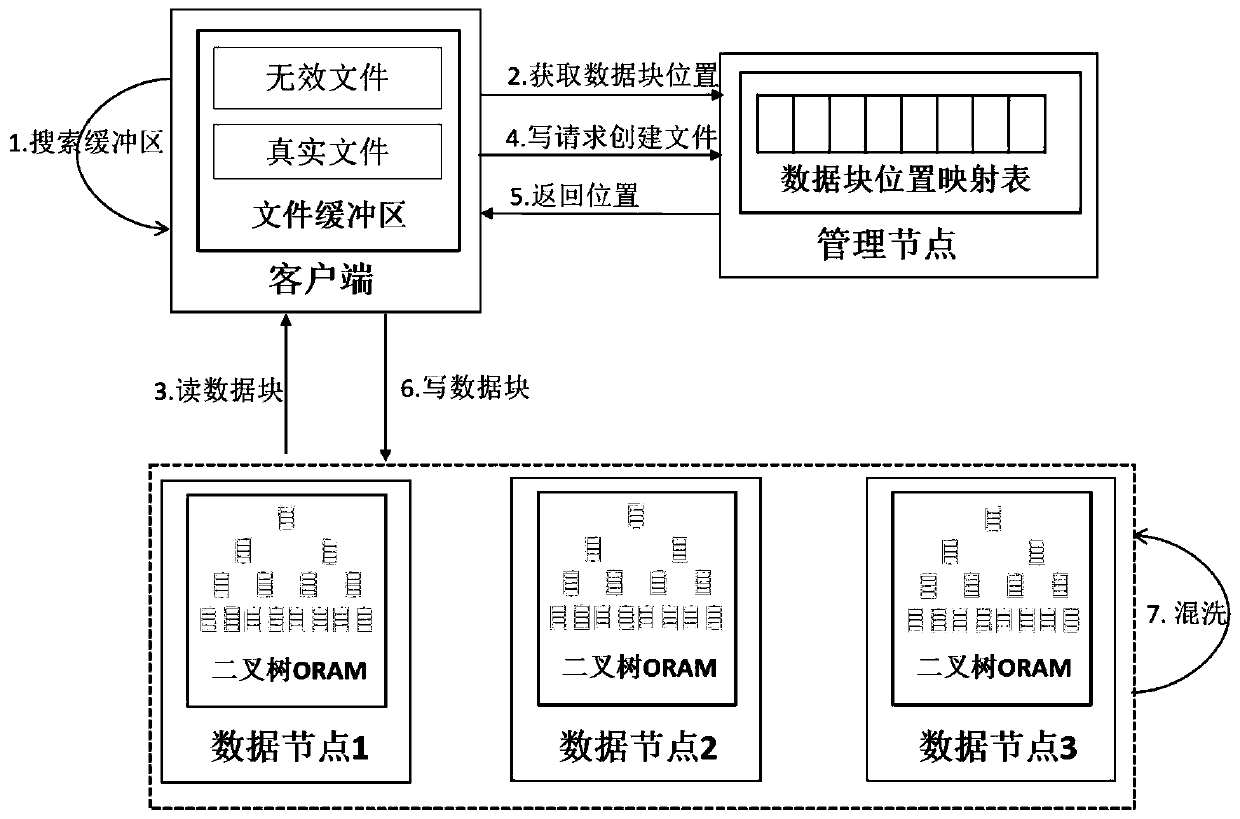
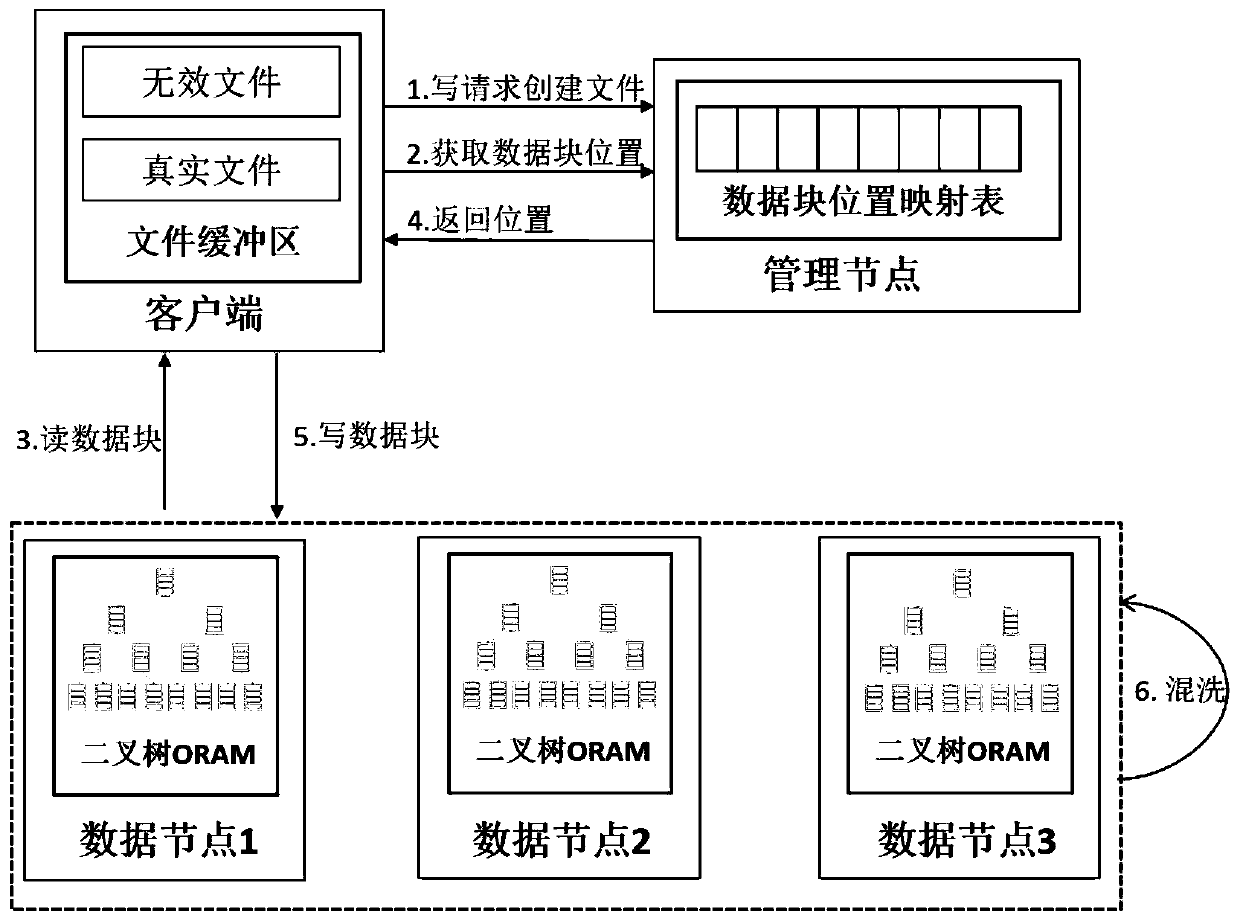
Protection method and system for HDFS access mode
An access mode and data node technology, applied in the fields of digital data protection, instruments, computing, etc., can solve the problems of reducing attack cost, inability to obtain user data storage location, access frequency and access sequence privacy information, confusion, etc., to enhance security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below through specific embodiments and accompanying drawings.
[0025]The code realization of the present invention is based on Hadoop 2.8.4 source code, revises source code according to function module and file read-write process, and the java file of main modification is CommandWithDestination.java, IOUtils.java and PathData.java, and newly added java file is FileBuffer. java, TreeNode.java and TreeORAM.java, the total code size is 4686 lines. The specific operation process is described below.
[0026] 1. Initialization
[0027] After the HDFS cluster is started, an initialization operation is required to transfer several dummy files to the data nodes. The dummyfile is an invalid file, and the difference between the dummy file and the real file cannot be distinguished outside the client. The role of initi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com