Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
129 results about "Binade" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In software engineering a binade is the set of numbers in a binary IEEE 754 floating-point format that all have the same exponent. In other words, a binade is the interval [2ⁿ, 2ⁿ⁺¹) for some value of n.
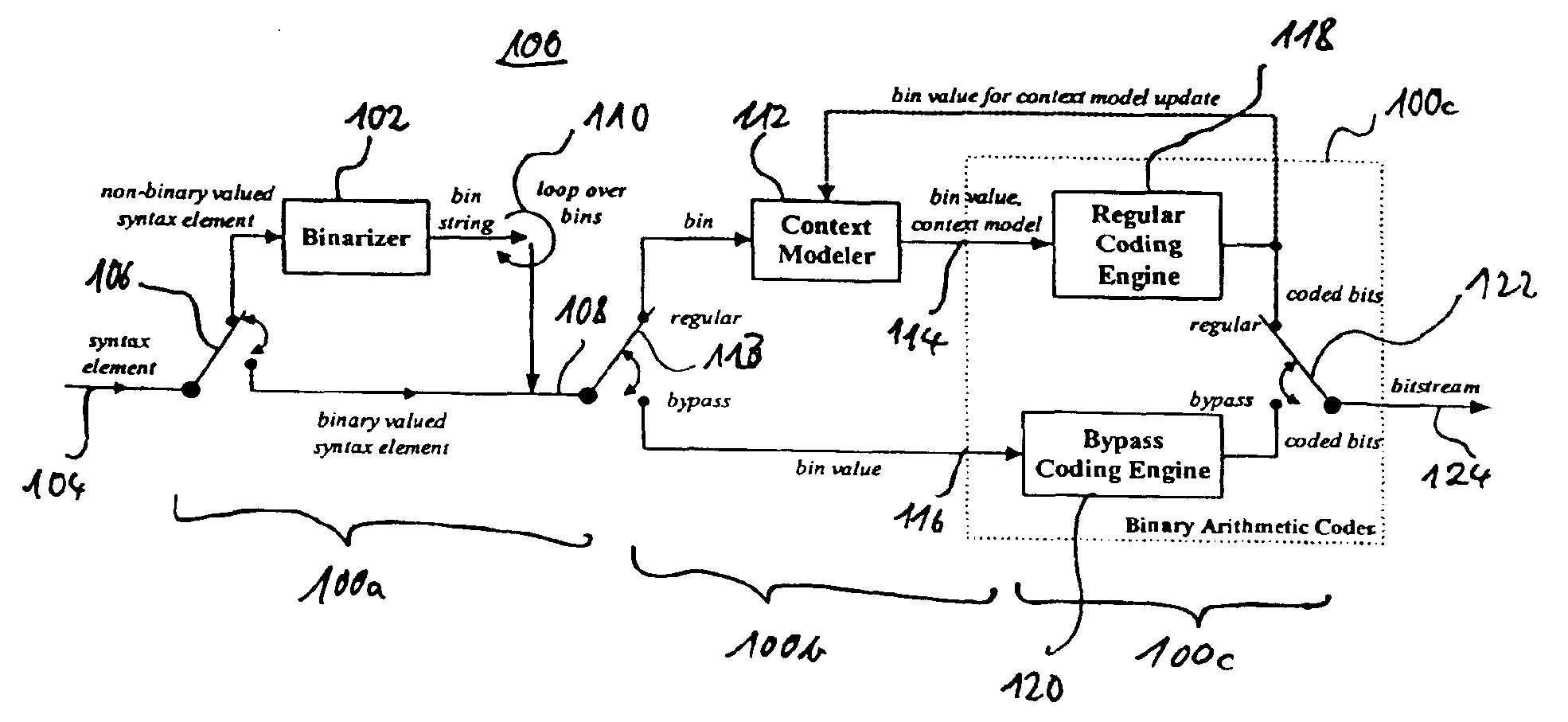
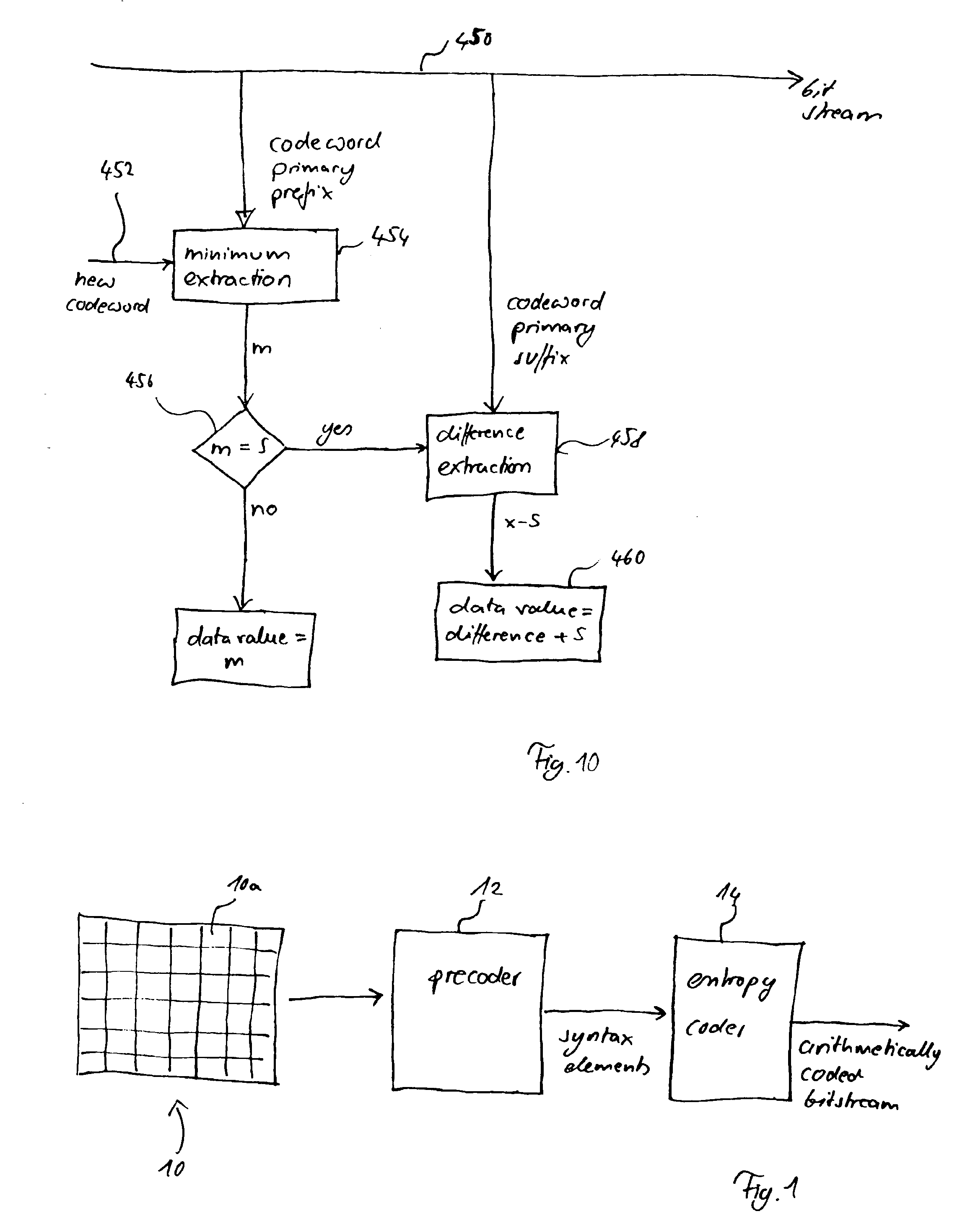
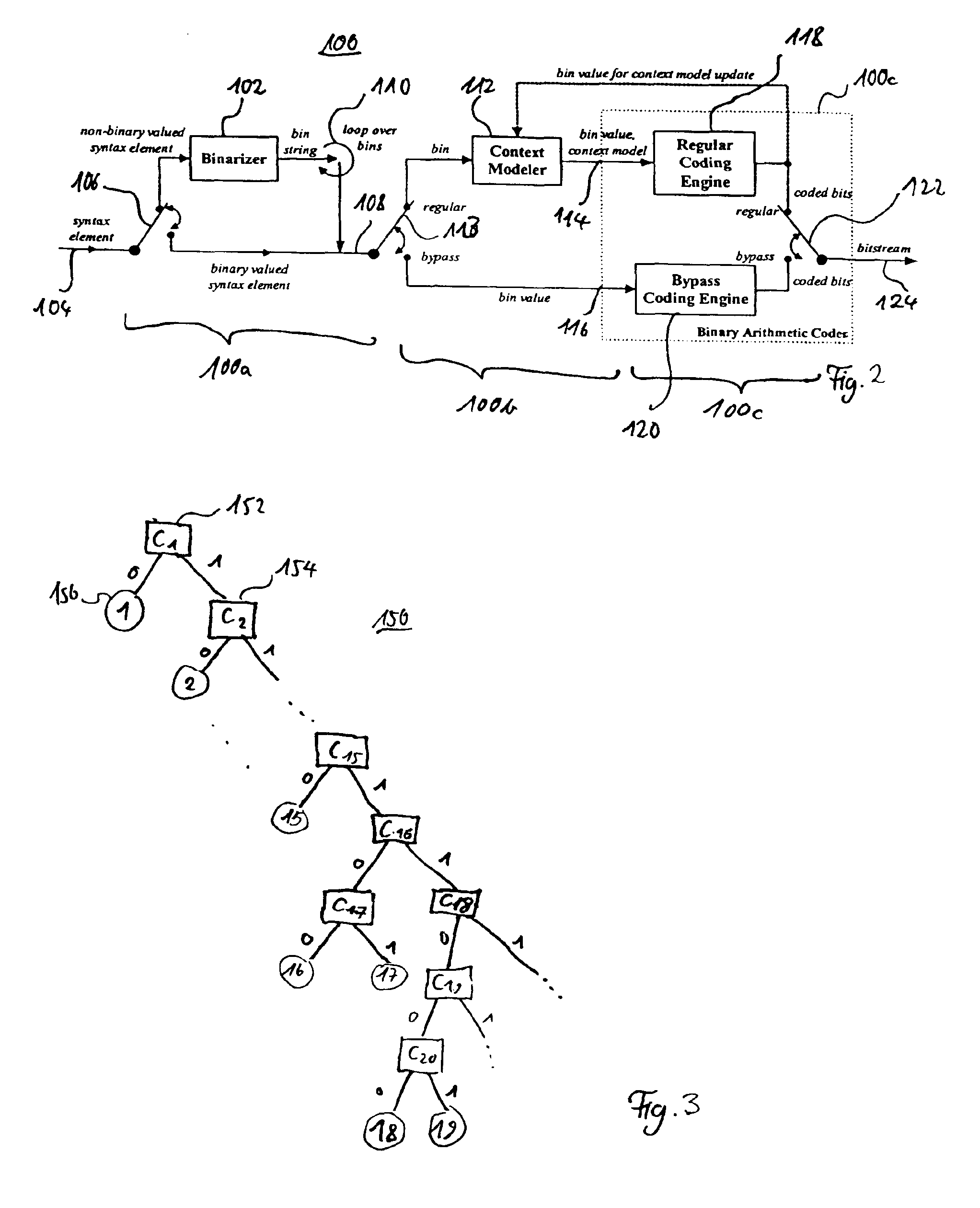
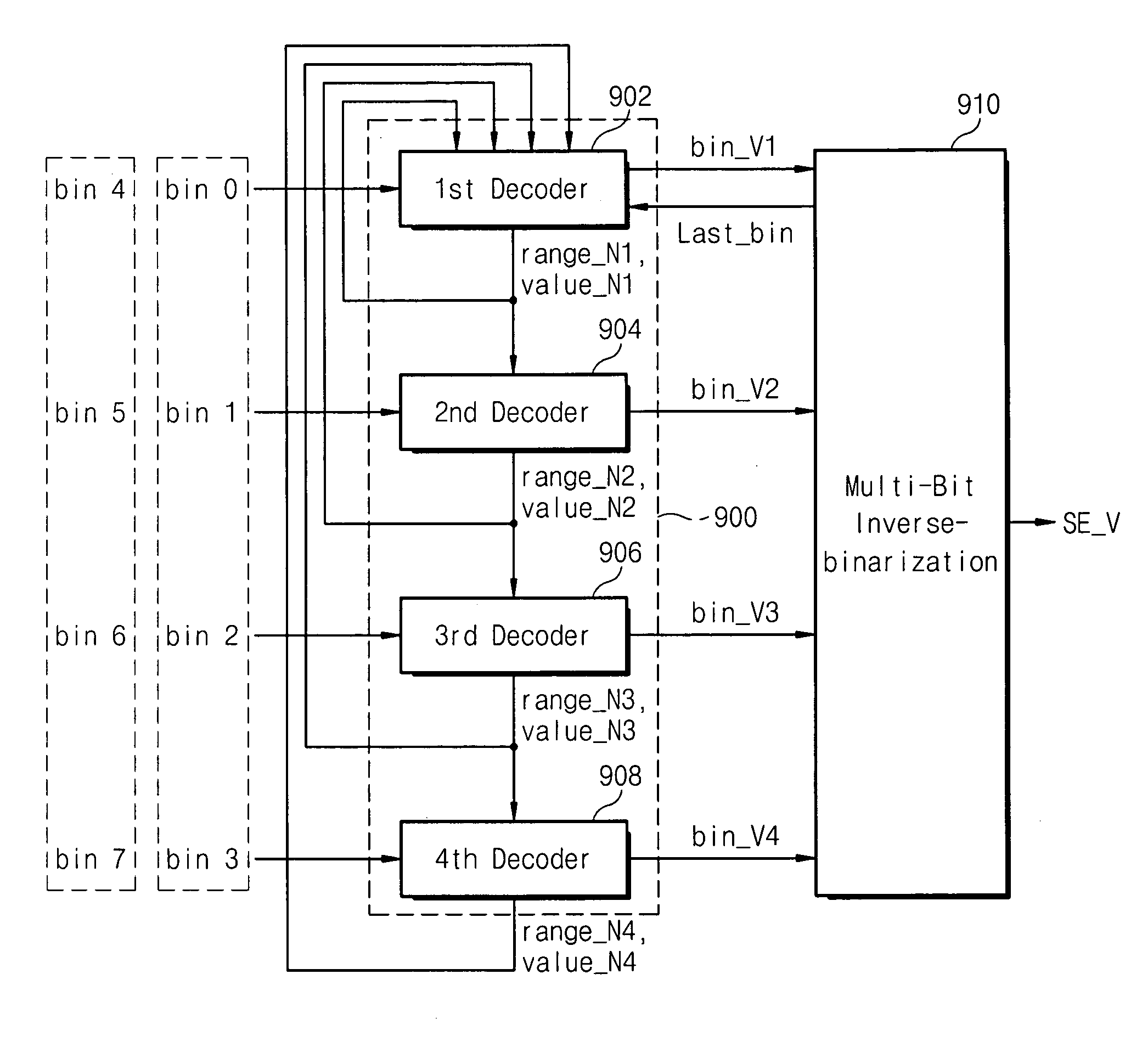
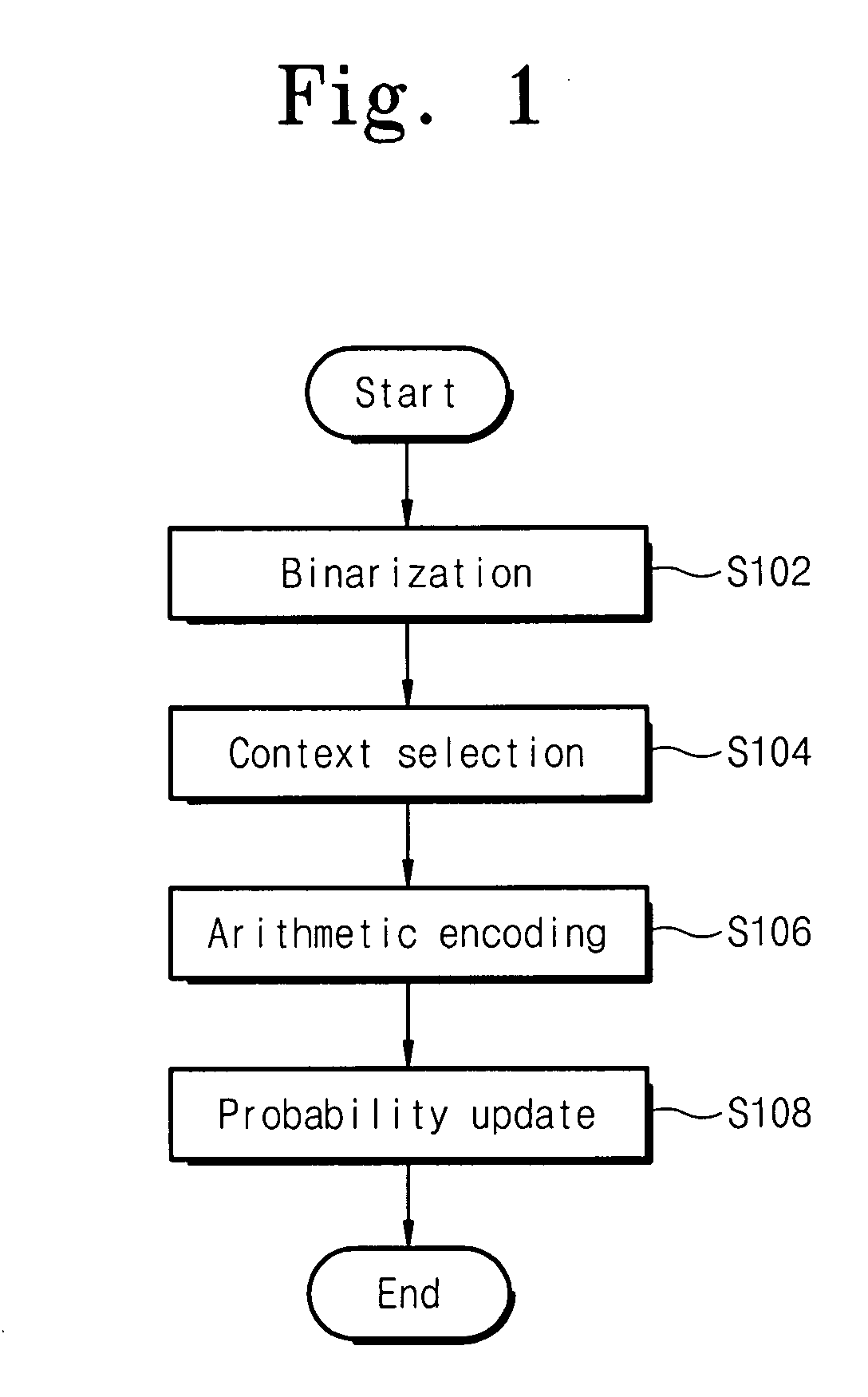
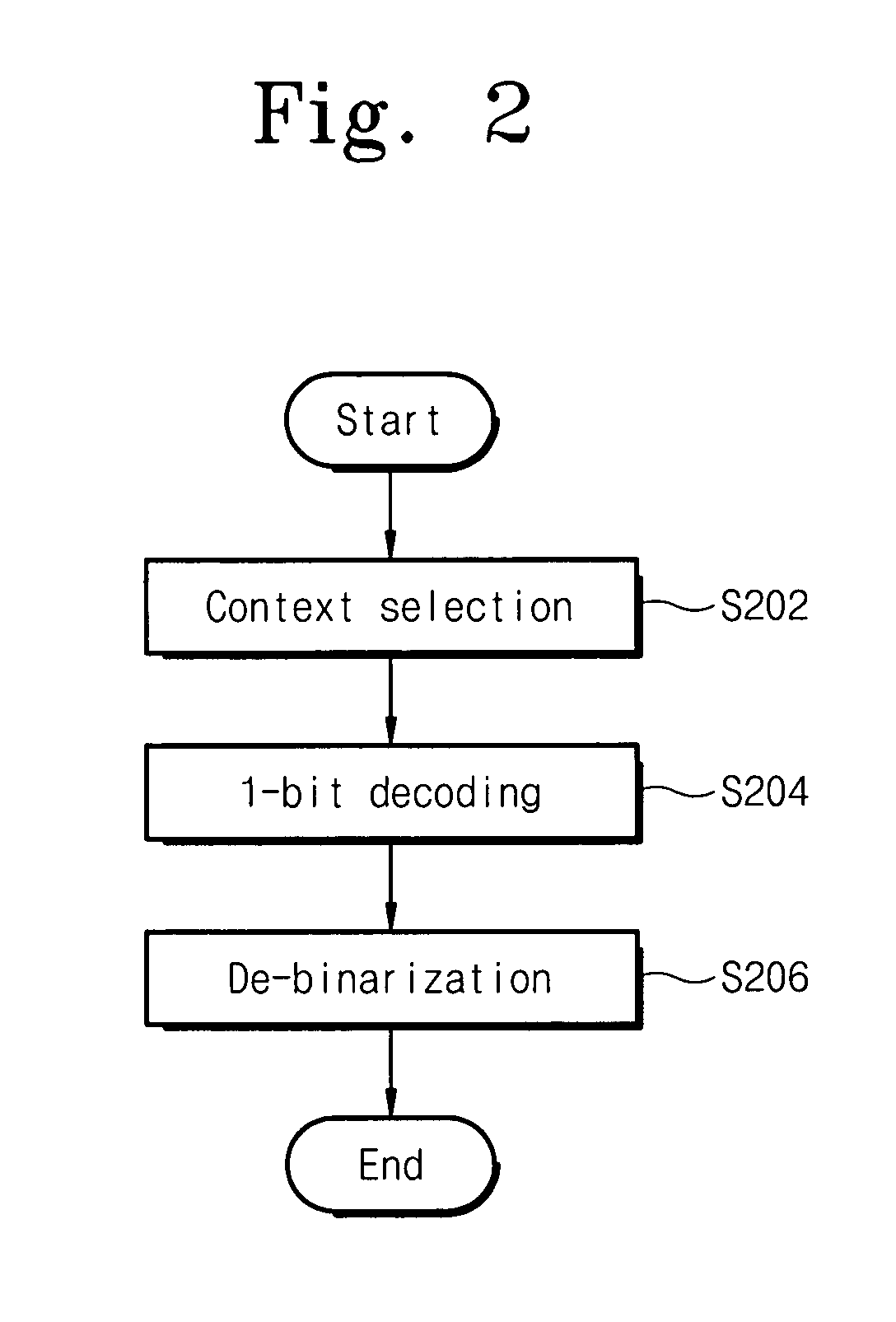
Method and apparatus for binarization and arithmetic coding of a data value
ActiveUS6900748B2Efficient compressionModerate computational overheadDigital data processing detailsDigital computer detailsComputer architectureCut off value
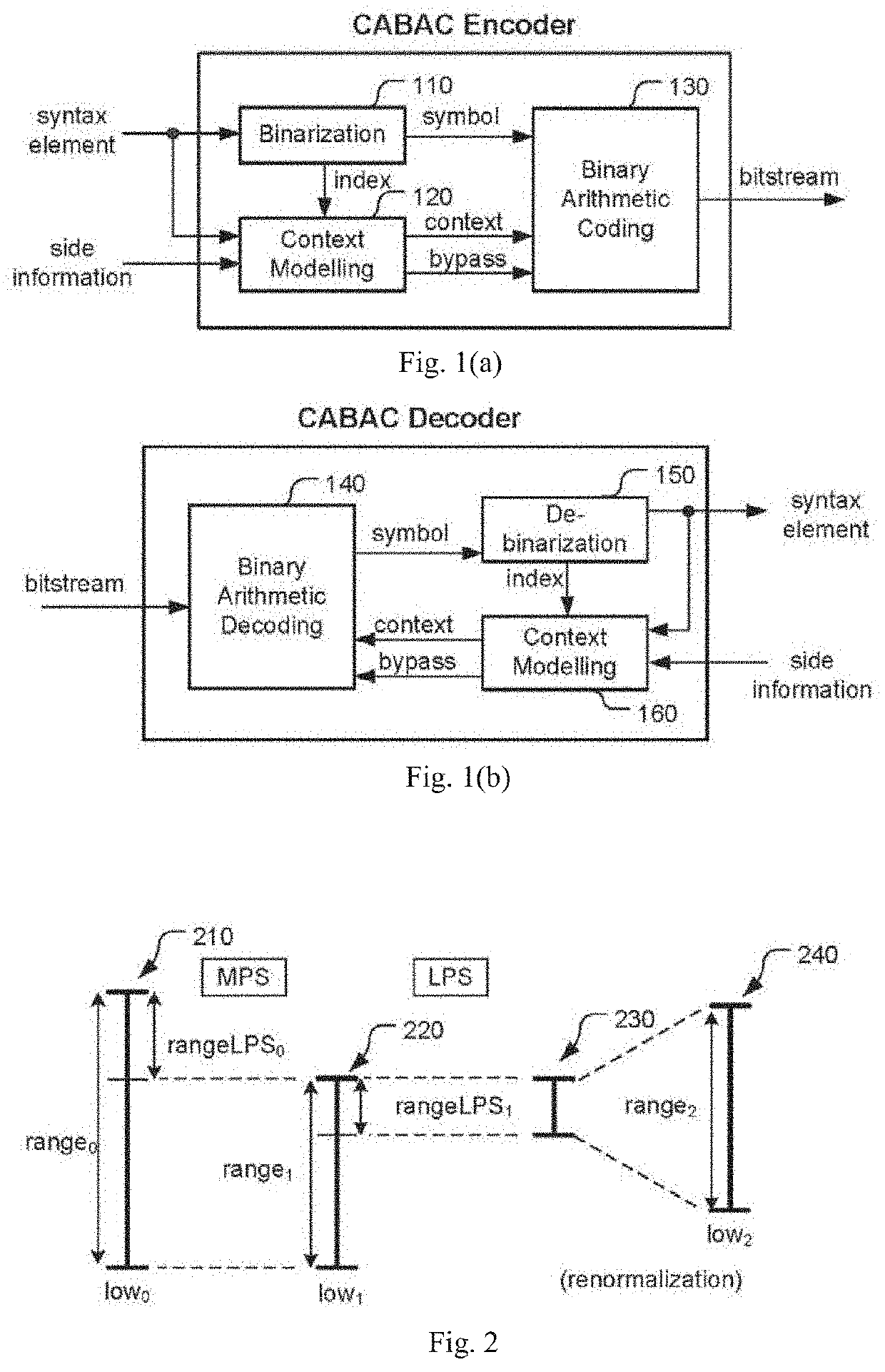
Binarization a data value comprises binarizing the minimum of the data value and a predetermined cut-off value in accordance with a first binarization scheme, in order to yield a primary prefix. If the data value is greater than the cut-off value, binarizing a difference of the data value minus the predetermined cut-off value in accordance with a second binarization scheme to obtain a binary suffix, the first binarization scheme being different from the second binarization scheme, and appending the primary suffix to the primary prefix is performed. A very effective compression of data values may be achieve by using the binarization scheme for preparing the syntax elements for the arithmetic coding, the binarization schemes substantially being a combination of two different binarization schemes, and by using binary arithmetic coding instead of m-ary arithmetic coding for coding the binarized syntax elements.
