Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1731results about "Acquiring/reconising fingerprints/palmprints" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
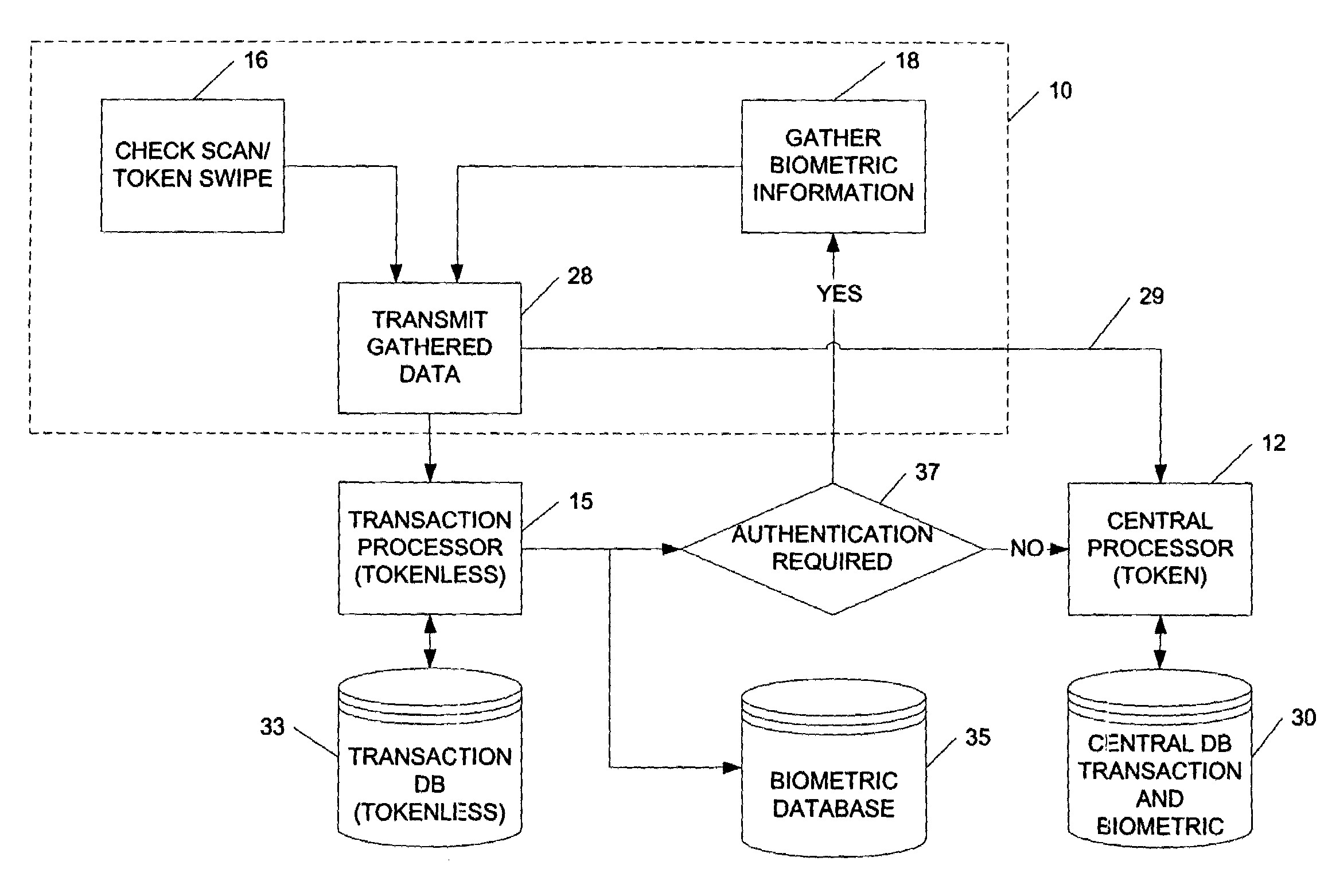
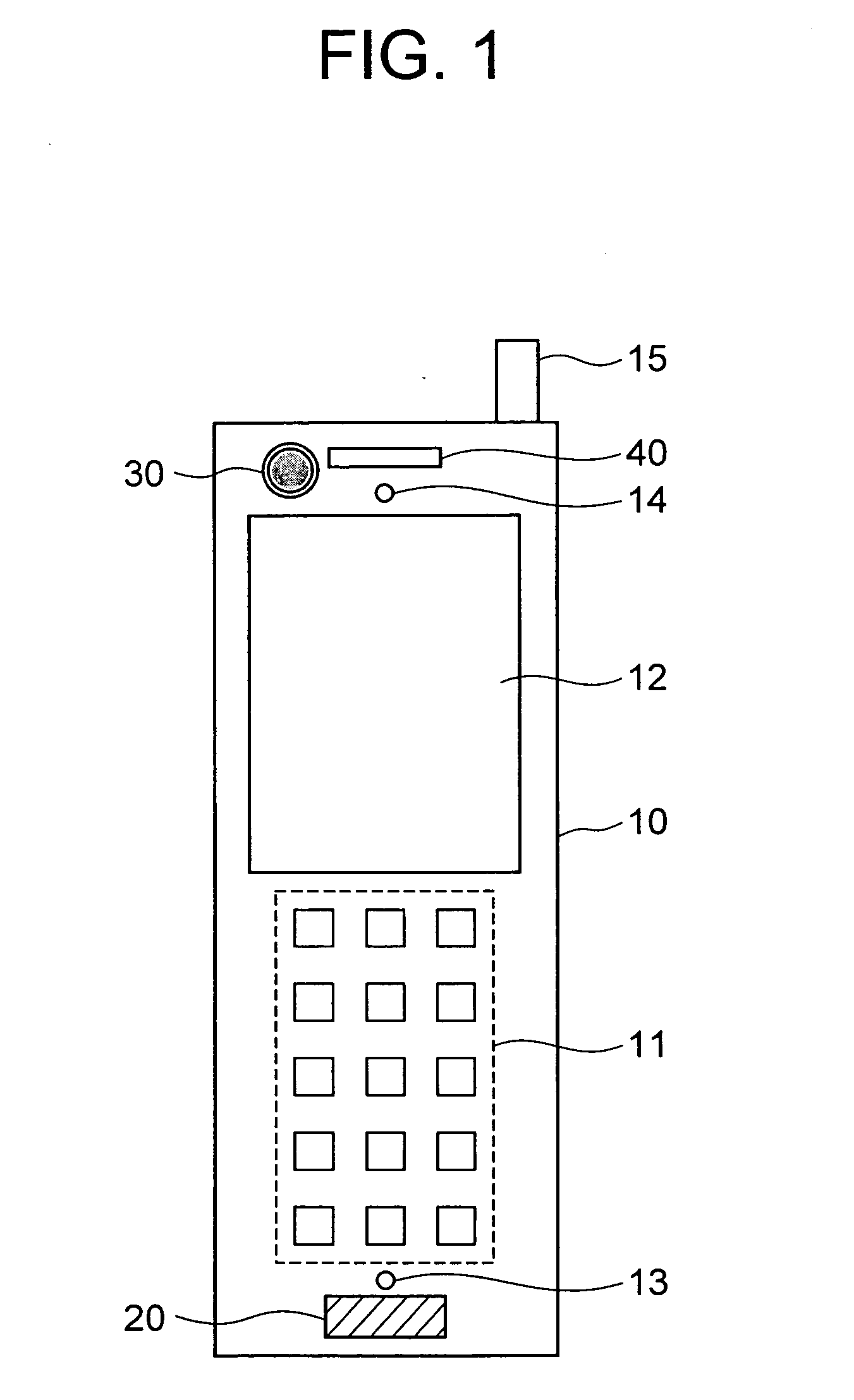
Flat panel display screen operable for touch position determination system and methods
InactiveUS20070216657A1Raising pixel capacitanceQuickly and easily determineStatic indicating devicesAcquiring/reconising fingerprints/palmprintsDisplay deviceQuantum dot display
A system and method are disclosed that determines the location of an object touching a display screen. The system and method modifies already existing display technology, including using the underlying structure of many types of existing displays as the touch detecting structure. The systems and methods are applicable to virtually all LCD and LCD-like displays, including emissive displays (OLED, PLED, quantum dot displays, etc.), electronic paper, and others.
Owner:KONICEK JEFFREY C
To a combined fingerprint acquisition and control device
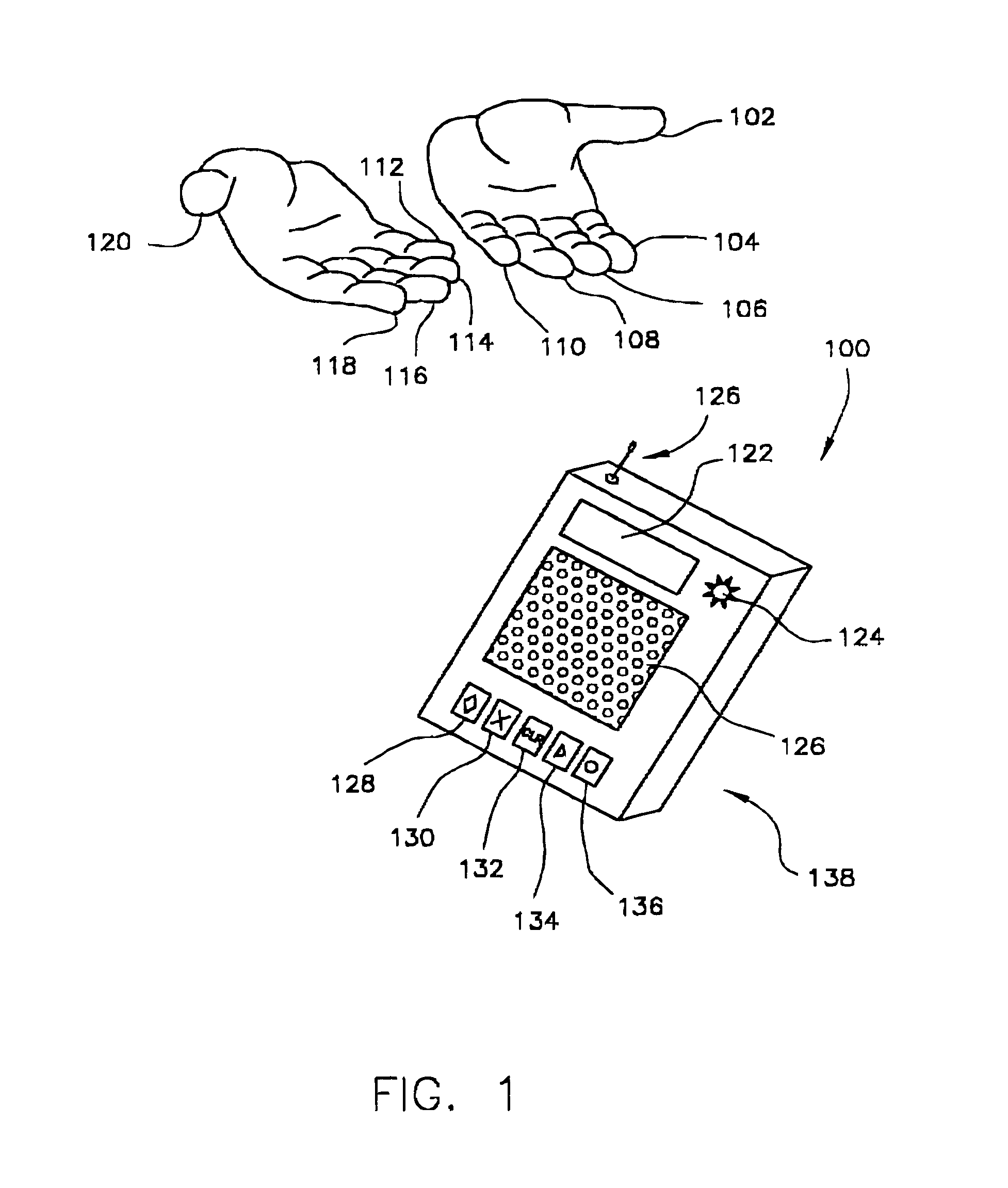
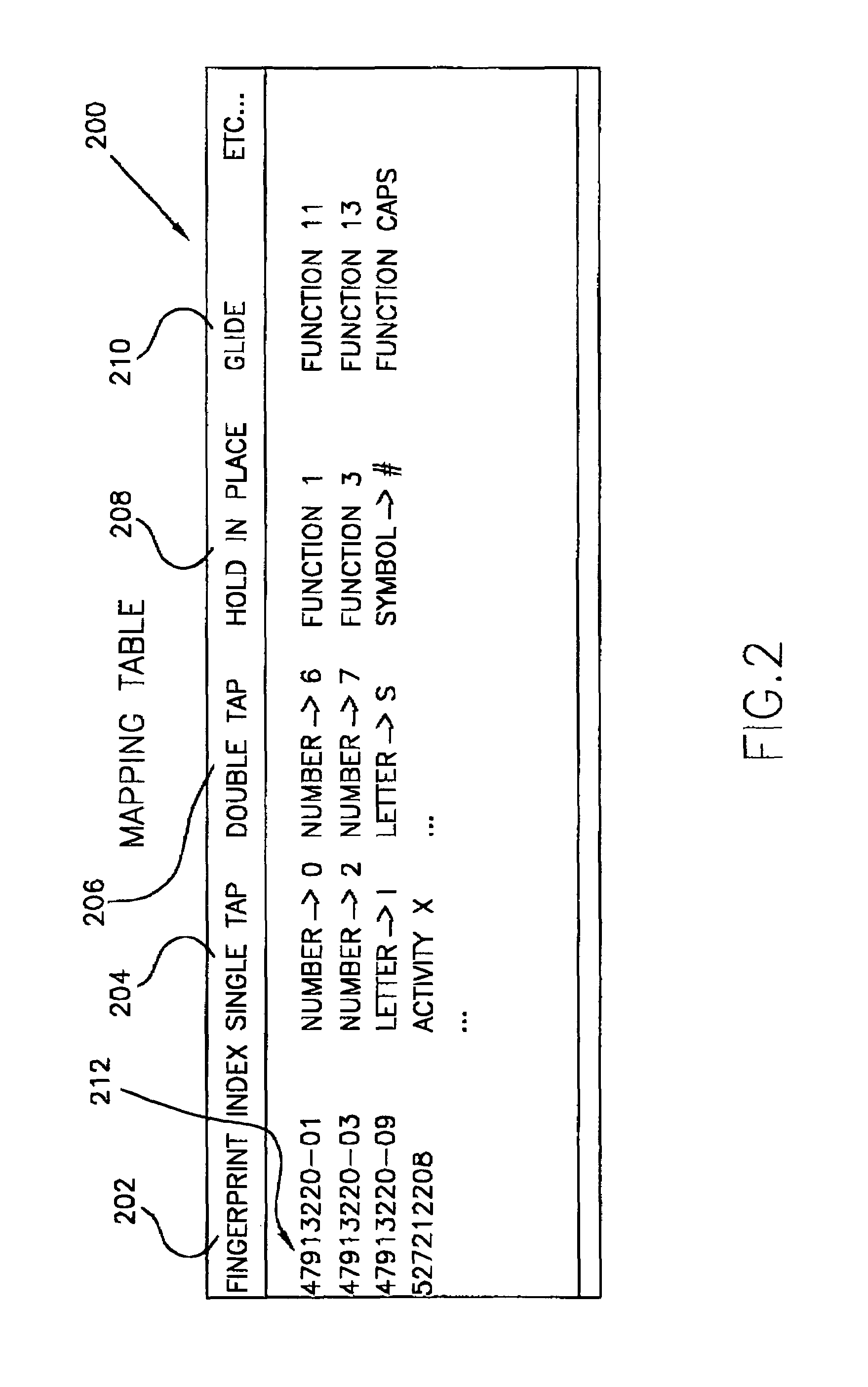
The present invention combines the functionality of a computer pointing device with a fingerprint authentication system, In the preferred embodiment, by regularly scanning fingerprints acquired from the pointing device touch pad, fingerprint features may be extracted and compared to stored data on authorized users for passive authentication. Furthermore, calculations based upon the acquired fingerprint images and associated features allows the system to determine six degrees of freedom of the finger, allowing the user to control a variety of functions or to manipulate a three-dimensional model or virtual reality system.
Owner:SYNAPTICS INC
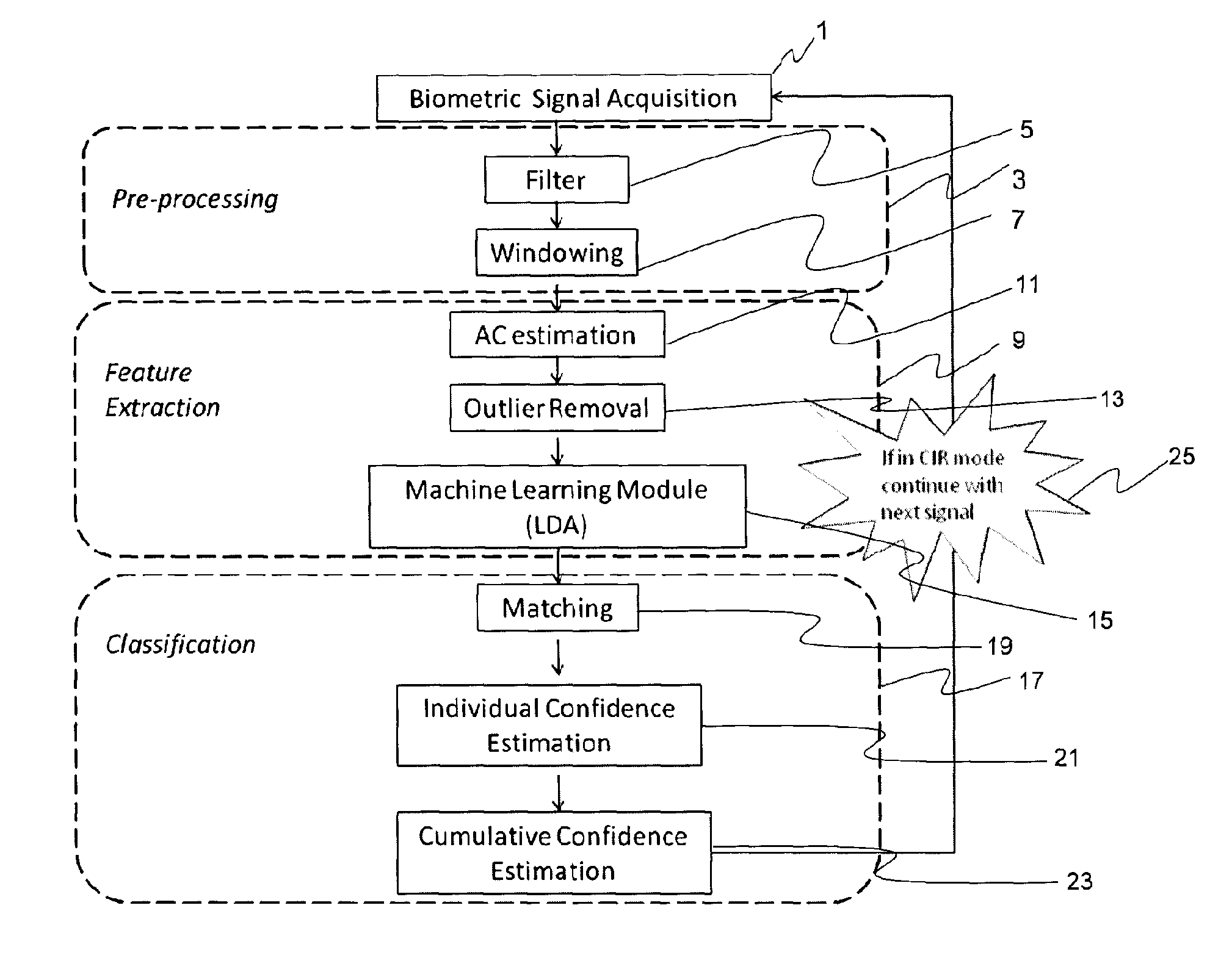
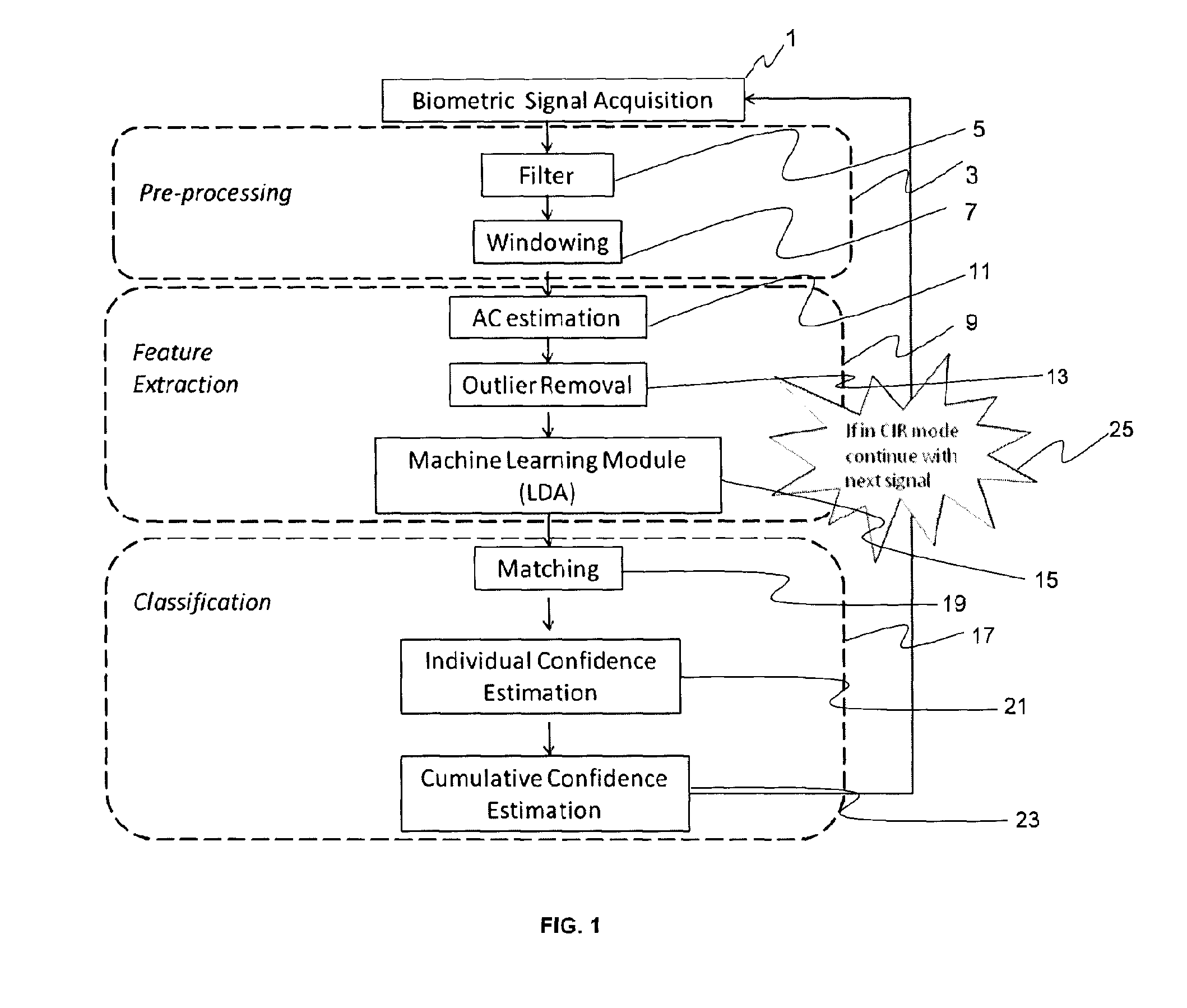
System and method for enabling continuous or instantaneous identity recognition based on physiological biometric signals
ActiveUS20140188770A1Medical data miningPerson identificationPattern recognitionIdentity recognition
The present invention is a biometric security system and method operable to authenticate one or more individuals using physiological signals. The method and system may comprise one of the following modes: instantaneous identity recognition (MR); or continuous identity recognition (CIR). The present invention may include a methodology and framework for biometric recognition using physiological signals and may utilize a machine learning utility. The machine learning utility may be presented and adapted to the needs of different application environments which constitute different application frameworks. The present invention may further incorporate a method and system for continuous authentication using physiological signals and a means of estimating relevant parameters.
