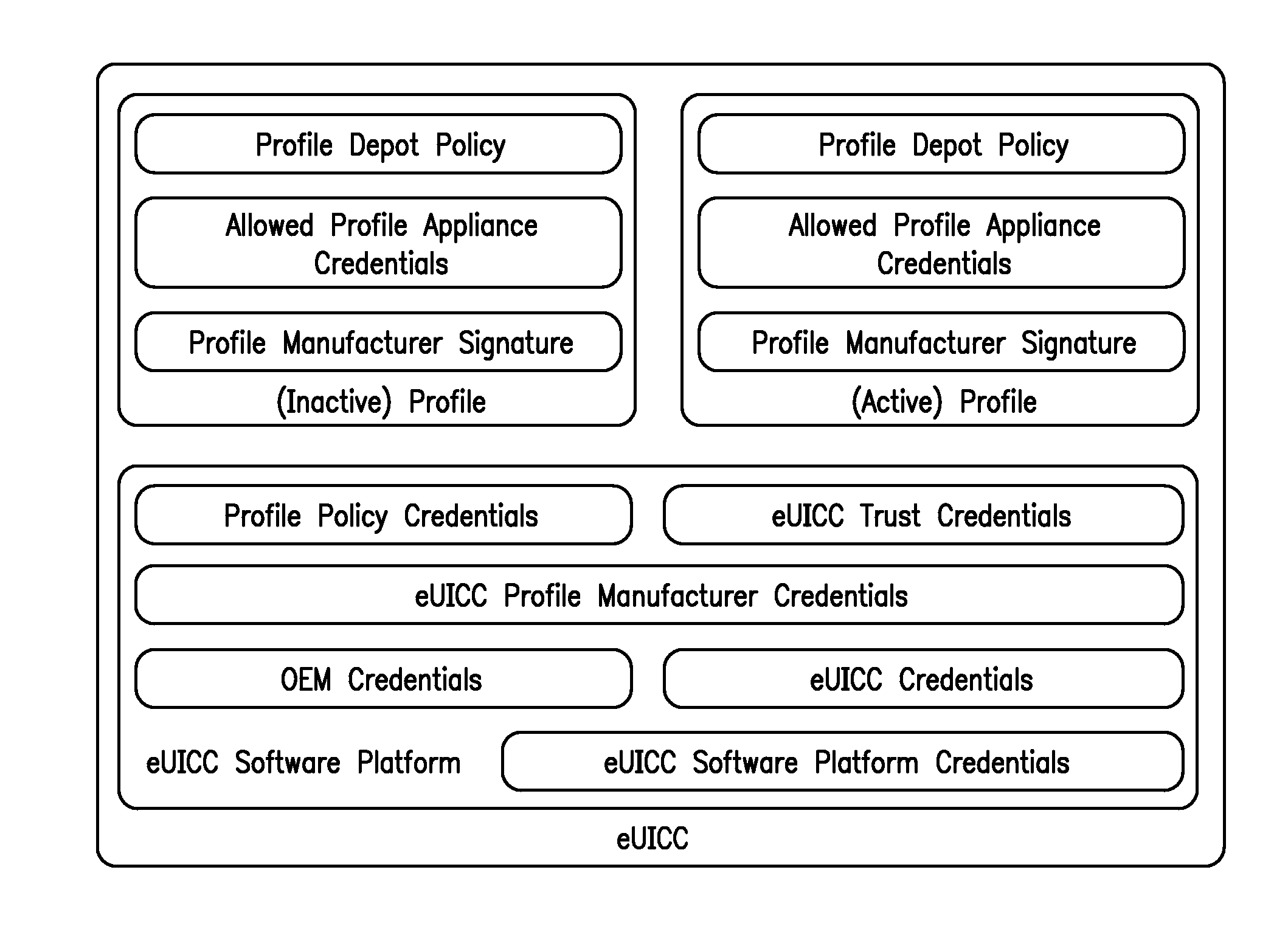
Methods and apparatus for large scale distribution of electronic access control clients. In one aspect, a tiered security software protocol is disclosed. In one exemplary embodiment, a server electronic Universal Integrated Circuit Card (eUICC) and client eUICC software comprise a so-called “stack” of software layers. Each software layer is responsible for a set of hierarchical functions which are negotiated with its corresponding peer software layer. The tiered security software protocol is configured for large scale distribution of electronic Subscriber Identity Modules (eSIMs)
Owner:APPLE INC
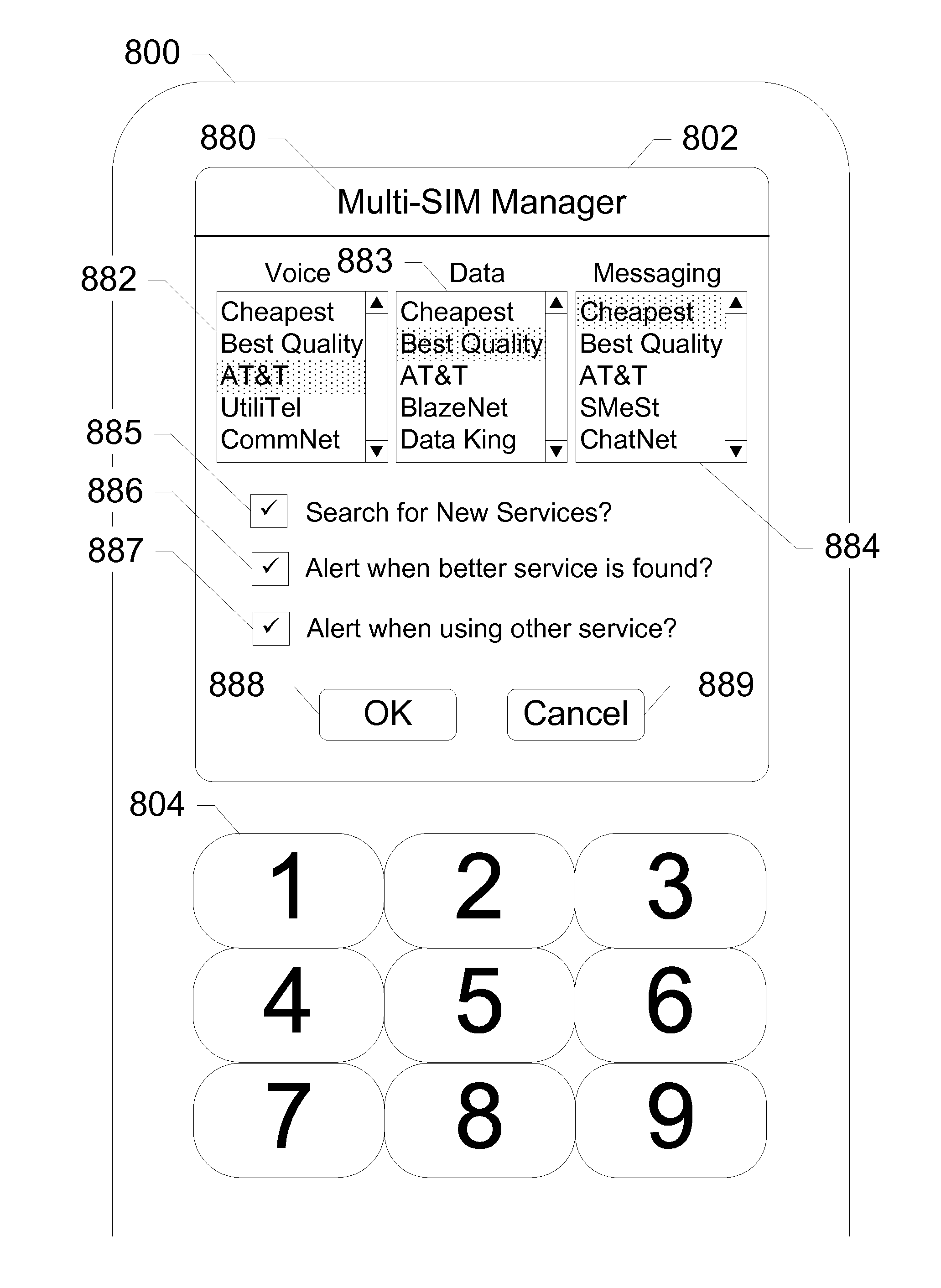
UICC Carrier Switching Via Over-The-Air Technology
ActiveUS20130023235A1Eliminate needService provisioningUnauthorised/fraudulent call preventionVirtual userCarrier signal
Devices, systems, and methods are disclosed which relate to provisioning a universal integrated circuit card (UICC) with multiple services. The UICC enables a wireless communication device to communicate through multiple carriers by using a unique virtual subscriber identity module (SIM) to register with each carrier. The unique virtual SIM is one of a plurality of virtual SIMs stored on and managed by the UICC. A carrier network includes a server for provisioning a new virtual SIM on a UICC over-the-air (OTA) when a new customer requests a service such as voice, data, or other type of service. These UICCs may also include logic to automatically select the best carrier for a voice call depending on the user settings.
Owner:AT&T INTPROP I L P
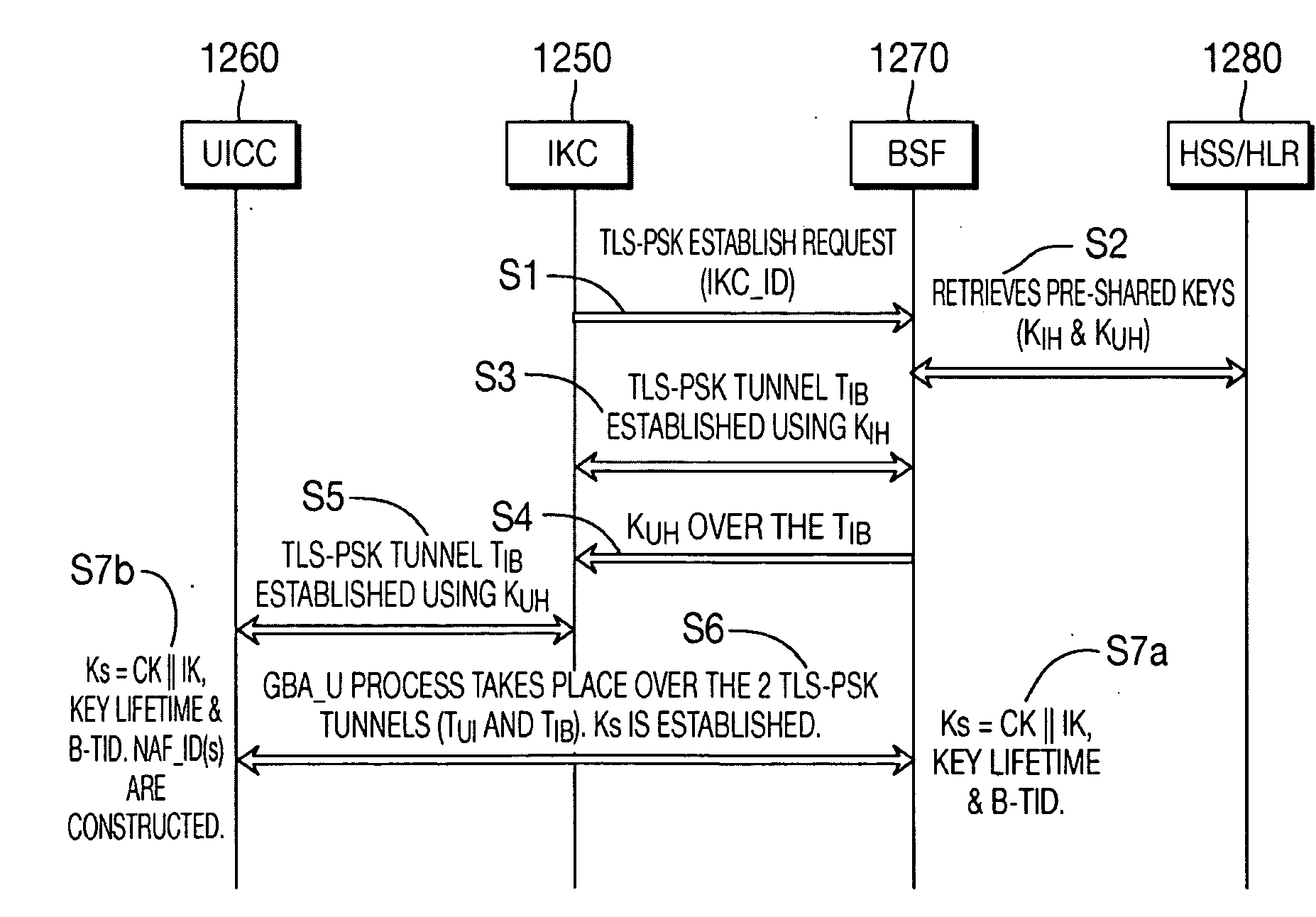
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
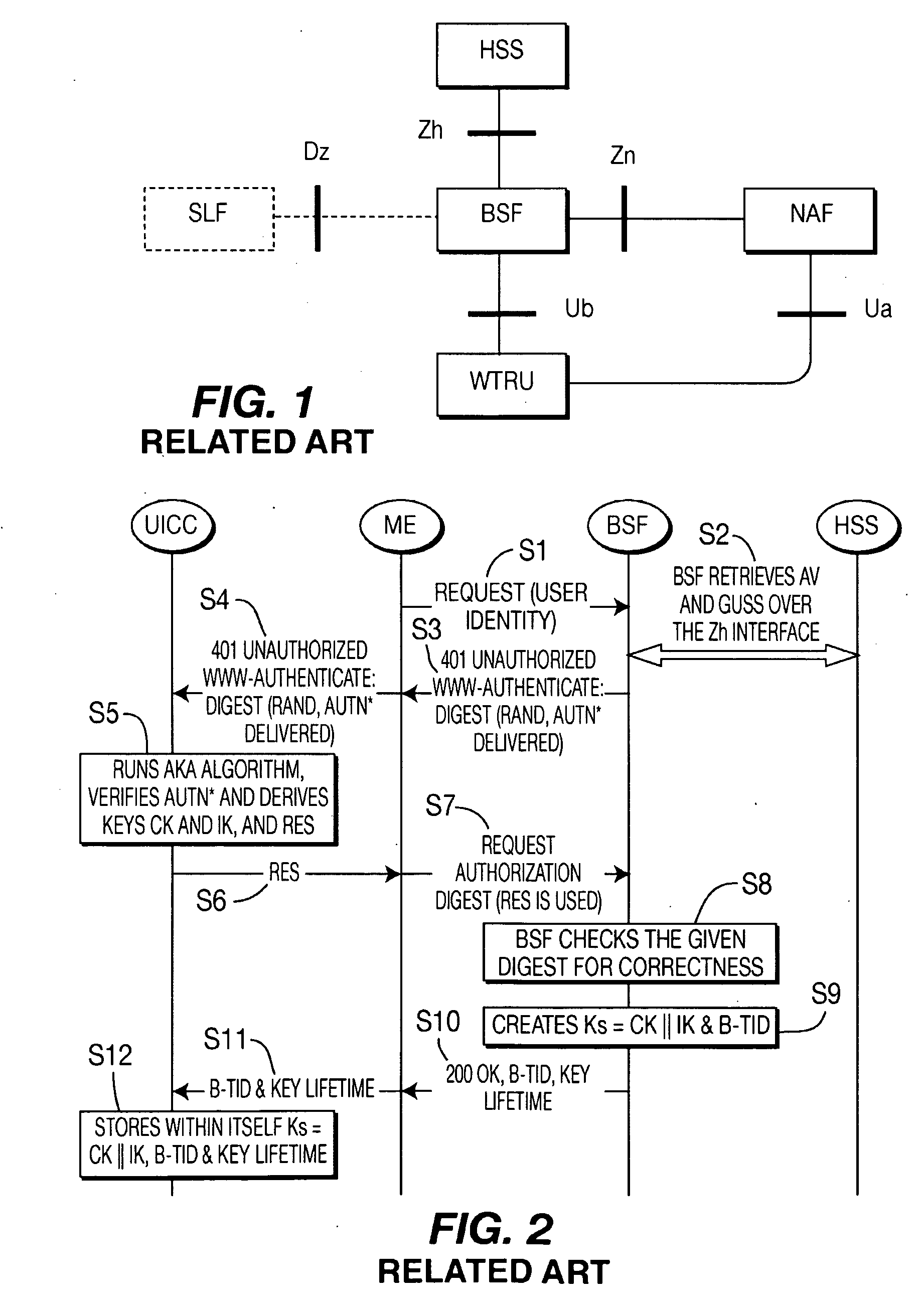
