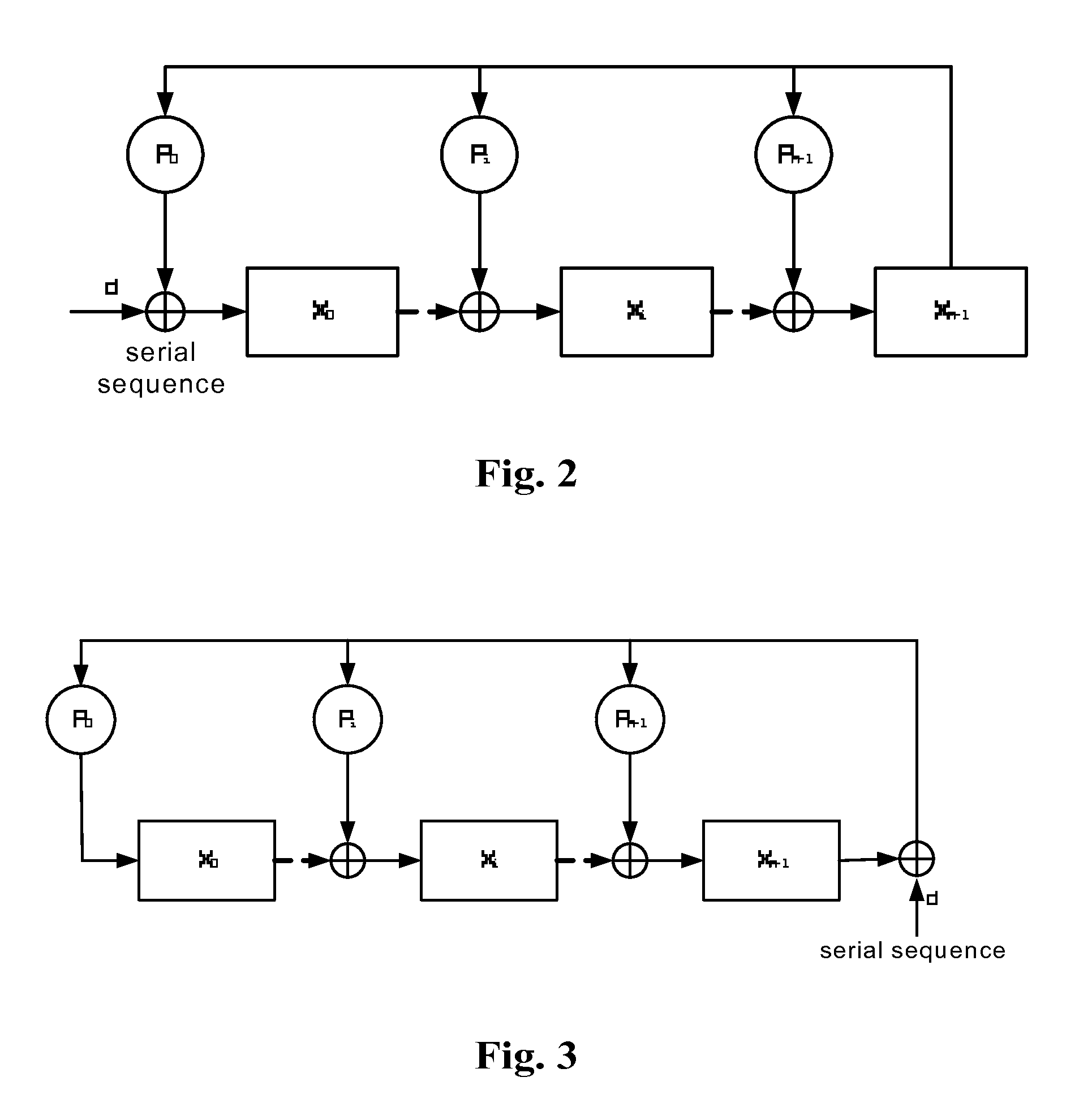
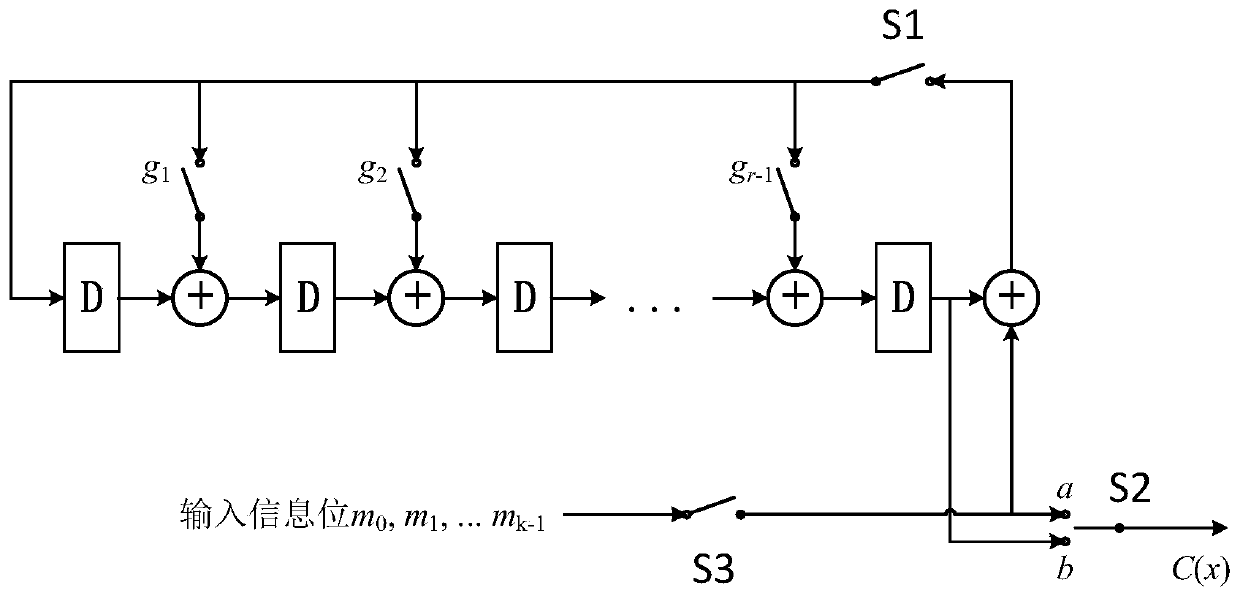
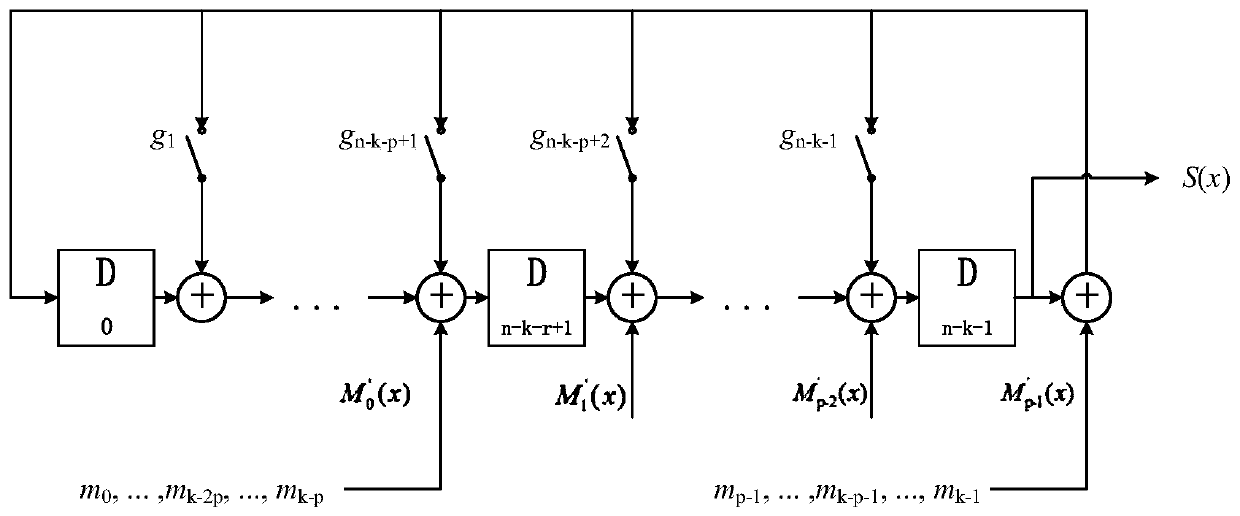
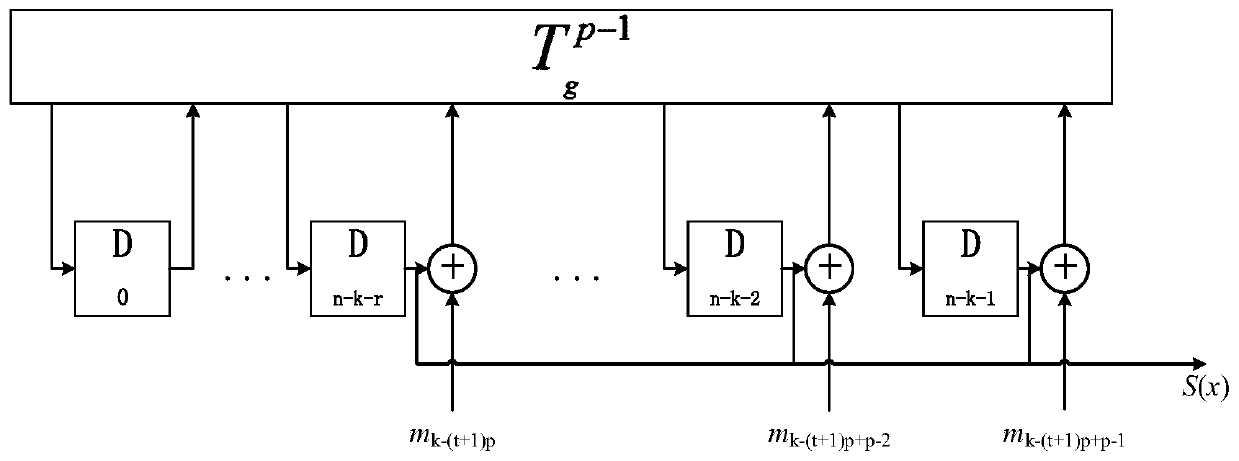
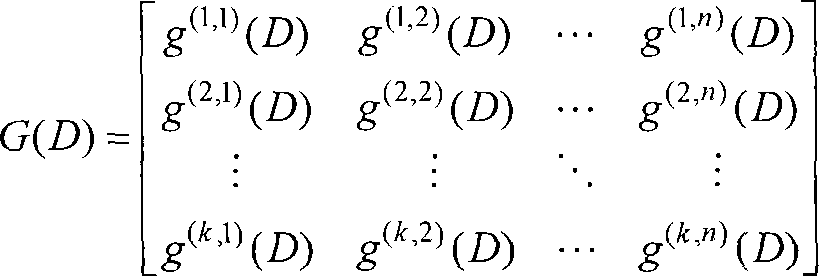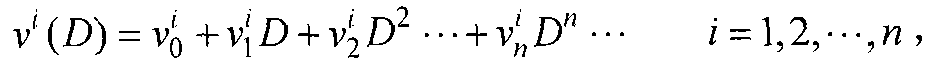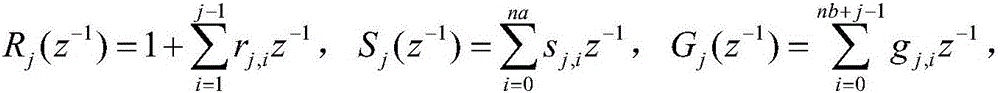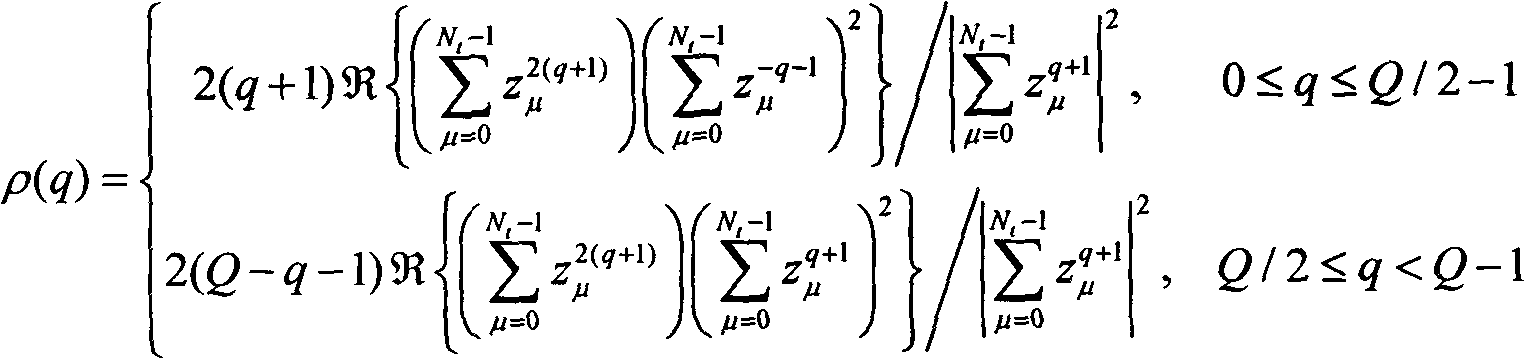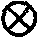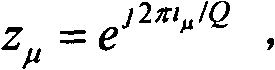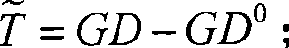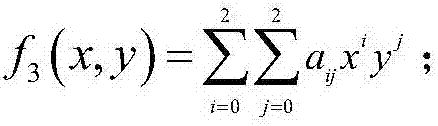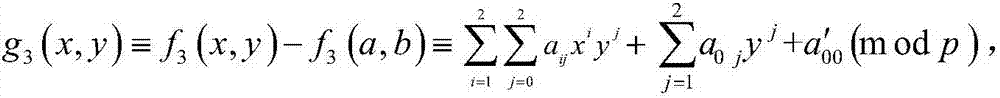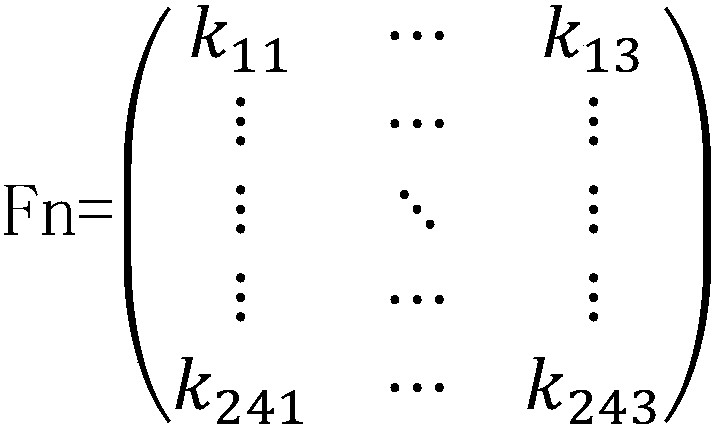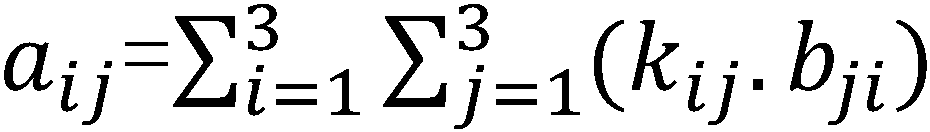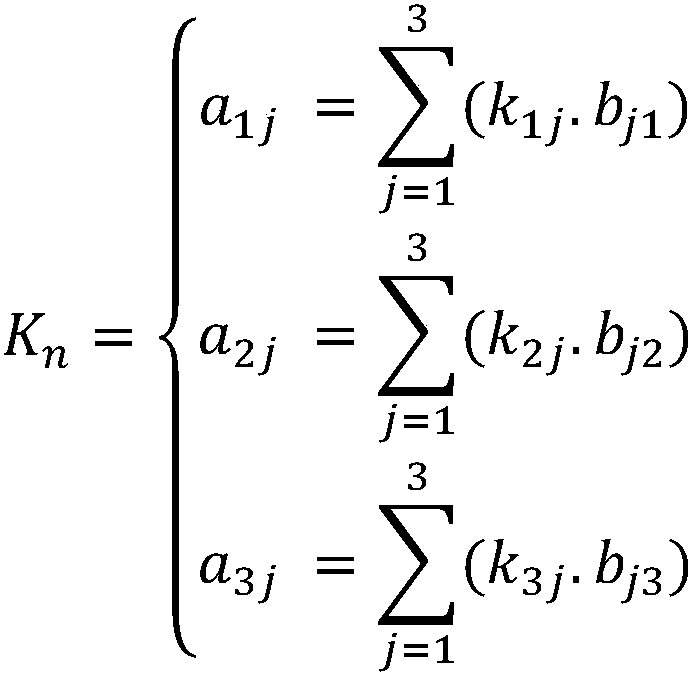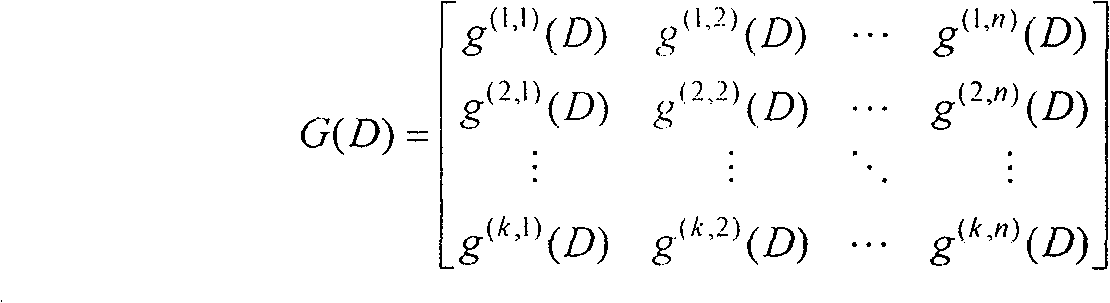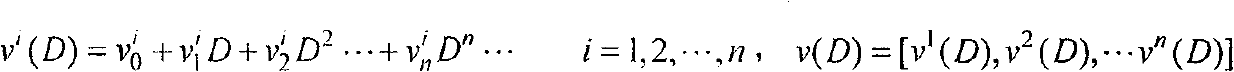Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39 results about "Polynomial matrix" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
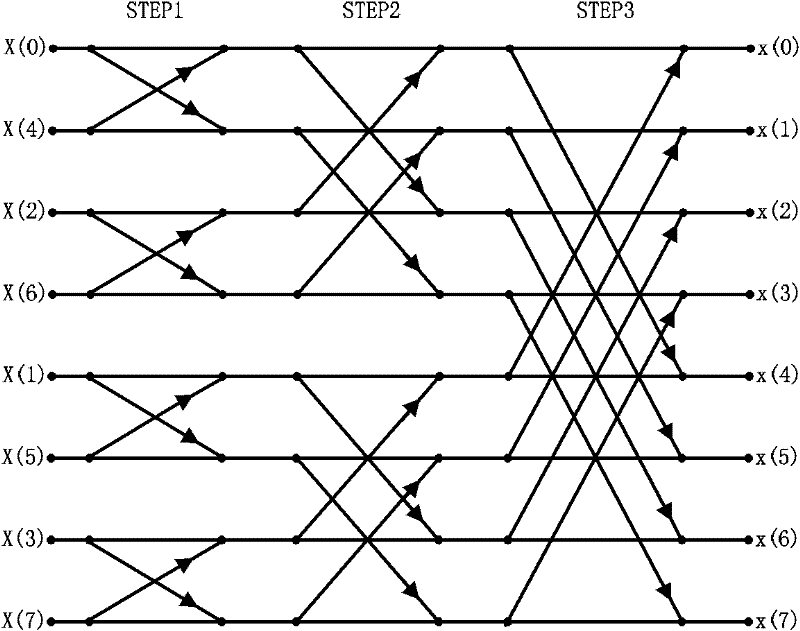
In mathematics, a polynomial matrix or matrix of polynomials is a matrix whose elements are univariate or multivariate polynomials. Equivalently, a polynomial matrix is a polynomial whose coefficients are matrices.