Owner:NYMI
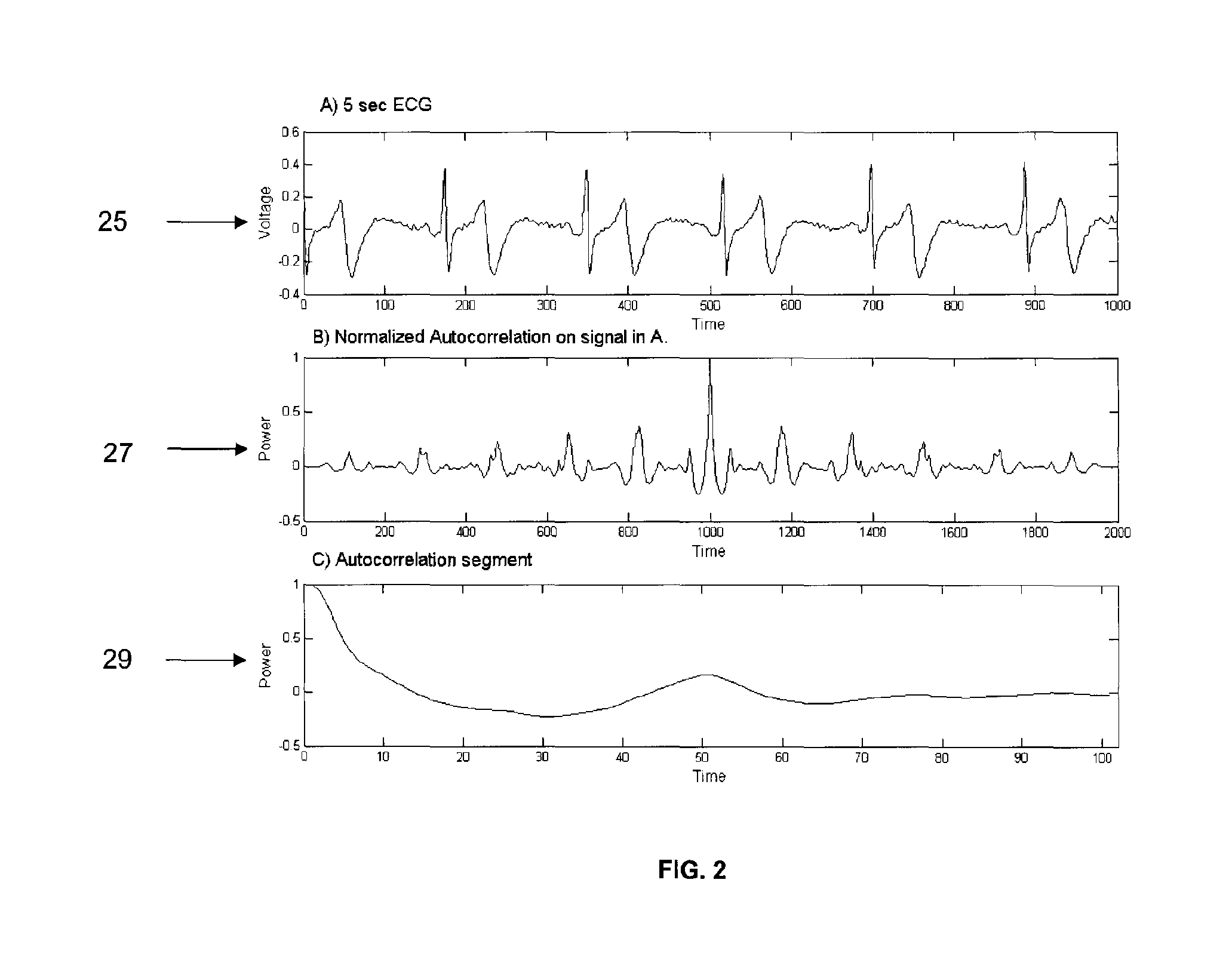
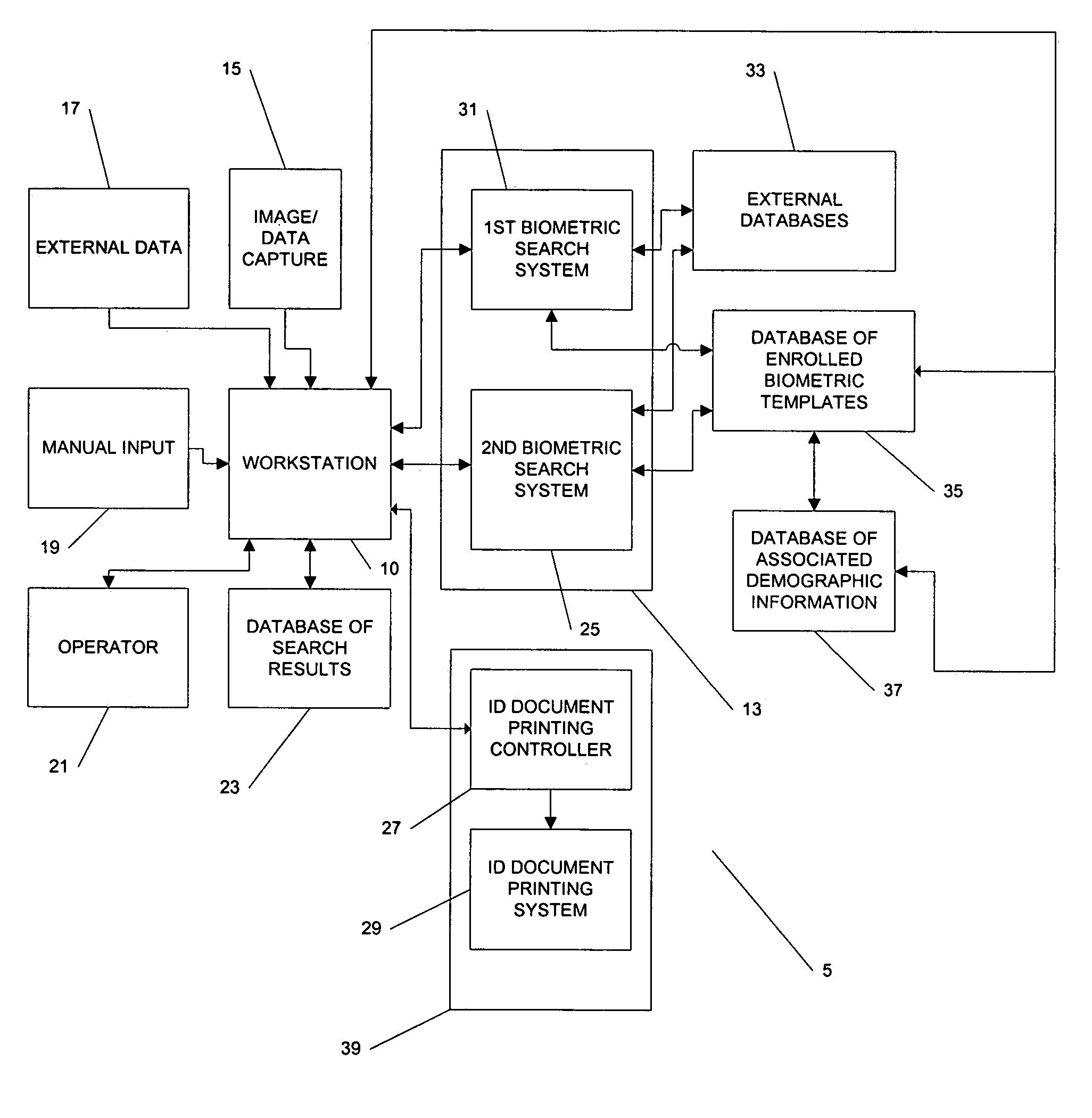
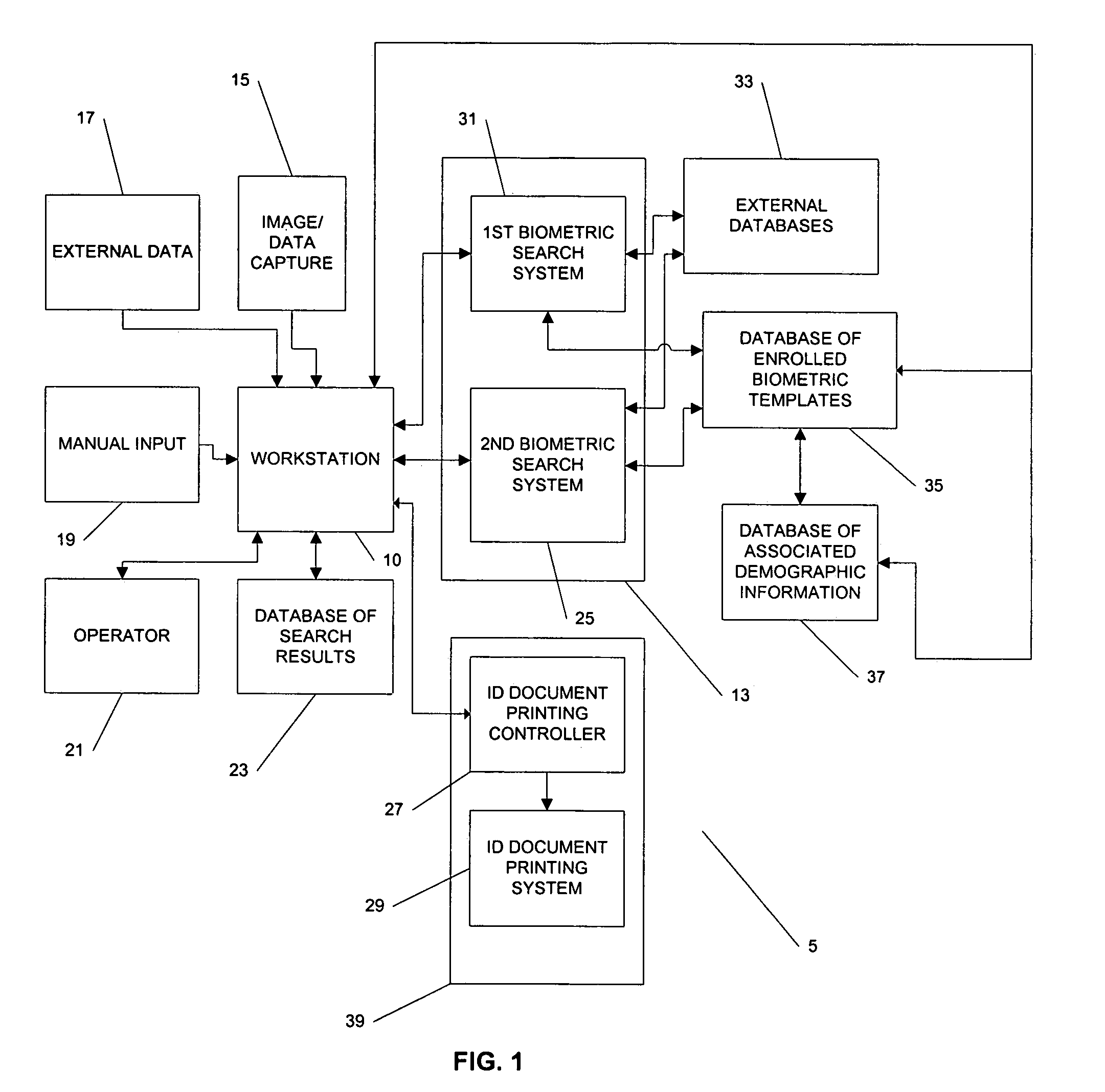
Systems and methods for recognition of individuals using multiple biometric searches
InactiveUS7277891B2Data processing applicationsDigital data processing detailsPattern recognitionData set
The invention provides a computer-implemented method for determining whether a database contains any images that substantially match at least one image provided of an individual. A probe data set is received, the comprising first and second biometric templates associated with the individual, the first biometric template associated with a different type of biometric than the second type of biometric template. A database of biometric templates is searched using the first biometric template to retrieve a first results set. A first predetermined portion of the first results set is selected. The first predetermined portion of the first results set is searched using the second biometric template to retrieve a second results set. A second predetermined portion of the second results set is selected. The second predetermined portion of the second results is provided for comparison with the image provided of the individual.
Owner:L 1 SECURE CREDENTIALING
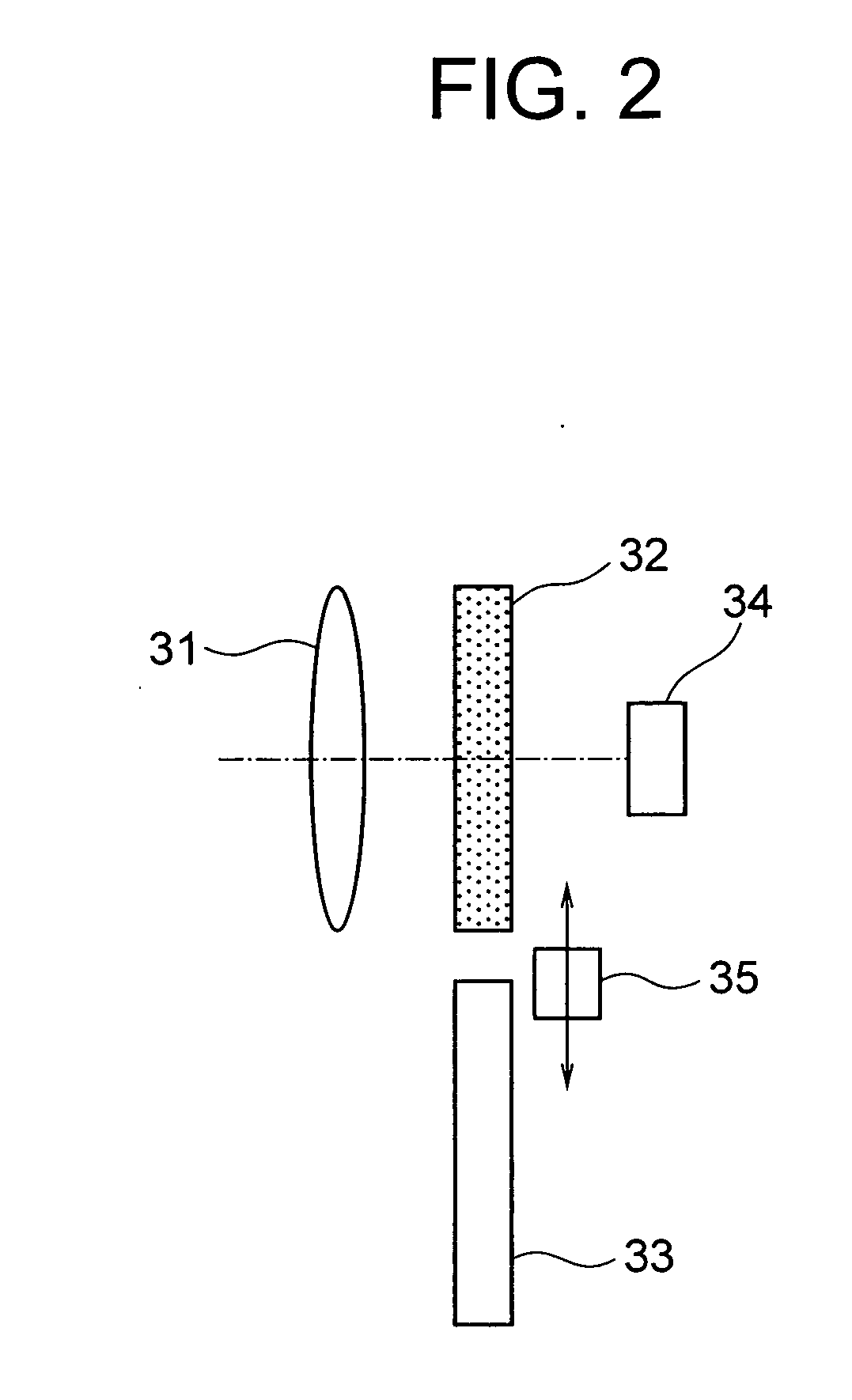
Fingerprint security systems in handheld electronic devices and methods therefor
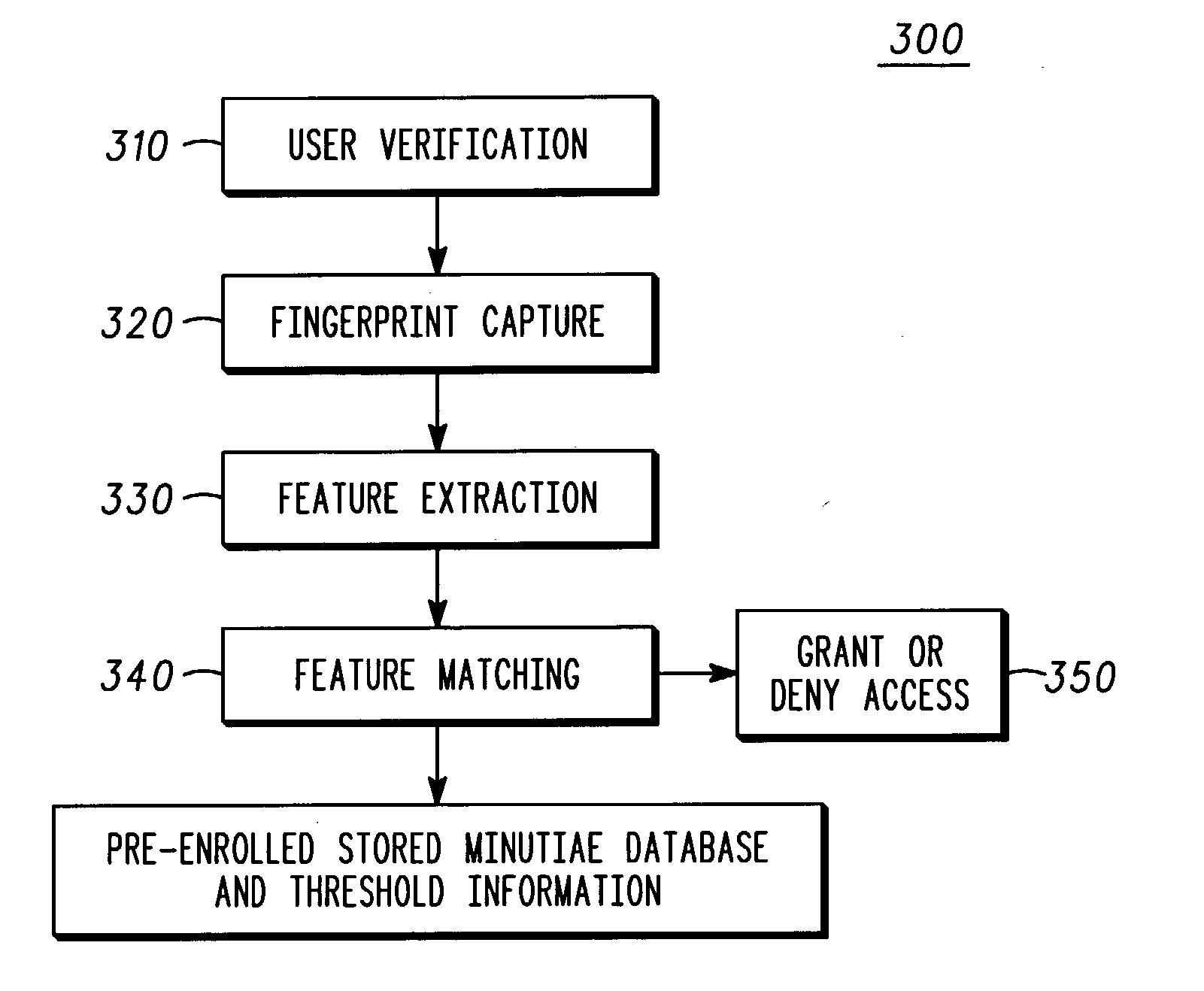
Fingerprint image processing methods for fingerprint security systems, for example, in wireless communications devices, including capturing fingerprint images (320), identifying features from images (330), matching the identified features with reference features (340), and providing access to the device based upon feature matching (350) results. In one embodiment, minutiae features are extracted from the image and matched to reference minutiae features.
Owner:MOTOROLA INC
Transaction authentication card
InactiveUS20070220273A1Electric signal transmission systemsImage analysisUser verificationComputer hardware
A transaction authentication card uses a biometric input and a wireless output. The biometric input may be a sensor pad on the transaction authentication card that measures blood flow patterns, temperature, and / or fingerprint patterns to identify a user to permit access. The transaction authentication card is preferably substantially rigid, but may be formed to have some flexibility. Power to the transaction authentication card may be accomplished through an internal battery that is optionally rechargeable. Biometric data is stored on the card only and used for user verification. Biometric data will not be transferred from the card. If authorized biometric data is authenticated the card will transmit a wireless access code to a proximity reader or transaction equipment.