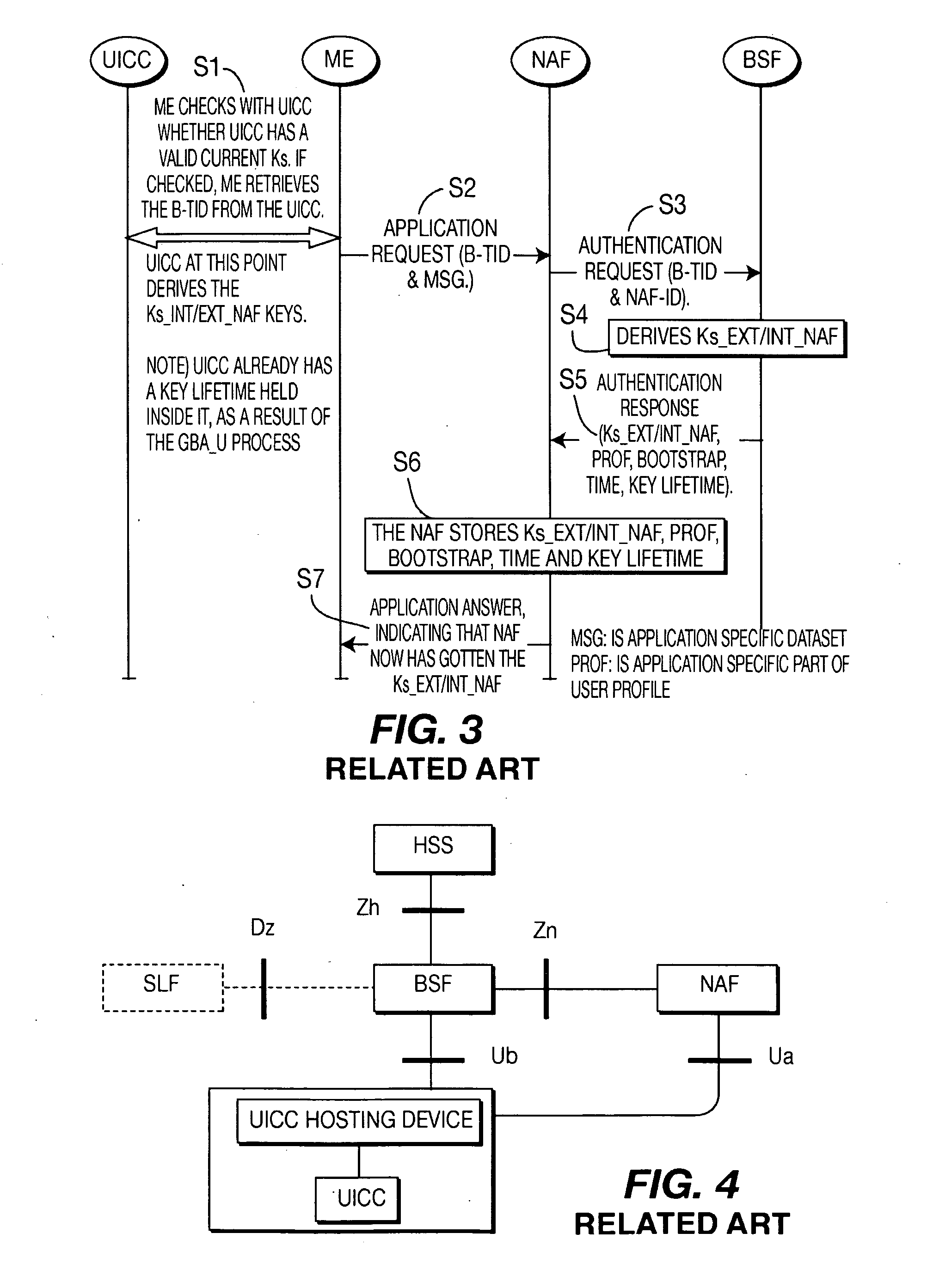
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
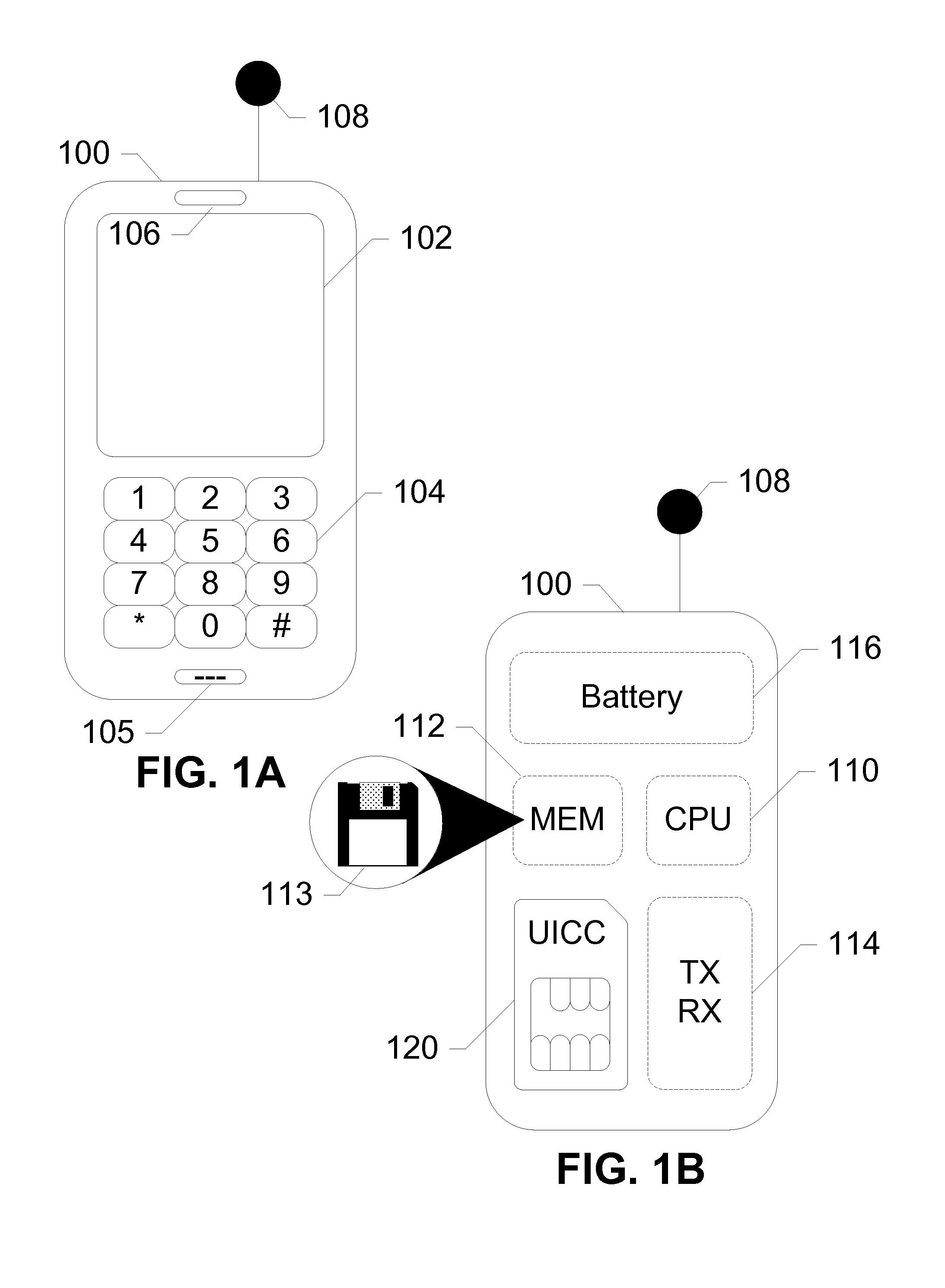
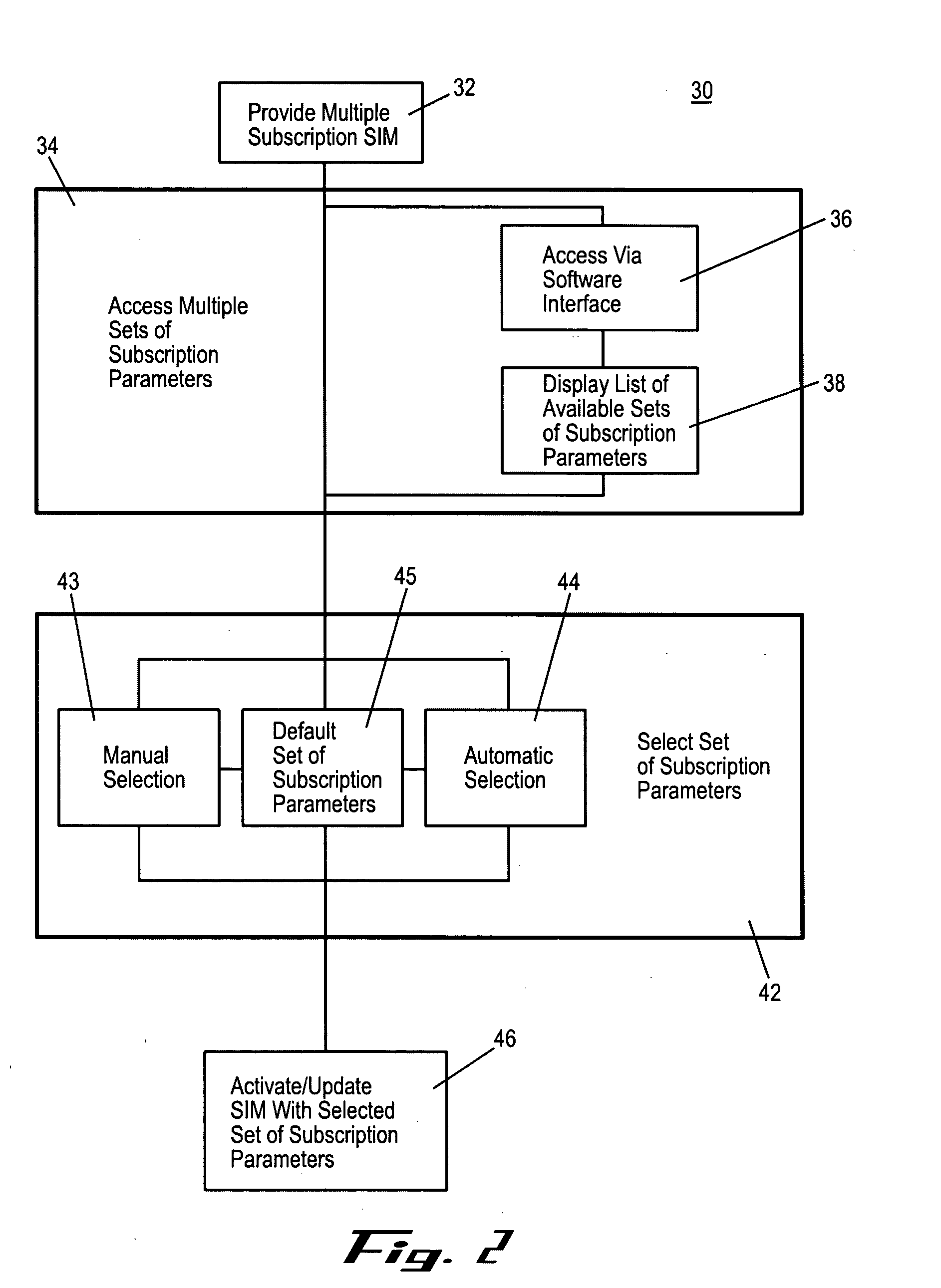
Multiple subscription subscriber identity module (SIM) card
ActiveUS20050164737A1Substation equipmentTransmissionSubscriber identity moduleInternational mobile subscriber identity
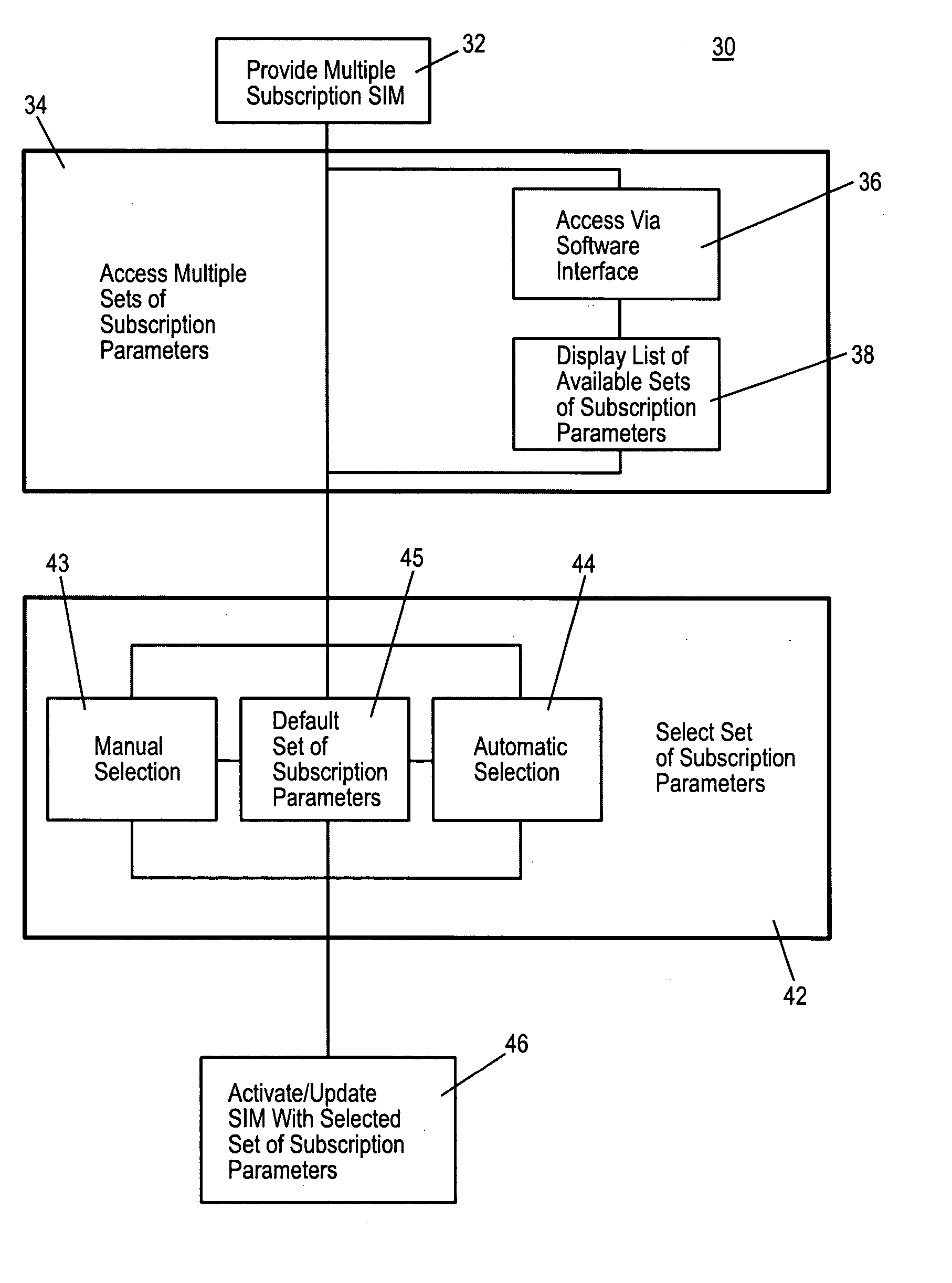
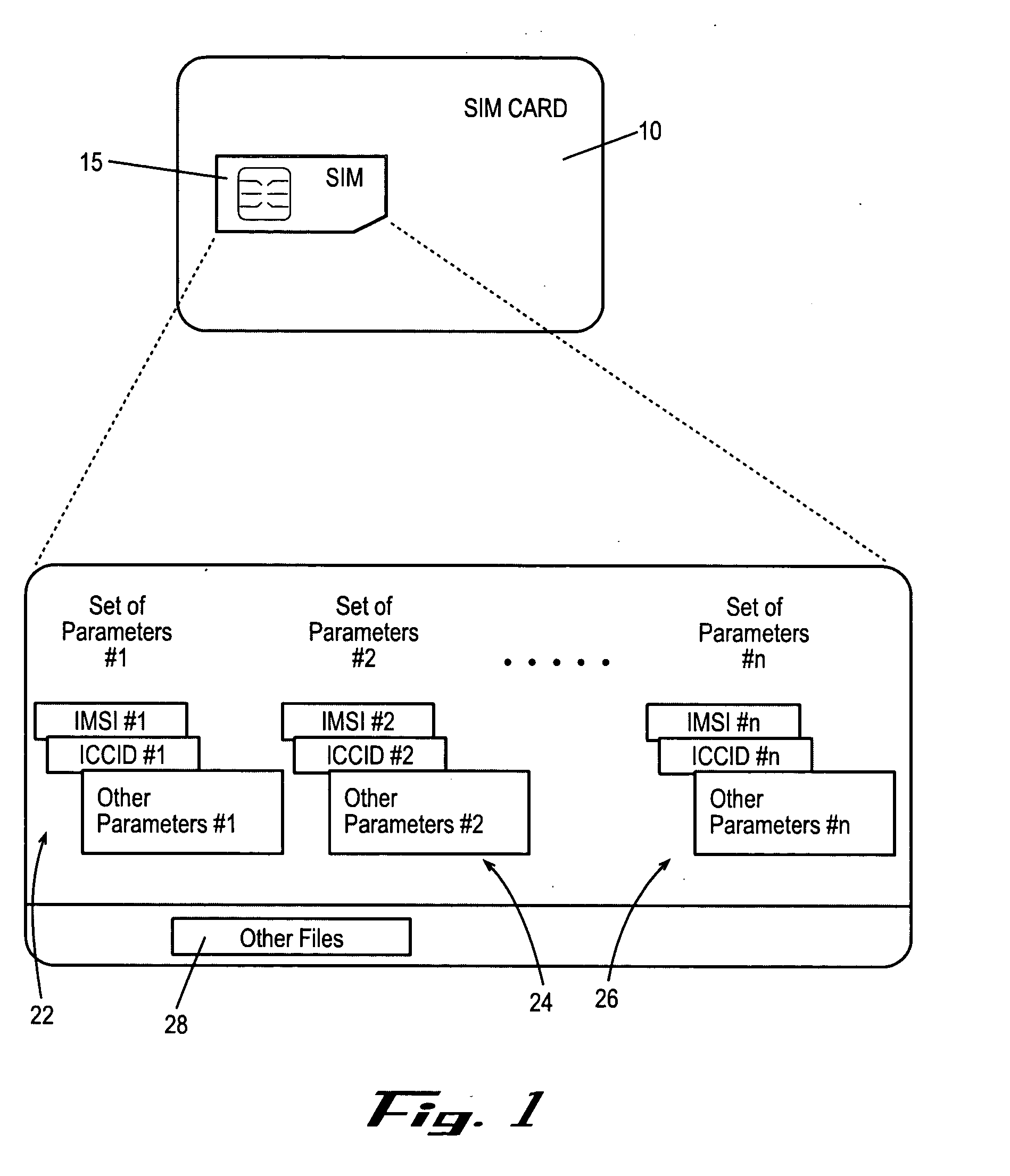
Embodiments of the invention include a multiple subscription subscriber identity module (SIM) card. The SIM card includes a plurality of sets of subscription parameters from which to select and activate a single set of parameters. The sets of subscription parameters each contain various information, e.g., information such as an Integrated Circuit Card Identifier (ICCID) and an International Mobile Subscriber Identity (IMSI), and are based on various criteria, e.g., different service regions of use for the electronic device on which the SIM card is installed. A set of subscription parameters is selected for a particular region of use either manually or automatically. The SIM card, which can include a software interface that provides a list of available sets of subscription parameters, is activated by updating the selected set of subscription parameters. Alternatively, a default set of subscription parameters is selected unless a different set of subscription parameters is selected manually from among the plurality of sets of subscription parameters. According to alternative embodiments of the invention, the selected set of subscription parameters can be deactivated and a different set of subscription parameters can be selected and updated to in the SIM card.
