Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
167 results about "Software vendor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
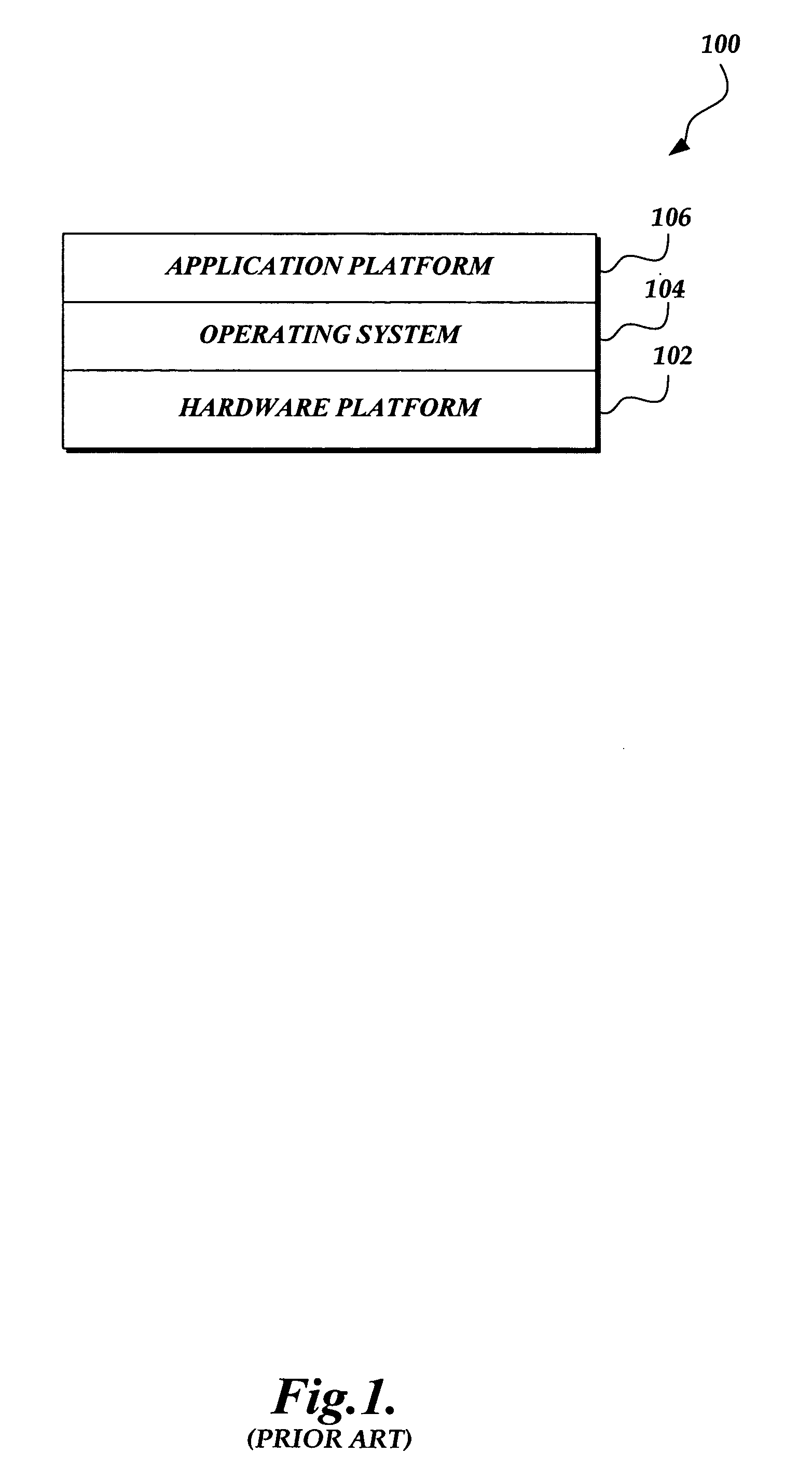
An independent software vendor (ISV) is an organization specializing in making and selling software, as opposed to hardware, designed for mass or niche markets. This is in contrast to in-house software, which is developed by the organization that will use it, or custom software, which is designed or adapted for a single, specific third party.
System and method for software certification
InactiveUS6862696B1Improve product reliabilityImprove reliabilityHardware monitoringSpecific program execution arrangementsSoftware engineeringHabit
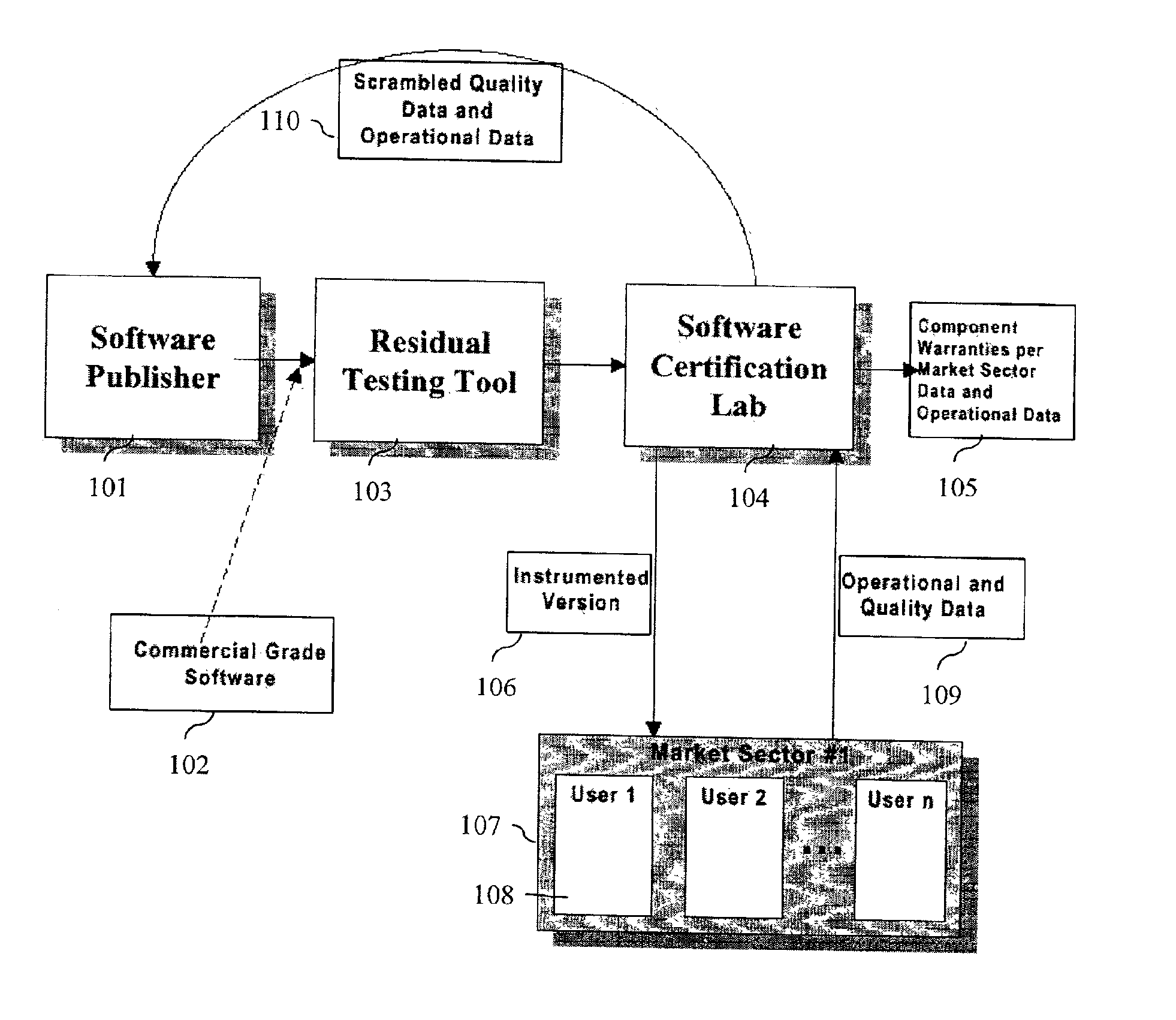
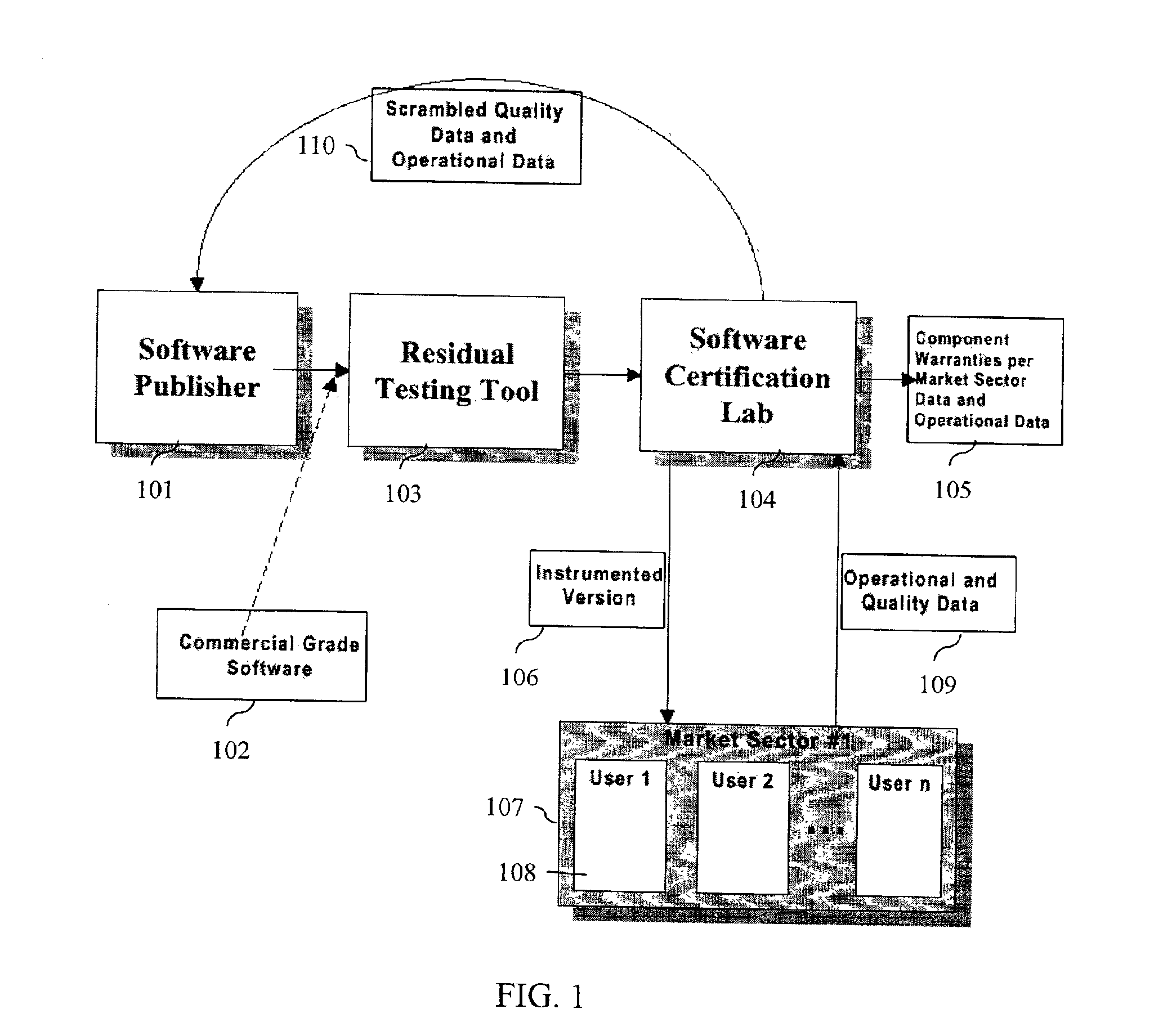
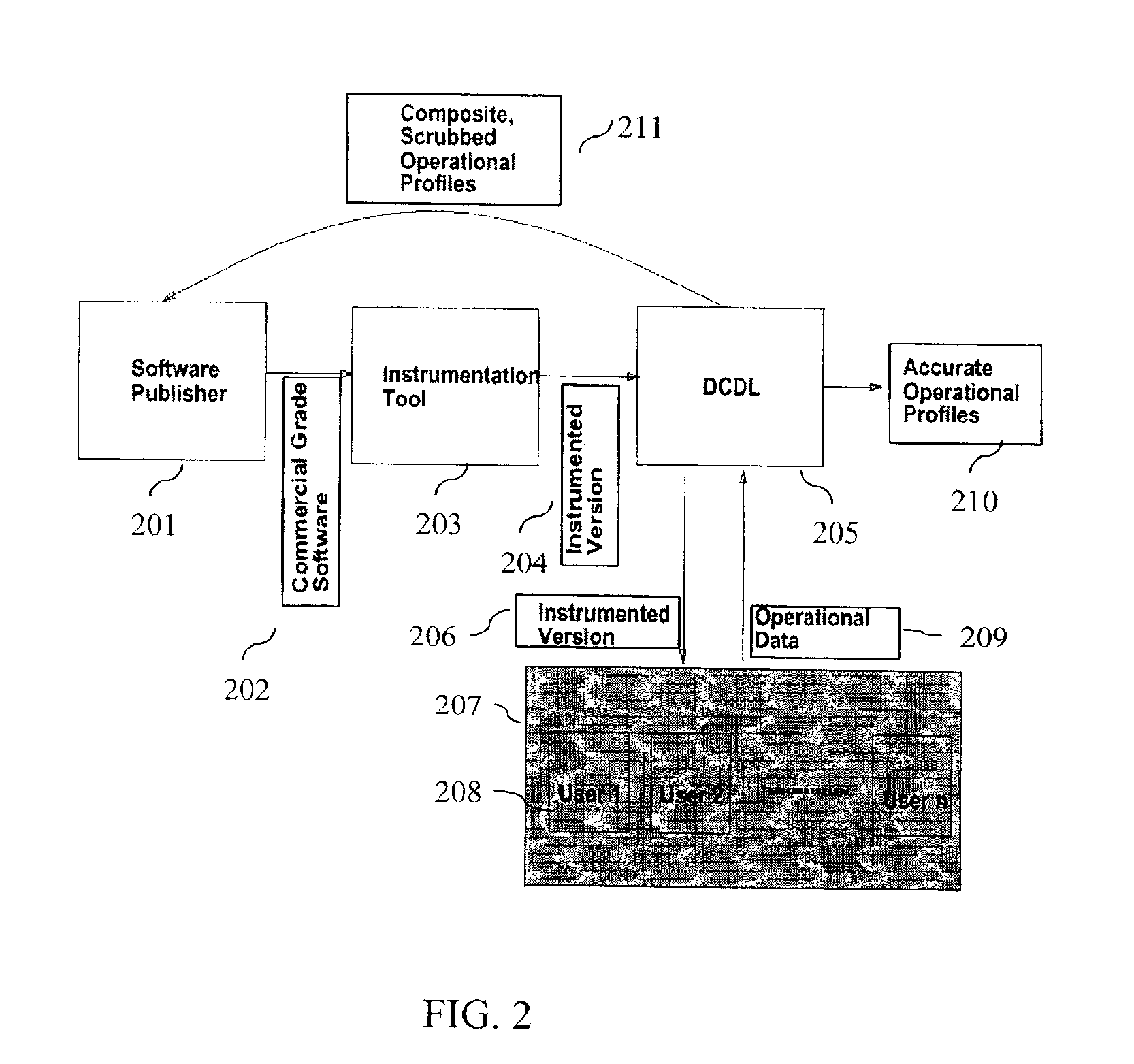
A method and method that builds accurate operational profiles for COTS software. The systems and methods disclosed allow software vendors to detect misused and unused features; identify common machine configurations for a given piece of software or software component; monitor changing user habits as new software version are released; derive more accurate testing methods for in-house testing purposes; and create user manuals which focus on those features most frequently used, or misused, by users. The disclosed system and method provides the tools enabling a software certification laboratory (SCL) to gather detailed usage data and failure data for a software application as it is used in the field. With this data the SCL can confidently issue certificates of reliability for software products.
Owner:SYNOPSYS INC
System and method for authorizing software use
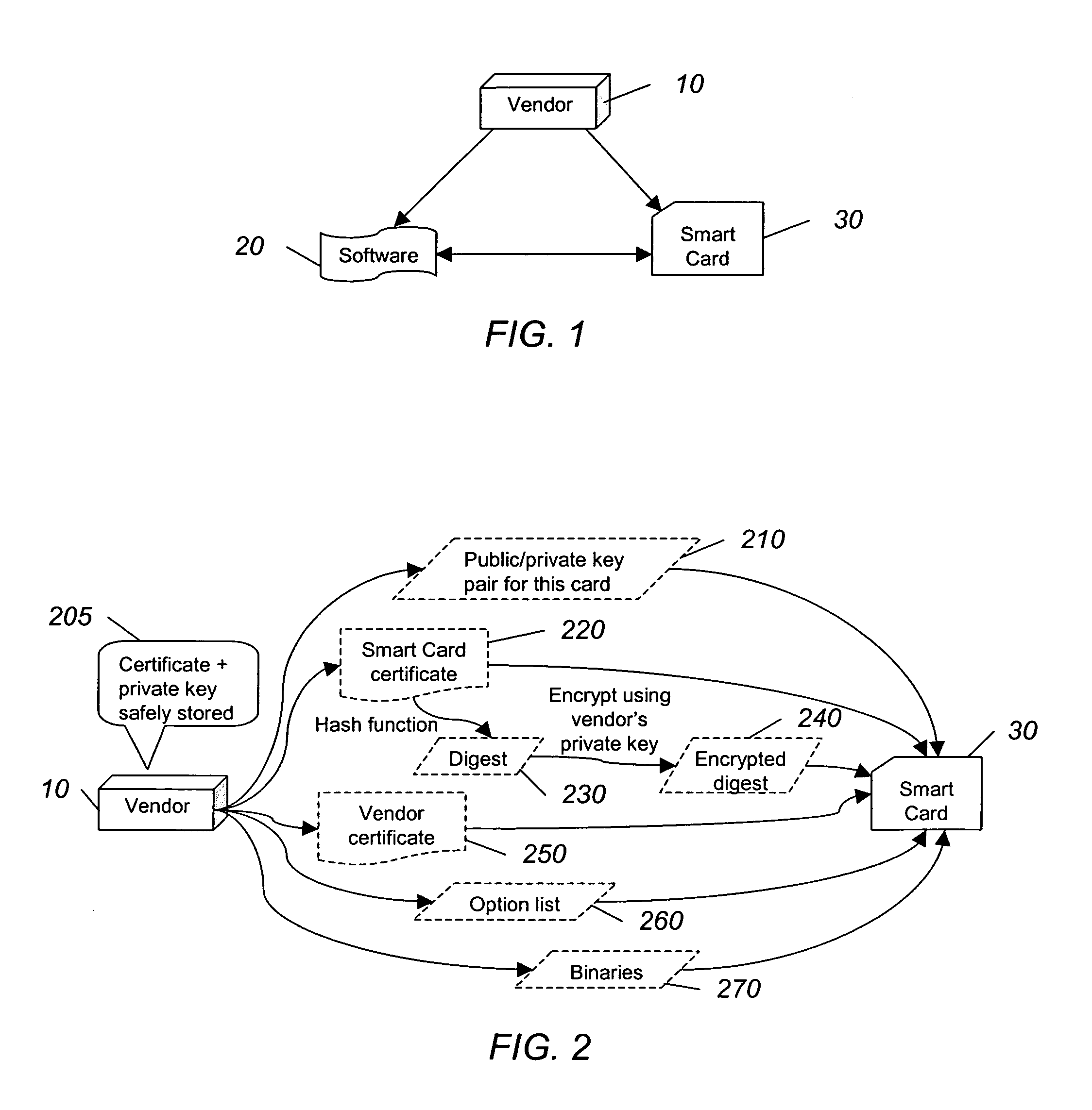
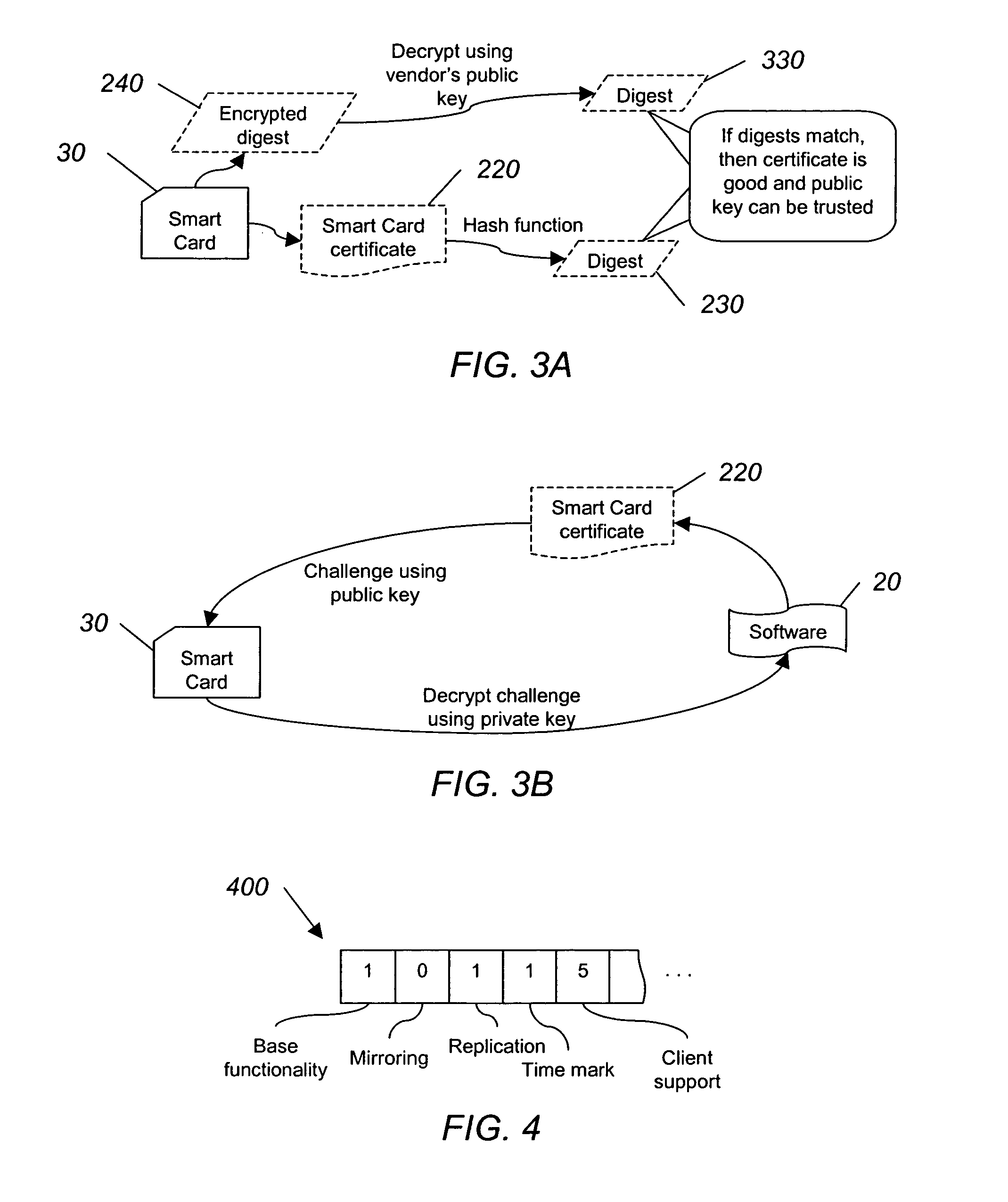
InactiveUS20050138387A1User identity/authority verificationComputer security arrangementsSmart cardSoftware vendor
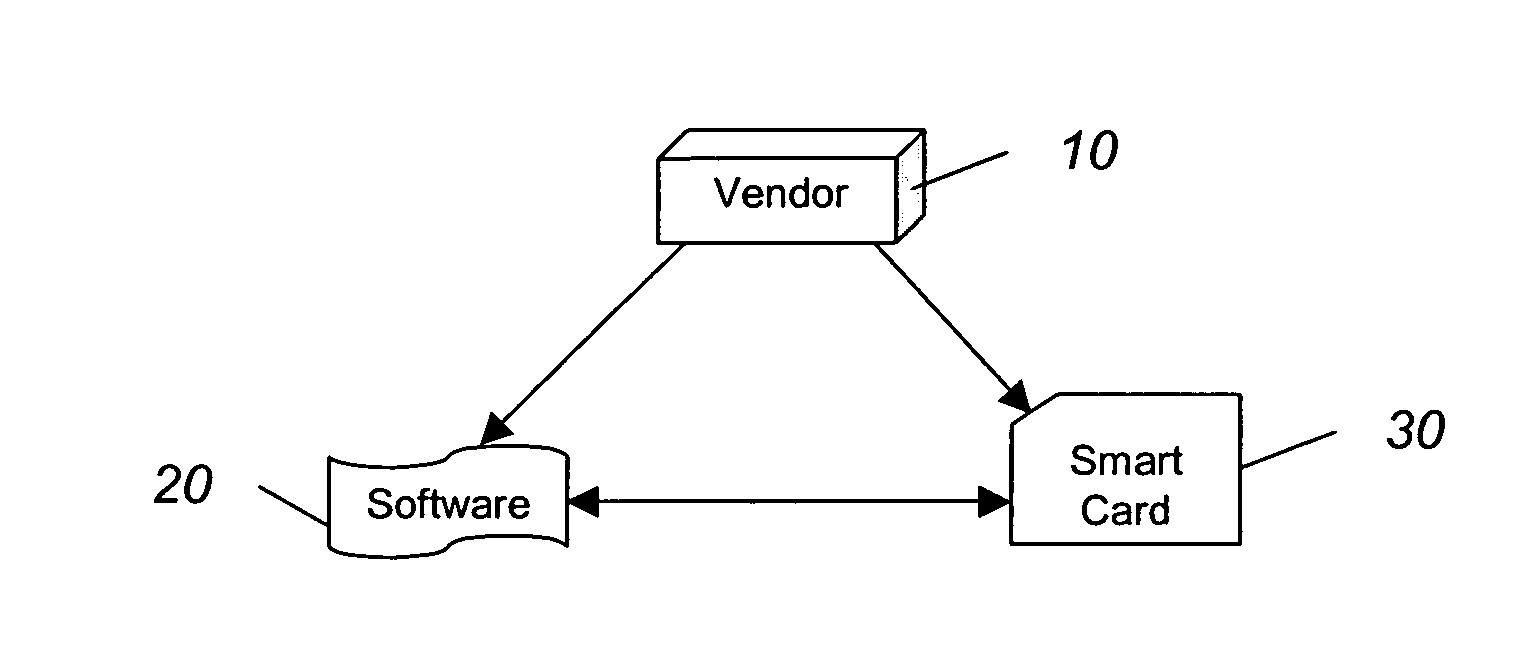
A software vendor freely distributes software to users and issues smart cards to be used with the software. The smart card includes at least one software module missing from the software package and a list of allowed functionality dictating the capabilities of the software package. A user authenticates, using, e.g., public key cryptography, the smart card, which authorizes the use of the software. Once authorized, the module missing from the software is reunited with the rest of the software package. The software can be used limited to the allowed functionality included with the card. If more or different functionality is needed, the user can purchase another card authorizing such additional functionality, and then transfer the new functionality to the old smart card.
