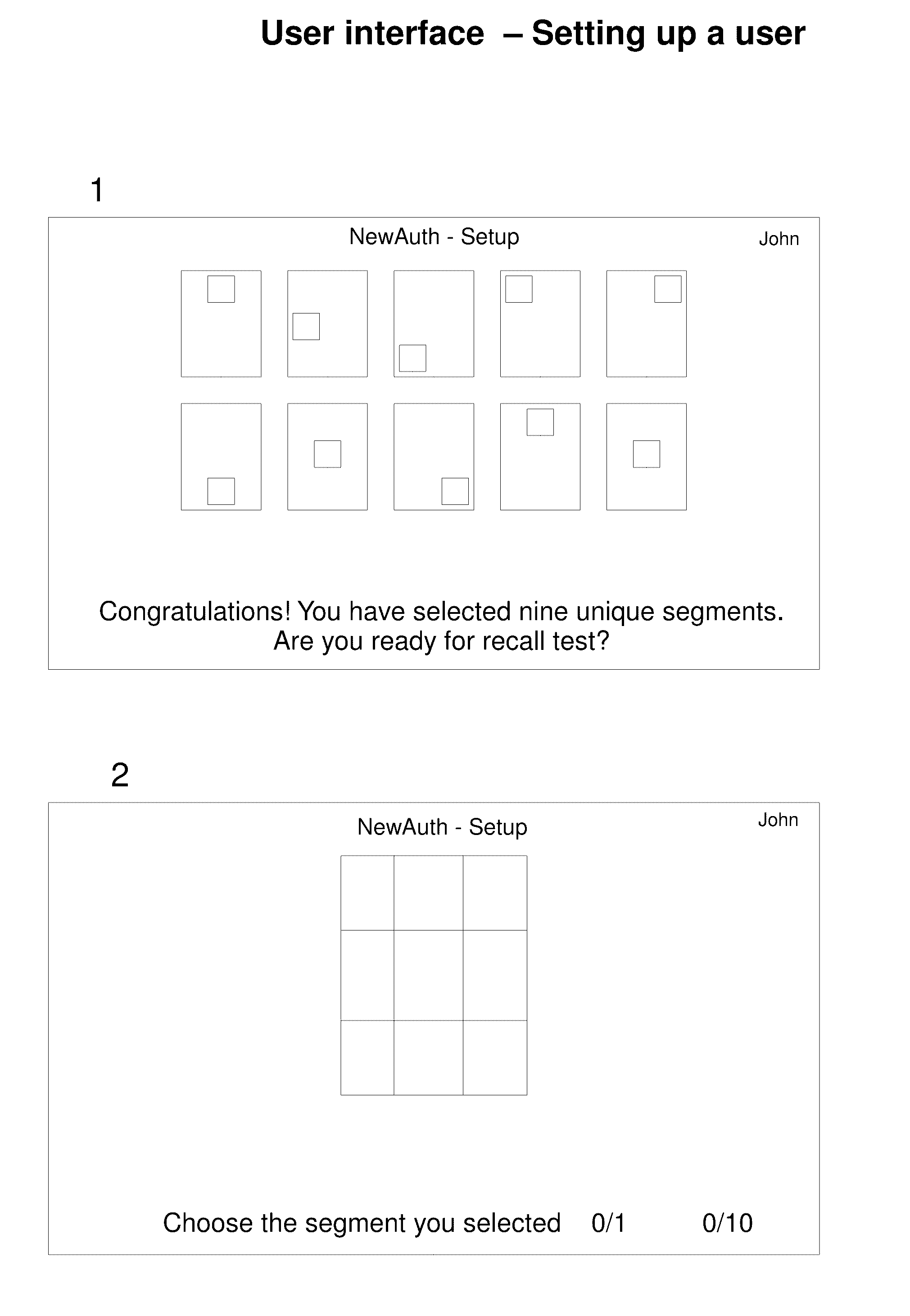Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48 results about "Text value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
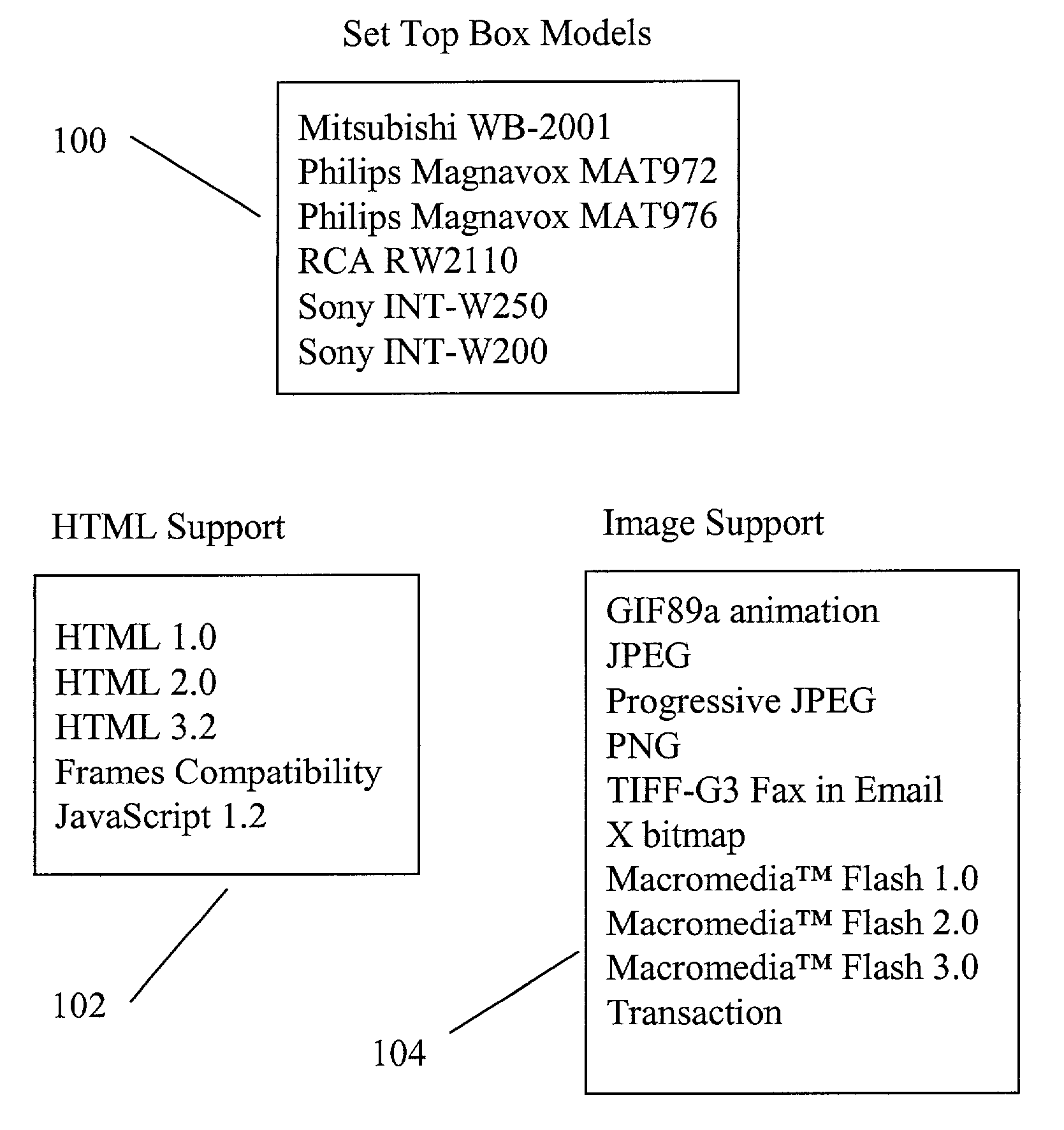
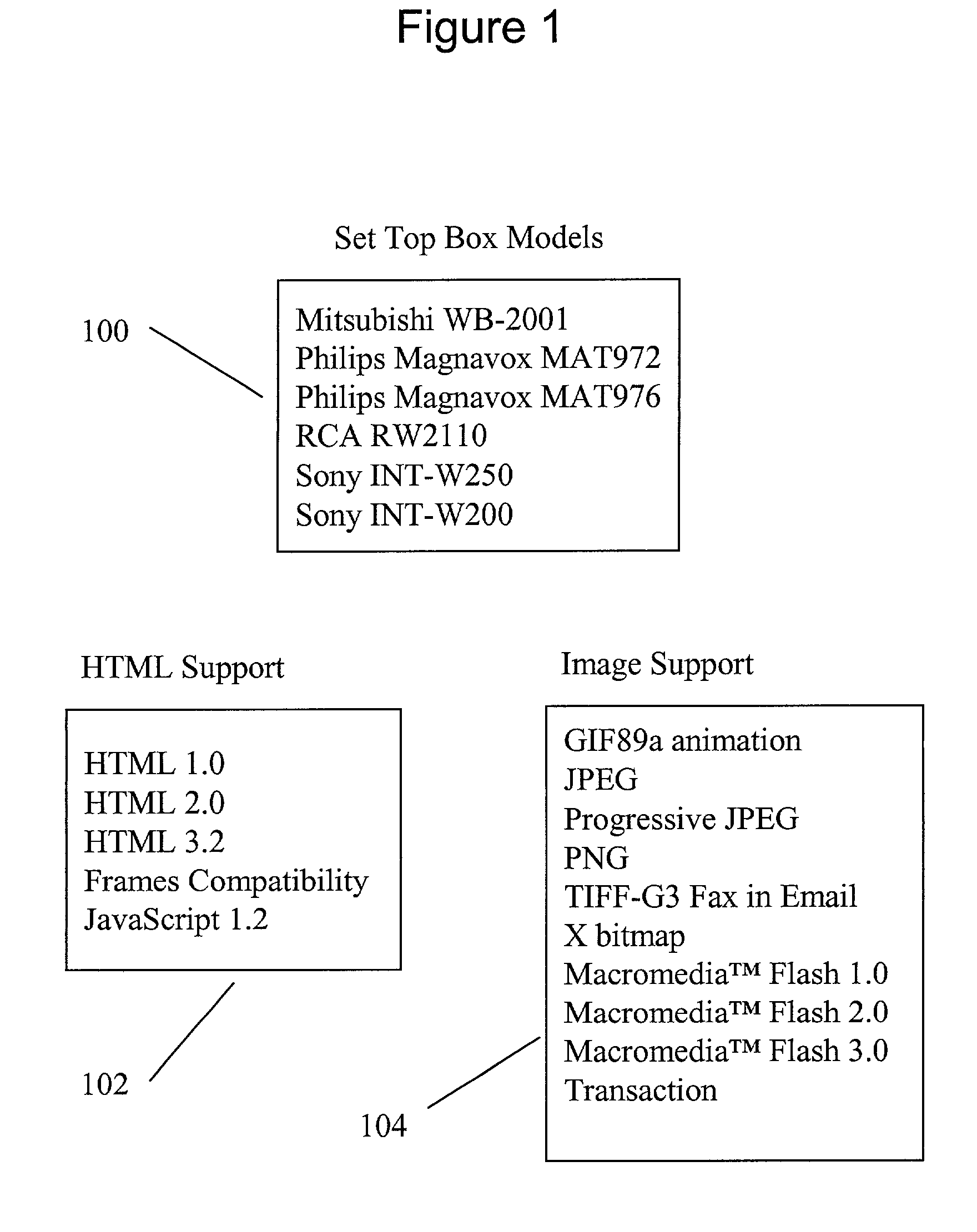
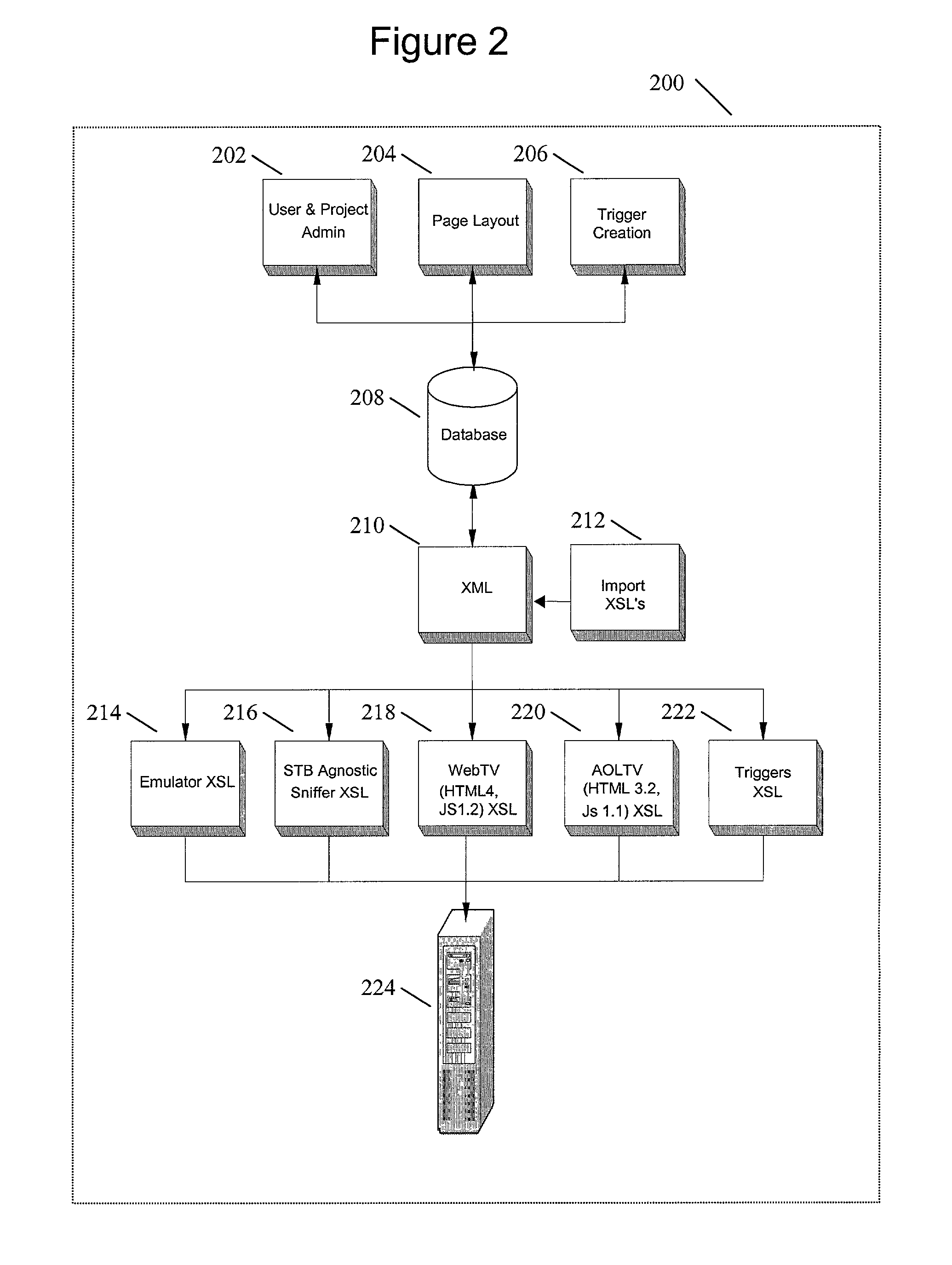
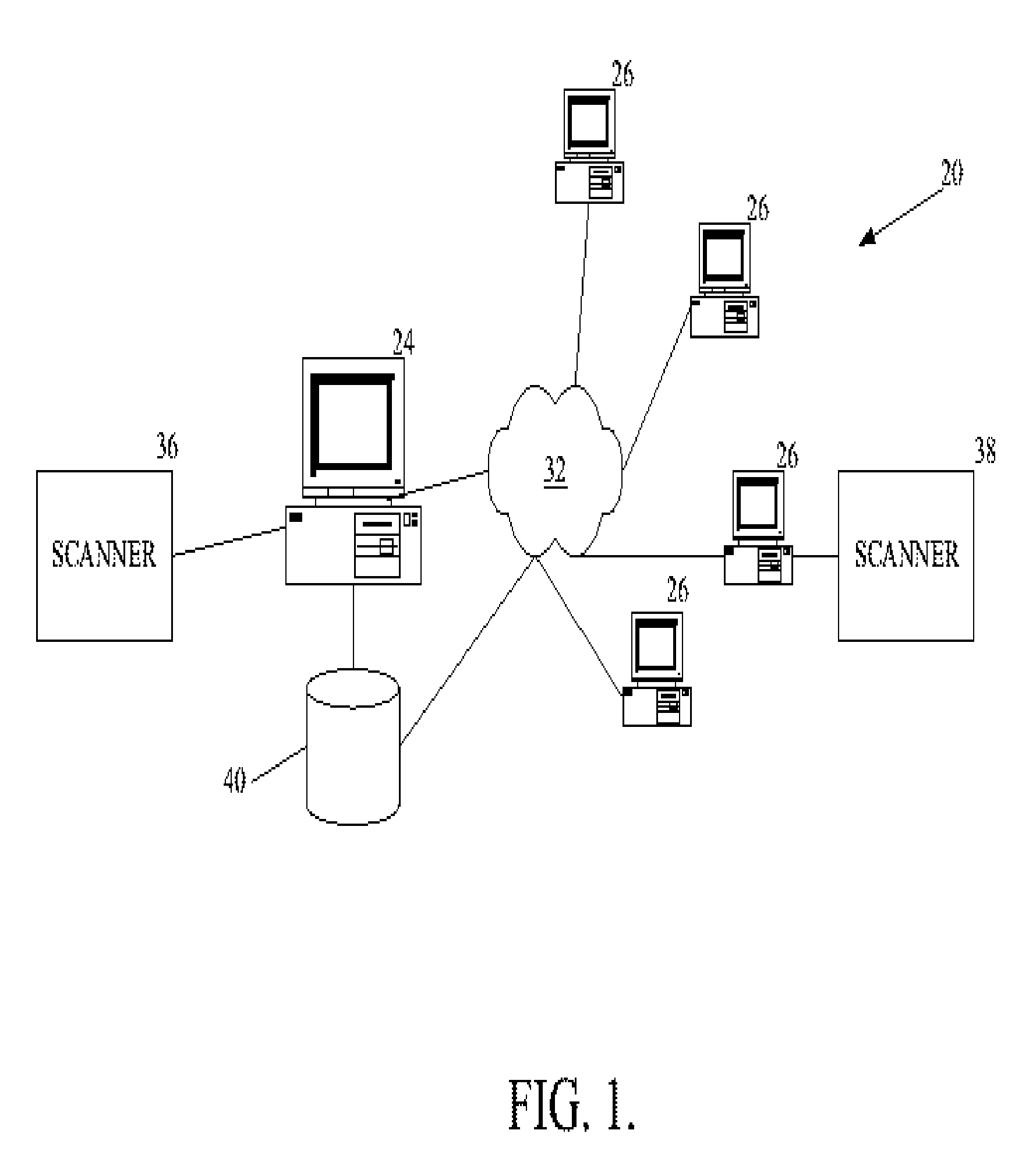
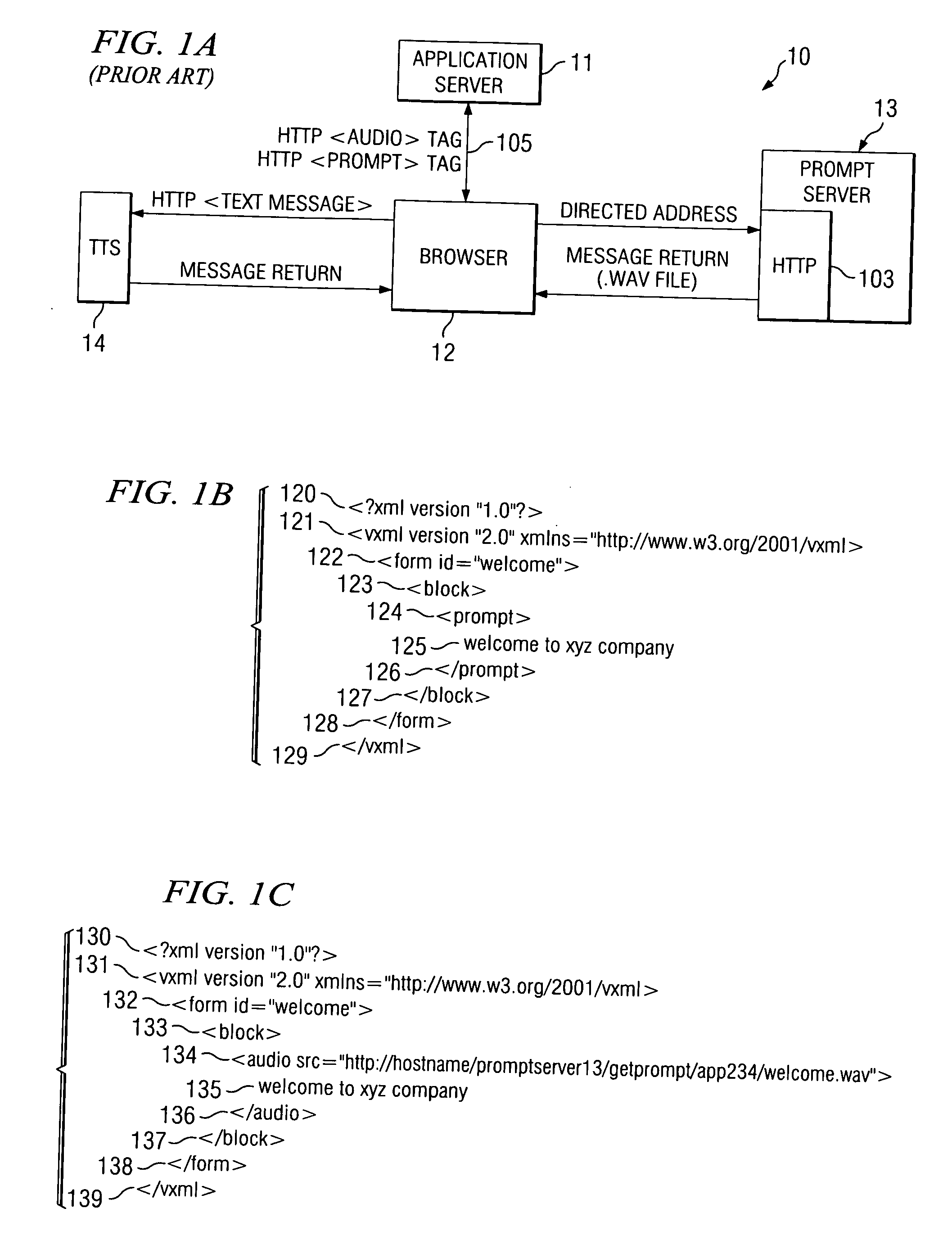
System and method for distribution of interactive content to multiple targeted presentation platforms
ActiveUS7162697B2Television system detailsAnalogue secracy/subscription systemsContent distributionDisplay device
A text based script file describing enhancements is parsed to produce platform dependent enhancement files that may be employed to produce enhancements on a set top box, enhanced television, or computer display. A script file may be of XML format and a parser may be an XSL translator. A parser may import HTML and Javascript from other applications. A parser may support a media player for emulation to view video and enhancements. Trigger data for rendering enhancements may be formatted into a javascript array. Trigger events may be employed to replace graphic pointers or text values. Multiple parsers, each supporting a specific platform, allow a single script file to be employed across multiple platforms. New platforms or versions of platforms are supported through new or updated parsers.