Owner:CINGULAR WIRELESS II LLC
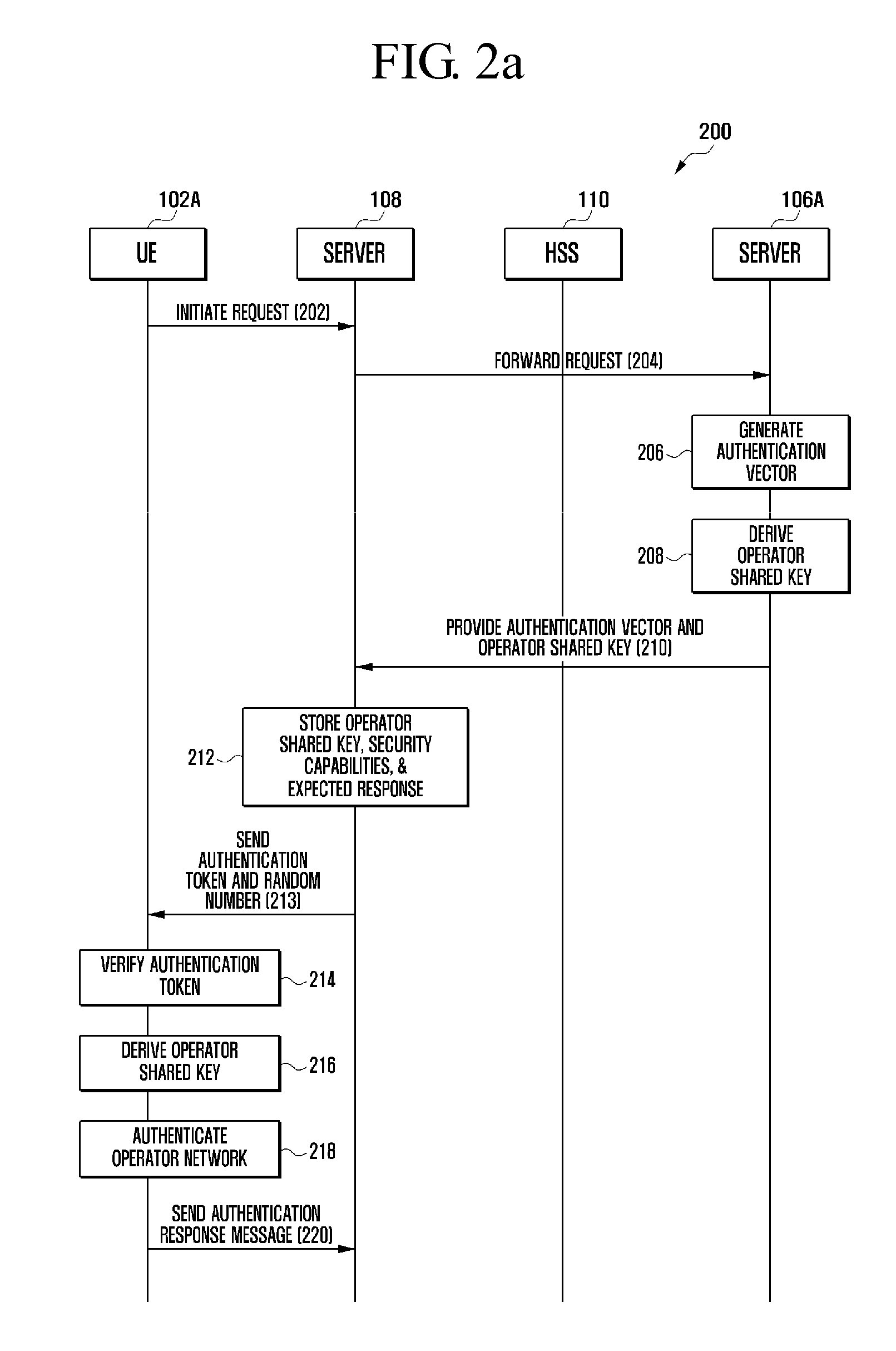
Method and system for secured remote provisioning of a universal integrated circuit card of a user equipment
ActiveUS20130012168A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwarePublic land mobile network
The present invention provides a method and system for secured remote provisioning of a universal integrated circuit card of a user equipment. A system includes a user equipment for initiating a request for remote provisioning of an universal integrated circuit card (UICC) in the user equipment, where the request for remote provisioning includes a machine identifier (MID) associated with the user equipment and a public land mobile network (PLMN) identifier (ID) associated with an network operator. The system also includes at least one shared key management server for dynamically generating security keys and an operator shared key using the security keys, the MID. Moreover, the system includes an operator network for generating a subscription key using the operator shared key and an international mobile subscriber identity (IMSI), and provisioning the IMSI in a secured manner to the UICC of the user equipment using the security keys.
Owner:SAMSUNG ELECTRONICS CO LTD
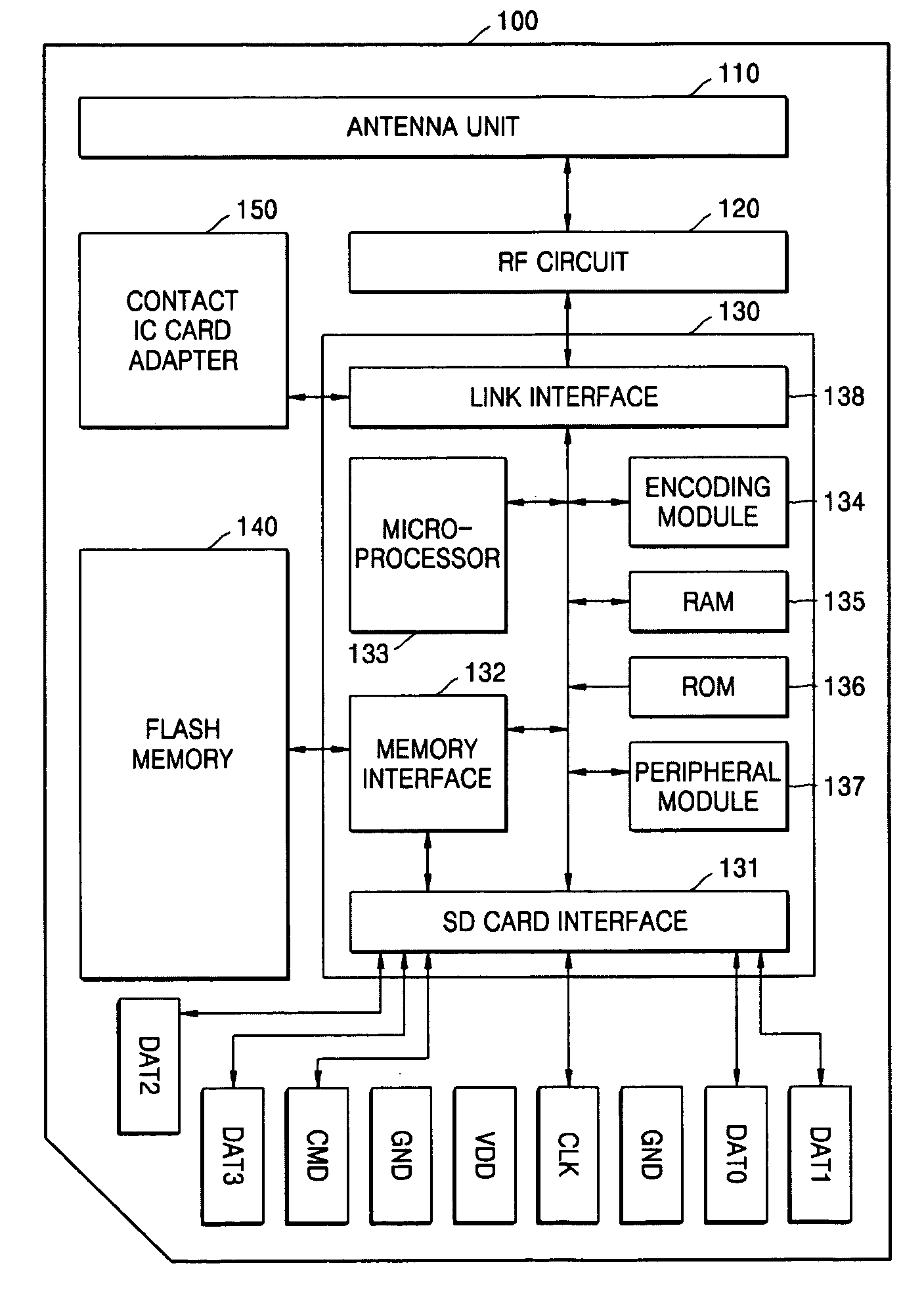
SD memory card for extension of function
InactiveUS20050224589A1Function increaseRecord carriers used with machinesData controlDigital storage
Provided is a secure digital memory card for extension of function, including: a flash memory installed in a host device and storing data generated by the host device; a controller controlling an access interface to the flash memory; a radio frequency circuit performing functions of a contactless integrated circuit card and a contactless integrated circuit card reader through a wireless interface control of the controller; an antenna unit connected to the radio frequency circuit to perform a function of a transmission and reception antenna; and a contact integrated circuit card adapter performing the function of the contact integrated circuit card reader through a wire interface control of the controller.
Owner:ELECTRONICS & TELECOMM RES INST
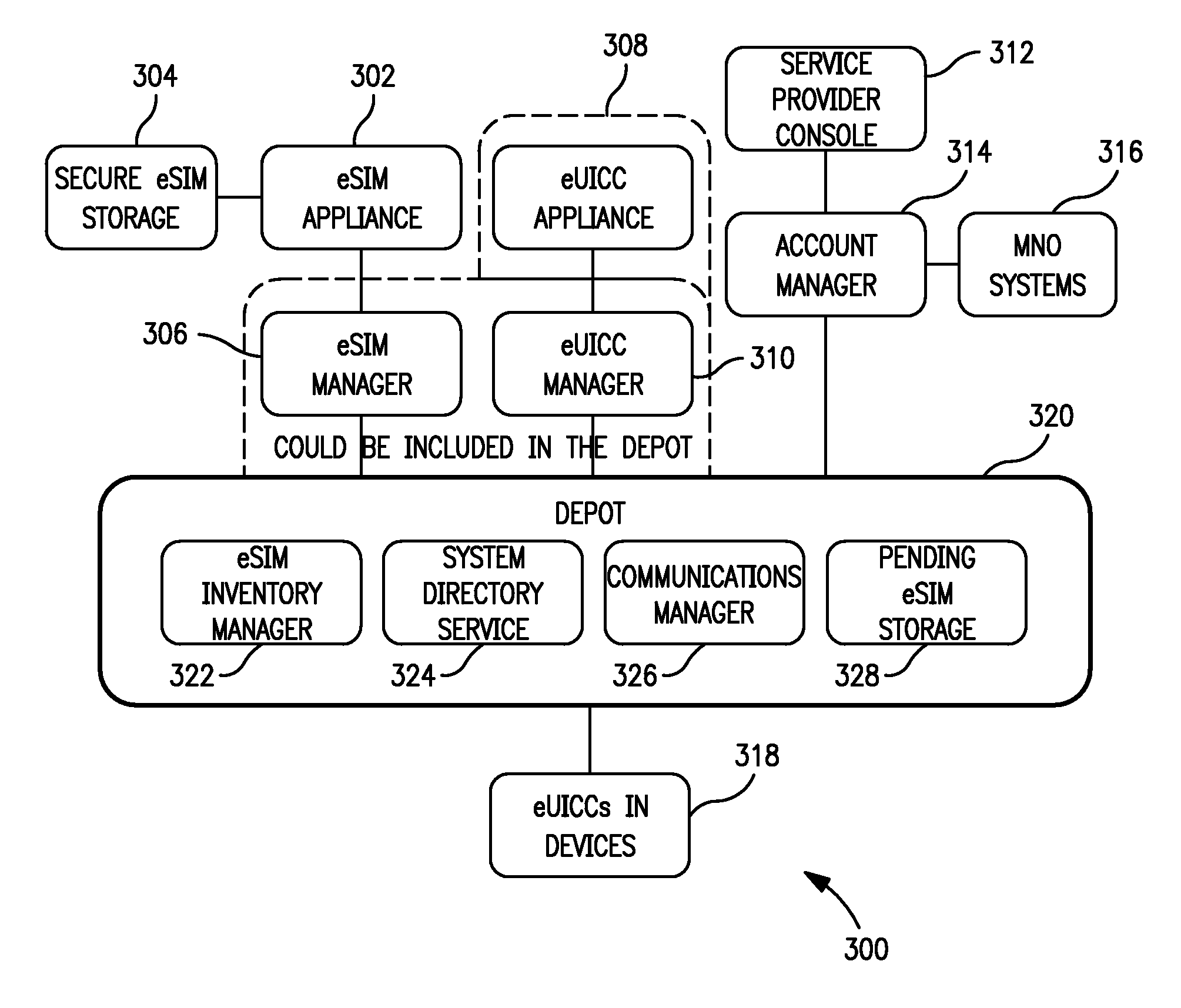
Electronic access client distribution apparatus and methods
ActiveUS20120331292A1Effective distributionEfficiently distributedDigital data processing detailsUser identity/authority verificationElectronic accessService provision
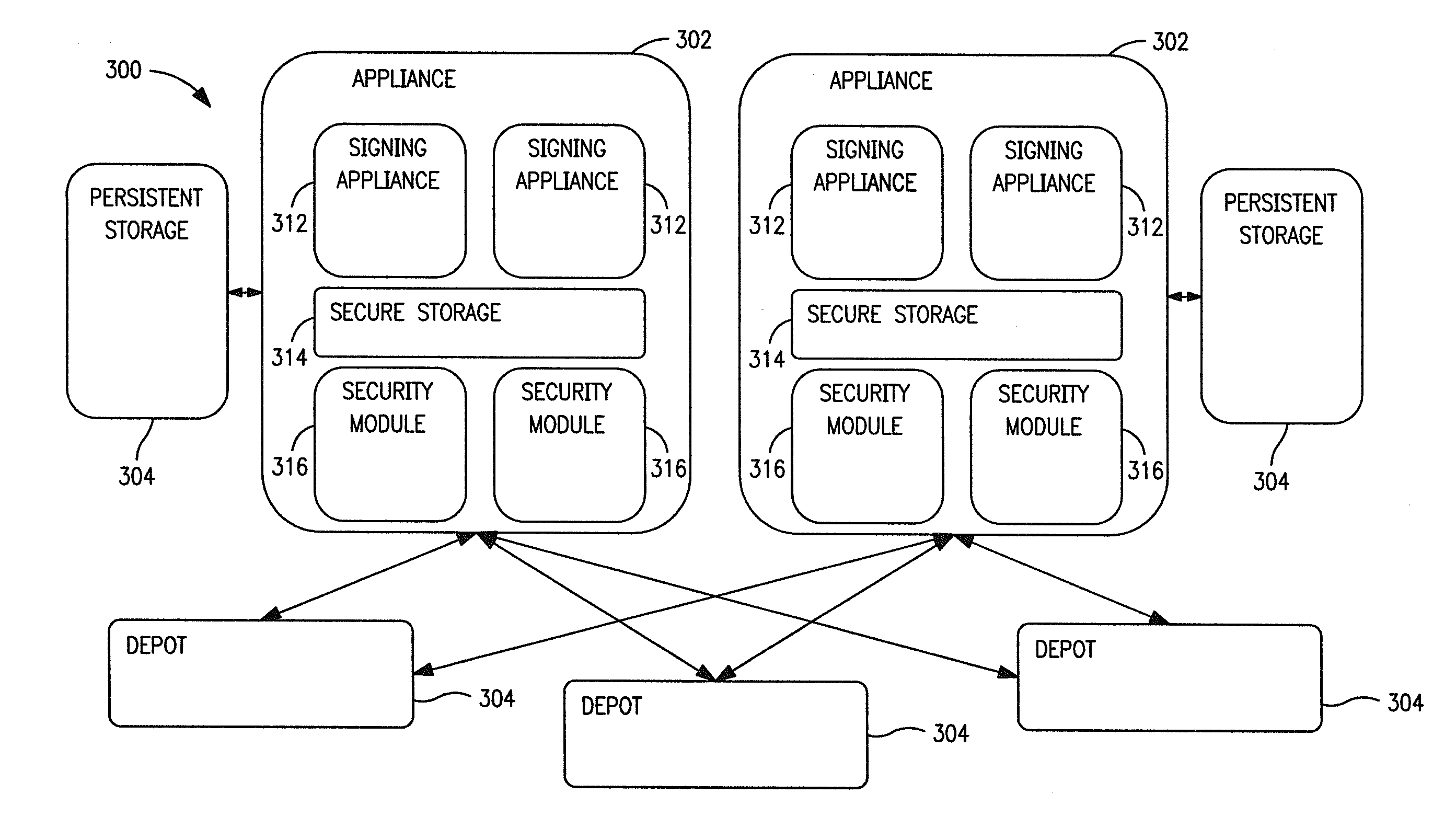
Apparatus and methods for distributing access control clients. In one exemplary embodiment, a network infrastructure is disclosed that enables delivery of electronic subscriber identity modules (eSIMs) to secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs), etc.) The network architecture includes one or more of: (i) eSIM appliances, (ii) secure eSIM storages, (iii) eSIM managers, (iv) eUICC appliances, (v) eUICC managers, (vi) service provider consoles, (vii) account managers, (viii) Mobile Network Operator (MNO) systems, (ix) eUICCs that are local to one or more devices, and (x) depots. Moreover, each depot may include: (xi) eSIM inventory managers, (xii) system directory services, (xiii) communications managers, and / or (xiv) pending eSIM storages. Functions of the disclosed infrastructure can be flexibly partitioned and / or adapted such that individual parties can host portions of the infrastructure. Exemplary embodiments of the present invention can provide redundancy, thus ensuring maximal uptime for the overall network (or the portion thereof).
