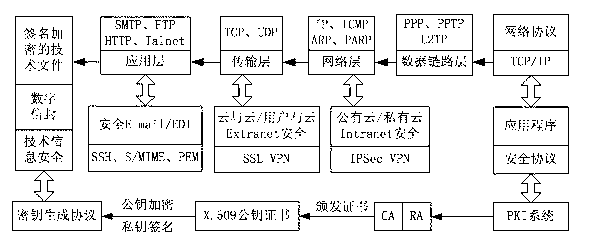
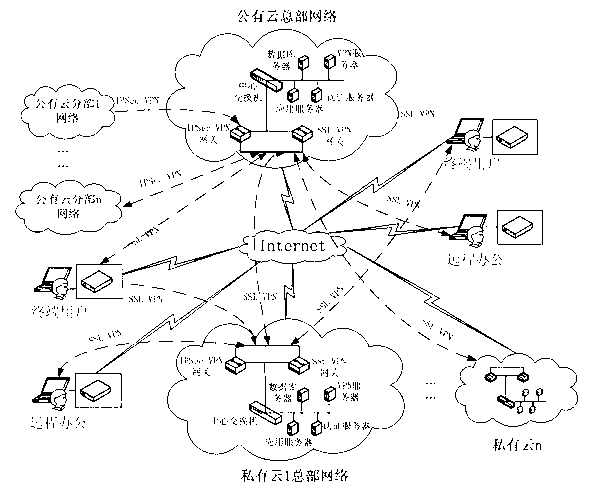
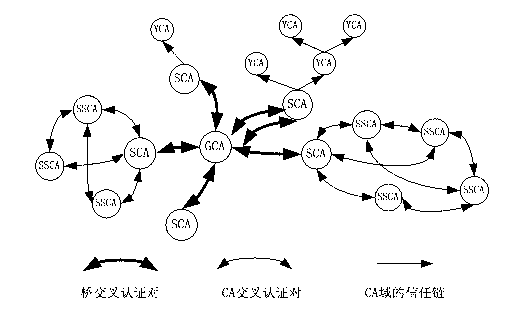
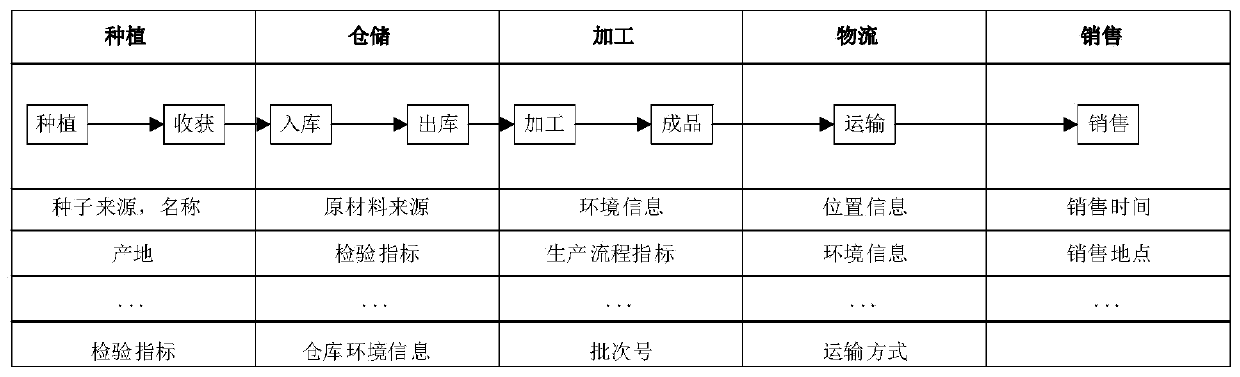
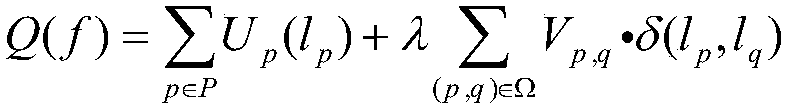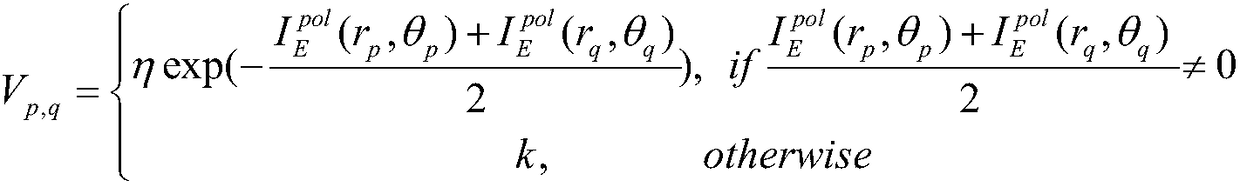Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
96 results about "Information security management system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An information security management system is a set of policies concerned with information security management or IT related risks. The idioms arose primarily out of BS 7799. The governing principle behind an ISMS is that an organization should design, implement and maintain a coherent set of policies, processes and systems to manage risks to its information assets, thus ensuring acceptable levels of information security risk.
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
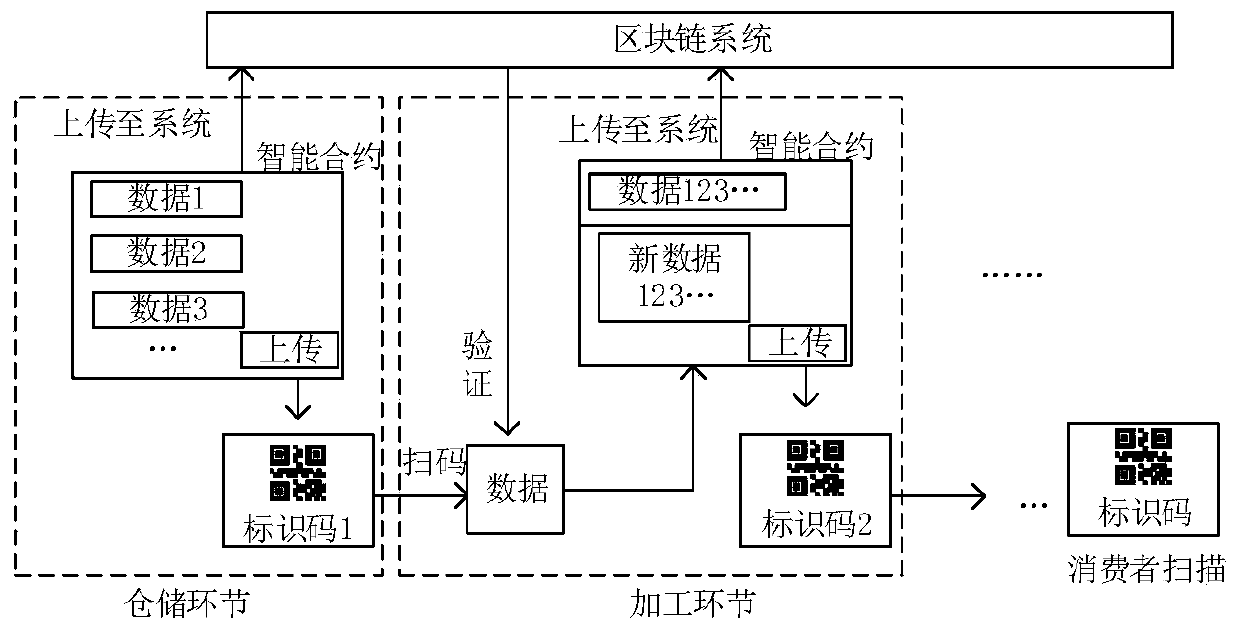
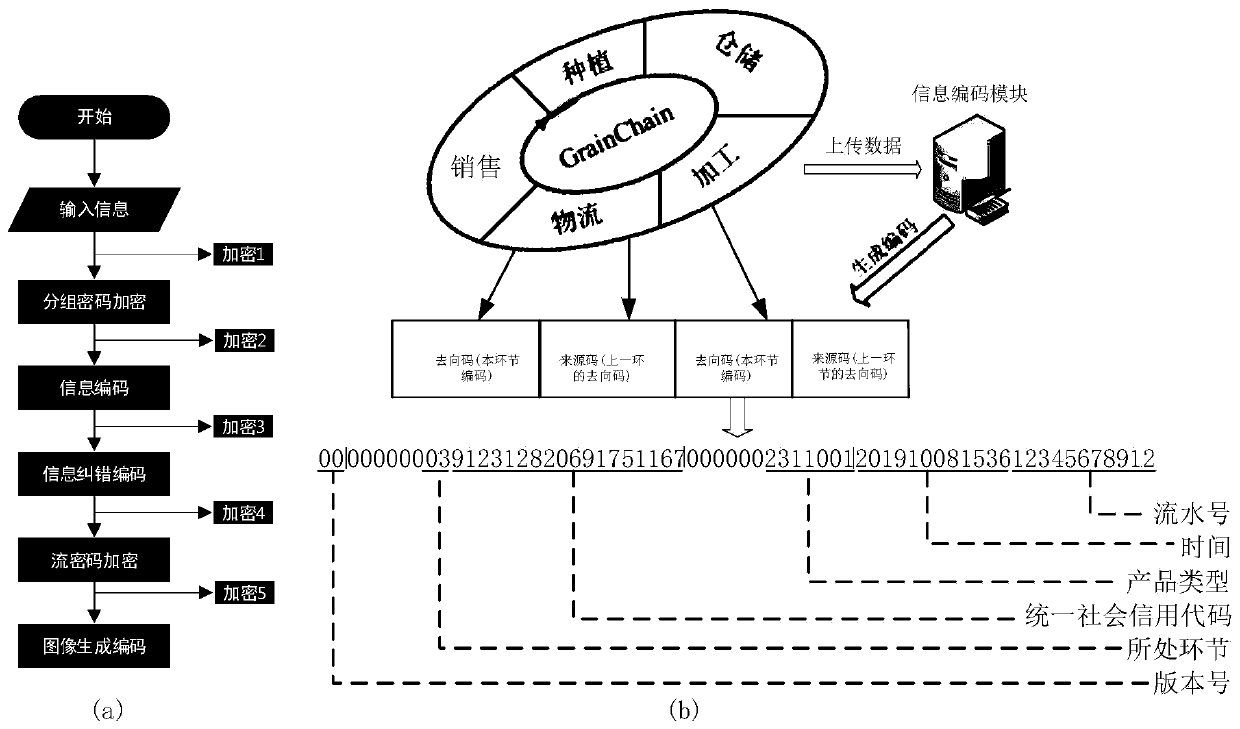
Grain and oil food full supply chain information security management system and method based on trusted identifier and IPFS
ActiveCN110879902AReduce the difficulty of traceabilityIncrease credibilityDigital data protectionInformation accessPrivacy protection
The invention provides a grain and oil food full supply chain information security management system and method based on a trusted identifier and an IPFS, and relates to the fields of block chain technology, grain and oil food security and the like. The system is realized by adopting a browser / server structure, and provides management functions of registration, information acquisition, informationquery, real-time monitoring and the like for a user based on a credible identification model of a block chain and an IPFS + block chain dual-mode storage mechanism. According to the method, the operation process of the grain and oil food full supply chain is analyzed, distributed nodes are set to upload data, a grain and oil food full supply chain credible identification model based on the blockchain is constructed, and a dual-mode data storage mechanism of IPFS and the block chain is adopted. According to the invention, the data transmission of each link on the grain and oil food full supply chain is safe and transparent, the information access speed and privacy protection are improved, the upper and lower chains of the supply chain information are controlled through the intelligent contract, and the management functions of grain and oil food full supply chain information acquisition, query, tracing, monitoring and the like are realized.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
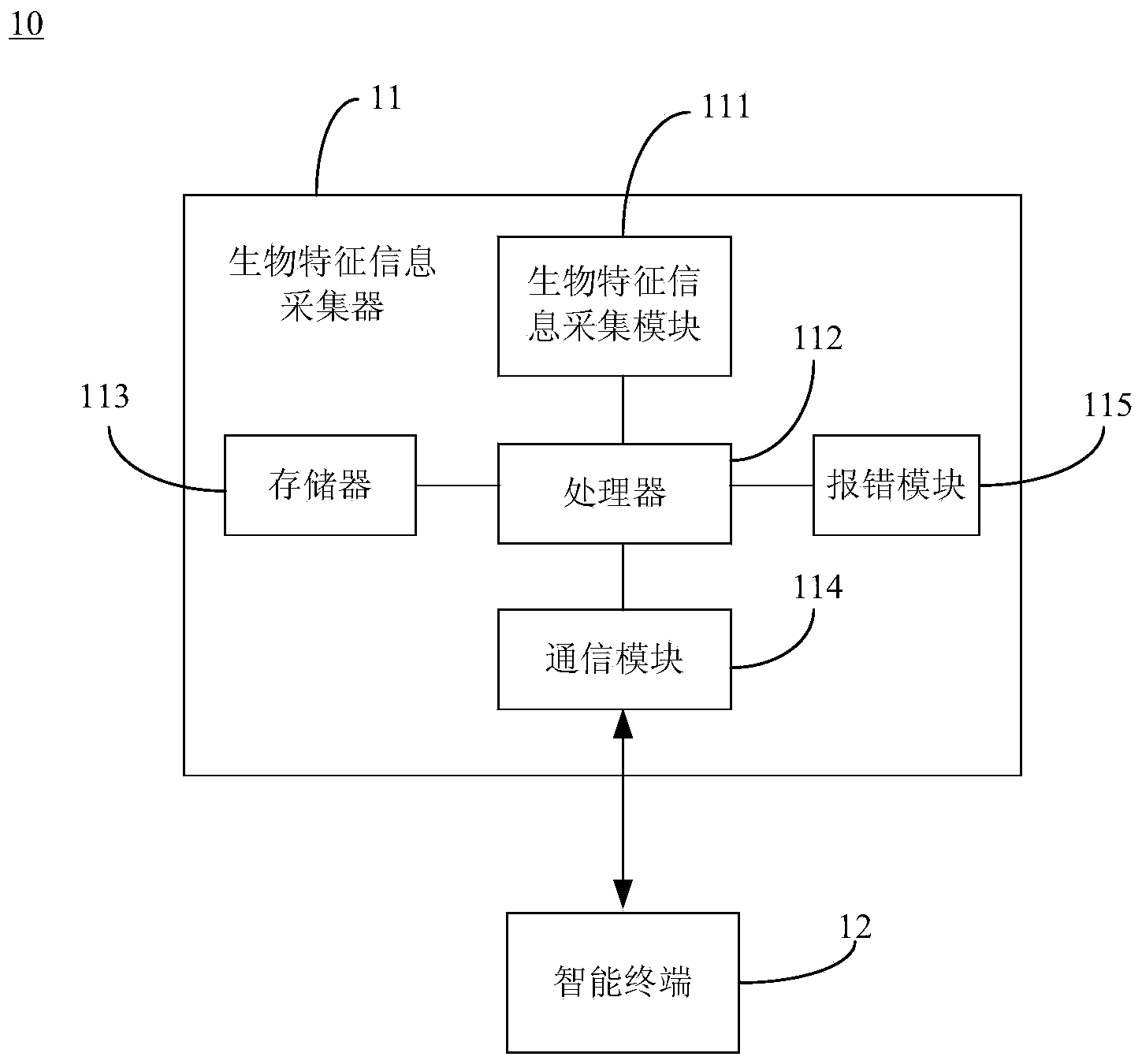
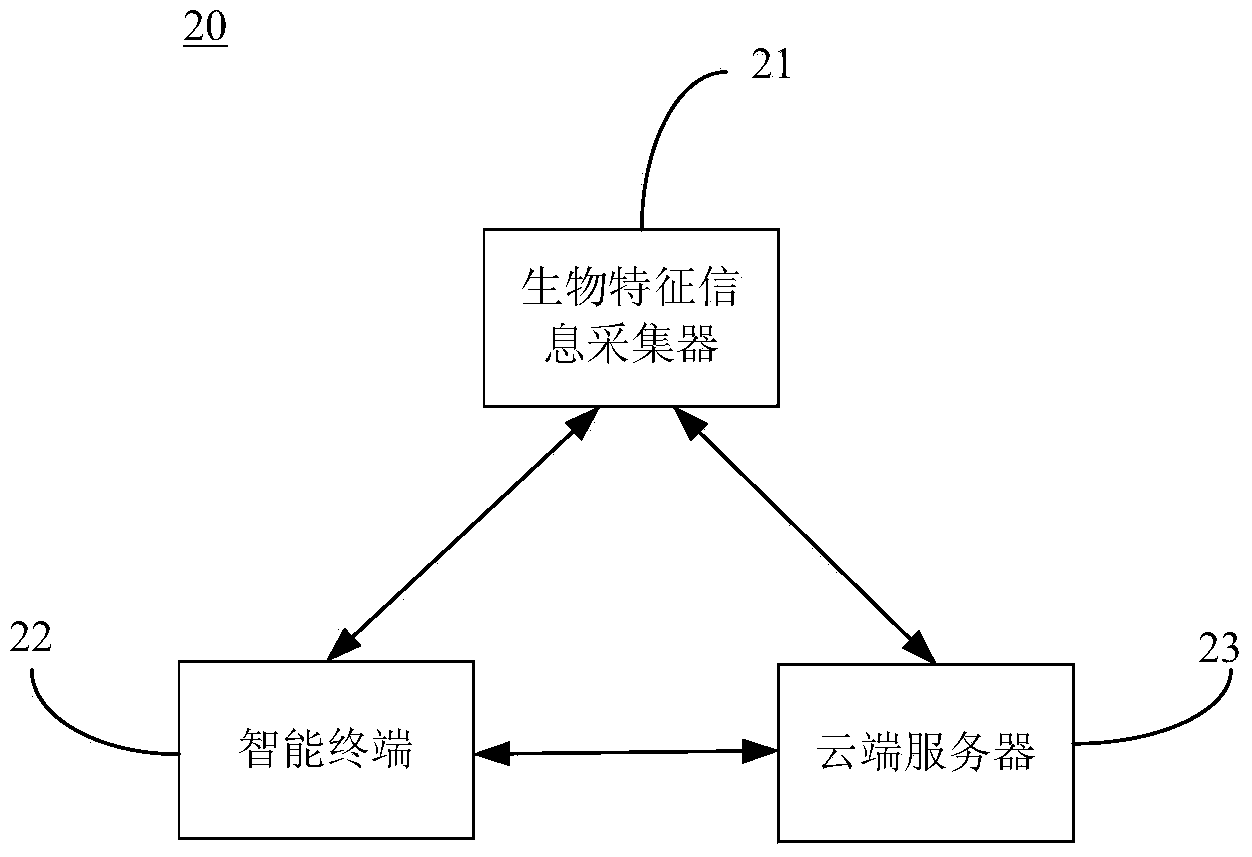
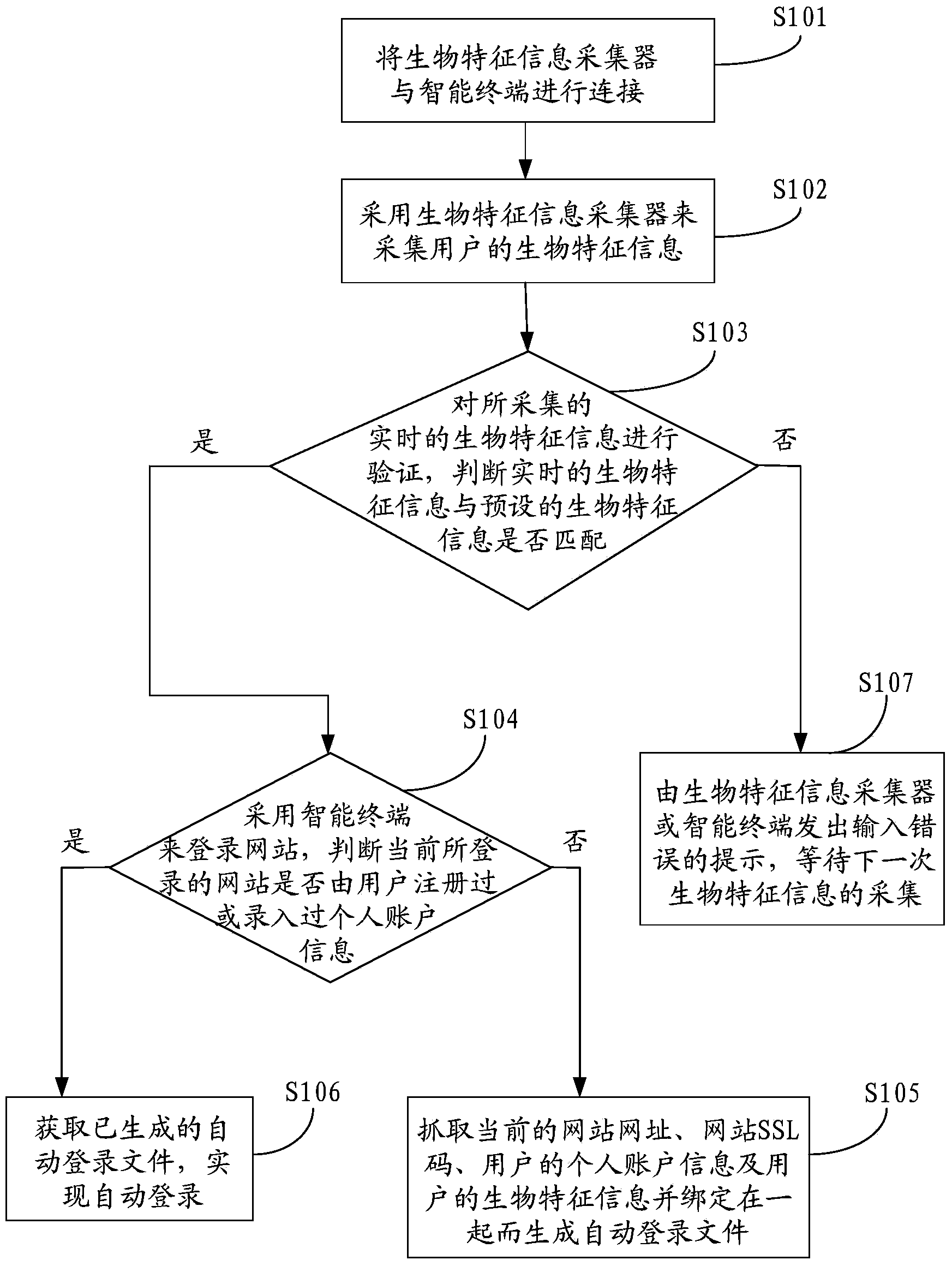
Personal account information security management system and method based on biologic characteristic information verification
ActiveCN104239768AEasy to operateEasy to storeUser identity/authority verificationDigital data authenticationTime informationSafety management systems
The invention discloses a personal account information security management system and method based on biologic characteristic information. The method comprises the following steps that (a) a biologic characteristic information collector is connected with an intelligent terminal; (b) the biologic characteristic information of a user is collected; (c) verification is carried out, if the real-time information is matched with the preset biologic characteristic information, a step (d) is executed, and otherwise, a step (g) is executed; (d) the website logging in is carried out, whether the current logged website is registered by users or not or whether the personnel account information is inputted or not is judged, if so, a step (f) is executed, and otherwise, a step (e) is executed; (e) the current website address, the website SSL code, the personnel account information of the user and the biologic characteristic information of the user are captured and are bound together for generating an automatic logging in file; (f), the generated automatic logging in file is obtained, and automatic logging in is realized; (g) input error prompt is given out, and the system waits for the next biologic characteristic information collection. The method and the system have the advantages that the personnel account information of the user and the biologic characteristic information with the unique label are associated for guaranteeing the security of the user personnel information, the use is convenient, and the system and the method can be favorably popularized in a wide range.
