Maintaining a soft-token private key store in a distributed environment
a technology of distributed environment and soft-token, applied in the direction of digital transmission, unauthorized memory use protection, instruments, etc., can solve the problems of unauthorized access, soft-tokens are vulnerable to security breaches, and the security of soft-tokens is becoming both important and complex
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
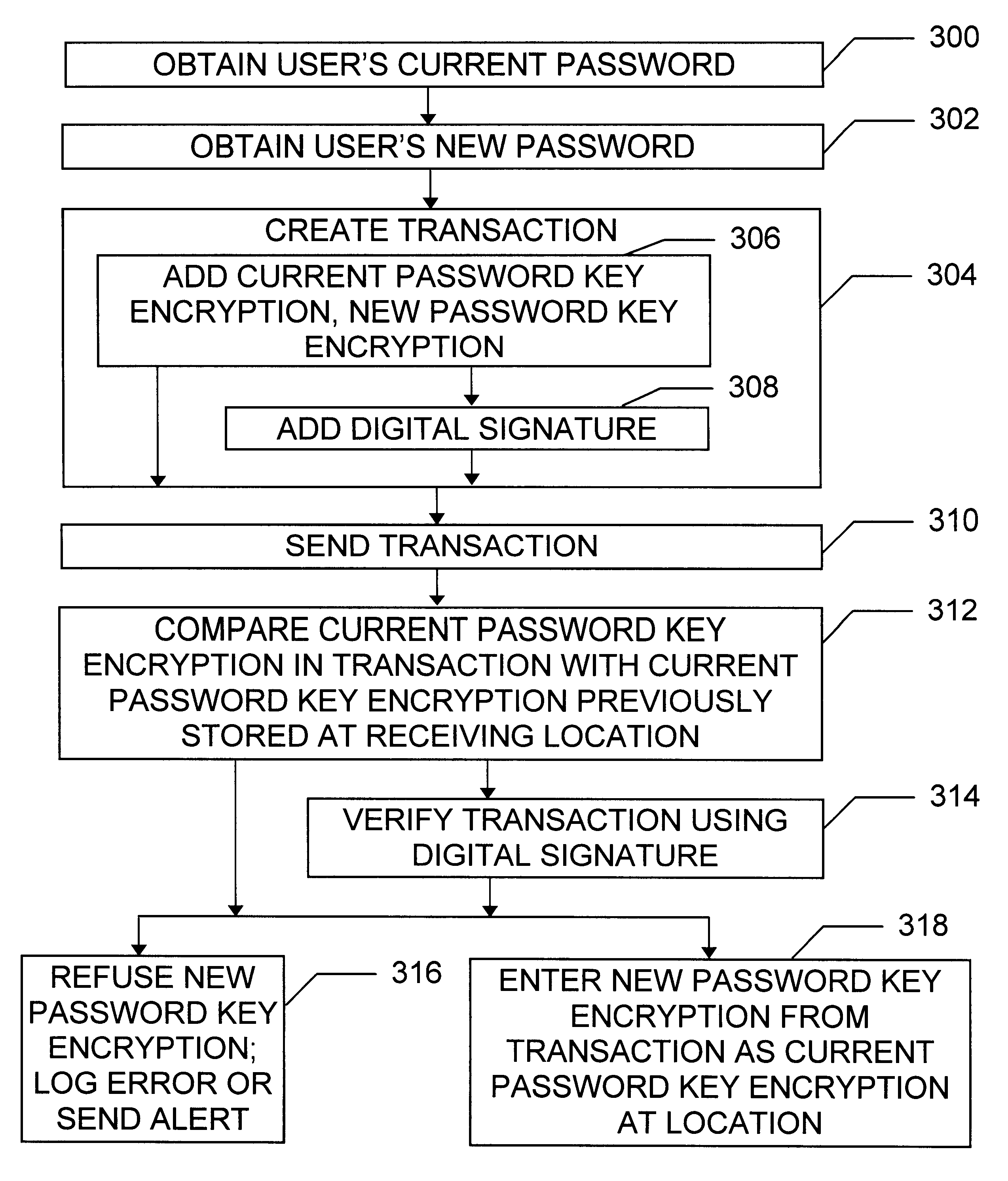
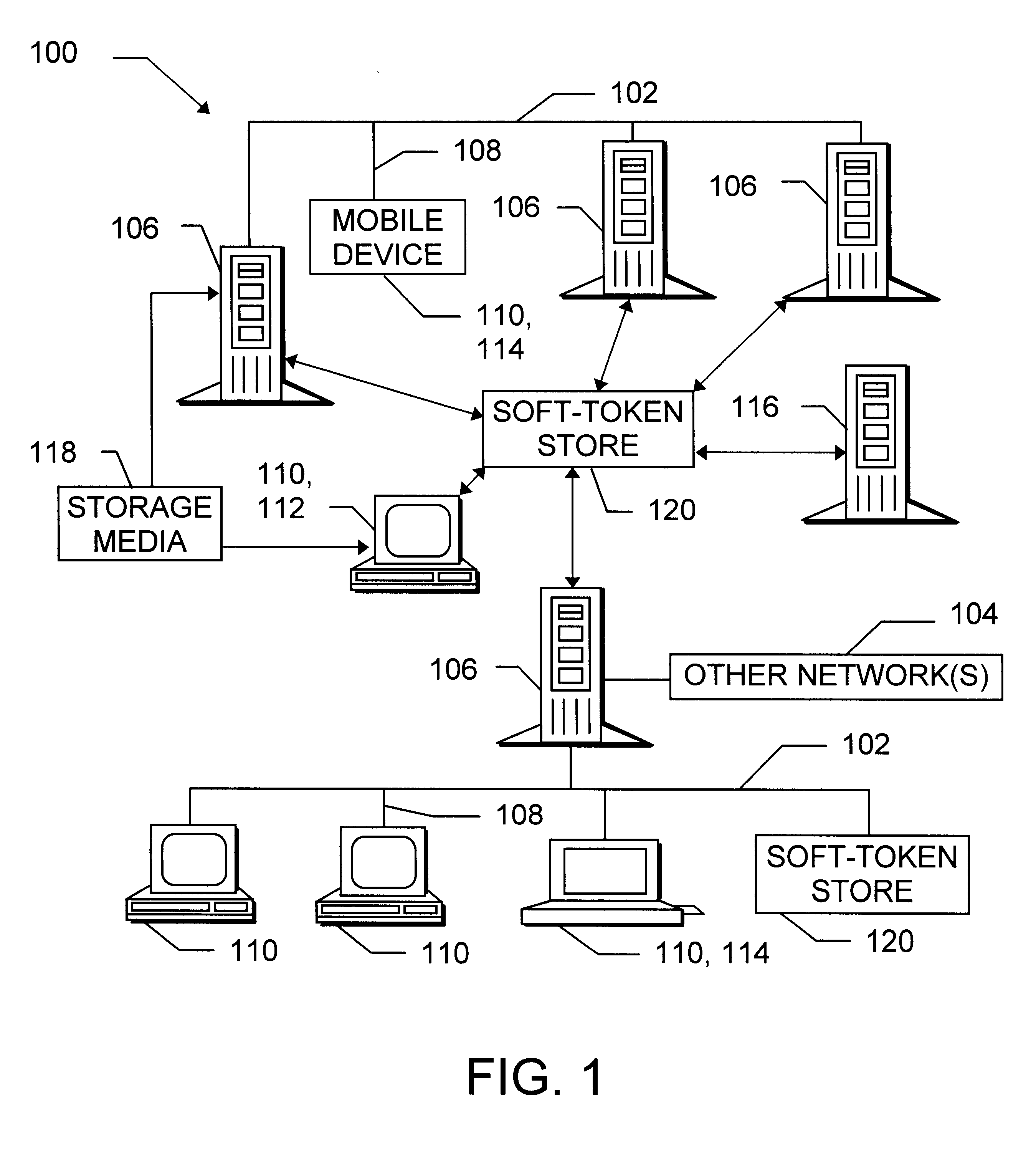