Owner:GE VIDEO COMPRESSION LLC
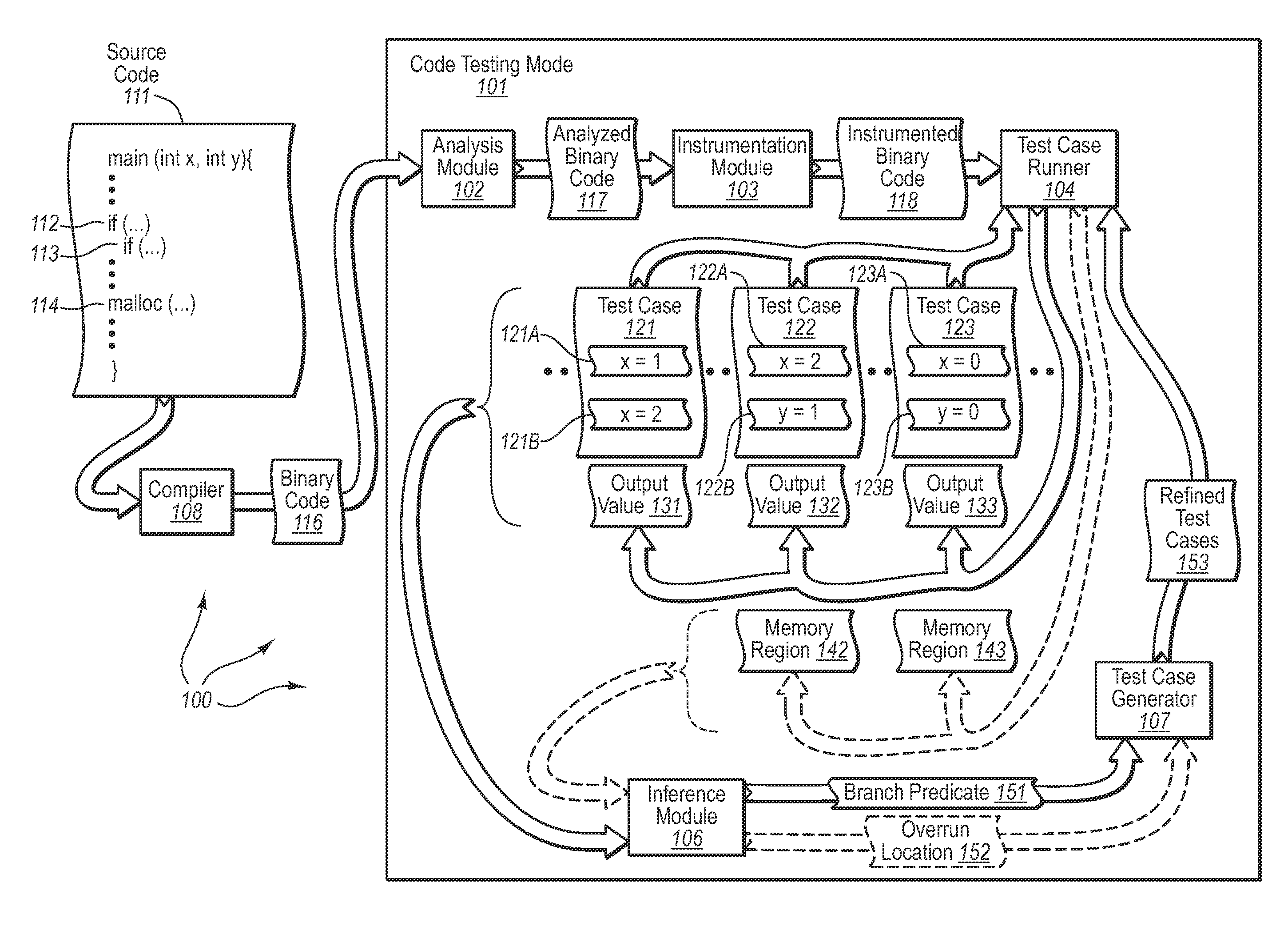
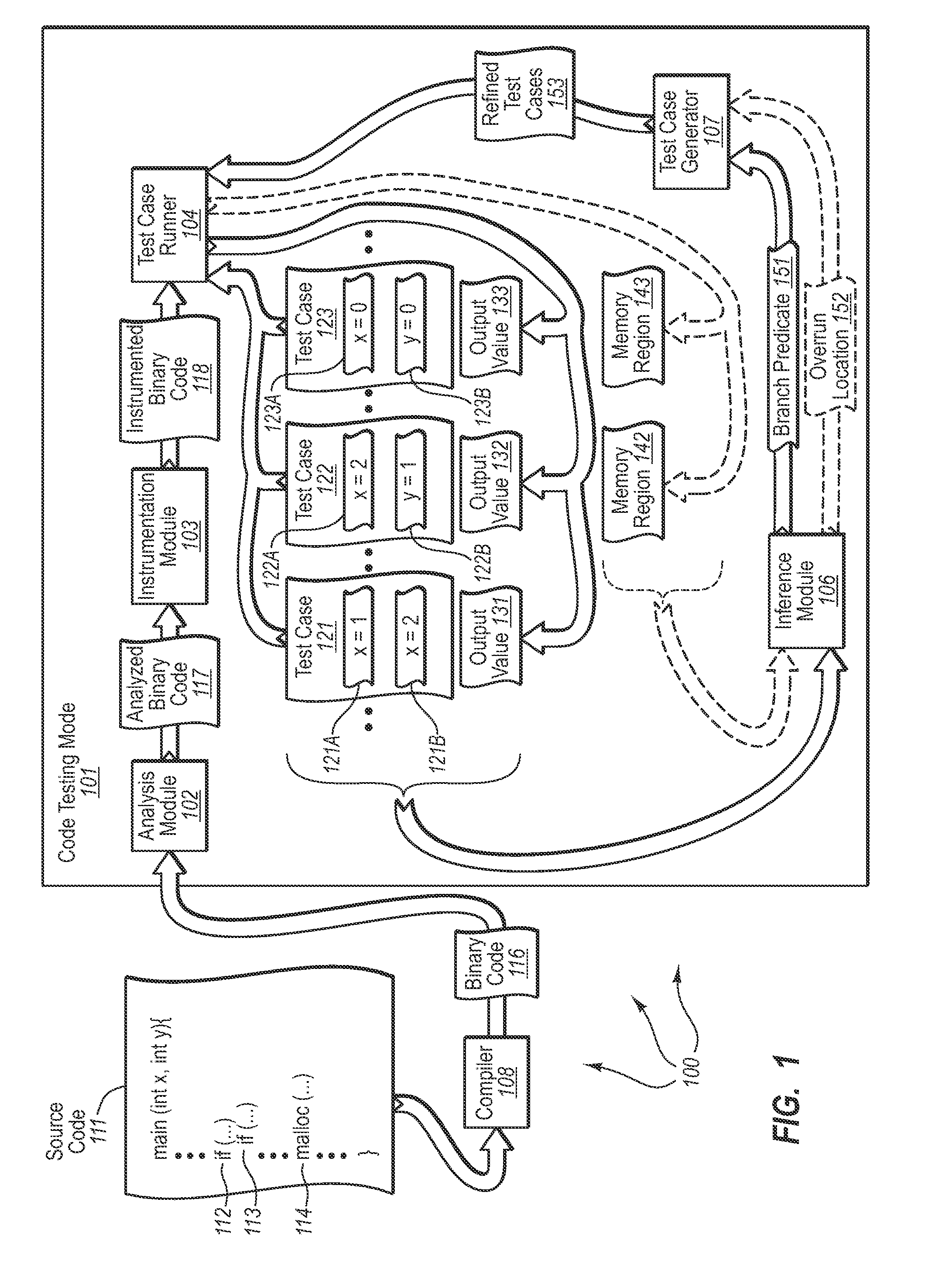
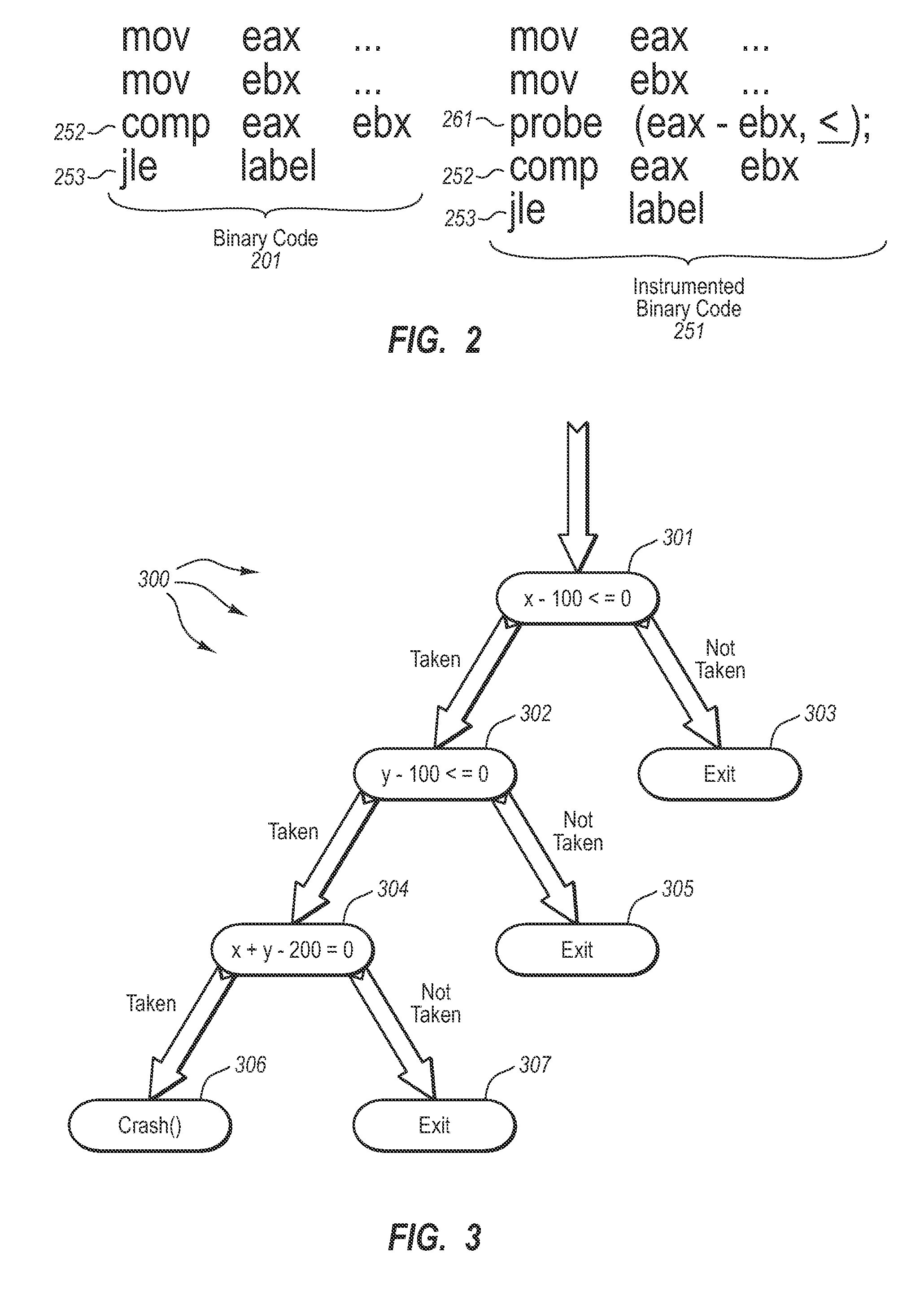
Automatically generating test cases for binary code
InactiveUS20090007077A1Efficient testingError detection/correctionSpecific program execution arrangementsTest inputParallel computing
The present invention extends to methods, systems, and computer program products for automatically generating test cases for binary code. Embodiments of the present invention can automatically generate test inputs for systematically covering program execution paths within binary code. By monitoring program execution of the binary code on existing or random test cases, branch predicates on execution paths can be dynamically inferred. These inferred branch predicates can then be used to drive the program along previously unexplored execution paths, enabling the learning of further execution paths. Embodiments of the invention can be used in combination with other analysis and testing techniques to provide better test coverage and expose program errors.
Owner:MICROSOFT TECH LICENSING LLC
Binary arithmetic decoding apparatus and methods using a pipelined structure
Binary arithmetic decoding methods and apparatus are provided. A first decoded bit and a first set of decoding parameters are generated using a previously generated set of decoding parameters. A second decoded bit and a second set of decoding parameters are generated using the first set of decoding parameters. If the first decoded bit is a last bit of a syntax element, the second set of decoding parameters is disregarded in generating subsequent decoded bits. The generation of the first and second decoded bits and determination of whether the first decoded bit is a last bit of a syntax element, e.g., a de-binarizing operation, may be pipelined such that the determination of whether the first decoded bit is a last bit of a syntax element occurs concurrent with and / or after generation of the second decoded bit and the second set of decoding parameters.