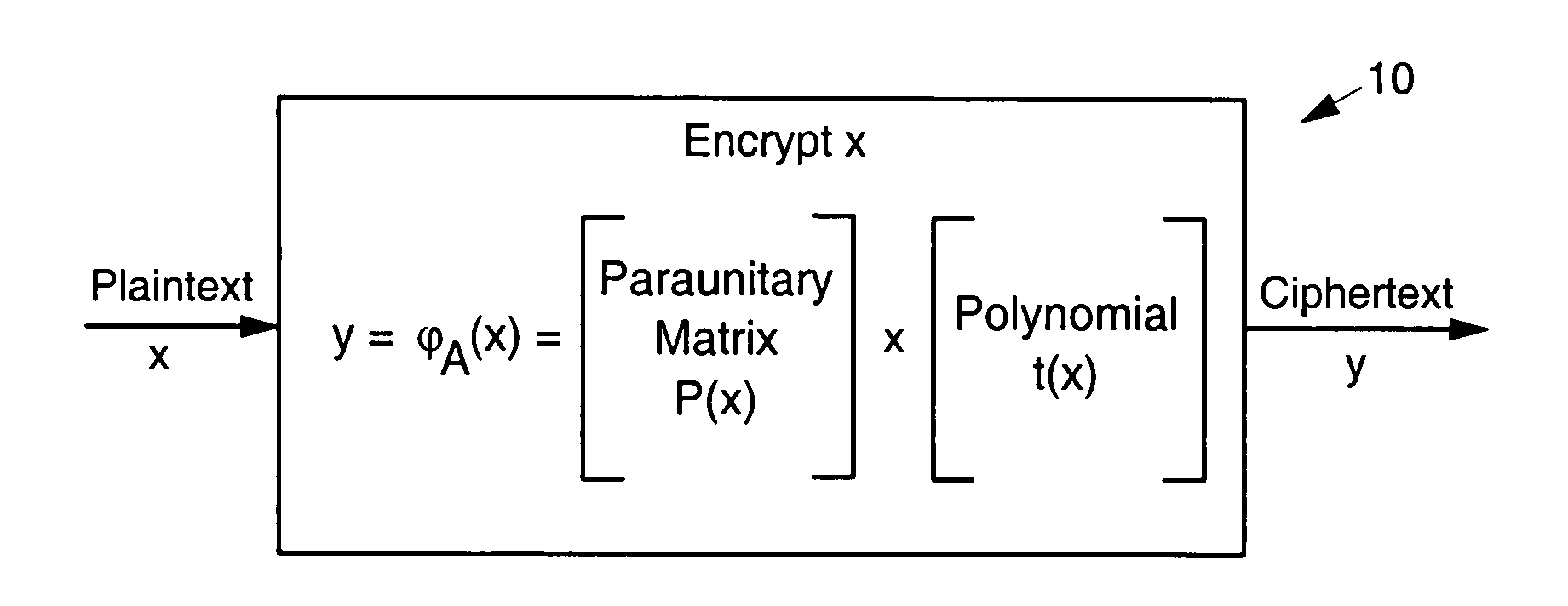
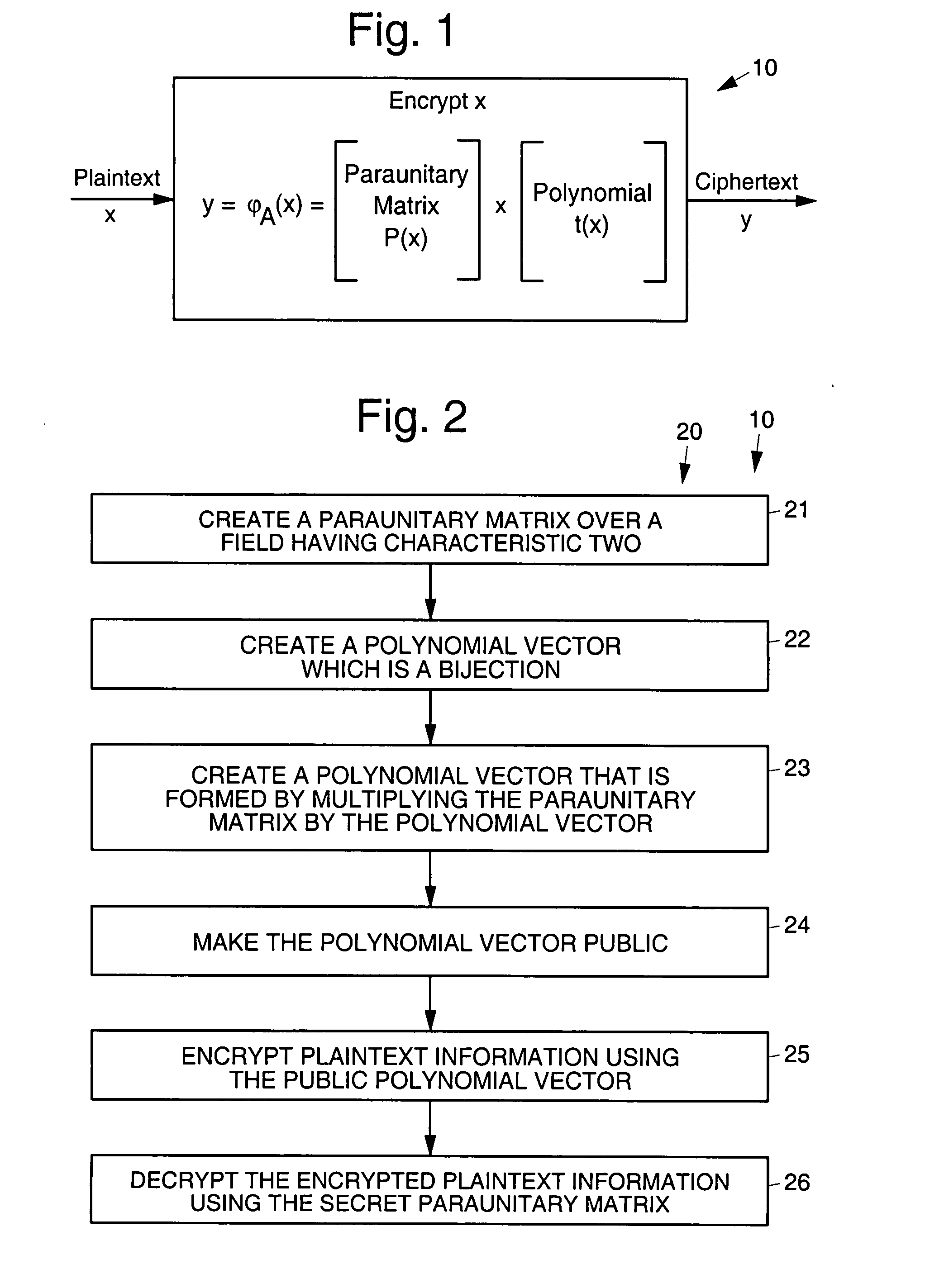
Asymmetric cryptosystem employing paraunitary matrices
InactiveUS20090010428A1Public key for secure communicationSecret communicationNon symmetricCiphertext
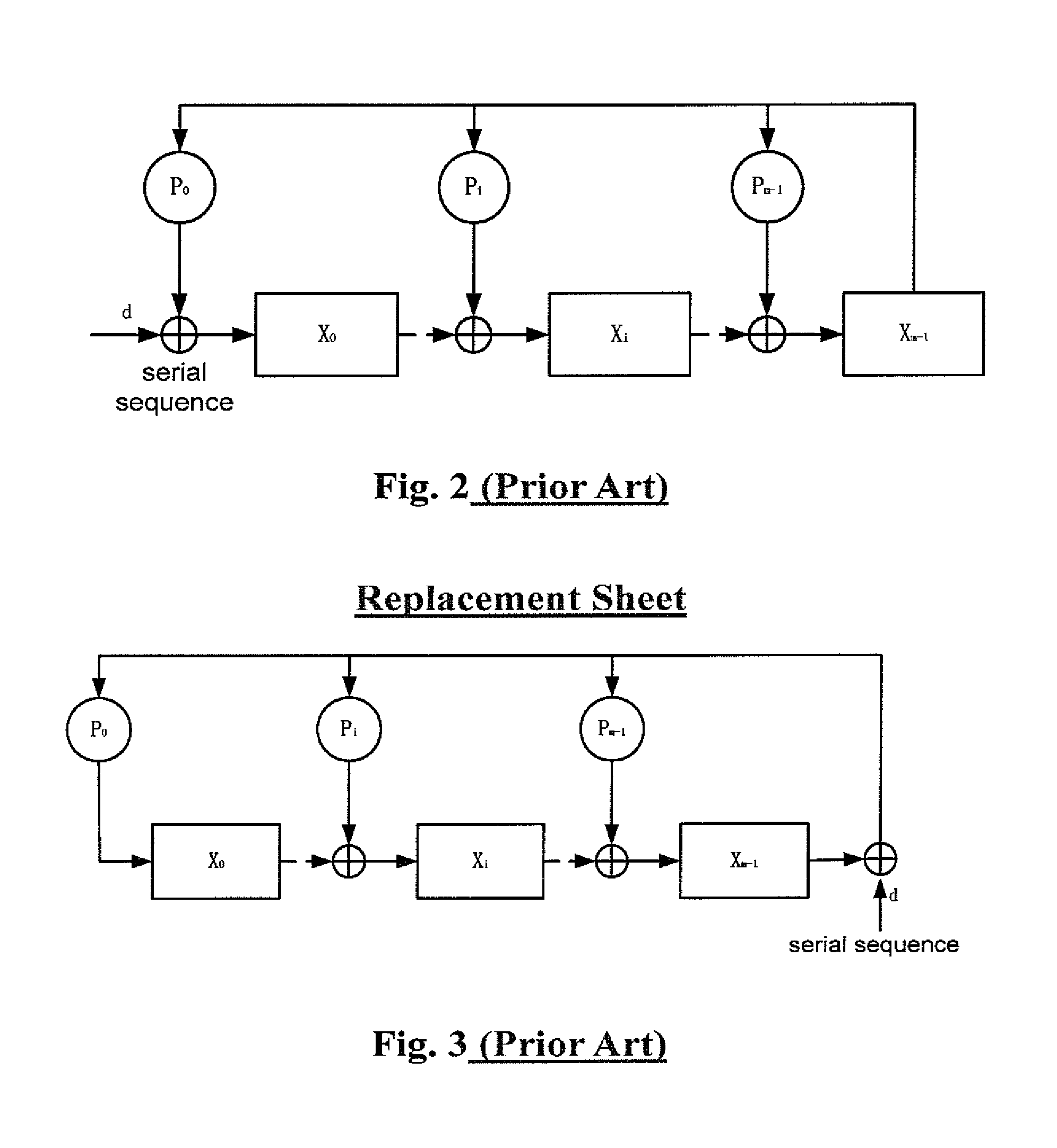
Disclosed are multivariate paraunitary asymmetric cryptographic systems and methods that are based on paraunitary matrices. An algebraic approach is employed in designing the multivariate cryptographic systems and methods. The cryptographic systems and methods are based on formulating a general system of multivariate polynomial equations by paraunitary matrices. These matrices are a family of invertible polynomial matrices that can be completely parameterized and efficiently generated by primitive building blocks. Using a general formulation that involves paraunitary matrices, a one-way function is designed that operates over the fields of characteristic two. To include a trapdoor, approximations are made to the paraunitary matrix. The result is a trapdoor one-way function that is efficient to evaluate, but hard to invert unless secret information about the trapdoor is known. An exemplary implementation operates on the finite field GF(256). In this example, the message block includes 16 to 32 symbols from GF(256), i.e., the block size n is an integer between 16 and 32. The ciphertext block takes its elements from the same field and has at least 10 extra symbols.
Owner:GEORGIA TECH RES CORP
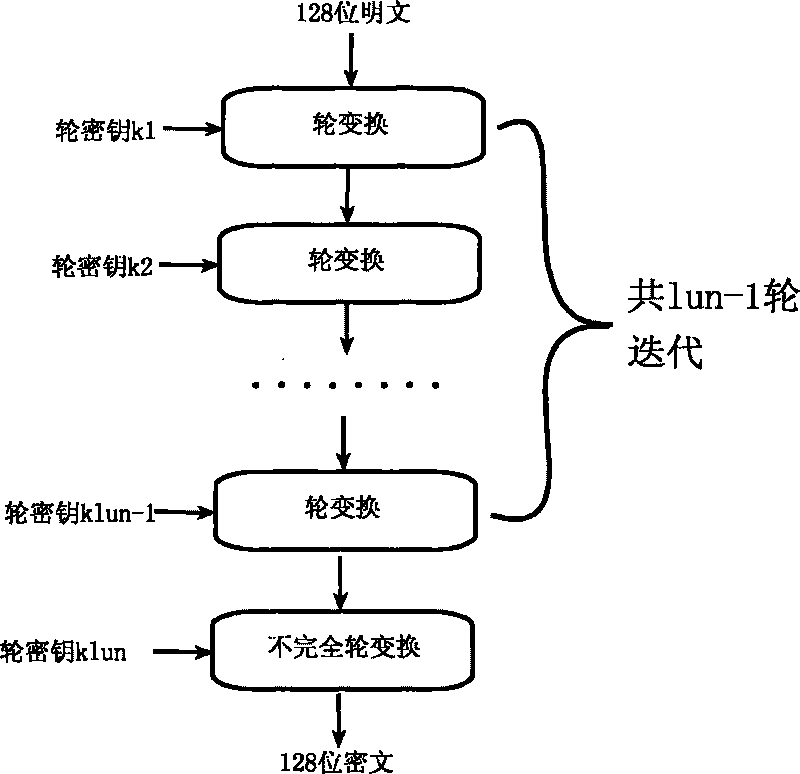
Encryption method for network and information security
ActiveCN101764686AHigh speedDiffusion is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareKey size
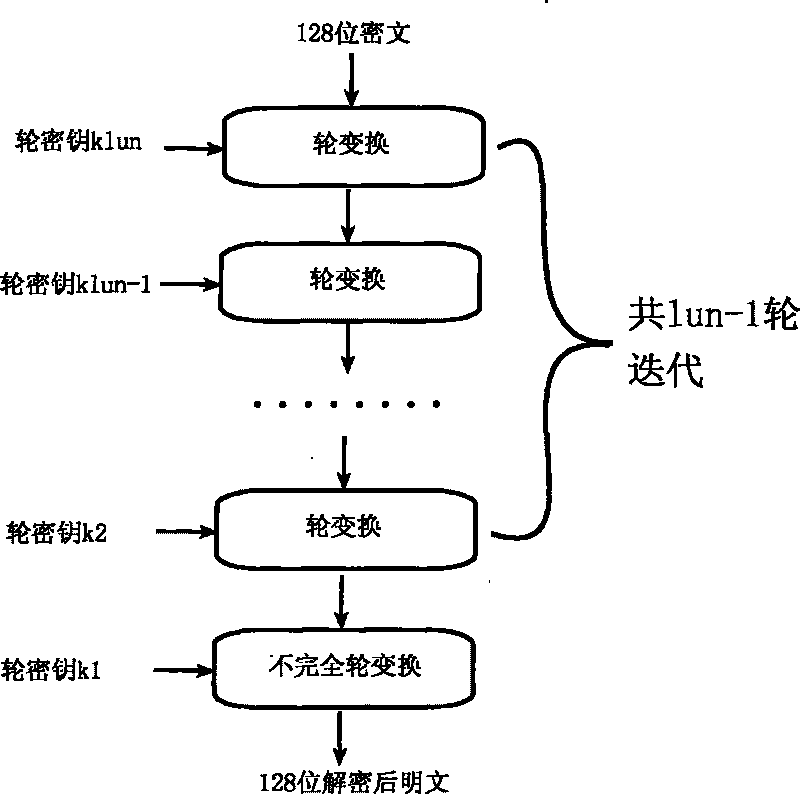
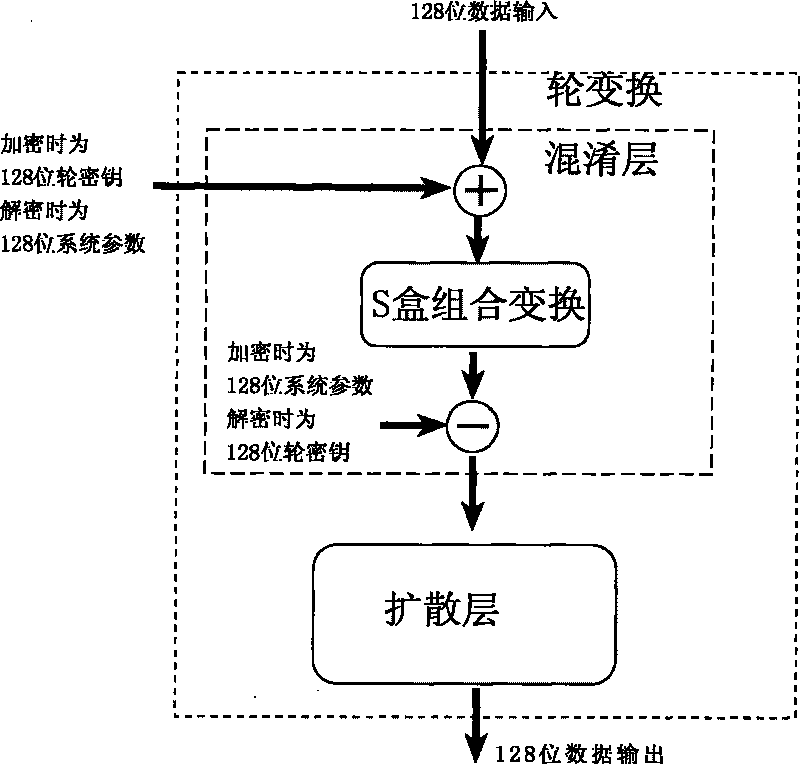
The invention relates to an encryption method for network and information security; the adopted packet length and key length are 128 bits, and a 128-bit system parameter is added; encryption algorithm comprises a plurality of rounds of round transform iteration consisting of mixed layers and diffusion layers, wherein the last round is incomplete round transformation, and the incomplete round transformation consists of the mixed layer; the mixed layer comprises key plus, S box portfolio transform and system parameter minus; the S box portfolio transform comprises 8-input 8-output reversible S box transform and inverse S box transform in the same number which are output by parity exchange; the diffusion layer can construct linear transformation with a reversible re-model polynomial matrix; an encryption round key is generated by an encryption key through encryption round transformation; and decryption algorithm is the inverse transformation of encryption algorithm. The encryption methodfor network and information security has the advantages of high diffusion speed, good security strength, hardware resource saving, and very high speed when being realized by hardware and on a software platform.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
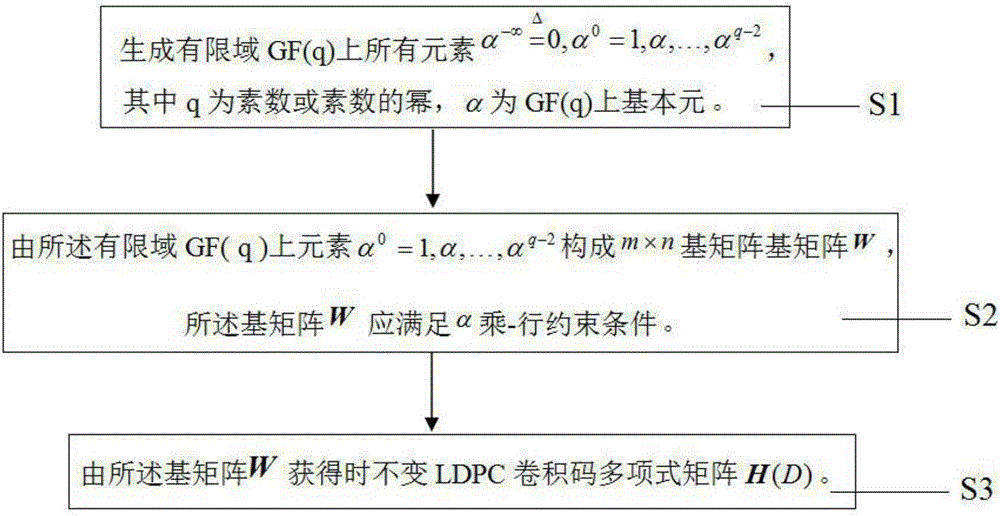
Method for constructing time invariant LDPCC based on PEG algorithm, and encoder/decoder
InactiveCN101094000AImprove performanceDoes not decode complex structuresError correction/detection using multiple parity bitsParallel computingConvolutional code
Construction method and codec of invariant time low-density parity check convolutional (LDPCC) code is based on item-by-item adding edge algorithm PEG. The invention discloses new method for constructing invariant time LDPCC code, and codec for compiling the LDPCC. The method for constructing LDPCC code includes encoder and decoder. Operational steps include as following: determining parameters of checkout matrix HQT of group code of permutation unit matrix LDPC; constructing checkout matrix HQT of group code of permutation unit matrix LDPC; constructing checkout polynomial matrix HT (D) of LDPCC code; exporting generated matrix G (D) of LDPCC code. Obtaining invariant time LDPCC code, the method guarantees fine loop characteristic and code gap characteristic, and superior performance. The invention implements encoding simple invariant time convolutional code and iterative decoding through pipeline.
