Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
59 results about "Internal identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internal identifier. If the identifier is used in an external link process, then it is called as external. These identifiers are also known as external names; include function names and global variable names that are shared between source files.
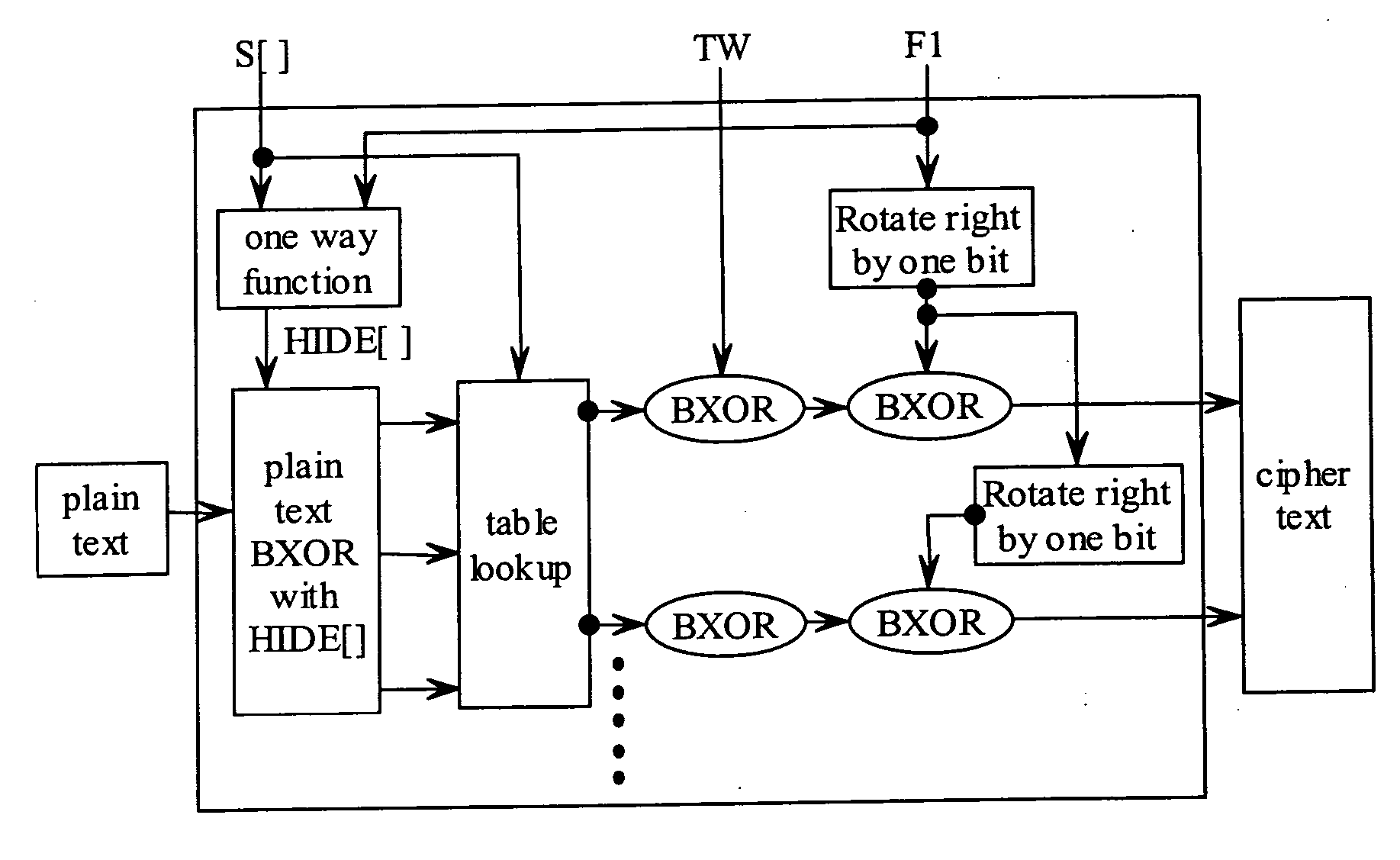
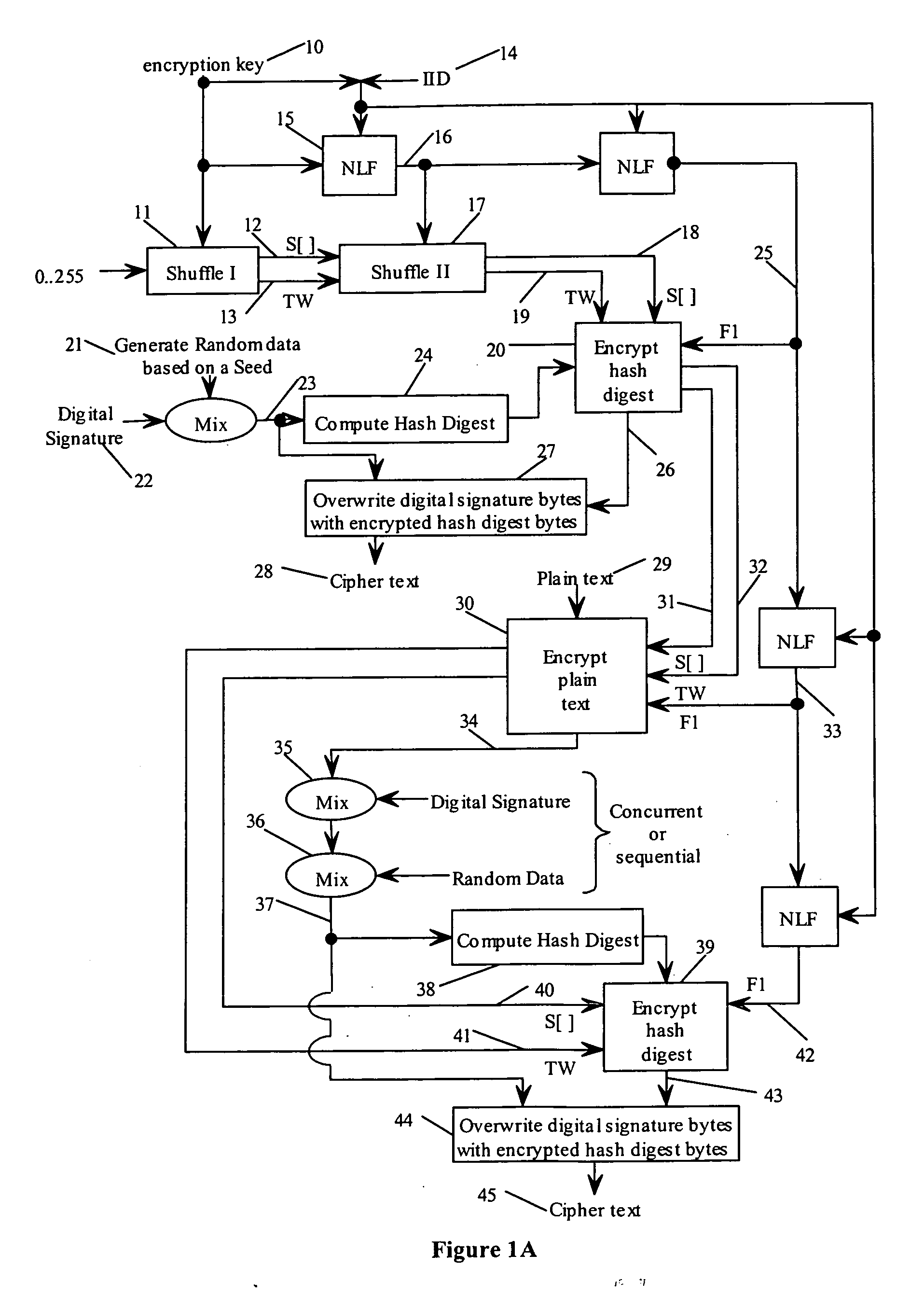
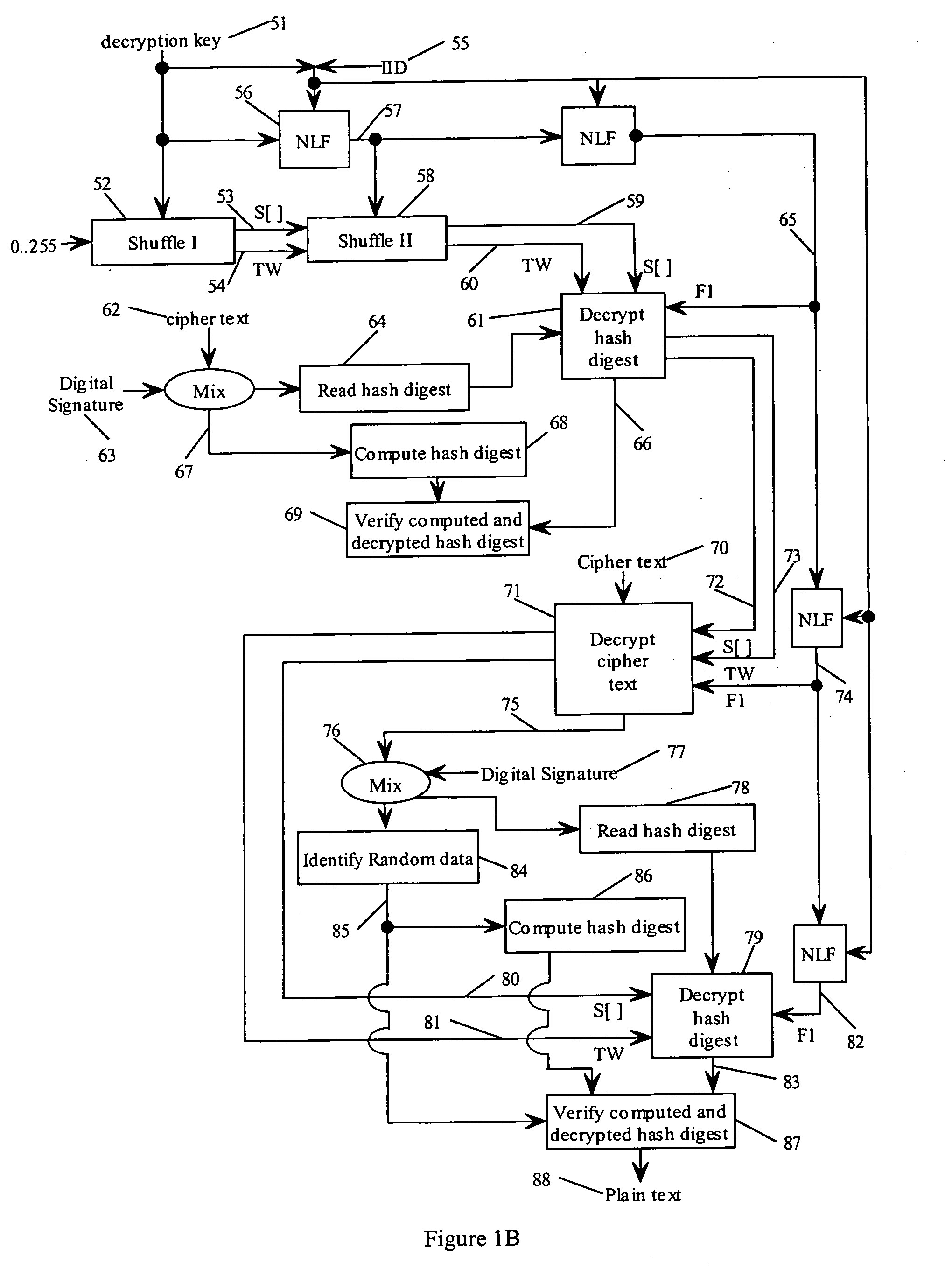
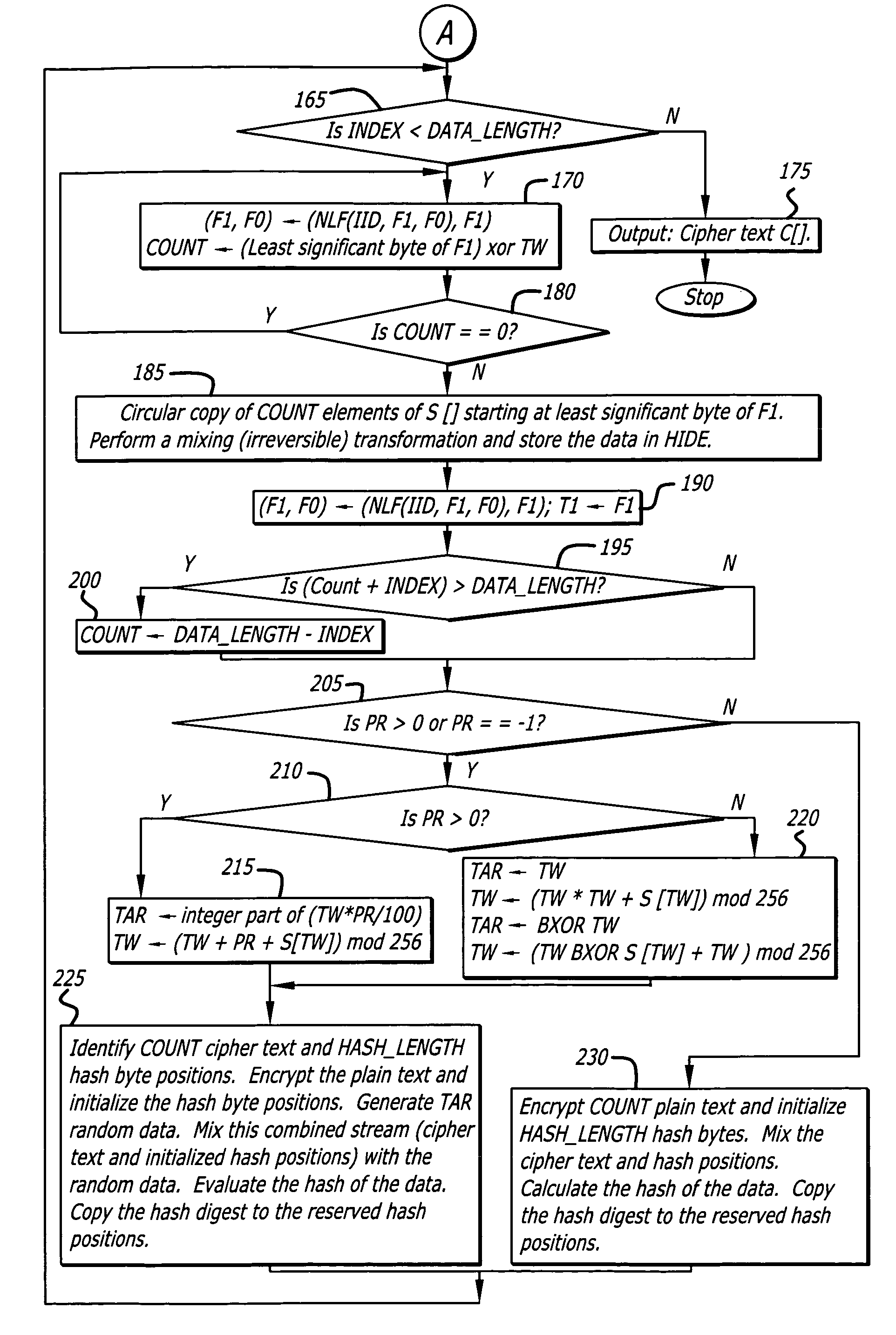
State-varying hybrid stream cipher
InactiveUS7103181B2Data stream serial/continuous modificationSecret communicationAlgorithmCiphertext
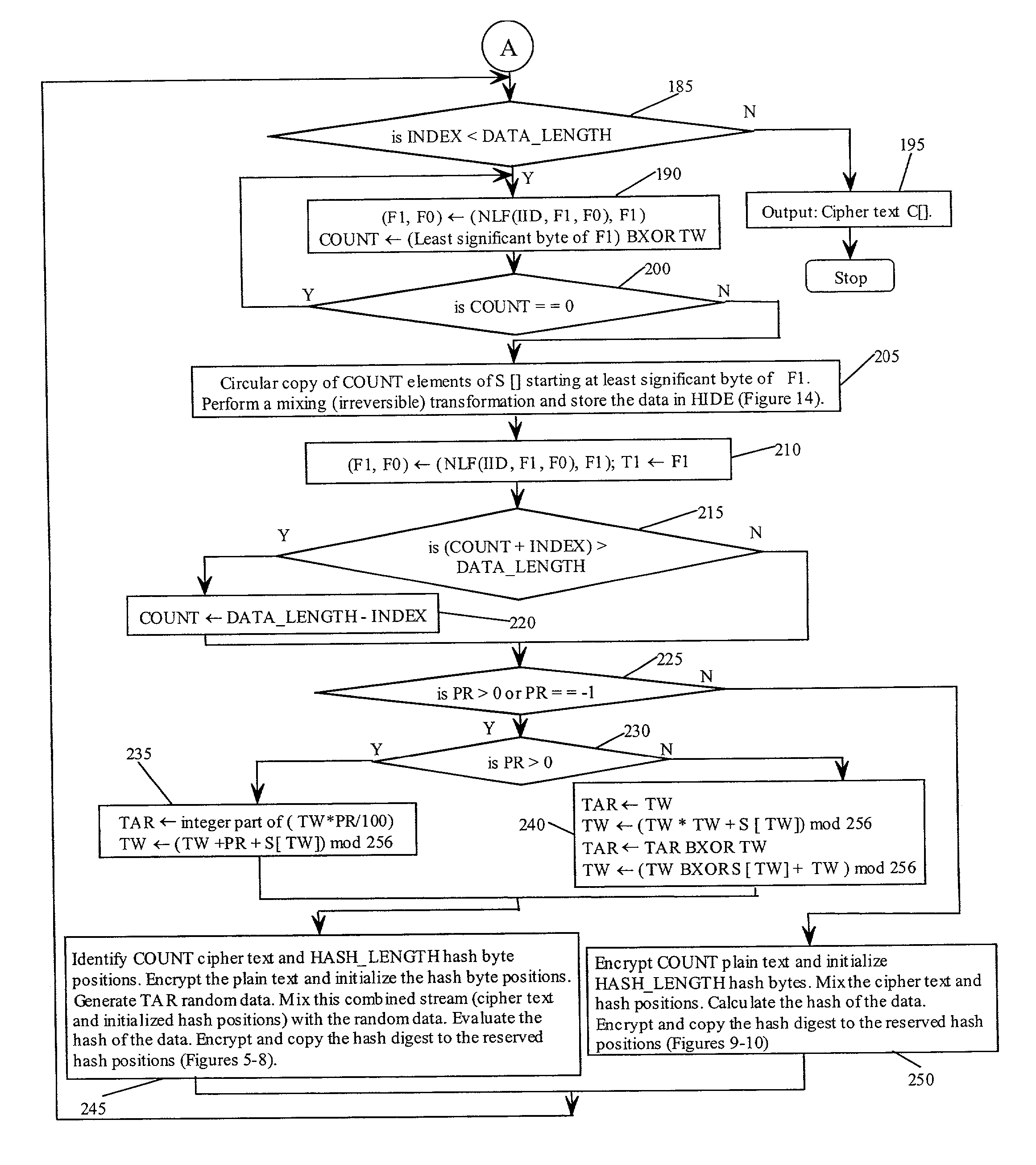
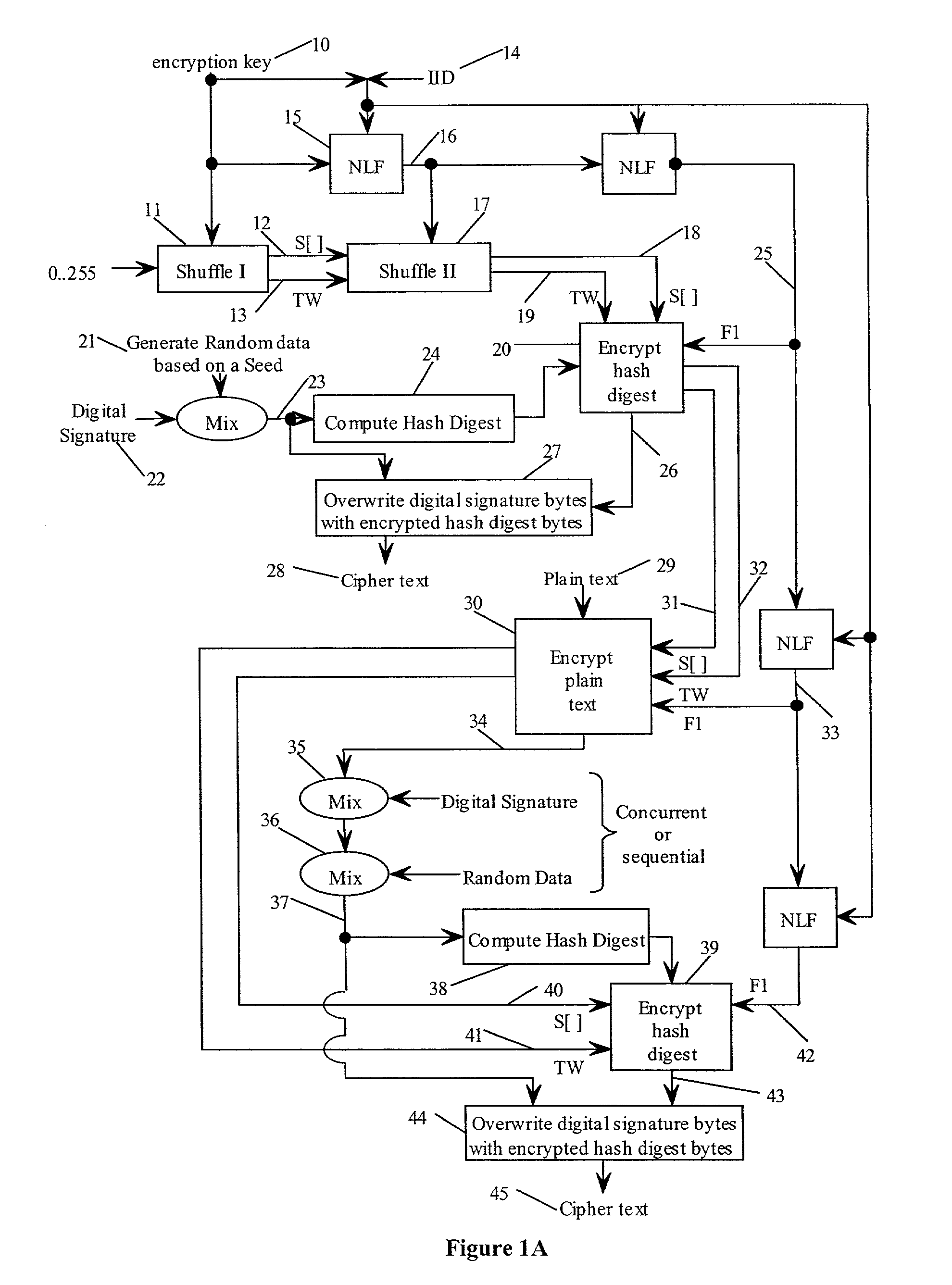
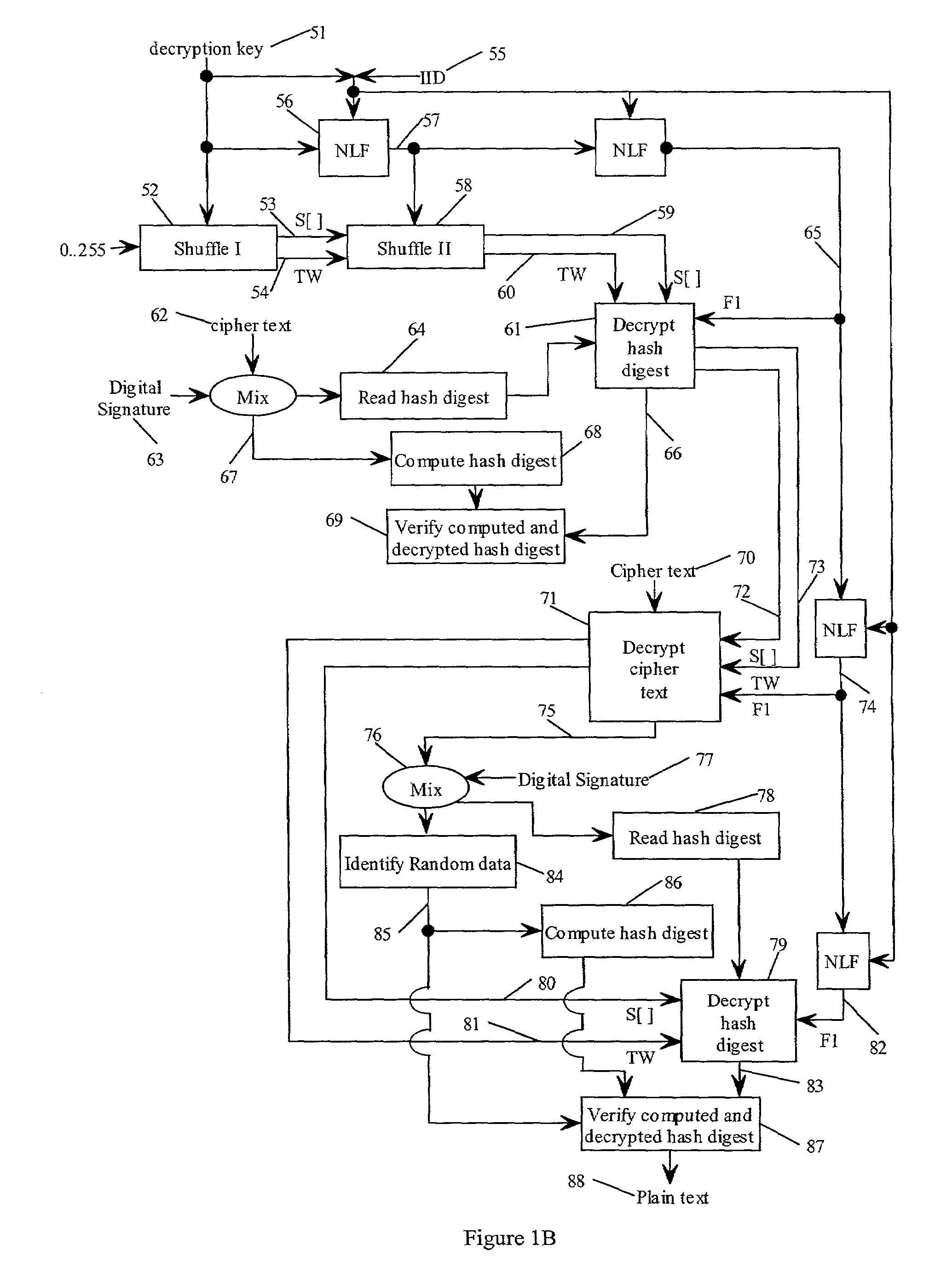
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
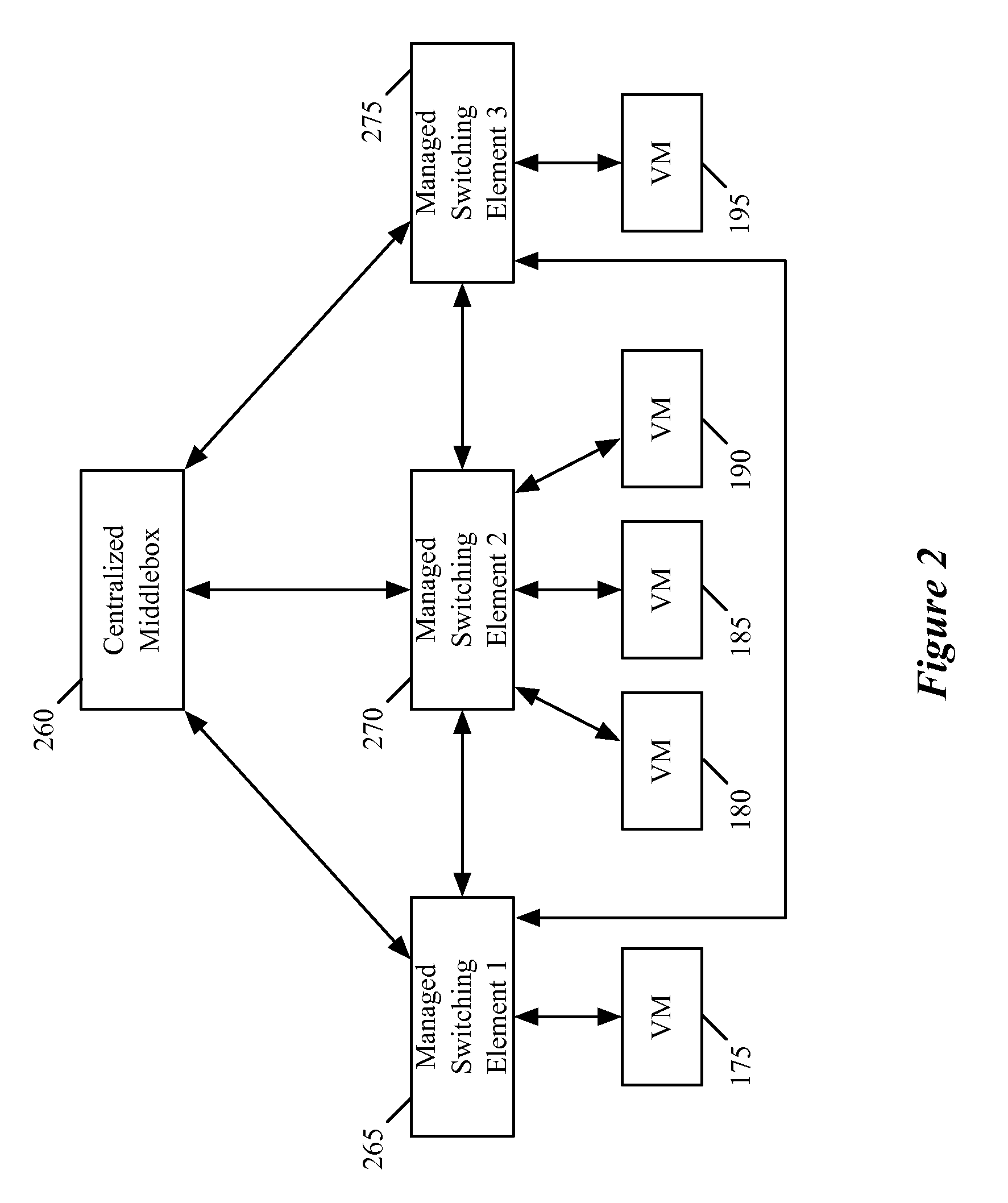
Control plane interface for logical middlebox services
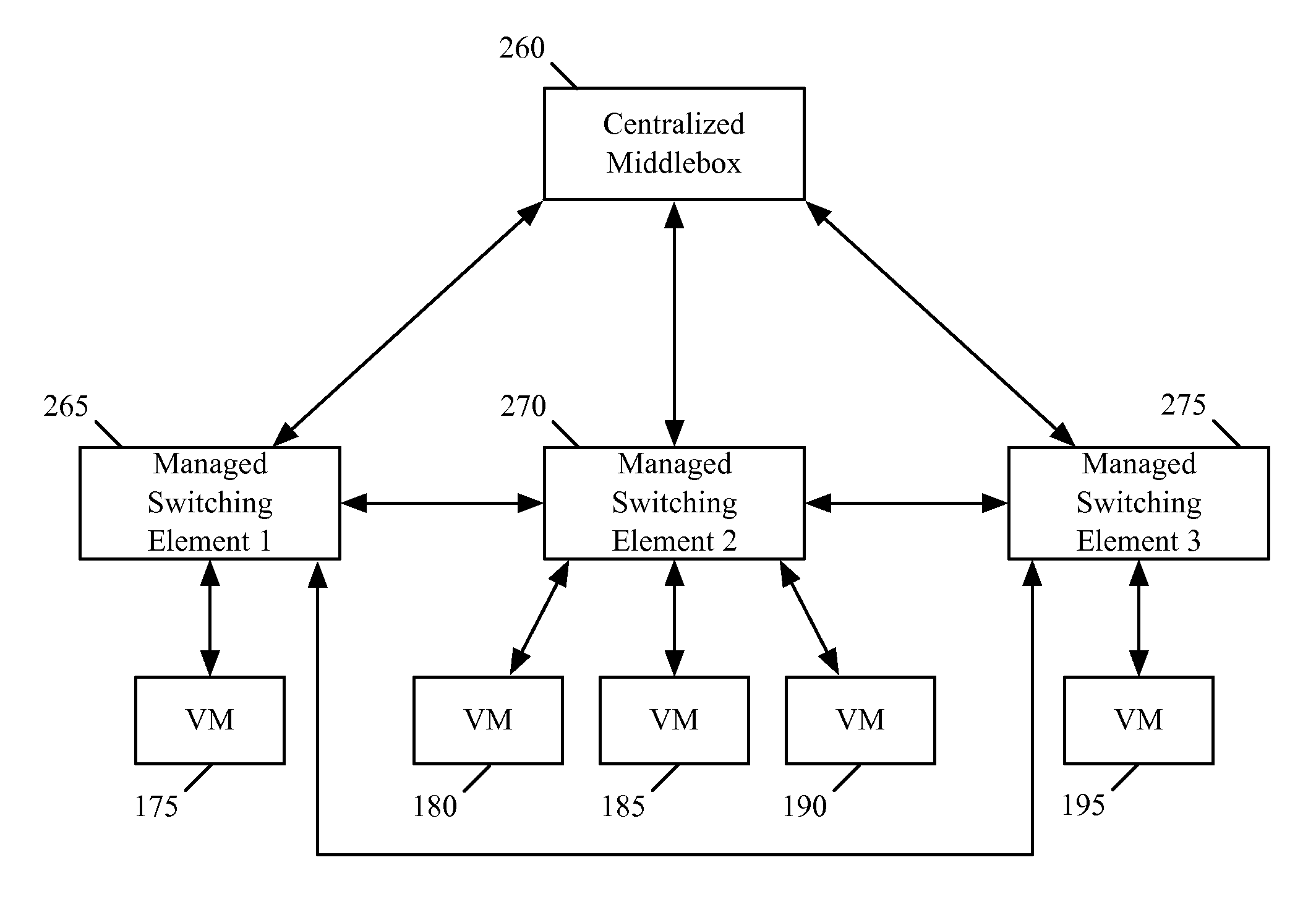
ActiveUS20130132533A1Digital computer detailsData switching networksInternal identifierLogical network
Owner:NICIRA
State-varying hybrid stream cipher
InactiveUS20060291650A1Data stream serial/continuous modificationUser identity/authority verificationState variationCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:ANANTH VISWANATH
Hybrid stream cipher
InactiveUS7003107B2Data stream serial/continuous modificationSecret communicationCiphertextInternal identifier
In one embodiment, a hybrid stream cipher operating within a computing device. The hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
Terminal identifier notification and maintenance methods and equipment
ActiveCN102238534ARealize the bindingConnection managementMachine-to-machine/machine-type communication serviceInternal identifierComputer terminal