Owner:SHENZHEN HOFAN ECOMMERCE
Provincial highway operation management data center system and implementation method thereof
InactiveCN105488641AVersatileClear logicDatabase management systemsGeographical information databasesSafety management systemsData platform
The invention discloses a provincial highway operation management data center system and an implementation method thereof. The system includes a comprehensive database, a data platform, an operation and maintenance system and a security management system; the comprehensive database is used for realizing source-division and class-division management storage of data; the data platform is used for realizing interactive sharing, mining analysis and fusion processing of the data; the operation and maintenance system is used for realizing infield equipment operation and maintenance, asset management and infield maintenance information statistic analysis; and the security management system can initiatively find out important security vulnerabilities and security events, and can rapidly recover a system after the system is damaged. The invention discloses a provincial highway operation and management data transmission, sharing, distribution, storage and processing big data processing implementation method. According to the provincial highway operation management data center system and implementation method thereof of the invention, a data center architecture and a data flow which can connect various service application systems and realize resource sharing are constructed.
Owner:SOUTHEAST UNIV
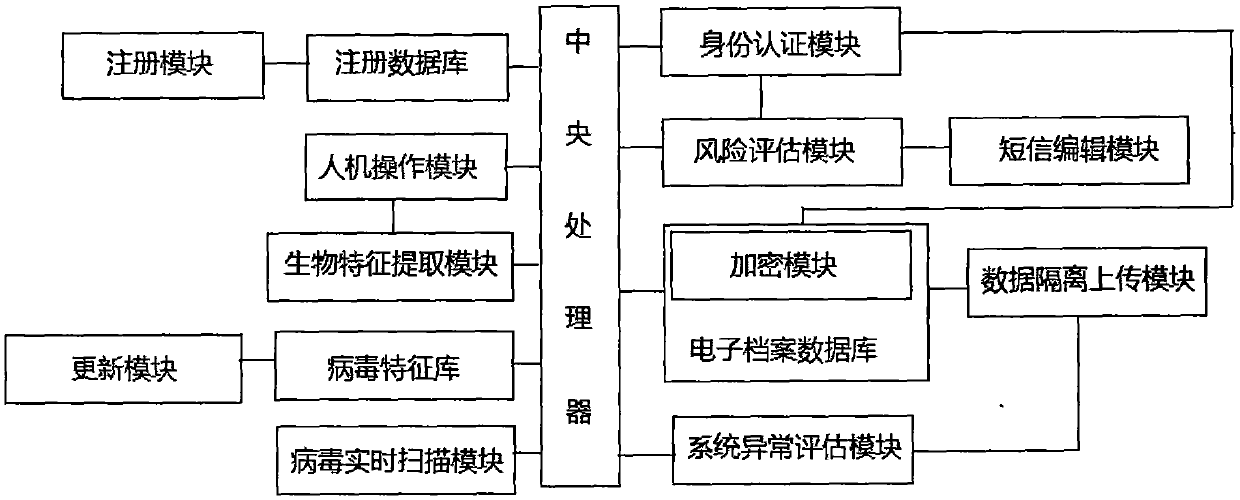
Electronic record information security management system
The invention discloses an electronic record information security management system, comprising a registering module, a man-machine operation module, a biological feature extraction module, an identity authentication module, a risk assessment module, a virus feature base, a virus real time scanning module, a system abnormity assessment module, an electronic record database with a built-in encryption module, a data isolation uploading module and a central processing unit. According to the invention, multiple verifications such as vocal print verification, face verification, palm vein verification and random secret key verification are integrated; the electronic record information security is greatly improved; meanwhile, the system is equipped with the built-in virus scanning function; once intrusion is discovered, the system built-in data protection and clear function further ensure the electronic record information security.
Owner:ZHONGBEI UNIV
Method and apparatus for detecting data collection omission in traffic collection device
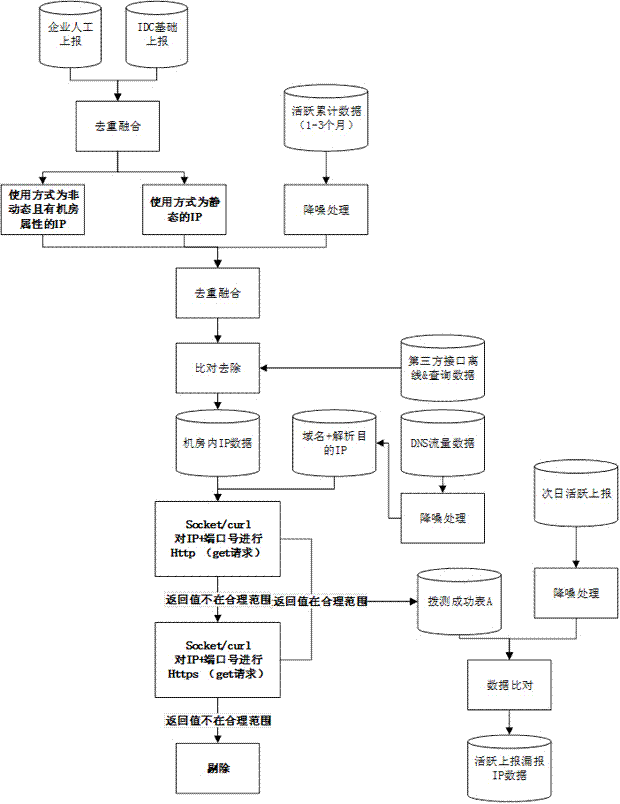
ActiveCN107579874AImprove regulatory capacityReduce performance requirementsData switching networksDomain nameComputer network
The invention discloses a method for detecting data collection omission in a traffic collection device and relates to an information security technology in the technical field of information. The method comprises the following steps: step 1 is discovery of omission of active IP data, and step 2 is discovery of omission of active domain name data. According to the invention, a DNS data source is used to supplement original data, and data which has the attribute of a computer room is extracted, and then a simulation request is performed, such that the performance demand for the simulation request is reduced, a more comprehensive simulation request is also provided, and discovered omission is more comprehensive and accurate. When the simulation request is performed, an http (get / post) requestis firstly performed, and then afterwards, data whose simulation request result return values are not within a reasonable scope is subjected to an https (get / post) request. Such a mode, compared to amode of performing http&https simulation requests on all data, can reduce the performance demand for the simulation request, and compared to a mode of only performing the http simulation request, canalso enhance comprehensiveness of the simulation request. According to the invention, the network supervision level can be effectively improved, and data missed by an information security managementsystem is discovered for analysis of omission reasons of the information security management system.
Owner:BEIJING ACT TECH DEV CO LTD
Internet data center/Internet service provider (IDC/ISP) information security management system and information management method thereof
InactiveCN105490831AA comprehensive understanding of social conditions and public opinionData switching networksSpecial data processing applicationsWeb siteSafety management systems
The invention relates to information security management, in particular to an Internet data center / Internet service provider (IDC / ISP) information security management system and an information management method thereof for performing basic data management, access log management and information security management on an IDC / ISP. The IDC / ISP information security management system consists of a control platform, a website record management system, an IDC operation management platform, a provincial end execution system and a uniform DPI equipment system which are in butt joint.
Owner:北京东方通网信科技有限公司
Computer information security management system
InactiveCN106656987AAvoid unresponsivenessPrevent leakageHardware monitoringTransmissionInformation security risk managementPrivate network
The invention discloses a computer information security management system in the network security technology field. The system comprises a manager control terminal and a computer terminal. The manager control terminal and the computer terminal are both in electrical output connection with an identity authentication unit. An omnibearing technical means is adopted, a host monitors a core, and a monitoring engine automatically adjusts the sampling frequency of information and priority levels of threads of the engine itself according to changes of utilization of host system resources. In this way, a control center is prevented from losing response to users, behaviors of private network users can be unified, and network security protection and control can be enhanced. Distributed multi-point monitoring and centralized management prevents private network information from leaking, and computer networks and user behaviors are comprehensively monitored and checked in terms of monitoring terminal illegal external link, equipment network access management or the like. Therefore, trusted access of computer networks is achieved, and security of computer information is greatly improved.
Owner:郑州理工职业学院
Embedded type file information security management system
ActiveCN101686294AOvercome the problems that are easy to cause leakagePictoral communicationSafety management systemsDocumentation
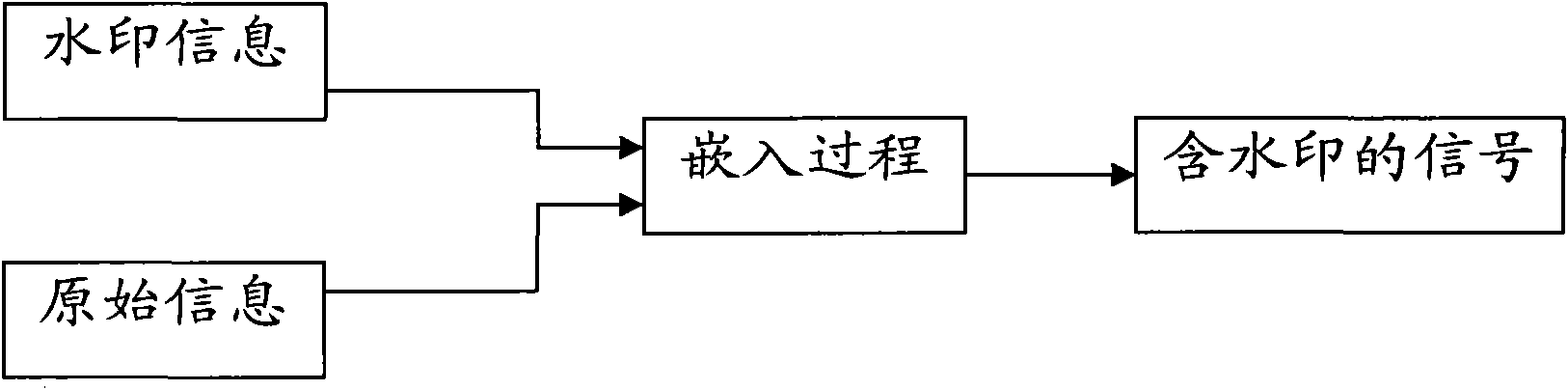
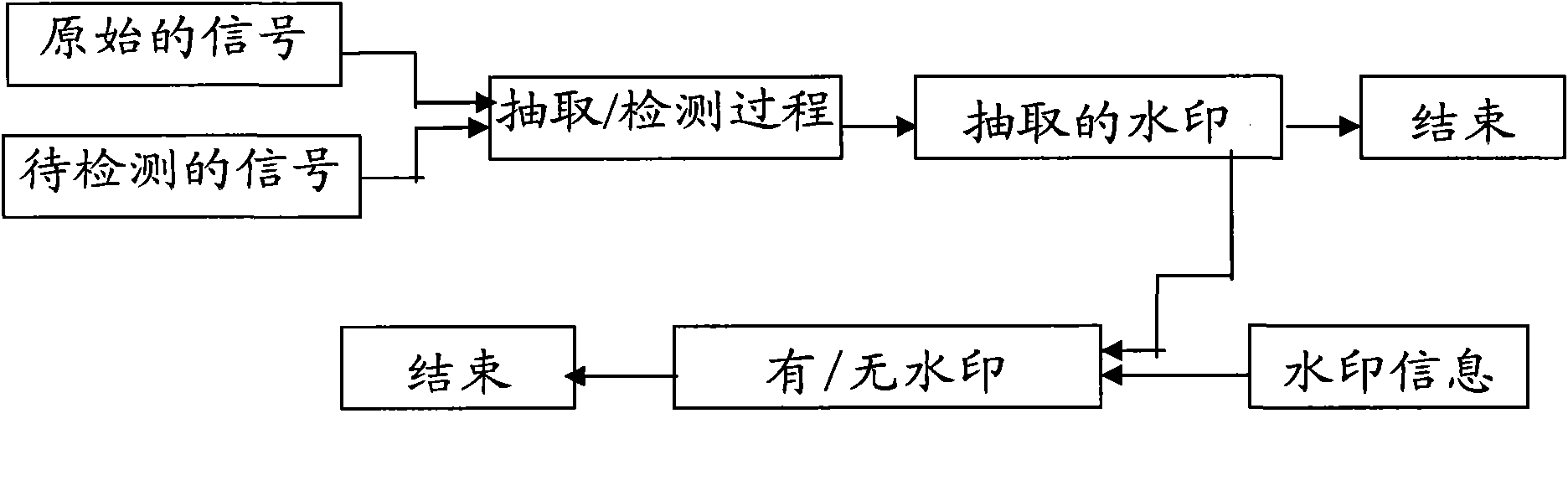
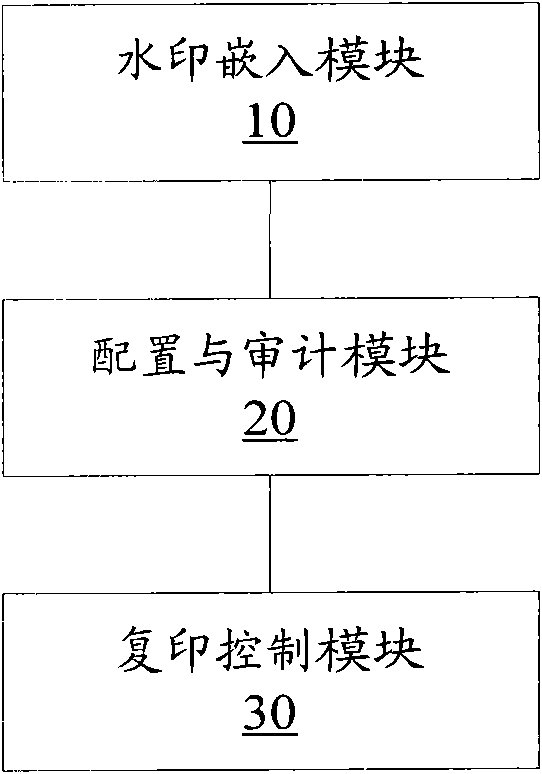
The present invention provides an embedded type file information security management system, comprising a watermark embedding module for generating an original paper file embedded with a watermark; aconfiguring and auditing module for configuring the operation authority of a user; and a copy control module for extracting the security classification information of the watermark of the original paper file, generating the watermark embedded type copy of the original paper file when the current user is judged to have the authority to copy according to the security classification information and the operation authority of the current user, and embedding the identification information of the current user in the watermark of the copy. The invention overcomes the drawback that file management inthe prior art is mainly implemented forcedly by security management system, particularly the paper file is basically registered and audited manually, leading to easy divulgence of documents in transmission and distribution.