Owner:OPEN TV INC
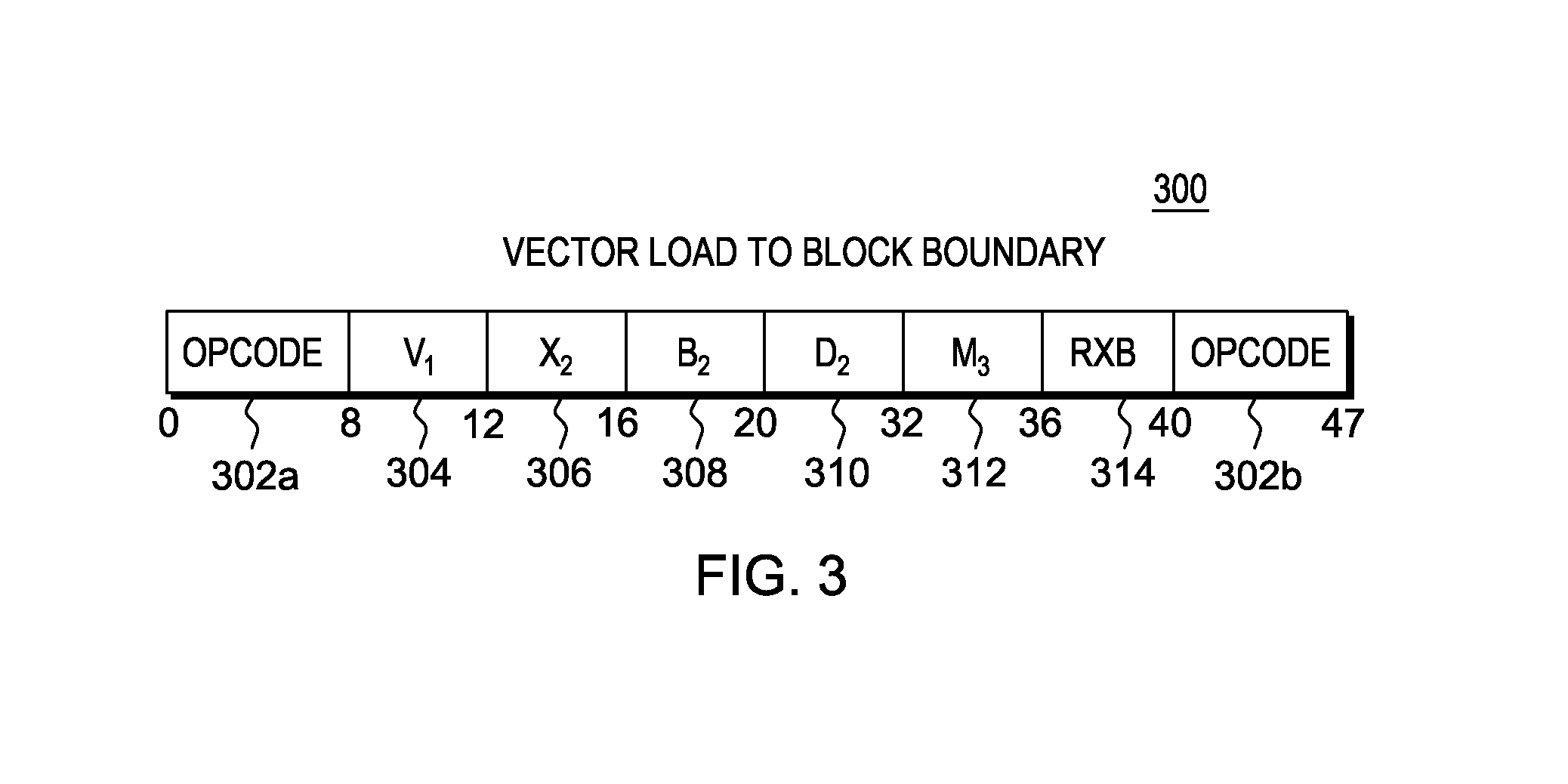
Instruction to load data up to a specified memory boundary indicated by the instruction
ActiveUS20130246764A1Quick conversionAccurate operationRegister arrangementsInstruction analysisProcessor registerParallel computing
A Load to Block Boundary instruction is provided that loads a variable number of bytes of data into a register while ensuring that a specified memory boundary is not crossed. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary.
Owner:IBM CORP
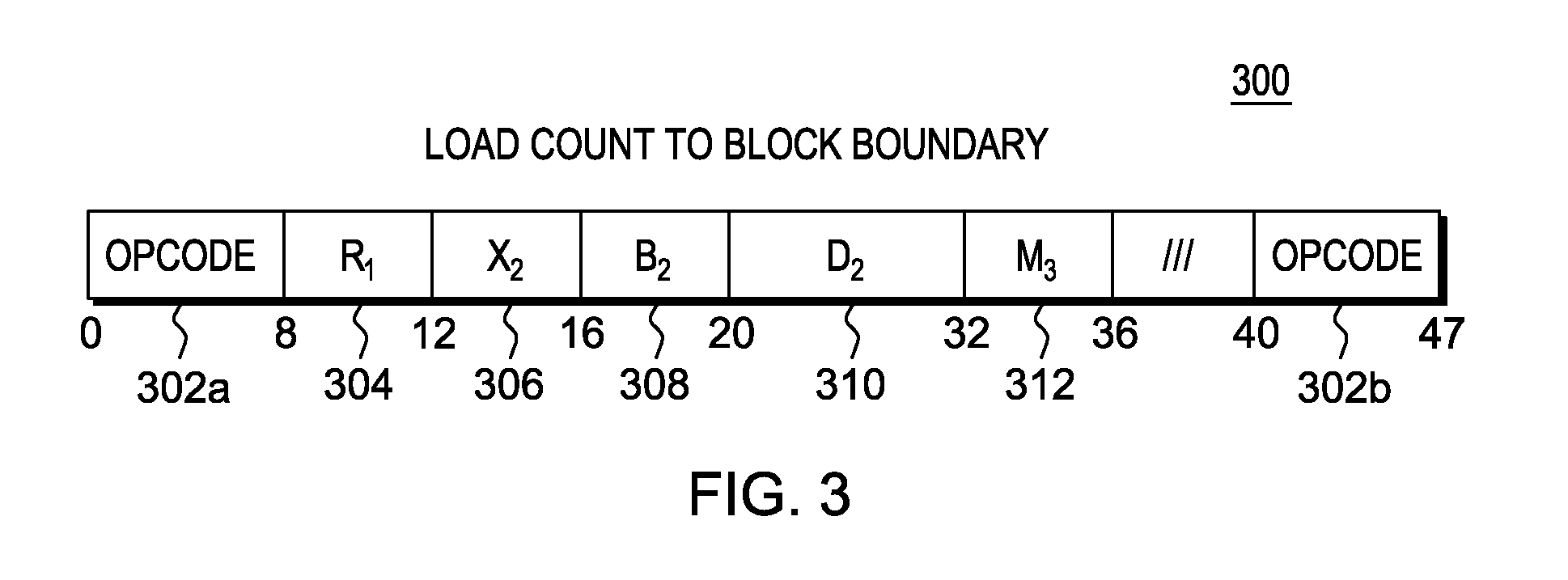
Instruction to compute the distance to a specified memory boundary
ActiveUS20130246767A1Quick conversionAccurate operationInstruction analysisDigital computer detailsMemory addressProcessor register
A Load Count to Block Boundary instruction is provided that provides a distance from a specified memory address to a specified memory boundary. The memory boundary is a boundary that is not to be crossed in loading data. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary; or it may be dynamically determined.
Owner:IBM CORP
Instruction to load data up to a specified memory boundary indicated by the instruction
ActiveUS20130246738A1Quick conversionAccurate operationRegister arrangementsInstruction analysisProcessor registerParallel computing
A Load to Block Boundary instruction is provided that loads a variable number of bytes of data into a register while ensuring that a specified memory boundary is not crossed. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary.
Owner:IBM CORP
Instruction to compute the distance to a specified memory boundary
A Load Count to Block Boundary instruction is provided that provides a distance from a specified memory address to a specified memory boundary. The memory boundary is a boundary that is not to be crossed in loading data. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary; or it may be dynamically determined.
Owner:IBM CORP
System and Method for Preserving and Displaying Physical Attributes in a Document Imaging System
InactiveUS20060031261A1Easy to browseSpecial data processing applicationsDocument management systemsGraphicsData mining
A system, method, and user interface that allows one to easily navigate a document hierarchy. Document groups are represented graphically with an icon that represents the group type. The icons represent preserved physical attributes of the physical original documents. The icons are dynamically generated based on the preserved physical attribute information. The preserved physical attribute information is initially stored within delimited text values that are stored in a filename but may also be extracted from the filename for storage or use in other data structures. When a document group is selected, the contents (subgroups, documents, etc.) are presented to a user.
Owner:BEE DOCUMENT
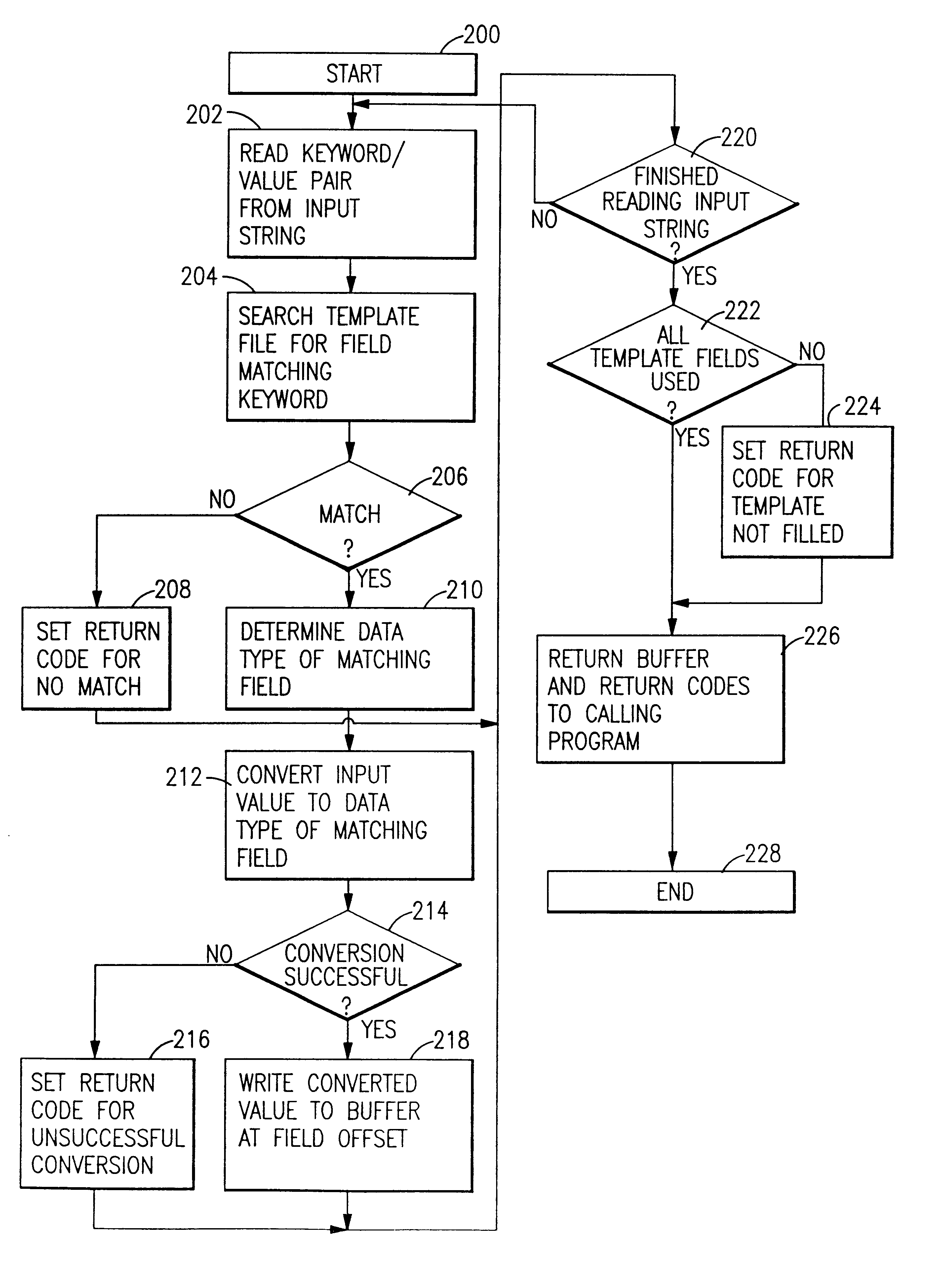
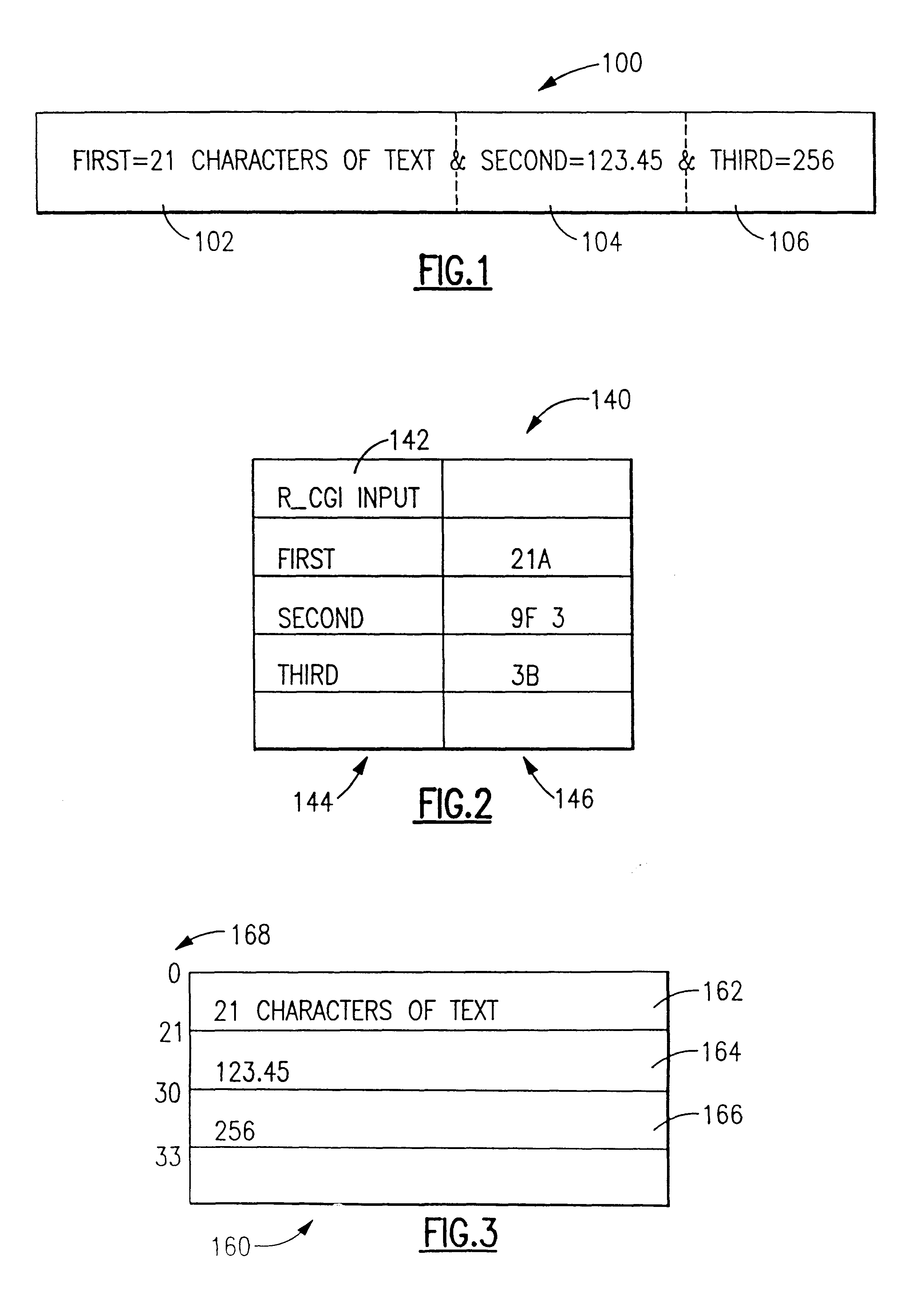
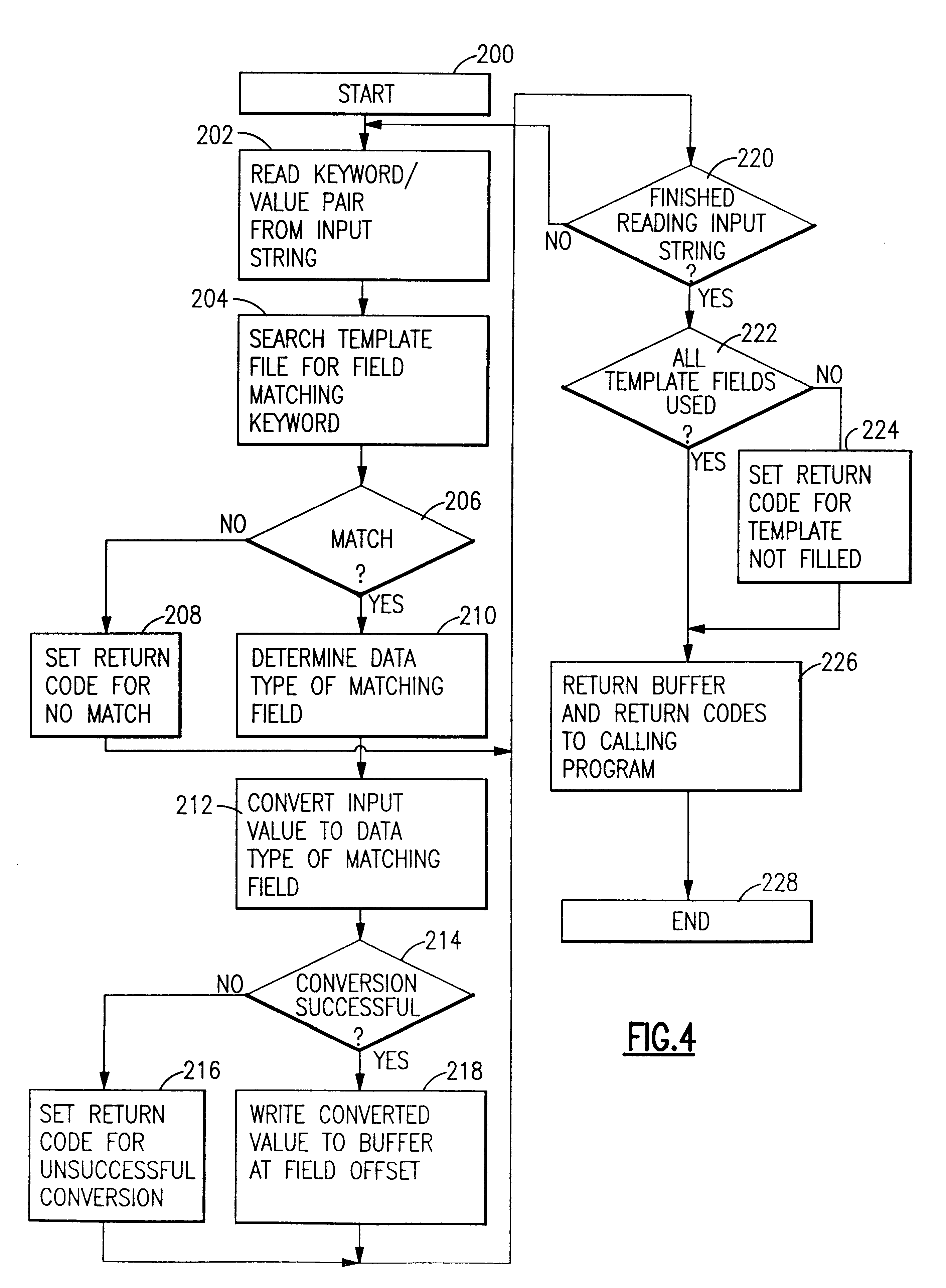
System and method for building a data structure of converted values without keywords from an input string including keyword/text value pairs
InactiveUS6173288B1Data processing applicationsDigital data information retrievalApplication softwareText value
An application program interface (API) provides an interface for common gateway interface (CGI) programs to parse a CGI input string of keywords and their values, each keyword / value pair being all text data separated by a deliminter character, into a buffer which is formated according to a data definition (DDS) file specification or template, thus building a data structure of converted values without keywords from an input string including keyword and text value pairs.