Owner:FALCONSTOR
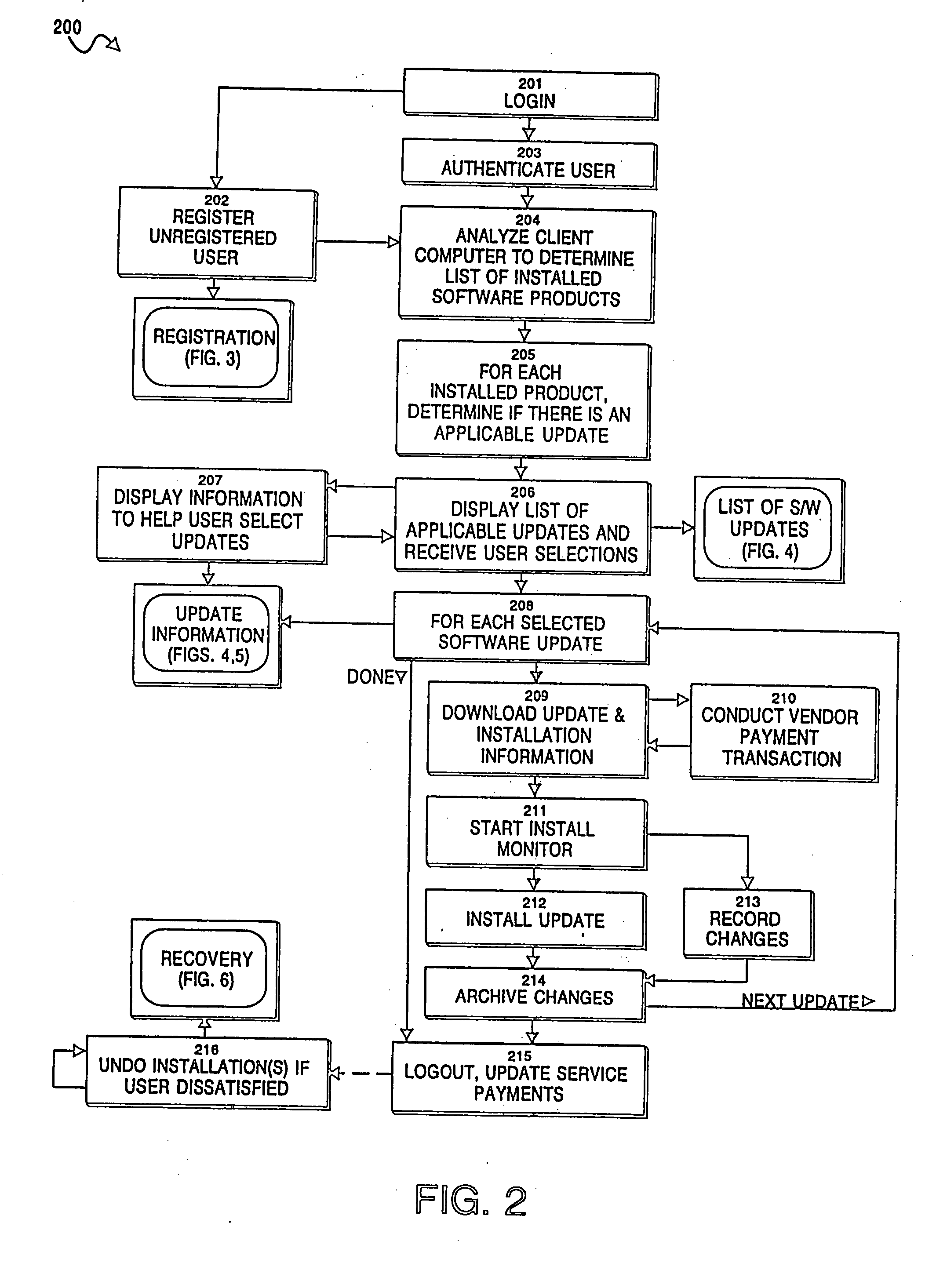
Automatic updating of diverse software products on multiple client computer systems
InactiveUS20050273779A1Program control using stored programsBuying/selling/leasing transactionsPaymentSoftware update
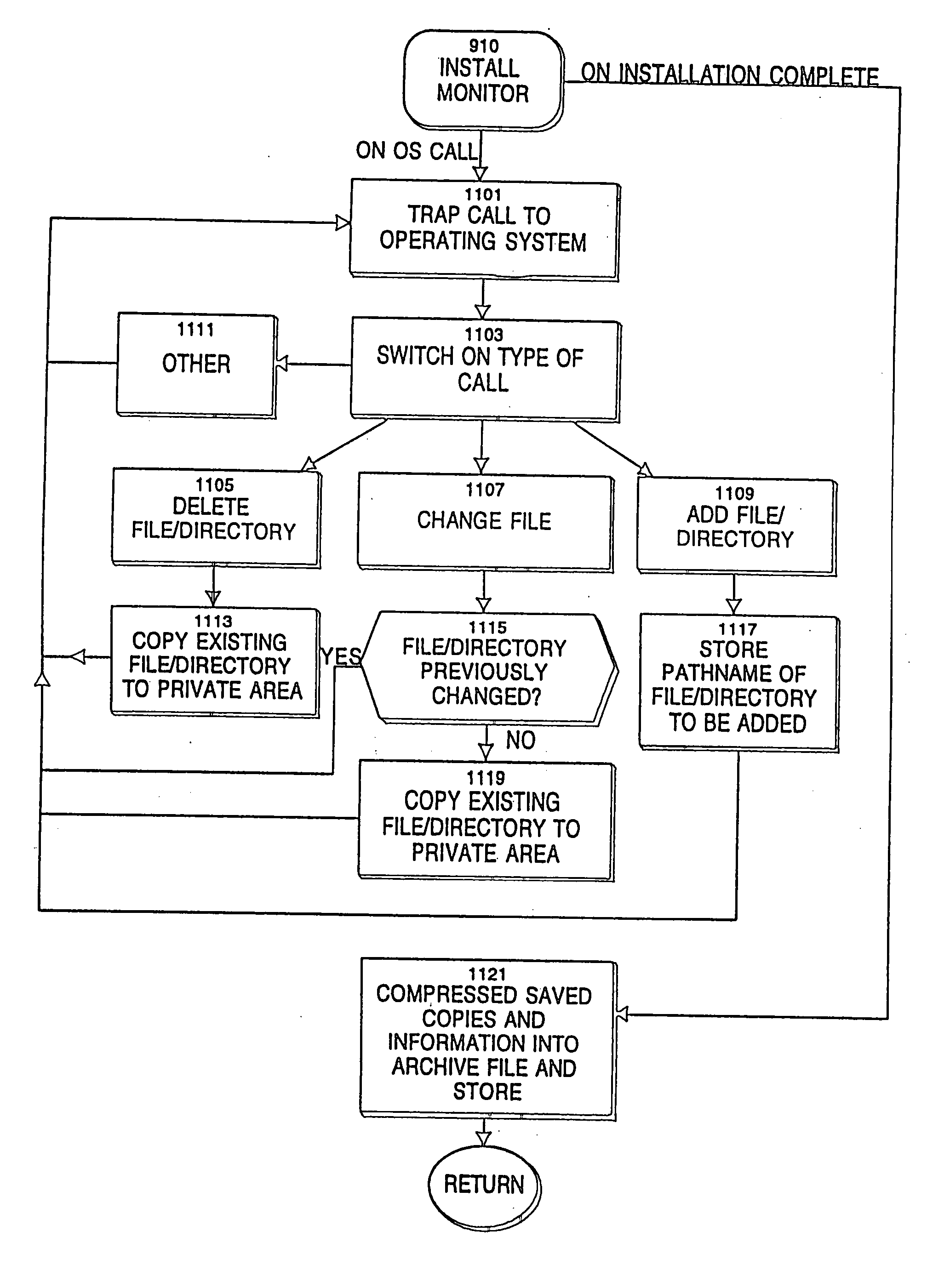
A system and method update client computers of various end users with software updates for software products installed on the client computers, the software products manufacturered by diverse, unrelated software vendors. The system includes a service provider computer system, a number of client computers and software vendor computer systems communicating on a common network. The service provider computer system stores in an update database information about the software updates of the diverse software vendors, identifying the software products for which software updates are available, their location on the network at the various software vendor computer systems, information for identifying in the client computers the software products stored thereon, and information for determining for such products, which have software updates available. Users of the client computers connect to the service provider computer and obtain a current version of portions of the database. The client computer determines that software products stored thereon, and using this information, determines from the database, which products have updates available, based on product name and release information for the installed products. The user selects updates for installation. The selected updates are downloaded from the software vendor computer systems and installed on the client computer. Payment for the software update and the service is mediated by the service provider computer. Authentication of the user ensures only registered users obtain software updates. Authentication of the software updates ensures that the software updates are virus free and uncorrupted. Changes to the client computer during installation are monitored and archived, allowing the updates to be subsequently removed by the user.
Owner:MCAFEE LLC
Automated software upgrade utility
InactiveUS6976062B1Multiple digital computer combinationsProgram loading/initiatingProduct typeOperational system
Owner:INTERMEC IP CORP
Support for multiple security policies on a unified authentication architecture
ActiveUS8166304B2Digital data processing detailsUser identity/authority verificationData processing systemSecurity kernel
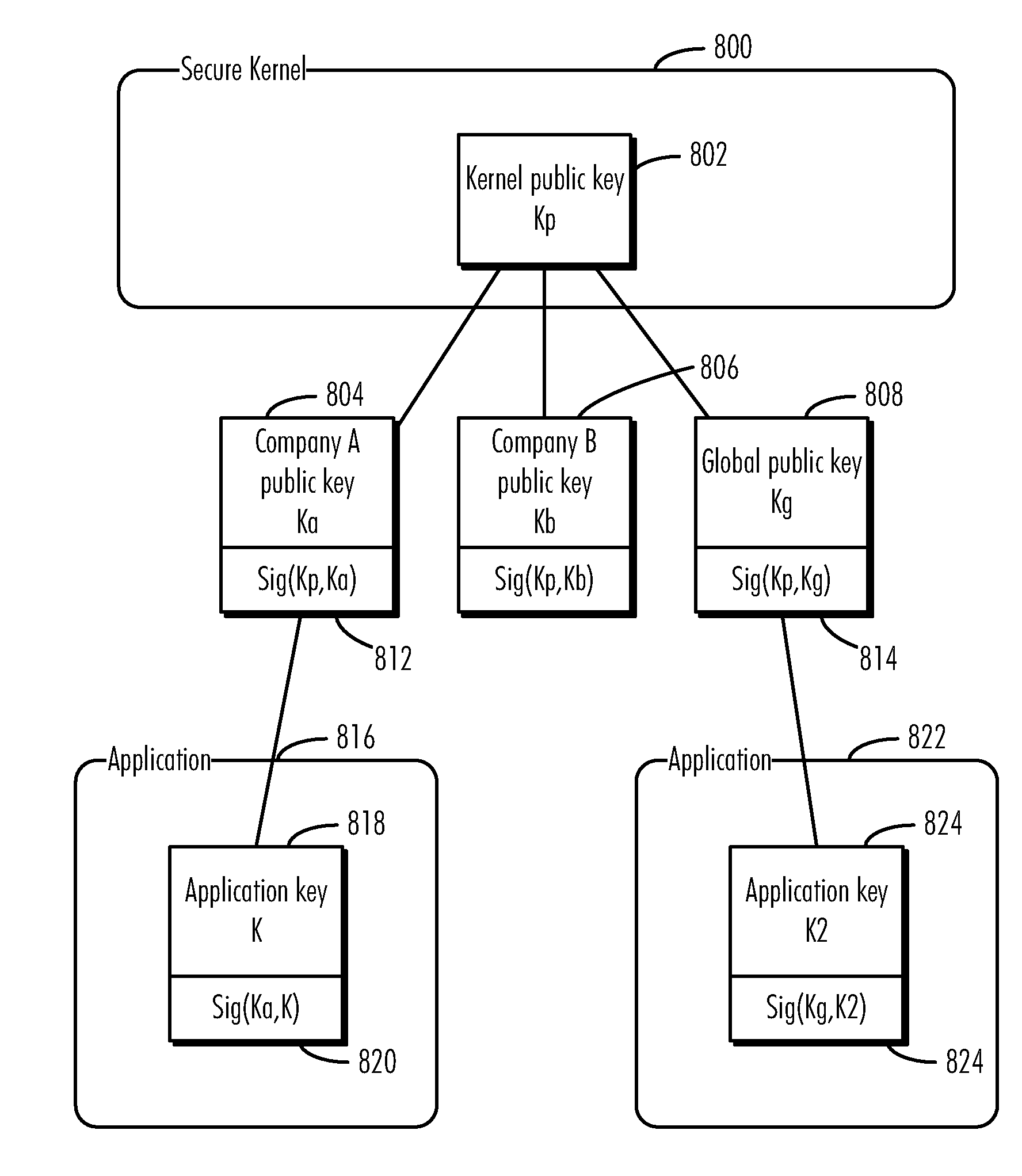
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for independent developers to develop software for the herein-described platform, a “global key pair” is provided in which both the public and private keys of the pair are publicly known, so that anyone may sign an application with the global key. Such an application may be allowed to execute by including the global key pair's public key in the key ring as a “vendor key” or, conversely, it may be disallowed by excluding the global public key from the key ring.
Owner:INT BUSINESS MASCH CORP
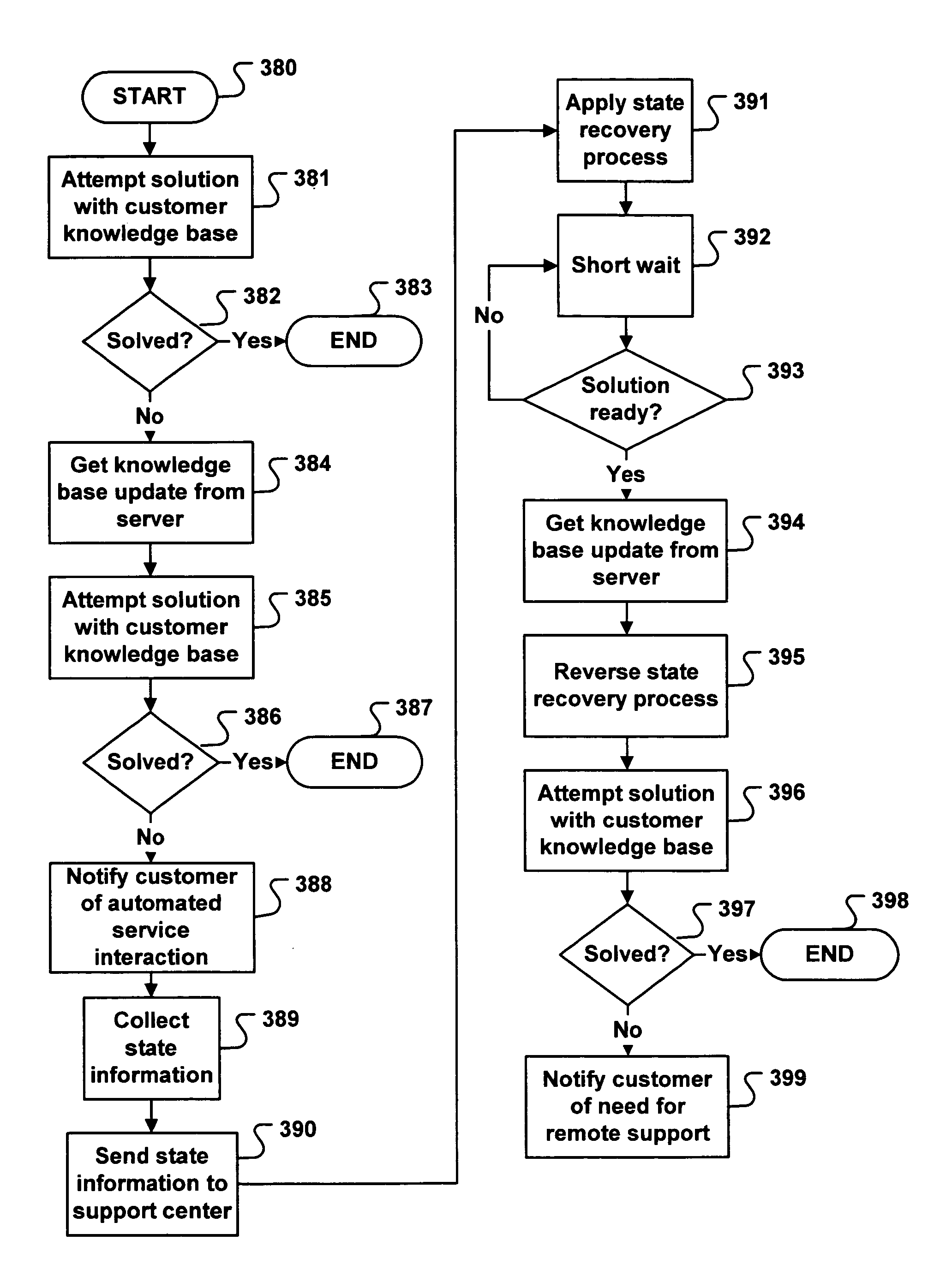
System for automated problem detection, diagnosis, and resolution in a software driven system
InactiveUS20050015678A1Guaranteed uptimeEasy to understandFault responseDetecting faulty hardware by remote testTheoretical computer scienceInstability
In many systems, computer software is a common source of failure or instability. The proliferation of multiple interacting applications from several different software vendors leads to “emergent” problems that are difficult or impossible to predict or prevent. The problems are compounded by the use of networks, which introduce the added complexity of applications on multiple machines interacting in complex scenarios. As a result, many business and home users are hindered from using software-based systems to their fullest potential. More effective use of these systems can be aided by an application which can provide services for