Owner:RESILENT
Integrated keypad system
InactiveUS7020270B1Save spaceQuick distinctionInput/output for user-computer interactionElectronic switchingComputer scienceData entry
Owner:GHASSABIAN FIROOZ BENJAMIN +1
Biometric data card and authentication method
InactiveUS20050232471A1Accurate authenticationResist attackImage analysisBathroom accessoriesComputer hardwareBiometric data
A biometric data card includes an image sensor for capturing an image of a biometric feature of a user of the biometric data card and producing first image data representing the image. The biometric data card compares the first image data to second image data stored within the biometric data card to authenticate the user. The biometric data card is usable with a terminal including a slot for receiving the biometric data card. The terminal can further include an optical element optically coupled to direct the image onto the image sensor of the biometric data card.
Owner:AGILENT TECH INC
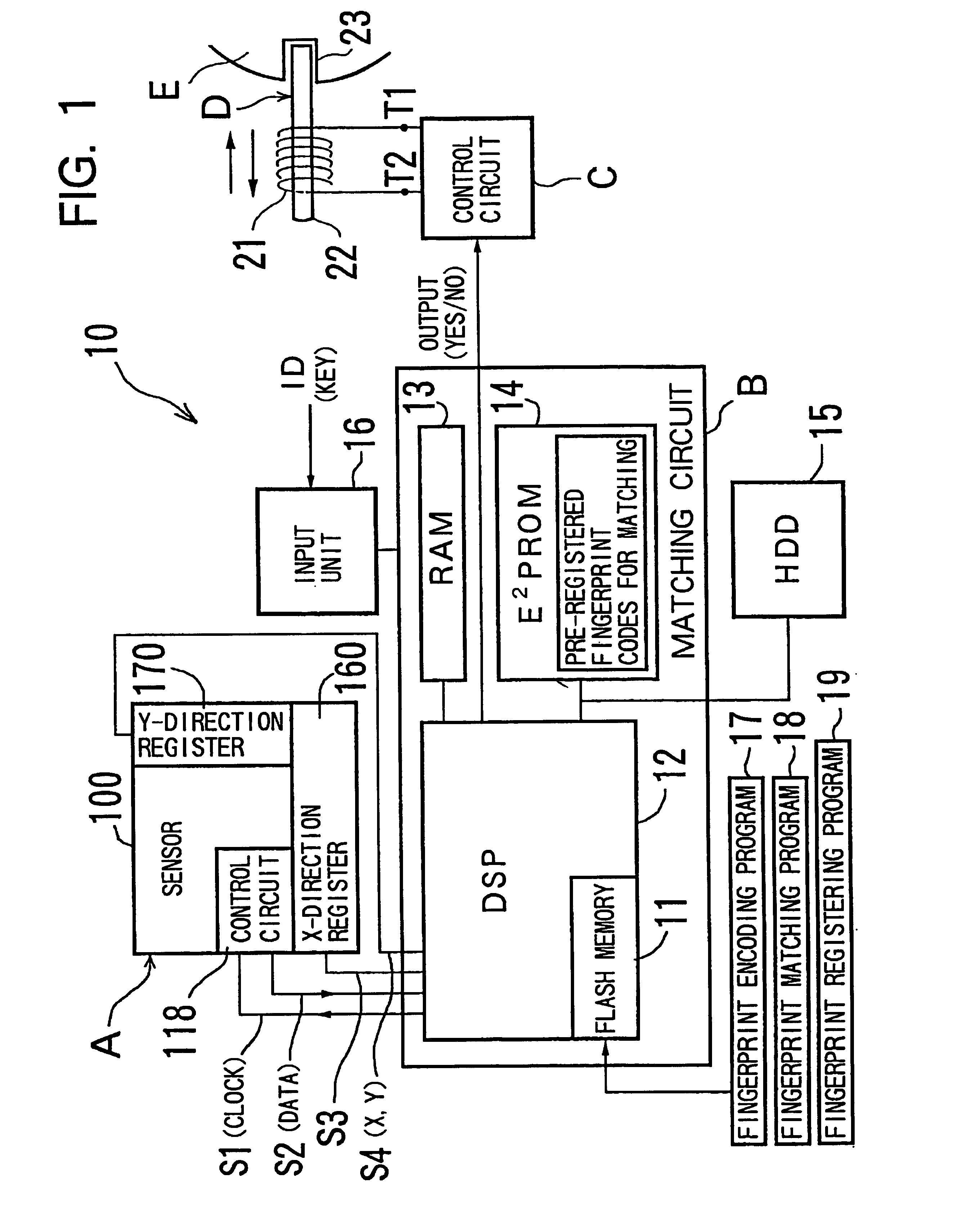
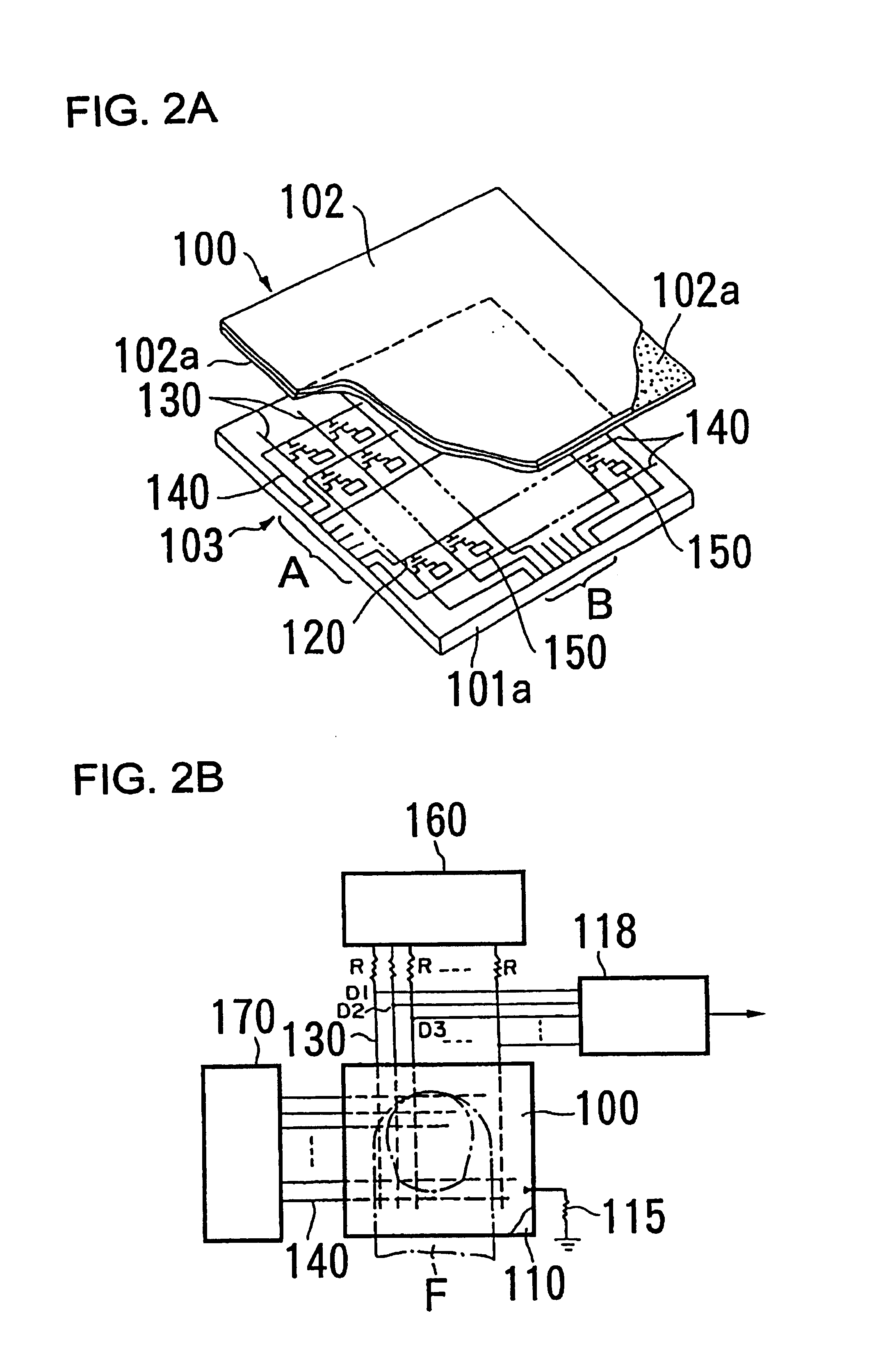
Lock and switch using pressure-type fingerprint sensor
InactiveUS6980672B2Prevent movementElectric signal transmission systemsImage analysisLocking mechanismComputer science
A lock has a pressure-based fingerprint sensor, the sensor detects the fingerprint pattern of the finger that presses the sensor, a matching circuit prepares a fingerprint code based on the detected fingerprint pattern, this code is compared with registered fingerprint codes stored in a memory device to determine whether there is a match, and if there is a match, a control unit unlocks the locking mechanism of a concerned object.
Owner:ENIX
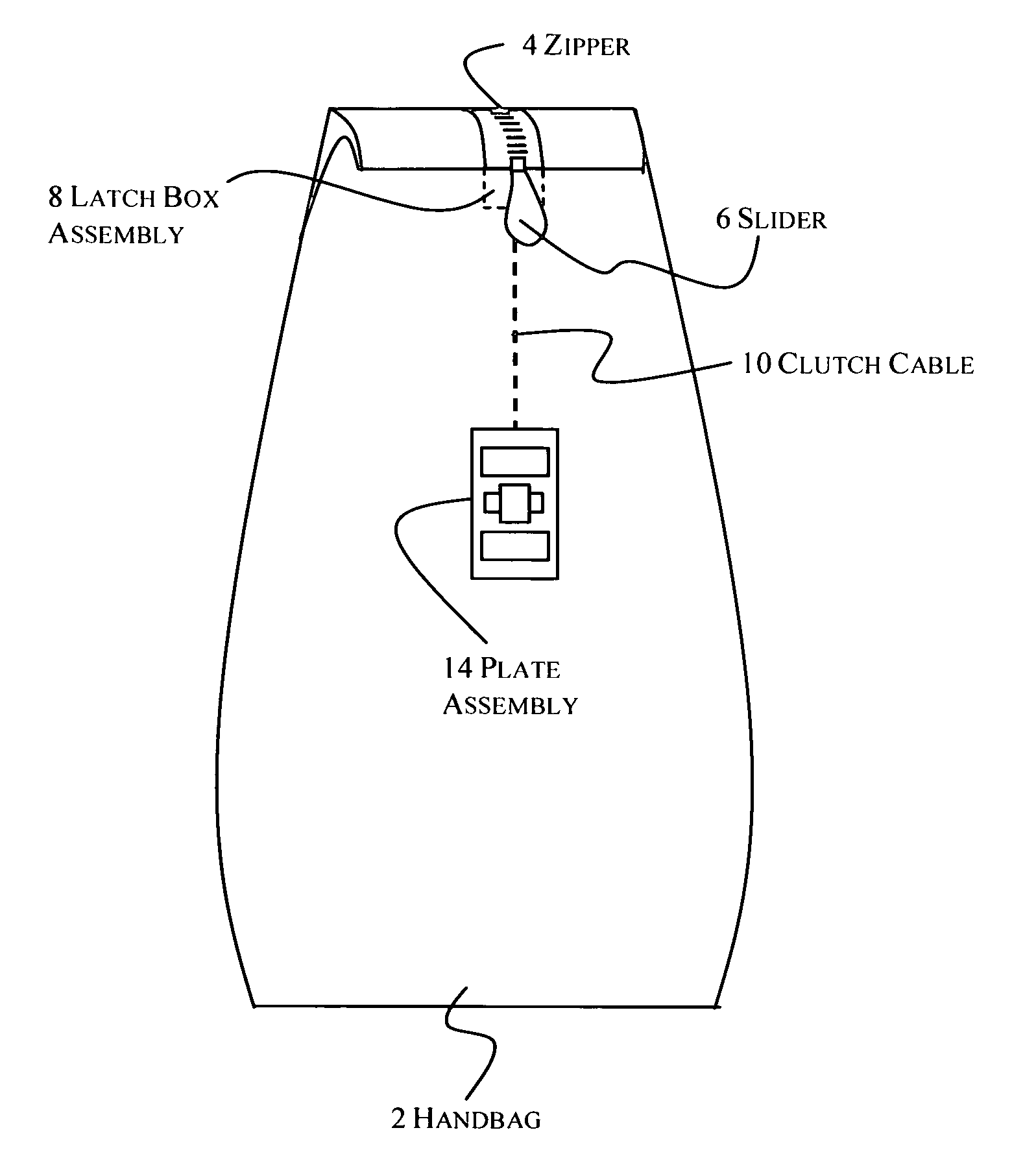
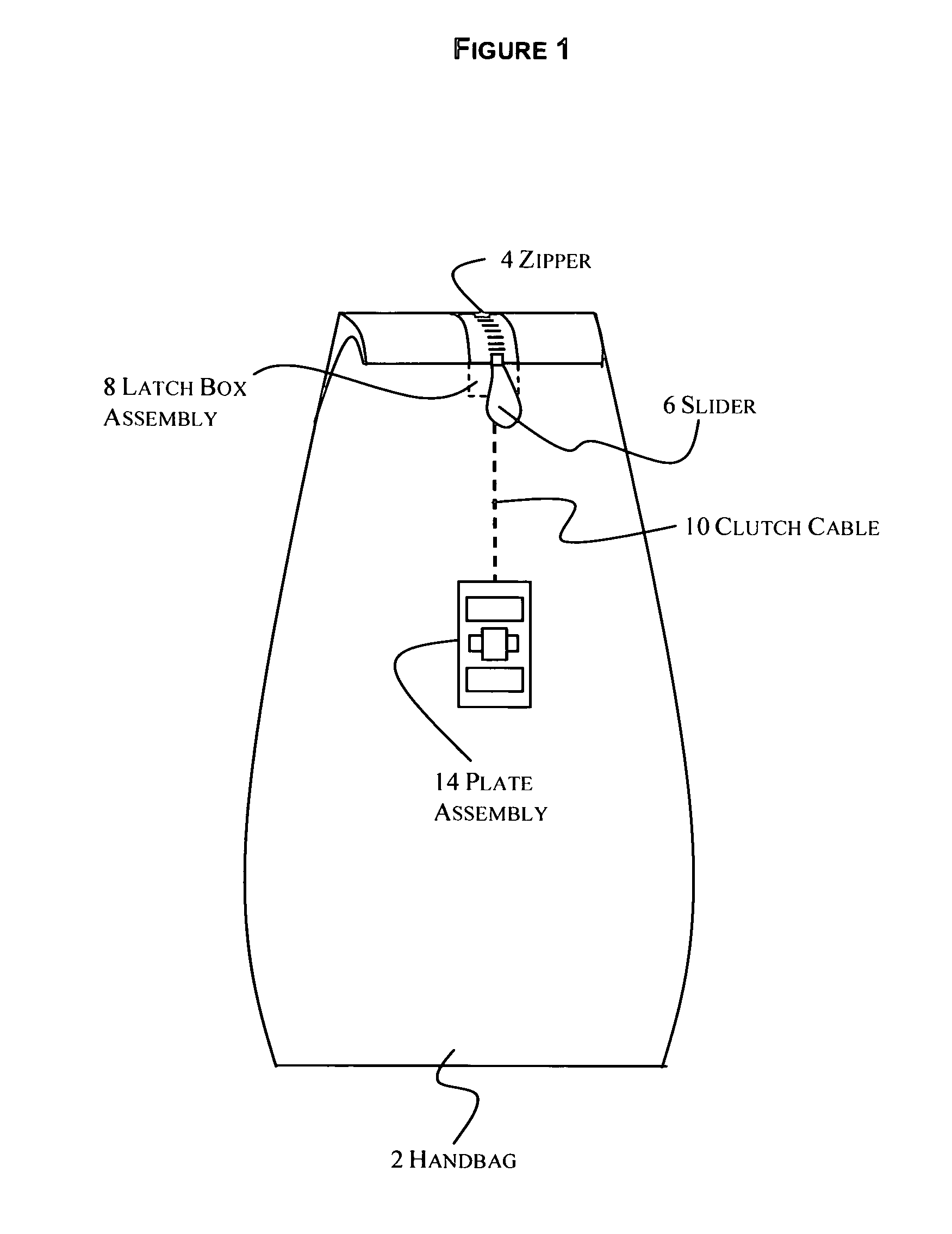
System and apparatus for securing an item using a biometric lock
A system and apparatus for securing an item using a biometric lock where a matching fingerprint allows a user access to the item secured. In one embodiment, the item is a container with an aperture. More specifically, the container is a handbag, luggage, briefcase, computer bag, storage container, shipping container or gun holster. In one embodiment, the biometric lock apparatus is self contained and is applied to the item being secured. More specifically, the self contained biometric lock is a padlock, bicycle lock, or an independent lock with a shackle applied to an item. In one embodiment, the biometric lock is divided into multiple components, one component being a biometric key containing a sensor where a user inserts the key into another component of the lock and applies a finger to the sensor to read a matching fingerprint and unlock the mechanism. In one embodiment, the systems and apparatuses include utilizing an unlocking apparatus that contains a generator whereby the swiping of a fingerprint over a sensor simultaneously moves a thumb roller which activates the generator to power the device, and a fingerprint is initially installed through the use of an external computer and a secondary power source.