The embodiment of the invention discloses a terminal identifier notification method, terminal identifier notification equipment, a terminal identifier maintenance method and terminal identifier maintenance equipment, which relate to the technical field of wireless communication and are used for realizing the binding of an external identifier of a machine type communication (MTC) terminal and an internal identifier of the MTC terminal. The terminal identifier notification method comprises that: core network equipment acquires the external identifier of the MTC terminal; and the core network equipment transmits the internal and external identifiers of the MTC terminal to a network edge. The terminal identifier maintenance method comprises that: the network edge receives the internal and external identifiers of the MTC terminal from the core network equipment; and the network edge locally establishes and maintains mapping relationships between the internal and external identifiers of the MTC terminal. By the scheme, the binding of the internal and external identifiers of the MTC terminal is realized at the network edge.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and apparatus for determining MTC-IWF entity
InactiveCN102523315AReduce consumptionReduce the number of queries to DNS ServerConnection managementTransmissionDomain nameName server
Owner:CHINA ACAD OF TELECOMM TECH
Method, system, wireless sharing device and terminal for accessing wireless local area network
ActiveCN103052063AEnsure safetyIncrease usageNetwork topologiesSecurity arrangementInternal identifierAuthentication server
Owner:CHINA MOBILE COMM GRP CO LTD
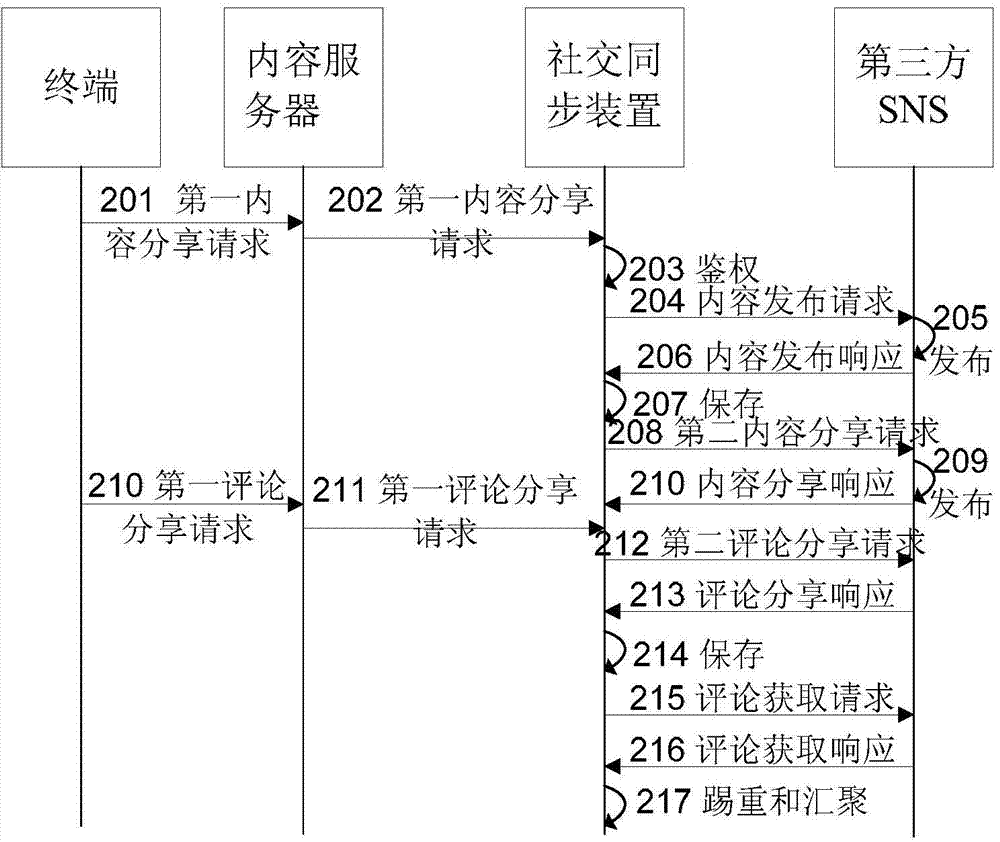
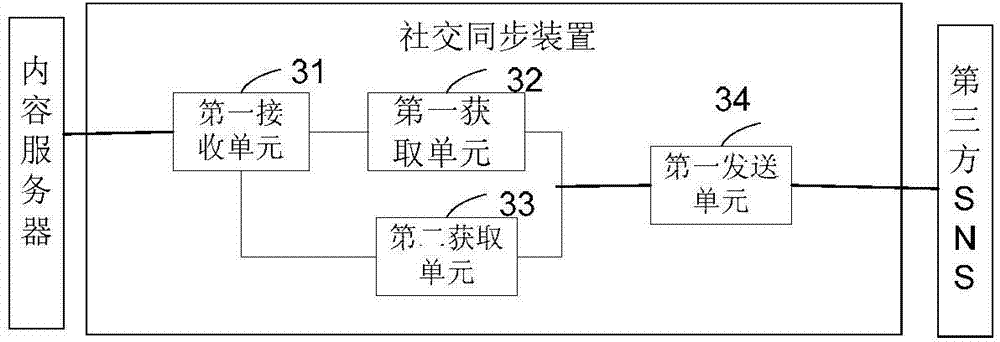
Content sharing method and Social Synchronizing Apparatus
ActiveCN103688513ASolve the problem that the same content is not relatedCorrectly reflect attentionTransmissionSpecial data processing applicationsInternal identifierContent sharing