monitoring, diagnosing, and solving problems that occur in the operation of the machines at a customer facility. In the system described herein, a database contains entries with executable code that can make use of these services in order to monitor, diagnose, and solve specific problems. Each entry in the database addresses a specific problem. The executable code is designed to isolate and recognize the problem, and then implement a fix or workaround for that problem. The executable code is designed to completely automate the entire process of detection and resolution of the problem. Further, manual intervention may be employed to complete the diagnosis or solution.
Owner:HFN LLC
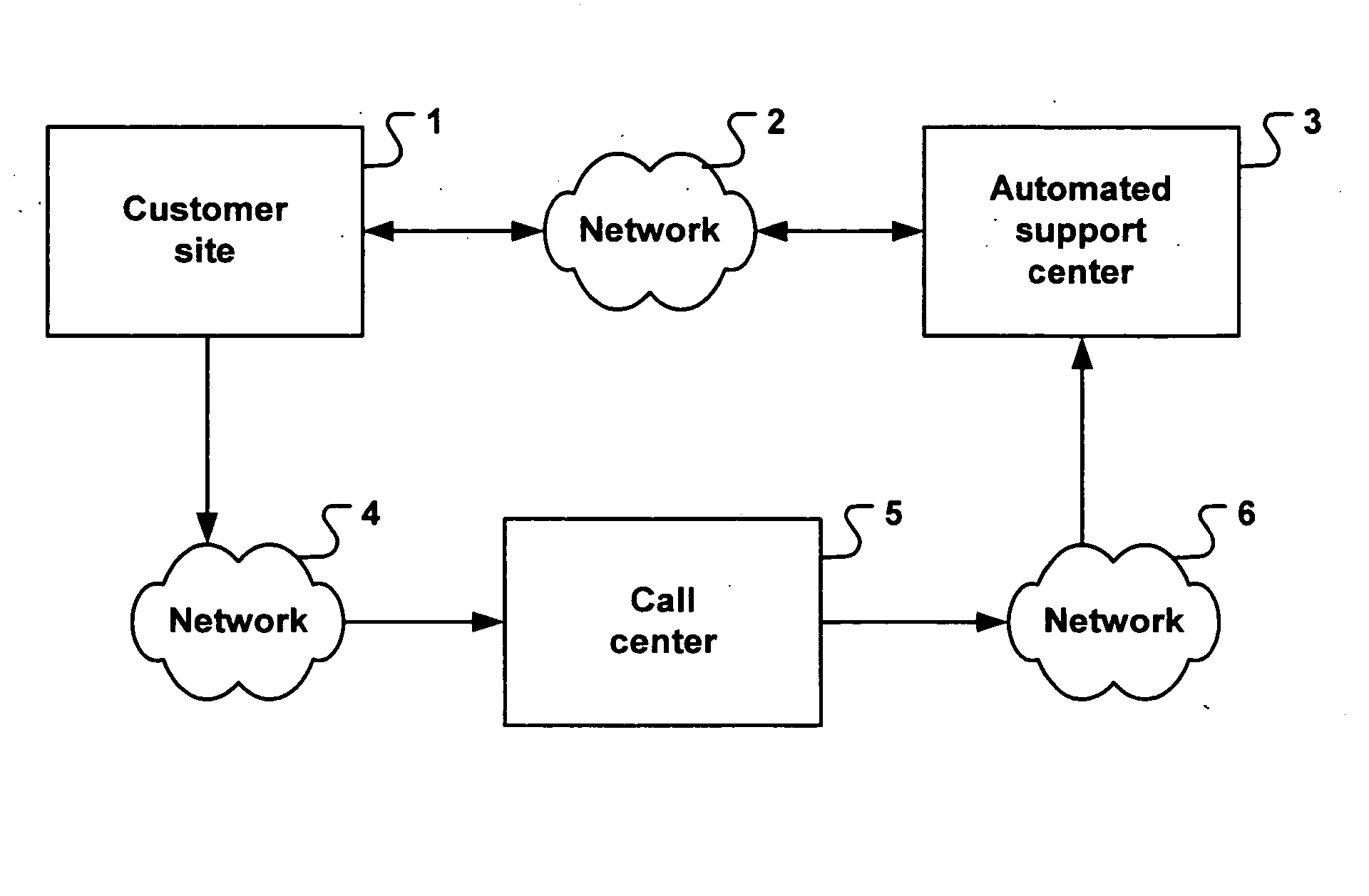
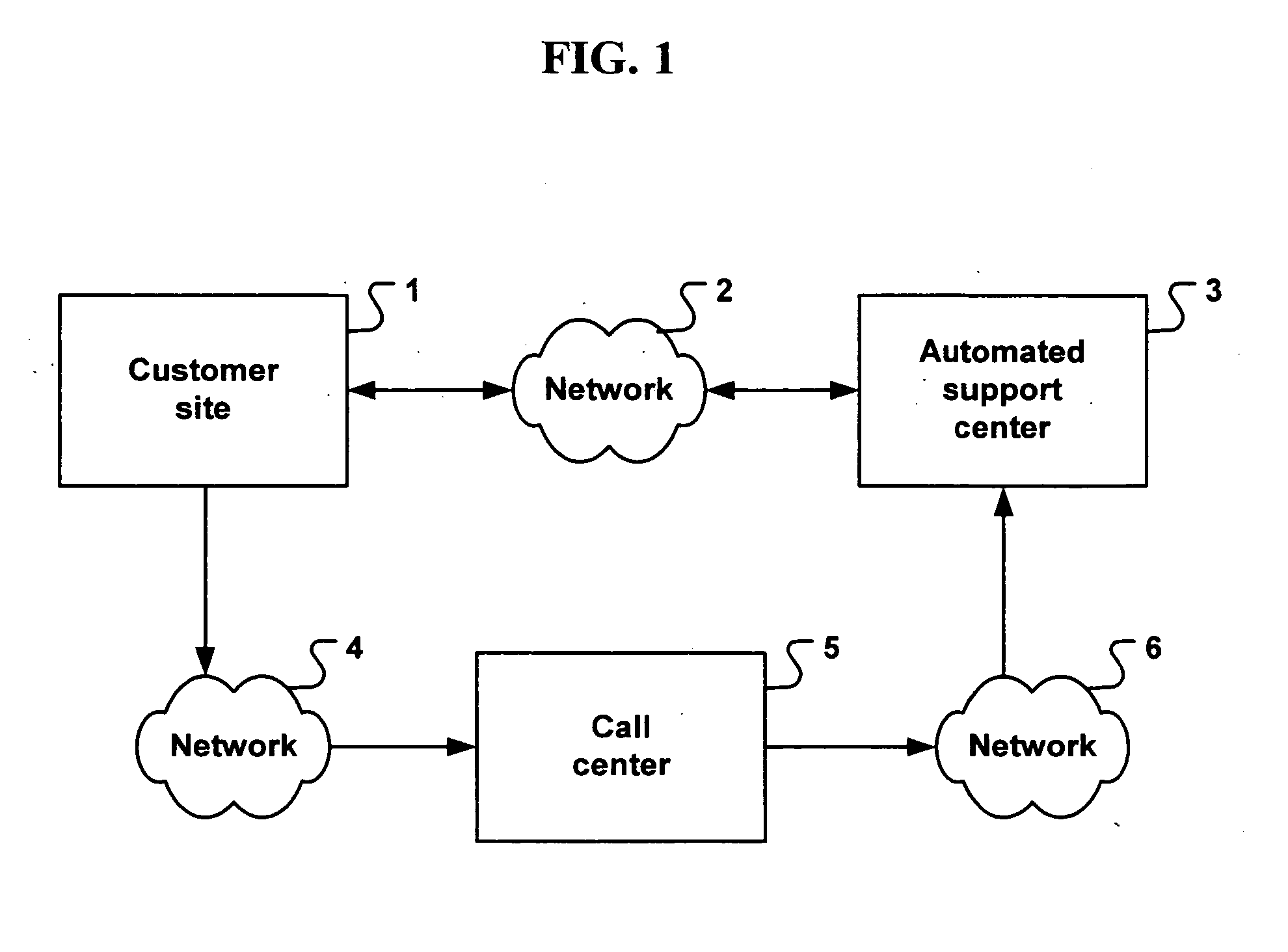
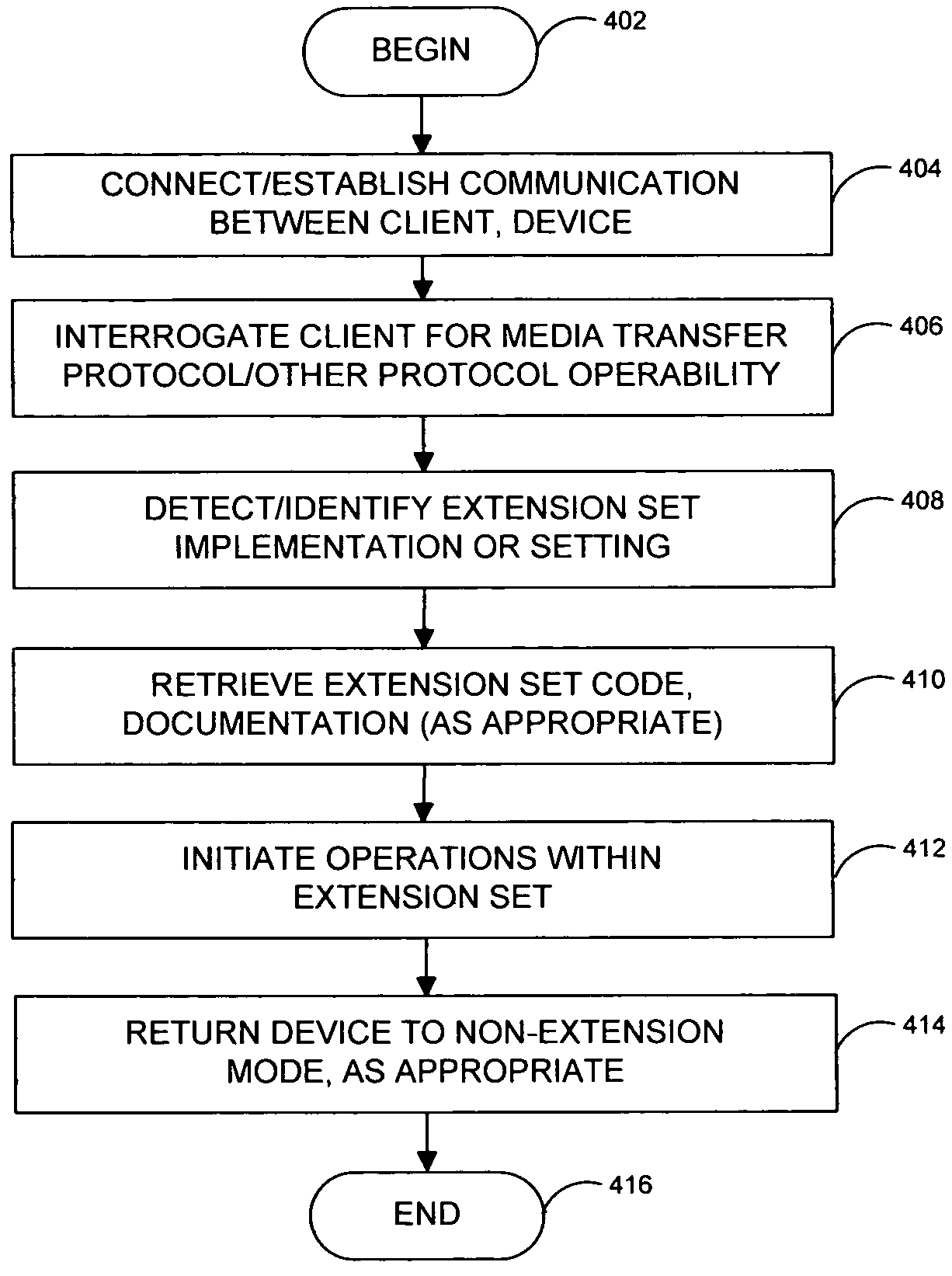
System and method for generating selectable extension to media transport protocol
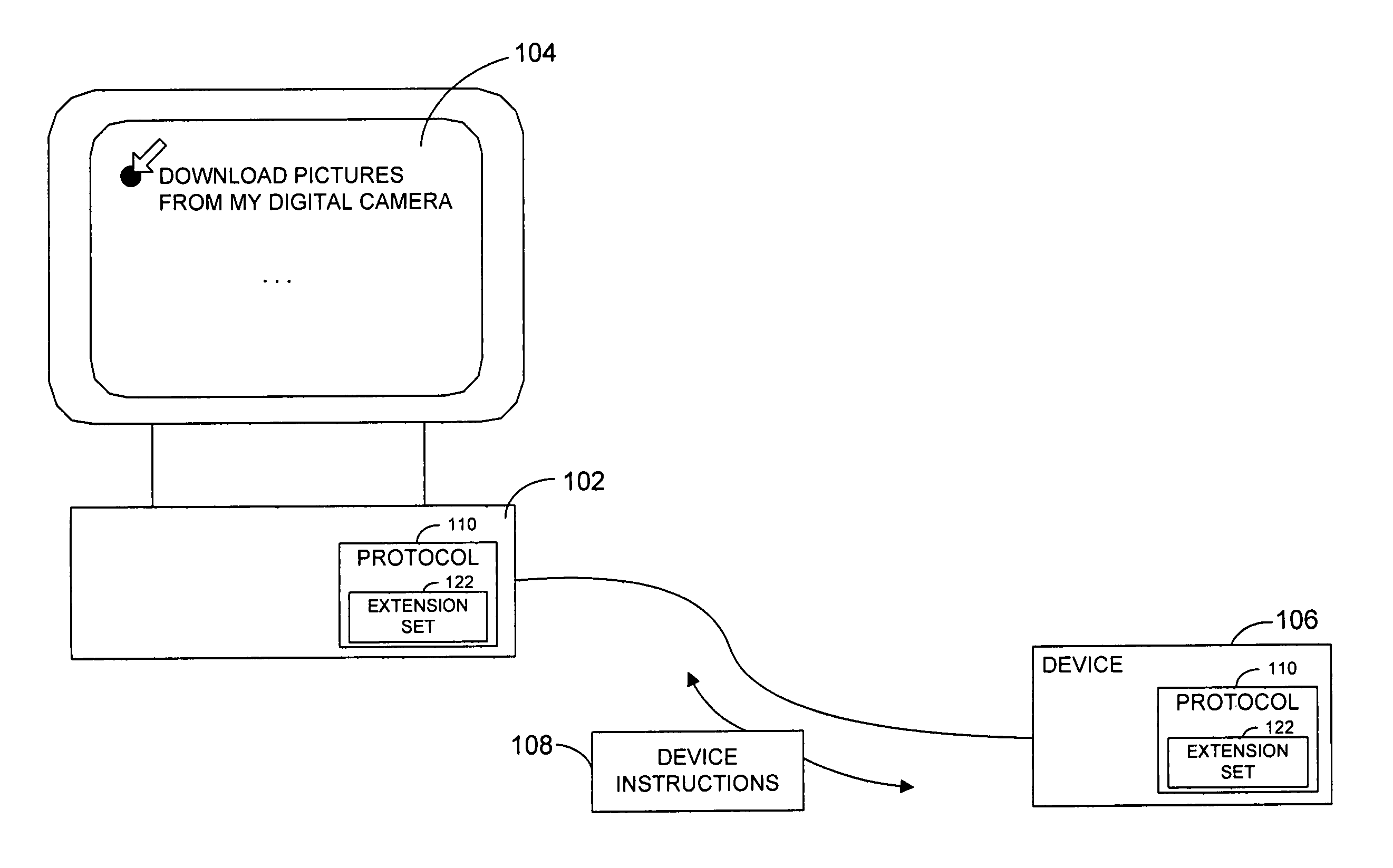
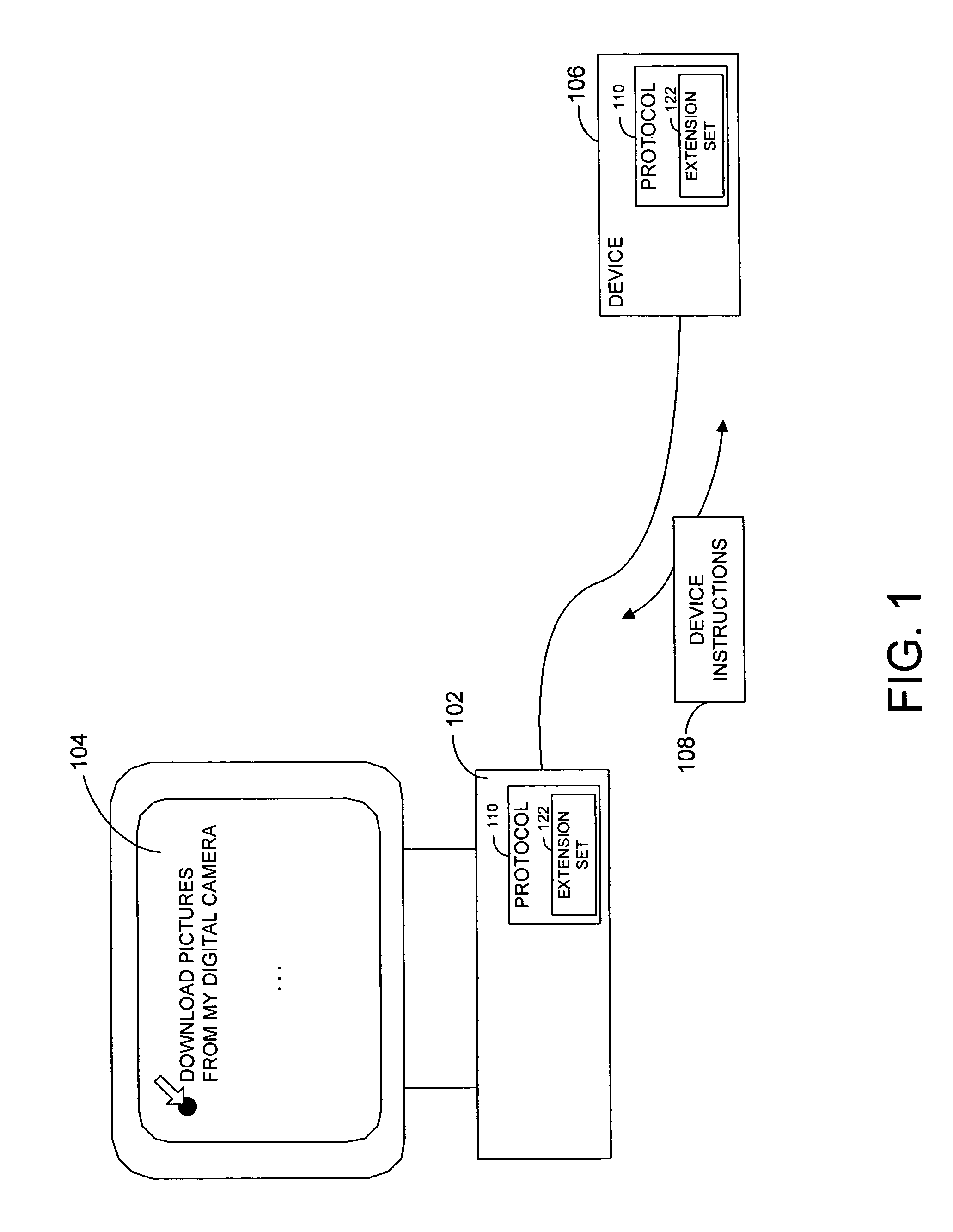
InactiveUS20060031545A1Special service provision for substationMultiple digital computer combinationsTransmission protocolExtension set
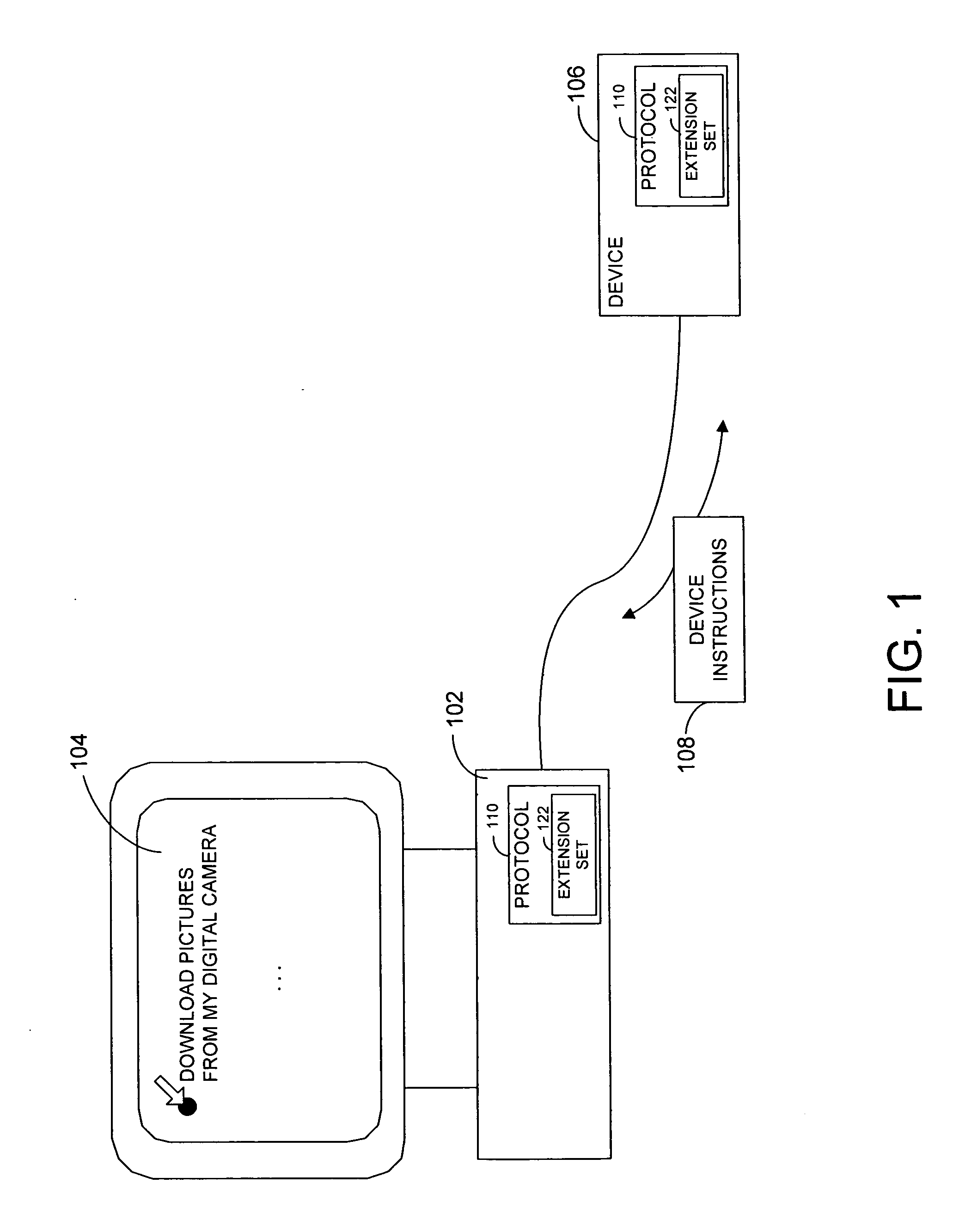
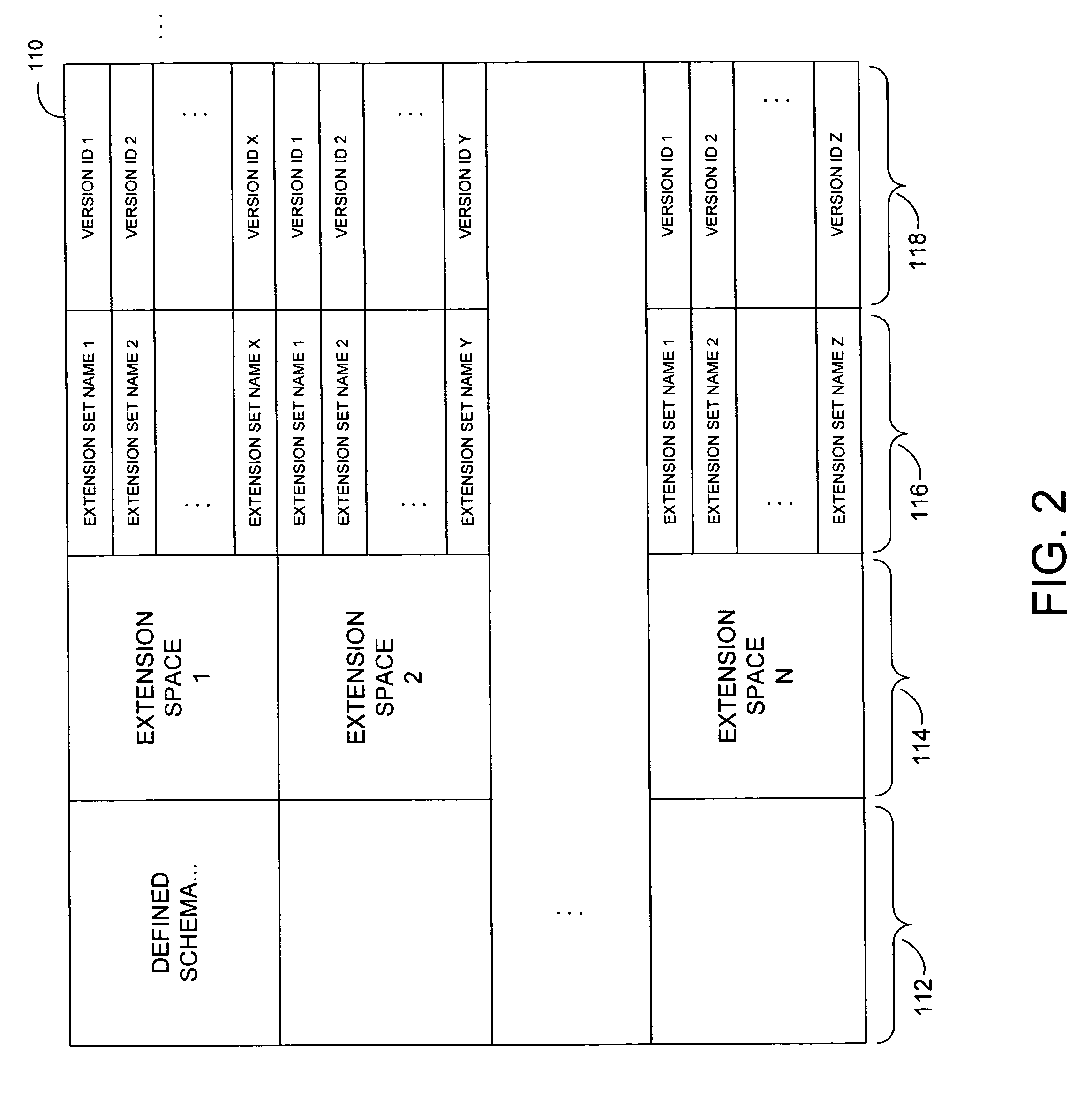
A protocol and related techniques and platforms allow vendors to selectably extend the Media Transport Protocol (MTP), or other defined protocols to implement vendor-specific commands, data fields, instructions and other extension sets. According to embodiments of the invention in one regard, one or more extension space may be utilized to derive independent extension sets, in part by separating the extension space according to a unique identifier assigned to or associated with a given vendor. In embodiments that unique identifier may be or include an Internet DNS (Domain Name System) domain name, or other extension set name or identifier. According to the invention in one regard, because a DNS domain name may be independently registered and secured by participating vendors or manufacturers and by definition uniquely assigned, the separation of vendor extension sets by that type of name may be automatic and free from conflict. Vendors or manufacturers, such as makers of digital cameras, digital video cameras, audio players such as MP3 or other players, software vendors or others may therefore freely design extensions to the Media Transport Protocol or other protocols, without a need to clear those extensions with a standards body and with confidence that their commands, data fields and other extensions may be free from overlap with that of other manufacturers.
Owner:MICROSOFT TECH LICENSING LLC
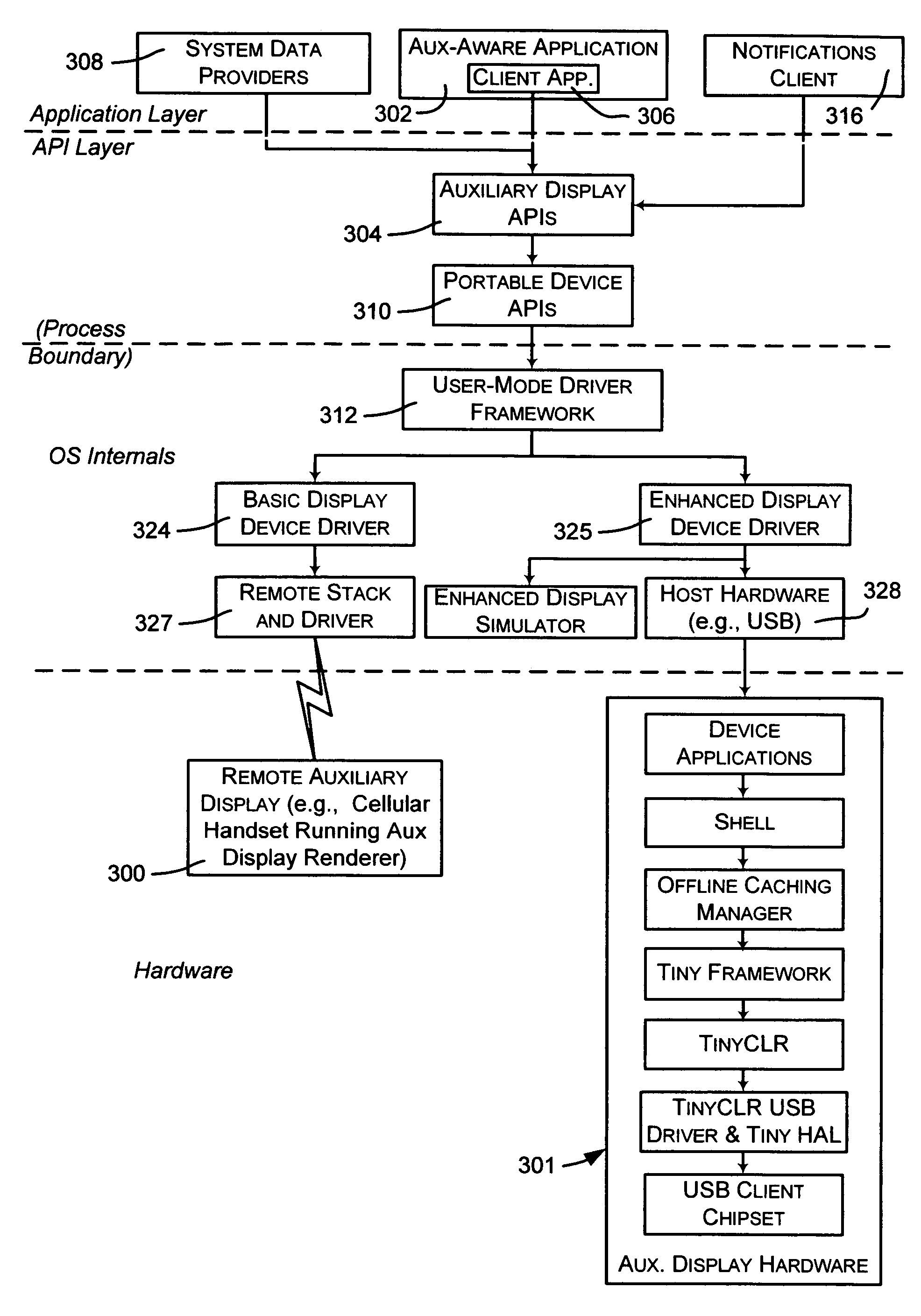
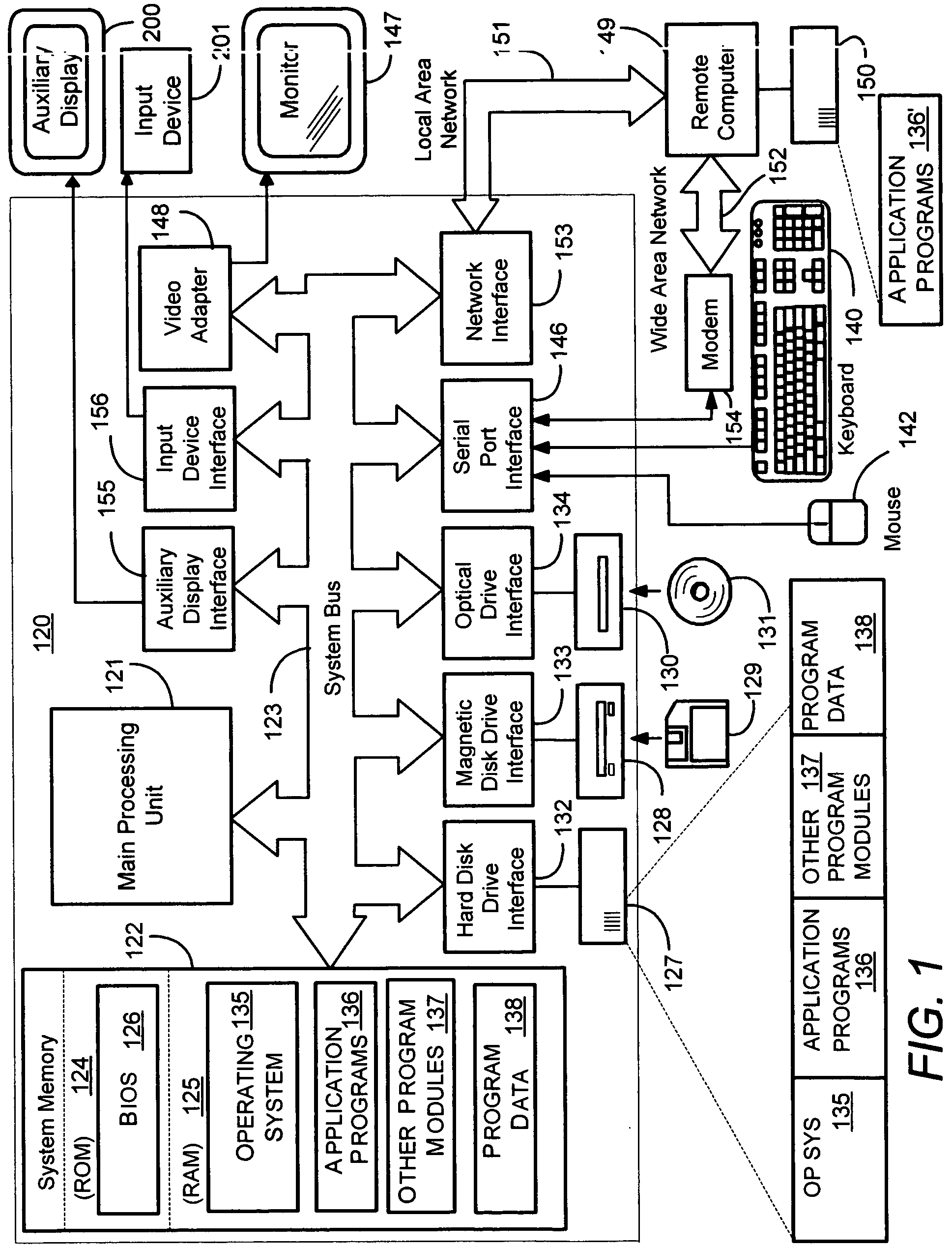
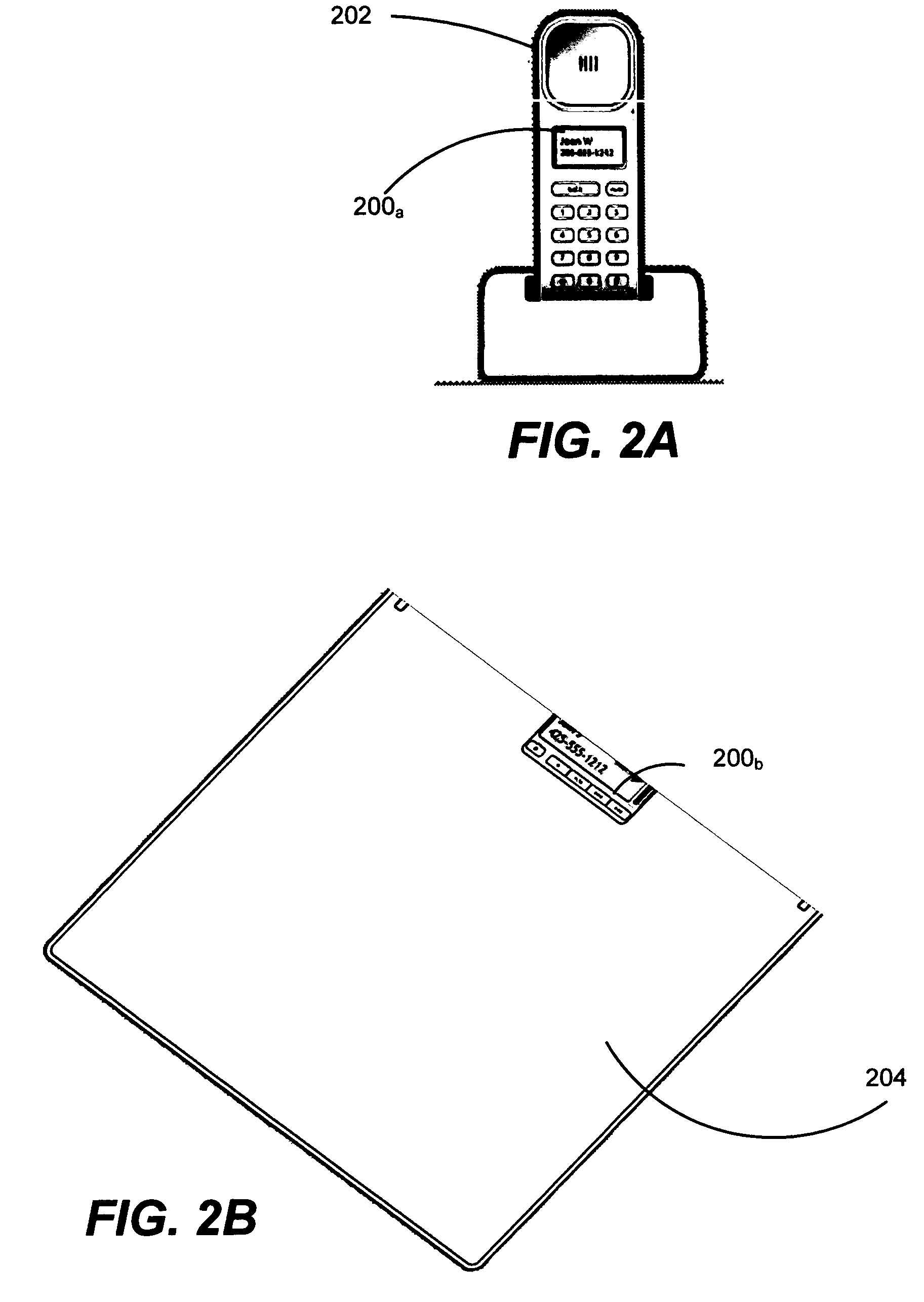
Sending notifications to auxiliary displays
InactiveUS7581034B2Increase profitImprove abilitiesInterprogram communicationCathode-ray tube indicatorsConnection typeRemote control
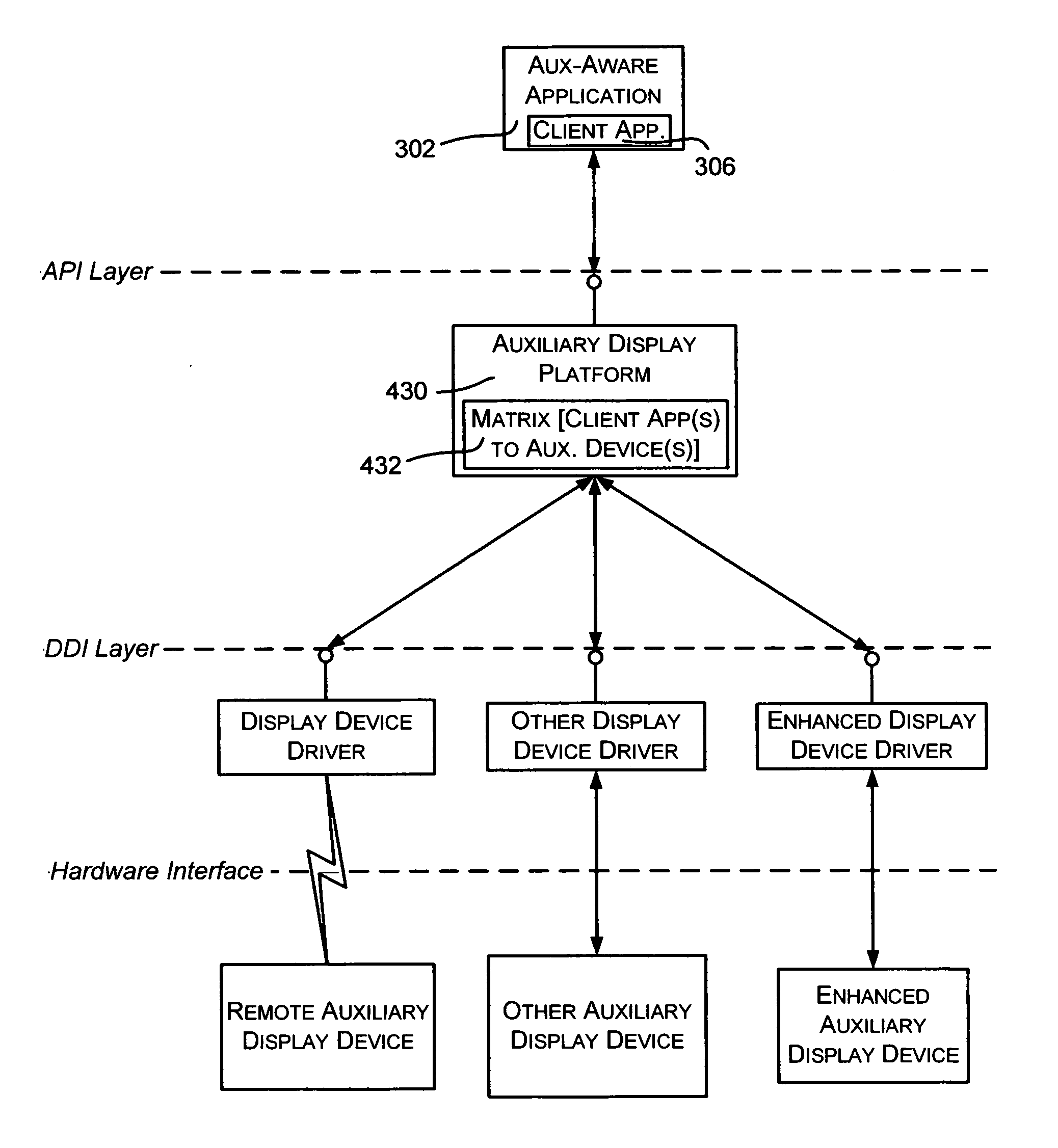
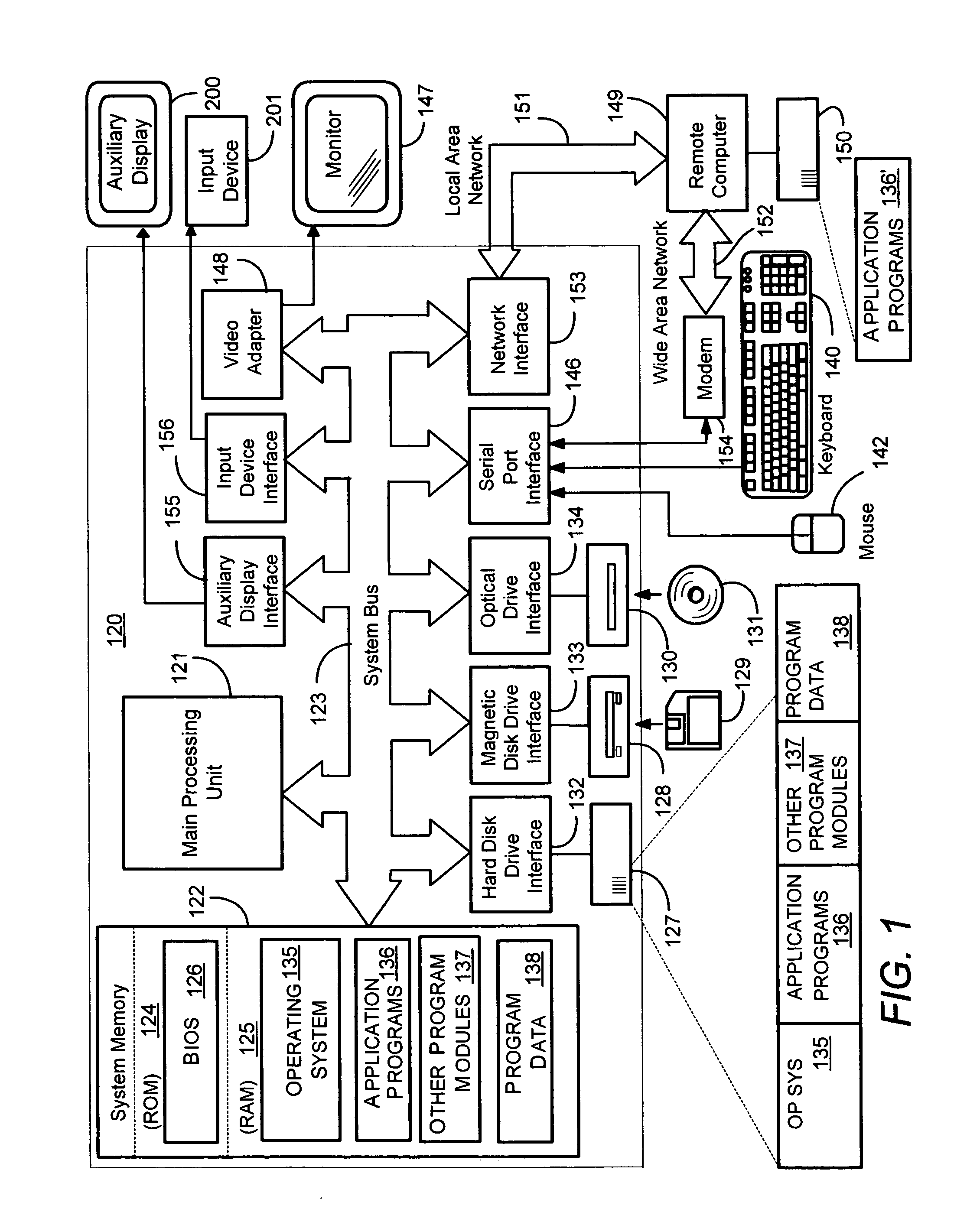
Described is a system and method by which application programs running on a main computer system communicate with an auxiliary display device (such as a cell phone, pocket-sized computer, alarm clock, television, digital picture frame and so forth) to provide viewable information on the device, remote control capabilities, and notifications. Via API calls, programs provide information in the same format regardless of the device capabilities and / or the connection type. An auxiliary display platform converts a notification into a format understood by a device driver, which then filters the notification as desired for its particular hardware device before the notification is communicated. Return communications return data such as status and user interaction with the displayed information. Software vendors may thus write code once to output notifications on auxiliary displays, while hardware manufacturers can have their devices work as auxiliary displays, with little or no modification to existing hardware.