Owner:SAMSUNG ELECTRONICS CO LTD
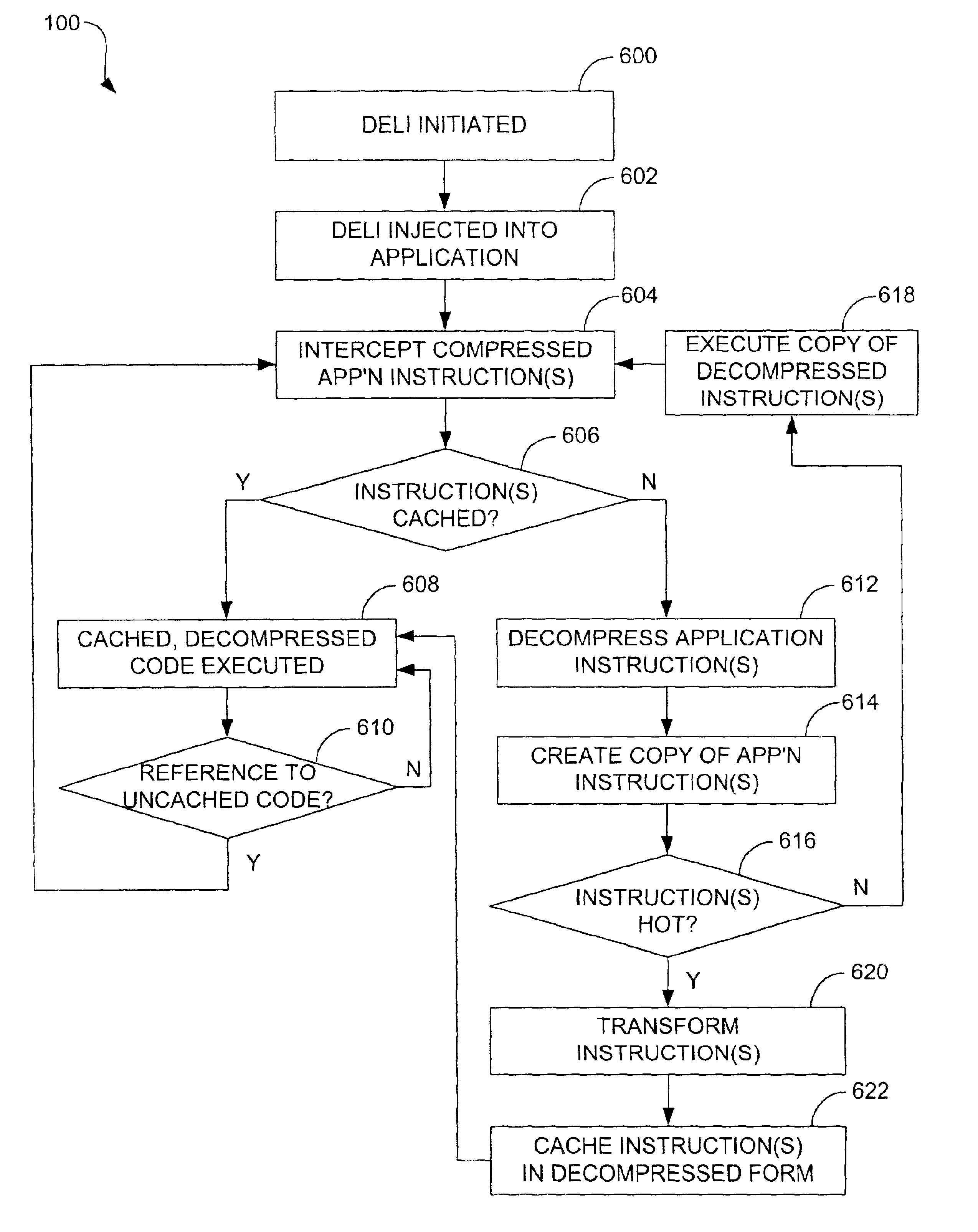
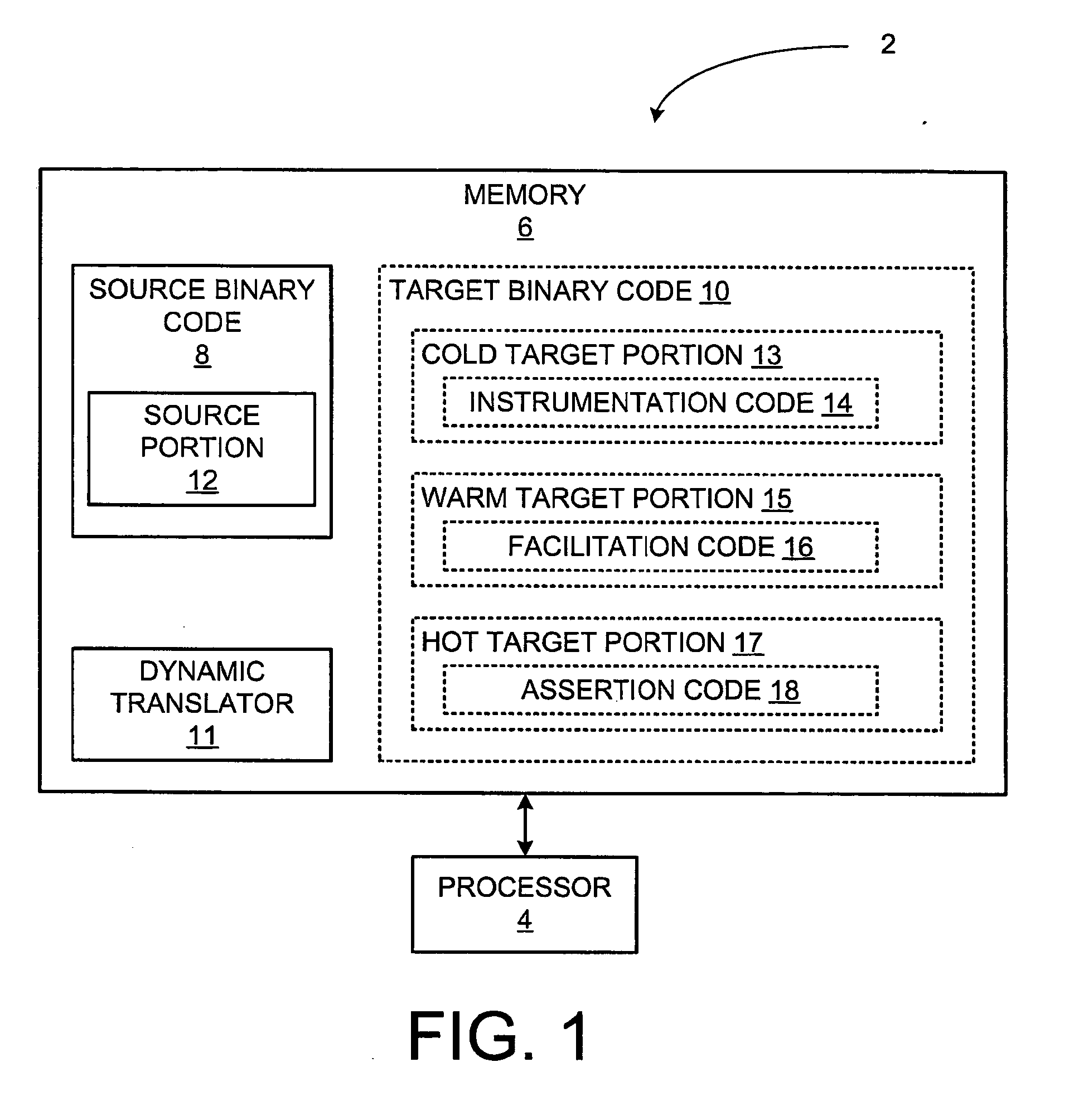
System and method for decoding and executing program binaries
InactiveUS6920550B2Digital computer detailsUnauthorized memory use protectionProgramming languageProgram instruction
The present disclosure relates to a system and method for decoding program binaries. In one arrangement, the system and method pertain to intercepting program instructions, determining if associated instructions have been decoded and cached, and decoding and copying the program instructions if associated instructions have not been cached.
Owner:HEWLETT PACKARD DEV CO LP
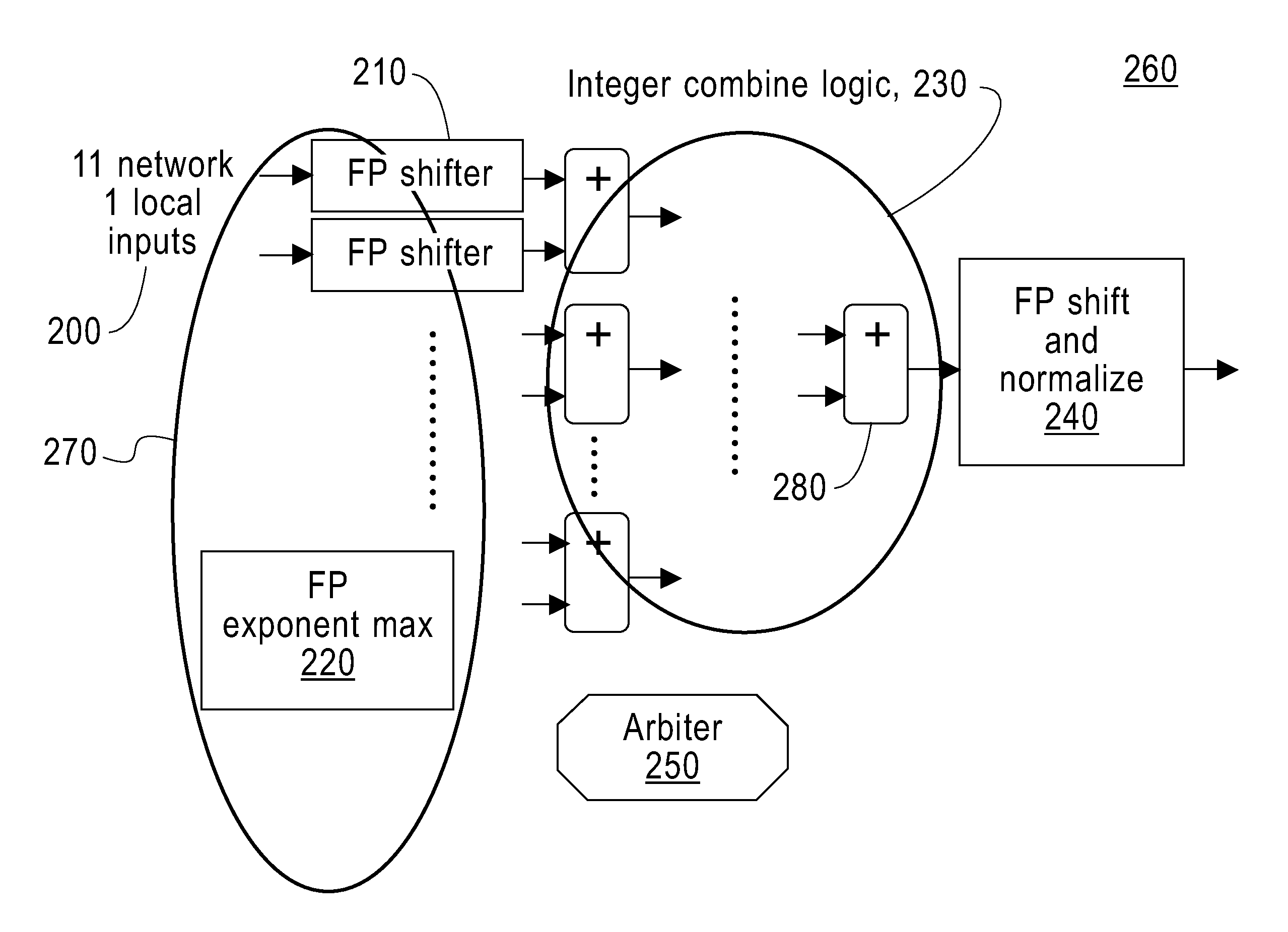
Multi-input and binary reproducible, high bandwidth floating point adder in a collective network
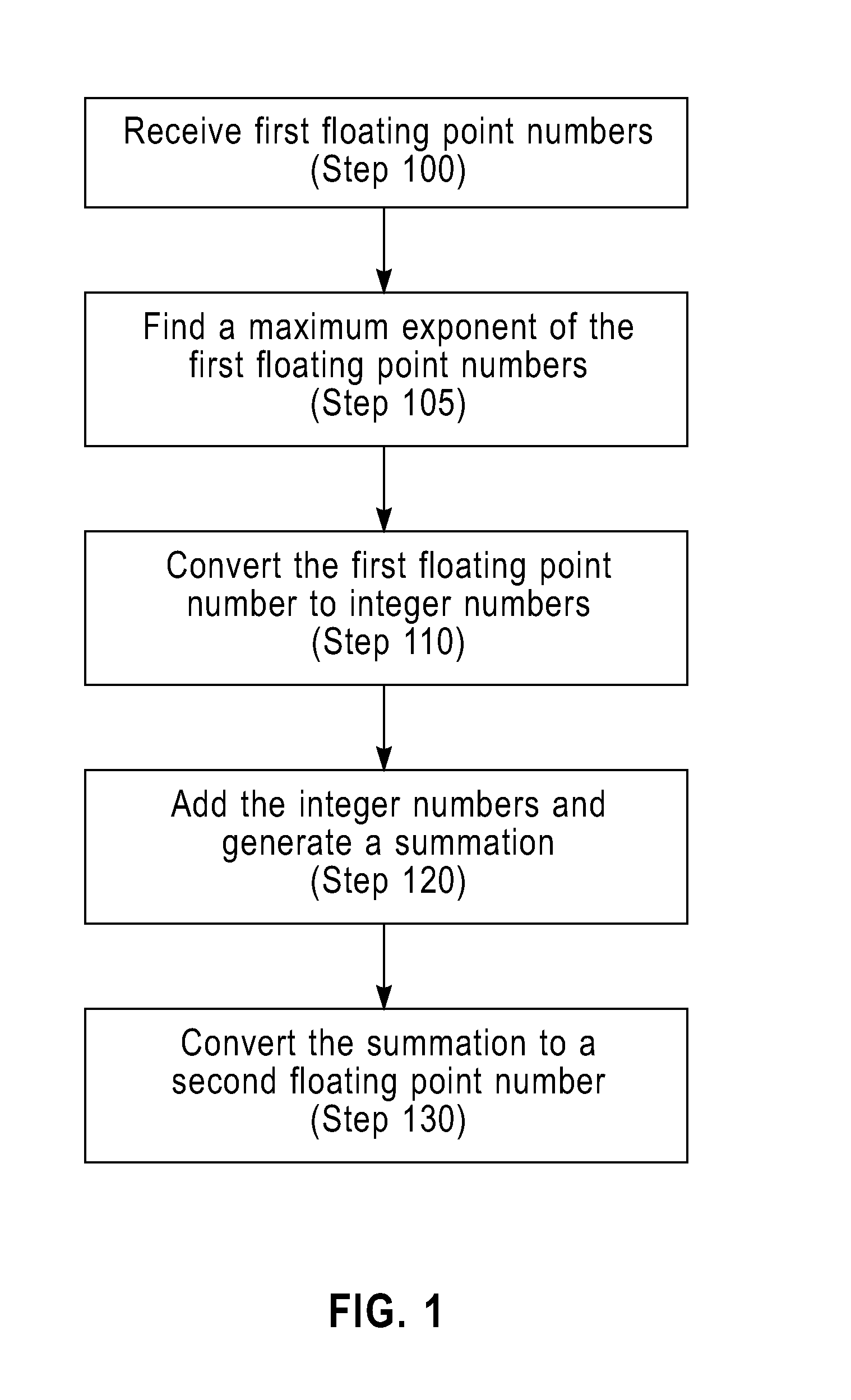
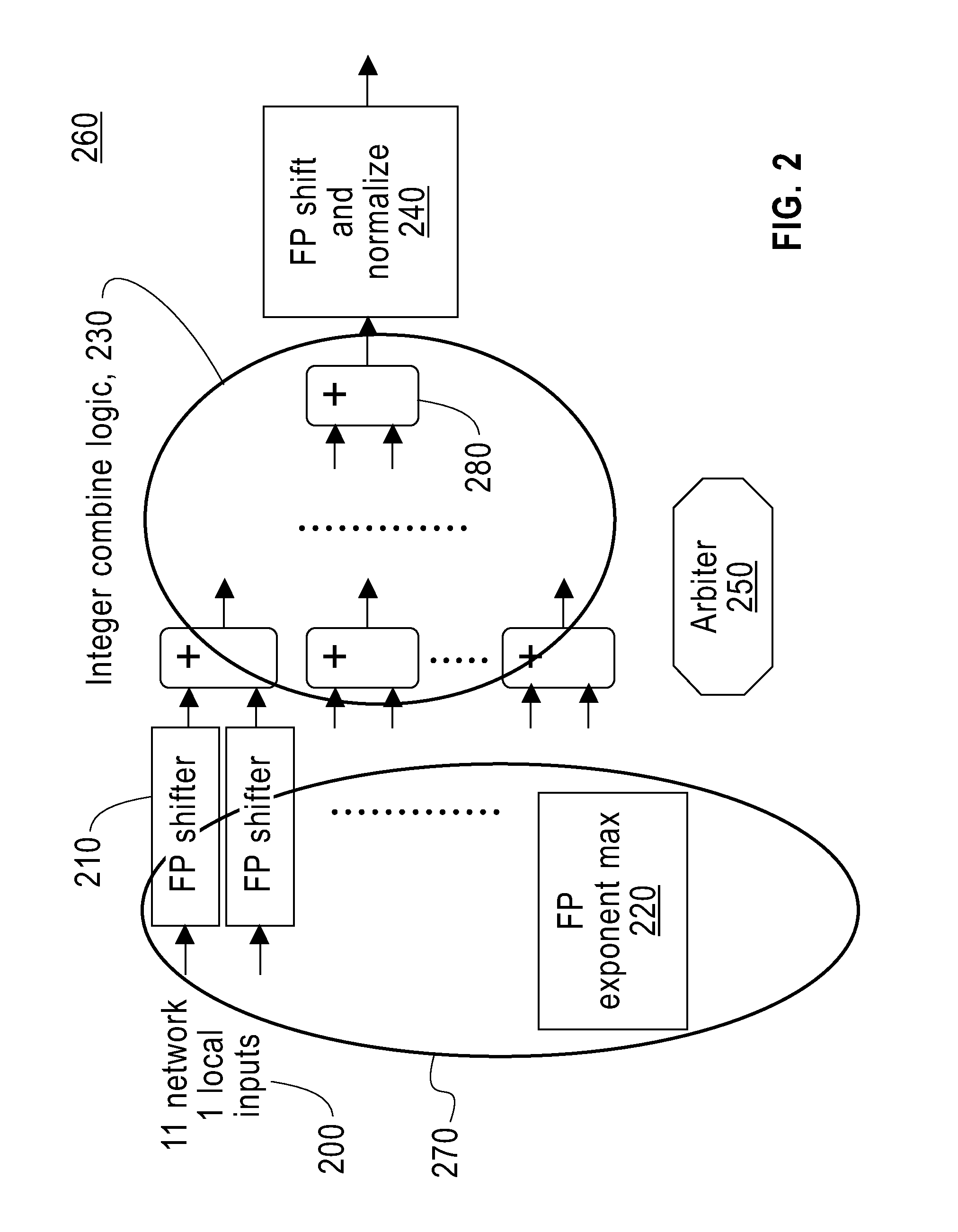
ActiveUS20110173421A1Digital computer detailsSpecific program execution arrangementsMulti inputConcurrent computation
To add floating point numbers in a parallel computing system, a collective logic device receives the floating point numbers from computing nodes. The collective logic devices converts the floating point numbers to integer numbers. The collective logic device adds the integer numbers and generating a summation of the integer numbers. The collective logic device converts the summation to a floating point number. The collective logic device performs the receiving, the converting the floating point numbers, the adding, the generating and the converting the summation in one pass. One pass indicates that the computing nodes send inputs only once to the collective logic device and receive outputs only once from the collective logic device.