Owner:HUGHES MICHAEL L
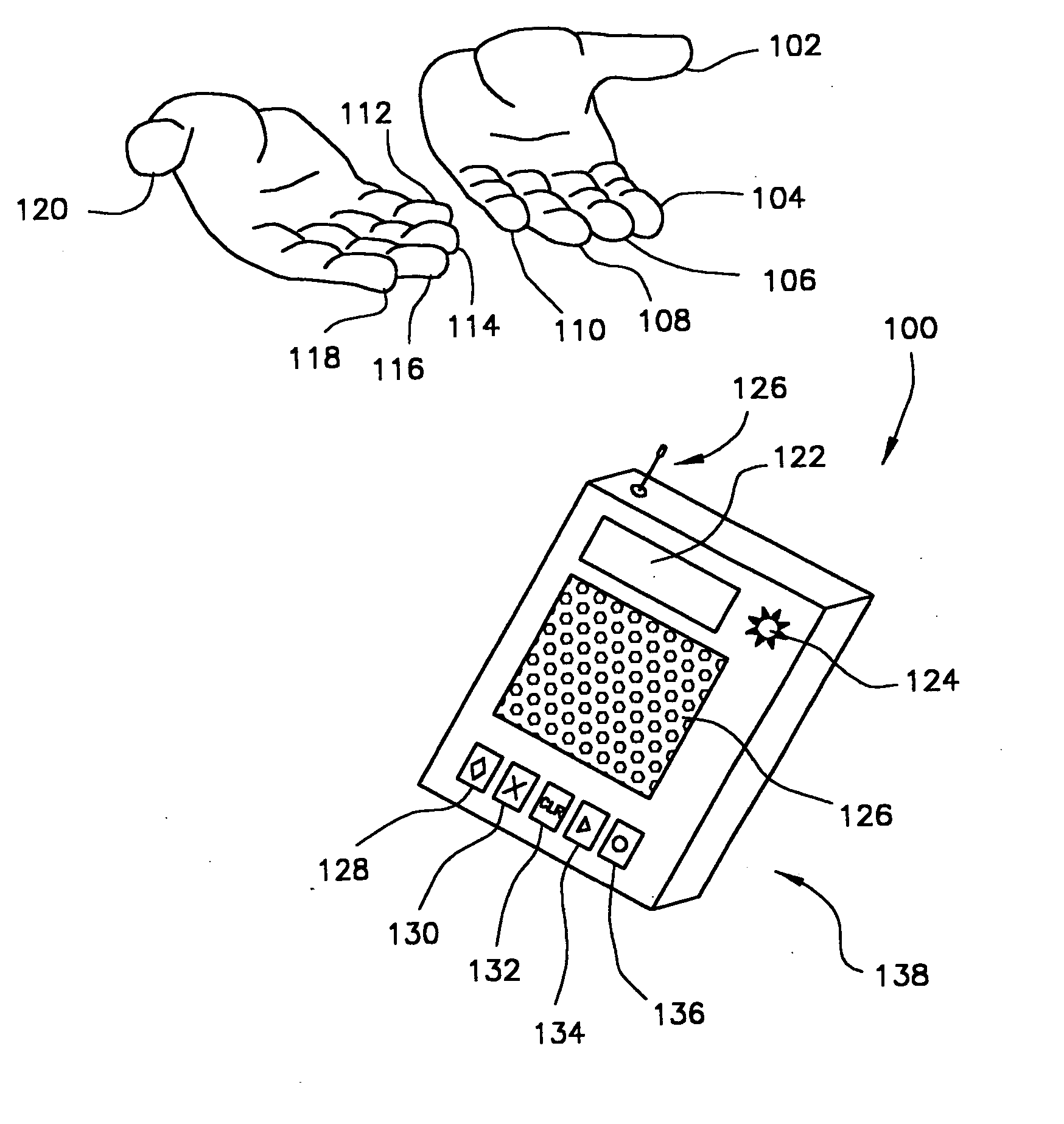
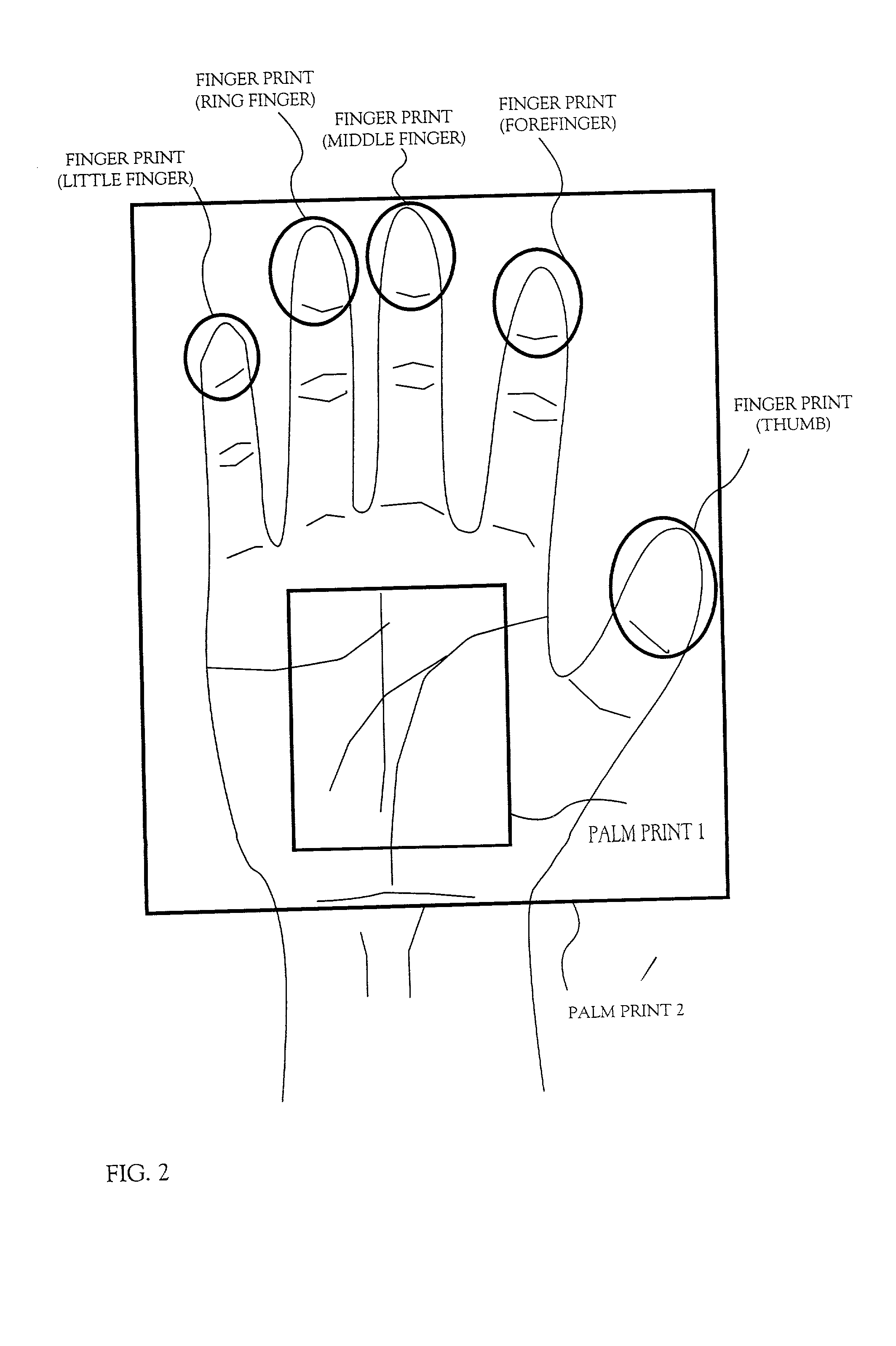
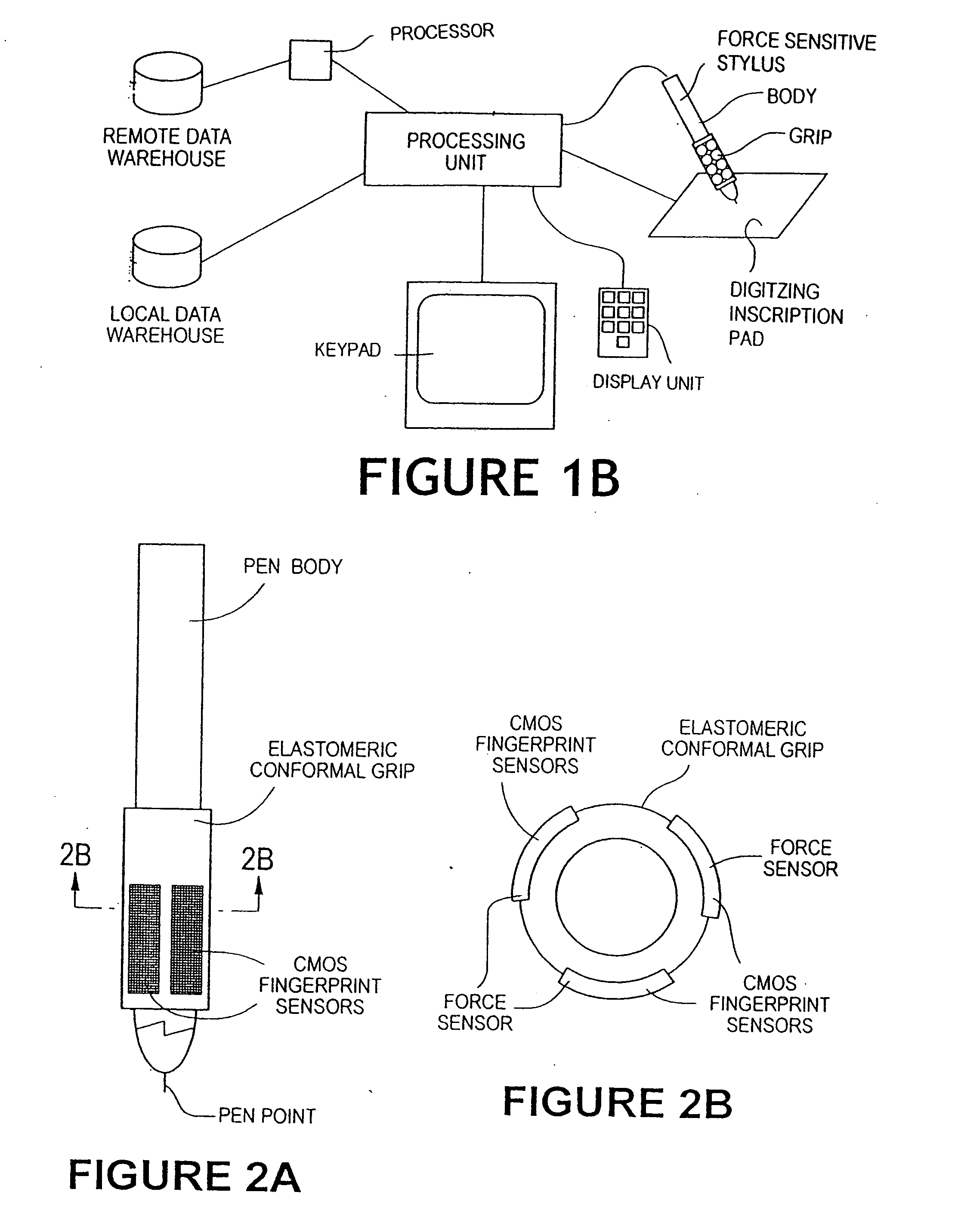
Method for identity verification
InactiveUS20050180618A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
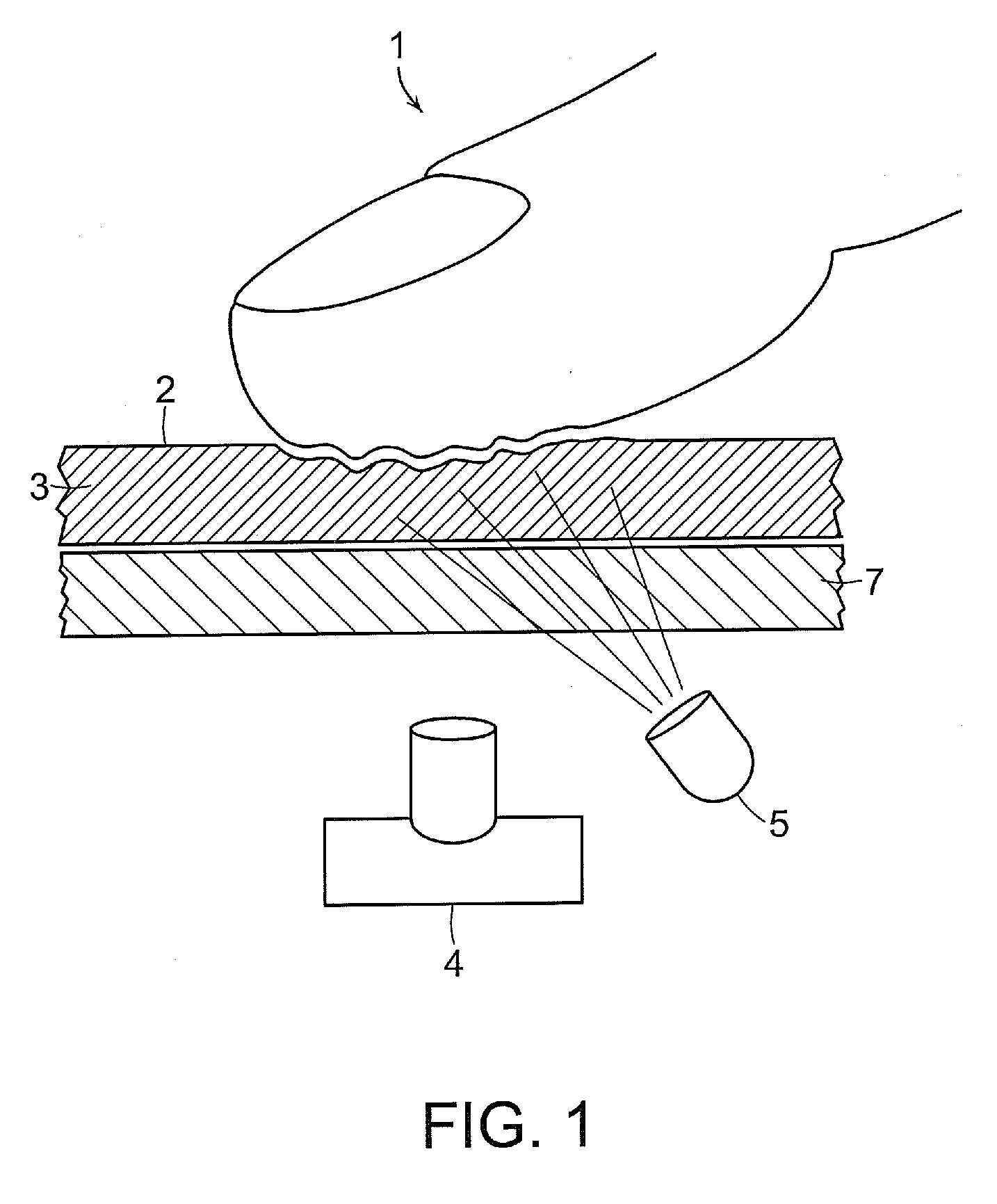
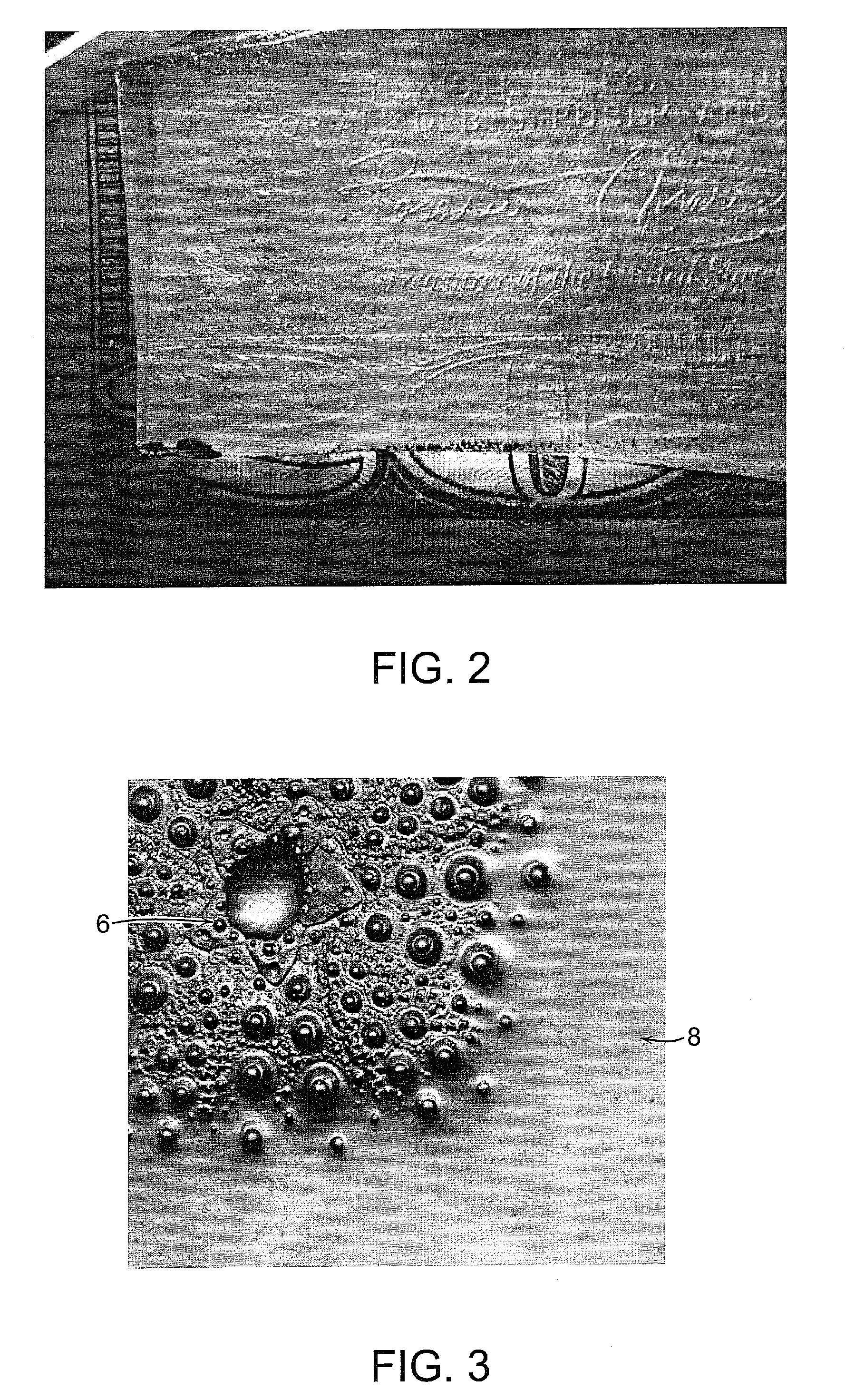
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
Tactile sensor using elastomeric imaging
ActiveUS20090315989A1Television conference systemsForce measurement by measuring optical property variationElastomerElastography
A tactile sensor includes a photosensing structure, a volume of elastomer capable of transmitting an image, and a reflective skin covering the volume of elastomer. The reflective skin is illuminated through the volume of elastomer by one or more light sources, and has particles that reflect light incident on the reflective skin from within the volume of elastomer. The reflective skin is geometrically altered in response to pressure applied by an entity touching the reflective skin, the geometrical alteration causing localized changes in the surface normal of the skin and associated localized changes in the amount of light reflected from the reflective skin in the direction of the photosensing structure. The photosensing structure receives a portion of the reflected light in the form of an image, the image indicating one or more features of the entity producing the pressure.
Owner:MASSACHUSETTS INST OF TECH
Data security system
InactiveUS7047419B2Easy accessNeed can be addressedDigital data processing detailsInternal/peripheral component protectionComputer usageData access
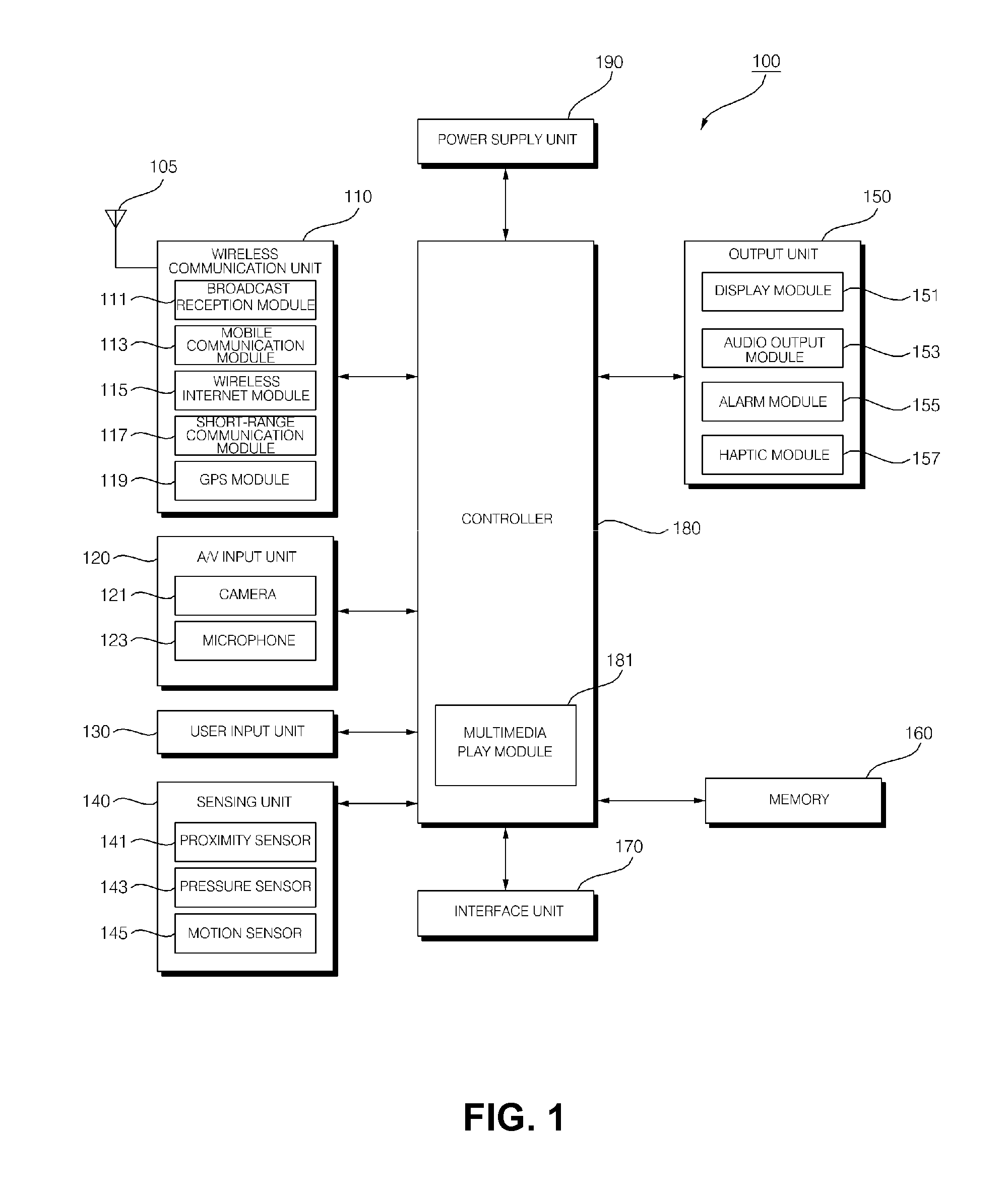
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
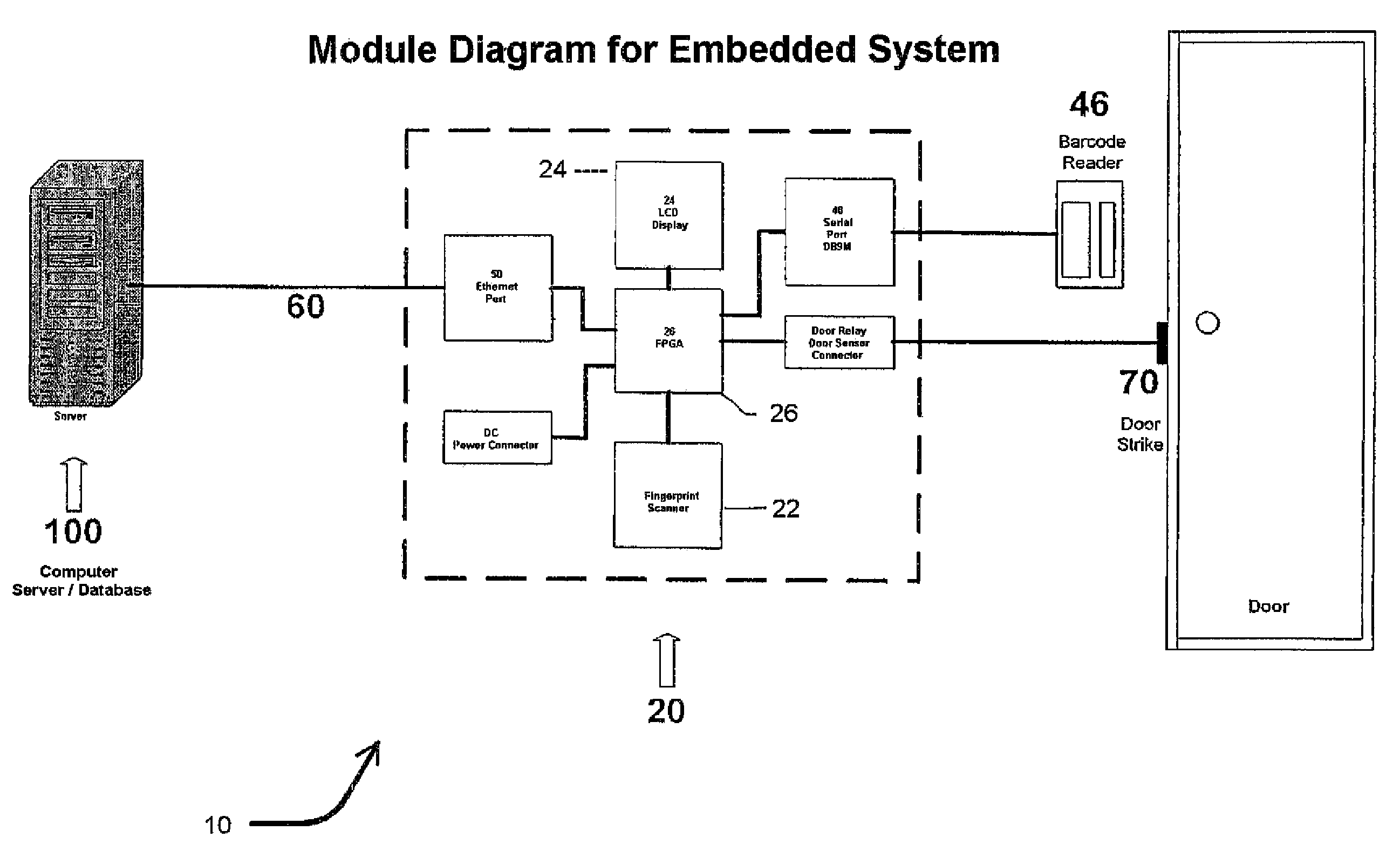
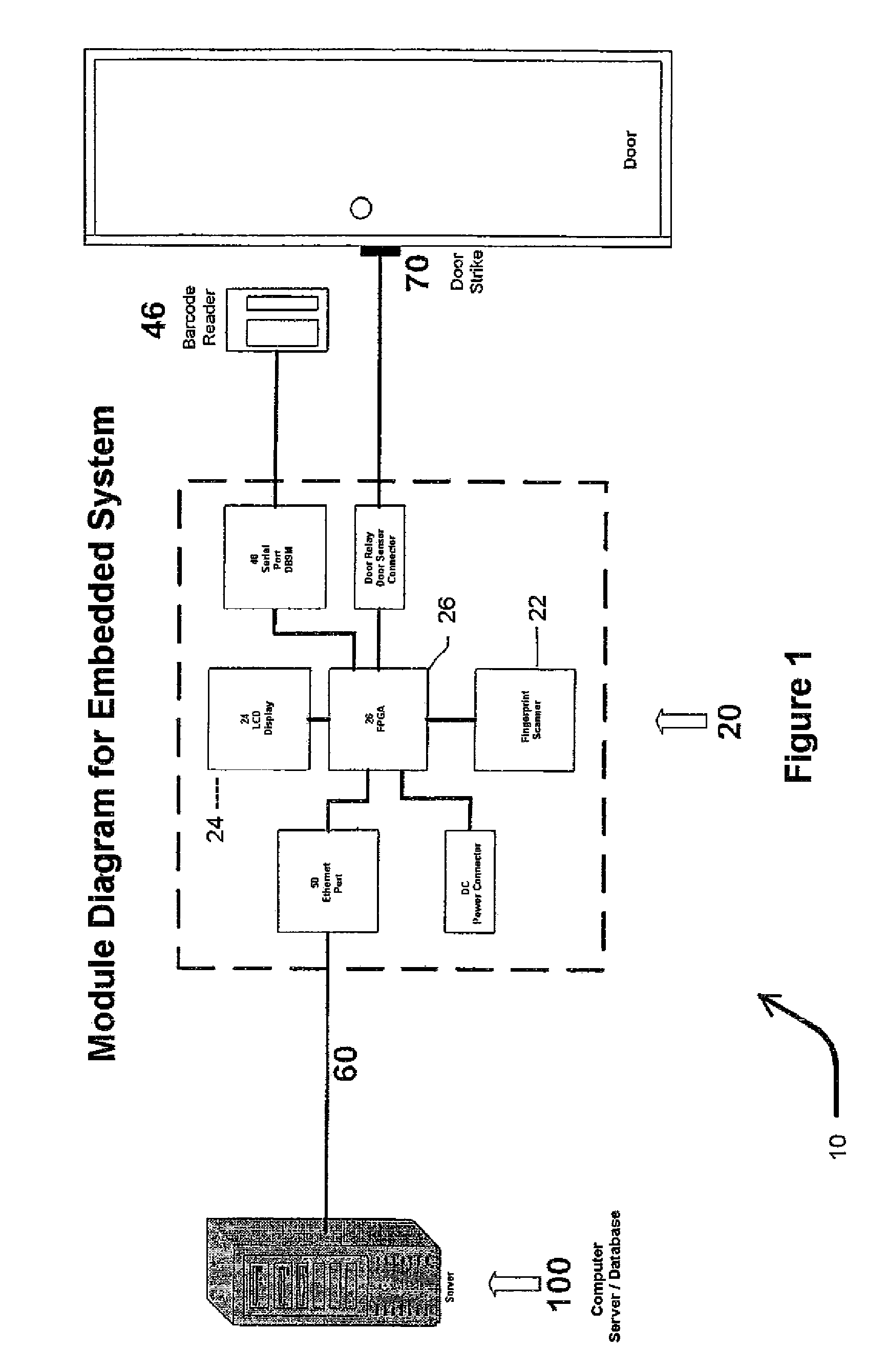
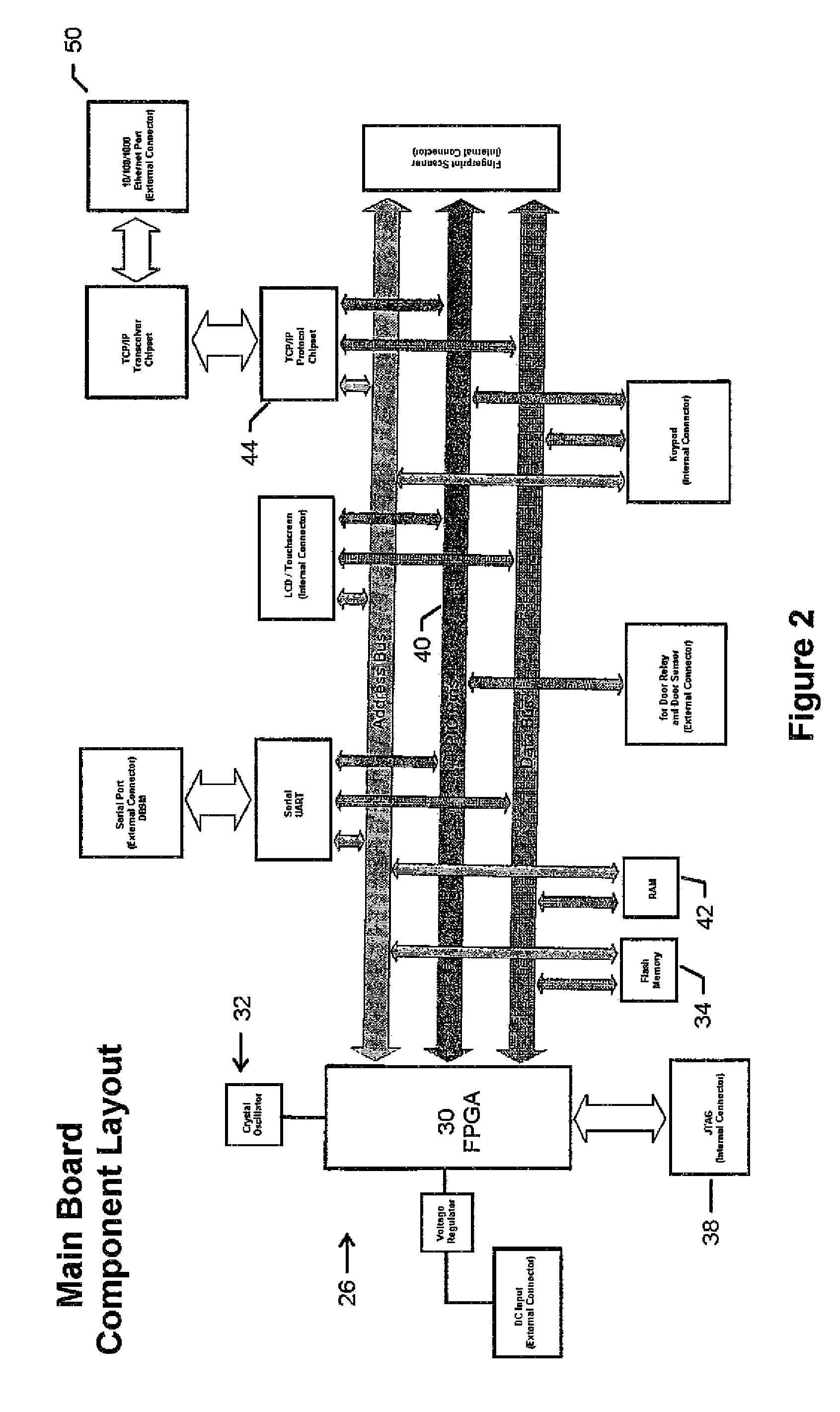
Biometric access control and time and attendance network including configurable system-on-chip (CSOC) processors with embedded programmable logic
ActiveUS7424618B2Compact efficient designCost efficient designElectric signal transmission systemsDigital data processing detailsHard disc driveHuman interaction
A biometric access control and time and attendance system comprises an integrated network including one or more remote access devices in electronic communication with a computer database. Each remote access device comprises a silicon chip based system and preferably includes a biometric input device, a liquid crystal display (LCD), computer processing capabilities based on embedded system architecture with configurable system-on-chip (CSOC) technology, and an electrical output for controlling a door lock or the like. The use of CSOC architecture in lieu of conventional personal computer technology (e.g. mother boards, hard drives, video controllers and the like) allows for a more compact and cost efficient design. A plurality of remote access devices is configured for communication with a primary computer database wherein data corresponding to biometric samples for all authorized users is stored. In an embodiment wherein the biometric input devices comprise fingerprint scanners, the devices are configured to facilitate fingerprint identification by incorporating an auto-targeting capability that enables the user to simply place his or her finger on the fingerprint scanner whereafter the system adjusts the scanned image by automatically shifting the scanned image data to a properly targeted position thereby enabling the system compare the scanned print to the biometric samples in the system's data storage memory. Auto-targeting capability eliminates the requirement for manual targeting present in systems of the background art thereby improving system performance and minimizing reliance on human interaction. The present invention contemplates the use of auto-targeting with other biometric systems, such as facial recognition and / or retinal scanning systems, or any other biometric identification technology.
