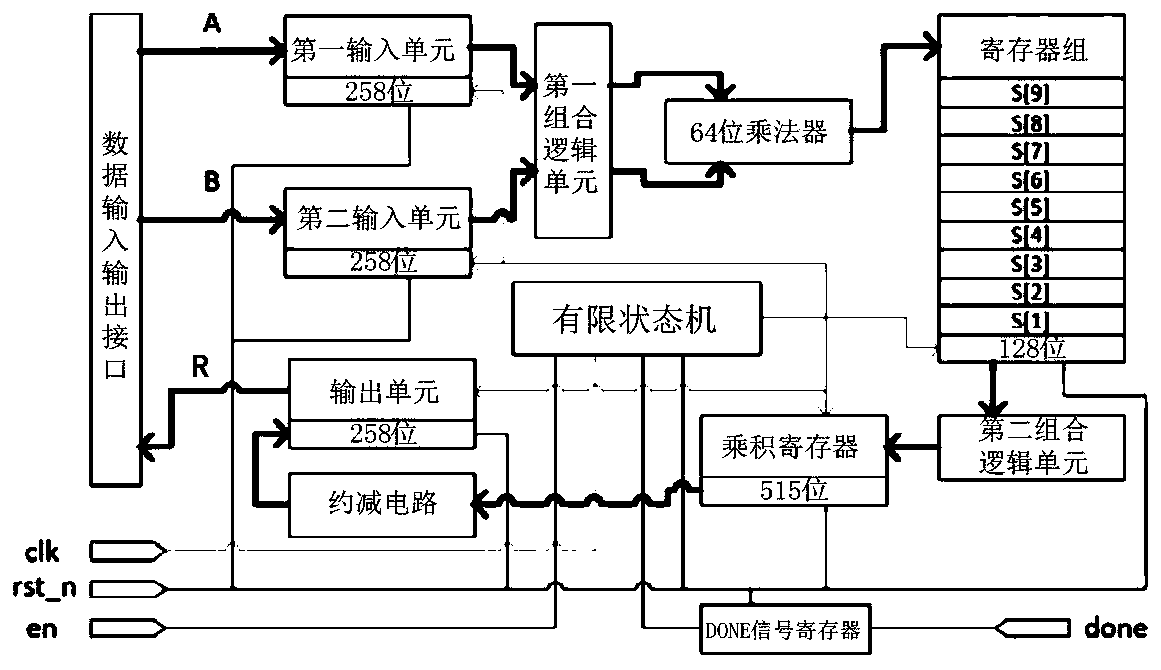
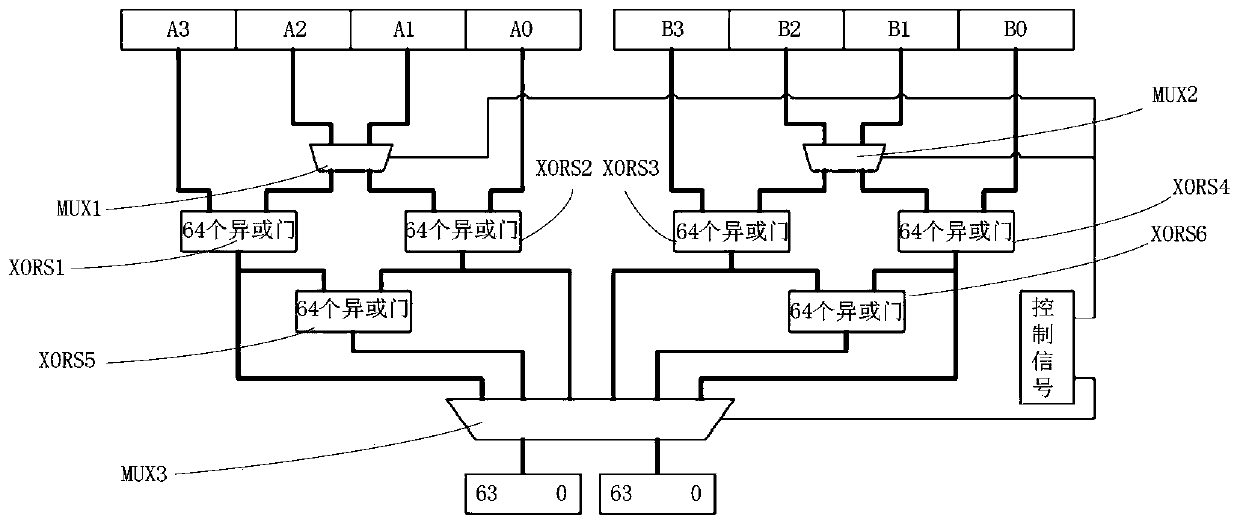
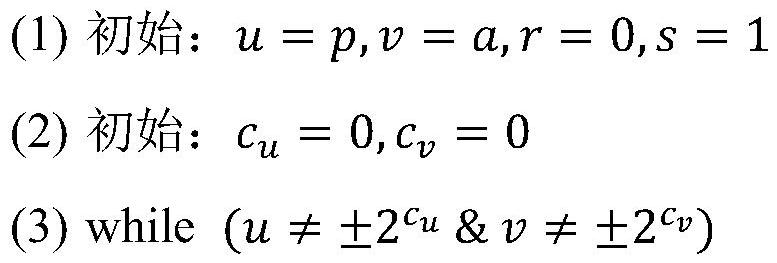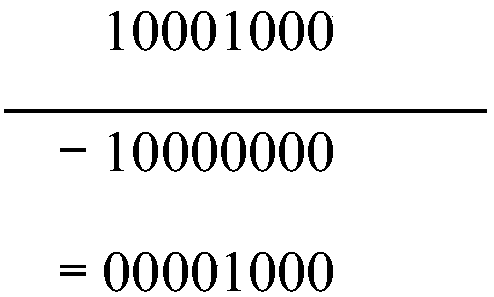Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Modular inversion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
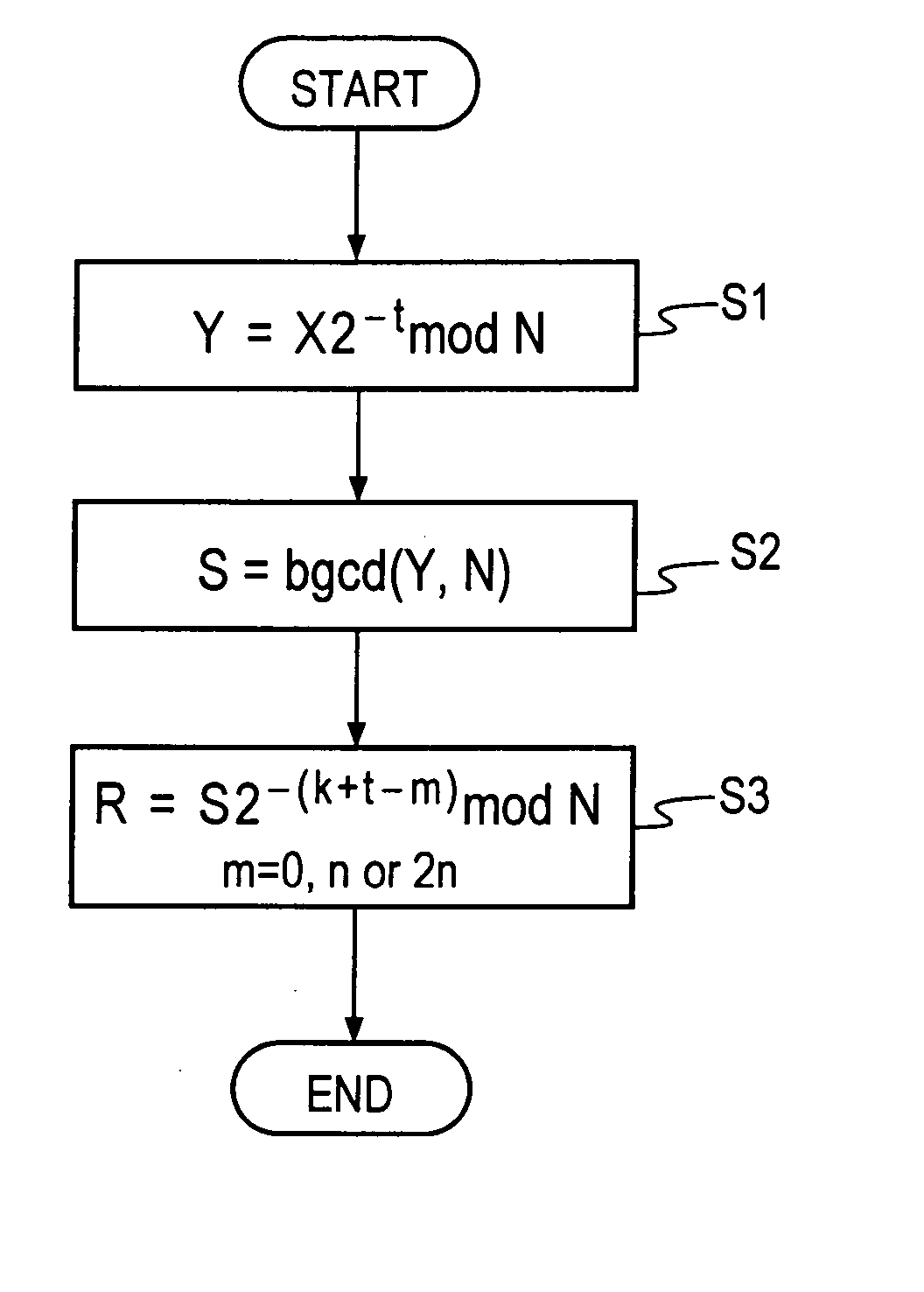
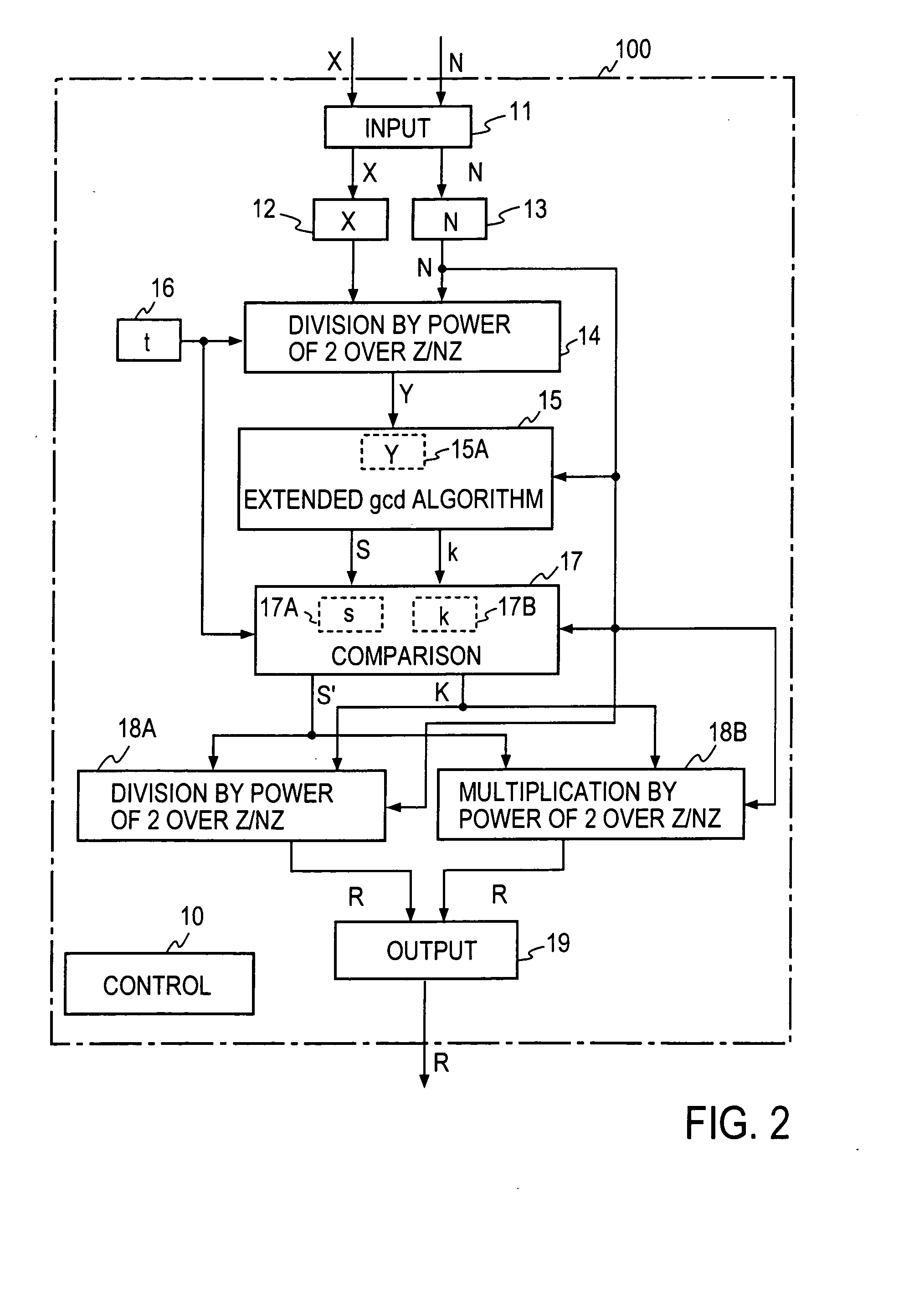
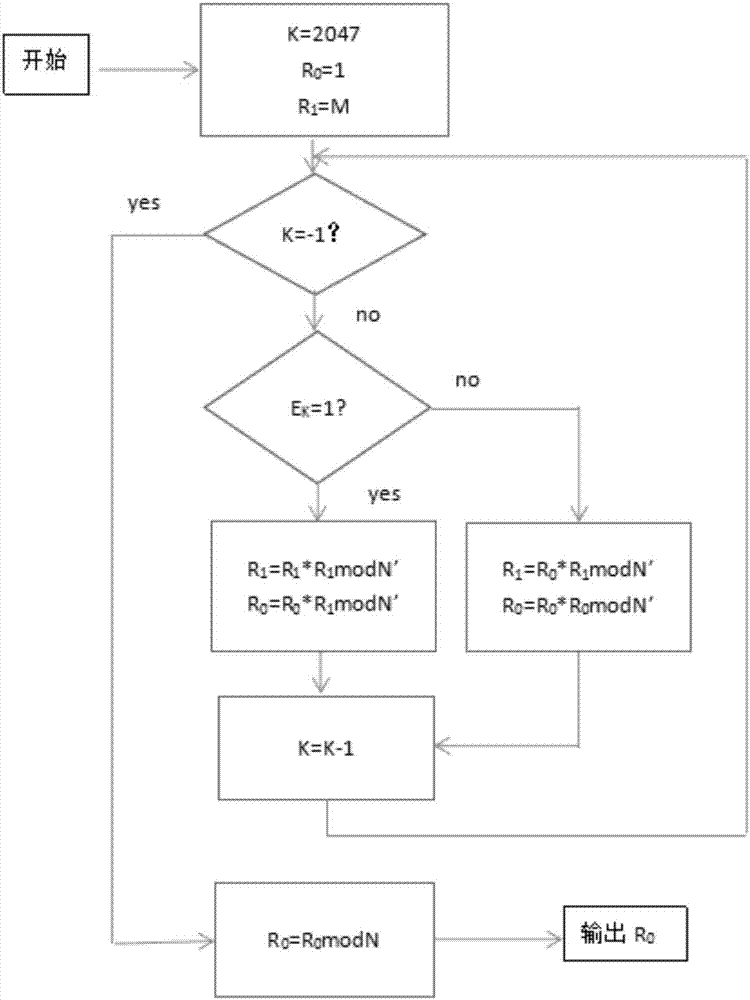
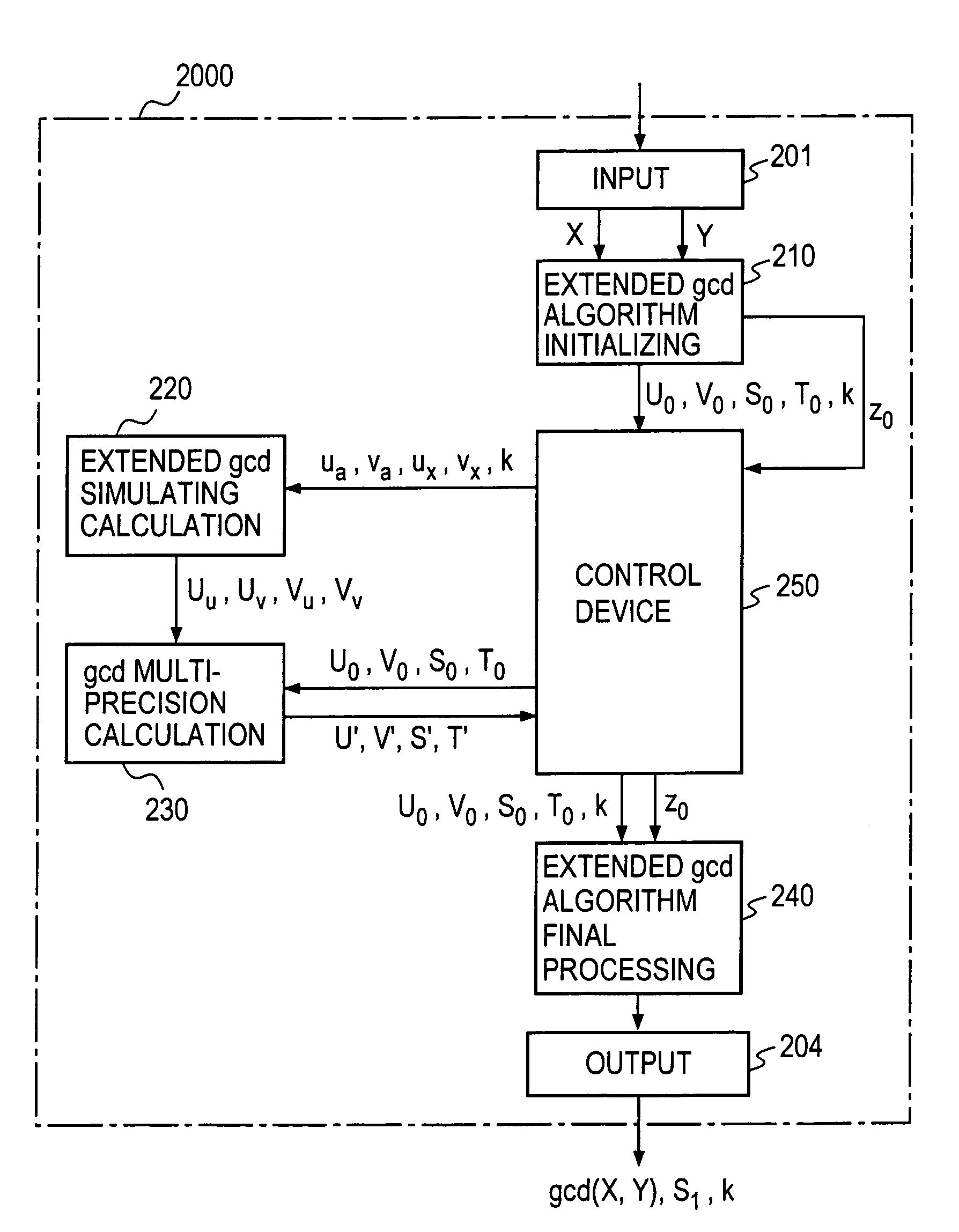
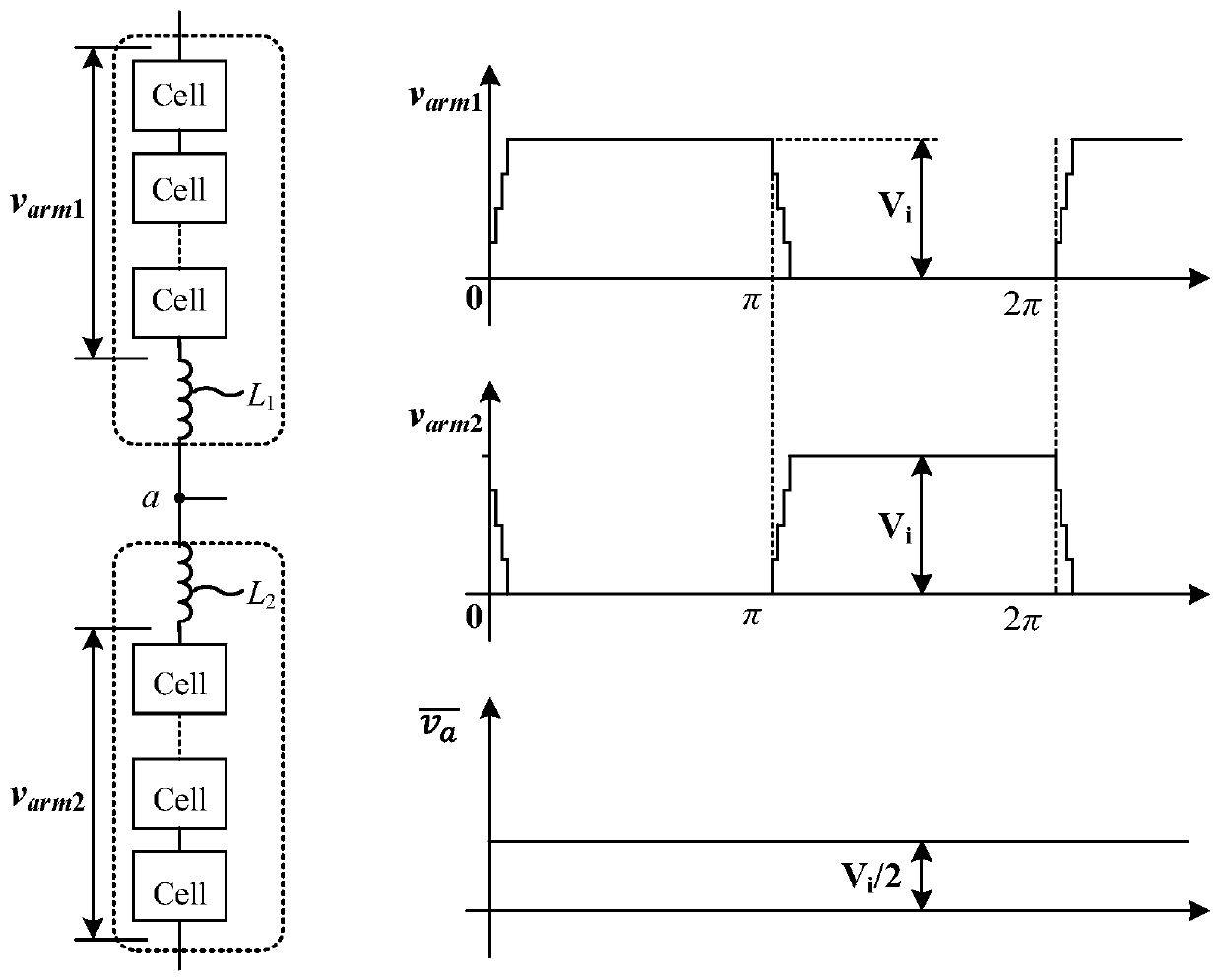
Method and apparatus for modular inversion for information security and recording medium with a program for implementing the method
InactiveUS20050041811A1Shorten the timeShort timeDigital computer detailsSecret communicationAlgorithmInformation security
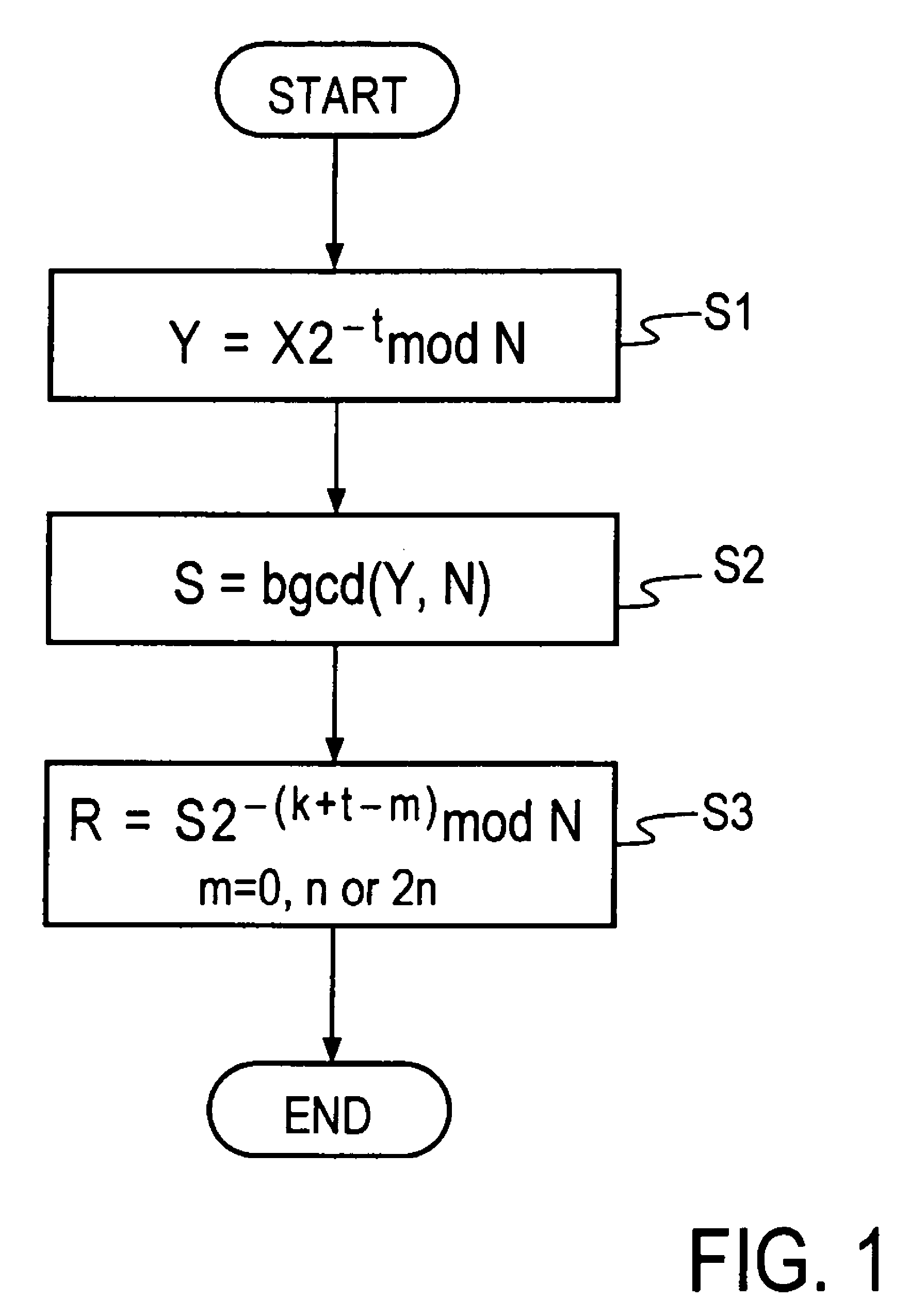
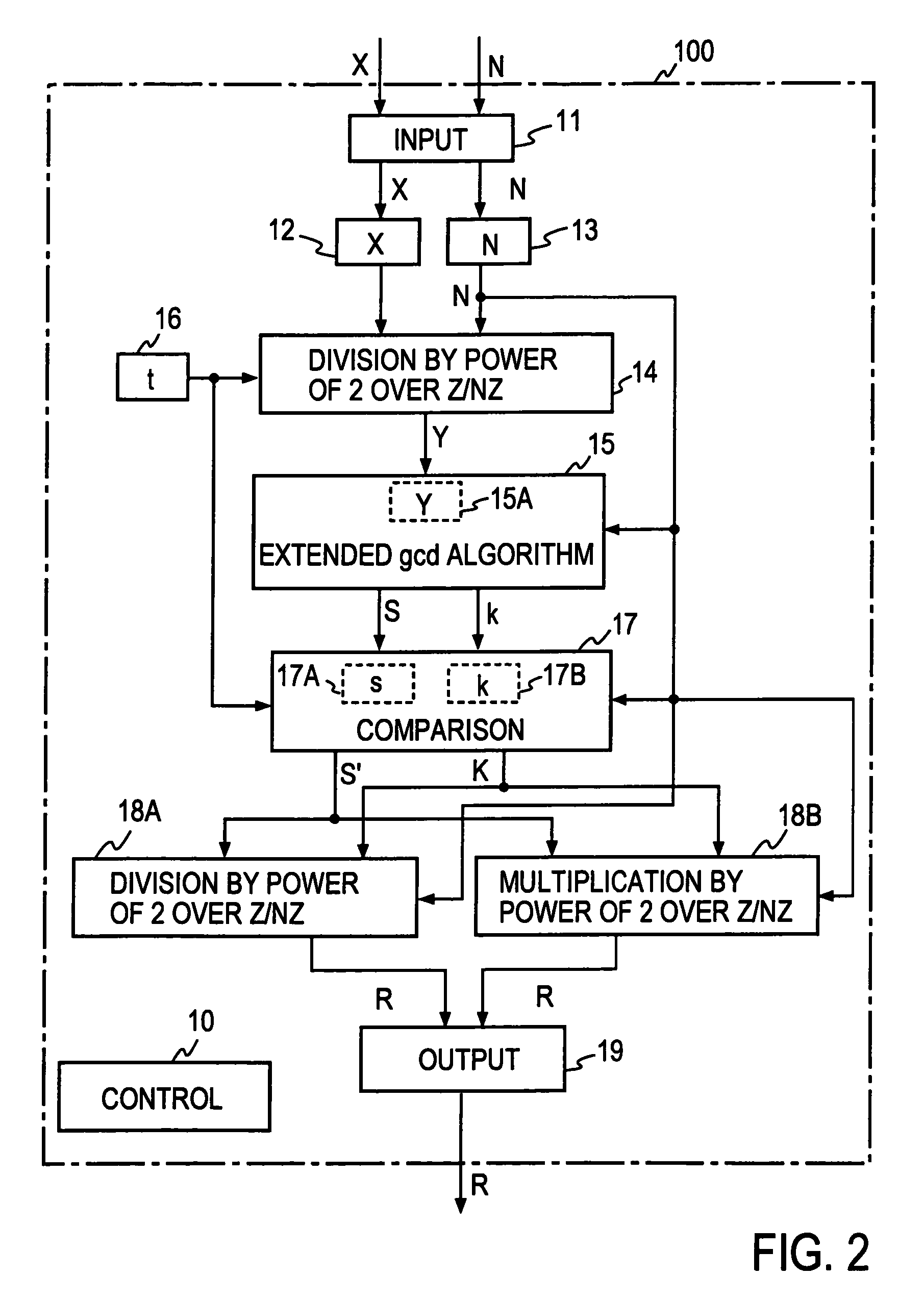
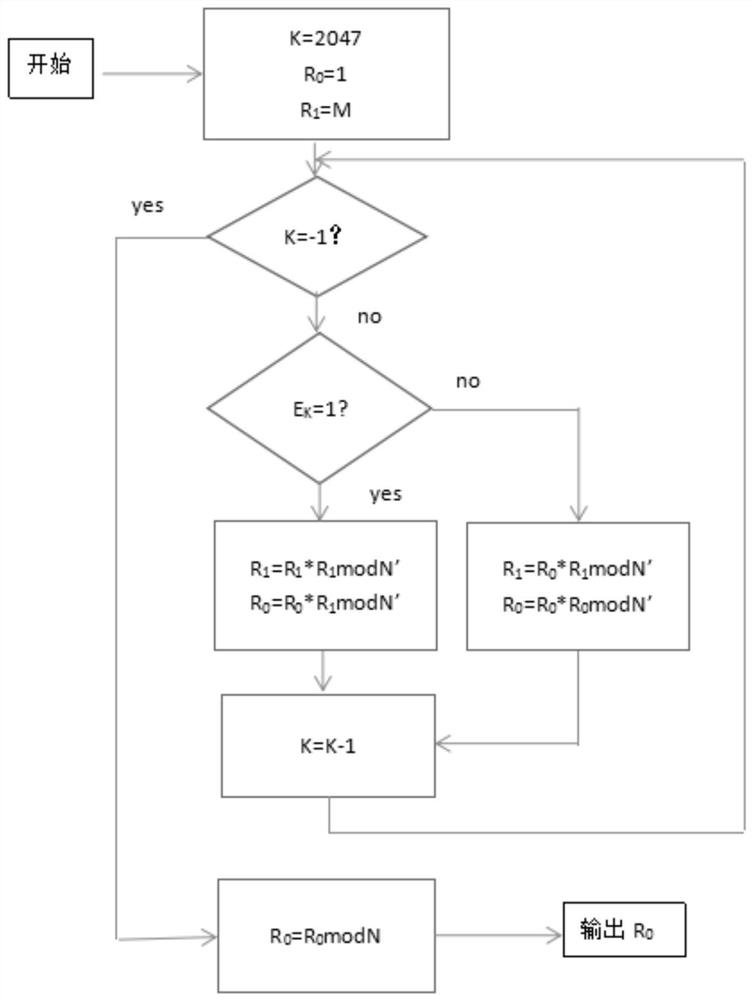
Values X and N of n bits and a parameter t are input, then Y=X2−t mod N is calculated, then an extended binary GCD algorithm is executed for Y to obtain S=[[Y]] y−12k mod N and k, and R=S2−(k+t=2n) is calculated for S, thereby obtaining a Montgomery inverse R=X−122n mod N of X on a residue class ring Z / NZ.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
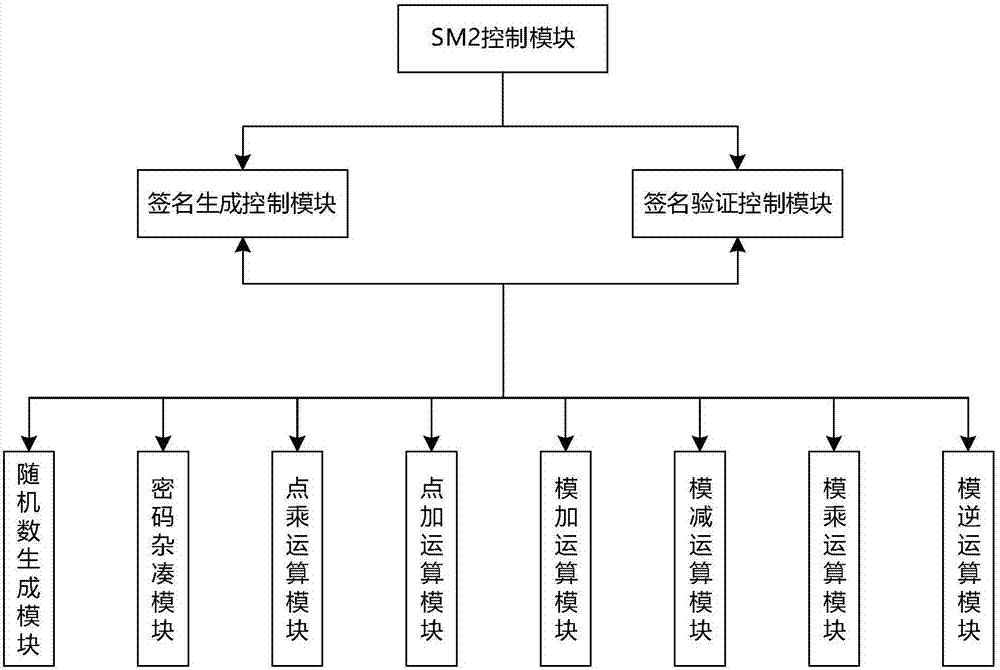
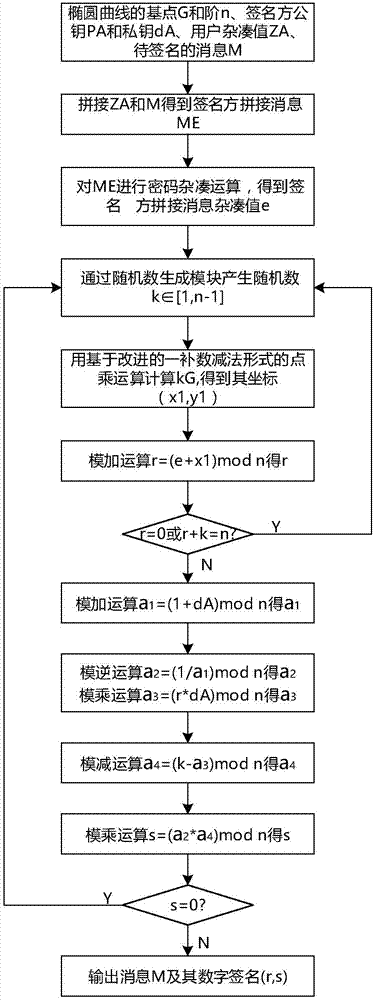
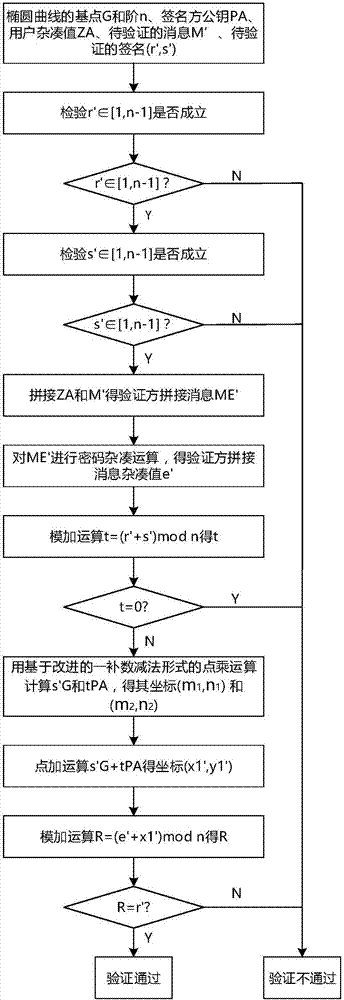
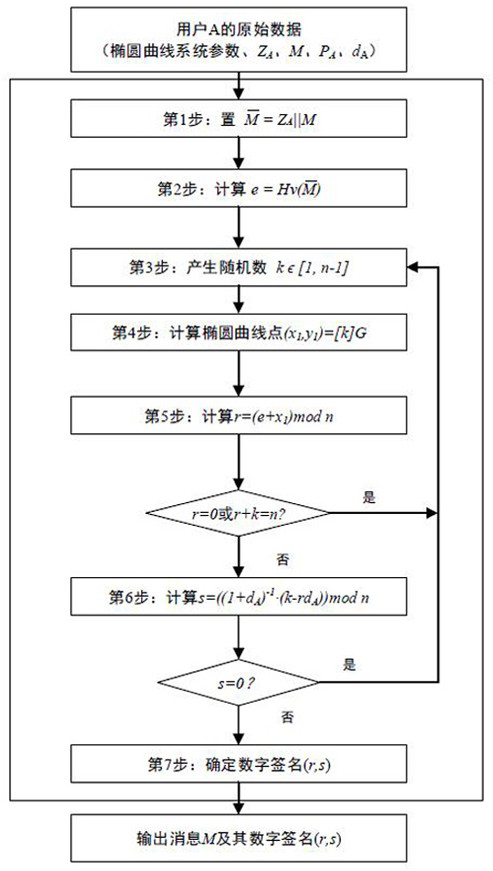
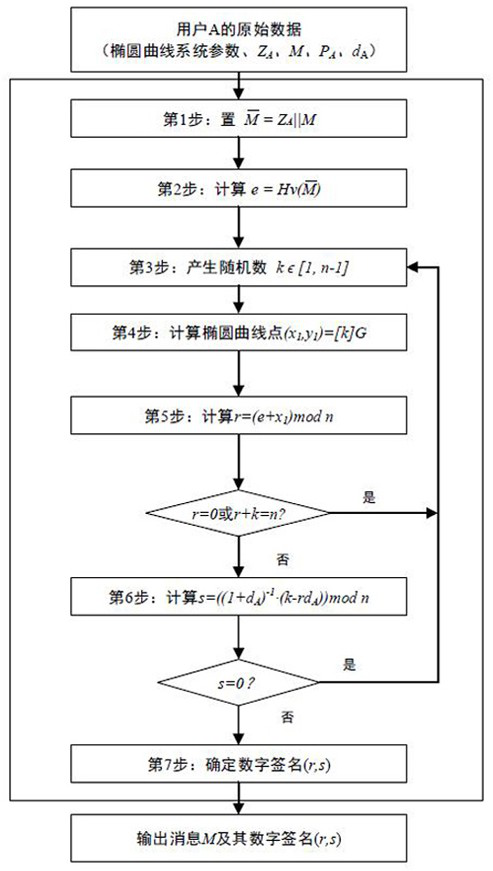
Realization method and system of signature verification algorithm based on SM2 elliptic curve
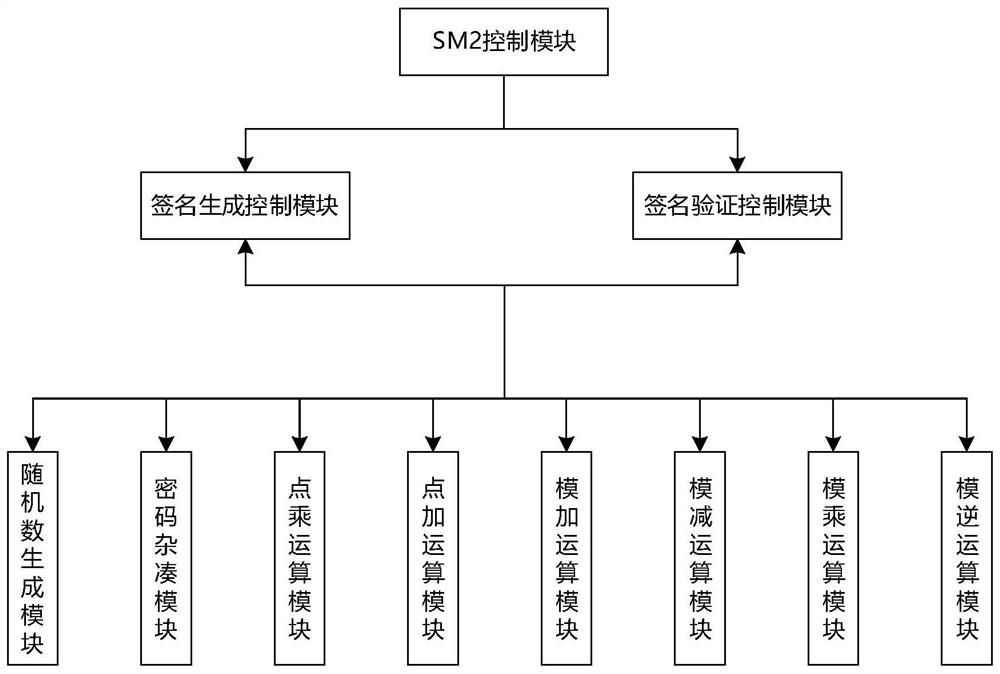
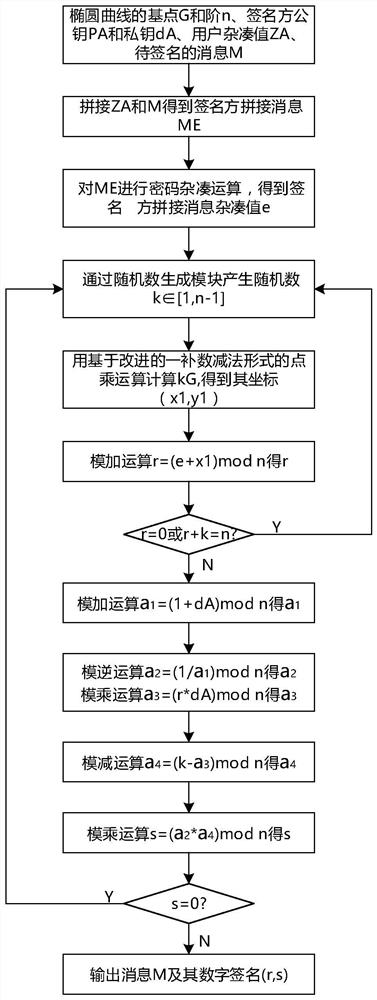
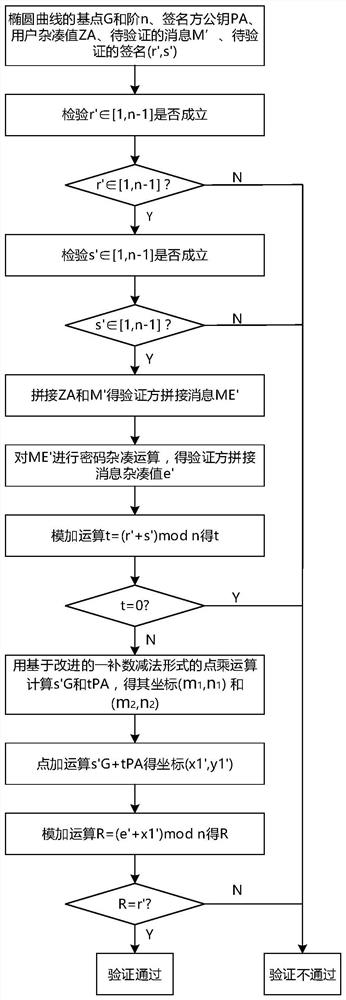
ActiveCN107040385AReduce the number of point addition operationsShorten operation timeUser identity/authority verificationGeneration processPassword