Owner:IBM CORP
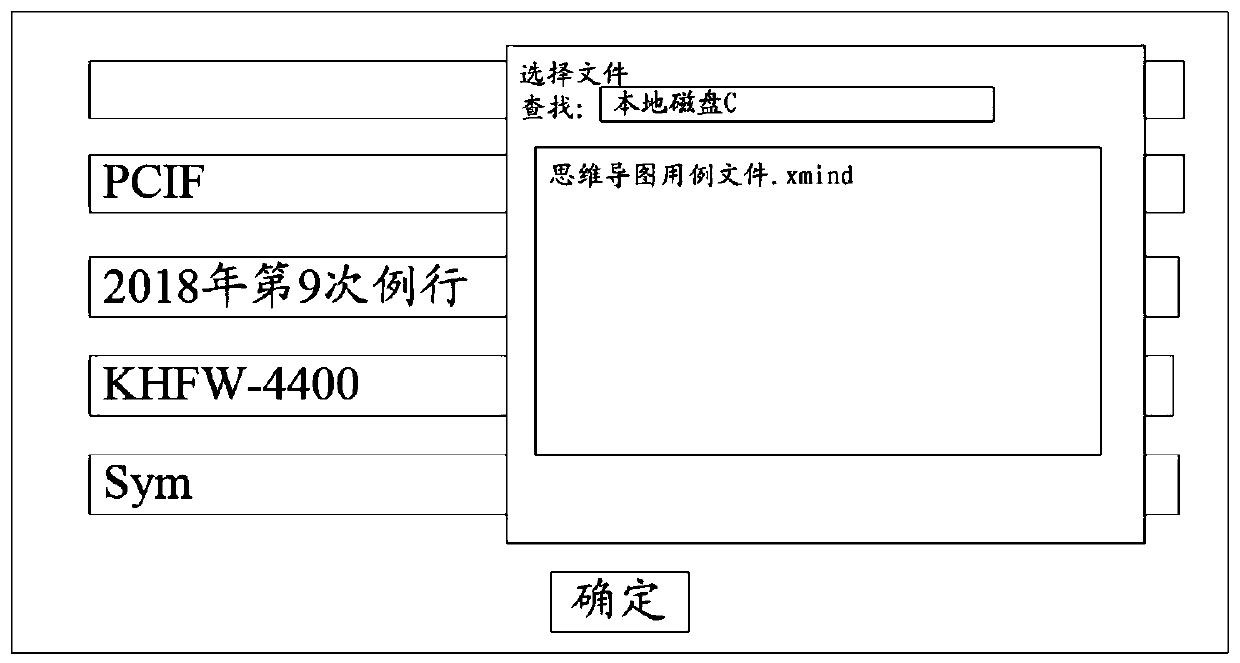
A mind map use case file conversion method and device
ActiveCN109740122AShorten the timeSoftware testing/debuggingEnergy efficient computingRelationship - FatherStandard form
The invention discloses a mind map use case file conversion method and device, relates to the computer technology, and the method and the device are used for converting a mind map use case file into an excel test case convenient for team management. The method comprises the steps of obtaining a mind map use case file; traversing the father node and the plurality of child nodes corresponding to thefather node to obtain a plurality of text values, and storing the plurality of text values to a dynamic array Array; obtaining a configuration file of the standard use case template file, the configuration file comprising a plurality of use case names; analyzing the Graylist to obtain a plurality of text values corresponding to the plurality of use case names; and determining a standard form fileaccording to the plurality of use case names and the text values corresponding to the plurality of use case names. The embodiment of the invention is applied to converting the mind map use case fileinto the standard excel test case.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
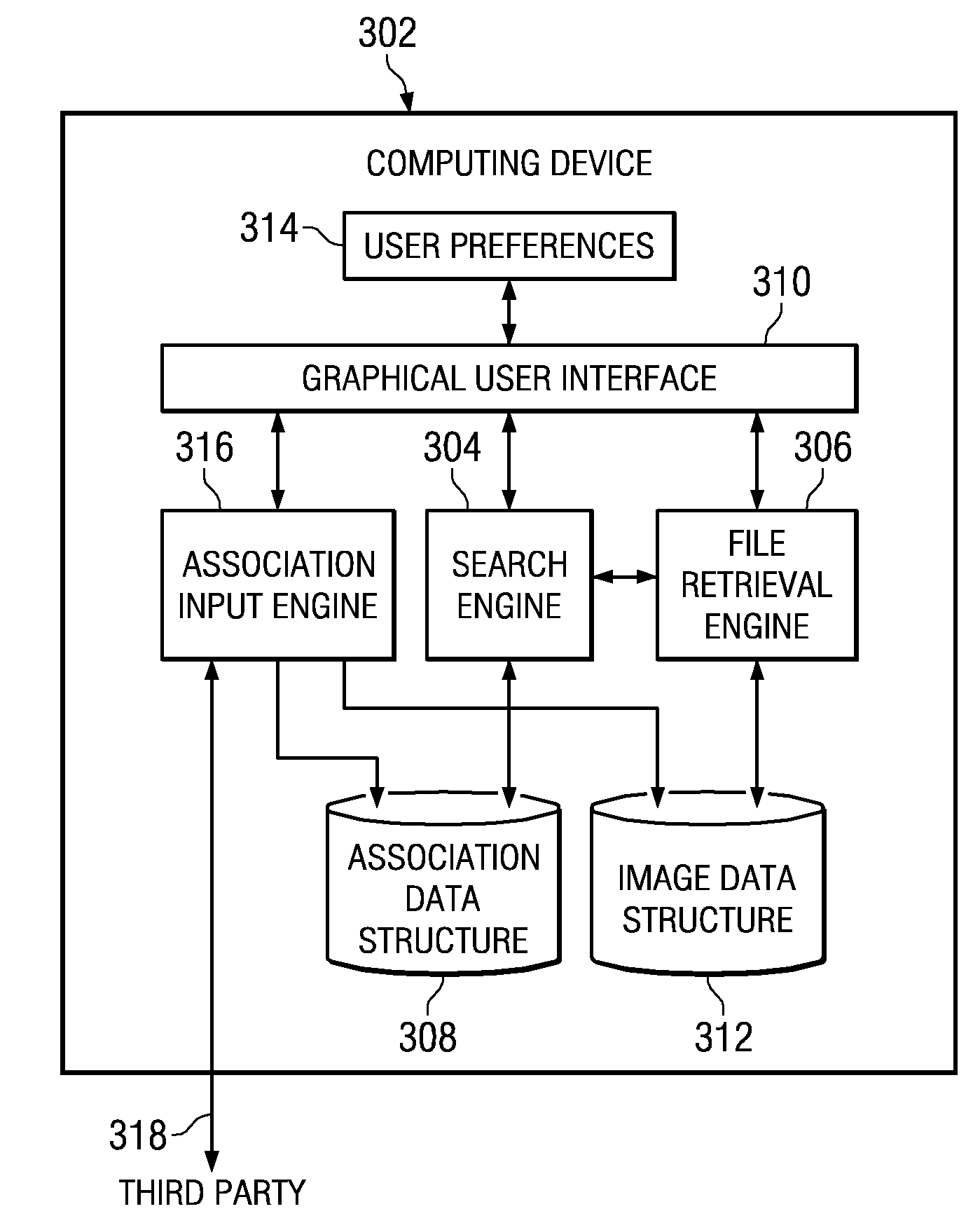
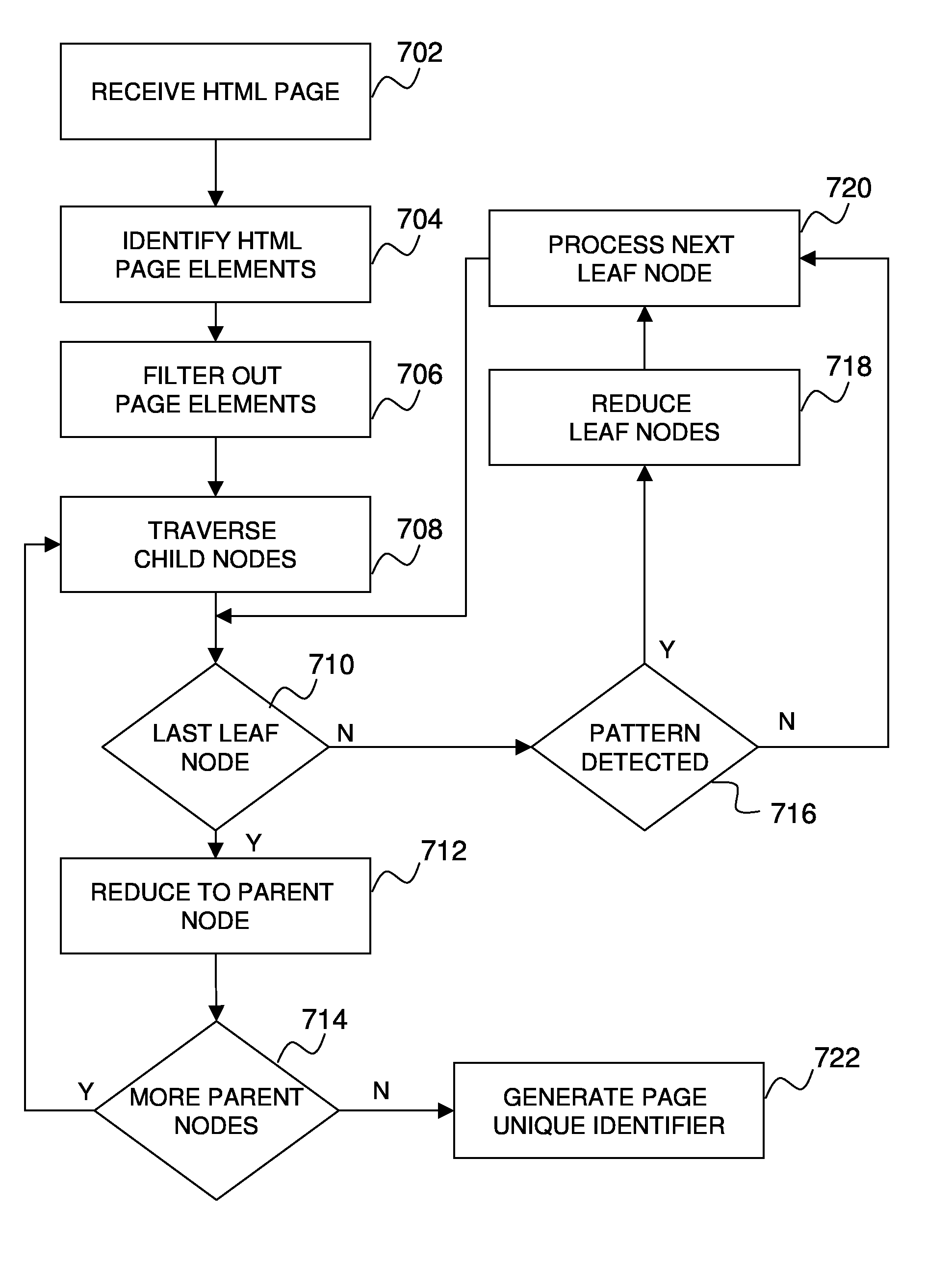
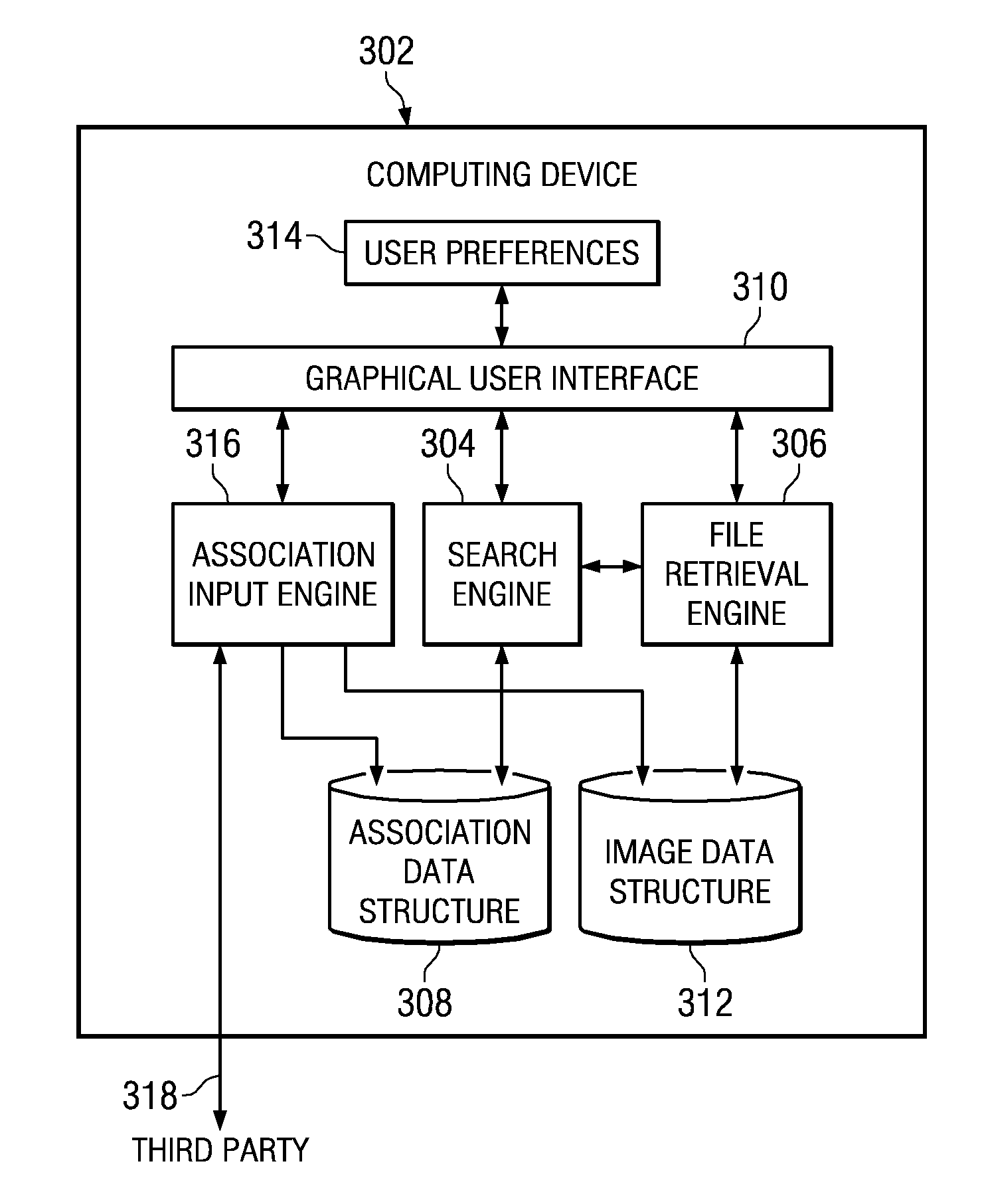
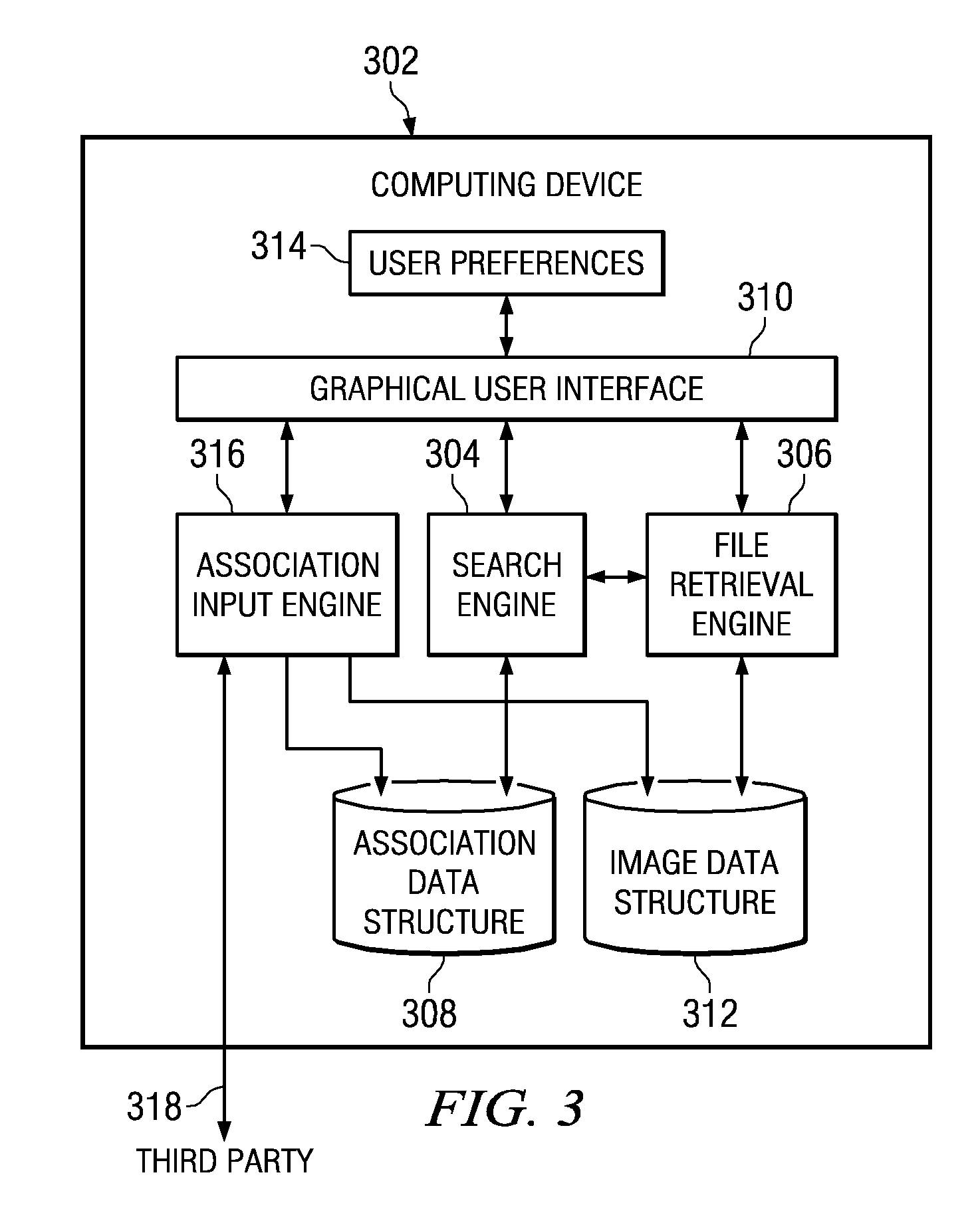
Method and system for translating text into visual imagery content
InactiveUS20090119308A1Natural language translationDigital data processing detailsSearch data structureGraphics
A method, system, and computer program product are provided for translating text into visual imagery content. A request is received to identify at least one image associated with a text value. At least one association category from a plurality of association categories is identified with which to perform a search. A data structure is searched, using the at least one association category, for an identification of the at least one image that is associated with the text value. The at least one image is a visual representation of the text value. At least one image is retrieved in response to identifying at least one image associated with the text value. The at least one image is presented in a graphical user interface to a user.
Owner:LINKEDIN
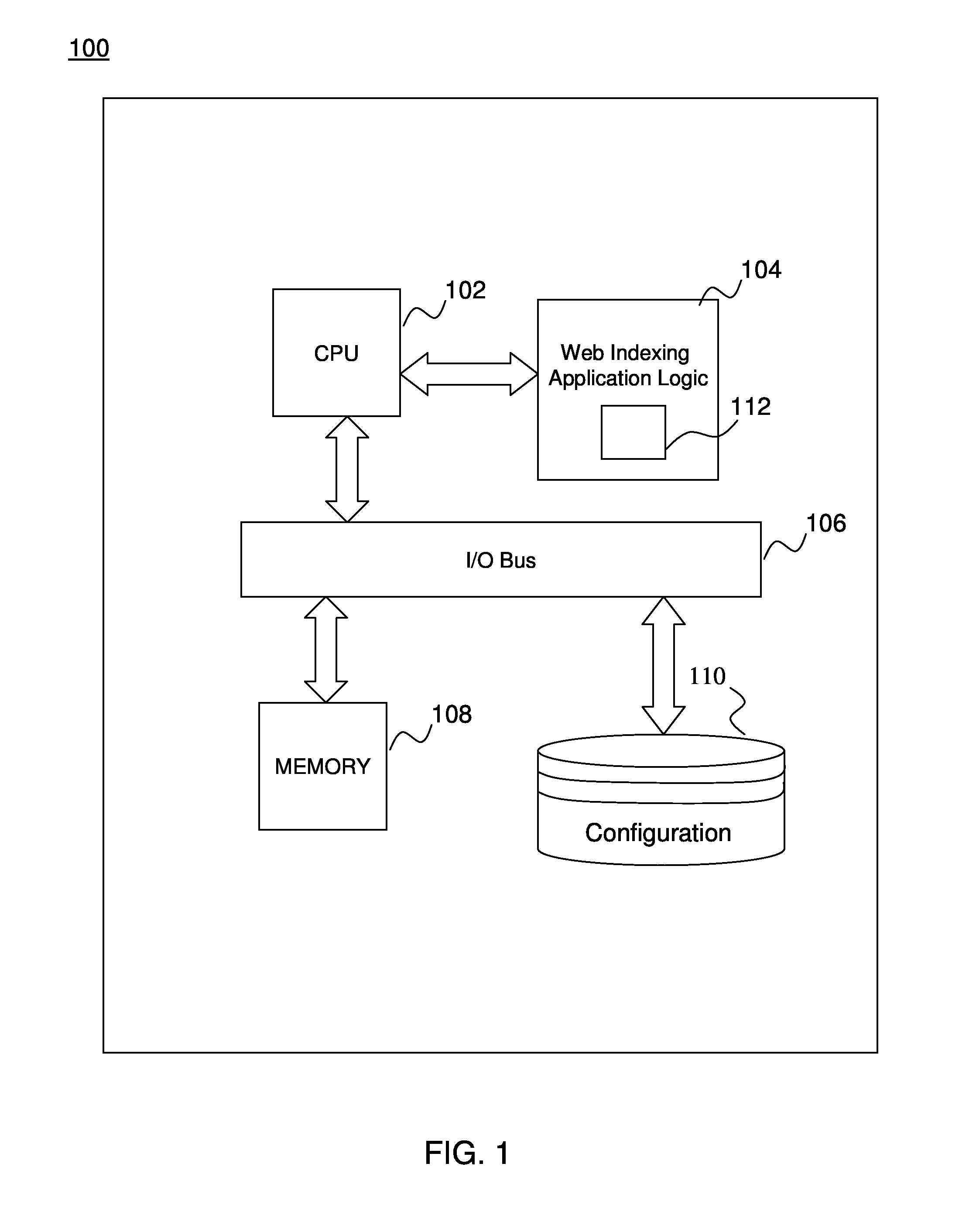
Document object model (DOM) based page uniqueness detection
DOM based unique ID generation, including receiving a hypertext markup language (HTML) page at a computer, and identifying HTML page elements in response to the receiving, the HTML page elements comprising parent nodes, the parent nodes comprising child nodes. The method further comprising processing each of the HTML page elements, the processing comprising: grouping the child nodes by parent node into a group of child nodes, detecting patterns in the group of child nodes in response to the grouping, reducing the group of child nodes to text strings in response to the detecting, storing the text strings as text values in the parent nodes, and generating a unique identifier (ID) of the HTML page in response to the processing.
Owner:TERRACE LICENSING LLC
Methods and devices for encoding and decoding messages
ActiveUS20140355627A1Free memory spaceMaintain compatibilityCode conversionTime-division multiplexDatabaseBitstream
Methods and devices for encoding or decoding messages, each message including a list of information items. The encoding method comprises determining a first list of indexes associated with information items that are already indexed in a local indexing table and a second list of literal values of other information items not yet indexed in said indexing table; encoding the indexes of the first list; binary compressing at least a serialized binary representation of the literal values of the second list; and concatenating the first list and the second list together to obtain an encoded bitstream of the information items. When the messages are sent over a plurality of connections, a global table is shared between the connections to store the indexed items of information; and a local indexing table for each connection associates indexes with references to an entry of the shared global table.