Owner:PROFILE SOLUTIONS
Electronic lock box using a biometric identification device
InactiveUS20070096870A1Reduce insecurityImprove securityElectric signal transmission systemsImage analysisEngineeringIdentification device
An improved electronic lock box system is provided for more secure control over the accessibility of a secure compartment in the electronic lock box, which is typically used to store a dwelling key. The new system uses biometric identification sensors to determine if the correct, authorized user is attempting to access the secure compartment of the electronic lock box. In one embodiment, the biometric identification sensor uses thermal scanning to detect a person's fingerprint pattern. This is compared to previously stored (enrollment) biometric identification information / data, and if the “live” (observed) biometric identification information / data sufficiently correlates to the stored enrollment biometric identification information / data, access will be granted.
Owner:SENTRILOCK
Portable device having biometrics-based authentication capabilities
InactiveUS7549161B2Highly convenient, secured and reliableImpossible to alter, duplicate, or crackDigital data processing detailsUser identity/authority verificationPasswordUser authentication
Apparatus and method for implementing biometrics-based access control to a restricted resource. In a preferred embodiment, the present invention is realized using a portable device. Specifically, in one embodiment, the portable device includes a microprocessor, a non-volatile memory coupled thereto, and a biometrics-based authentication module controlled by the microprocessor. Preferably, the biometrics technology used is fingerprint authentication technology. The authentication module is capable of registering a fingerprint upon first use of the portable device, storing an encoded version of the fingerprint in the non-volatile memory. Subsequently, the authentication module can read a person's fingerprint and reliably determine whether the fingerprint matches the registered fingerprint stored in the non-volatile memory. If a match is found, access to the restricted resource is granted to that person; otherwise, access is denied. Embodiments of the present invention thus provide a highly convenient, secured and reliable method and system for user authentication and access control which was not achievable in prior art password-based authentication approaches.
Owner:S COM SYST S
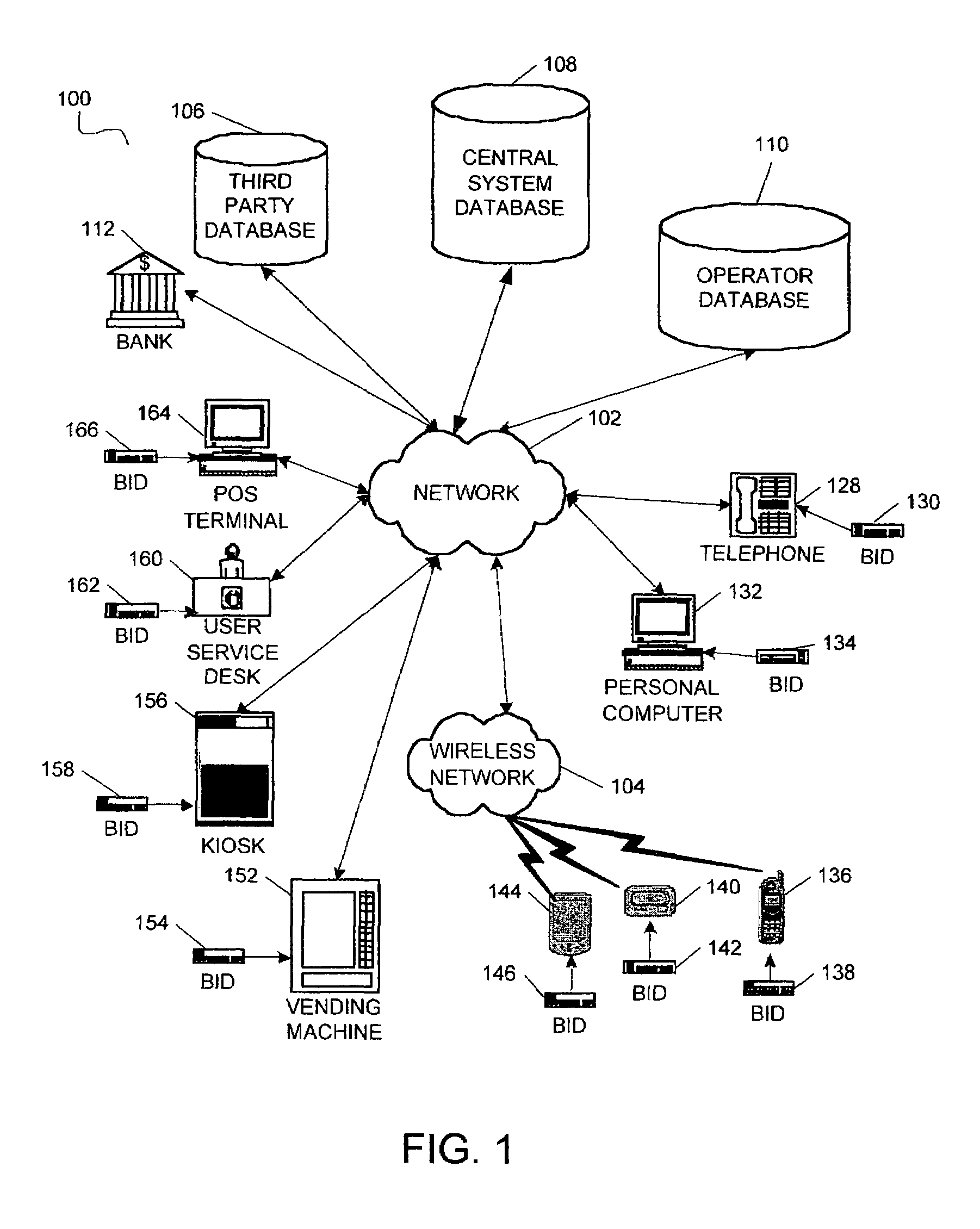
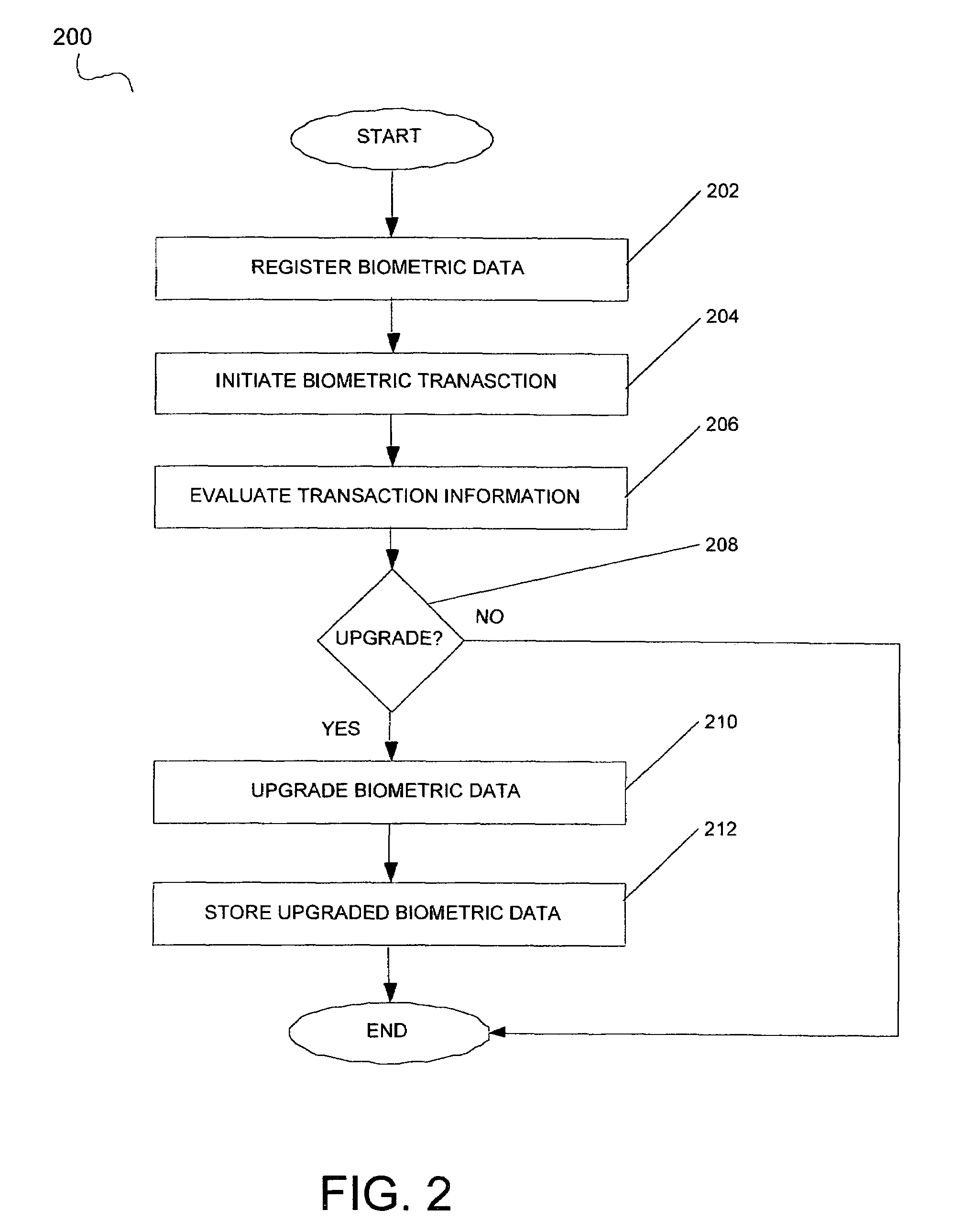
System and method for upgrading biometric data
ActiveUS7542590B1Biometric pattern recognitionAcquiring/reconising fingerprints/palmprintsBiometric dataAuthorization
A system and method of improving biometric information registered in a biometric authorization system is disclosed. System user biometric information entered into the system is upgraded at subsequent biometric authorizations at numerous biometric input devices.