Owner:BEIJING LANXUM NEW TECH CO LTD
Medical and health information security management system
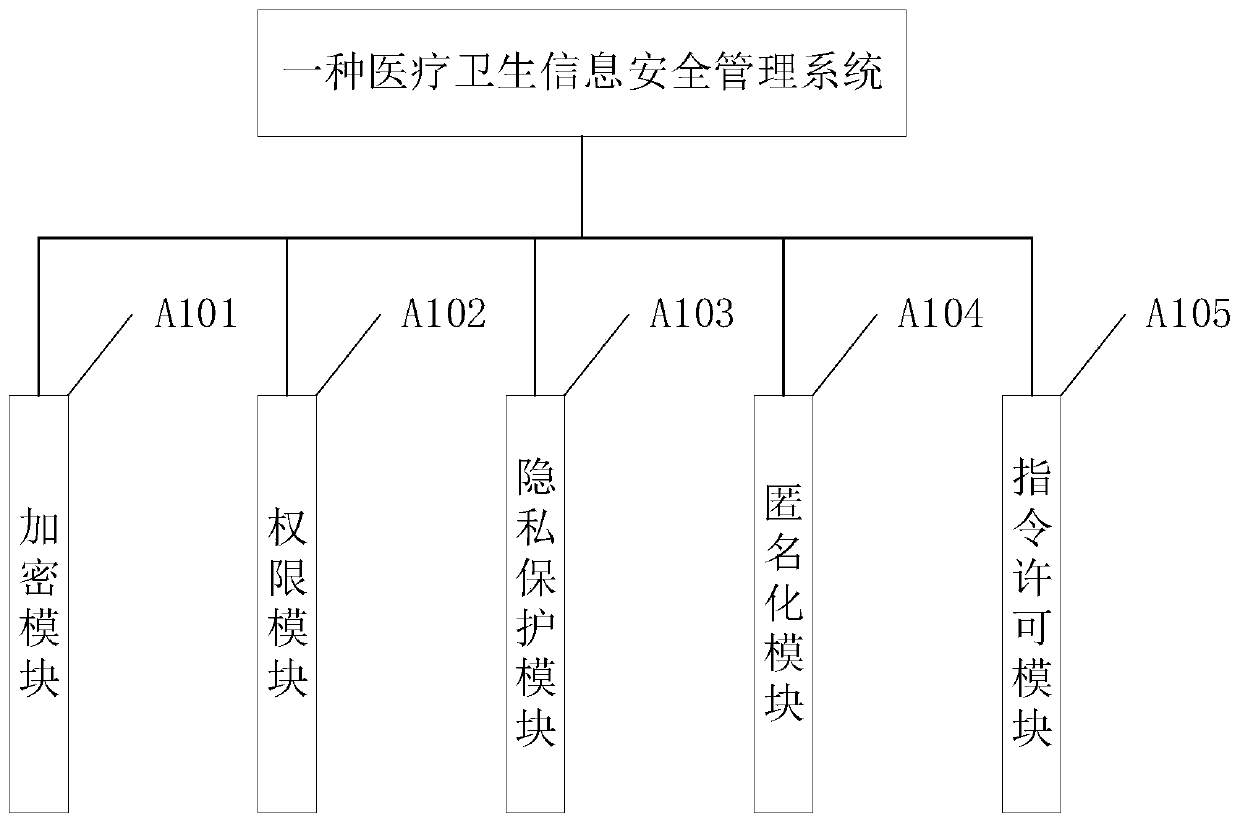
PendingCN110957025AHigh precisionImprove collection efficiencyDigital data protectionDigital data authenticationPrivacy protectionInformation security
The invention provides a medical and health information security management system. The system comprises an encryption module, an authority module, a privacy protection module, an anonymization moduleand an instruction permission module; the encryption module is used for realizing resident privacy protection while ensuring file sharing by setting security means of access authority and data encryption; the authority module is used for providing single sign-on, authorization, authentication, role-based access, database advanced security and application process control to achieve access permission setting; the privacy protection module is used for authorizing a user to access the archive information of a patient on the basis of determination of whether the patient agrees or not; the anonymization module is used for hiding privacy information when the archives of the patient are used; and the instruction permission module is used for verifying whether the access is legal or not when the patient file is accessed. According to the medical and health information security management system, the stratum data, the sampling data, the standard penetration data and the dynamic exploration datacorresponding to the rock core are acquired through the rock core pictures and uploaded to the server, so that the efficiency and the quality of exploration drilling logging data acquisition can be greatly improved, the links of manual participation are reduced, and the data accuracy is greatly improved.
Owner:重庆亚德科技股份有限公司
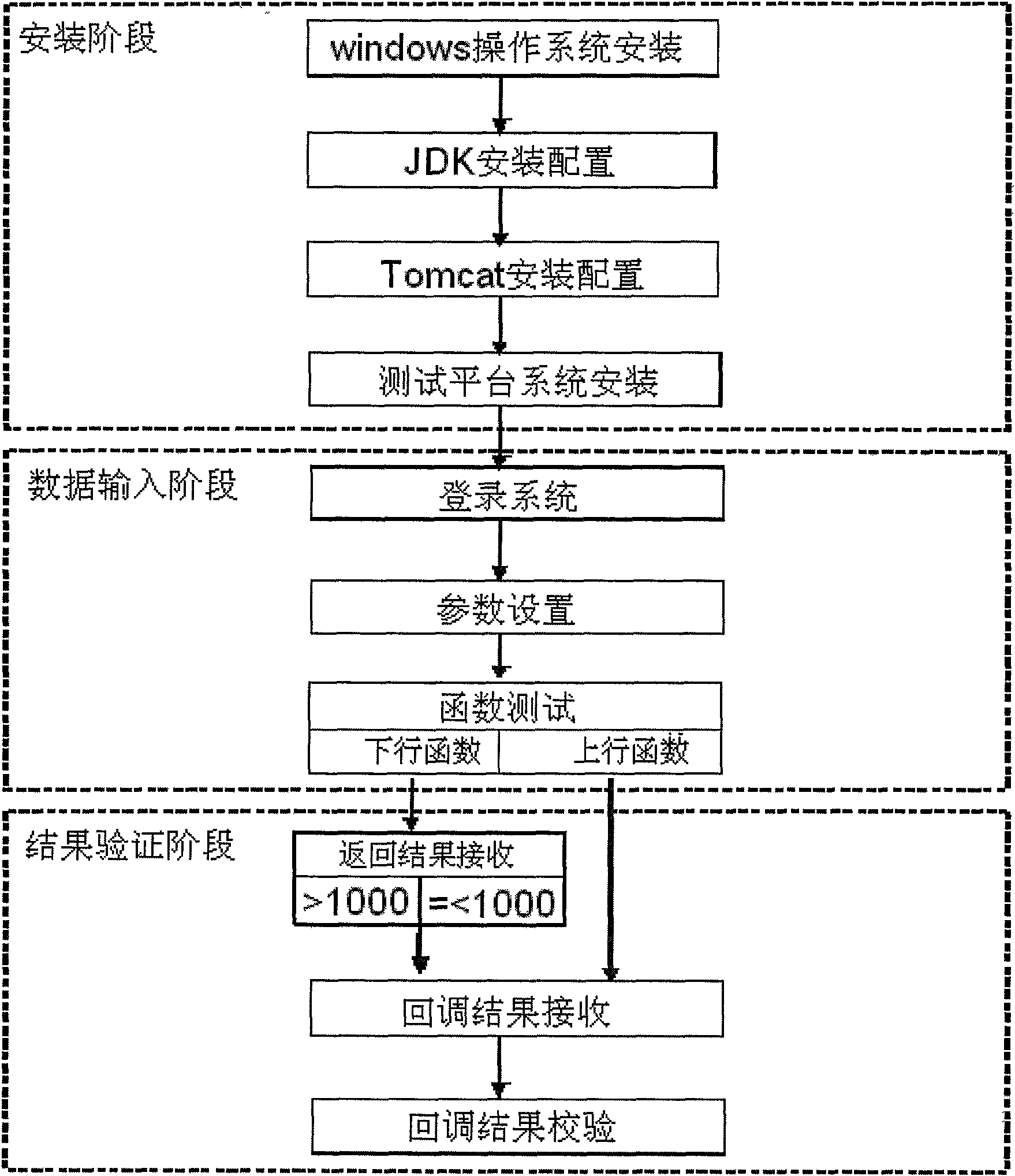
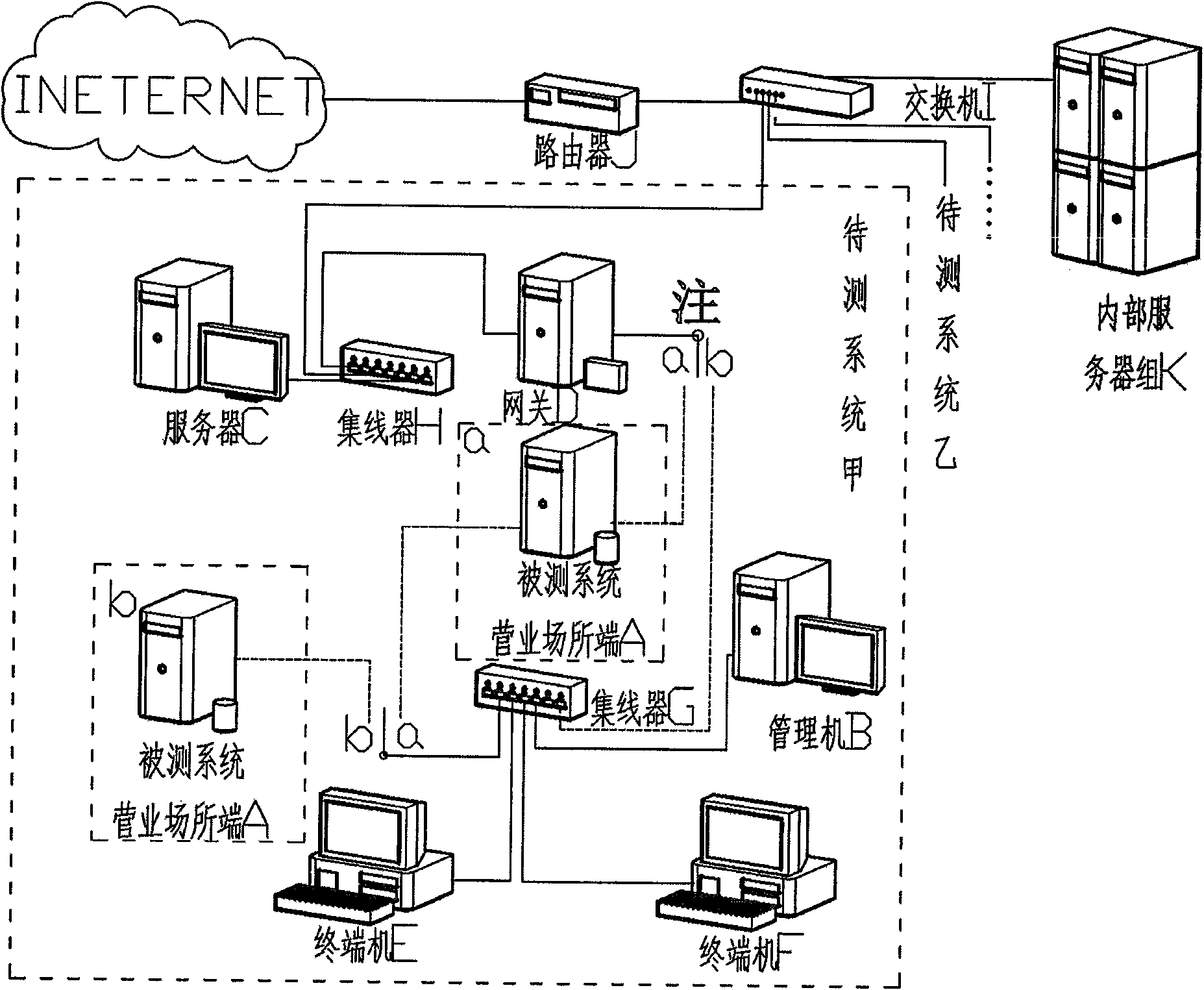
Method for testing management end interface of information security management system
InactiveCN101572632AImprove efficiencyEnsure consistencyData switching networksTest managementEmbedded system
The invention discloses a method for testing a management end interface of an information security management system, which comprises the following steps: (1) constructing a testing environment; (2) setting parameters of a server; (3) according to the set related parameters, calling related interface functions of a management end; (4) if the calling is successful, returning results obtained by the operation of the interface functions according to the related parameters by the management end; and (5) comparing the returned results by using related standards to judge whether the related interface functions of the management end accord with the requirement. The method can ensure the high efficiency, consistency, reproducibility and comparability of the testing.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Locating documents for providing data leakage prevention within an information security management system
InactiveUS20120084868A1Prevent leakageDigital data processing detailsAnalogue secracy/subscription systemsPaper documentDocument preparation
A method for locating documents has a step of, on each entity of the plurality of document-storing entities, calculating a respective fingerprint for each document of the documents stored on the entity, a step of transferring the calculated fingerprints by the entities to a data localization server having a fingerprint database for storing the transferred fingerprints, and a step of, at the data localization server, locating copies of a specimen document by calculating a fingerprint of the specimen document and comparing the calculated fingerprint of the specimen document with the fingerprints stored in the fingerprint database.