Owner:CANON KK
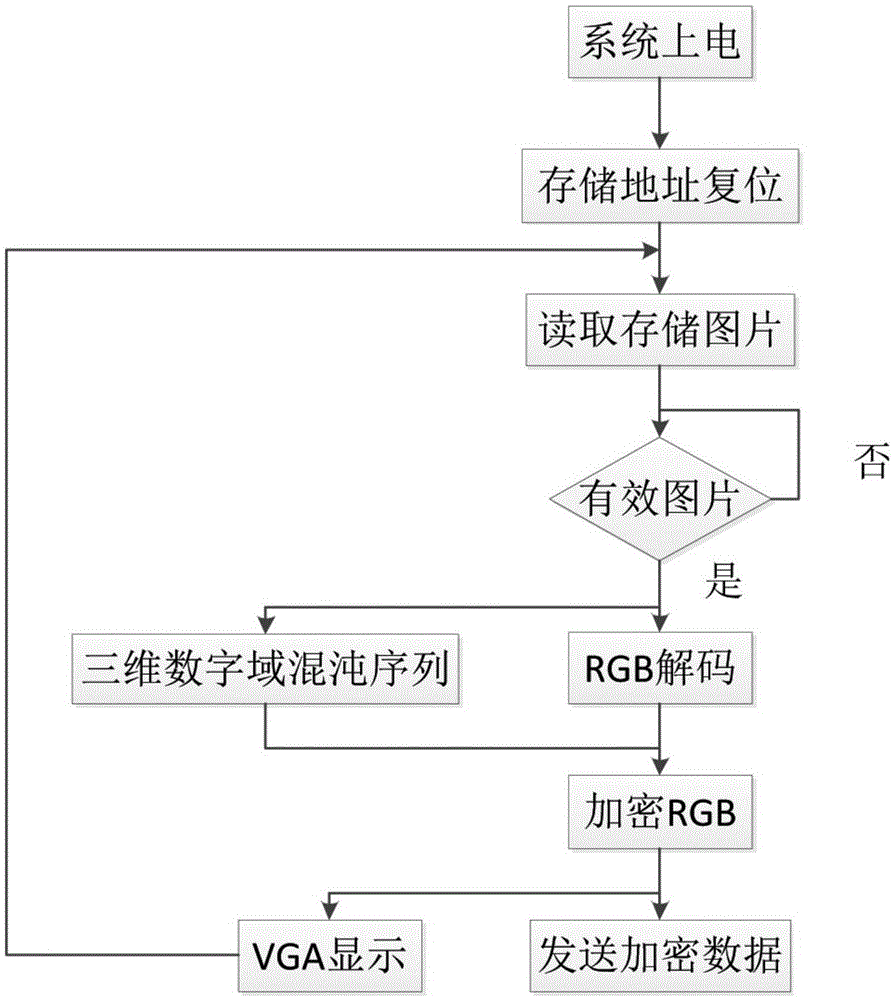
Video secure communication method based on integer field chaos
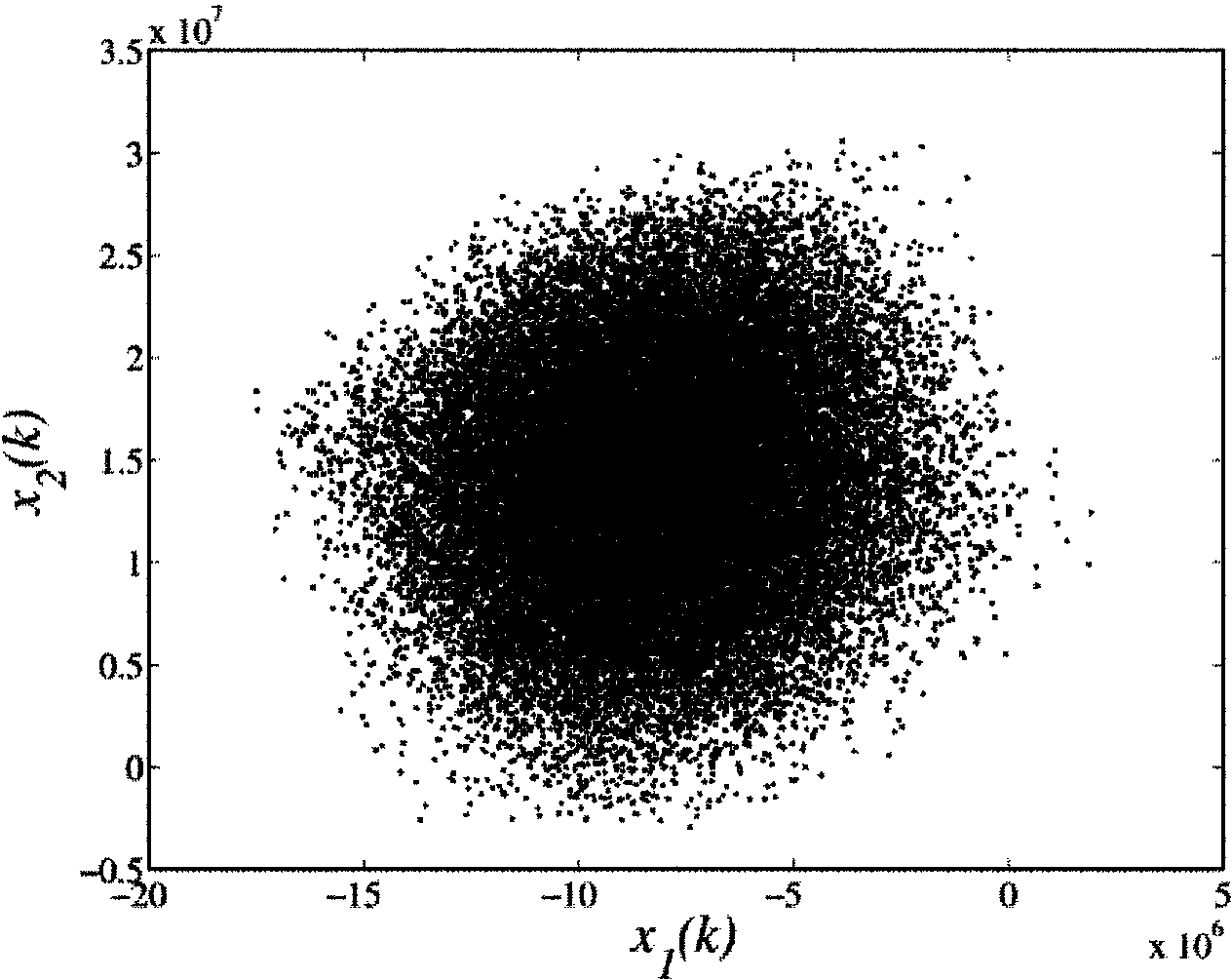
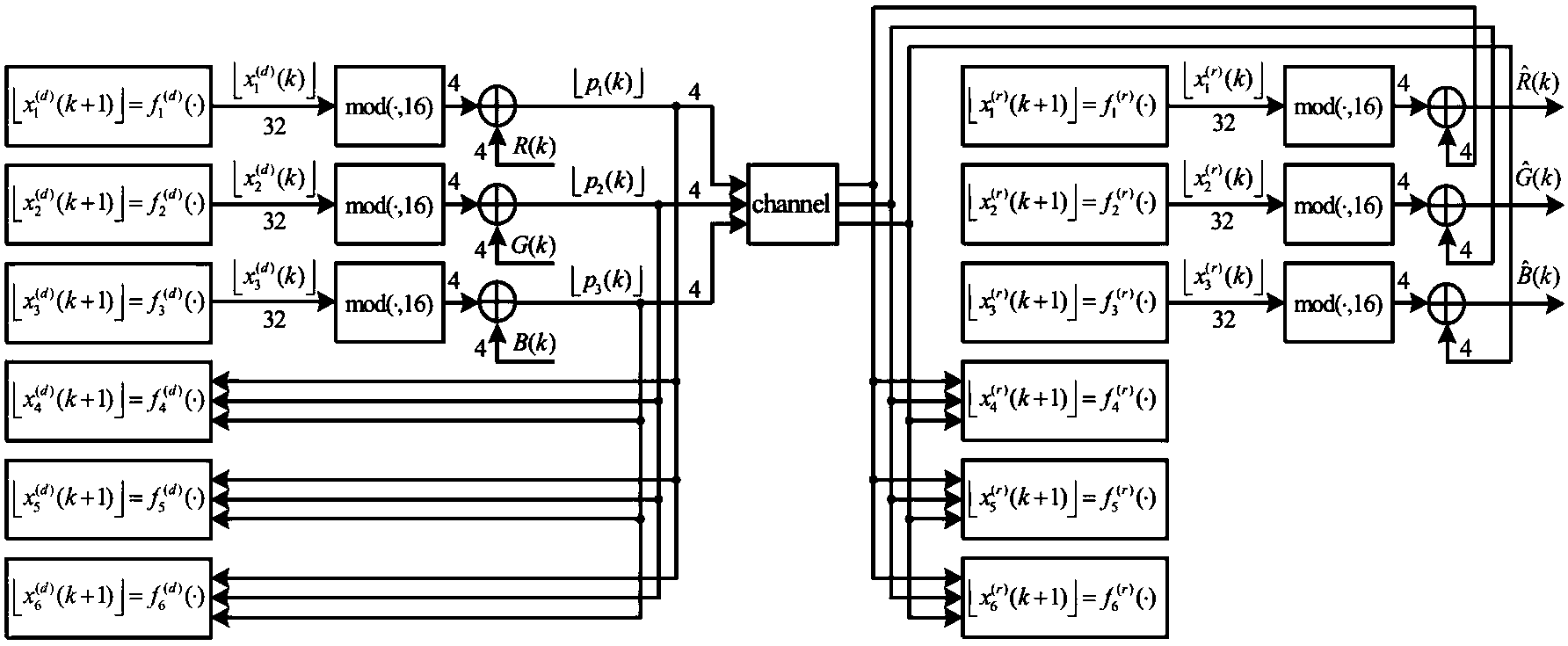
ActiveCN104320241AHigh degree of reductionAchieve synchronizationSecuring communicationSecure communicationComputer hardware
The invention discloses a video chaos secure communication method based on integer field chaos. The method comprises the following steps: establishing a six-dimensional integer field discrete time chaos system; iterating three variables x<1><(d)>(k), x<2><(d)>(k) and x<3><(d)>(k), and converting the iterated variables into binary digital information through digital information encryption equipment; performing encryption operation on information of a transmitting end; transmitting cipher text values of red, green and blue video signals from the transmitting end to a receiving end through a channel; and decrypting the information of the receiving end. Real-time encryption and decryption of videos are implemented by adopting an integer field chaos system, so that the problems of large video data operation amount and complex algorithm are solved. Since a cascade closed-loop principle is adopted, a transmitting end system and a receiving end system have completely the same driving signals; strict synchronization can be realized without being influenced by information size adjustment; and decrypted information has a very high reduction degree under the condition that parameters of the transmitting end and the receiving end are matched.
Owner:GUANGDONG UNIV OF TECH
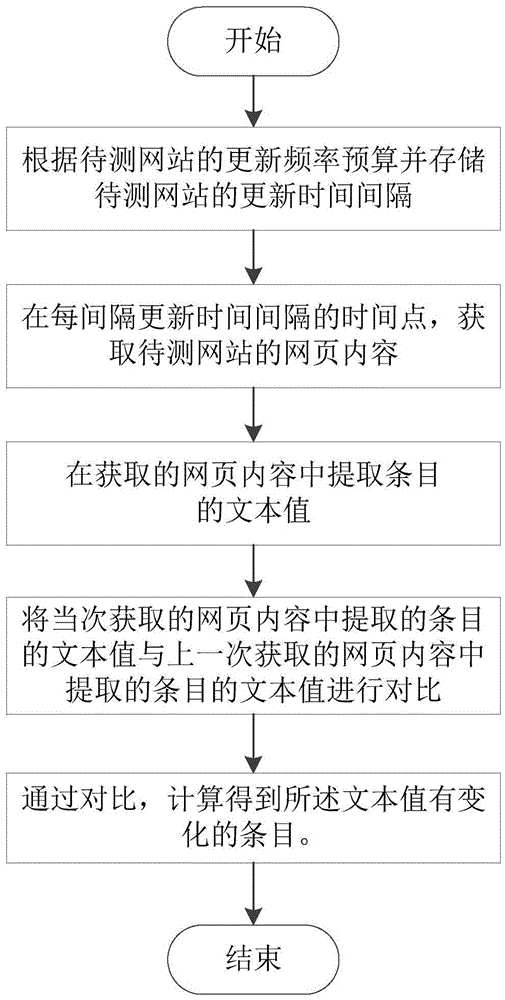
Method and system for monitoring update contents of website
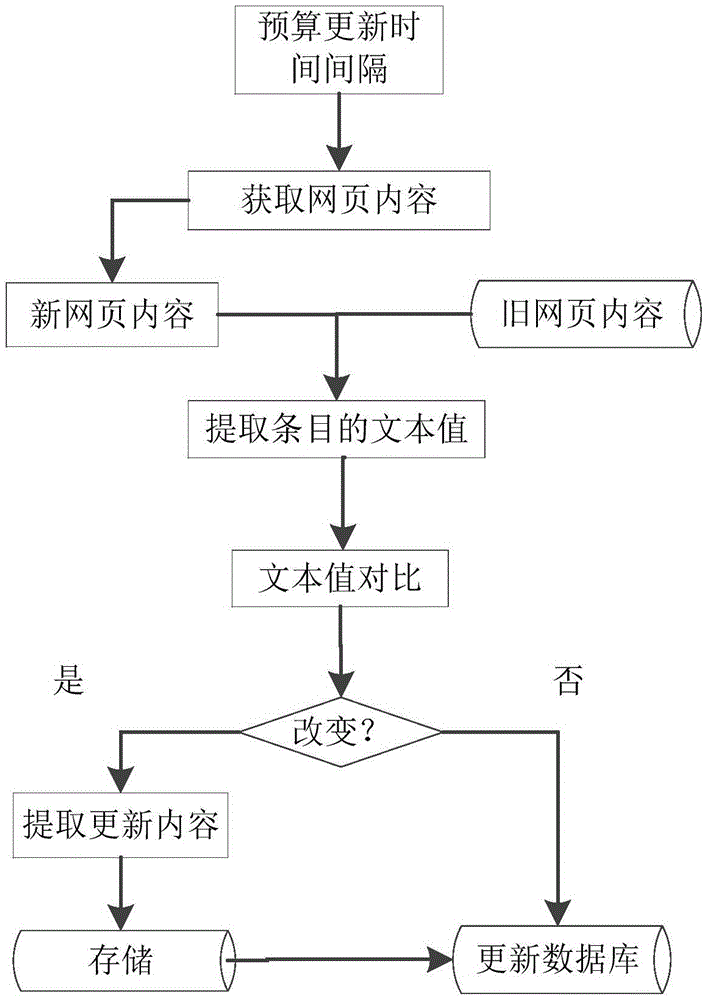
ActiveCN105528416AReduce network trafficSmall amount of calculationWeb data indexingWebsite content managementWeb siteRenewal time
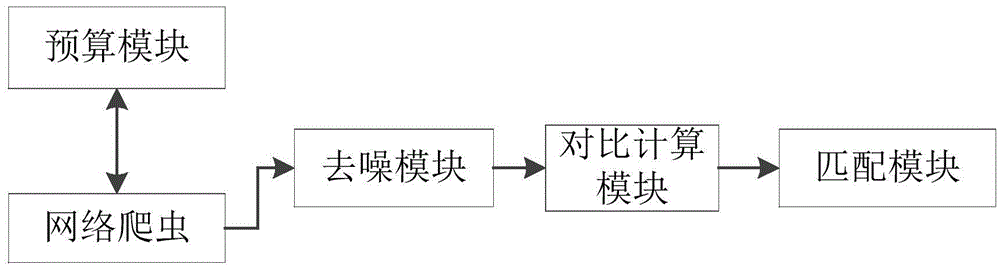
The present invention discloses a method and system for monitoring update contents of a website. The method comprises the steps of pre-calculating and storing update time intervals of a to-be-tested website according to update frequency of the to-be-tested website; obtaining webpage contents of the to-be-tested website and extracting text values of items at a time of every update time interval; and comparing the text values of the items extracted from the current webpage contents with the text values of the items extracted from the last webpage contents, and calculating and obtaining the items with the text values changed. The system comprises a pre-calculating module, a web crawler, a denoising module, a comparing and calculating module and a matching module. The update contents of the website can be rapidly and accurately obtained with little calculated amount, real-time update monitoring can be carried out for any website, and application is wide and comprehensive.
Owner:CENT SOUTH UNIV
Positioning method and device of mobile application page object
ActiveCN105335288AImprove accuracyImprove compatibilitySoftware testing/debuggingComputer hardwareText value
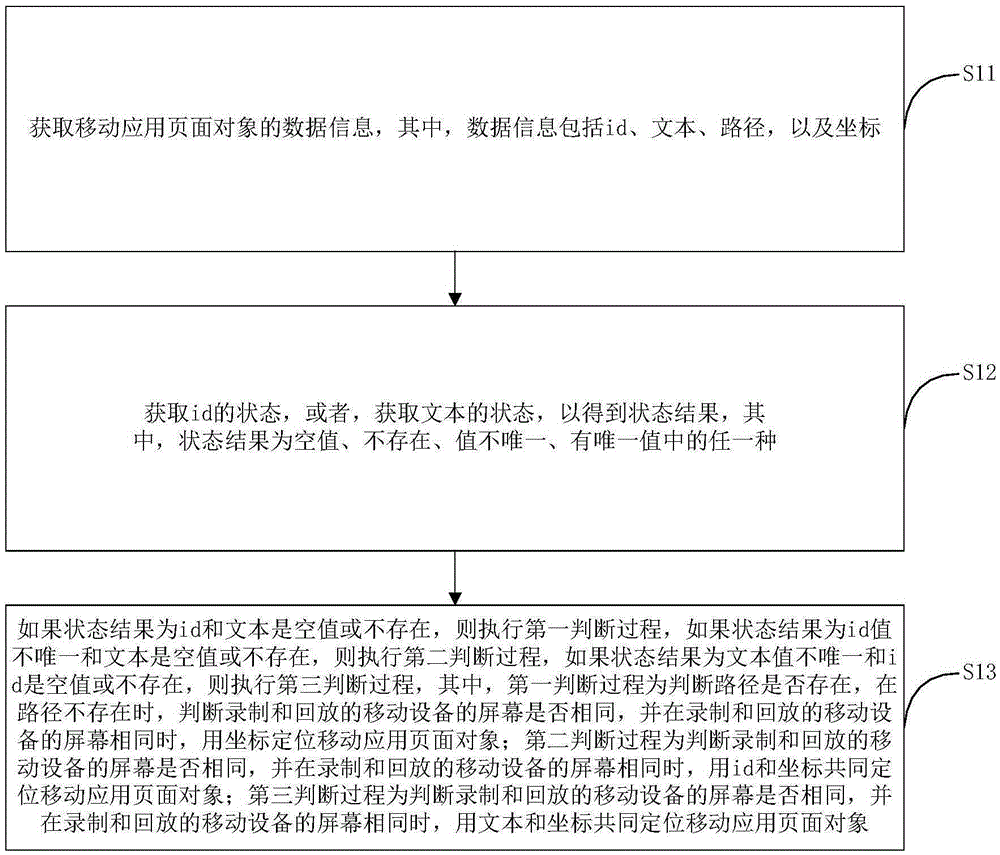
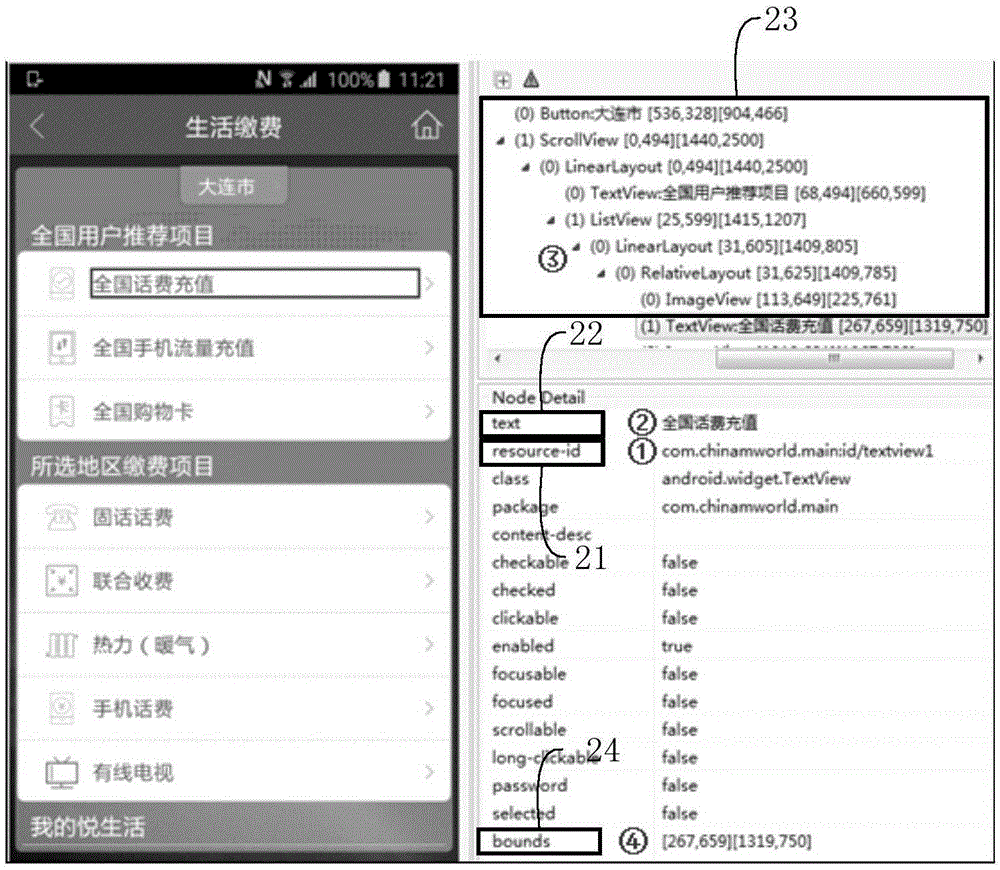
The invention provides a positioning method and device of a mobile application page object. The positioning method of the mobile application page object comprises the steps that when an id and a text of the mobile application page object are a null value or do not exist, executing a first judgment process, when the id value is not exclusive and the text is a null value or does not exist, executing a second judgment process, when the text value is not exclusive and the id is a null value or does not exist, executing a third judgment process, wherein the first judgment process is that when a route does not exist and screens of a recording device and a playback mobile device are identical, the object is positioned by using a coordinate, the second judgment process is that when the screens of the recording and playback mobile devices are identical, the object is collectively positioned by the id and the coordinate, and the third judgment process is that when the screens of the recording and playback mobile devices are identical, the object is collectively positioned by the text and the coordinate. By adopting the method, an appropriate positioning strategy can be self-adaptively determined, and the positioning accuracy and compatibility of the mobile application page object when an automatic testing script is played back can be improved.