The invention relates to a content sharing method comprising the following steps: a first content sharing request transmitted by a content server is received, wherein the first content sharing request includes internal identifiers of content that users request to share and target website identifiers; identifiers of the users on a target website are obtained; according to the internal identifiers of the content and the identifiers of the target website, first corresponding relations among internal identifiers of stored content, the identifiers of the target website and external identifiers of the content are searched in order to obtain external identifiers of content on the target website of the content; according to the target website identifiers and the identifiers of the users on the target website, a second content sharing request is transmitted to the target website, wherein the second content sharing request carries the external identifiers of the content and the identifiers of the users on the target website in order to share the content on a homepage of the users on the target website, so that the different users can share the same content on the same website in an associated way, and the heat degree of the content can be raised.
Owner:广东南邦新能源有限公司
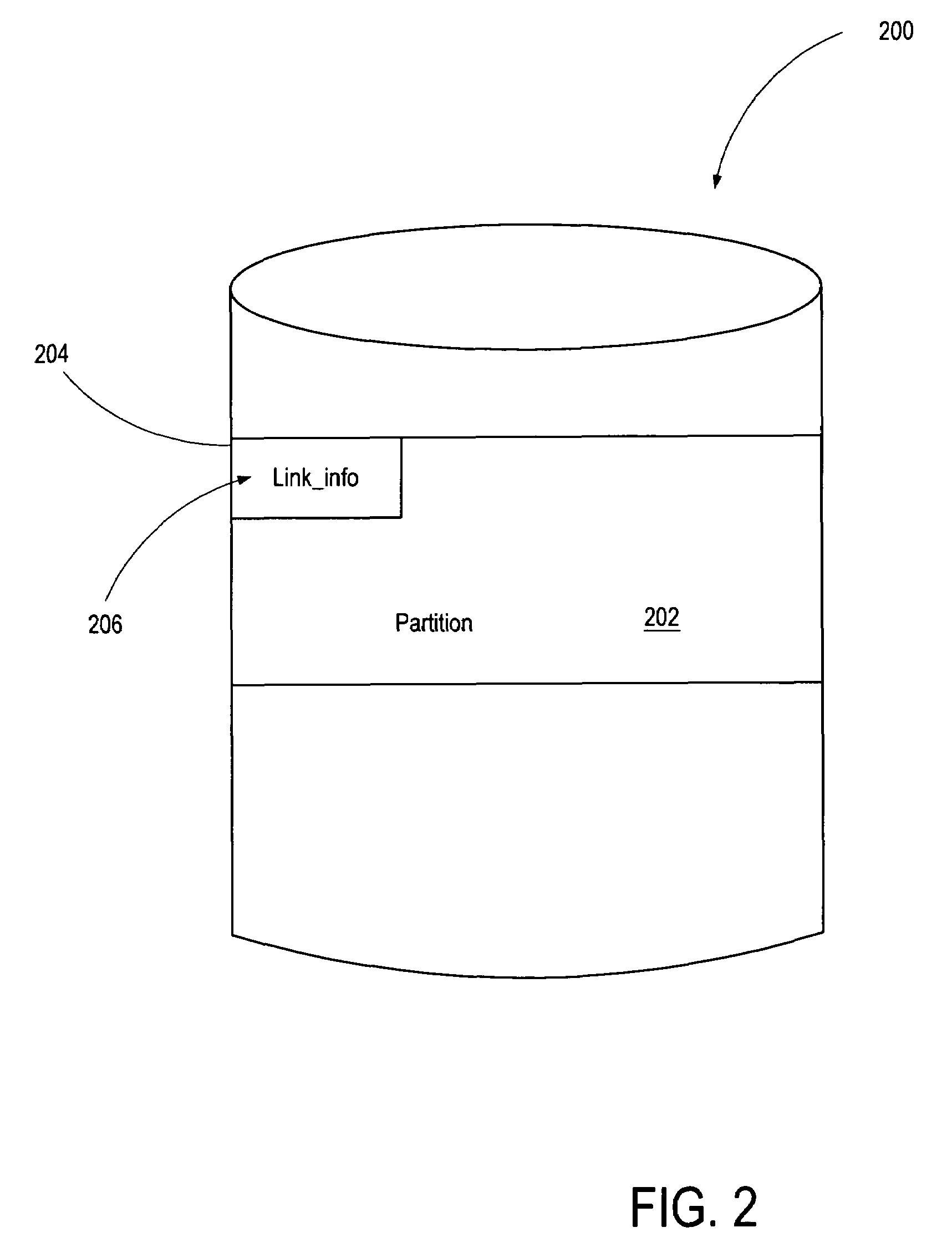
Method and system for object linking
InactiveUS6970888B1Input/output to record carriersData processing applicationsInternal identifierComputer science
Disclosed is a mechanism and method for object linking. According to an aspect of one embodiment of the invention, name linking information is co-located with the storage object, rather than being stored only at a computer node. By maintaining name liking information with a storage object, that name linking information can still be used to correctly associate an alternate name with that storage object, regardless of configuration changes that move or delete storage objects in the system and regardless of any changes to internal identifiers for that storage object.