Owner:PHILIPS NORTH AMERICA LLC
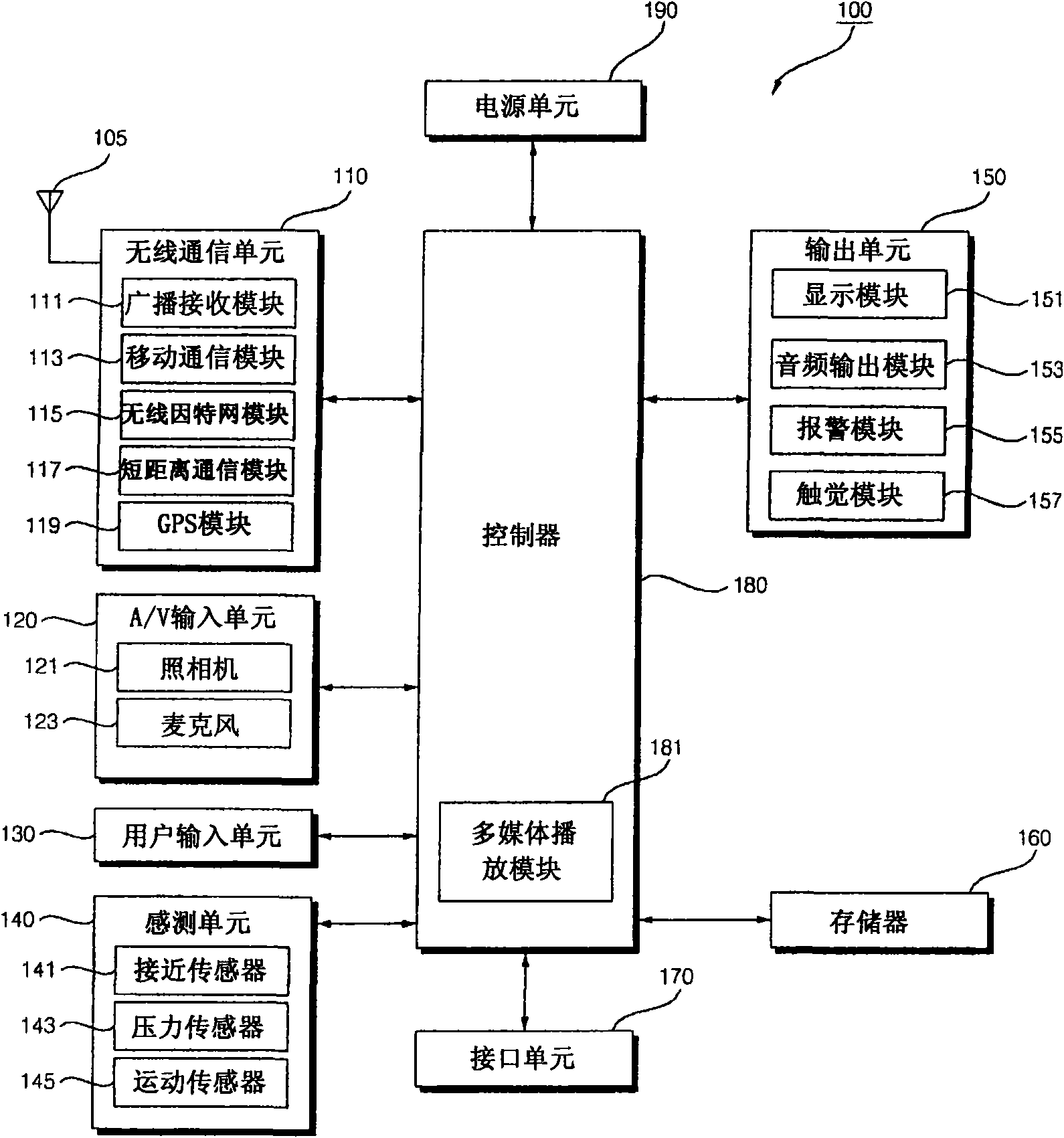
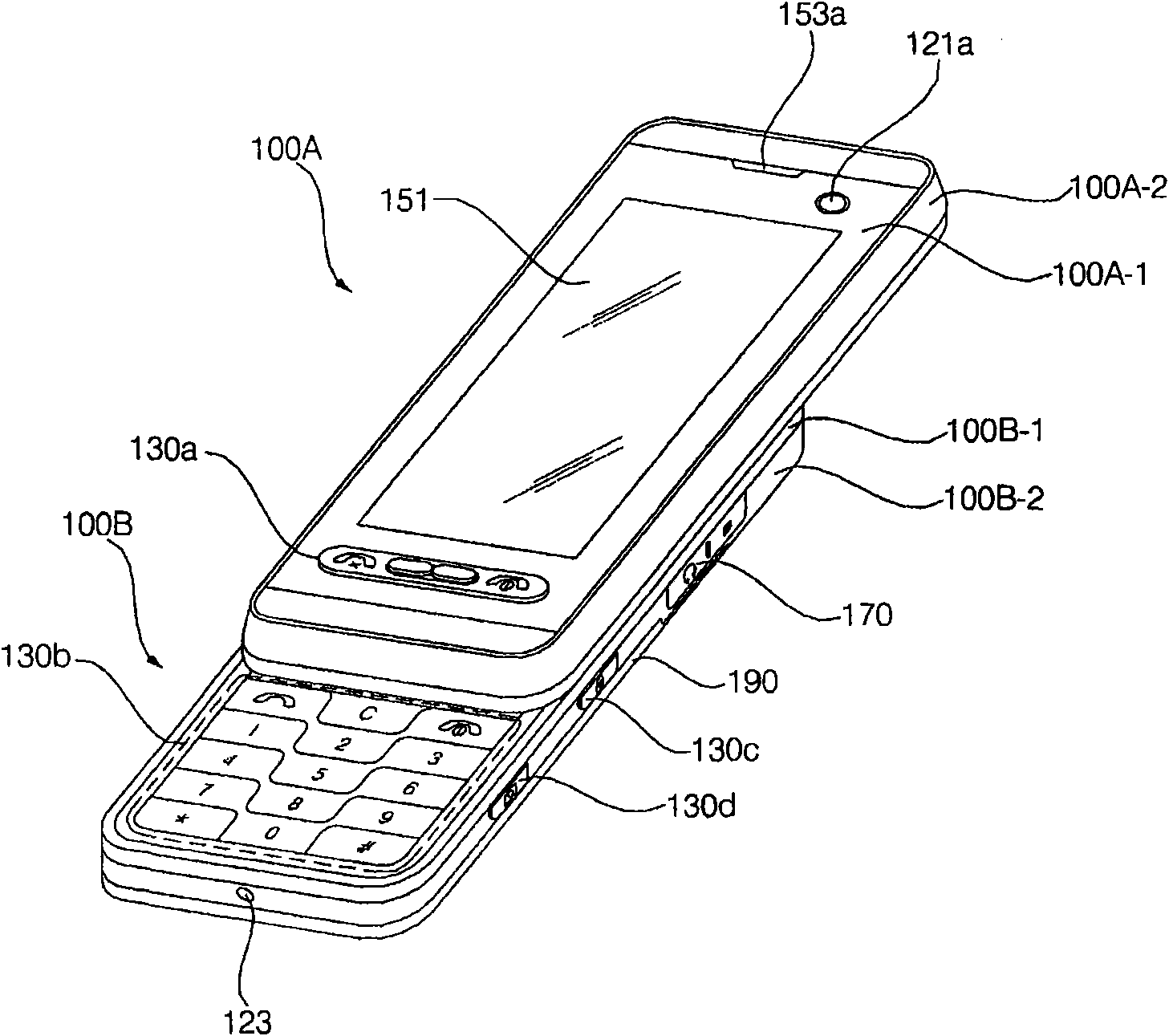
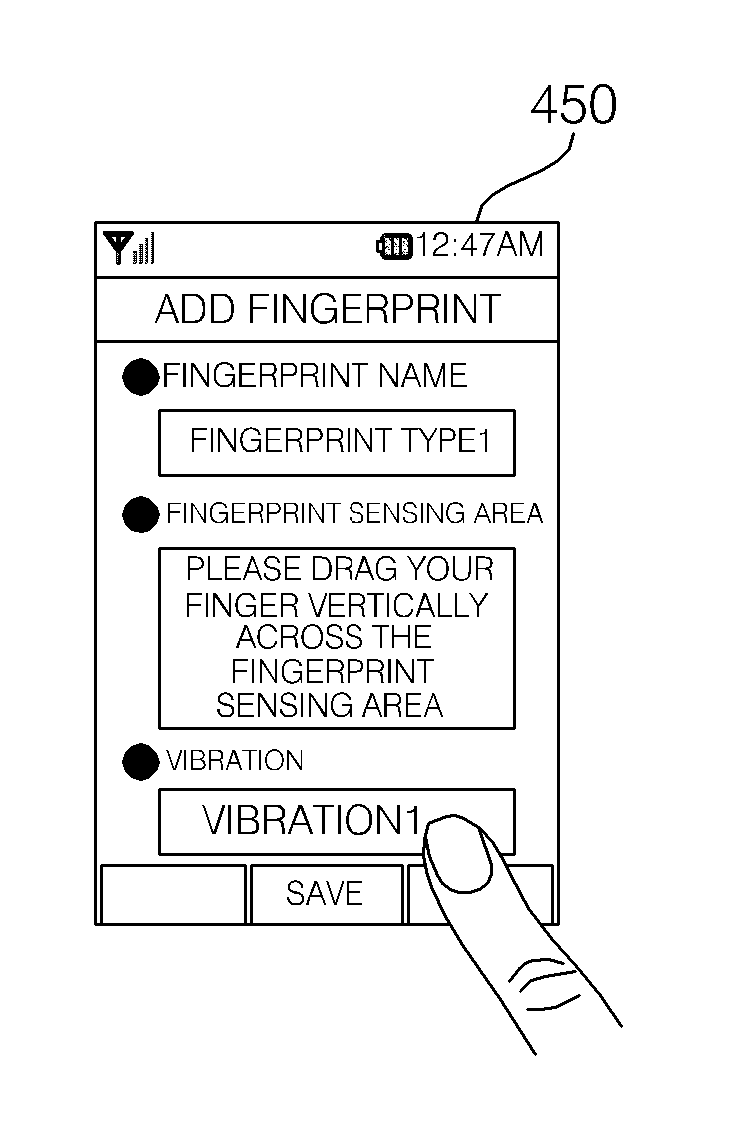
Mobile terminal and control method thereof
InactiveCN101833651AUnauthorised/fraudulent call preventionDigital data processing detailsComputer moduleComputer terminal
A mobile terminal and a method of controlling the mobile terminal are provided. The method includes storing a plurality of pieces of fingerprint information on at least one of a finger-by-finger basis, on a user-by-user basis, and a pattern-by-pattern basis; receiving a fingerprint-touch input through a display module capable of identifying a fingerprint; and if fingerprint information of the received fingerprint-touch input matches with one of the plurality of pieces of fingerprint information, performing a first control operation corresponding to the fingerprint information that matches with the fingerprint information of the received fingerprint-touch input. Therefore, it is possible to control various operations performed by the mobile terminal in response to a fingerprint-touch inputincluding fingerprint information.
Owner:LG ELECTRONICS INC
Integrated keypad system
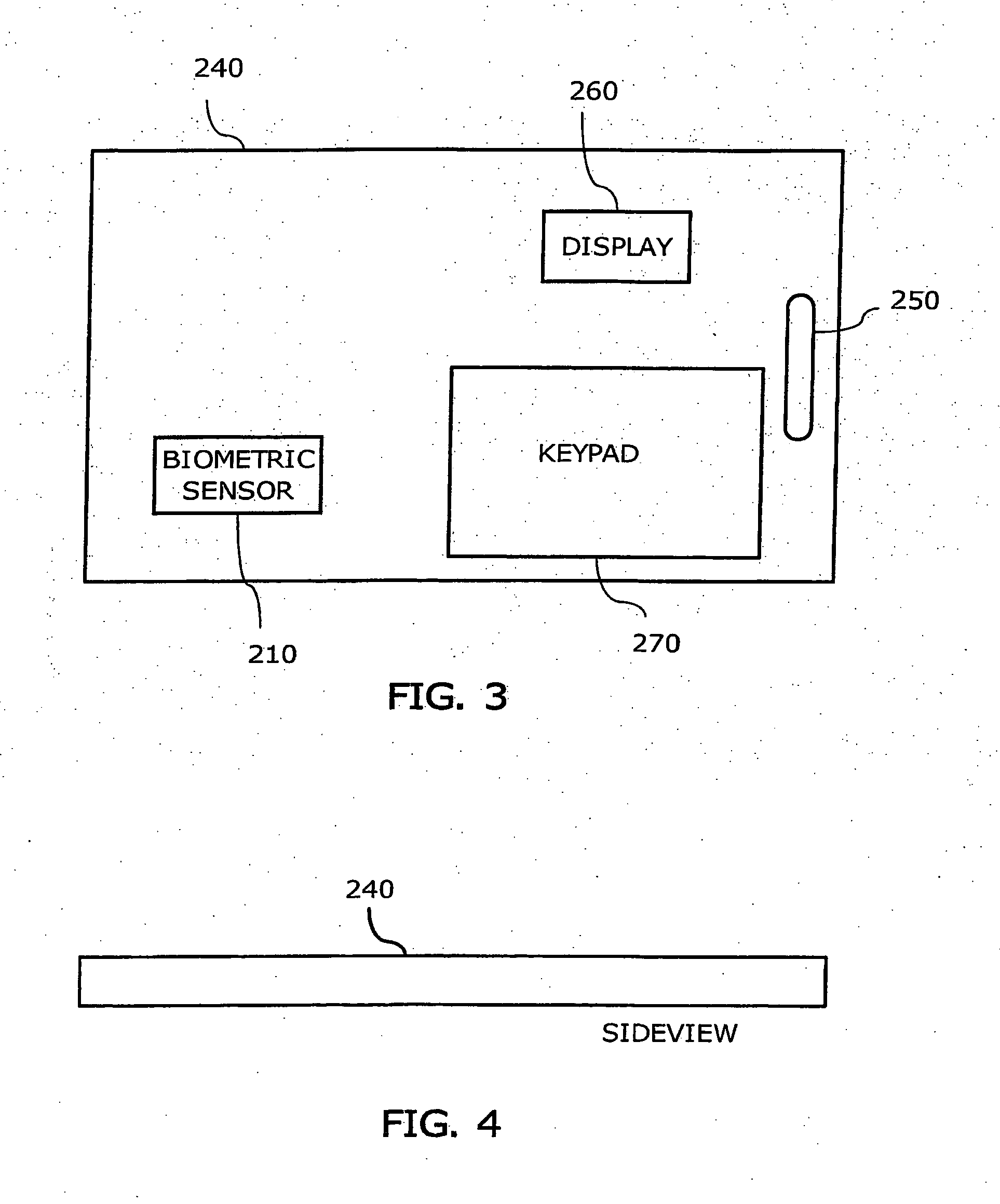
InactiveUS20050253814A1Quick distinctionAvoid lengthInput/output for user-computer interactionElectronic switchingArtificial intelligenceSpeech sound
A data entry system includes a predefined number of keys for at least inputting arbitrary characters through the keys. The data entry system uses a number of symbols having at least the letters of the alphabet of at least one language and where the symbols are assigned to the keys such that at least two of the letters are assigned to at least one of the keys. A symbol assigned to a key is inputted by providing a predefined type of interaction such as one type of pressing action on the key and providing a speech information corresponding to the symbol. The speech information is detected and analyzed based on at least one of, a user's voice and a user's lips movements. The data entry system uses a database of words of a language such that in order to enter a word of the database a user provides a combined information corresponding to the word, where the combined information includes a first and second type of information. The first type of information includes entering precisely at least one of the letters of the word by providing a corresponding pressing action on a key corresponding to the at least one letter and speaking the at least one letter. The second type of information includes providing the key presses corresponding to at least some of the other characters of the word, and based on the combined information, the system predicts the word.
Owner:FIROOZ GHASSABIAN +1
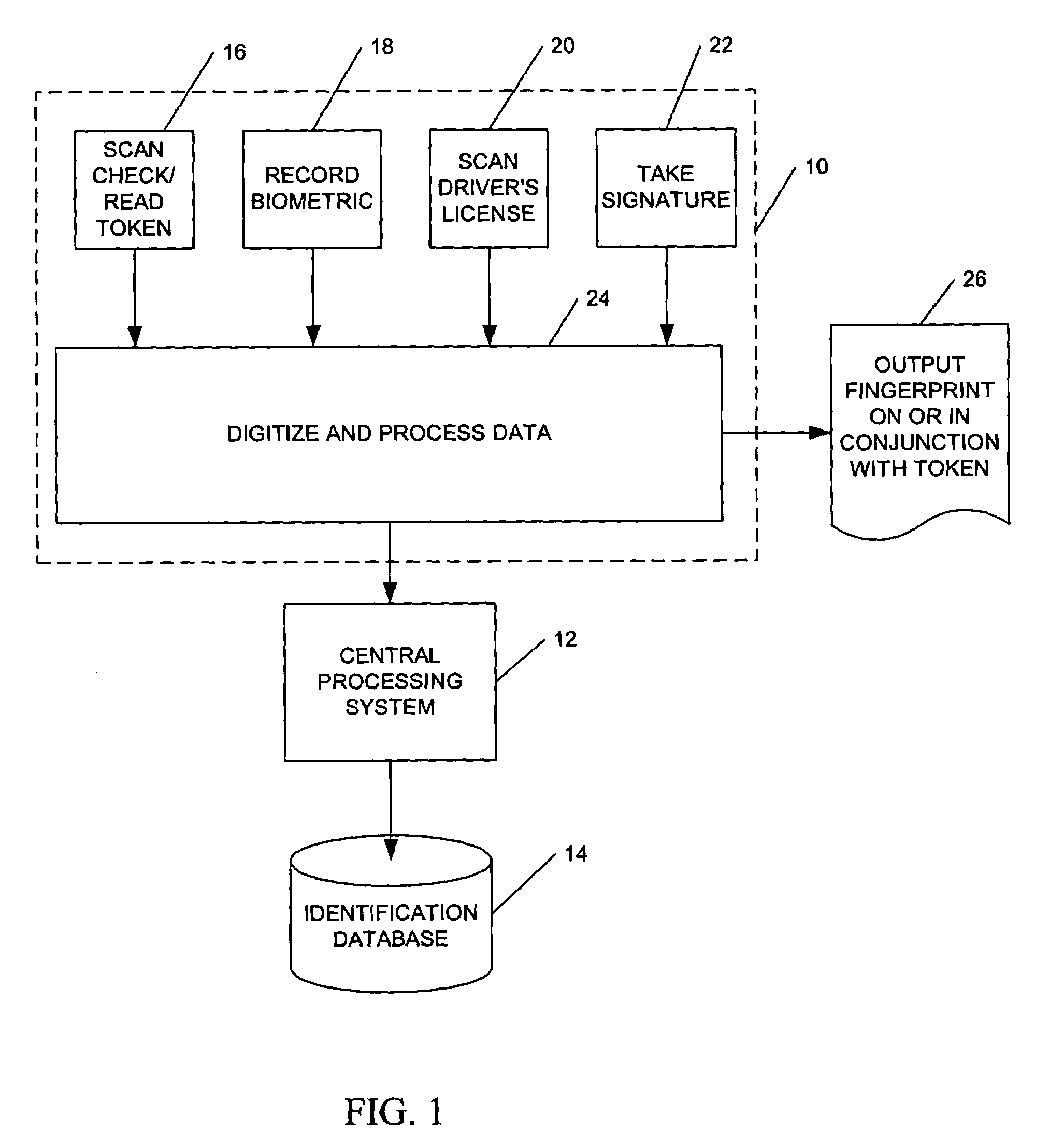
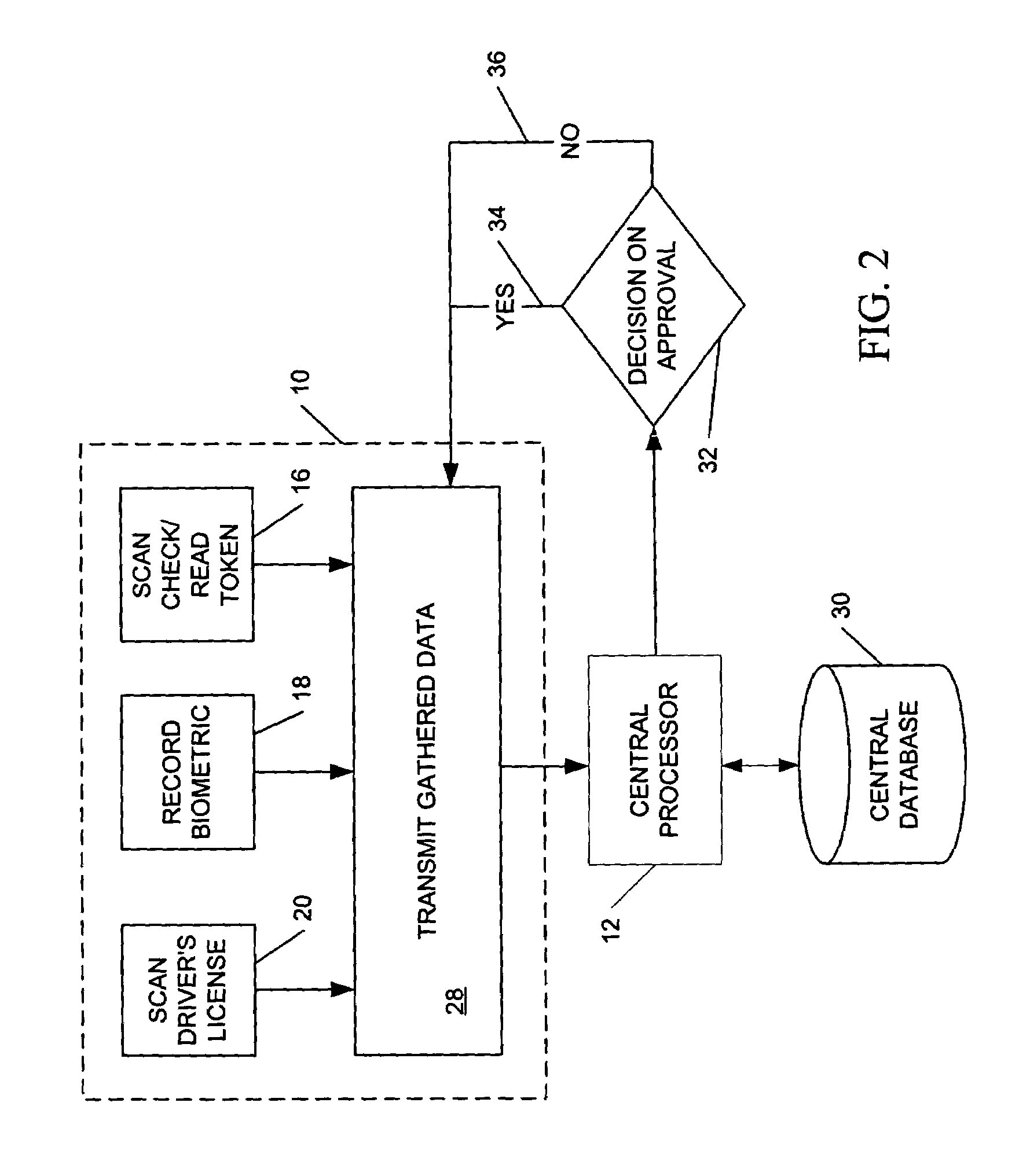
Electronic transaction verification system
InactiveUS7349557B2Inhibitory activityIndustrial applicabilityElectric signal transmission systemsDigital data processing detailsPaymentBiometric data
An electronic transaction verification system for use at a location where a transaction token is presented for payment. The electronic transaction verification system digitizes various indicia of the token, and transmits the transaction information data to a central processing system. The central processing system compares the transaction data with an existing database of information to determine if the customer at the point of the transaction is authorized to use the account. The electronic verification system includes a biometric data device for recording and / or transmitting biometric data taken at the transaction location. The electronic transaction verification system can be used in conjunction with a tokenless transaction processing system to determine if the token presented for payment is associated with an account established for an authorized user that has registered with the tokenless transaction processing system.