Owner:APPLE INC
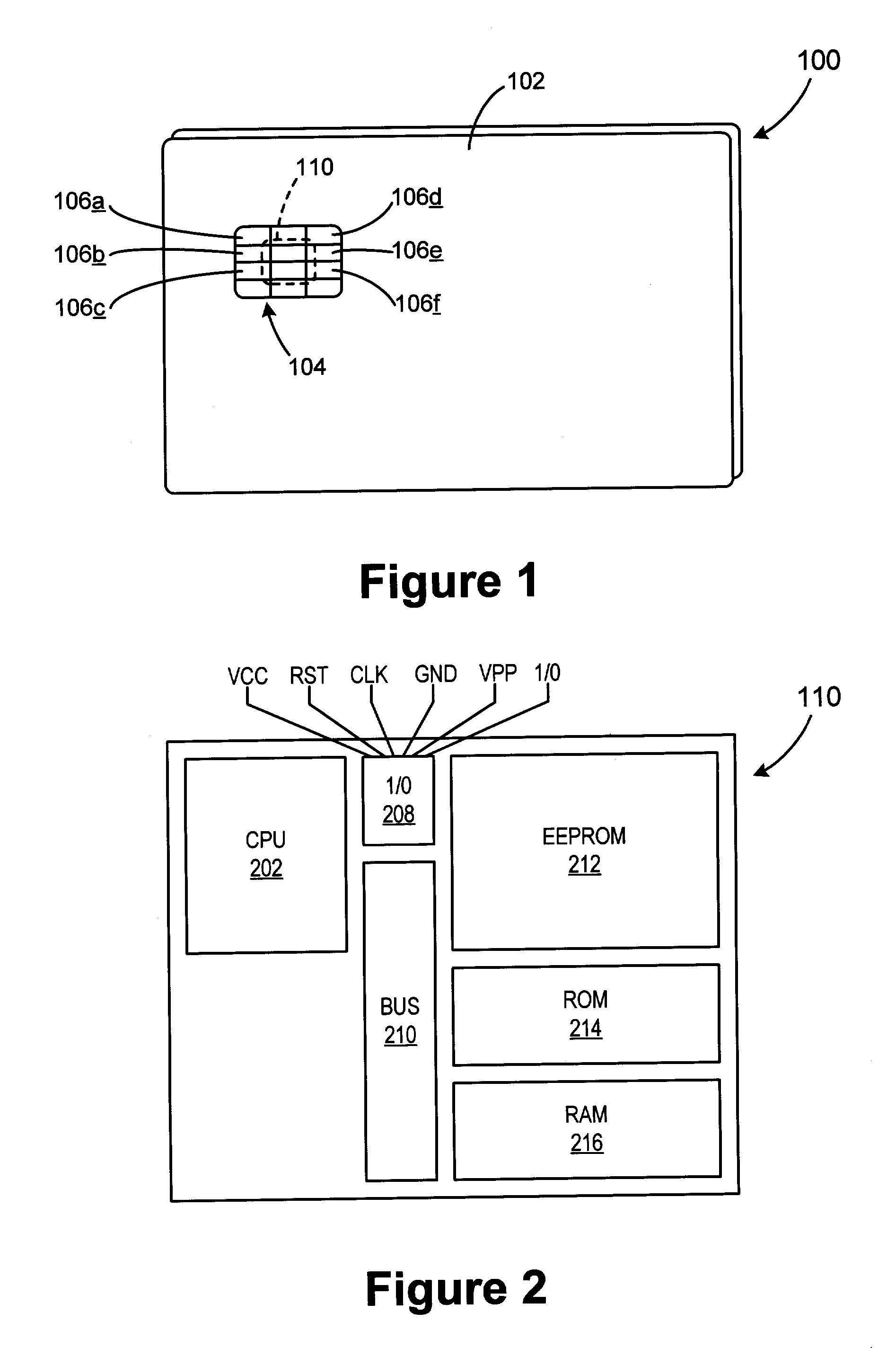
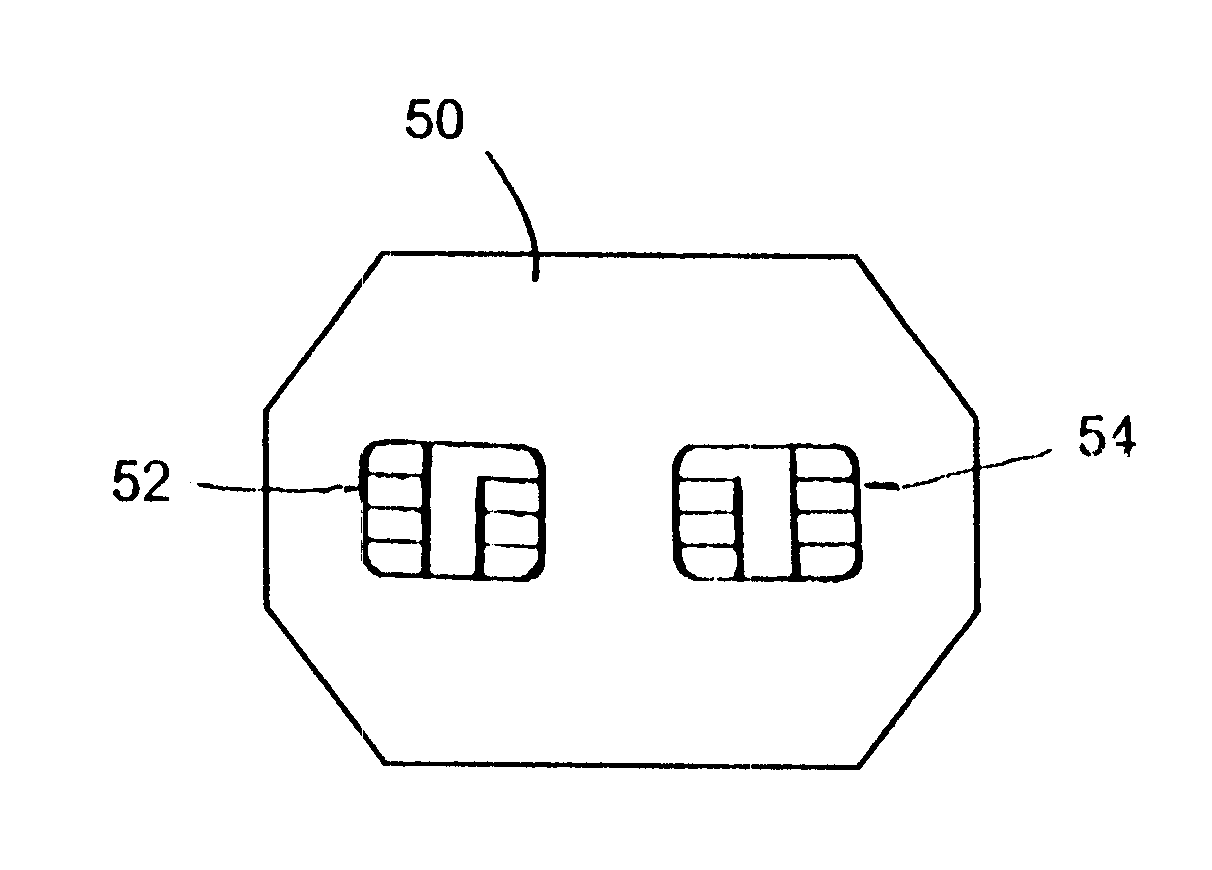
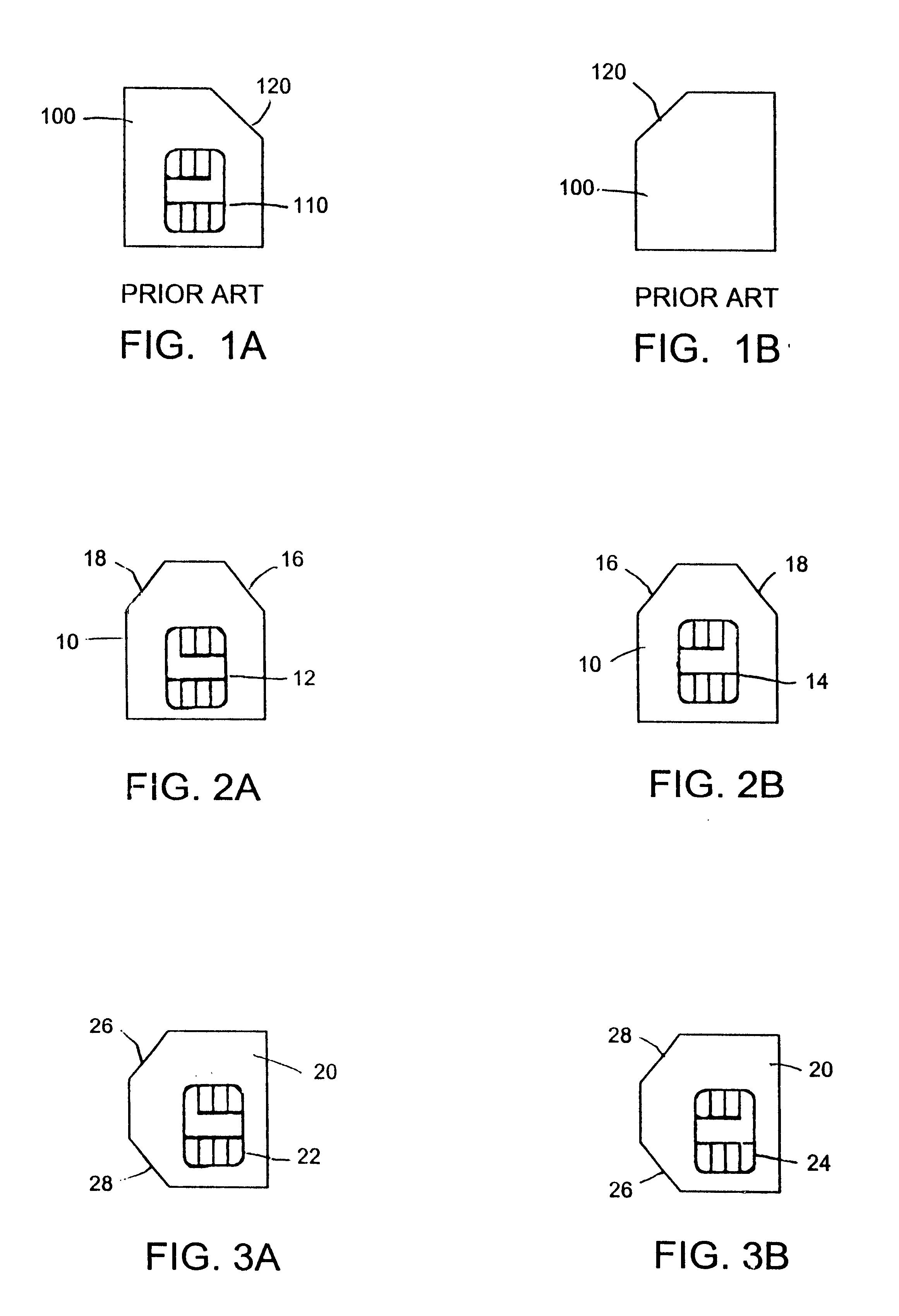
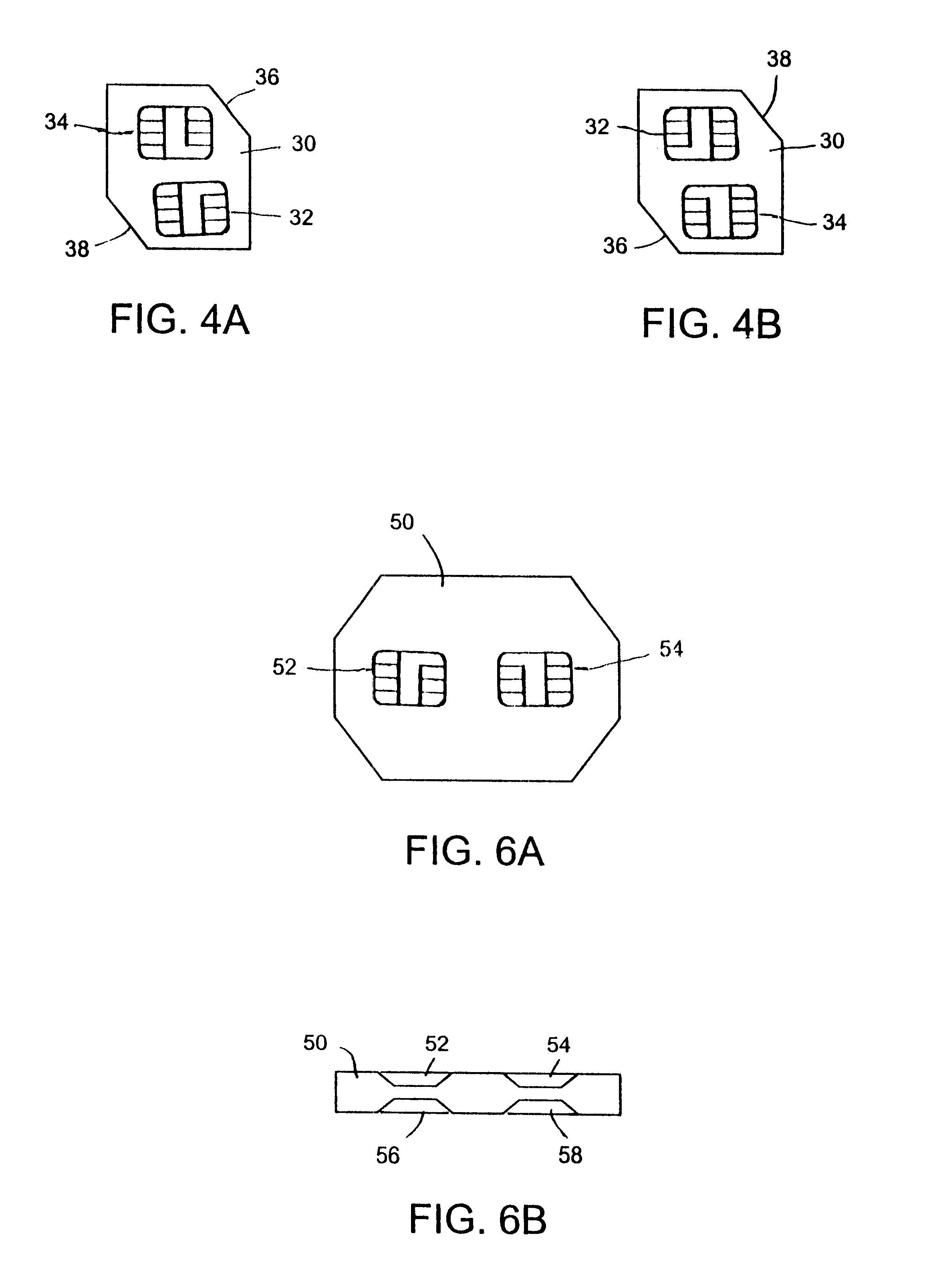
Integrated circuit card with multiple integral electronic modules
InactiveUS6641049B2Unauthorised/fraudulent call preventionSensing record carriersComputer moduleEngineering
The smart card according to the present invention includes a first integrated electronic module on one surface and another integrated electronic module on the opposite surface of the card, whereby the card is merely flipped over and reinserted into the electronic device to change applications or functions. The two integrated electronic modules provided on opposing surfaces of the card may be formed as two separate chips each embedded on one side of the card, or as one chip having exposed contact terminals on both faces of the card, depending on the size of the chip(s) mounted in the card. Alternatively, two integrated electronic modules can be both provided on the same surface of the card, in which case the card is rotated 180° to place the desired integrated electronic module in contact with the contact interface in the device to access the desired application or function. In a further embodiment, the card is provided with four integrated electronic modules, so that four different functions or applications can be realized using the same electronic device by simply arranging the card in the electronic device so that the appropriate integrated electronic module is aligned with the contact interface in the device. When the card includes a plug-in sized SIM card, two or more corners of the card are notched, with each notch corresponding to the orientation of a respective integrated electronic module when correctly positioned in the activated position in an electronic device.
Owner:QUADNOVATION
Conditional access method and device
InactiveUS6070796AInput/output for user-computer interactionAcutation objectsComputer hardwareAccess method
PCT No. PCT / FR96 / 01269 Sec. 371 Date Feb. 20, 1998 Sec. 102(e) Date Feb. 20, 1998 PCT Filed Aug. 8, 1996 PCT Pub. No. WO97 / 07448 PCT Pub. Date Feb. 27, 1997A conditional access device for use in connection with a host electronic equipment. The device includes a pointer peripheral containing one or more integrated circuit card coupler units. In addition, it also includes a device for acquiring personal information about a user. The personal information is locally compared with information stored in the integrated circuit card without passing through the host equipment.
Owner:SIRBU CORNEL
System and Methods for Dynamic SIM Provisioning on a Dual-SIM Wireless Communication Device
ActiveUS20150304506A1Accounting/billing servicesSecurity arrangementComputer hardwareCredential management
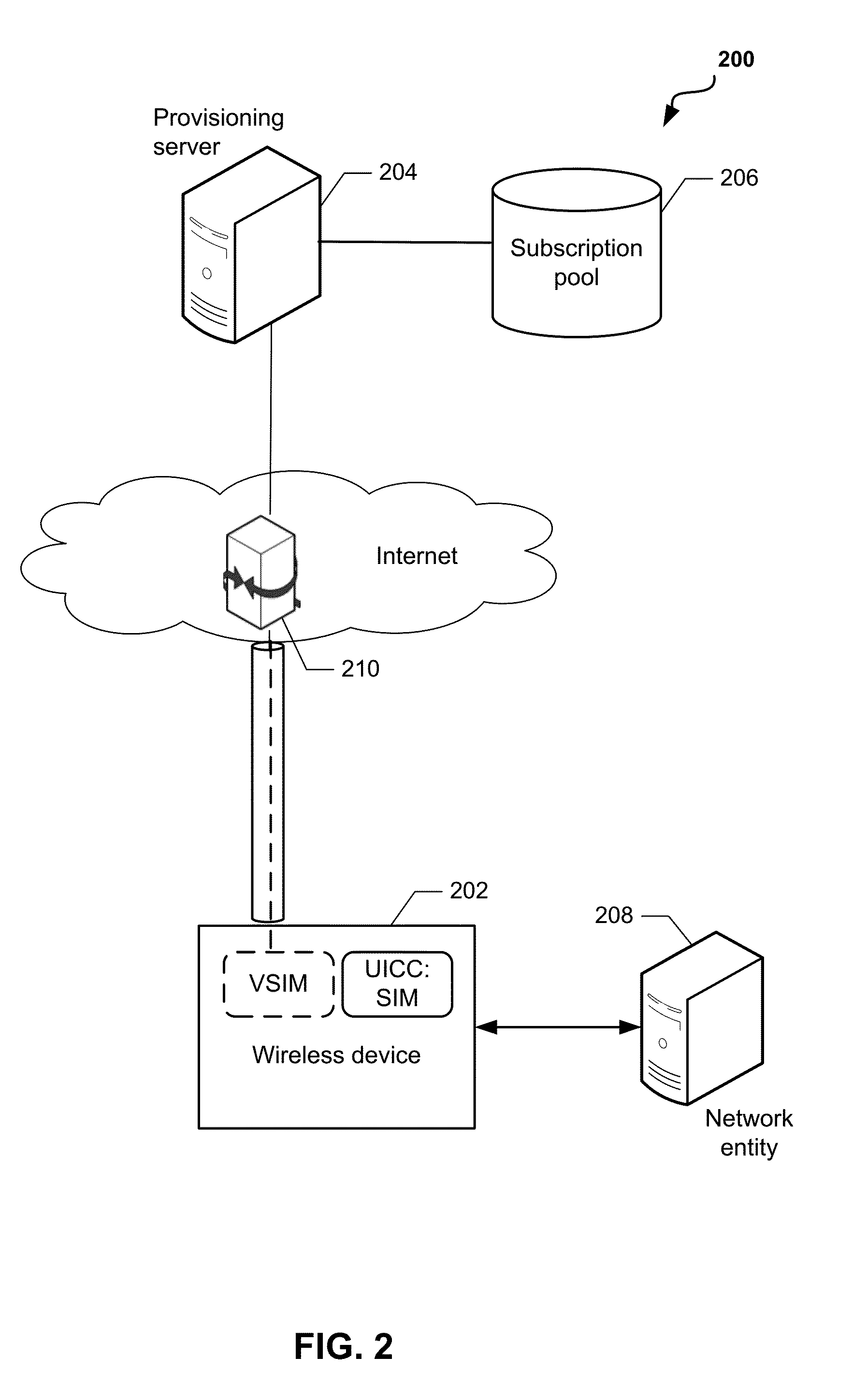
Methods and devices for dynamic VSIM provisioning on a multi-SIM wireless device having a first SIM as a Universal Integrated Circuit Card (UICC) and a virtual SIM (VSIM). A provisioning server may receive updated information from the wireless device, and based at least partially on the received information, determine whether the SIM profile on the VSIM of the wireless device should be changed. To change the SIM profile, the provisioning server may determine whether remote credential management procedures are enabled. If so, the provisioning server may select a new SIM profile from a plurality of SIM profiles, and provision the new SIM profile in the VSIM using remote credential management procedures. If remote credential management procedures are unavailable, the provisioning server may select a remote SIM from a plurality of remote SIMs associated with the provisioning server, and run the remote SIM to execute authentication processes for the wireless device.
Owner:QUALCOMM INC
Methods and apparatus for a secure proximity integrated circuit card transactions
ActiveUS7587756B2Digital data processing detailsAnalogue secracy/subscription systemsFinancial transactionSystem parameters
Methods and apparatus for a smartcard system are provided which securely and conveniently provides for secure transaction completion in a contact or contactless environment. The invention utilizes selection of processing applications based on the account issuer parameters and risk factors (stored on a smartcard) and merchant system parameters and risk factors (stored on a merchant system database). The invention permits a merchant system and smartcard to exchange information useful for determining if particular transactions should be completed online or offline.