Owner:MICROSOFT TECH LICENSING LLC
Sending notifications to auxiliary displays
InactiveUS20060164324A1Improve abilitiesIncrease profitInterprogram communicationCathode-ray tube indicatorsConnection typeRemote control
Described is a system and method by which application programs running on a main computer system communicate with an auxiliary display device (such as a cell phone, pocket-sized computer, alarm clock, television, digital picture frame and so forth) to provide viewable information on the device, remote control capabilities, and notifications. Via API calls, programs provide information in the same format regardless of the device capabilities and / or the connection type. An auxiliary display platform converts a notification into a format understood by a device driver, which then filters the notification as desired for its particular hardware device before the notification is communicated. Return communications return data such as status and user interaction with the displayed information. Software vendors may thus write code once to output notifications on auxiliary displays, while hardware manufacturers can have their devices work as auxiliary displays, with little or no modification to existing hardware.
Owner:MICROSOFT TECH LICENSING LLC
Application store
ActiveUS20110252415A1Reduce decreaseQuickly and efficiently locatingResourcesSpecific program execution arrangementsSoftware distributionPurchasing
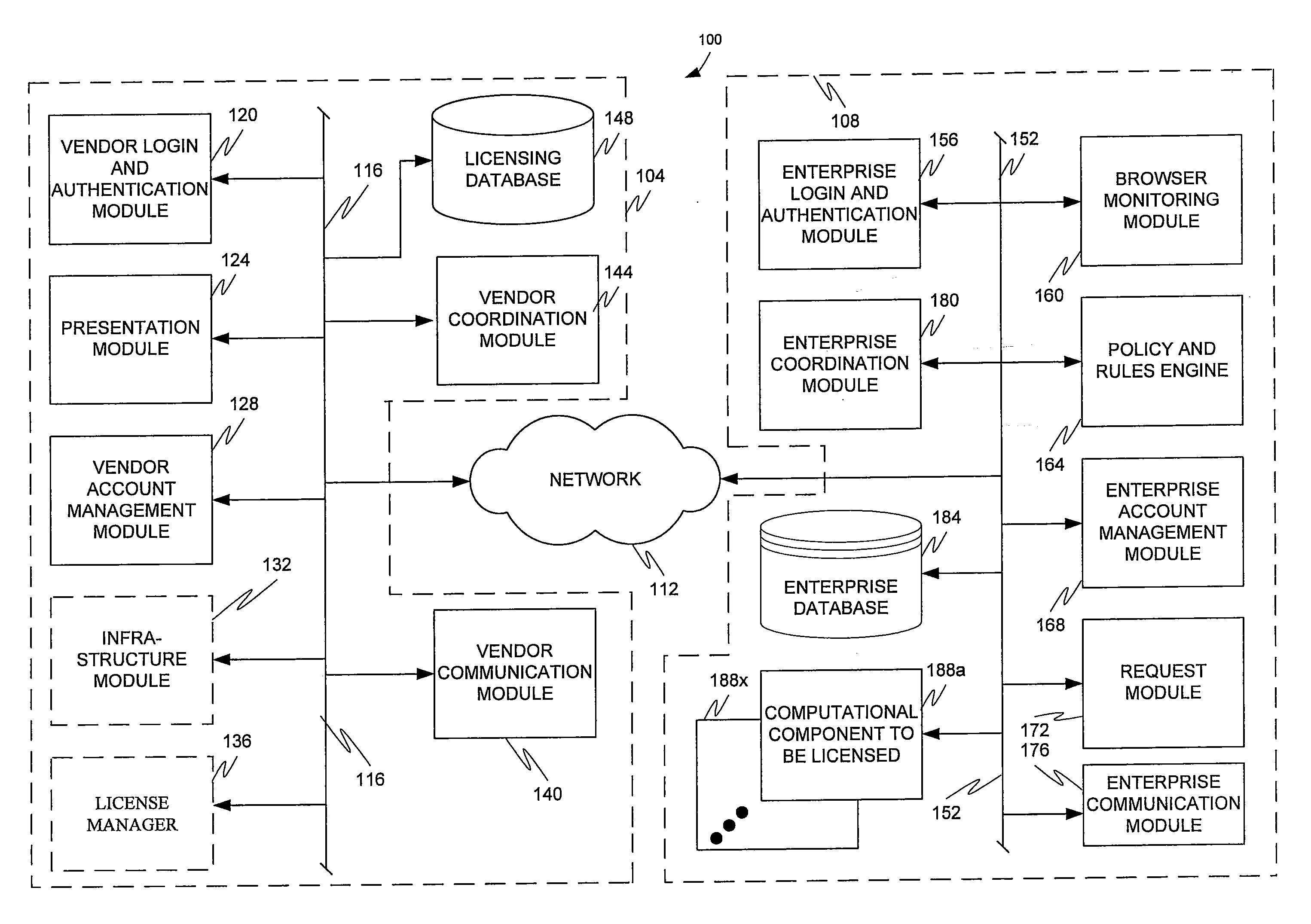
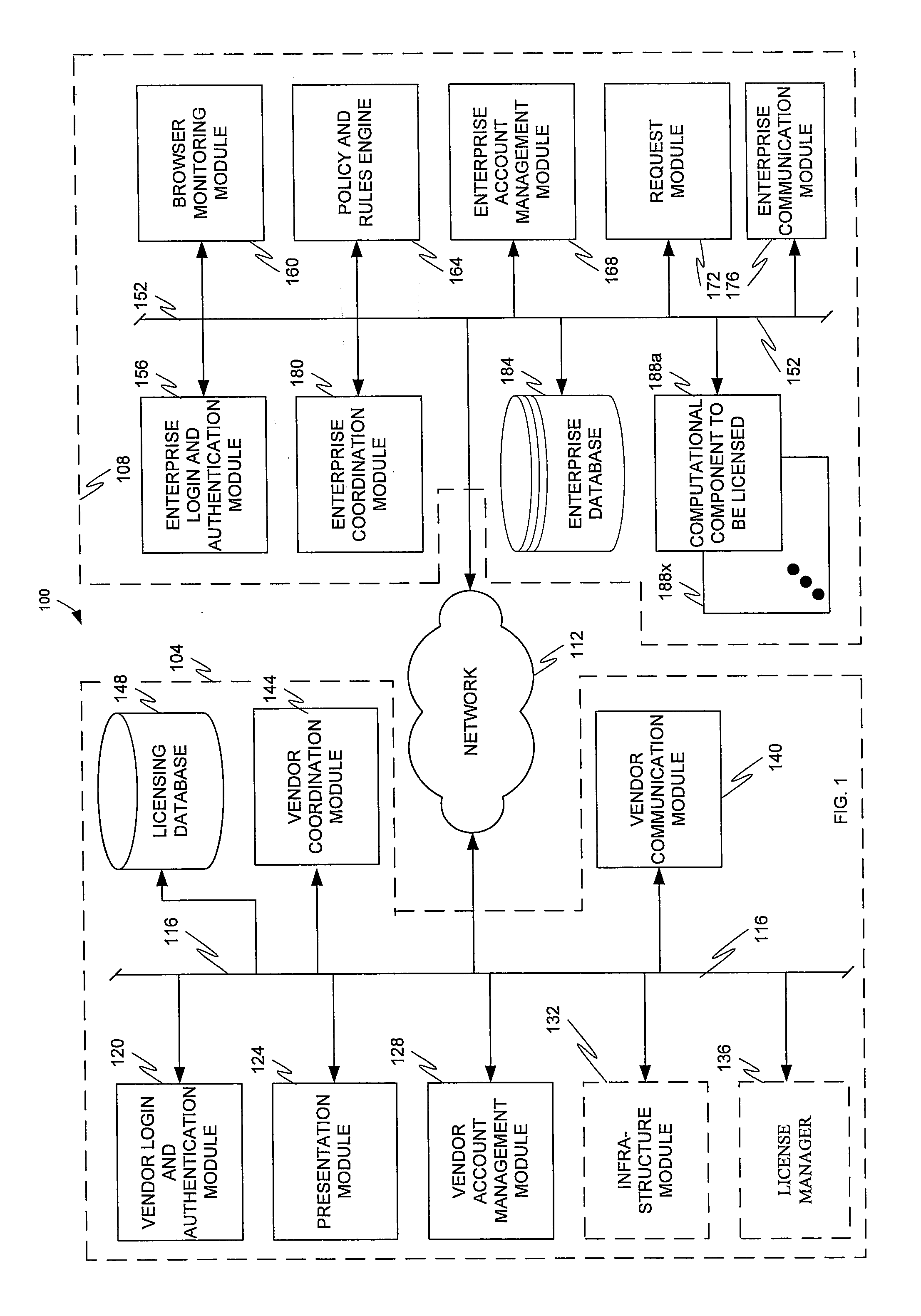
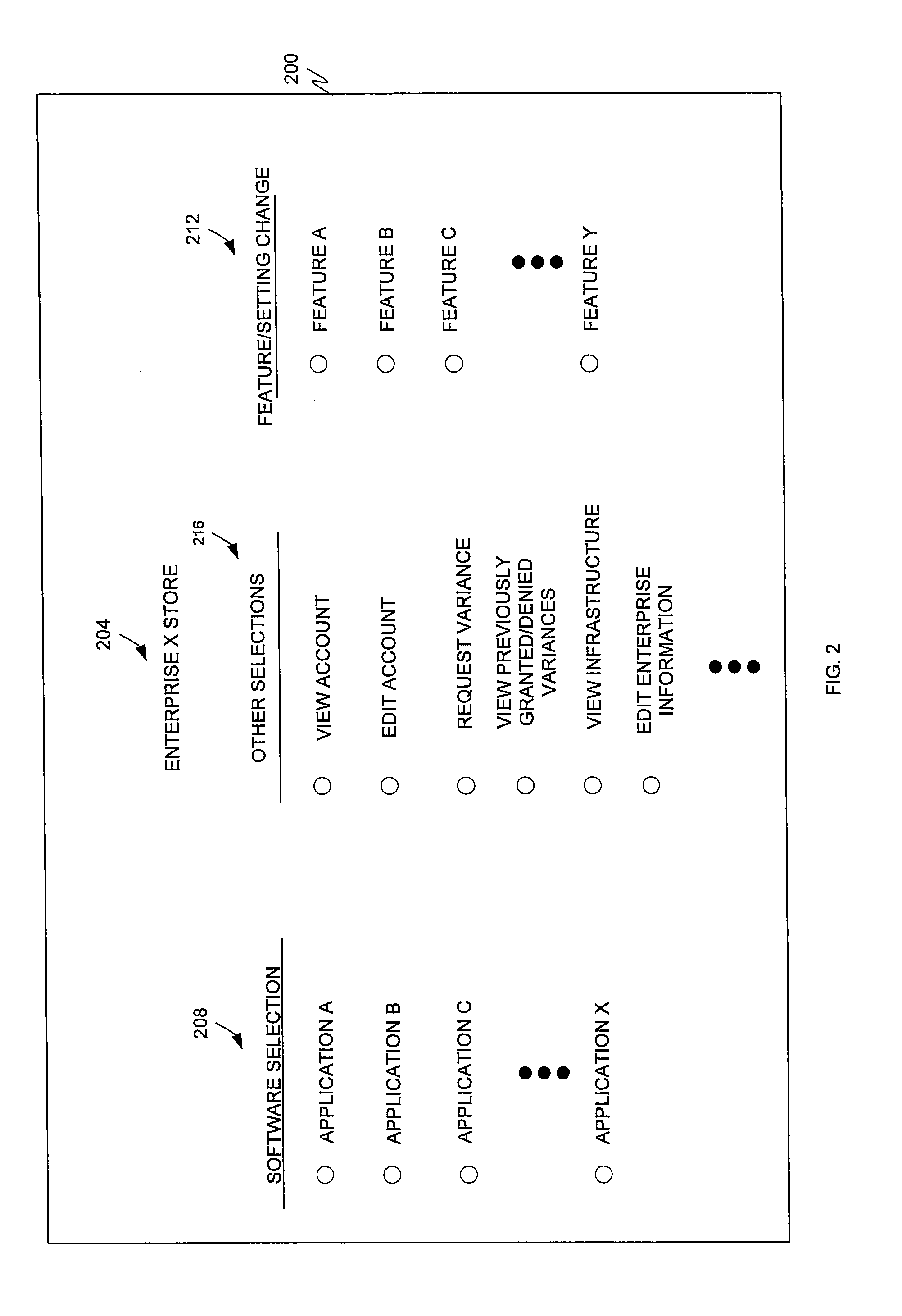
The present invention is directed to a software distribution architecture in which a software vendor provides a software store that is coordinated with the unique requirements of a software purchasing enterprise. Examples of the requirements include the enterprise infrastructure, information technology requirements and / or approval, account billing, and other attributes.
Owner:AVAYA INC
User authorization method and system and device thereof
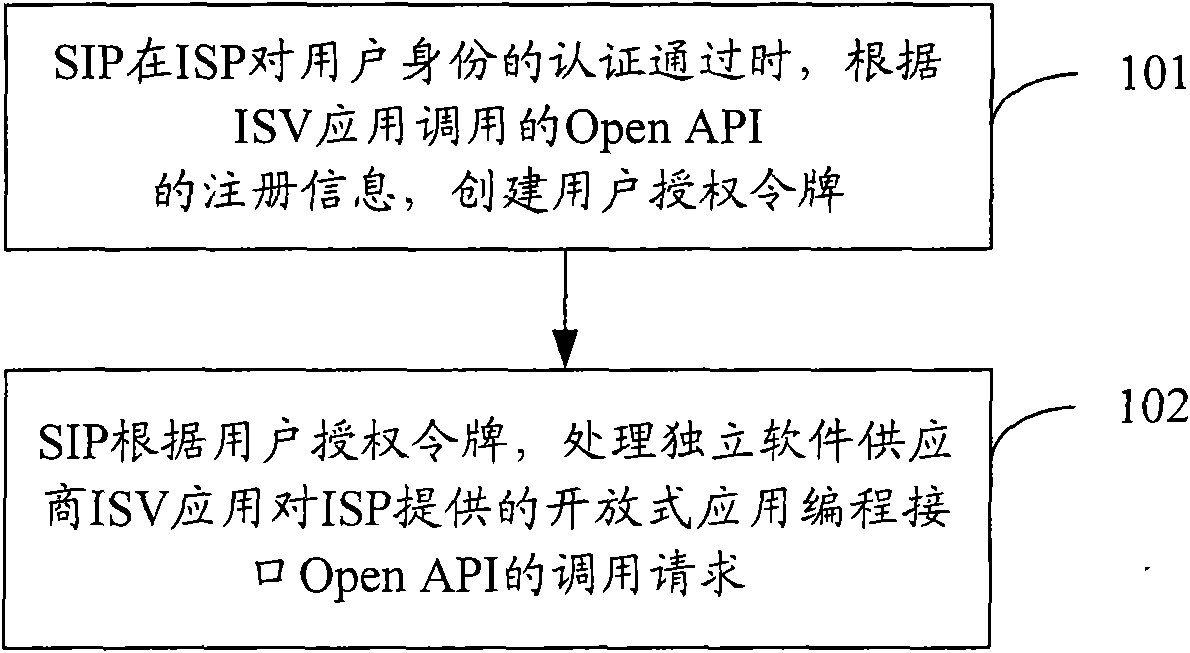
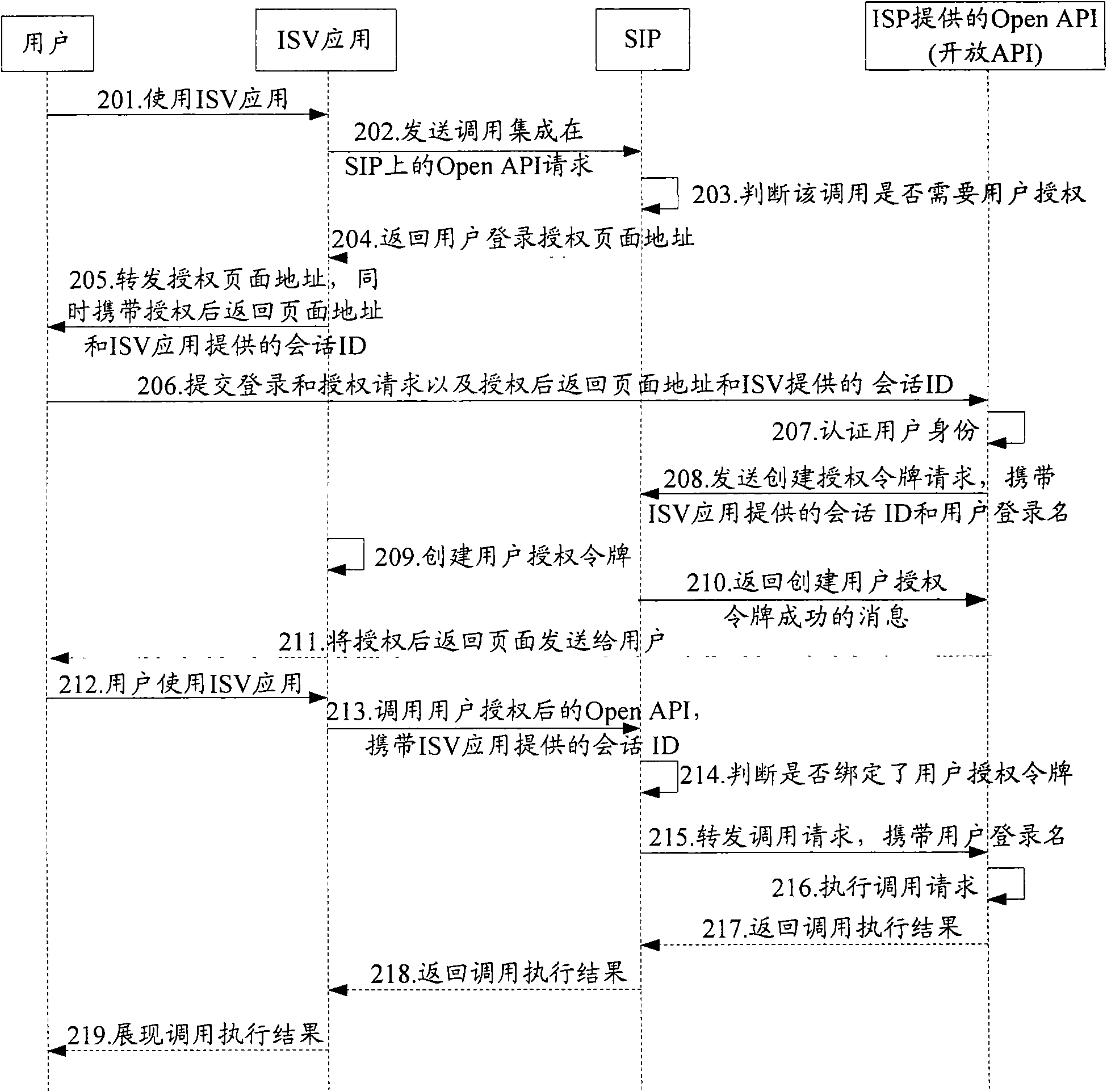
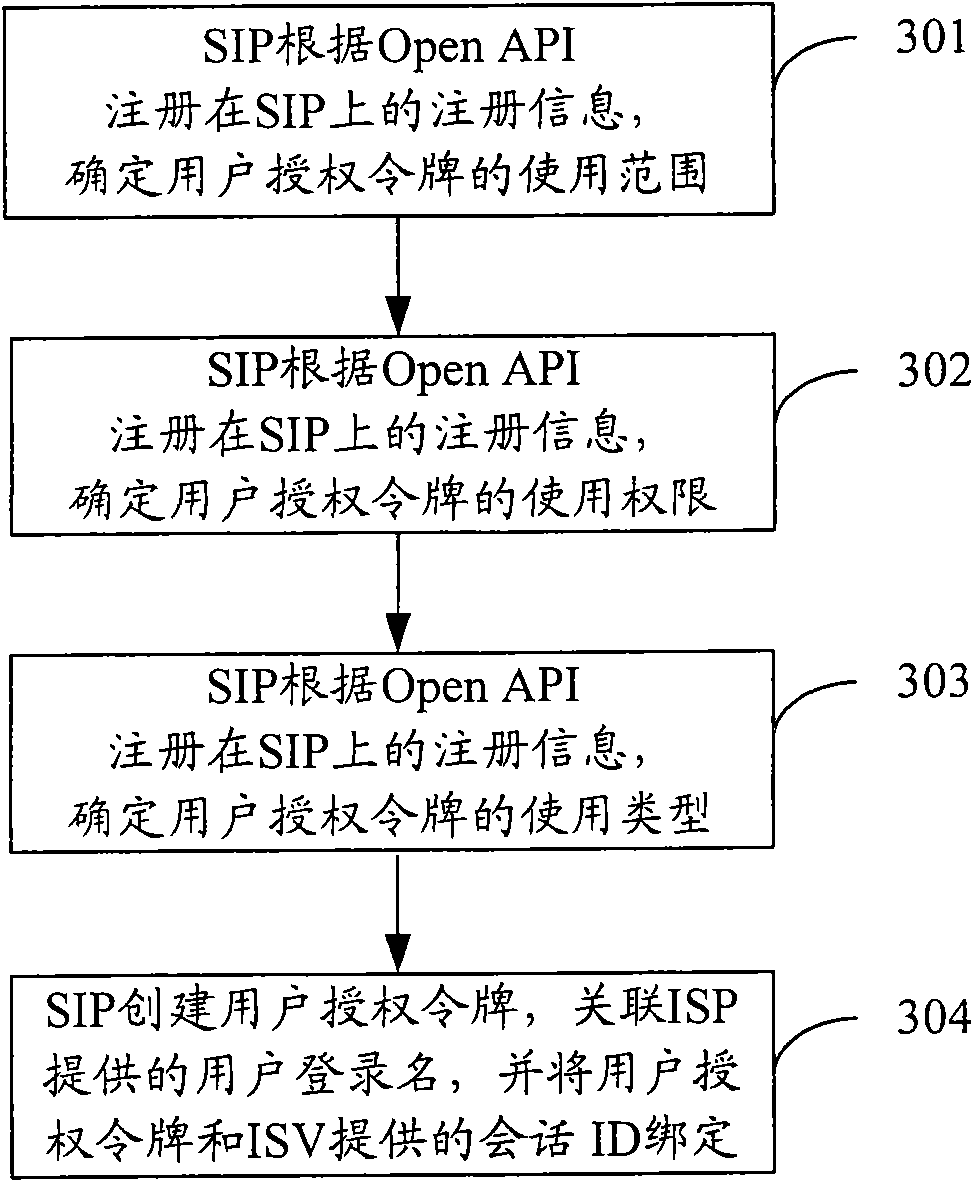
ActiveCN101562621AImprove securityFix service inefficienciesUser identity/authority verificationApplication programming interfaceIntegration platform
The invention discloses a user authorization method and a system and a device thereof, which are applied to a network consisting of a service integration platform (SIP), an Internet service provider (ISP) and an independent software vendor (ISV) application. The ISP provides different open application programming interfaces (Open API); the method comprises the following steps: the SIP creates a user authorization token according to the registration information of the Open API called by the ISV application when the ISP authorizes user identity; the SIP processes a call request for the Open APIby the ISV application according to the user authorization token. The invention refines the application range, the use type and the use right of the user authorization token, supports the mode of asynchronous user authorization, improves the safety of the system and solves the problem of low service efficiency due to data relay during service request of large data.