Owner:IBM CORP
Method and system for avoiding software conflict
Owner:INT BUSINESS MASCH CORP
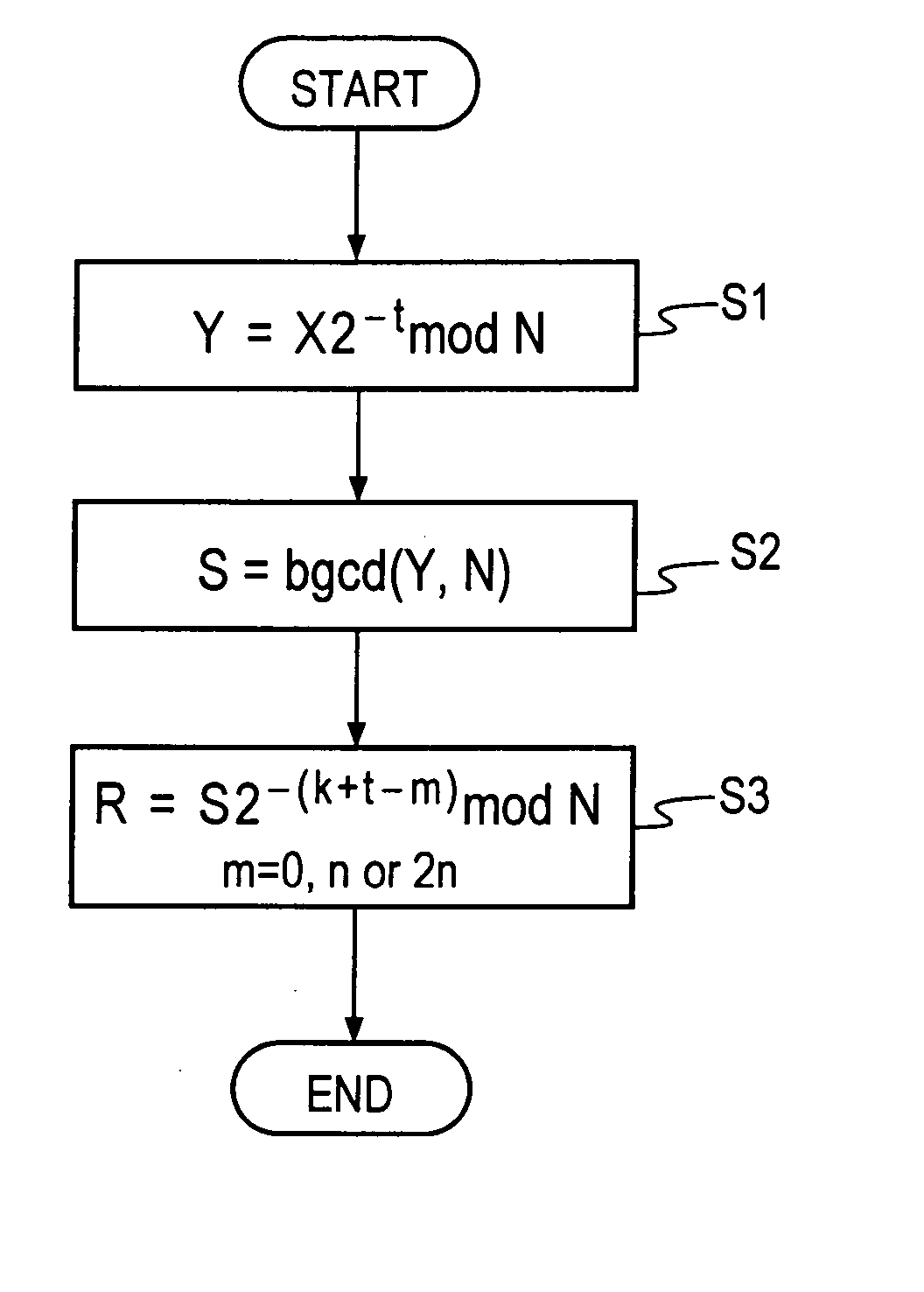
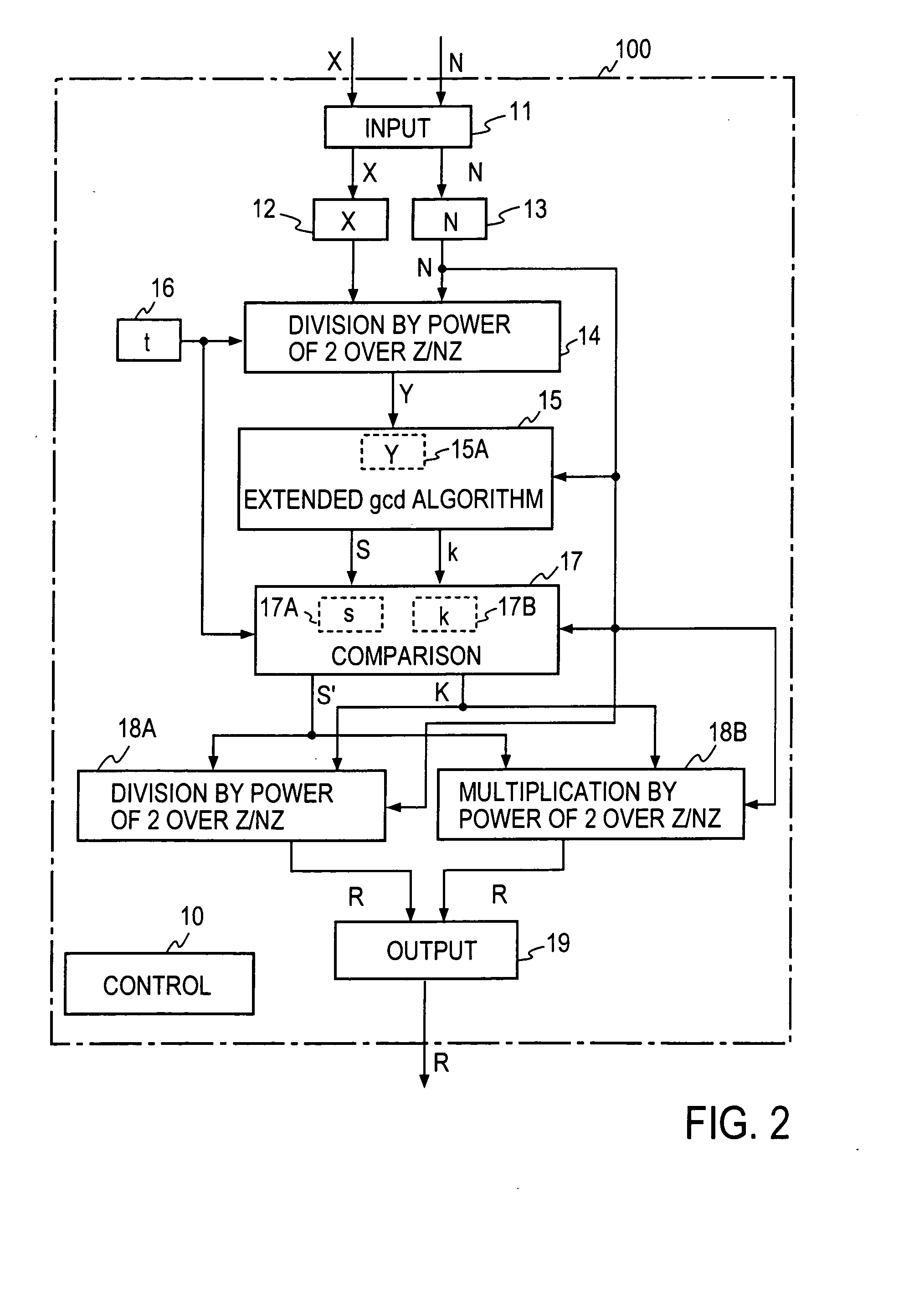
Method and apparatus for modular inversion for information security and recording medium with a program for implementing the method
InactiveUS20050041811A1Shorten the timeShort timeDigital computer detailsSecret communicationAlgorithmInformation security
Values X and N of n bits and a parameter t are input, then Y=X2−t mod N is calculated, then an extended binary GCD algorithm is executed for Y to obtain S=[[Y]] y−12k mod N and k, and R=S2−(k+t=2n) is calculated for S, thereby obtaining a Montgomery inverse R=X−122n mod N of X on a residue class ring Z / NZ.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
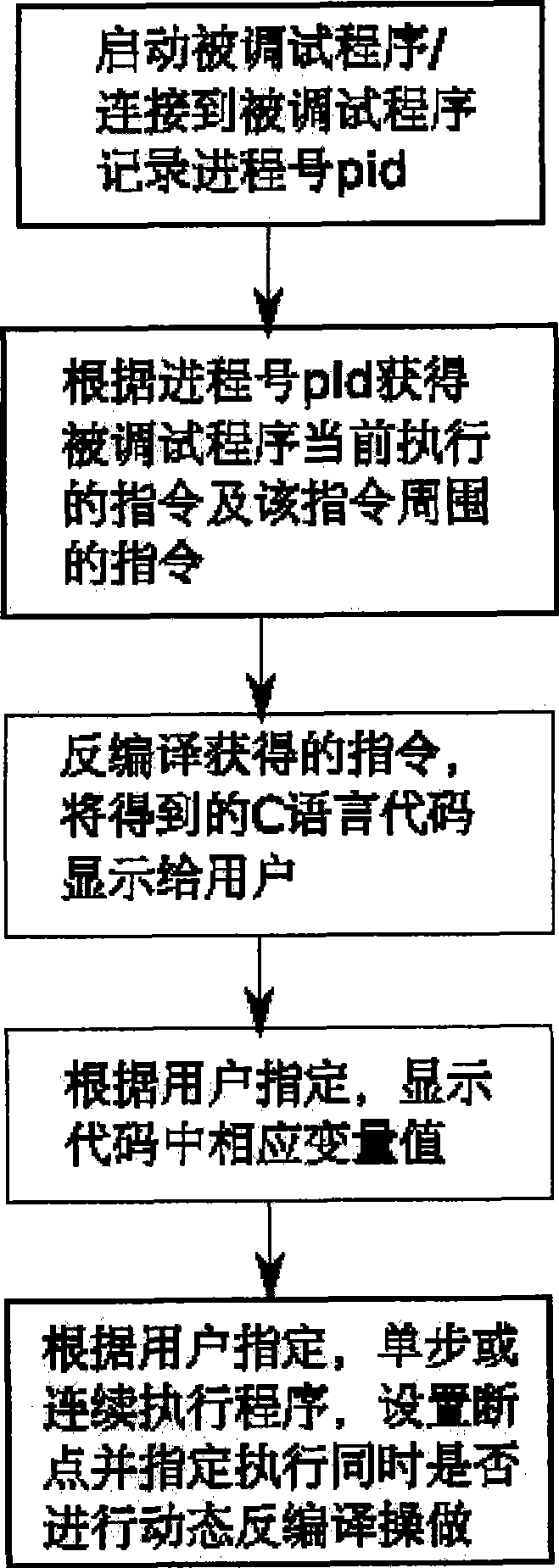
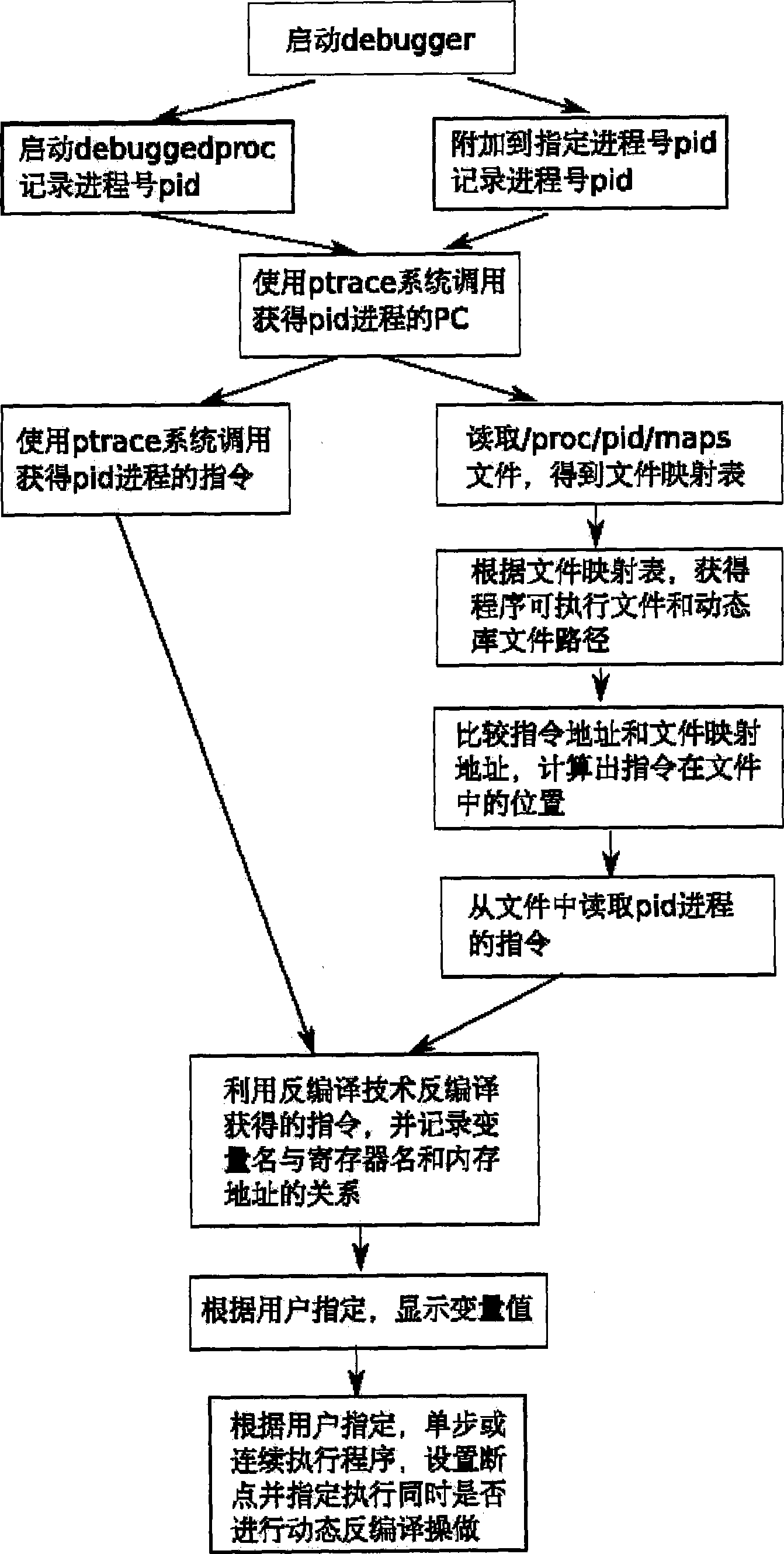
Method for debugging binary application program based on dynamic inverse compiling technique
ActiveCN101414278AImprove efficiencyEasy to callSoftware testing/debuggingProgram controlApplication softwareDebugger
The invention relates to a debug method of a binary application program based on a dynamic decompiling technology. Debug staff starts the application program by a debugger or assigns a process number of a process to be debugged, if the debugged program is started by the debugger, the debugger records a process number of a sub-process; when the program is executed to a breakpoint, an operating system suspends the debugged program, and the debugger obtains a command; an instruction of the debugged program is obtained by a system call or application programming interface (API) which is provided by the operating system, the instruction is decompiled by the dynamic decompiling technology, and the obtained C language code is displayed to the debug staff. The debug method has the advantages of being capable of facilitating the debug staff to debug the binary application program without reading complicated assembly codes, and effectively enhancing efficiency of debugging programs.
Owner:INSIGMA TECHNOLOGY CO LTD
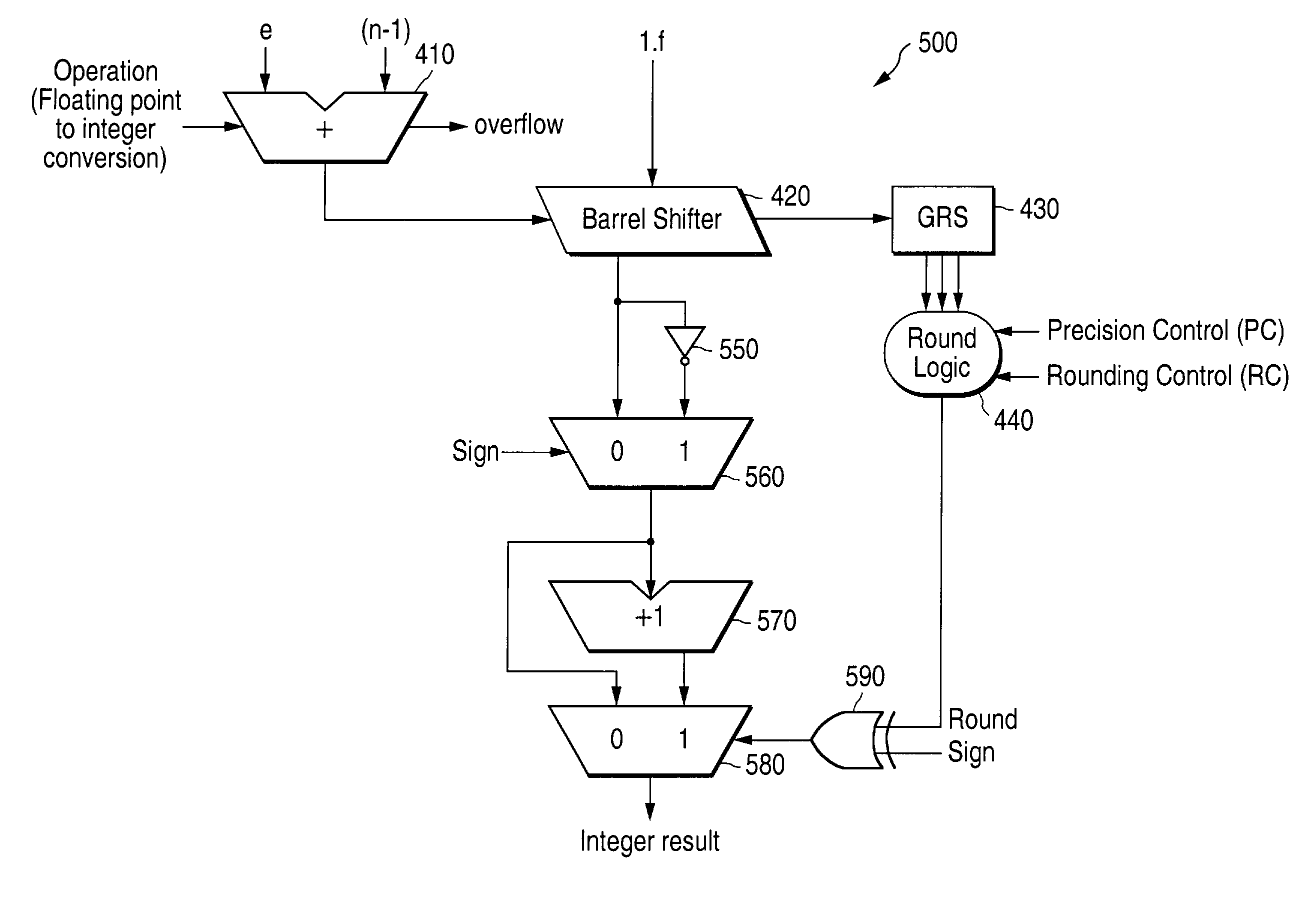
Converting negative floating point numbers to integer notation without two's complement hardware
InactiveUS6965906B1Digital data processing detailsDigital computer detailsMultiplexerParallel computing
For use in a processor having integer and floating point execution cores, logic circuitry for, and a method of, converting negative numbers from floating point notation to integer notation. In one embodiment, the logic circuitry includes: (1) a shifter that receives a number in floating point notation and shifts a fraction portion of the received number as a function of an exponent portion thereof to yield a shifted fraction portion and rounding data, (2) a one's complementer, coupled to the shifter, that inverts the shifted fraction portion to yield an unincremented inverted shifted fraction portion, (3) an incrementer, coupled to the one's complementer, that increments the unincremented inverted shifted fraction portion to yield an incremented inverted shifted fraction portion and (4) a multiplexer, coupled to the one's complementer and the incrementer, that selects one of the unincremented inverted shifted fraction portion and the incremented inverted shifted fraction portion based on the rounding data thereby to yield the received number in integer notation.
Owner:NAT SEMICON CORP
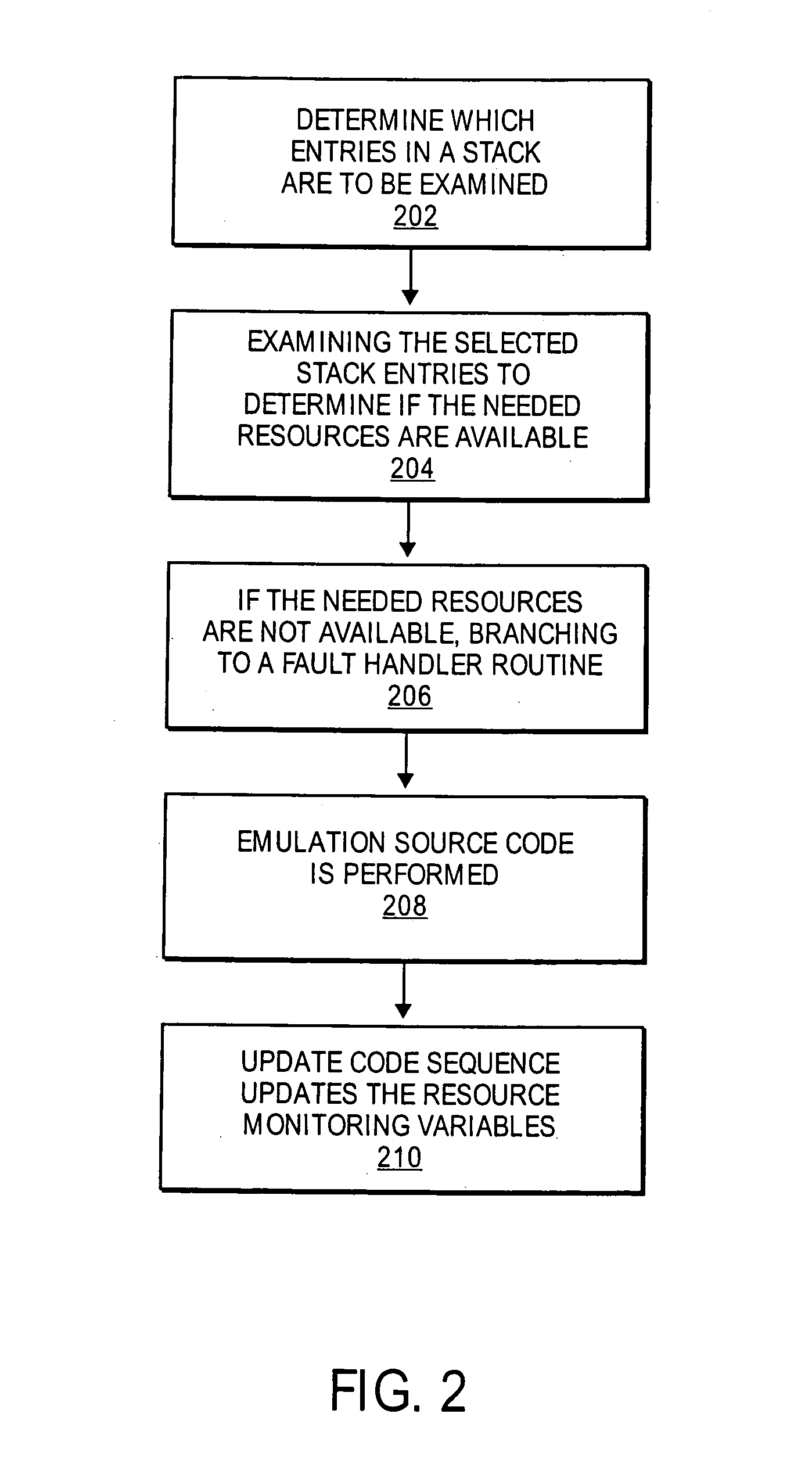
Method and apparatus for stack emulation during binary translation
InactiveUS7219335B1Error detection/correctionSpecific program execution arrangementsComputer hardwareBinary translation
Owner:INTEL CORP
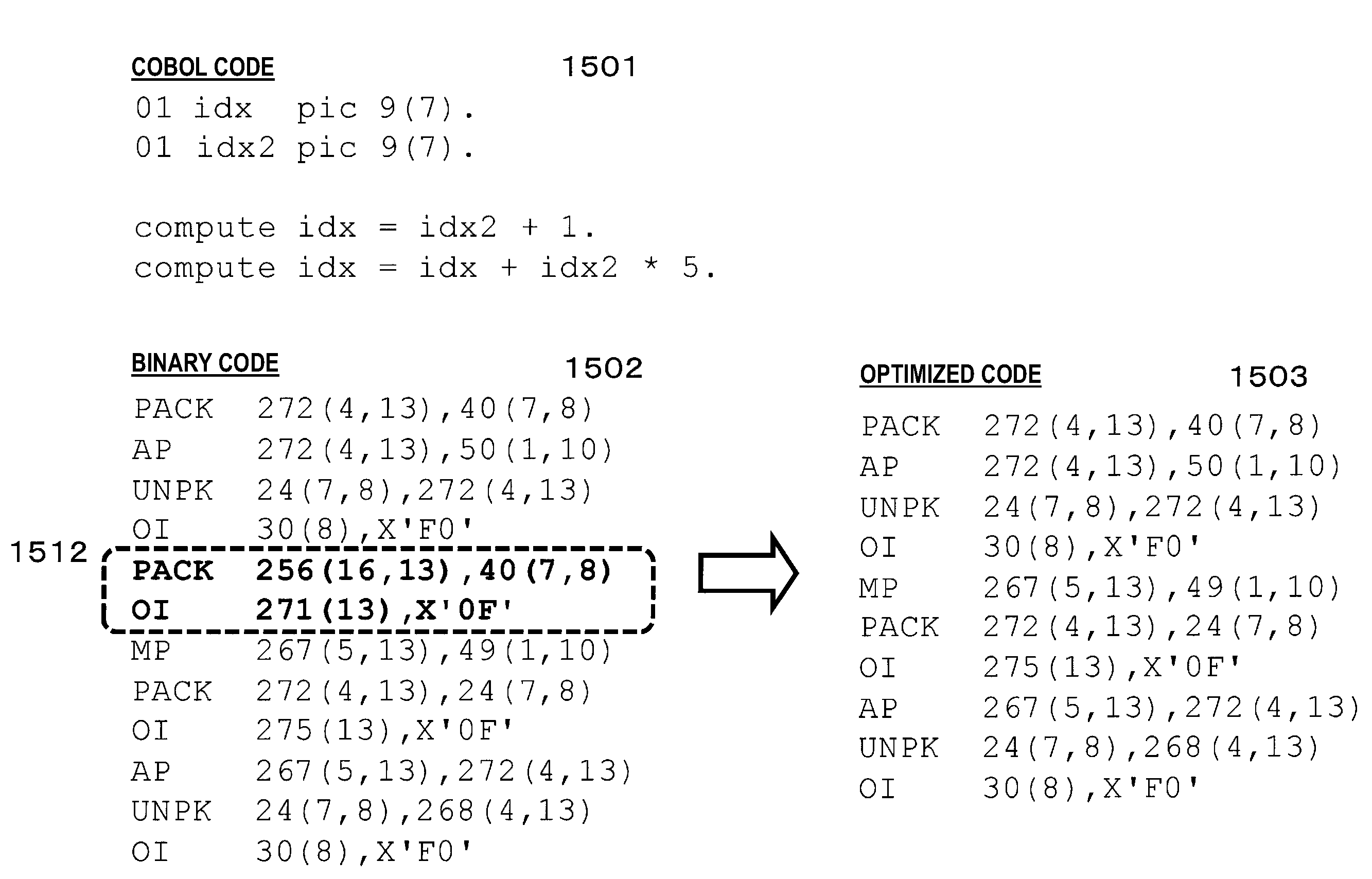
Method for optimizing binary codes in language having access to zoned decimal type variable, optimization apparatus and computer program for the same
An optimization technique for optimizing binary codes in a language having access to a zoned decimal type variable and applicable to binary codes including instructions which can cause side effects. The optimization technique includes: detecting, for each variable, an area including access to a zoned decimal type variable and not including an instruction that can cause a side effect, from the binary codes read into a memory; and performing, in the detected area, a process for converting a zoned decimal type variable to a binary type variable, a process for deleting such a pack / unpack code that a converted result does not change even in case the pack / unpack code is deleted, from the binary codes, or a process for performing combination of the processes.