The invention relates to a realization method and system of a signature verification algorithm based on an SM2 elliptic curve. The system, under control of an SM2 control module, realizes generation and verification of digital signatures by communicating with a signature generation control module and a signature verification control module, and calling a random number generation module, a password hash module, a point multiplication operation module, a point addition operation module, a modulo addition operation module, a modulo subtraction operation module, a modular multiplication operation module and a modular inversion operation module. In the digital signature generation and verification process, point multiplication operation adopts an improved partly use 1's complement subtraction form point multiplication algorithm (PCS algorithm); and in the signature generation process, modular multiplication operation adopts an improved Blakley modular multiplication algorithm, and modular inversion operation and modular multiplication operation are carried out simultaneously through a parallel operation method, thereby greatly improving operation speed and reducing operation time.
Owner:GUANGDONG UNIV OF TECH
Lightweight digital signature method facing wireless sensing network
ActiveCN105025474AGood choiceImprove securityNetwork topologiesSecurity arrangementDigital signatureSecret code
The invention discloses a lightweight digital signature method facing a wireless sensing network based on an elliptic curve cryptography mechanism. The method comprises the following steps: initializing a parameter, establishing a public and private key pair, generating a digital signature, and verifying the signature. By utilizing a deformation of a signature equation in a digital signature verification step for the elliptic curve cryptography mechanism, time-consuming modular inversion operation in original signature generation and verification is changed into additive operation, and a TinyECC 2.0 function library after multiple optimization is introduced at the same time, so operation for ECCs is simple and is easy to understand, the lightweight digital signature method has high safety performance, and generation and verification processes of the digital signature has the advantages of the small computation amount and the fast speed.