Owner:ALIBABA GRP HLDG LTD
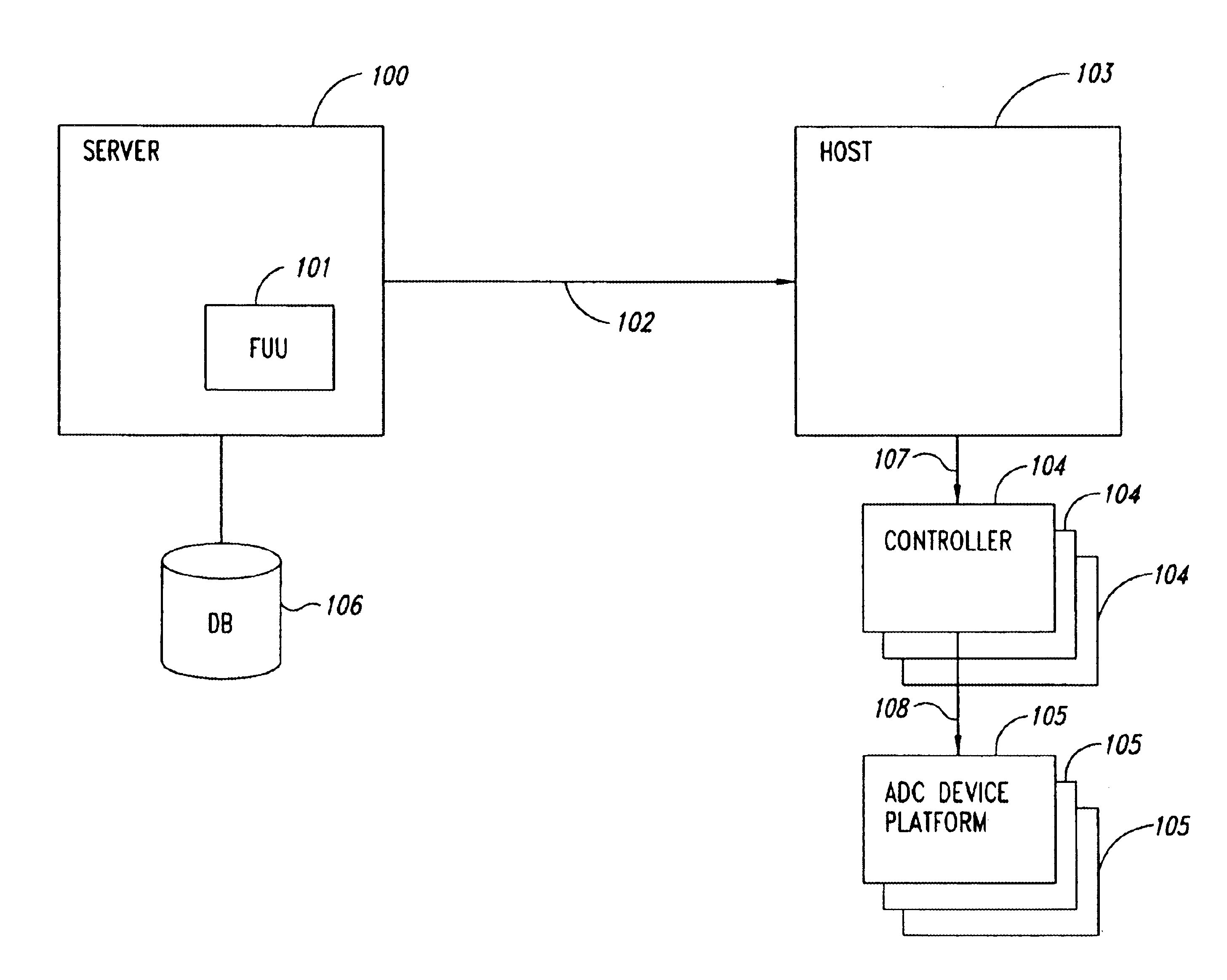
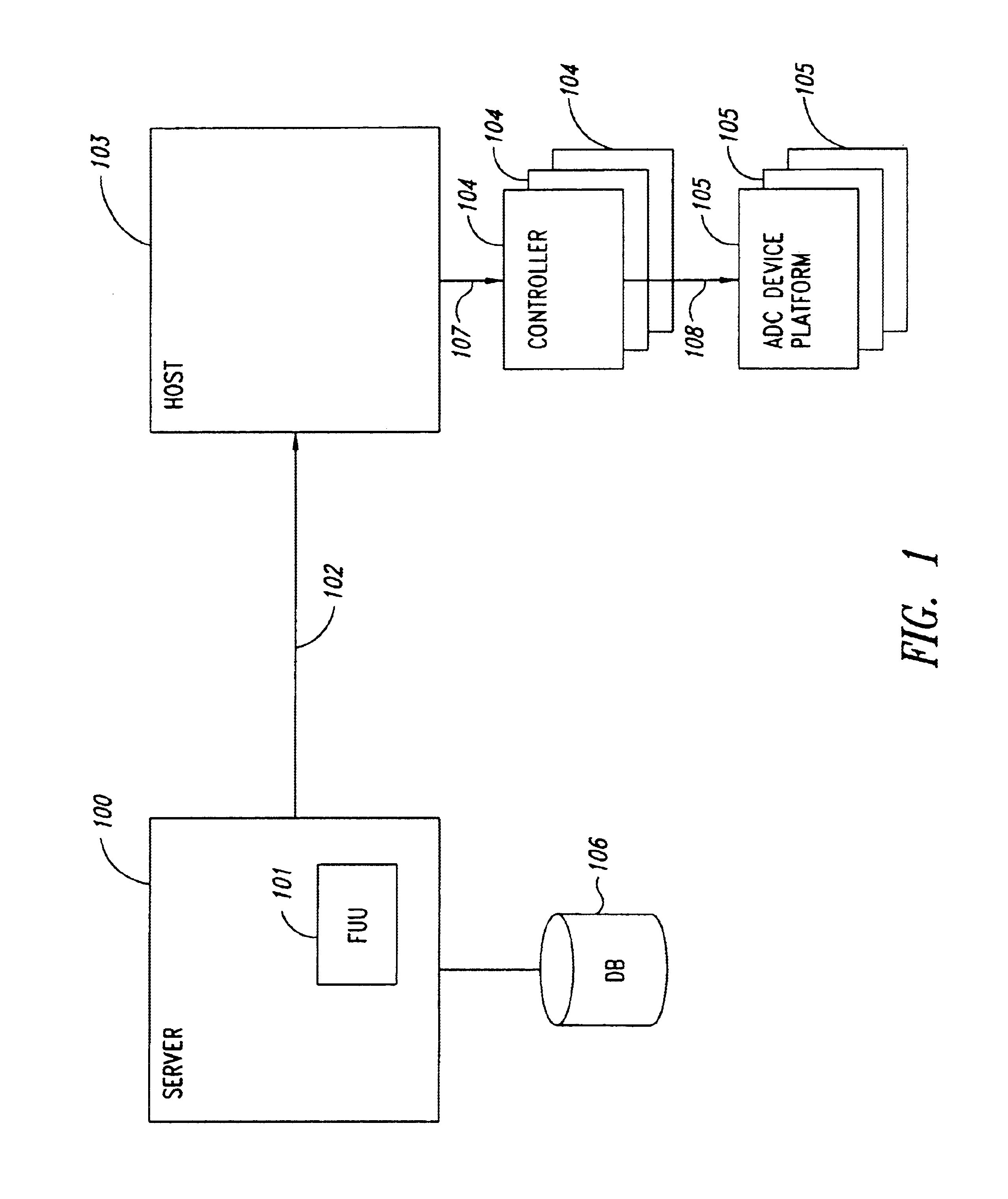
Automated software upgrade utility
InactiveUS20050257215A1Digital computer detailsProgram loading/initiatingProduct typeOperational system
The automated software upgrade utility allows a customer, product supplier or software vendor to upgrade the operating system, firmware, applications and data files on any product regardless of the product type and characteristics. This upgrade process can be invoked from a remote location or via interaction directly with the target device.
Owner:INTERMEC IP
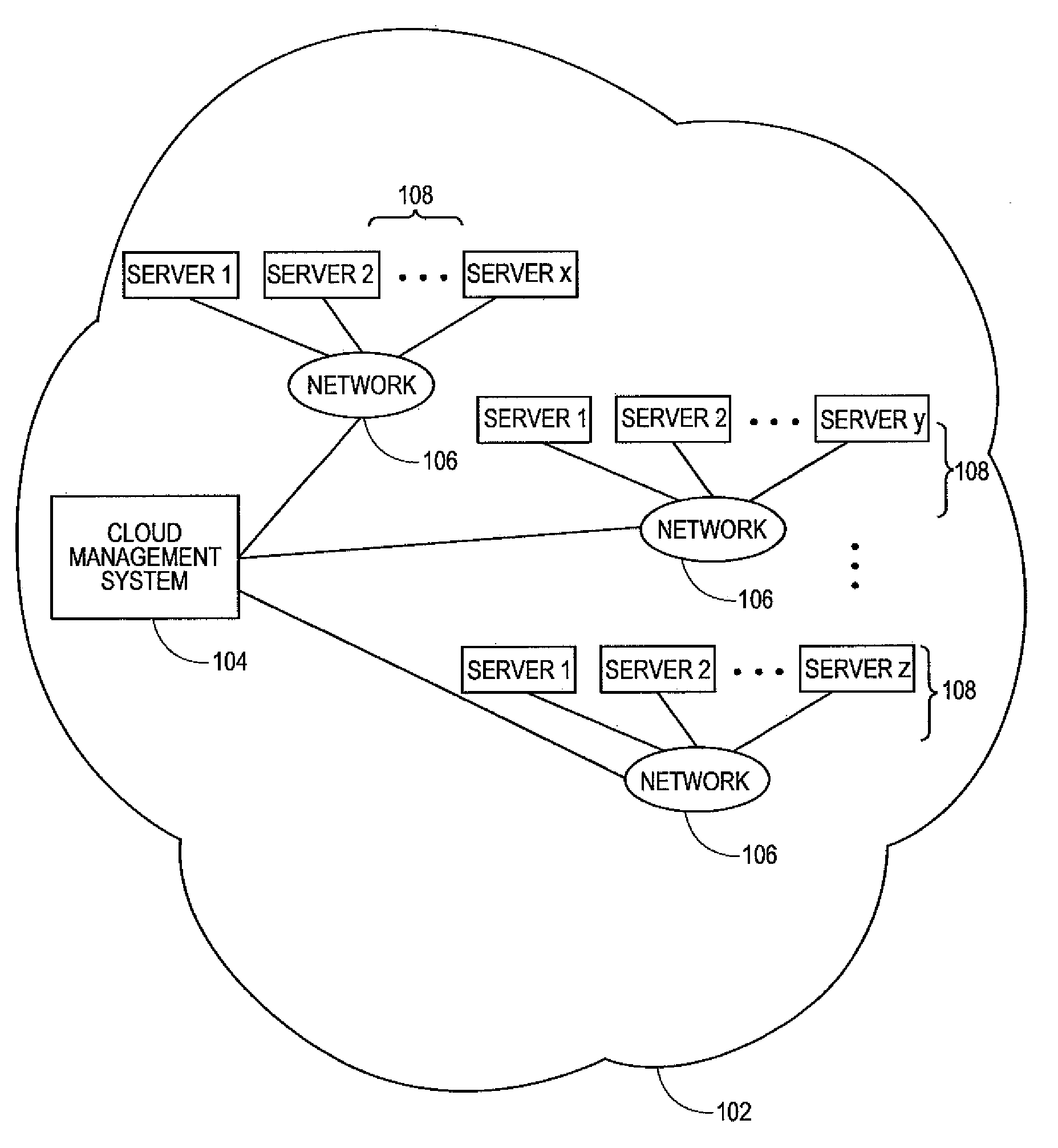
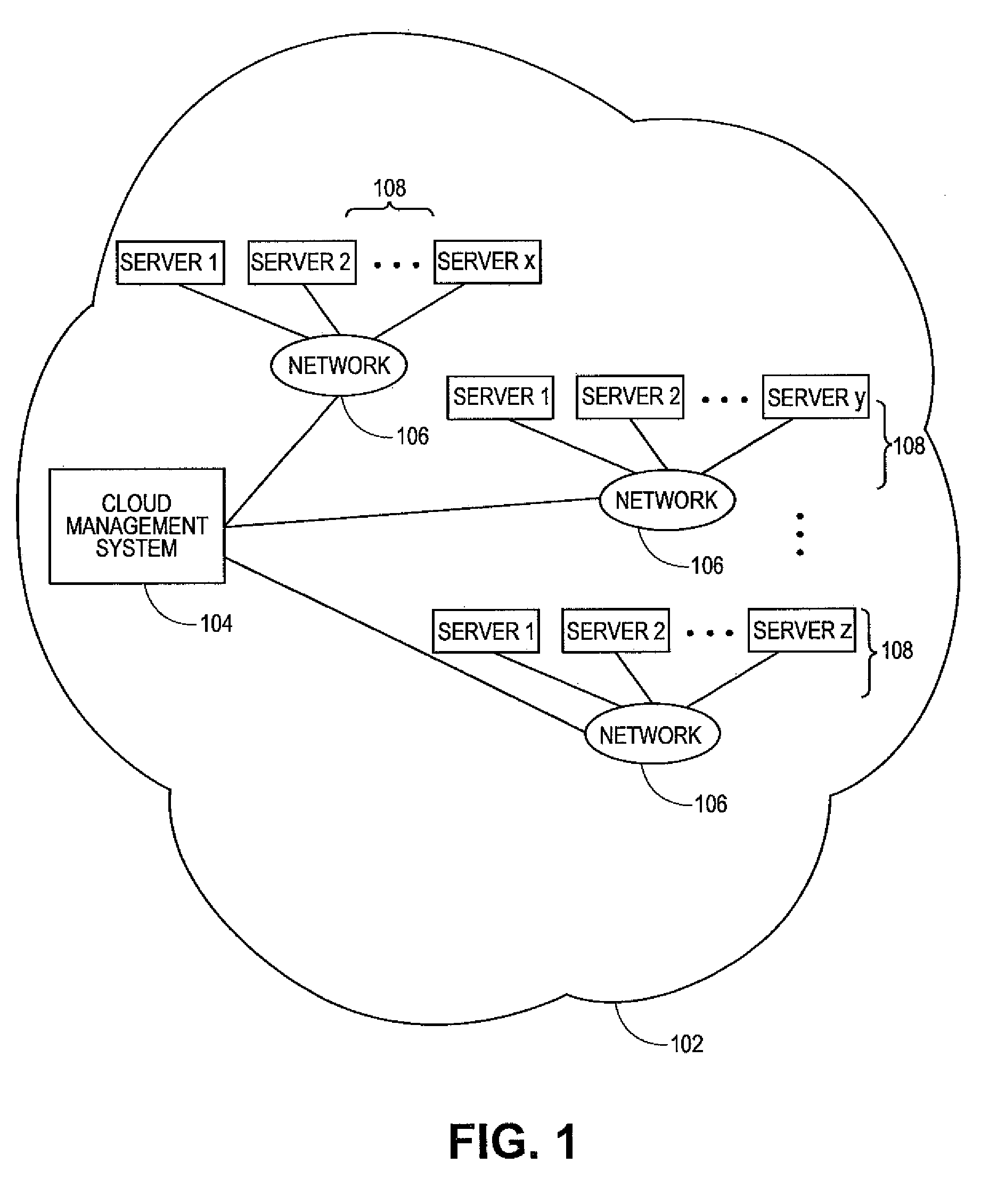
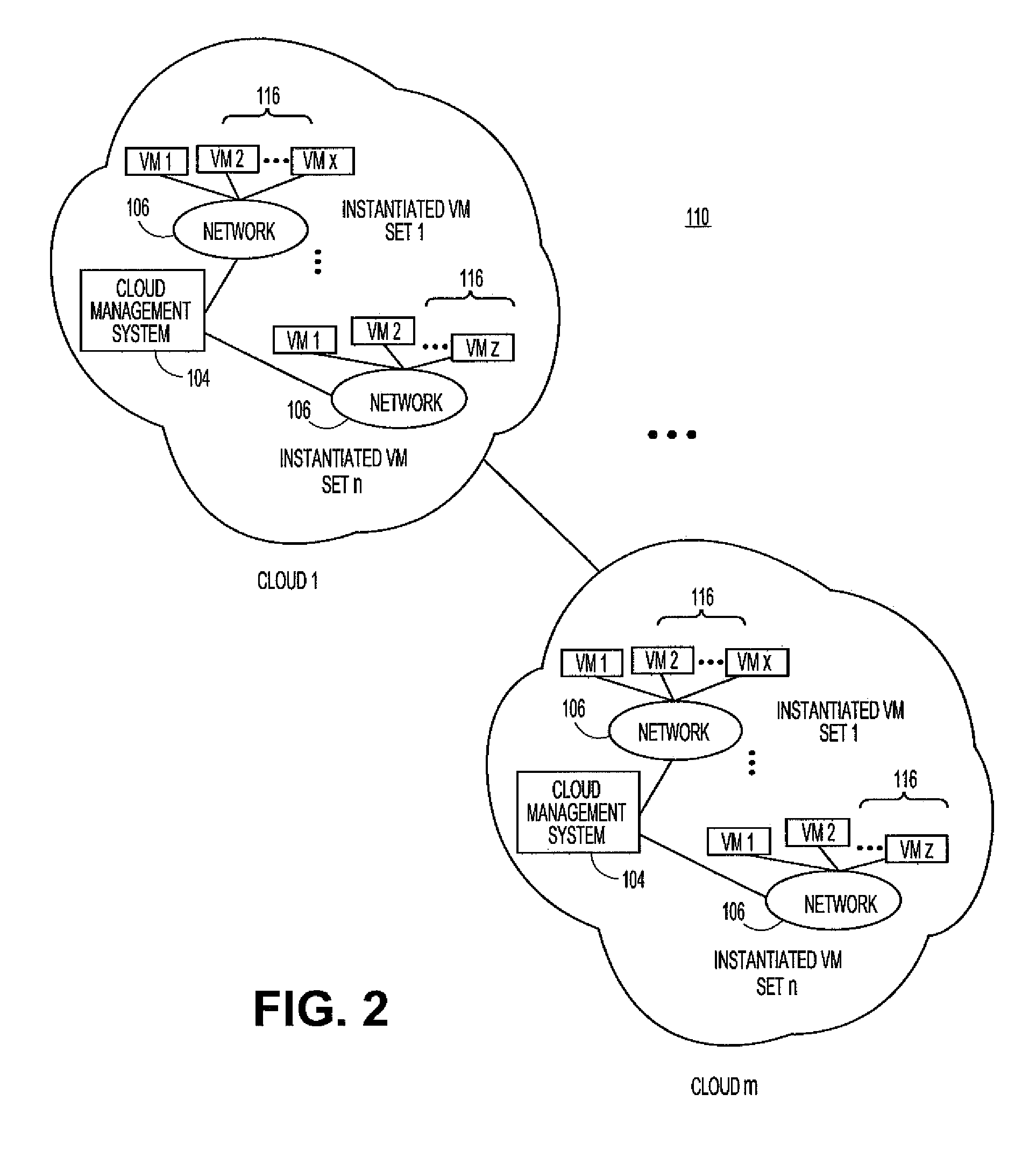
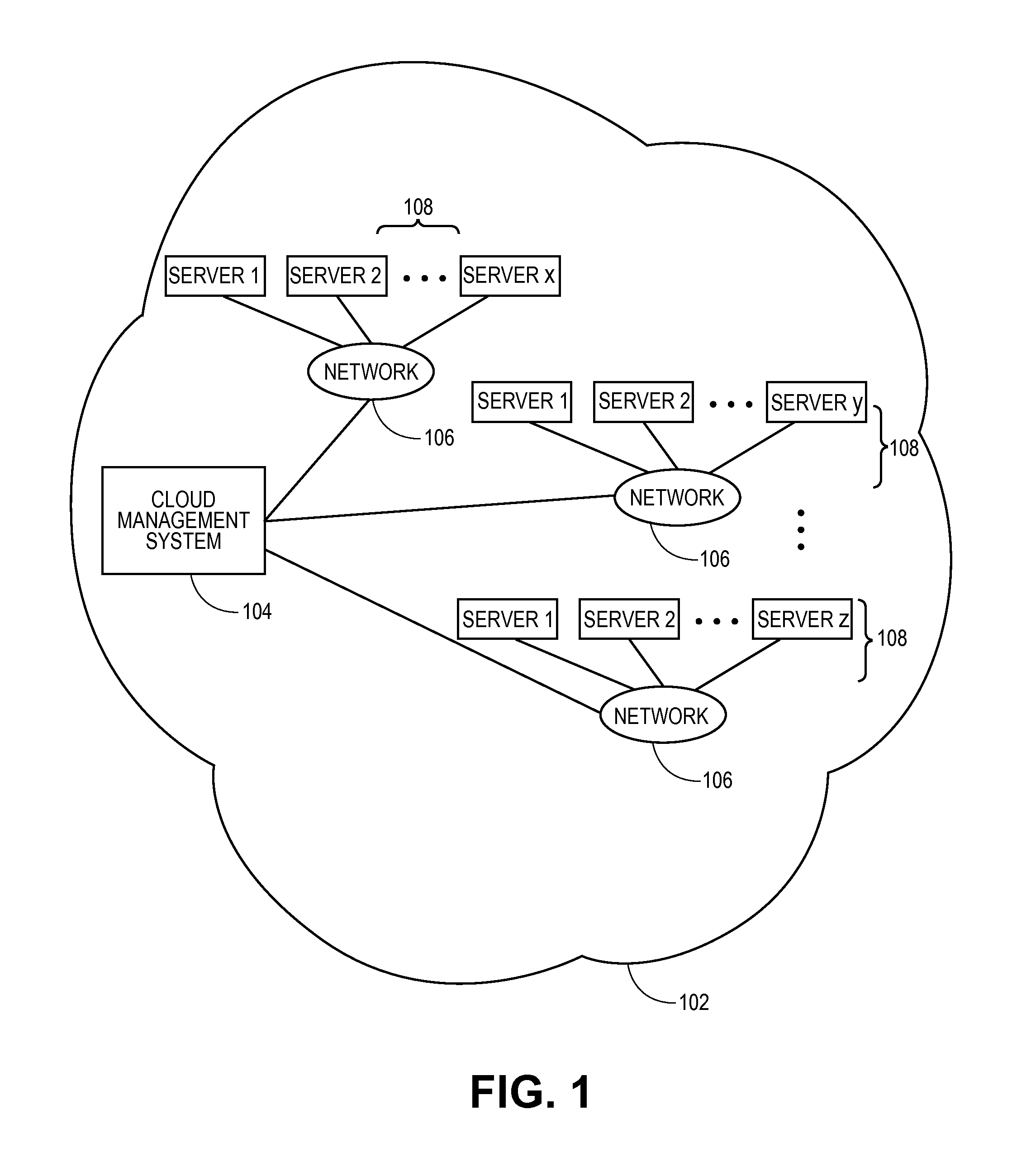
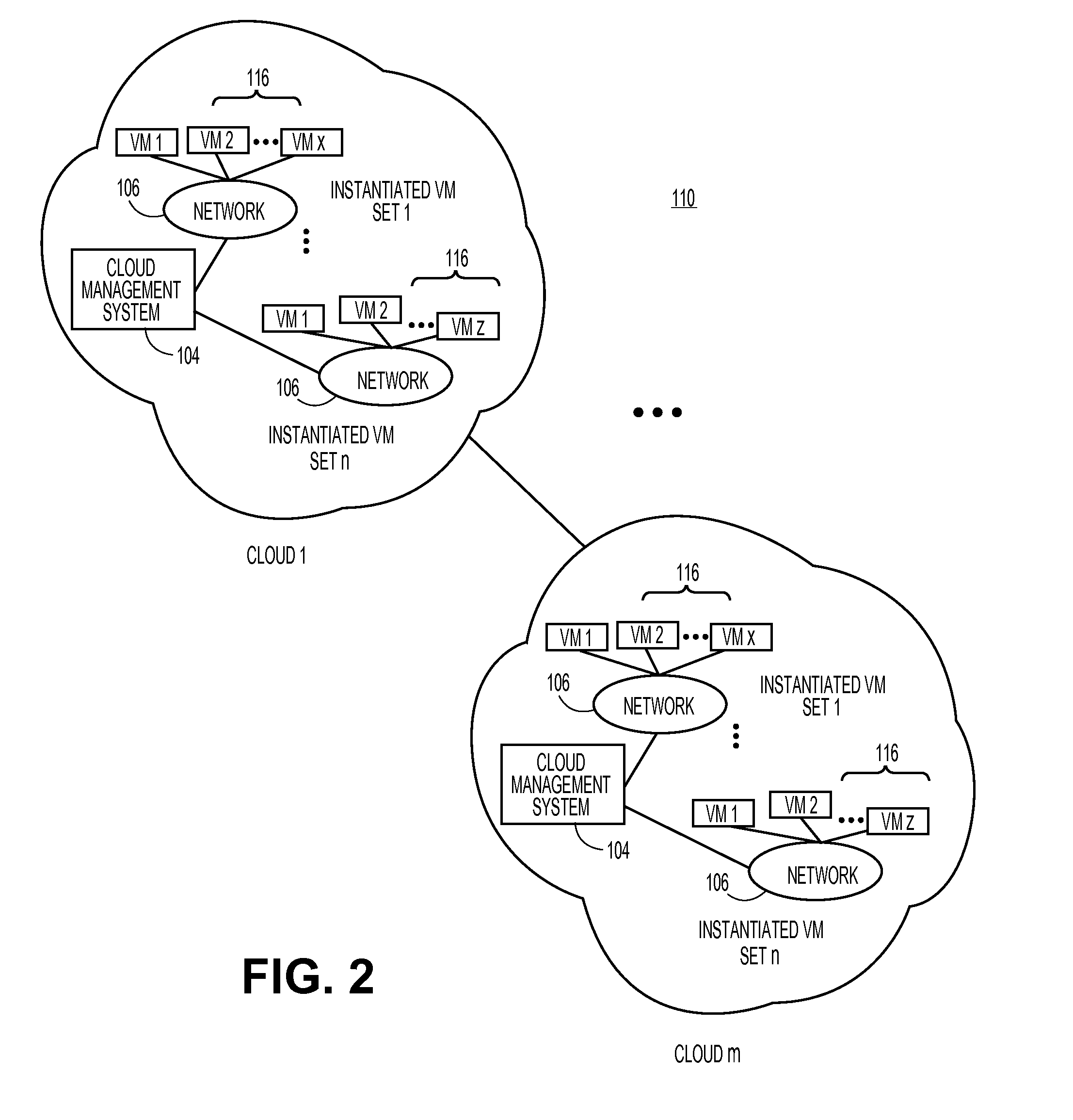
Systems and methods for service aggregation using graduated service levels in a cloud network
Embodiments relate to systems and methods for service aggregation using graduated service levels in a cloud network. In embodiments, a service aggregation platform can encode a service delivery profile to manage the delivery of support services to both vendors, such as independent software vendors (ISVs), and their users in a cloud-based network or networks. Vendors may choose to host their technical support and related services in the service aggregation platform, and define a graduated set of levels of service to which their customers, subscribers, and / or other users may be registered or entitled Users of virtual machines hosted in the one or more cloud can receive technical support, help desk, updating, and / or other support directly from the service aggregation platform, or indirectly through the vendor. The aggregation platform can serve as a trusted portal for delivery of software certification, dependency testing, issue resolution, and / or other degrees or types of support.