Owner:BIOMETRIC PAYMENT SOLUTIONS
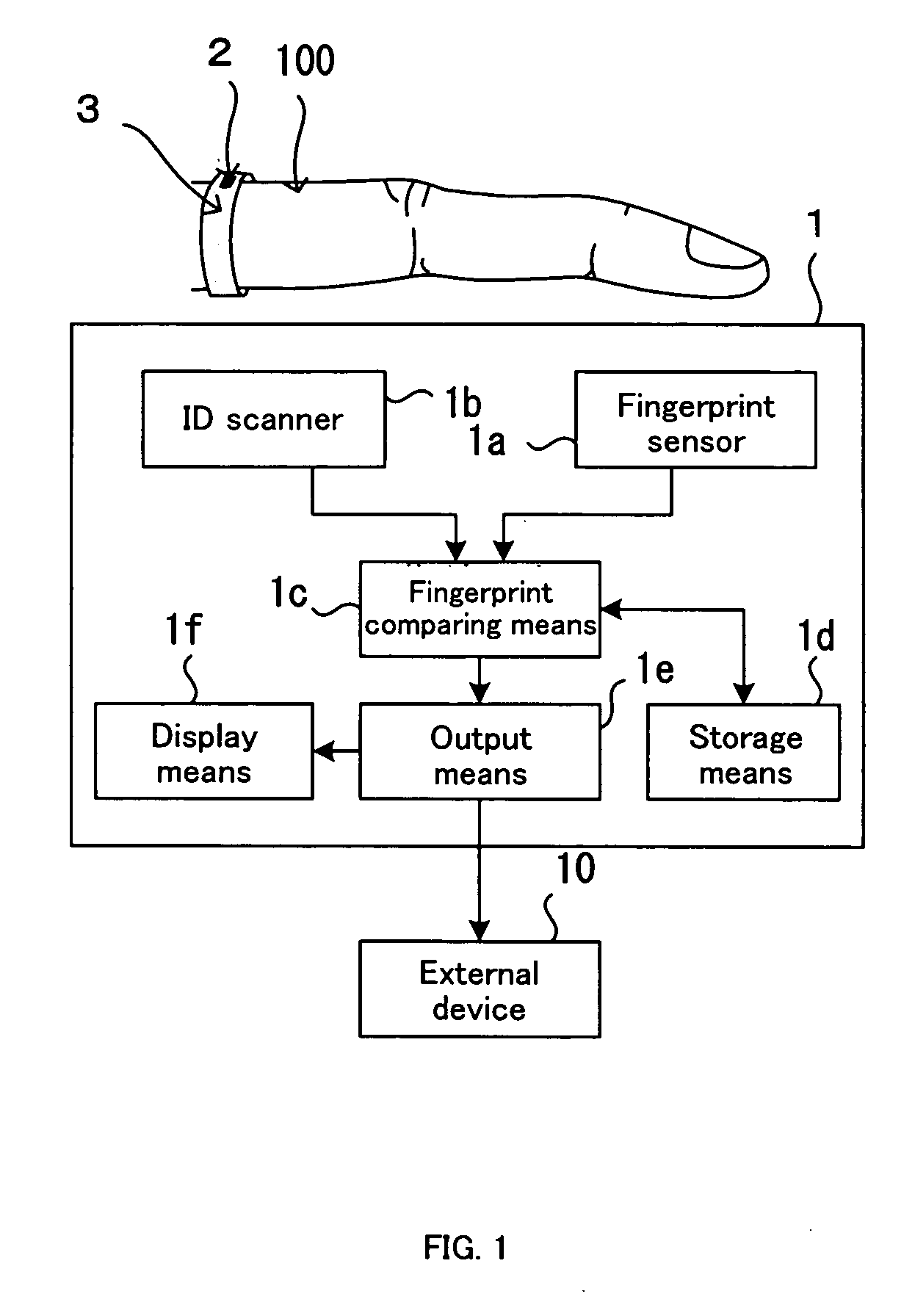
Personal identification device and system having personal identification device
InactiveUS20060274920A1Simple configurationEasy to operateElectric signal transmission systemsImage analysisComputer hardwareIdentification device
A personal identification device 1 comprises a fingerprint sensor 1a that detects a fingerprint; and a scanner 1b that calls a storage medium 2 mounted on a portable device 3 worn on a finger, a wrist, or an ankle of a user for reading recording information stored on the storage medium 2. The fingerprint sensor and the scanner are integrally provided in a device main body of the personal identification device. The personal identification device further comprises fingerprint comparison means 1c for comparing fingerprint data of a user's finger detected by the fingerprint sensor 1a with fingerprint comparison data read by the scanner 1b from the storage medium 2 of the portable device 3 worn on the finger or the wrist of the user. The fingerprint comparison means 1c identifies that the holder of the storage medium is an authentic user based on a match between the fingerprint data and the fingerprint comparison data.
Owner:YOKOHAMA TLO
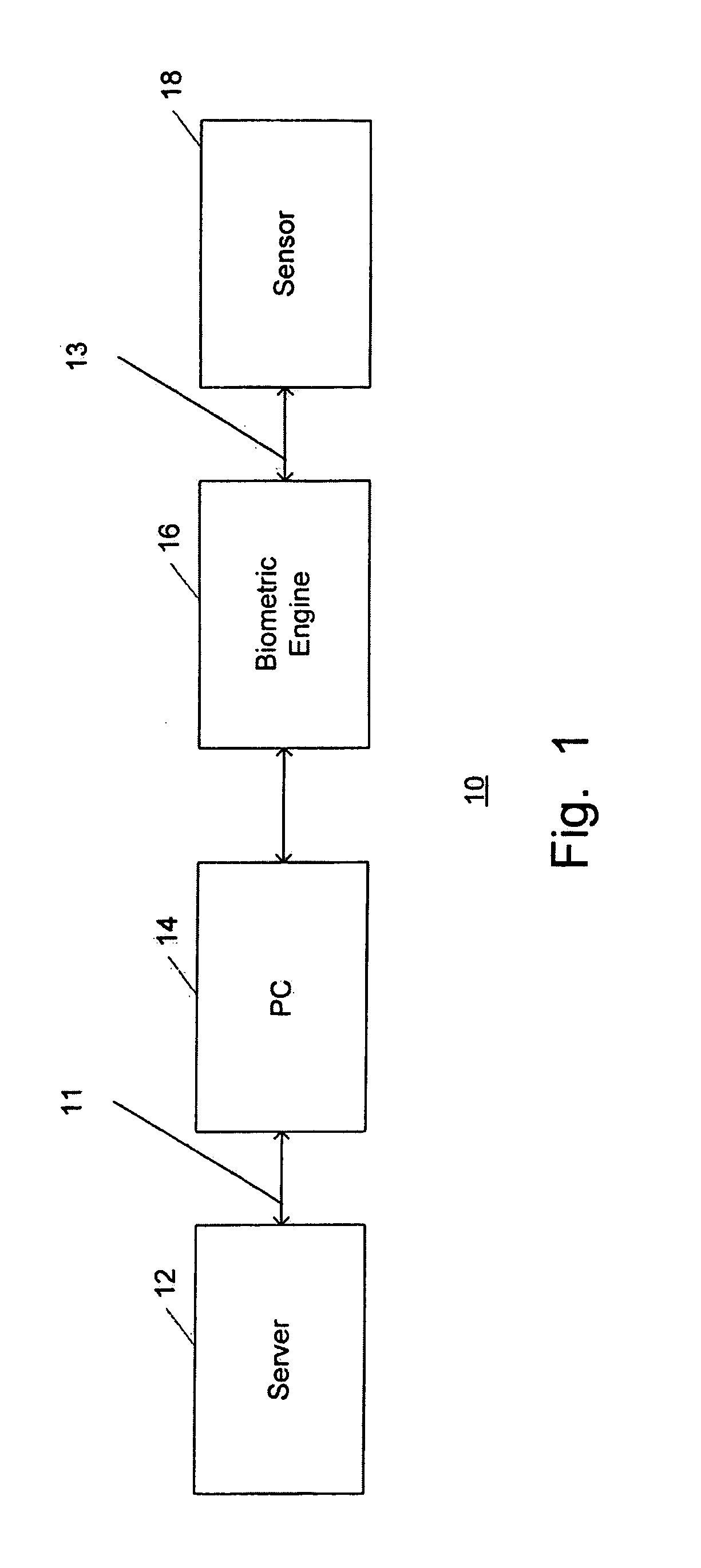
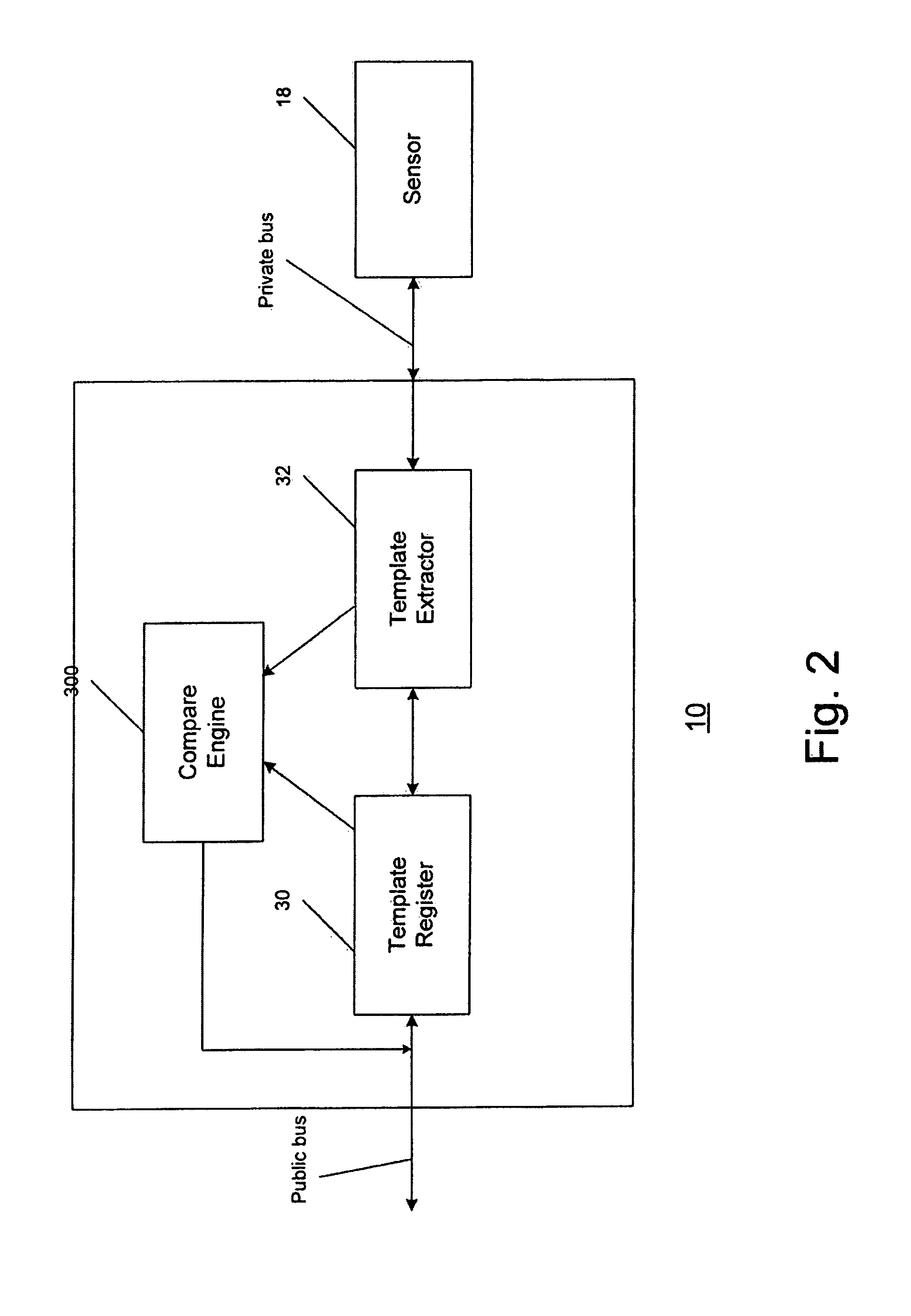
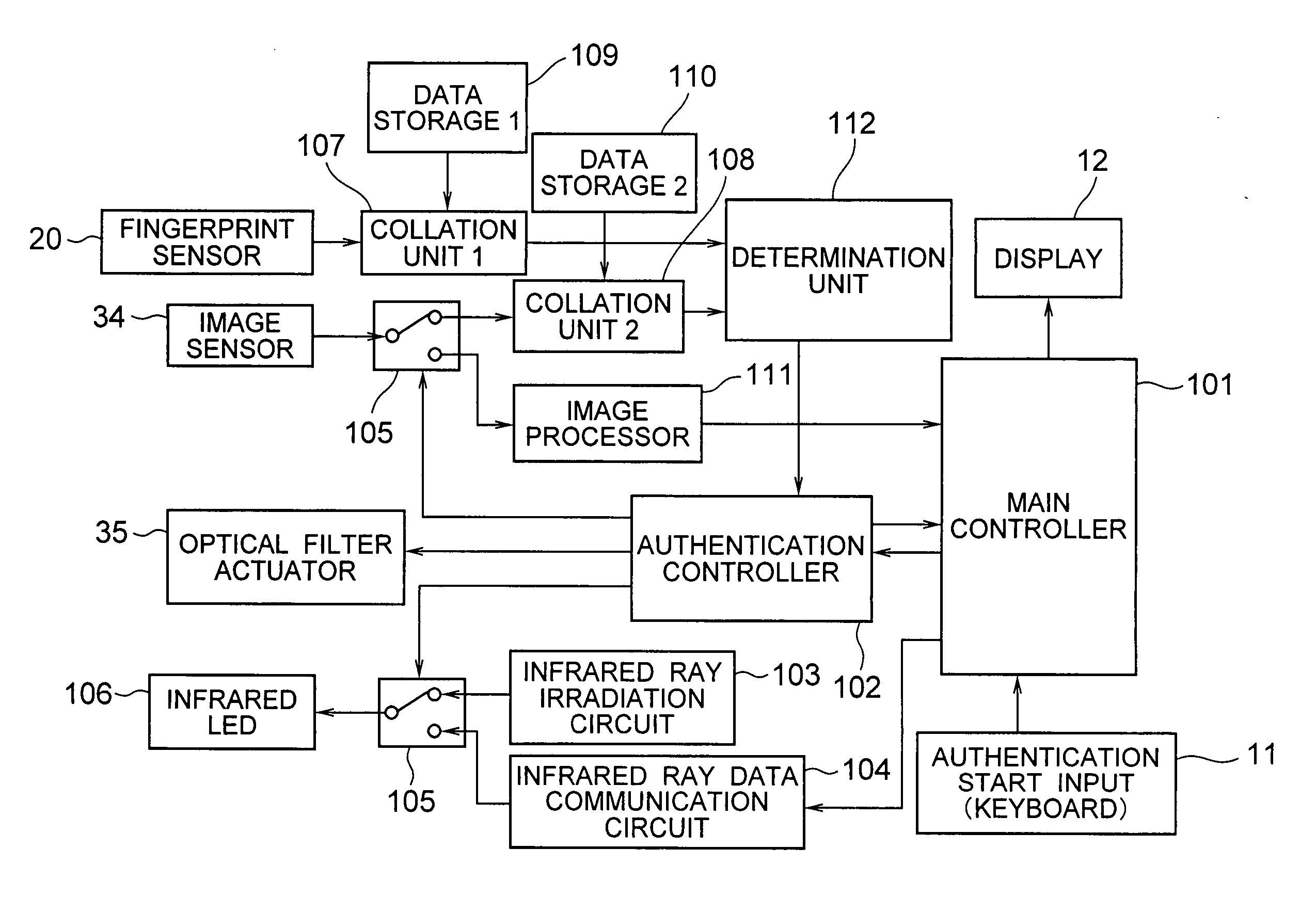
Secure biometric processing system and method of use
InactiveUS20070237366A1Programme controlElectric signal transmission systemsSecurity designHandling system
A secure biometric processing system is disclosed. The system comprises a processing system for providing image acquisition and biometric comparison. The processing unit utilizes public key cryptography for handling templates securely and authenticating operations using the template. The system includes a complete biometric engine which implements image reconstruction, template extraction and matching. The secure design of the system combines complete privacy with security, while offering a flexible usage model including on-chip template storage along with encrypted and authenticated communications to the system.
Owner:ATMEL CORP
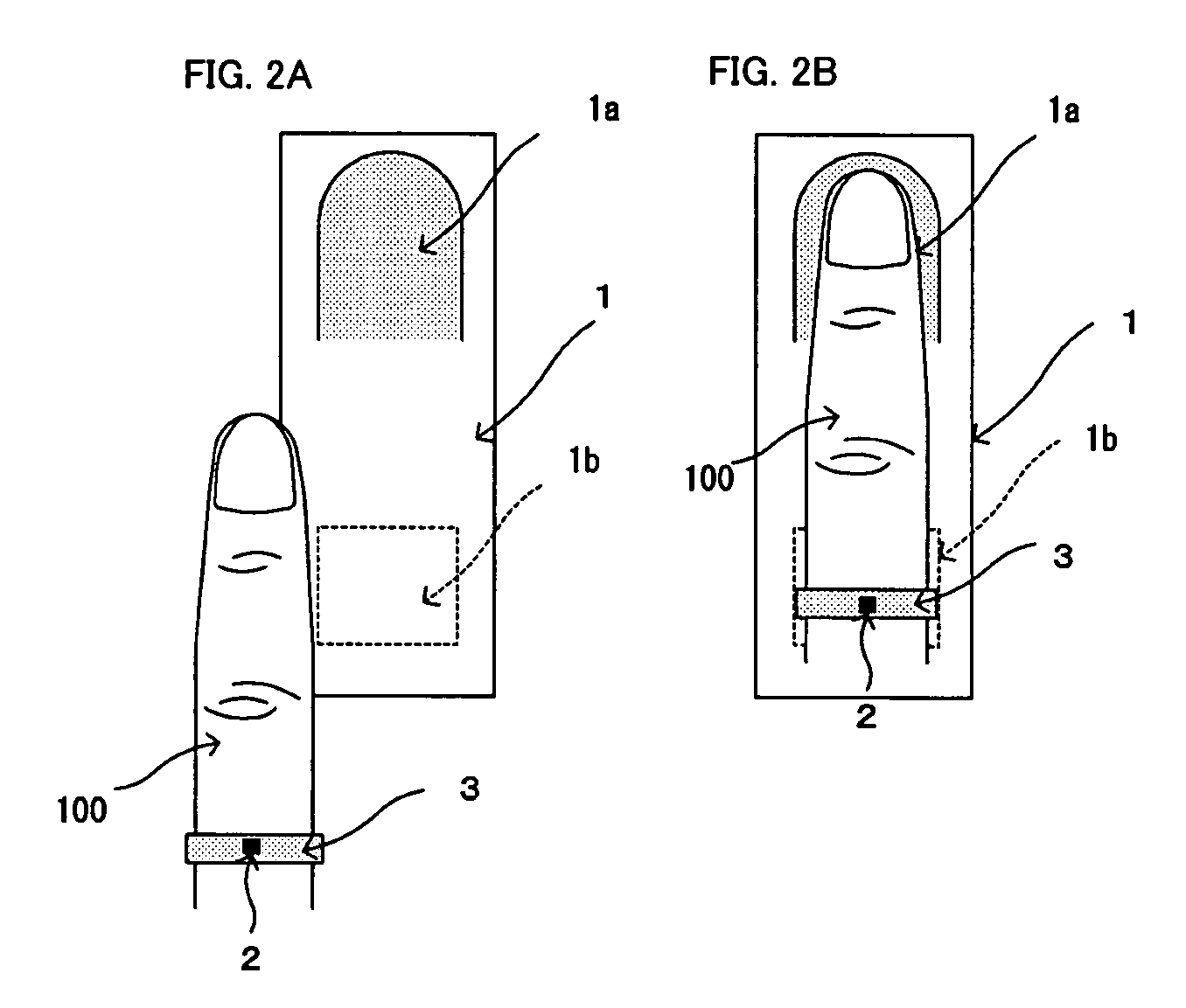
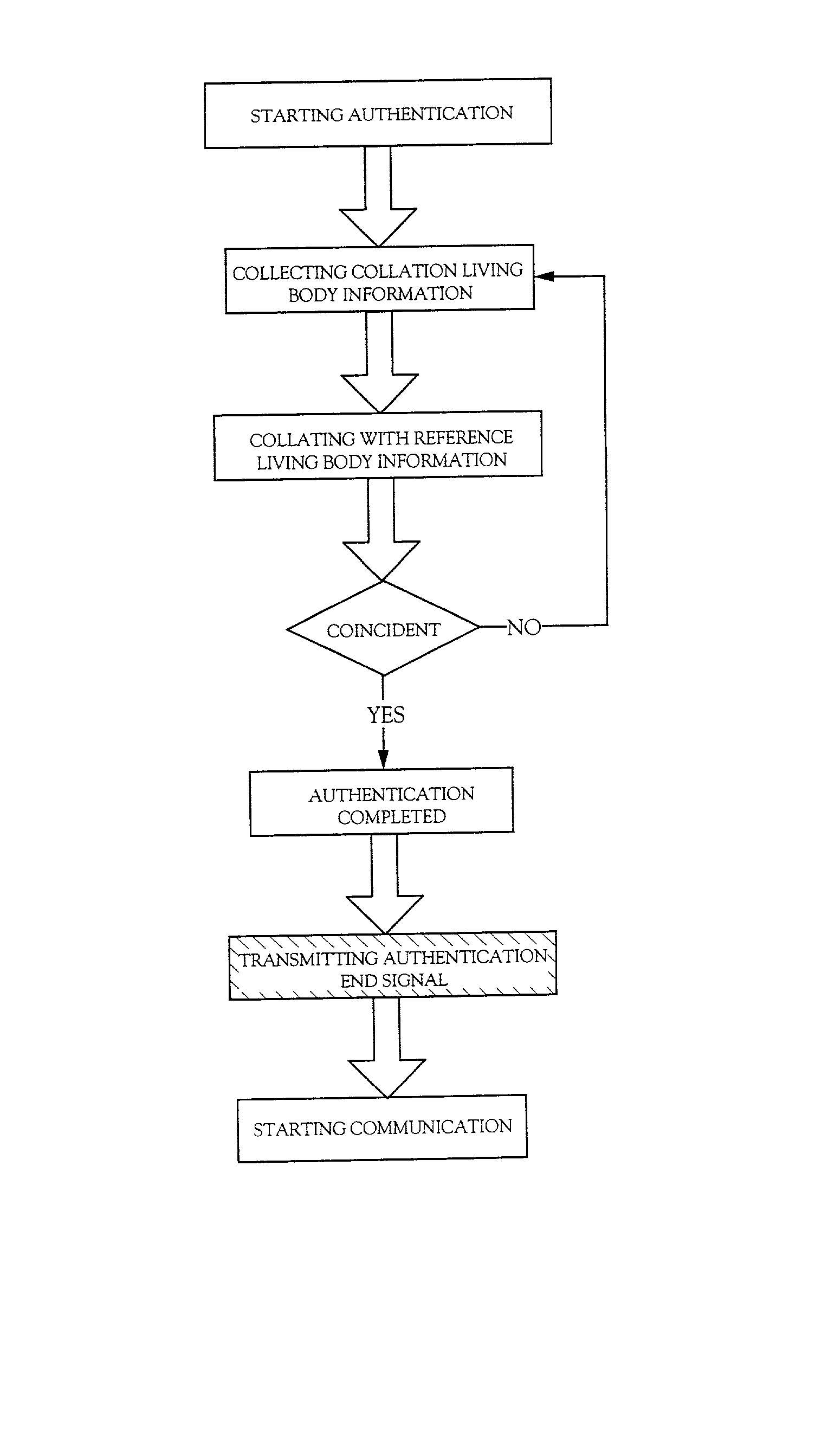
Communication system
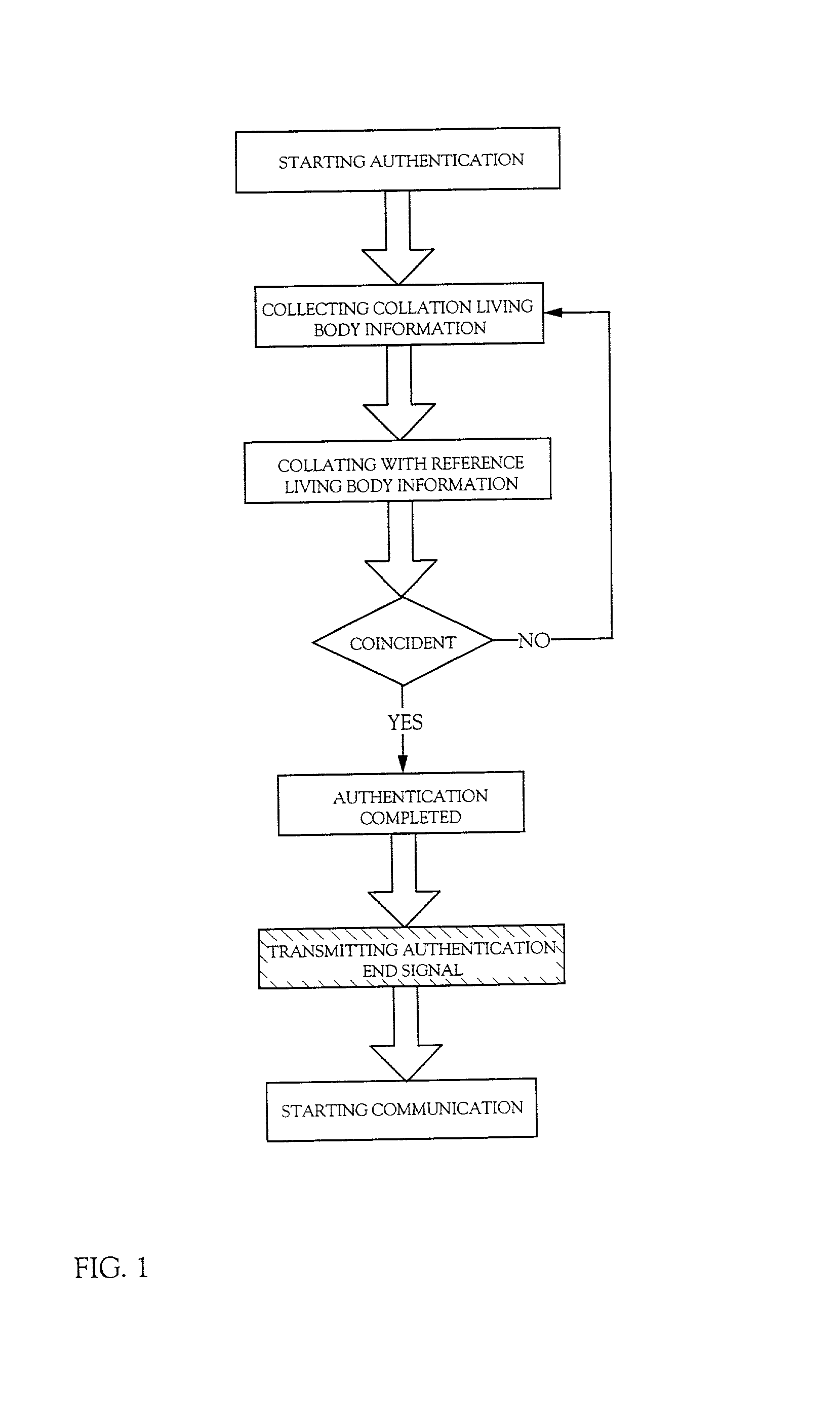
InactiveUS20020049714A1Digital data processing detailsDigital data authenticationBiological bodyCommunications system
A communication system capable of easily distinguishing a user includes means for storing reference living body information, means for reading collation living body information of the user, means for collating the collation living body information with the reference living body information and means for sending a notice of coincidence as data to a mating party when the collation result proves coincident.