Owner:ANHUI UNIVERSITY
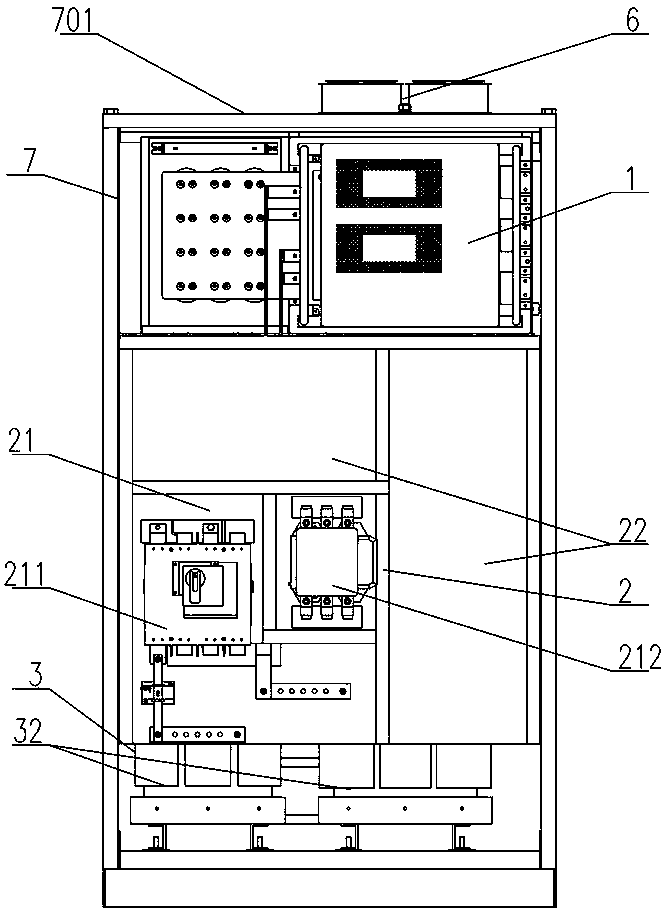
Modular photovoltaic grid-connected inverter structure
ActiveCN103441689AReduce the temperatureReduce the types of design and production specificationsCircuit arrangements on support structuresAc-dc conversionPower inverterGrid connected inverter
The invention discloses a modular photovoltaic grid-connected inverter structure which comprises more than one unit cabinet, wherein each unit cabinet comprises a modular inversion module, an electrical plate, a filtration system, a cabinet body heat dissipation fan and a cabinet body mechanism; the inversion modules are arranged at the upper parts of the cabinet body mechanisms; the electrical plates are fixed in the cabinet body mechanisms and are vertically arranged at the middle lower parts of the cabinet body mechanisms; the electrical plates are provided with standard configuration electrical regions and optional circuit electrical regions; the standard configuration electrical regions are high-voltage regions and comprise direct current input modules and alternating current output modules; the optional circuit electrical regions can select system control modules and / or alternating current main output modules according to demands; direct current filtration modules in the filtration systems are arranged on the back surface sides of the electrical plates; reactor modules in the filtration systems are arranged in rear spaces of the electrical plates side by side. The modular photovoltaic grid-connected inverter structure has the advantages of easiness in maintenance and repair, small size, modulation, high generality, low large-scale cost and the like.
Owner:CSR ZHUZHOU ELECTRIC LOCOMOTIVE RES INST
Low cost digital signature SPOC design method based on RSA and SHA-512
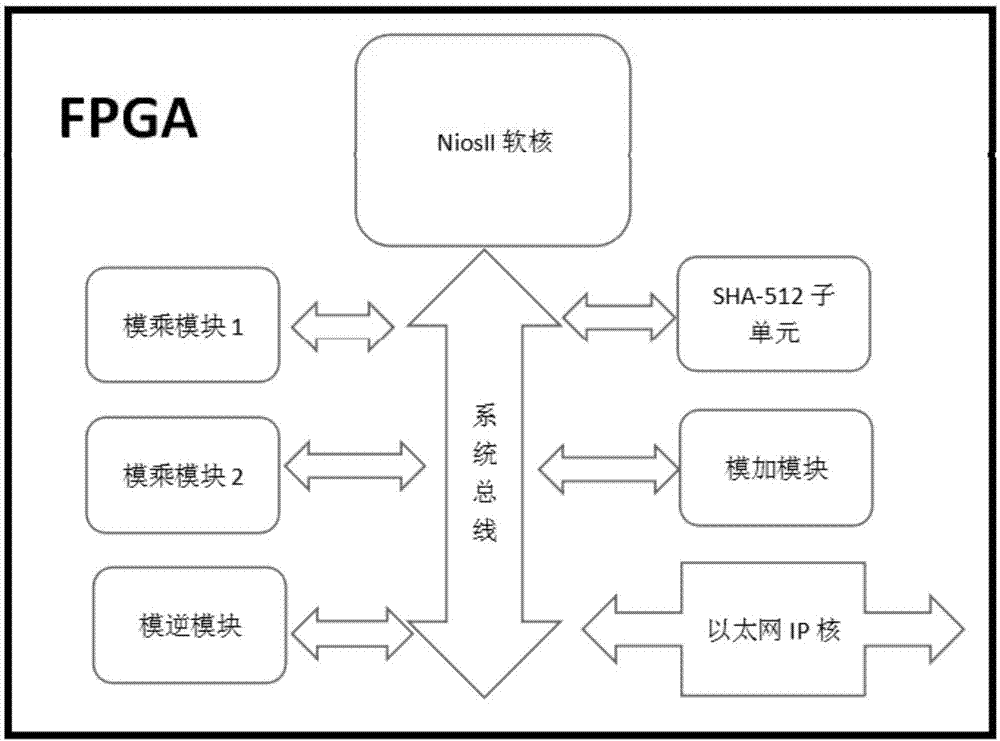
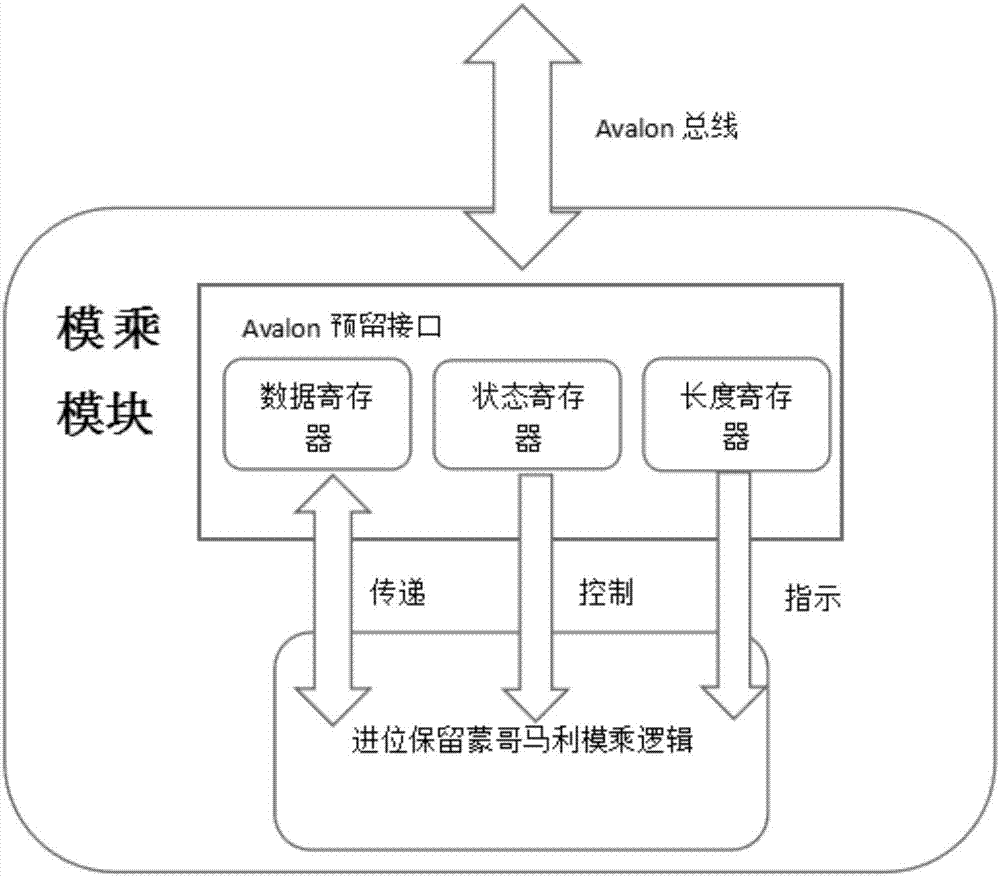
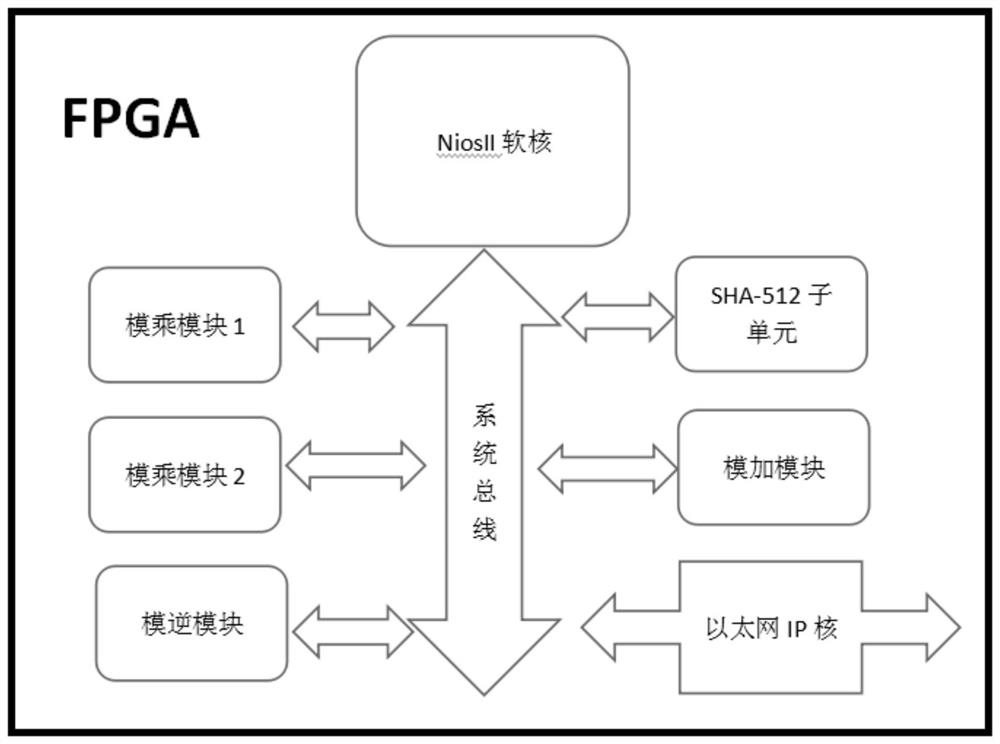
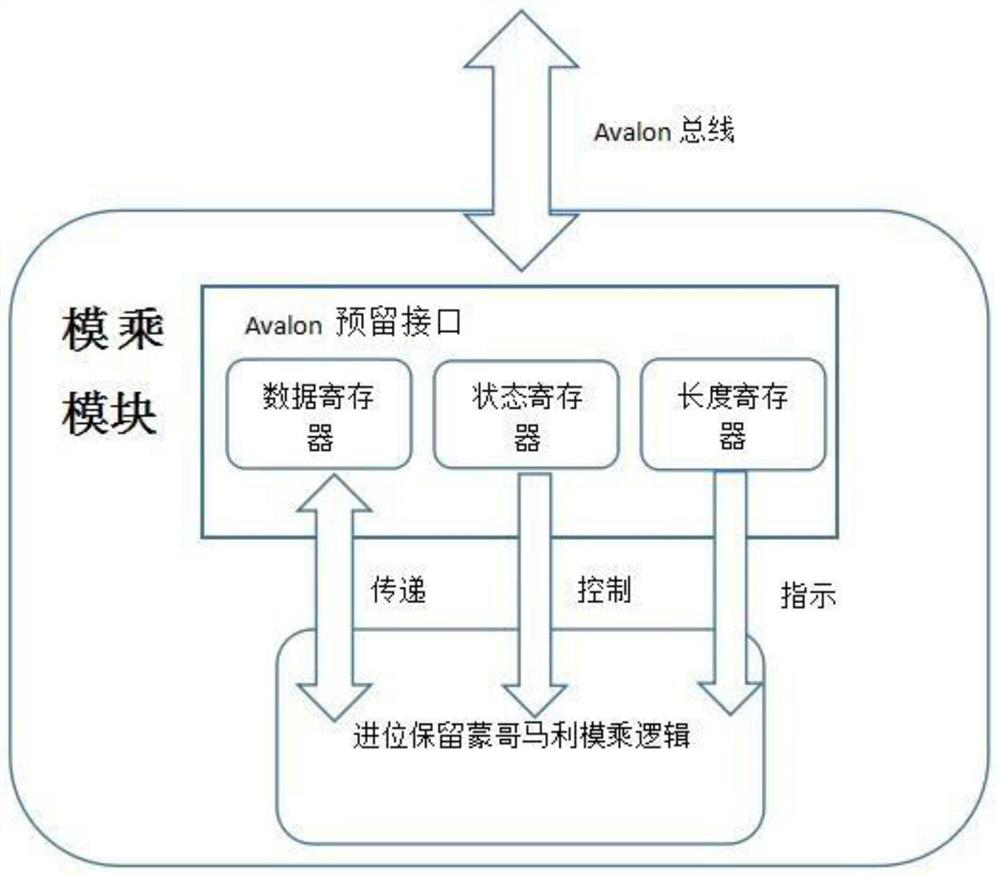
ActiveCN107508666AFast operationDefense against side channel attacksEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareHash function
The invention provides a low cost digital signature SPOC design method based on RSA and SHA-512. An in-chip MCU uses a soft core NiosII of an ALTERA to perform hardware and software partitioning on the RSA and SHA-512 according to operation characteristics; a software part comprises interaction with off-chip data, RSA modular exponentiation, and SHA-512 data filling; hardware finishes RSA modular multiplication, a modular addition operation, a modular inversion operation and an operation for taking 80 rounds as a subunit in the SHA-512. The low cost digital signature SPOC design method based on RSA and SHA-512 utilizes parallelism of hardware calculation to obtain a high speed operation result, uses flexibility of software to guarantee an attack resisting capability of a system, can support different RSA lengths and calculation modes of different HASH functions. Functionally, the low cost digital signature SPOC design method based on RSA and SHA-512 can be used for digital autographing and identity authentication.
Owner:SOUTH CHINA UNIV OF TECH
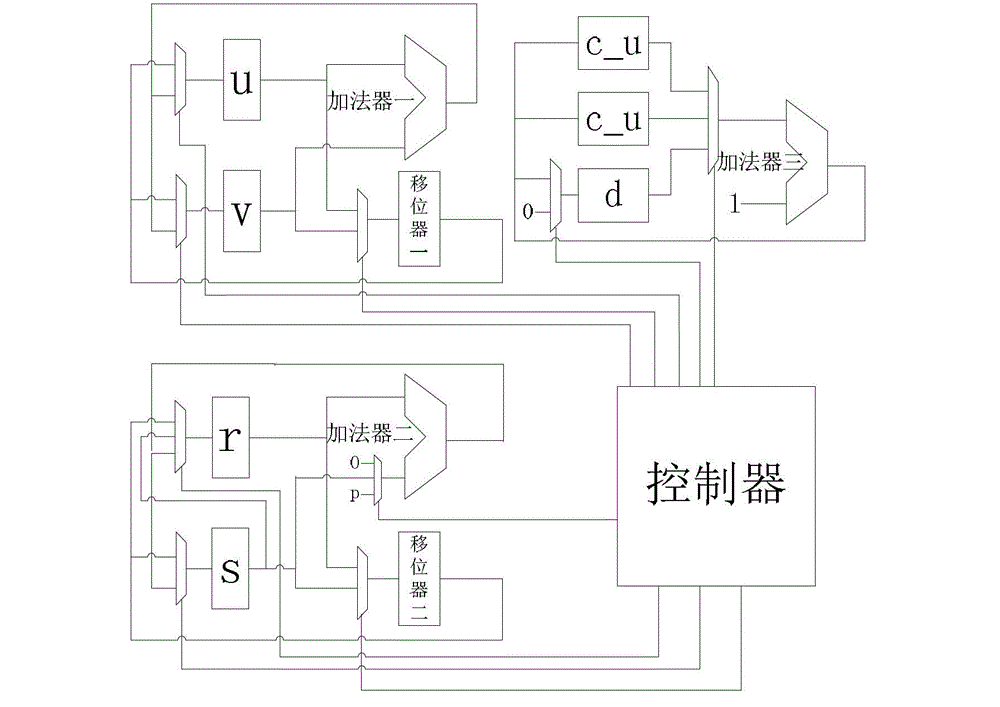
Improved binary-system left-shifting modular inversion algorithm
InactiveCN103336680AReduce occupancyReduce areaComputations using residue arithmeticIntermediate variableComputer science
The invention relates to an improved binary-system left-shifting modular inversion algorithm. For a given modulus p, during a process of calculating the modular inversion, the condition of skipping out of circulation of the bits of the p is c_u=n-1 or c_v=n-1, namely, the comparison between c_u as well as c_v and the constant n-1, wherein u and v are intermediate variables of n bits for storing left-shifted data and are respectively initialized as p and a; r is the intermediate variable for obtaining modular inversion through left shifting and is initialized as 0; after the algorithm is ended, the value in r is a resolved modular inversion result; c_u shows the times of the left shifting; and c_v shows the times of the left shifting of the v. The invention also provides a circuit structure for realizing the algorithm. The algorithm provided by the invention has simpler operation steps and occupies fewer storing units, so that the circuit area and the circuit power consumption are reduced, and a low power consumption requirement of a low-end code system is preferably met.
Owner:TSINGHUA UNIV
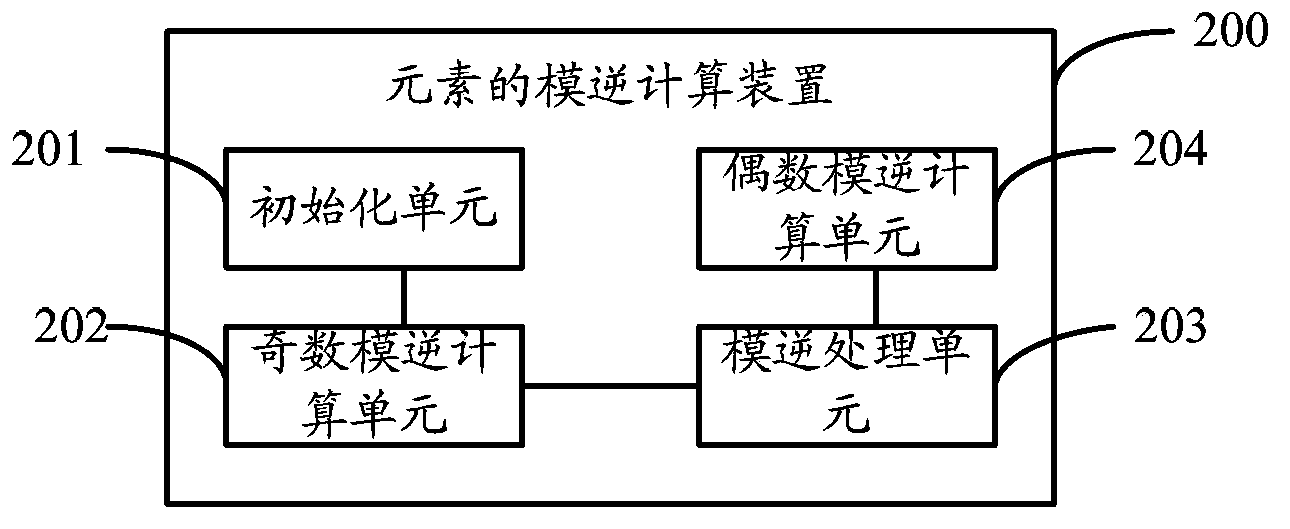
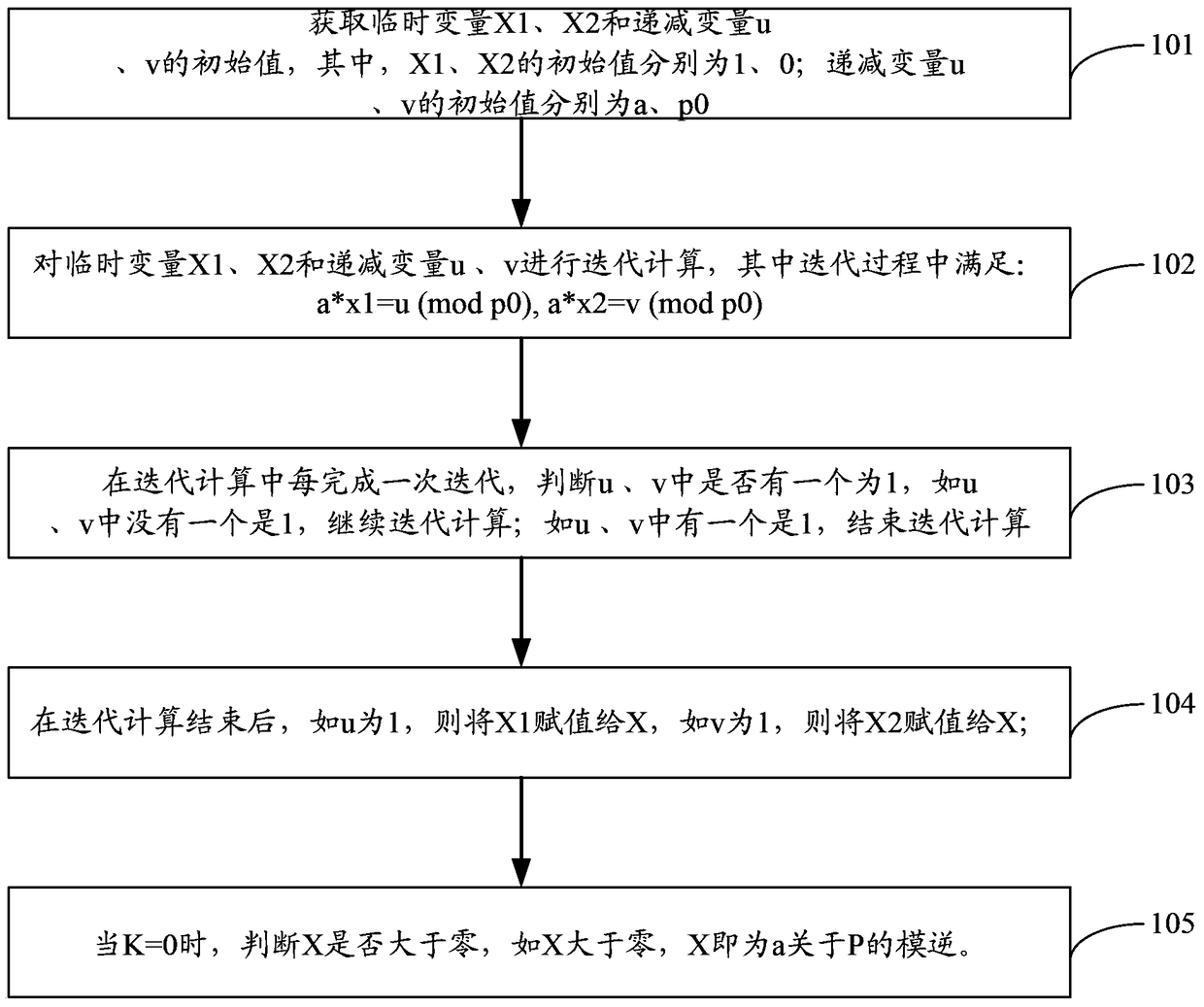
Element modular inversion calculation method and device
ActiveCN104123431ACalculation speedReduce resource requirementsSpecial data processing applicationsTemporary variableTheoretical computer science
The invention is applicable to the technical field of computers and communication and provides an element modular inversion calculation method and device. The method comprises the steps that the initial values of temporary variables X1 and X2 and decreasing variables u and v are obtained, wherein the initial values of the temporary variables X1 and X2 are 1 and 0 respectively, and the initial values of the decreasing variables u and v are a and P0 respectively; the temporary variables X1 and X2 and the decreasing variables u and v are subjected to iterative computation, wherein the iteration process meets the equations: a*x1=u(mod P0), a*x2=v(mod P0); after each time of iteration is completed in the iterative computation, whether one of u and v is 1 is judged, if neither u nor v is 1, the iterative computation is continued, and if either u or v is 1, the iterative computation is ended; after the iterative computation is ended, if u is 1, X1 is assigned to X, and if v is 1, X2 is assigned to X; when K=0, whether X is greater than zero or not is judged, and if X is greater than zero, X is the modular inversion related to P. By means of the technical scheme, the element modular inversion calculation method and device have the advantages that the computing speed is high, and the number of required computing resources is small.