Owner:IBM CORP
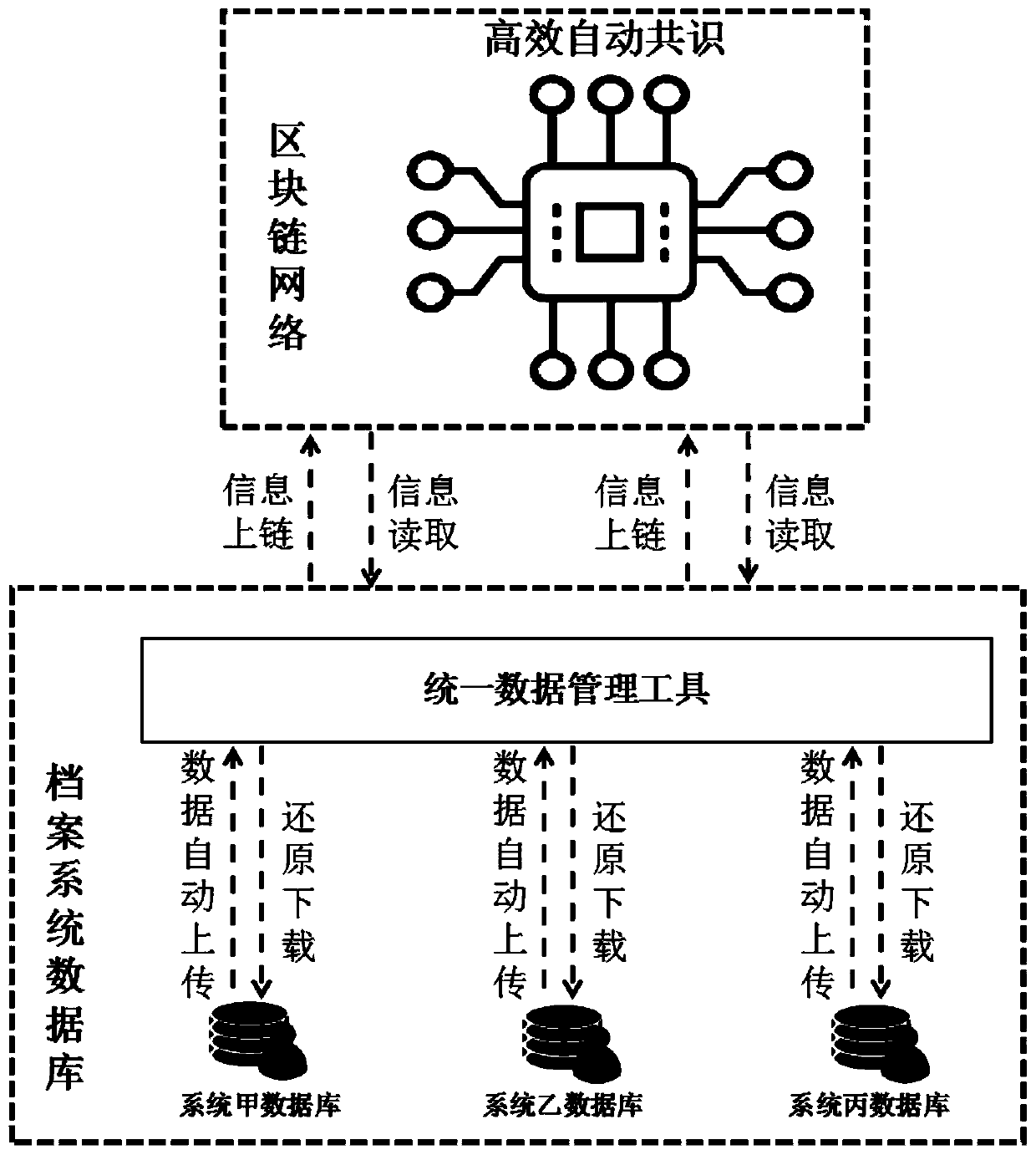
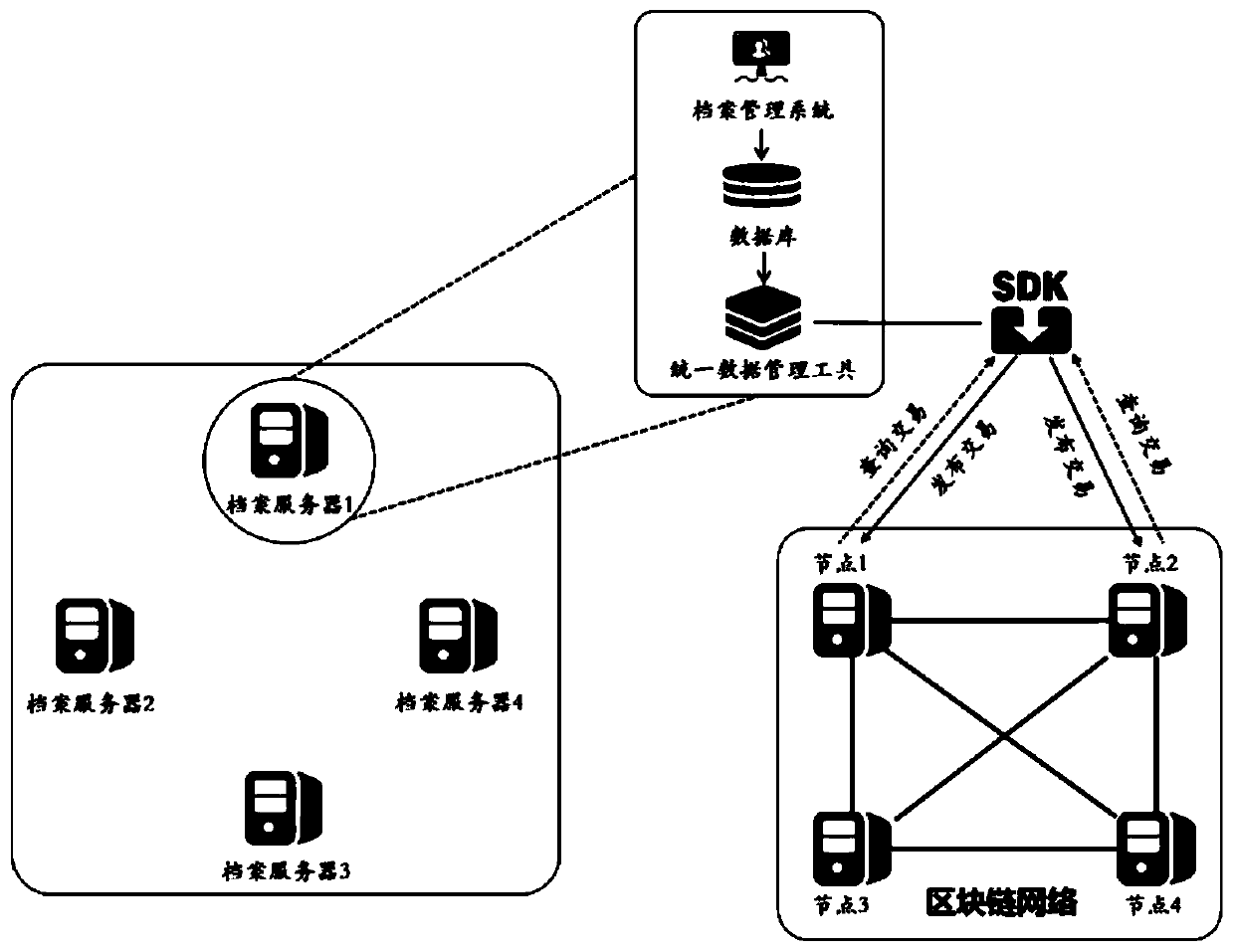
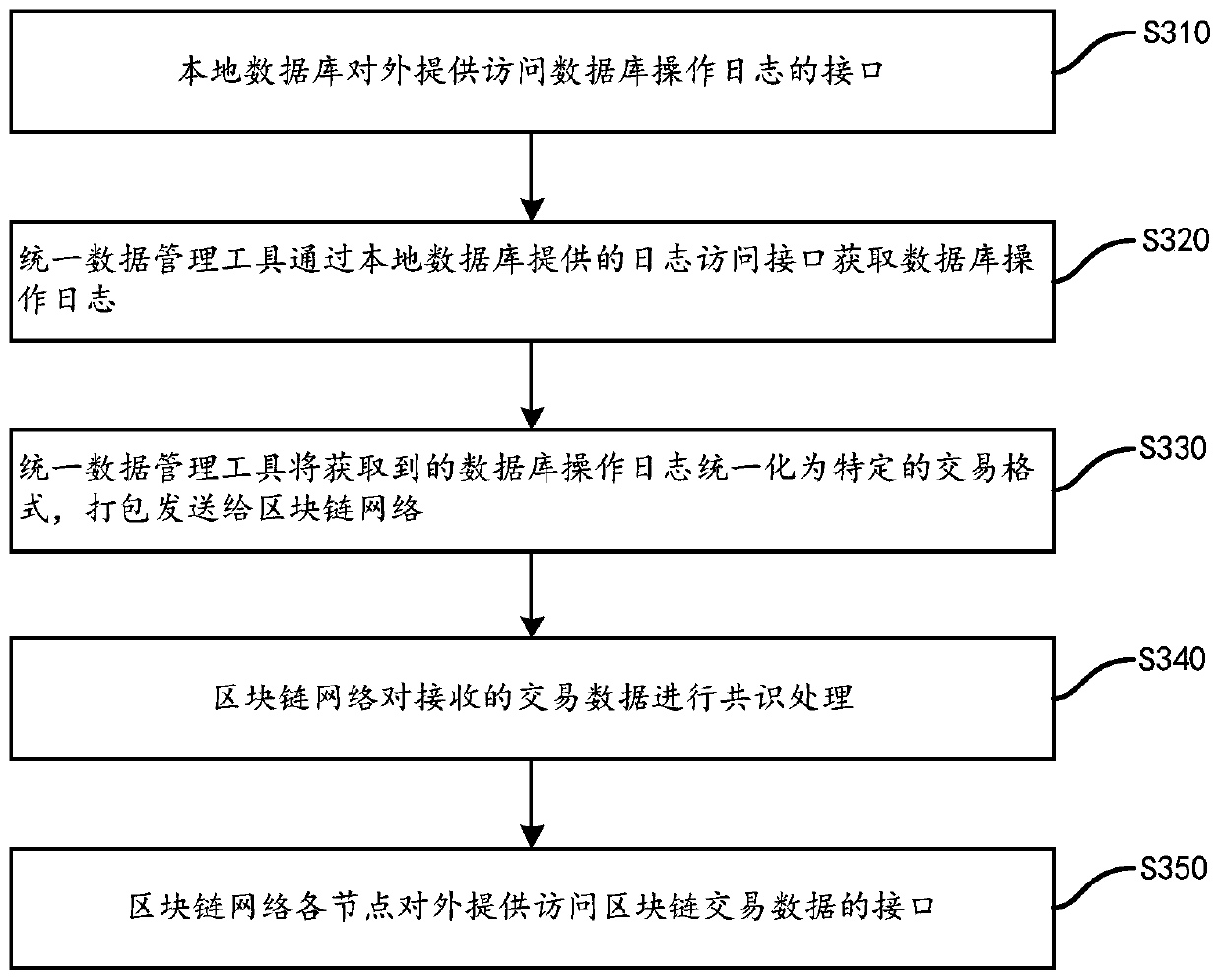
Archive information security management system and method based on blockchain
PendingCN110781525AStrong expandabilityImprove versatilityDigital data protectionManagement toolFile system
The invention provides an archive information security management system and a method based on a blockchain. The system comprises a unified data management tool, a local file system database and a blockchain network, the unified data management tool is configured to be in communication connection with a local archive system database and adapt to various types of archive databases. The blockchain network comprises a plurality of nodes which are in communication connection with one another and performs information interaction with the unified data management tool, and the unified data managementtool acquires an operation log of the local file system database and unifies the operation log into transaction data to be published to the blockchain network; the blockchain network performs signature verification and transaction data consensus on the received transaction data; and the unified data management tool operates the local file system database according to the transaction result. According to the system, efficient and automatic database log consensus is realized, and support is provided for file integrity authentication, operation tracing and file data backup.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
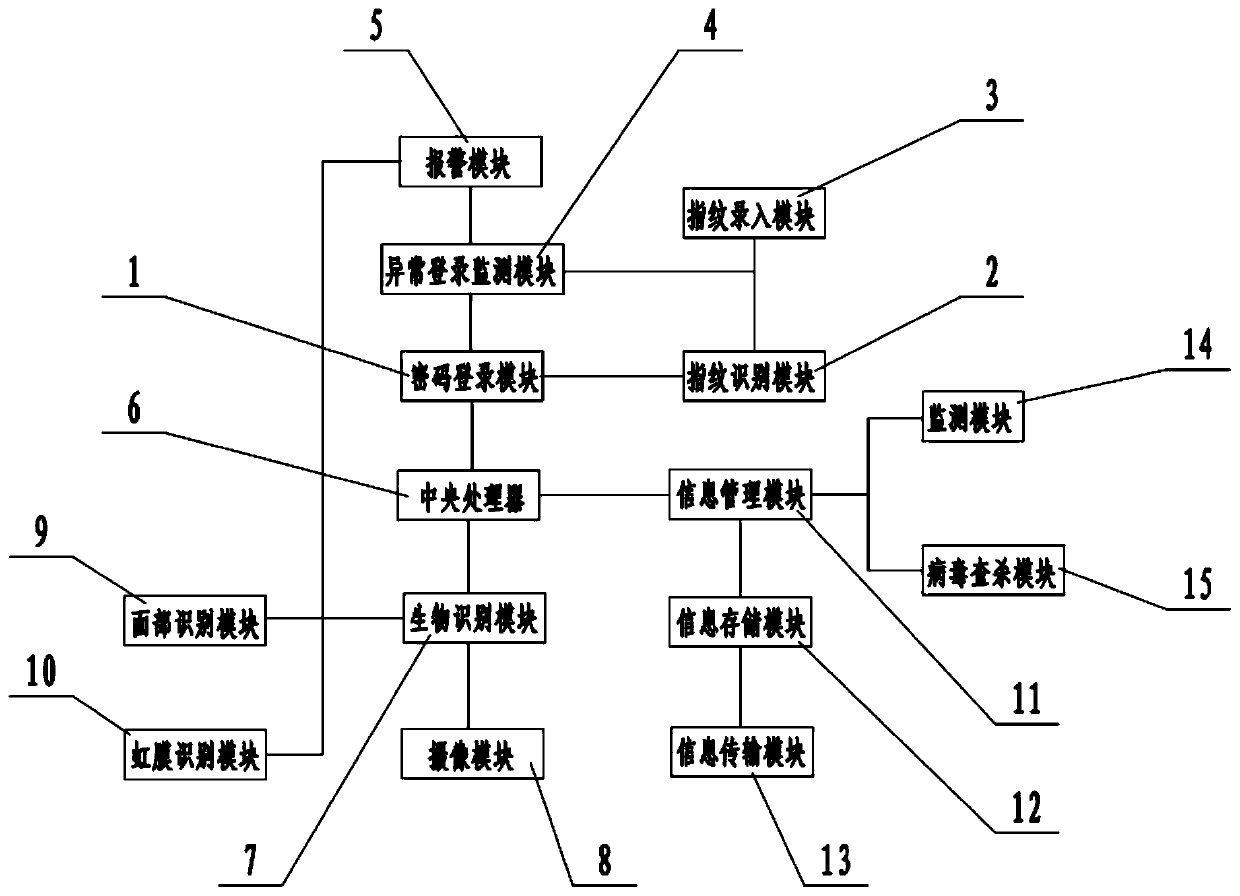
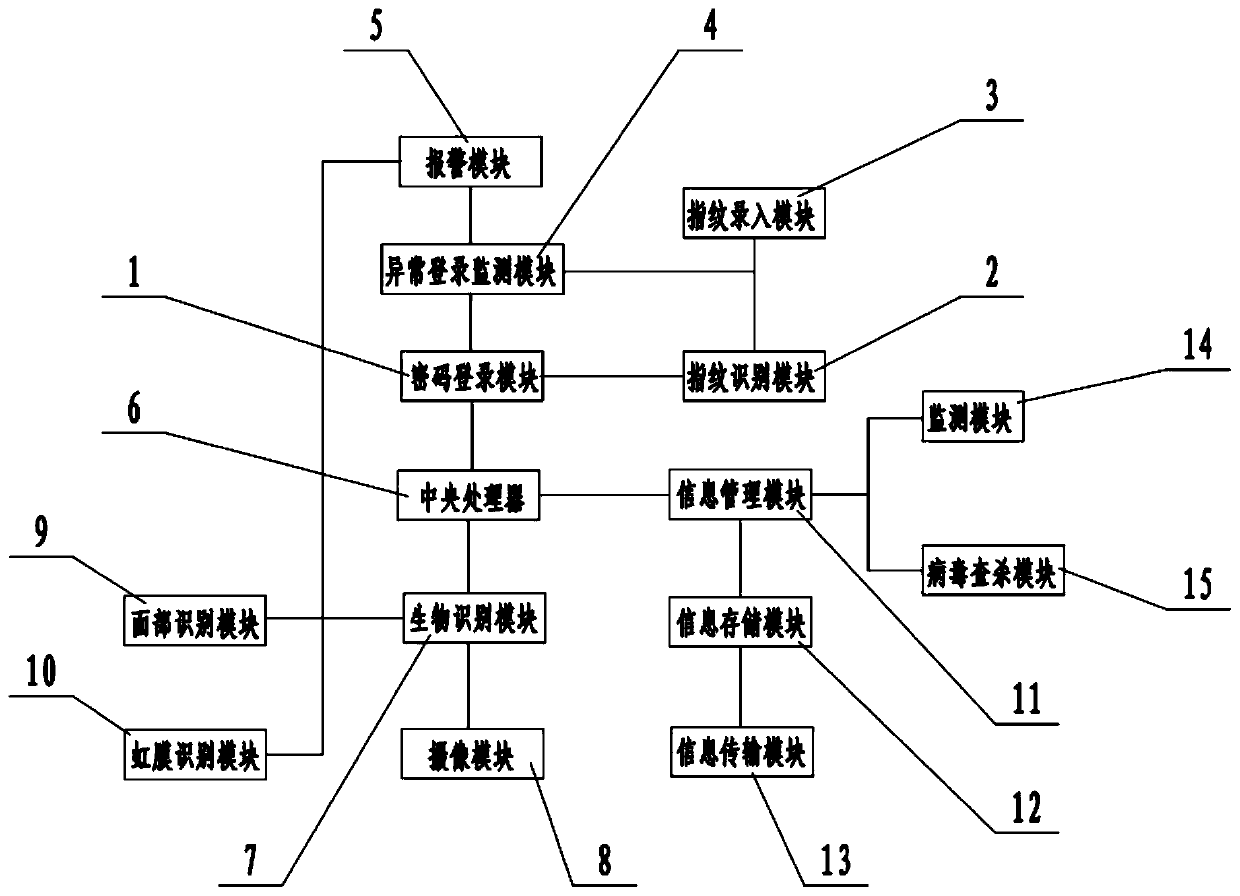
A computer information security management system and method
PendingCN109711126AImprove securityDigital data authenticationPlatform integrity maintainanceInformation transmissionPassword
The invention relates to the technical field of Internet. More specifically, the invention relates to a computer information security management system and method. The system comprises a password login module, a fingerprint identification module, a fingerprint input module, an abnormal login monitoring module, an alarm module, a central processing unit, a biometric identification module, a cameramodule, a facial recognition module, an iris recognition module, an information management module, an information storage module, an information transmission module, a monitoring module and a virus searching and killing module. According to the invention, the password login module is arranged; combined with the fingerprint identification module, when the user inputs a password, the fingerprint ofthe user is identified to confirm the identity of the user, the safety is greatly improved, the safety is further improved by arranging the biological identification module, dynamically monitoring theuser and identifying the identity of the user, and the virus searching and killing module is independently arranged to search and kill the system, so that the safety is further improved.
