A computer information security management system and method
An information security and management system technology, applied in the direction of platform integrity maintenance, digital data authentication, etc., can solve problems such as low security and lack of more accurate identification of user identities, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
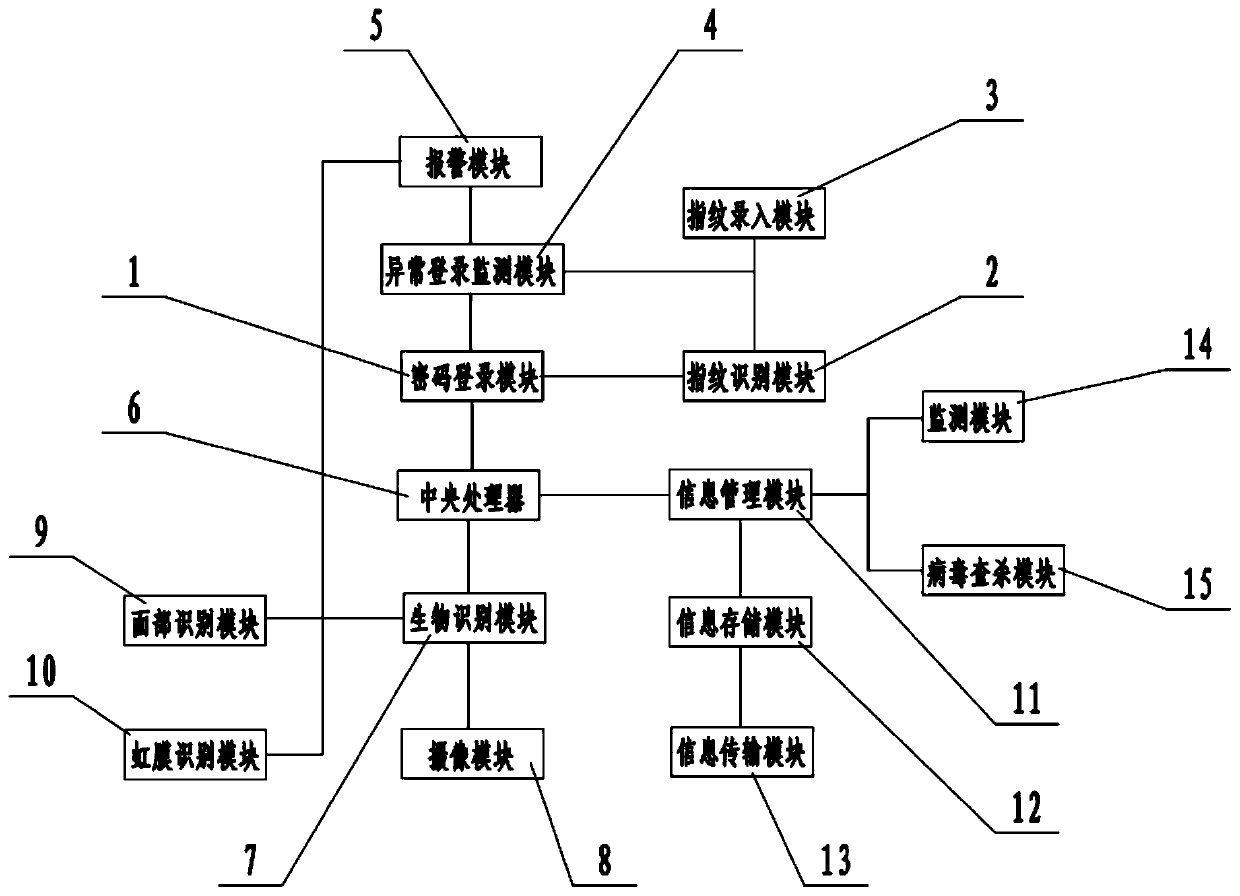
[0024] see figure 1 In an embodiment of the present invention, a computer information security management system includes a password login module 1, a fingerprint identification module 2, a fingerprint input module 3, an abnormal login monitoring module 4, an alarm module 5, a central processing unit 6, and a biometric identification module 7 , camera module 8, facial recognition module 9, iris recognition module 10, information management module 11, information storage module 12, information transmission module 13, monitoring module 14 and virus killing module 15, the user logs in this system by password login module 1, Log in to the system by entering a preset password. At the same time, a fingerprint identification module 2 is integrated on the password login module 1. Using the fingerprint identification module 2, the fingerprint is identified while entering the password. The fingerprint input module 3 is used to advance Input fingerprints for comparison and identification...
Embodiment 2
[0034] On the basis of Embodiment 1, the computer information security management system also includes a monitoring module 14 and a virus killing module 15, and the monitoring module 14 is used for real-time monitoring of the management process of the information management module 11, and creates a management log, which is convenient for consulting the management log later The virus checking and killing module 15 is used for checking and killing the system to prevent computer viruses from invading the system.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com