Owner:IBM CORP
Multi-level hybrid vulnerability automatic mining method
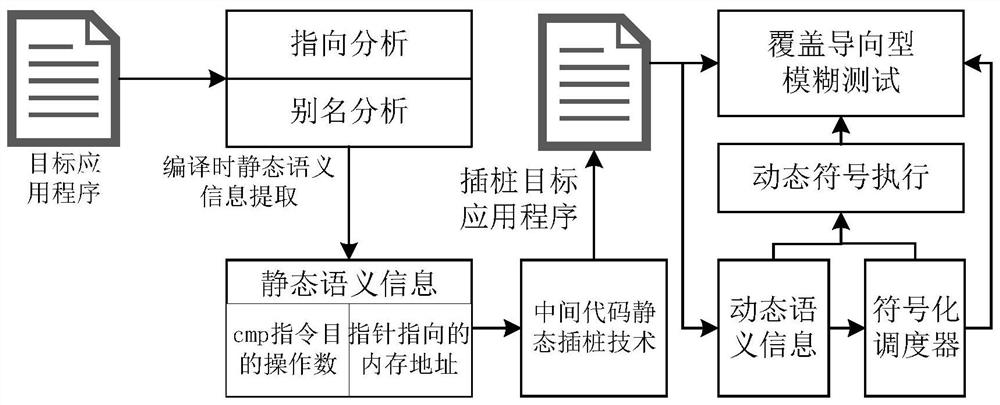
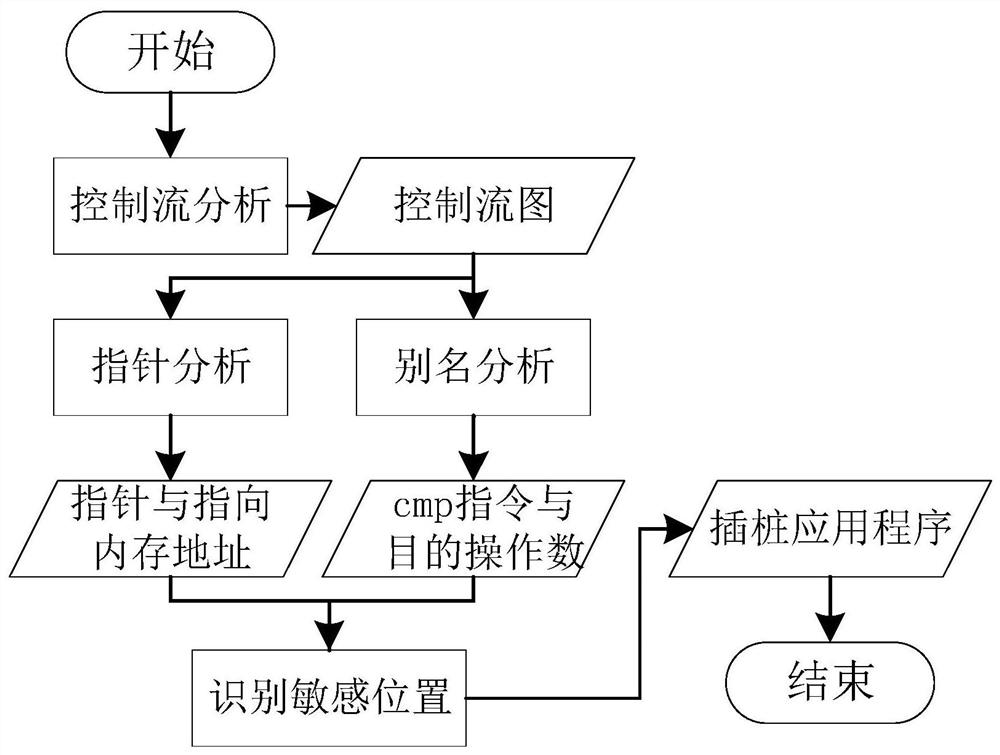
ActiveCN111859388ARich semantic informationImplement extractionSoftware testing/debuggingPlatform integrity maintainanceMemory addressRepresentation language
The invention belongs to the technical field of computers, and particularly relates to a multi-level hybrid vulnerability automatic mining method, which comprises the following steps: S1, obtaining pointer distribution and assignment processes in a program by utilizing pointer analysis through a static analysis technology, and recording memory address positions pointed by all pointers; obtaining adestination operand of the CMP type instruction by using an alias analysis technology so as to clarify a jump address of the target program; and S2, realizing instrumentation of the monitoring code to the key position of the target program through an intermediate code static instrumentation technology. According to the invention, the binary executable program is translated into the middle-layer representation language of the compiler, and compared with the binary executable program, the middle-layer representation language source code obtained through processing of the method has more semantic information; compared with C / C + + language analysis, the static analysis technology for the LLVM IR intermediate representation language can realize finer-grained static semantic information extraction during compiling.
Owner:GUANGZHOU UNIVERSITY
Method and device for realizing cross-platform multi-language development, medium and electronic equipment
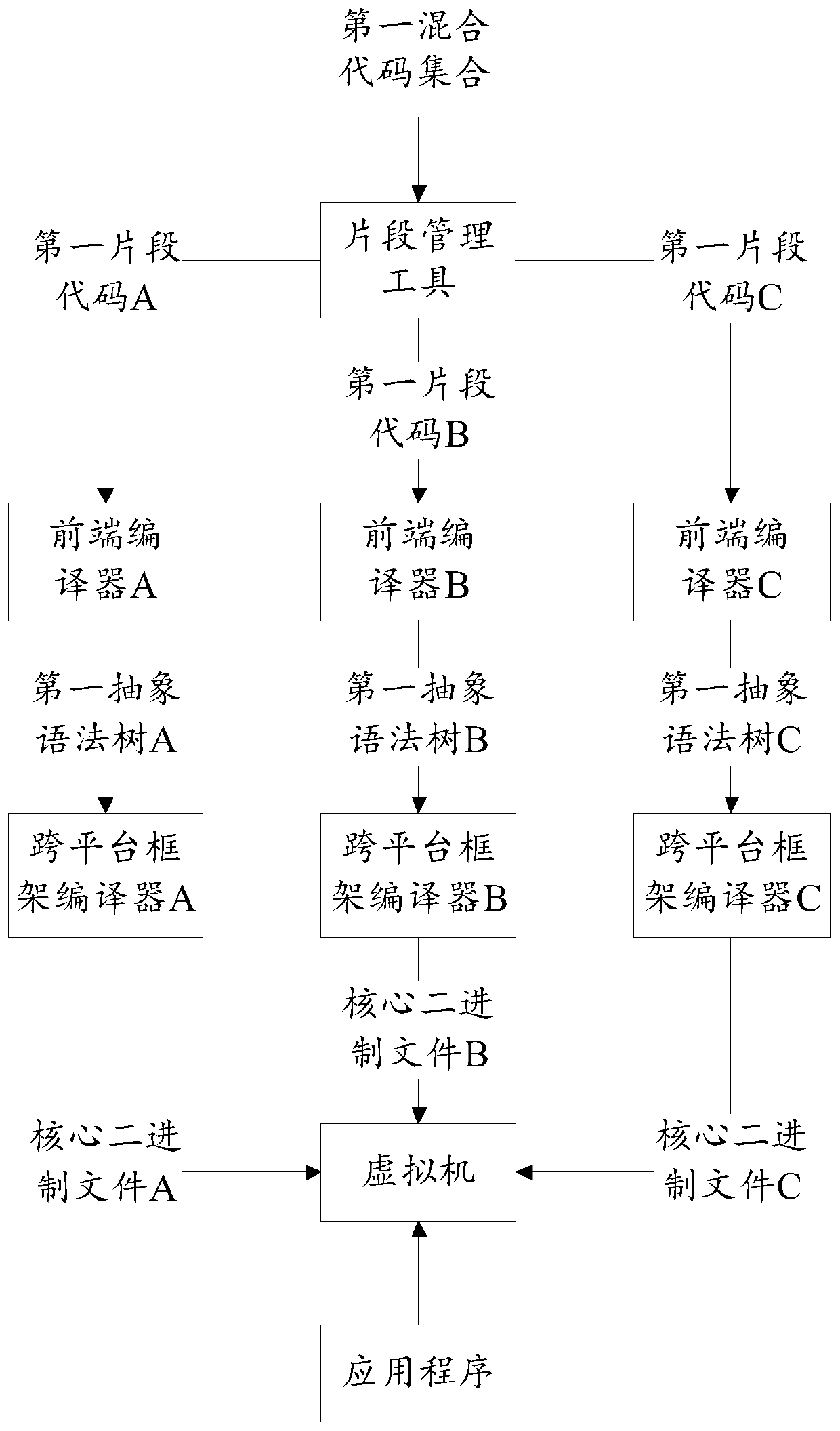
PendingCN111381817AImplement mixed loadingEasy to implementProgramming languages/paradigmsProgram code adaptionEngineeringAbstract syntax tree
The invention provides a method and device for realizing cross-platform multi-language development, a medium and electronic equipment. The method comprises the steps of obtaining a first mixed code set; analyzing the first mixed code set to obtain a first fragment code corresponding to each programming language; analyzing all first fragment codes corresponding to the programming language based onthe grammatical analysis model of each programming language, and generating a first abstract syntax tree corresponding to the programming language; utilizing the cross-platform framework compiler of each programming language to compile a first abstract syntax tree corresponding to the programming language, and generating a core binary file corresponding to the programming language; wherein the core binary file can run in a virtual machine of a cross-platform framework.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method and Apparatus for Range Derivation in Context Adaptive Binary Arithmetic Coding
Owner:HFI INNOVATION INC
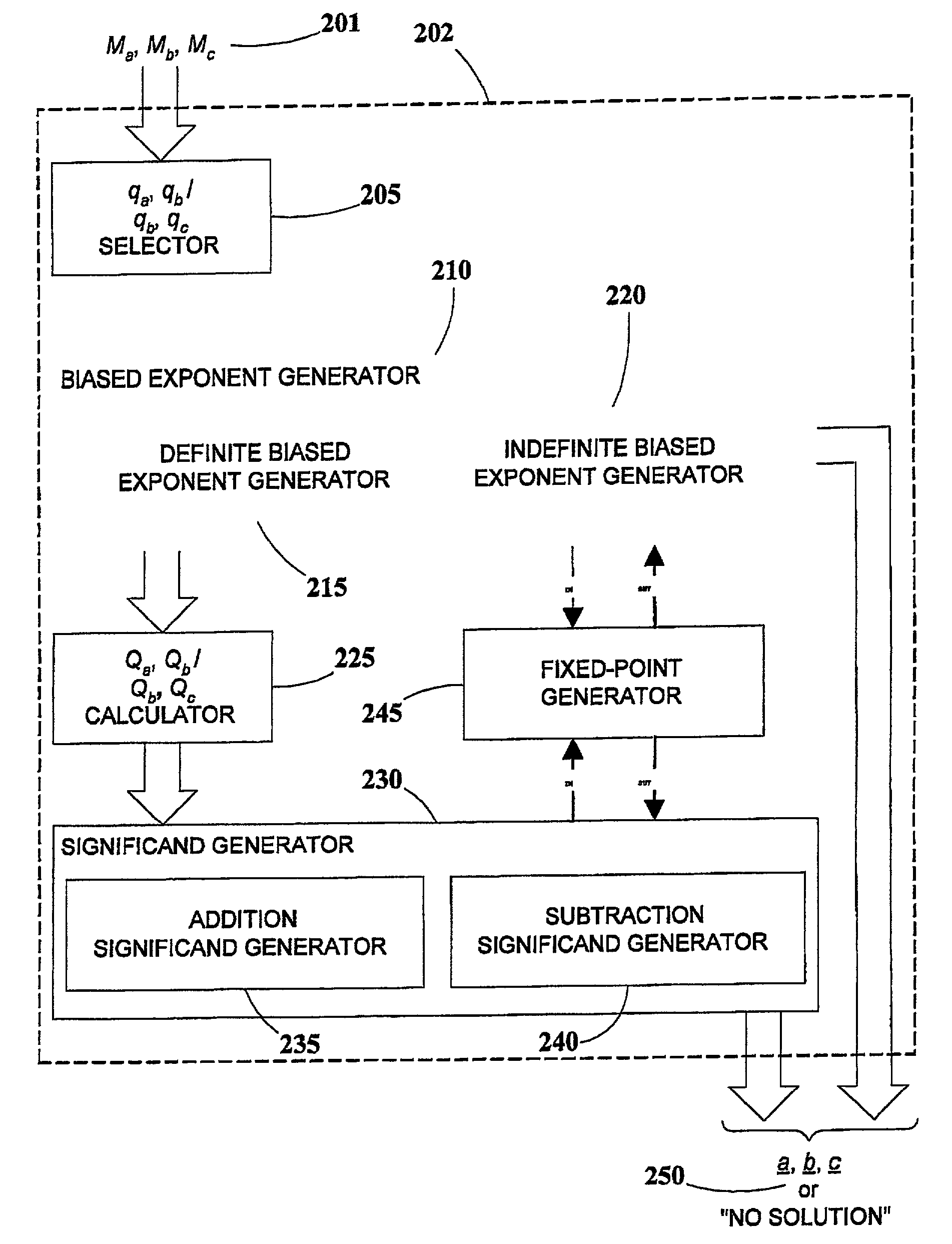
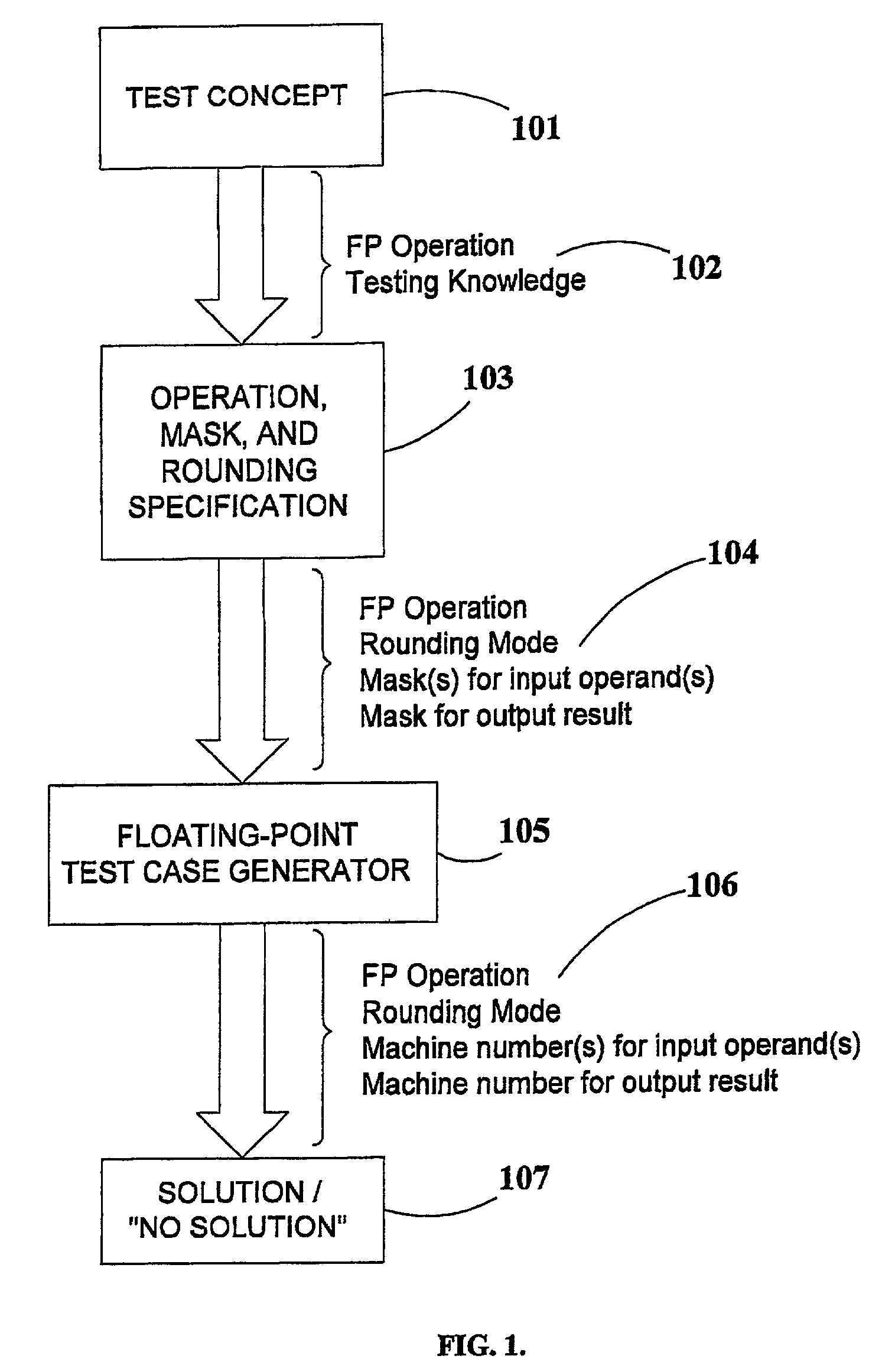
Generation of mask-constrained floating-point addition and subtraction test cases, and method and system therefor
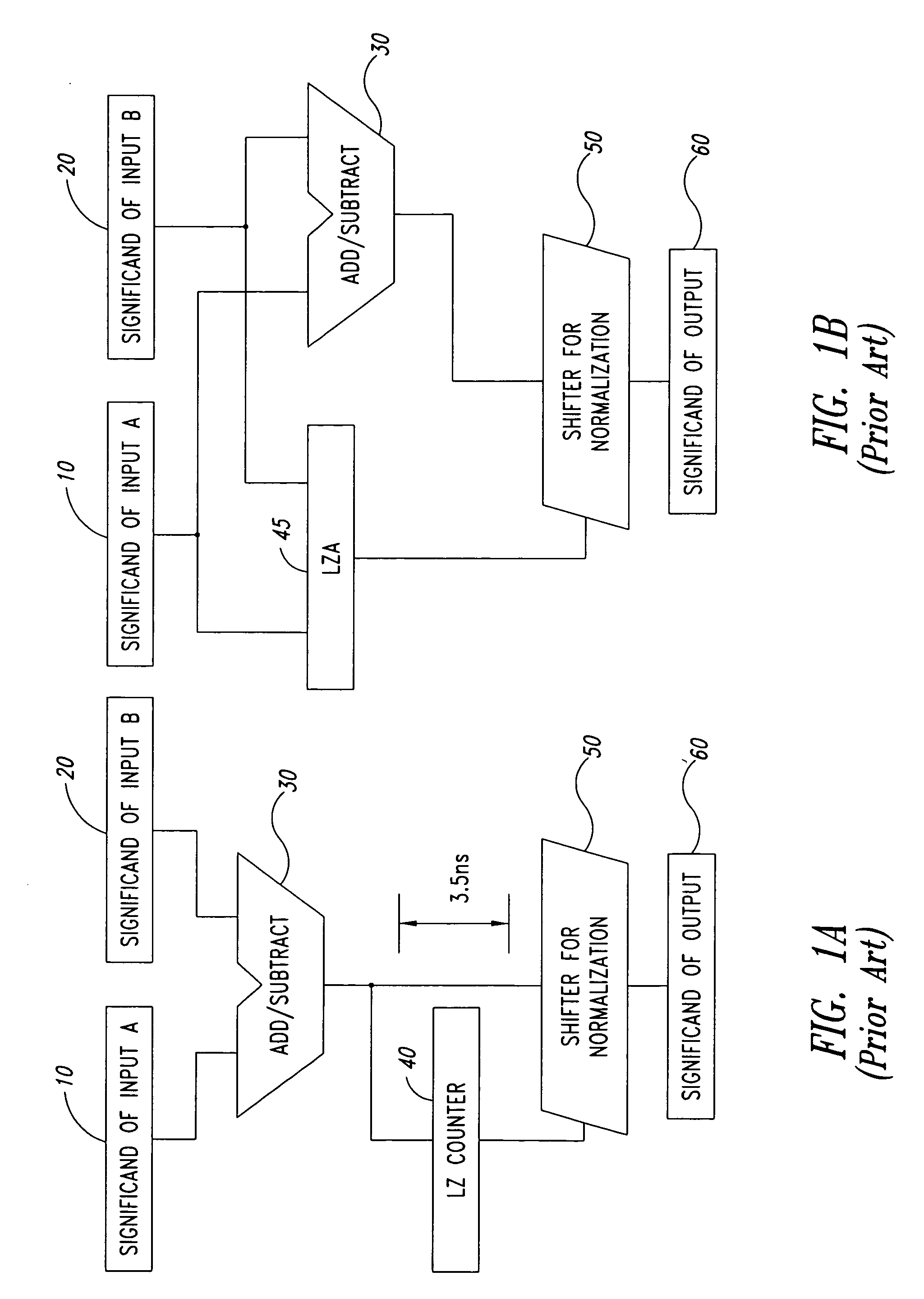
ActiveUS7028067B2Comprehensive verificationElectronic circuit testingError detection/correctionSignificandIEEE floating point
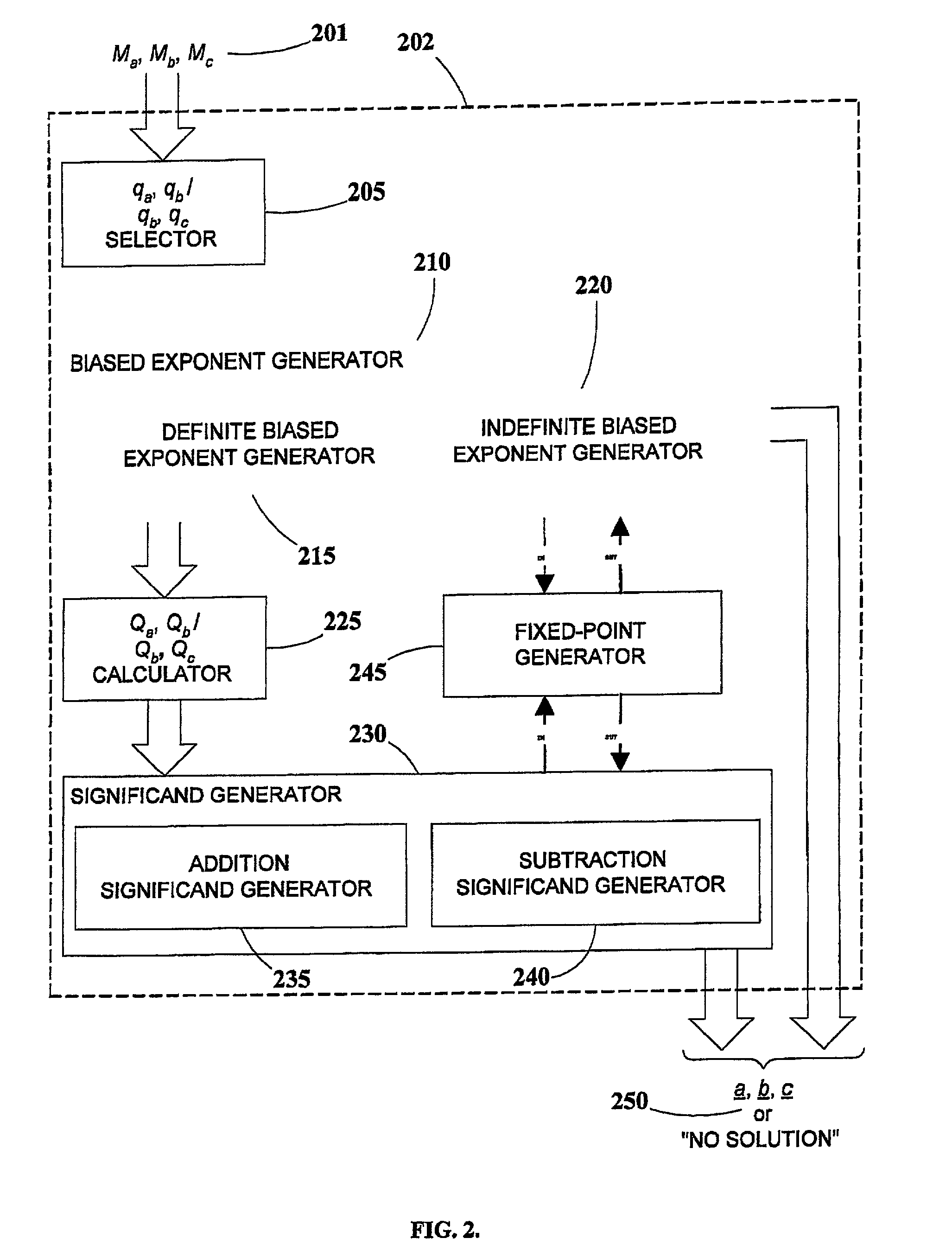
