Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
98 results about "Temporary variable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, a temporary variable is a variable with short lifetime, usually to hold data that will soon be discarded, or before it can be placed at a more permanent memory location. Because it is short-lived, it is usually declared as a local variable, i.e., a variable with local scope. There is no formal definition of what makes a variable temporary, but it is an often-used term in programming.
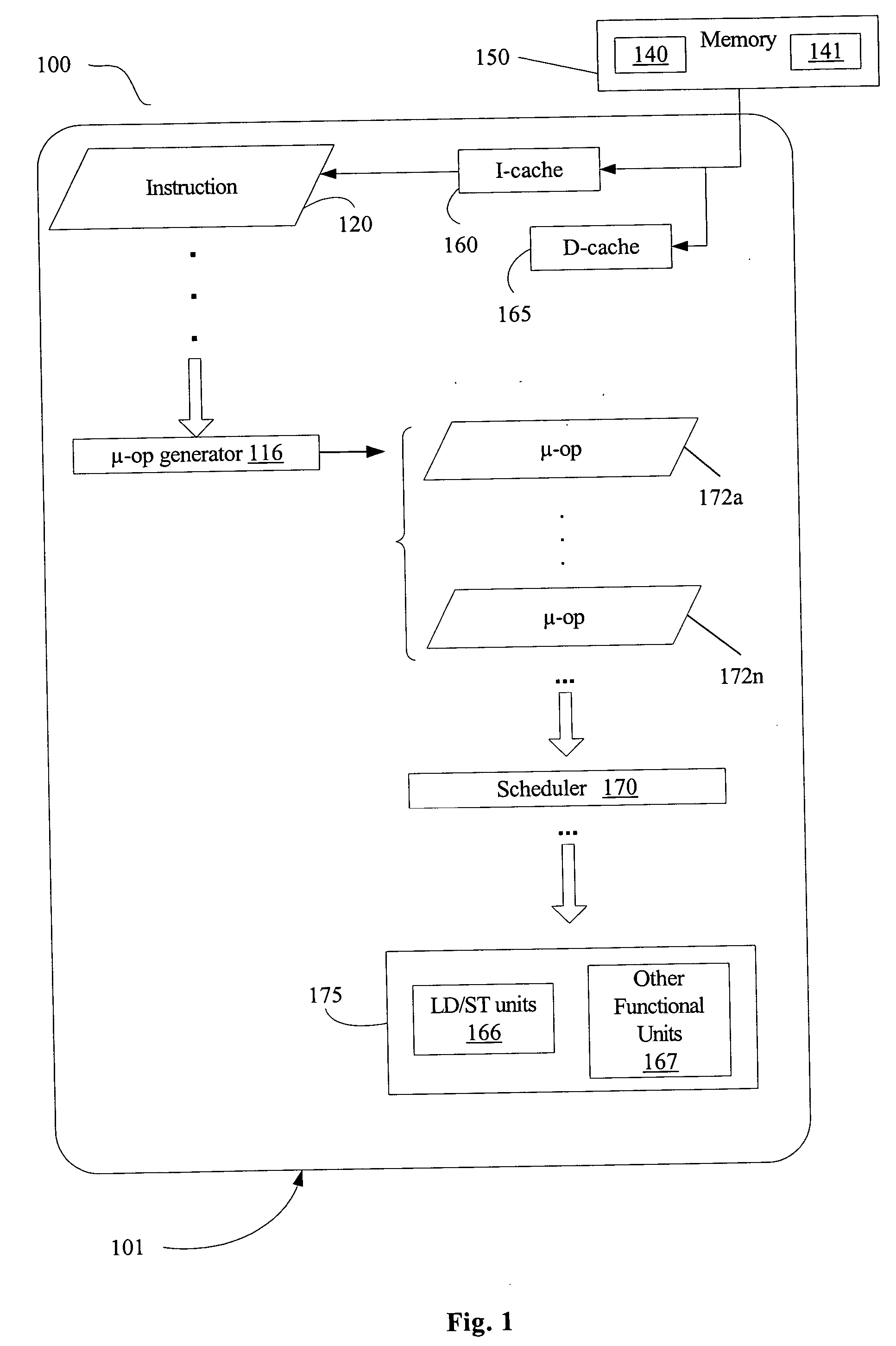
Tile-based processor architecture model for high-efficiency embedded homogeneous multicore platforms
ActiveUS20120303933A1Reduce power consumptionEasy to takeEnergy efficient ICTGeneral purpose stored program computerTemporary variableCommunication link
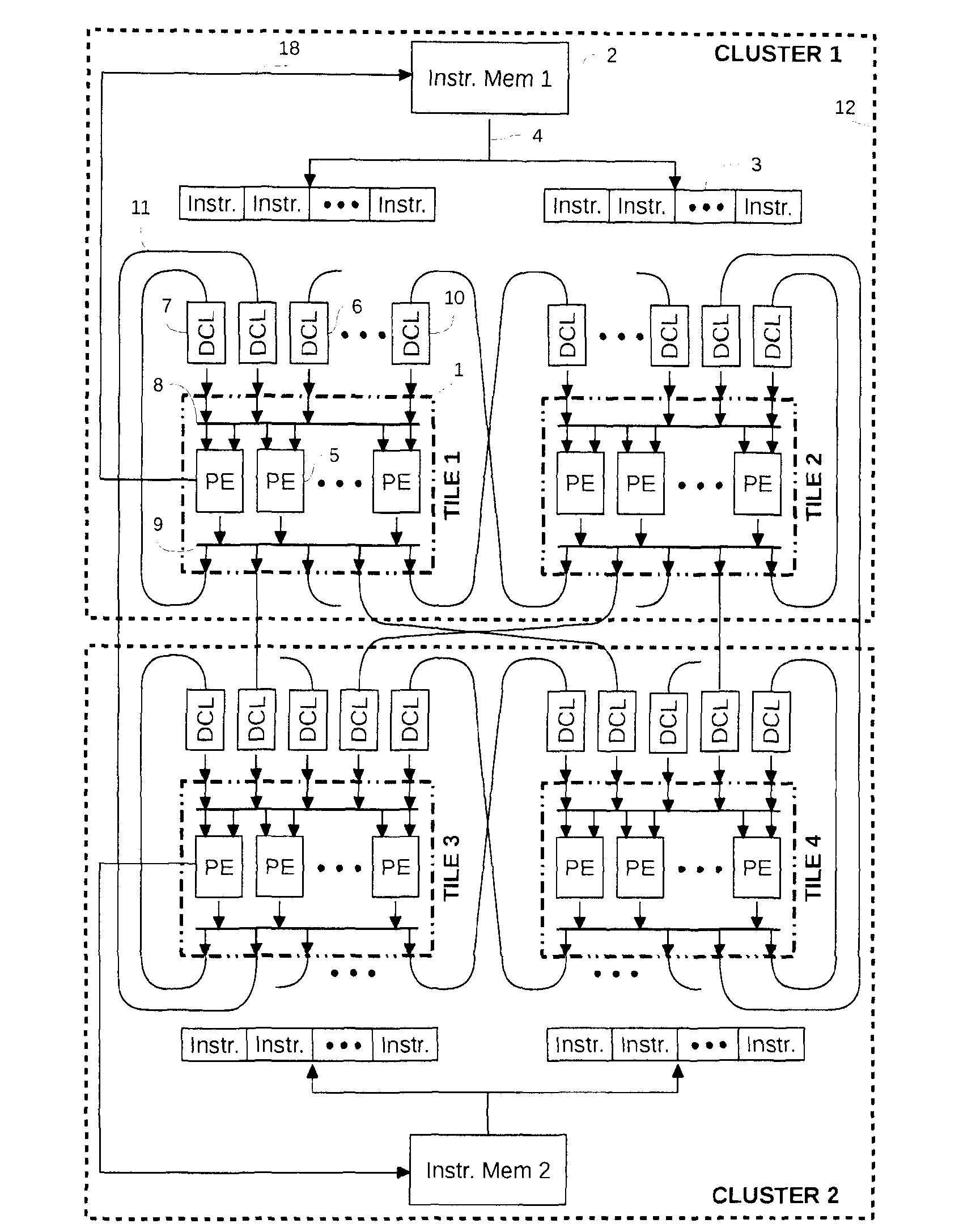