Owner:NEUSOFT CORP
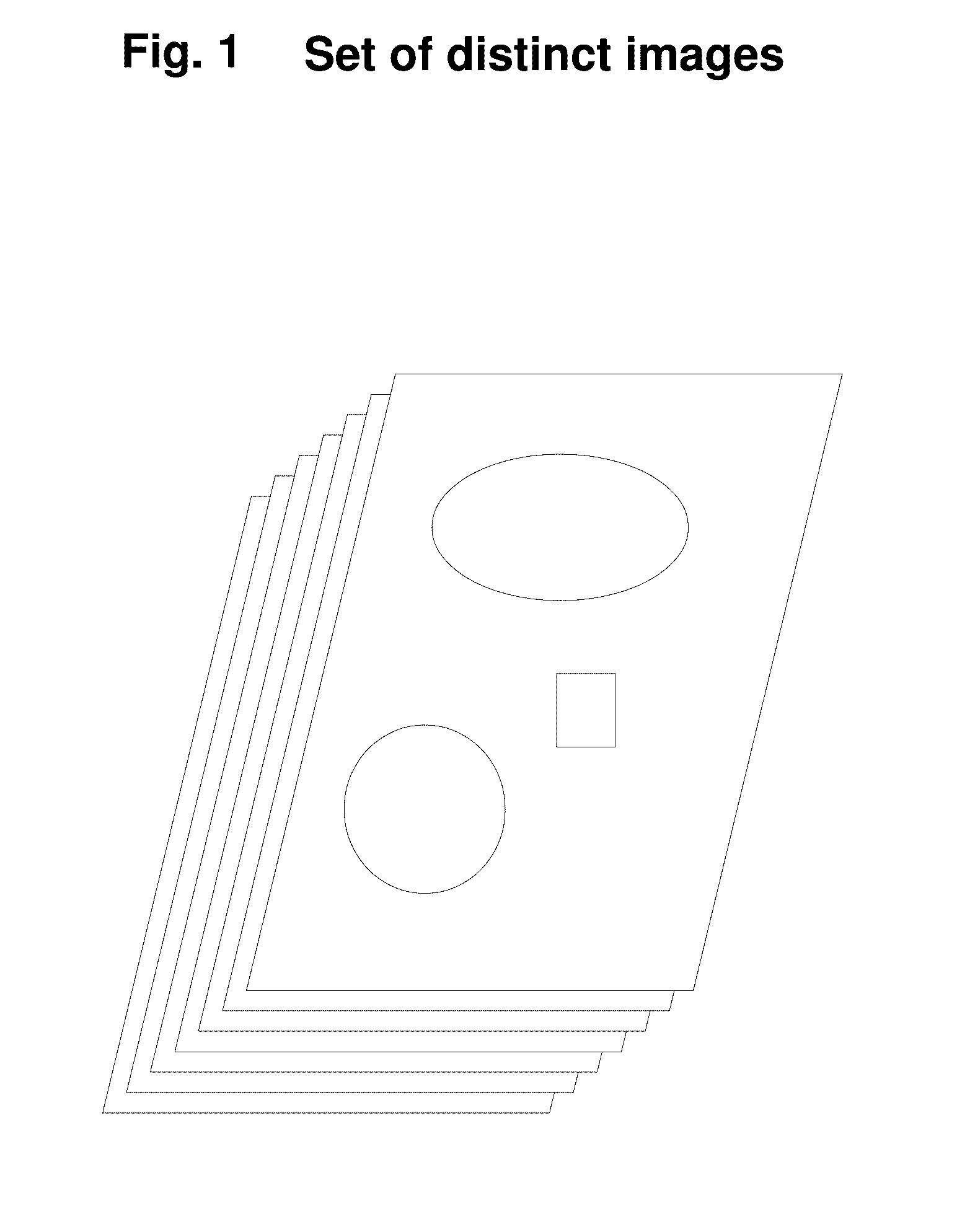
Authentication Based On Visual Memory
ActiveUS20160352722A1Increase and decrease difficultyIncrease the lengthCryptography processingDigital data authenticationPasswordUser input
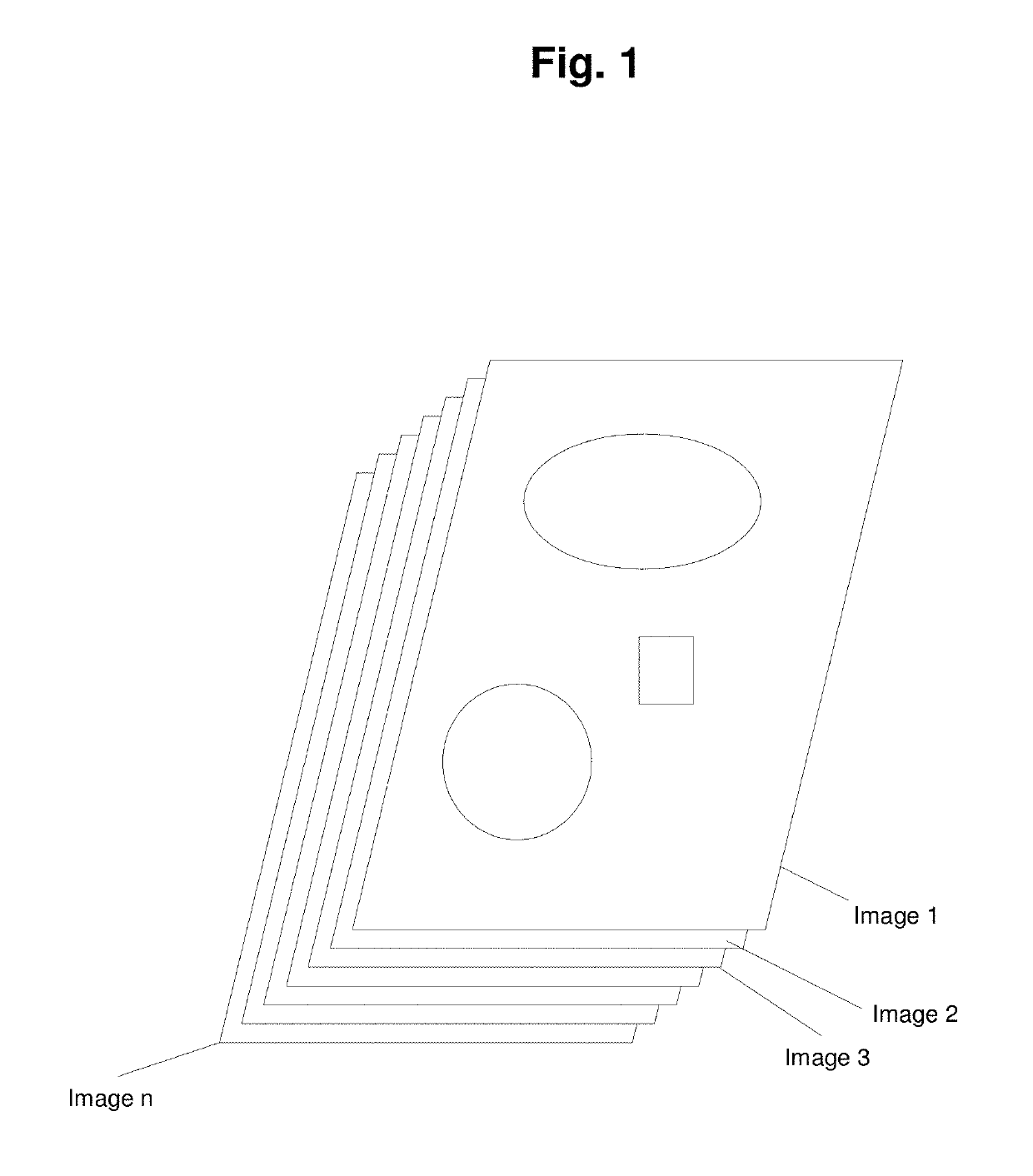
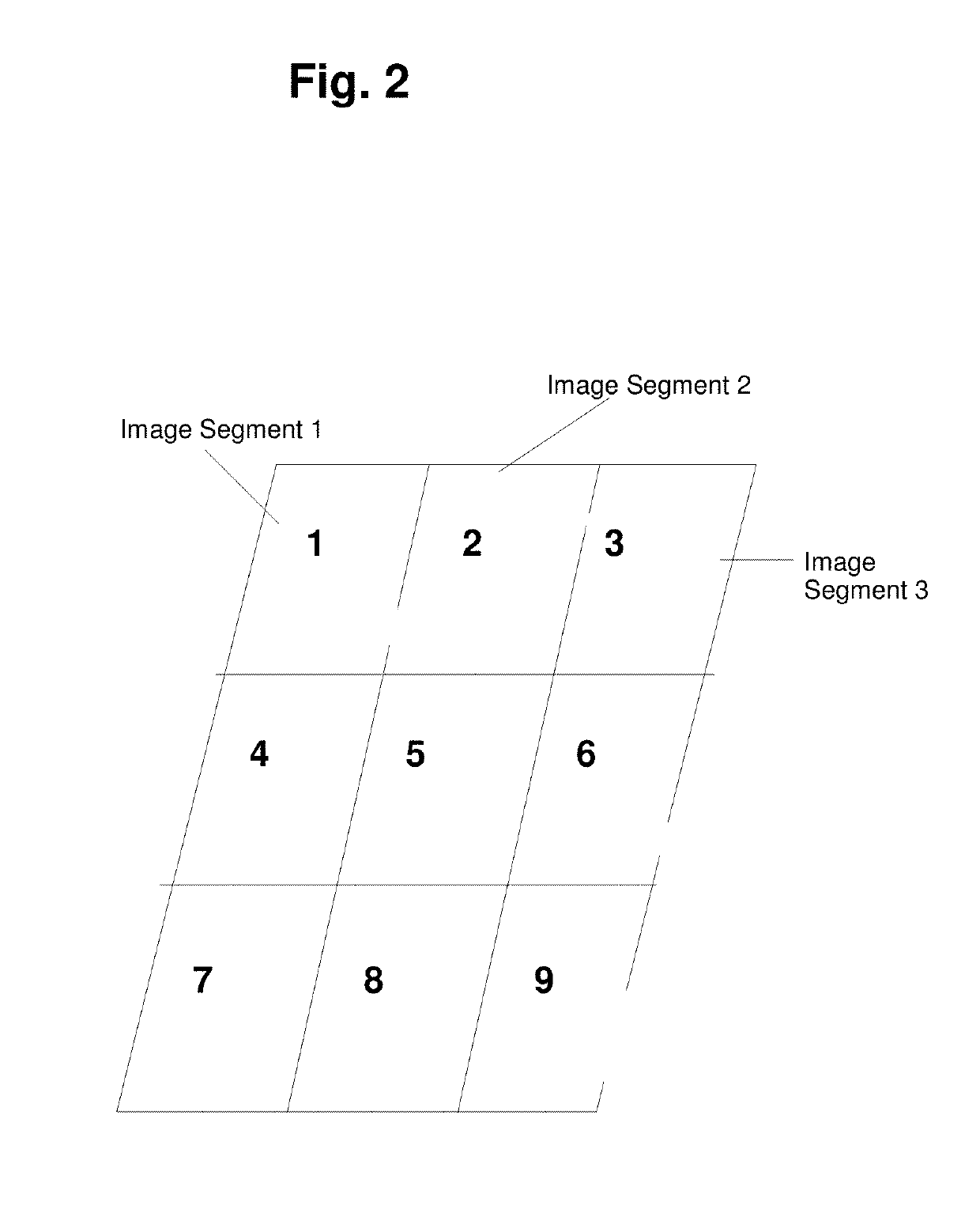
Passwords are used in various system access applications in order to ascertain that the user seeking access to a system resource is indeed the person with said access. Passwords are usually supposed to be entered through a keyboard and are a combination of alphanumeric values. With the advent of devices equipped with visual displays and touch inputs, it is possible to create a system which utilizes a person's visual memory to authenticate the person.A system and method is described which uses multiple images to perform authentication. This system does not require its user to input a text value as a password. The password is created by user's actions. These actions are in the form of selecting a segment on a displayed image. Few different systems are described. One system is capable of creating variable passwords which by design keep changing from one authentication attempt to another. Another system uses one high resolution image to effectively hide the password in an image with lots of detail.
Owner:JOHRI RAJUL
System and method for defining, synthesizing and retrieving variable field utterances from a file server
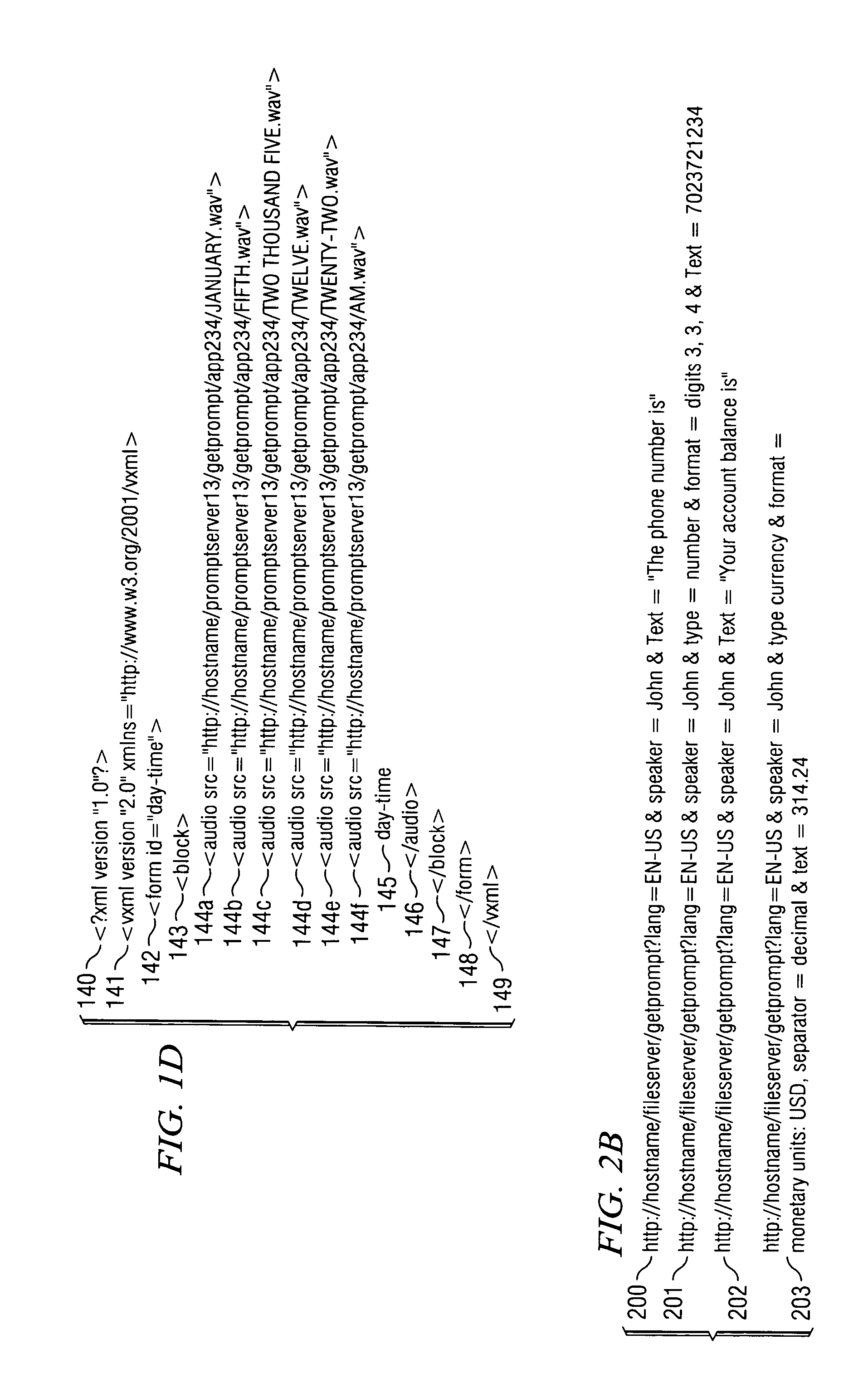
InactiveUS20070201631A1Reduce in quantityNatural soundAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesCredit cardUniform resource locator
There is disclosed a system and method for addressing an audio file server to play pre-recorded audio files, including variable audio files, using a query URL containing the required file's attributes, without requiring a fully-resolved file address. The HTTP URL protocol is used by adding attributes, such as the language, the speaker, and a text version of the desired message, along with other required attributes of the audio file to the URL. The audio file server accepts and analyzes the attributes in the URL to find out what type of variable field is being requested. Normally, variable field prompts created from spliced audio clips are restricted to a few specific types of variable fields, such as time, date, or amount, fields, or numeric strings such as telephone numbers, credit card numbers, etc. Once the audio file server determines the field type, language and speaker from the URL, it examines the field text value from the query attribute string. The file server then calculates and retrieves the set of utterances required to create the desired phrase. The audio file server splices all of the short files together, and returns the completed utterance to the voice browser for playing to the user.
Owner:INTERVOICE A NEVADA COMPOSED OF AS ITS SOLE GENERAL PARTNER INTERVOICE GP
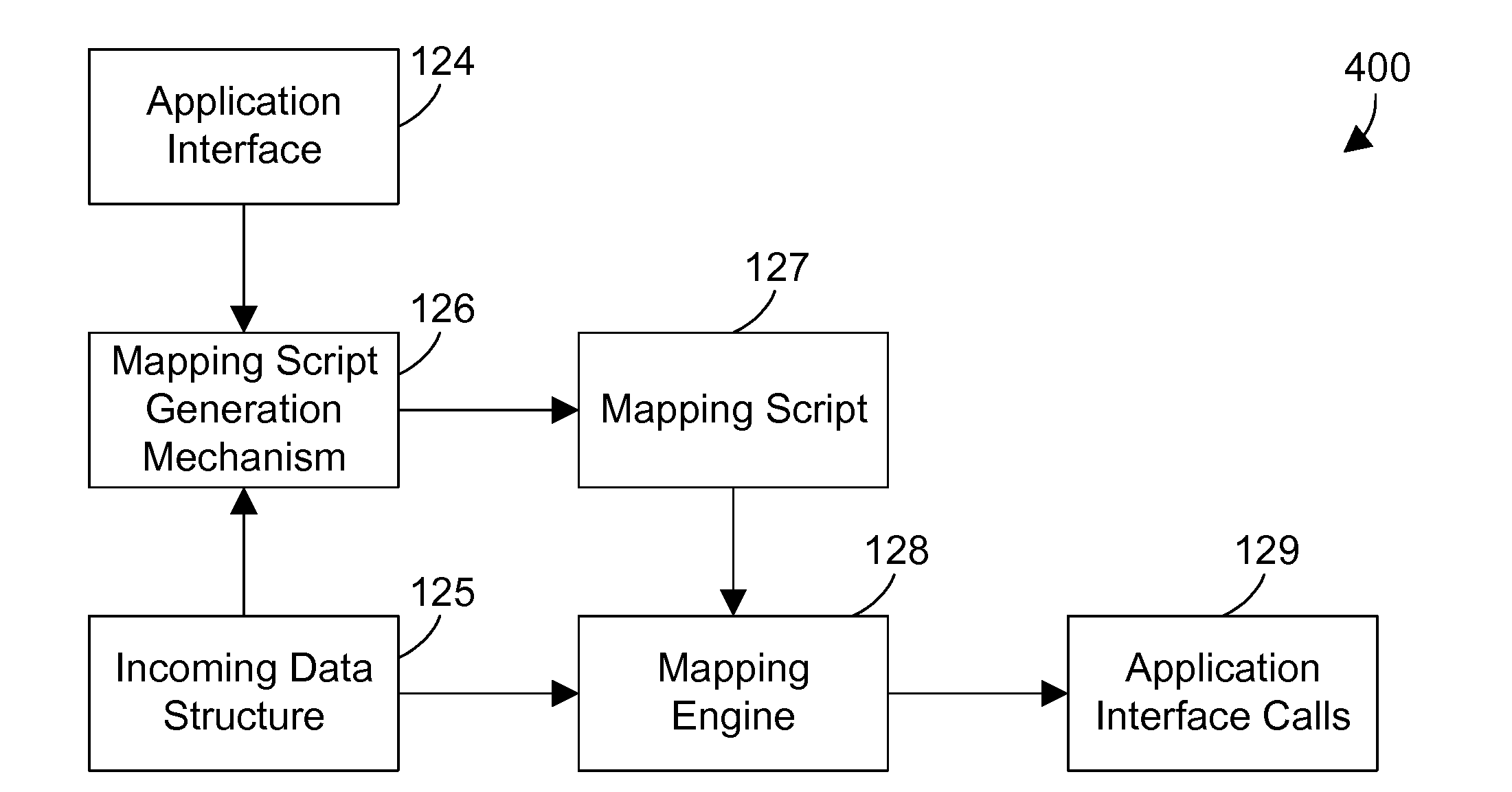
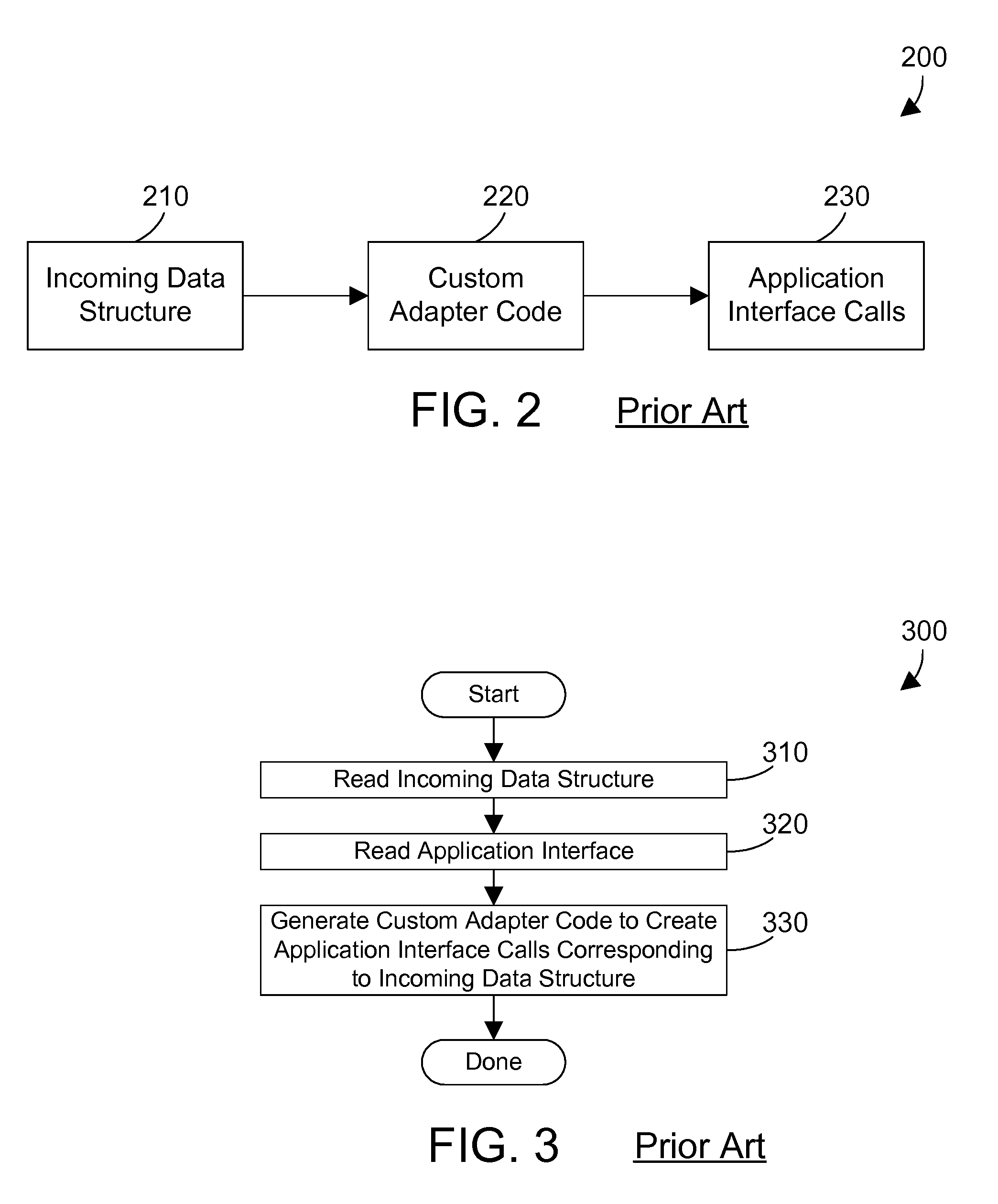
Apparatus and Method for Generating Programming Interactions for a Computer Program from an Incoming Data Structure
InactiveUS20090044203A1Easily definedEasy maintenanceExecution for user interfacesCreation/generation of source codeTheoretical computer scienceApplication software
A user generates a mapping script using a mapping script generation mechanism. The mapping script is in a format that allows the mapping script to be generated and maintained by a non-programmer. A mapping engine reads a mapping script, reads an incoming data structure, and generates calls to an application interface that allows the incoming data structure to interact with the application. The mapping engine is a computer program, but does not need to change with different incoming data structures and different applications. The logic for mapping between a particular incoming data structure and a particular application is encapsulated in the mapping script, which is in a format that may be easily defined and maintained by a non-programmer. The mapping script may optionally include various mechanisms including a data conversion mechanism, a literal value mechanism, a conditional logic mechanism, and a mapping script selection mechanism.
Owner:IBM CORP
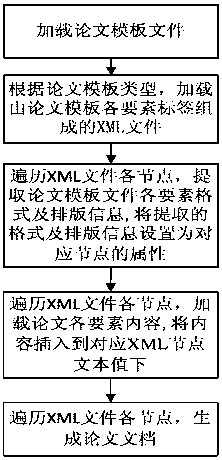
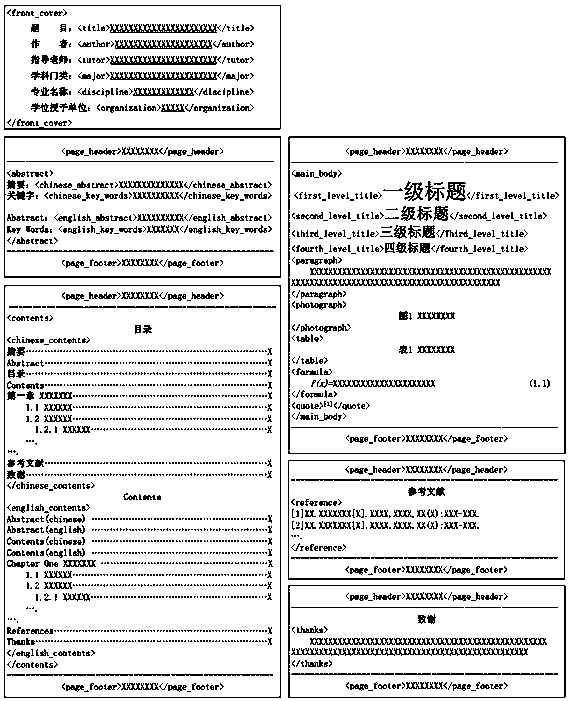
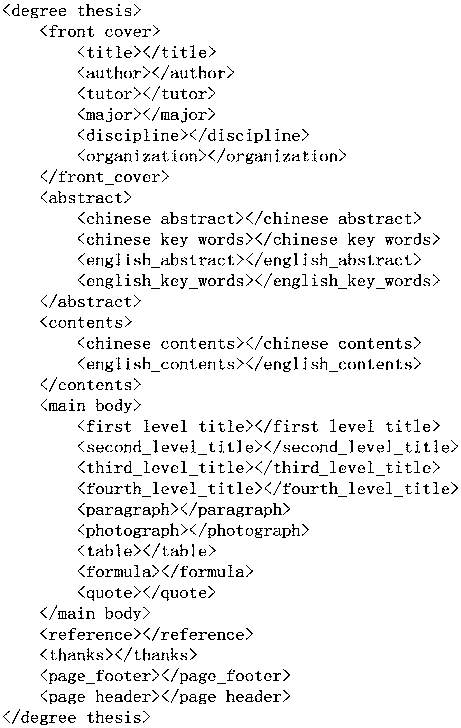
Template-based thesis automatic generation method
InactiveCN108052488AImprove quality and efficiencyImprove work efficiencyText processingSpecial data processing applicationsProperty valueTemplate based
The invention relates to a template-based thesis automatic generation method and belongs to the field of thesis automatic generation technology. According to the method, a thesis template file is loaded, and a corresponding XML file composed of all element tags of a template is loaded according to the type of the template file; the template file is traversed according to the XML file composed of all the element tags, and format and typesetting information of all elements of a thesis is extracted and filled in as property values of all XML nodes; a thesis content module file is traversed according to the XML file composed of all the element tags, and content of all the elements of the thesis is extracted and filled in as text values of all the XML nodes; and last, all the nodes of the XML file are traversed, the format and the typesetting style of the content of all the elements of the thesis are set according to the property values and the text values of all the nodes, the content of the corresponding elements in the template file is replaced, and automatic generation of the thesis is completed. Through the method, a thesis writer does not need to concern the format and typesettingof the thesis and has more time for improving thesis quality and working efficiency.