Owner:ORACLE INT CORP
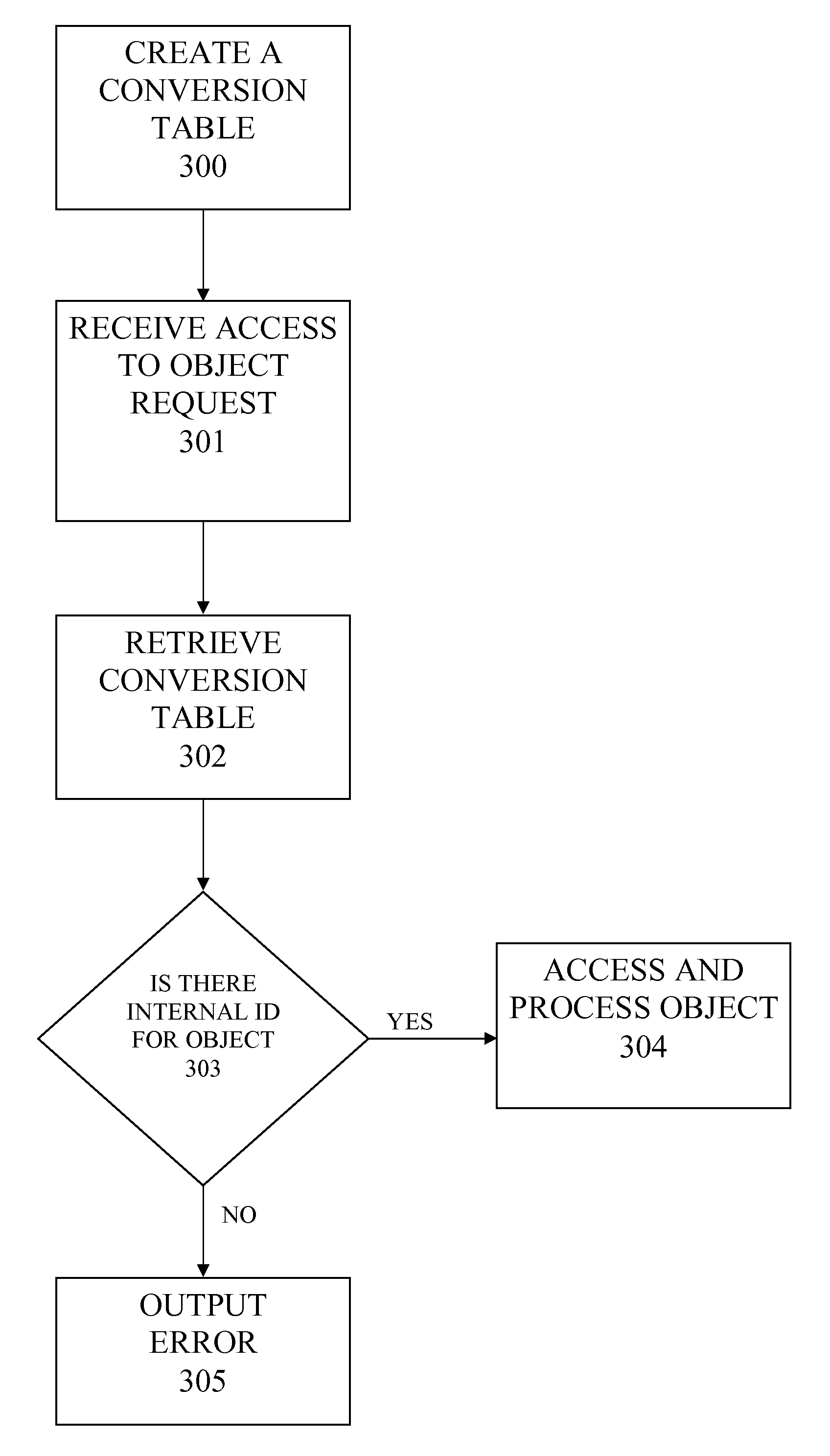
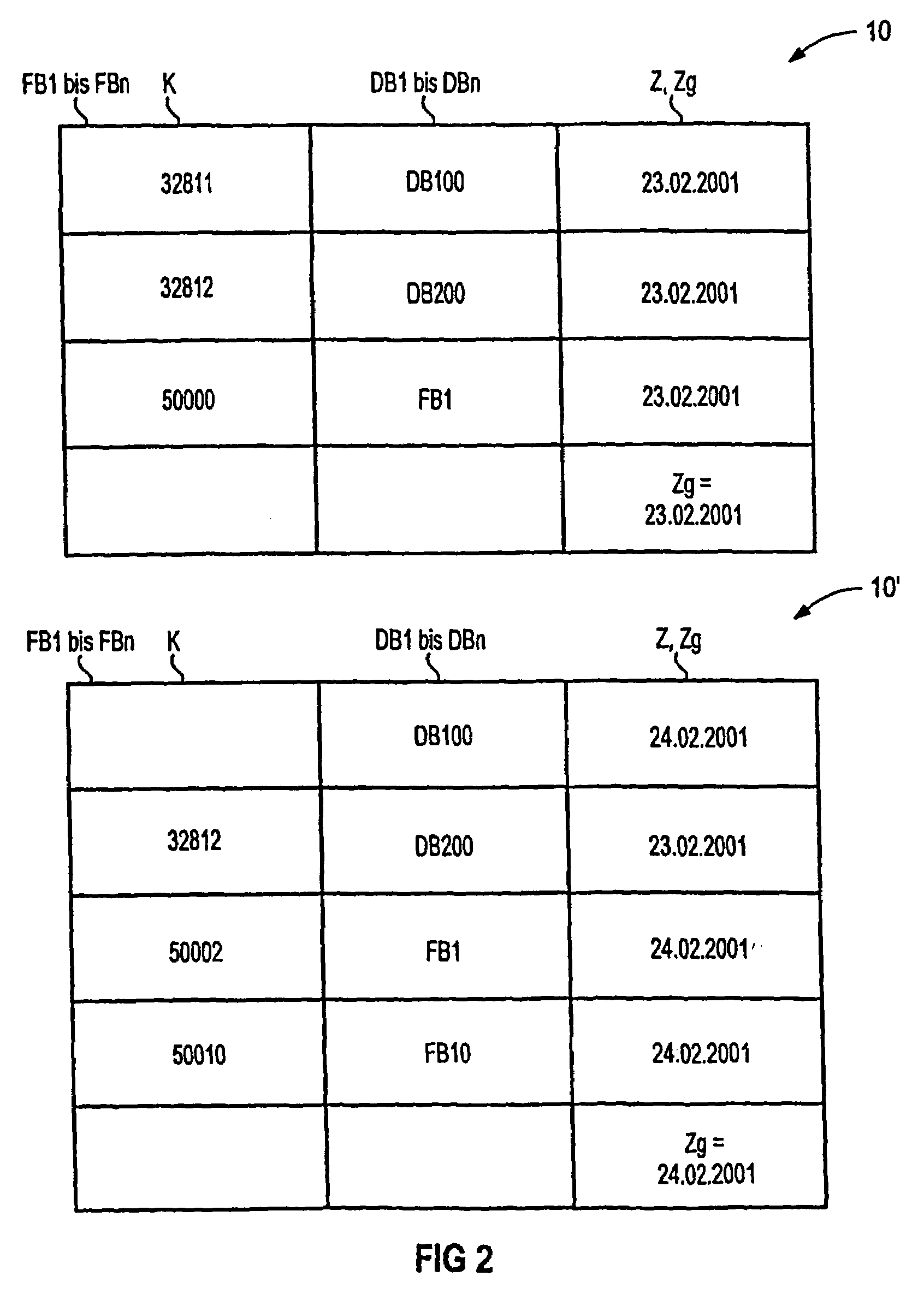
Method for processing data using external and internal identifiers to provide reliable access to the data even when reconfigurations of the data occur, and associated system
InactiveUS7234135B2Facilitate documentationEffective and economicalComputer controlSimulator controlData processing systemExternal data
A method for processing data in a data processing system (1) which includes a number of data processing units (2), and operator and observation units (4), which are interconnected by way of a data transmission unit (6), whereby a respective data processing program (8) with corresponding function modules (FB1 to FBn) and data modules (DB 1 to DBn) is implemented in the data processing units (2). At least one identifier (K, KE, KI) for the function modules and data modules is stored in a respective conversion table (10) belonging to each data processing unit (2). When an external data processing unit (2) accesses a data module (DB1 to DBn) and / or a function module (FB1 to FBn) of another data processing unit (2), a conversion table (10) mediates by using an external identifier (KE) that characterizes the access and verifies whether a matching internal identifier (KI) is stored for the particular external identifier (KE).
Owner:SIEMENS AG
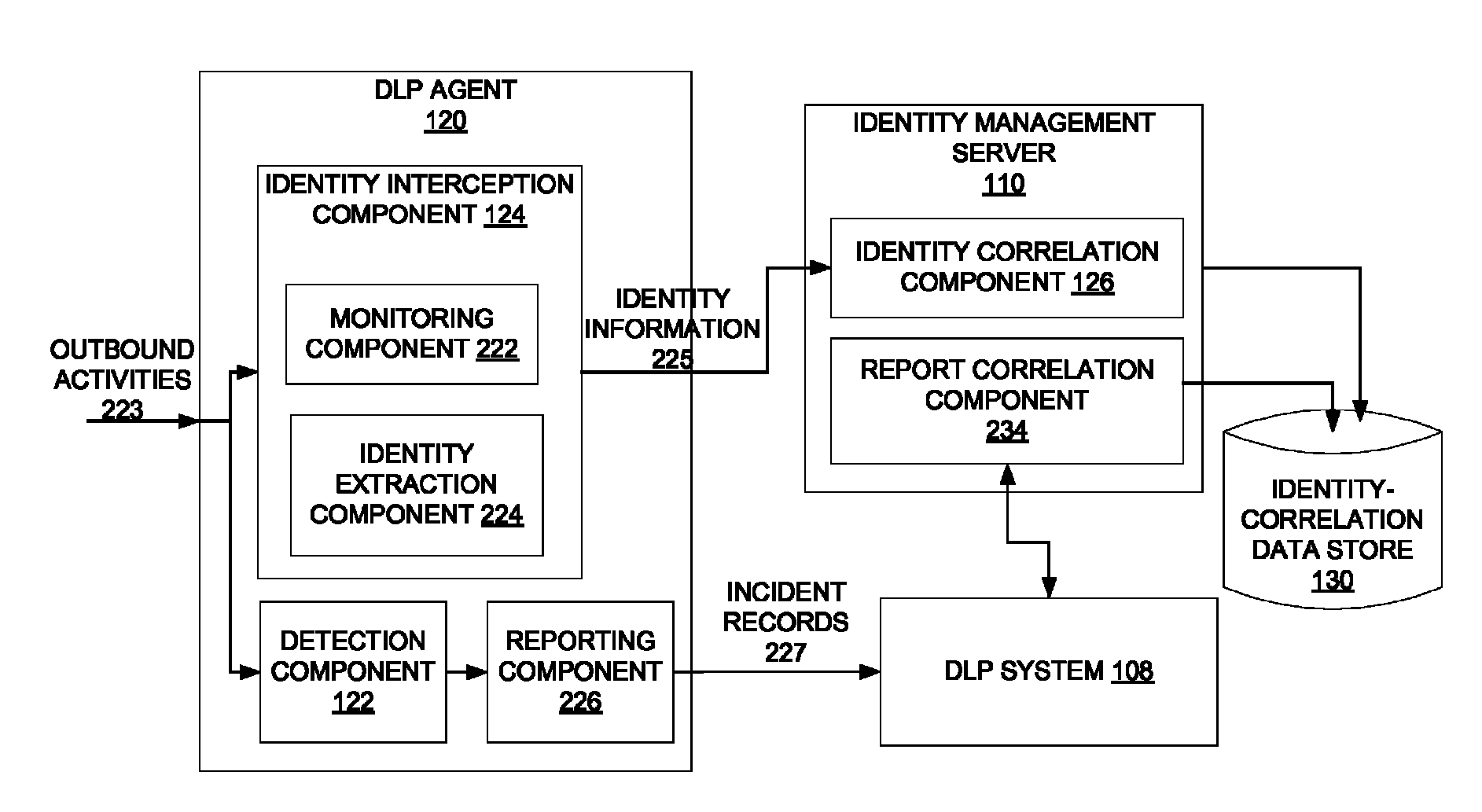
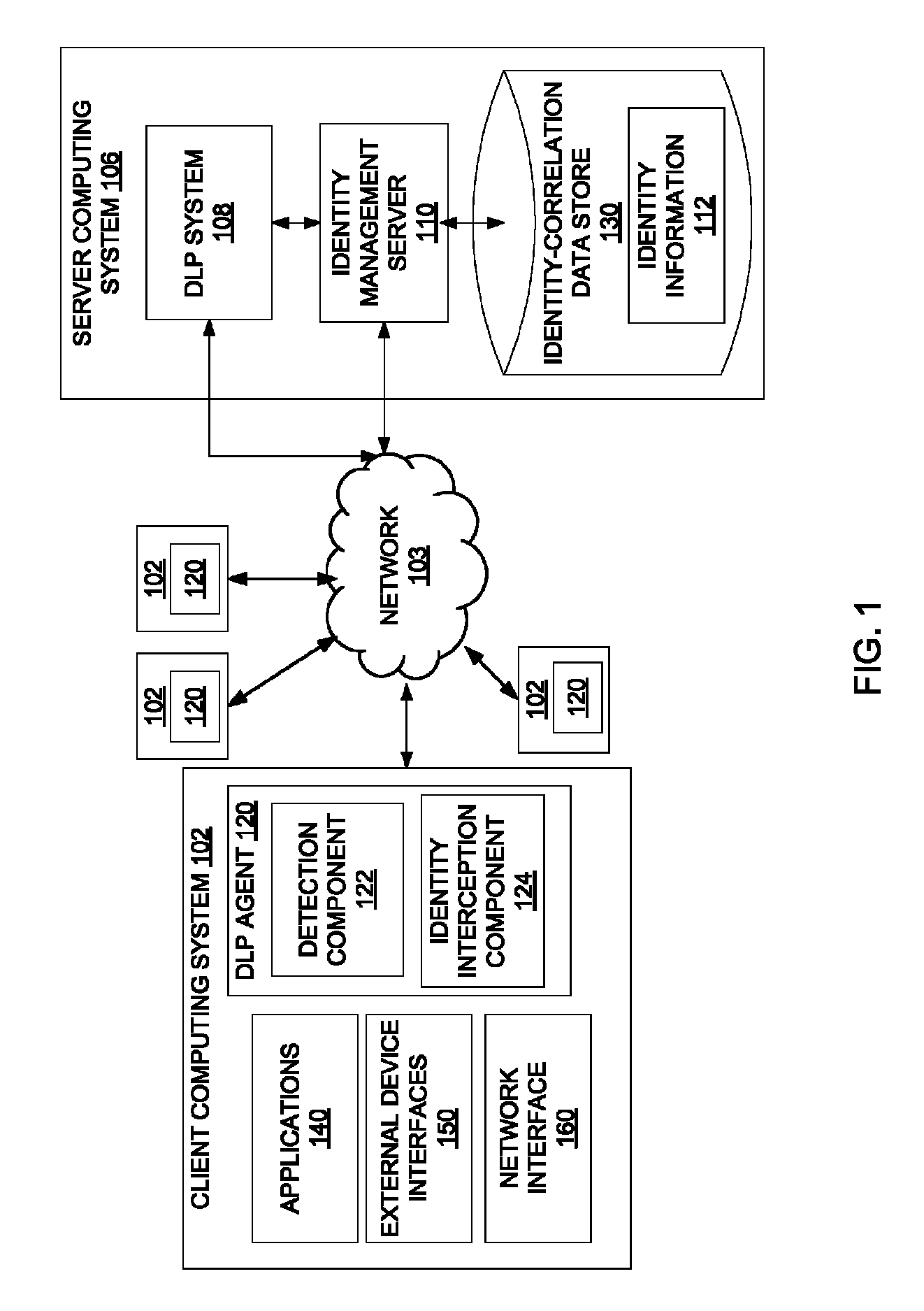
Dynamically populating an identity-correlation data store
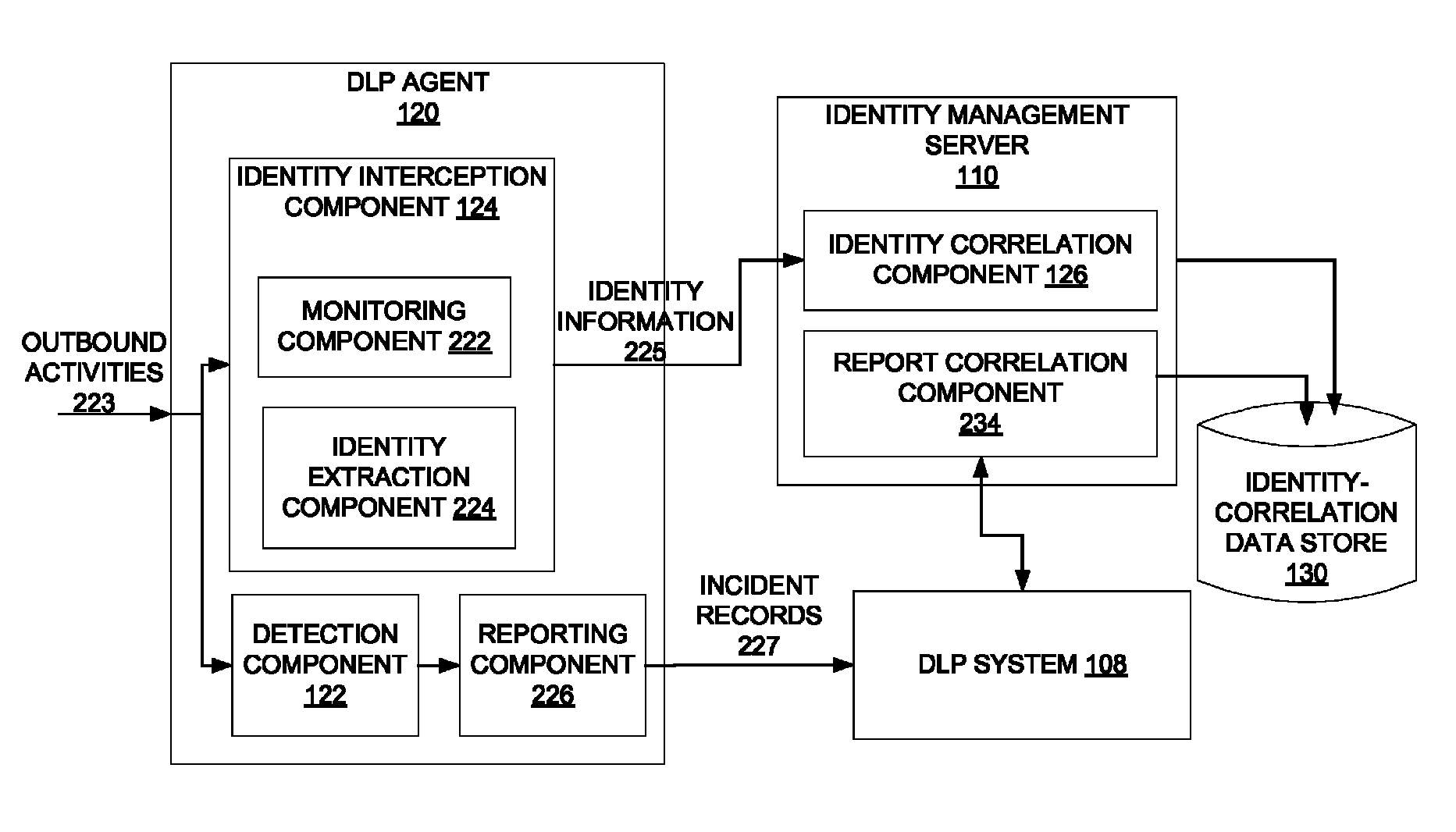
ActiveUS8510446B1Digital computer detailsPlatform integrity maintainanceIdentity correlationInternal identifier
A method and apparatus for dynamically populating an identity-correlation data store and using the identity-correlation data store to correlate external identifiers and unique internal identifiers are described.
Owner:CA TECH INC
Anti-fake battery pack and identification system thereof
ActiveUS20110121951A1Improve securityReduce the possibilitySmall-sized cells cases/jacketsUser identity/authority verificationInternal identifierProtection layer