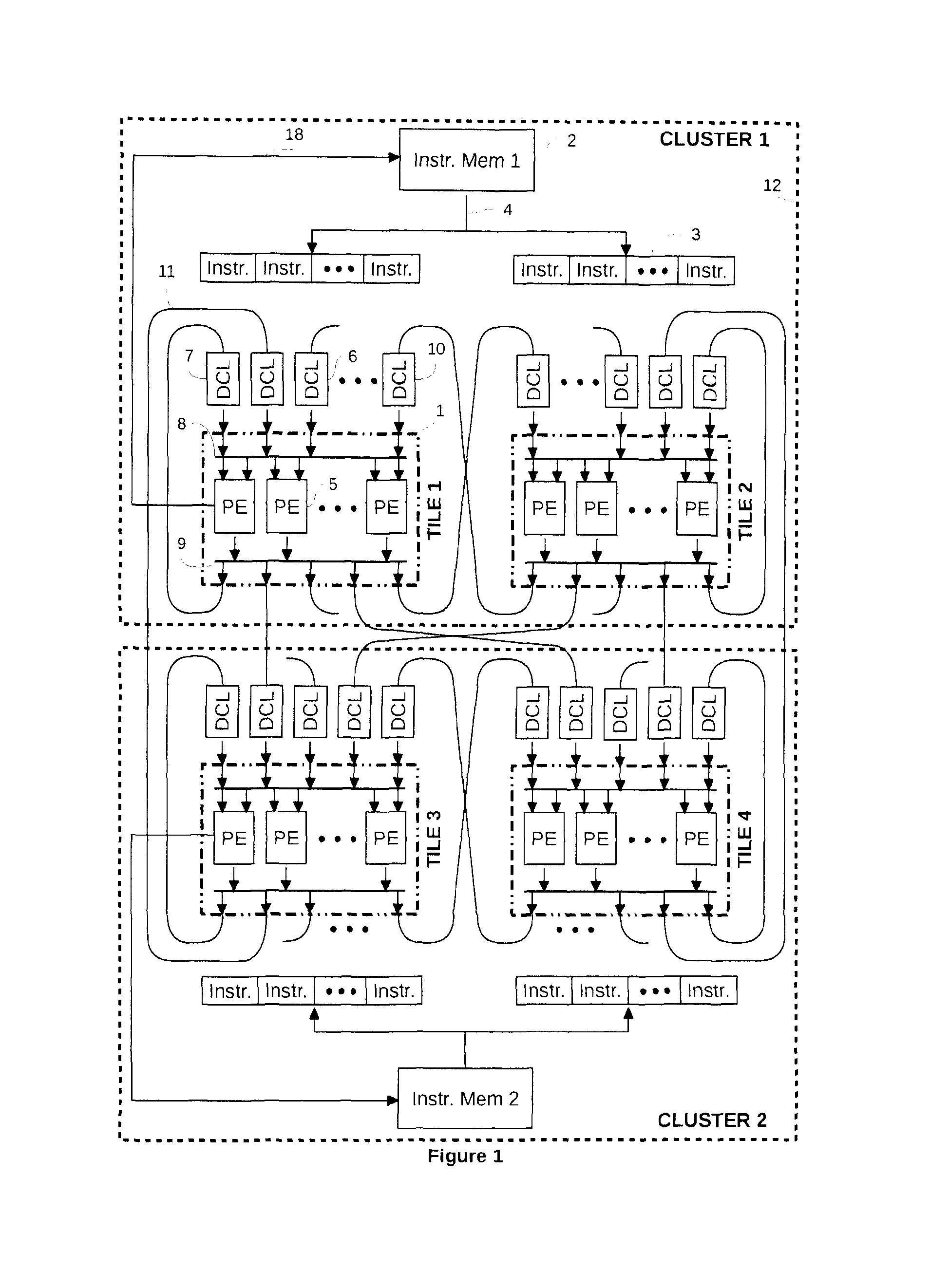
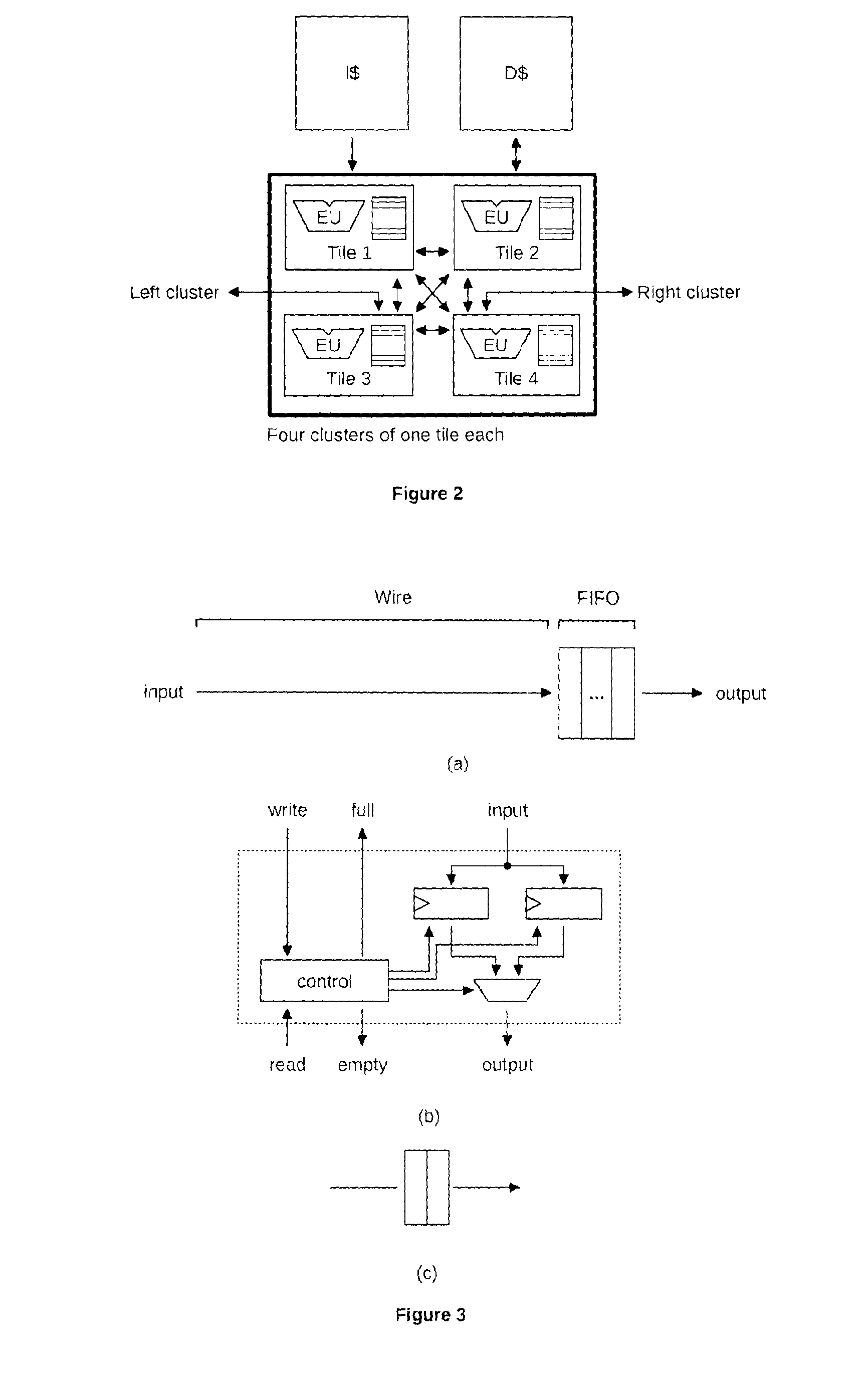
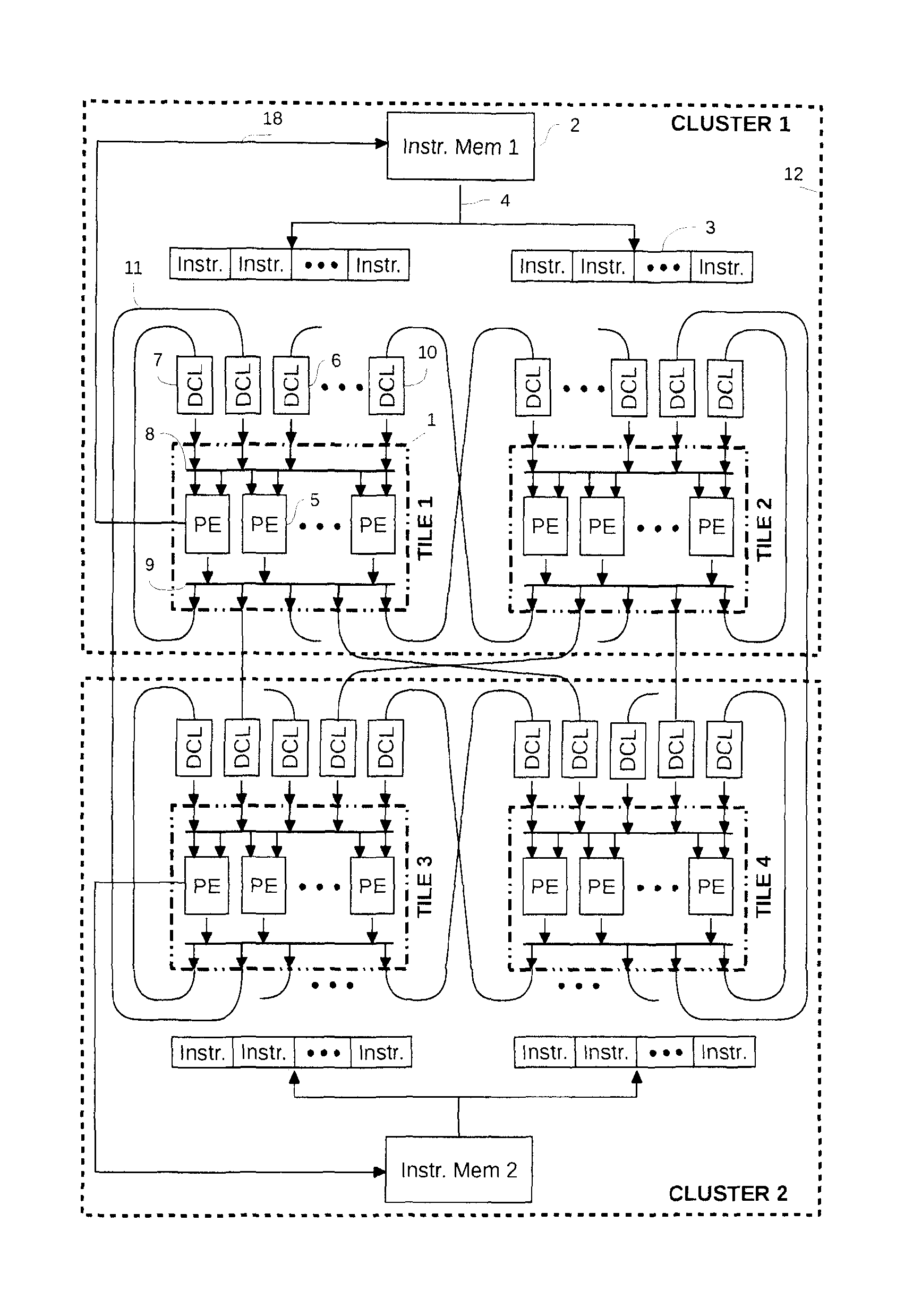
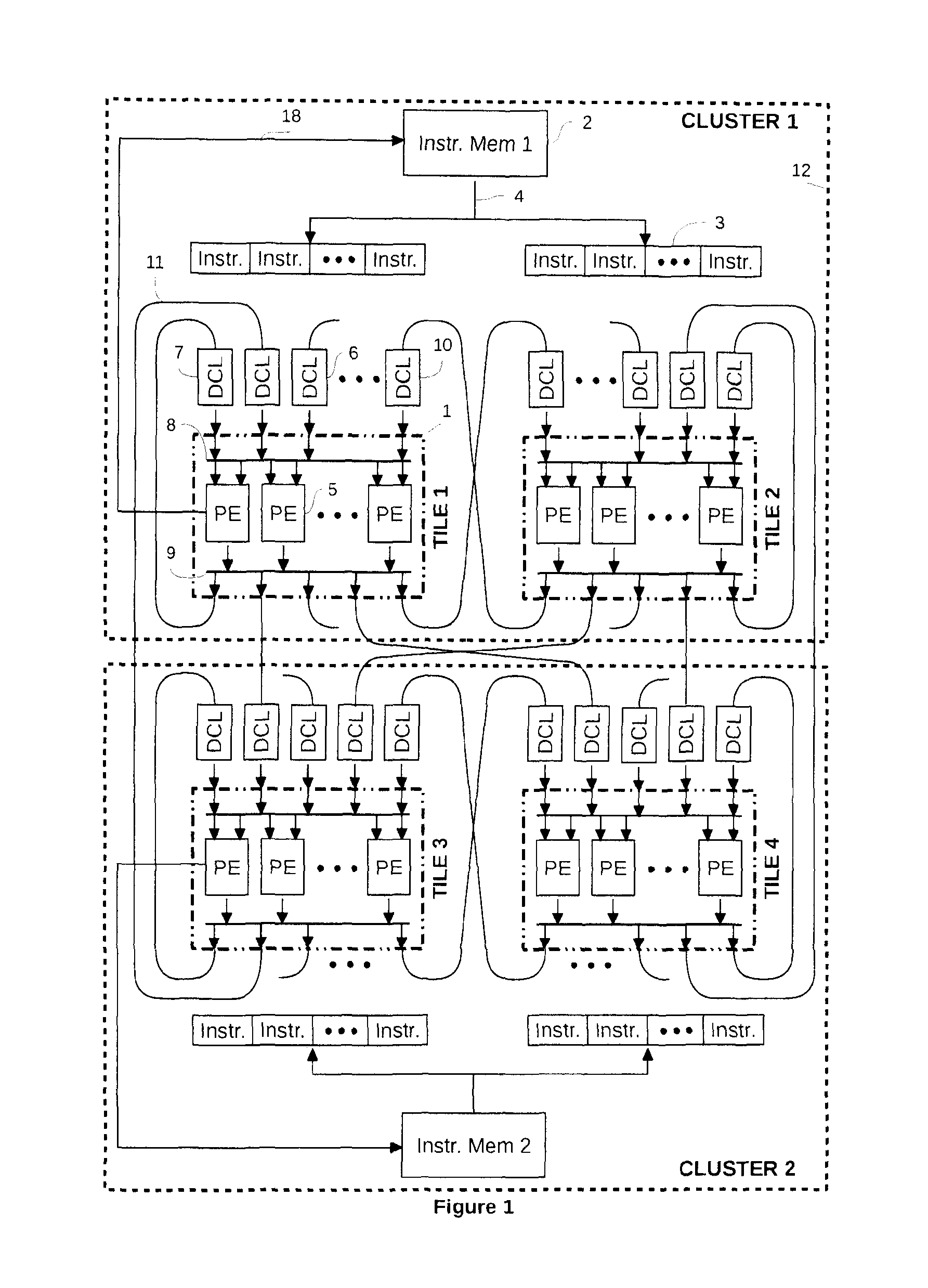
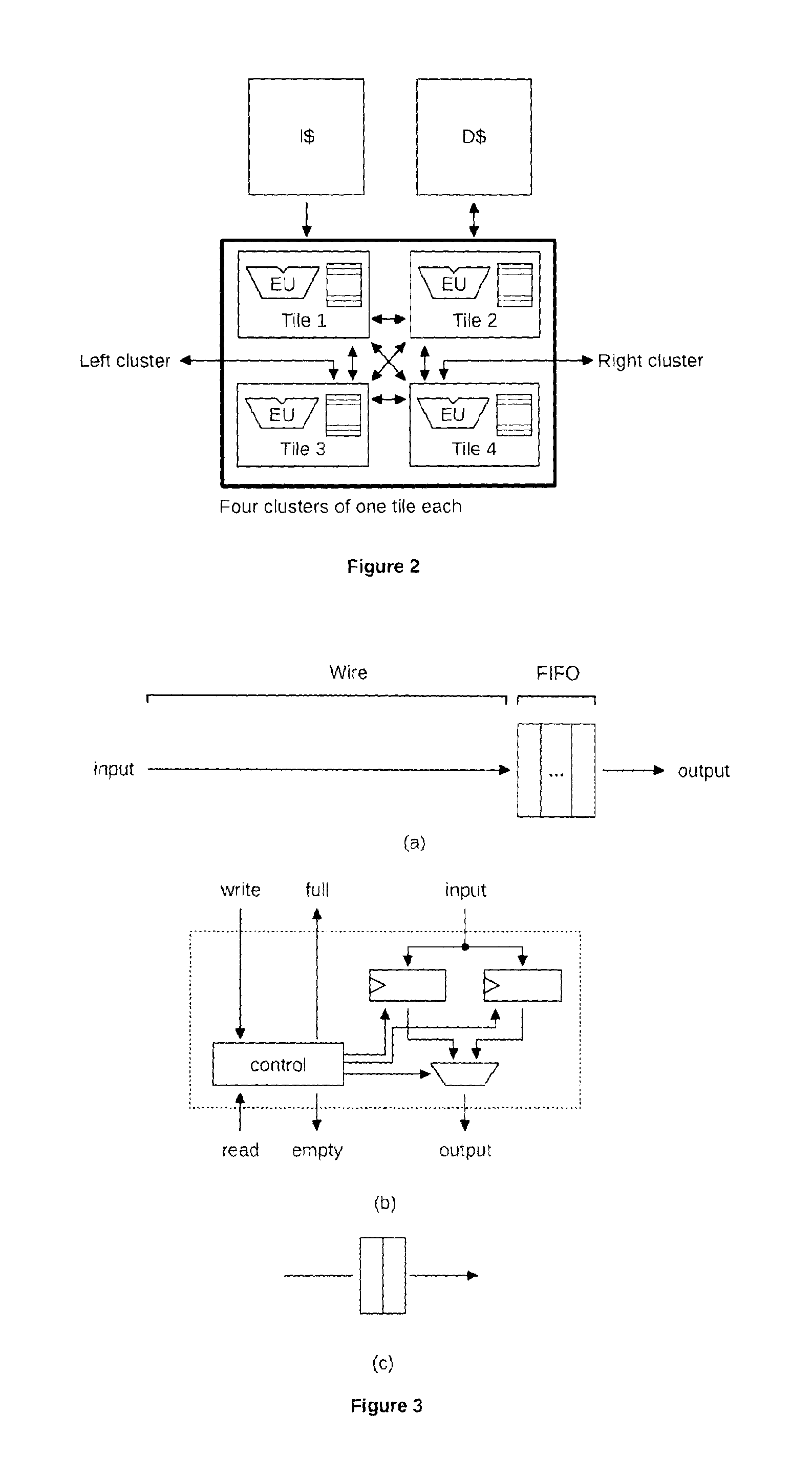
The present invention relates to a processor which comprises processing elements that execute instructions in parallel and are connected together with point-to-point communication links called data communication links (DCL). The instructions use DCLs to communicate data between them. In order to realize those communications, they specify the DCLs from which they take their operands, and the DCLs to which they write their results. The DCLs allow the instructions to synchronize their executions and to explicitly manage the data they manipulate. Communications are explicit and are used to realize the storage of temporary variables, which is decoupled from the storage of long-living variables.