Owner:NATIONZ TECH INC
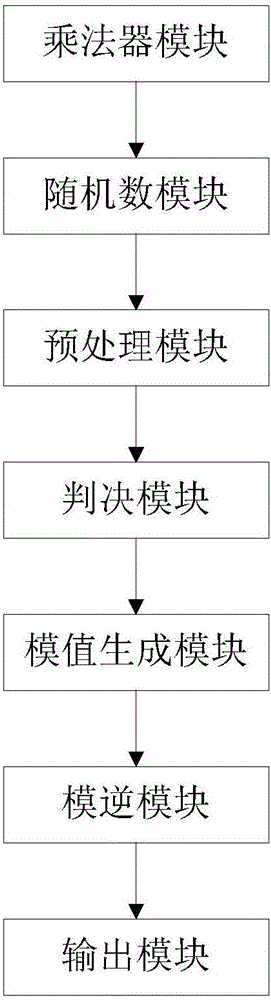
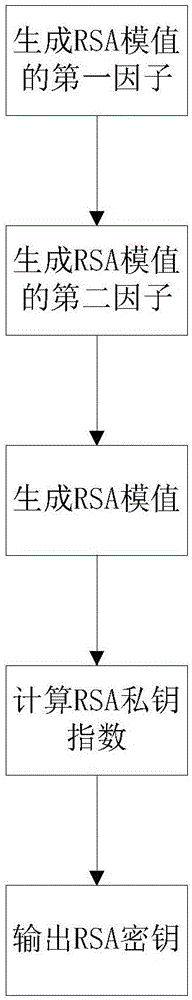
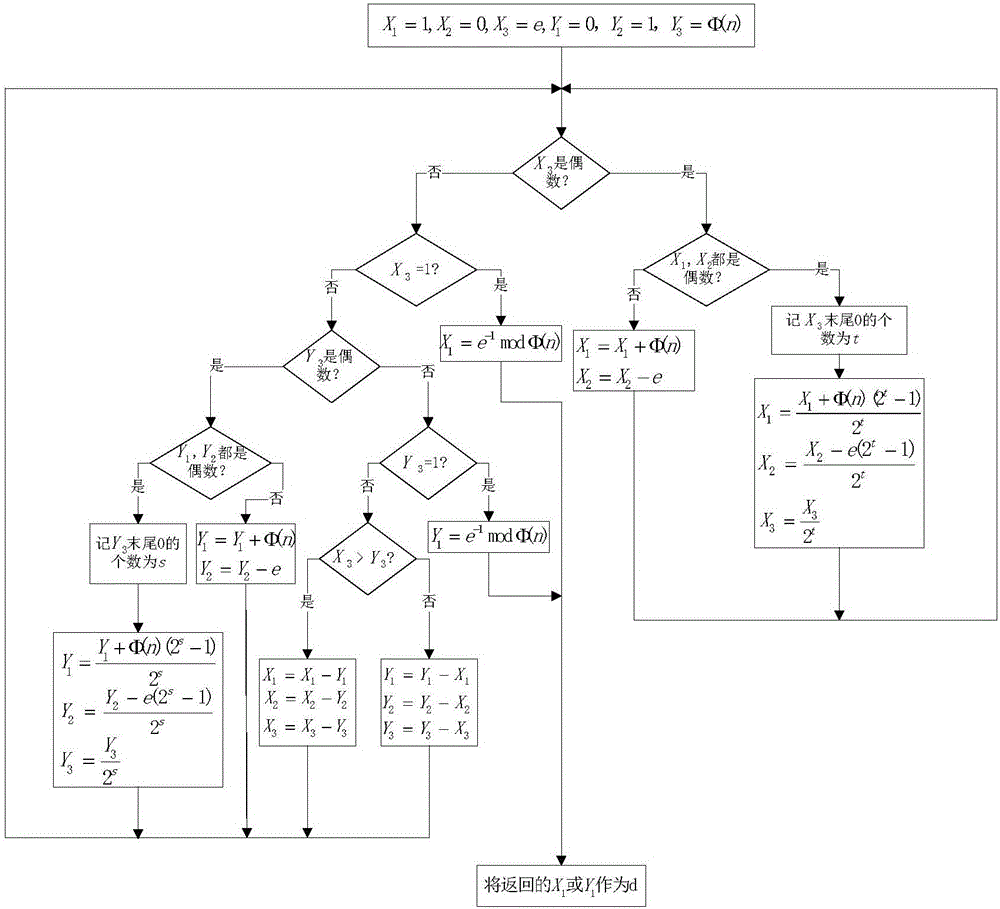
Cipher key generation system and method based on RSA cryptographic algorithm
InactiveCN106850212AAffects spawn speedAvoid insecurityKey distribution for secure communicationPublic key for secure communicationComputer scienceKey generation
The invention discloses a cipher key generation system and method based on an RSA cryptographic algorithm. The cipher key generation system comprises a multiplier module, a random number module, a preprocessing module, a decision module, a module value generation module, a modular inversion module and an output module. The method comprises the following implementation steps: (1) generating a first factor of the RSA module value; (2) generating a second factor of the RSA module value; (3) generating the RSA module value; (4) calculating an RSA private key index; and (5) outputting an RSA cipher key. According to the cipher key generation system and method disclosed by the invention, the calculation burden of the RSA cipher key generation process can be effectively reduced, the generation speed of the RSA cipher key can be increased, and the security of the RSA cryptographic algorithm can be ensured.
Owner:XIDIAN UNIV
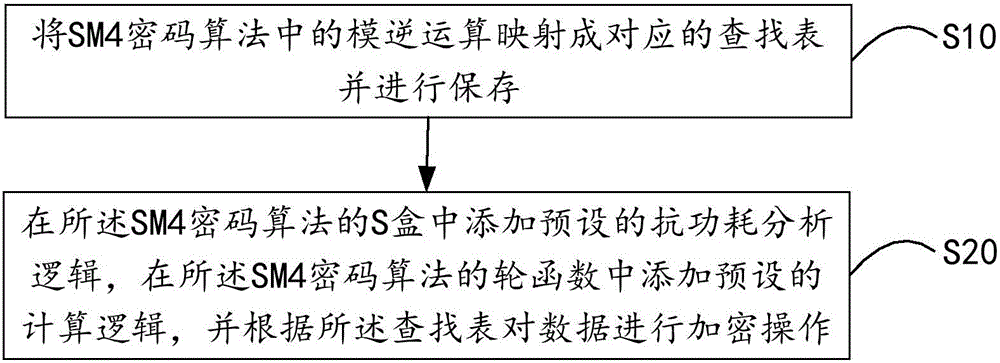
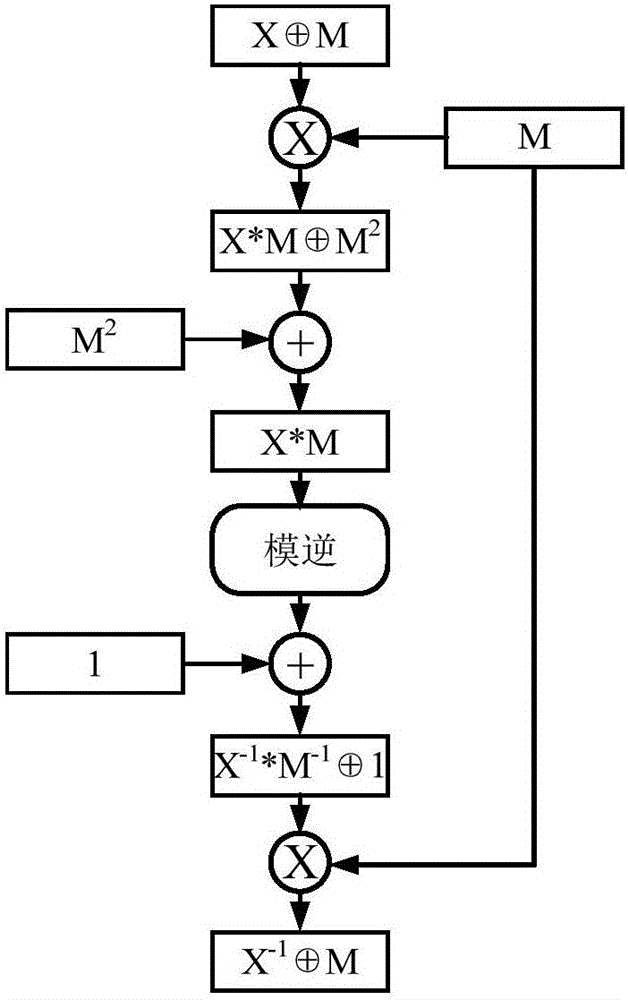
Cipher algorithm anti-power consumption analysis realization method and device
InactiveCN105790923ASmall area overheadImprove performanceEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresState of artS-box
The present invention discloses a cipher algorithm anti-power consumption analysis realization method and device. The method comprises the steps of mapping the modular inversion in a SM4 cipher algorithm into a corresponding lookup table, and saving; adding the preset anti-power consumption analysis logic in an S box of the SM4 cipher algorithm, adding the preset calculation logic in a round function of the SM4 cipher algorithm, and encrypting data according to the lookup table. According to the present invention, the safety problem in the prior art that the SM4 cipher algorithm can be carried out the power consumption analysis easily is solved, the operation efficiency of the finite field modular inversion in the SM4 cipher algorithm is improved, at the same time, the safety of the SM4 cipher algorithm is improved.
Owner:SHENZHEN ZHENGTONG ELECTRONICS
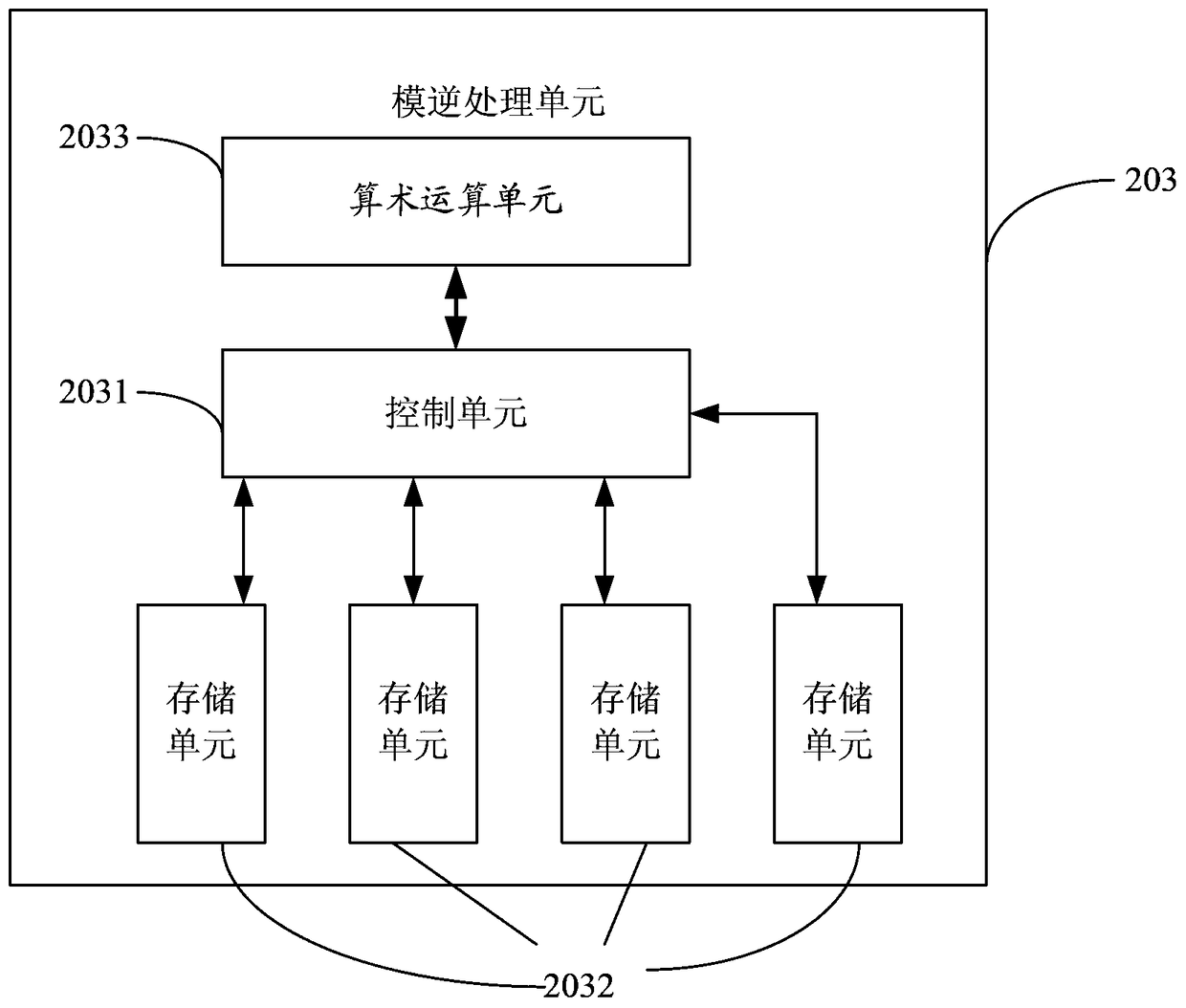
Unsigned processing method of modular inversion algorithm and modular inversion accelerator
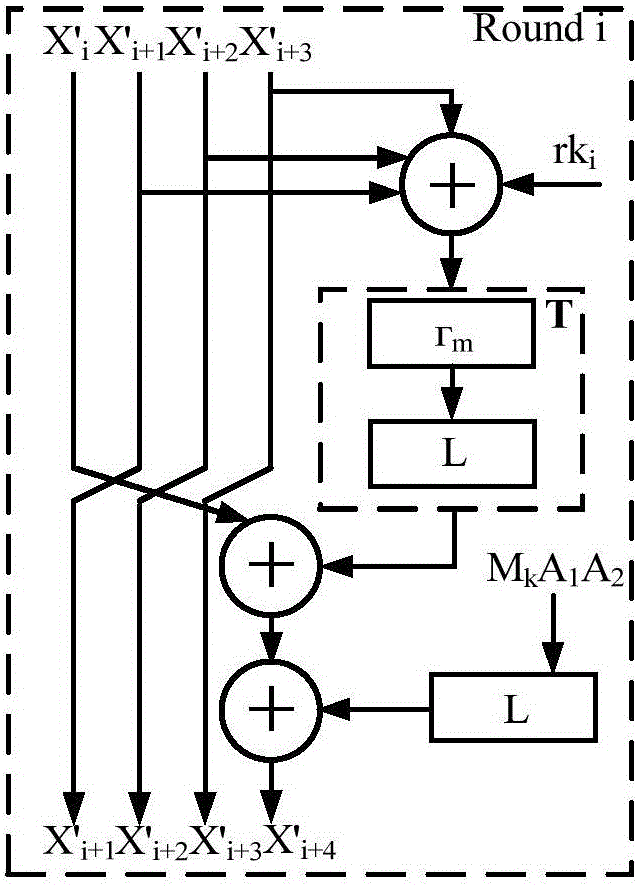
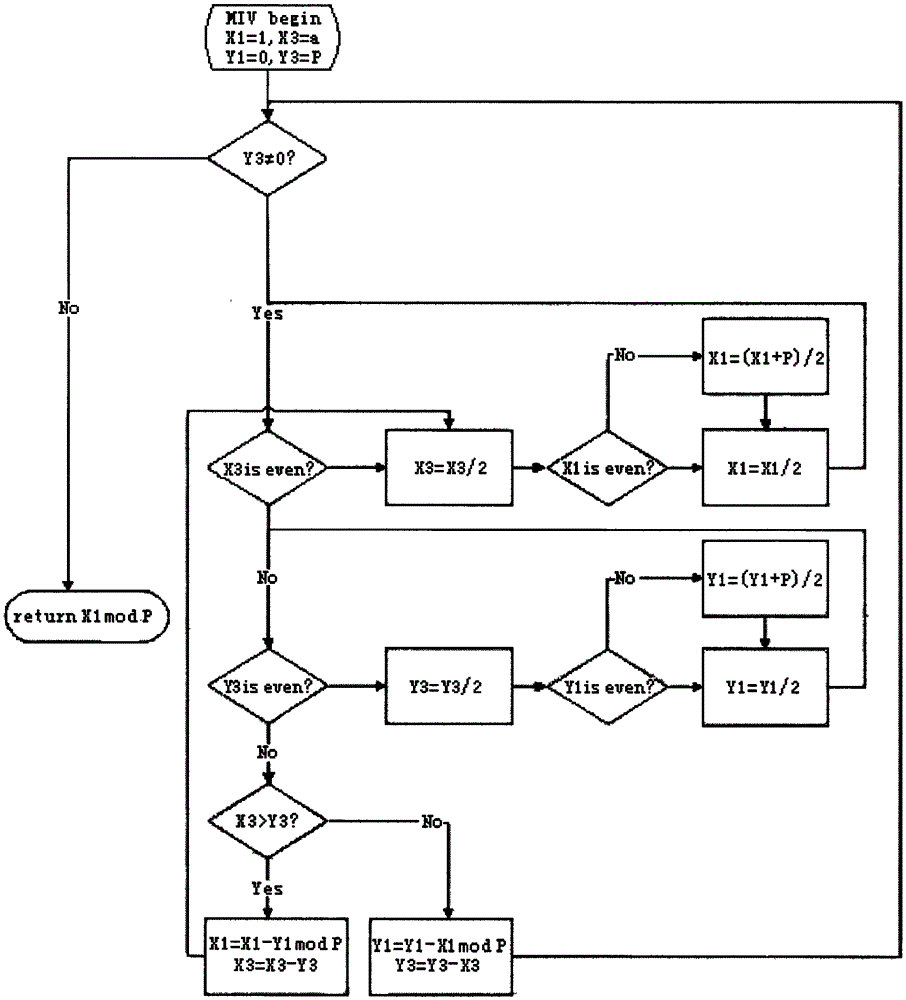
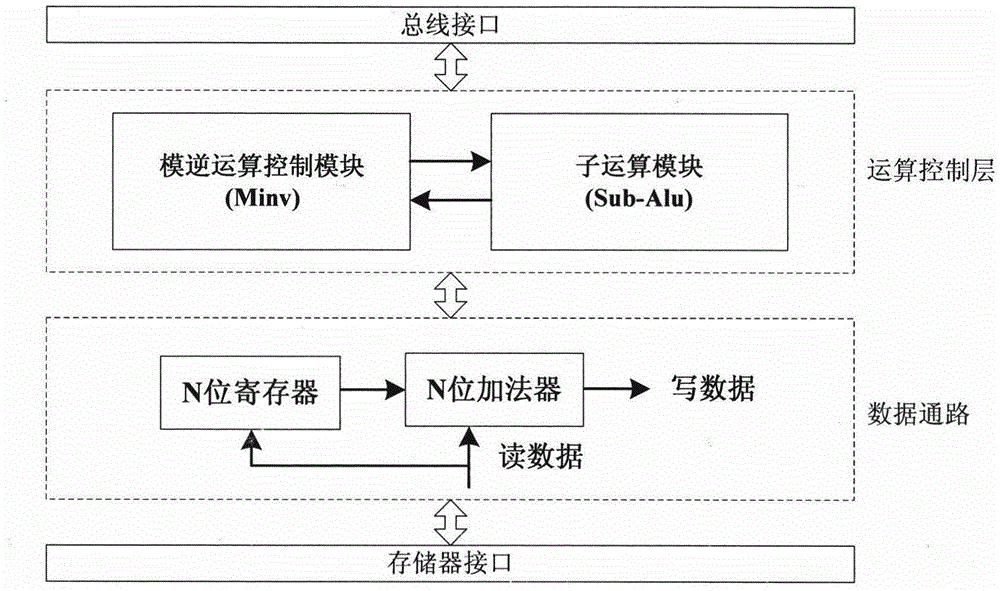
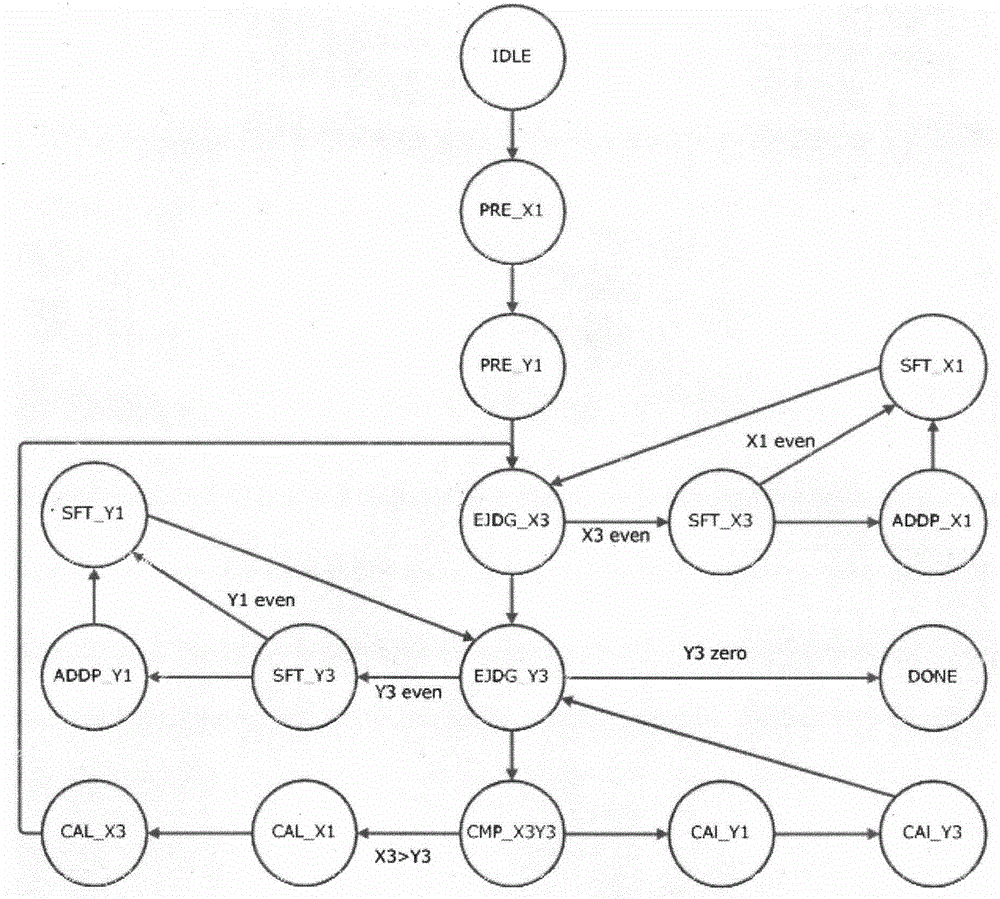
InactiveCN105577372AReduce occupancyFast operationPublic key for secure communicationModular inversionHardware circuits
The invention discloses an unsigned processing method of a modular inversion algorithm and a modular inversion accelerator. Based on the extended Euclidean algorithm in a public key cryptography algorithm, the subtraction operation in the condition 3 in the step 3 of the expanded Euclidean algorithm is replaced by the modular reduction operation. Related operation about temporary variables X2 andY2 in the condition 1 and the condition 2 in the step 3 of the expanded Euclidean algorithm is eliminated. The modular inversion accelerator comprises a bus port, an operation control layer, a data path and a memory port, which are successively connected. The operation control layer is formed by a modular inversion operation control module and a sub-operation module, which are mutually communicated. The data path is formed by an N-bit register and an N-bit summator, which are communicated to each other. In this way, a hardware circuit of the modular inversion algorithm is easy to achieve; theexpanded Euclidean algorithm is simplified; processing of symbols and carry bits in the process is eliminated; the two variables are eliminated; unnecessary operation and occupancy of a storage unit are reduced; and 1 / 3 of operation speed is increased.
