Encryption method for network and information security
A technology of information security and encryption method, which is applied in the field of data encryption, and can solve problems such as slow calculation speed and slow diffusion speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
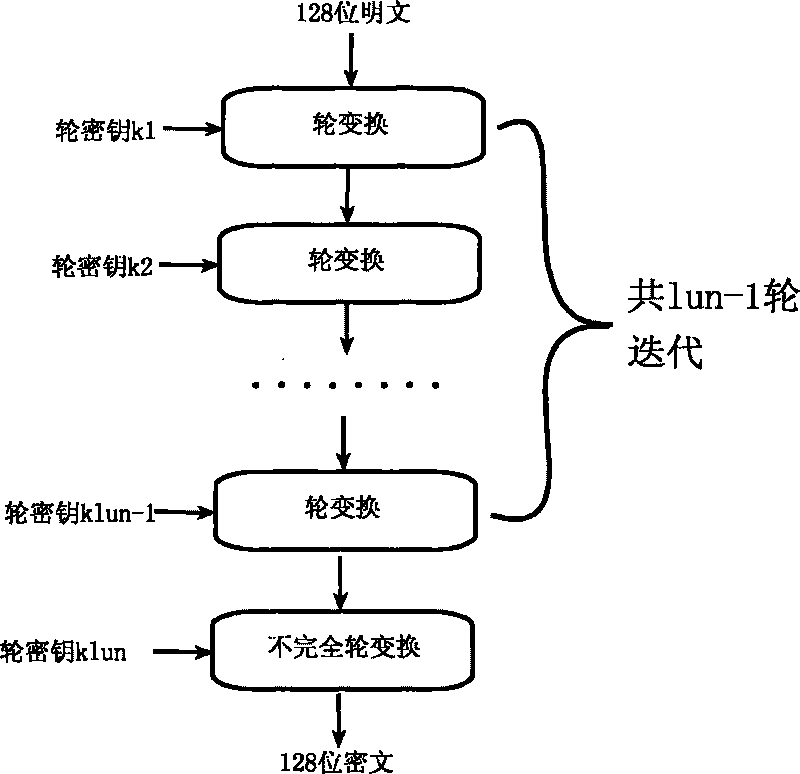
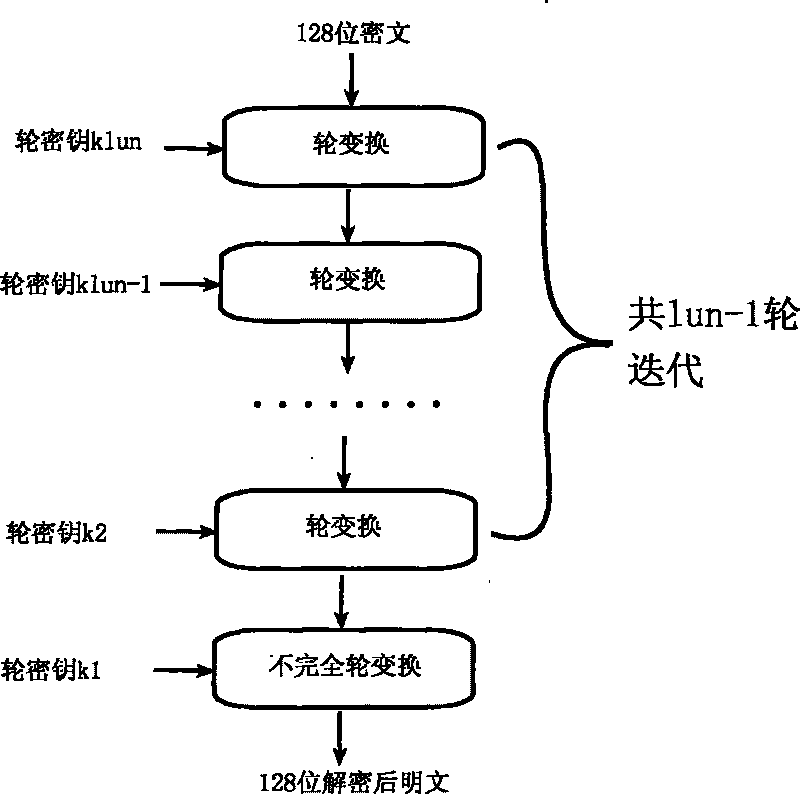
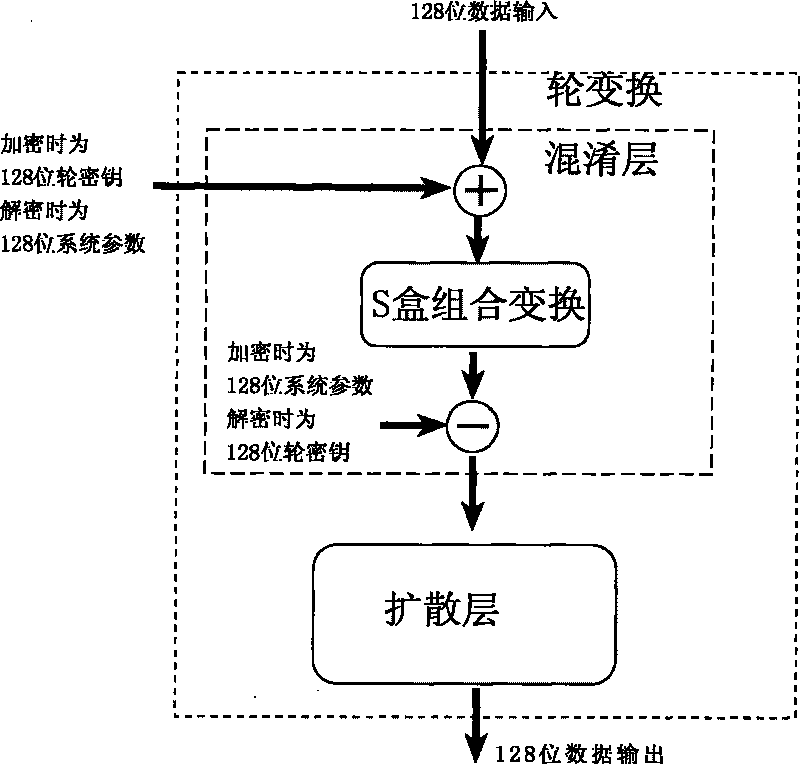
[0096]The invention is an efficient symmetrical block cipher algorithm. The block length of this algorithm is 128 bits, and the key length is 128 bits. This algorithm adds 128-bit system parameters, which provides a guarantee for mutual isolation under different systems, and also provides a basis for realizing public key ciphers based on integrated circuits and block cipher algorithms. Programs offer possibilities. The encryption algorithm adopts a multi-round SP network type nonlinear iterative structure, and the encryption round key is generated by the encryption key through the encryption round transformation. The decryption algorithm is the inverse transformation of the encryption algorithm, the decryption key is the last output of the key expansion of the encryption key, and the decryption round key is the reverse order of the encryption round key, which is generated by the decryption key using the decryption round transformation.
[0097] 1. This encryption algorithm fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com