Owner:HUANGHE S & T COLLEGE
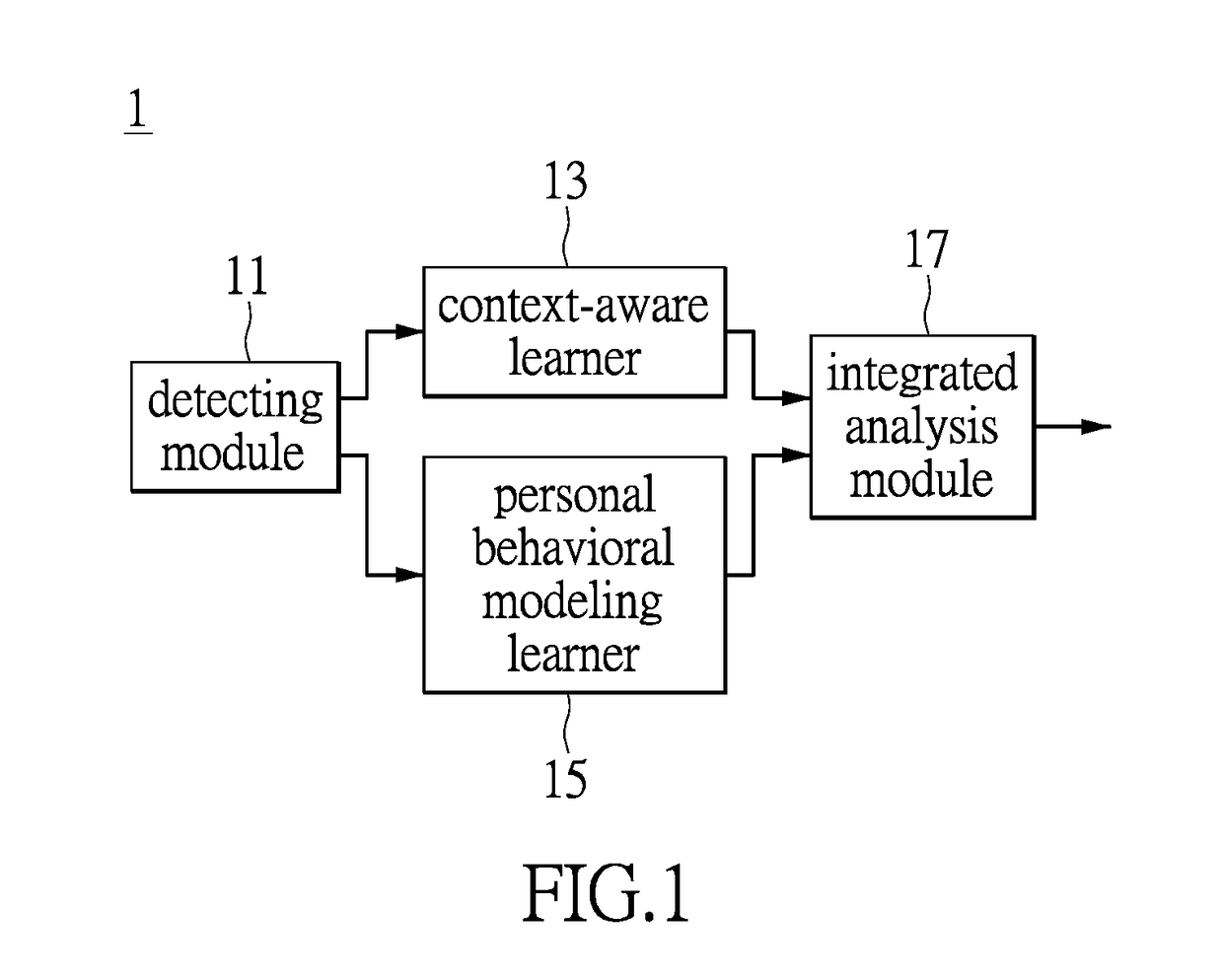
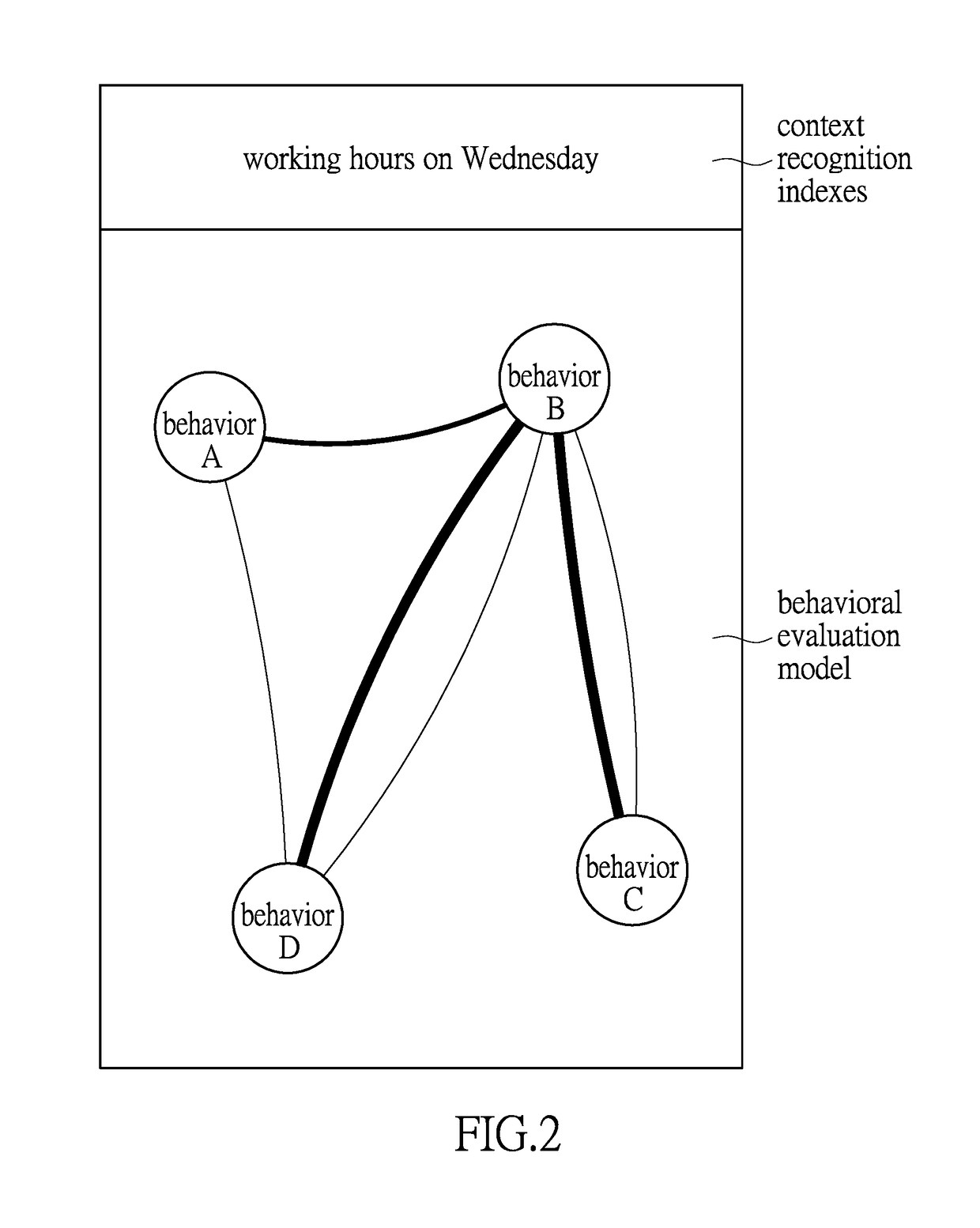
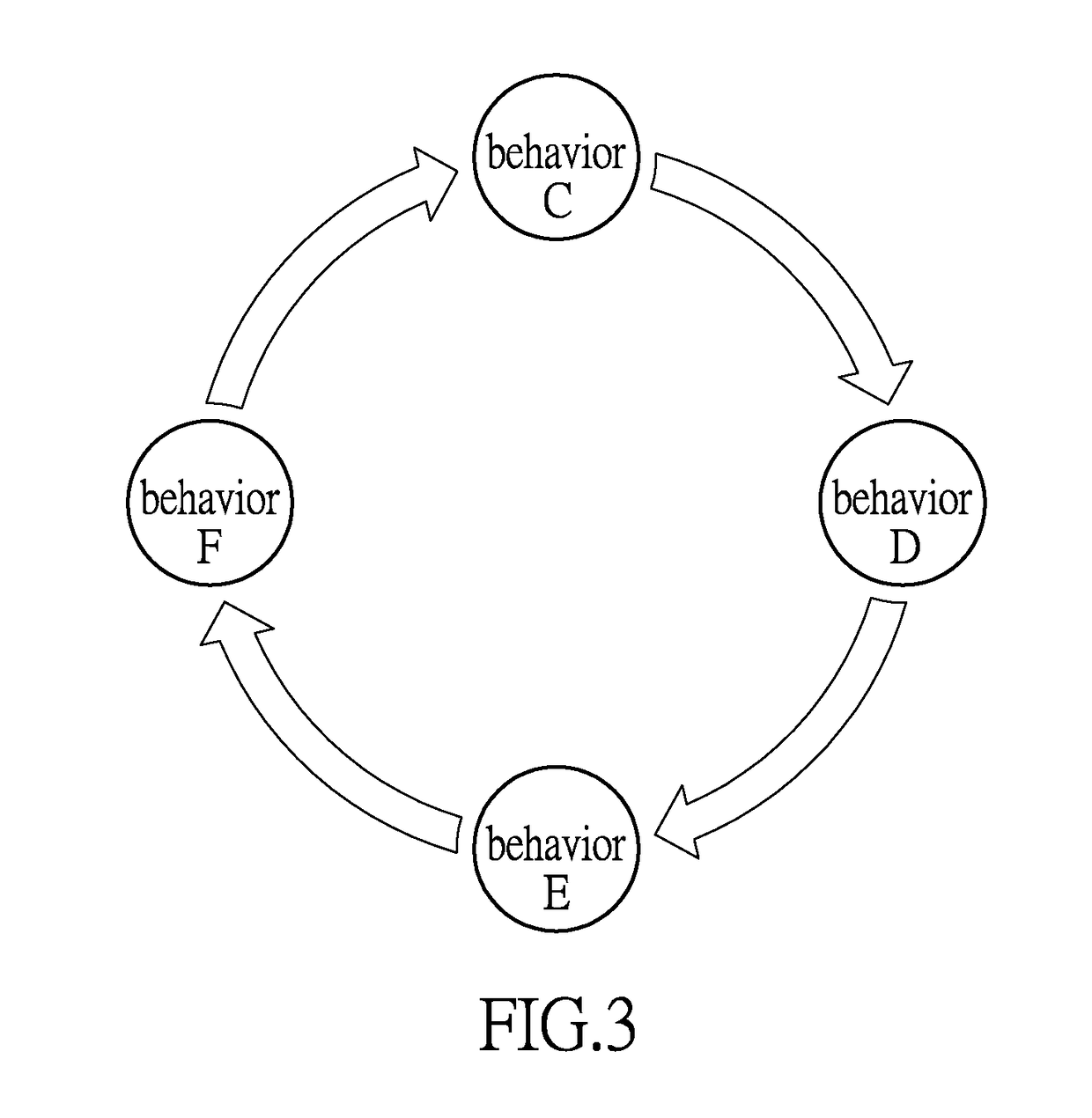
System and method for information security management based on application level log analysis
InactiveUS20170149800A1Effective judgmentImprove accuracyTransmissionSecurity arrangementInformation security risk managementInformation security management
The instant disclosure illustrates a system and method for information security management based on application level log analysis. The system and method for information security management involve analyzing a plurality of application level logs of a user and modeling the continuative behaviors of the user. Furthermore, the system and method for information security management include the selection of models according to different environmental contexts, thereby efficiently determining whether the user has had an abnormal behavior occur.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Information security management and control system and information security management and control method
InactiveCN107171855AMeet Internet needsPrevent Mobile Security AccidentsData switching networksData connectionInformation security risk management
The invention discloses an information security management and control system comprising a virtual private dialup network module, an intranet management and control module and a hardware prevention and control module, wherein the virtual private dialup network module is in data connection with the intranet management and control module, the hardware prevention and control module is in data connection with the intranet management and control module, and the hardware prevention and control module is in data connection with an external Internet. According to the information security management and control system and the information security management and control method provided by the invention, a set of comprehensive security management and control system is established for the network access of user terminals, the network management and control means and the wireless communication technology are fully used to effectively manage and control the network access behaviors and the network access time periods of the user terminals, potential security threats of network access, instant messaging and the like are mainly solved, the user terminals are used for performing network access within proper and regular time periods, and meanwhile public sentiment statistic analysis is carried out so as to carry out targeted education and guidance, prevent the occurrence of mobile security accidents and meet the network access needs of special groups.
Owner:山东掌游网络科技有限公司
Information security monitoring system
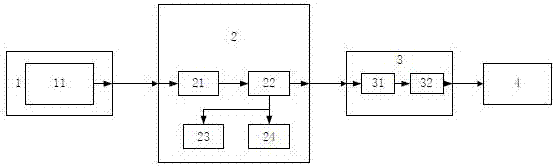
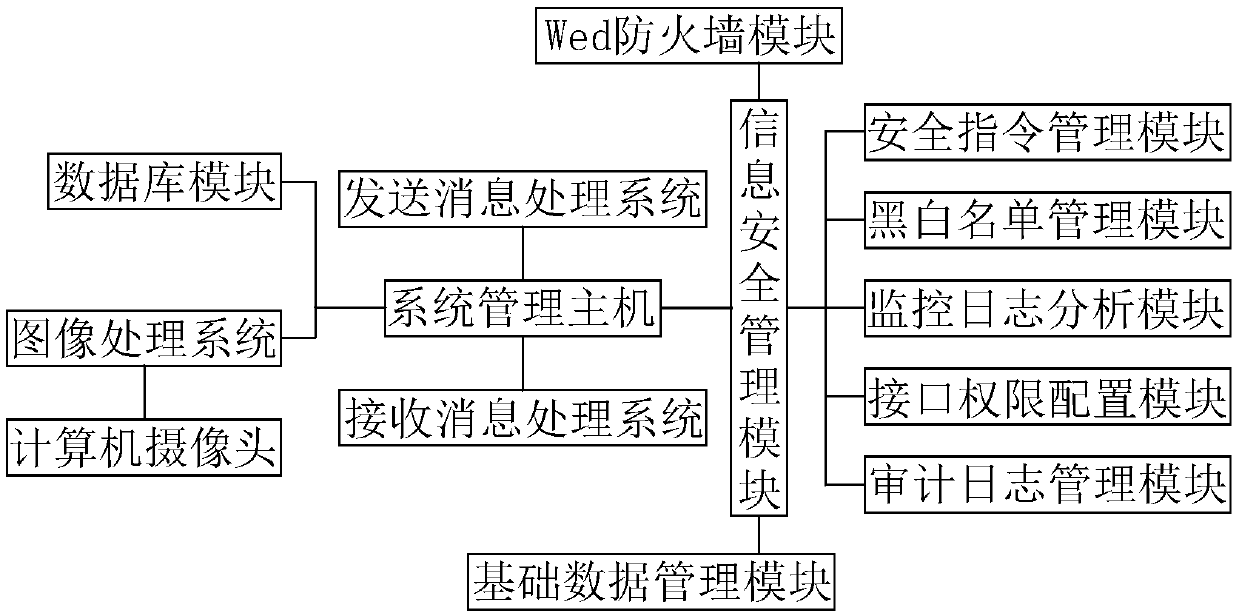
ActiveCN109639742ASend blockAvoid spreadingTransmissionSystems managementInformation security management
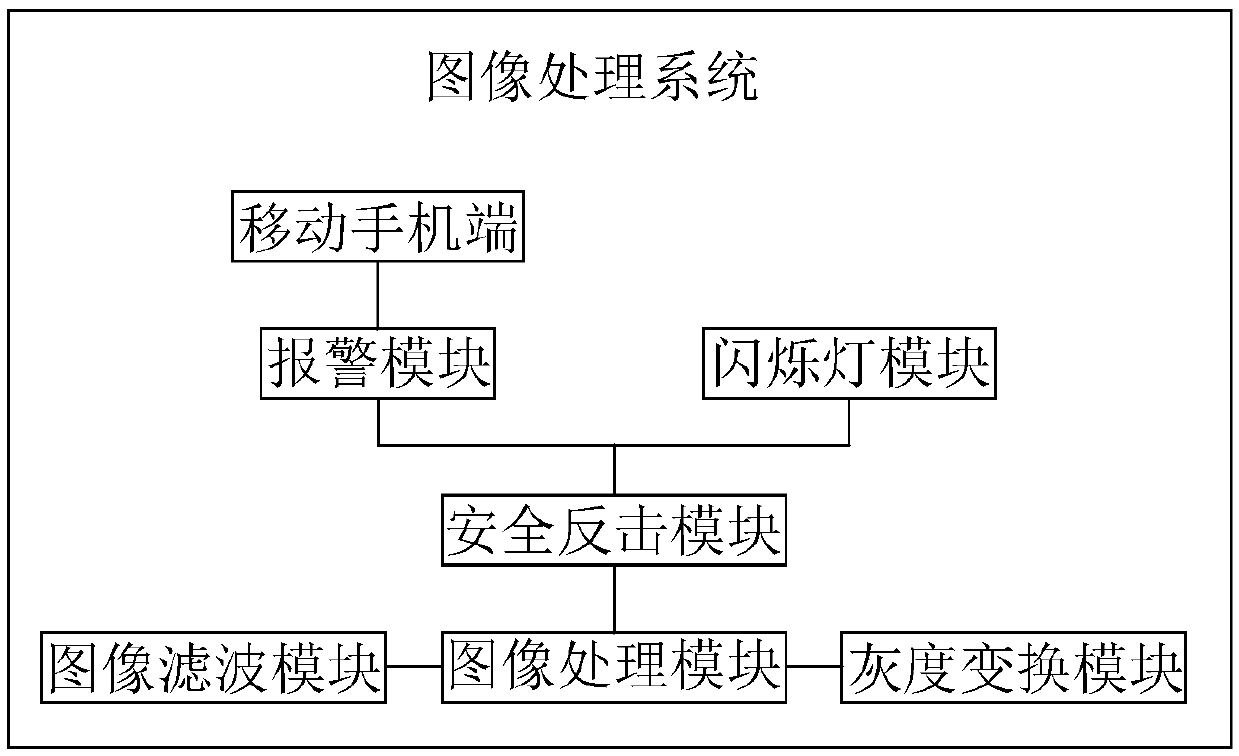
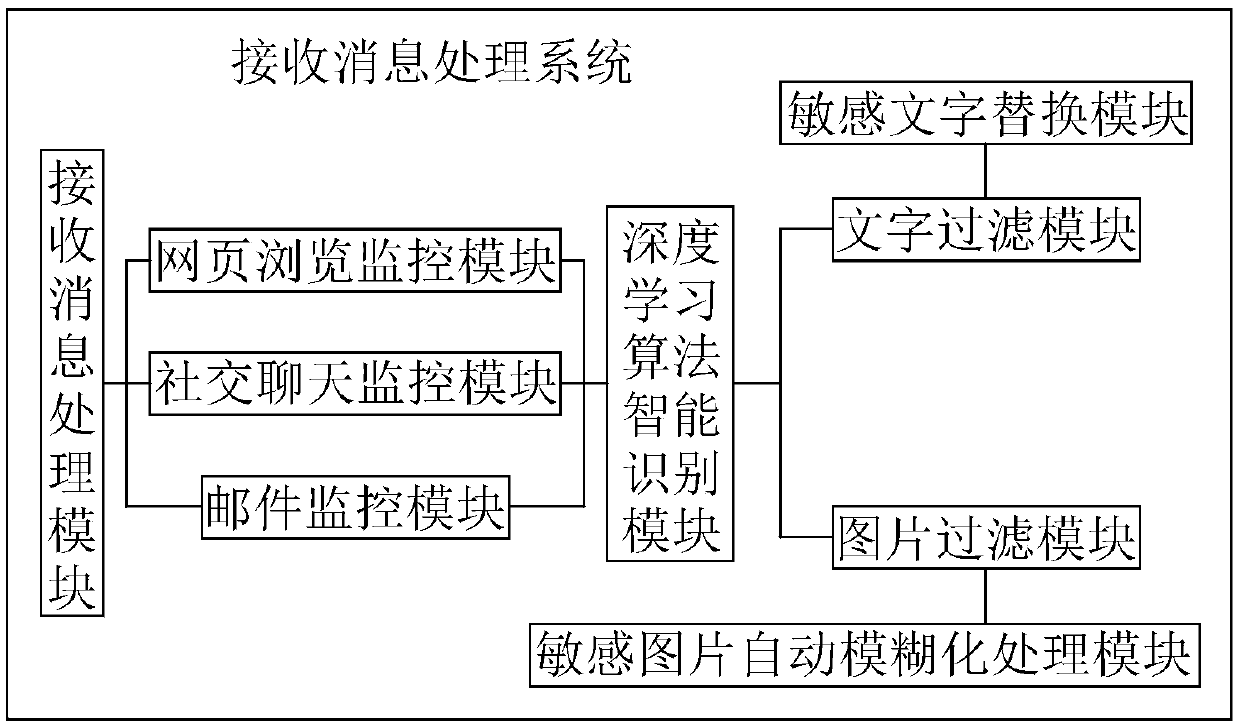
The invention relates to the technical field of network security, and in particular relates to an information security monitoring system comprising a system management host that is separately connected with an information security management module, a database module, a sent message processing system and a received message processing system; the received message processing system is used for processing received messages; and the received message processing system comprises a received message processing module that is connected with the system management host via a signal. According to the system provided by the invention, character filtering treatment and picture filtering treatment are performed on received content to completely deal with sensitive characters and sensitive pictures, so that the people can be prevented from receiving pornographic and violent contents; through monitoring messages sent by the people, and stopping the sending of the sensitive characters and the sensitivepictures, the people can be prevented from propagating the pornographic and violent contents; the system can well achieve the purpose of preventing the pornographic and violent contents from being propagated, and thus the security of the network information is achieved.