Owner:杭州朔天科技有限公司
Implementation method for efficiently resisting differential power analysis of RSA
InactiveCN108173657ADoes not compromise securityAvoid modular inversionPublic key for secure communicationCryptographic attack countermeasuresPower analysisComputer architecture
The invention discloses an implementation method for efficiently resisting differential power analysis of RSA and provides an implementation instance of an RSA CRT implementation method adopting the method. According to the scheme, complex modular inversion in a traditional blind scheme is avoided, and the modular inversion is replaced by modular multiplication which is easy to achieve, the RSA operation efficiency can be greatly improved on the premise that the safety is not influenced, and the time and the space for RSA implementation are saved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT +1
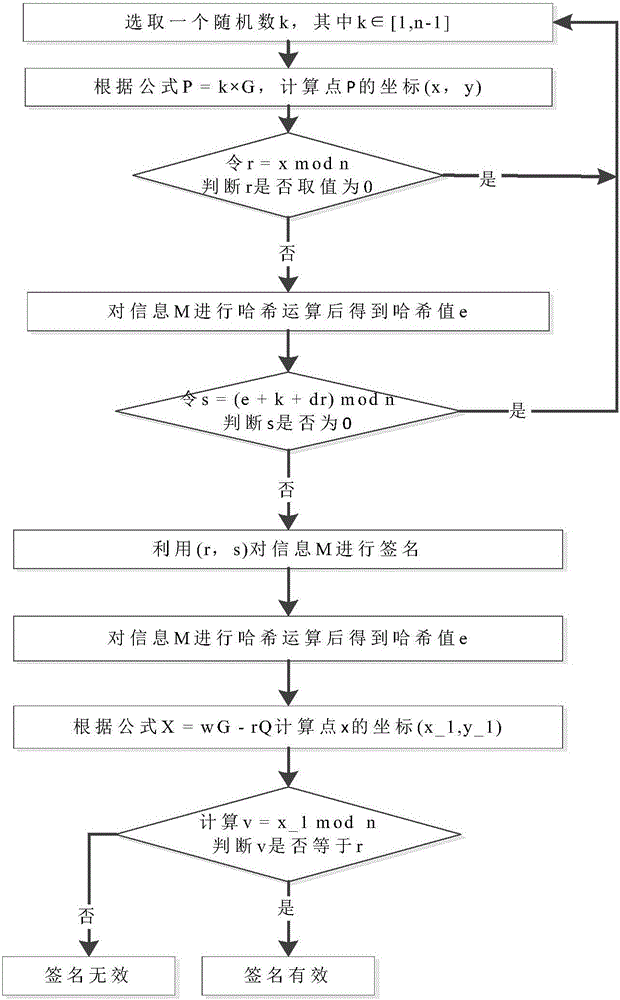
Elliptical digital signature curve hardware implementation method and system based on high-performance modular inversion
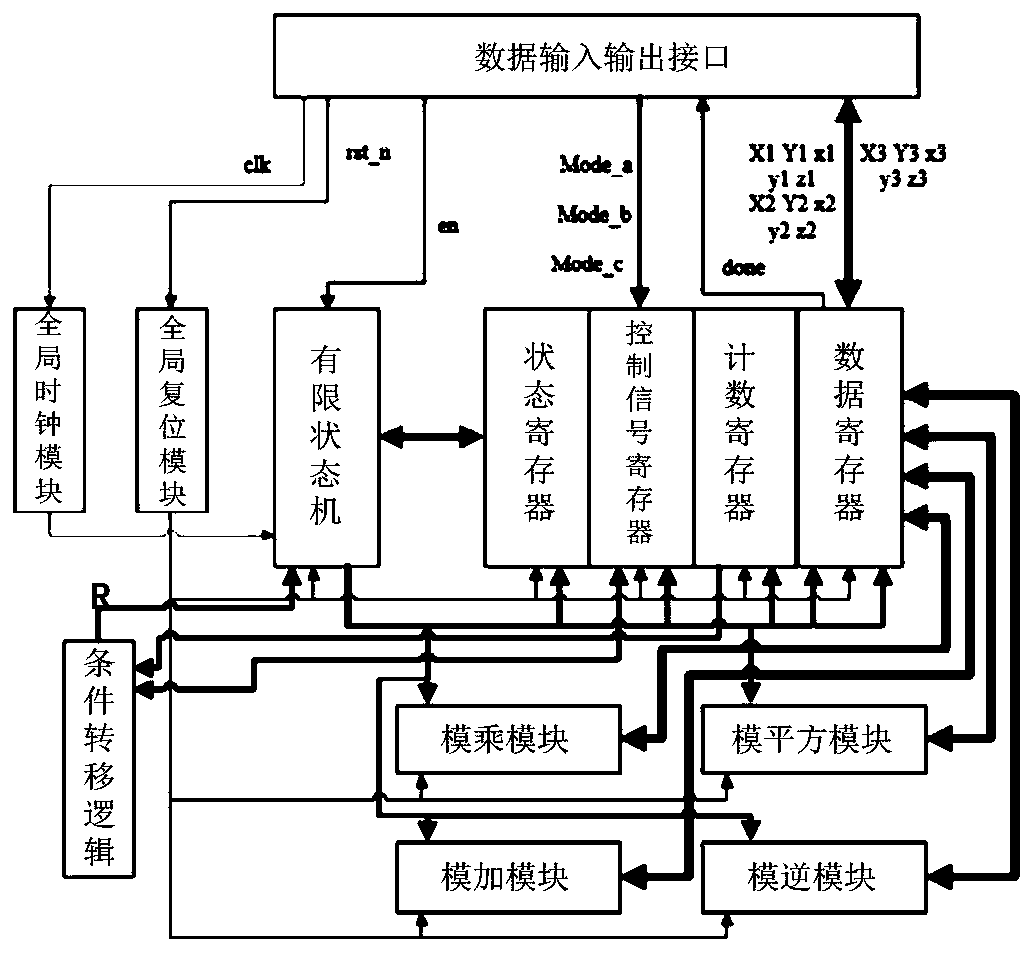
PendingCN114553425AImprove performanceFlexible adjustmentPublic key for secure communicationUser identity/authority verificationComputer hardwareAlgorithm
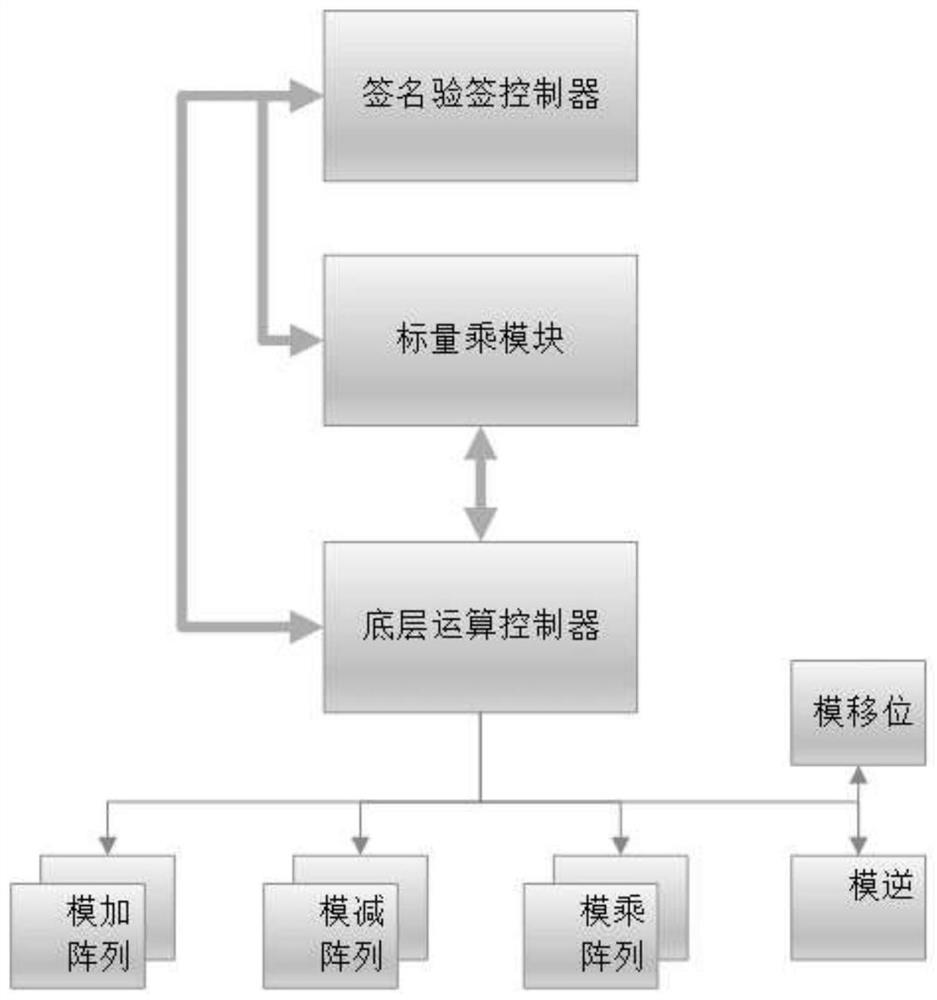
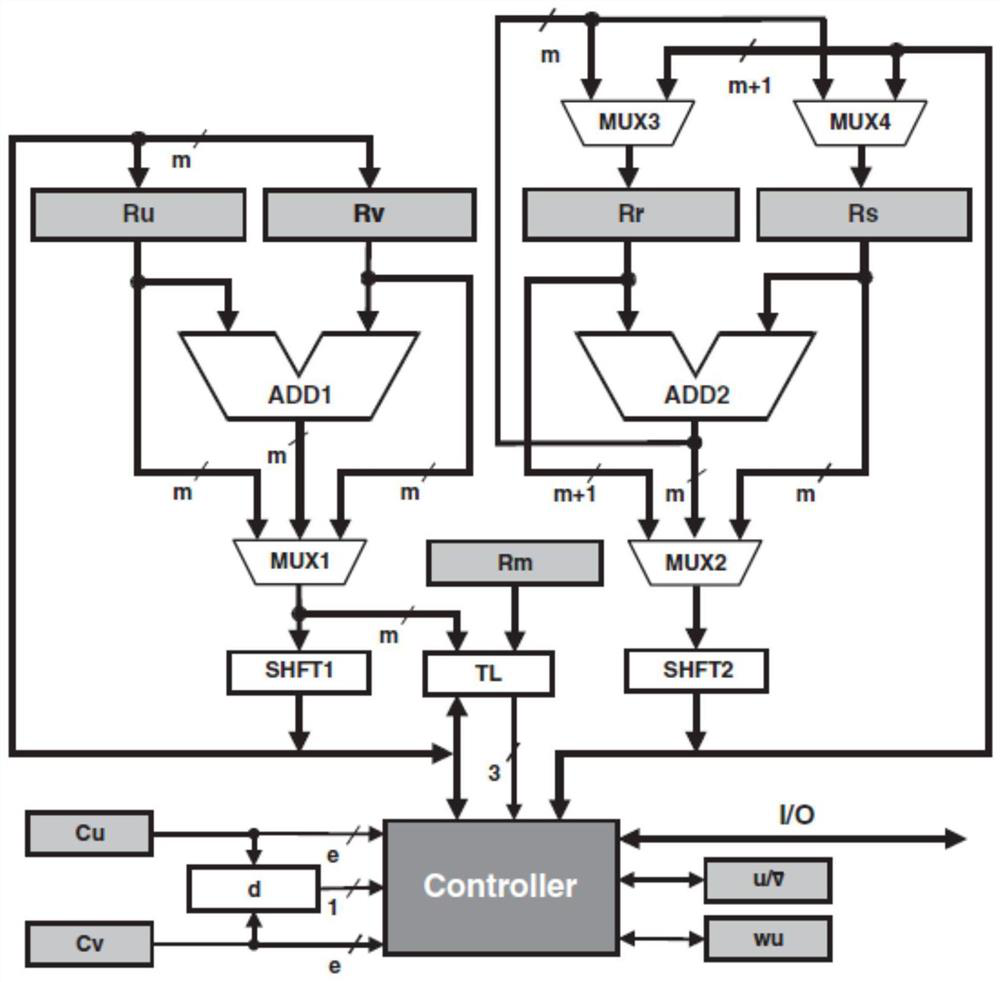
The invention provides an elliptic curve digital signature hardware implementation method and system based on high-performance modular inversion, and realizes a complete elliptic curve digital signature hardware scheme. The system comprises three parts: a signature verification control module, a scalar multiplication module and a bottom modular operation controller. According to the method, the Euclidean algorithm is improved and expanded to conform to the characteristics of hardware circuit operation, the cost of subtraction and large number comparison in hardware is avoided, multiple odd-even shift judgment in Montgomery modular inversion is not needed, and the method has the characteristics of high performance and low hardware cost. According to the method, point addition, point doubling, modular multiplication operation, modular addition operation, modular subtraction operation, modular inversion operation and other underlying operations are integrated to be called by a higher-layer module, and the improved modular inversion algorithm in the method is combined, so that underlying resource sharing of the whole system is realized, the calculation efficiency is improved, and a high-performance elliptic curved surface digital signature and signature verification system is realized under relatively low hardware overhead.
Owner:SOUTHEAST UNIV
Method and apparatus for modular inversion for information security and recording medium with a program for implementing the method
InactiveUS7831651B2Shorten the timeShort timeDigital computer detailsSecret communicationAlgorithmInformation security
Values X and N of n bits and a parameter t are input, then Y=X2−t mod N is calculated, then an extended binary GCD algorithm is executed for Y to obtain S=y−12k mod N and k, and R=S2−(k+t=2n) is calculated for S, thereby obtaining a Montgomery inverse R=X−122n mod N of X on a residue class ring Z / NZ.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Software and hardware collaborative segmented scanning type Montgomery modular exponentiation computing system and readable storage medium
PendingCN114138235AImplement modular exponentiationEfficient implementation of modular multiplication operationsComputations using residue arithmeticComputer architectureStatic random-access memory
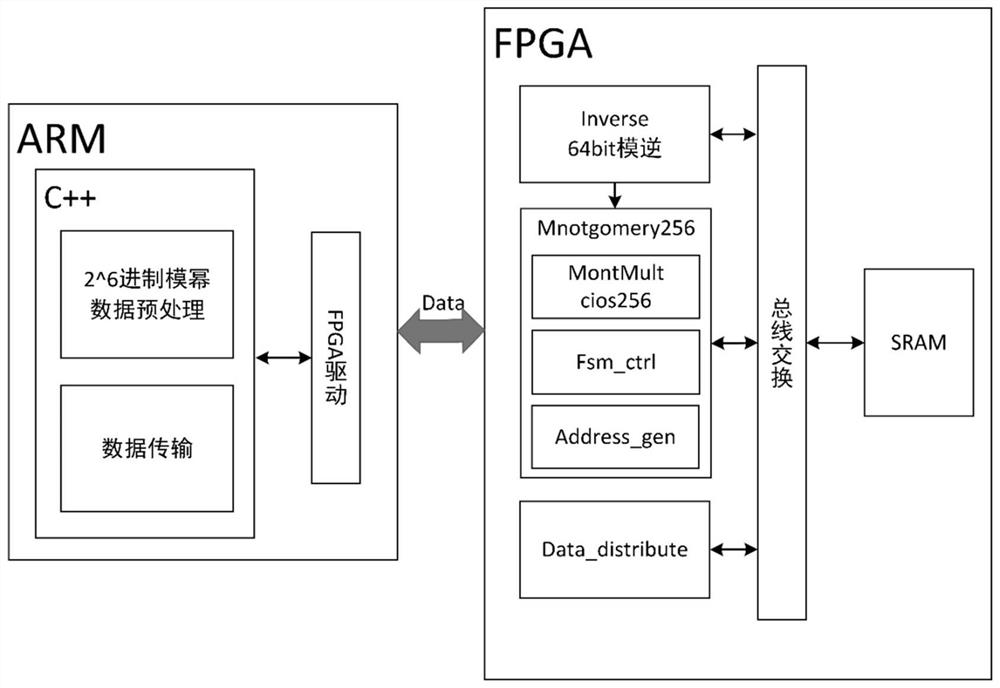
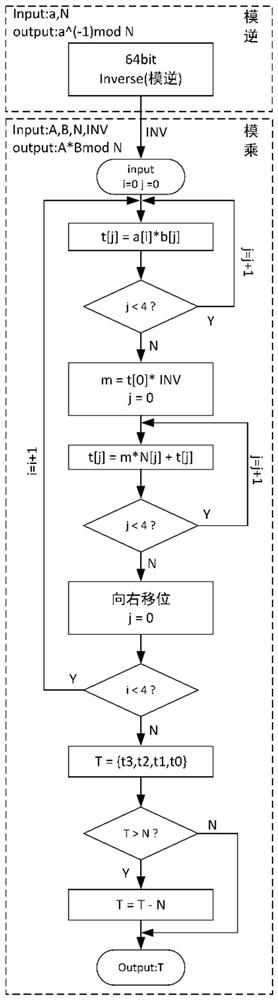
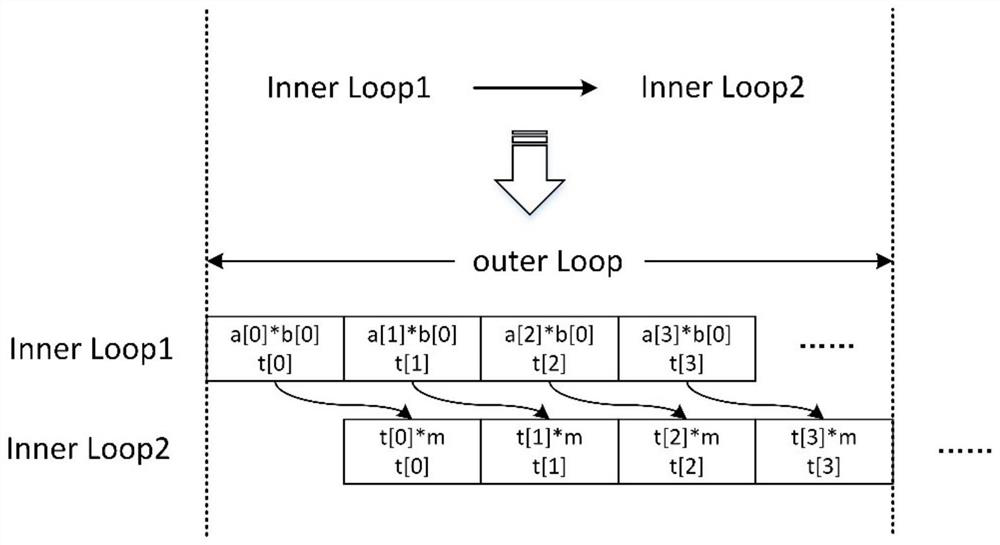
The invention provides a soft and hard collaborative segmented scanning type Montgomery modular exponentiation calculation system. An ARM processor and FPGA resources are arranged in the SoC platform. The ARM end is mainly used for overall task scheduling and data preprocessing necessary for a system segmentation scanning algorithm. Storing the processed data into a specific address of an SRAM (Static Random Access Memory), and then starting an FPGA (Field Programmable Gate Array) for operation. The FPGA end realizes modular design and comprises an address generation module, a modular inversion module, a CIOS Montgomery modular multiplication module, a segmented scanning type Montgomery modular exponentiation control module and the like. According to the invention, 256-bit modular exponentiation is realized, a 6-bit segmented scanning mode is adopted, and data to be pre-processed is stored in an SRAM (Static Random Access Memory). Specifically, the Montgomery modular multiplication module is realized by adopting a CIOS algorithm, large-bit-width 256-bit multiplication is subjected to 64-bit splitting, the area consumption caused by the large-bit-width multiplication is reduced, meanwhile, the CIOS algorithm is optimized in the streamlined aspect, two original internal loops are subjected to streamlined processing, the two internal loops are completed only by increasing a small number of periods, and the execution efficiency is improved.
Owner:NANJING UNIV
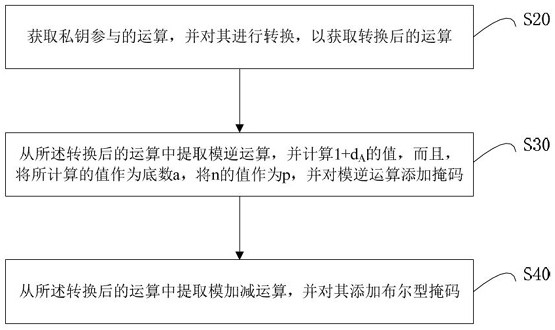
Method and device for defending side channel attack and readable storage medium
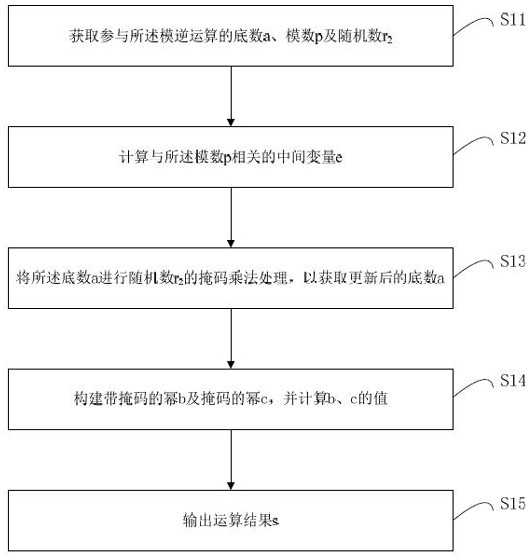
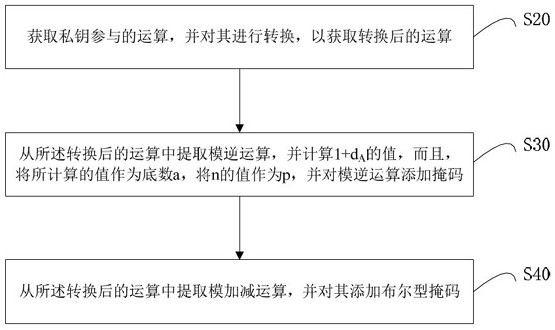
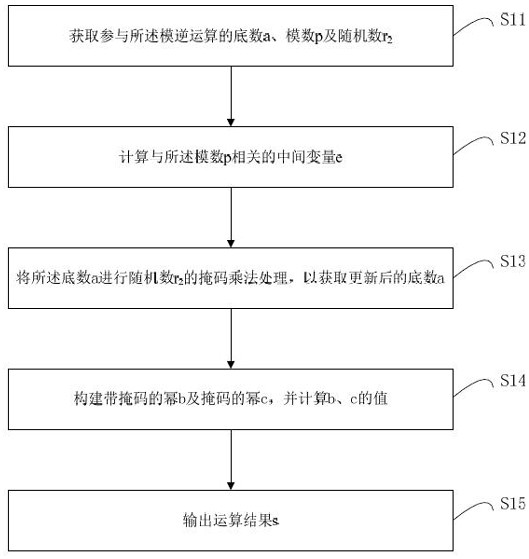
ActiveCN111931176ADefense against simple power consumption attacksDefense against Differential Power AttacksPlatform integrity maintainanceAlgorithmInverse operation
The invention relates to a method and device for defending a side channel attack, and a readable storage medium. The method, when adding a mask to modular inversion operation, comprises the followingsteps: obtaining a base number a, a modulus p and a random number r2 participating in modular inverse operation; calculating an intermediate variable e related to the modulus p according to e = p-2; performing mask multiplication processing of the random number r2 on the base number a to obtain an updated base number a; respectively constructing the power b = aemodp with a mask and the power c = r2emodp with a mask, and calculating the values of b and c; and outputting an operation result s according to s = b * cmodp. By implementing the technical scheme of the invention, simple power consumption attacks and differential power consumption attacks can be resisted.