Owner:PEKING UNIV
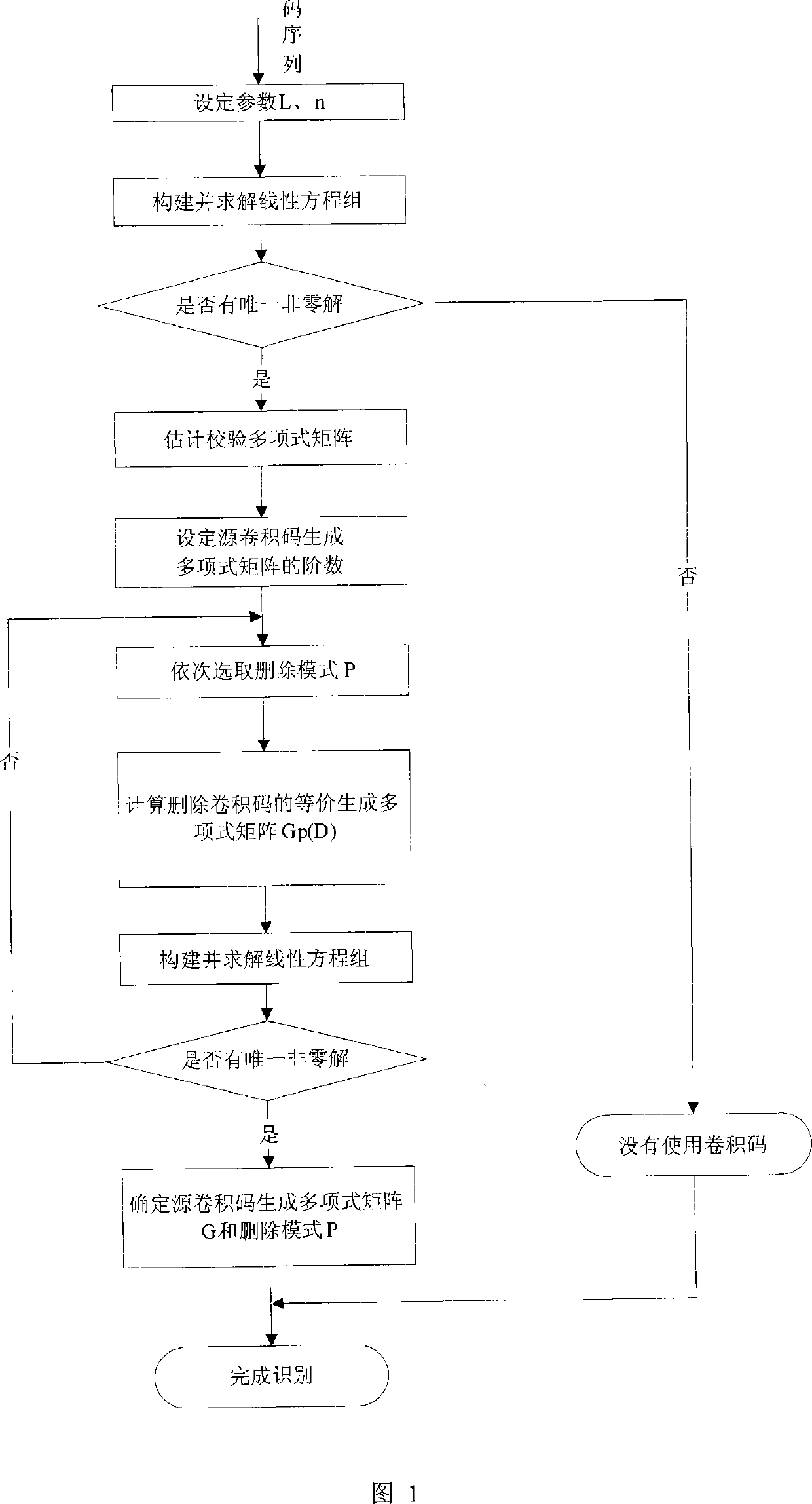
A blind recognition method for deleting cirrocumulus code of (n-1)/n code rate
InactiveCN101237239ASolve quickly and efficientlyReduce orderError correction/detection using convolutional codesError preventionMathematical modelTheoretical computer science
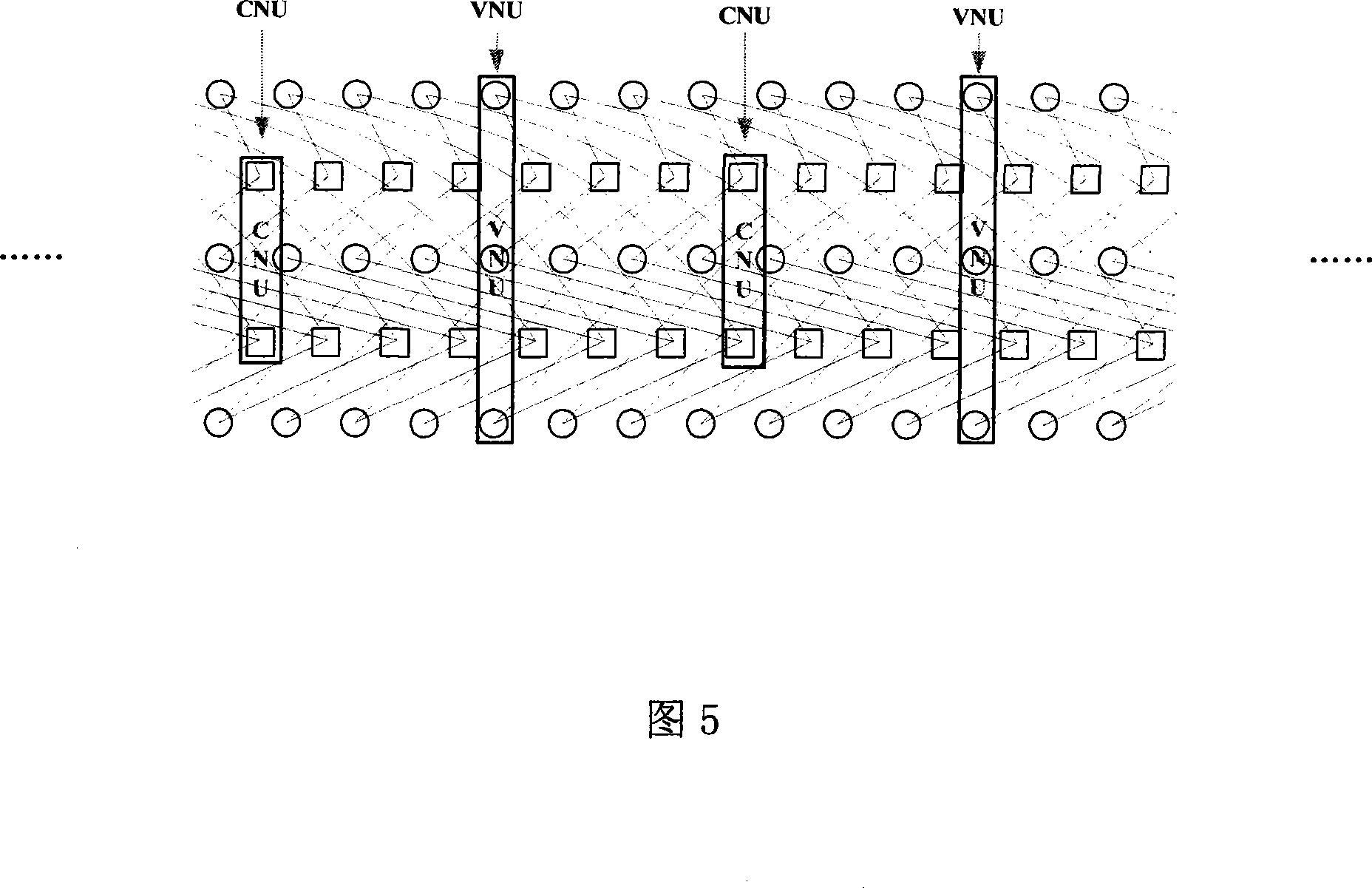
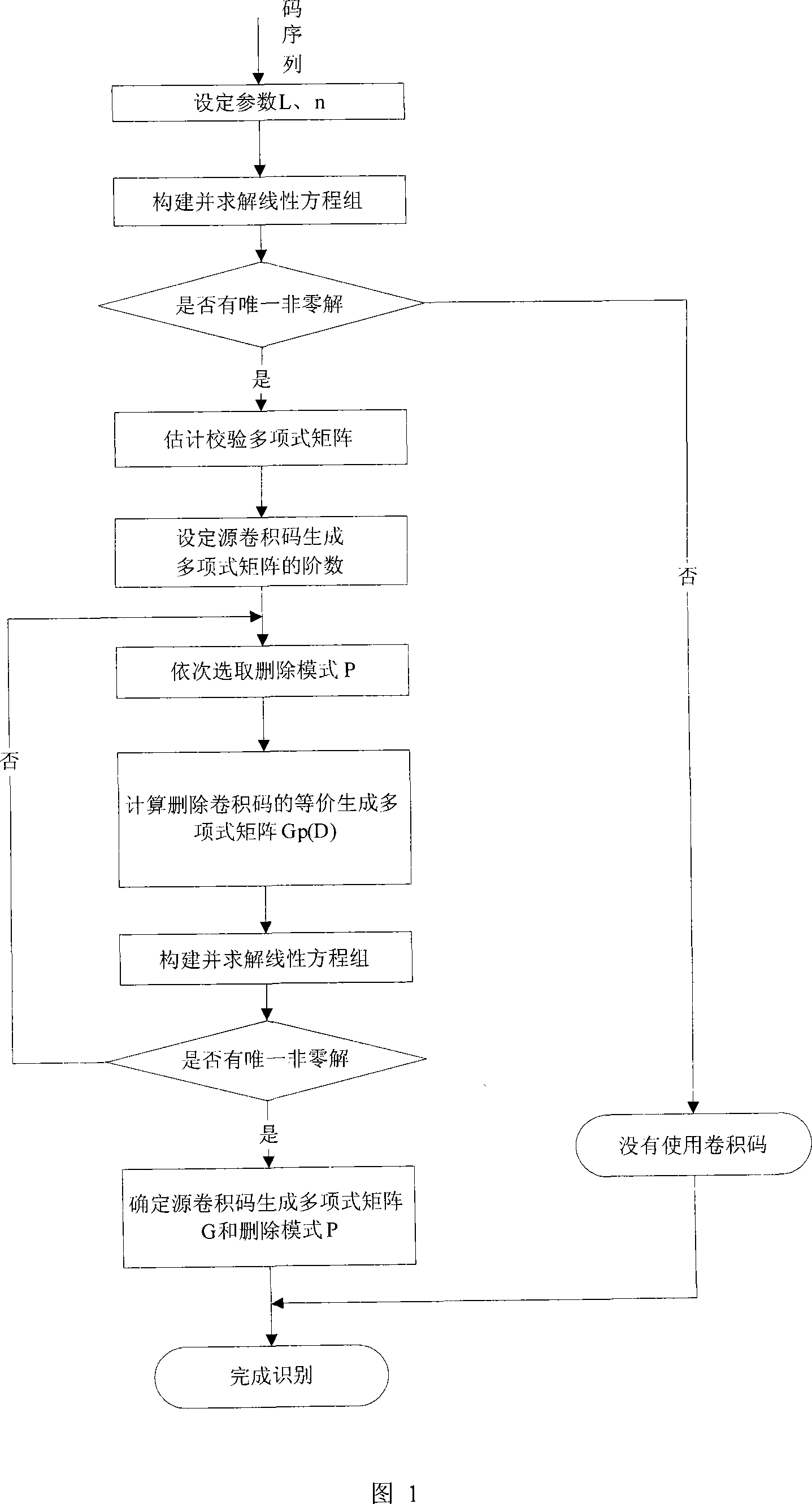
The invention discloses a blind identification method for punctured convolutional codes with a code rate of (n-1) / n. A mathematical model v(D)=m(D)G(D) for blind identification of the punctured convolutional codes is established at first, wherein, v(D) represents code output sequence; m(D) represents information sequence waiting for coding; G(D) represents generator polynomial matrix; on the ground that the code output sequence v(D), the generator polynomial matrix G(D) and a check polynomial matrix H(D) meet relational expressions G(D)H(D)<T>=0 and v(D)H(D)<T>=m(D)G(D)H(D)<T>=0, the check polynomial matrix H(D) is estimated by the v(D) at first and then the generator polynomial matrix G(D) is estimated, and finally the received code output sequence v(D) is combined and the information sequence m(D) is recovered. The blind identification method for the punctured convolutional codes with a code rate of (n-1) / n can identify the punctured convolutional codes more simply and more quickly and simultaneously solve the problem that initial place values of code words of the convolutional codes are fuzzy.
Owner:黄知涛
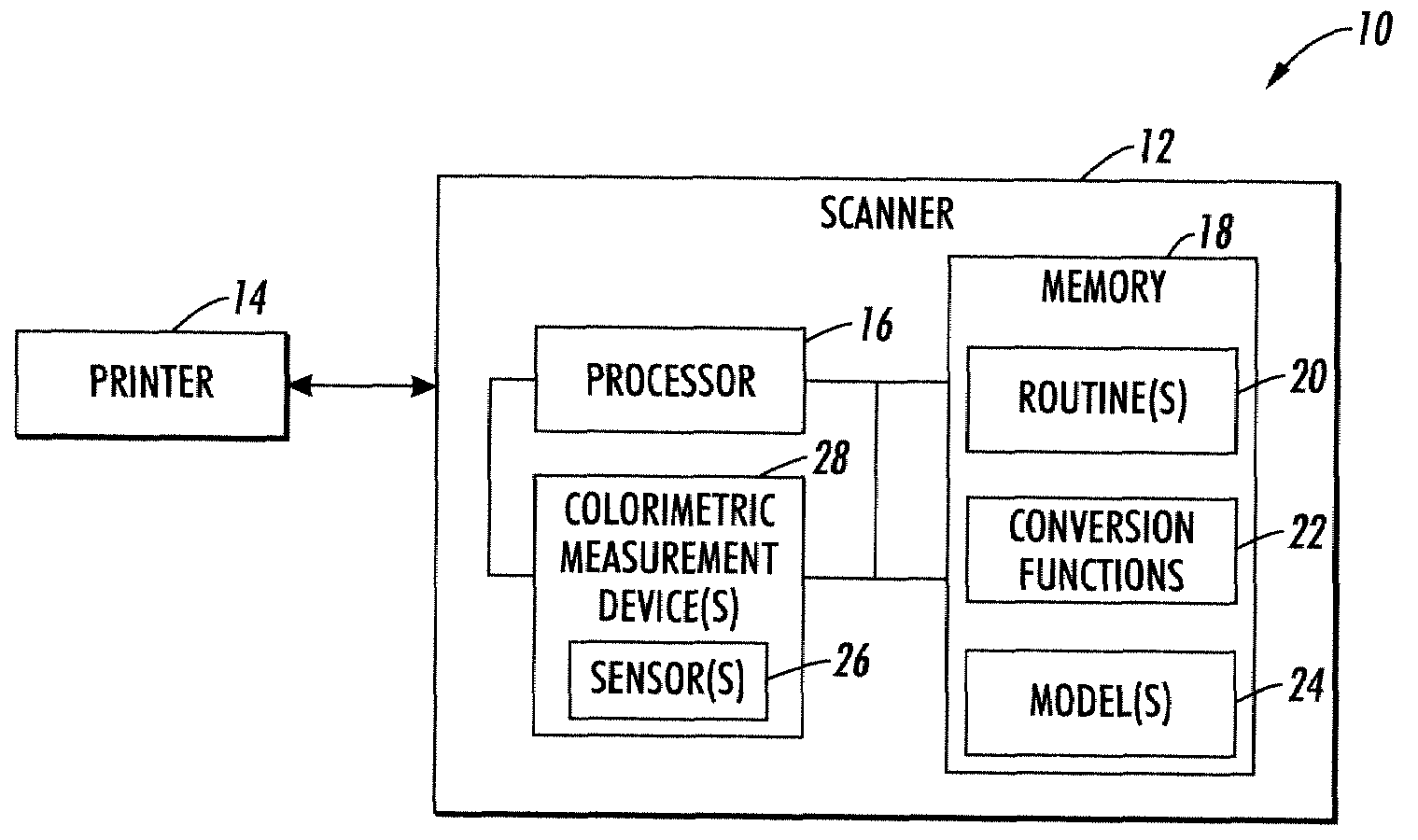
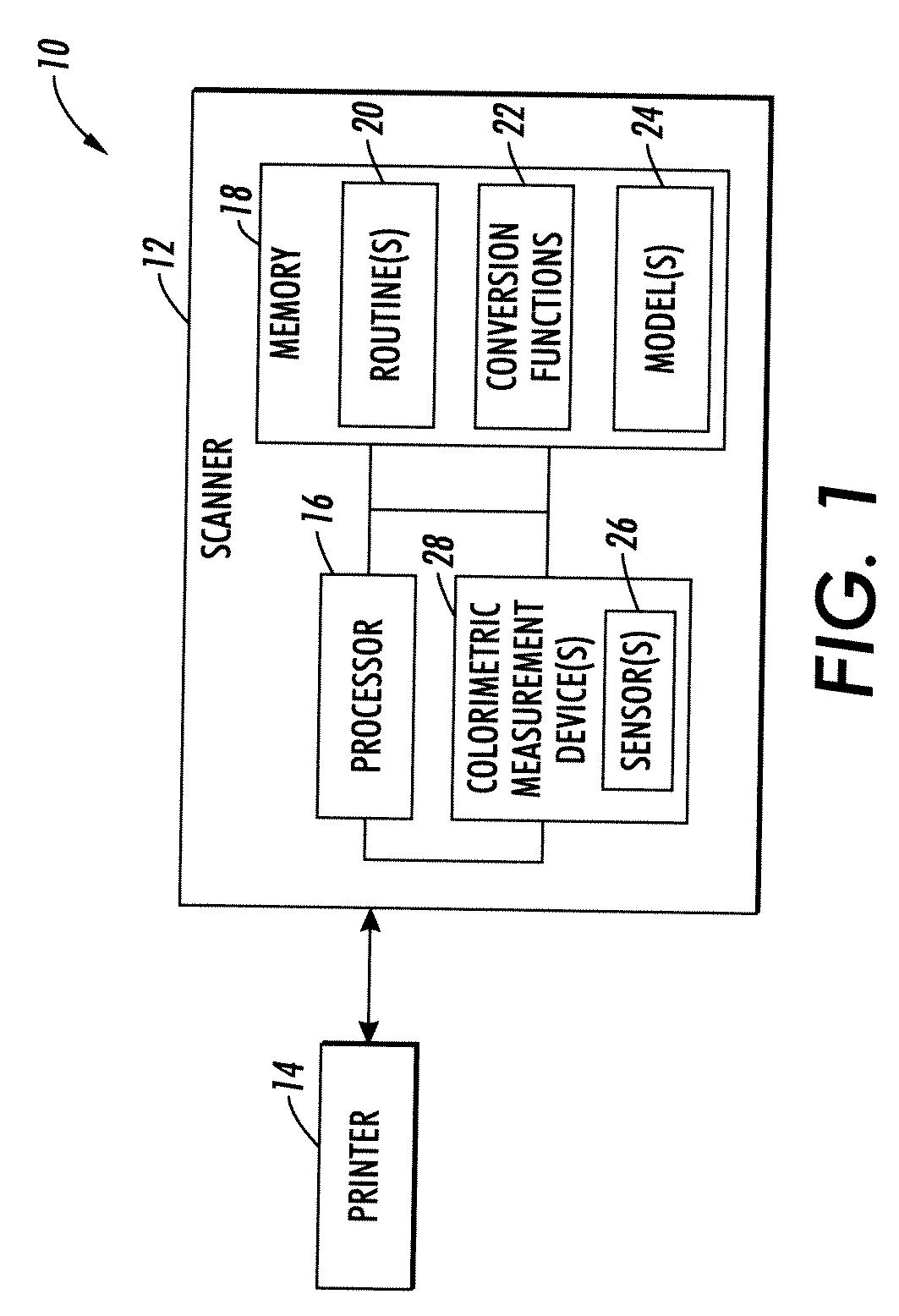
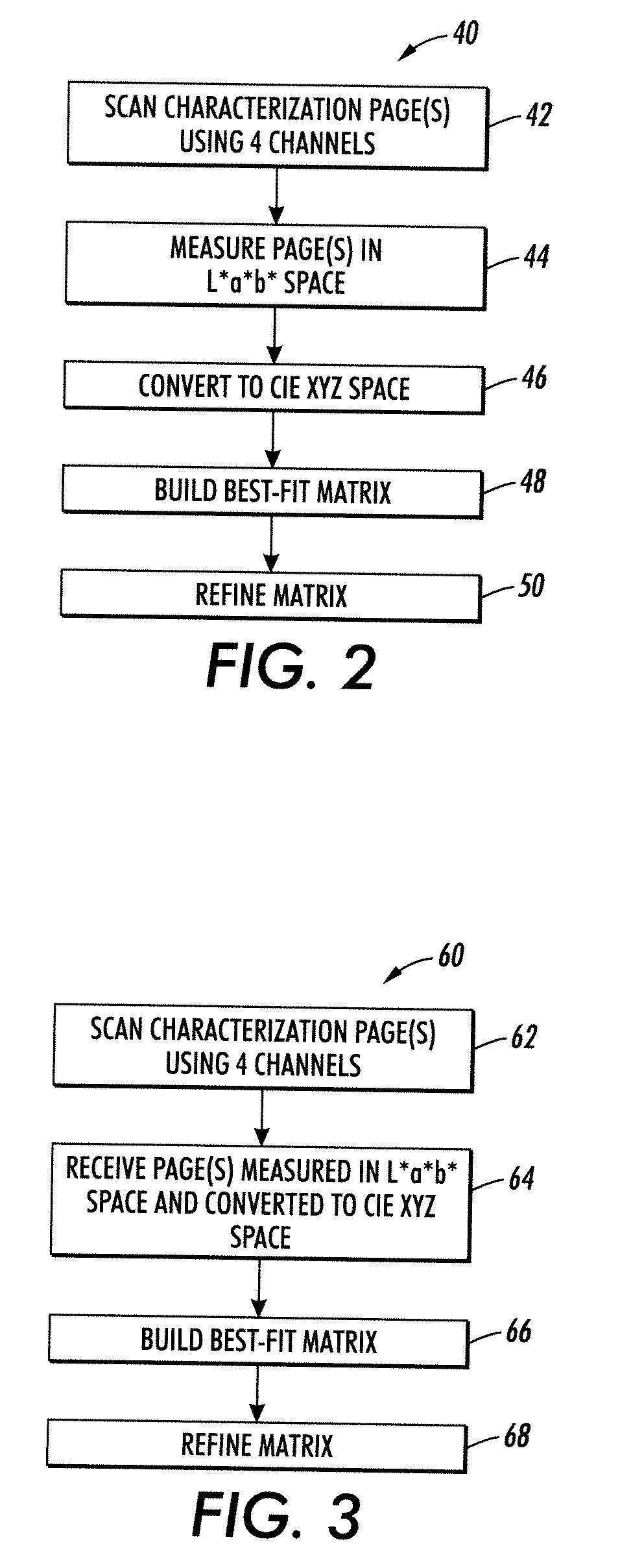
L*a*b* SCANNING USING RGB-CLEAR
InactiveUS20090086292A1Easy CalibrationReduced metamerismColour-separation/tonal-correctionPictoral communicationAlgorithmLinear model
Systems and methods are described that facilitate reducing metamerism in a scanner or printer system by evaluating and manipulating unfiltered clear channel information. Using a four channel model to predict CIE XYZ tristimulus values from RGB and clear, a linear model is generated based on a polynomial matrix conversion. For example, one such model has coefficients weighting 1, R, G, B, W, R2, G2, B2, W2, RG, RB, RW, GB, GW, BW, and corresponding third order terms. The XYZ values predicted by the linear model are converted to L*a*b*, and compared with measured L*a*b* values. A statistic involving the difference between measured and computed L*a*b* values is used as a metric in a non-linear optimization to obtain the best values for the matrix elements. Once the matrix is optimized, it is employed for printer calibration, error detection, and the like.
Owner:XEROX CORP
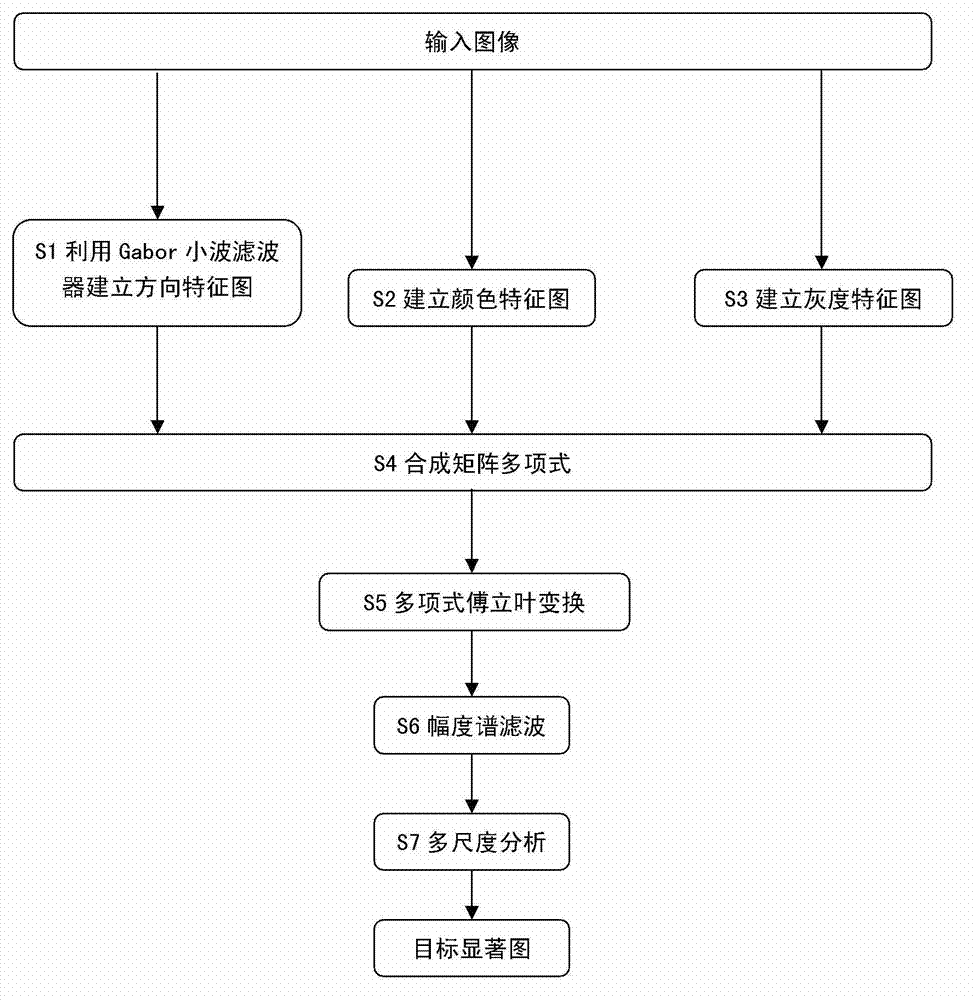
Frequency domain saliency target detection method based on Gabor wavelets
The invention relates to a frequency domain saliency target detection method based on Gabor wavelets. The method includes the steps: S1, switching inputted color images into gray images and building a directional feature map; S2, building two color feature maps according to sensitivity of human eyes on different colors of the inputted color images; S3, building a gray feature map for the inputted color images; S4, building a polynomial matrix by the aid of the four feature maps; S5, performing Fourier transformation for the polynomial matrix comprising the four feature maps to obtain a frequency domain polynomial matrix and extracting a magnitude spectrum matrix; S6, performing Gaussian low-pass filter for the magnitude spectrum matrix by a plurality of scales and performing polynomial inverse Fourier transformation for a group of magnitude spectra to obtain a plurality of time domain polynomial matrixes; and S7, dividing the time domain polynomial matrixes into different time domain polynomials according to different scale factors, building a histogram for each time domain polynomial, calculating a one-dimensional entropy function and extracting a time domain saliency map corresponding to the minimum information entropy as a final detection result.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
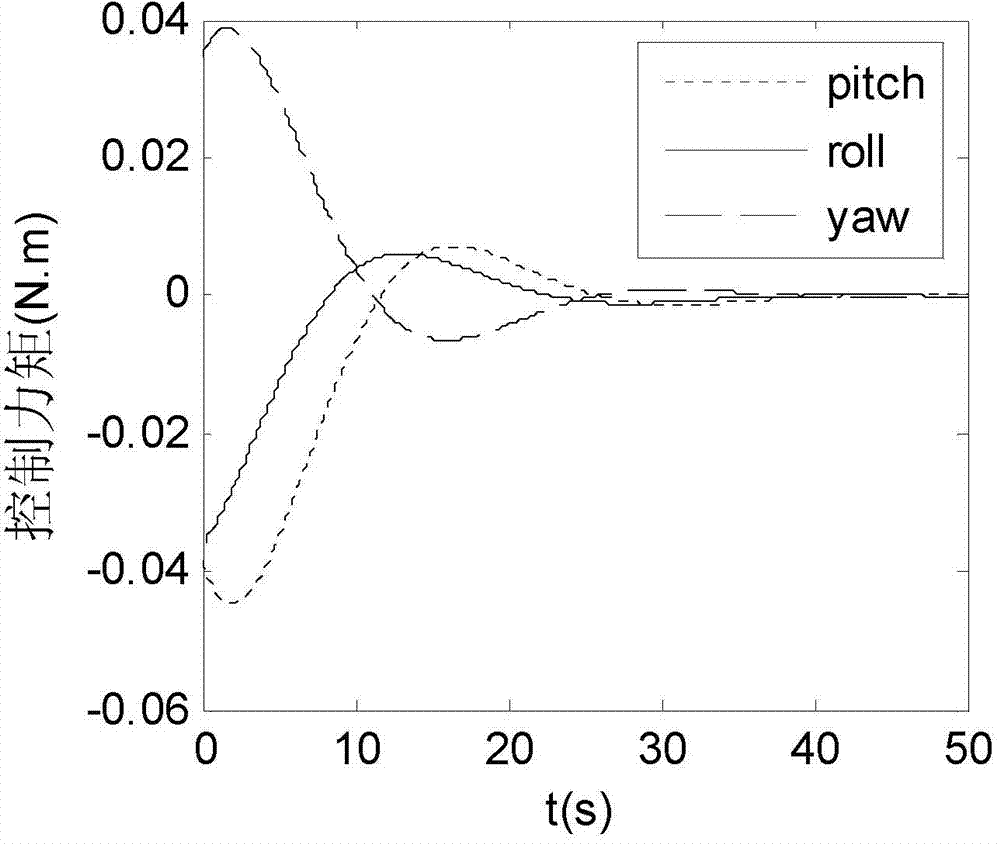
Rotational inertia determination method for satellite attitude control system
The invention discloses a rotational inertia determination method for a satellite attitude control system and relates to the technical field of satellite control. The method aims to determine the accurate change range of rotational inertia in the satellite attitude control system. The method is technically characterized by comprising the following steps of firstly, building a satellite attitude control system model containing indeterminacy; secondly, making a corresponding constraint index, and acquiring a proper H(u) infinity ( / u) state feedback controller; finally, expressing the indeterminacy in a closed loop system as a form of a polynomial matrix cell, and solving the change range of the indeterminacy of the rotational inertia by using a linear matrix inequality method. According to the method, the change range of the rotational inertia of a satellite under the condition of state feedback is judged by using the stability conditions of the polynomial matrix cell. The indeterminacy is taken into consideration in the design stage of the controller, and the influence on output caused by the indeterminacy serves as a control index, and the indeterminacy in the closed loop system is expressed as the polynomial matrix cell.