A method and system for generating numerical test cases for testing binary floating-point arithmetic units for addition and subtraction operations, in order to verify the proper operation of the units according to a specified standard. The space for eligible test-cases is compatible with masks which stipulate the allowable forms of the operands and the result, including constant as well as variable digits in both the exponent and significand fields. The test-cases, which are generated randomly, cover the entire solution space without excluding any eligible solutions. All standard rounding modes are supported, and if a valid solution does not exist for a given set of masks, this fact is reported. The method is general and can be applied to any standard, such as the IEEE floating-point standard, in any precision. A system according to the present invention utilizes a set of sub-generators for biased exponents and significands, and also incorporates a fixed-point generator for performing calculations common to the other generators. The method relies on searching for solutions based on feasible carry sequences, and is also capable of generating test-cases for mask-constrained carry sequences.
Owner:TWITTER INC
Digital Implementation of Fractional Exponentiation
InactiveUS20070282936A1Efficient preparationComputationally efficientDigital function generatorsNumbering systemComputer science
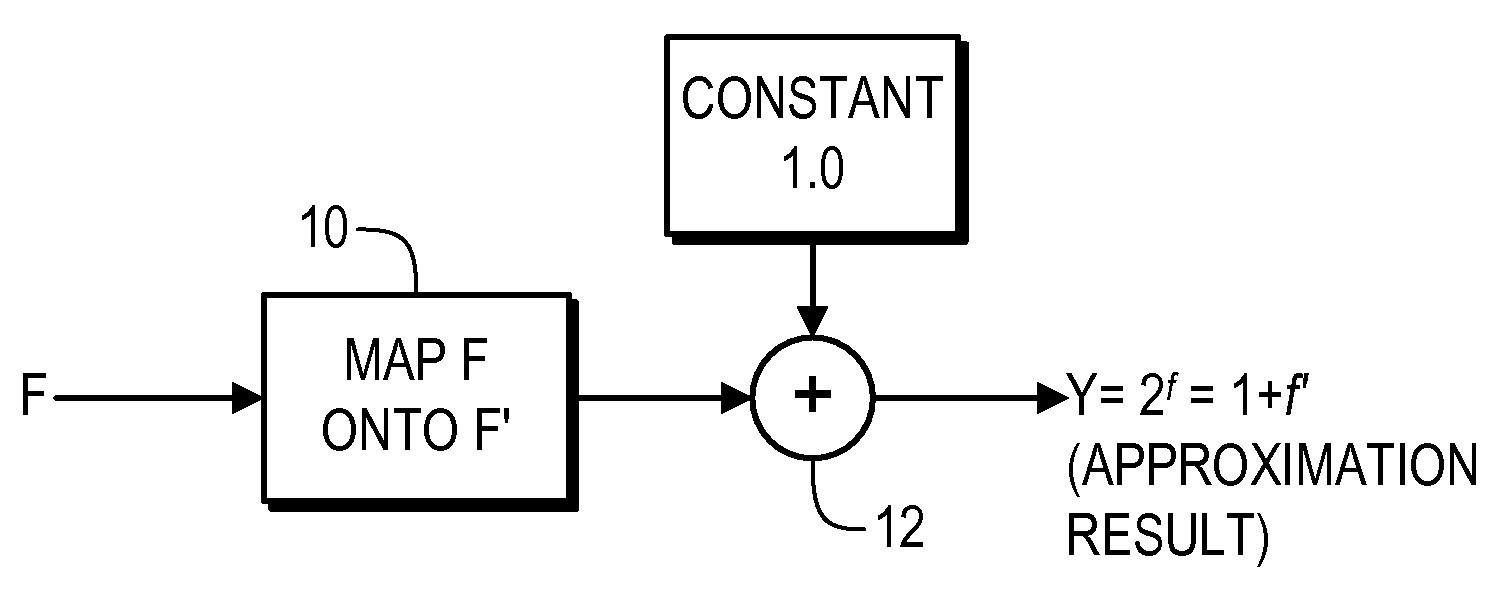
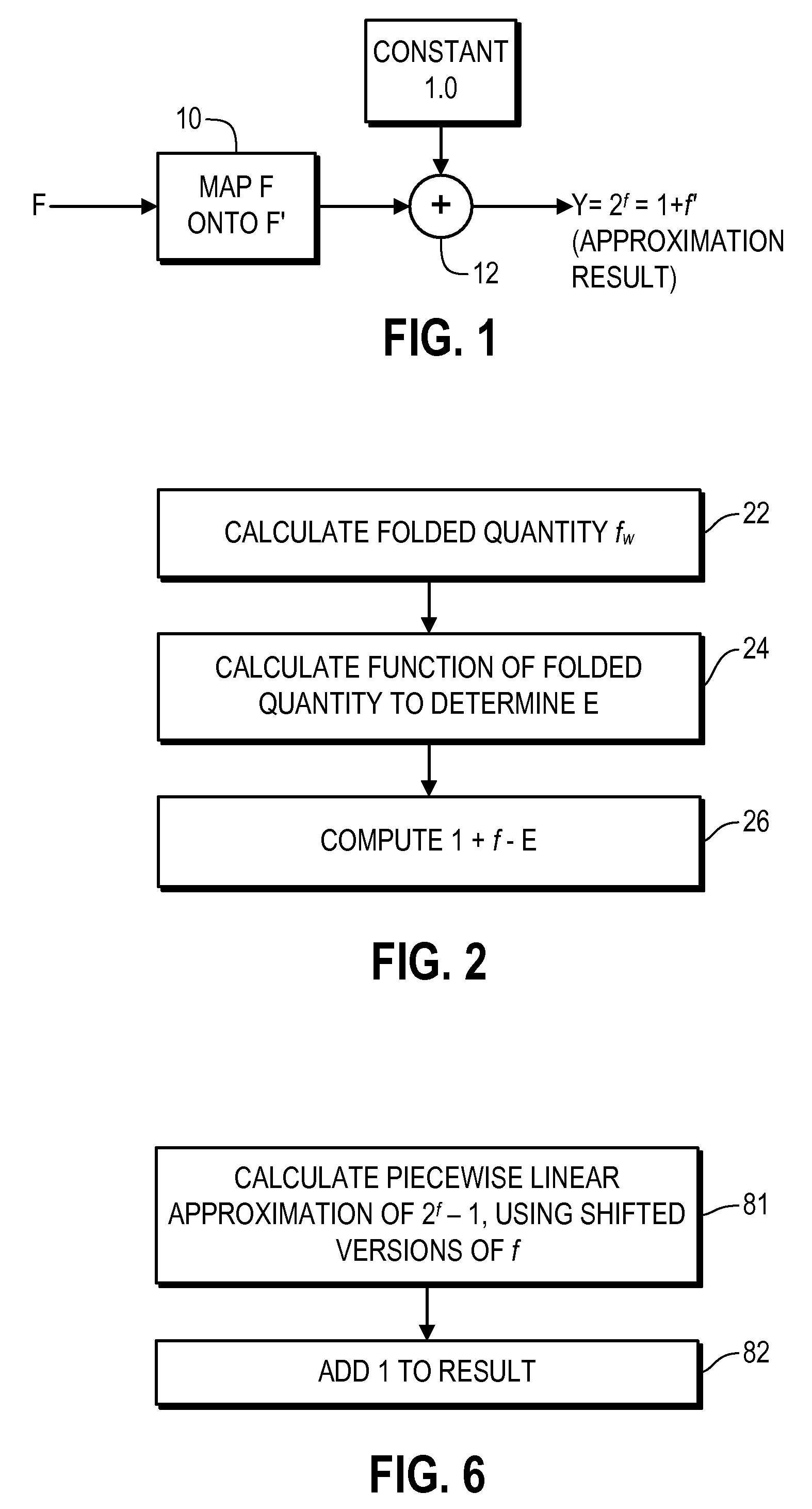
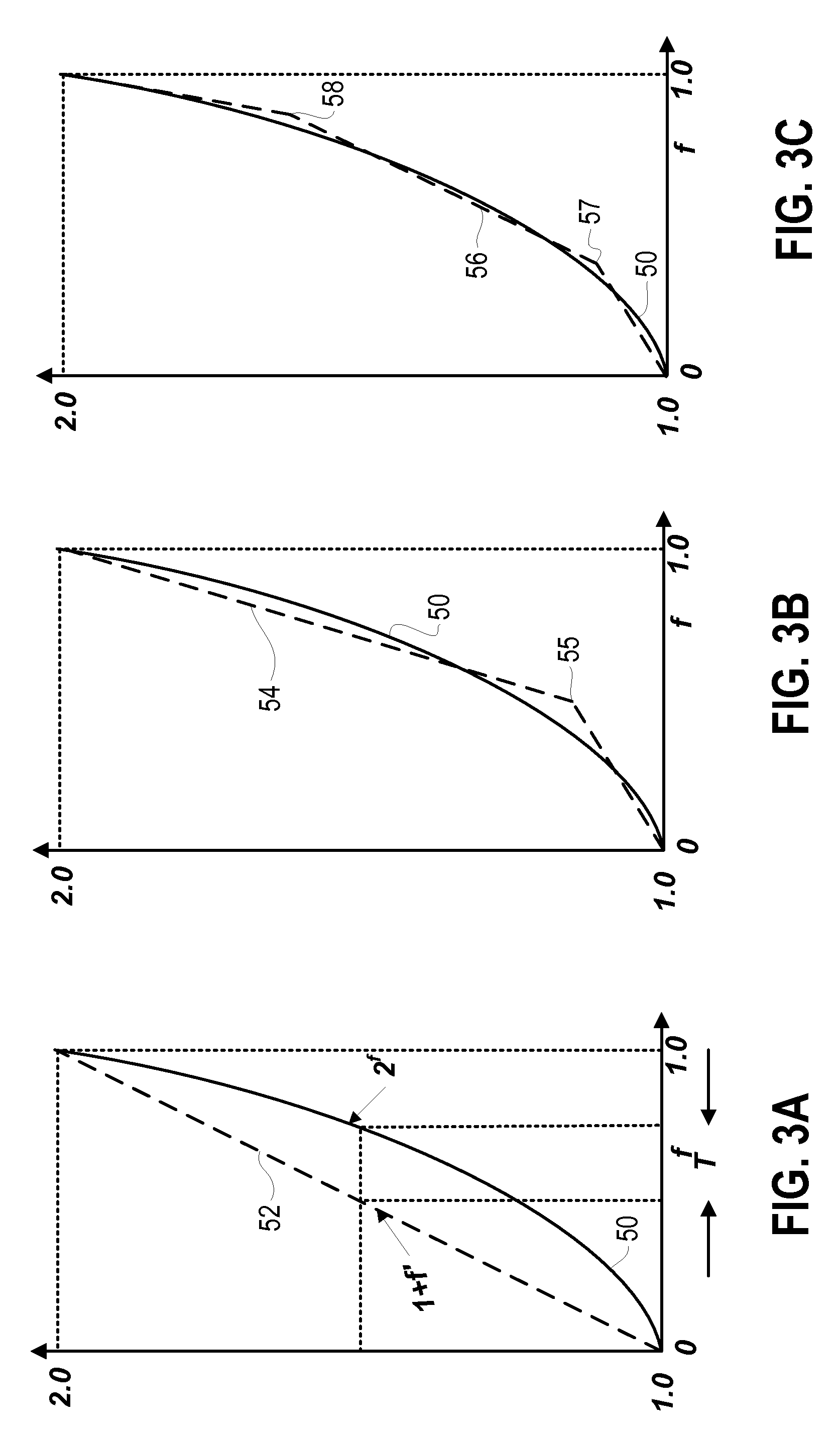
Provided are digital processing apparatuses and techniques for estimating the fractional exponentiation of the base number 2, i.e., 2f where f is a fractional value. In one representative embodiment, a calculation is made of a folded quantity, which is equal to 1−f if f is greater than a specified threshold and is equal to f otherwise; then, a function of the folded quantity is calculated; and finally, the function of the folded quantity is subtracted from the fraction f and 1 is added. In another embodiment, 2f is approximated by calculating 1+f′ in the binary numbering system.
Owner:INTEL CORP
Circuit protection system and method
ActiveUS10331912B2Low costDetecting faulty computer hardwareInternal/peripheral component protectionBoolean circuitAlgorithm
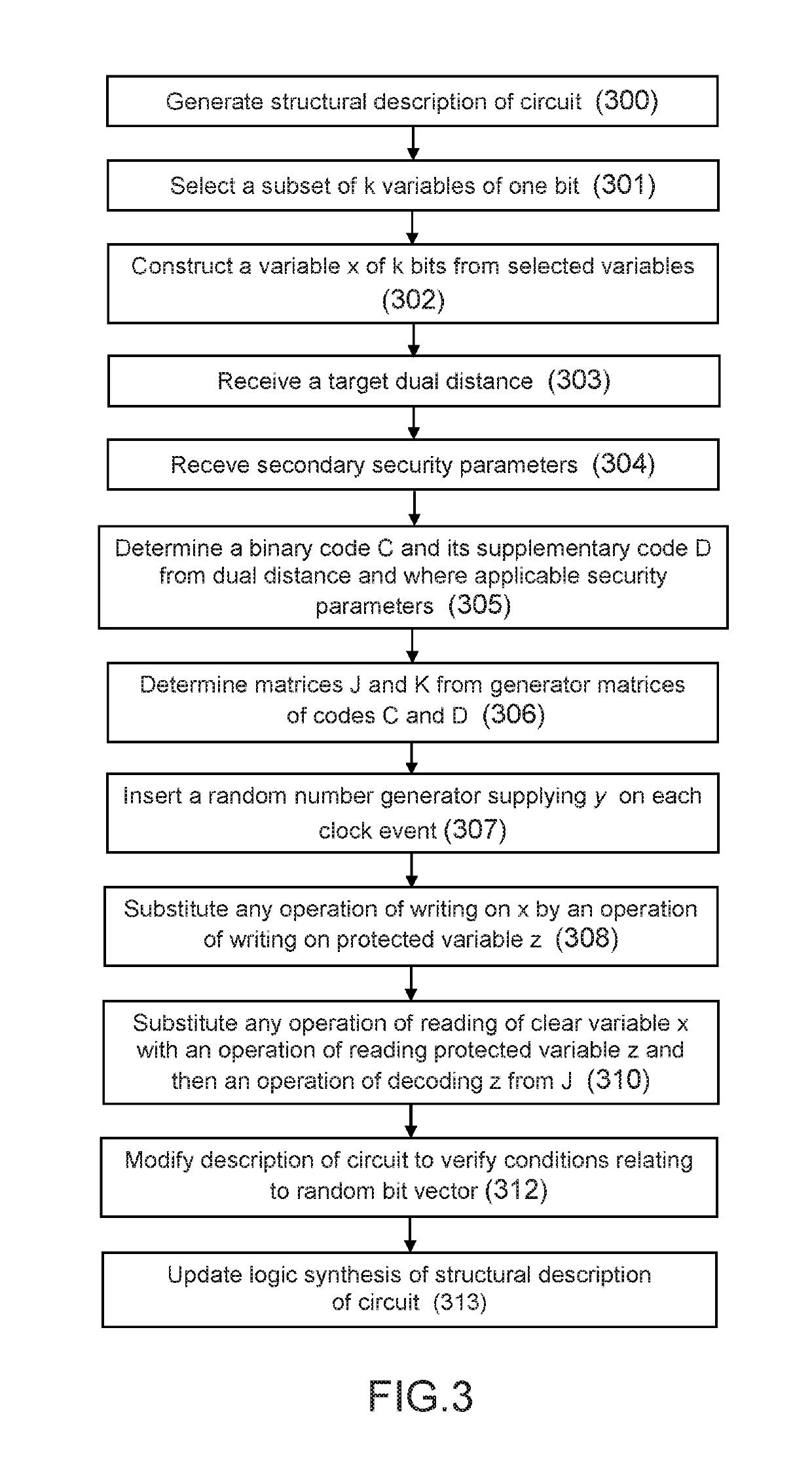
The invention proposes a method of protection of a Boolean circuit associated with a structural description of the circuit comprising elementary Boolean variables, each represented by one bit, the method comprising the steps consisting in:selecting a set of k elementary Boolean variables of the circuit as a function of predefined selection criteria,constructing a variable x represented by k bits by concatenation of the k selected variables in accordance with a chosen order,determining a binary code C comprising a set of code words and belonging to a given vector space and the supplementary code D of said binary code C as a function of a condition bearing on the dual distance of said supplementary code D, said binary code C having a length n and a size 2k, where k designates the number of bits representing said variable x;substituting the variable x in the structural description of the Boolean circuit with a protected variable z represented by n bits so that:any operation of writing on the variable x in the circuit is substituted with an operation of writing on the variable z, the variable z being generated by adding the variable x encoded by said code C to a random bit vector y encoded by the supplementary code D, andany operation of reading the variable x in the circuit is substituted with an operation of reading the value of the protected variable z and an operation of decoding said read value of the protected variable z using a decoding matrix J of size (n×k) determined from the binary code C and the supplementary code D of the binary code C.