Owner:TIANHE COLLEGE GUANGDONG POLYTECHNIC NORMAL UNIV
Translating text into visual imagery content
InactiveUS7792785B2Natural language translationDigital data processing detailsGraphicsSearch data structure
A mechanism is provided for translating text into visual imagery content. A request is received to identify at least one image associated with a text value. At least one association category from a plurality of association categories is identified with which to perform a search. A data structure is searched, using the at least one association category, for an identification of the at least one image that is associated with the text value. The at least one image is a visual representation of the text value. At least one image is retrieved in response to identifying at least one image associated with the text value. The at least one image is presented in a graphical user interface to a user.
Owner:LINKEDIN
Method and system for in-line processing of standardized text values
InactiveUS20090030913A1Digital data processing detailsProgram loading/initiatingApplication softwareJava classes
A method of in-line processing of standardized text values. A standardization utility defines multiple standardization rules in response to user input from a graphical user interface (GUI). The standardization rules correspond to text and integer data in a database. The standardization utility generates a Java class template for each data model object that requires standardization. The standardization utility generates public methods for each data attribute that corresponds to a standardization rule and converts the public methods into Java code. The standardization utility compiles the Java code into multiple helper classes and stores the helper classes within a Java Archive (JAR) file in the library path of applications that input text into the database. The standardization utility assigns a tracking number to each new helper class. The standardization utility loads the helper classes into Java Virtual Machines (JVMs) that are accessible to applications capable of inputting data into the database.
Owner:IBM CORP
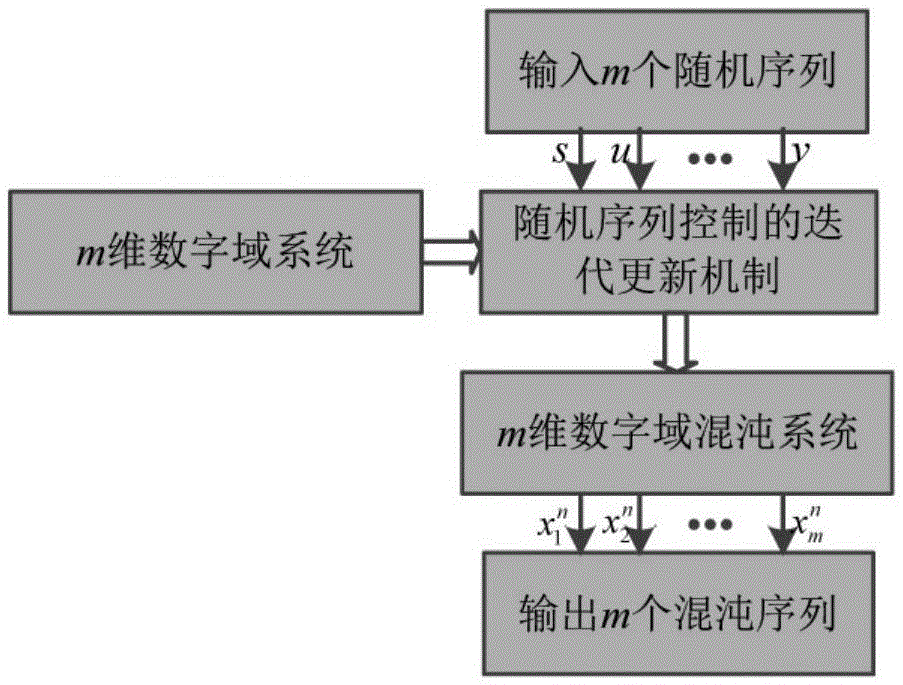
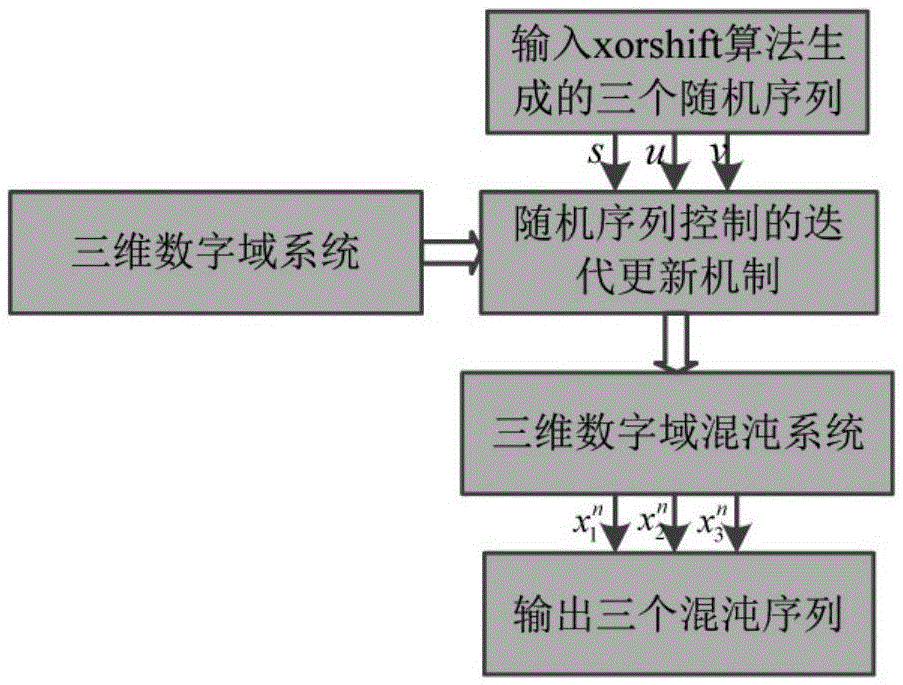
Image encryption method for high dimension digital domain chaotic system
ActiveCN105550972ASolving Kinetic Degradation ProblemsFinite Precision Effects OvercomeImage data processing detailsChaotic systemsText value
The invention discloses an image encryption method for a high dimension numerical field chaotic system, comprising steps of establishing a m-dimension digital domain chaotic system, wherein m=3, utilizing a three-dimension digital domain chaotic system to generate three chaotic sequences, using the three chaotic sequences to perform encryption on image information of three paths which are red, green and blue paths, transmitting the cipher text value from a transmission terminal to a reception terminal through a channel, and performing deciphering on the information on the reception terminal. Because the high dimension numerical field chaotic system is adopted to realize the image encryption and deciphering, the effective accuracy effect problem which is generated by the numerical field chaotic system when the digital device is realized is solved.
Owner:GUANGDONG UNIV OF TECH
Method and device for serializing data object as well as method and device for deserializing data object
InactiveCN106294385AImprove query efficiencyImprove modification efficiencyUnstructured textual data retrievalSpecial data processing applicationsAlgorithmTheoretical computer science
The invention discloses a method and a device for serializing a data object as well as a method and a device for deserializing the data object. The method for serializing the data object comprises the following steps: acquiring the data object; by taking the data object as a parameter, calling a serialization function, and acquiring root properties included in the data object; generating a text path according to positions of the root properties in the data object; acquiring attribute value objects corresponding to the root properties, and converting the attribute value objects into text values; linking the text path and the text values corresponding to the same root properties through equal signs to form a text format of attribute value pairs, and generating serialized results of the respective root properties. According to the method disclosed by the invention, a hierarchical structure described by the data object can be simplified, and data query efficiency and data modification efficiency can be increased.
Owner:ALIBABA GRP HLDG LTD
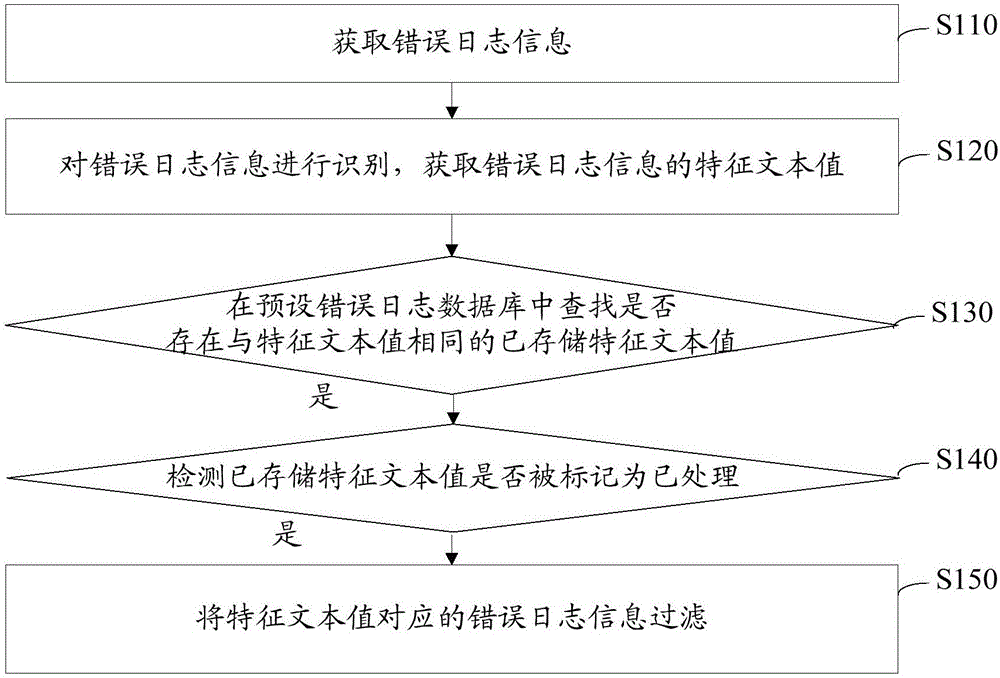
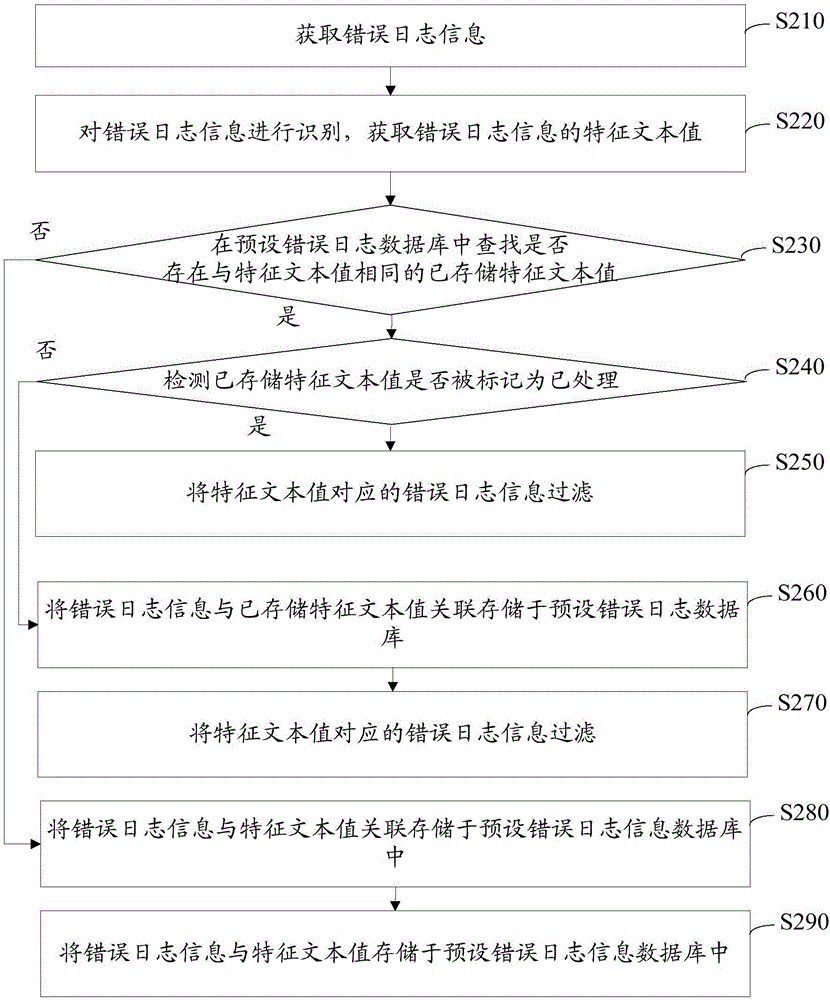
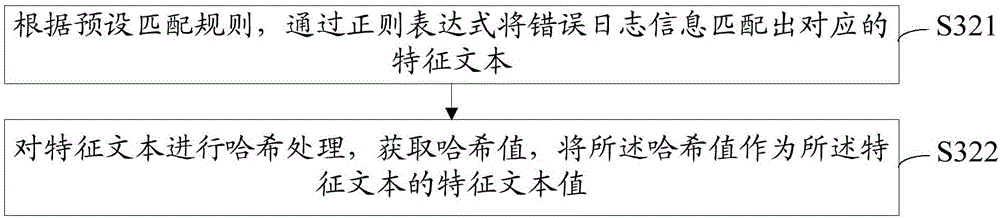
Error log information filtering method and device
InactiveCN106407350ALess quantityImprove work efficiencySpecial data processing applicationsText valueData mining
The invention relates to an error log information filtering method and device. The method comprises the steps of obtaining error logs; identifying the error logs; obtaining characteristic text values of error log information; detecting whether stored characteristic text values are marked as being processed or not when the stored characteristic text values the same to the characteristic text values are searched from a preset error log database; and filtering the error log information corresponding to the characteristic text values if the stored characteristic text values are marked as being processed. Whether the error log information corresponding to the stored characteristic text values is processed or not can be known by detecting whether the stored characteristic text values are marked as being processed or not; if the error log information is processed, equivalently, the error log information corresponding to the characteristic text values is processed, wherein the error log information corresponding to the characteristic text values is the same to the error log information corresponding to the stored characteristic text values; the same error log information does not need to be processed again; the error log information is filtered; the volume of the error log information is reduced; and the working efficiency of processing the error log information is improved.
Owner:GUANGZHOU SHIRUI ELECTRONICS +1
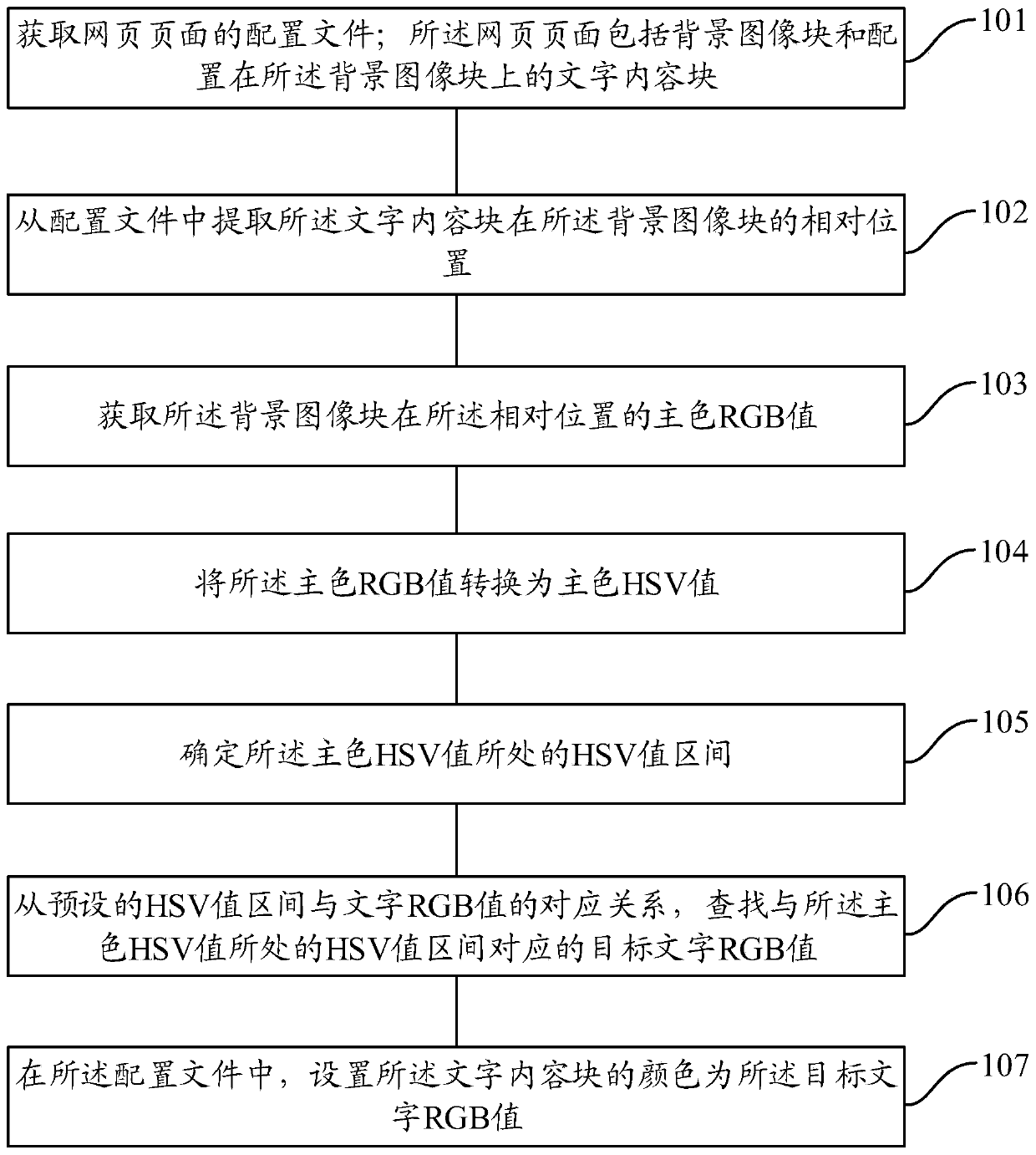
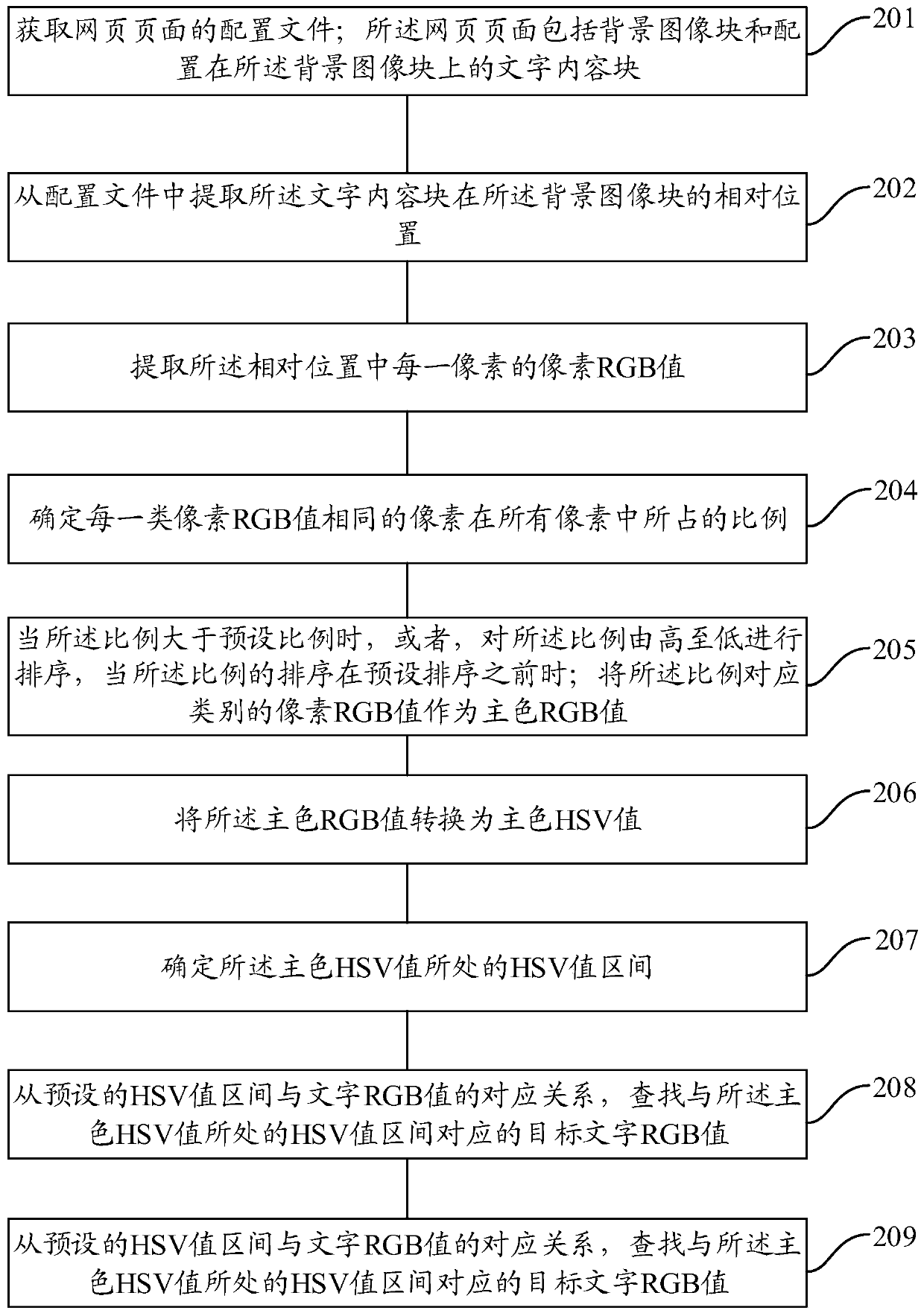