An anti-fake battery pack and an identification system thereof has a casing and multiple battery cells, each of which as a battery body, an inner identifier mounted outside the battery body, a protection layer mounted around outside of the battery body and the outer identifier formed on the protection layer. An external identifying device has to read a first and second identification codes from the inner and outer identifiers to determine whether the battery cell is authentic or not. In addition, the inner identifier is covered by the protection layer, so the inner identifier can not stolen without breaking the protection layer with the outer identifier. Therefore, the identifying system provides double identifying procedures to increase security of identification and decrease the possibility of copying the first and second identification codes.
Owner:YAO LI HO
Storing sensitive information
InactiveUS20060106799A1RiskDigital data protectionSpecial data processing applicationsInternal identifierWorld Wide Web
The invention relates to a method, a system, telecommunication servers and a network node for storing sensitive information such that they are easily retrievable when needed for instance using an identity number without extra identifiers, but stored such that they cannot be associated with an individual. The invention is based on the use of an internal identifier and two separate databases such that upon reception of a storage request (700) including data to be stored and the first identifier for identifying the individual with whom the data to be stored is associated, then a second identifier is generated such that its value does not depend on the first identifier; the first identifier and the second identifier are stored in the first database by binding the first identifier to the second identifier; and the data to be stored is stored in the second database together with the second identifier.
Owner:MEDIWEB
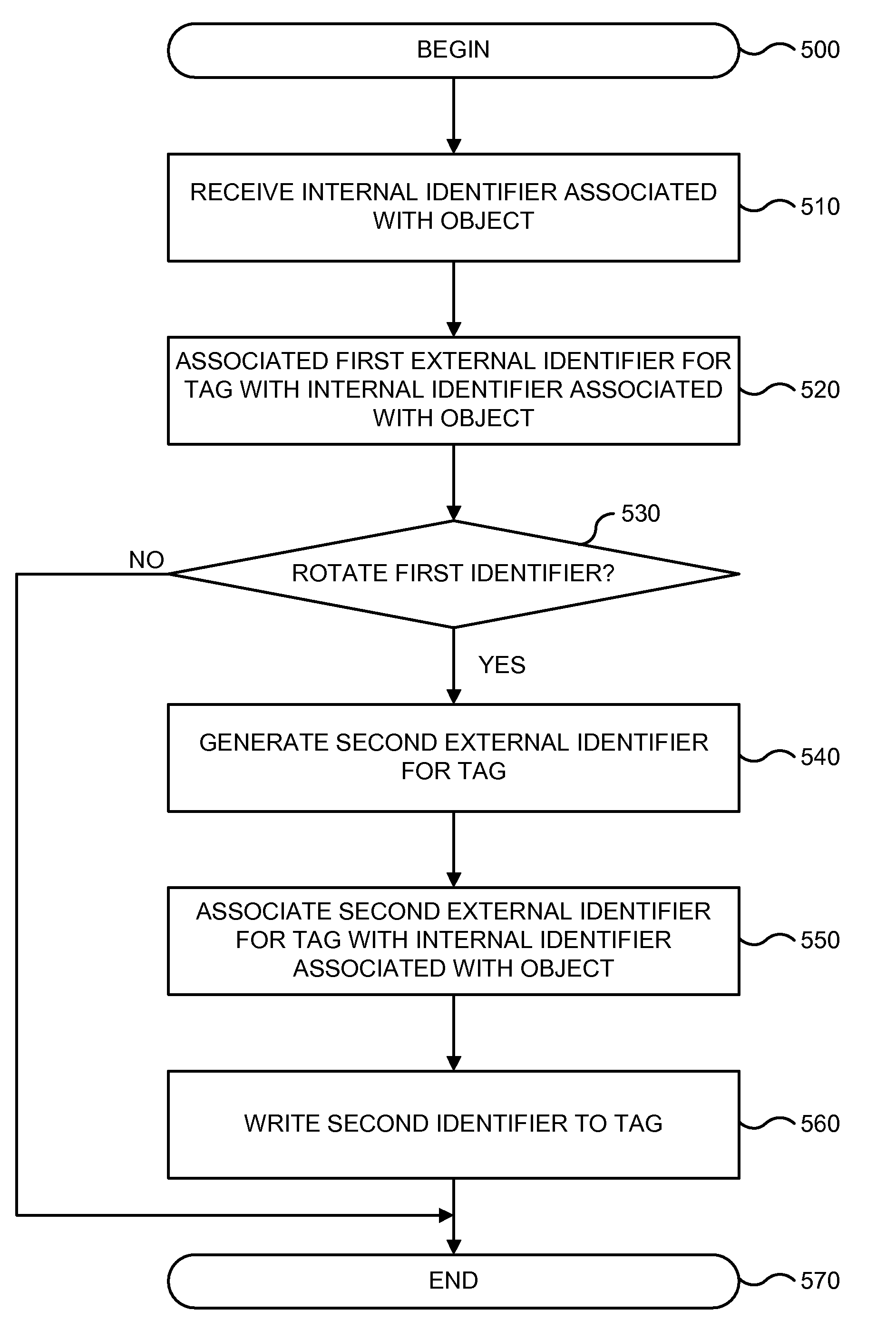
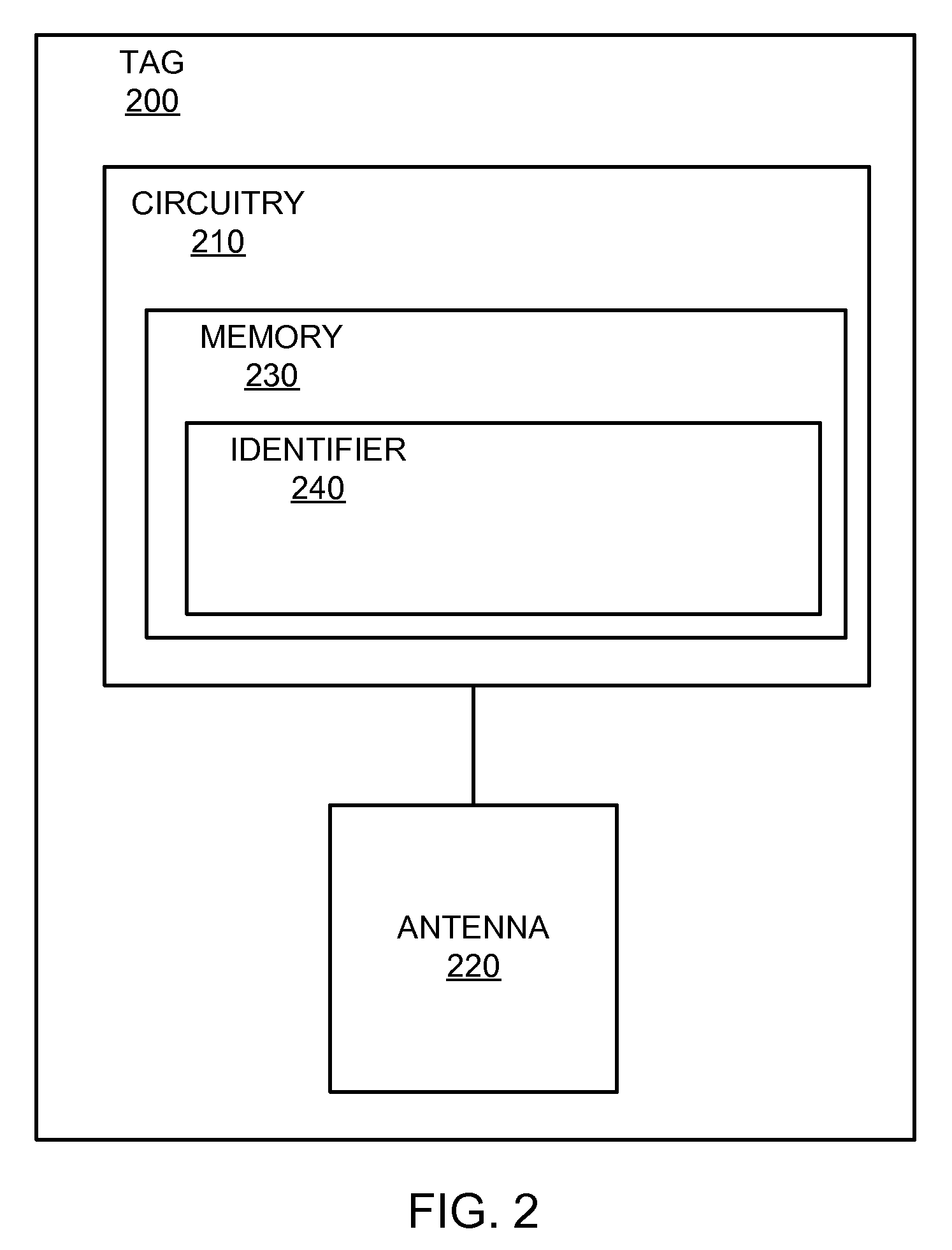
RFID Key Rotation System
In various embodiments, a method for tracking objects includes receiving an internal identifier associated with an object. A first key or external identifier for a tag is associated with the internal identifier. A second external identifier is generated and the second external identifier is then written to the tag. The second external identifier is associated with the internal identifier associated with the object.