Owner:SEMICON ENERGY LAB CO LTD
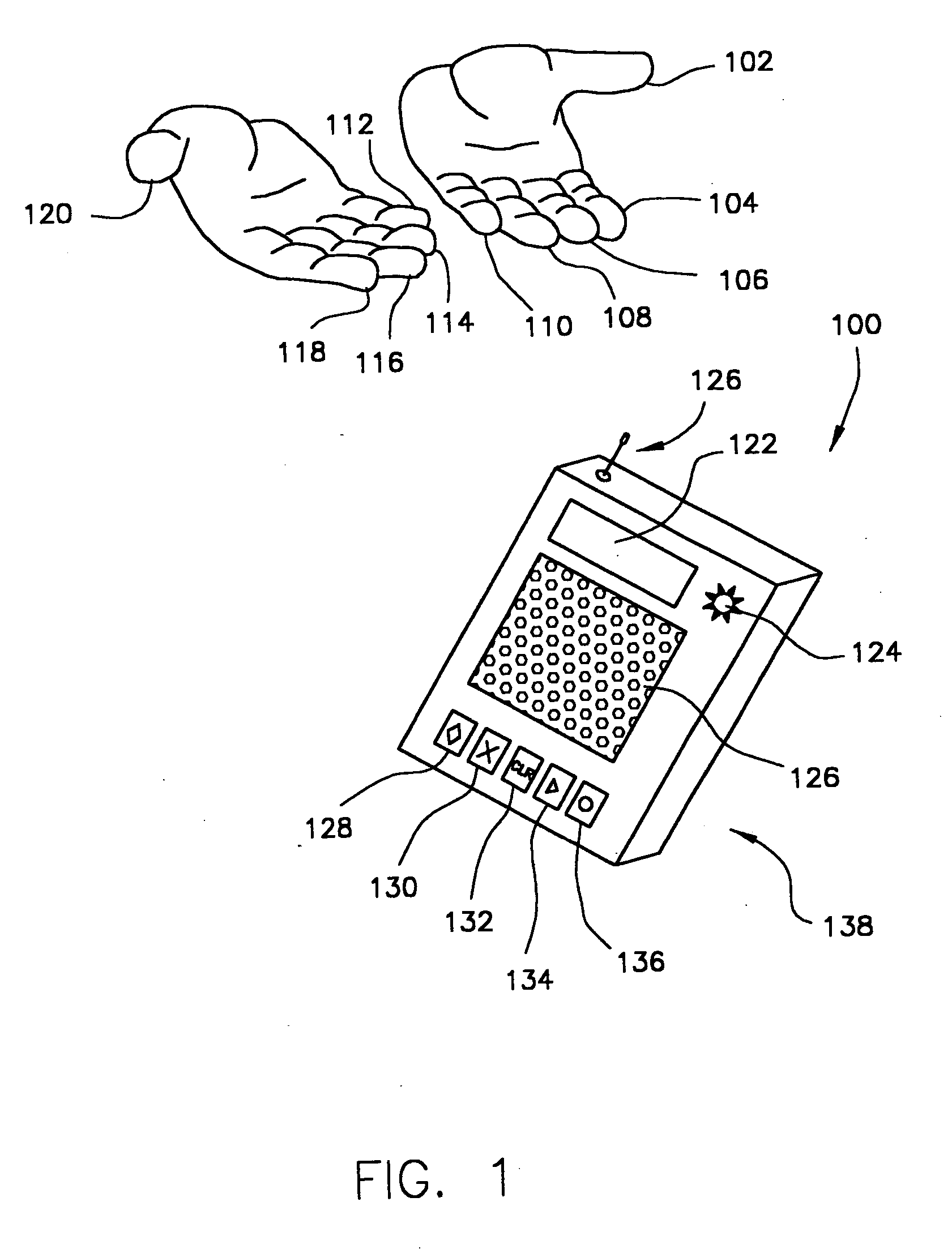
Method for identity verification
InactiveUS20050169504A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:PEN ONE INC
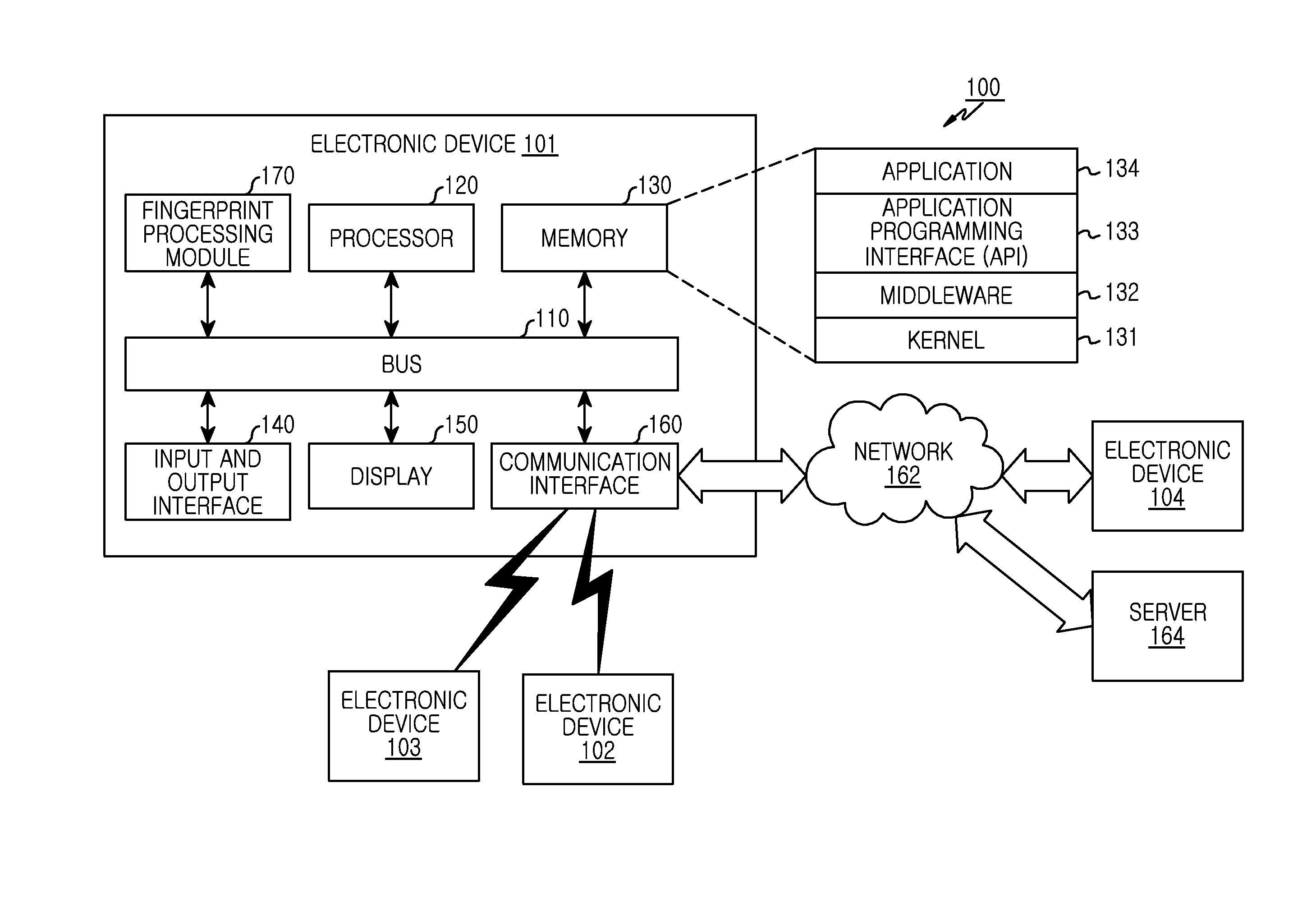
Method for processing fingerprint and electronic device thereof
ActiveUS20150220767A1Digital data authenticationAcquiring/reconising fingerprints/palmprintsDisplay deviceFingerprint
A method of operating an electronic device and the electronic device is provided. The method includes setting a fingerprint detecting area functionally connected to a display; identifying a function corresponding to a gesture of an input means input to the display, and determining whether to perform the function with fingerprint information acquired in the fingerprint detecting area. The electronic device includes a display configured to display at least one content; a memory configured to store at least one fingerprint information acquired in a fingerprint detecting area; the fingerprint detecting area functionally connected to the display; and at least one processor configured to set the fingerprint detecting area, identify a function corresponding to a gesture of an input means input to the display, and determine whether to perform the function with the at least one fingerprint information acquired in the fingerprint detecting area.
Owner:SAMSUNG ELECTRONICS CO LTD
Remote control with the fingerprint recognition capability
InactiveUS20030108227A1Television system detailsColor television detailsPattern recognitionRemote control
Disclosed is a method and system for controlling access to a television set using a remote control unit having a finger verification means. The method includes the steps of: placing at least one finger on the remote control unit for scanning; obtaining fingerprint data indicative of the scanned finger; comparing the fingerprint data to predetermined reference data to establish a fingerprint match; and, if a match is established, providing access to a number of channels associated with the scanned finger. The system includes a fingerprint reader for generating fingerprint data; a processor programmed to prompt the user to enter fingerprint data; and, a fingerprint recognition means for verifying that the user is an authorized user of the remote control apparatus.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Transaction authentication card
InactiveUS20070220272A1Acutation objectsComputer security arrangementsComputer hardwareUser verification
A transaction authentication card uses a biometric input and a wireless output. The biometric input may be a sensor pad on the transaction authentication card that measures blood flow patterns, temperature, and / or fingerprint patterns to identify a user to permit access. The transaction authentication card is preferably substantially rigid, but may be formed to have some flexibility. Power to the transaction authentication card may be accomplished through an internal battery that is optionally rechargeable. Biometric data is stored on the card only and used for user verification. Biometric data will not be transferred from the card. If authorized biometric data is authenticated the card will transmit a wireless access code to a proximity reader or transaction equipment.
Owner:RESILENT
Mobile terminal and method of controlling the mobile terminal
InactiveUS20100231356A1Effective controlInput/output for user-computer interactionElectric signal transmission systemsComputer hardwareFingerprint
A mobile terminal and a method of controlling the mobile terminal are provided. The method includes storing a plurality of pieces of fingerprint information on at least one of a finger-by-finger basis, on a user-by-user basis, and a pattern-by-pattern basis; receiving a fingerprint-touch input through a display module capable of identifying a fingerprint; and if fingerprint information of the received fingerprint-touch input matches with one of the plurality of pieces of fingerprint information, performing a first control operation corresponding to the fingerprint information that matches with the fingerprint information of the received fingerprint-touch input. Therefore, it is possible to control various operations performed by the mobile terminal in response to a fingerprint-touch input including fingerprint information.
Owner:LG ELECTRONICS INC
Mobile communication terminal, authentication method and authentication program
InactiveUS20070057764A1Reduce bothersome workImprove authentication accuracyElectric signal transmission systemsUnauthorised/fraudulent call preventionAuthenticationControl unit
A mobile communication terminal having a security function using biological information for authentication includes: authentication units for performing authentication based on at least two kinds of biological information; and a control unit for performing operational control of the authentication units. The control unit has a function of proceeding with capturing of biological information and authentication processing based on the captured biological information, performed for the respective kinds of biological information by the authentication units, in parallel.
Owner:NEC CORP
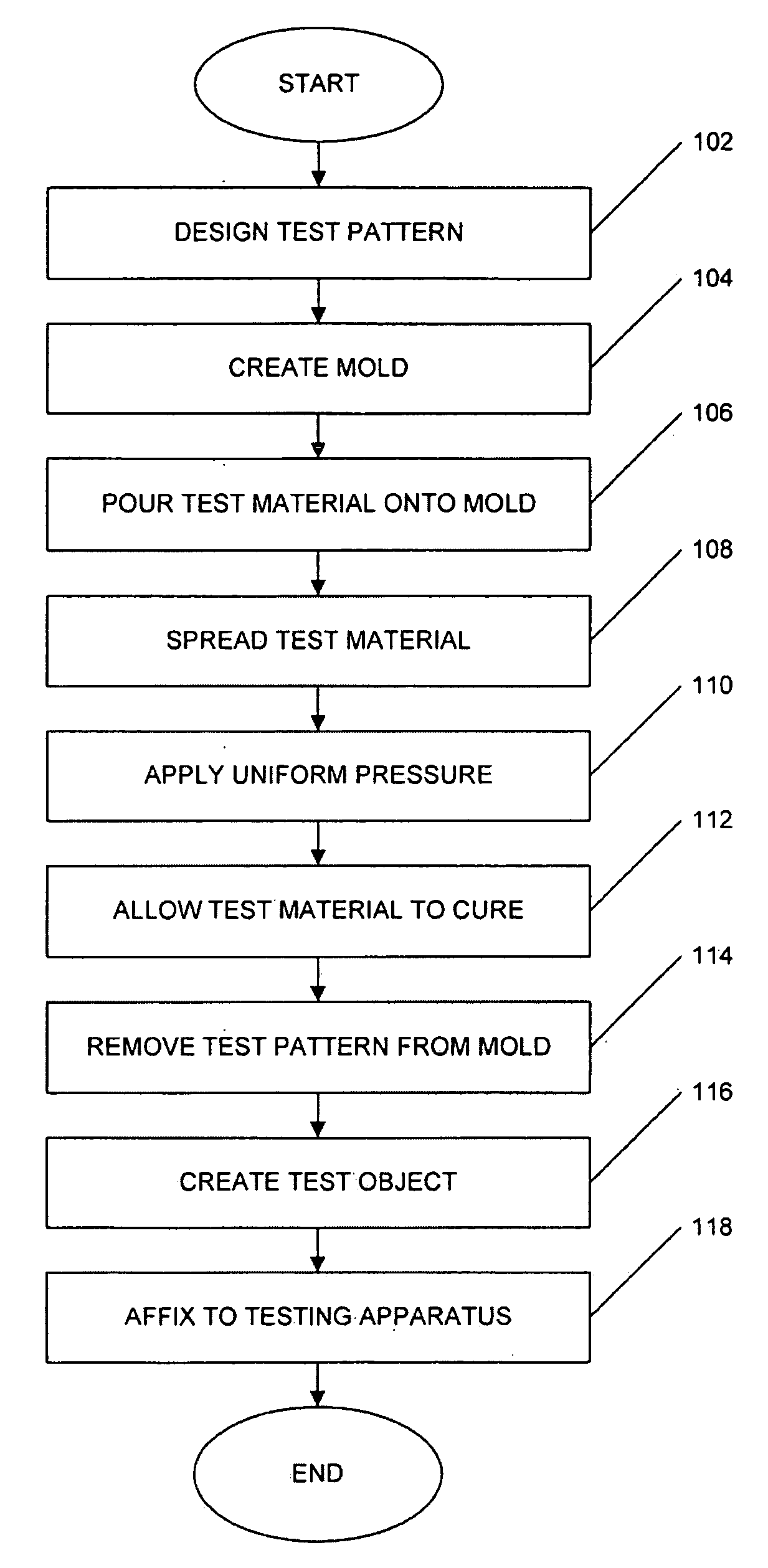
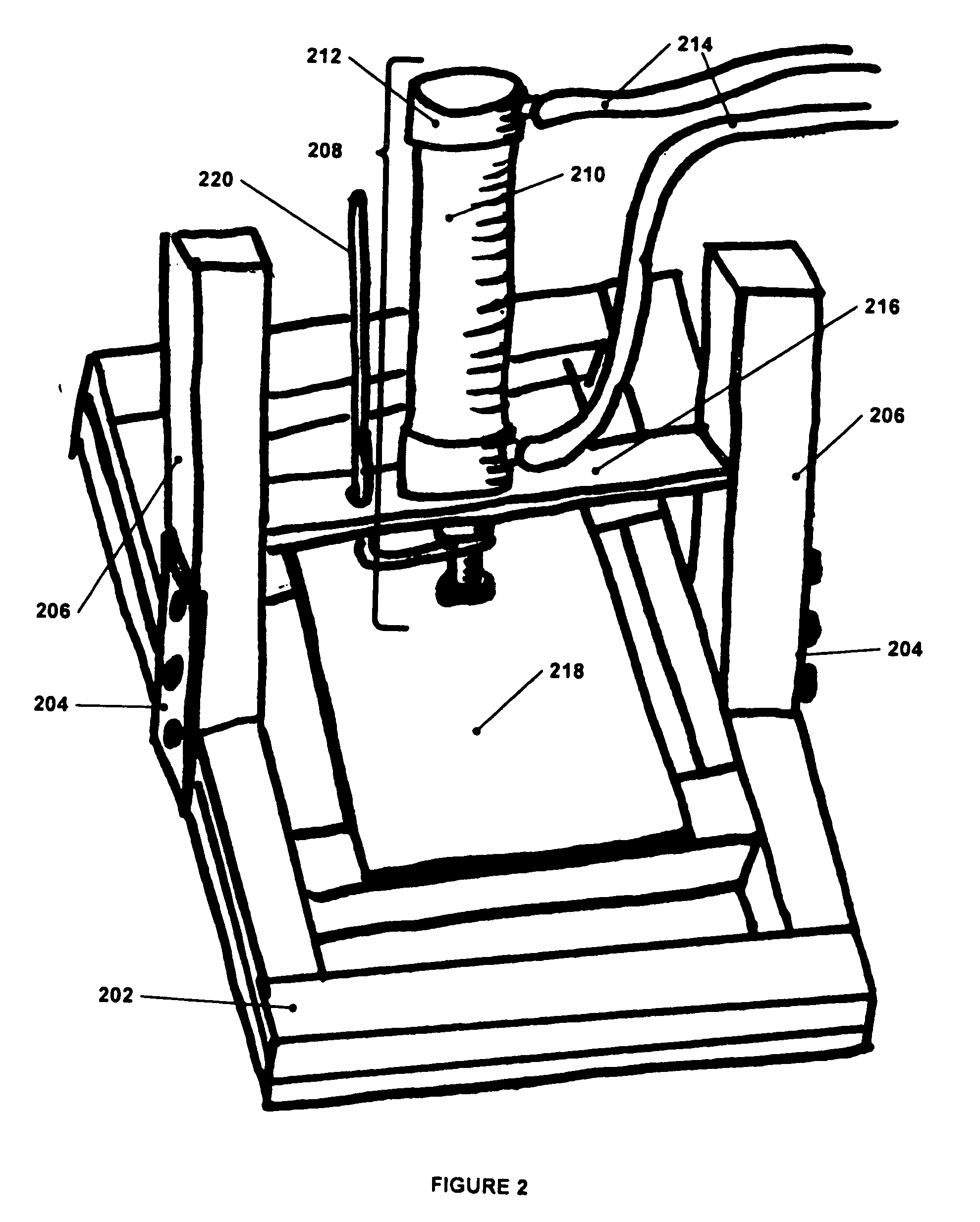
Apparatus and methods for testing biometric equipment
This invention encompasses an apparatus and methods which enable the testing of fingerprint readers in an automated fashion. A test object representative of a fingerprint can be created from an electrically conducive silicone material. Due to the properties of this material, the same test object can be read by fingerprint sensors of various types. Once the test object is generated, it can be affixed to an automated apparatus thus allowing tests to be conducted in closed chambers, on an assembly line, or under other conditions that would be impossible or impractical were human fingers to be used.
Owner:OPEN INVENTION NEWTORK LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com