Owner:RED HAT
System and method for generating selectable extension to media transport protocol
InactiveUS7555554B2Special service provision for substationMultiple digital computer combinationsTransmission protocolExtension set
A protocol and related techniques and platforms allow vendors to selectably extend the Media Transport Protocol (MTP), or other defined protocols to implement vendor-specific commands, data fields, instructions and other extension sets. According to embodiments of the invention in one regard, one or more extension space may be utilized to derive independent extension sets, in part by separating the extension space according to a unique identifier assigned to or associated with a given vendor. In embodiments that unique identifier may be or include an Internet DNS (Domain Name System) domain name, or other extension set name or identifier. According to the invention in one regard, because a DNS domain name may be independently registered and secured by participating vendors or manufacturers and by definition uniquely assigned, the separation of vendor extension sets by that type of name may be automatic and free from conflict. Vendors or manufacturers, such as makers of digital cameras, digital video cameras, audio players such as MP3 or other players, software vendors or others may therefore freely design extensions to the Media Transport Protocol or other protocols, without a need to clear those extensions with a standards body and with confidence that their commands, data fields and other extensions may be free from overlap with that of other manufacturers.
Owner:MICROSOFT TECH LICENSING LLC
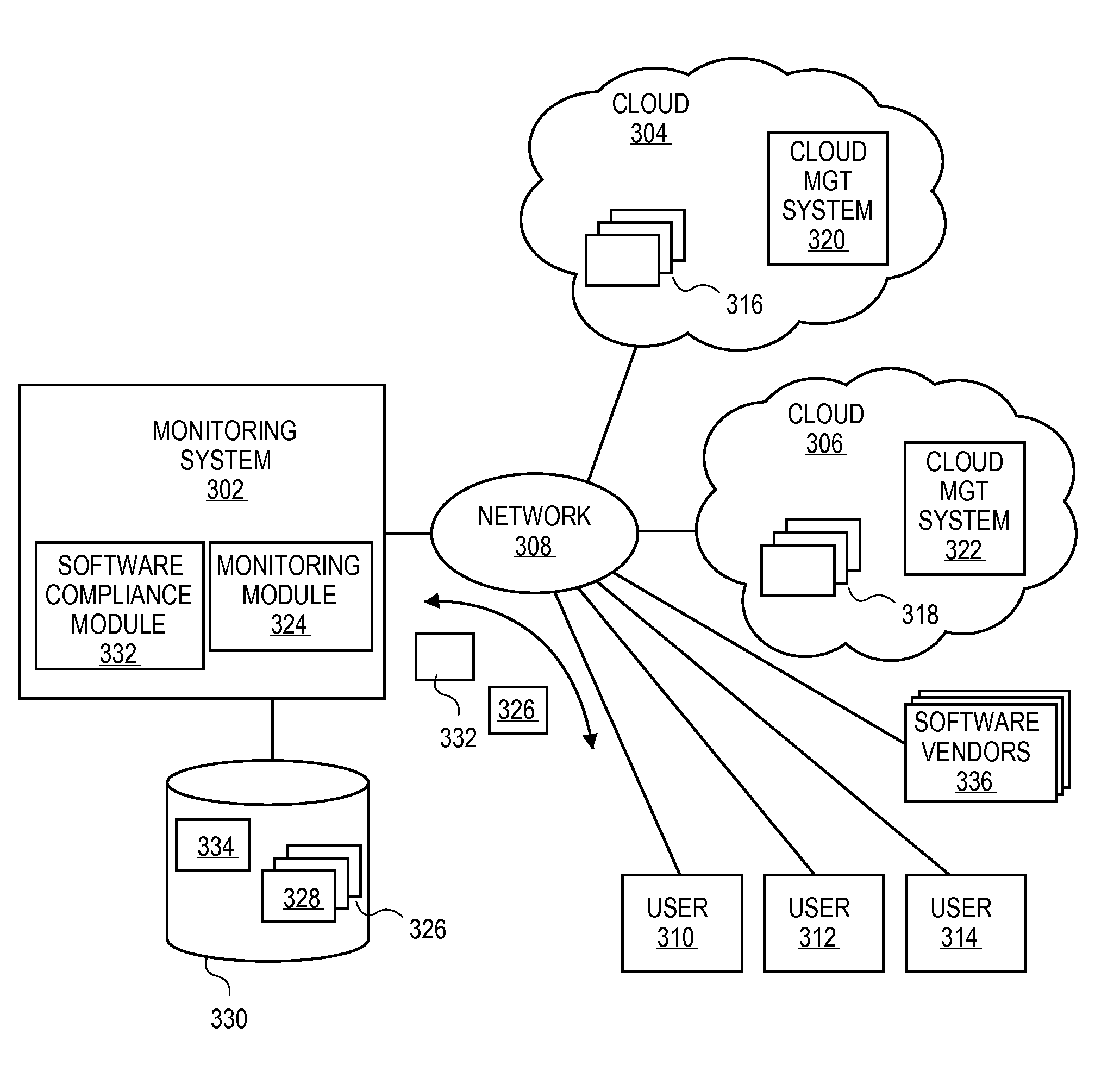
Methods and systems for generating a software license knowledge base for verifying software license compliance in cloud computing environments
A monitoring system can monitor computing processes in clouds. The monitoring system can verify software license compliance in the computing processes instantiated in the clouds. The monitoring system can generate and maintain a software license knowledge base. The software license knowledge base can include the software license requirements for various software programs. To generate the software license knowledge base, the monitoring system can communicate with various sources (software vendors, clouds, publicly available sources, etc.) to determine license requirements for the various software programs.
Owner:RED HAT
Method and system for sharing and networking in learning systems
Online course and learning material management system and methods are provided where students, instructors, publishers, administrators, publishers, software vendors, and industry partners utilize the disclosed systems' databases and networking features to interact, to network, to improve learning outcome, and to exchange information elements. The system furthermore allows for networking among different user categories based on users' roles, professional profiles, and professional interests.
Owner:DELART TECH SERVICES
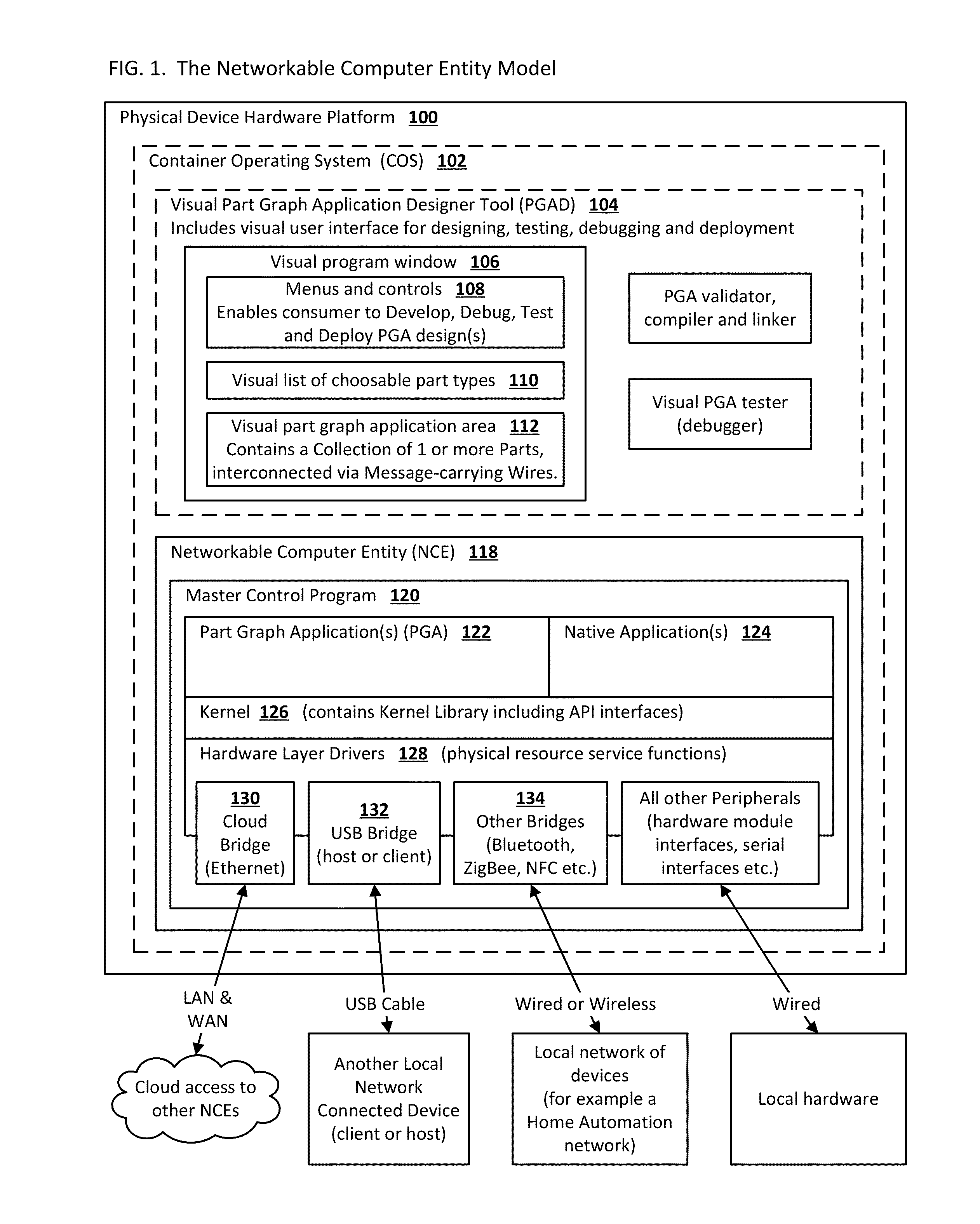
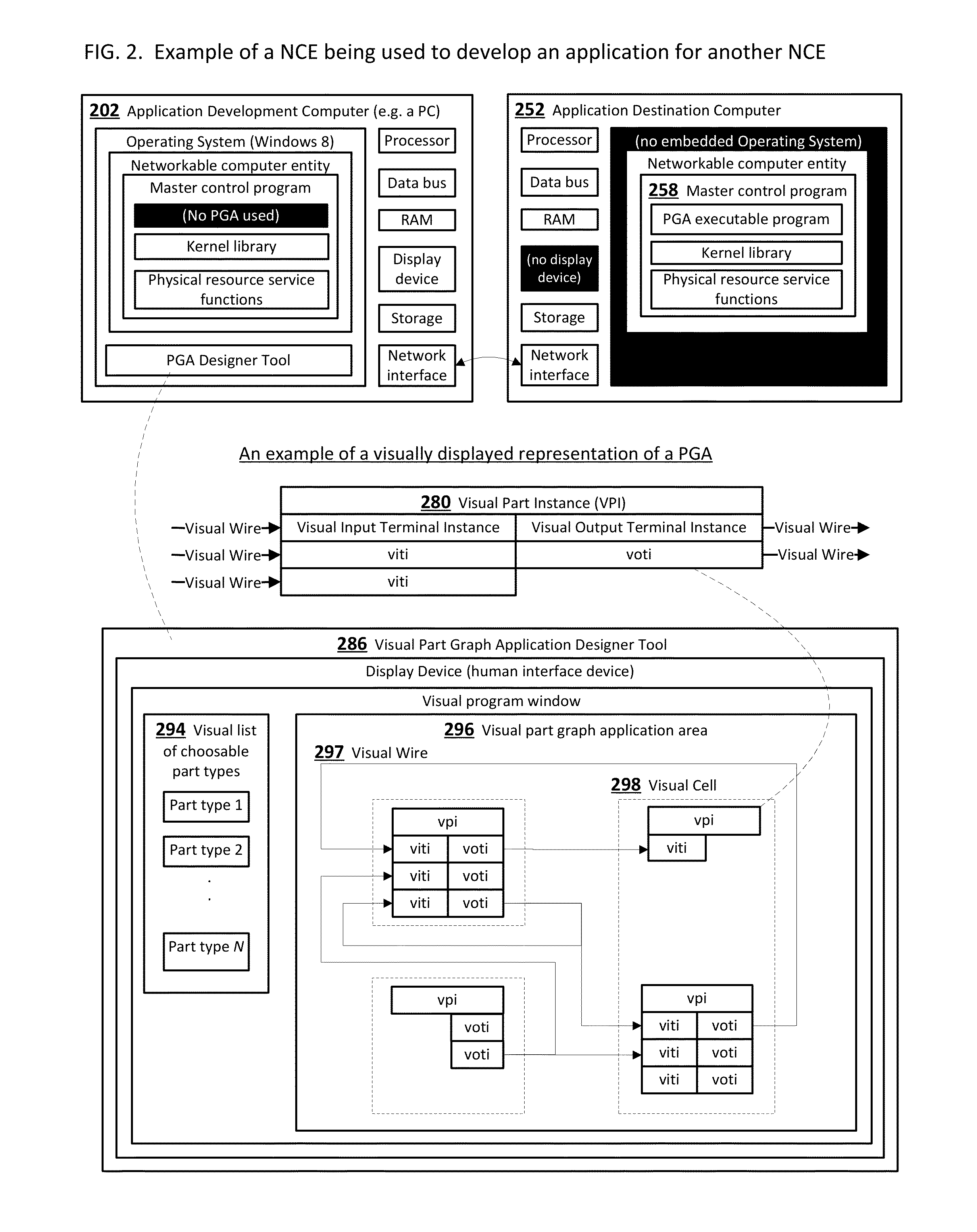
System and methods for end-users to graphically program and manage computers and devices
InactiveUS20140359558A1Reduce needReduce testingSoftware designVisual/graphical programmingInformation processingGraphics
A system that enables end-users who are not skilled in the art of traditional computer programming to intuitively program, configure and manage computers and devices and / or systems that contain many computers and devices. End-users connect graphical parts using graphical wires using a graphical user interface. The timing of the messages that are carried in the wires that connect the parts is deterministic, consistent and intuitive to the end-user. Parts and their user-configurable features are typically designed, fully tested and certified by the original equipment manufacturer or independent software vendor. This invention relates to ubiquitous computing, a model of human-computer interaction in which information processing has been thoroughly integrated into everyday objects and activities associated with those objects.
Owner:CHAMBERLAIN MARK SPENCER
Method and system for exchanging data between computer systems and auxiliary displays
ActiveUS20060130075A1Improve abilitiesIncrease profitMultiprogramming arrangementsCathode-ray tube indicatorsDigital picturesSoftware vendor
Described is a system and method by which application programs running on a main computer system communicate with an auxiliary display device (such as a cell phone, pocket-sized computer, alarm clock, television, digital picture frame and so forth) to provide viewable information on the device, remote control capabilities, and notifications. Via API calls, programs provide information in the same format regardless of the device capabilities and / or the connection type. An auxiliary display platform converts the information into a format understood by a device driver, which then filters the information as desired for its particular hardware device before the information is communicated. Return communications return data such as status and user interaction with the displayed information. Software vendors may thus write code once to output information on auxiliary displays, while hardware manufacturers can have their devices work as auxiliary displays, with little or no modification to existing hardware.
Owner:MICROSOFT TECH LICENSING LLC
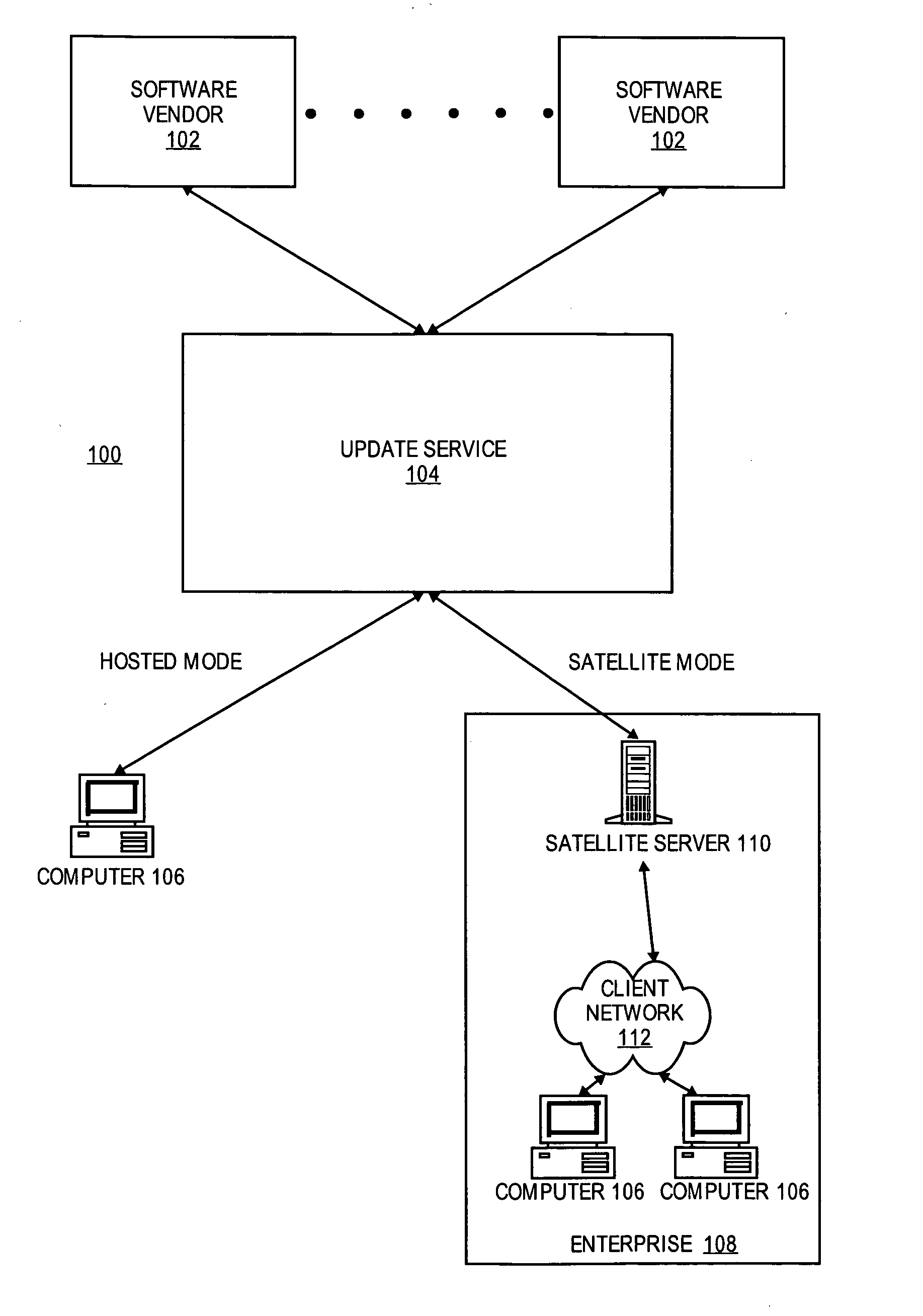
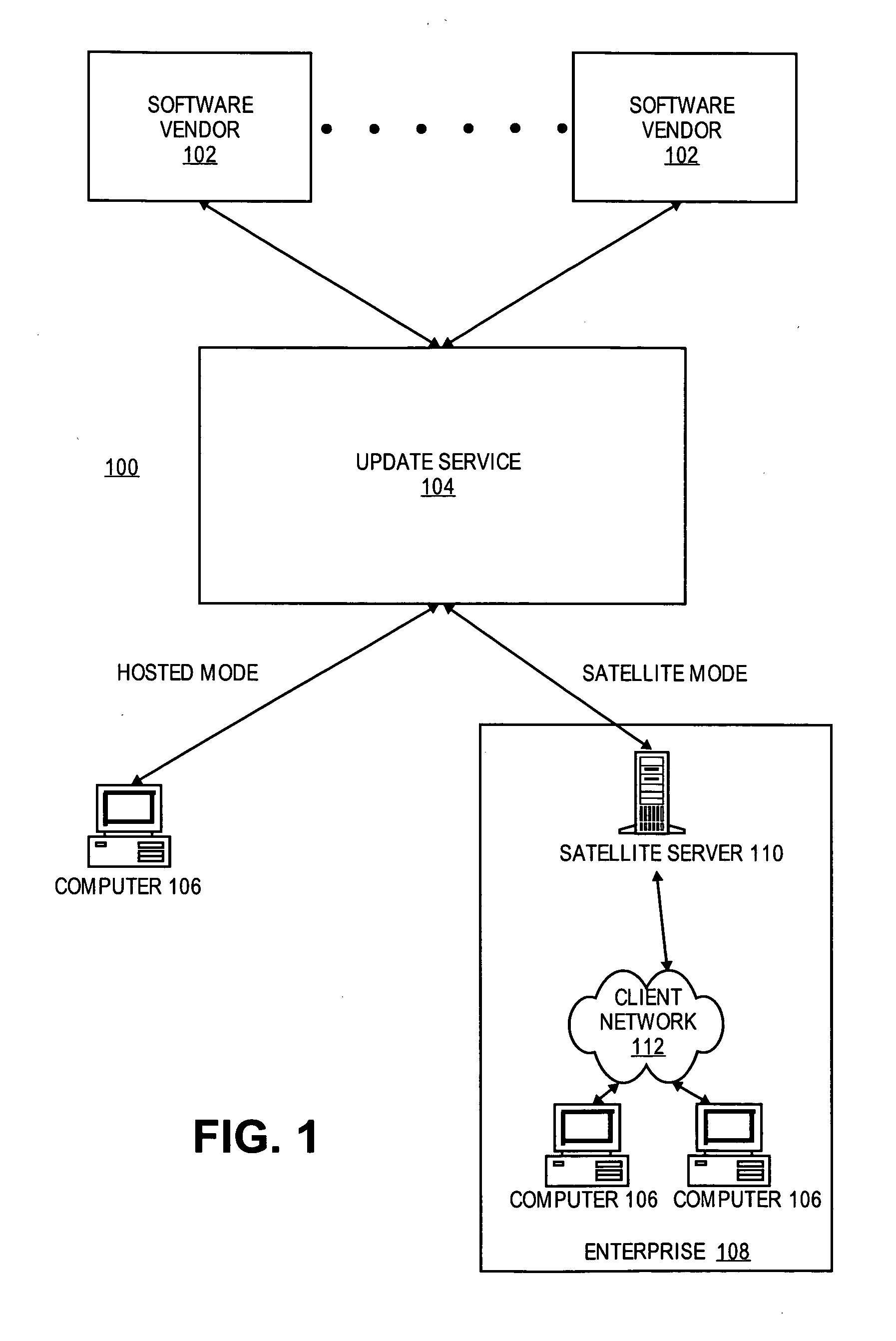
Software certification and update process
ActiveUS20060184927A1Platform integrity maintainanceSpecific program execution arrangementsSoftware updateSoftware vendor
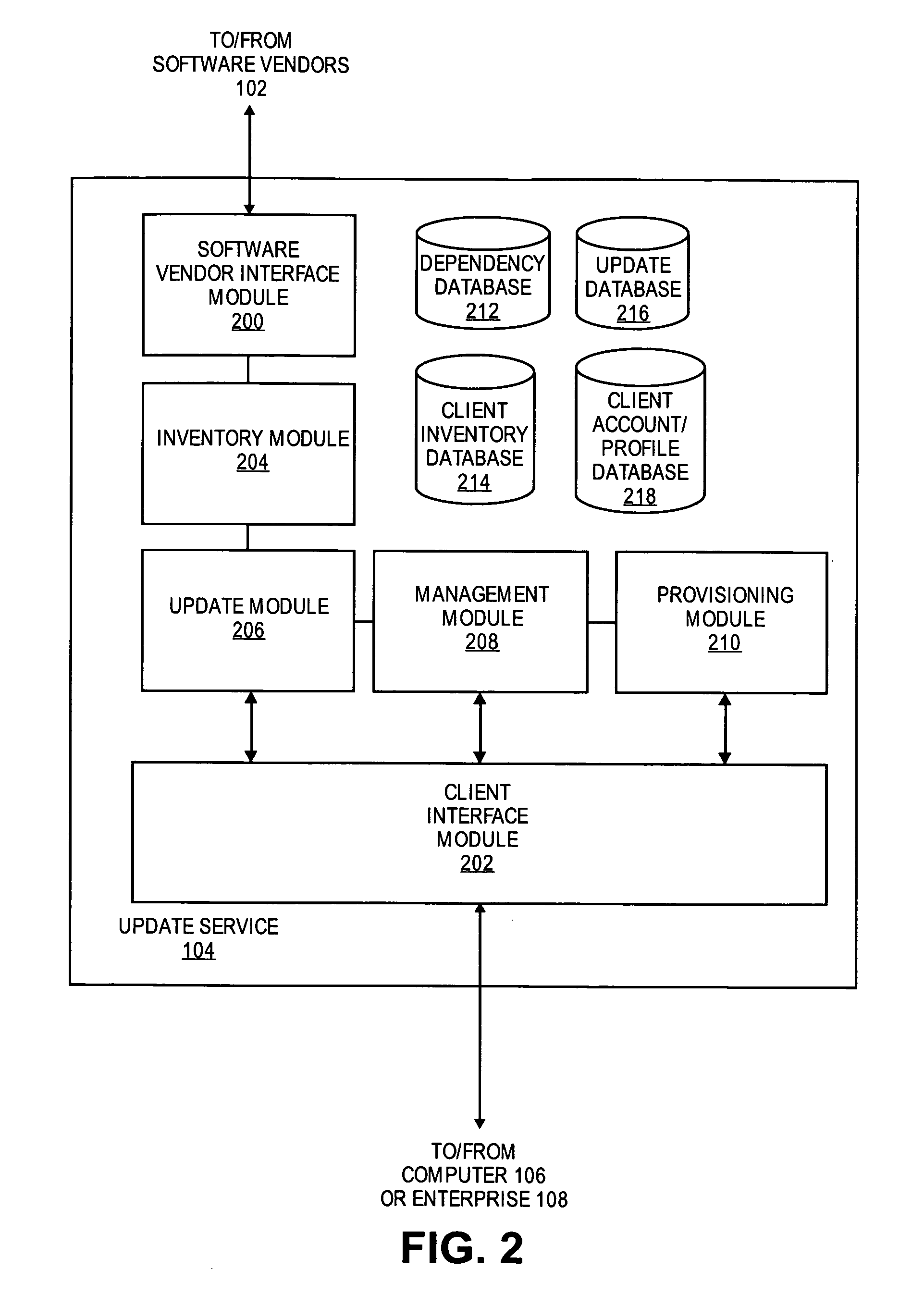
An update service is provided for maintaining software of one or more users, or an enterprise. On behalf of users or enterprises, the update service collects information from various software vendors about the certification and updates for their software. Dependencies or issues between the software are determined based on the information collected from the software vendors. A set of applicable updates for particular users or enterprises may then be determined based on the dependencies or issues. The update service may then broker various aspects of the delivery and installation of these updates.