Owner:LIBERTY PEAK VENTURES LLC
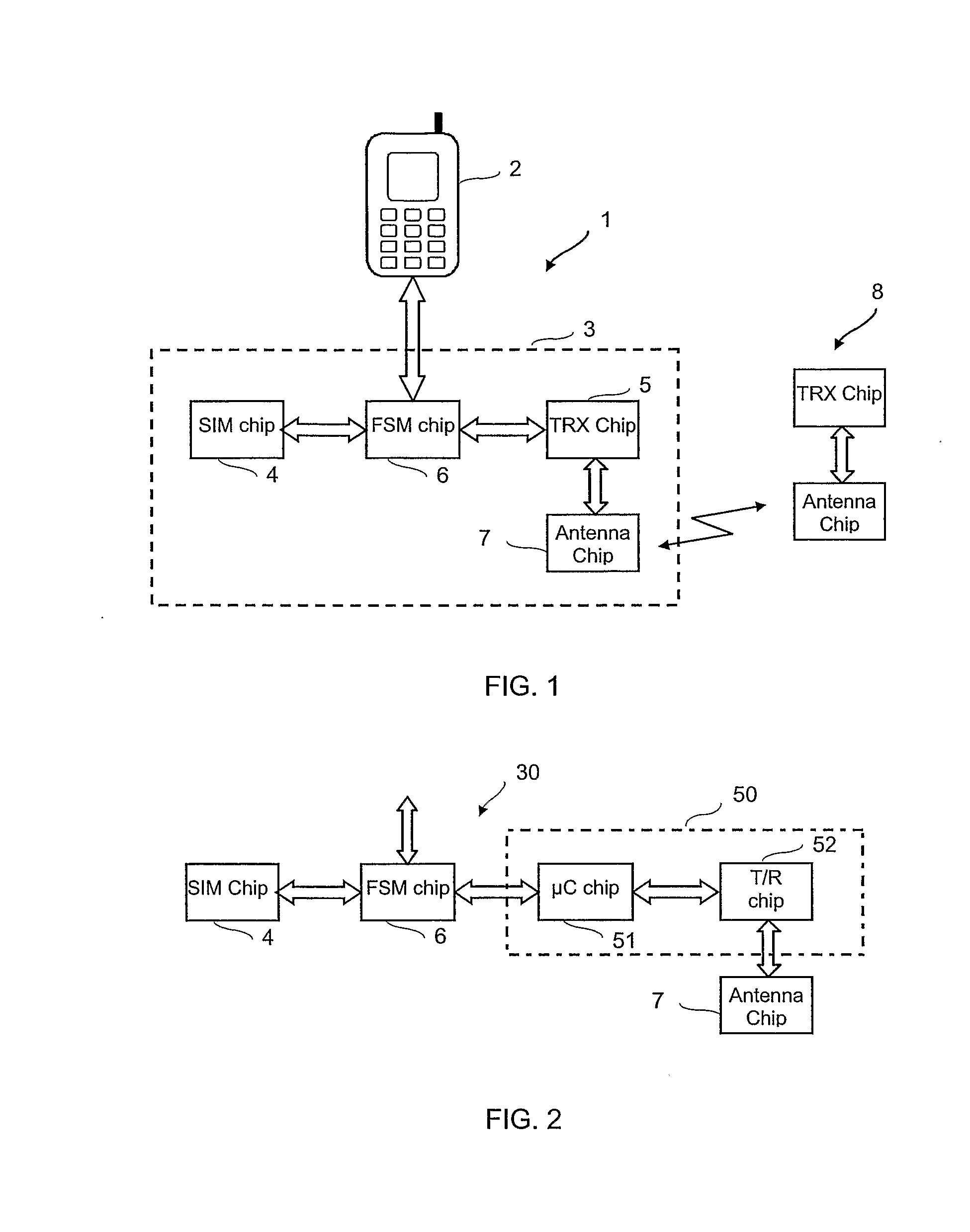
Joint Ic Card And Wireless Transceiver Module For Mobile Communication Equipment
InactiveUS20080261656A1Digital data processing detailsPayment architectureWireless transceiverTransceiver
Owner:TELECOM ITALIA SPA
Simulacrum of physical security device and methods
ActiveUS20120117635A1Service provisioningDigital data processing detailsSoftware emulationPhysical security
A simulacrum security device and methods. In one embodiment, a simulacrum or likeness of a physical security device is provided for use in conjunction with a software emulation of the security device. In one implementation, a “faux SIM card” is provided that does not contain Subscriber Identification Module (SIM) information itself, but instead enables a user to download Electronic SIM (eSIM) information (e.g., from a network or eSIM server) which is loaded into a software emulation of a Universal Integrated Circuit Card (UICC) device. The faux card is printed with an activation code, scan pattern, or other activation or access information. The subscriber purchases the faux card, and enters the activation code into a device; the entered activation code enables the device to log onto a network, and download the appropriate eSIM data. Delivery of eSIM information as enabled by the faux card addresses deficiencies in existing SIM distribution schemes, provides users with an enhanced perception of security, and further addresses various legal requirements.
Owner:APPLE INC
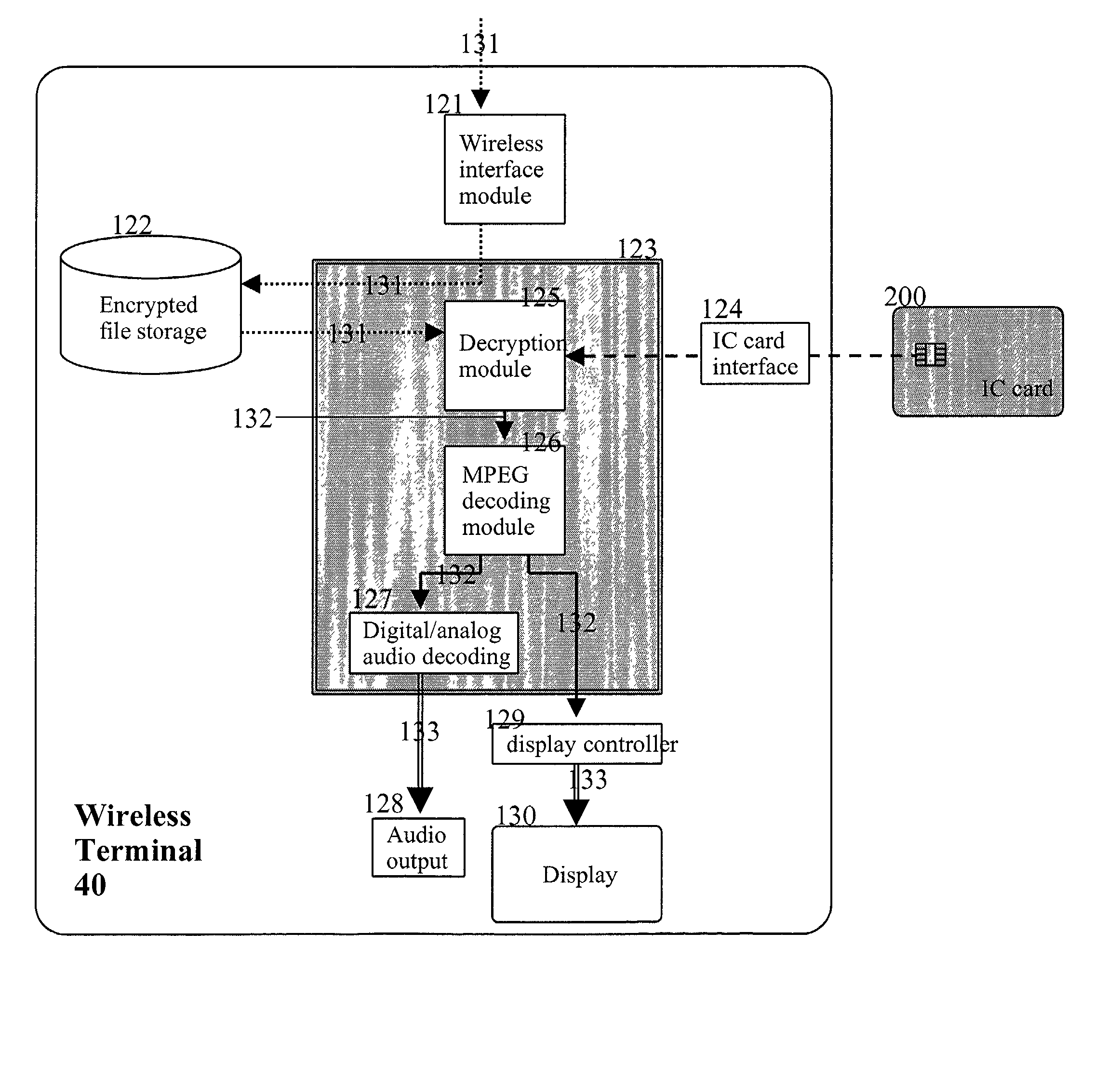
Method for providing multimedia files and terminal therefor
InactiveUS20020076051A1Easy accessMechanically effected encryptionPayment architectureComputer hardwareData file
A method of and a system for securely distributing data files to a user. A first key is encrypted using a second key. The encrypted first key is stored on an integrated circuit card that is associated with the user. The integrated circuit card is provided to the user. Data files are encrypted using the first key to get an encrypted data file at a first party. The encryption parameters are exchanged between the first party and integrated circuit card.
Owner:NOKIA TECHNOLOGLES OY
Integrated circuit card comprising files classified in a tree structure
InactiveUS6216204B1Memory adressing/allocation/relocationPayment architectureOperating systemTree structure
An IC card includes card including a memory containing files classified in a tree structure of various levels, each file having an associated access path. Each file is physically located in the memory independently of its location in the virtual tree structure, and contains information specifying the full access path associated with the file.
Owner:GEMPLU
System and Method for Remote Security Management of a User Terminal Via a Trusted User Platform
InactiveUS20070294744A1Easily and safely takeMemory loss protectionError detection/correctionSupporting systemData terminal
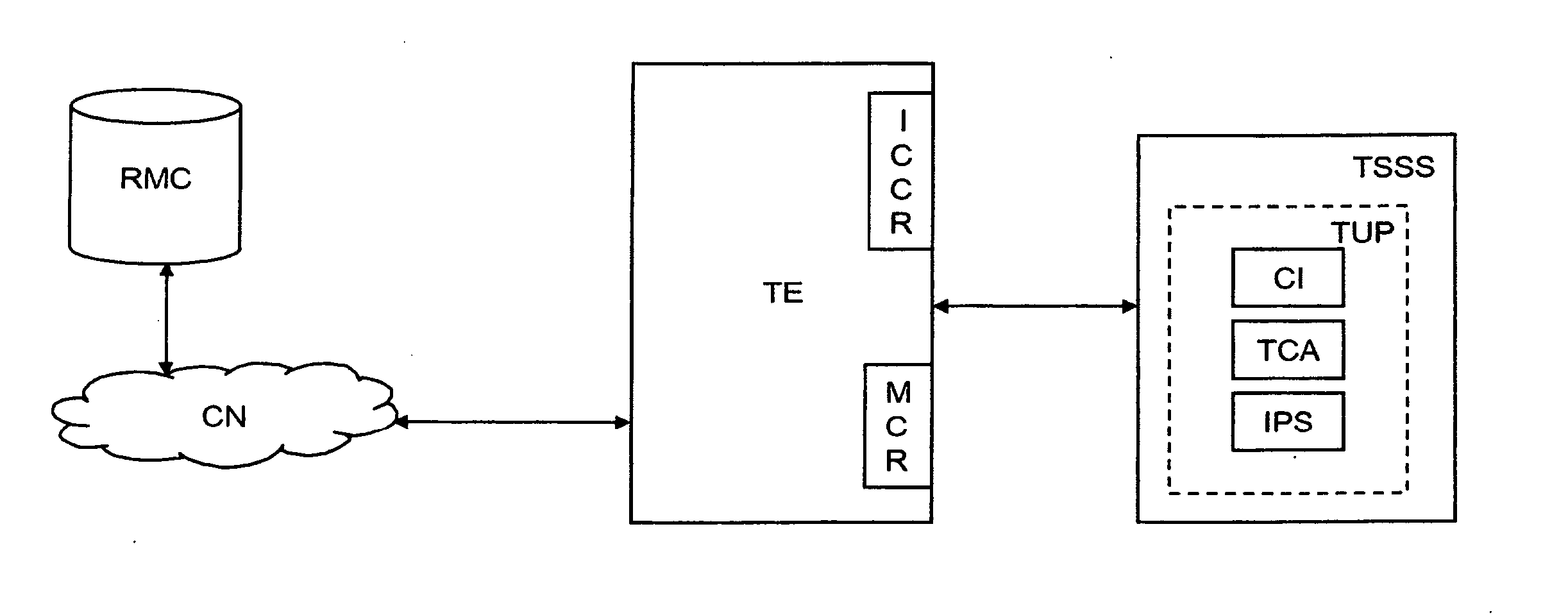
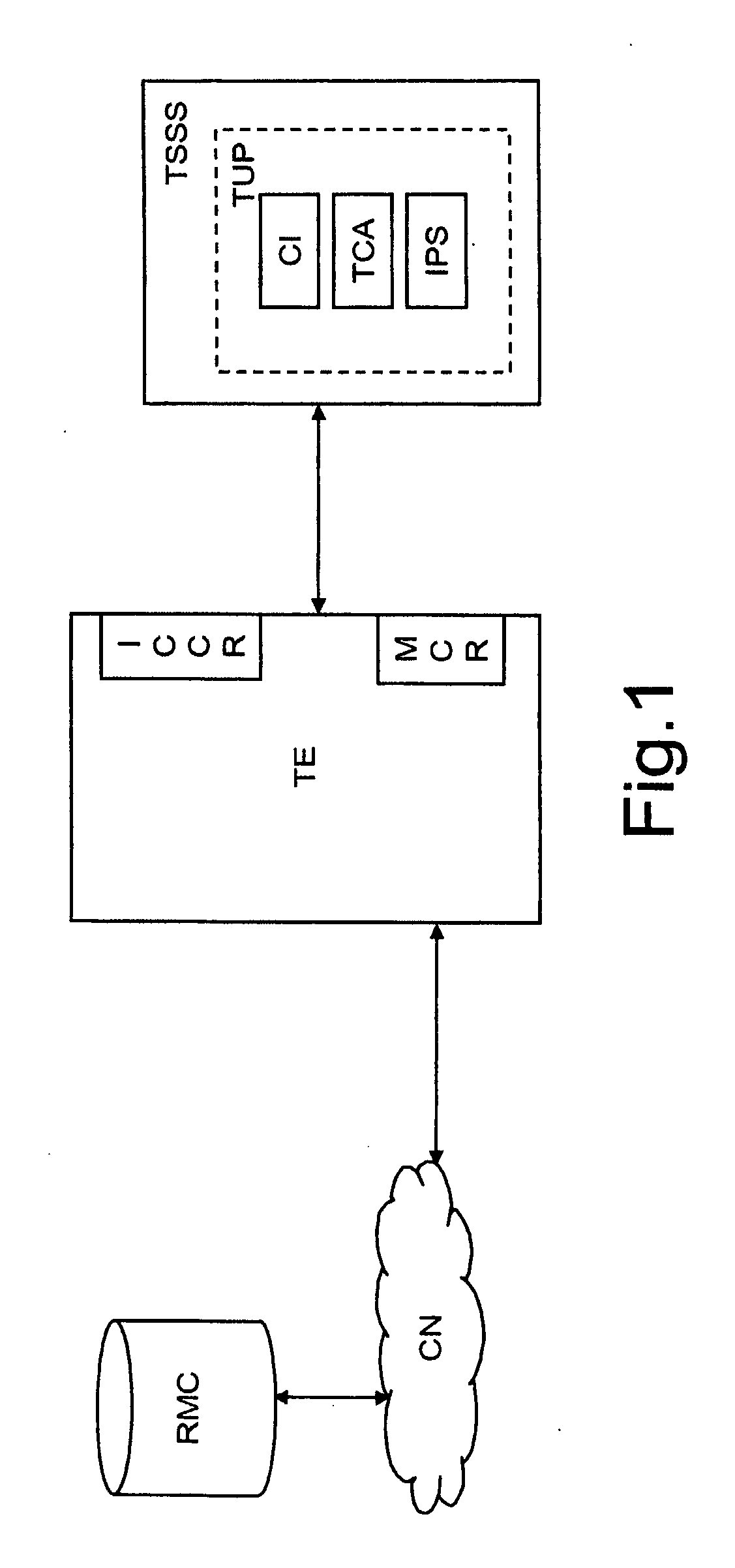
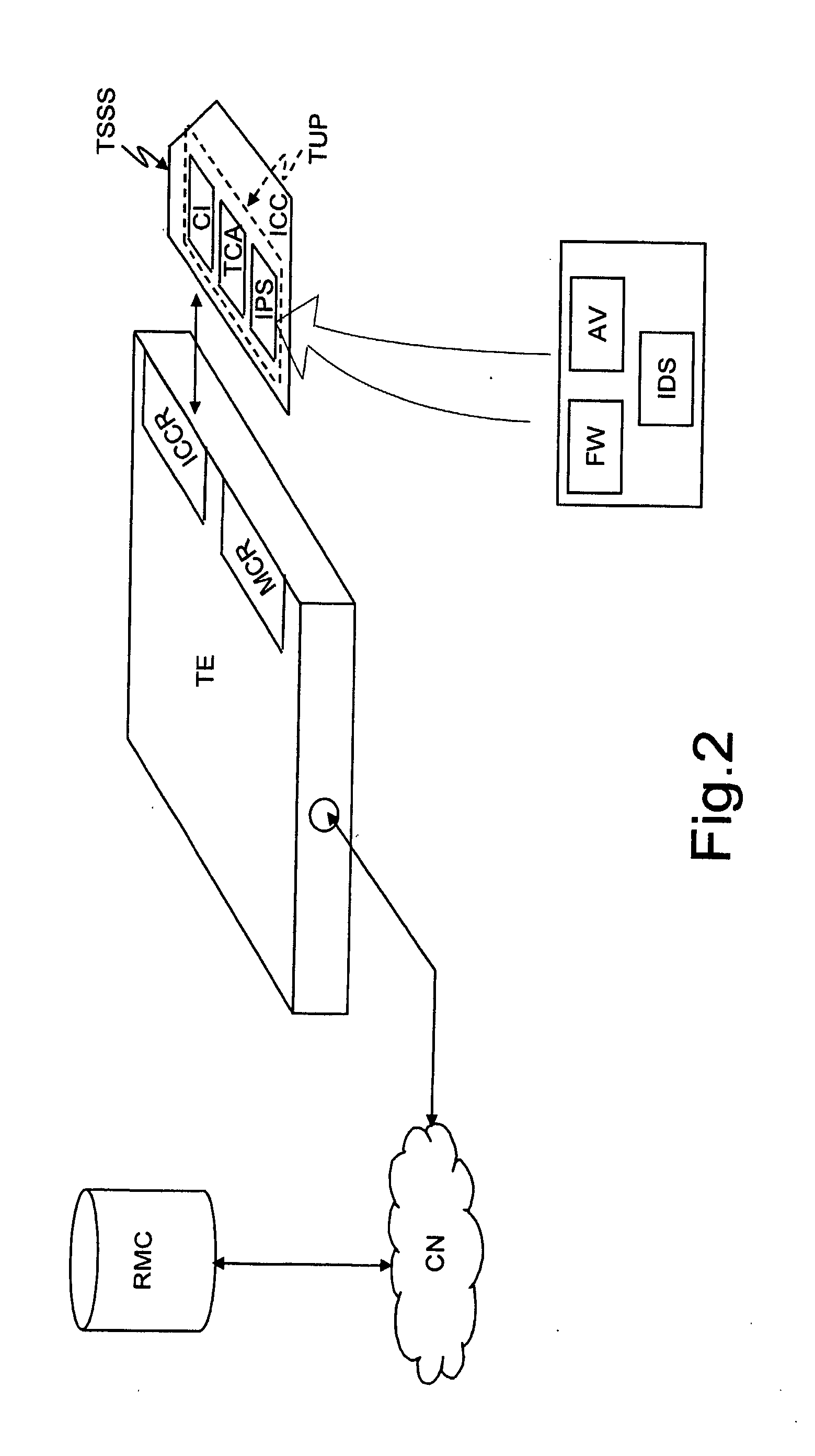
A user system includes terminal equipment configured to receive and send data through a communication network; a terminal security support system removably insertable in, and configured to cooperate with, the terminal equipment; and a trusted user platform for the terminal equipment. The trusted user platform includes an information protection system configured to implement security functionalities, configuration instances for the information protection system, and a trusted communication agent configured to provide a safe communication between the terminal security support system and a remote management centre through the terminal equipment to allow the information protection system to be remotely configured from the remote management centre. The terminal security support system includes an integrated circuit card and / or a memory card which wholly supports the trusted user platform, and the terminal equipment is configured to send data to be subjected to security control to, and to receive security-controlled data from, the trusted user platform.