Owner:HARBIN INST OF TECH
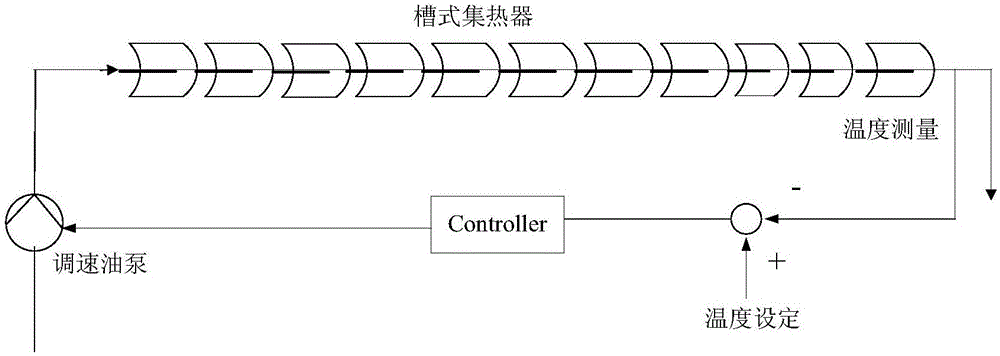
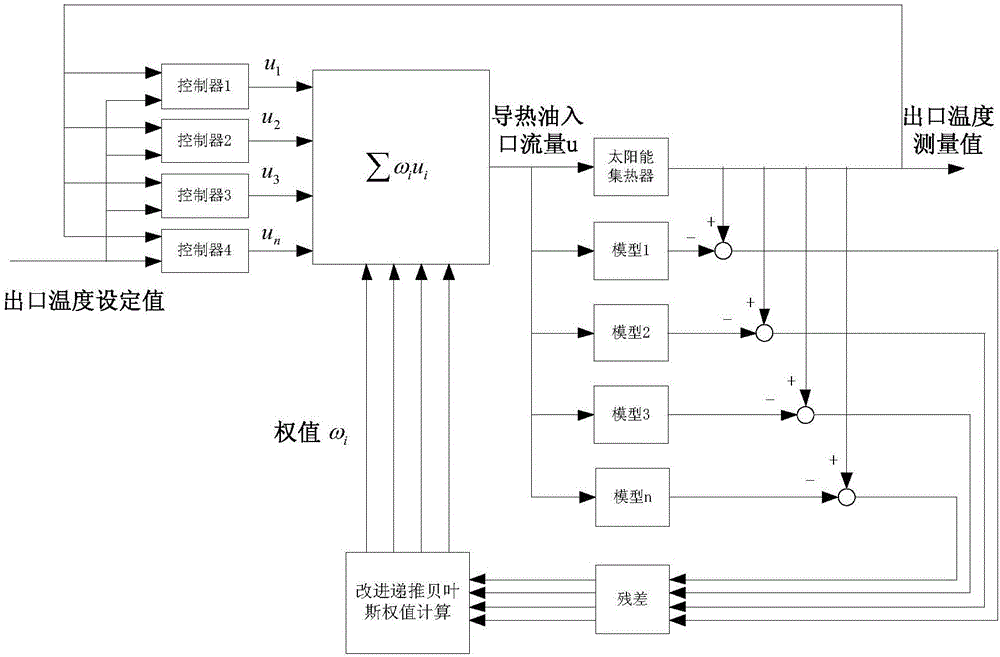
Temperature multi-model prediction function control method and device
InactiveCN106610587AEffective controlSmall amount of calculationAdaptive controlTemperature controlTransfer function model
The invention relates to a temperature multi-model prediction function control method and device, and the method comprises the steps: constructing a transfer function model based on CARIMA description; defining a polynomial matrix, and determining a control increment of a conduction oil outlet temperature control system according to a conventional unrestraint generalized prediction control algorithm; adding the conduction oil inlet flow control increment constraint, control constraint and outlet conduction oil temperature constraint at a current moment t; carrying out the weighted connection calculation for controllers which are built according to the models, and obtaining an optimal conduction oil inlet flow control increment. The method is used for solving a problem that a conventional constrained prediction control method is difficult for engineering application and the solving of problems of large lag and nonlinearity of a conduction oil outlet temperature thermotechnical object of a heat collector, achieves the quick, stable and accurate tracking of a set value of the outlet conduction oil temperature, effectively reduces the fluctuation in a temperature adjustment process, and remarkably increases the response speed of temperature adjustment.
Owner:CHINA ELECTRIC POWER RES INST +2
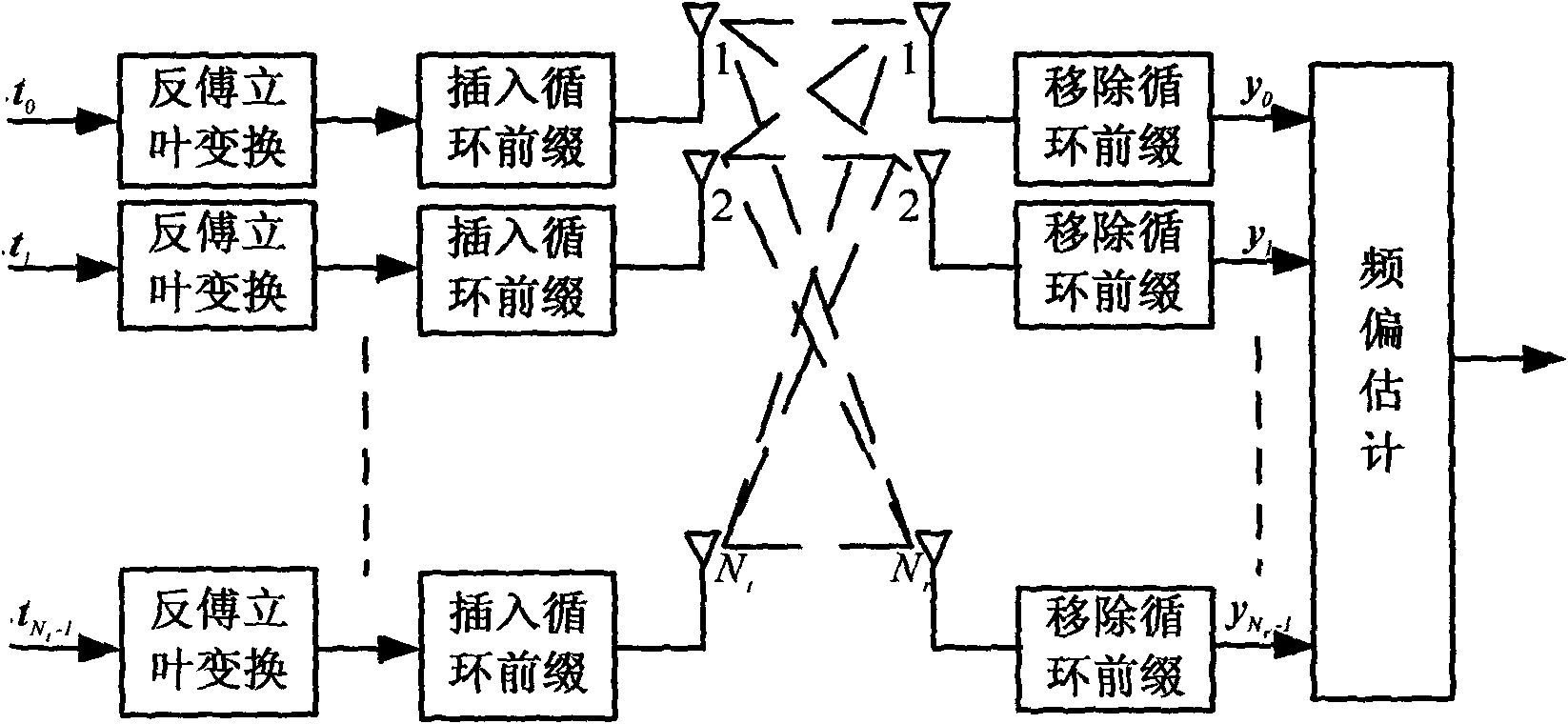
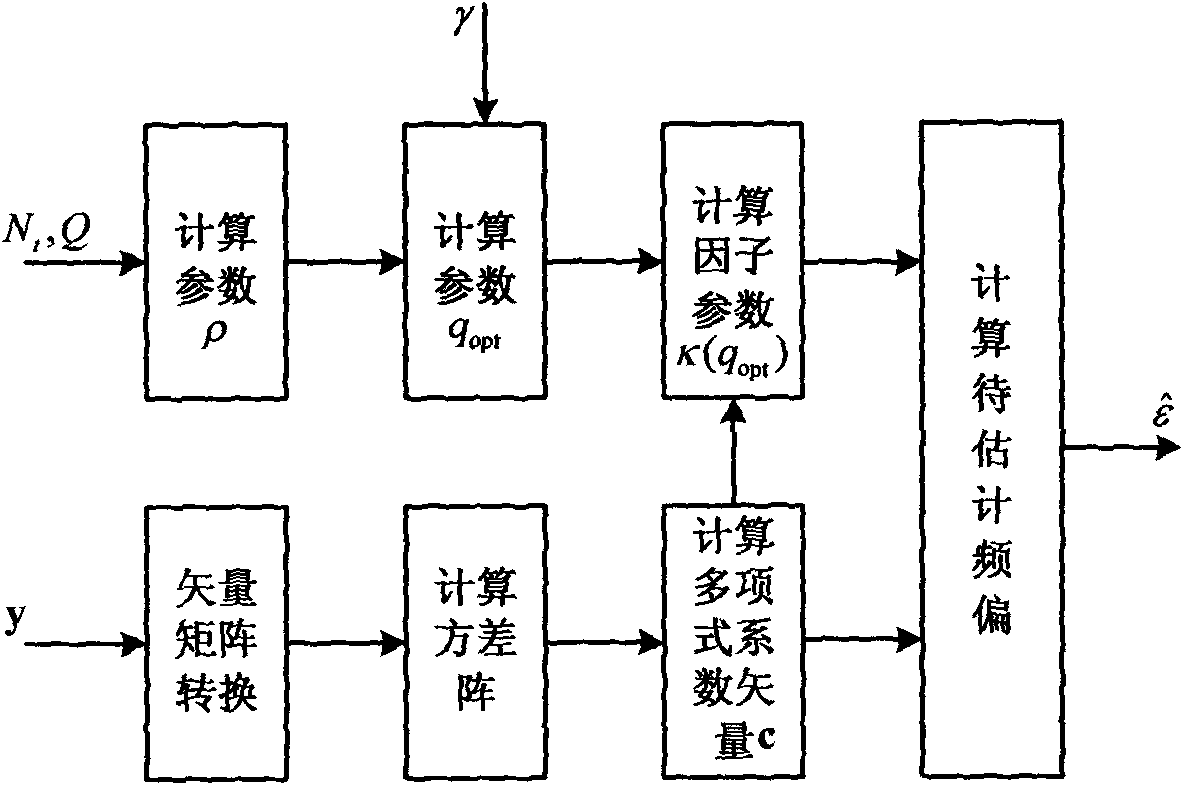
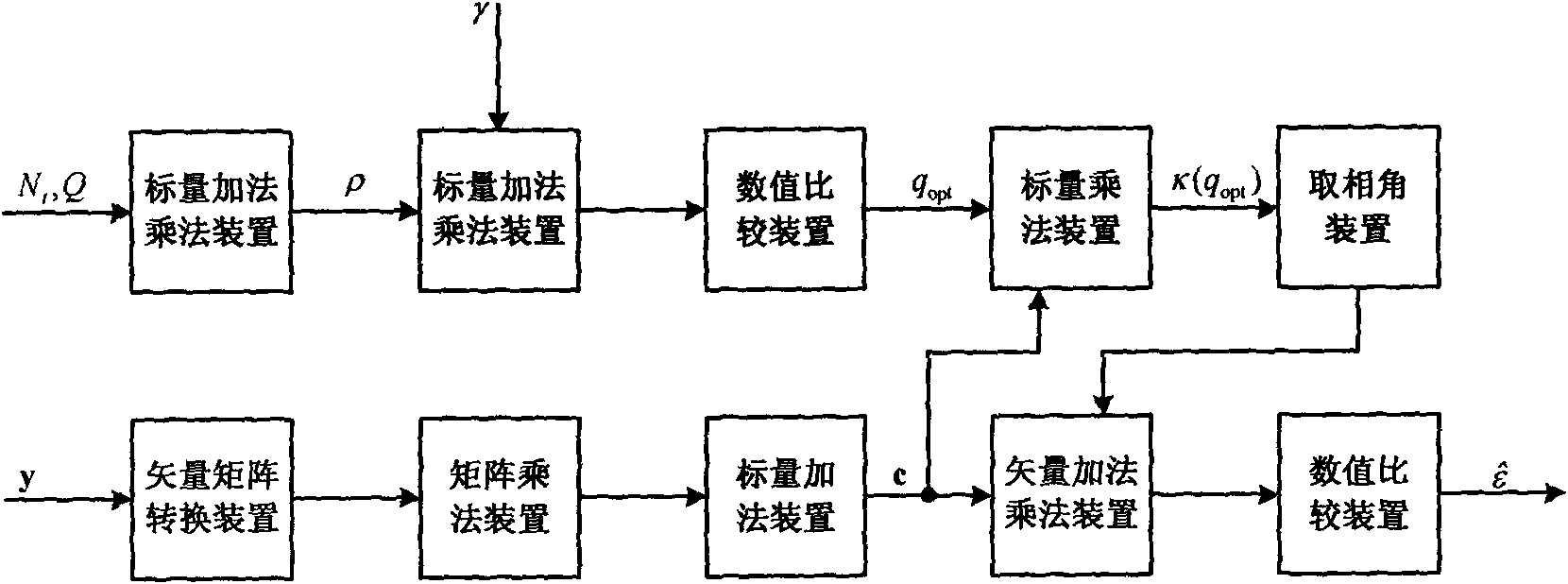
Environment self-adaptation frequency offset estimating method by simplifying polynomial factors
ActiveCN102111356AEasy to operateAvoid linear searchBaseband system detailsMulti-frequency code systemsMean squareEstimation methods
The invention provides an environment self-adaptation frequency offset estimation method by simplifying polynomial factors, which is characterized by comprising the following steps: according to the number Nt of transmitting antennas and a Q value, calculating a parameter rho related to mean square errors of frequency offset estimation, wherein Q=N / P>Nt; Q represents the gap between adjacent non-zero pilot frequencies in a training sequence on the transmitting antennas; N represents the length of the training sequence; P represents the length of a base training sequence; P is less than N and (N)2P is equal to 0; and (N)2P represents to carry out model 2P operation related to N. According to the method, the optimizations related to frequency offset estimation parameters can be realized in a self-adoption mode with the change of the environment, thus realizing the high-accuracy environment self-adoption frequency offset estimation.
Owner:白盒子(上海)微电子科技有限公司
Inverse discrete cosine transform lookup fast algorithm with variable complexity
ActiveCN102547263AAccurate removalReduce the number of multiplicationsTelevision systemsDigital video signal modificationFast algorithmDiscrete Fourier transform
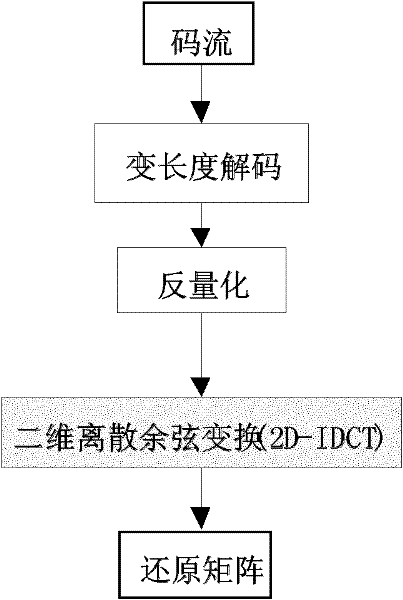
The invention discloses an inverse discrete cosine transform (IDCT) lookup fast algorithm with variable complexity, which mainly aims at reducing the redundant operation in the original acceleration IDCT algorithm and accelerating the computation speed of an IDCT module. The algorithm provided by the invention comprises the steps of decomposing an inverse quantized DCT (discrete cosine transform) coefficient matrix F into polynomial matrixes to add; performing inverse discrete cosine transform for each decomposed matrix; and finally, adding the inverse discrete cosine transformed matrixes to obtain an original matrix f. The algorithm disclosed by the invention reduces the redundant operation in the original algorithm and effectively accelerates the computation speed of the inverse discrete cosine transform.