Owner:网御安全技术(深圳)有限公司
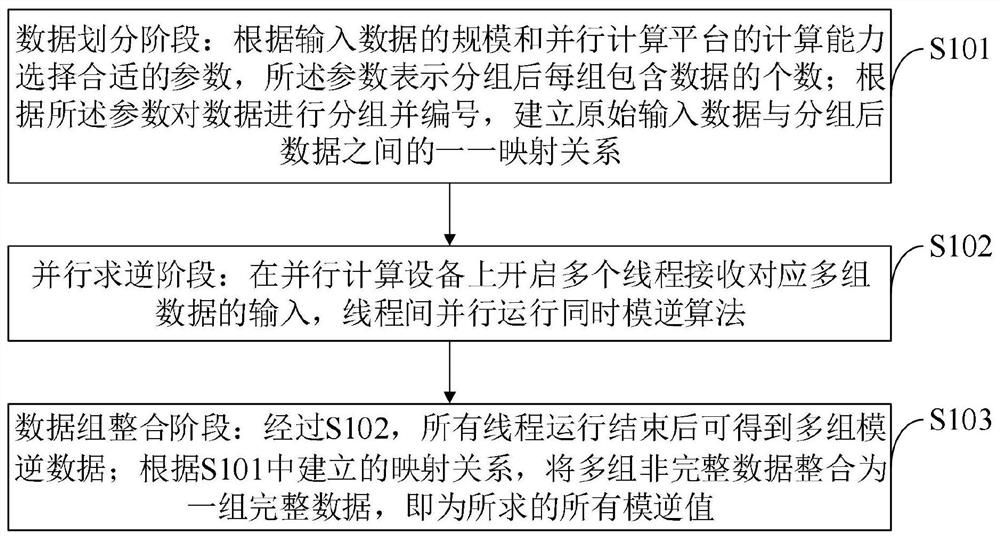
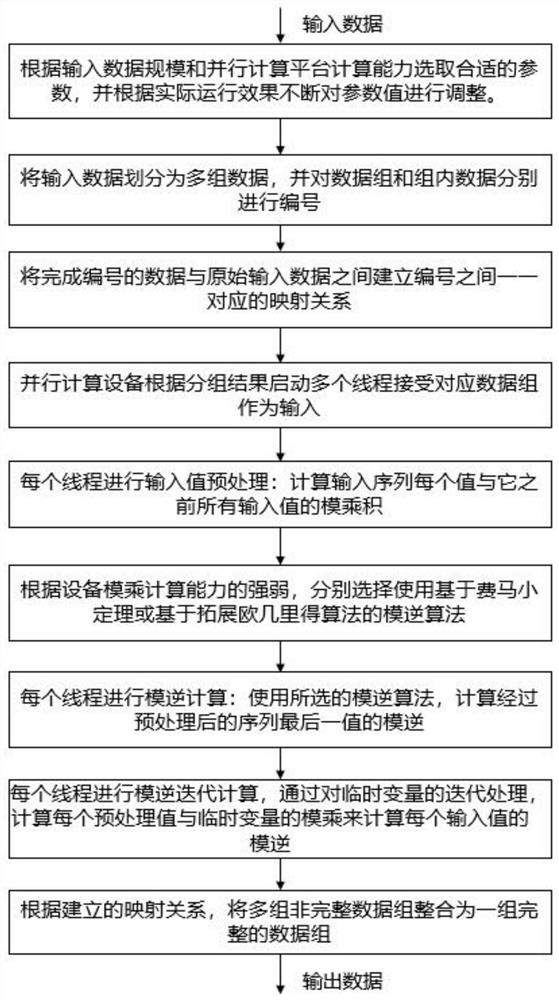
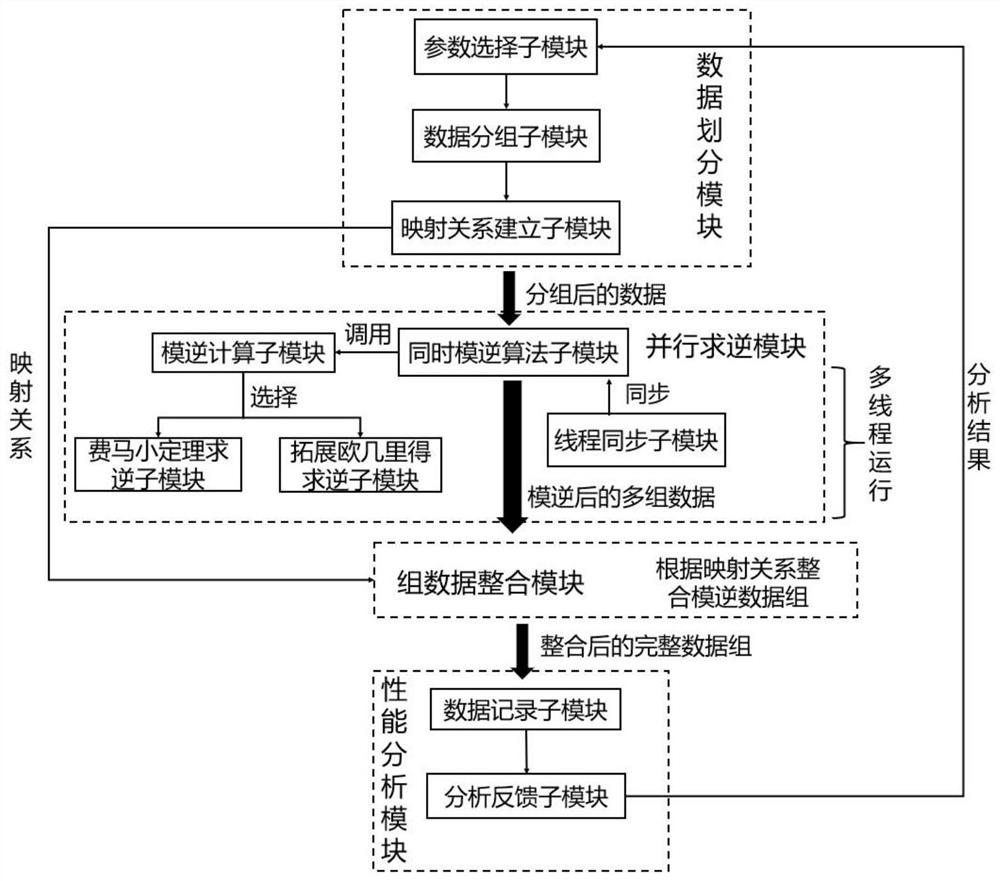
High-throughput modular inversion calculation method and system in parallel environment
ActiveCN112799637AImprove throughputAlleviate the phenomenon of high concurrency mode reverse time warp differentiationDigital data protectionComputations using residue arithmeticData setAlgorithm
The invention belongs to the technical field of information security, and discloses a high-throughput modular inversion calculation method and system in a parallel environment. M to-be-inversed values (a1, a2, ..., am) and a modulus p are received, m modular inversion values are output, wherein the processes comprise three stages: a data division stage, a parallel inversion stage and a data group integration stage. The high-throughput modular inversion computing system in the parallel environment comprises a data division module based on parallel platform computing resources, a parallel inversion module based on a simultaneous modular inversion algorithm, a data set integration module based on a mapping relation and a performance analysis module based on a historical operation result. According to the method, the characteristic that modular inverse operation is converted into modular multiplication operation through the simultaneous modular inverse algorithm is utilized, so that the high-concurrency modular inverse time thread beam differentiation phenomenon is relieved, and the parallel simultaneous modular inverse algorithm is designed for solving the problem that the serial simultaneous modular inverse algorithm cannot give full play to all performance of a parallel platform. Therefore, the modular inverse operation throughput in the parallel environment is greatly improved.
Owner:XIDIAN UNIV
Modular inverse operating method and operational unit
InactiveCN107239258AReduce power consumptionVersatilityComputations using residue arithmeticExtended Euclidean algorithmHardware implementations
The invention relates to a modulo inversion operation method and an arithmetic unit. The positive integers u and m are known, and u‑1modm is calculated. In the modular inverse operation method and arithmetic unit provided by the present invention, the algorithm only needs to add one flag bit, and at most one multiplication and two subtraction operations, which can greatly improve the operation speed, and has the characteristics of versatility and high efficiency in terms of hardware implementation; Compared with the existing binary extended Euclidean algorithm, there is no need to eliminate the weight factor of the operation result, and the modulus is not limited to be an odd number, and the modulus inverse operation of any non-zero integer can be realized, and Improve the computational efficiency of modular inverse operations and reduce hardware power consumption.
Owner:张家豪
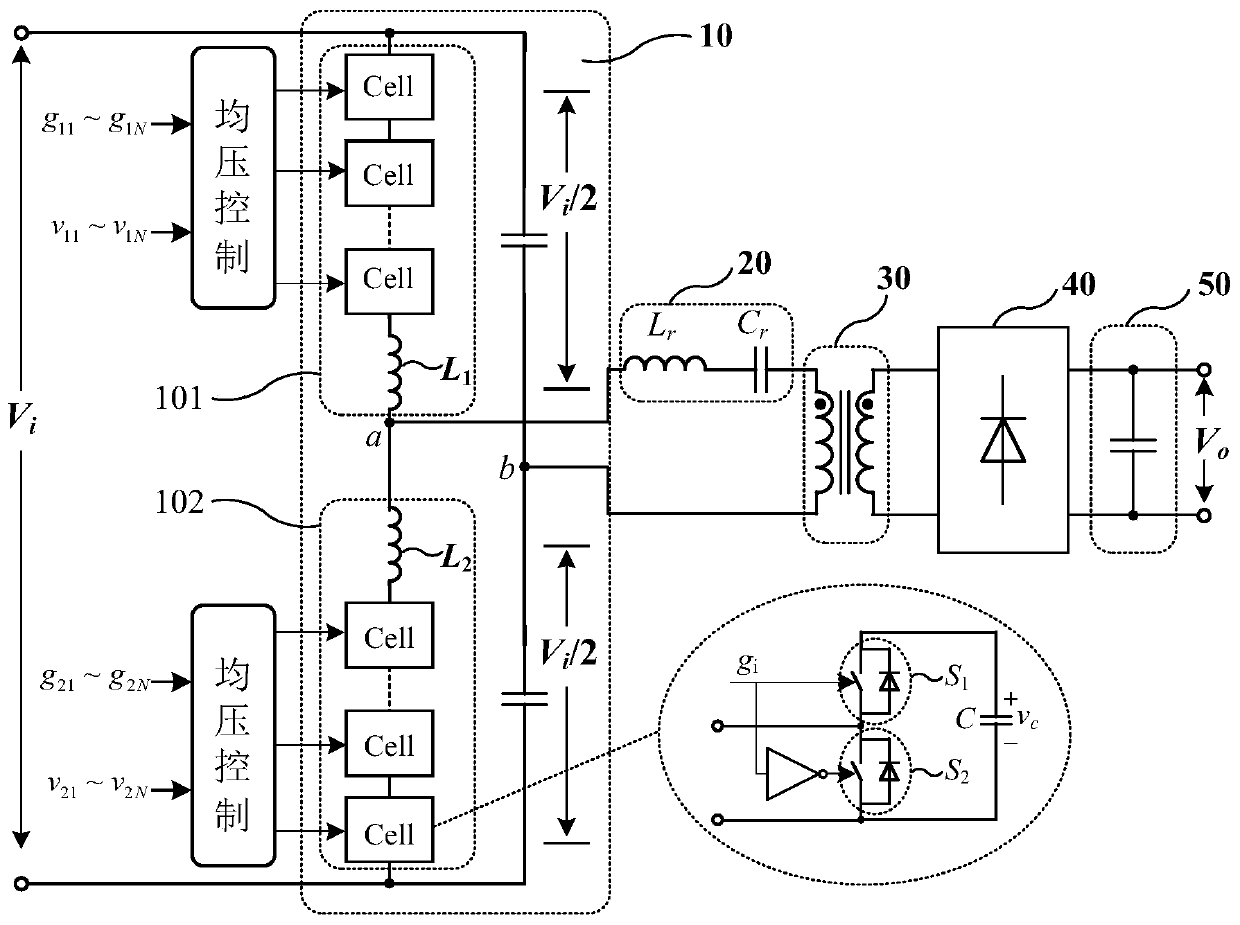
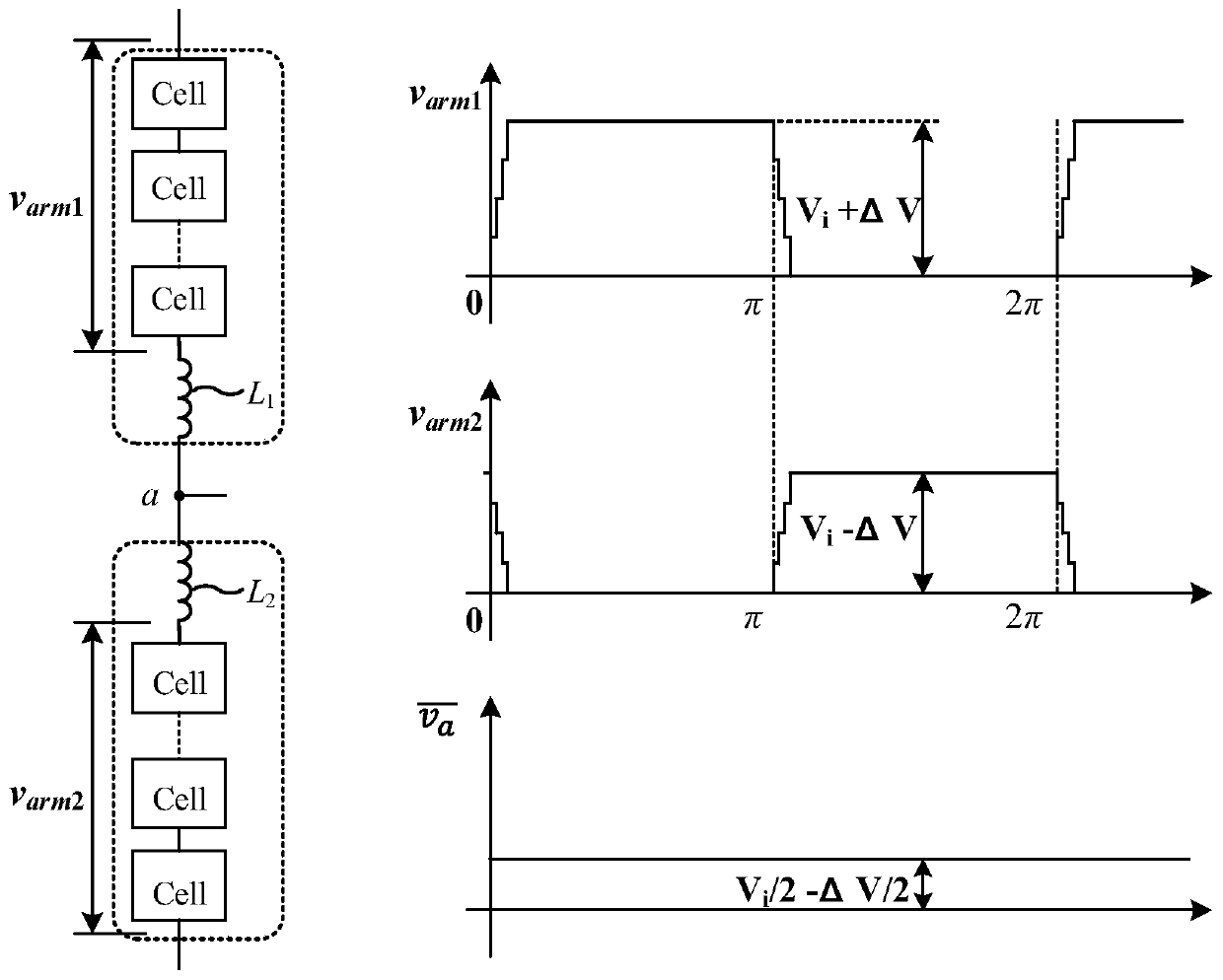
Bridge arm voltage-sharing control method of modular multilevel resonant converter
ActiveCN110350798ADo not change the normal working stateVoltage balanceEfficient power electronics conversionAc-dc conversionVoltage amplitudeCapacitance
The invention relates to a DC-DC conversion technology, and aims to provide a bridge arm voltage-sharing control method of a modular multilevel resonant converter. The modular multilevel resonant converter comprises a modular inversion circuit, a resonant network, a transformer, a rectifier and an output capacitor. Bridge arm voltage-sharing control is in a way that voltage amplitudes of an upperbridge arm and a lower bridge arm is balanced by adjusting DC components of middle-point voltages of the bridge arms. According to the voltage-sharing control method provided by the invention, the DCcomponents of the middle-point voltages of the bridge arms are controlled, the voltage distribution of the upper bridge arm and the lower bridge arm is automatically corrected by closed-ring control on the premise that a switch frequency is not adjusted, the voltage balance of the upper bridge arm and the lower bridge arm is maintained, and meanwhile, the normal working state of MMR is not changed. By the control method, the inductance values of the bridge arms are not needed to be adjusted by manual, the bridge arm voltage automatic balance of the modular multilevel resonant converter is achieved by control, and the converter is enabled to stably and reliably work.
Owner:ZHEJIANG UNIV
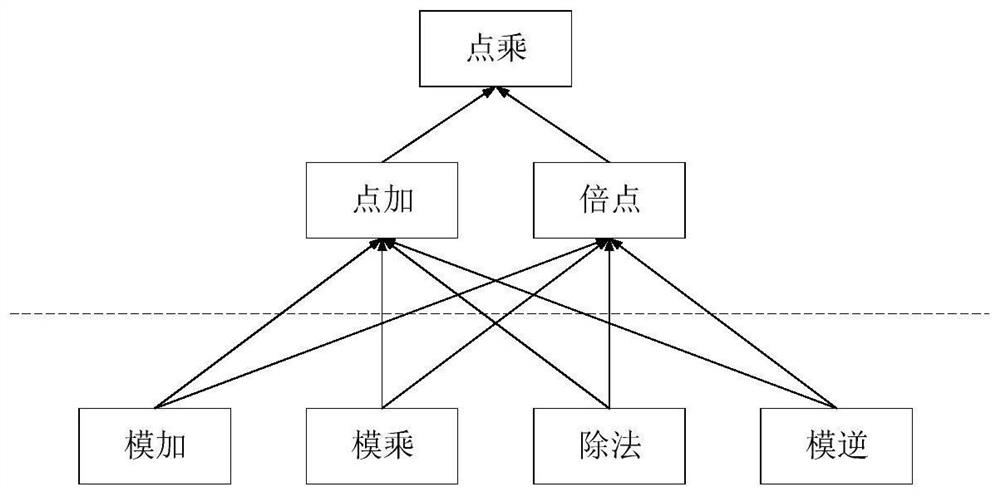
Double-domain elliptic curve dot product hardware accelerator
PendingCN111835517AImprove the efficiency of core operation dot multiplicationIncrease flexibilityPublic key for secure communicationComputer hardwareComputer architecture
A double-domain elliptic curve dot product hardware accelerator is divided into a modular operation layer and a point operation layer, wherein the modular operation layer comprises a prime number domain and binary domain modular modular reduction module, a multiplication module and a modular inversion module, and the point operation layer comprises a prime number field NAF dot product operation module and a multiple point and point addition and binary system field dot product module. The hardware accelerator is mounted on an equipment bus as slave equipment and is connected to a processor, andthe processor realizes different acceleration operation modes by configuring a function register in the hardware accelerator.