Owner:TELECOM ITALIA SPA
Methods and apparatus for providing management capabilities for access control clients
InactiveUS20130122864A1Satisfies needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSoftware updateClient-side
Methods and apparatus for managing access control clients (e.g., electronic Subscriber Identity Modules (eSIMs)). In one embodiment, secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs)) and management entities of secure elements are associated with credentials. Post-deployment managerial operations can be executed, by transmitting the requested operation with the appropriate credentials. For example, a device can receive secure software updates to electronic Subscriber Identity Modules (eSIMs), with properly credentialed network entities.
Owner:APPLE INC
Embedded Universal Integrated Circuit Card Supporting Two-Factor Authentication
ActiveUS20150163056A1Increase flexibilityLow costKey distribution for secure communicationSecurity arrangementPlaintextComputer hardware
A module with an embedded universal integrated circuit card (eUICC) can include a profile for the eUICC. The profile can include a first and second shared secret key K for authenticating with a wireless network. The first shared secret key K can be encrypted with a first key, and the second shared secret key K can be encrypted with a second key. The module can (i) receive the first key, (ii) decrypt the first shared secret key K with the first key, and (iii) subsequently authenticate with the wireless network using the plaintext first shared secret key K. The wireless network can authenticate the user of the module using a second factor. The module can then (i) receive the second key, (ii) decrypt the second shared secret key K, and (iii) authenticate with the wireless network using the second shared secret key K. The module can comprise a mobile phone.
Owner:NIX JOHN A +1
Method of and a system for distributing electronic content
A terminal device, a memory module and a system for and method of distributing electronic content. A content provider stores a number of multimedia files. A first integrated circuit card interface receives a host integrated circuit card containing first authorization information, and a second integrated circuit card interface receives a user integrated circuit card containing second authorization information. An input device permits selection of one or more multimedia files from the stored of multimedia files. A control unit is responsive to insertion into the second integrated circuit card interface of a user interface card containing second authorization information compatible with the first authorization information contained in a host integrated circuit card inserted in the first integrated circuit card interface to actuate an output device to provide the content of multimedia files selected by the input device. The content provider, control unit, input device, and output device might be a laptop computer, a wireless personal terminal, or a personal computer. The multimedia content delivery system might be provided in a kiosk in a public place, permitting a user to wirelessly download an electronic copy of the selected media to a laptop computer or wireless personal terminal.
Owner:NOKIA TECHNOLOGLES OY
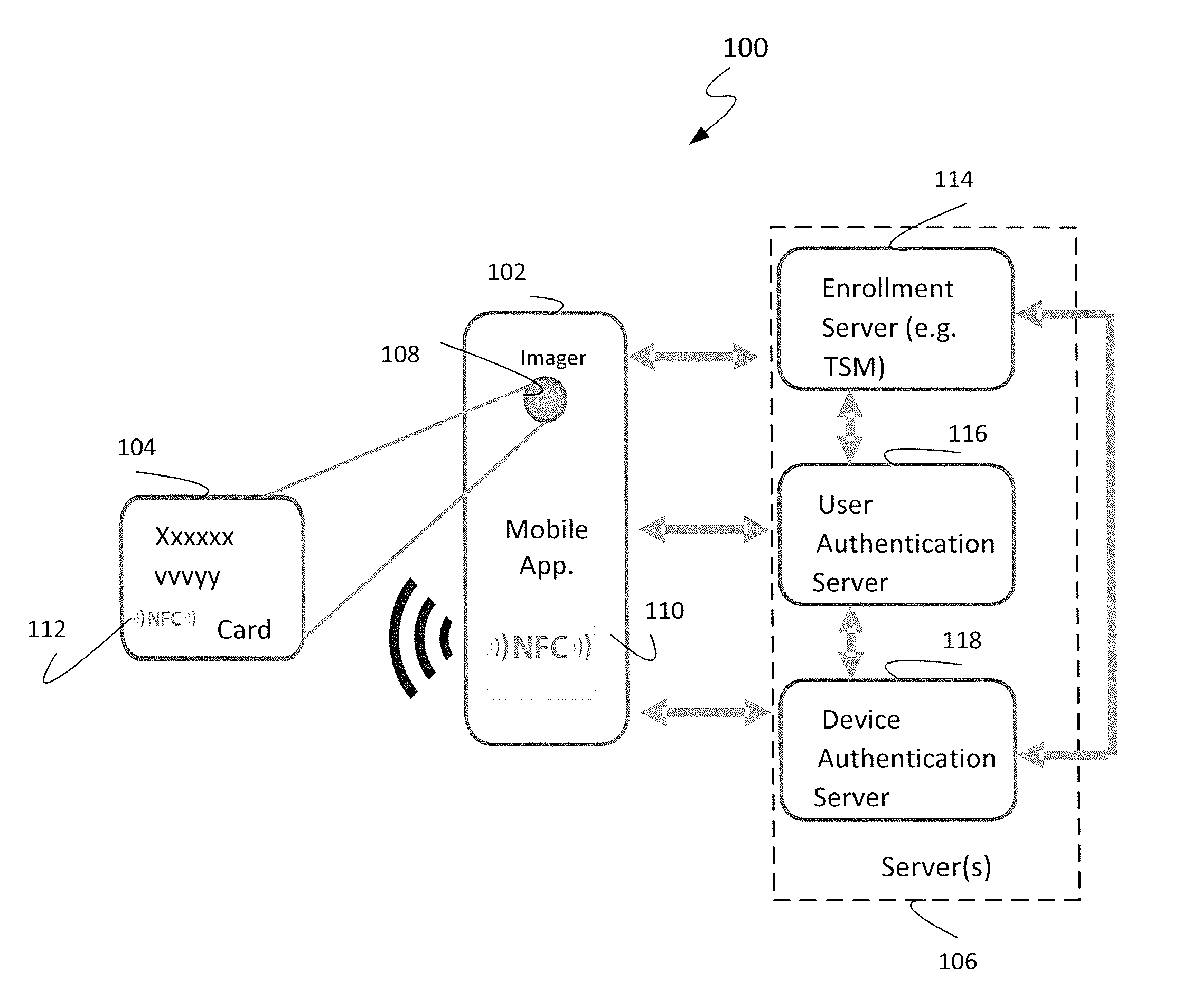
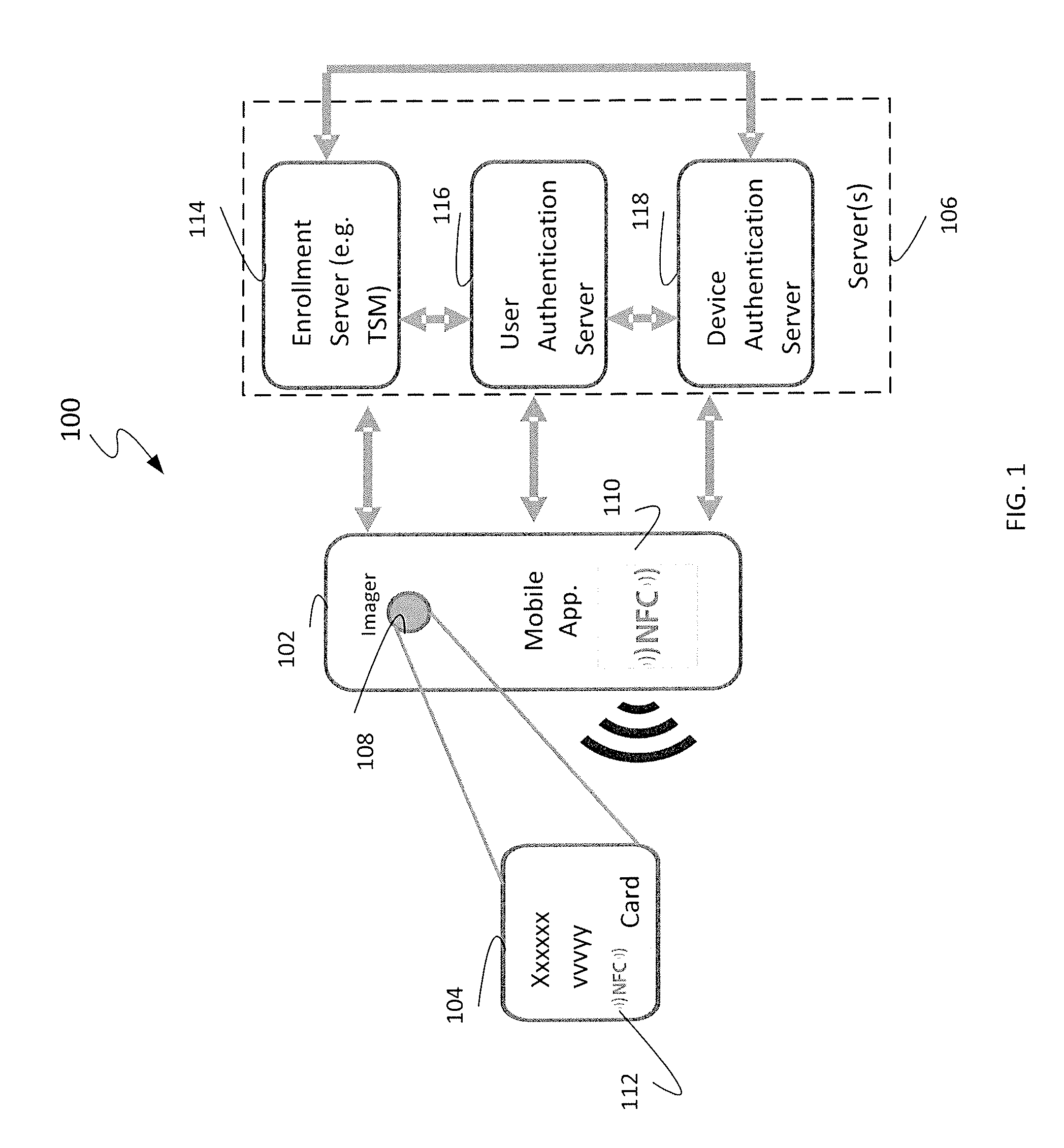
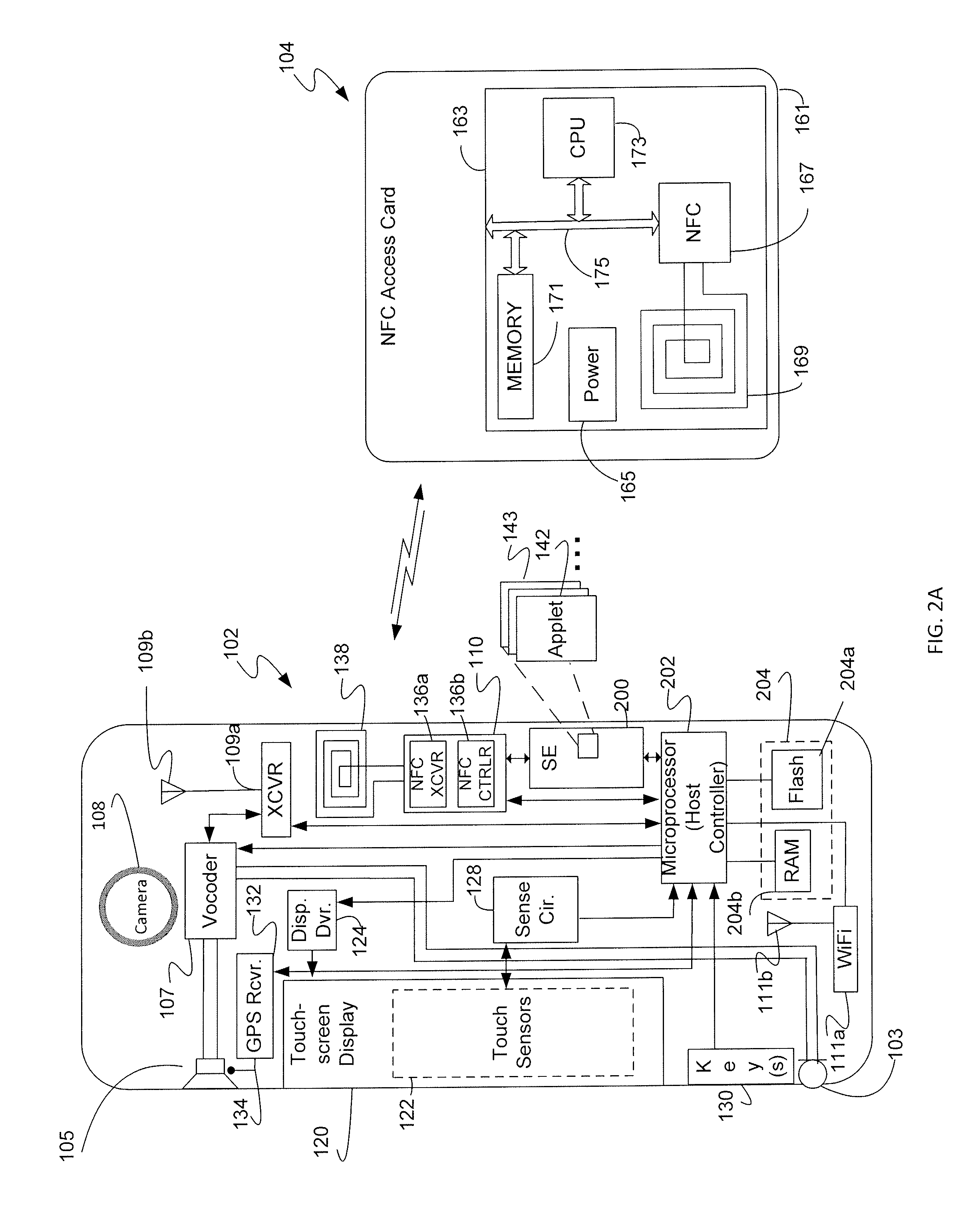
Express mobile device access provisioning methods, systems, and apparatus
ActiveUS20150004934A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsUser authenticationIntegrated circuit card
Methods, systems, and apparatus enable provisioning of a mobile device with access information for an account. A secure element within a subscriber identity module (SIM) or universal integrated circuit card (UICC) of the mobile device may be provisioned to enable account access. Provisioning may be performed by obtaining card data for a card associated with an account using an automated data capture device, confirming validity of the account by exchanging the card data with a user authentication server, confirming validity of the mobile device by exchanging mobile device information with a device authentication server, sending a request from the mobile device to provision the mobile device after confirming validity of the account and the mobile device, receiving provisioning instructions to provision the mobile device with the access information for the account, and provisioning the mobile device with the access information for the account based on the provisioning instructions.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS
Apparatus and methods for distributing and storing electronic access clients
ActiveUS20120260086A1Efficiently distributedEffective controlPublic key for secure communicationUser identity/authority verificationElectronic accessBottle neck
Apparatus and methods for efficiently distributing and storing access control clients within a network. In one embodiment, the access clients include electronic Subscriber Identity Modules (eSIMs), and an eSIM distribution network infrastructure is described which enforces eSIM uniqueness and conservation, distributes network traffic to prevent “bottle necking” congestion, and provides reasonable disaster recovery capabilities. In one variant, eSIMs are securely stored at electronic Universal Integrated Circuit Card (eUICC) appliances which ensure eSIM uniqueness and conservation. Access to the eUICC appliances is made via multiple eSIM depots, which ensure that network load is distributed. Persistent storage is additionally described, for among other activities, archiving and backup.
Owner:APPLE INC
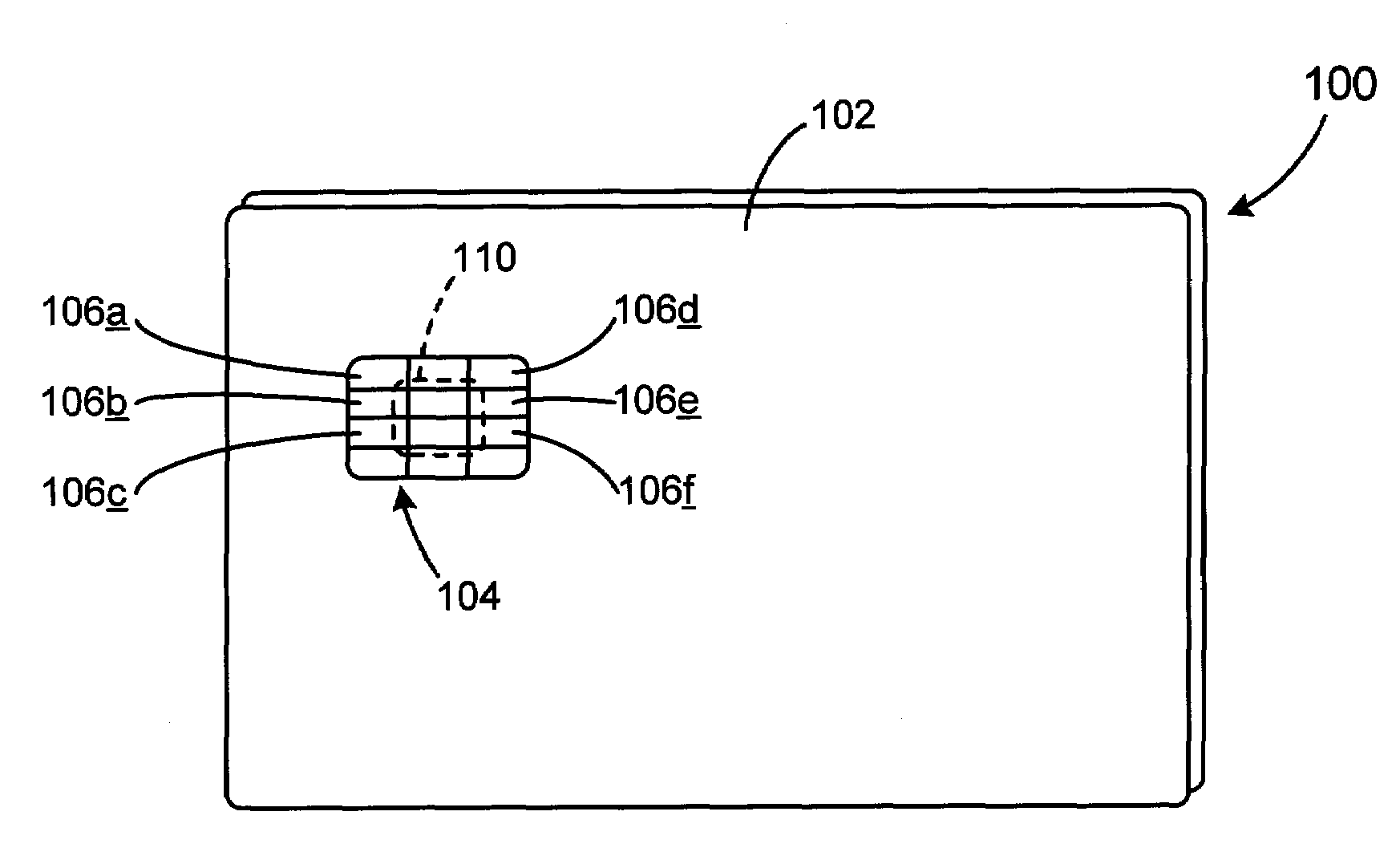
Integrated circuit card having staggered sequences of connector terminals
InactiveUS6945465B2Prevent electrostatic dischargeEasy to solveOther printing matterElectrically conductive connectionsEngineeringSemiconductor
An IC card has a card substrate having semiconductor integrated circuit chips mounted thereon and a plurality of connector terminals formed thereon. The connector terminals are exposed from a casing. The connector terminals are laid out in plural sequences in staggered form between sequences adjacent to one another forward and backward as viewed in an IC card inserting direction. Owing to the adoption of the staggered layout, a structure or configuration wherein the amounts of protrusions of socket terminals of a card socket are changed and the socket terminals are laid out in tandem, can be adopted with relative ease. If a connector terminal arrangement of a downward or low-order IC card is adopted as a specific connector terminal sequence as it is, whereas a function dedicated for an upward or high-order IC card is assigned to another staggered connector terminal arrangement, then backward compatibility can also be implemented with ease.