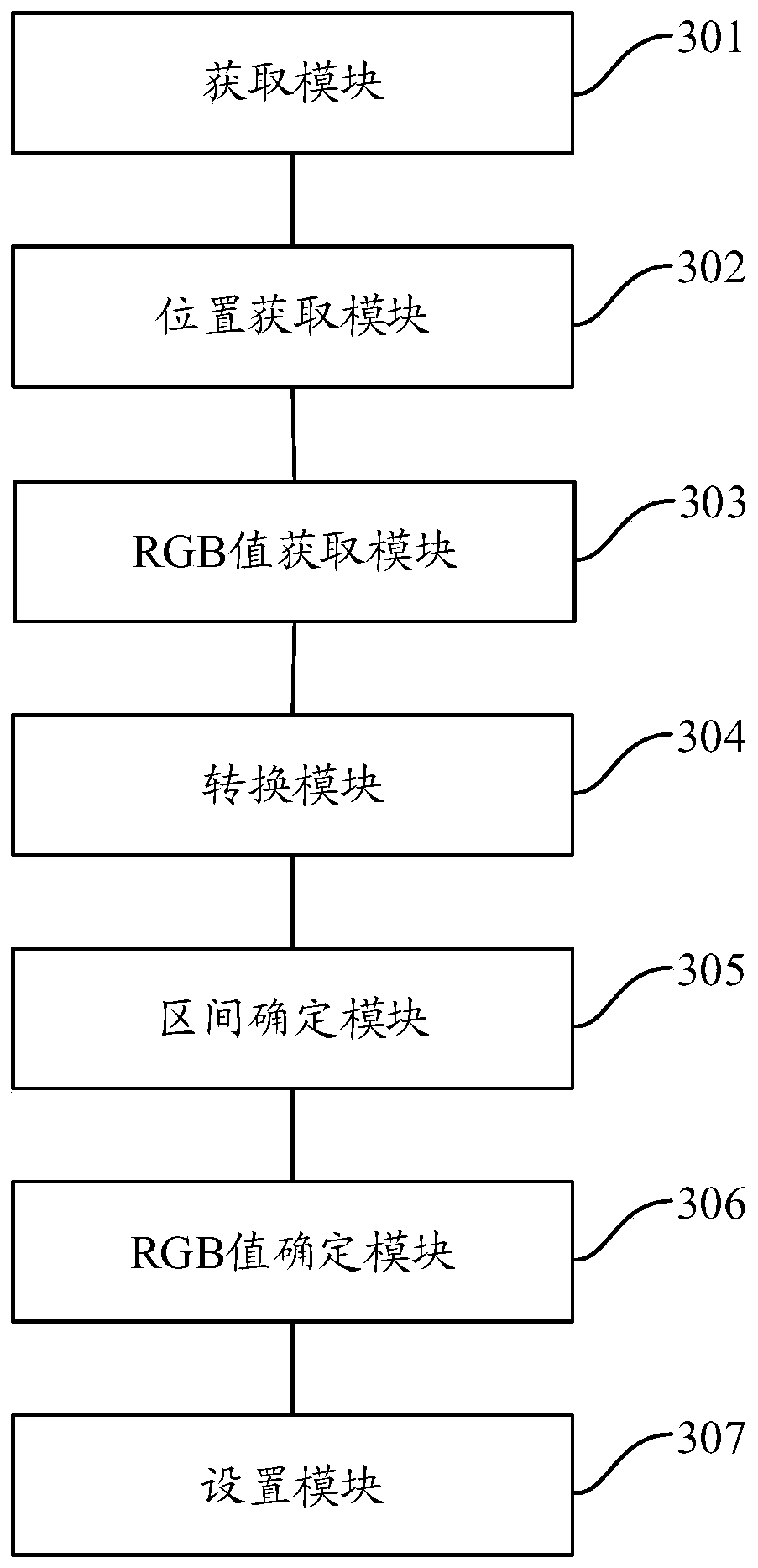
Method and device for determining color matching of page characters
ActiveCN111090368ARealize automatic color matchingImprove production efficiencyInput/output processes for data processingFilling planer surface with attributesComputer graphics (images)Algorithm
The embodiment of the invention provides a method and device for determining color matching of page characters. The method comprises the steps that a configuration file of a webpage is obtained; wherein the web page comprises a background image block and a text content block configured on the background image block; extracting a relative position of the text content block in the background image block from a configuration file; obtaining a main color RGB value of the background image block at the relative position; converting the main color RGB value into a main color HSV value; determining anHSV value interval where the main color HSV value is located; searching a target character RGB value corresponding to the HSV value interval where the main color HSV value is located from a preset corresponding relationship between the HSV value interval and the character RGB value; and in the configuration file, setting the color of the text content block as the RGB value of the target text. Andrealizing automatic color matching of the text content in the webpage according to the color of the background image block corresponding to the region where the text content is located.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
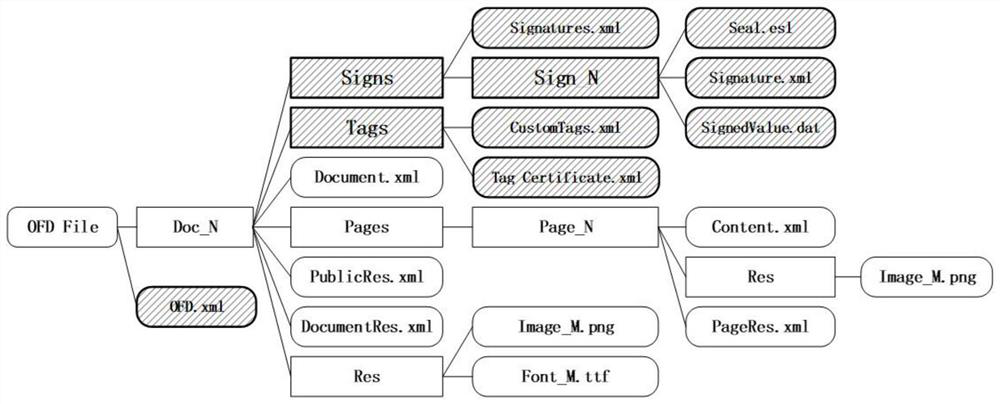
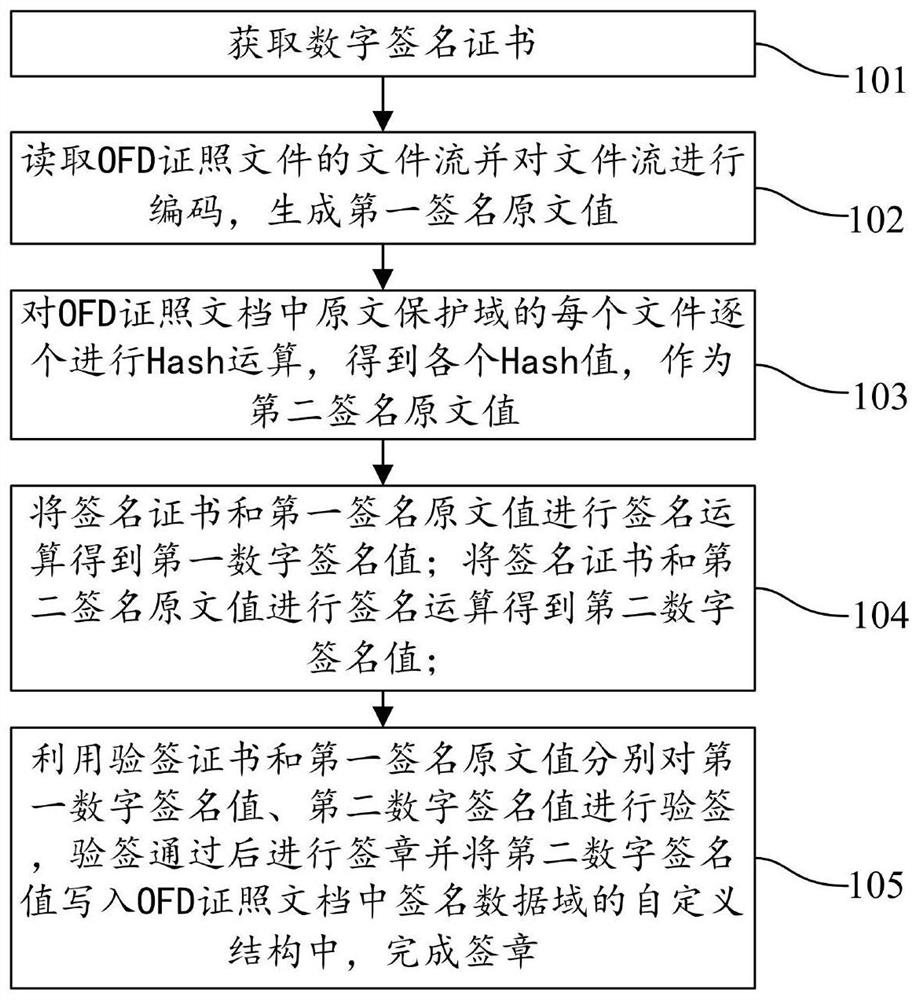
OFD format real estate electronic certificate file signature method and system
ActiveCN112364385AIntegrity guaranteedGuaranteed validityDigital data protectionDigital signatureProtection domain
The invention discloses an OFD format real estate electronic certificate file signature method and system. The method comprises the steps of obtaining a digital signature certificate; encoding the file stream to generate a first signature original text value; performing Hash operation on each file in the original text protection domain one by one to obtain each Hash value as a second signature original text value; performing signature operation on the signature certificate and the first signature original text value to obtain a first digital signature value; performing signature operation on the signature certificate and the second signature original text value to obtain a second digital signature value; and performing signature verification on the first digital signature value and the second digital signature value respectively by utilizing the signature verification certificate and the first signature original text value, performing signature after the signature verification is passed, and writing the second digital signature value into the self-defined structure of the signature data domain to complete signature. According to the invention, the information interaction between the real estate service system and the certificate relying service is ensured to be safe, efficient and convenient, and the integrity and effectiveness of the certificate file are ensured.
Owner:山东省国土空间数据和遥感技术中心
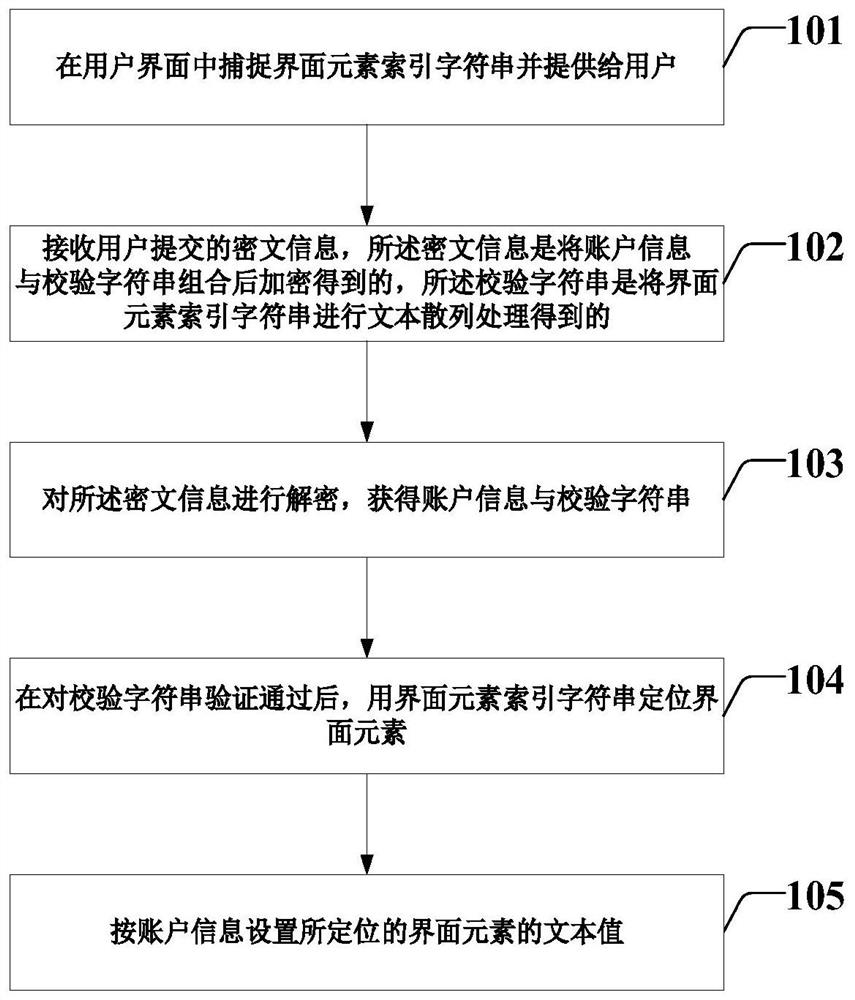
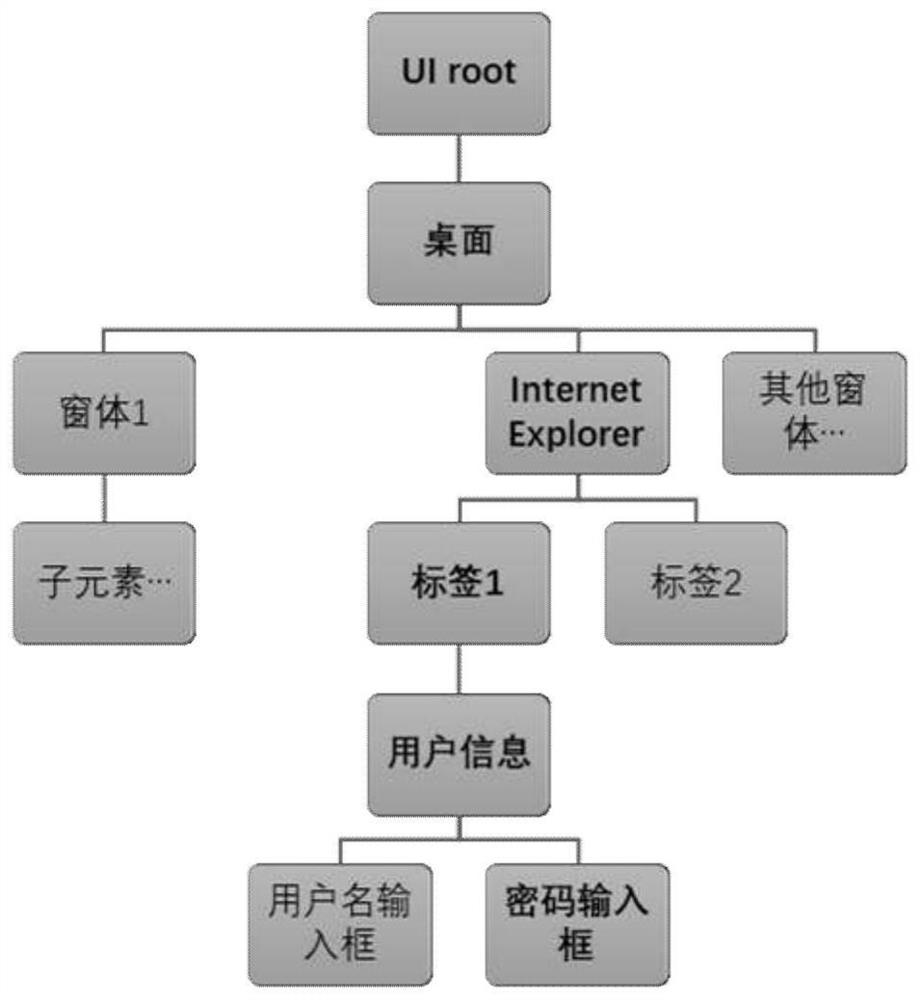
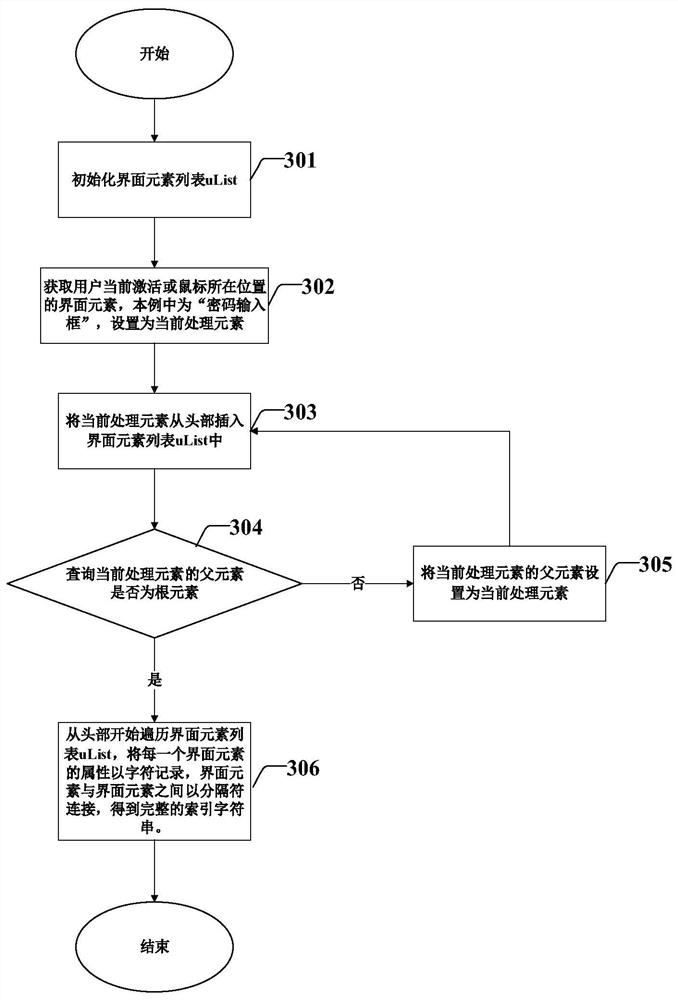
Robot automation process account information processing method and device
PendingCN113076548APrevent leakagePrevent tamperingDigital data protectionOther databases queryingInformation processingCiphertext
The invention discloses a robot automation process account information processing method and device. The method comprises steps of capturing an interface element index character string in a user interface and providing the interface element index character string to a user; ciphertext information submitted by a user being received, the ciphertext information being obtained by combining account information and a verification character string and encrypting the account information and the verification character string, and the verification character string being obtained by performing text hash processing on an interface element index character string; decrypting the ciphertext information to obtain the account information and a verification character string; after the verification of the verification character string is passed, positioning the interface element by using the interface element index character string; and setting a text value of the positioned interface element according to the account information. According to the method, the sensitive account information can be ensured to be normally quoted in the development and use process of an automatic process, and account information leakage caused by interpretation and recording is avoided.
Owner:CHINA CONSTRUCTION BANK
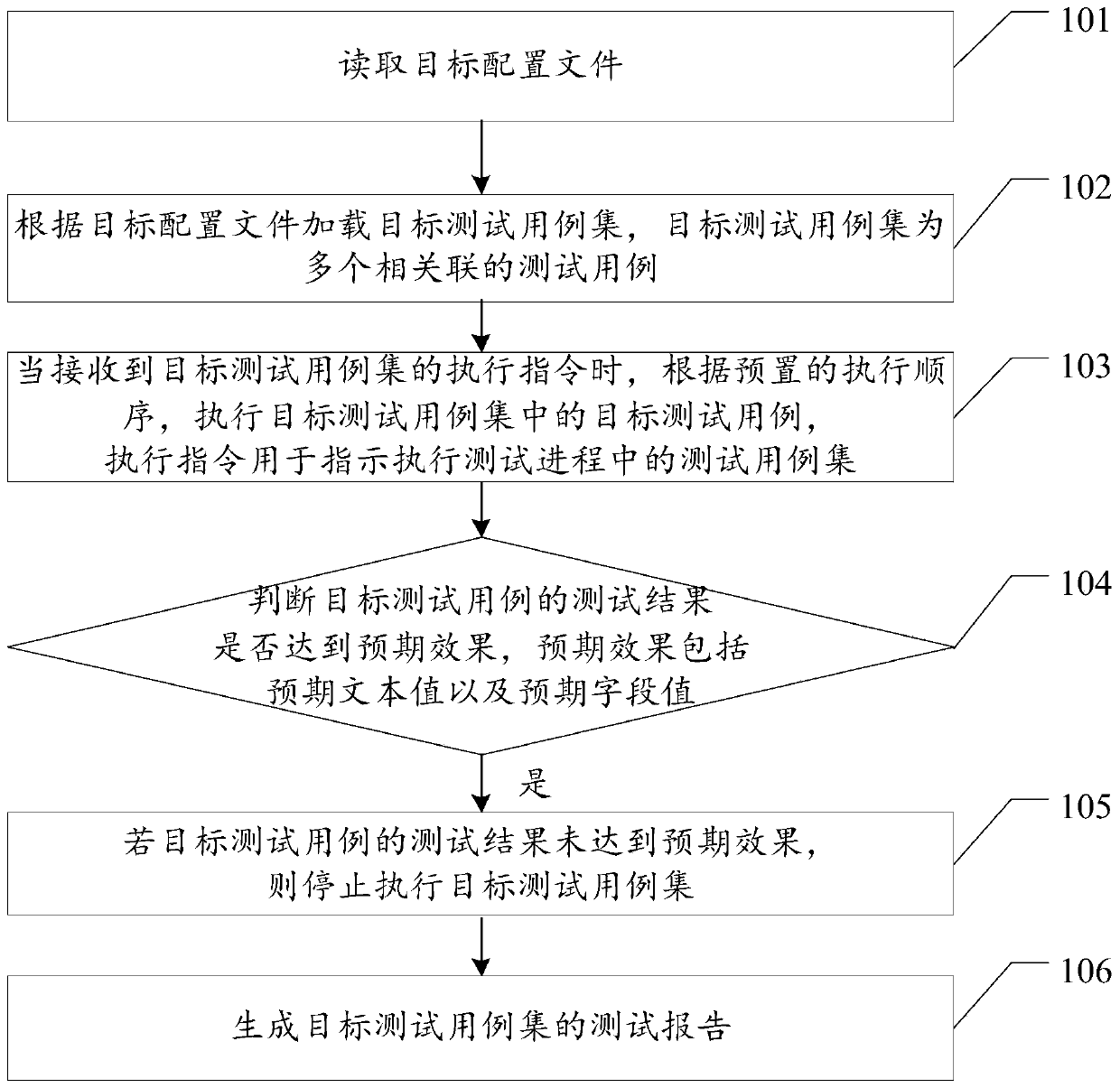
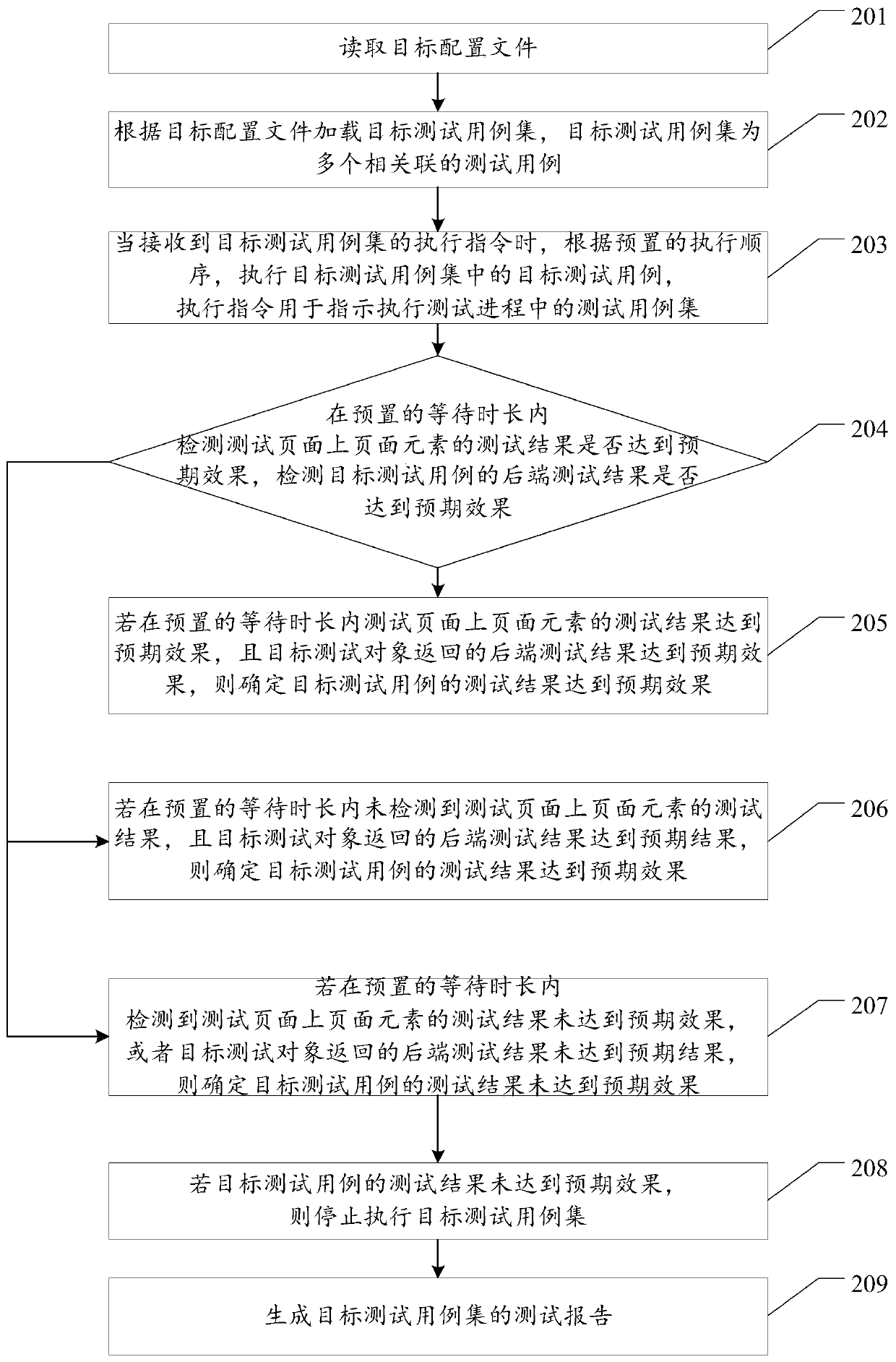
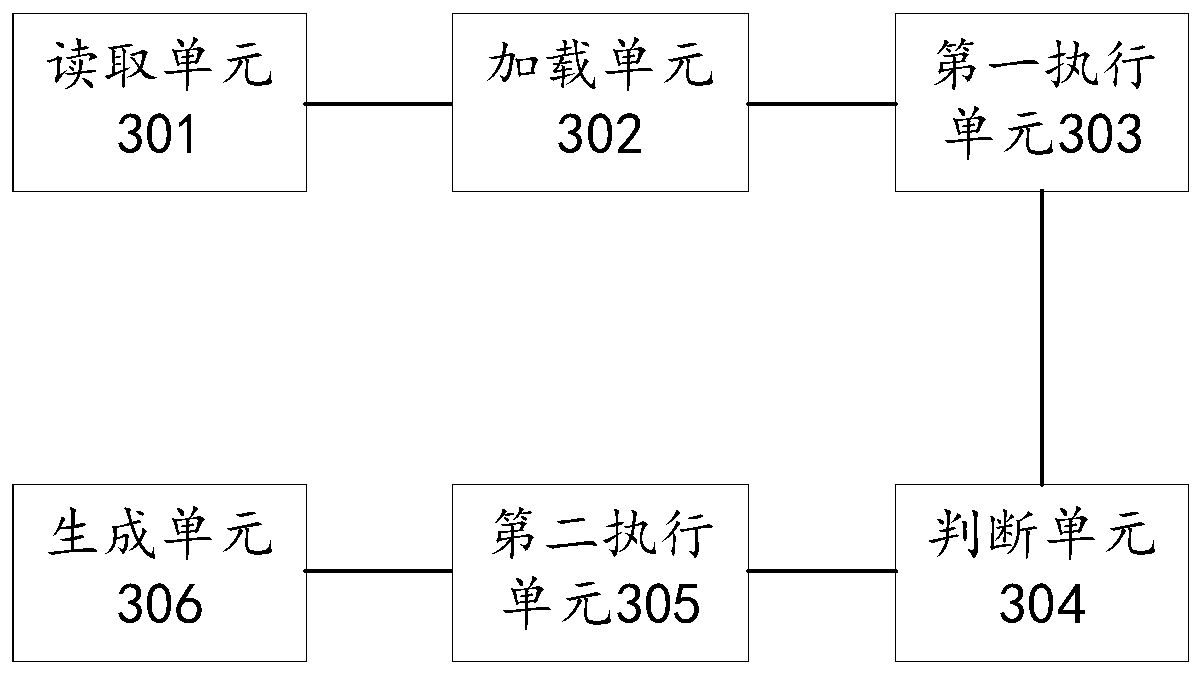
Test case automatic execution method and device, equipment and storage medium
PendingCN110297767AImprove execution efficiencySoftware testing/debuggingEnergy efficient computingProgramming languageText value
The invention relates to the field of research and development management, and discloses a test case automatic execution method and device, equipment and a storage medium, which are used for skippingassociated cases with execution errors or not achieving expected effects and verifying test pages which are not responded for a long time, so that the execution efficiency of the cases is improved. The method comprises the following steps: reading a target configuration file; loading a target test case set according to the target configuration file, wherein the target test case set is a pluralityof associated test cases; when an execution instruction of the target test case set is received, executing the target test cases in the target test case set according to a preset execution sequence, and the execution instruction being used for indicating to execute the test case set in the test process; judging whether a test result of the target test case reaches an expected effect or not, wherein the expected effect comprises an expected text value and an expected field value; if the test result of the target test case does not reach the expected effect, stopping executing the target test case set; and generating a test report of the target test case set.