Owner:ORACLE INT CORP
Selective execution of trace mechanisms for applications having different bit structures
InactiveUS8261243B2Error detection/correctionSpecific program execution arrangementsData processing systemInternal identifier
A computer implemented method, a computer program product, and a data processing system trace information about current context and system state for either 32-bit or 64-bit applications. A 32-bit trace executable code and a 64-bit trace executable code are compiled for a trace script. A determination is then made as to whether an application process is a 32-bit process or a 64-bit process. Responsive to determining that the application process is the 32-bit process or the 64-bit process, an internal indicator is set to indicate the application process as either a 32-bit process or a 64-bit process. Subsequently, the internal indicator is identified as either indicating the 32-bit process or the 64-bit process. If the internal identifier indicates the application process is a 32-bit process, an instruction pointer is set to indicate the 32-bit trace executable code, and the 32-bit trace executable code is executed. If the internal identifier indicates the application process is a 64-bit process, an instruction pointer is set to indicate the 64-bit trace executable code, and the 64-bit trace executable code is executed.
Owner:INT BUSINESS MASCH CORP
Connection establishment method and gateway unit
InactiveCN103369712AAvoid triggering requestsConnection managementWireless commuication servicesComputer networkInternal identifier
The invention discloses a connection establishment method and a gateway unit. The connection establishment method comprises the following steps of storing the corresponding relationship information of an internal identifier, an external identifier parameter and an external identifier of a terminal; and receiving a connection establishment request of the terminal, querying the external identifier of the terminal according to the internal identifier and the external identifier parameter in the connection establishment request, and establishing connection for the terminal according to the external identifier by using a service gateway unit of the terminal. According to the connection establishment method and the gateway unit, corresponding relationships among the internal identifier, the external identifier parameter and the external identifier of the terminal are stored, and a plurality of external identifiers of the terminal can be distinguished through a network when the terminal is triggered by a server to establish the connection, so that the use of a fault external identifier for responding to a terminal triggering request of the server is avoided, and success in the establishment of the connection between the terminal and the server is ensured.
Owner:ZTE CORP
Composite electrical appliance subset description information generation method and device, and composite electrical appliance control method and device
ActiveCN105278339AEasy to controlComputer controlProgramme total factory controlInternal identifierInterface standard
The invention discloses a composite electrical appliance subset description information generation method, a composite electrical appliance subset description information generation device, a composite electrical appliance control method and a composite electrical appliance control device. The composite electrical appliance subset description information generation method comprises the steps of: assigning internal identifiers for subsets of a composite electrical appliance, and generating a subset list; sending the subset list to control equipment, and receiving display names of the subsets fed back by the control equipment; and setting corresponding relations between the display names of the subsets and the subsets, and generating description information of the subsets of the composite electrical appliance. The devices and the methods provided by the invention effectively solve the problem that the subsets of the composite electrical appliance cannot be distinguished semantically by the interface standard in the prior art, and users can control the composite electrical appliance containing a plurality of the subsets of the same type (with same interfaces) conveniently.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Data transmission method and device
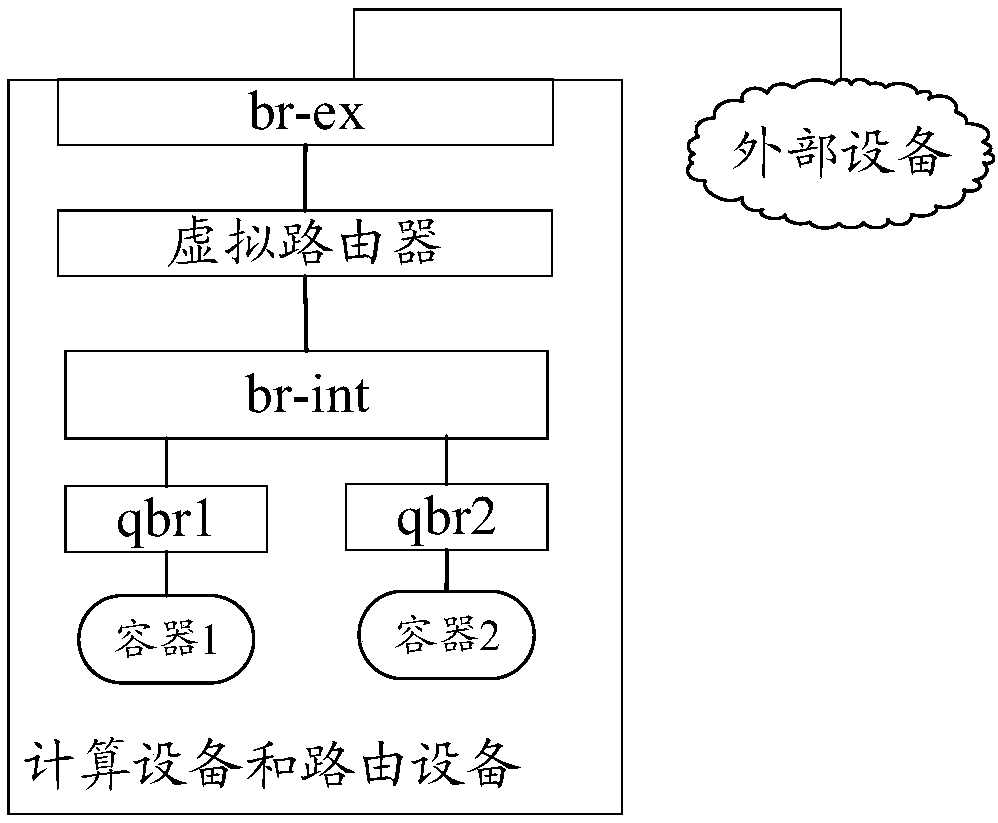
ActiveCN107770298ARealize communicationInterprogram communicationData switching networksCommunications systemInternal identifier
The application provides a data transmission method and device. The data transmission method and device are applied to a communication system that includes at least one computing device and at least one routing device, wherein at least one container is configured in each computing device, the communication system is equipped with a plurality of container groups, each container group in the plurality of container groups includes at least one container, and one container belongs to only one container group. The data transmission method comprises the following steps: a routing device confirms a first mapping relationship and a plurality of second mapping relationships, wherein the first mapping relationship is used to indicate a one-to-one mapping relationship between the plurality of container groups and a plurality of external identifiers, the plurality of second mapping relationships have one-to-one correspondence with the plurality of container groups, and each second mapping relationship is used to indicate a one-to-one mapping relationship between the plurality of containers of the corresponding container group and a plurality of internal identifiers; and the routing device controls the data transmission between the container and the external device according to the first mapping relationship and the second mapping relationship, so that the communication between the container and the external device can be easily realized.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Adjacent communication service realizing method and device
The invention discloses an adjacent communication service realizing method and device, and relates to the communication technology. In the UE contact signing process, an adjacent communication service identifier is assigned for the UE, so that after an adjacent communication service request sent by the UE is received, the adjacent communication service identifier of the UE is determined, and then adjacent communication service is realized according to the adjacent communication service identifier of the UE, so that the condition that the adjacent communication service cannot be performed because a network cannot determine the 3GPP network internal identifier of the UE according to the application identifier of a user can be avoided, so the adjacent communication service of the UE can be realized.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Transferring of a message
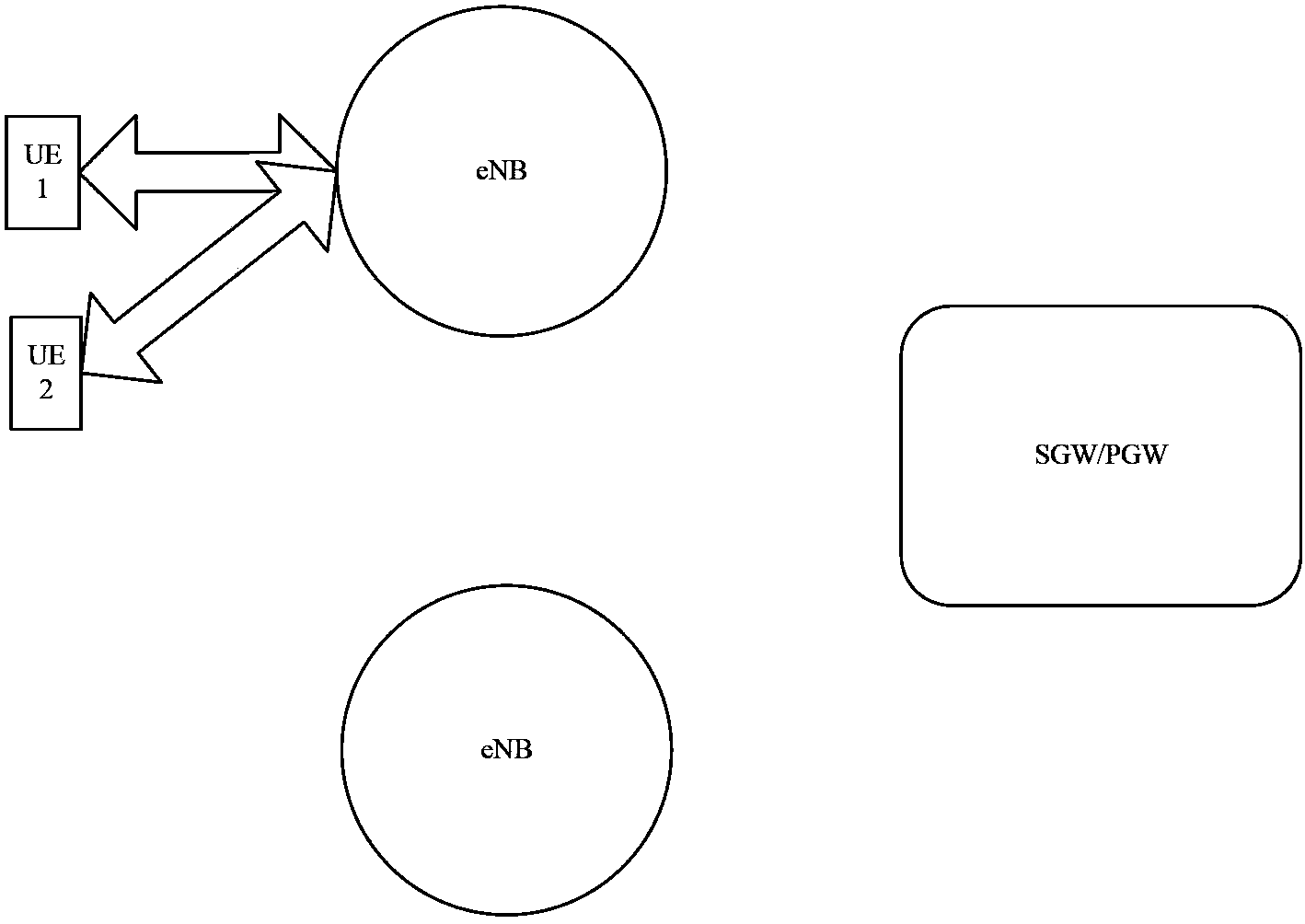
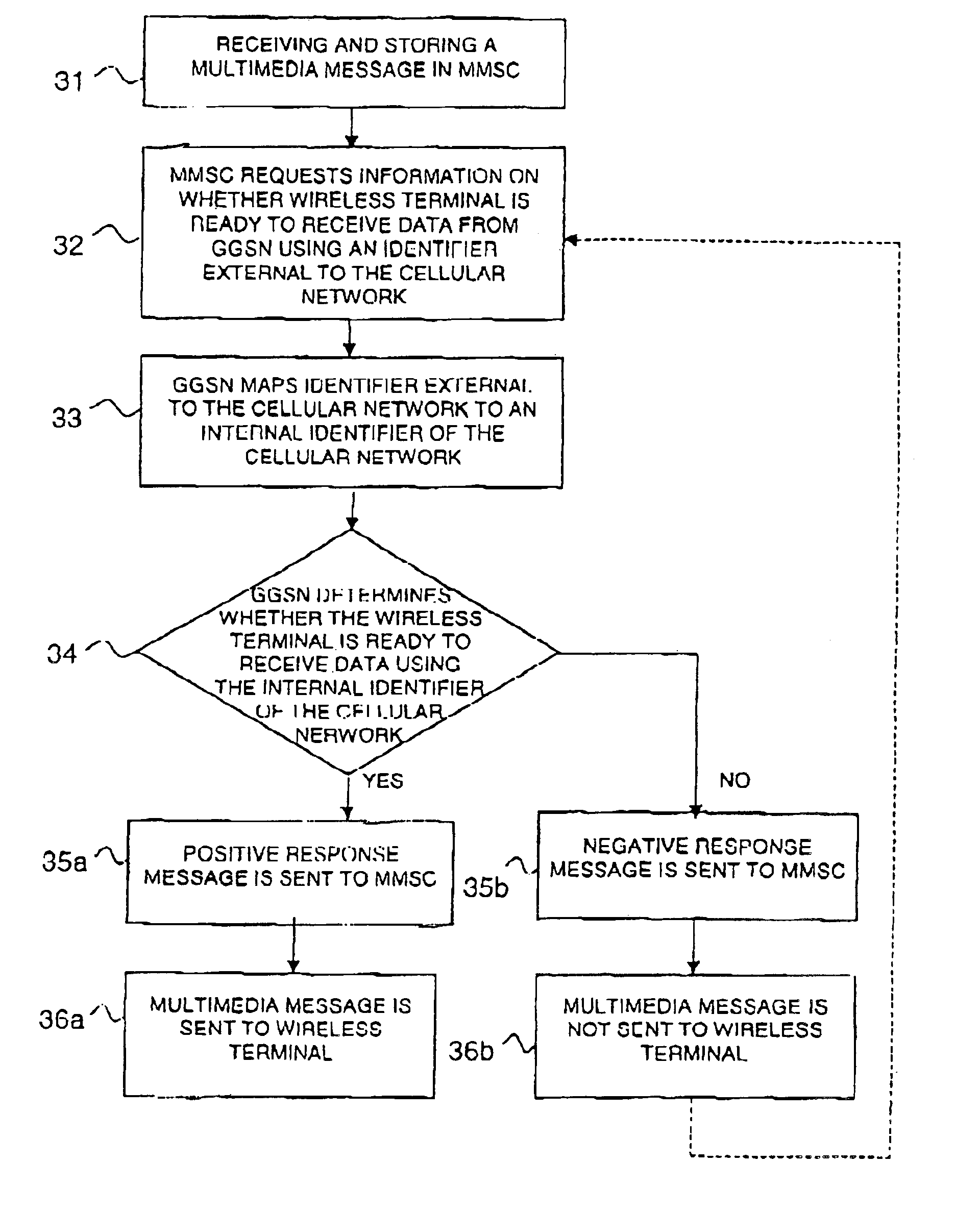
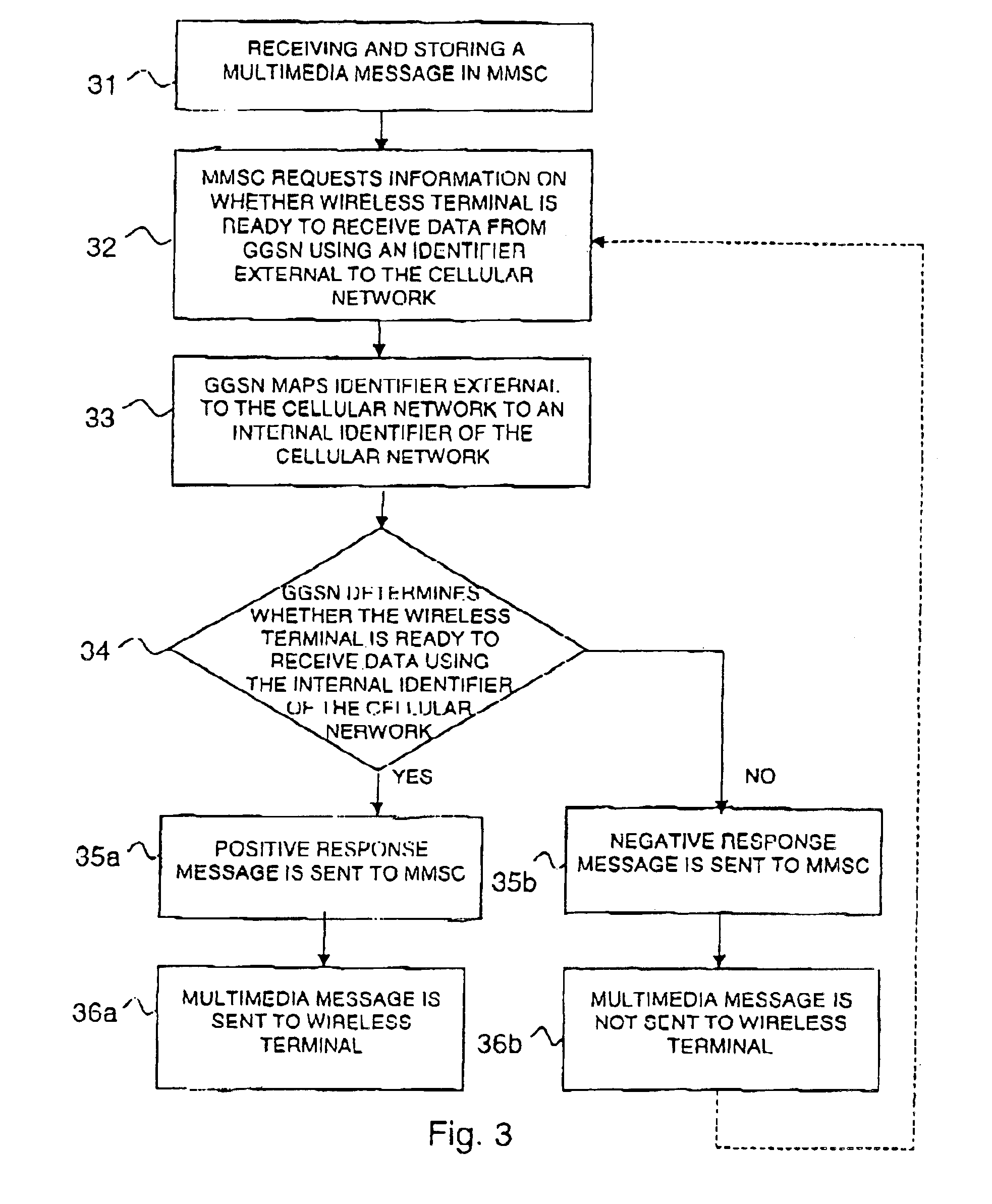
InactiveUS6885870B2Data switching by path configurationRadio/inductive link selection arrangementsInternal identifierUser identifier
A method is provided for inquiring about information relating to a mobile terminal of a cellular network, from a messaging server external to the cellular network. An inquiry is sent from the messaging server to the cellular network, comprising an external first identifier for identifying said terminal. In the cellular network the first identifier is mapped to a second internal identifier. The information relating to the terminal (MS) is determined with the aid of said second identifier and a responsive message is sent from the cellular network to said messaging server. In the response message, said information relating to the terminal is indicated by the first identifier.