Owner:WENZHOU UNIVERSITY
Intelligent production park management system
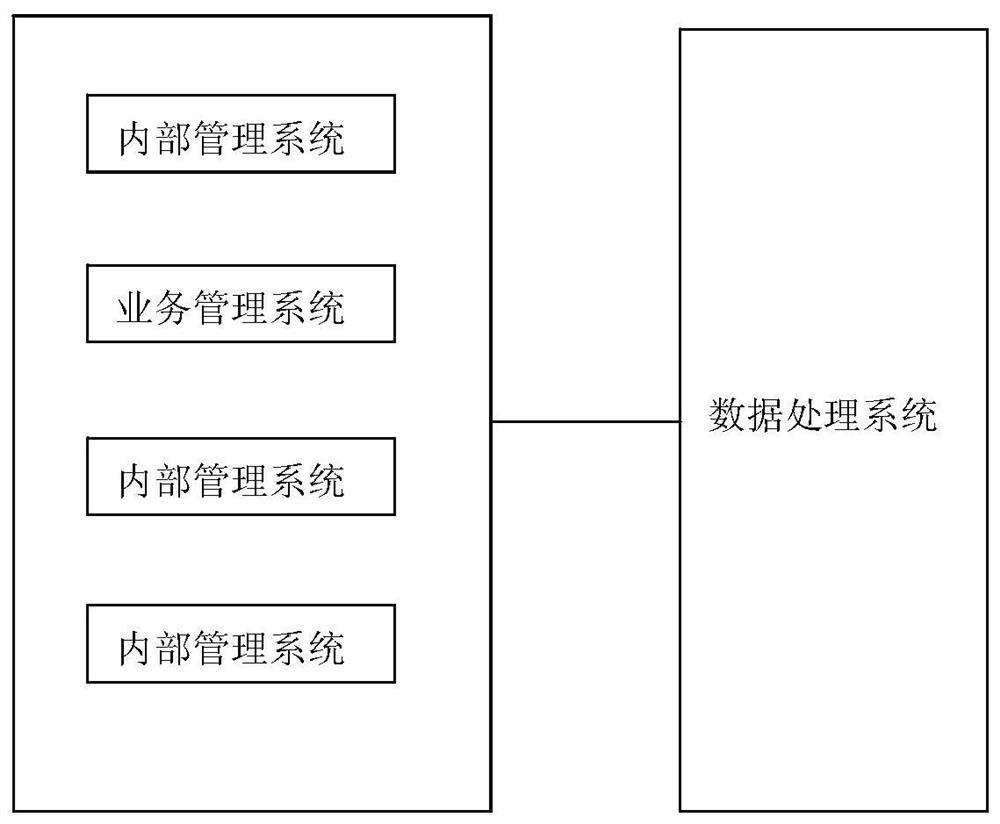
PendingCN112132535ARealize unified managementReal-timeOffice automationLogisticsInternal managementSafety management systems
The invention, which relates to the technical field of the intelligent production park, provides an intelligent production park management system comprising: an internal management system for storingand managing various information inside an enterprise; the business management system that is used for storing and managing various information of external business of an enterprise; the safety management system that is used for monitoring and managing safety conditions of various scenes in an enterprise; and the system management system that is used for setting, storing and managing the system ofthe whole management platform. The intelligent management system for the production park comprises a plurality of different types of management subsystems, the subsystems are managed in a unified andcentralized mode, the relation between the subsystems is established, and unified management and real-time supervision of people, vehicles and objects in the whole production park can be achieved.
Owner:ZHEJIANG WEIYI IND
Information security management system and multifunction printer using the same
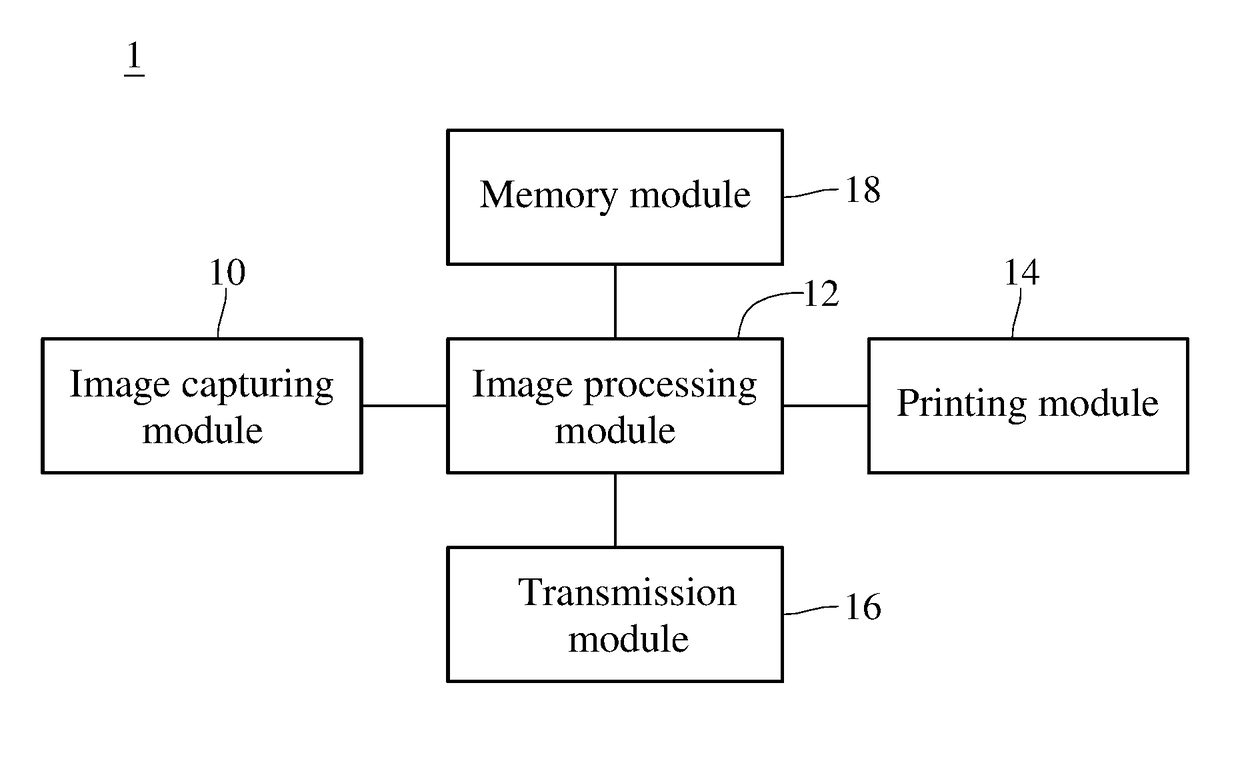
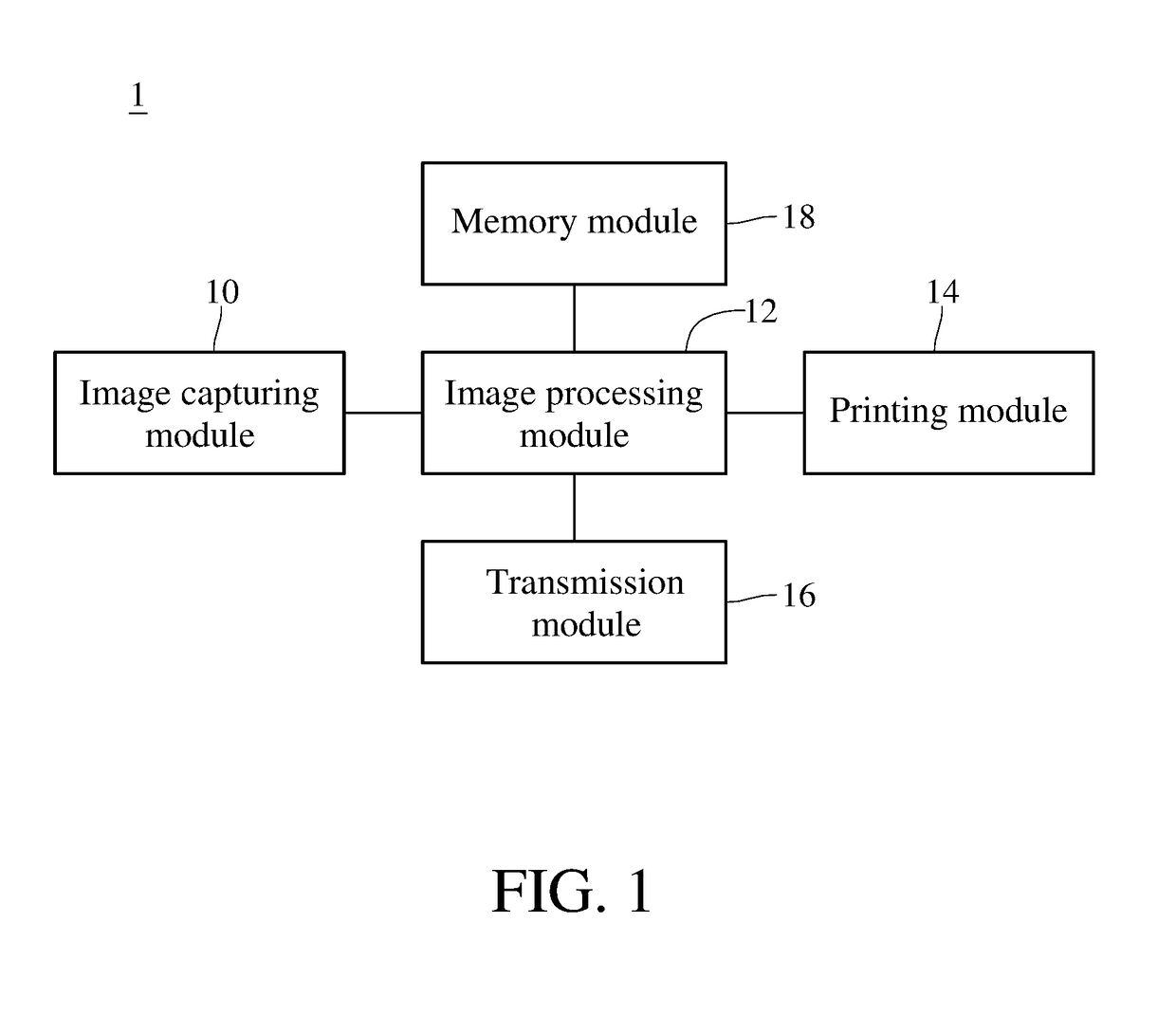
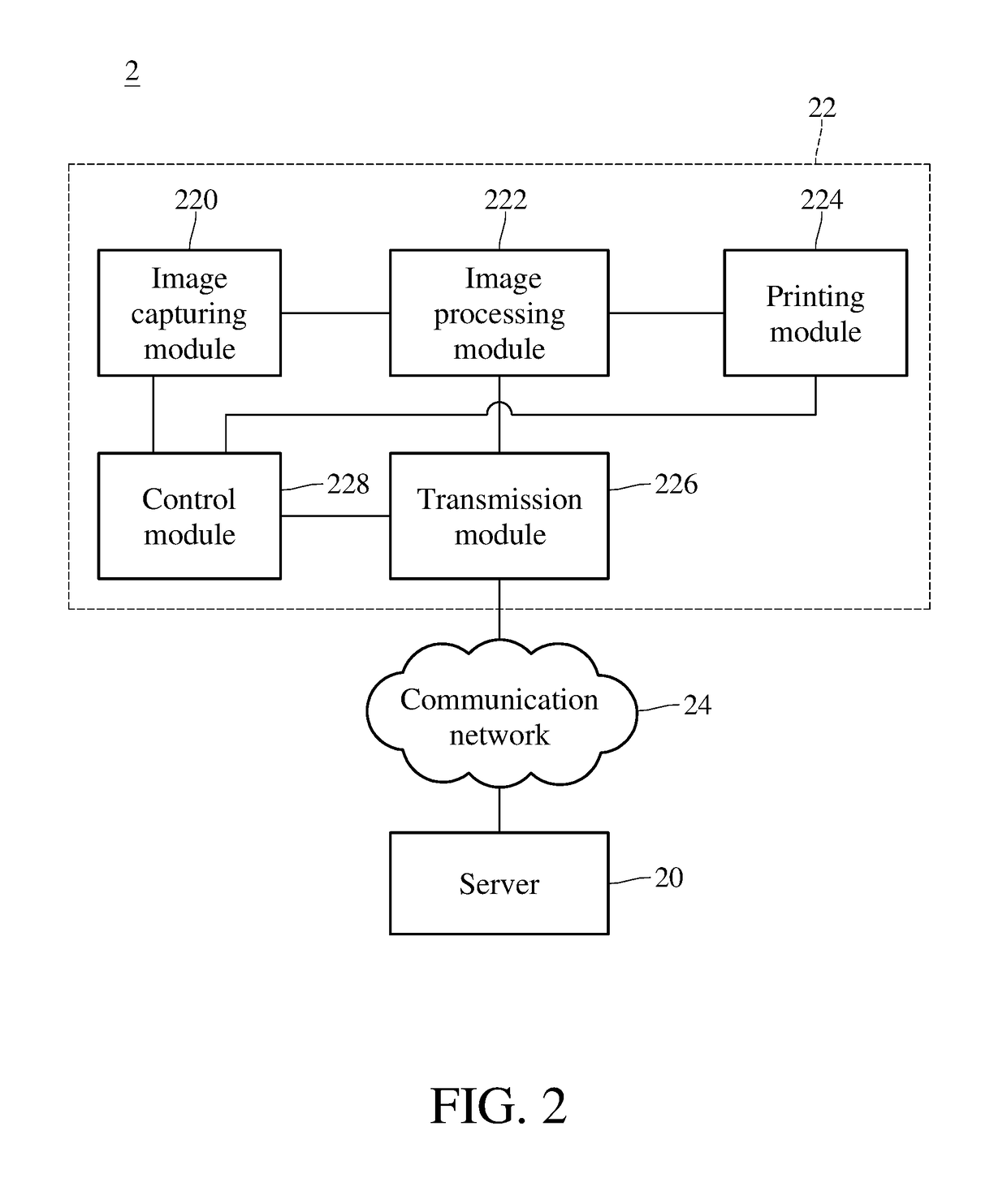
ActiveUS20180293019A1Improve abilitiesReduce the possibilityInput/output to record carriersCharacter and pattern recognitionImaging processingComputer module
An information security management system and a multifunction printer thereof are provided. The multifunction printer includes an image capturing module, an image processing module, an output module and a transmission module. The image capturing module captures a data image of a document paper. The image processing module is coupled to the image capturing module and encodes the data image to generate first encoded data. The output module is coupled to the image processing module and prints second encoded data related to the data image. The transmission module is coupled to the image processing module and transmits one of the first and second encoded data. The multifunction printer deletes the first encoded data from a memory after transmitting the first encoded data, and deletes the second encoded data from the memory after transmitting / outputting the second encoded data.
Owner:AVISION
Information security management system
InactiveUS20080005131A1Improve developmentEasy procedureDigital data processing detailsOrganizational impactTechnical standard
An information security management system and tool for developing standards and procedures related to those standards across an organization. The system of the invention takes proposed information technology (IT) requirements for an organization and rationalizes these requirements as standards or procedures or rejects the requirements as neither a standard nor a procedure. Each proposed standard is scored for its relationship to a rule, the risk to the organization from failing to comply with the requirement and the operational impact on the organization. Proposed procedures are also scored for organizational impact. The rationalization score and risk score for the standard to which the procedure relates are also used to score the procedures. Each standard is linked to the rule on which it is based and each procedure is linked to the standard it supports.
Owner:BANK OF AMERICA CORP
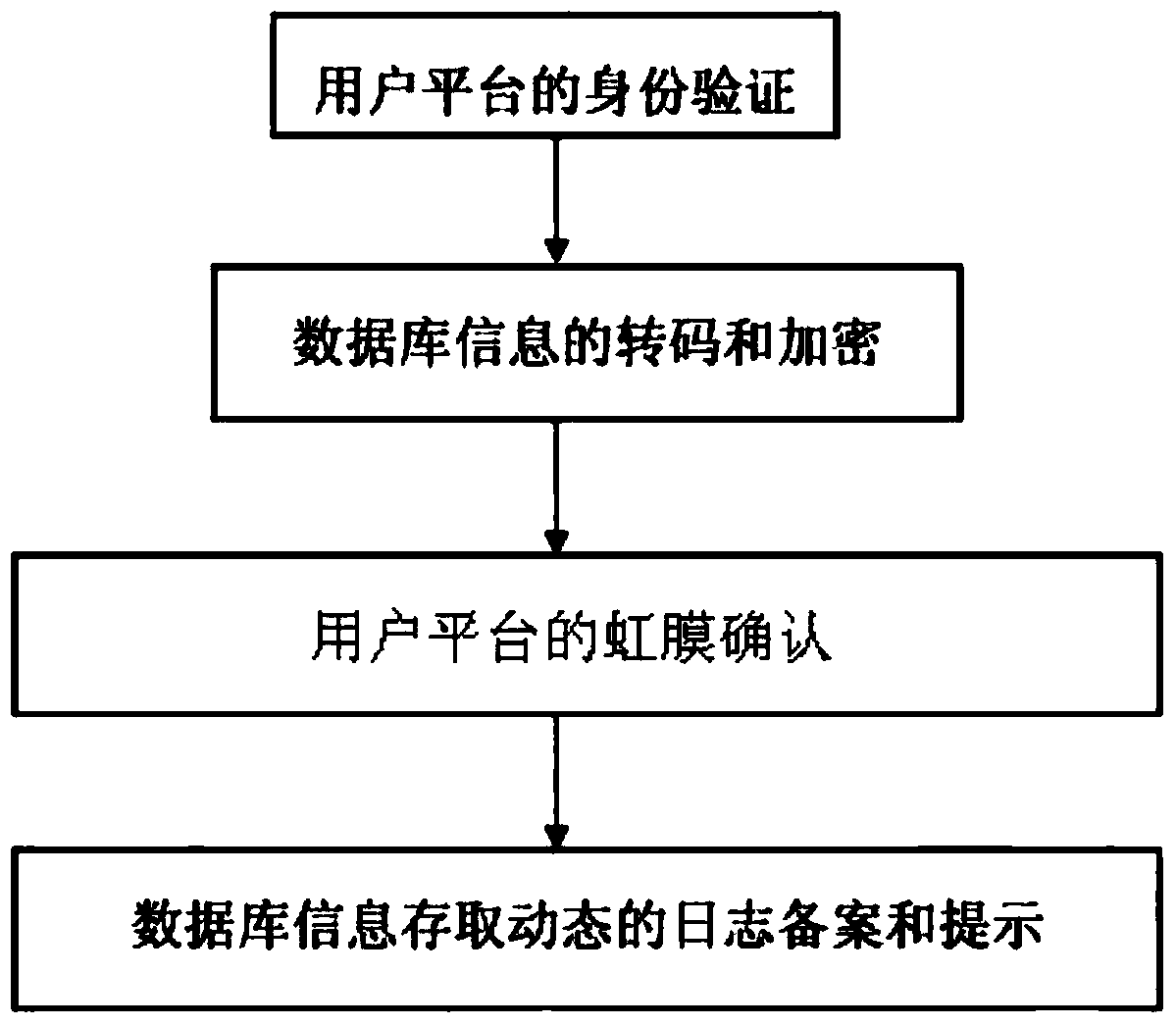
Information security management method
InactiveCN103699828ADigital data protectionDigital data authenticationInformation security risk managementInformation security management
The invention relates to an information security management method. The information security management method comprises the following steps of (1) authentication of a user platform, (2) transcoding and encryption of information of a database, (3) iris confirmation of the user platform, and (4) log filing and prompting on information storage and retrieval dynamic states of the database. By using the information security management method, the problem that information management is not safe in the prior art is solved.