Owner:LEADCORE TECH
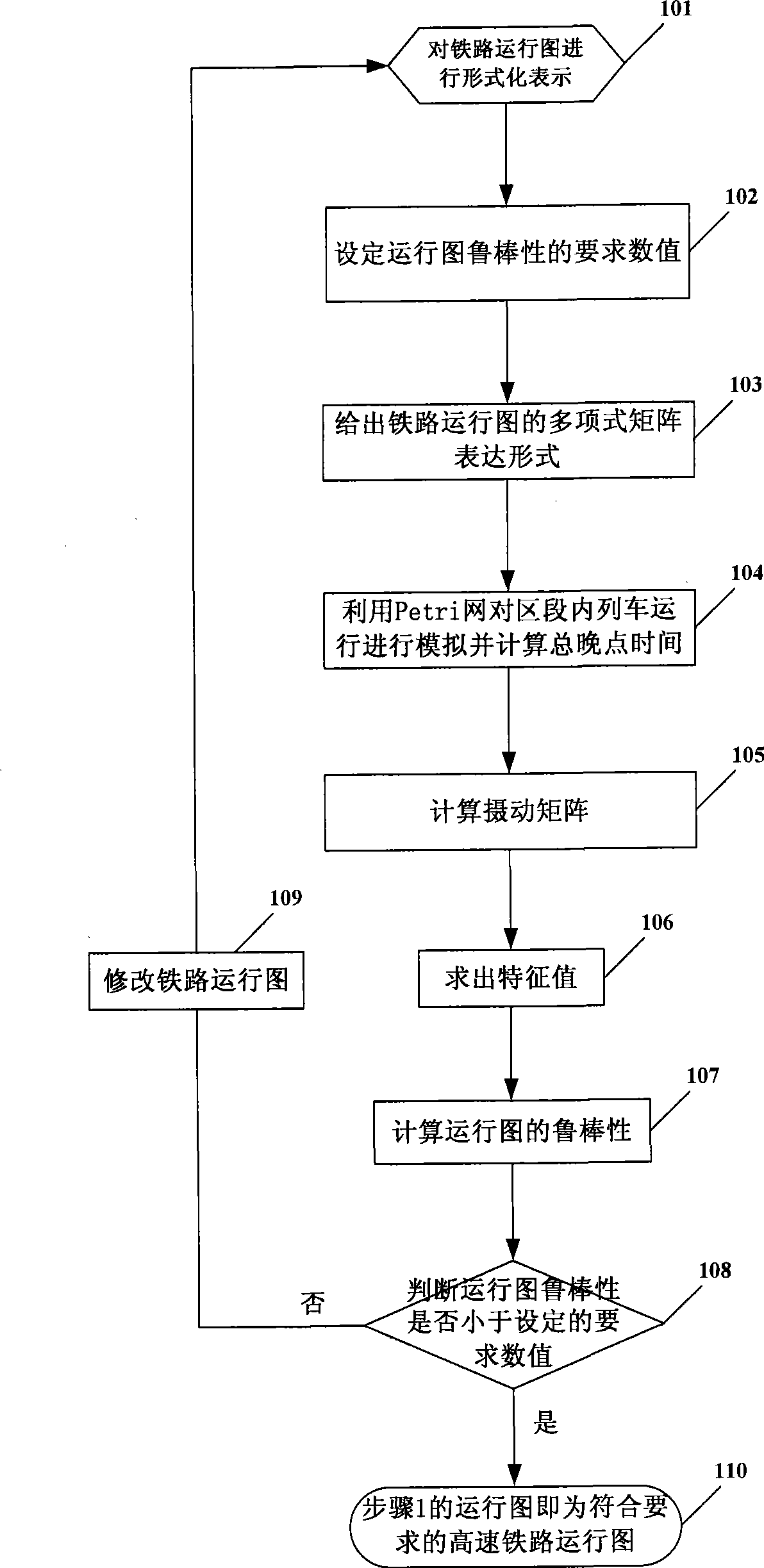
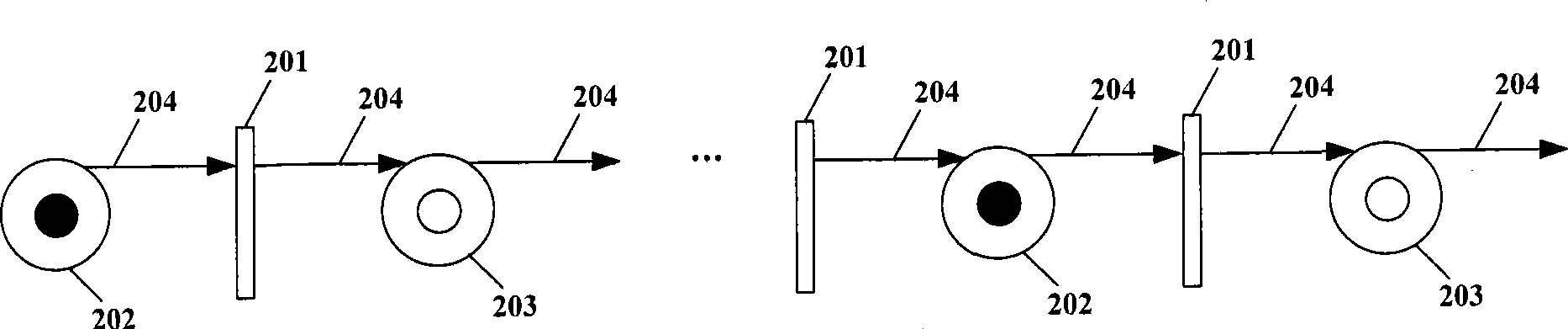
Method for improving high speed rail train operation right time rate by running chart robustness
InactiveCN101441680AImprove the punctuality rateBiological modelsSpecial data processing applicationsTotal delayComputer science
Owner:BEIJING JIAOTONG UNIV
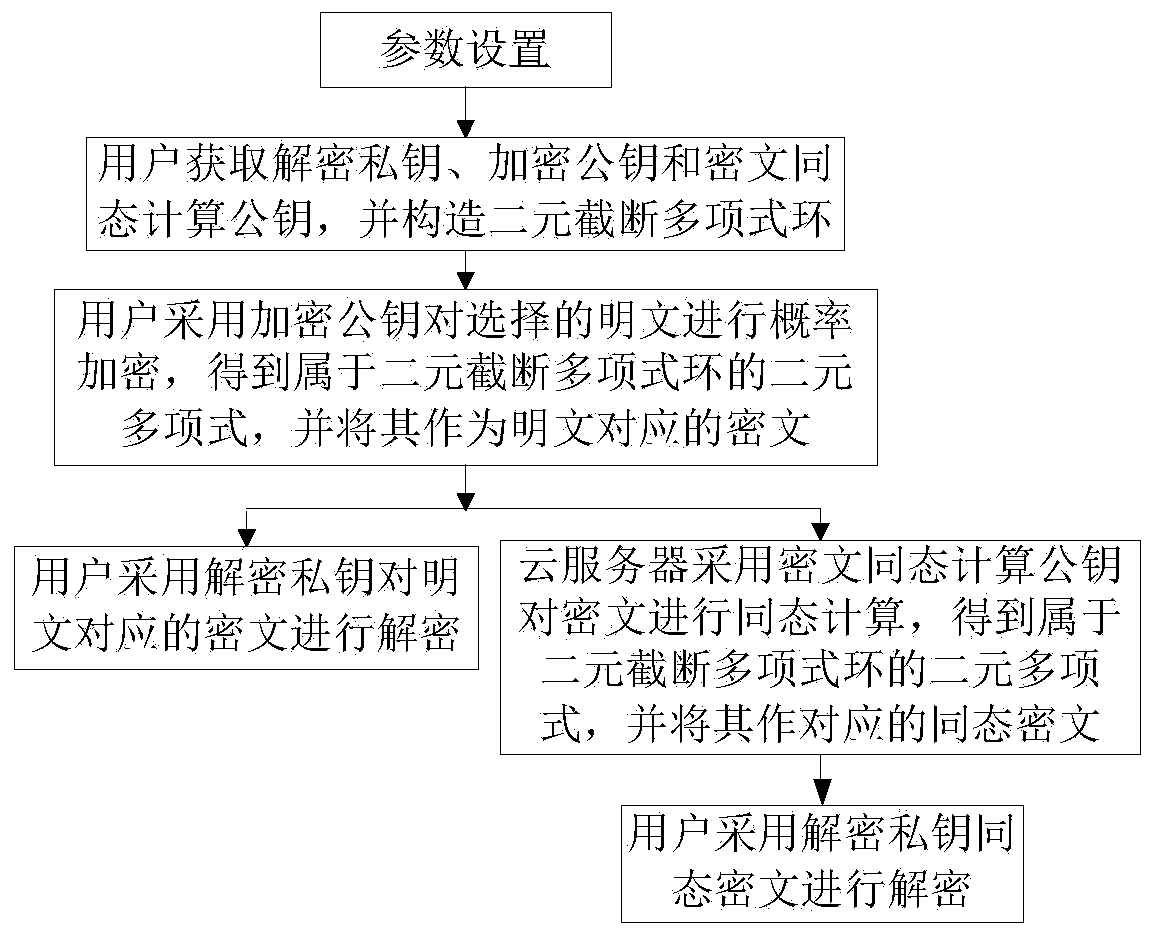
Noiseless fully homomorphic public key encryption method based on binary truncated polynomial ring
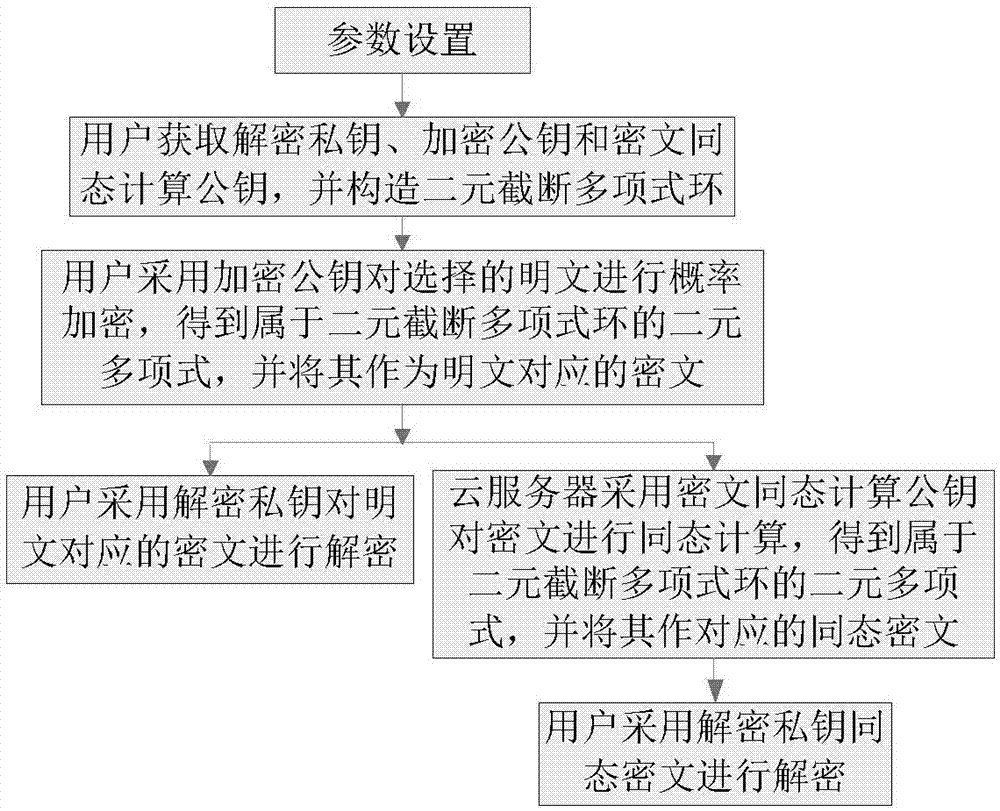
ActiveCN107317669AControl growthReduce storage spaceKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextProbabilistic encryption
The invention discloses a noiseless fully homomorphic public key encryption method based on a binary truncated polynomial ring and is used for solving the technical problem that in the prior art, keys and ciphertexts are too long and the ciphertext homomorphic computation efficiency is low. The method comprises the realization steps that a user sets parameters, obtaining a decryption private key, an encryption public key and a ciphertext homomorphic computation public key, establishes the binary truncated polynomial ring, carries out probability encryption on a plaintext through adoption of the encryption public key to obtain the ciphertext belonging to the binary truncated polynomial ring, and decrypts the ciphertext through adoption of the decryption private key to obtain the plaintext corresponding to the ciphertext; a cloud server carries out homomorphic computation on the ciphertext through adoption of the ciphertext homomorphic computation public key, thereby obtaining the homomorphic ciphertext belonging to the binary truncated polynomial ring; and the user decrypts the homomorphic ciphertext through adoption of the decryption private key, thereby obtaining a result obtained by carrying out the same computation on the corresponding ciphertexts. According to the method, the lengths of the ciphertexts and the keys are normal levels and the homomorphic computation efficiency is high.
Owner:XIDIAN UNIV
Parameterization BCH (broadcast channel) error-correcting code parallel encoding method and device
InactiveCN103401566AImprove encoding speedFast encodingCyclic codesBroadcast channelsTemporary variable
The invention discloses a parameterization BCH (broadcast channel) error-correcting code parallel encoding method and device. The method comprises the following steps of determining three variable parameters such as the error-correctable bits t, bit width p of the parallel encoding and length k of data information bit, solving a generation polynomial matrix, wherein the number of times of the generation polynomial matrix g(X) is (n-k); carrying out the logic operation for a temporary variable of a check bit and the generation polynomial matrix, and finally outputting a complete encoding module described through a verilog HDL (hardware description language) language. The generated encoding module is high in encoding speed and less in occupied resource. The encoding module utilizes one generation matrix to realize the parallel encoding function and is finally solved through a series of operation according to the generation polynomial of the BCH code. The method and the device are applicable to the application with long code word, high encoding speed and capability for continuously enhancing the error correcting capacity of the error-correcting code.
Owner:HOHAI UNIV
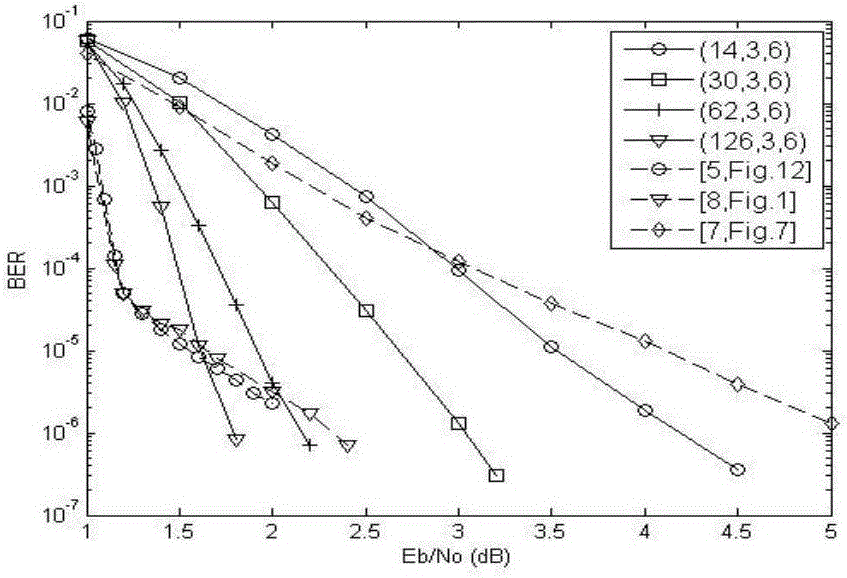
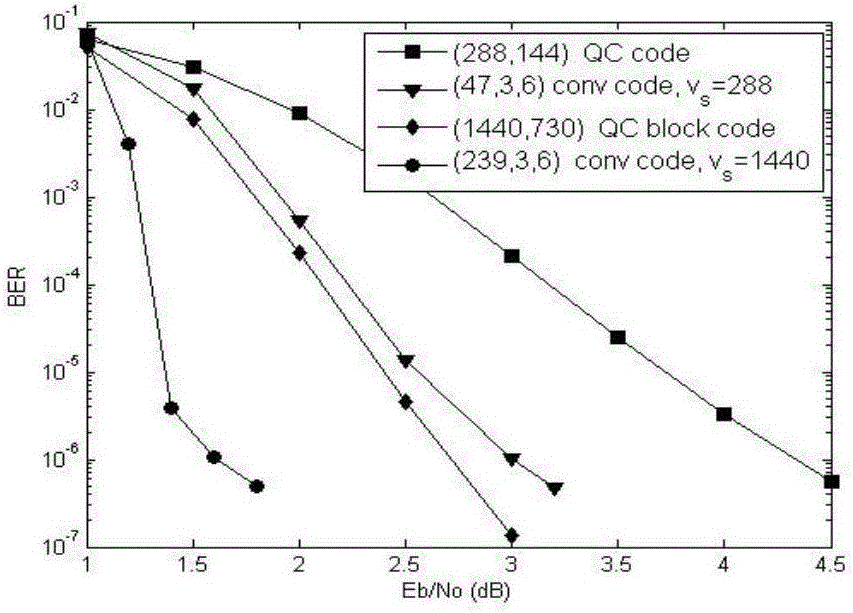
LDPC convolutional code construction method
InactiveCN105871385AAchieve fitQuick Coding FeaturesError correction/detection using multiple parity bitsCode conversionLdpc convolutional codesTheoretical computer science
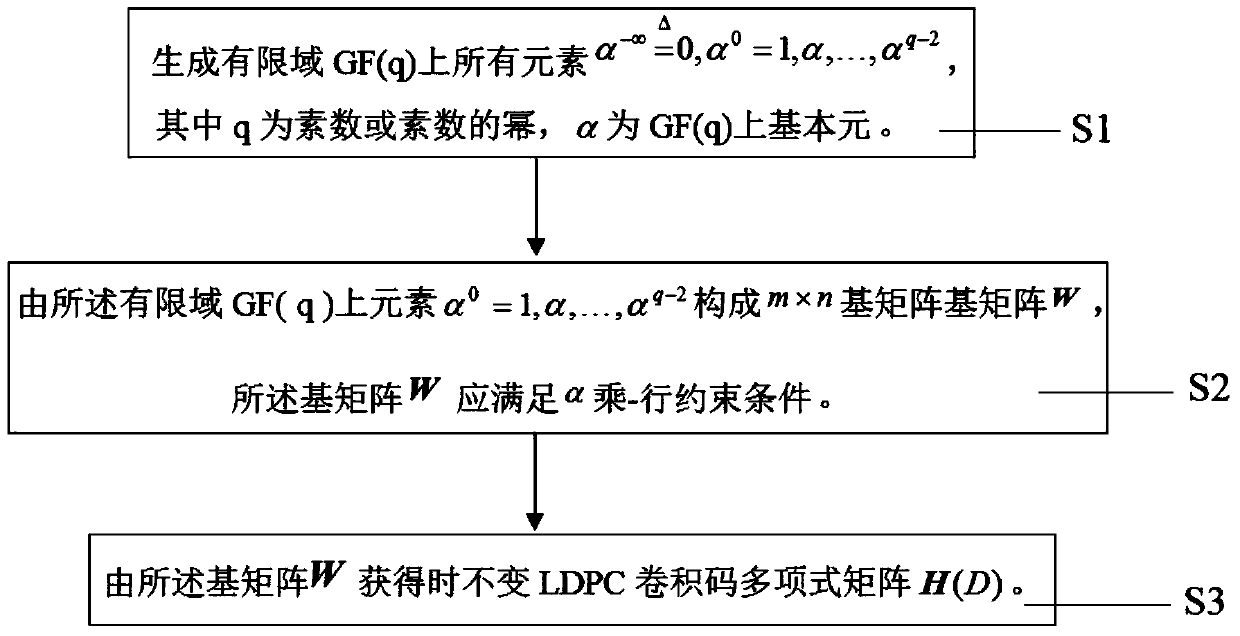
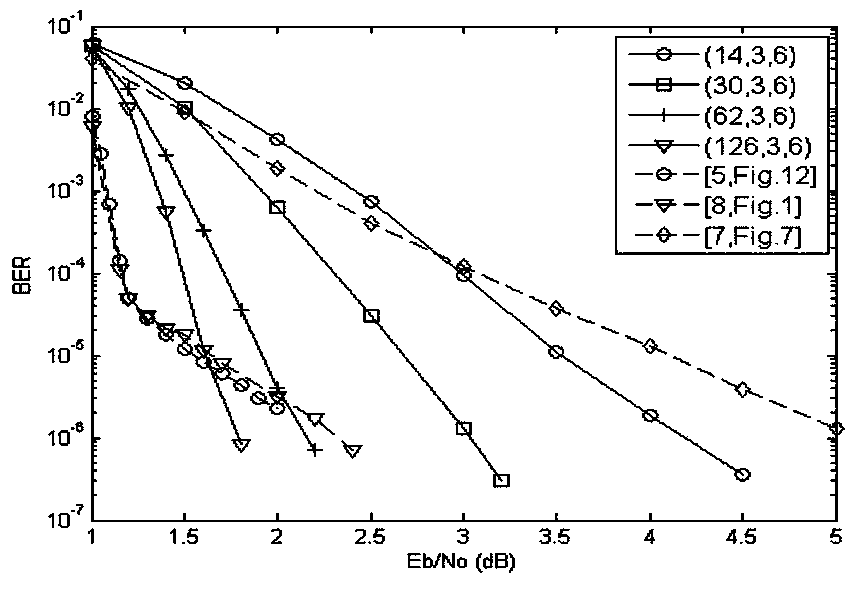
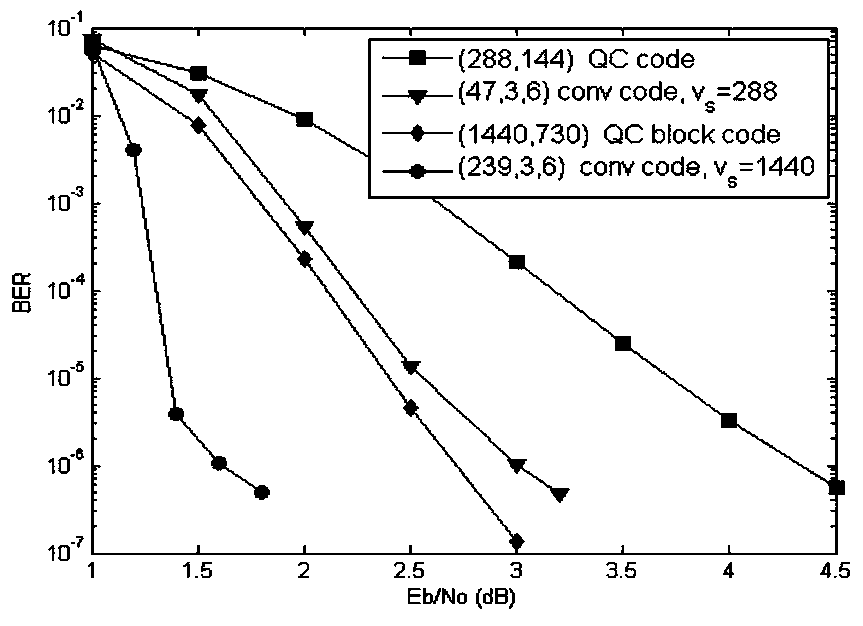
The invention relates to a LDPC convolutional code construction method, comprising the steps of generating all elements over a finite field GF(q), FORMULA, wherein q is an prime number or a power of the prime number, and alpha is a basic element over the GF(q); forming a m*n base matrix W by using the elements alpha<0> = 1, alpha, ..., alpha<q-2> of the finite field GF(q); and obtaining a time-invariant LDPC convolutional code polynomial matrix H(D) via the base matrix W. Compared with the existing skills, the LDPC convolutional code construction method provided by the invention has the characteristic of rapid coding, can obtain the code with the maximal achievable code memory, and has the lower error floor and good coding performance under the small constraint length.