Owner:RED HAT
System for automated problem detection, diagnosis, and resolution in a software driven system
InactiveUS7100085B2Simple interfaceEffortless and reliable and affordable supportFault responseDetecting faulty hardware by remote testInstabilityTheoretical computer science
In many systems, computer software is a common source of failure or instability. The proliferation of multiple interacting applications from several different software vendors leads to “emergent” problems that are difficult or impossible to predict or prevent. The problems are compounded by the use of networks, which introduce the added complexity of applications on multiple machines interacting in complex scenarios. As a result, many business and home users are hindered from using software-based systems to their fullest potential. More effective use of these systems can be aided by an application which can provide services for monitoring, diagnosing, and solving problems that occur in the operation of the machines at a customer facility. In the system described herein, a database contains entries with executable code that can make use of these services in order to monitor, diagnose, and solve specific problems. Each entry in the database addresses a specific problem. The executable code is designed to isolate and recognize the problem, and then implement a fix or workaround for that problem. The executable code is designed to completely automate the entire process of detection and resolution of the problem. Further, manual intervention may be employed to complete the diagnosis or solution.
Owner:HFN LLC
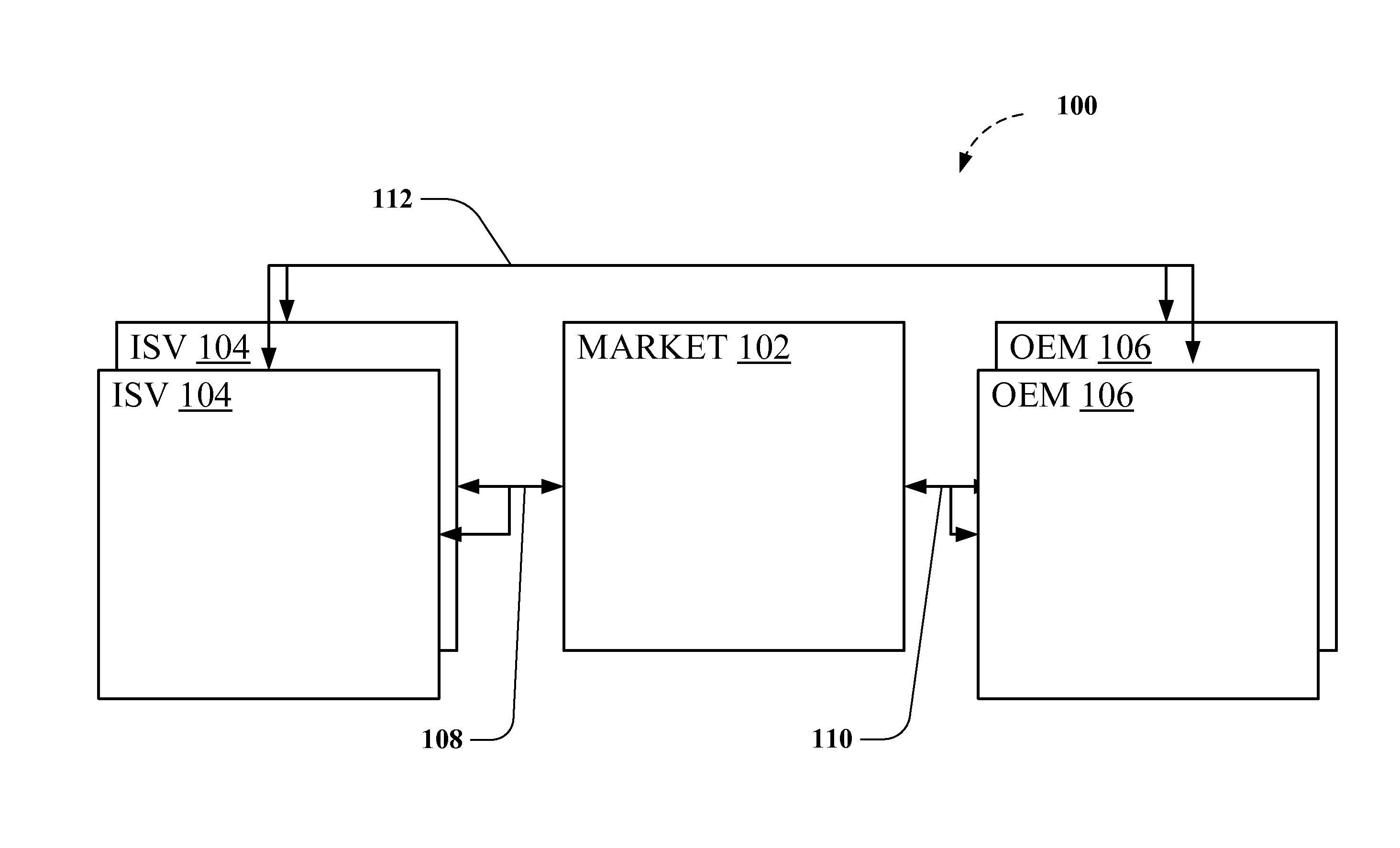
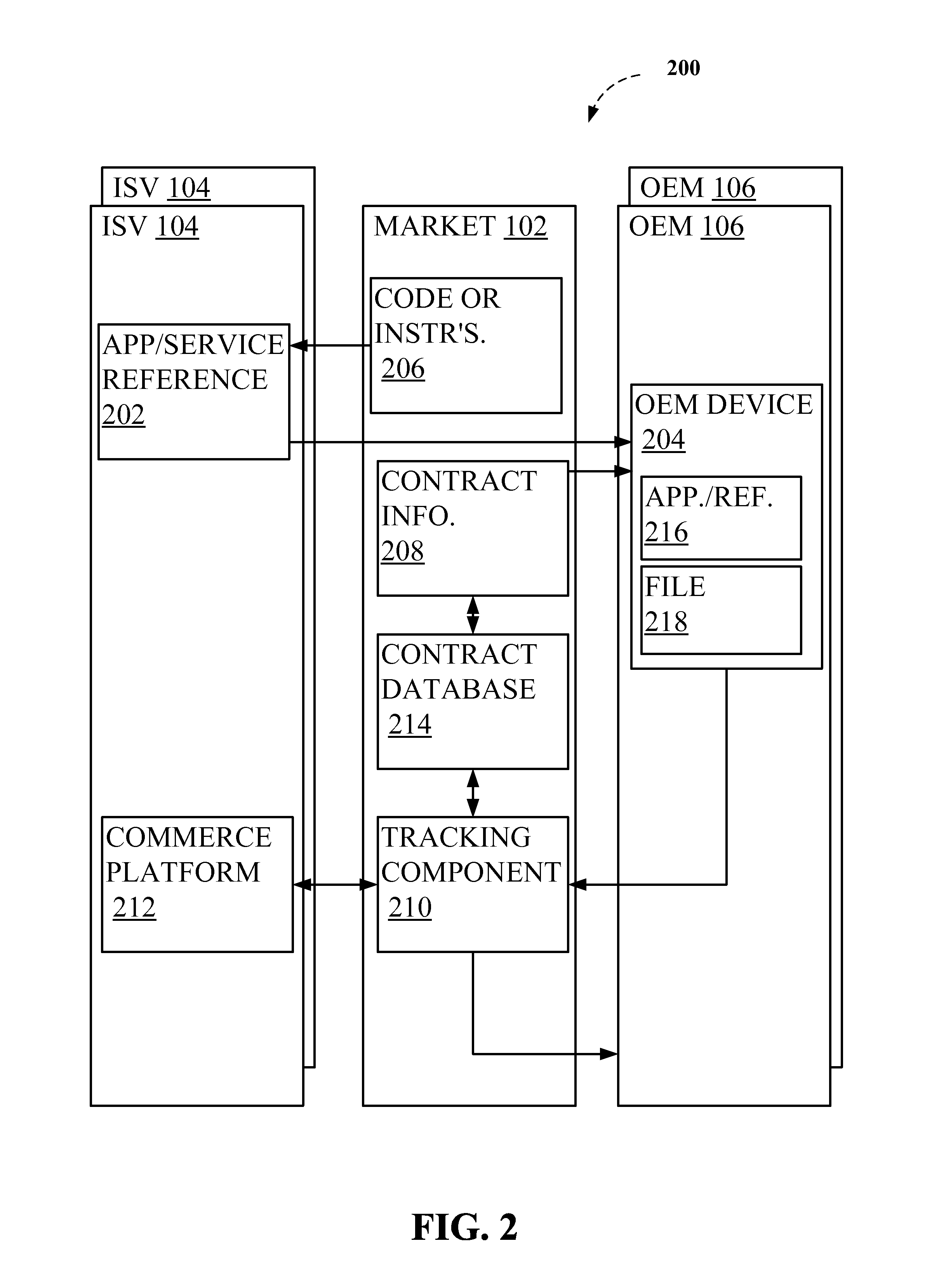
Online marketplace for pre-installed software and online services
ActiveUS20110296401A1Reduce facilitationProviding transparencyProgram loading/initiatingBuying/selling/leasing transactionsSubject matterDevice placement
The subject disclosure relates to pre-installed software and services, such as online services, and markets for pre-installed software and online services. In one aspect, the disclosed subject matter facilitates contracting between software vendors and device manufacturers or redistributors for placement and / or conversion of software applications or services in devices. As further advantages, embodiments of the disclosed subject matter can provide transparency into markets for device placement and can facilitate detailed contract performance tracking. Further non-limiting embodiments are provided that illustrate the advantages and flexibility of the disclosed subject matter.
Owner:SWEETLABS
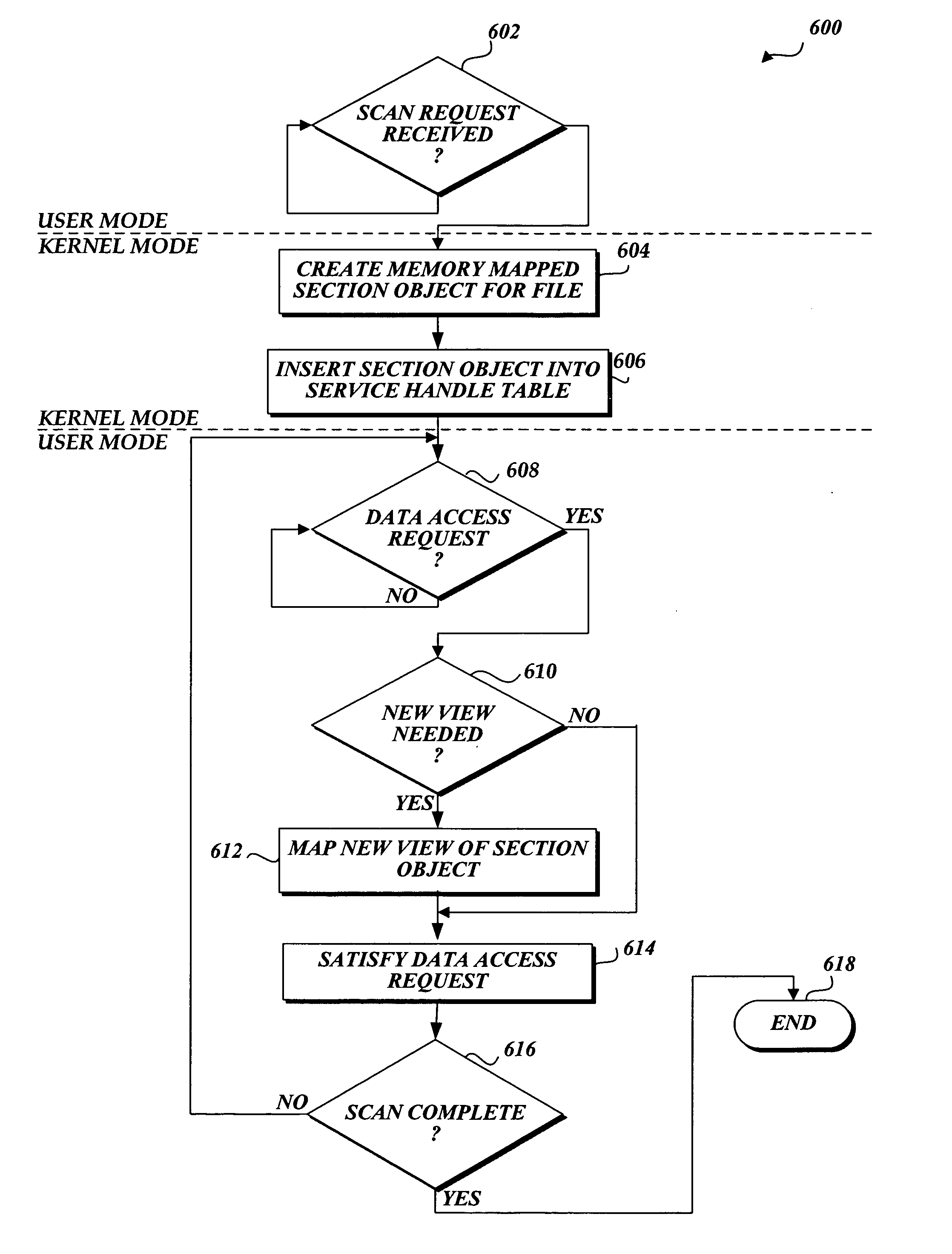
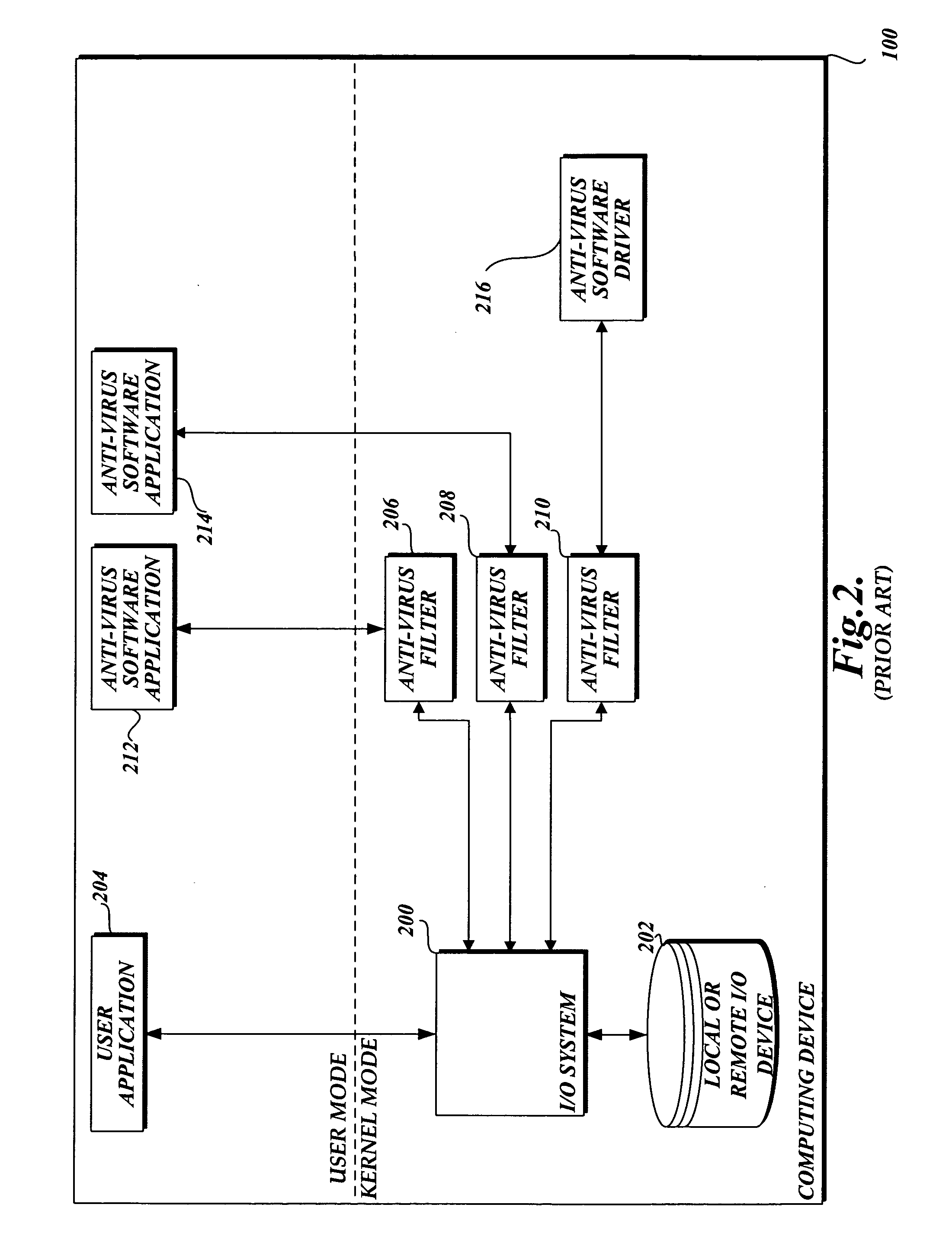
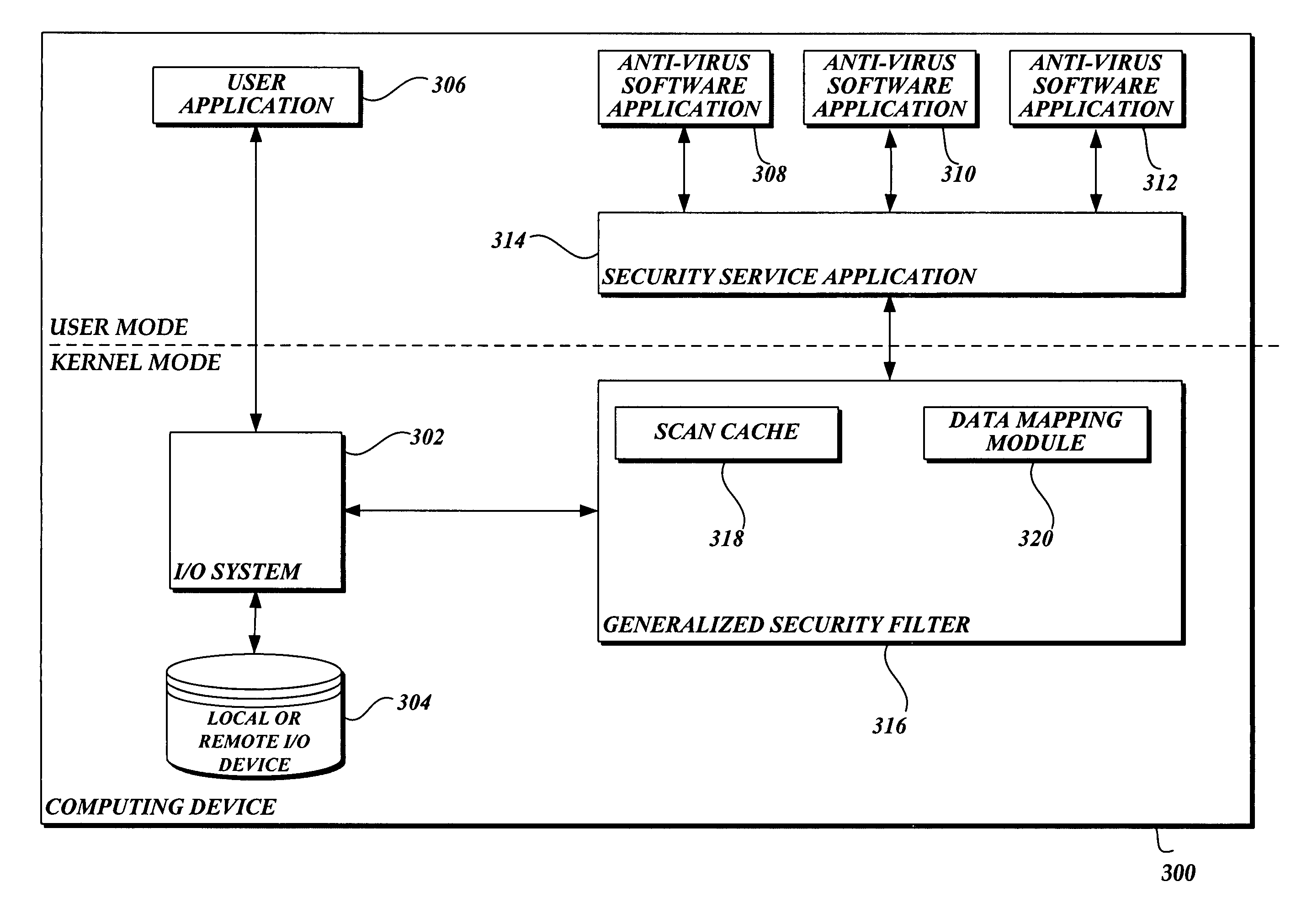
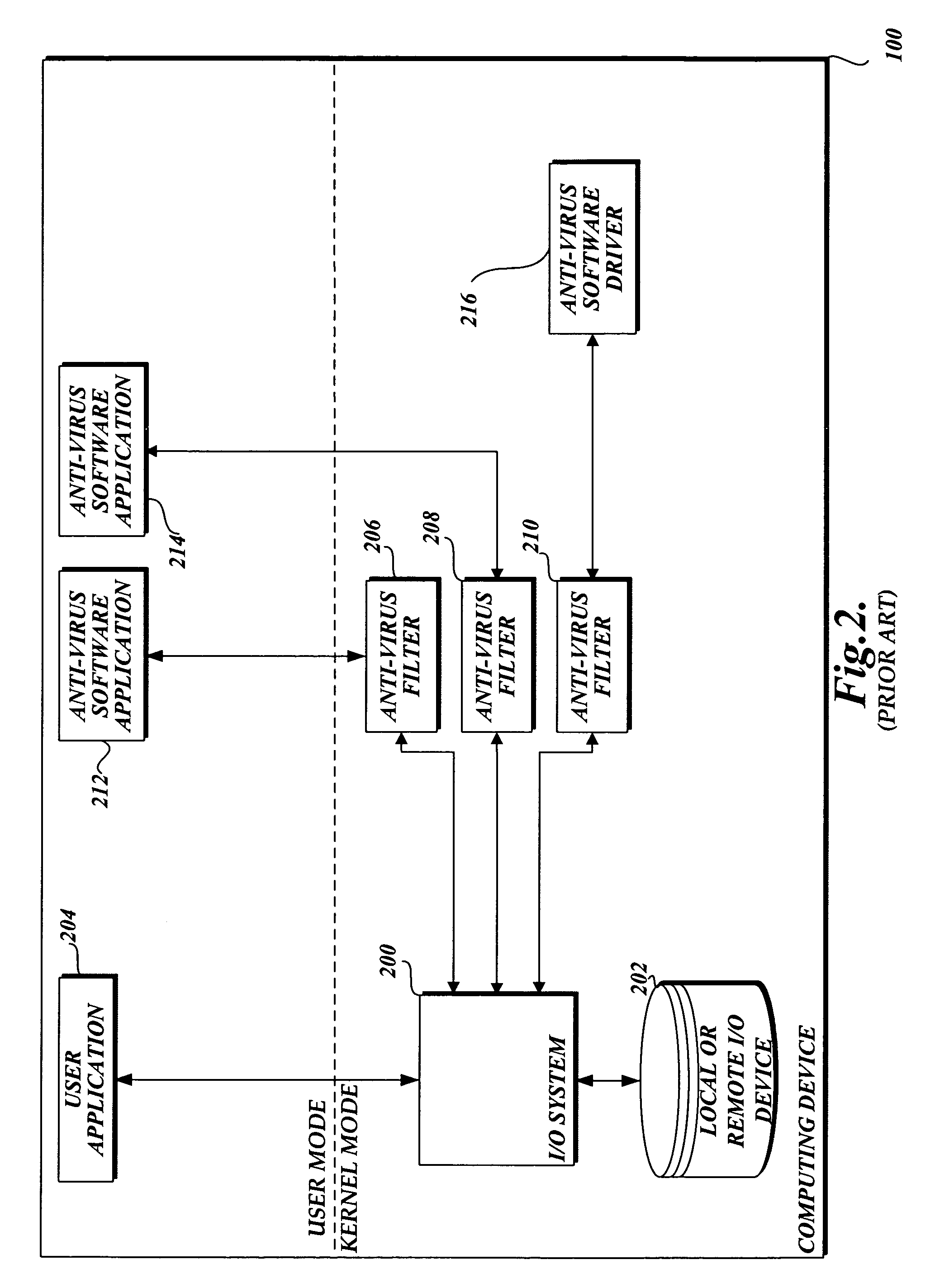
System and method of aggregating the knowledge base of antivirus software applications
InactiveUS20060101282A1Attempt have been hamperedIncrease speedMemory loss protectionDigital data processing detailsFile systemPublic information
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
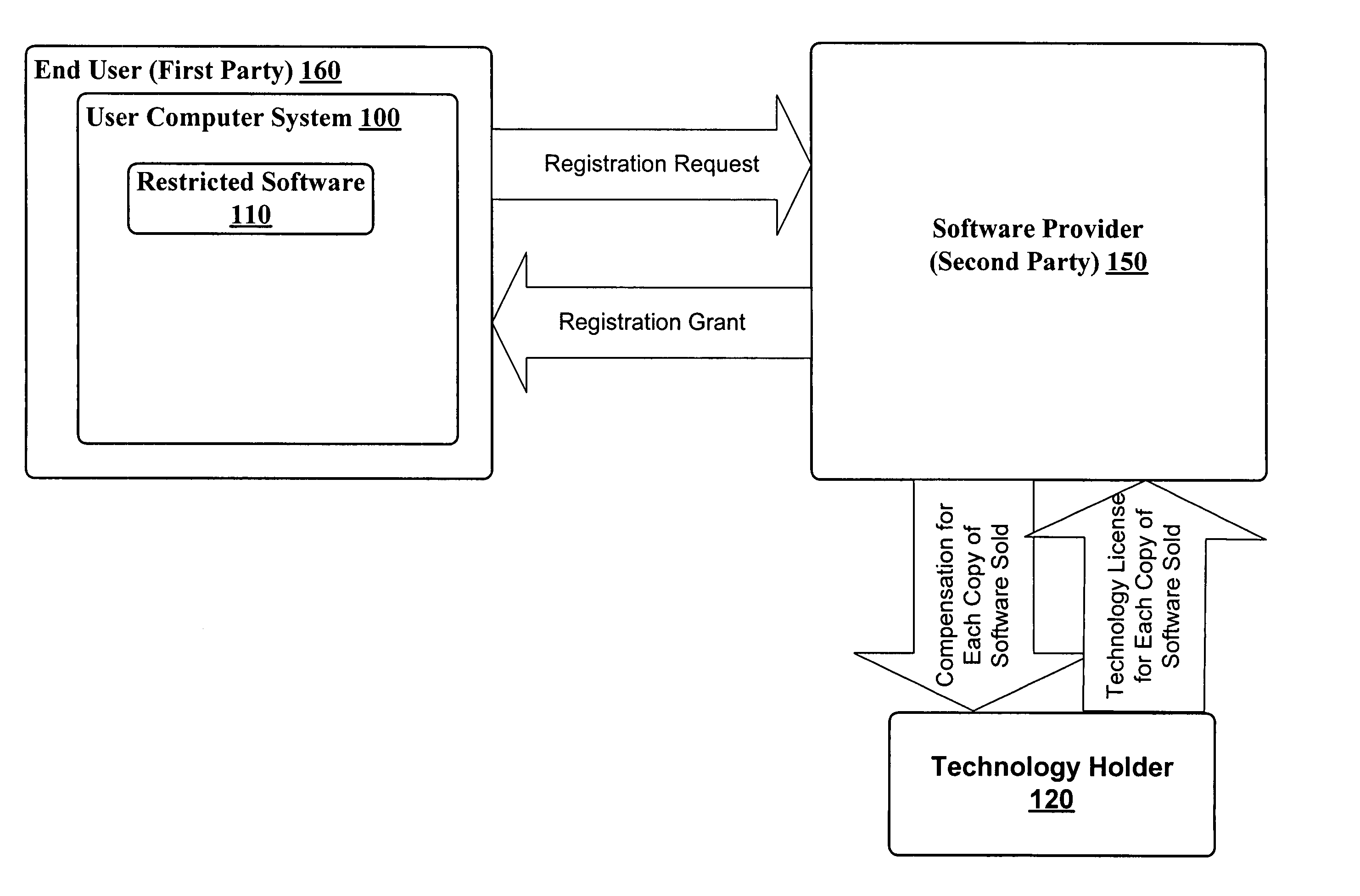
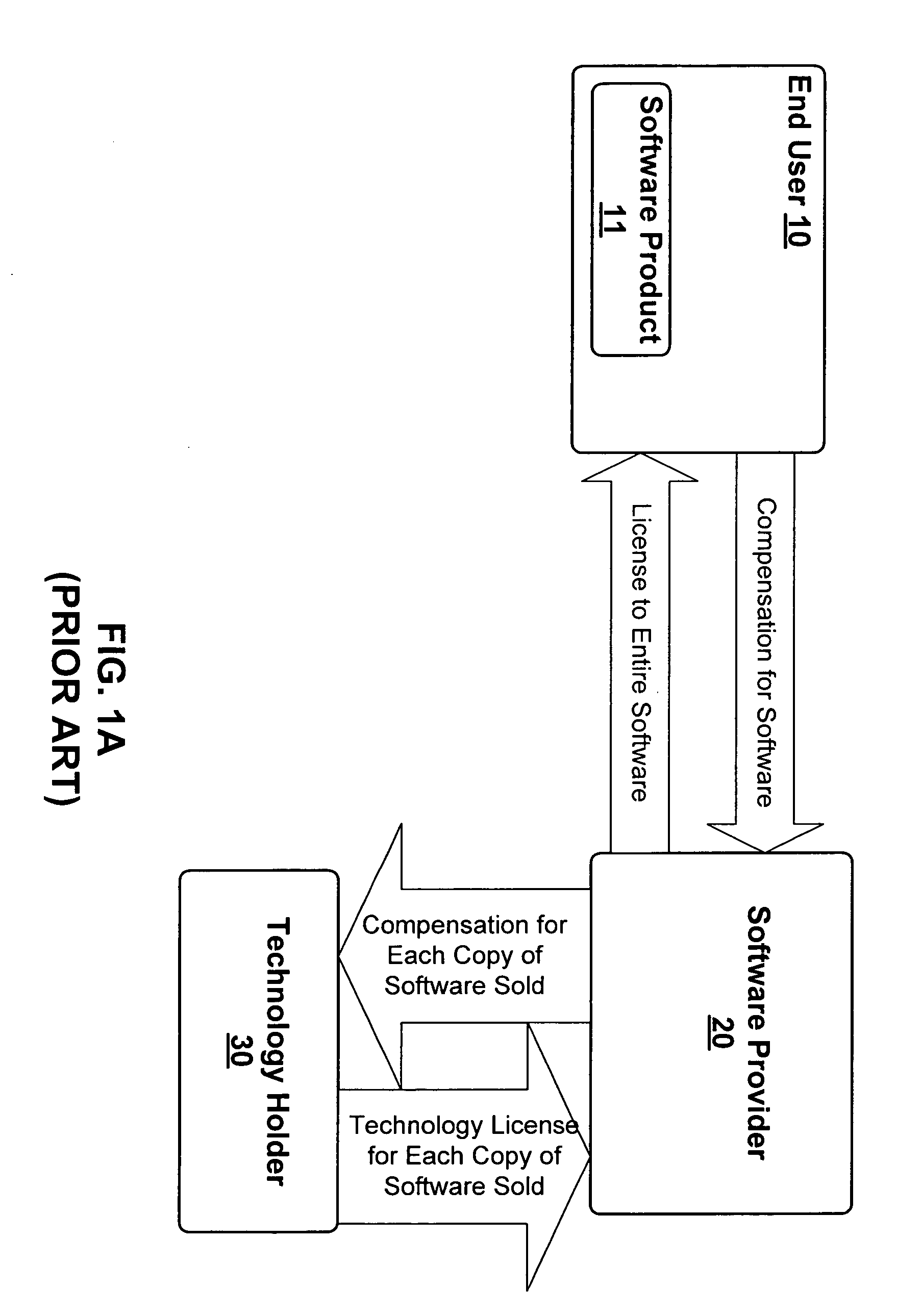
System and method for licensing software
ActiveUS20050076334A1Low costUnderstand clearlyProgram loading/initiatingProgram/content distribution protectionSoftware engineeringSoftware vendor
A system and method for licensing software using a clearinghouse to license only the technology modules that an end user registers. The clearinghouse maintains registration information which can be used to bill a software provider for the technology licensed to the end user. The system can be used to compensate technology owners only after the end user registers an unlicensed technology module. Thus, the system and method allows software vendors to reduce costs by licensing only the technologies that an end user actually uses. The clearinghouse can also be used to track the usage of software functionality to determine the popularity of a particular technology.