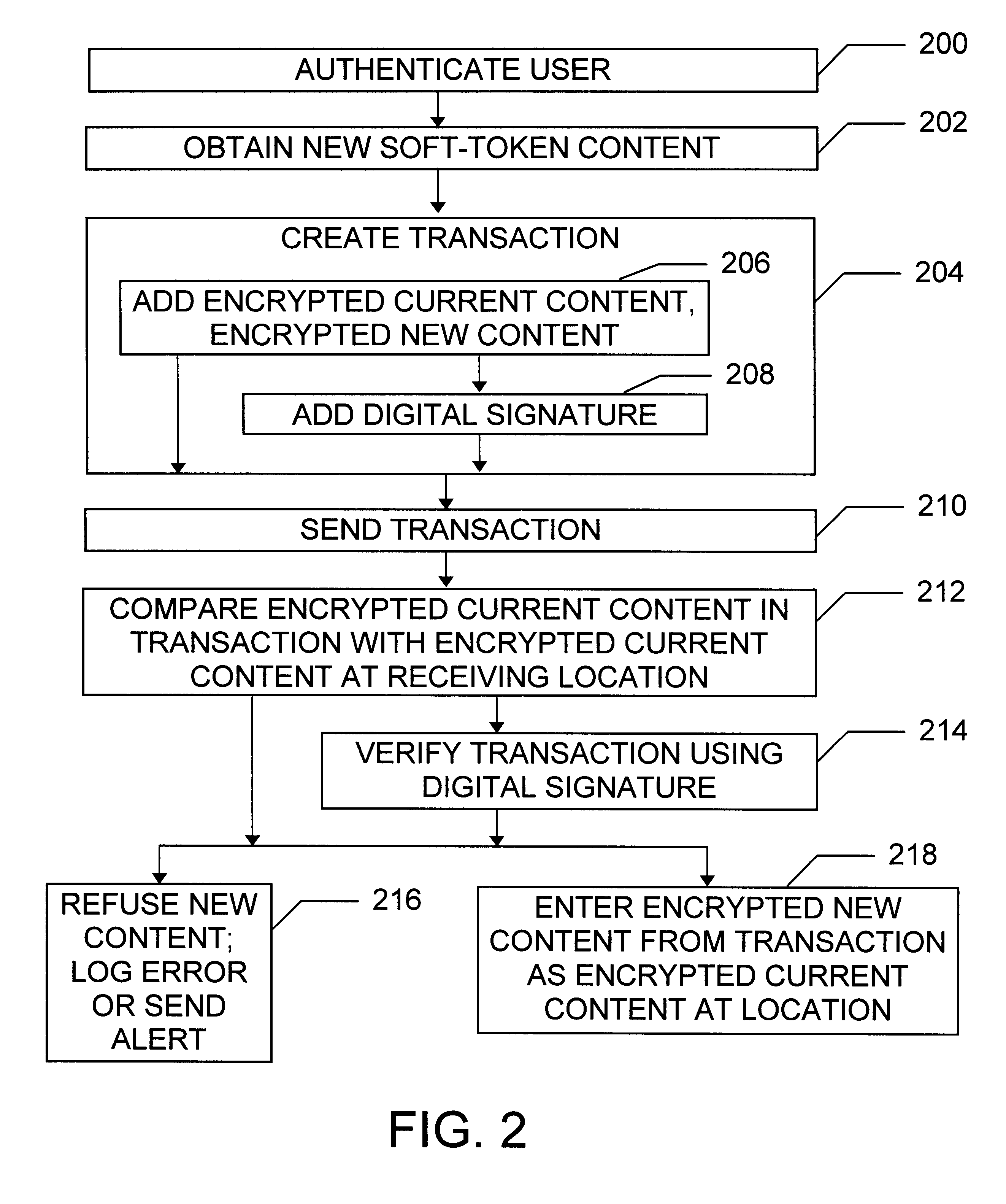
To further illustrate the invention, another example will now be provided. This example is not the only possible use of the invention, and embodiments not discussed in the example also lie within the scope of the claims.
Assume that administration of the distributed environment is the responsibility of several administrators, that a single administration private-public key pair is used by the administrators in their official duties, and that each administrator has a copy of the private key which is encrypted with a symmetric key known only to that administrator. The goal is for an administrator we shall call "Able" to securely change both the administration private key and the corresponding public key certificate. Because Able does not know the symmetric keys of the other administrators, Able cannot simply give them encrypted copies of the new private key.
To solve this problem, we proceed as follows. First, we temporarily modify the administrative user record 500 of a given administr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com