Owner:SOUTH CHINA NORMAL UNIVERSITY
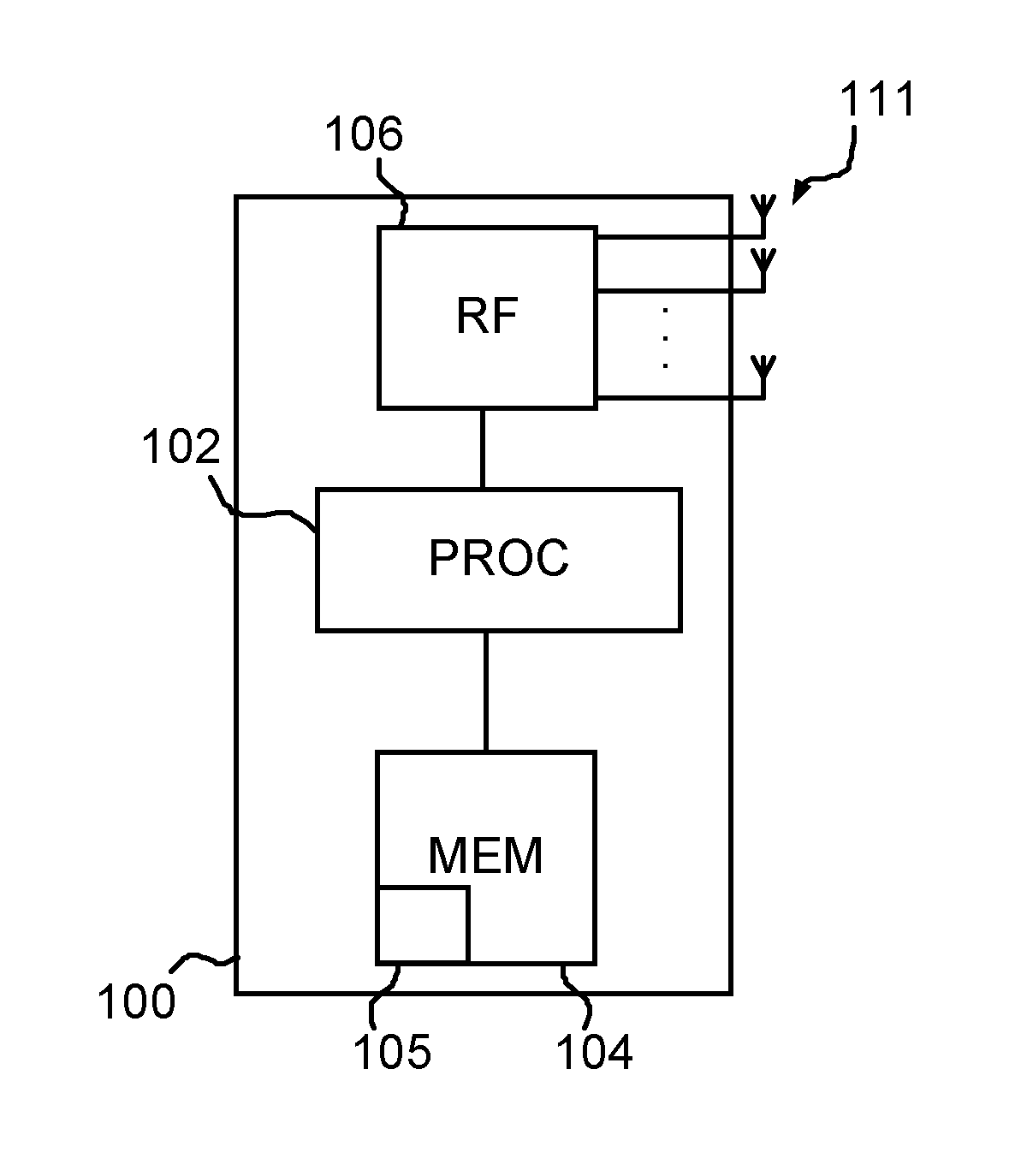
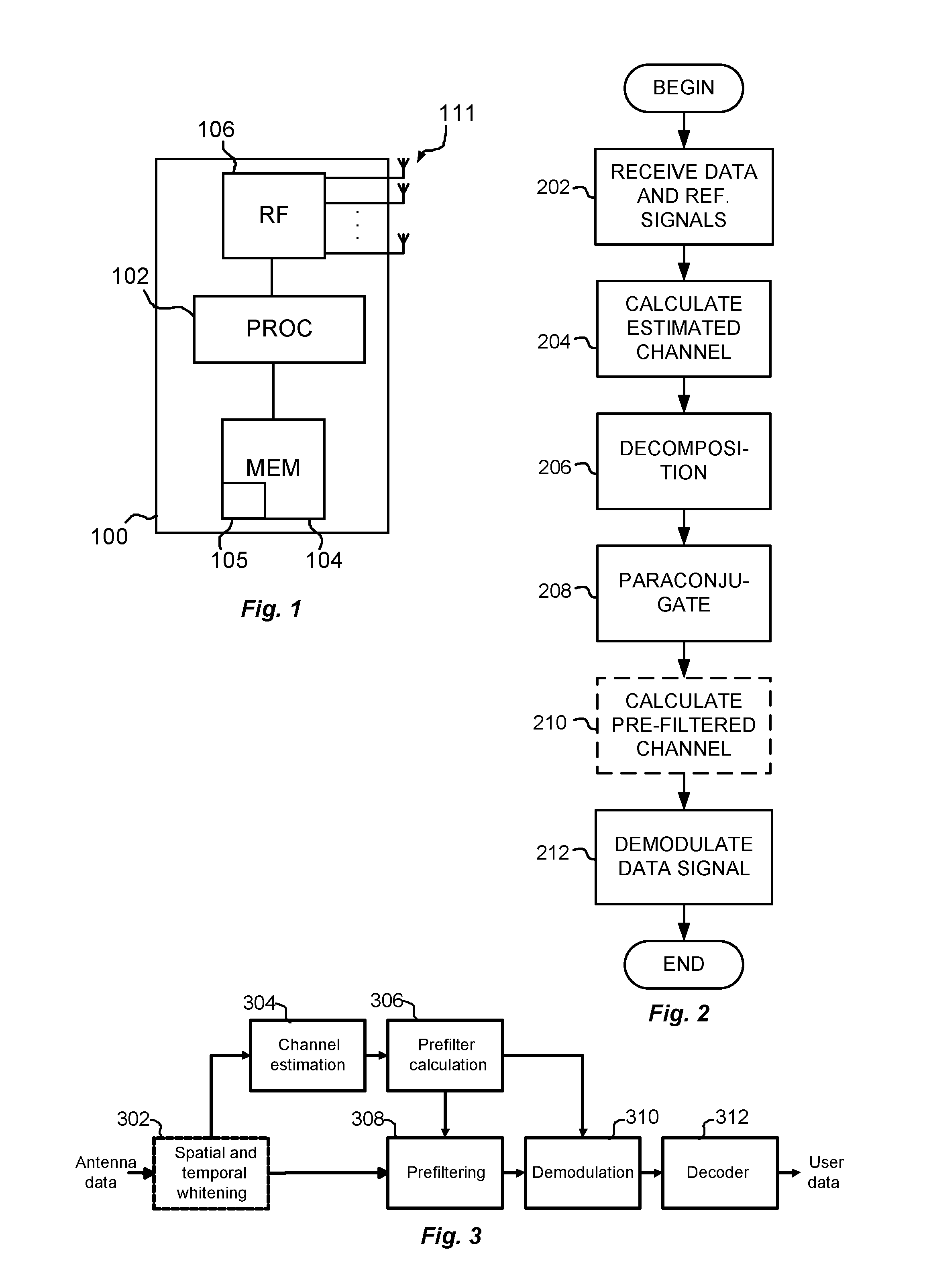
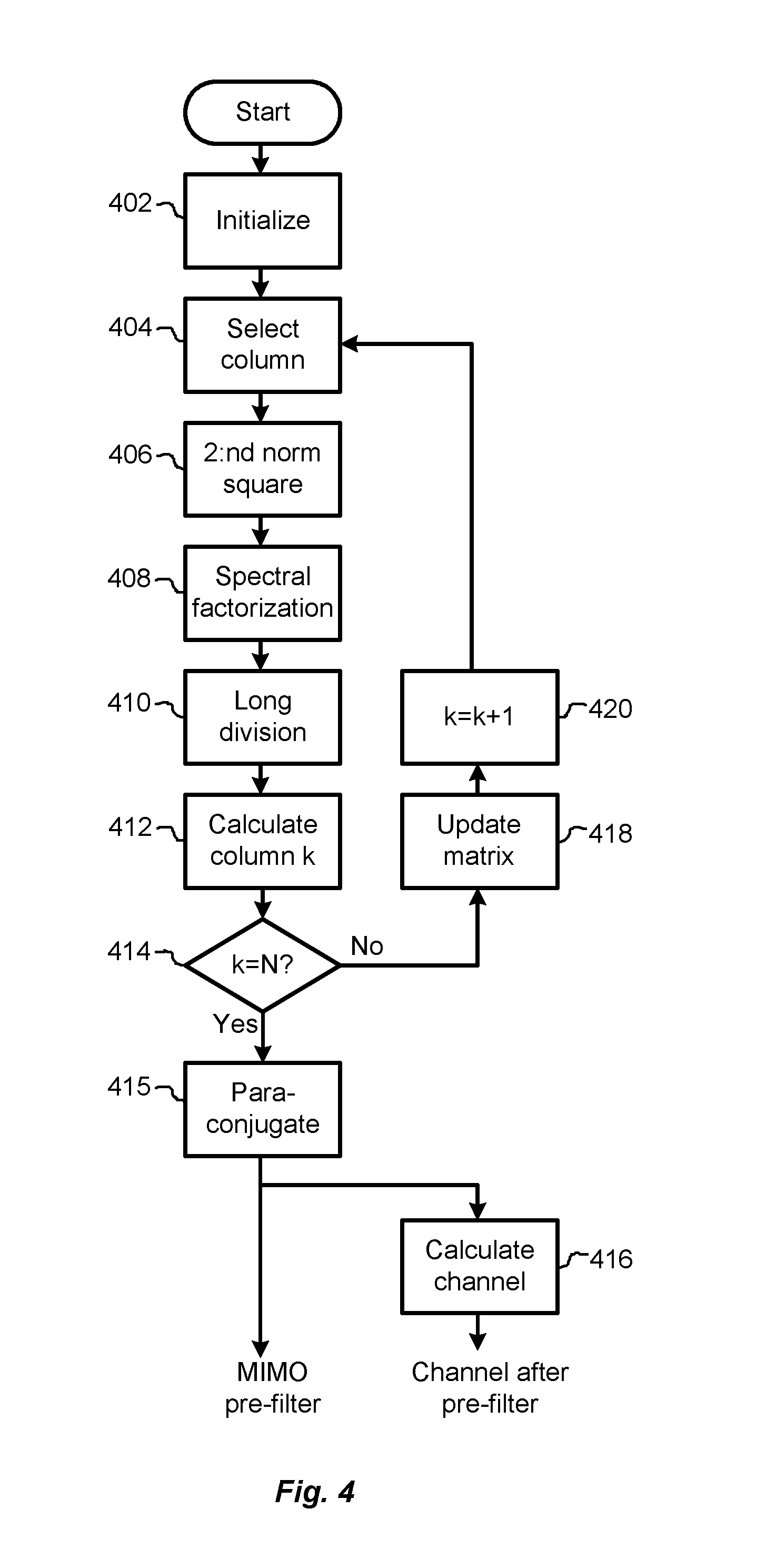
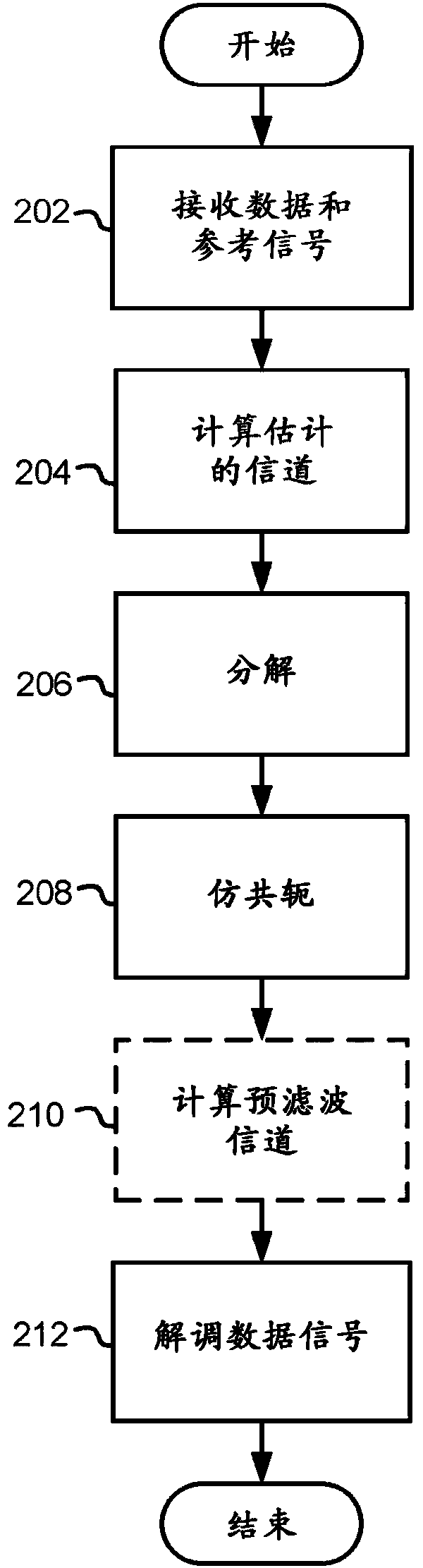
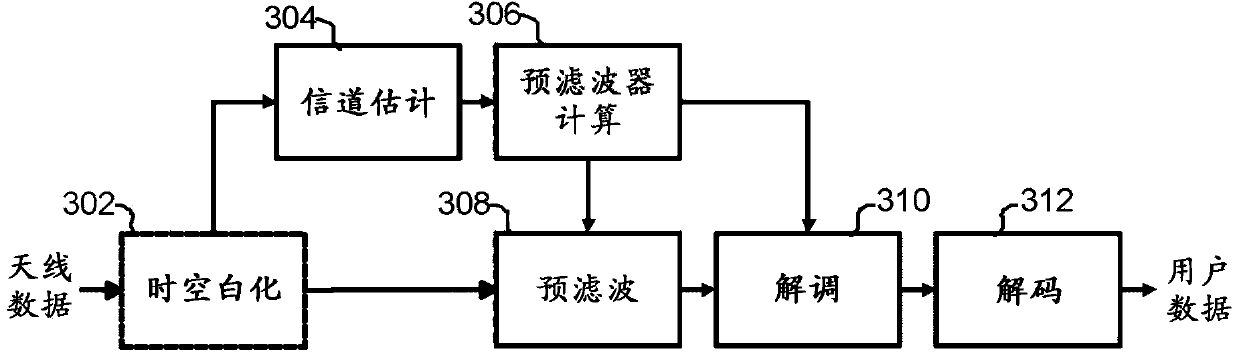
Prefiltering in mimo receiver
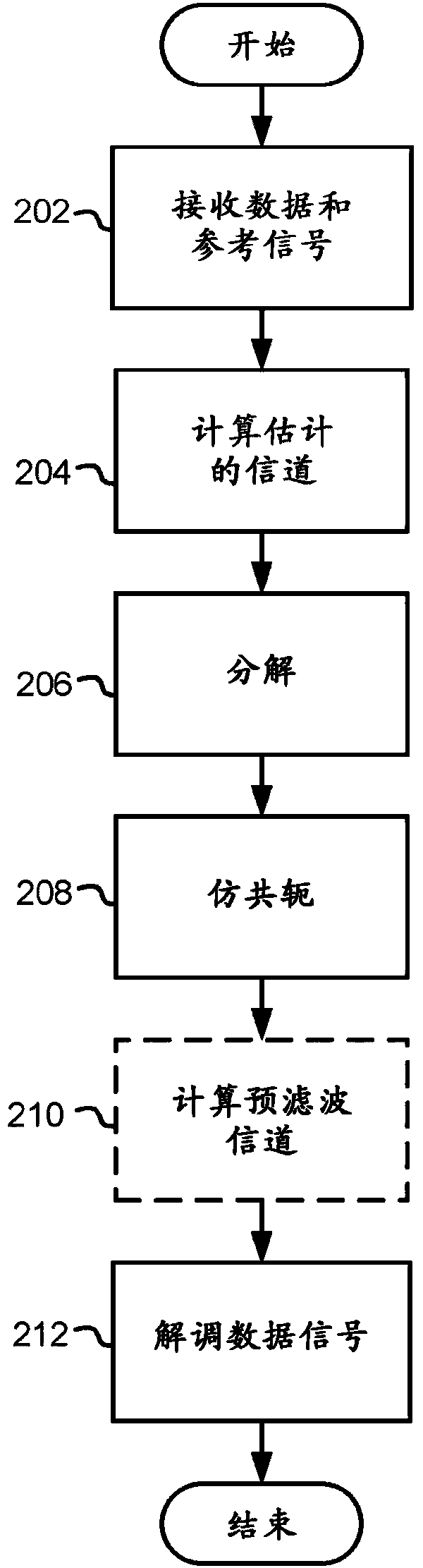
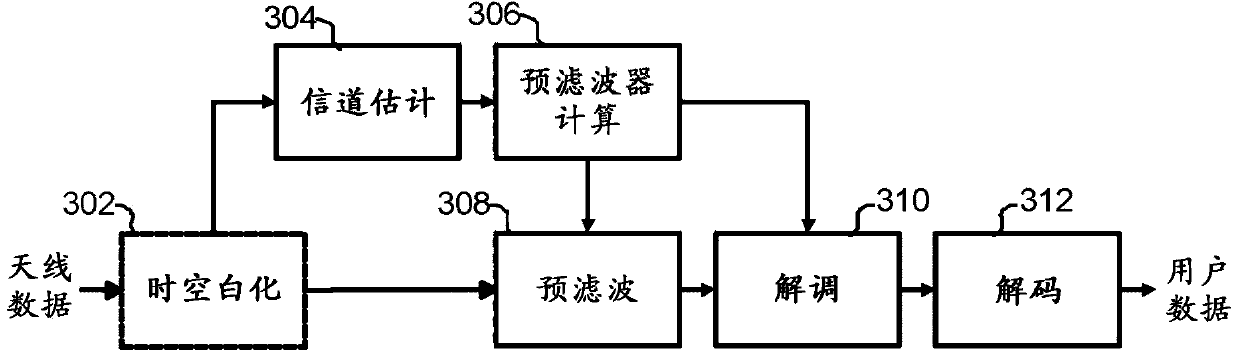
Data signals transmitted by a plurality of transmitting antennas over a radio channel are demodulated. The method comprises receiving (202) on a plurality of receiving antennas, a data signal and a reference signal, the contents of the reference signal being known a priori to the receiver. The contents of the reference signal are used for calculating (204) an estimated polynomial channel matrix. A polynomial pre-filter matrix is calculated (206, 208) by a decomposition of the estimated polynomial channel matrix into a product of a paraunitary polynomial matrix and an upper triangular polynomial matrix with minimum phase filters on its main diagonal, where the polynomial pre-filter matrix is obtained by calculating the paraconjugate of the paraunitary polynomial matrix. The received data signal is demodulated (212) where the received data signal is multiplied with the calculated polynomial pre-filter matrix.