Owner:COMCAST CABLE COMM LLC
Procedure for the global unified registration and universal identification of donors
InactiveUS20180247346A1Fundraising managementMedical data managementRelevant informationInternal identifier
Procedure for the global unified registration and universal identification of donors that comprises:Creation of one or more donor profiles and relevant medical data profiles, in addition to a common internal identifier, from the initial registration of a user in the system, associated with a personal and non-transferable identification code, installation of the code on an electronic device and storage of the user's data and profiles in a database accessible by different centres.Identification of the user / donor by a donation centre through the personal and non-transferable code for access to the user data, the common internal identifier and the stored profiles, creation, registration and incidence communication if there is an impediment: automatic updating of user data, their profiles and donation history in the database accessible by different centres.Optionally:Detect information of a donation process (donation result, existence of adverse reaction after donation, result of analytical tests, . . . ), storage in the database and user notification.Detect relevant information from other medical centres and incorporate it to the user data and / to the stored profiles for access from the donation centres.Send a global notification to donation centres after a serious illness is detected in an individual.Detect the presence of users close to donation points or to endemic disease zones and notify them.Verify the accuracy of the data given by the user, then compare them with the results of a laboratory analysis or with those of a donation centre, and updating the state of the user's data and / or their donor profiles as verified.
Owner:CONECTATE SOLUCIONES Y APLICACIONES S L U
RFID key rotation system
In various embodiments, a method for tracking objects includes receiving an internal identifier associated with an object. A first key or external identifier for a tag is associated with the internal identifier. A second external identifier is generated and the second external identifier is then written to the tag. The second external identifier is associated with the internal identifier associated with the object.
Owner:ORACLE INT CORP
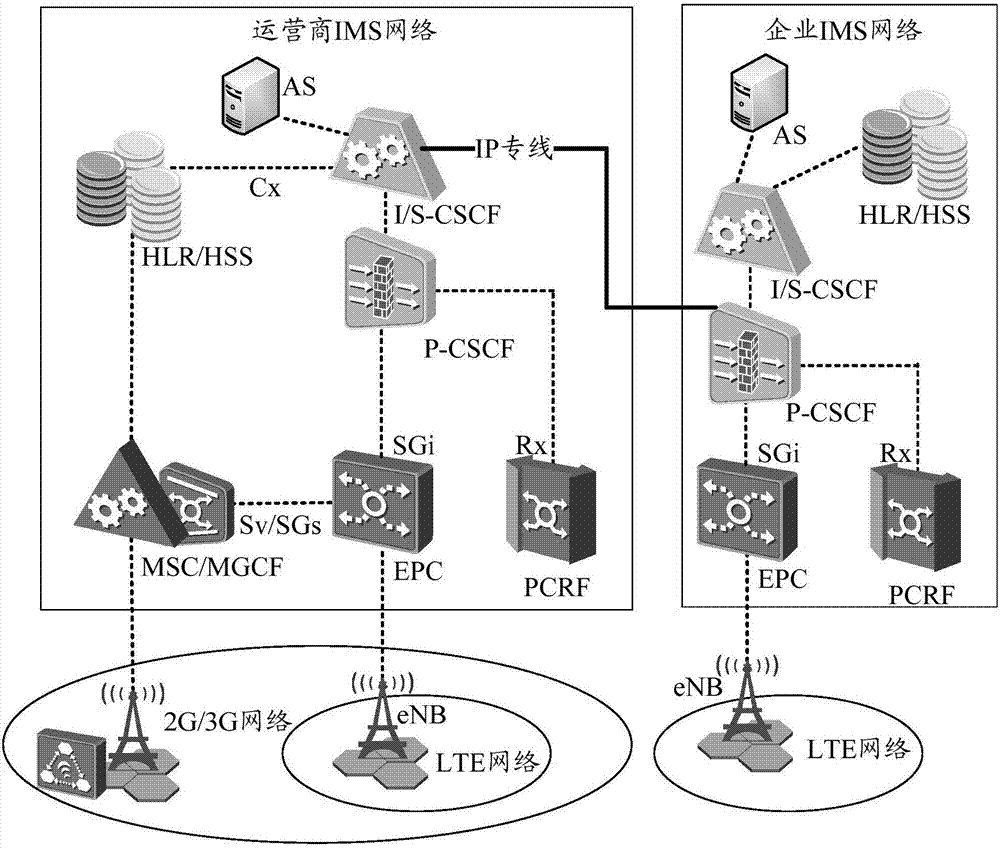
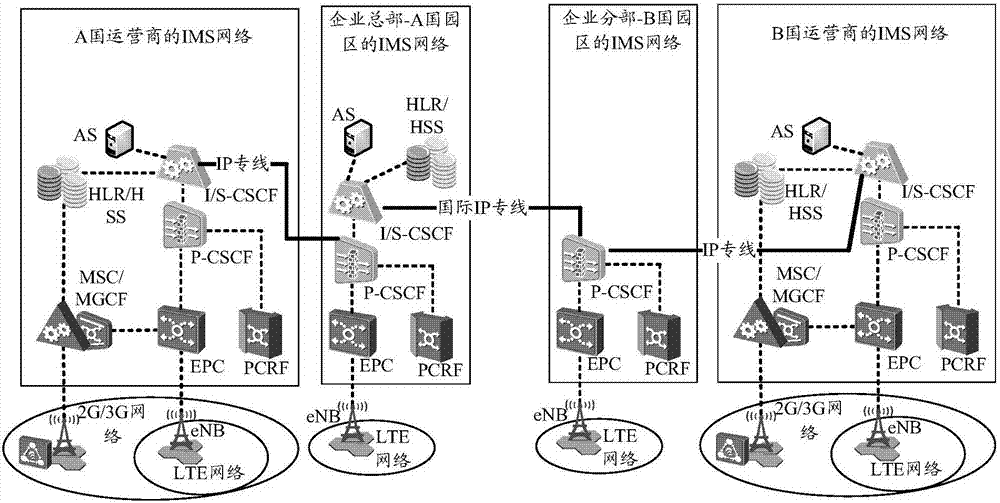
Wireless communication method and P-CSCF equipment
ActiveCN106941669ACommmunication supplementary servicesWireless network protocolsTelecommunicationsVoice communication
The invention provides a wireless communication method and P-CSCF equipment. The method comprises the steps of receiving a first INVITE message sent from a first mobile terminal by first P-CSCF equipment in an enterprise IMS network, wherein the first INVITE message contains the identifier of a called second mobile terminal; on the condition that the identifier of the second mobile terminal belongs to an internal identifier of the enterprise IMS network, routing a call to the second mobile terminal by the first P-CSCF equipment through S-CSCF equipment in the enterprise IMS network; on the condition that the identifier of the second mobile terminal does not belong to the internal identifier of the enterprise IMS network, routing the call to the second mobile terminal by the first P-CSCF equipment through S-CSCF equipment in a network operator IMS network. According to the technical scheme of the invention, the free voice communication among employees of an enterprise can be realized inside the enterprise through mobile terminals.
Owner:HUAWEI TECH CO LTD
Method, equipment and system for triggering applications
ActiveCN103685172AWireless commuication servicesTransmissionInternal identifierApplication Identifier
The invention provides a method, equipment and a system for triggering applications. According to the embodiment of the invention, MTC SP utilizes signing identifiers, application identifiers and external identifiers of MTC (Machine Type Communication) equipment to trigger MTC service; as triggering messages contain internal identifiers of the MTC equipment and the application identifiers, mobile management equipment can be enabled to record the internal identifiers of the MTC equipment and the application identifiers according to the received triggering messages, so that core network equipment can control and manage the applications triggered by the MTC equipment.