Owner:PING AN TECH (SHENZHEN) CO LTD
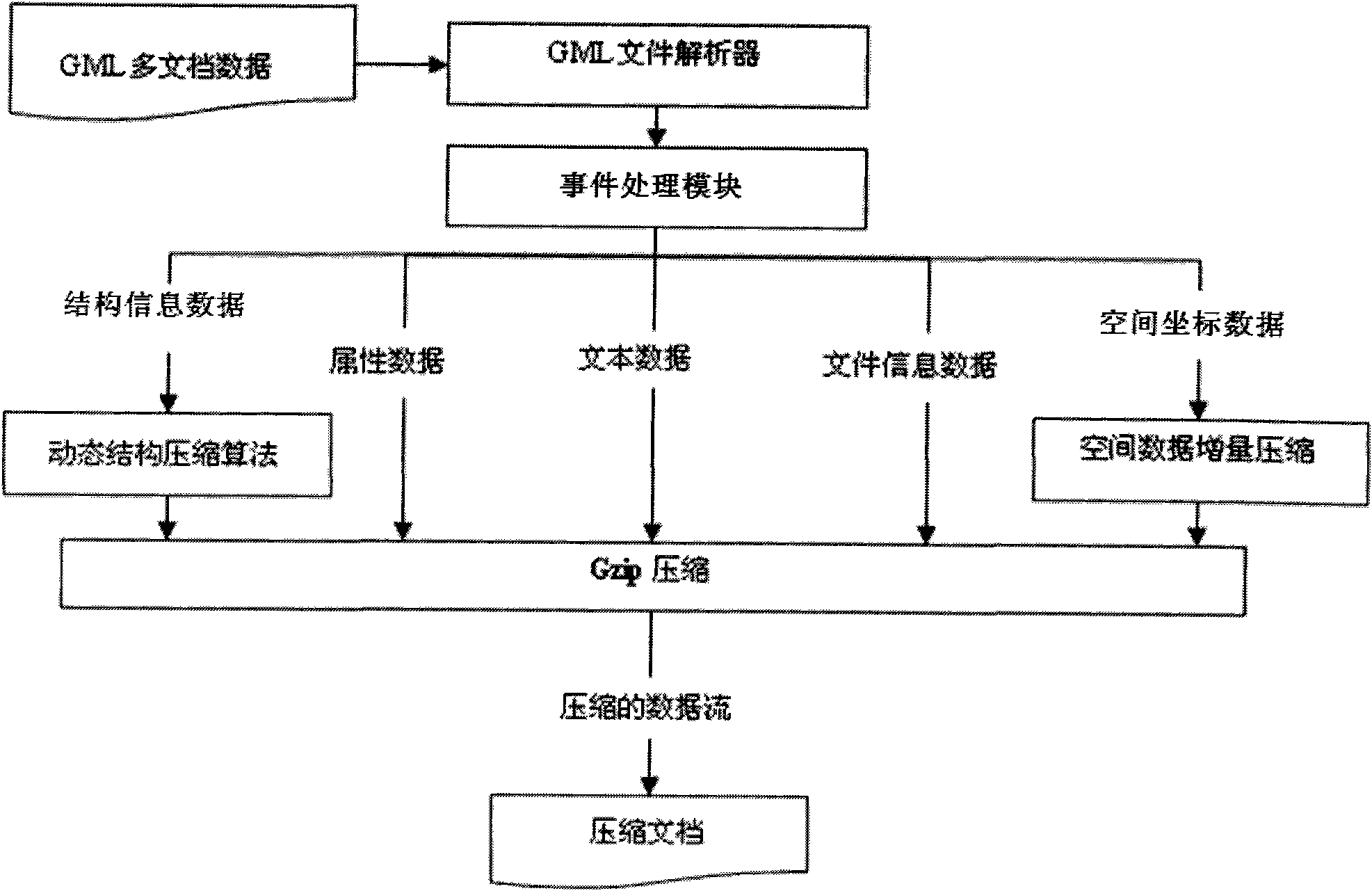
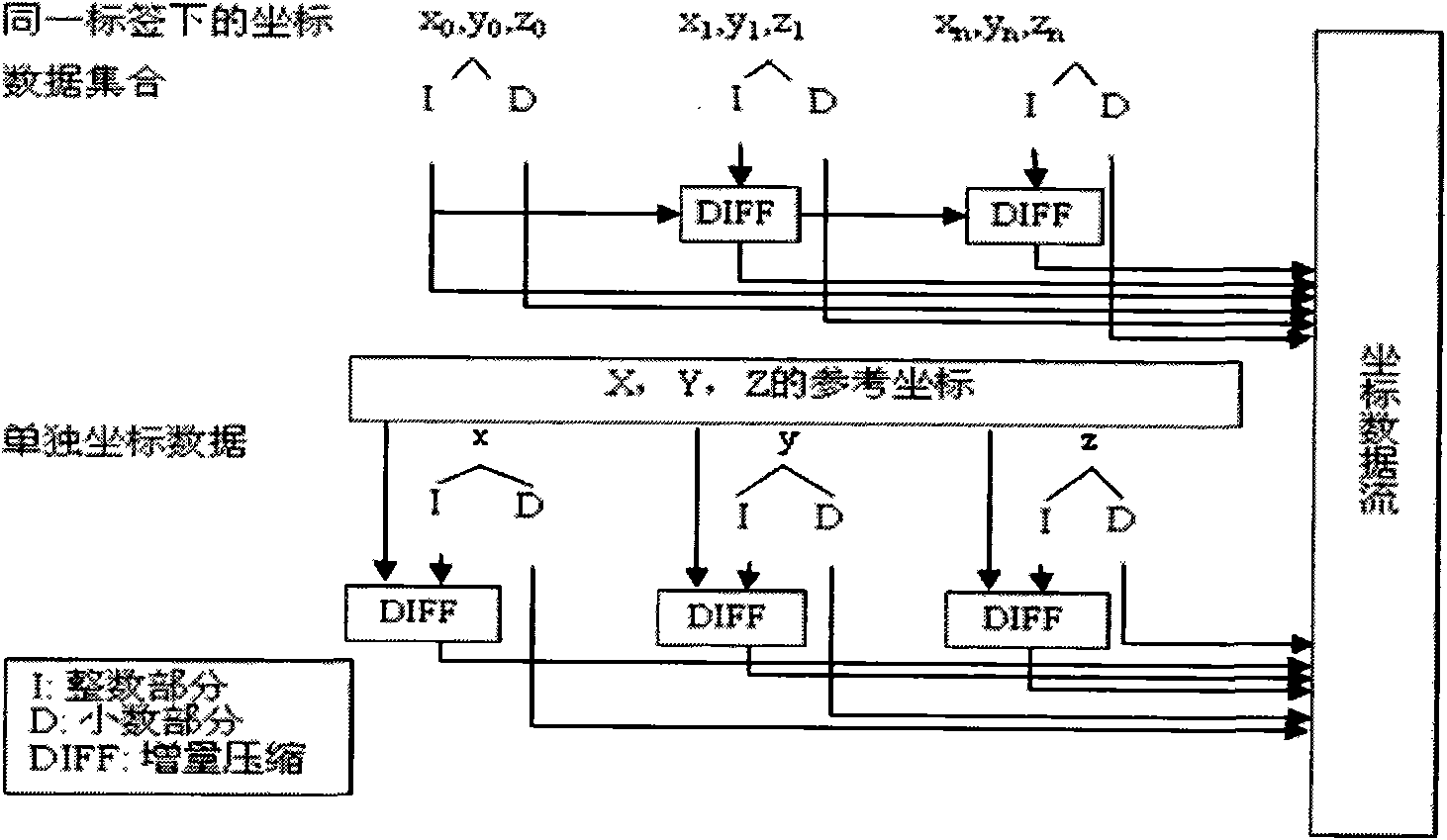
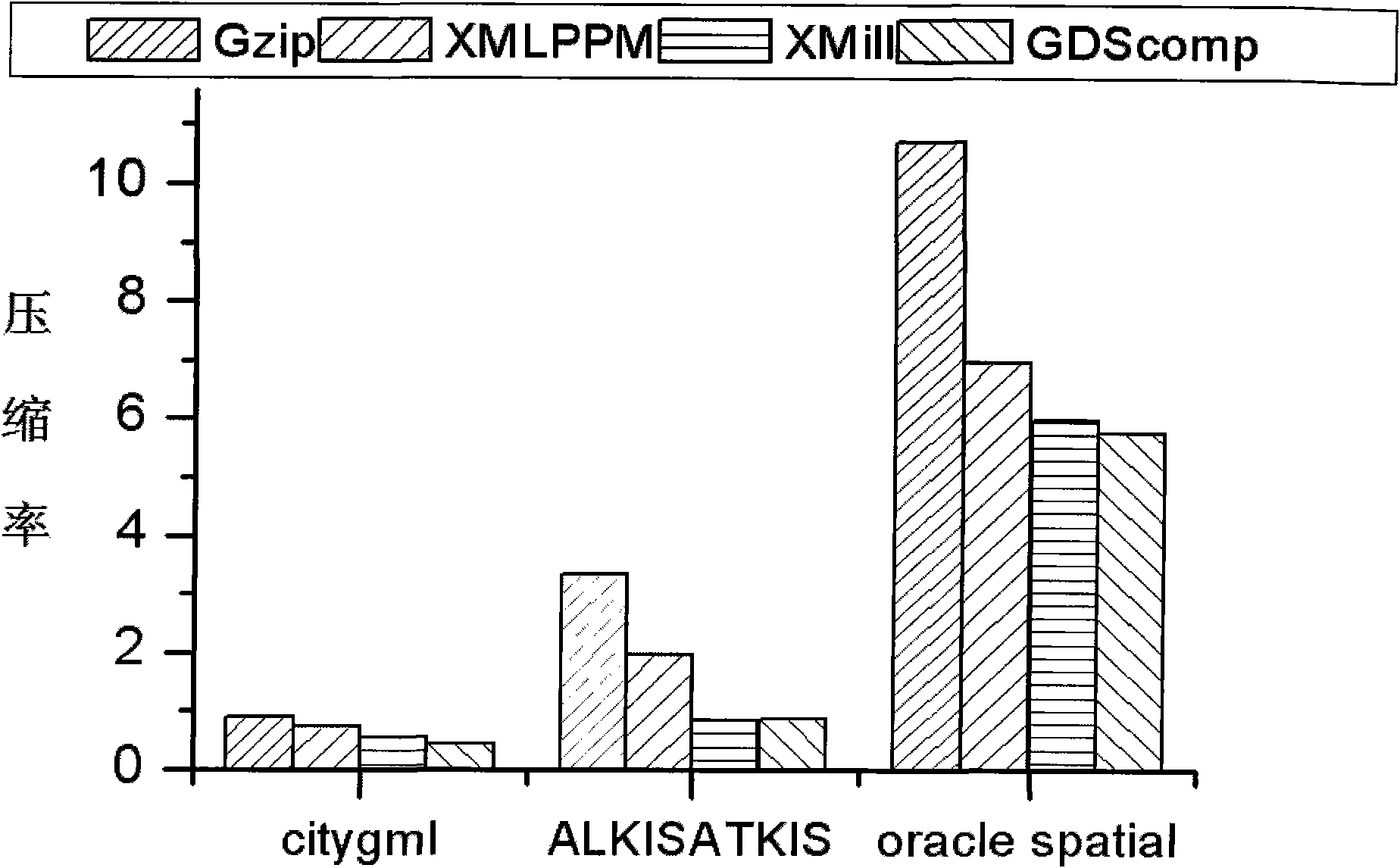
High performance geography markup language (GML) multi-document stream compression information processing method
InactiveCN102591869AIncrease the compression ratioReduce compression timeTransmissionSpecial data processing applicationsInformation processingSoftware engineering
The invention relates to a high performance geography markup language (GML) multi-document stream compression information processing method, which includes the following steps that 1 an input device inputs GML multi-document data to a GML document analyzer; 2 the GML document analyzer uses simple API for XML (SAX) to analyze the multi-document data; 3 an event processing module compresses structural information in the multi-document data through a dynamic structure compression algorithm to be stored in a structural container, spatial data in the multi-document data are compressed through a spatial data incremental compression algorithm to be stored in a spatial data container, and attribute data, text value and current document information data in the multi-document data are stored in an attribute container, a text container and a document information container respectively; and 4 data in all containers are compressed through a text compression tool Gzip as a background compression tool to obtain an integrated independent compression document of the document. Compared with the prior art, the high performance GML multi-document stream compression information processing method has the advantages of being high in compression rate, short in compressing time and uncompressing time, convenient to use and the like.
Owner:TONGJI UNIV +1
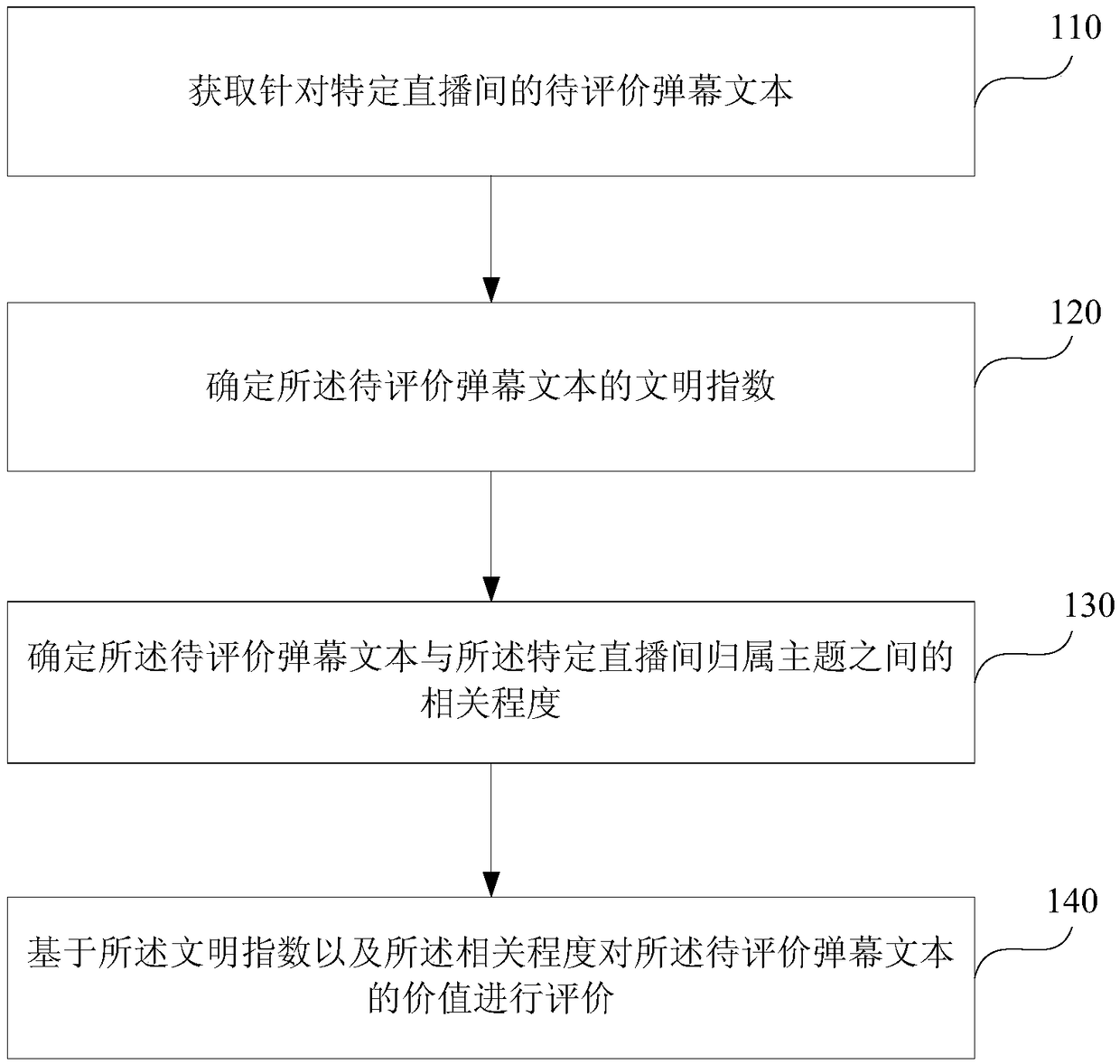
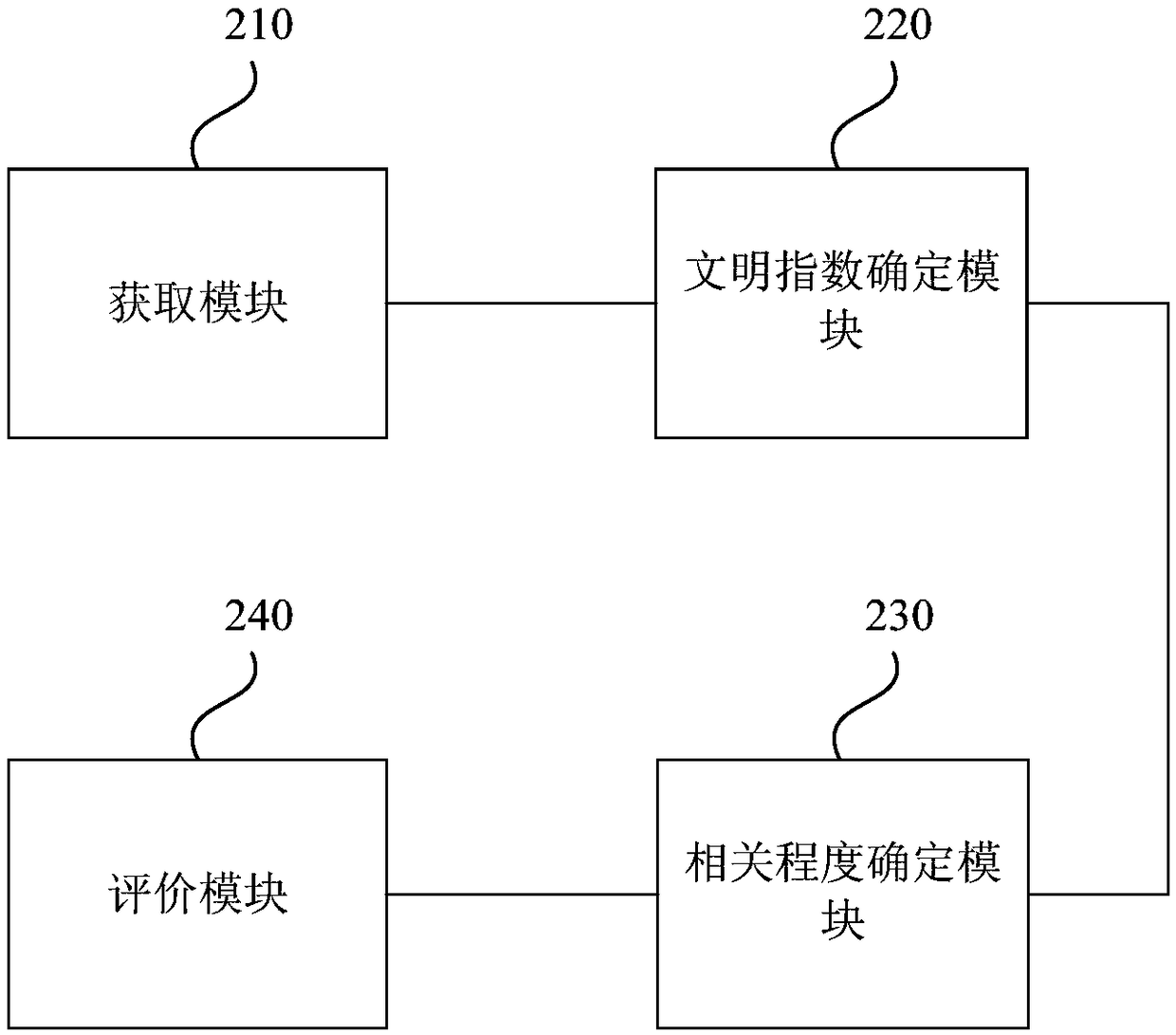
Barrage text value evaluation method, apparatus, device and medium
ActiveCN109062905AAccurate evaluationSemantic analysisSpecial data processing applicationsText valueSubject specific
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Authentication based on visual memory
Passwords are used in various system access applications in order to ascertain that the user seeking access to a system resource is indeed the person with said access. Passwords are usually supposed to be entered through a keyboard and are a combination of alphanumeric values. With the advent of devices equipped with visual displays and touch inputs, it is possible to create a system which utilizes a person's visual memory to authenticate the person.A system and method is described which uses multiple images to perform authentication. This system does not require its user to input a text value as a password. The password is created by user's actions. These actions are in the form of selecting a segment on a displayed image. Few different systems are described. One system is capable of creating variable passwords which by design keep changing from one authentication attempt to another. Another system uses one high resolution image to effectively hide the password in an image with lots of detail.
Owner:JOHRI RAJUL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com