Owner:MANET PHILIPPE +1
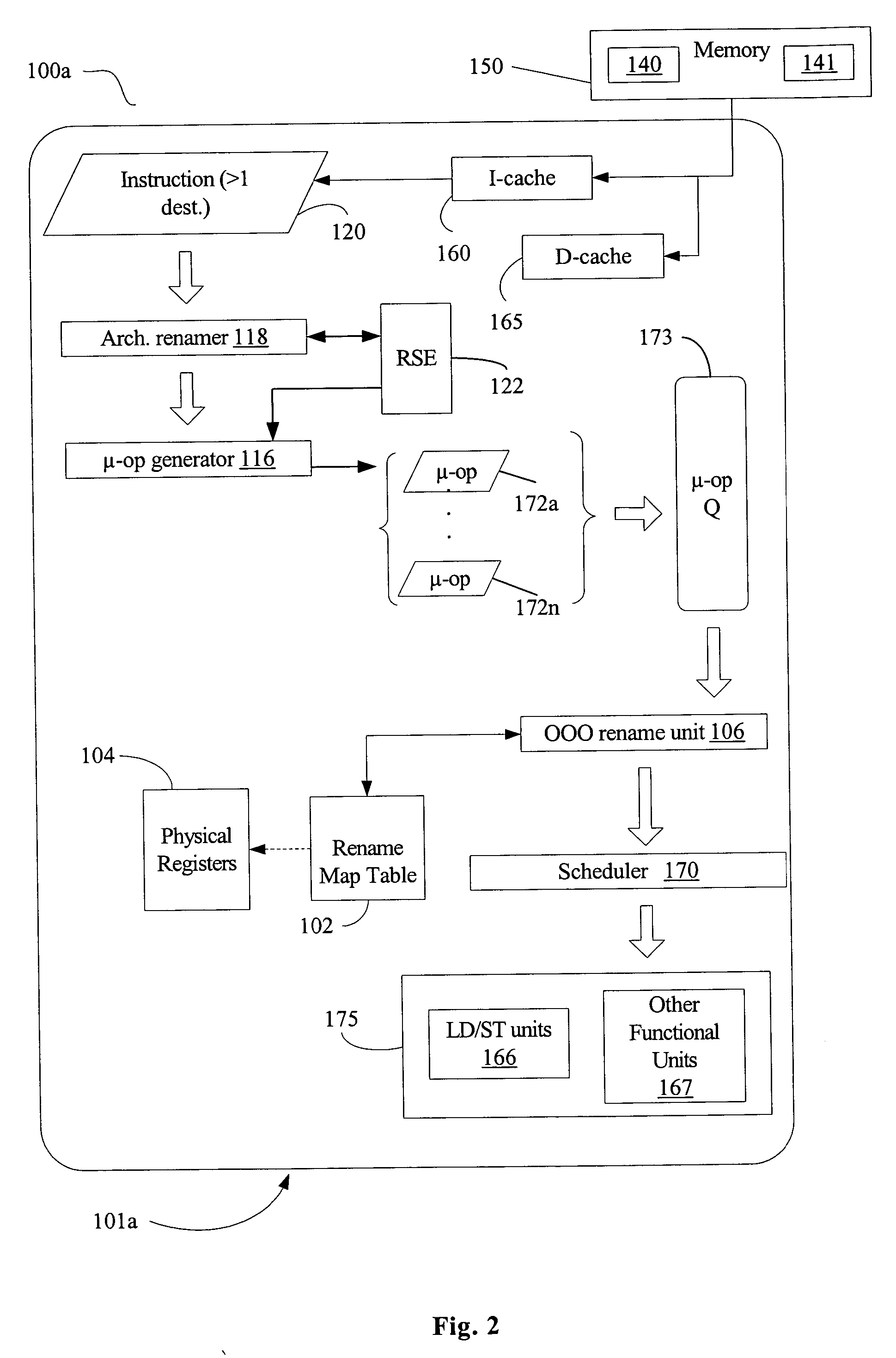
Method and apparatus for predication using micro-operations
InactiveUS20050081017A1Instruction analysisRuntime instruction translationTemporary variableMicro-operation
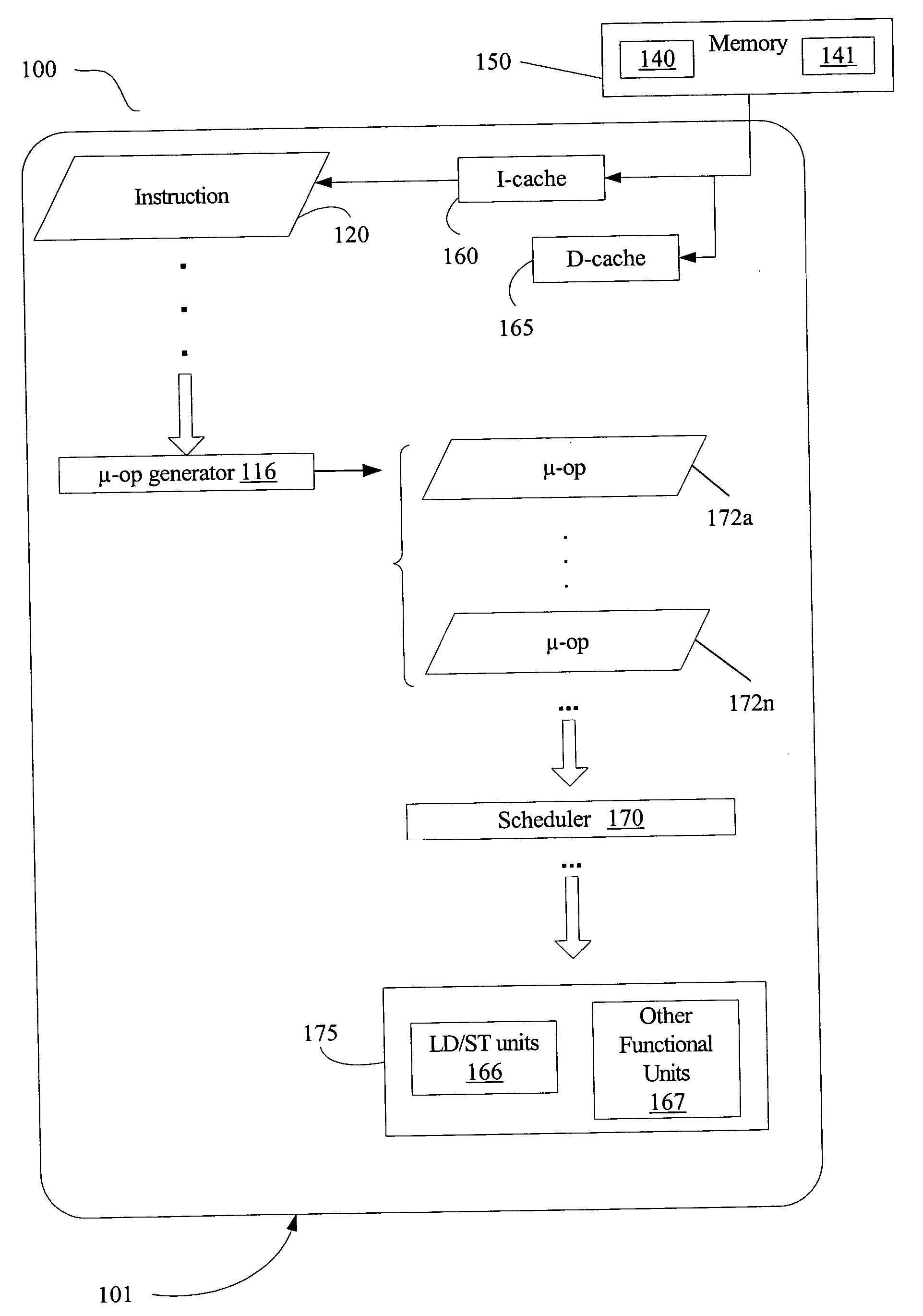
Disclosed are an apparatus, system, and method for implementing predicated instructions using micro-operations. A micro-code engine receives an instruction, decomposes the instruction, and generates a plurality of micro-operations to implement the instruction. Each of the decomposed micro-operations indicates a single destination register. For predicated instructions, the decomposed micro-operations include “conditional move” micro-operations to select between two potential output values. Except in the case that one of the potential output values is a constant, the decomposed micro-operations for a predicated instruction also include an append instruction that saves the incoming value of a destination register in a temporary variable. For at least one embodiment, the qualifying predicate for a predicated instruction is appended to the incoming value stored in the temporary register.
Owner:INTEL CORP
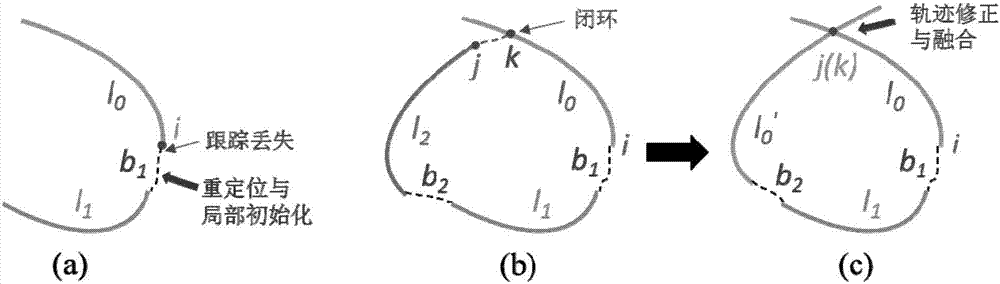
Simultaneous localization and mapping method of monocular vision robot based on retracking strategy
ActiveCN106885574AImprove completenessThe solution cannot be estimatedNavigational calculation instrumentsPhotogrammetry/videogrammetryTemporary variableSimultaneous localization and mapping
The invention discloses a simultaneous localization and map construction method of a monocular vision robot based on a retracking strategy. The method comprises the following steps: 1) extracting ORB characteristics of each picture; 2) tracking camera postures by utilizing characteristic matching of the adjacent pictures; 3) carrying out relocation and retracking strategy on pictures which are not tracked; 4) if the relocation is successfully executed, estimating postures of a current camera; stopping the retracking strategy and deleting a temporary variable generated by the retracking strategy; 5) if the retracking strategy is successfully executed, generating a new track; 6) judging the quantity of the generated tracks; if the quantity is more than a threshold value, eliminating an initial track; 7) carrying out closed-loop detection on each key frame and carrying out track fusion after the detection is successful; 8) when a localization system is finished, screening the tracks to obtain one track with the accurate posture. The simultaneous localization and map construction method disclosed by the invention has the advantages that the complete camera track can be located under the conditions of rapidness in movement, shielding, insufficient textures and illumination changes.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
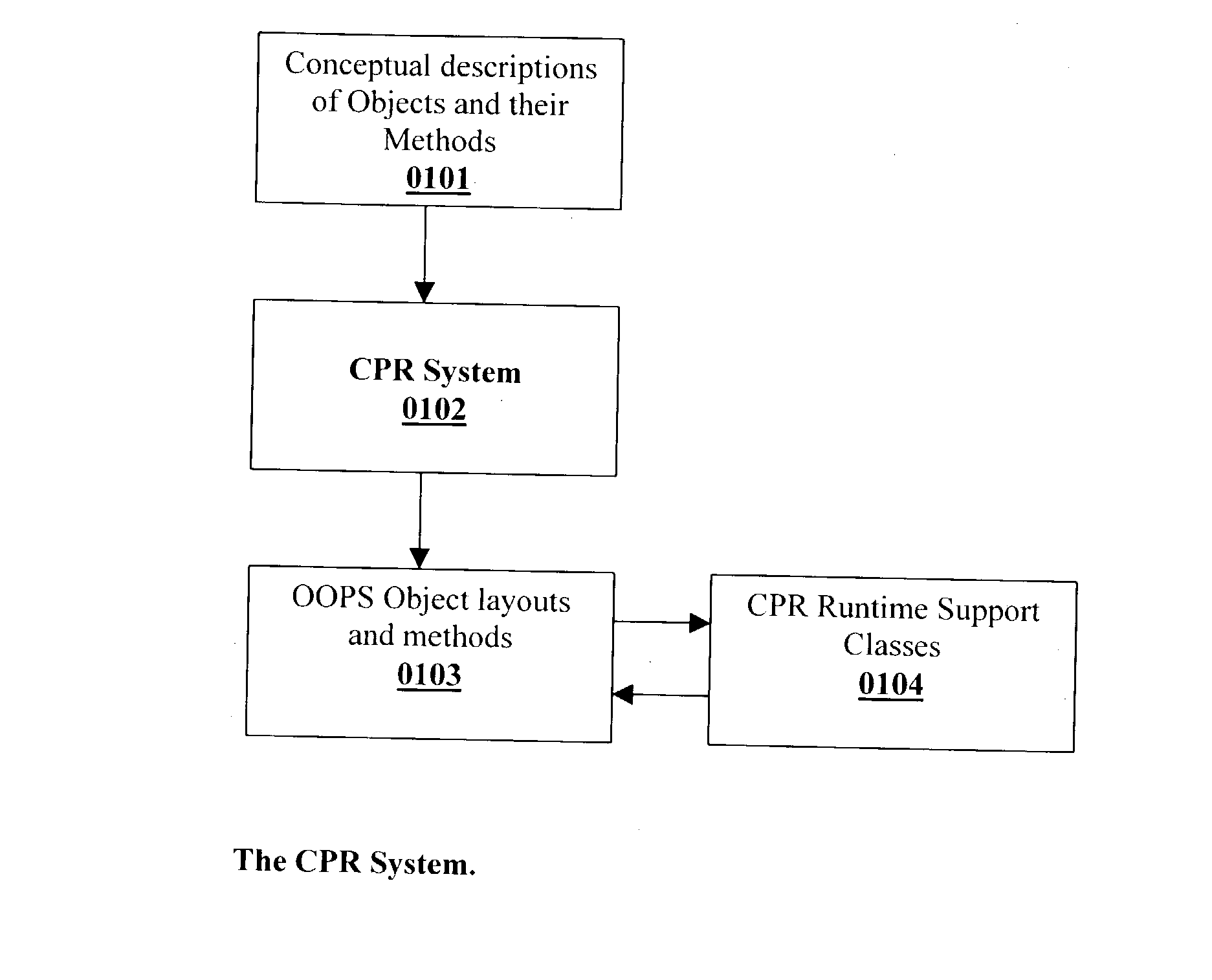
Conceptual process redactor
InactiveUS20030212954A1Digital computer detailsRequirement analysisTemporary variableType conversion
Conceptual Process Redactor (CPR) is a method and system, for describing and translating conceptual descriptions of objects and their methods to OOPS object layouts and methods. CPR utilizes conceptual structures (C-structures or CPR classes), to describe information. C-structures are hierarchical information structures, and each hierarchical path is considered as a CPR data type. Thus, instead describing data in terms of OOPS data types, which are bound to storage layouts of the underlying machines, CPR describes data in terms of CPR data types, which may be regarded as concepts. The CPR translator, translates the CPR data types to their Oops equivalents by making use of Type Translation library, supplied with the CPR class description. CPR data types are unique within the class they are defined, and hence serve to identify the field as well describe a data type. Thus, a typical usage like Part quantity field of sales order header is now a data type in its own right, as well as a field. The uniqueness of the CPR data types is made use of in identifying the parameters of a method, if the context in which the method is invoked in known a priori. The CPR system provides a mechanism, called collaboration, to conceptualize process descriptions. As per collaboration, a group of objects may collaborate to accomplish a particular task (method). The collaboration serves as a context, and hence method invocations in CPR may omit the parameters, and these are identified from the collaboration. Each object acts as a client and the rest of the objects and temporary variables, act as servers. The client / server relationship is made use of by process descriptions called CPR Interface groups, which are specified for each of the collaboration objects, participating in the collaboration. In addition, to the intra object client / server relationship, objects are broadly classified as data sources or data containers, where the first form is considered as a sequential representation of data, and the latter form is considered as a random representation of data. Each data source may be grouped with zero or more data containers, and each such group is called a collaboration group. One or more collaboration groups may be specified in a table called the collaboration table, and collaboration groups with sequential group numbers are considered as a logical unit of execution. Thus, collaboration groups and the associated client / server relationship between the objects in the collaboration groups, may be used to conceptualize fairly complex method descriptions. The CPR translator will translate the process descriptions specified as CPR Interface groups for the collaboration objects into oops methods. The CPR runtime system provides necessary support to access / update the collaboration objects, and to invoke the oops methods generated during translation.