Owner:YICHIP MICROELECTRONICS (HANGZHOU) CO LTD
Quick encryption system based on base-4 binary system underlying modular operation
ActiveCN110493003AFast additionFast operationUser identity/authority verificationComputer moduleNumber generator
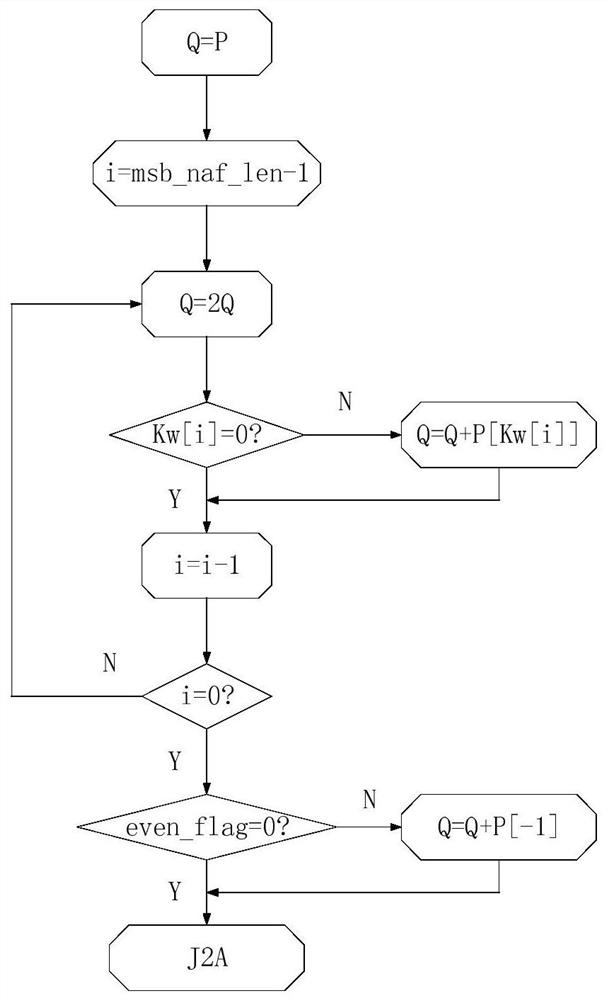
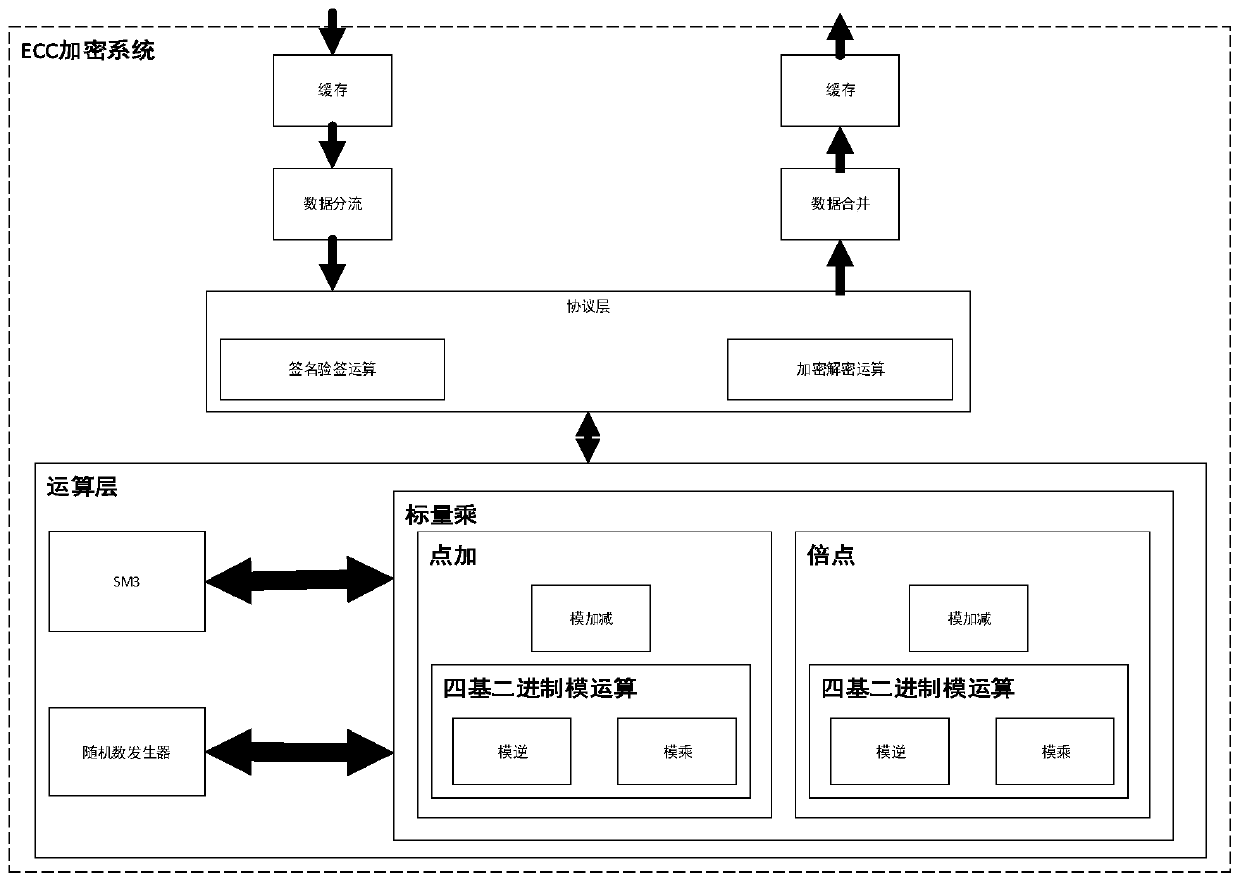
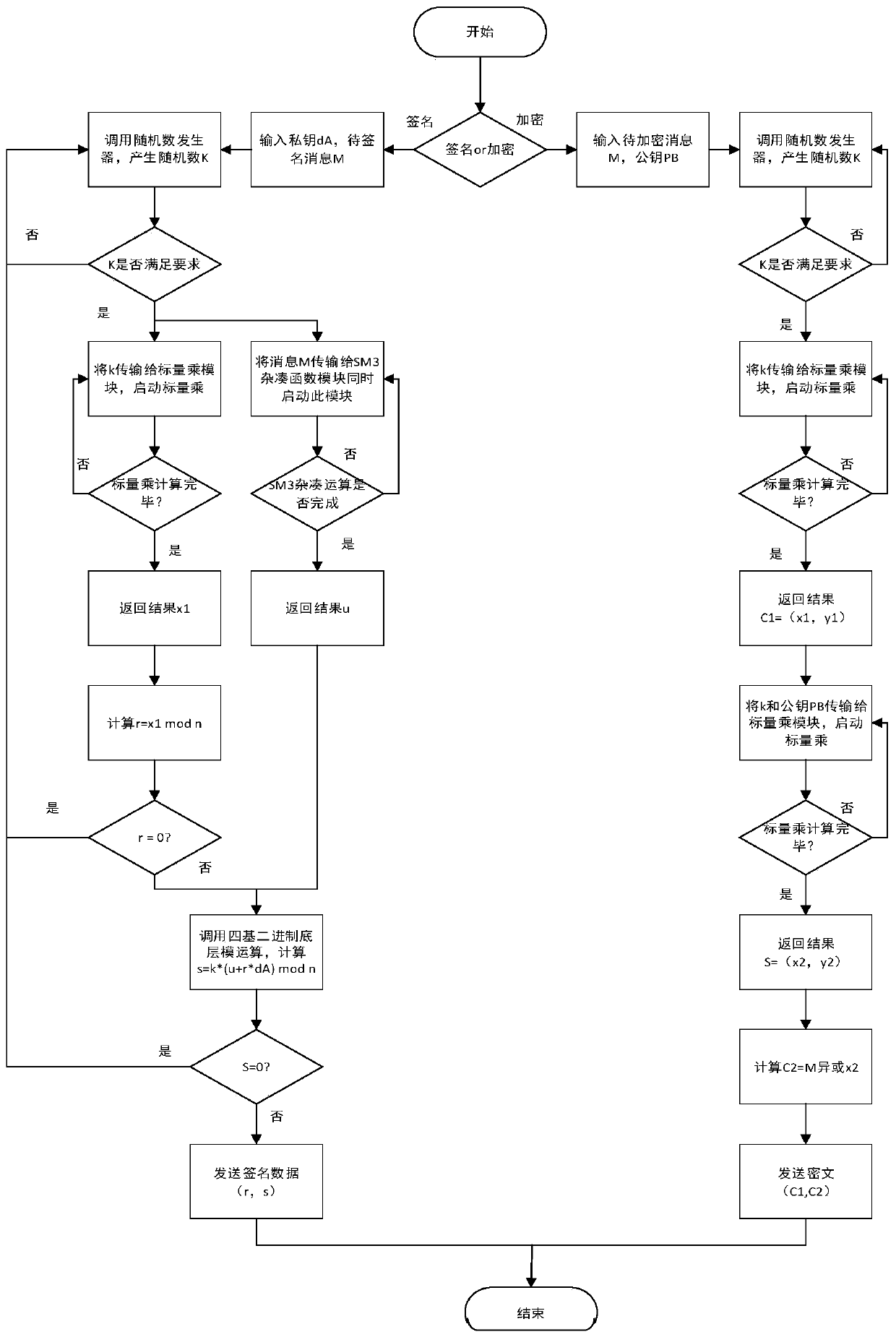
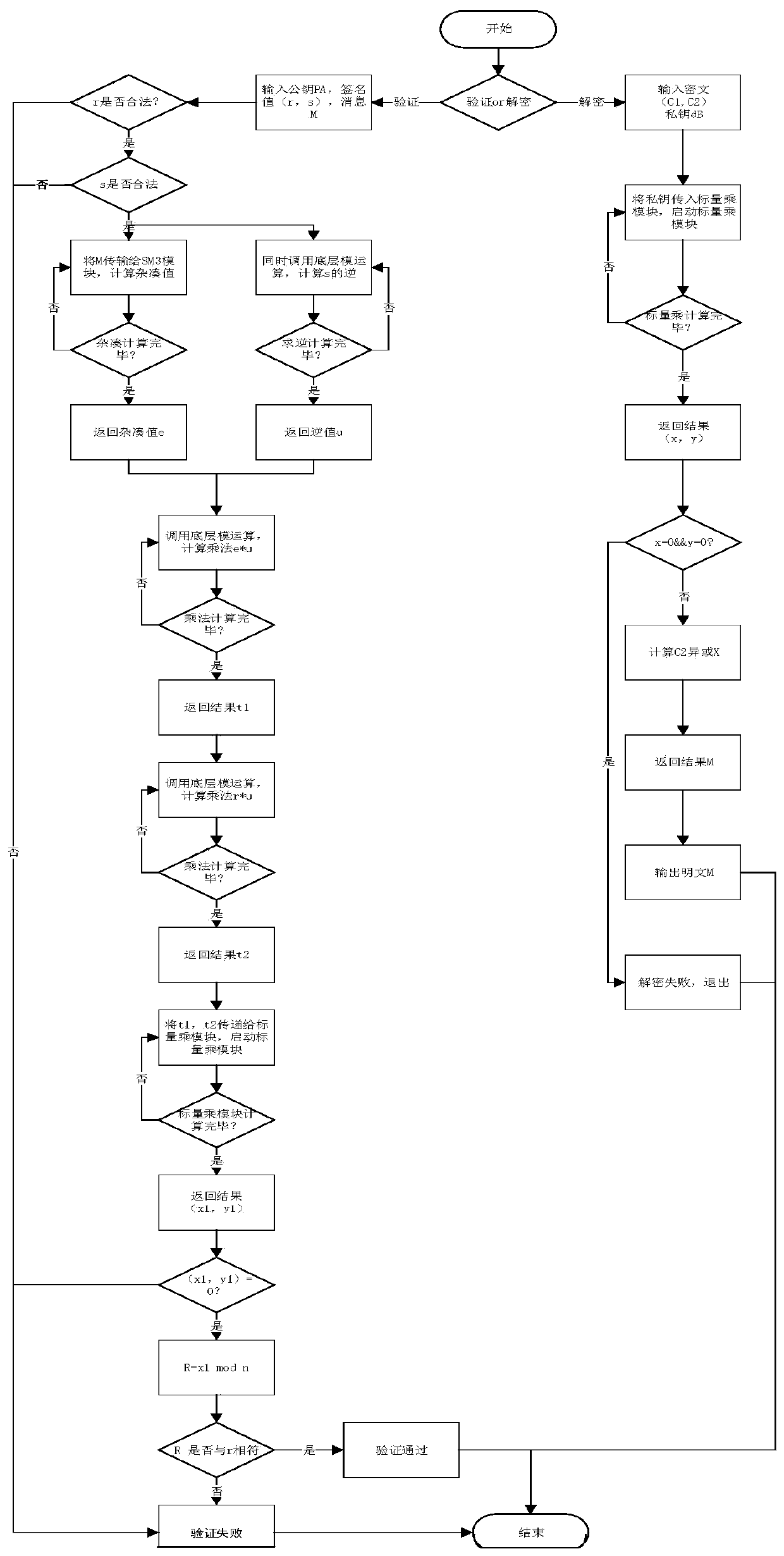
The invention discloses a quick encryption system based on base-4 binary system underlying modular operation. The system comprises a protocol layer for realizing signature verification and encryptionand decryption functions of the system, an operation layer used for realizing curve domain arithmetic and prime number domain modular operation; wherein the operation layer comprises a scalar multiplication module, the scalar multiplication module is connected with an SM3 module used for carrying out hash operation and a random number generator used for generating random numbers, and the scalar multiplication module comprises a point addition module and a point multiplication module and is used for realizing modular inversion, modular multiplication and modular addition and subtraction operation; according to the scheme, the bottom-layer modular operation of the elliptic curve encryption system is improved, so that the quick encryption system based on the four-base binary bottom-layer modular operation is realized, and the scheme is mainly characterized in that the four-base binary quick modular operation is introduced into the elliptic curve encryption system, so that the operation efficiency of the encryption system is improved.
Owner:GUANGDONG UNIV OF TECH
A method and system for implementing a signature verification algorithm based on sm2 elliptic curves
ActiveCN107040385BReduce the number of point addition operationsShorten operation timeUser identity/authority verificationGeneration processDigital signature
The invention relates to a realization method and system of a signature verification algorithm based on an SM2 elliptic curve. The system, under control of an SM2 control module, realizes generation and verification of digital signatures by communicating with a signature generation control module and a signature verification control module, and calling a random number generation module, a password hash module, a point multiplication operation module, a point addition operation module, a modulo addition operation module, a modulo subtraction operation module, a modular multiplication operation module and a modular inversion operation module. In the digital signature generation and verification process, point multiplication operation adopts an improved partly use 1's complement subtraction form point multiplication algorithm (PCS algorithm); and in the signature generation process, modular multiplication operation adopts an improved Blakley modular multiplication algorithm, and modular inversion operation and modular multiplication operation are carried out simultaneously through a parallel operation method, thereby greatly improving operation speed and reducing operation time.
Owner:GUANGDONG UNIV OF TECH
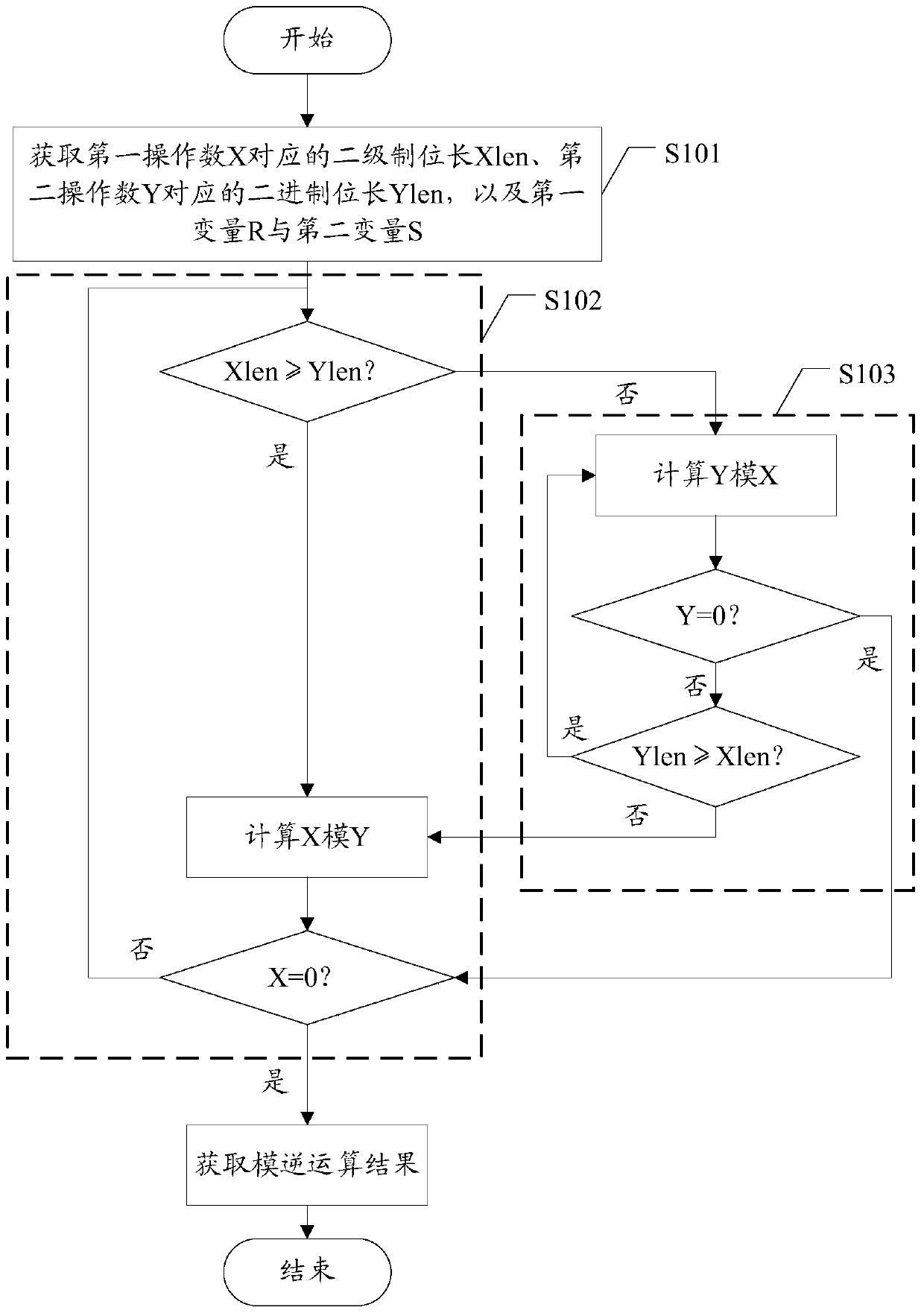
modular inverse operator
ActiveCN105988772BImprove computing efficiencyReduce power consumptionComputations using residue arithmeticOperandInverse operator
The invention provides a modular inverse operation method and an arithmetic device. The modular inversion operation method and the arithmetic device are used for calculating Z=Y<-1>mod X, wherein Z is a result of a modular inverse operation, X is a first operand and Y is a second operand. The modular inverse operation method comprises the following steps of calculating and acquiring a binary bit length Xlen of the first operand X and a binary bit length Ylen of the second operand Y; initializing a first variable R and a second variable S; when Xlen is greater than and equal to Ylen, calculating X <-1>modY; and when Xlen is smaller than and equal to Ylen, calculating Y <-1>modX. When the updated X is equal to 0 and the updated Y is equal to 1, a result of the modular inverse operation is the updated second variable S; when the updated X is equal to 1 and the updated Y is equal to 0, a result of the modular inverse operation is a difference between an X initial value and the updated first variable R; and when one of the updated X and the updated Y is equal to 0 and the other of the updated X and the updated Y is not equal to 1, a result of the modular inverse operation does not exist. By using the method and the arithmetic device, the modular inverse operation, in which the module is any non-zero integer can be realized, the calculation efficiency of the modular inverse operation is improved and the power consumption of hardware is reduced.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
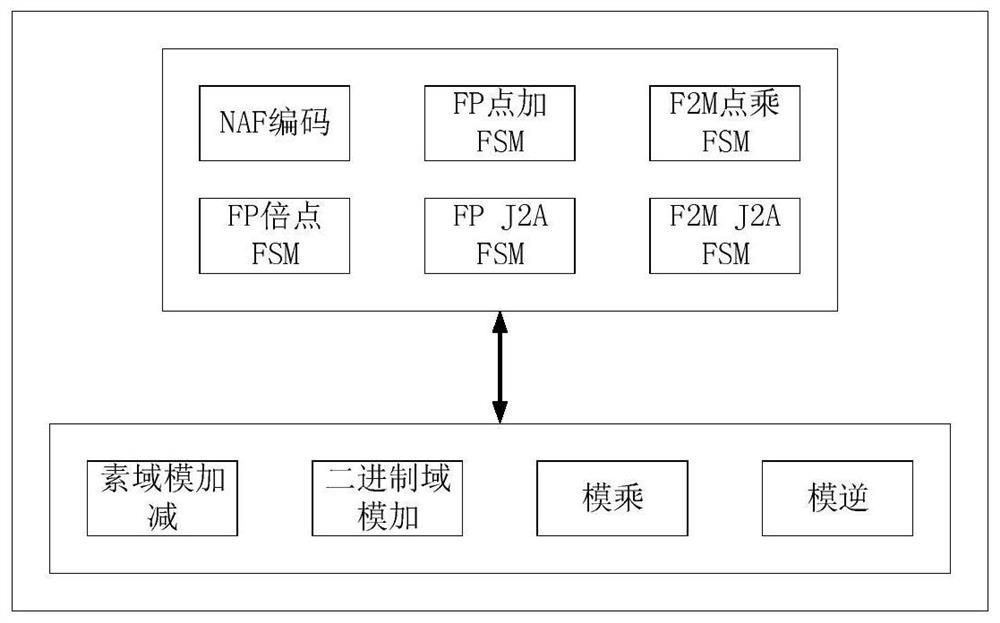
A Hardware Implementation Method of Dual Domain Modular Inversion
ActiveCN108390761BSave resourcesOptimized areaKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareHardware implementations
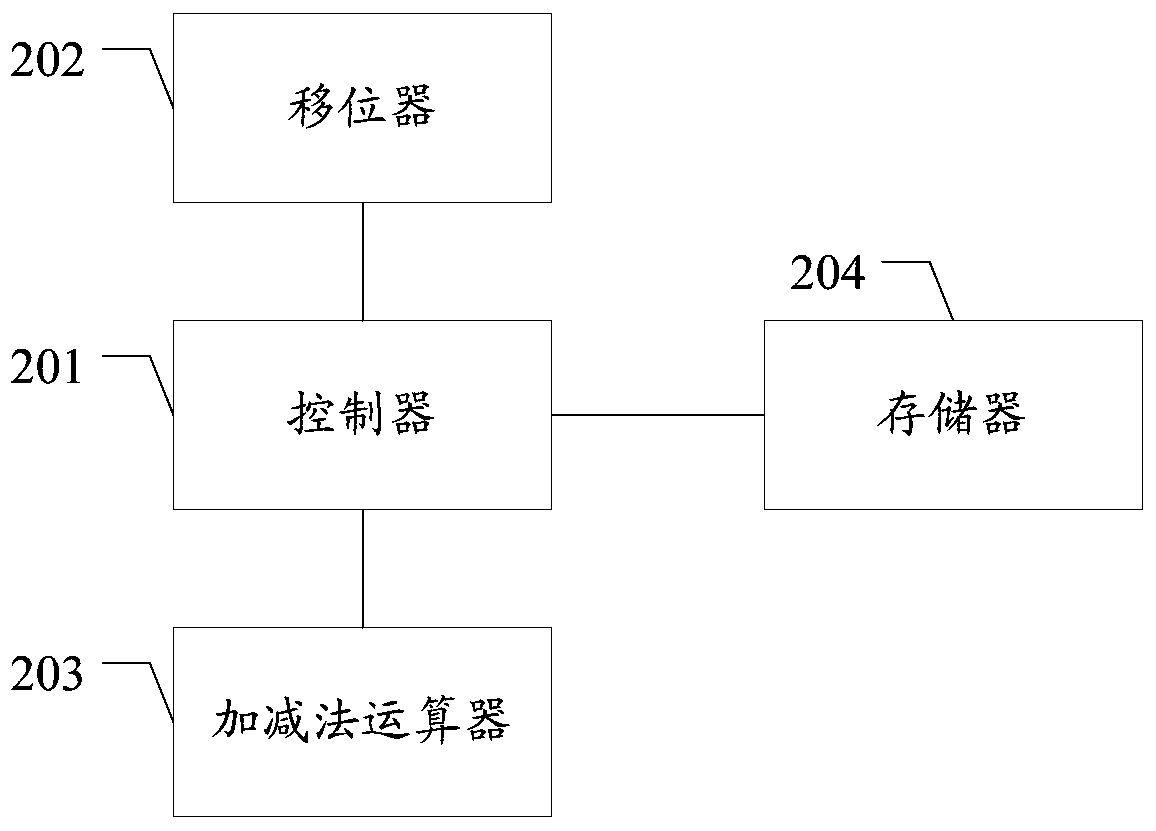
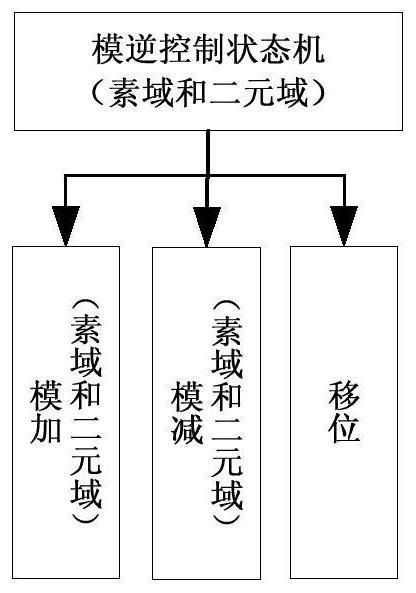
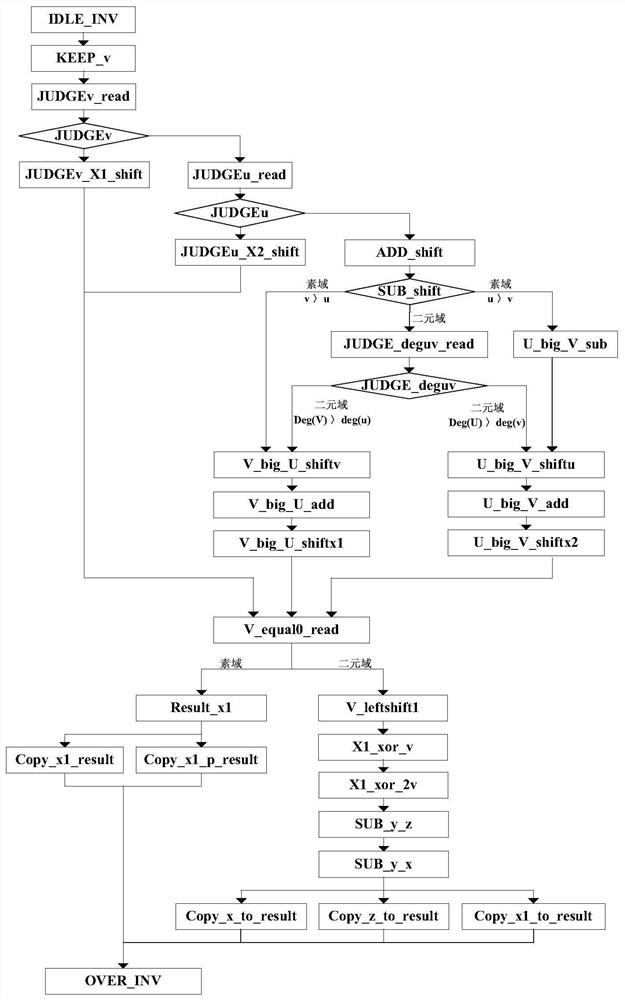
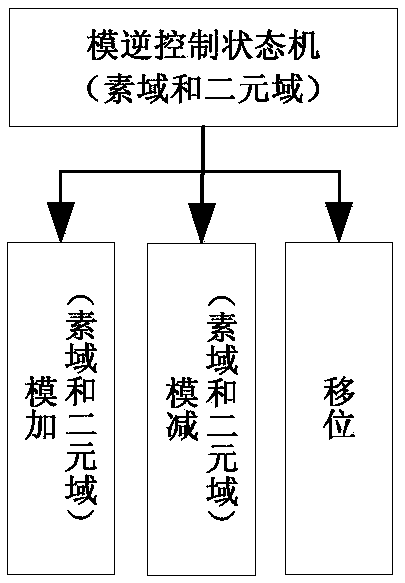
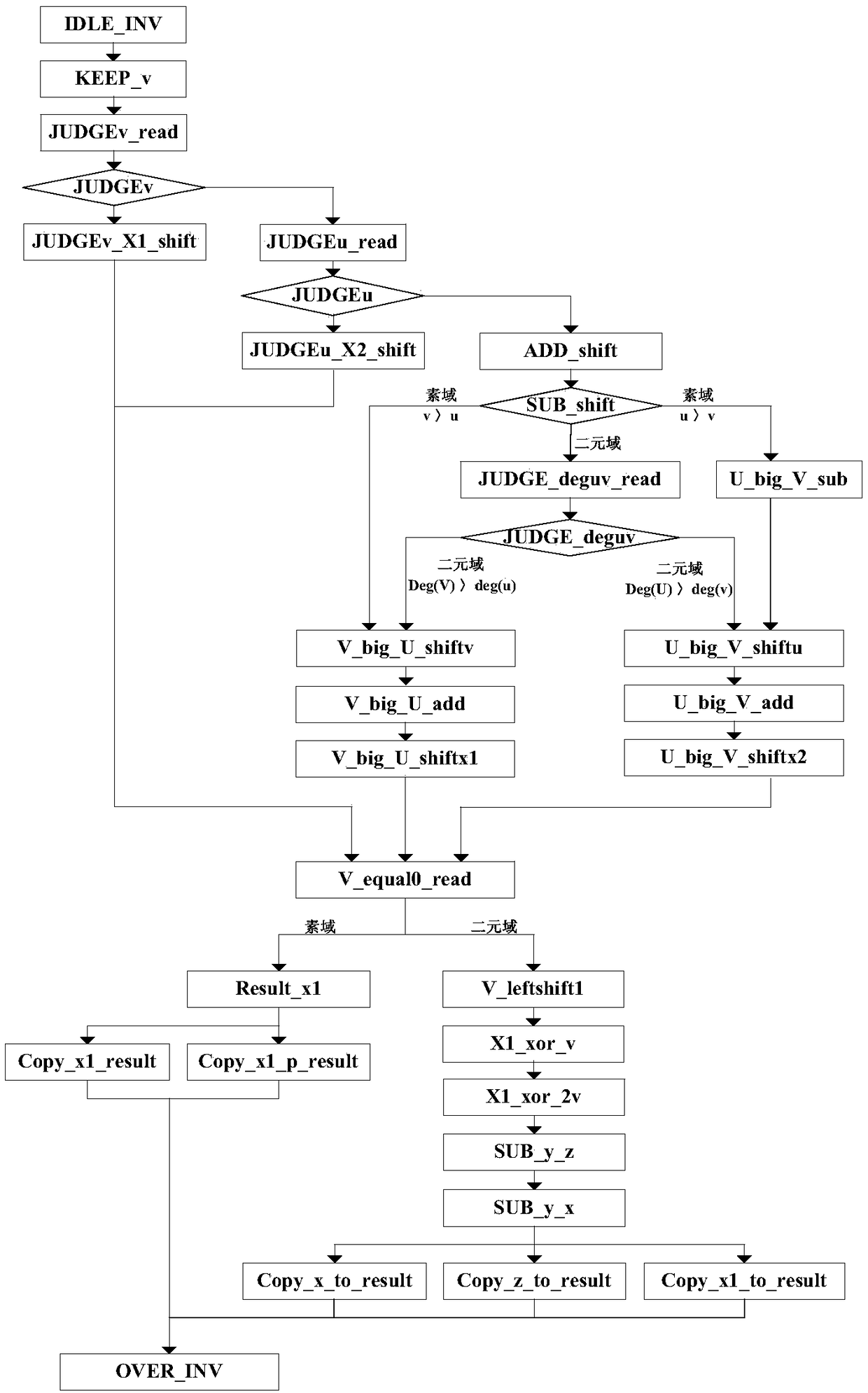
The invention discloses a hardware realization method of dual-field modular inversion, and relates to the technical field of the information security. The method comprises the following steps: constructing a modular inversion control state machine, modular addition, modular subtraction and shift operation units of two finite fields, and the modular addition, modular subtraction and shift operationunits of two finite fields are called through the modular inversion control state, and the hardware realizes the dual-field modular inversion operation of two finite fields of a prime field and a binary field. Through the method provided by the embodiment of the invention, the algorithm structures of two different finite fields can be integrated at the same time, the operation resource is efficient and reusable, the hardware resource is greatly saved, the operation speed is improved, and a hardware area is optimized.