Owner:TELEFON AB LM ERICSSON (PUBL)
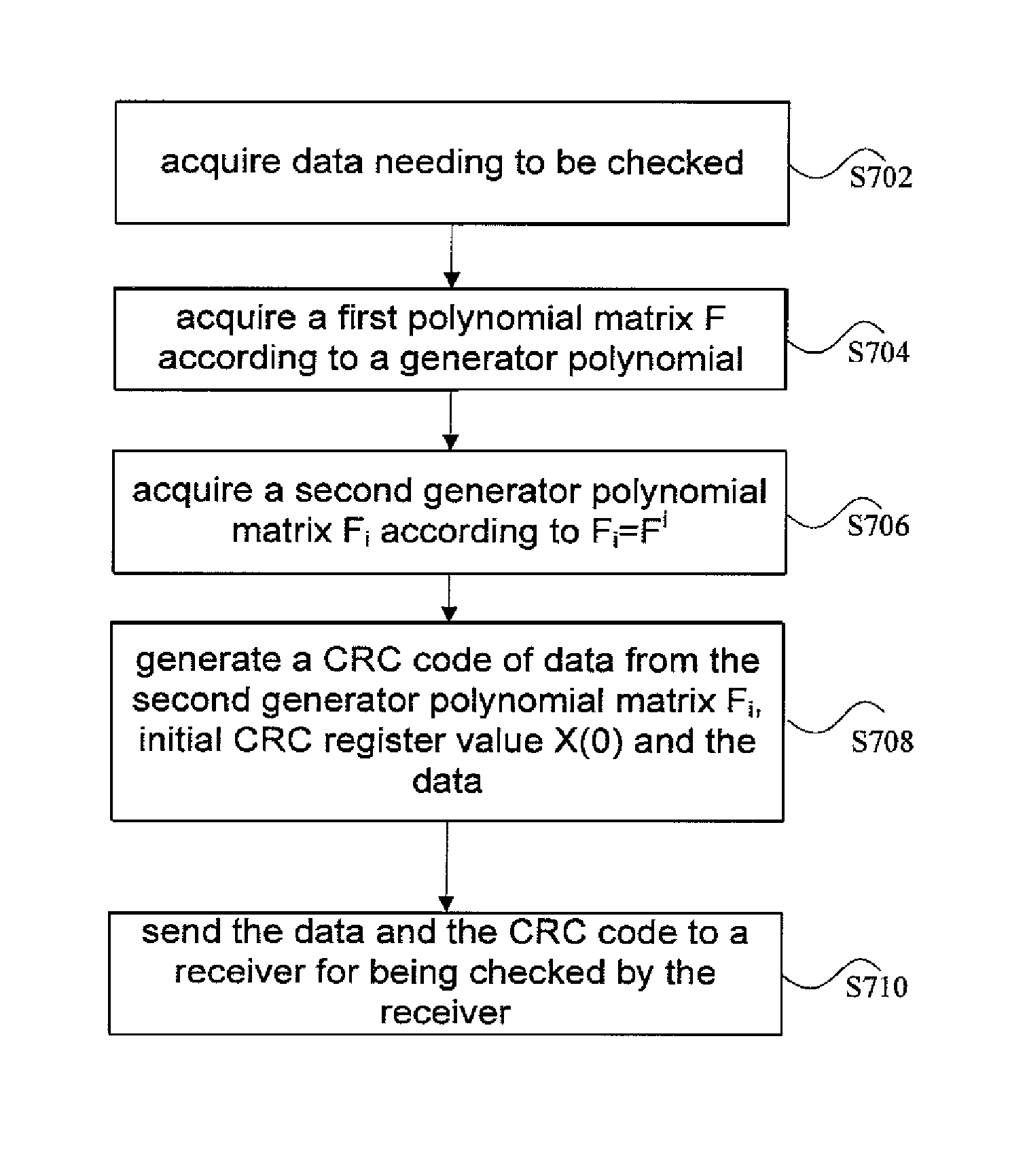
Method and apparatus for data check processing
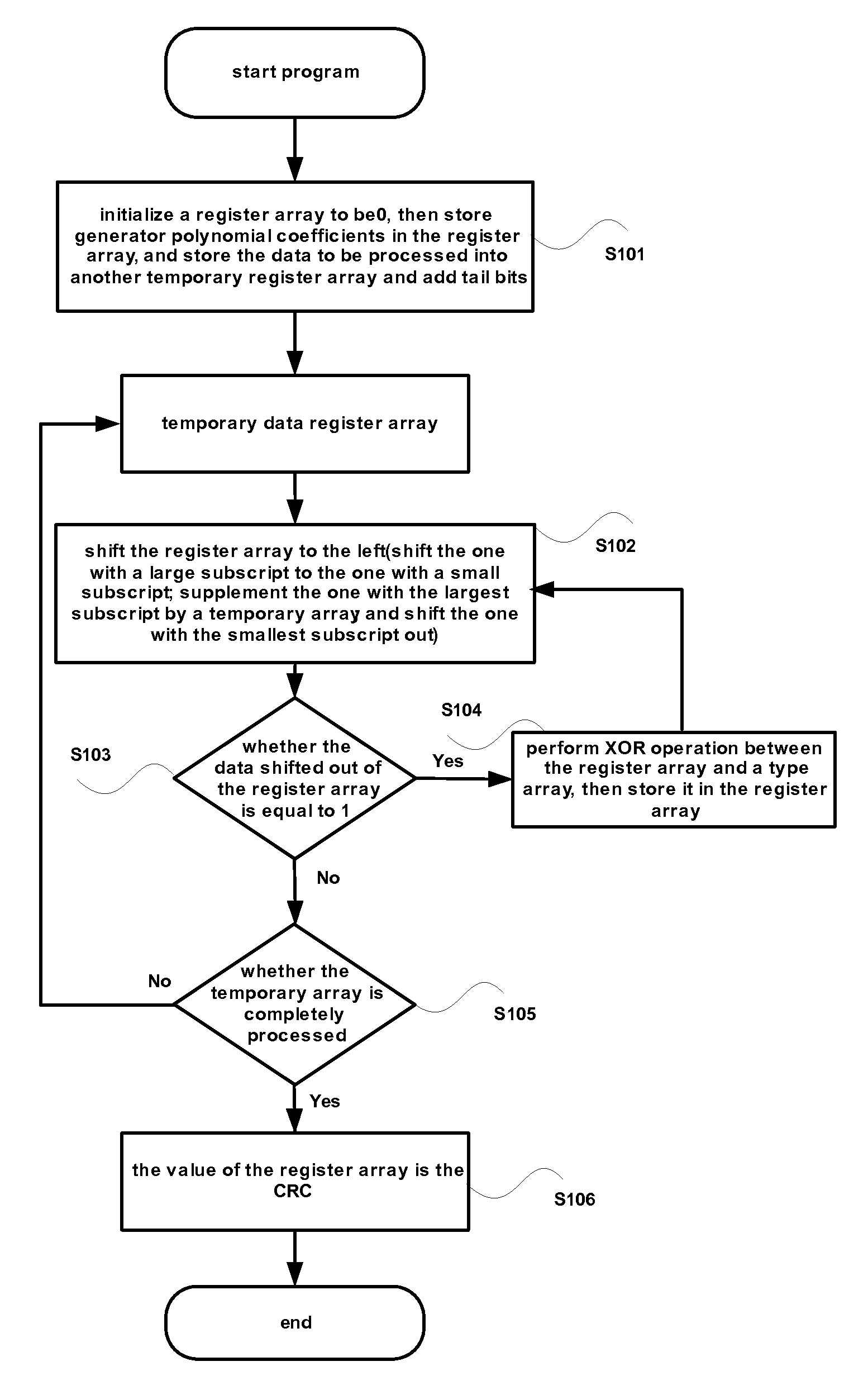
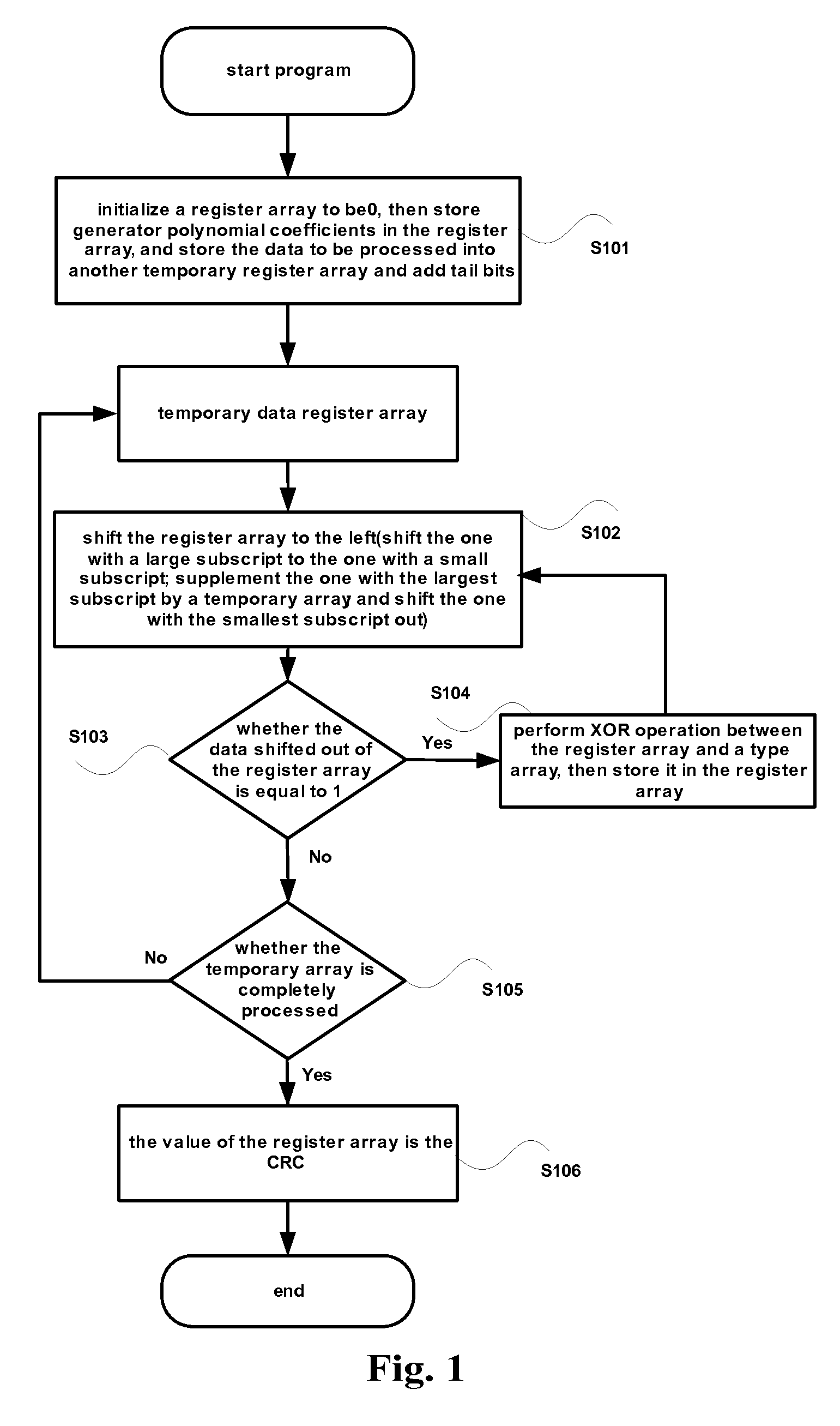
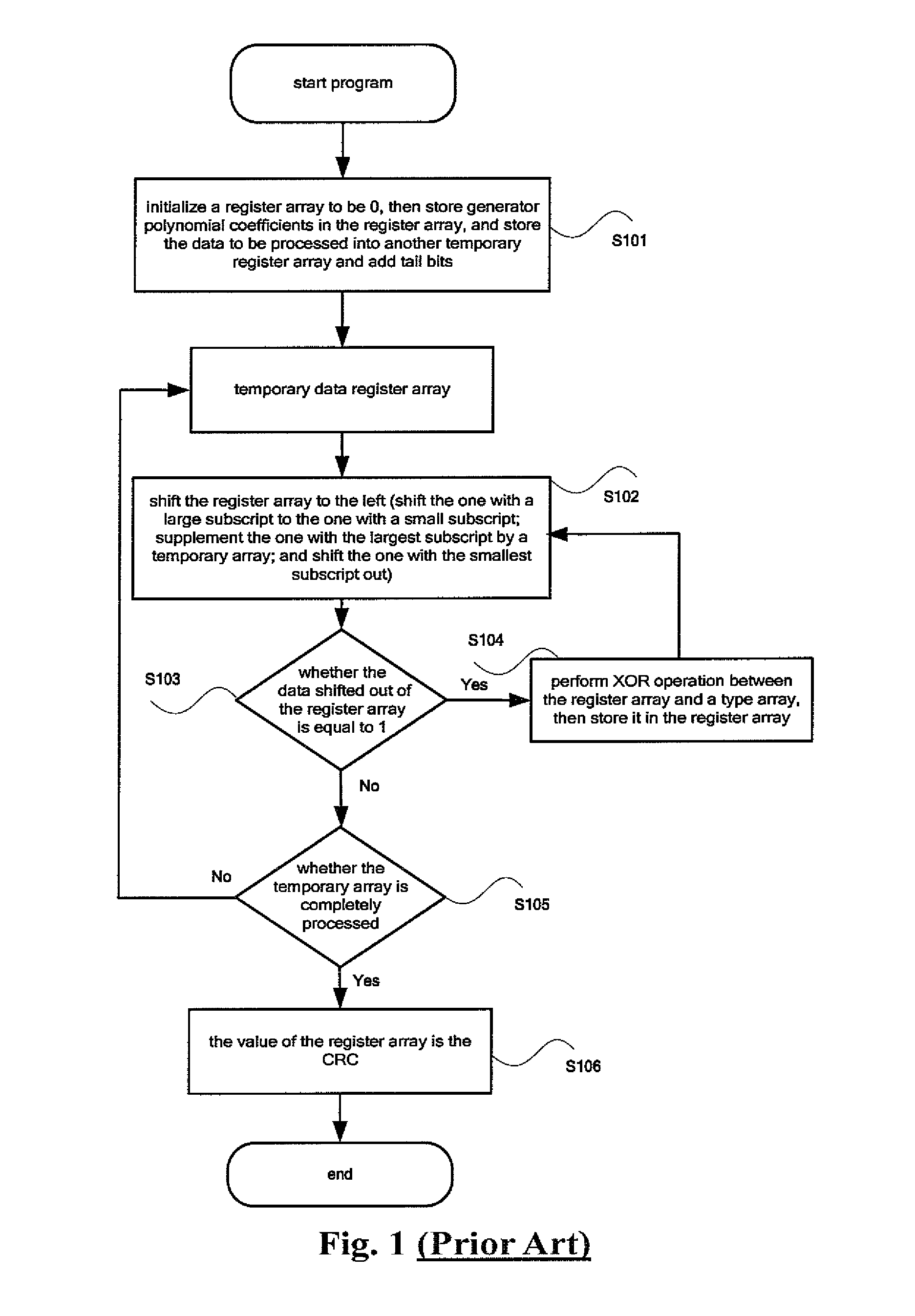
InactiveUS20120317466A1Easy loadingReduce loadError preventionCode conversionProcessor registerData needs
The invention discloses a method and an apparatus for data check processing, the method comprises: acquiring data to be checked; acquiring a first polynomial matrix F according to a generator polynomial; acquiring a second generator polynomial matrix Fi according to Fi=Fi, wherein i is the digit of the data; generating a CRC code of the data from the second generator polynomial matrix Fi, initial CRC register value X(0) and the data; and sending the data and the CRC code to a receiver for being checked by the receiver. Through the present invention, the problem that the load of registers is increased when the number of digits of the data needing to be checked is not the nth power of 2 in the conventional art is solved, and the effect of reducing the load of registers is achieved.
Owner:ZTE CORP
configurable parallel BCH error correction coding method
InactiveCN109756235AAchieve outputReduce time consumptionCyclic codesComputer hardwareError correction coding
The invention relates to a configurable parallel BCH error correction coding method, and the method comprises the steps: determining the coding configuration: an information bit k, a check bit r, a code word length n, an error correction bit t, and a primitive polynomial f (x); Calculating parameters: generating a polynomial g (x); Generating a polynomial matrix Tg, and verifying the calculation matrix Tg (p-1); Generating and calculating processing circuit. Performing coding calculation, including: inputting information bit data in parallel; Calculating check bit data; And judging whether theinput is finished or not, if so, outputting information bit data M (x), and if not, outputting check bit data S (x). According to the coding method, parallel input and output of data are realized, the time consumption of the processing flow is reduced in equal proportion, and the coding processing efficiency is remarkably improved.
Owner:TIANJIN JINHANG COMP TECH RES INST
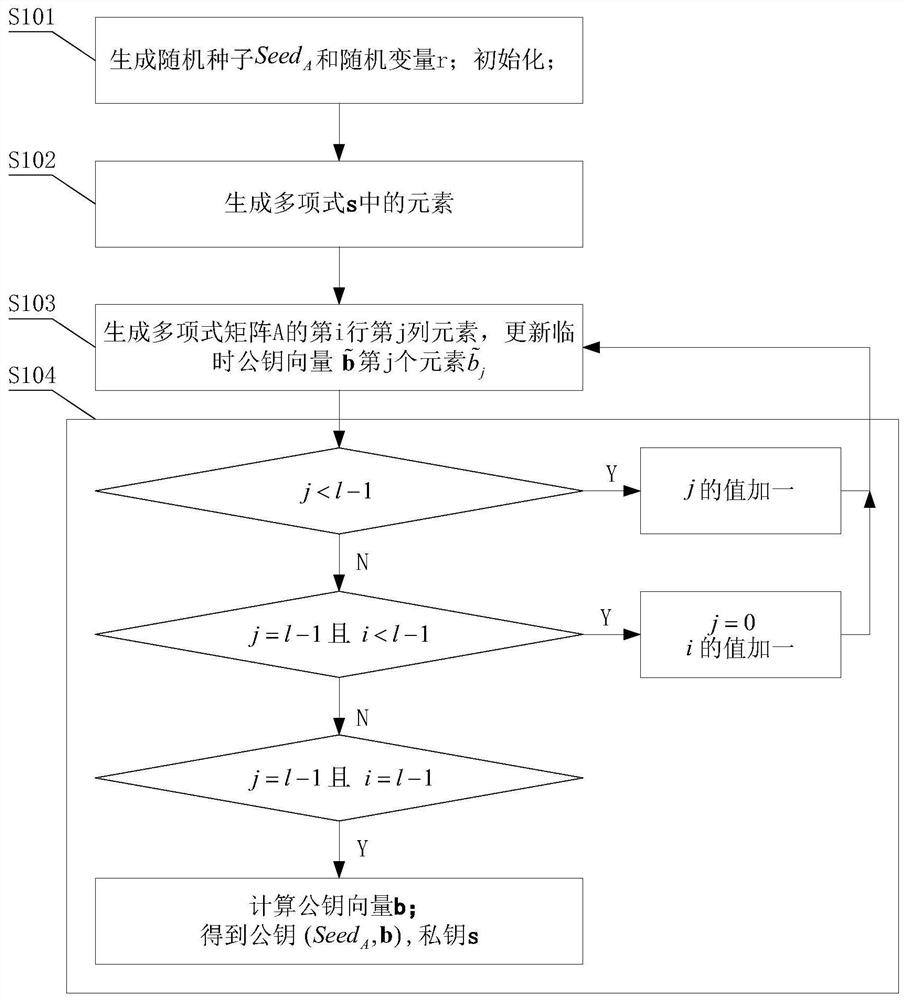
Low-memory-occupancy implementation technology based on post quantum cryptography Saber algorithm
ActiveCN113472525AReduce memory usageReduce the difficulty of deploymentKey distribution for secure communicationKey (cryptography)Algorithm
The invention discloses a low-memory-occupancy implementation technology based on a post quantum cryptography Saber algorithm. The low-memory-occupancy implementation technology comprises a key generation method and system, an encryption method and system and a decryption method and system. The vector multiplication of the polynomial matrix is calculated by adopting the immediate generation of the matrix, and the memory space occupied by the polynomial matrix is reduced to the memory size occupied by a single element, so that the memory occupation of the Saber scheme is remarkably reduced, and the deployment of the Saber scheme in the Internet of Things equipment is facilitated.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and apparatus for performing a CRC check
InactiveUS8843810B2Easy loadingReduce loadError preventionCode conversionComputer hardwarePolynomial matrix
The invention discloses a method and an apparatus for data check processing, the method comprises: acquiring data to be checked; acquiring a first polynomial matrix F according to a generator polynomial; acquiring a second generator polynomial matrix Fi according to Fi=Fi, wherein i is the digit of the data; generating a CRC code of the data from the second generator polynomial matrix Fi, initial CRC register value X(0) and the data; and sending the data and the CRC code to a receiver for being checked by the receiver.
Owner:ZTE CORP
LDPC encoding method and device for communication signal
ActiveCN109951250AError preventionError correction/detection using multiple parity bitsAlgorithmColumn vector
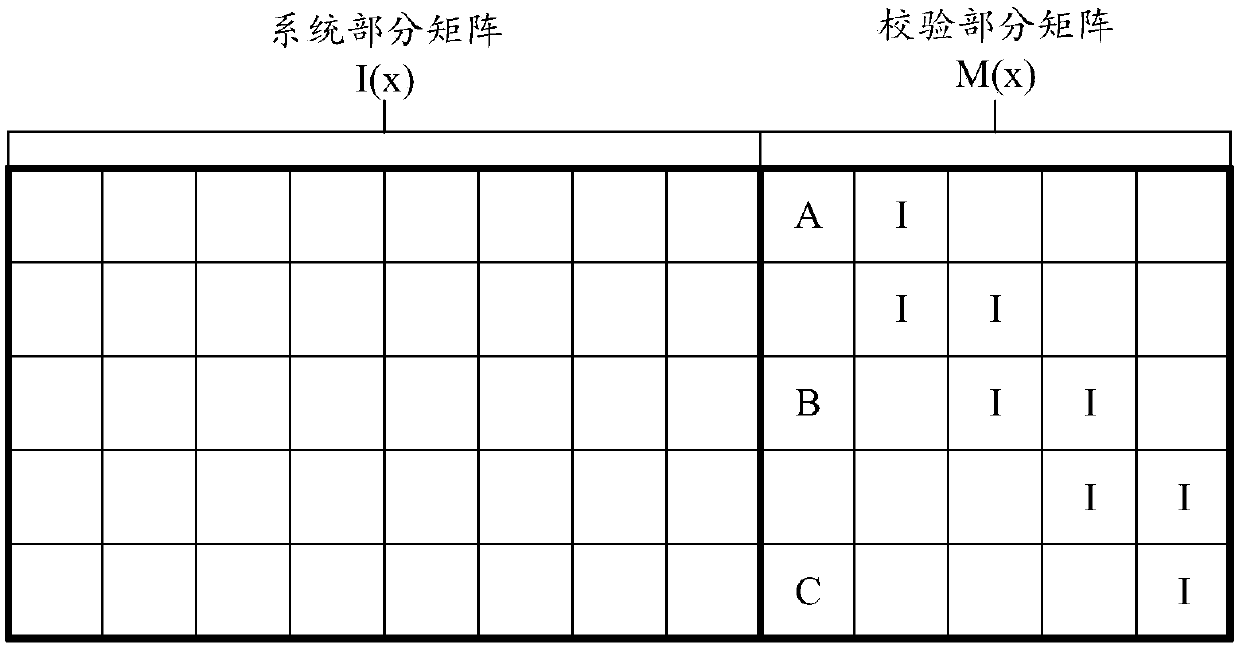
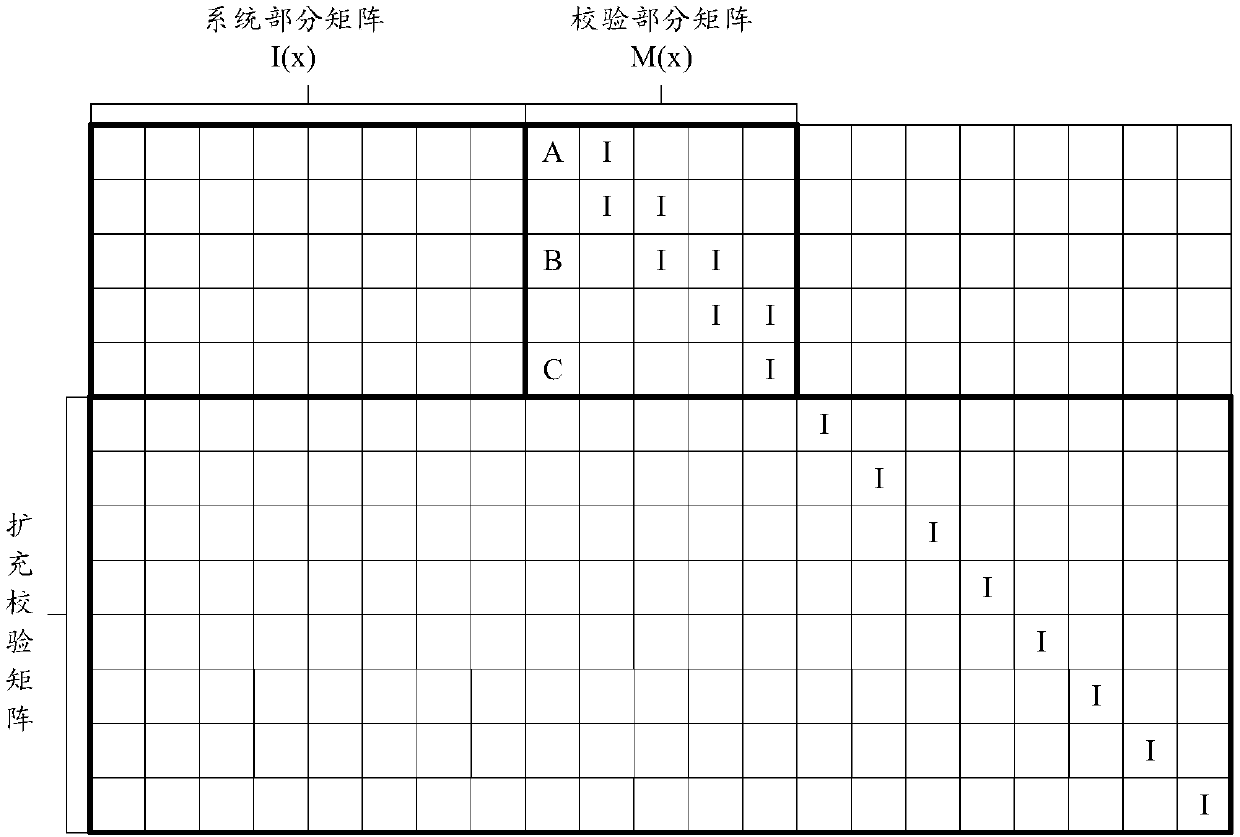
The invention provides an LDPC encoding method and device for a communication signal, which can reduce the coding complexity. The encoding method comprises the following steps: acquiring a (N-M) * 1 information bit vector I (x) according to information bits of a communication signal to be sent; obtaining a check set vector D (x) according to the I (x) and the M * (N-M) system partial matrix N (x),the D (x) satisfying the following conditions: D (x) = {N (x) I (x)} mod2; determining an M * M check part matrix M (x), the M (x) being a bidiagonal matrix, a polynomial matrix Q (x) corresponding to a first column vector of the M (x) being expressed as Q (x) = I + xah + xbh, and Q-1 (x)=x-2 *[beta]* hQ (x), a and b are constants different from each other, and h = 2j-1, wherein [beta] is a positive integer, and j is a positive integer; determining a check bit vector C (x) corresponding to the I (x) according to the D (x) and the M (x), the C (x) satisfying the following conditions: D (x) = {M (x) C (x)} mod2; and according to the I (x) and the C (x), generating a coding code word corresponding to the to-be-sent communication signal.
Owner:HUAWEI TECH CO LTD
Parallel low and asymmetric rate Reed Solomon coding
ActiveUS9032277B1Error preventionTransmission systemsSymbol of a differential operatorComputer science
Owner:ALTERA CORP
Automatic color correction matrix algorithm based on the least square method
ActiveCN107846532ASolve the accuracy problemSolve the errorColor signal processing circuitsColor correctionErrors and residuals
The invention provides an automatic color correction matrix algorithm based on the least square method. The algorithm performs sampling statistics on two images with differences, outputs respective standard color correction matrixes, and fits a polynomial matrix satisfying the difference of sensors according to the basic principle of the least square method. The problem of visual error caused by insufficient precision of the sensor, the optical filter, the lens and other hardware, and such factors as sensitometric curve discreteness is solved.