Owner:PATRUDU PILLA GURUMURTY
Mechanism and system for representing and processing rules
ActiveUS20050027507A1Semantic analysisDigital data processing detailsTemporary variableAuxiliary verb
This invention utilizes a concept called color, which implies a variation, and applies it to natural language attributes like verbs and nouns. The verb color is defined as a role or operation in which the field participates. The noun color is defined as a form of the field. The auxiliary verb color is defined as a path to the field from a known object reference. The noun color may be defined by the user or may be determined, based on the object state in which the field resides. Equations are made generic, by making the colors of the fields parametric. The equivalence of methods and equations was established, and a method might be invoked, as if it was a rule. Similarly, processes involving several methods, and other rules, may be described by rules. A special kind of classes called conceptual classes were invented, which can project a subset of the fields of a class, as well as group and reorder a particular field found in several classes. Several objects called collaboration objects, may interact with each other in several cycles, and in each cycle, several methods of the objects are invoked. Each method may view the collaboration objects in a predefined order called collaboration sequence. Temporary variables created during processing may be stored in a global or local table, and may be assigned user defined or state based nouns. By utilizing all the mechanisms defined above, rules may be specified and evaluated in a generic manner.
Owner:PATRUDU PILLA GURUMURTY
Program monitoring method and defending method thereof, as well as relevant device
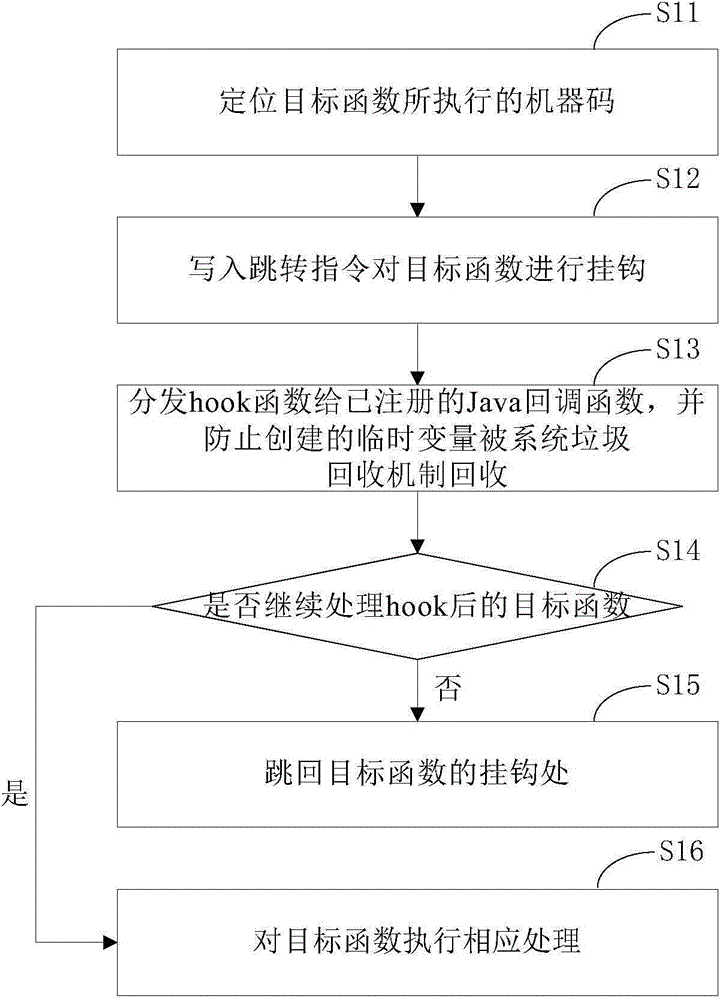
ActiveCN104598809AHook implementationAvoid markingPlatform integrity maintainanceTemporary variableProgram monitoring
The invention provides a program monitoring method and device. The program monitoring method comprises the following steps: writing in a skip instruction for positioned objective functions so as to perform a hook operation; distributing hook functions to registered Java callback functions, and preventing created temporary variables from being collected by a garbage collection mechanism of a system; enabling the objective functions which are not processed to skip back to hook positions, or else, continuing to process the objective functions. Through the adoption of the program monitoring method disclosed by the invention, any Java function of an Android system under an ART mode can be monitored without destroying the stack of the objective functions, so that the garbage collection mechanism of the ART can perform normal memory collection. The invention further provides a program defending method and device, which realize a defending mechanism of the Android system under the ART mode by adopting the program monitoring method disclosed by the invention.
Owner:BEIJING QIHOO TECH CO LTD
Coaxial powder delivery nozzle applied to variable spot technique
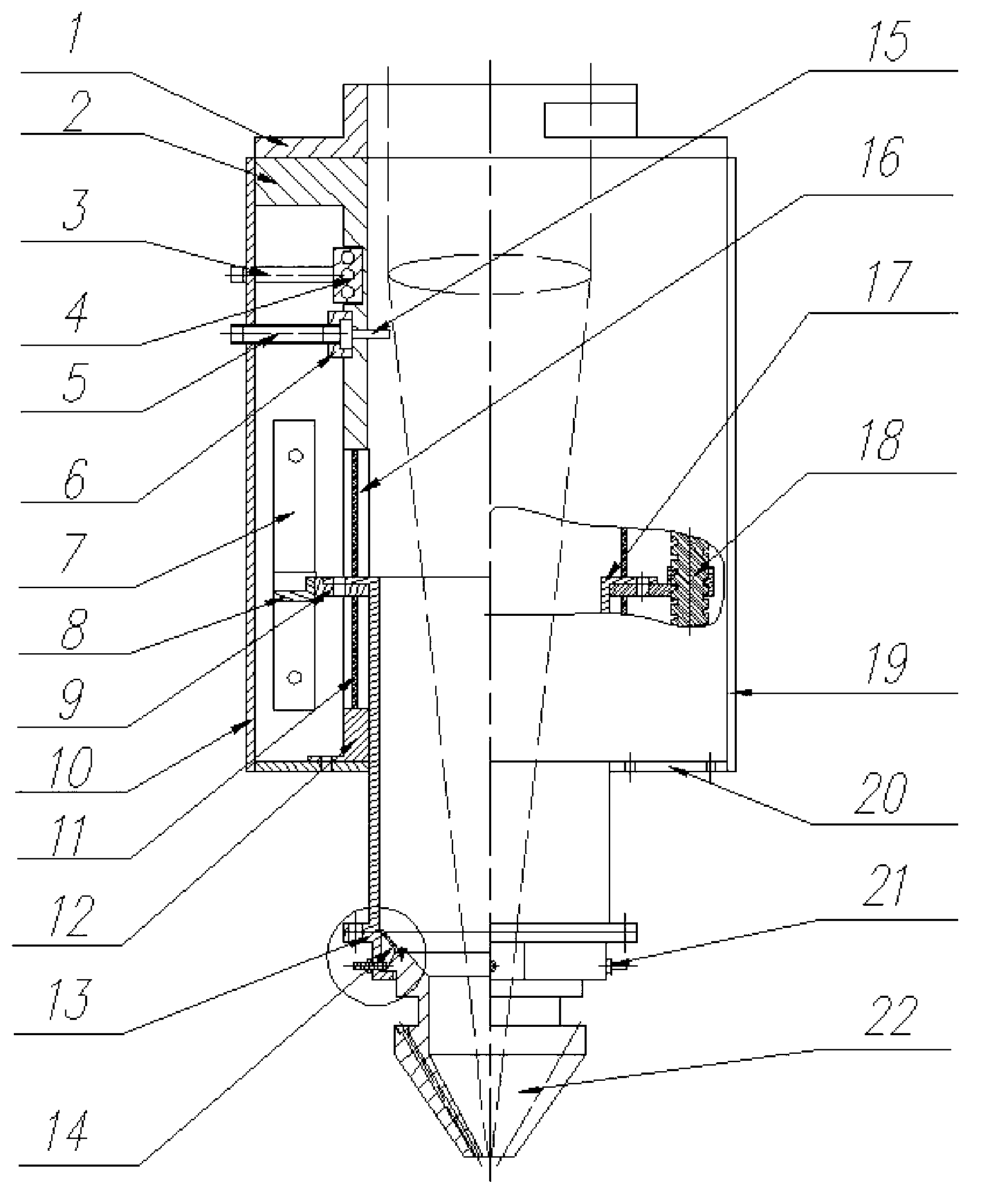
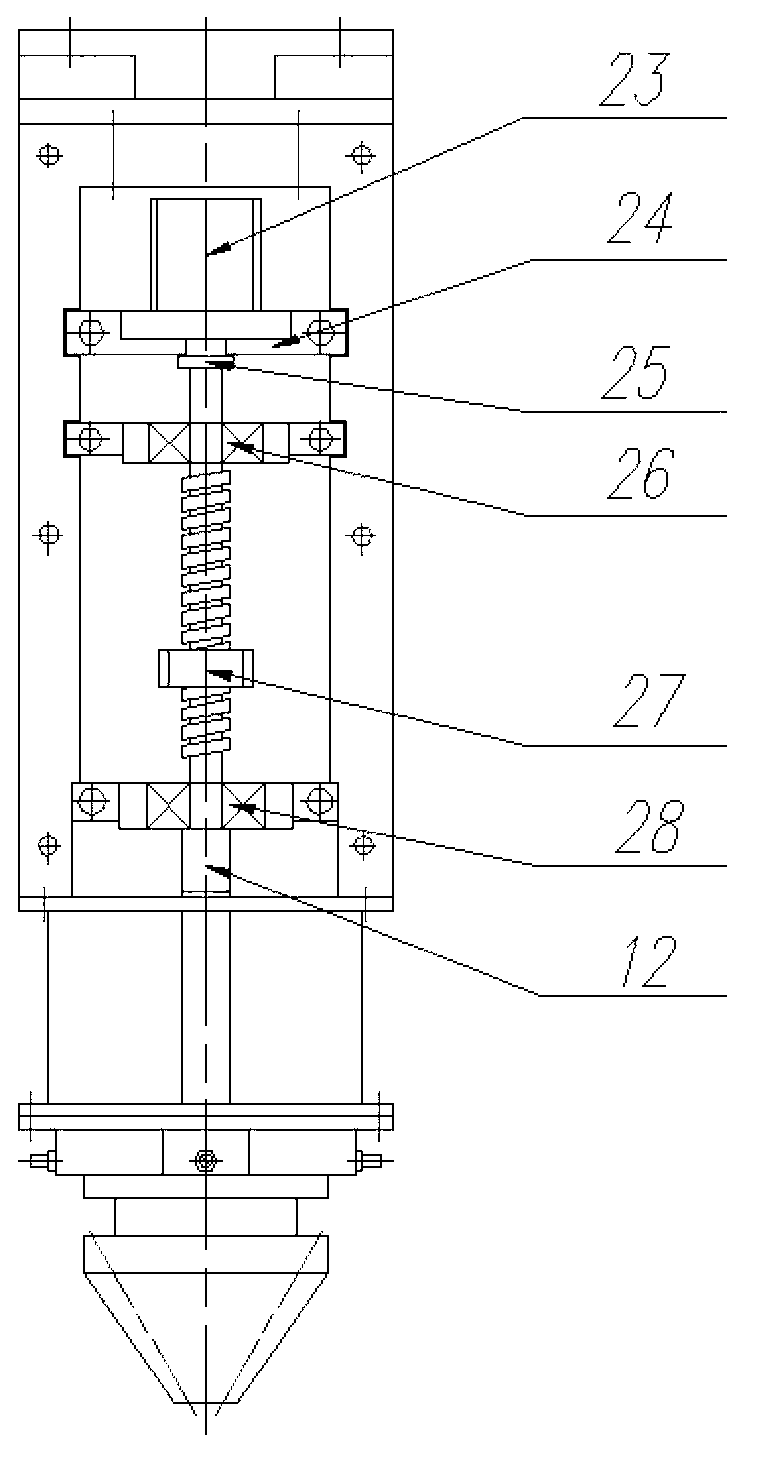
InactiveCN103060801APrecise automatic control of up and down moving distancePrecise guarantee of verticalityMetallic material coating processesLaser beam welding apparatusTemporary variableSpray nozzle
The invention relates to a coaxial powder delivery nozzle applied to a variable spot technique. The nozzle consists of three parts, wherein a first part is a structure for automatically regulating the collection position of powder in the nozzle in the vertical direction, and the part further comprises a cooling water loop and a gas protecting device; a second part is a structure for manually regulating the collection position of the powder in the horizontal diameter direction; and a third part is a powder delivery sprayer structure. The coaxial powder delivery nozzle disclosed by the invention is applicable to the field of material increase manufacturing, and especially applicable to an application place adopting a defocusing manner to realize temporary variable spot formation of laser for realizing both formation efficiency and precision. The coaxial powder delivery nozzle disclosed by the invention can also be applied to the field of laser welding.