Owner:柳州市欧博科技有限公司
Method of managing information security program maturity
InactiveUS20200342374A1Effective displayEfficient managementFinanceDigital data protectionSafety management systemsEngineering
Disclosed is a method of more effectively managing and displaying an Information Security Management System (ISMS), or Cybersecurity Framework, by an application executing on a computer device for computing and displaying real time dynamic metrics and market comparison for the User. The method includes authenticated and authorized Users to conduct security baselines based on industry accepted standards in order to establish a plurality of metric baselines dynamically and in real time. The method further includes projects submitted to be measured against organizational goals and simulate the impact to the Security baselines. The method further includes the ability to provide financial visibility into the financial exposure of a Security Breach, or Data exfiltration and other available financial metrics. The method further includes a platform by which companies may request Virtual CISO's services from a pool of executive level resources.
Owner:V3 CYBERSECURITY INC
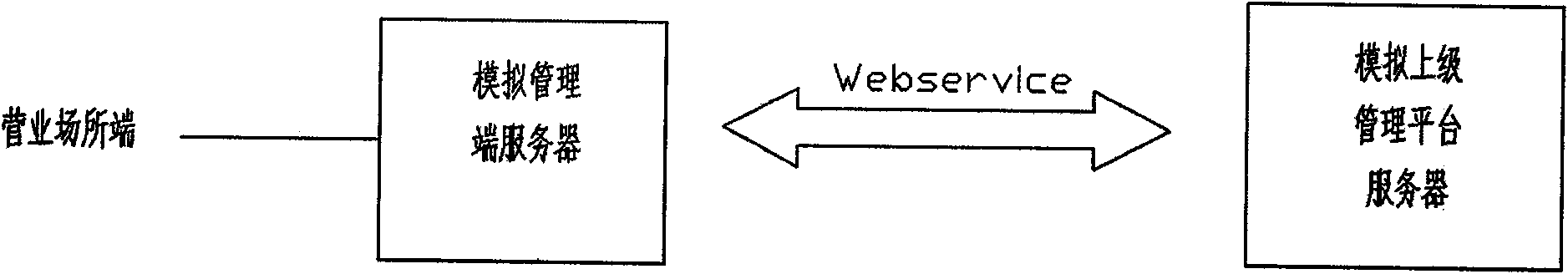
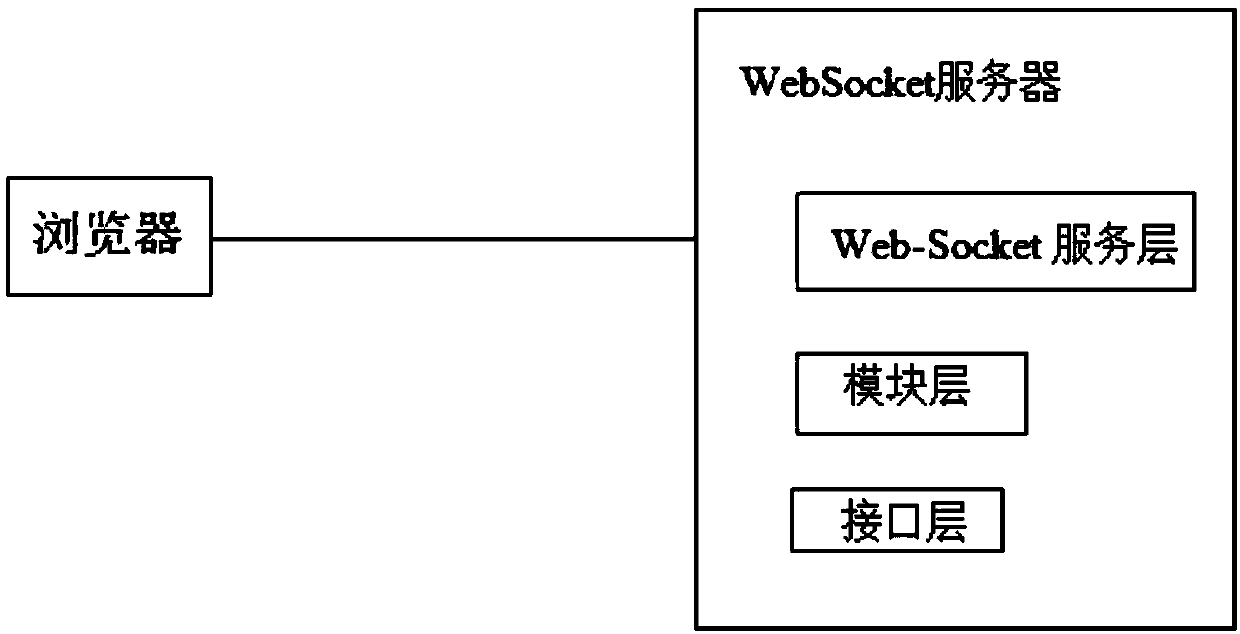
Information security management system
An information security management system comprises a browser and a WebSocket server, wherein the browser needs to support an HTML5 technical standard, the WebSocket server is realized based on a layered architecture, the system comprises a Web-Socket service layer, a module layer and an interface layer from top to bottom, the browser is used as an interactive display page of the security system client, through a WebSocket API of an HTML5 standard, safe communication with the WebSocket service is realized on the basis of a WSS protocol, the WebSocket service layer monitors the connection of the browser based on the WebSocket protocol, responds to an access request of the browser to the security hardware so that protocol interaction with the browser is completed, the module layer is used for realizing decoupling between different services and supporting expansion of service types, and the interface layer is mainly used for packaging an operation interface of the external security hardware and providing a unified access interface for the upper module layer.
Owner:武汉新软科技有限公司
Information security management system based on big data
ActiveCN111784989AEnsure safetyAvoid safety hazardsNetwork topologiesAlarmsData acquisitionInformation security
The invention provides an information security management system based on big data. The information security management system comprises a data acquisition module, a big data analysis module and a safety prompt module, wherein the big data acquisition module is used for acquiring state data of equipment in a machine room and environment data of the machine room and sending the state data and the environment data to the big data analysis module; the big data analysis module is used for judging whether the numerical value of the state data and / or the environmental data is within a preset threshold interval or not, and sending a judgment result to the safety prompt module; and the safety prompt module is used for receiving the judgment result, and if the judgment result is that the numericalvalue of the state data and / or the environmental data is not in a preset threshold value interval, the safety prompt module sends a safety prompt to a machine room manager. The problem that potentialsafety hazards in the machine room cannot be found in time due to the fact that safety inspection is conducted on the machine room in a mode of regular inspection by a specially-assigned person can beeffectively solved.
Owner:安全能力生态聚合(北京)运营科技有限公司
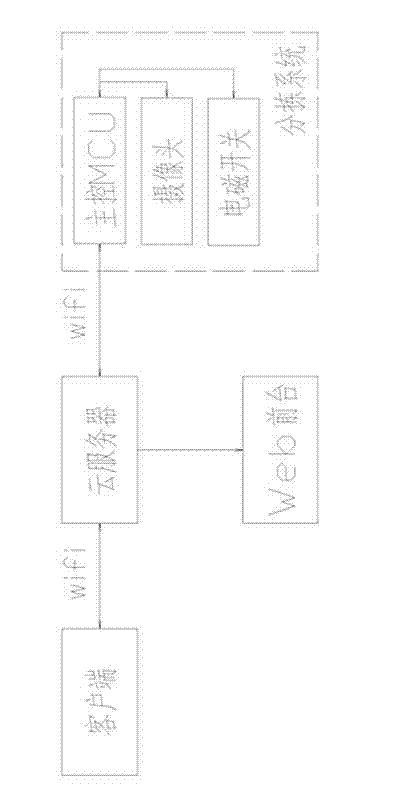
Information security management system
The invention discloses an information security management system, which is characterized in that the system comprises a client-side capable of generating two-dimensional codes, wherein the client-side is connected with a cloud server through a WiFi (wireless fidelity) network, a sorting system is also connected with the cloud server through the WiFi network, and comprises a master control unit MCU, the MCU is capable of controlling a plurality of electromagnetic switches matched with a conveying belt of the sorting system, and is also capable of controlling a camera, and the cloud server is also connected with a Web foreground through the WiFi network. The information security management system is capable of protecting client information, is convenient and safe in operation and is capable of automatically realizing information updating.
Owner:FUJIAN EADING CORE INTELLIGENT TECH
Inspection method for internet service business place information safety management
ActiveCN101465764AImprove efficiencyEnsure consistencyData switching networksDesign testingInformation security management
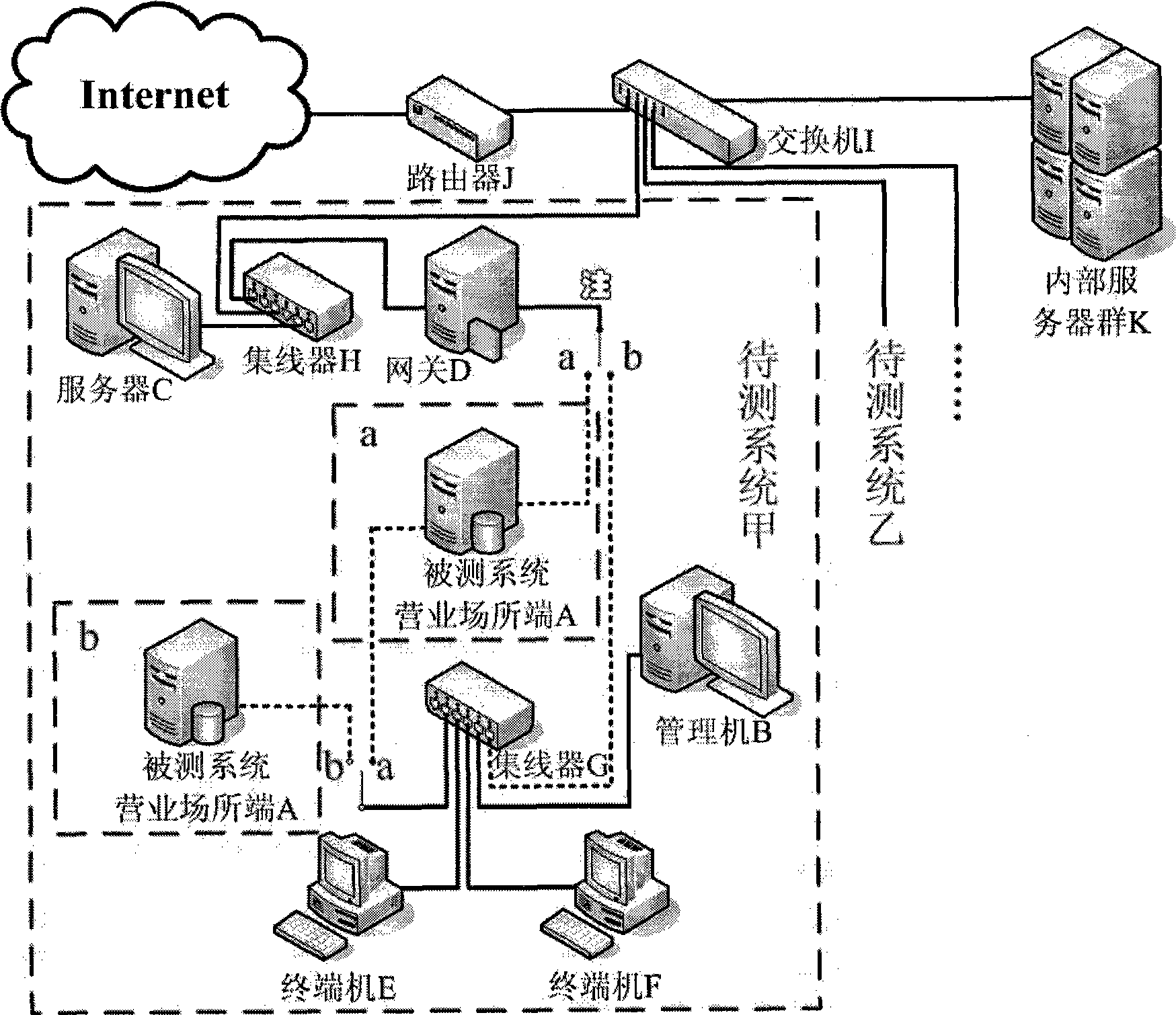
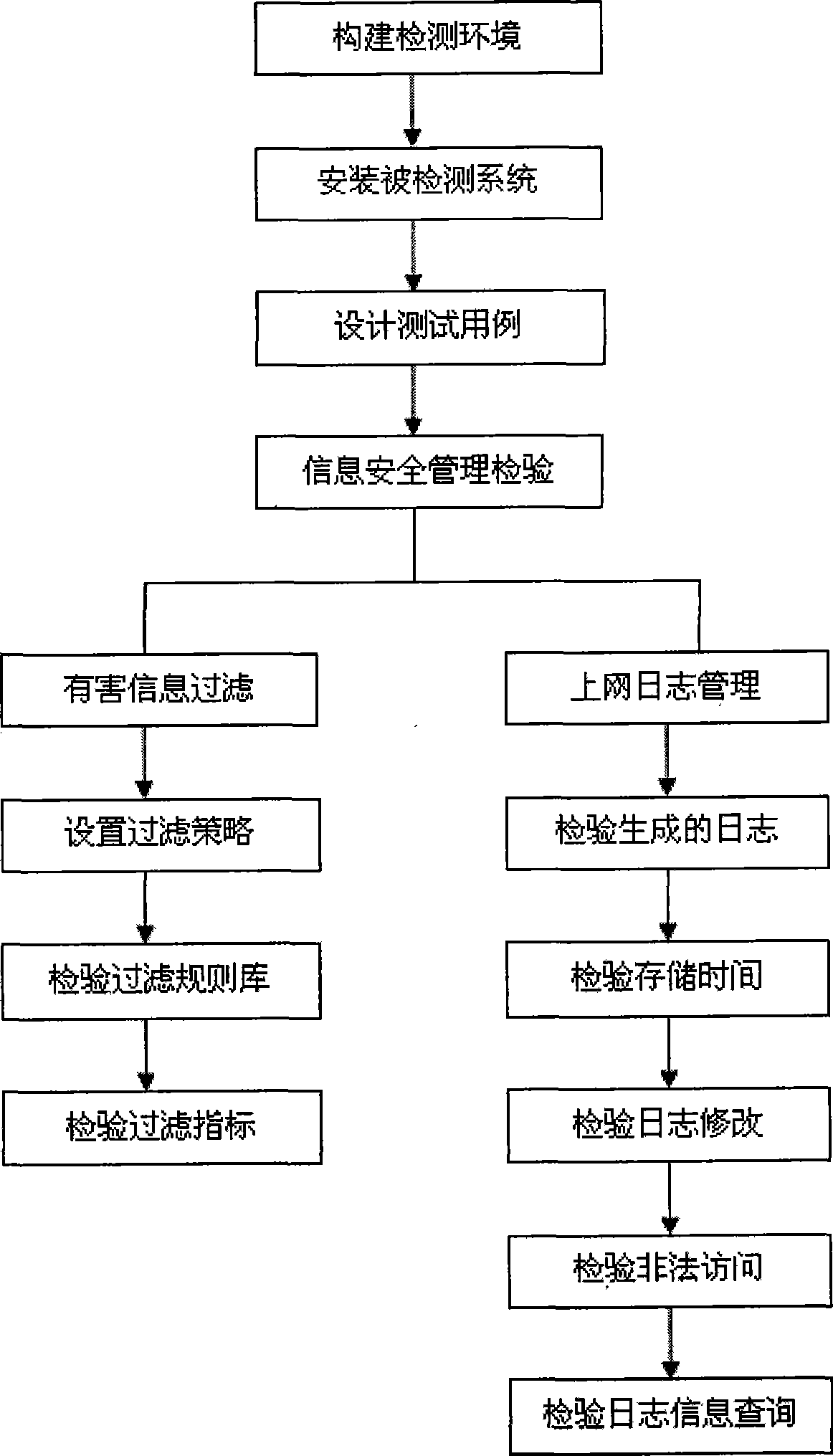
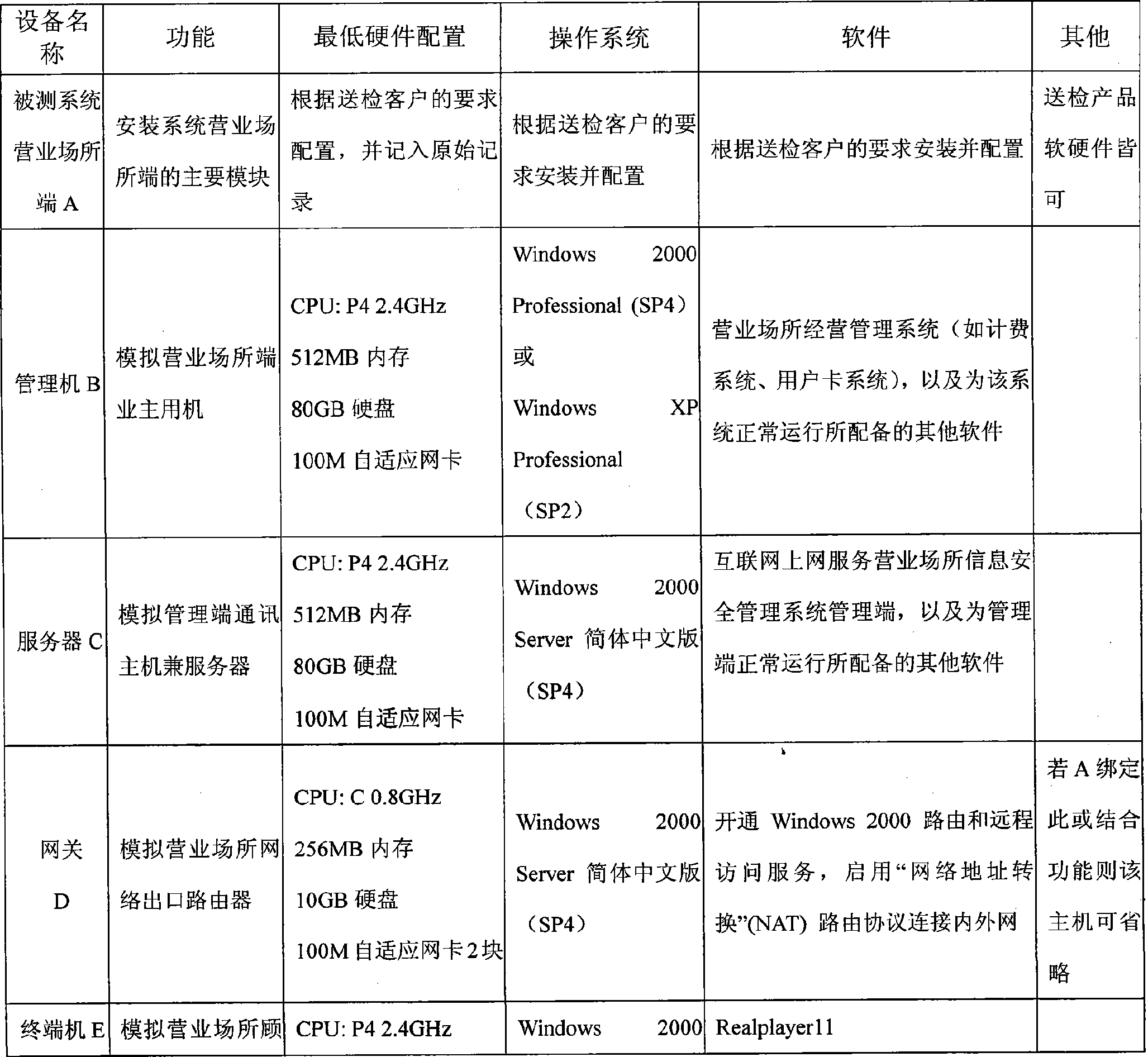
The invention discloses a testing method of information security management for internet access service business places; the method mainly performs under a detection platform and includes the following steps: (1) detection environment is established; (2) a detected system is installed; (3) test cases are designed; (4) system functional test unit adopts test cases designed in step (3) to test the information security management function of business places. The method can evaluate and test the function and performance of information security management system of internet access service businessplaces.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Financial union cloud service platform
The invention discloses a financial union cloud service platform. The financial union cloud service platform is characterized in that an only-true identity certification system of a billion-level certification scale is established through a combined public key and dynamic password technology, and self-certificating electronic identification of uniqueness and certification of all the people and things in the world can be provided. The core technology problem of an information security management system is solved accordingly, and a solid and credible security base is laid for electronic commerce. A user accesses to the financial union cloud service platform securely through network cloud, the amount of electronic certificates issued from the financial union cloud service platform is ten billion times of that of a conventional CA (certificate authority) certification system, while system investment and operating cost are only less than one tenth of those of a same-scaled CA. Therefore, the financial union cloud service platform has incomparable technical advantages and cost advantages in the field of the electronic certification. The invention further discloses an identity-certification based small and medium-sized financial institution safety integrated service platform, an identity-certification based mobile banking general service platform and an identity-certification based general card service system.