Owner:北京万协通信息技术有限公司
Hardware realization method of dual-field modular inversion
ActiveCN108390761ASave resourcesOptimized areaKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringInformation security
The invention discloses a hardware realization method of dual-field modular inversion, and relates to the technical field of the information security. The method comprises the following steps: constructing a modular inversion control state machine, modular addition, modular subtraction and shift operation units of two finite fields, and the modular addition, modular subtraction and shift operationunits of two finite fields are called through the modular inversion control state, and the hardware realizes the dual-field modular inversion operation of two finite fields of a prime field and a binary field. Through the method provided by the embodiment of the invention, the algorithm structures of two different finite fields can be integrated at the same time, the operation resource is efficient and reusable, the hardware resource is greatly saved, the operation speed is improved, and a hardware area is optimized.
Owner:北京万协通信息技术有限公司
Modular inversion that is protected against espionage
InactiveUS7474748B2Reduce sensitivityPublic key for secure communicationUser identity/authority verificationModularityComputer module
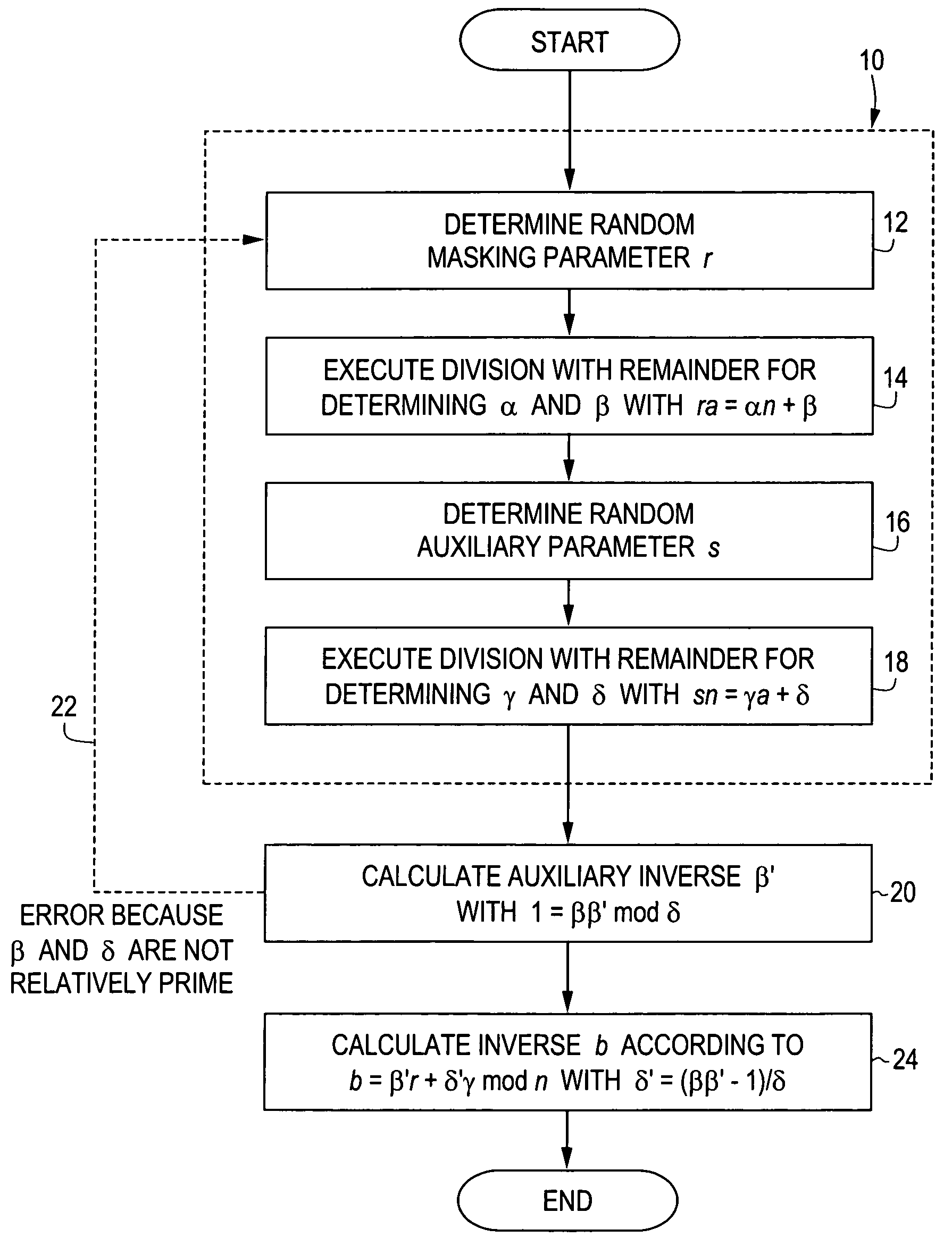
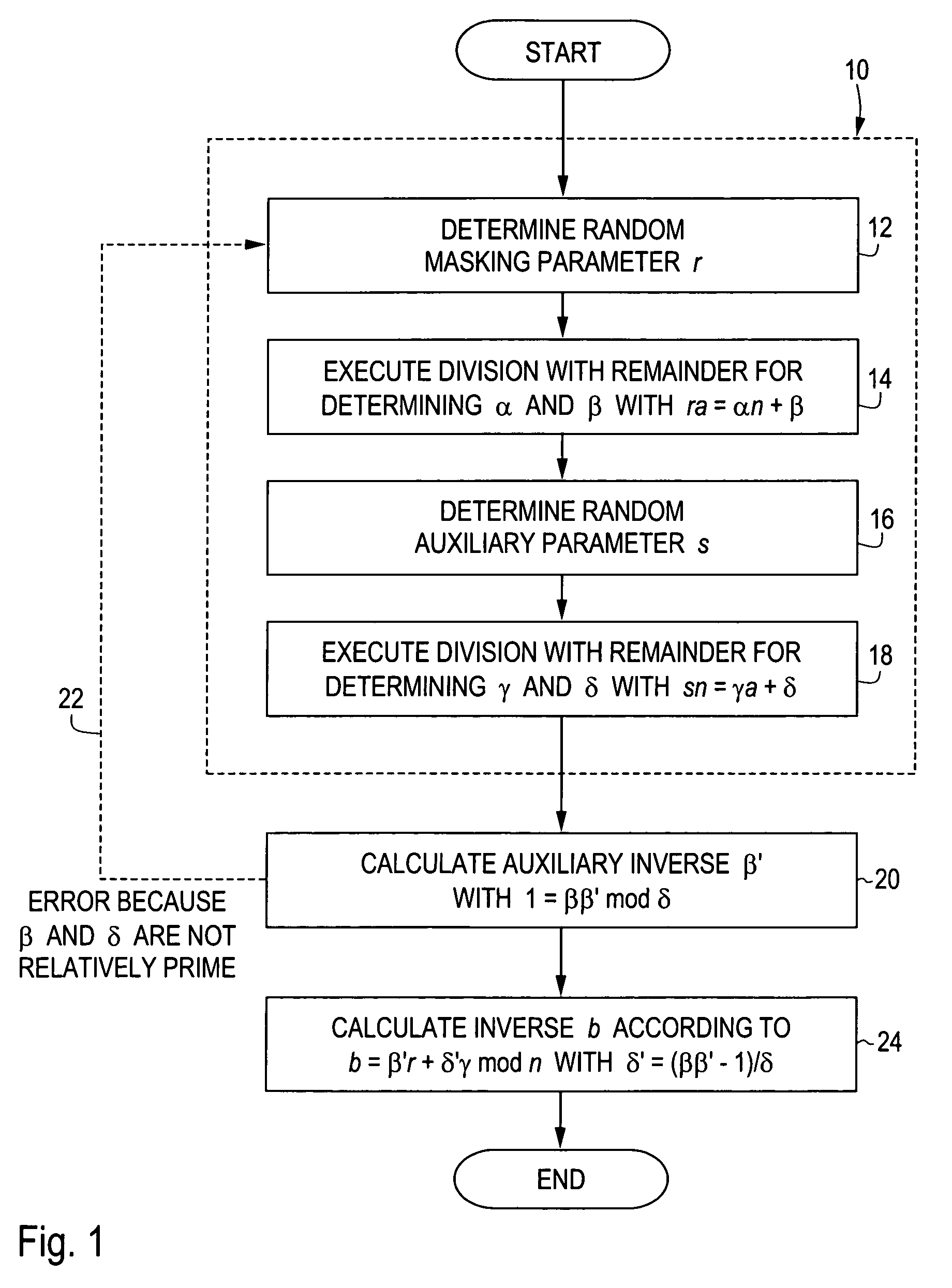
In methods for determining, in a way that is protected against spying, the modular inverse b of a value a in relation to a module n for a cryptographic application, an auxiliary value β and an auxiliary module δ are determined at least depending on the value a, the module n and at least one masking parameter r, an auxiliary inverse β′ is determined as the modular inverse of the auxiliary value β in relation to the auxiliary module δ, and the modular inverse b is determined at least depending on the auxiliary inverse β′, the at least one masking parameter r, and the auxiliary value β and / or the auxiliary module δ. A computer program product and a portable data carrier have corresponding features. The invention provides a method for modular inversion, secured against spying, which is suitable for applications where security is critical, such as, e.g. cryptographic calculations on a portable data carrier.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
Digital image encryption method and image decryption method based on modular inversion operation
ActiveCN110958458AThe classification method is simple and easyEasy to operateDigital video signal modificationInformation transmissionAlgorithm
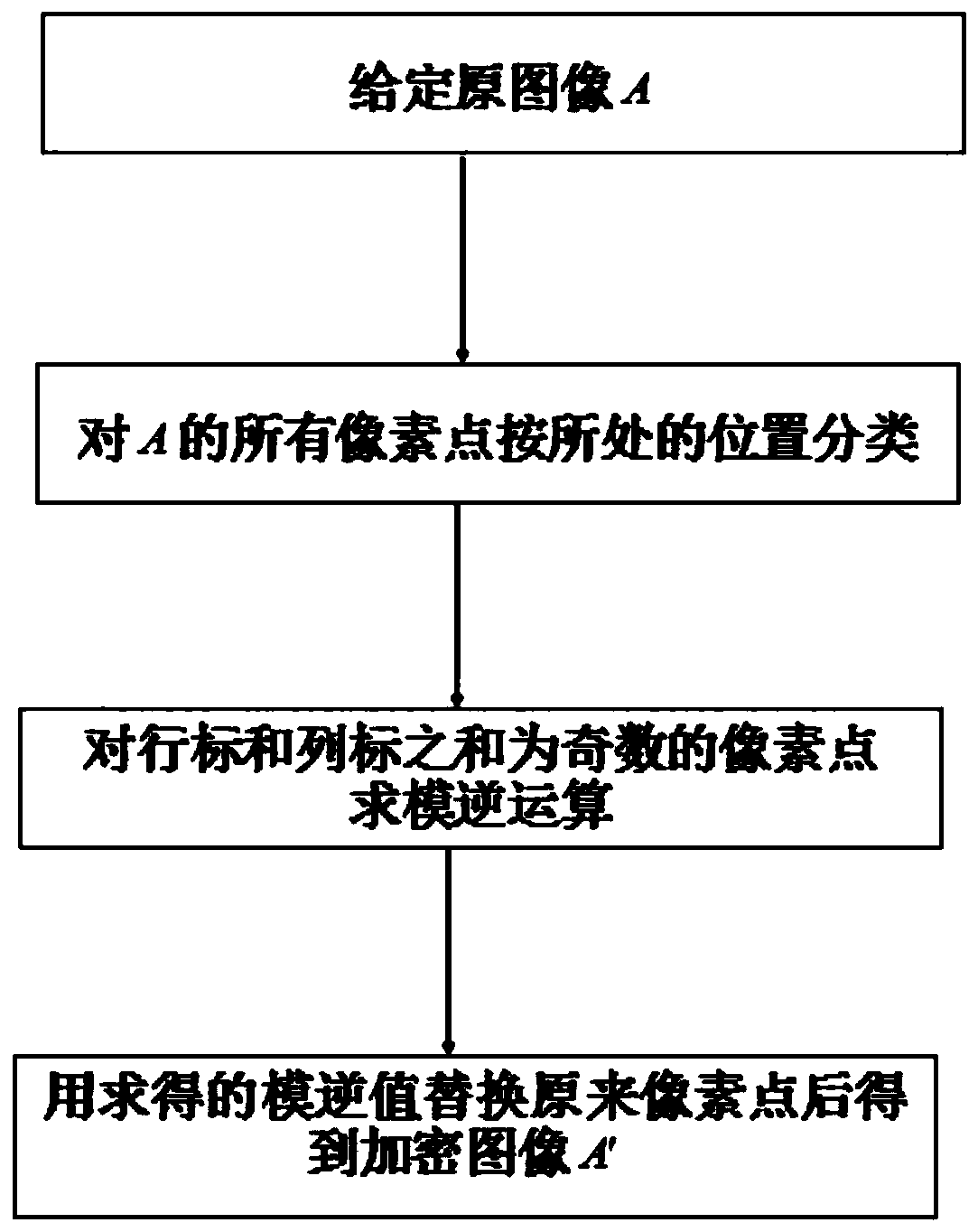
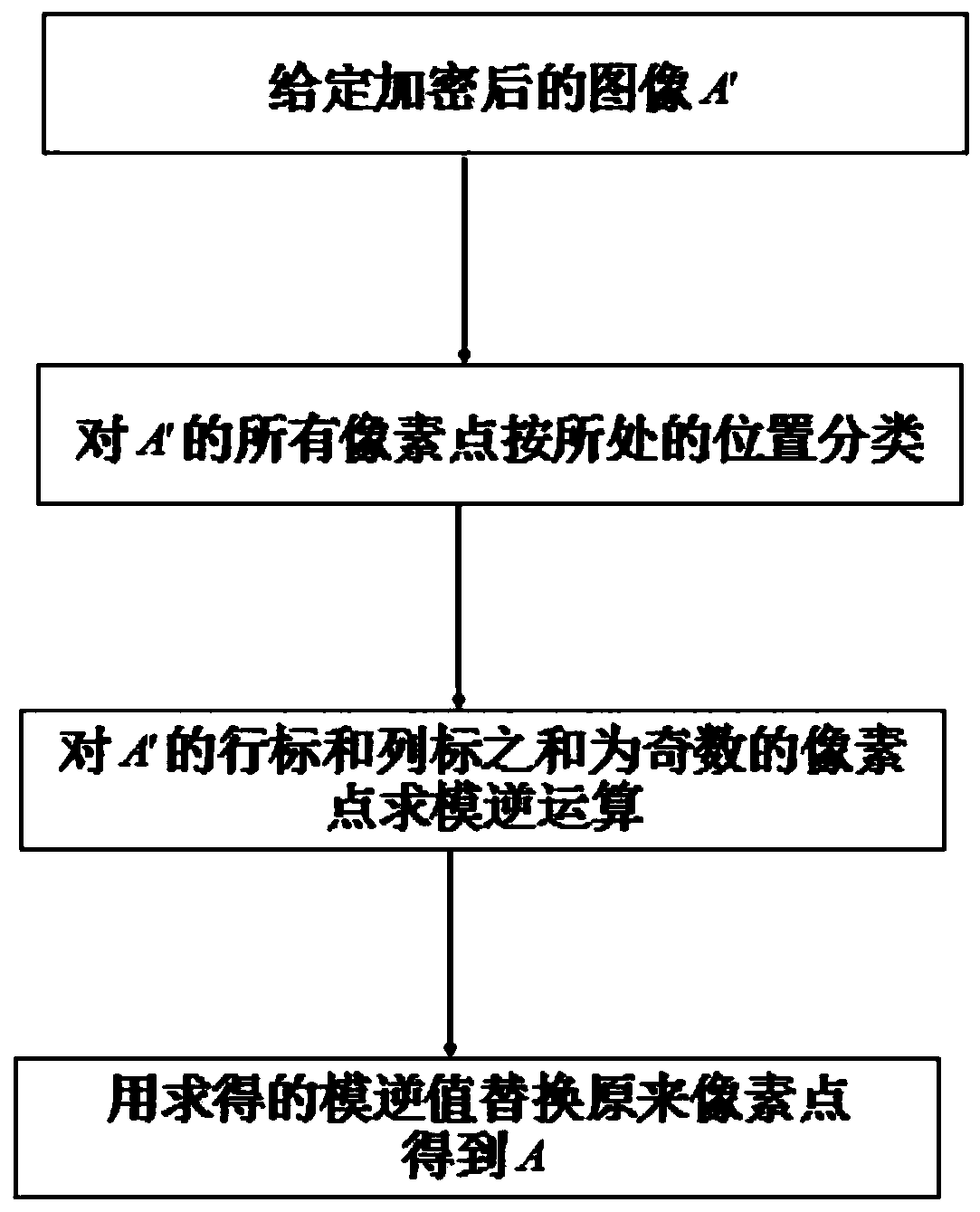
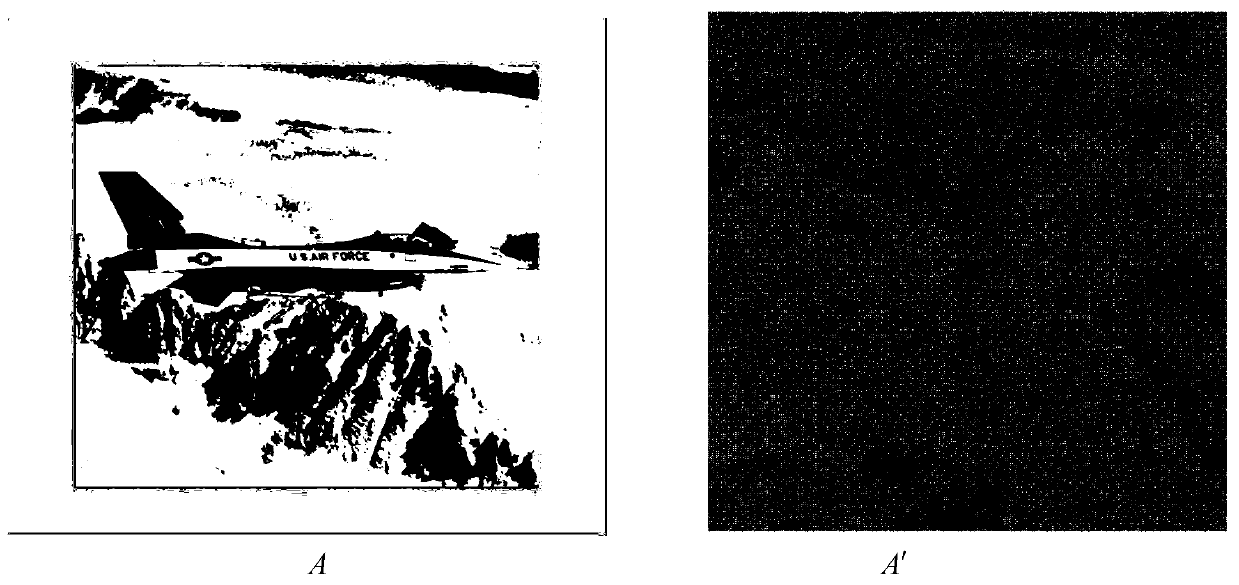
The invention discloses a digital image encryption method based on modular inversion operation. The method comprises the following steps: giving an original image A, wherein the pixel point located atthe ith row and the jth column in the A are expressed as pi, j, all the pixel points with the value of i + j being an odd number are classified into a first type, and all the pixel points with the value of i + j being an even number are classified into a second type; performing modular inversion operation on all the pixel points of the first type or the second type, and replacing the original pixel value with the obtained modular inversion value to obtain an encrypted image A'; performing modular inversion operation on the pixel points obtained by performing modular inversion operation on thepixel points of the first type or the second type in the A according to the claim 1 in the A'; and replacing the original pixel value with the obtained modular inversion value to recover the originalimage A. The method for classifying the pixel points of the image is simple and easy to implement, the encryption operation of the pixel points is simple, extra information is not needed in the wholeencryption and recovery process, the image information transmission efficiency is high, and errors of individual pixel points cannot cause the diffusion phenomenon of errors.
Owner:李小平
Method, device and readable storage medium for defending against side channel attacks
ActiveCN111931176BDefense against simple power consumption attacksDefense against Differential Power AttacksPlatform integrity maintainanceAlgorithmEngineering
The invention relates to a method and device for defending a side channel attack, and a readable storage medium. The method, when adding a mask to modular inversion operation, comprises the followingsteps: obtaining a base number a, a modulus p and a random number r2 participating in modular inverse operation; calculating an intermediate variable e related to the modulus p according to e = p-2; performing mask multiplication processing of the random number r2 on the base number a to obtain an updated base number a; respectively constructing the power b = aemodp with a mask and the power c = r2emodp with a mask, and calculating the values of b and c; and outputting an operation result s according to s = b * cmodp. By implementing the technical scheme of the invention, simple power consumption attacks and differential power consumption attacks can be resisted.
Owner:网御安全技术(深圳)有限公司
Method and device for modular inverse calculation of elements
ActiveCN104123431BCalculation speedReduce resource requirementsEncryption apparatus with shift registers/memoriesTemporary variableTheoretical computer science
Owner:NATIONZ TECH INC
A low-cost digital signature sopc design method based on rsa and sha-512
ActiveCN107508666BFast operationDefense against side channel attacksEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareHash function
The invention provides a low cost digital signature SPOC design method based on RSA and SHA-512. An in-chip MCU uses a soft core NiosII of an ALTERA to perform hardware and software partitioning on the RSA and SHA-512 according to operation characteristics; a software part comprises interaction with off-chip data, RSA modular exponentiation, and SHA-512 data filling; hardware finishes RSA modular multiplication, a modular addition operation, a modular inversion operation and an operation for taking 80 rounds as a subunit in the SHA-512. The low cost digital signature SPOC design method based on RSA and SHA-512 utilizes parallelism of hardware calculation to obtain a high speed operation result, uses flexibility of software to guarantee an attack resisting capability of a system, can support different RSA lengths and calculation modes of different HASH functions. Functionally, the low cost digital signature SPOC design method based on RSA and SHA-512 can be used for digital autographing and identity authentication.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com