Owner:XI AN JIAOTONG UNIV +1
Adjusting method for wireless signal-path band width
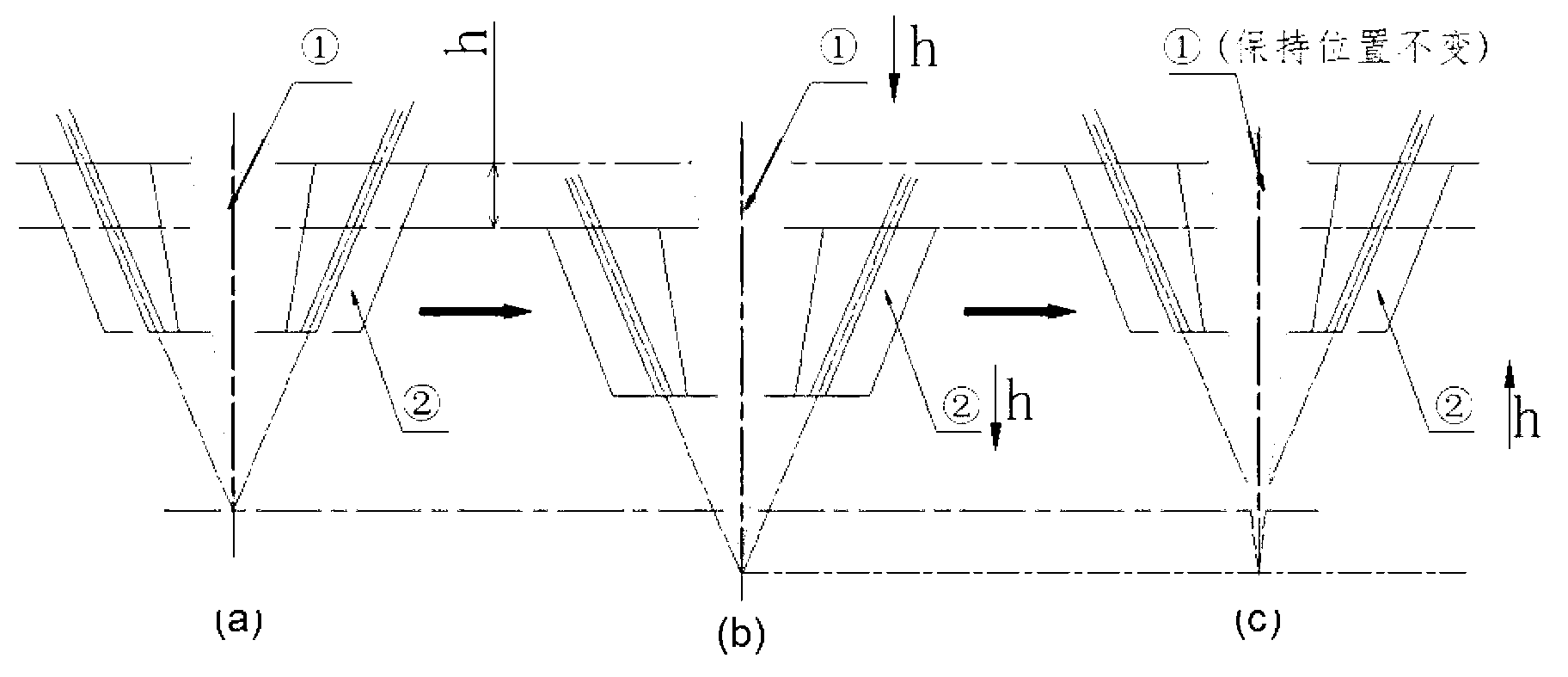
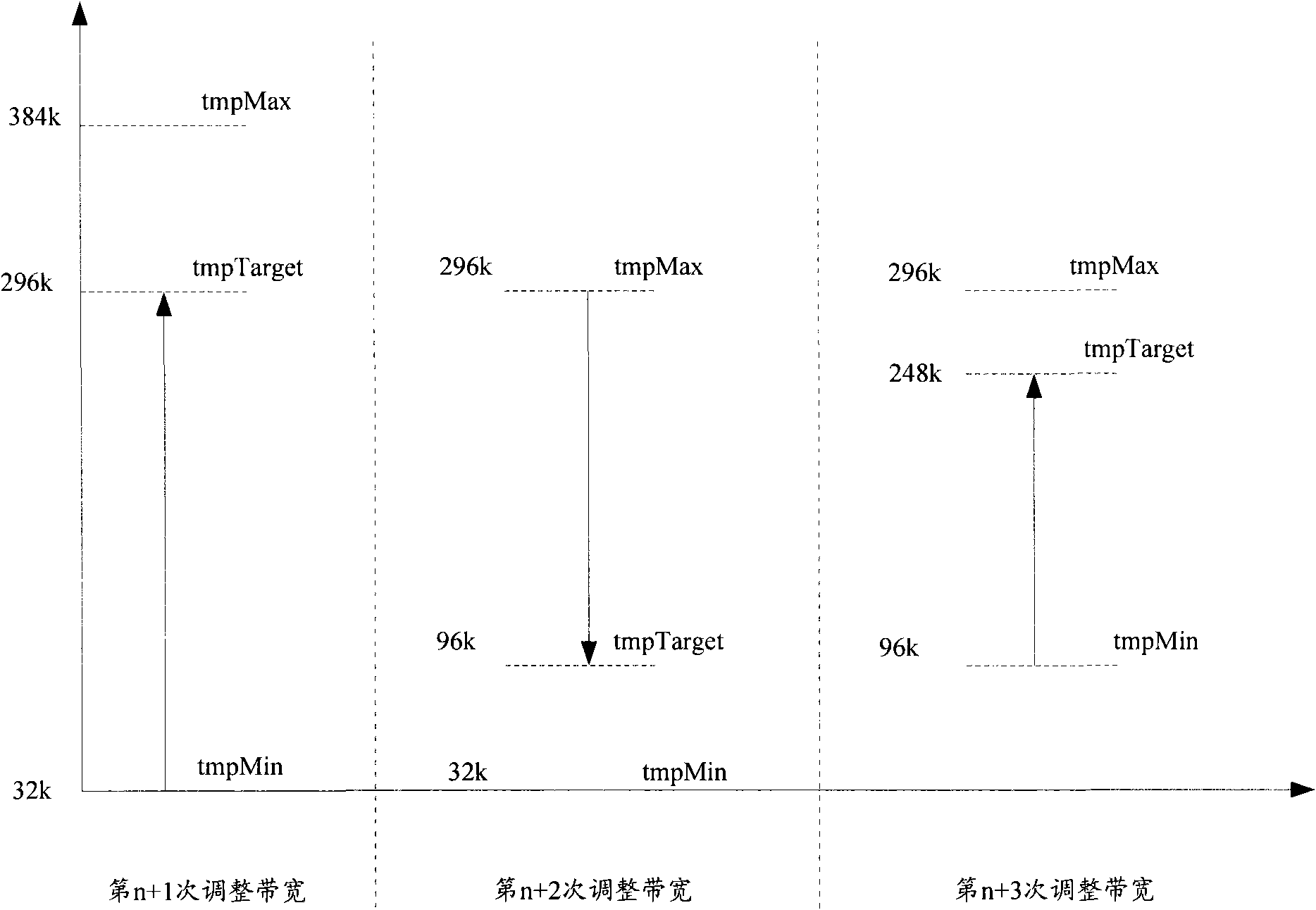
InactiveCN101557644AReal-time grasp of the timing of adjustmentsTake advantage ofWireless communicationTemporary variableLower limit
The invention discloses an adjusting method for wireless signal-path band width, which has the following steps: the upper limit value and the lower limit value of the band width of an up signal path and a down signal path of a mobile terminal, the maximum rising step frequency, the maximum lowering step frequency and three temporary variables are set; the maximum value of the band width of the former target, the minimum value of the band width of the former target, and the target value are adjusted; the band width of the prior wireless signal path is adjusted according to the measuring report of business volume; whether the adjusting direction of the band width of the current time and the adjusting direction of the band width of the last time is same is compared; the target band width value, the upper limit value of the band width of the current time and the lower limit value of the band width of the current time to be adjusted are respectively determined according to different conditions to carry out dynamic band width distribution. The method of the invention enables the air interface of the mobile communication system to timely response the change of the band width requirement of the business, rapidly raise or lower the band width, increase the utilizing rate of the band width of the mobile region, and improve the experience of the user.
Owner:XUZHOU POWER THAI STEEL STRUCTURE
Common sub-expression elimination for inverse query evaluation
InactiveUS20070078816A1EliminateEffective evaluationDigital data information retrievalSpecial data processing applicationsTemporary variableMessage handling
Provided herein are optimizations for an instruction tree of an inverse query engine. Secondary sub-expression elimination trees are provided, which are data structures configured to include nodes that allow for temporary variables that hold processing context or state for idempotent fragments of query expression(s). As such, when sub-paths for a query expression are processed against a message, the processing context may be stored within nodes of one or more sub-expression elimination trees. The next time this same fragment is processed, regardless of where it appears within the instruction tree, the data structure is accessed to identify and retrieve the state information such that the idempotent fragment is only calculated or evaluated once.
Owner:MICROSOFT TECH LICENSING LLC
Multi-distributed SM9 decryption method, medium and key generation method
ActiveCN108418686AEnsure safetyImprove securityKey distribution for secure communicationPublic key for secure communicationTemporary variablePlaintext
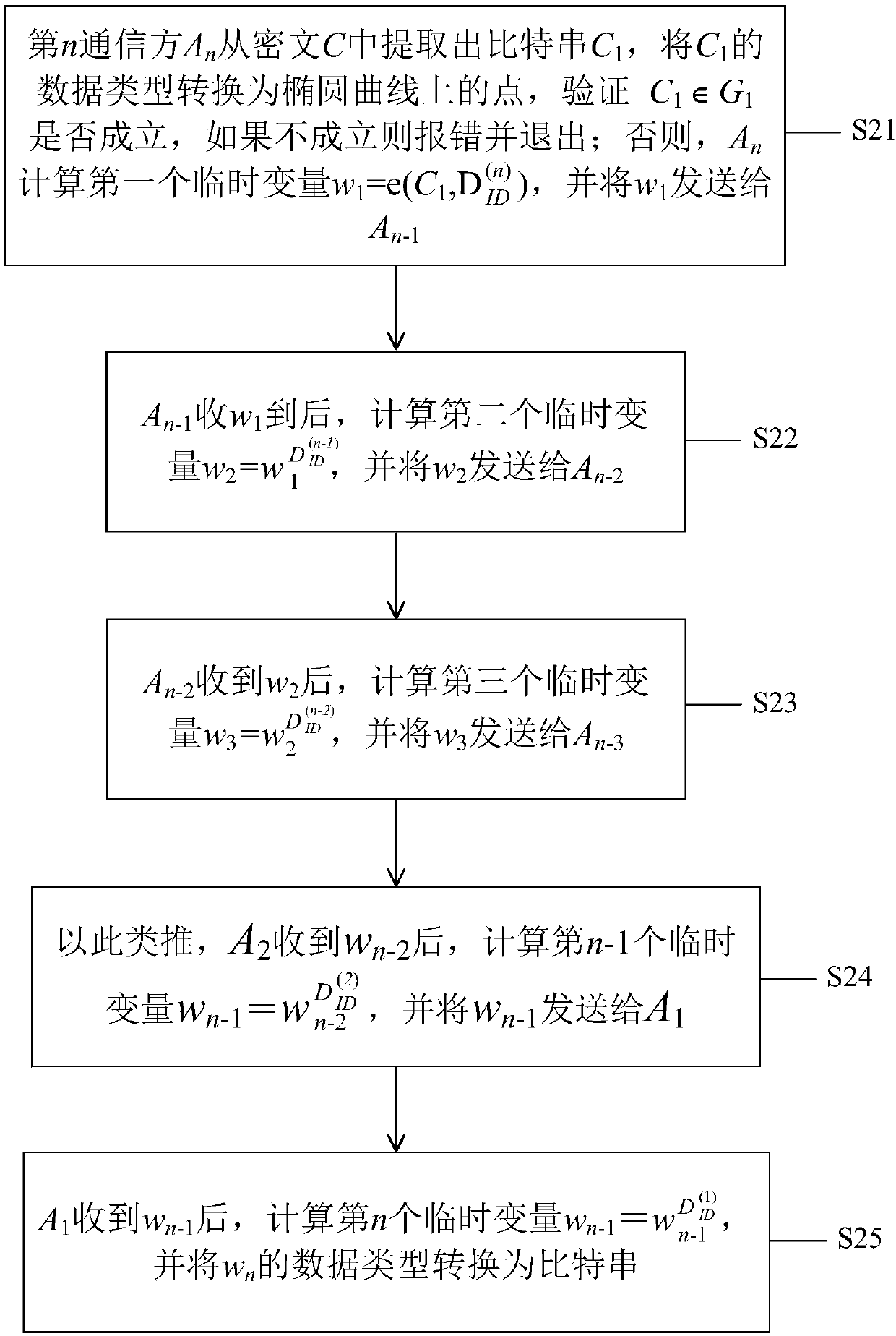
The invention discloses a multi-distributed SM9 decryption method, a medium and a key generation method. Multiple communication methods jointly complete a message decryption process under the condition of not leaking respective part of encryption keys and being unable to acquire the complete encryption key. The technical scheme of the method is as follows: a key generation center (KGC) generates the corresponding part of keys for communication parties participating into an SM9 decryption system. After the key is received, an n-th communication party An computes a first temporary variable, andreturns the first temporary variable back to the An-1. After the An-1 receives w1, a second temporary variable is computed, and returned back to An-2, and so on, until the A1 receives the wn-1, the n-th temporary variable is computed, and is subjected to decryption computing in a classified manner according to a plaintext encryption method, and finally plaintext M' is output.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Universal tree structure storage analysis method
ActiveCN107092659ACRUD process is simpleImprove maintainabilitySpecial data processing applicationsNODALTemporary variable
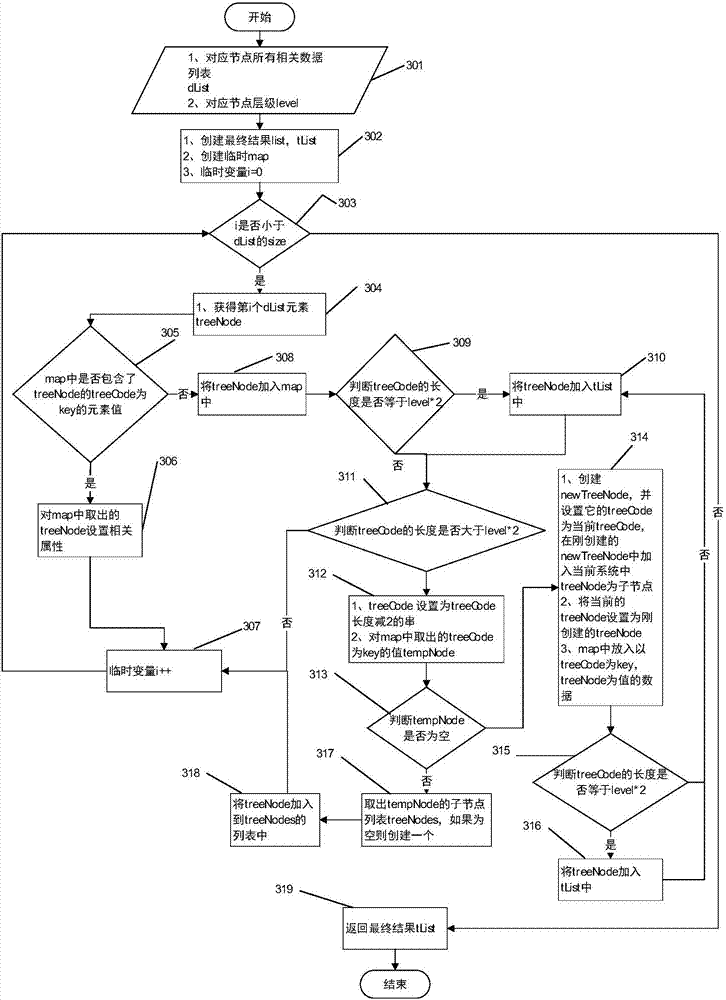
The invention discloses a universal tree structure storage analysis method, relates to the field of computer application and solves the technical problems of huge calculated amount, complex storage code, complex logic, non-visual data tree structure and the like in the prior art since a recursion way is adopted to analyze tree structure data. The method mainly comprises the following steps that: through a temporary variable, circularly traversing a data list generated by hierarchy associated data; reading the root data of the data list; utilizing tree node characteristics in the data list to combine with a temporary data set to construct a threshold value condition; setting a tree code for the tree node which conforms to the threshold value condition in a progressive increase way in sequence; storing the tree code corresponding to the current tree node in the data list into the temporary data set; after circulation ends, obtaining an integral tree temporary data set relative to the data list; and searching the temporary data set by corresponding to the root data to obtain the root tree node and all subtree nodes of the tree structure. The method has the characteristics of being simple, easy in use and high in maintainability and maneuverability.