Owner:BEIJING HUFU TECH
Human face identification-based information security management system
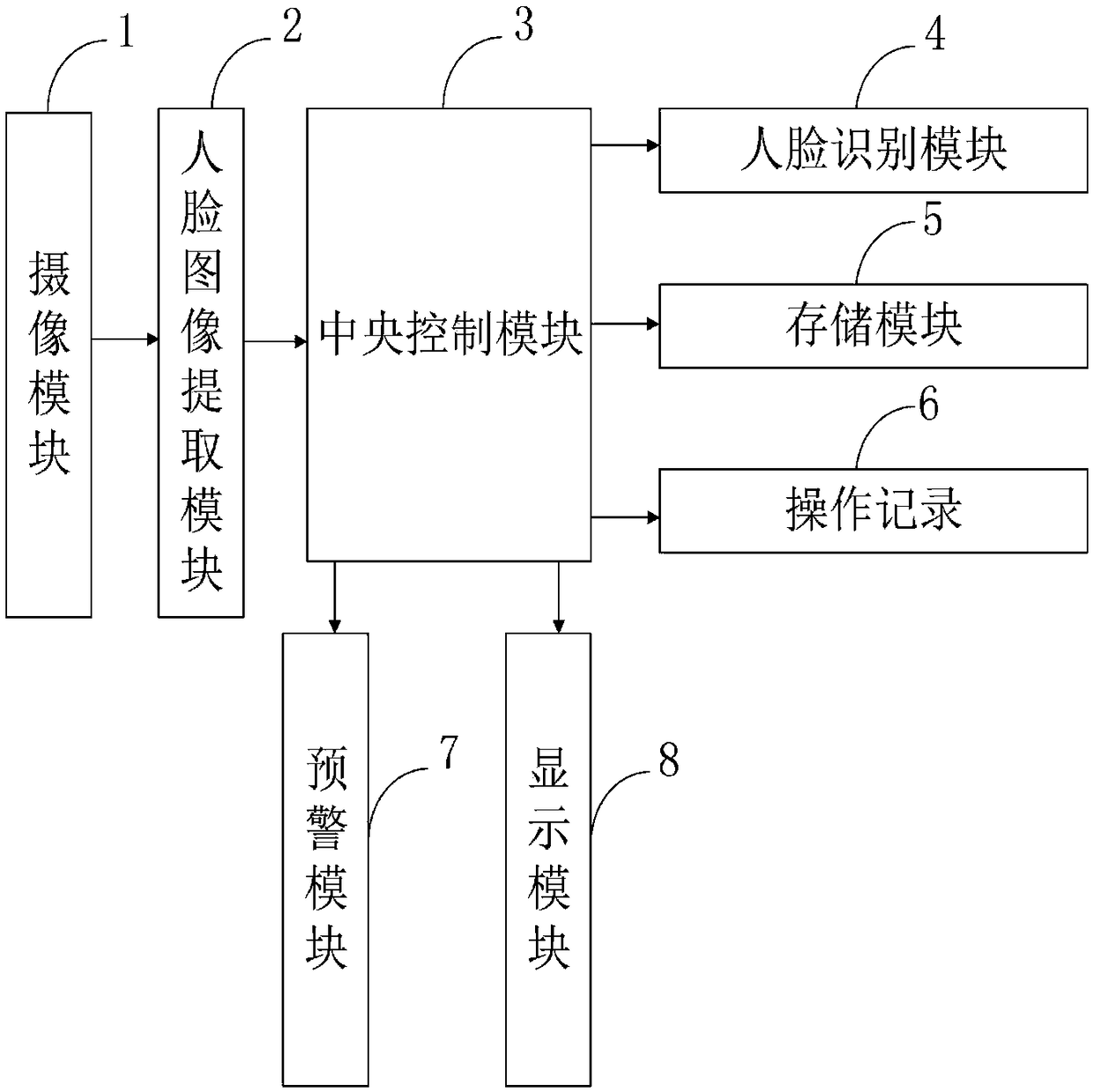
ActiveCN108596057ACalculation speedReduce sensitivityCharacter and pattern recognitionImage extractionComputer module
The invention belongs to the technical field of human face identification, and discloses a human face identification-based information security management system. The human face identification-based information security management system comprises a camera module, a human face image extraction module, a central control module, a human face identification module, a storage module, an operation recording module, an early warning module and a display module. A human face image is identified by utilizing histogram matching through the human face identification module, so that the calculation speedis high and the degree of sensitivity to poses, illumination, expressions and environmental changes can be reduced; and meanwhile, a human face decryption loser can continue to record facial features, operation processes, operation contents and operation time after an early warning subsystem performs early warning through the early warning module, and identities of intruders and specific leaked information can be obtained, so that guarantee is provided for adopting subsequent remedial measures.
Owner:CHONGQING UNIV OF EDUCATION
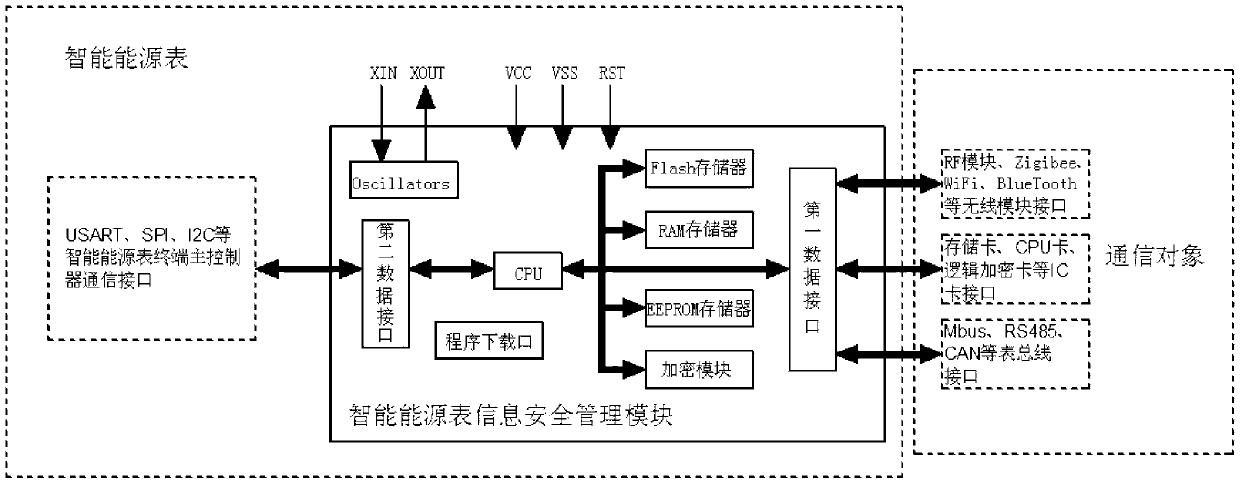
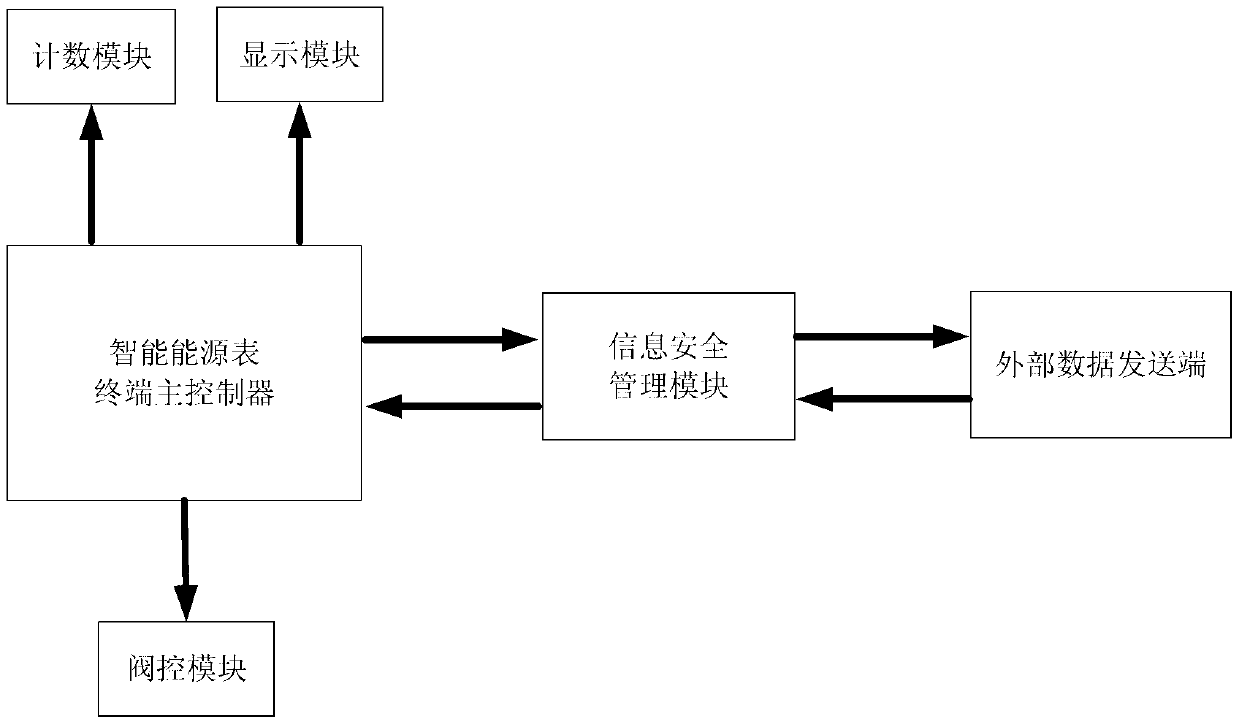
Intelligent energy meter information security management module
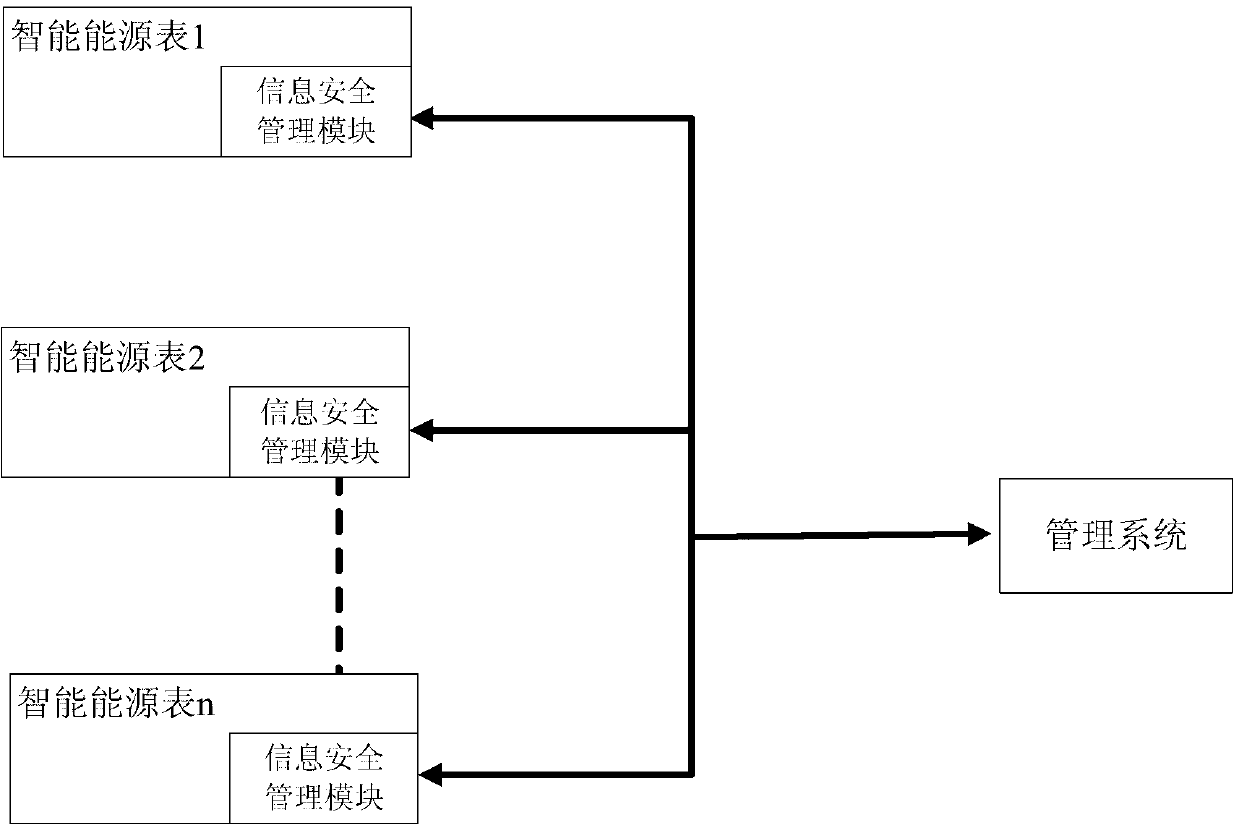
ActiveCN103136481ASimple structureGuaranteed legalityDigital data protectionStructure of Management InformationInformation security management
The invention discloses an intelligent energy meter information security management module, and belongs to an intelligent energy meter management auxiliary device. The information security management module comprises a processor, a first data interface, a second data interface and a flash storage, wherein the processor are respectively connected with the first data interface, the second data interface and the flash storage. When the information security management module and an external data sending end exchange data, identity authentication is performed, and validity of communications between the information security management module and the external data sending end is guaranteed. An intelligent energy meter terminal master controller can only communicate with the exterior through the information security management module. Permission settings of level-to-level management of an energy company are achieved by using different secret keys, and security of the secret keys is enabled to be high by using a 3 data encryption standard (DES) or advanced encryption standard (AES) multistage encryption mode, and furthermore risks caused by secret key exposure are prevented by upgrading the secret keys in real time through a program downloading port on the information security management module. The intelligent energy meter information security management module is simple in structure, can guarantee independence of the energy company on gas meter control, and is unrestrained by the external world.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
A method for automatic safety management of a dreamful database
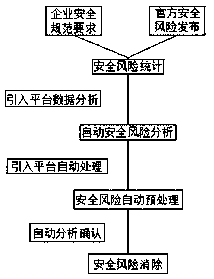
InactiveCN109902079AImprove securityReduce security risksPlatform integrity maintainanceDatabase design/maintainanceInformation security risk managementSecurity compliance
The invention discloses a method for automatic safety management of a dreamful database. Risk requirements issued by enterprises and dream officials are collected, security risk statistics, content security baselines, account security, patch security and the like are carried out, the security risks are accessed to an automatic operation and maintenance management platform, the security is analyzedby using the operation and maintenance management platform, and the platform automatically completes security compliance operation after the analysis is completed; And security contents related to the dreaminess database in the enterprise information security specification are collected, such as security baseline management, account security management, patch management and the like, and collecting security risk contents published by dreaminess officials. According to the invention, the work efficiency of information center security management can be improved, and the security of the dreamfuldatabase is improved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com