Efficient and helpful reading method for static data
A static data, efficient technology, applied in the field of network security, can solve the problems of inferring user privacy, large performance overhead, consumption of large storage space and computing resources, etc., to reduce computing and storage overhead, ensure data confidentiality, and high practicability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Attached below Figure 1~6 The present invention will be further described with specific implementation examples.
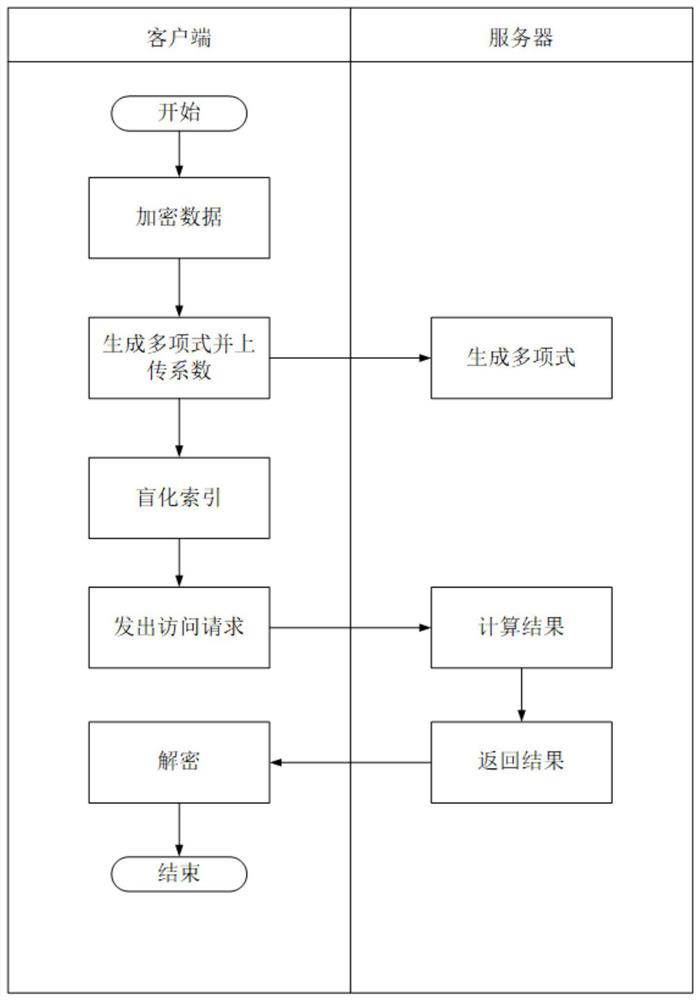
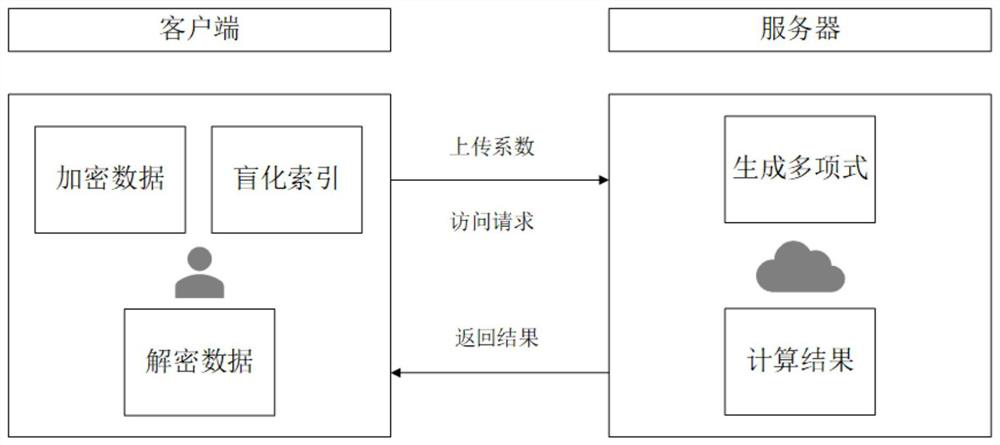
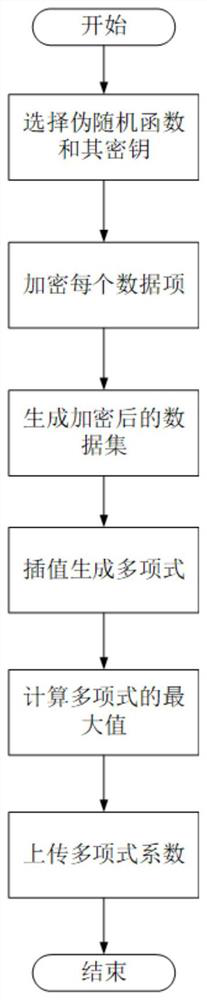
[0035] The present invention proposes a high-efficiency dazed reading method for static data. The client uses a pseudo-random function F to encrypt the data locally, generates an encrypted data set C, and interpolates to create a polynomial function f(x) such that f(i )=C[i], upload the coefficients of the polynomial function to the server; when the client wants to access the data item corresponding to the real index i, blind the real index i into a fake indexγ i sent to the server; after the server receives the access request, it calculates f(γ i ) and return the result to the client; the client receives f(γ i ) is restored to C[i] locally, and then decrypted using the pseudo-random function F to obtain the data item corresponding to the real index i;
[0036] The implementation of the entire technical solution includes two parts: client and server:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com