Owner:TIANJIN TIANDY DIGITAL TECH
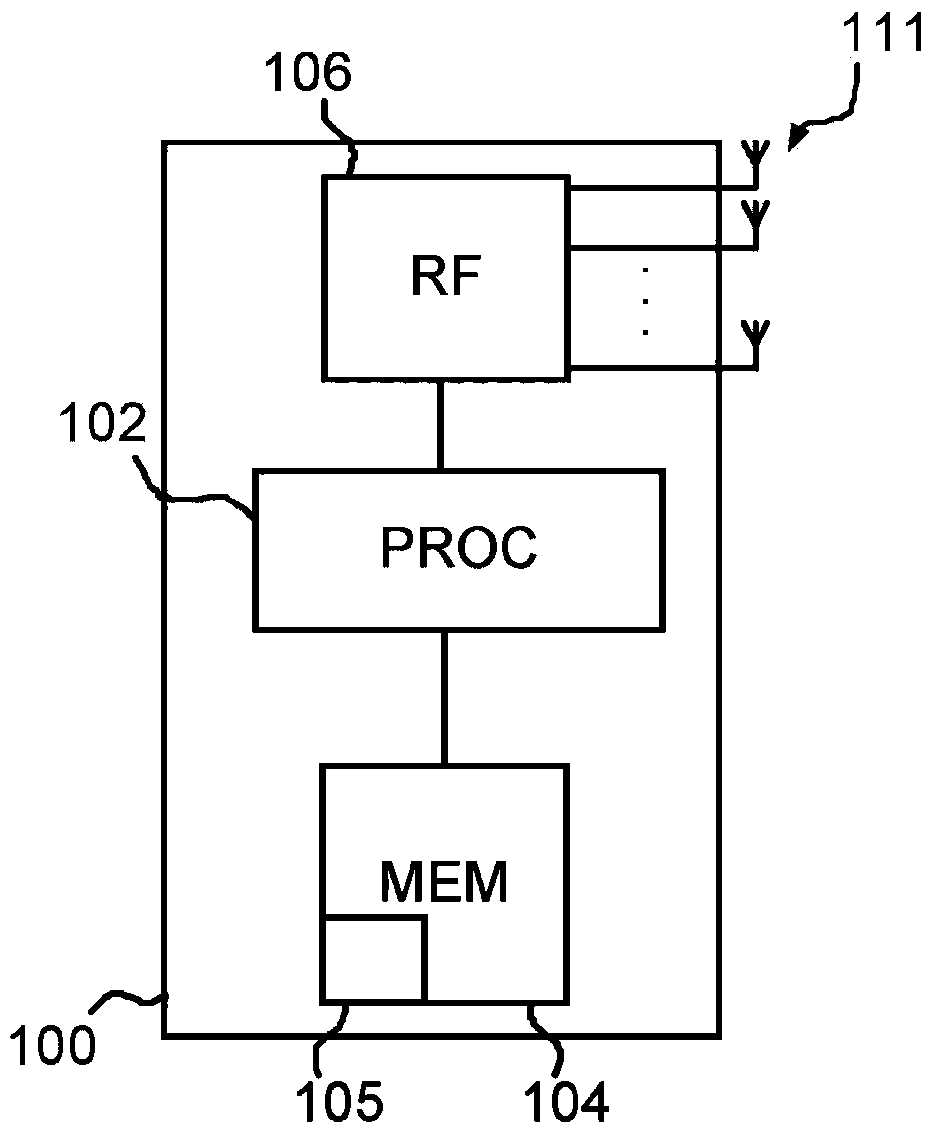
Prefiltering in MIMO Receiver
ActiveUS20150303970A1Reduce complexityReduce computational complexitySpatial transmit diversityAmplitude-modulated carrier systemsMatrix decompositionMain diagonal
Data signals transmitted by a plurality of transmitting antennas over a radio channel are demodulated. The method comprises receiving (202) on a plurality of receiving antennas, a data signal and a reference signal, the contents of the reference signal being known a priori to the receiver. The contents of the reference signal are used for calculating (204) an estimated polynomial channel matrix. A polynomial pre-filter matrix is calculated (206, 208) by a decomposition of the estimated polynomial channel matrix into a product of a paraunitary polynomial matrix and an upper triangular polynomial matrix with minimum phase filters on its main diagonal, where the polynomial pre-filter matrix is obtained by calculating the paraconjugate of the paraunitary polynomial matrix. The received data signal is demodulated (212) where the received data signal is multiplied with the calculated polynomial pre-filter matrix.
Owner:TELEFON AB LM ERICSSON (PUBL)
Noiseless Fully Homomorphic Public Key Encryption Method Based on Binary Truncated Polynomial Ring
ActiveCN107317669BControl growthReduce storage spaceKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextProbabilistic encryption
The invention discloses a noiseless fully homomorphic public key encryption method based on a binary truncated polynomial ring and is used for solving the technical problem that in the prior art, keys and ciphertexts are too long and the ciphertext homomorphic computation efficiency is low. The method comprises the realization steps that a user sets parameters, obtaining a decryption private key, an encryption public key and a ciphertext homomorphic computation public key, establishes the binary truncated polynomial ring, carries out probability encryption on a plaintext through adoption of the encryption public key to obtain the ciphertext belonging to the binary truncated polynomial ring, and decrypts the ciphertext through adoption of the decryption private key to obtain the plaintext corresponding to the ciphertext; a cloud server carries out homomorphic computation on the ciphertext through adoption of the ciphertext homomorphic computation public key, thereby obtaining the homomorphic ciphertext belonging to the binary truncated polynomial ring; and the user decrypts the homomorphic ciphertext through adoption of the decryption private key, thereby obtaining a result obtained by carrying out the same computation on the corresponding ciphertexts. According to the method, the lengths of the ciphertexts and the keys are normal levels and the homomorphic computation efficiency is high.
Owner:XIDIAN UNIV
Prefiltering in mimo receivers
Demodulates data signals transmitted by a plurality of transmit antennas over a radio channel. The method includes receiving (202) a data signal and a reference signal on a plurality of receive antennas, the content of the reference signal being known a priori to the receiver. The content of the reference signal is used to compute (204) an estimated polynomial channel matrix. Compute the (206,208) polynomial pre-filter matrix by decomposing the estimated polynomial channel matrix into the product of a pseudo-unitary polynomial matrix and an upper-triangular polynomial matrix with a minimum phase filter on its main diagonal, where by computing the pseudo-unitary polynomial matrix Pseudoconjugate of a unitary polynomial matrix to obtain a polynomial prefilter matrix. The received data signal is modulated (212), wherein the received data signal is multiplied by the computed polynomial prefilter matrix.
Owner:TELEFON AB LM ERICSSON (PUBL)
Environment self-adaptation frequency offset estimating method by simplifying polynomial factors
ActiveCN102111356BEasy to operateReduce complexityBaseband system detailsMulti-frequency code systemsMean squareEstimation methods
The invention provides an environment self-adaptation frequency offset estimation method by simplifying polynomial factors, which is characterized by comprising the following steps: according to the number Nt of transmitting antennas and a Q value, calculating a parameter rho related to mean square errors of frequency offset estimation, wherein Q=N / P>Nt; Q represents the gap between adjacent non-zero pilot frequencies in a training sequence on the transmitting antennas; N represents the length of the training sequence; P represents the length of a base training sequence; P is less than N and (N)2P is equal to 0; and (N)2P represents to carry out model 2P operation related to N. According to the method, the optimizations related to frequency offset estimation parameters can be realized in a self-adoption mode with the change of the environment, thus realizing the high-accuracy environment self-adoption frequency offset estimation.
Owner:白盒子(上海)微电子科技有限公司
A Blind Recognition Method of Erased Convolutional Codes with a Code Rate of (n-1)/n
InactiveCN101237239BSolve quickly and efficientlyReduce orderError correction/detection using convolutional codesError preventionMathematical modelTheoretical computer science
The invention discloses a blind recognition method of a deletion convolutional code with a code rate of (n-1) / n. Firstly, a mathematical model for blind recognition of a deletion convolutional code is established: v(D)=m(D)G(D) , where v(D) represents the coded output sequence, m(D) represents the information sequence to be coded, G(D) is the generator polynomial matrix, according to the coded output sequence v(D), the generator polynomial matrix G(D) and the checksum The polynomial matrix H(D) satisfies the relation G(D)·H(D)T=0 and v(D)·H(D)T=m(D)·G(D)·H(D)T=0 , first estimate the parity check polynomial matrix H(D) from v(D), and then estimate the generator polynomial matrix G(D), and combine the received encoded output sequence v(D) to recover the information sequence m(D). The method for identifying the erasure convolutional code of the (n-1) / n code rate in the present invention can identify the erasure convolutional code more concisely and quickly, and at the same time solve the problem that the initial bit value of the convolutional code code word is fuzzy .
Owner:黄知涛
A construction method of ldpc convolutional code
InactiveCN105871385BError correction/detection using multiple parity bitsCode conversionLdpc convolutional codesTheoretical computer science
The invention relates to a LDPC convolutional code construction method, comprising the steps of generating all elements over a finite field GF(q), FORMULA, wherein q is an prime number or a power of the prime number, and alpha is a basic element over the GF(q); forming a m*n base matrix W by using the elements alpha<0> = 1, alpha, ..., alpha<q-2> of the finite field GF(q); and obtaining a time-invariant LDPC convolutional code polynomial matrix H(D) via the base matrix W. Compared with the existing skills, the LDPC convolutional code construction method provided by the invention has the characteristic of rapid coding, can obtain the code with the maximal achievable code memory, and has the lower error floor and good coding performance under the small constraint length.
Owner:SOUTH CHINA NORMAL UNIVERSITY
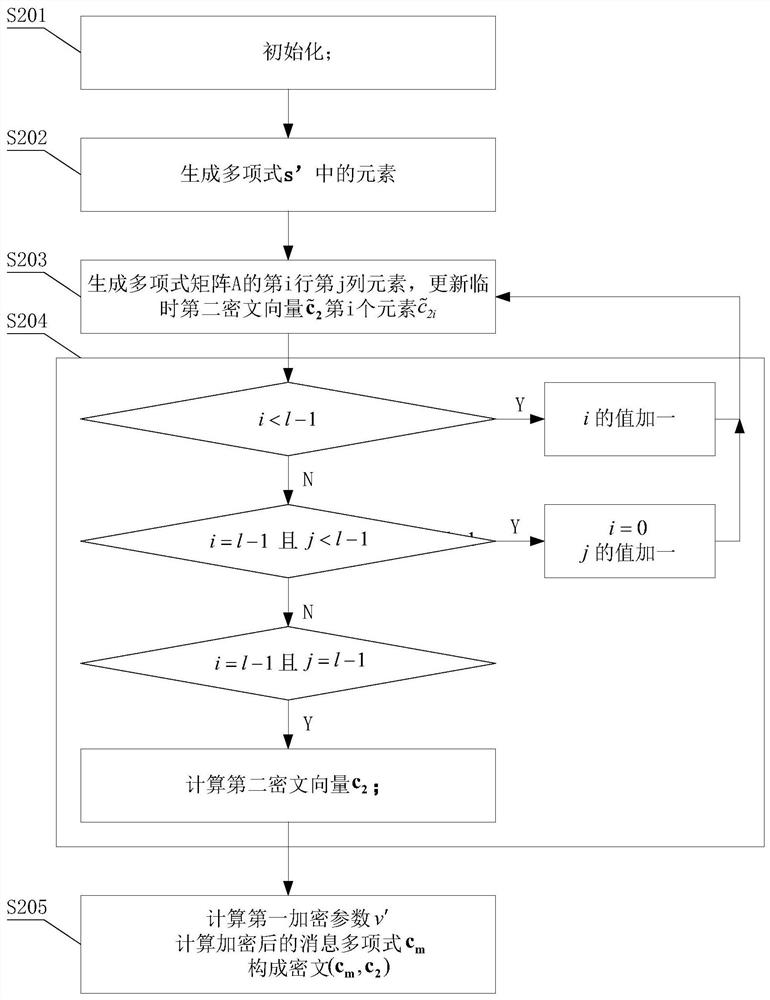
A Lattice-Based Encryption Method
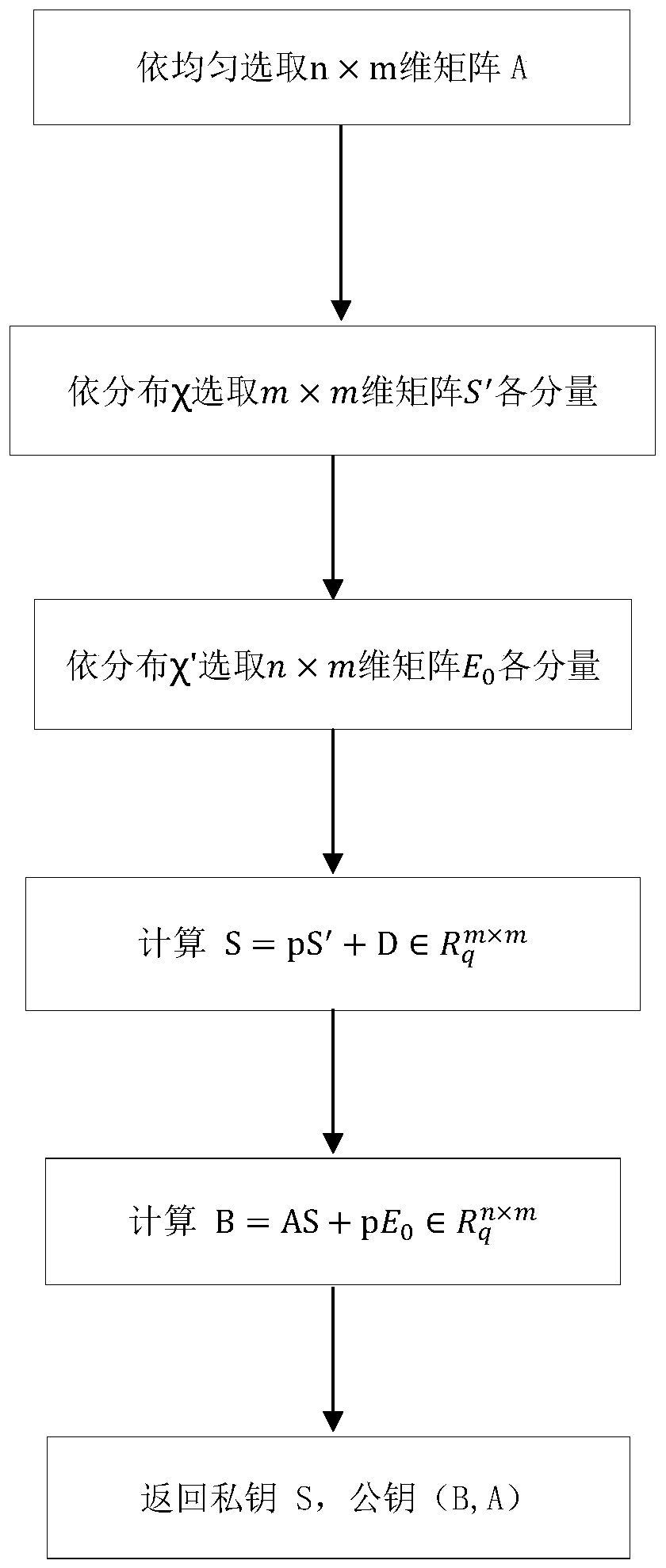
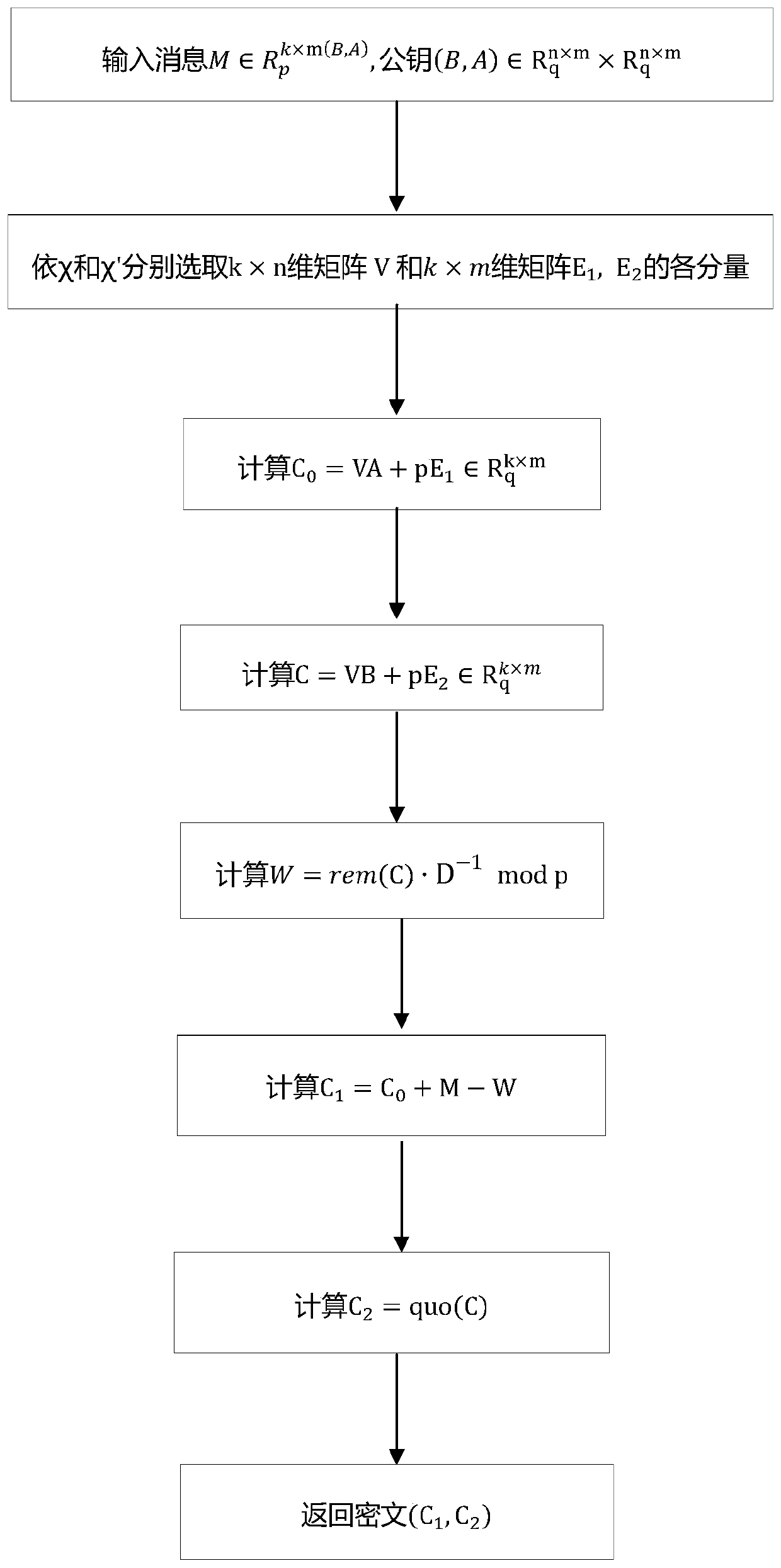
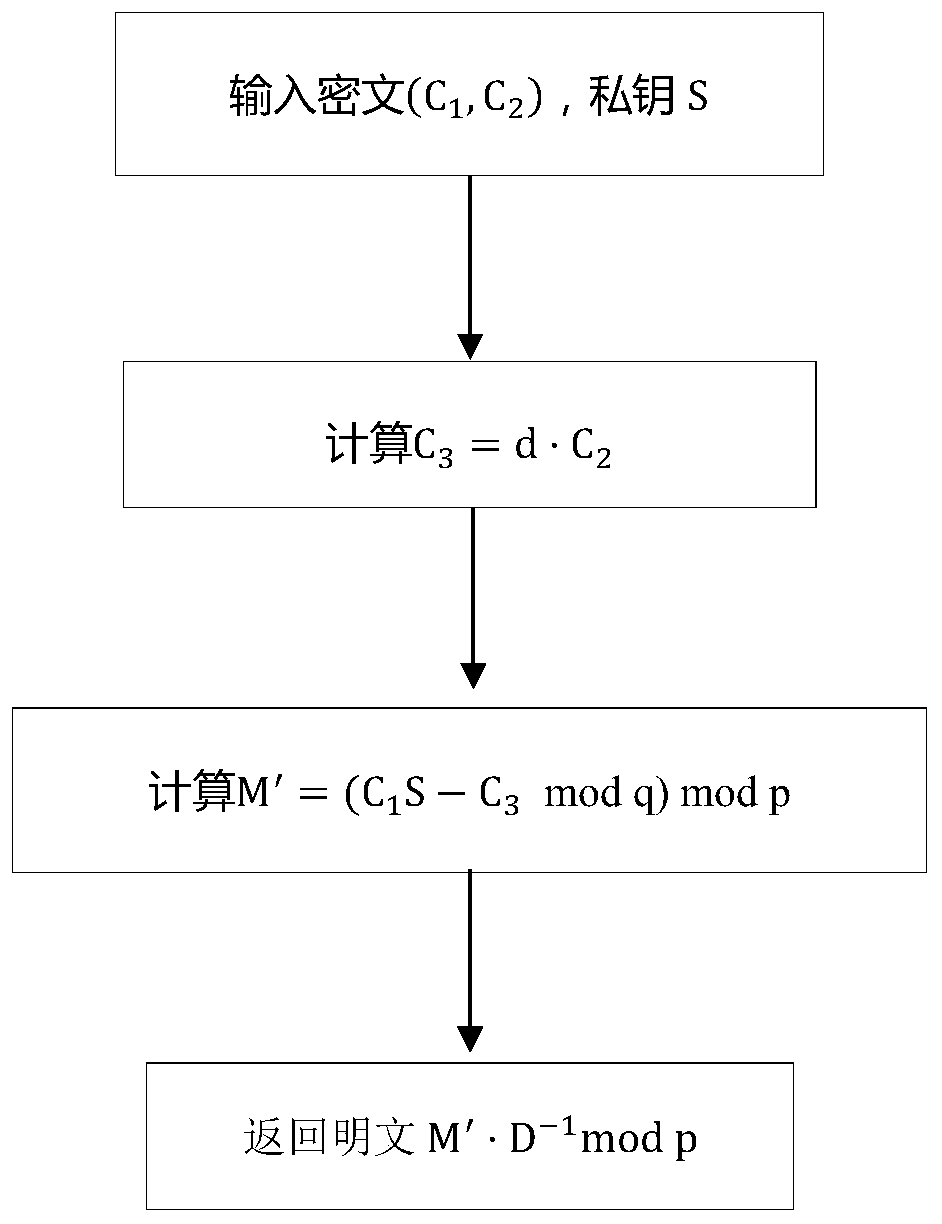
ActiveCN110474772BReduce bandwidth requirementsEfficient solutionPublic key for secure communicationAlgorithmCiphertext
The invention discloses a lattice-based encryption method, which comprises the following steps of: 1) a private key S and a public key (B, A) are generated; 2) the sender calculates C0 = VA + pE1 andC = VB + pE2 by using the receiver public key; (3) the sender calculates a remainder of each coefficient of each component polynomial of the matrix C for d, the obtained remainder polynomial matrix isrecorded as rem (C), and W is made to be equal to rem (C) * D-1 mod p; then, C1 = C0 + M-W is obtained through calculation; 4) the sender calculates the quotient of each coefficient of each componentpolynomial of the matrix C to d, and the obtained quotient polynomial matrix is recorded as C2 = quo (C); and then ciphertext (C1, C2) is output. According to the method, the ciphertext is hidden ata low position and can be combined with other technologies for use, and then the purpose of simultaneously hiding the high position and the low position is achieved; meanwhile, due to the introductionof a ciphertext compression technology, the bandwidth requirement of communication is also reduced.
Owner:ACAD OF MATHEMATICS & SYSTEMS SCIENCE - CHINESE ACAD OF SCI
An Automatic Color Correction Method Based on Least Square Method
ActiveCN107846532BSolve the problem of visual errorColor signal processing circuitsAlgorithmColor correction
The invention provides an automatic color correction matrix algorithm based on the least square method. The algorithm performs sampling statistics on two images with differences, outputs respective standard color correction matrixes, and fits a polynomial matrix satisfying the difference of sensors according to the basic principle of the least square method. The problem of visual error caused by insufficient precision of the sensor, the optical filter, the lens and other hardware, and such factors as sensitometric curve discreteness is solved.
Owner:TIANJIN TIANDY DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com