Owner:成都优易数据有限公司
Blind signature generation method and system based on SM9 digital signature
ActiveCN108551392AGuaranteed correctnessGuaranteed privacyPublic key for secure communicationUser identity/authority verificationGeneration processTemporary variable
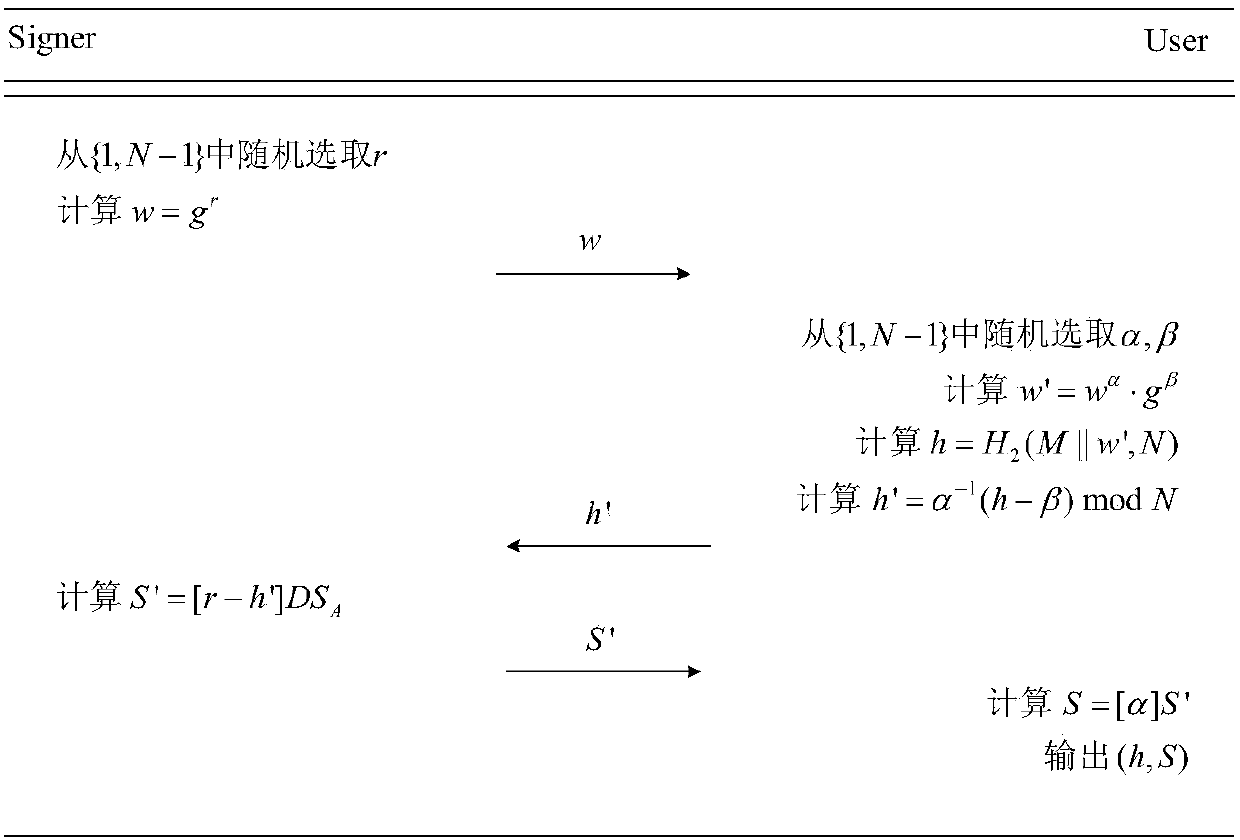
The invention discloses a blind signature generation method and system based on SM9 digital signature. The method comprises the following steps: 1) a key generation center KGC generates a signature private key DSA of a Signer; 2) the Signer calculates a first temporary variable w and sends the w to a User; 3) after the User receives the w, a second temporary variable w' and a hash value h) of a to-be-signed message M are generated, and a third temporary variable h' is calculated and sent to the Signer finally; 4) after the Signer receives the h', the temporary signature S' is calculated and sent to the User; 5) the User receives the S' and then calculates a signature value S, and outputs the signature (h, S). The method has the characteristics of low complexity, high security, easy verification, etc. The signature generation process must have both Signer and User participating simultaneously, and the process of generating the SM9 blind signature does not leak the signed message to thesigner, thus ensuring the security of the message, and improving the fairness of the SM9 digital signature generation.
Owner:WUHAN UNIV
Method and apparatus for address taken refinement using control flow information
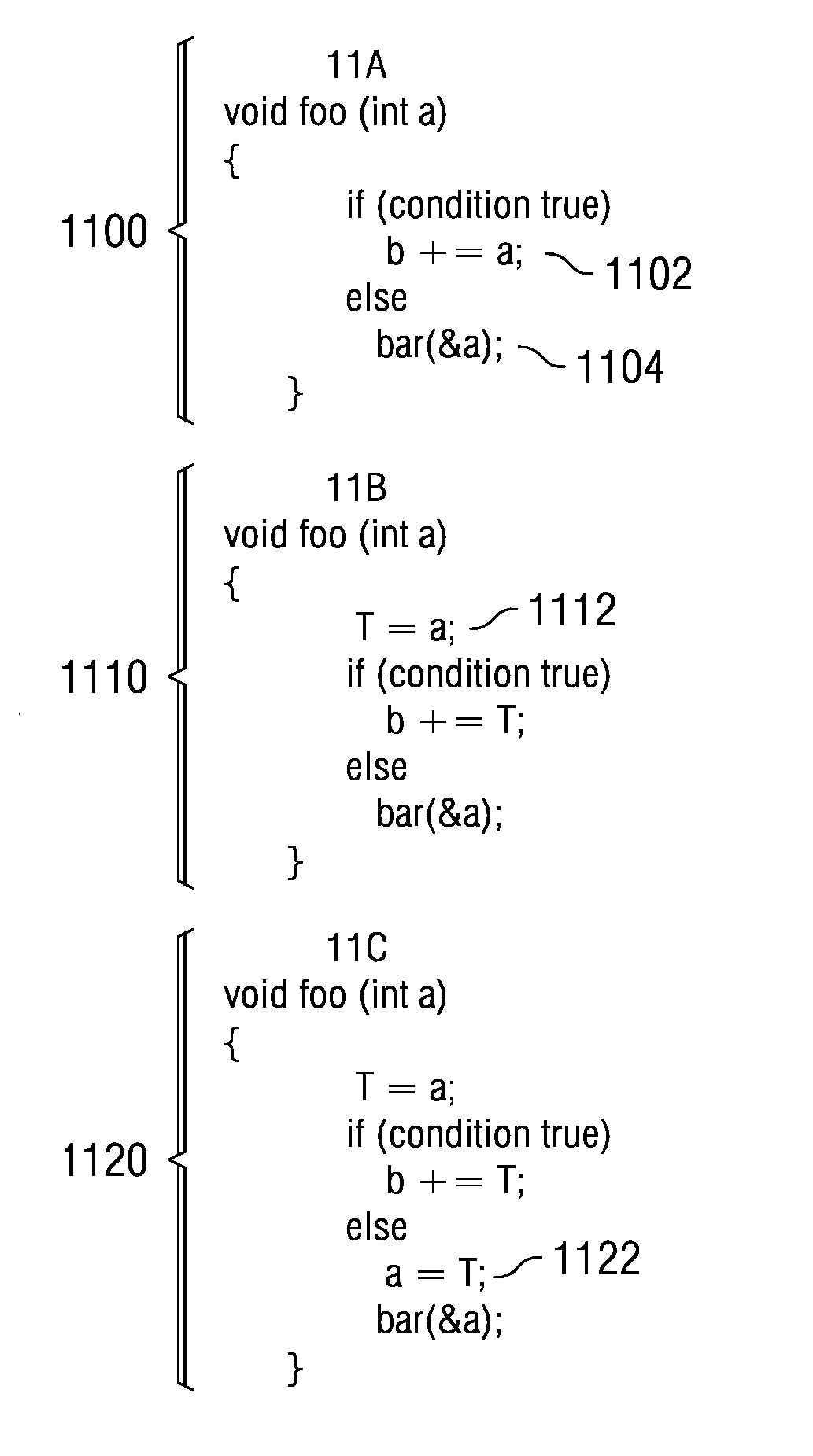
InactiveUS20090055798A1Software engineeringSpecific program execution arrangementsControl flowTemporary variable
A computer implemented method, apparatus, and computer program product for obtaining aliasing information for a target variable in a computer program. A control flow graph representing the computer program is partitioned into an taken address portion that includes all reachable nodes in which an address of the target variable is taken and an untaken address portion that includes all other reachable nodes. All references to the target variable are replaced with a temporary variable in the untaken address portion. The target variable is initialized with the value from the temporary variable at each intermediary node in a set of intermediary nodes in the taken address portion. An intermediary node is a node at which an address of a target variable is taken. The aliasing information for the target variable is generated using the modified computer program.
Owner:IBM CORP
Method and apparatus for automatically producing efficient code for computing derivatives
InactiveUS6895574B2Minimize the numberSpecific program execution arrangementsMemory systemsTemporary variableComputerized system
One embodiment of the present invention provides a system that automatically computes a derivative of a numerical expression within a digital computer system. The system operates by receiving a representation of the numerical expression, wherein the numerical expression includes one or more independent variables. Next, the system forms an expression tree for the derivative of the numerical expression with respect to an independent variable, wherein the expression tree makes use of temporary variables to form results of sub-expressions for computing the derivative. While forming this expression tree, the system seeks to introduce only temporary variables and associated sub-expressions as necessary to eliminate repeated common sub-expressions, thereby substantially minimizing the number of temporary variables. The system subsequently uses this expression tree to compute the derivative of the numerical expression during a computation.
Owner:ORACLE INT CORP
Online prediction method and system for remaining service life of hard disk equipment
ActiveCN110413227AImprove accuracyReflect stateInput/output to record carriersNeural architecturesNerve networkPredictive methods
The invention discloses an online prediction method and system for the remaining service life of hard disk equipment, and belongs to the technical field of computer storage. According to the invention, SMART information and I / O state information of hard disk equipment are taken as the basis; remaining service life online prediction of the hard disk equipment is carried out, SMART data records reliability indexes of multiple hard disk operation states, I / O state information comprises time consumed by an I / O request on the hard disk equipment, and time irrelevant to the service life of the harddisk equipment is removed; based on the collected I / O state information, a plurality of derivative variable attributes are generated, and the derivative variables are strongly related to the service life of the hard disk and reflect the internal relation between the hard disk state information and faults; group label assignment is adopted, the training effect is prevented from being affected by using temporary variables with large changes, a bidirectional long-short-term memory neural network is selected as a prediction model, a current value is reasonably predicted in combination with front and back hidden layers, the root mean square error and the average absolute error are effectively reduced, and therefore the hard disk life prediction precision is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Controlling cleaning of data values within a hardware accelerator
InactiveUS7865675B2Efficient detectionReliable identificationGeneral purpose stored program computerMemory systemsGeneral purposeTemporary variable
A data processing apparatus 2 includes a programmable general purpose processor 10 coupled to a hardware accelerator 12. A memory system 14, 6, 8 is shared by the processor 10 and the hardware accelerator 12. Memory system monitoring circuitry 16 is responsive to one or more predetermined operations performed by the processor 10 upon the memory system 14, 6, 8 to generate a trigger to the hardware accelerator 12 for it to halt its processing operations and clean any data values held as temporary variables within registers 20 of the hardware accelerator back to the memory system 14, 6, 8.