Owner:RENESAS ELECTRONICS CORP
Integrated circuit card programming modules, systems and methods
InactiveUS6695205B1Improve programming performanceSpace minimizationDigitally marking record carriersOther printing matterComputer moduleModularity
The invention relates to the programming of integrated circuit cards. More particularly, the invention concerns systems and methods for integrated circuit card programming, as well as modules used for integrated circuit card programming. Each module includes a movable cassette mechanism having a plurality of card programming stations thereon. The use of multiple card programming stations permits simultaneous programming of a plurality of cards. Further, the use of a single cassette in the module permits the size of the module to be reduced significantly. A modular concept is more readily adaptable to customer needs and requirements. For instance, if a customer requires more card production than that provided by a single module, a second module that is identical to the first module can be connected to the first module so that the two modules working together provide two cassettes. Additional modules can be added to further increase card production capacity.
Owner:ENTRUST CORP
Authentication
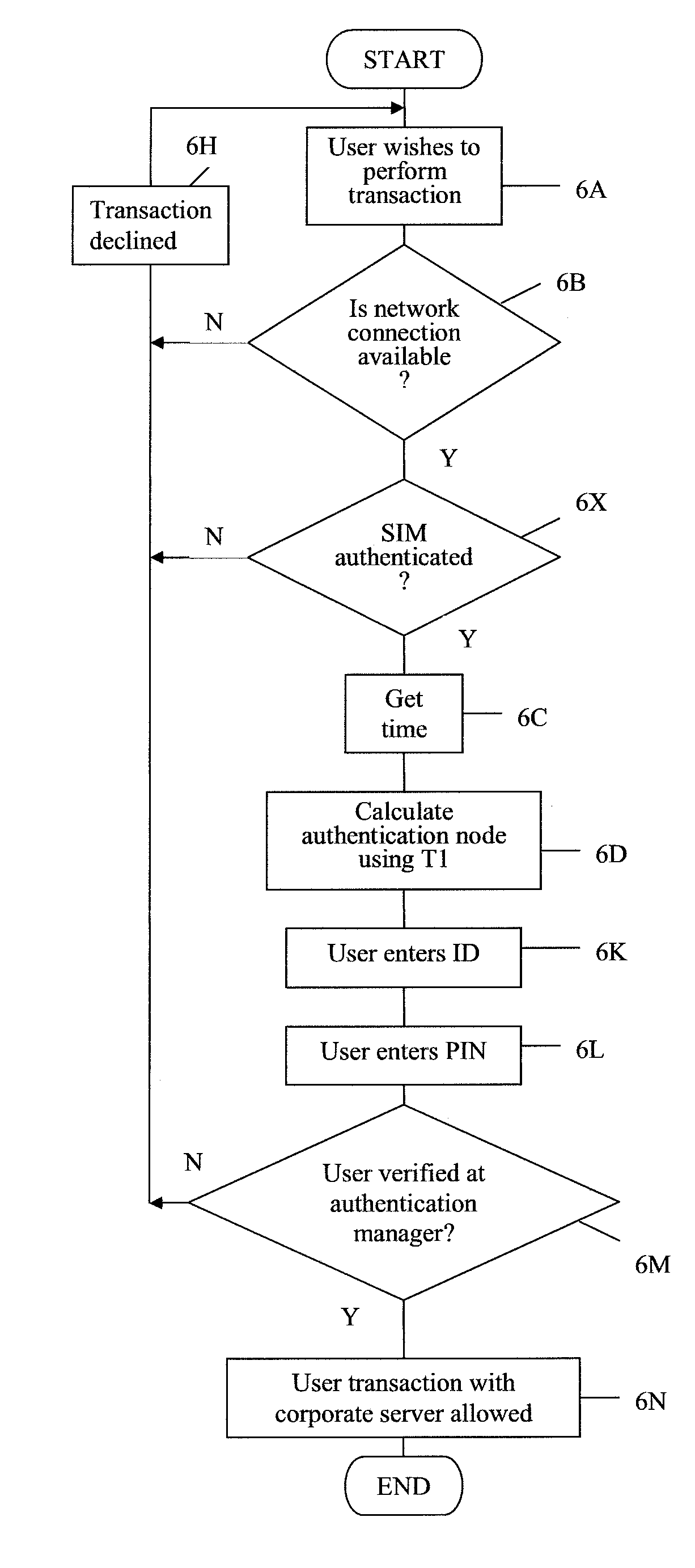
InactiveUS20120047563A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwarePassword
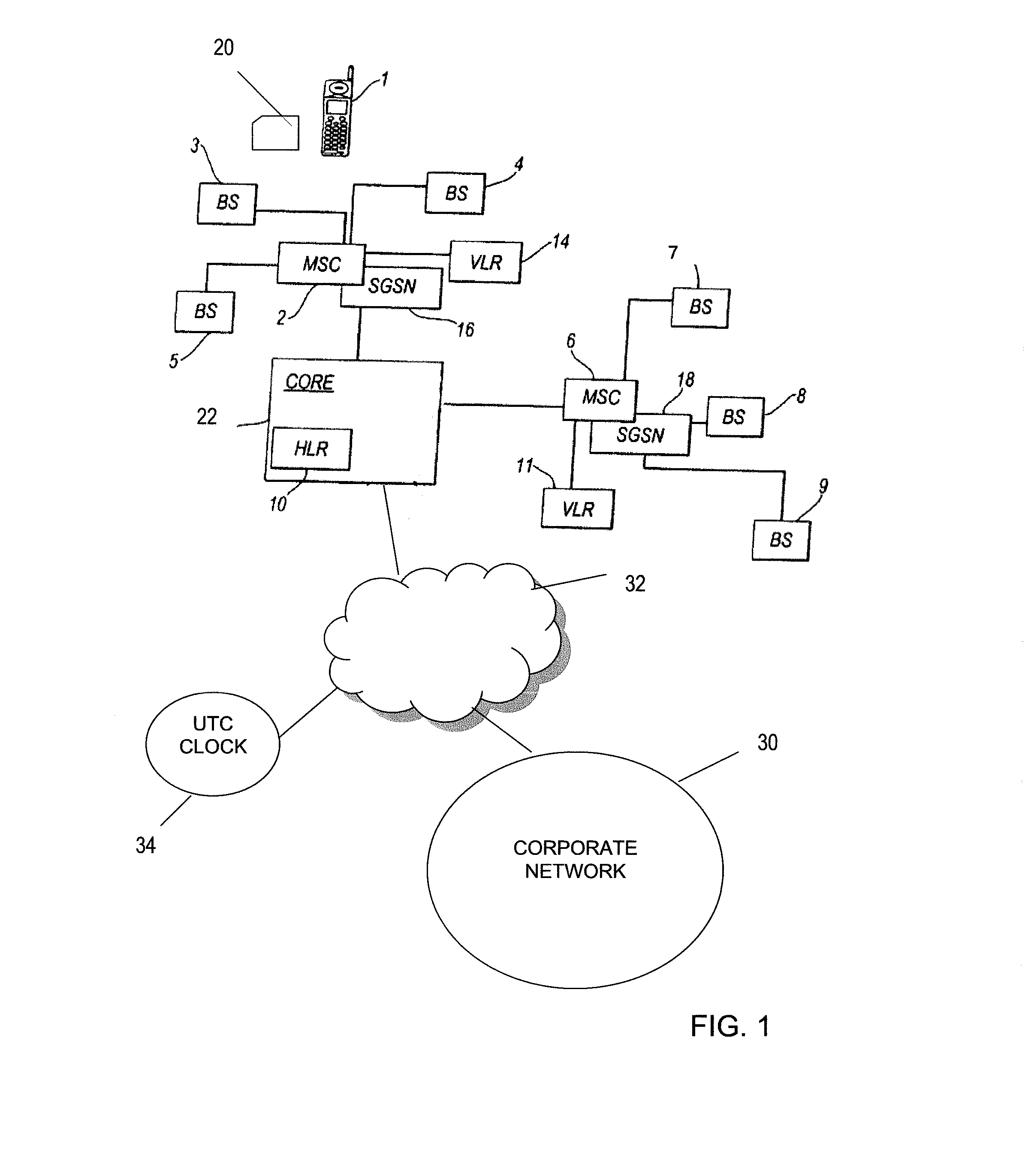
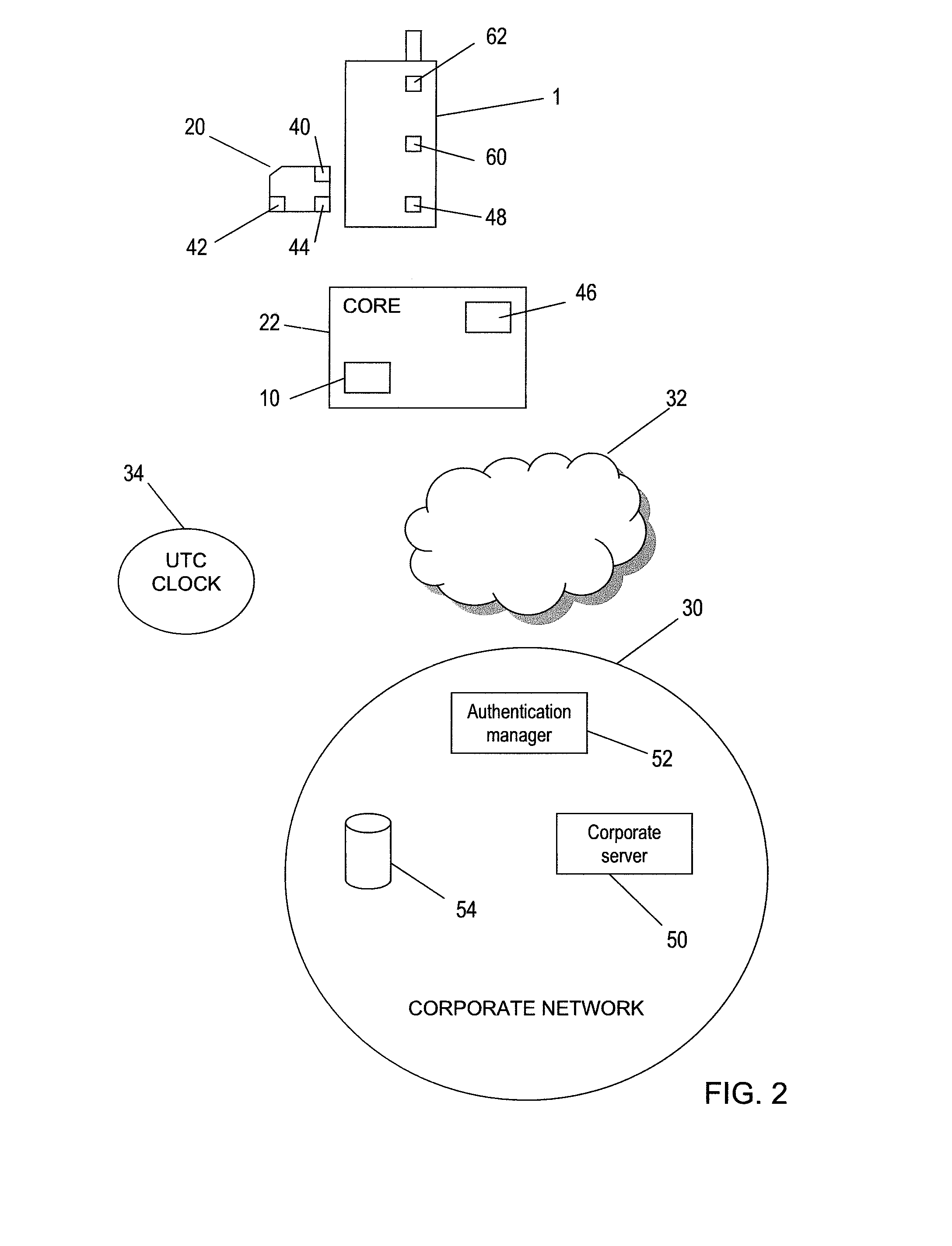
An arrangement for authenticating a transaction between a user's mobile device and an entity such as a corporate server is disclosed. The user's universal integrated circuit card (UICC) is adapted to generate a time-dependent authentication code which is dependent on a time value and which is usable to authenticate the transaction only during a predetermined period. A time verification processor verifies a time value to ensure that the time-dependent authentication code was generated based on the correct time value. The time value is based on the UTC time obtained from UTC clock. The verified time is used to generate a “one-time” password (authentication code) by the authentication code calculator of the UICC. This is used to authenticate a transaction with the corporate network.