Owner:CYBERLINK
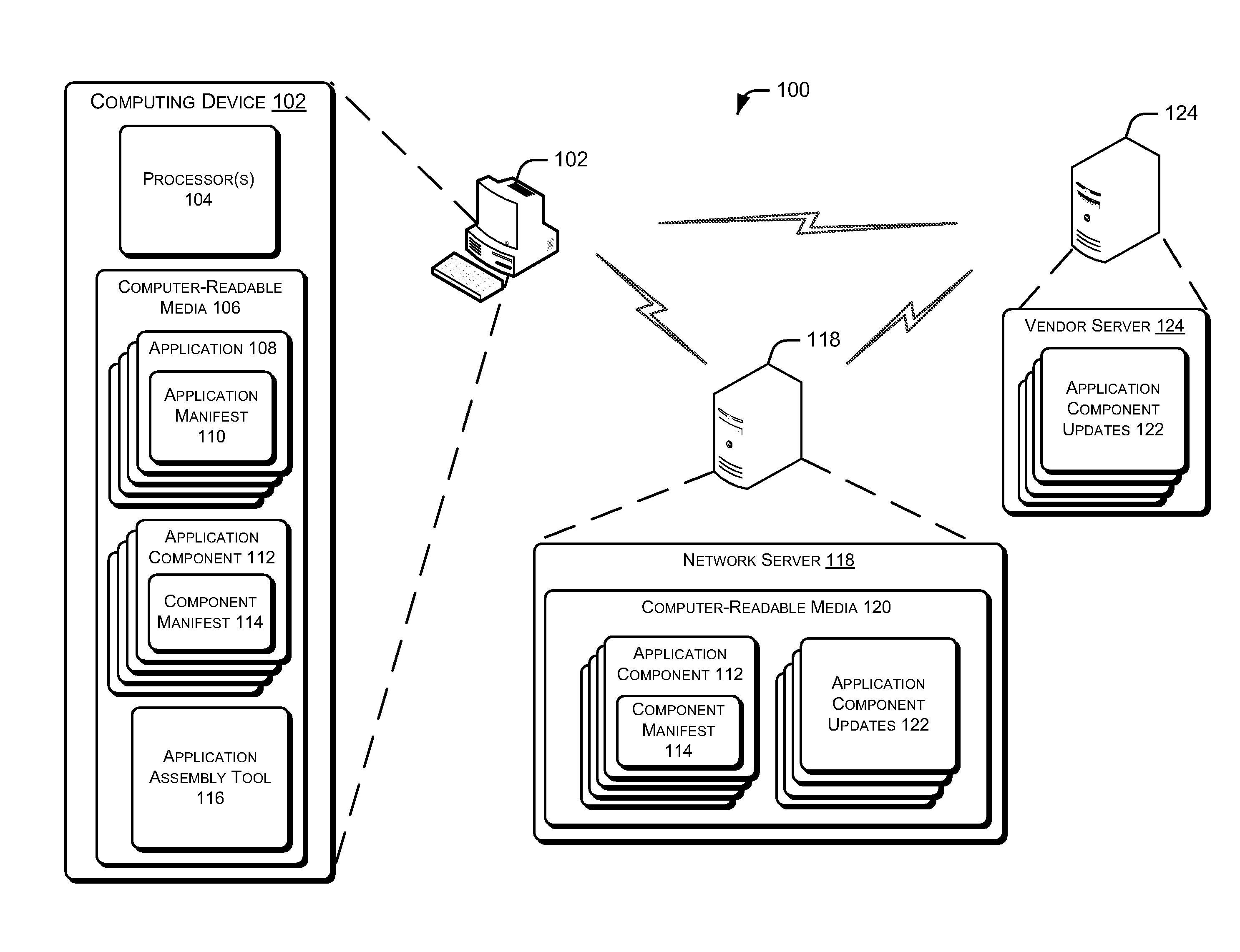
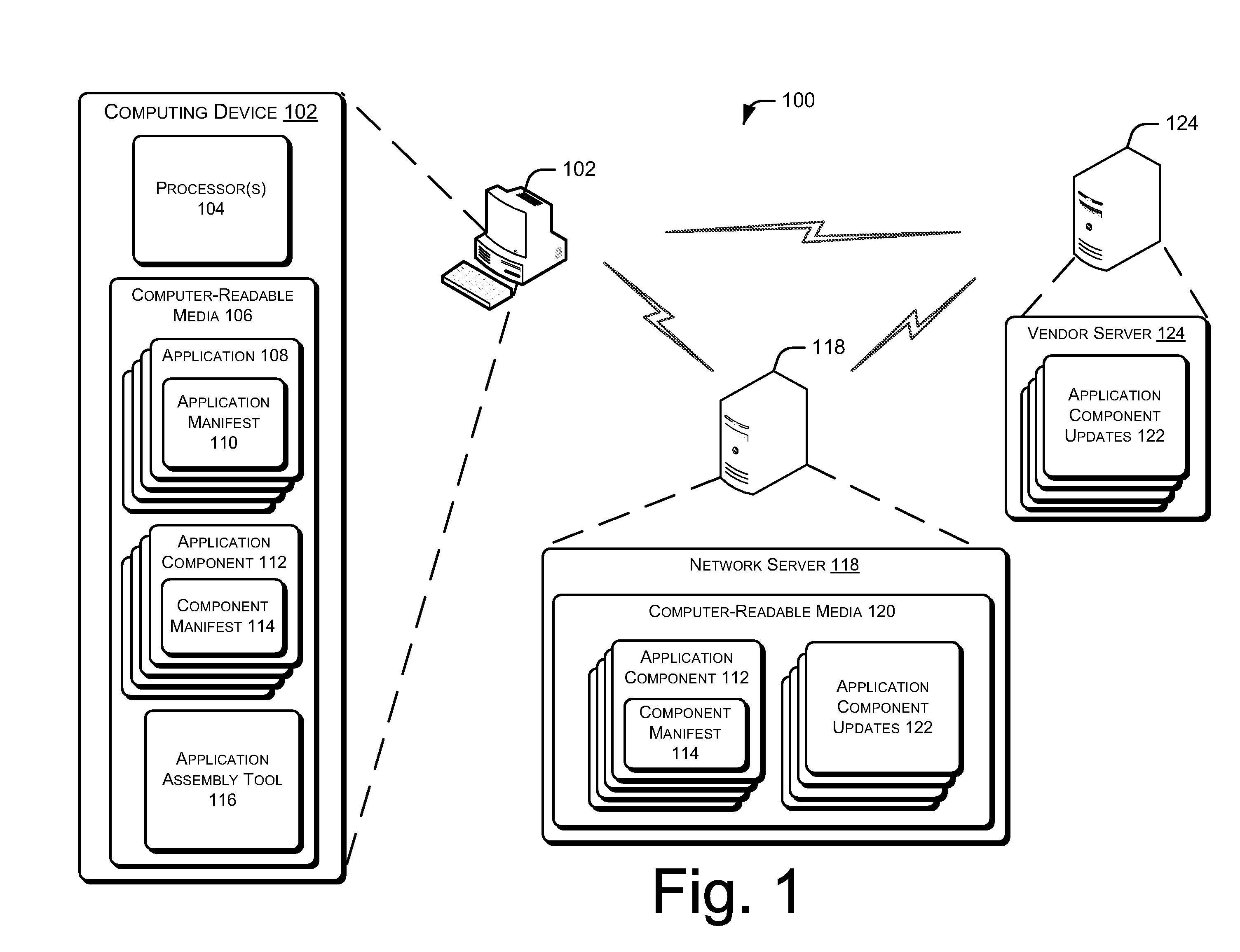
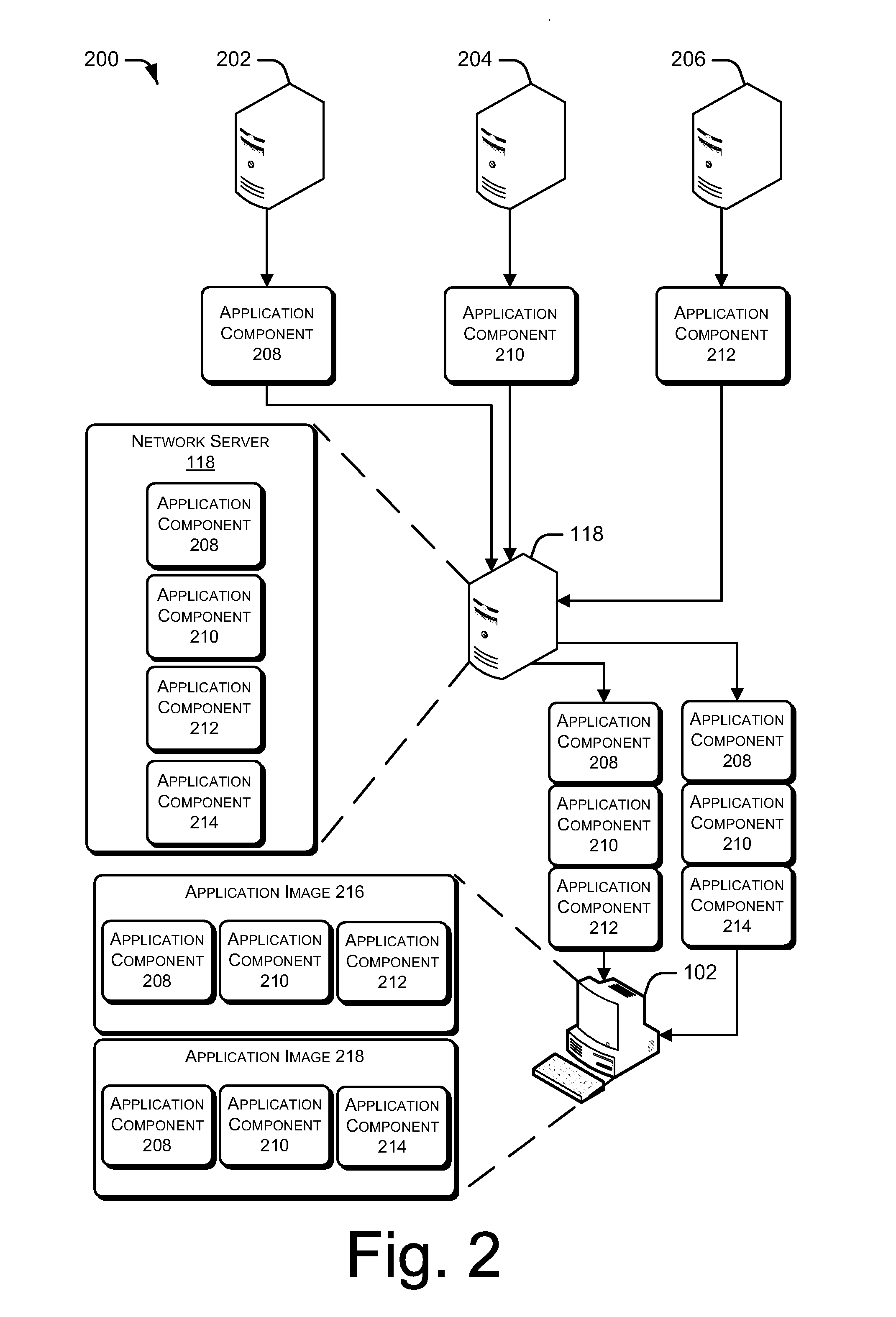
Dynamic Composition of Virtualized Applications
Various embodiments enable an application to be run on a computing device via dynamic composition of a virtual application image on a client device. The virtual application image is constructed using one or more application components retrieved from a local storage location and / or a remote resource, such as a network server. Each application component can be an independently serviceable unit that can be updated and / or replaced by any suitable entity, such as an independent software vendor, a network administrator, and so on.
Owner:MICROSOFT TECH LICENSING LLC
System and method for executing a rental software program in distributed computing environment
InactiveUS7171390B1Reduce storage spaceReservationsUser identity/authority verificationDistributed Computing EnvironmentSystem call
A system and method for executing a rental software program in a distributed computing environment is provided. The system enables the streaming of software applications to the client computer. It also enables the system calls of the software application to be intercepted and analyzed in order to determine when one or more optional files are needed. The system also suspends the operation of the software application during retrieval of the optional files from the server so that the software application does not crash and then restarts the software application once the optional files are retrieved. The system also protects the software application and its optional files from unwanted copying in that the system may remove all of the files from the client computer once the rental of the software application has been completed. Finally, the system also enables a software vendor to easily and quickly upload a new software application to the server so that client computers may rent the software application.
Owner:SOFTONNET
Method and system for providing internet services
ActiveUS20090328174A1Reduce complexityDigital data processing detailsUser identity/authority verificationApplication programming interfaceIntegration platform
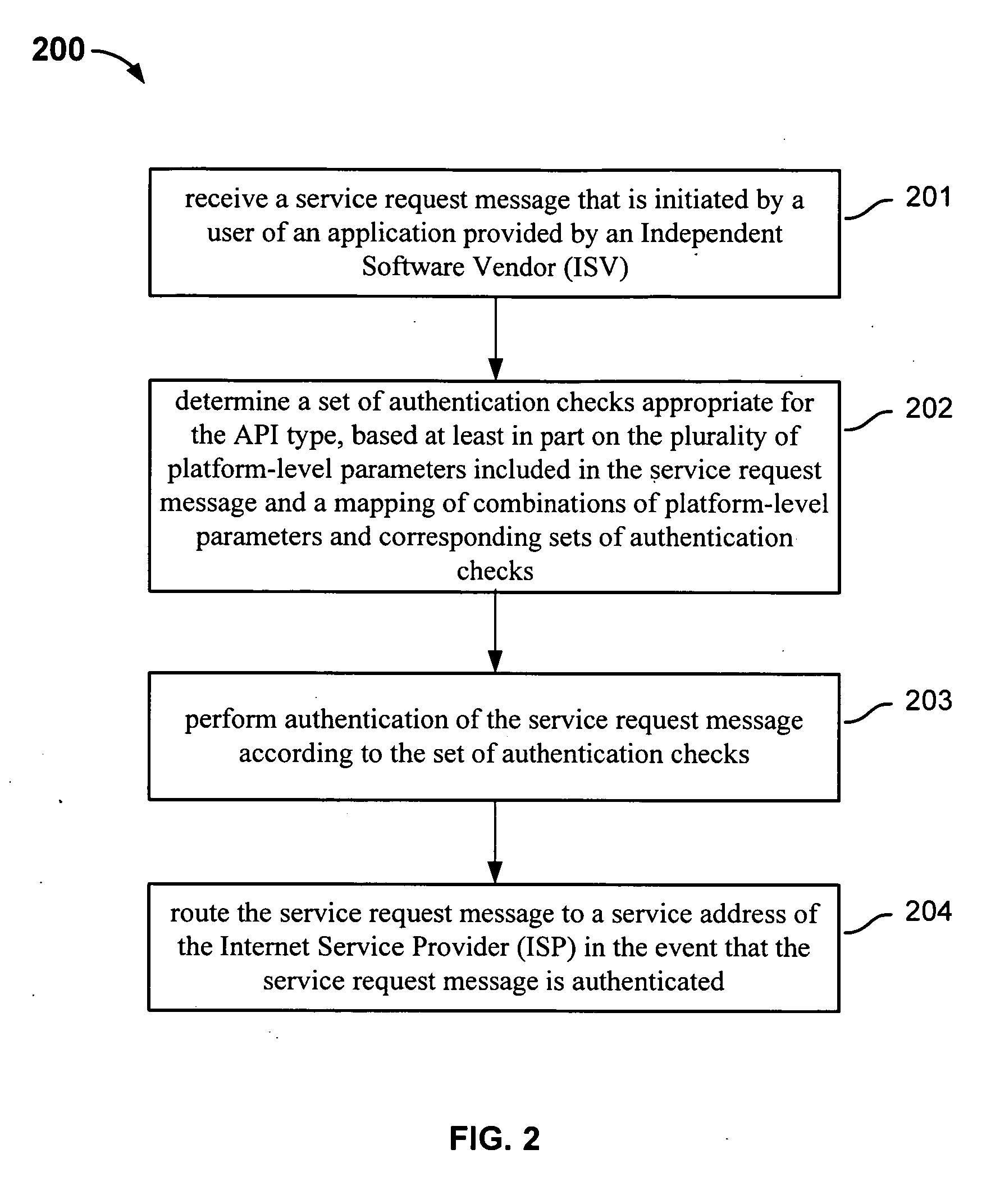
A service integration platform system for providing Internet services includes: an interface configured to receive a service request message that is initiated by a user of an application provided by an Independent Software Vendor (ISV), the service request message being implemented according to an Application Programming Interface (API) type and including a plurality of platform-level parameters that conform to the API type. The system further includes one or more processors coupled to the interface, configured to: locate a set of authentication checks that are appropriate for the API type, based at least in part on the plurality of platform-level parameters included in the service request message and a mapping of predefined combinations of platform-level parameters and corresponding sets of authentication checks; perform authentication of the service request according to the set of authentication checks; and route the service request to a service address of the Internet Service Provider (ISP) in the event that the service request is authenticated.
Owner:ALIBABA GRP HLDG LTD
Software-as-a-service (SaaS) application generation and deployment supporting method and device
ActiveCN102135883AStrong development independenceSupport personalized customizationTransmissionSpecific program execution arrangementsPortletSoftware engineering
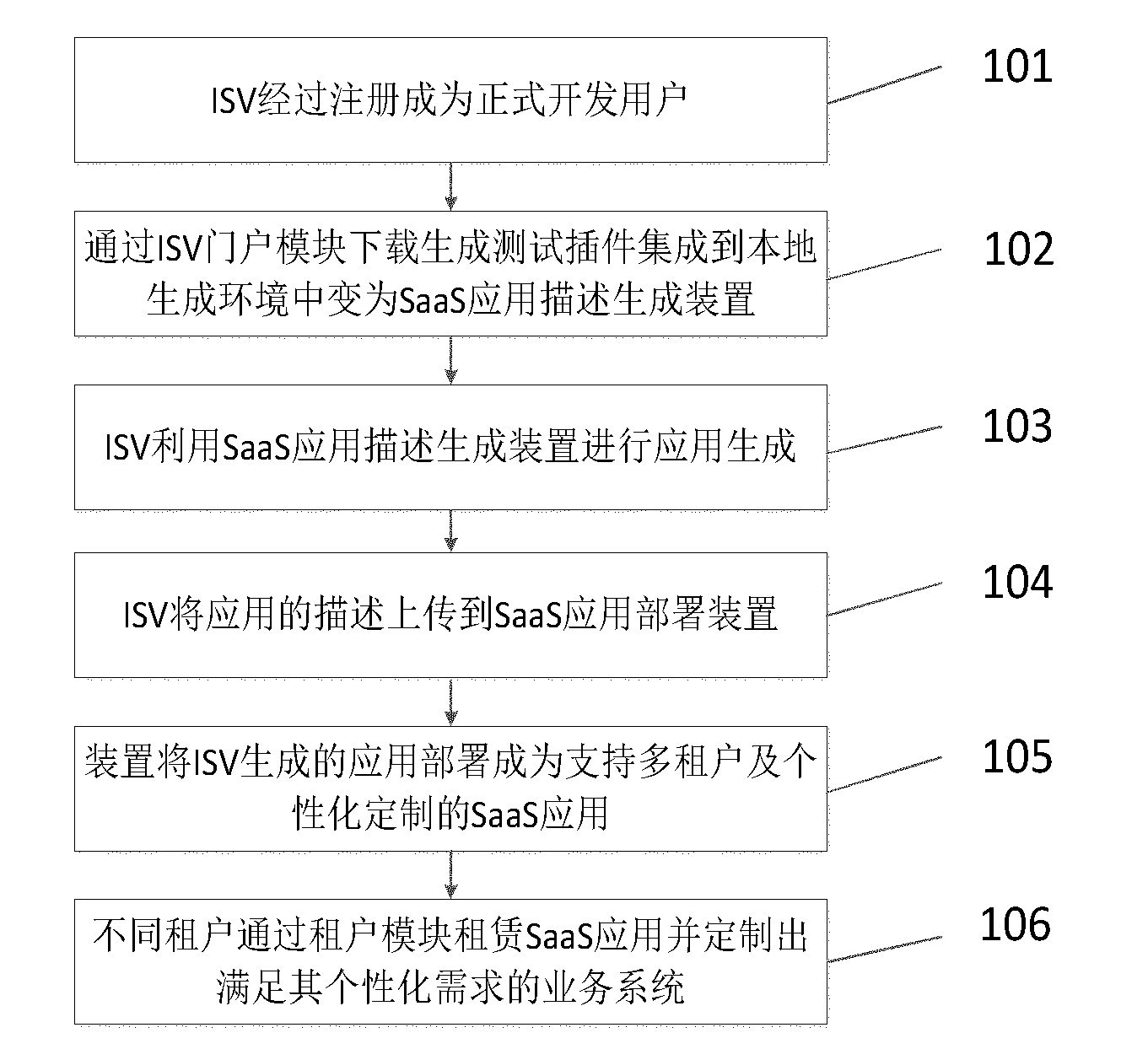
The invention relates to a software-as-a-service (SaaS) application generation and deployment supporting method and an SaaS application generation and deployment supporting device, which aim to solve the problems of the conventional SaaS software generation and release. The method comprises the following steps that: A, an independent software vendor obtains a development license of an SaaS application generation and deployment device by registration to become an official development user; B, the independent software vendor downloads a generation and testing tool kit by an independent software vendor (ISV) portlet, and integrates the tool kit into a local generation environment to make the local generation environment become an SaaS application description generation device for rapidly generating SaaS application; C, the independent software vendor performs application generation by utilizing the SaaS application description generation device, and uploads the description of the application into an SaaS application deployment device; D, the SaaS application deployment device adds bottom-layer realization to the application generated by the ISV to deploy the application into the SaaS application supporting multiple tenants and personalized customization; and E, the tenants try on, rent and customize the SaaS application.
Owner:SHANDONG UNIV
Aggregation of the knowledge base of antivirus software
InactiveUS7765400B2Attempt have been hamperedIncrease speedData processing applicationsMemory loss protectionFile systemMalware
Owner:MICROSOFT TECH LICENSING LLC
Secure Policy Differentiation by Secure Kernel Design
InactiveUS20090089579A1Computer security arrangementsSecuring communicationData processing systemSecurity kernel
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for users to execute software from independent software developers, an administrative user may disable the above-described vendor key-checking as an option.
Owner:IBM CORP
System and method of aggregating the knowledge base of antivirus software applications
InactiveUS7765410B2Attempt have been hamperedIncrease speedMemory loss protectionDigital data processing detailsFile systemApplication software
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com