Owner:ARM LTD
Encryption device, program, and method
InactiveUS20090323956A1Inhibit deteriorationImprove securitySynchronising transmission/receiving encryption devicesRandom number generatorsTemporary variableComputer science
Disclosed is an encryption device for generating a pseudo-random number based on a secret key and generates an encrypted text by applying the pseudo-random number sequence to a plain text, uses, an internal state in accordance with a state based on a permutation of a sequence of a finite number of numeric values, as an internal state used for generation of the pseudo-random number sequence, executes a predetermined leftward or rightward rotate shift, depending on a number smaller than an internal state number, based on the result of linear or non-linear, or combination of linear and non-linear using one or more numeric values of the internal state and sets at least one temporary variable used for generation of the pseudo-random number sequence to be a temporary variable having as a value a result of the execution of the predetermined leftward or rightward rotate shift, and generates the pseudo-random number by a predetermined prescribed operation on one or a plurality of numeric values of the internal state and the temporary variable.
Owner:NEC CORP +1
Automatic result inspection method for database service operation in Windows platform
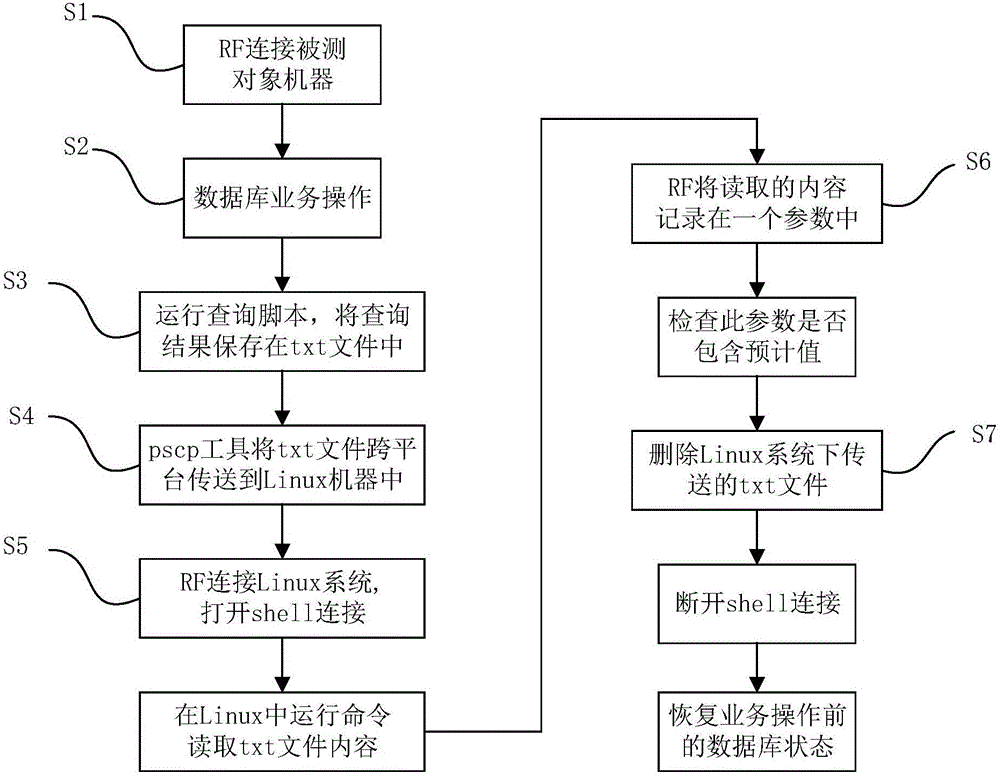
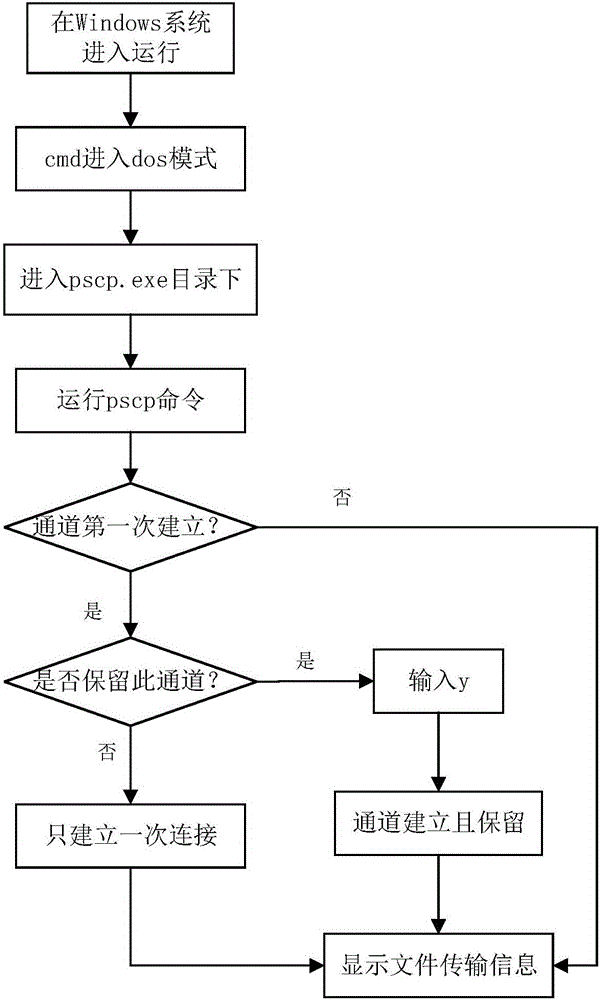
InactiveCN106095678AEasy to testImprove efficiencySoftware testing/debuggingDatabase servicesTest object
The invention relates to an automatic result inspection method for database service operation in a Windows platform. The method comprises the following steps that a tested object is connected to a Robot Framework testing framework; relevant test cases of database service operation are compiled; a database is searched for certain specific content, and the search result is stored in a txt file; a pscp command is operated, and the txt file is transmitted to a Linux machine from a Windows client side; the Robot Framework testing framework is connected to the Linux machine, the txt file is read, and read content is recorded into a temporary variable; the temporary variable is read, whether the result meeting testing requirements exists in the temporary variable or not is judged, if yes, the testing result is successful, and if not, the testing result is failing; the state of the tested object and the state of the Linux machine are restored so that subsequent cases can be operated. Compared with the prior art, the problem that an automatic testing framework cannot directly inspect database relevant parameters of the database operating in the Windows platform can be solved.
Owner:EISOO SOFTWARE
A software data stream analysis method based on intermediate language and stain analysis
ActiveCN109324971AEasy to captureRich expressive abilitySoftware testing/debuggingPlatform integrity maintainanceTemporary variableLocal variable
The invention discloses a software data flow analysis method based on intermediate language and stain analysis. The method comprises the following steps of S1 defining instruction format and expression format; uniformly describing the general instruction types of the intermediate languages, and construting the temporary variable expressions, register expressions and stain marker expressions for the data representation in stain analysis process; S2 constructing a stain propagation rule based on an intermediate language, wherein the stain mark is represented by a taint_label; S3 dynamic tracking an analysis flow based on a program data flow of the intermediate language; S4 when the program is executed, constructing the data flow relationship between the stain source and the global variableTG, the local variable TL, and the system call function parameter TF based on the tracked stain information. The method of the invention has the advantages of better accuracy, stronger comprehensiveness and richer information.
Owner:NAT UNIV OF DEFENSE TECH
Optimizing instructions for execution on parallel architectures
InactiveUS20060288335A1Software engineeringSpecific program execution arrangementsTemporary variableParallel computing
Instructions may be optimized for execution on parallel architectures. In one embodiment, the invention includes parsing a code sequence into an internal representation of the sequence, finding an input channel in the internal representation, finding a put to the input channel in the internal representation, finding a get to the input channel in the internal representation, replacing the input channel with a temporary variable, replacing the put with a first function call to the temporary variable, and replacing the get with a second function call to the temporary variable. Other embodiments are described and claimed.
Owner:INTEL CORP
Low-energy-consumption small-area data processing method and data processing device thereof
InactiveCN103888246AReduce the number of cyclesReduce power consumptionEncryption apparatus with shift registers/memoriesTemporary variableControl signal
Owner:CHINA VISION MICROELECTRONICS
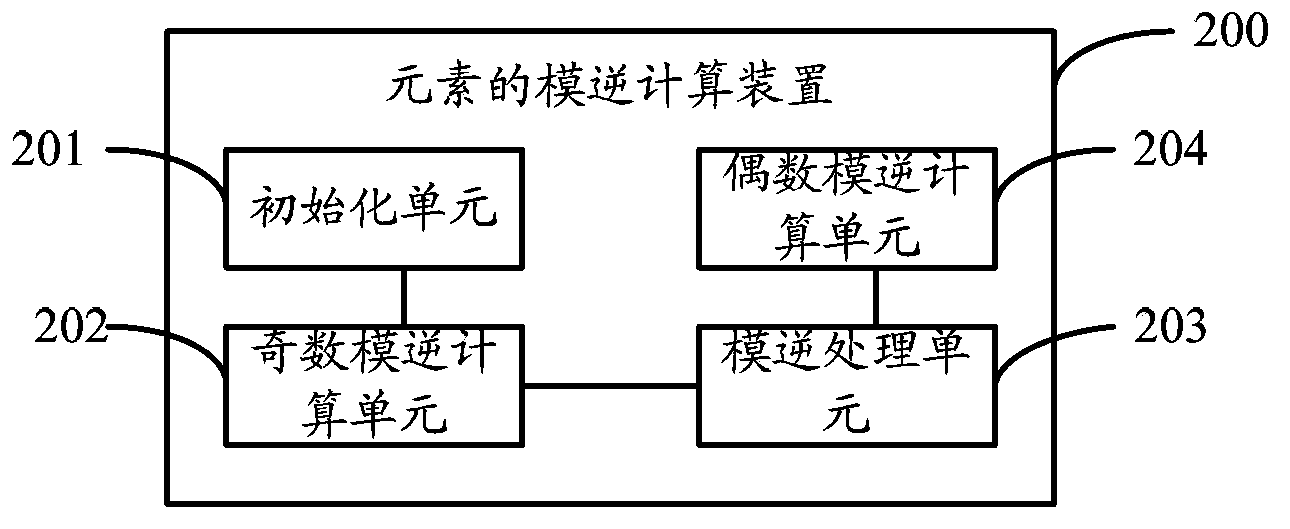
Element modular inversion calculation method and device
ActiveCN104123431ACalculation speedReduce resource requirementsSpecial data processing applicationsTemporary variableTheoretical computer science
The invention is applicable to the technical field of computers and communication and provides an element modular inversion calculation method and device. The method comprises the steps that the initial values of temporary variables X1 and X2 and decreasing variables u and v are obtained, wherein the initial values of the temporary variables X1 and X2 are 1 and 0 respectively, and the initial values of the decreasing variables u and v are a and P0 respectively; the temporary variables X1 and X2 and the decreasing variables u and v are subjected to iterative computation, wherein the iteration process meets the equations: a*x1=u(mod P0), a*x2=v(mod P0); after each time of iteration is completed in the iterative computation, whether one of u and v is 1 is judged, if neither u nor v is 1, the iterative computation is continued, and if either u or v is 1, the iterative computation is ended; after the iterative computation is ended, if u is 1, X1 is assigned to X, and if v is 1, X2 is assigned to X; when K=0, whether X is greater than zero or not is judged, and if X is greater than zero, X is the modular inversion related to P. By means of the technical scheme, the element modular inversion calculation method and device have the advantages that the computing speed is high, and the number of required computing resources is small.
Owner:NATIONZ TECH INC
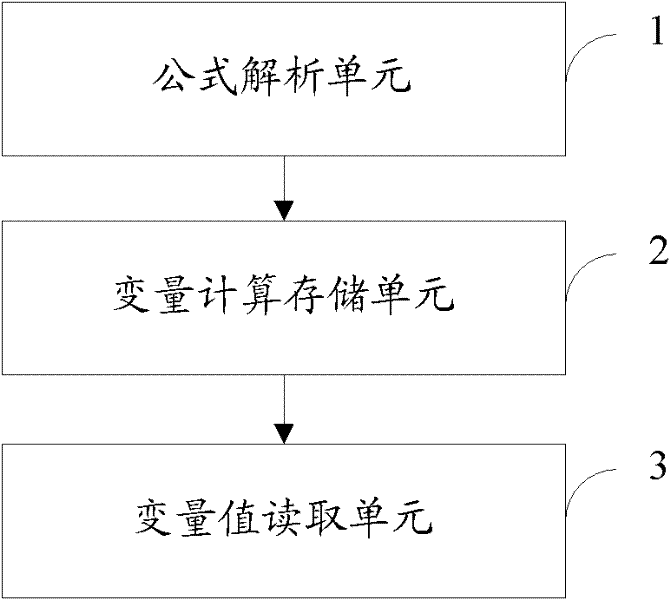
Analytic method, device and operation system of report formula
InactiveCN102446164AShorten the lengthAvoid double countingSpecial data processing applicationsTemporary variableComputer software
The invention is suitable for the filed of computer software, and provides an analytic method, a device and an operation system of report formula. The method includes that analyzing the report formula, establishing a temporary variable when the temporary variable is used for showing expression in analysis of the report formula, enabling the value of the expression to be stored in the temporary variable, and reading the value of the temporary variable when the temporary variable is quoted in the analysis of the report formula. The method uses the temporary variable to show the expression in the report formula, thereby avoiding repeated reference and repeated calculation of the same formula code in the report formula, improving execution efficiency, and being convenient to maintain. The action range of the temporary variable is only the current report formula.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Method for optimizing binary code in language having access to binary coded decimal variable, and computer and computer program
A method for optimizing binary code in a language having access to binary coded decimal variable. The method includes: generating a first compiler expression of the binary code; analyzing a use-definition and / or a definition-use for the first compiler expression; generating a second compiler expression by identifying logical binary coded decimal (BCD) variables in the first compiler expression; assigning temporary variables to the logical BCD variables, wherein the second compiler expression includes packed decimal operations and the assigned temporary variables; and converting a packed decimal operation in the second compiler expression and an assigned temporary variable to a decimal floating point (DFP) if sign information and precision information are not lost during conversion from BCD to DFP, wherein identifying logical BCD variables includes: in the use-definition and / or definition-use of operands, regarding an operand of definition and an operand of use as the same logical BCD variables.