Owner:SECURE IC
A coder and method and device to realize adaptive arithmetic code
InactiveCN1964496AGuaranteed average speedImprove coding efficiencyTelevision systemsDigital video signal modificationAlgorithmEngineering
Owner:WUXI ZGMICRO ELECTRONICS CO LTD
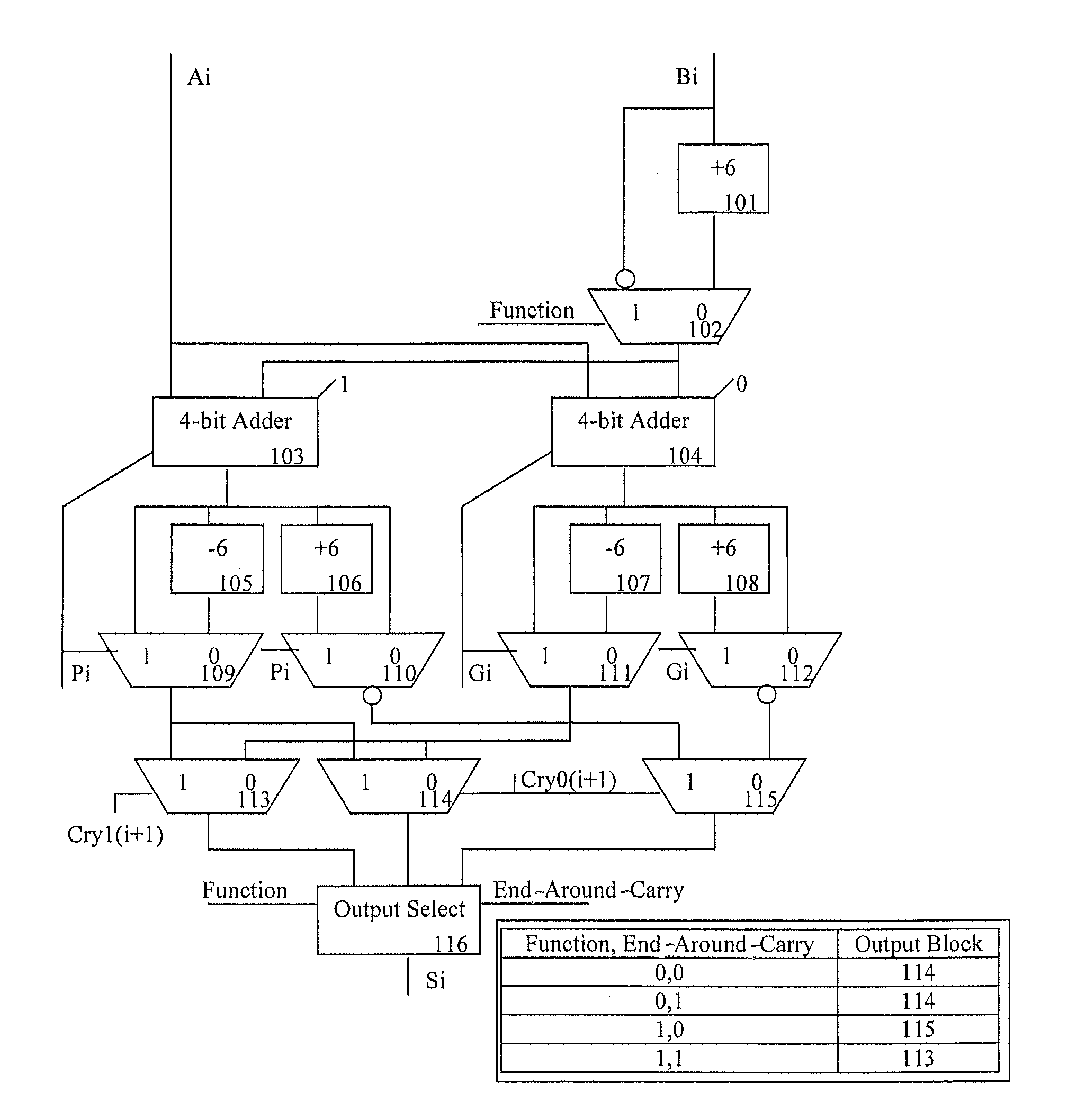
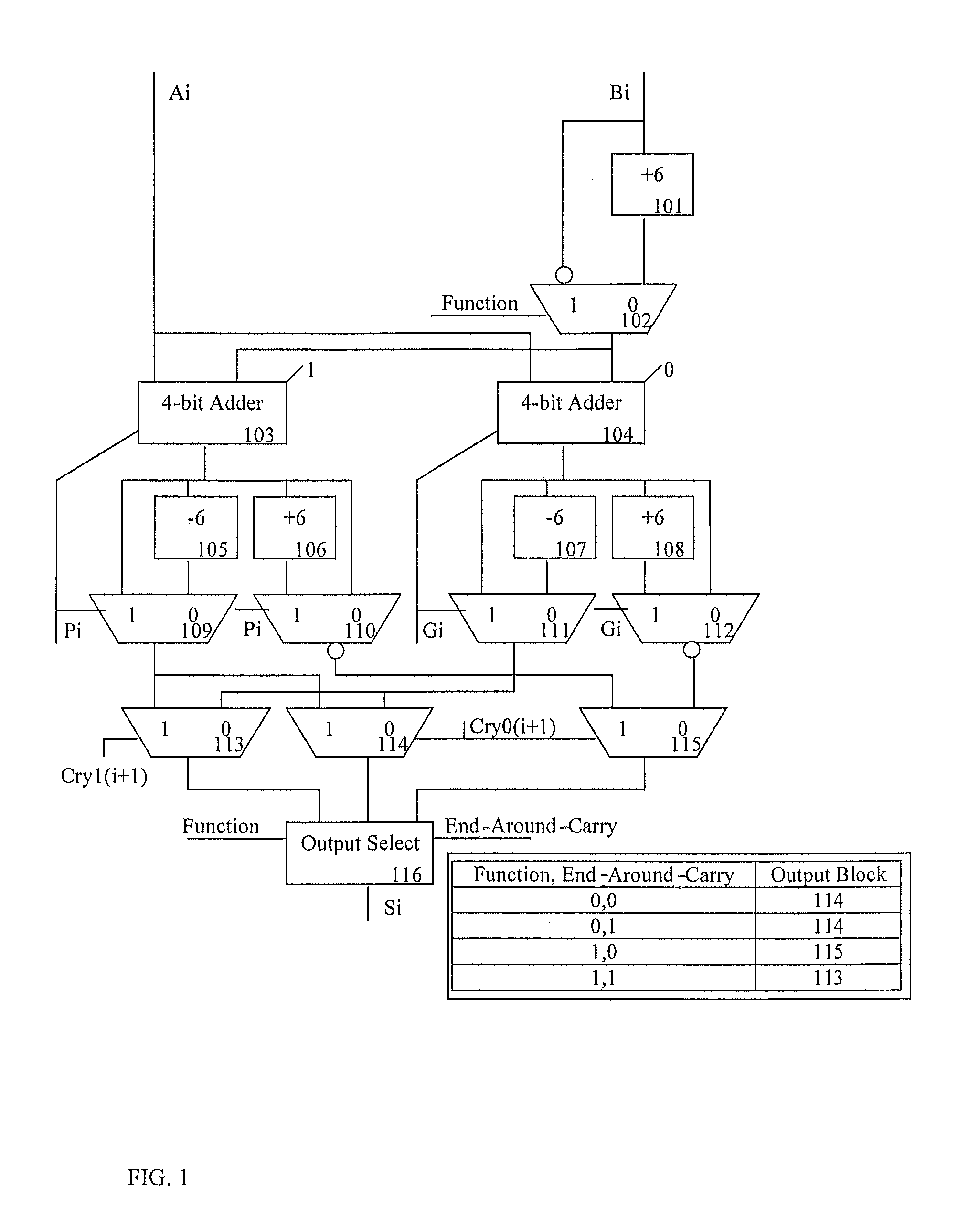
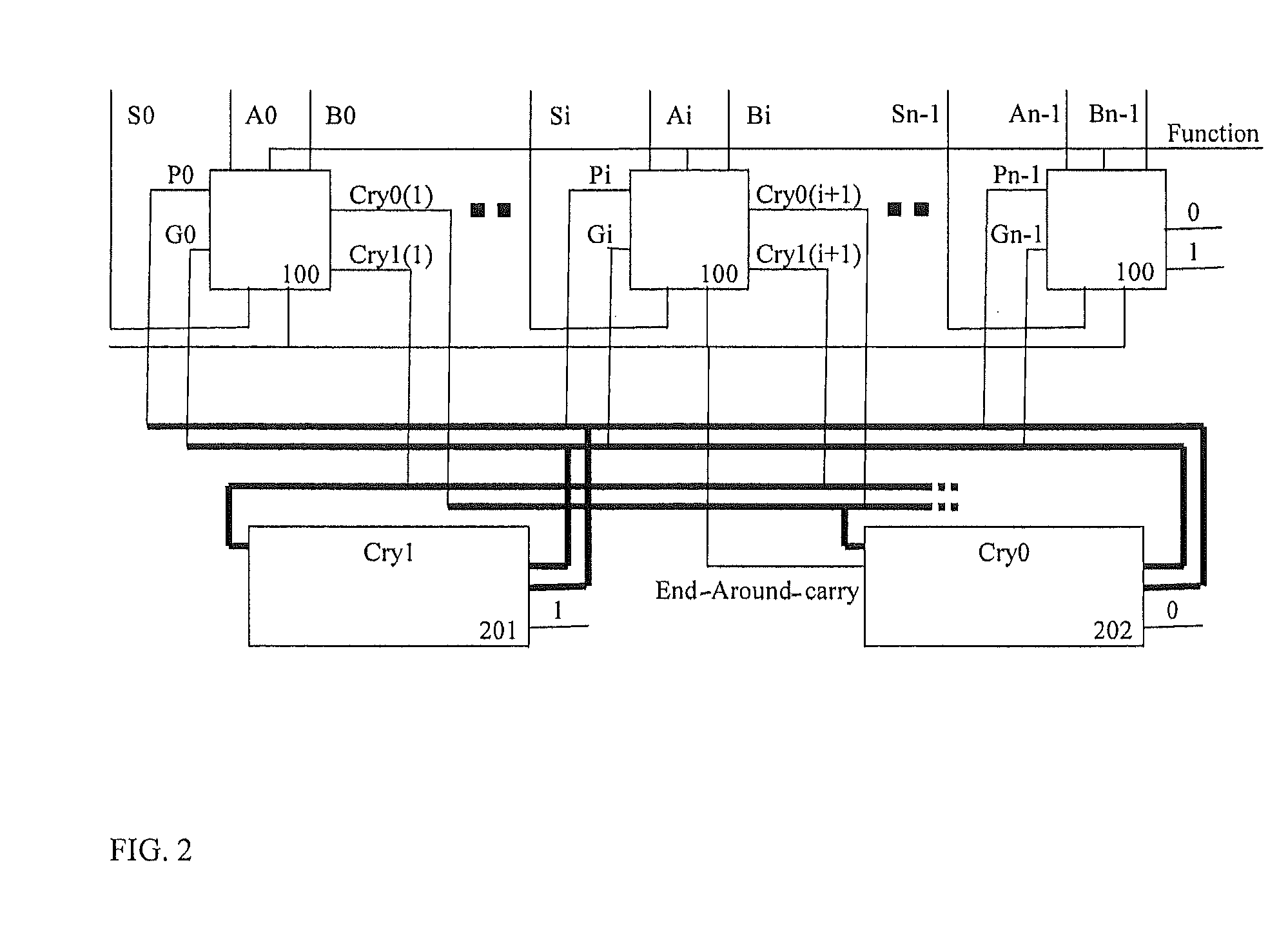
Decimal adder with end around carry
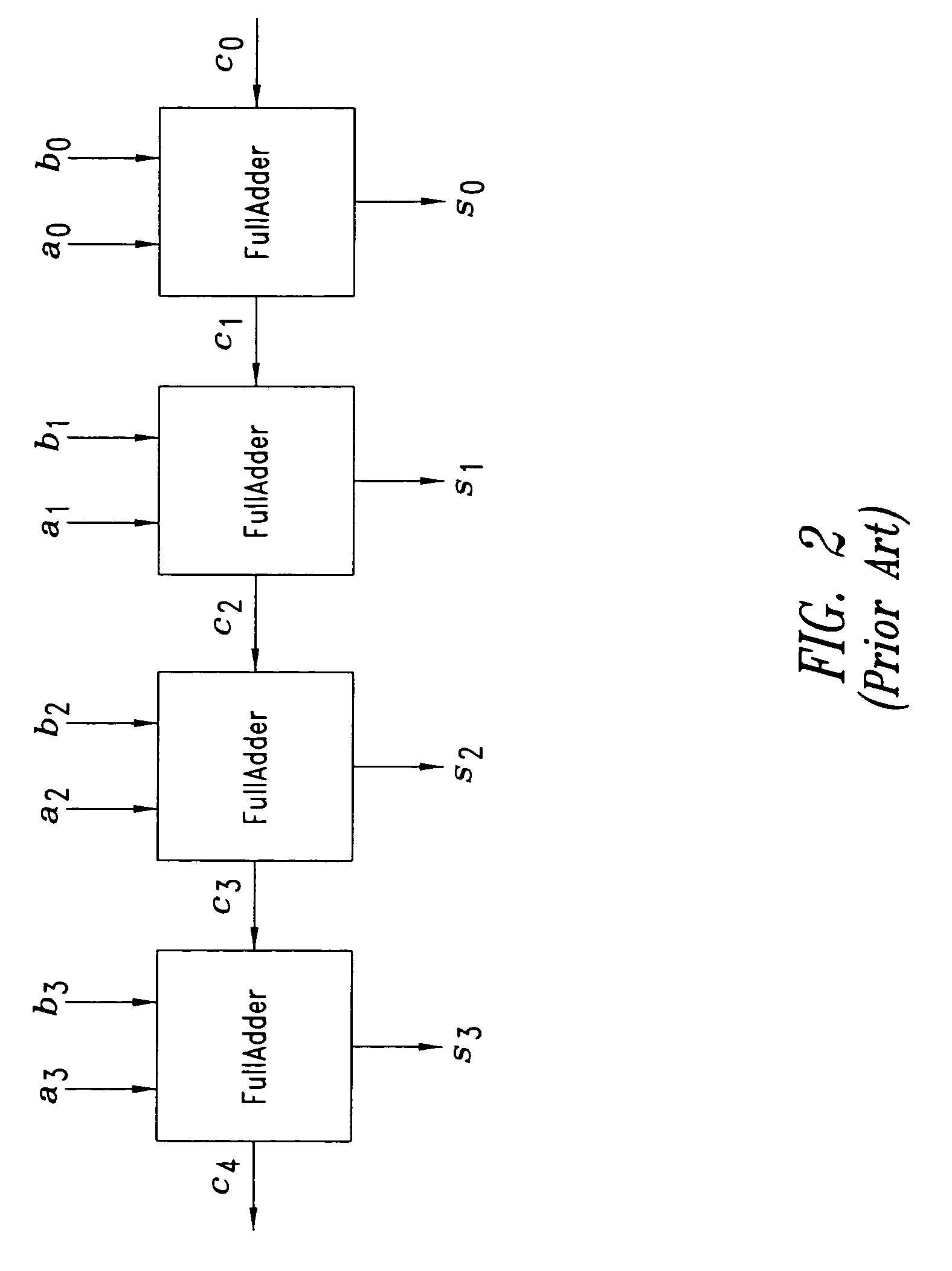
InactiveUS20110320514A1Computations using contact-making devicesComputation using non-contact making devicesAlgorithmEngineering
Binary code decimal (BCD) arithmetic add / subtract operations on two BCD numbers independent of which BCD number is of a greater magnitude include, responsive to the BCD arithmetic add / subtract operation being a subtract operation, performing a BCD arithmetic subtraction operation on a first BCD number and a second BCD number, the first BCD number having a first magnitude and the second BCD number having a second magnitude. The first magnitude is greater than, equal to, or less than the second magnitude. The performing includes: in parallel to a carry generation, partial sums or partial differences of the first and second BCD numbers are computer such that a final result in signed magnitude form is selectable from the partial sums or differences based on carry information without any post processing steps.
Owner:IBM CORP
Improved binary-system left-shifting modular inversion algorithm
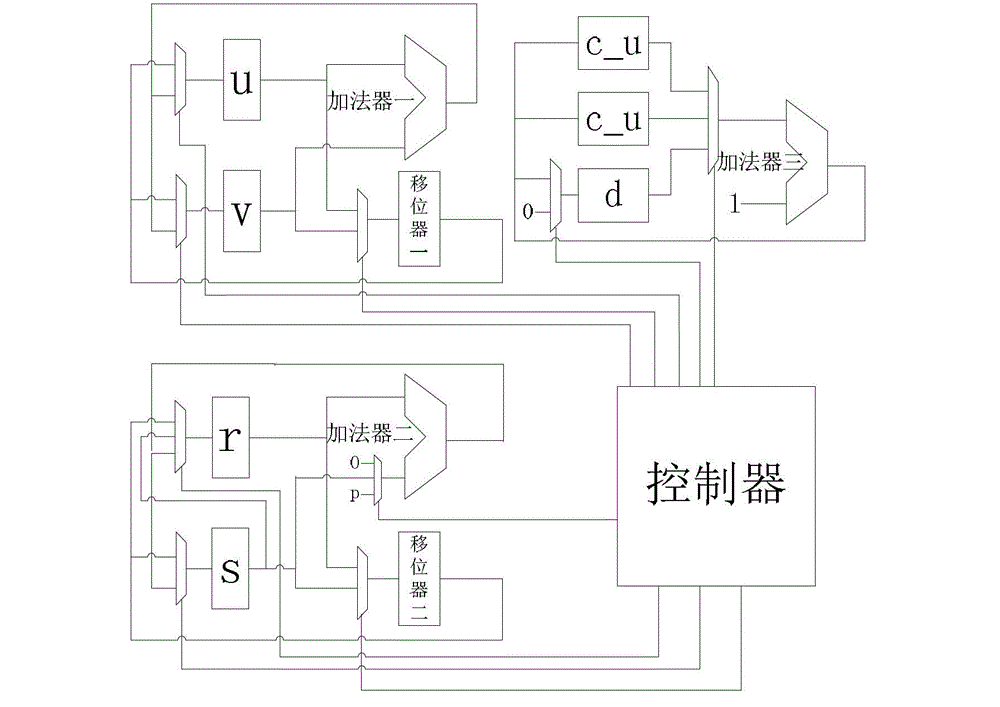
InactiveCN103336680AReduce occupancyReduce areaComputations using residue arithmeticIntermediate variableComputer science
The invention relates to an improved binary-system left-shifting modular inversion algorithm. For a given modulus p, during a process of calculating the modular inversion, the condition of skipping out of circulation of the bits of the p is c_u=n-1 or c_v=n-1, namely, the comparison between c_u as well as c_v and the constant n-1, wherein u and v are intermediate variables of n bits for storing left-shifted data and are respectively initialized as p and a; r is the intermediate variable for obtaining modular inversion through left shifting and is initialized as 0; after the algorithm is ended, the value in r is a resolved modular inversion result; c_u shows the times of the left shifting; and c_v shows the times of the left shifting of the v. The invention also provides a circuit structure for realizing the algorithm. The algorithm provided by the invention has simpler operation steps and occupies fewer storing units, so that the circuit area and the circuit power consumption are reduced, and a low power consumption requirement of a low-end code system is preferably met.