Owner:HUAWEI DEVICE CO LTD
Method and system for object linking
InactiveUS20060041575A1Data processing applicationsInput/output to record carriersInternal identifierDatabase
Owner:ORACLE INT CORP
Network Relay Device
ActiveUS20140321458A1Large capacityIncreased retrieval timeMultiplex system selection arrangementsCircuit switching systemsInternal identifierProcessing element
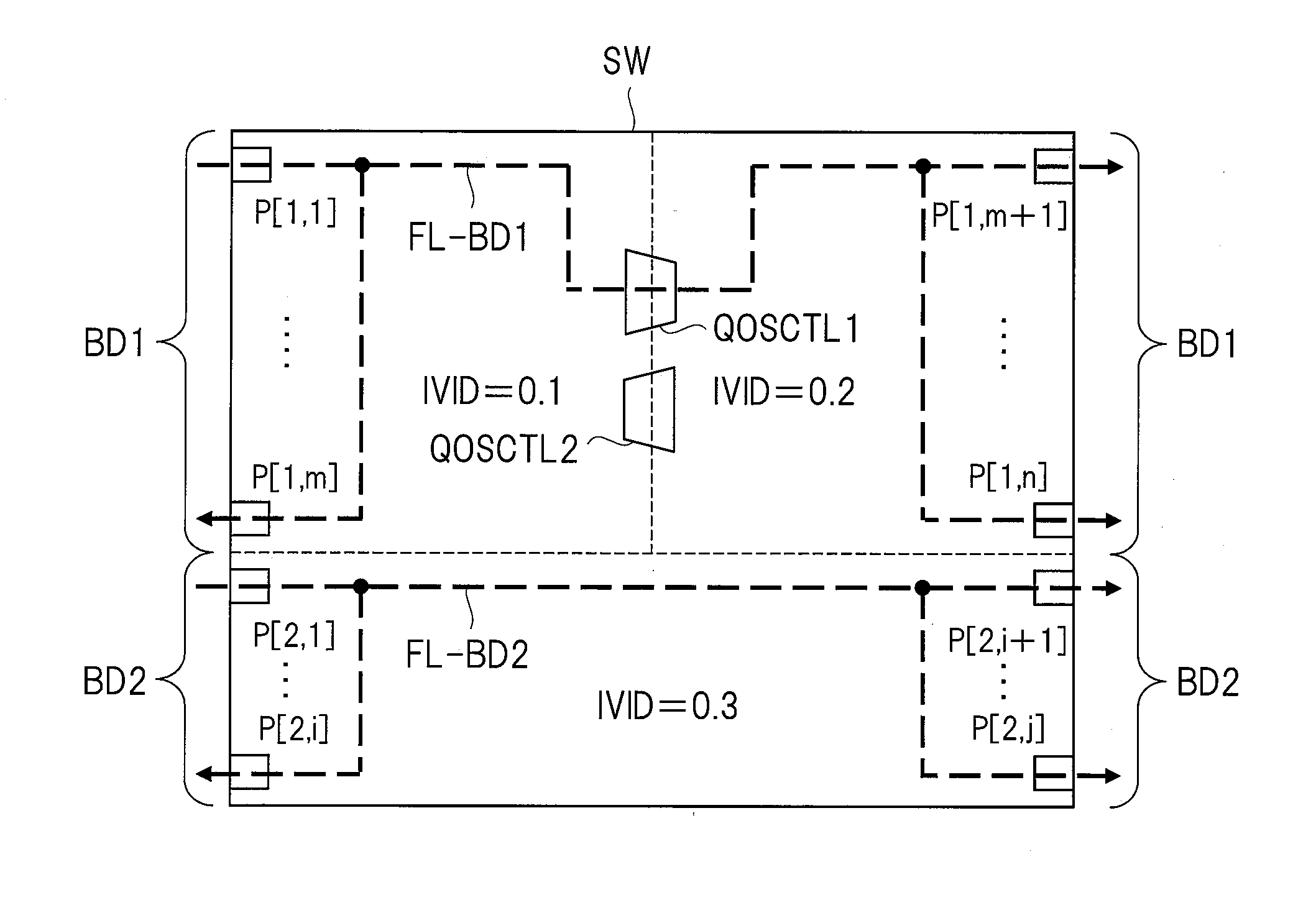
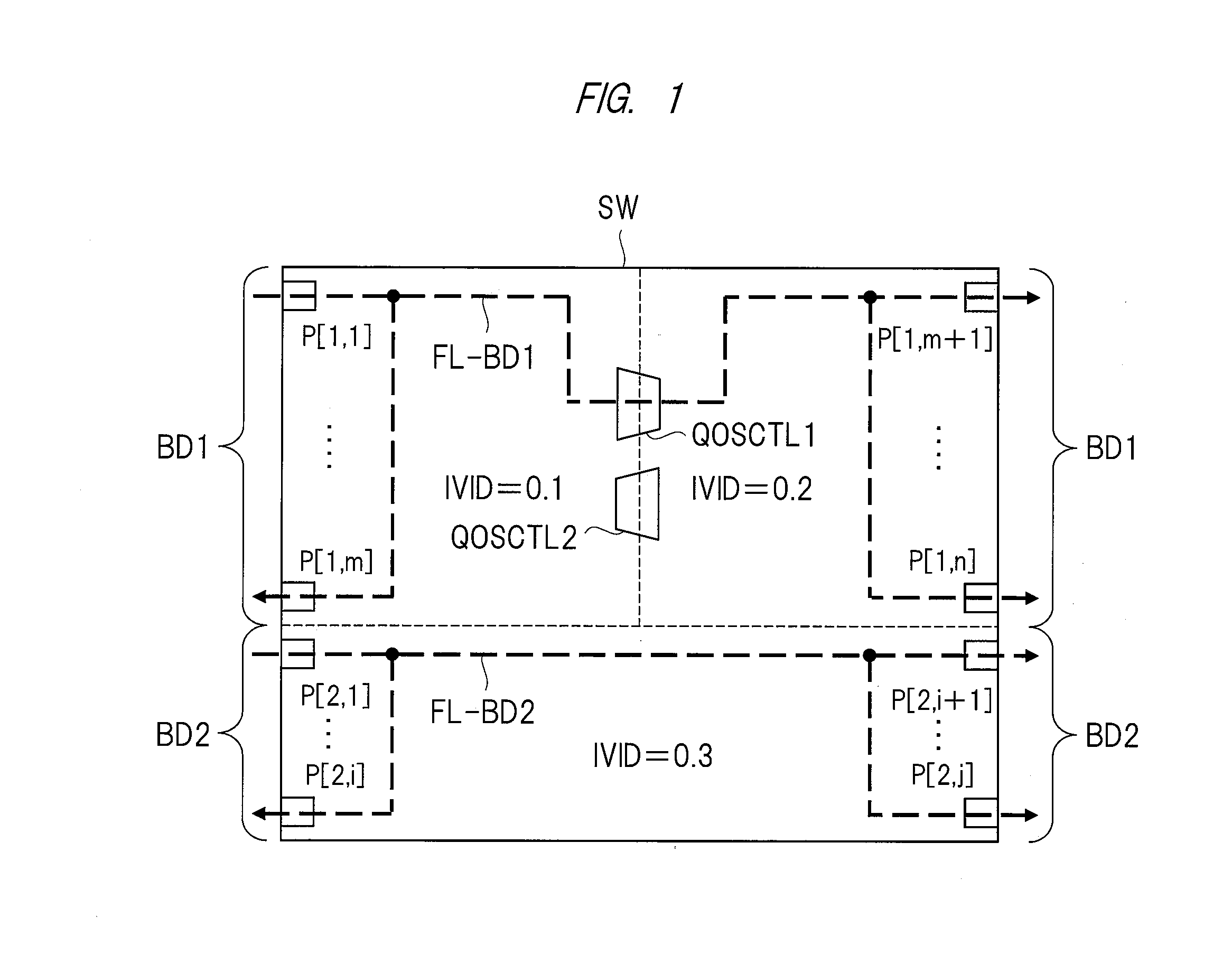
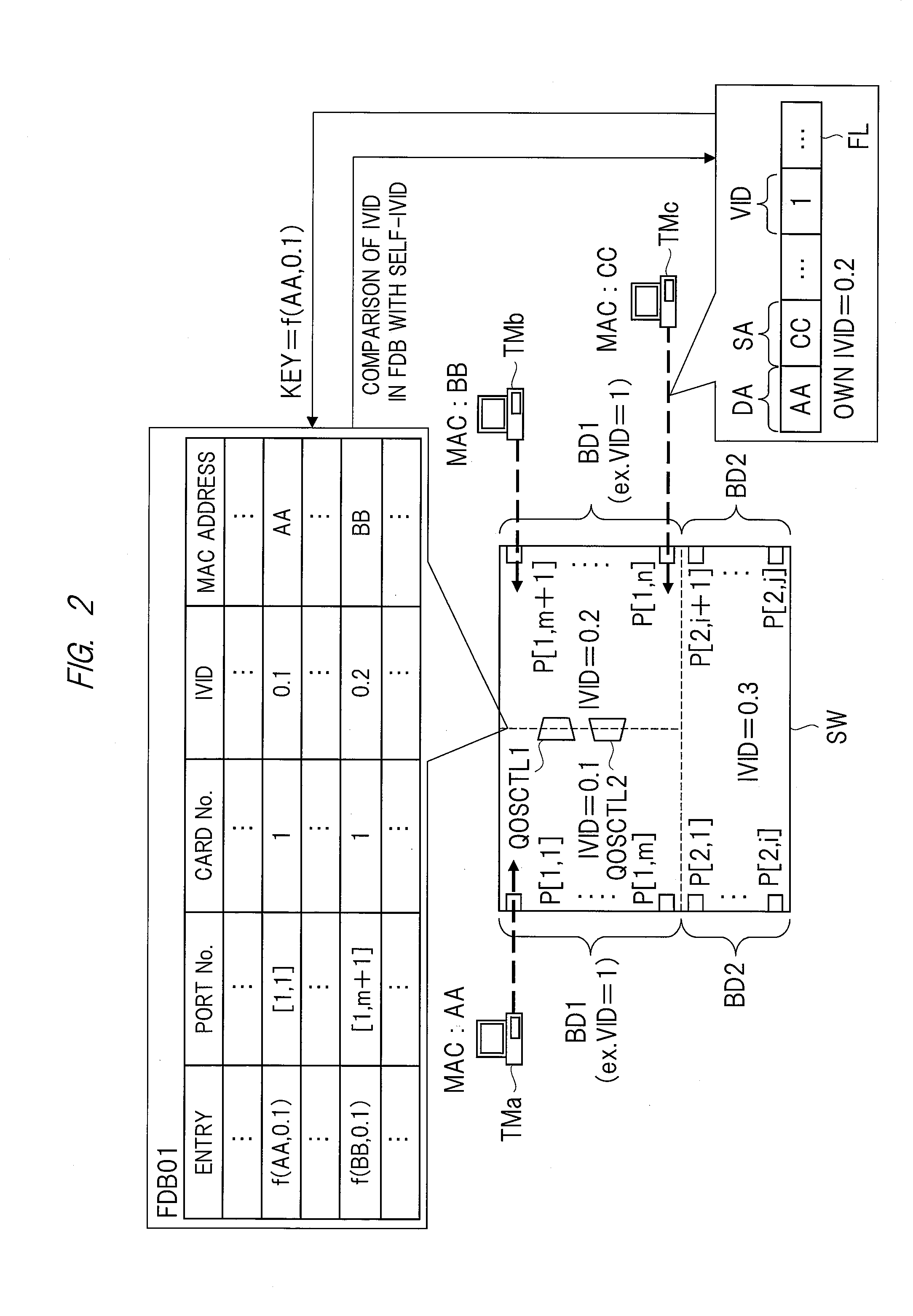
A network relay device capable of shortening retrieval time for an address table or reducing a capacity of the address table is provided. When a transmission-source address of a frame received at first and second port groups is learned, a frame processing unit performs a hash calculation by using the transmission-source address and a first internal identifier 0.1. Then, an internal identifier etc., corresponding to the receiving port is registered in an entry inside an address table obtained by the hash calculation. On the other hand, when a transmission-destination address of a frame received at the first and second pot groups is retrieved, the frame processing unit performs a hash calculation by using the transmission-destination address and 0.1, reads out an entry inside the address table obtained by the hash calculation, and compares the internal identifier inside the address table with an internal identifier corresponding to the receiving port.
Owner:APRESIA SYST LTD
System and method for executing database operations on a database
InactiveUS20190205436A1Easy to usePromote generationSpecial data processing applicationsDatabase design/maintainanceDatabase interfaceRepresentational state transfer
Owner:COMPTEL CORP
Automatic transfer of machine-to-machine device identifier to network-external service providers
Techniques for automatically transferring an external identifier for a wireless device from a wireless communication network serving the wireless device to a service provider external to the wireless communication network are disclosed. In an example method, carried out in one or more nodes of the wireless communication network, a binding between the external identifier and an internal identifier for the wireless device is maintained. A data session for the wireless device and corresponding to the service provider is established, wherein said establishing includes an assignment of an IP address to the wireless device. A request for the external identifier is received from the service provider, said request including the IP address for the wireless device. The external identifier is then sent to the service provider, in response to the request.
Owner:TELEFON AB LM ERICSSON (PUBL)
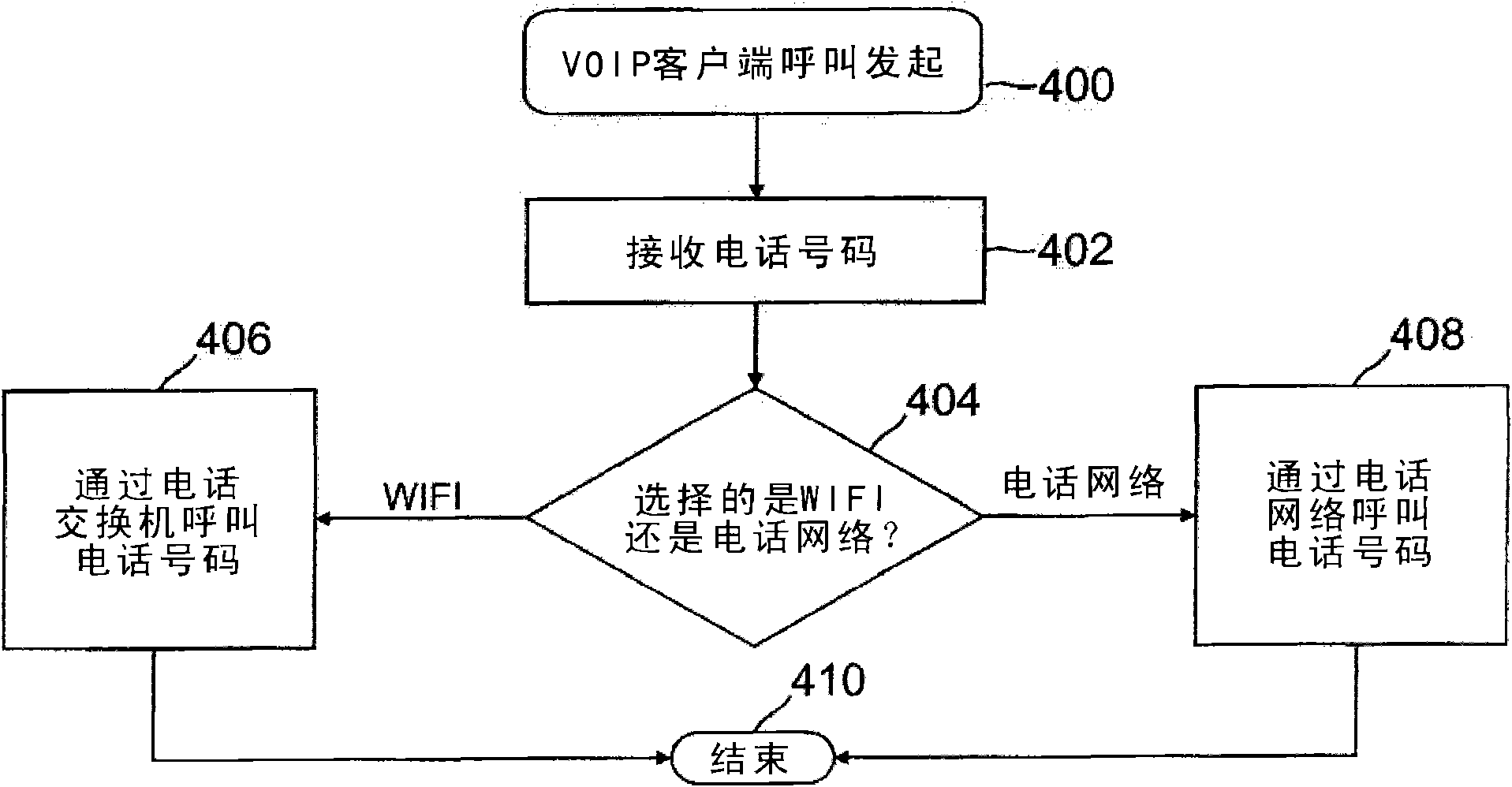
Call processing telecommunication system and methods thereof in a wifi network
The invention provides a call processing telecommunication system and methods thereof in a wifi network. Global identifiers can be dialled from anywhere in the world. The present application relates to a call processing telecommunication system and methods thereof in a wireless network for connecting communication devices. The integrated system can resolve issues with global identification using internal identifiers. In one illustrative embodiment, the global identifiers can be registered and mapped to an internal number such that the global numbers can be used to contact individuals. When a call is placed by a communication device, the internal identifier of the calling device can be tied back to the global identifier, which then provides access to the IP address of the VoIP client to complete the call. For incoming calls, the global identifiers can be translated into an internal identifier to route the call through the network.
Owner:MITEL
Dynamically populating an identity-correlation data store
ActiveUS8868754B1Digital computer detailsPlatform integrity maintainanceInternal identifierData loss
A method and apparatus for detecting a violation of a data loss prevention (DLP) policy and correlating an external identifier of an incident record of the violation to a unique internal identifier using an identity-correlation data store are described.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com