Owner:IBM CORP
Data management/control method and system used for monitoring system
InactiveCN108595302AGuaranteed to be documentedSolve the insufficient amount of dataHardware monitoringTemporary variableIn-memory database
The invention discloses a data management / control method and system used for a monitoring system. The method includes: acquiring real-time monitoring data of target equipment; judging whether real-time monitoring data and data in temporary variables in the monitoring system are the same, wherein the data in the temporary variables are historical monitoring data of the target equipment; if not, storing the real-time monitoring data into a memory database of the monitoring system, and updating the data in the temporary variables to the real-time monitoring data; and if yes, discarding the real-time monitoring data. Changed real-time data are all stored in the memory database, an effect that all data are well documented and can be queried is guaranteed, data as detailed as possible can be provided for a user, data analysis and problem locating in problem appearing of the monitored equipment are facilitated, the amount of data needing to be stored is reduced, system resources are saved, the monitoring data are stored in the memory database, operation speed is high, too many burdens cannot be caused on the system, and system loads are reduced.
Owner:XIAMEN KECAN INFORMATION TECH +1
Quenching Device for a Converter Bridge with Line Regeneration
InactiveUS20080037960A1Convenient ArrangementReliable controlAC motor controlEmergency protective circuit arrangementsTemporary variableEngineering
There is described a method for controlling a quenching device for a converter bridge with line regeneration, whereby the converter bridge controlled by a network-timed control circuit by ignition pulses is connected with its at least three inputs to the phases of a three-phase network and the at least two outputs of the bridge are connected to a direct-current motor which feeds, when operated as a generator, current back to the three-phase network via the bridge. The quenching device is controlled by a trigger unit which emits trigger pulses depending on the monitoring of electrical and temporary variables. The device has measuring values “direct output current” and / or “supply voltages” used to determine characteristic values which are compared with theoretical characteristic values. Depending on the result of said comparison, the quenching device is optionally activated.
Owner:SIEMENS AG
Tile-based processor architecture model for high-efficiency embedded homogeneous multicore platforms
ActiveUS9275002B2Energy efficient ICTConcurrent instruction executionTemporary variableTelecommunications link
The present invention relates to a processor which comprises processing elements that execute instructions in parallel and are connected together with point-to-point communication links called data communication links (DCL). The instructions use DCLs to communicate data between them. In order to realize those communications, they specify the DCLs from which they take their operands, and the DCLs to which they write their results. The DCLs allow the instructions to synchronize their executions and to explicitly manage the data they manipulate. Communications are explicit and are used to realize the storage of temporary variables, which is decoupled from the storage of long-living variables.
Owner:MANET PHILIPPE +1
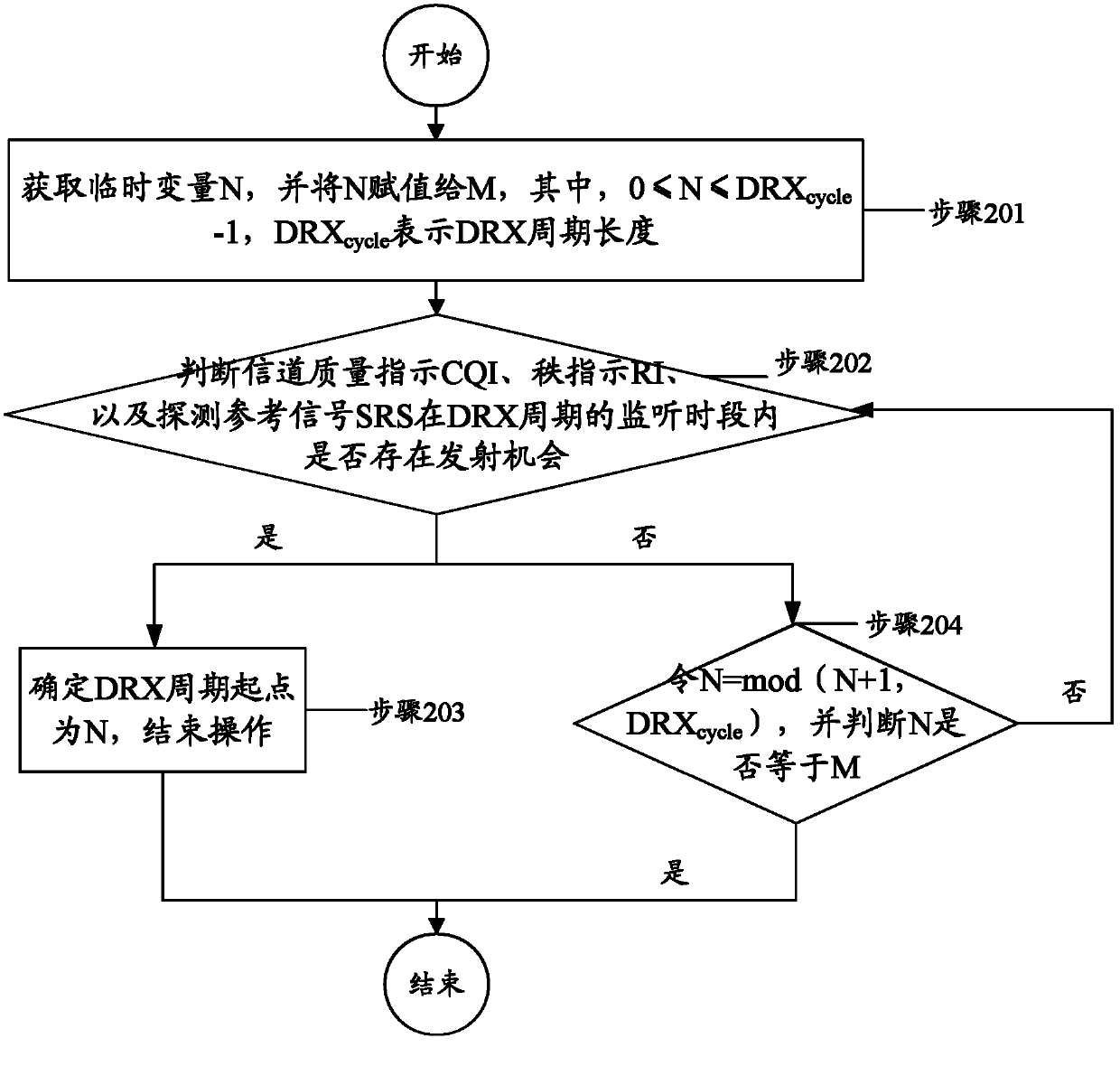
Method of determining starting point of drx discontinuous reception cycle and apparatus thereof
ActiveCN103378959AGuaranteed assessmentBalance hardware loadError preventionTransmission path multiple useTemporary variableSounding reference signal
The invention discloses a method of determining a starting point of a drx discontinuous reception cycle and an apparatus thereof. The method comprises a first step of obtaining a temporary variable N and assigning N to M, where, 0 is less than or equal to N is less than or equal to DRXcycle-1 and DRXcycle represents a DRX cycle length; a second step of determining whether a channel quality indicator (CQI), a rank indication (RI) and a sounding reference signal (SRS) have a launch opportunity in a DRX cycle monitoring period, and executing a third step if the answer is yes or executing a fourth step otherwise; the third step of determining N as the starting point of the DRX cycle and ending the operation; and the fourth step of letting N equal to mod(N+1, DRXcycle), determining whether N is equal to M or not, and ending the operation if the answer is yes, or executing the second step otherwise. With the technical scheme of the invention, evaluation of the quality of uplink and downlink channels can be effectively ensured and throughput of the system is improved.
Owner:苏州医疗器械产业发展集团有限公司
Parameterization BCH (broadcast channel) error-correcting code parallel encoding method and device
InactiveCN103401566AImprove encoding speedFast encodingCyclic codesBroadcast channelsTemporary variable
The invention discloses a parameterization BCH (broadcast channel) error-correcting code parallel encoding method and device. The method comprises the following steps of determining three variable parameters such as the error-correctable bits t, bit width p of the parallel encoding and length k of data information bit, solving a generation polynomial matrix, wherein the number of times of the generation polynomial matrix g(X) is (n-k); carrying out the logic operation for a temporary variable of a check bit and the generation polynomial matrix, and finally outputting a complete encoding module described through a verilog HDL (hardware description language) language. The generated encoding module is high in encoding speed and less in occupied resource. The encoding module utilizes one generation matrix to realize the parallel encoding function and is finally solved through a series of operation according to the generation polynomial of the BCH code. The method and the device are applicable to the application with long code word, high encoding speed and capability for continuously enhancing the error correcting capacity of the error-correcting code.
Owner:HOHAI UNIV
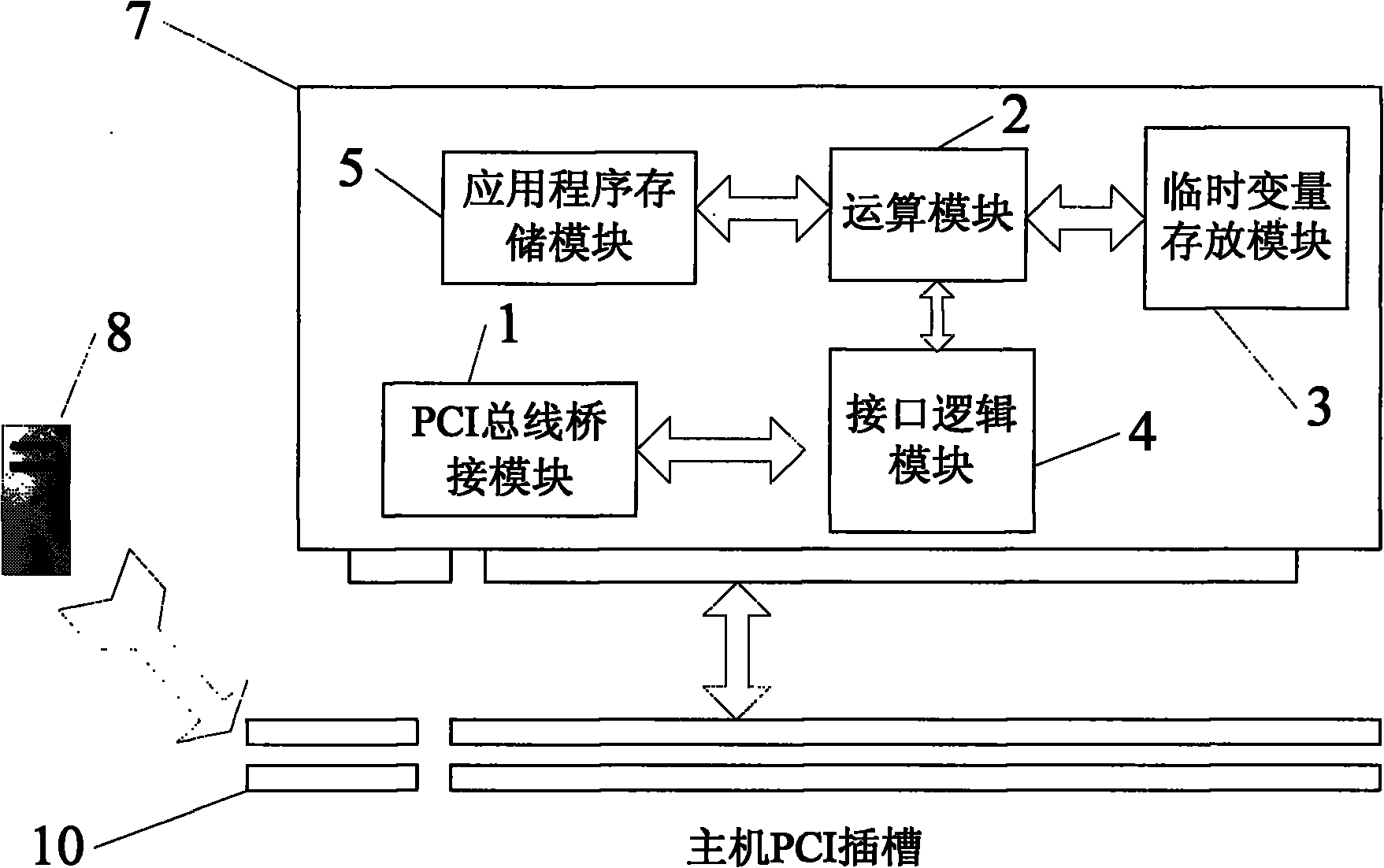
FPGA (Field Programmable Gate Array) high-performance operating PCI (Peripheral Component Interconnect) card
InactiveCN101833534ATransmission speed blockMature technologyGeneral purpose stored program computerElectric digital data processingTemporary variableOperational system
The invention relates to an FPGA (Field Programmable Gate Array) high-performance operating PCI (Peripheral Component Interconnect) card which comprises hardware comprising a PCI bus bridging module, a computing module, a temporary variable storage module, an interface logical module and an application storage module. During working, the PCI card is inserted in a PCI slot of a computer, driven under the Windows operation system and controlled by application software to realize high-speed operation. The PCI card has the advantages of high transmission speed and strong functionality, expansibility and programmability, and corresponding application software can be designed according to different applications to realize different operation functions so as to be convenient for the PCI card to be applied to other fields.
Owner:WUXI TONGWEI TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com