Owner:VODAFONE IP LICENSING
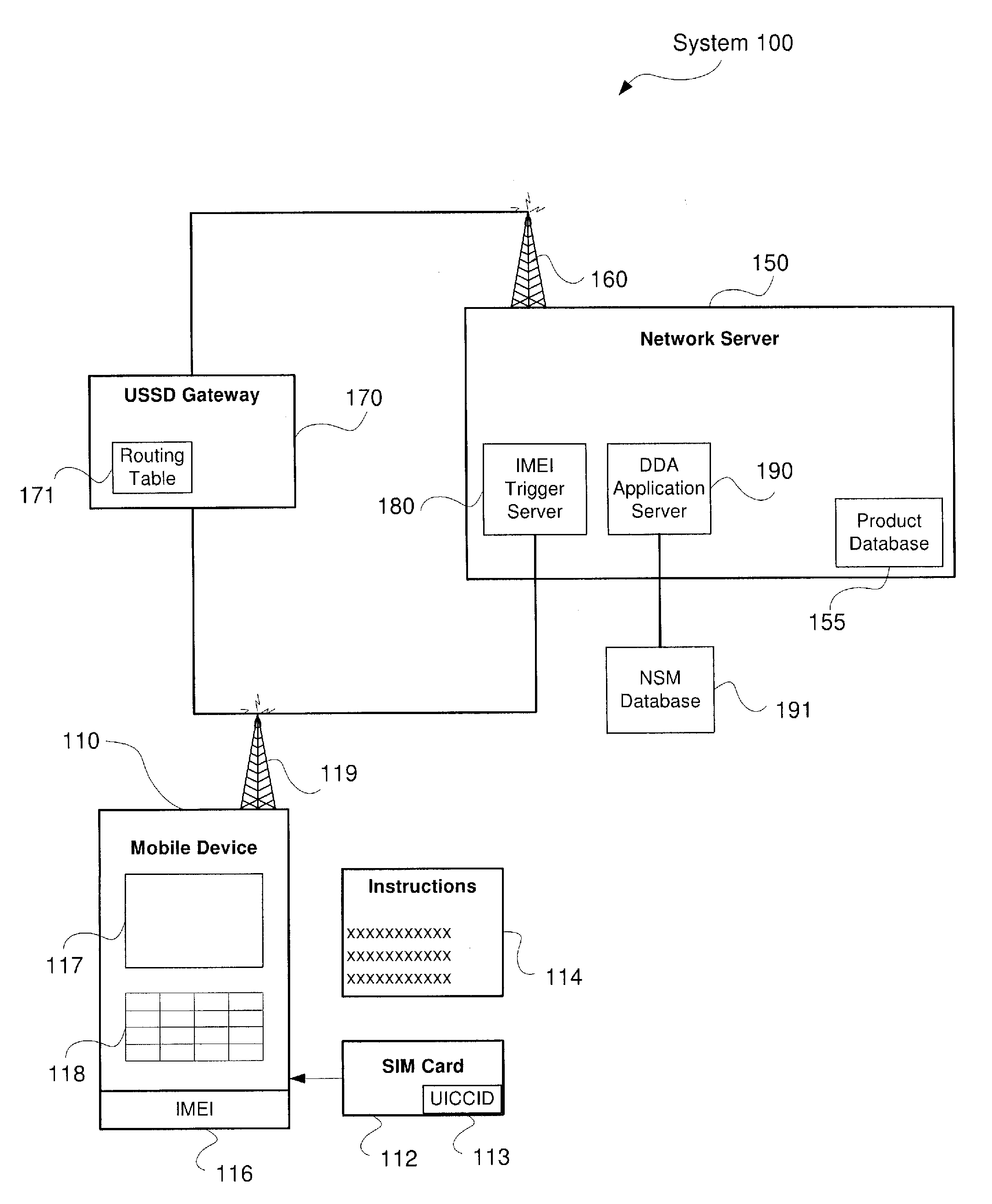
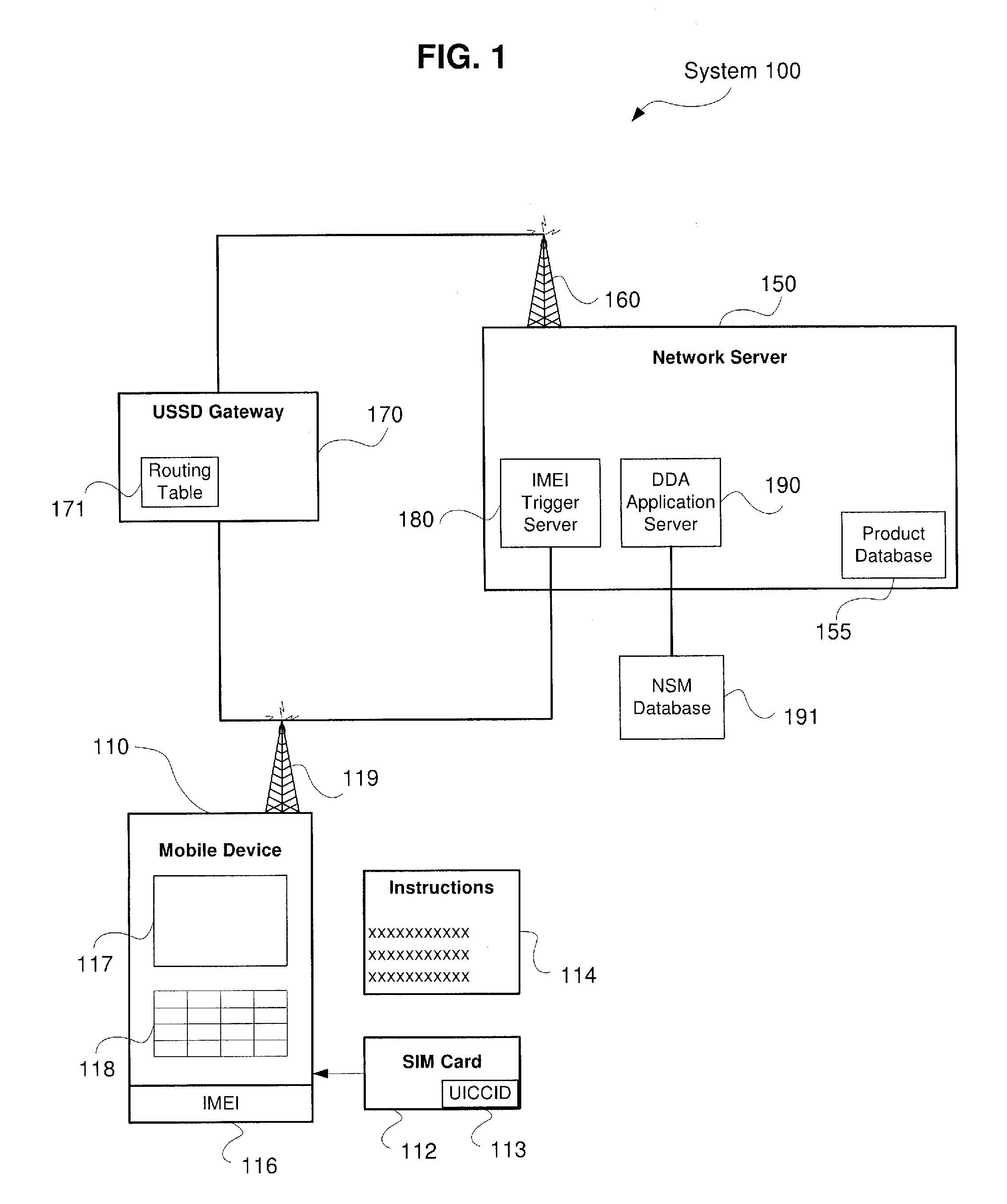
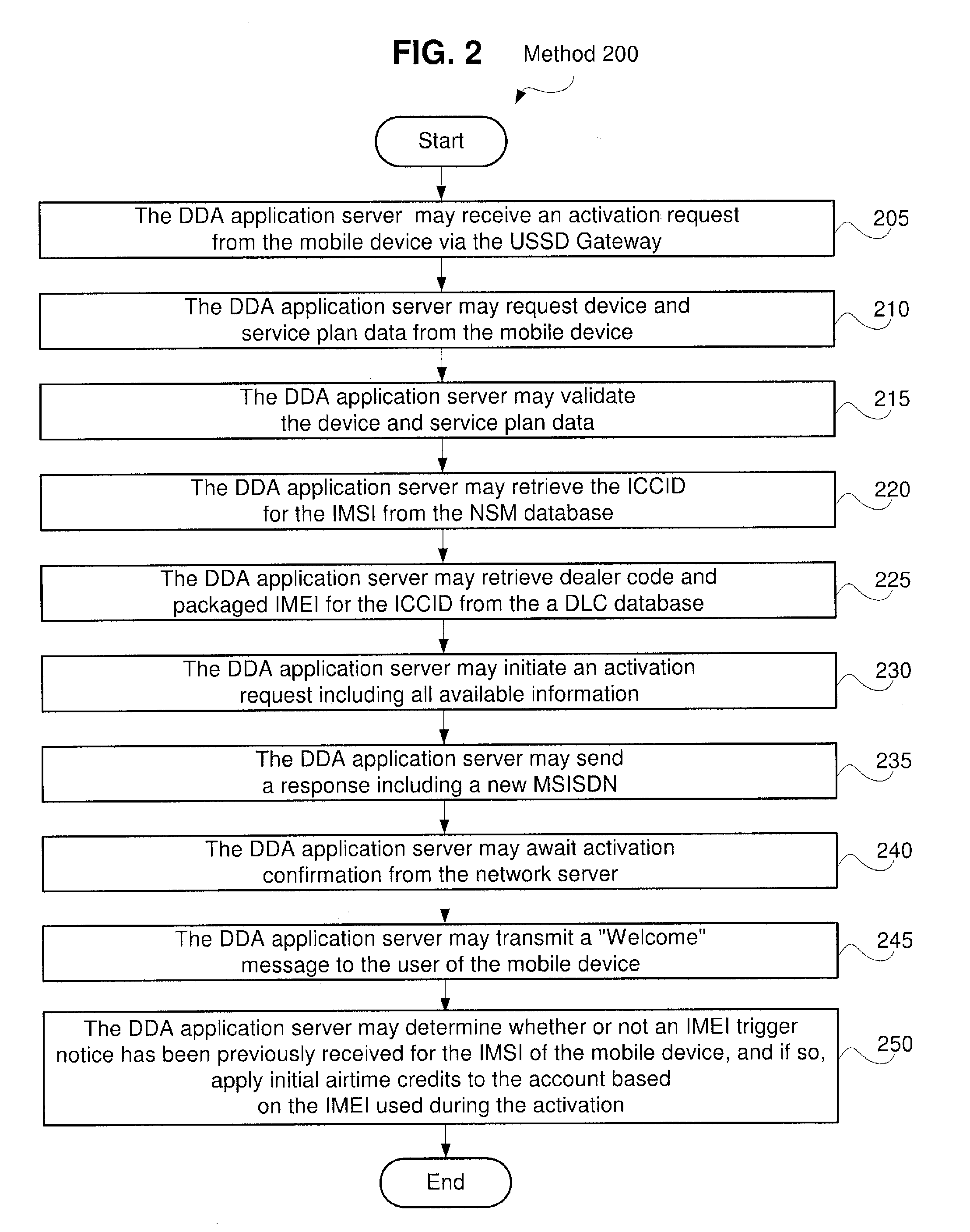
System and Method for Direct Device Activation
InactiveUS20110159843A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTransceiverBiological activation
Described herein are systems and methods for single-step direct activation of telecommunication services for a mobile device. One embodiment of the disclosure of this application is related to a system comprising a transceiver receiving product information from a mobile device and receiving service plan information from the mobile device, and a server verifying availability of service for the mobile device based on at least one of the product information and the service plan information, and activating telecommunication service with the mobile device. The received product information including an international mobile equipment identity (“IMEI”) number received from an IMEI trigger event and an international mobile subscriber identity (“IMSI”) number received from a pre-provisioned subscriber identity module (“SIM”) component. The server accesses a national SIM manager (“NSM”) database, wherein the NSM includes pre-populated pairing of IMSI numbers with corresponding integrated circuit card identification (“ICCID”) numbers, and the server further retrieves a corresponding ICCID number for the IMSI of the mobile device and including the corresponding ICCID number with the product information.
Owner:AT&T INTPROP I L P
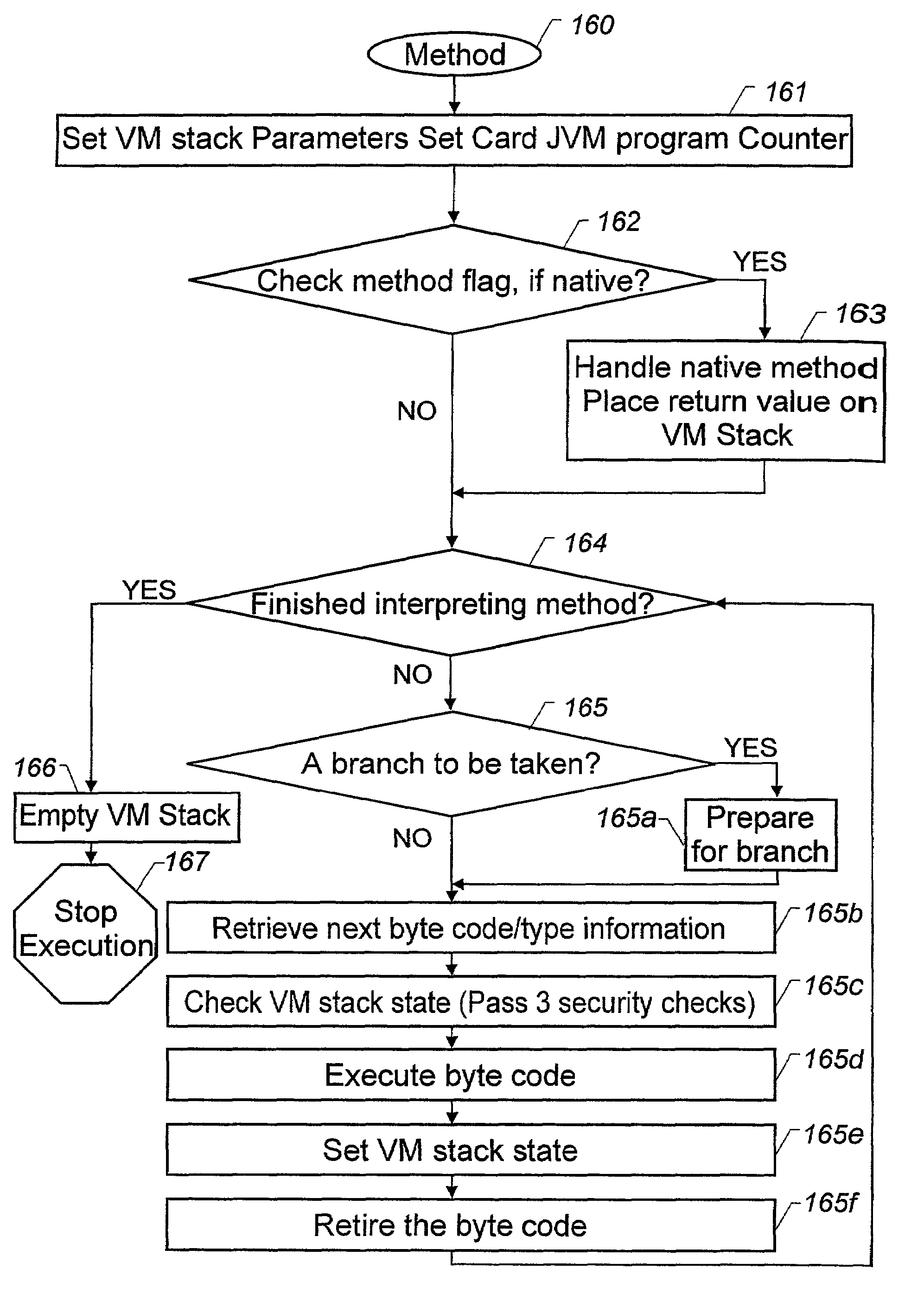
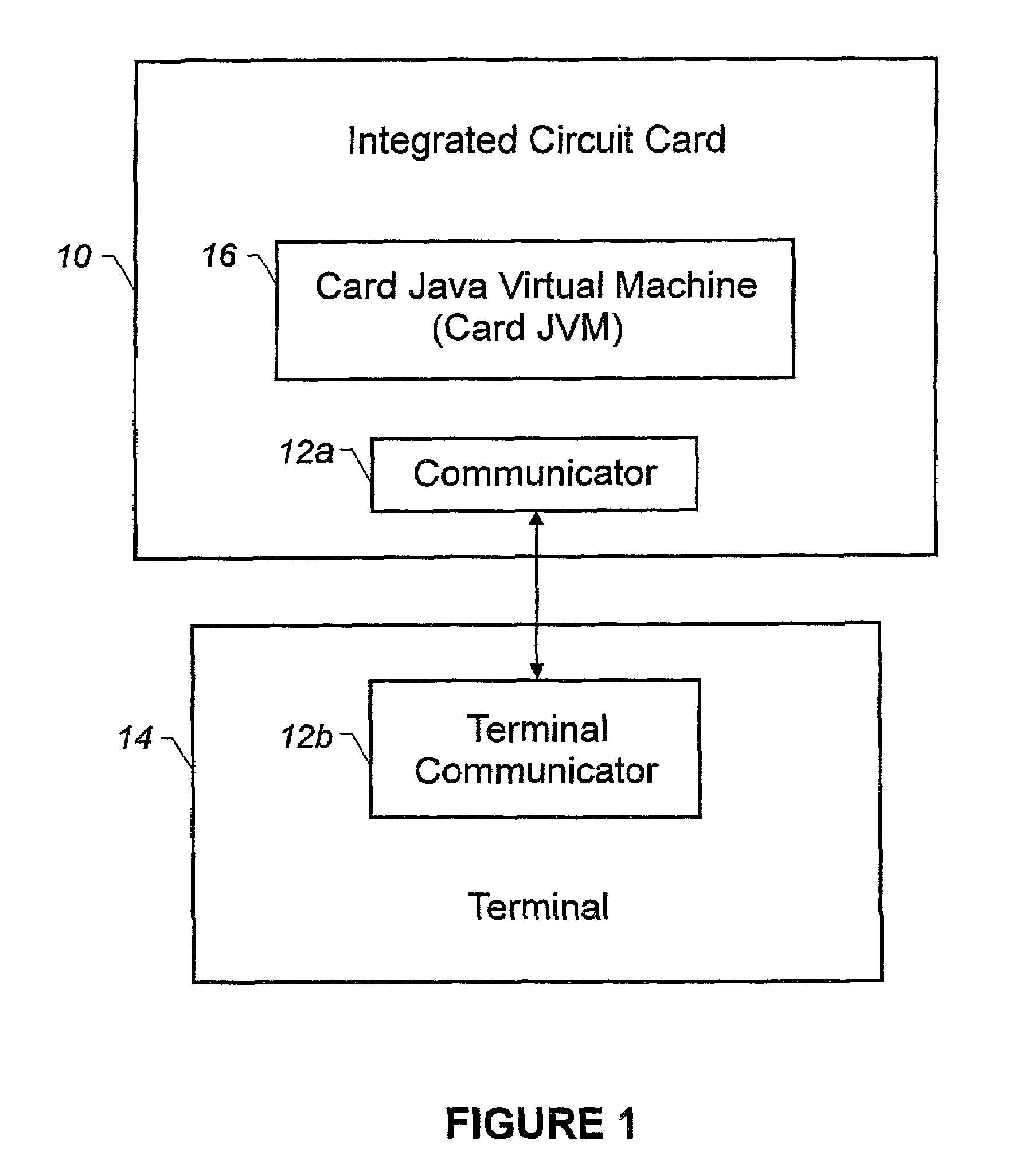
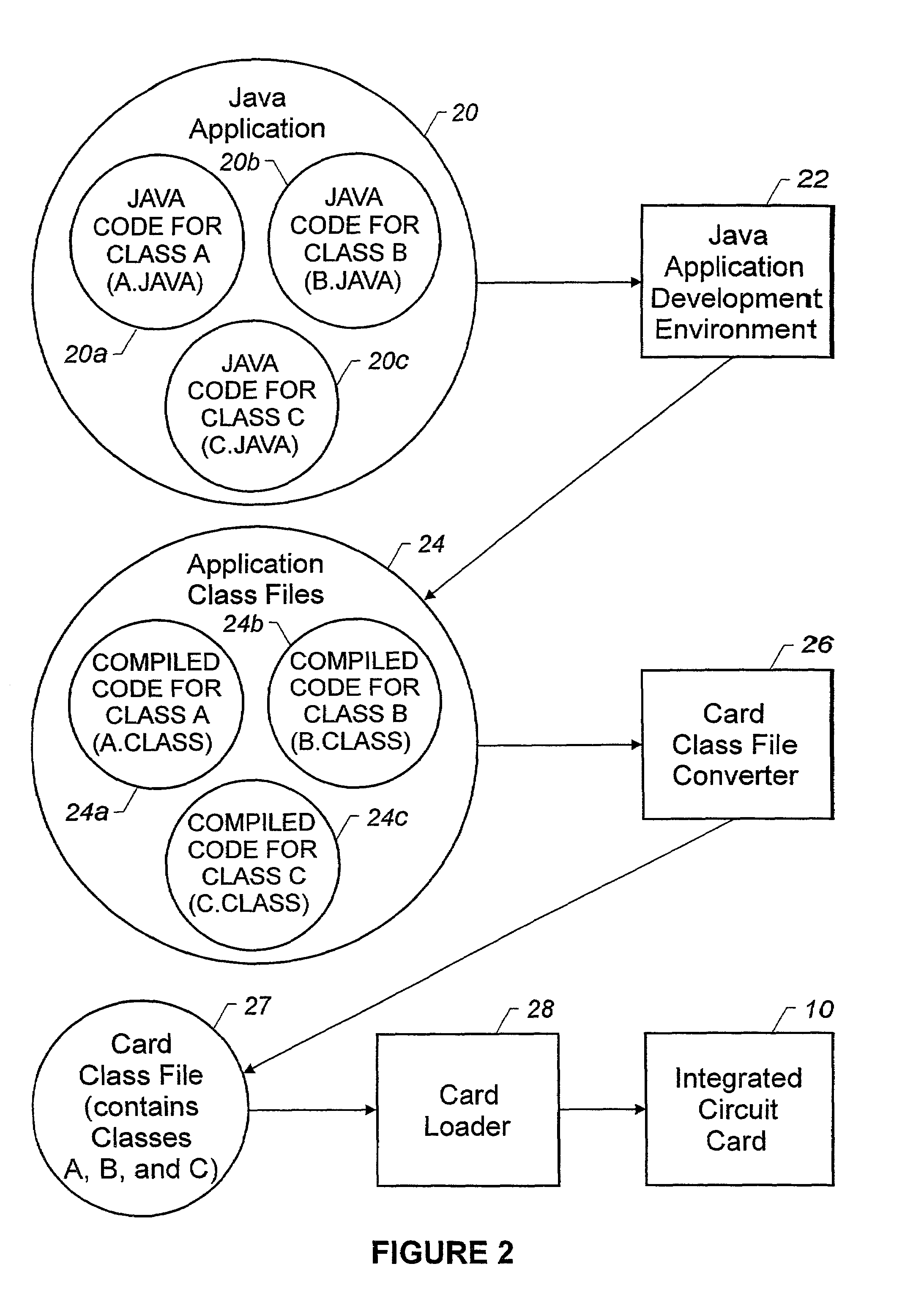
Using a high level programming language with a microcontroller
InactiveUS7117485B2Quickly prototypedFast downloadBinary to binaryProgram control using stored programsMicrocontrollerComputer terminal
An integrated circuit card is used with a terminal. The integrated circuit card includes a memory that stores an interpreter and an application that has a high level programming language format. A processor of the card is configured to use the interpreter to interpret the application for execution and to use a communicator of the card to communicate with the terminal.
Owner:GEMPLU
Apparatus and methods for selecting services of mobile network operators
ActiveUS20130340059A1Service provisioningUser identity/authority verificationComputer scienceMobile network operator
A system that incorporates teachings of the subject disclosure may include, for example, a method for detecting, by a first device including a least one processor and a first Universal Integrated Circuit Card (UICC), a second device having a second UICC, detecting, by the first device, that the second UICC is unprovisioned, selecting, by the first device, one of a plurality of selectable options, where the selection identifies a first network operator selected from a plurality of network operators, receiving, by the first device, first credential information of the first network operator, and transmitting, by the first device, to the second device the first credential information for enabling the second device to facilitate establishment of communication services with network equipment of the first network operator according to the first credential information. Other embodiments are disclosed.
Owner:AT&T MOBILITY II LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com