Owner:TSINGHUA UNIV
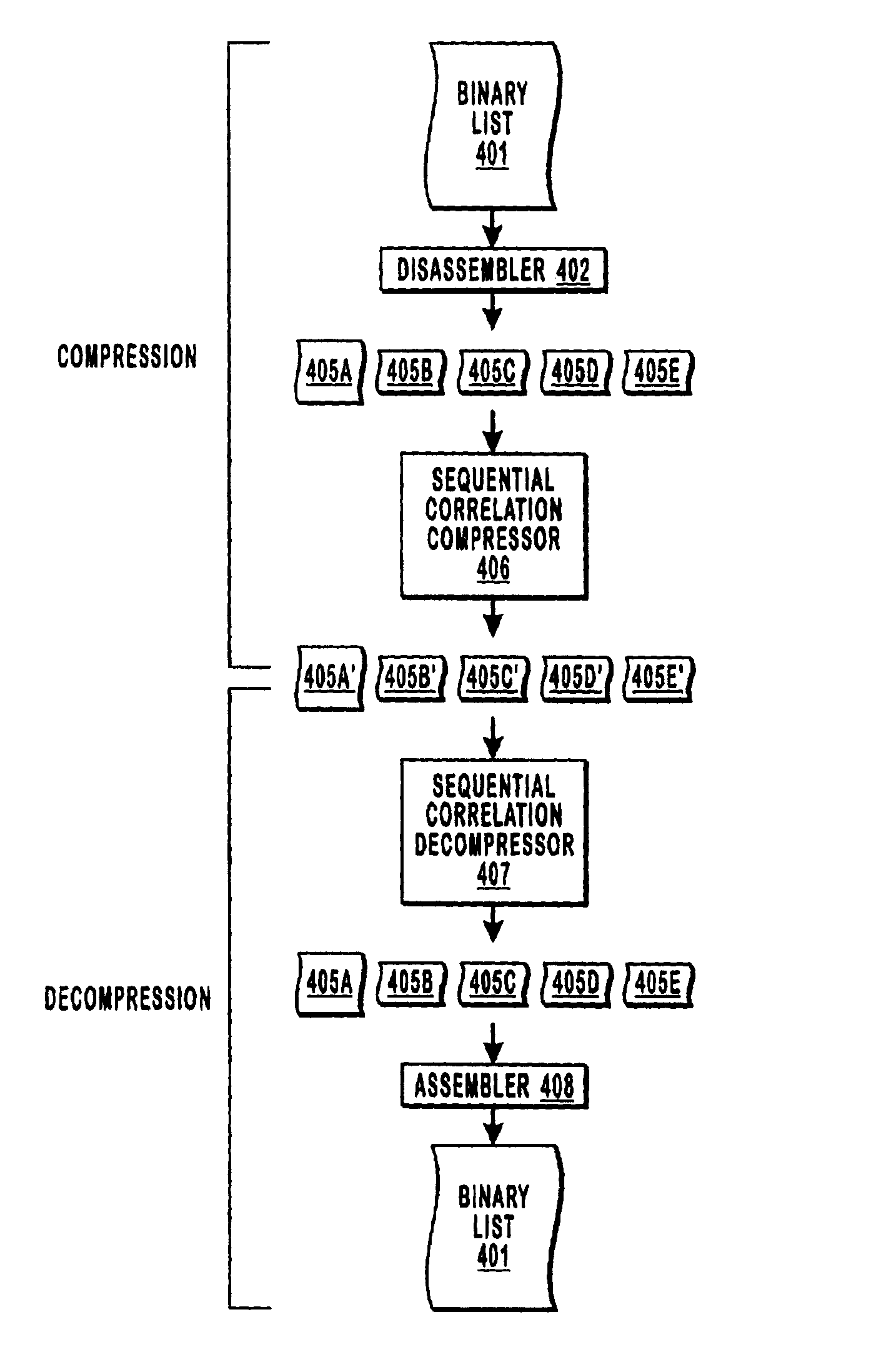
Compression of program instructions using advanced sequential correlation
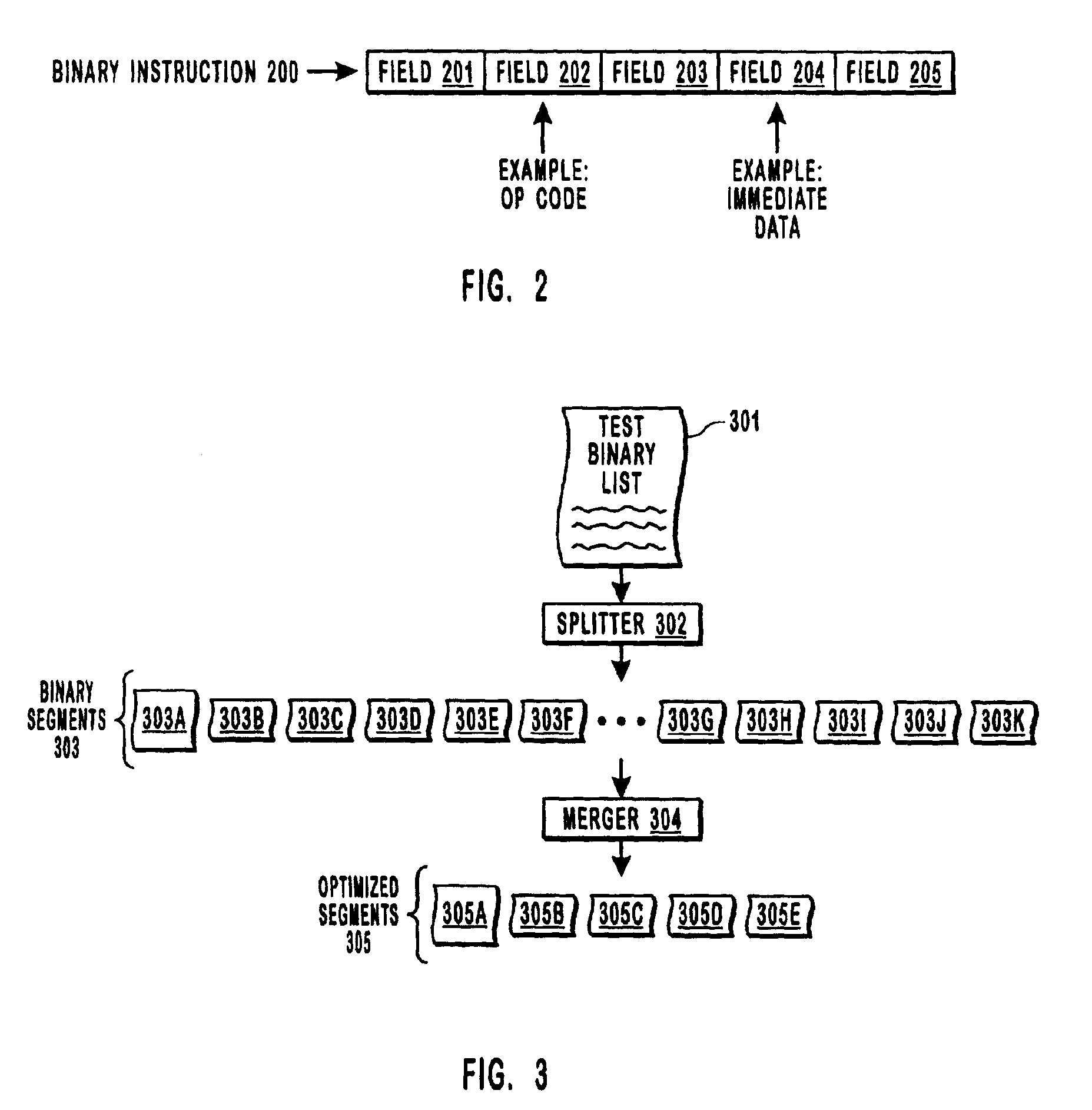
InactiveUS6907516B2Reduce compressionMeet cutting requirementsBinary to binaryCode conversionProgram instructionAlgorithm
Compressing program binaries with reduced compression ratios. One or several pre-processing acts are performed before performing compression using a local sequential correlation oriented compression technology such as PPM, or one of its variants or improvements. One pre-processing act splits the binaries into several substreams that have high local sequential correlation. Such splitting takes into consideration the correlation between common fields in different instructions as well as the correlation between different fields in the same instruction. Another pre-processing reschedules binary instructions to improve the degree of local sequential correlation without affecting dependencies between instructions. Yet another pre-processing act replaces common operation codes in the instruction with a symbols from a second alphabet, thereby distinguishing between operation codes that have a particular value, and other portions of the instruction that just happen to have the same value. Local sequential correlation compression such as PPM is then performed.
Owner:MICROSOFT TECH LICENSING LLC
Software similarity measurement method and device
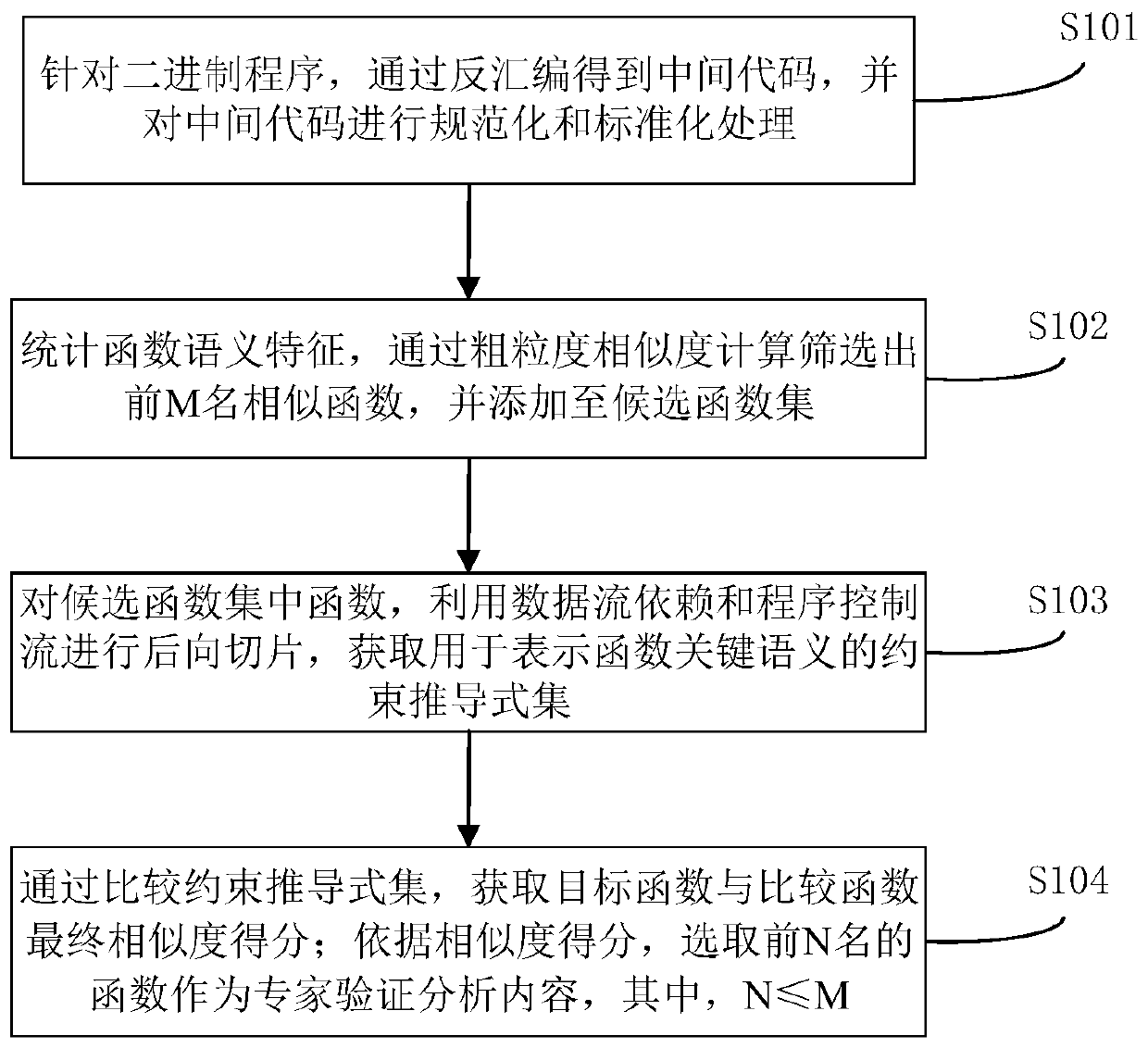
ActiveCN110990058AReduce varianceEfficient screeningDecompilation/disassemblySoftware metricsOperational systemAlgorithm
The invention relates to a software similarity measurement method and device. The method comprises the following steps: acquiring an intermediate code through disassembly for a binary program, and carrying out the normalization and standardization on the intermediate code; counting semantic features of functions, screening first M similarity functions through coarse-grained similarity calculation,and adding the first M similarity functions to a candidate function set; conducting backward slicing on the functions in the candidate function set through data flow dependence and program control flow, and acquiring a constraint derivation formula set used for representing key semantics of the functions; acquiring a final similarity score of the target function and the comparison function by comparing the constraint derivation formula set; and according to the similarity score, selecting the first N functions as expert verification analysis contents. According to the method, differences of programs under different system architectures, operating systems, compilers and optimization options are reduced by preprocessing codes, patch upgrading functions similar to vulnerability function semantics are screened out through extraction and comparison of a function constraint derivation formula, and accuracy is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Method for optimizing binary code in language having access to binary coded decimal variable, and computer and computer program
A method for optimizing binary code in a language having access to binary coded decimal variable. The method includes: generating a first compiler expression of the binary code; analyzing a use-definition and / or a definition-use for the first compiler expression; generating a second compiler expression by identifying logical binary coded decimal (BCD) variables in the first compiler expression; assigning temporary variables to the logical BCD variables, wherein the second compiler expression includes packed decimal operations and the assigned temporary variables; and converting a packed decimal operation in the second compiler expression and an assigned temporary variable to a decimal floating point (DFP) if sign information and precision information are not lost during conversion from BCD to DFP, wherein identifying logical BCD variables includes: in the use-definition and / or definition-use of operands, regarding an operand of definition and an operand of use as the same logical BCD variables.
Owner:IBM CORP
Method and system for high-speed floating-point operations and related computer program product
InactiveUS7899860B2Reduce errorsIncrease the areaComputation using non-contact making devicesDigital computer detailsTraffic capacityKarnaugh map
A circuit for estimating propagated carries in an adder starting from operands that include actual addition inputs or at least one earlier carry, the circuit performs statistical circuit operations with independent binary traffic for the operands. Preferably, this binary traffic is independent and equiprobable or quasi-equiprobable binary traffic, and the adder is a leading zero anticipatory logic integer adder producing a number having the same number of leading zeroes as the result of the integer addition performed. The carry value may be produced from a logic function (e.g., Karnaugh Map, Quine-McClusky) of the operands, as a logic combination of the operands covering all the 1s in the logic function.
Owner:STMICROELECTRONICS SRL
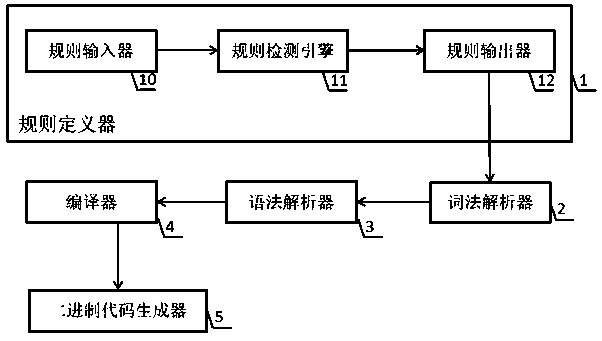
Matching rule engine supporting combined expression of multivariate protocol variables
PendingCN111580931AComparable to execution efficiencyImprove portabilityProgram code adaptionTransmissionCode generationDynamic compilation
The invention discloses a matching rule engine supporting a combined expression of multivariate protocol variables, and relates to the technical field of information. The matching rule engine is composed of a rule definition device, a lexical parser, a grammar parser, a compiler and a binary code generator. The rule definition device is composed of a rule input device, a rule detection engine anda rule output device. According to the matching rule engine, an extended Berkeley packet filtering technology is improved, so that rule grammar of the matching rule engine can be customized, and function nesting calling, function variable reference, cache range offset and nesting expression evaluation are supported. According to the matching rule engine, the JIT technology is adopted, dynamic compilation is carried out into machine code operation, the execution efficiency can be comparable to that of a C program, and good system portability is achieved.
Owner:江苏省互联网行业管理服务中心 +1
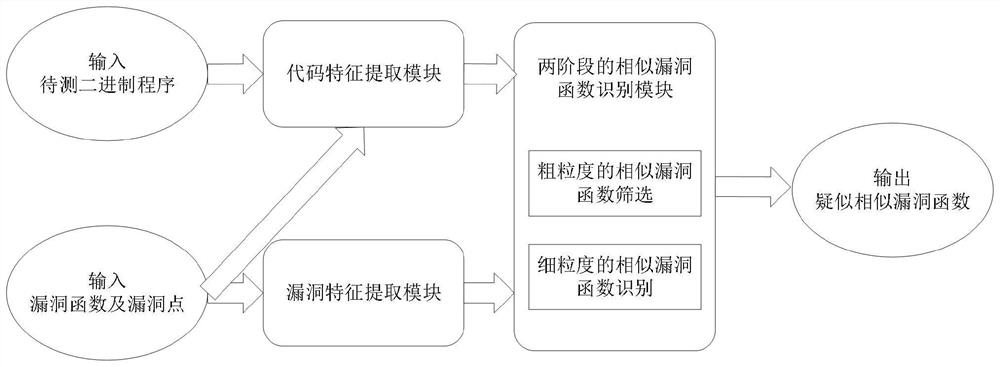
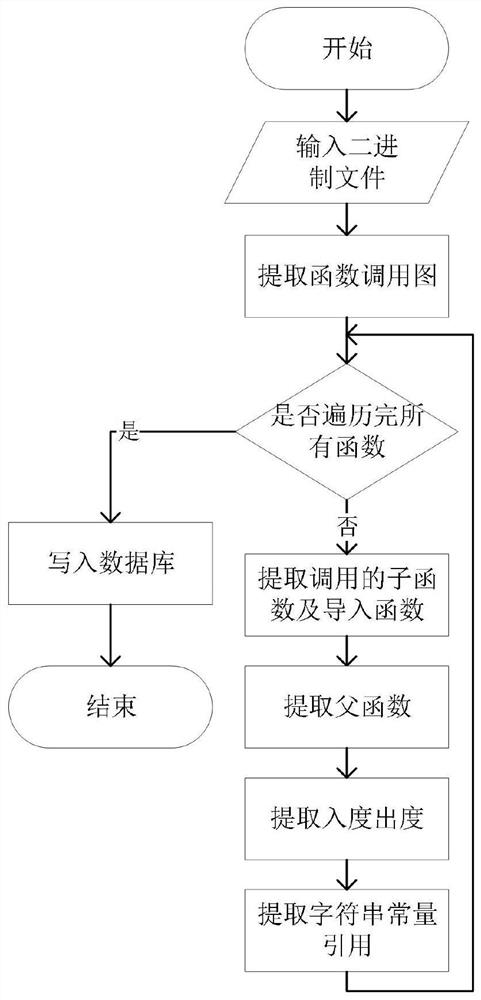
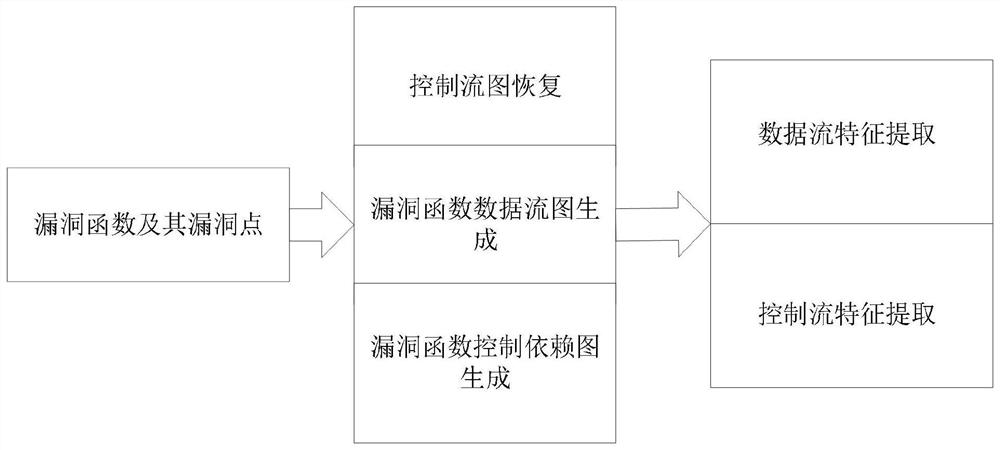
Similar vulnerability detection method and device for binary program
ActiveCN113468525AImprove detection efficiencyEasy to detectPlatform integrity maintainanceEnergy efficient computingAlgorithmInstruction set
The invention discloses a similar vulnerability detection method and device for a binary program, and the method comprises the steps: carrying out the coarse-grained similar vulnerability function screening and the fine-grained similar vulnerability function recognition of each to-be-detected function in a to-be-detected binary file according to a known vulnerability function, a corresponding binary file and a known vulnerability point; and a similar vulnerability function similar to the known vulnerability is acquired. By introducing known vulnerability points and combining information of functions and vulnerabilities, coarse-grained screening can be carried out on a to-be-detected function set through the lightweight feature distance, the extraction of the lightweight features does not depend on a specific instruction set, meanwhile, the features are less affected by compiling options and code customization reuse. And the execution semantics of the binary codes can be accurately captured, so that the detection efficiency and accuracy are effectively improved.
Owner:INST OF INFORMATION ENG CAS
Method and apparatus with floating point processing
Methods and apparatus with floating point processing are provided. A method includes receiving a first floating point operand and a second floating point operand, each having an n-bit format comprising a sign field, an exponent field, and a significand field, normalizing a binary value obtained by performing arithmetic operations for fields corresponding to each other in the first and second floating point operands for an n-bit multiplication operation, determining whether the normalized binary value is a number that is representable in the n-bit format or an extended normal number that is not representable in the n-bit format, according to a result of the determining, encoding the normalized binary value using an extension bit format in which an extension pin identifying whether the normalized binary value is the extended normal number is added to the n-bit format, and outputting the encoded binary value using the extended bit format, as a result of the n-bit multiplication operation.
Owner:SAMSUNG ELECTRONICS CO LTD
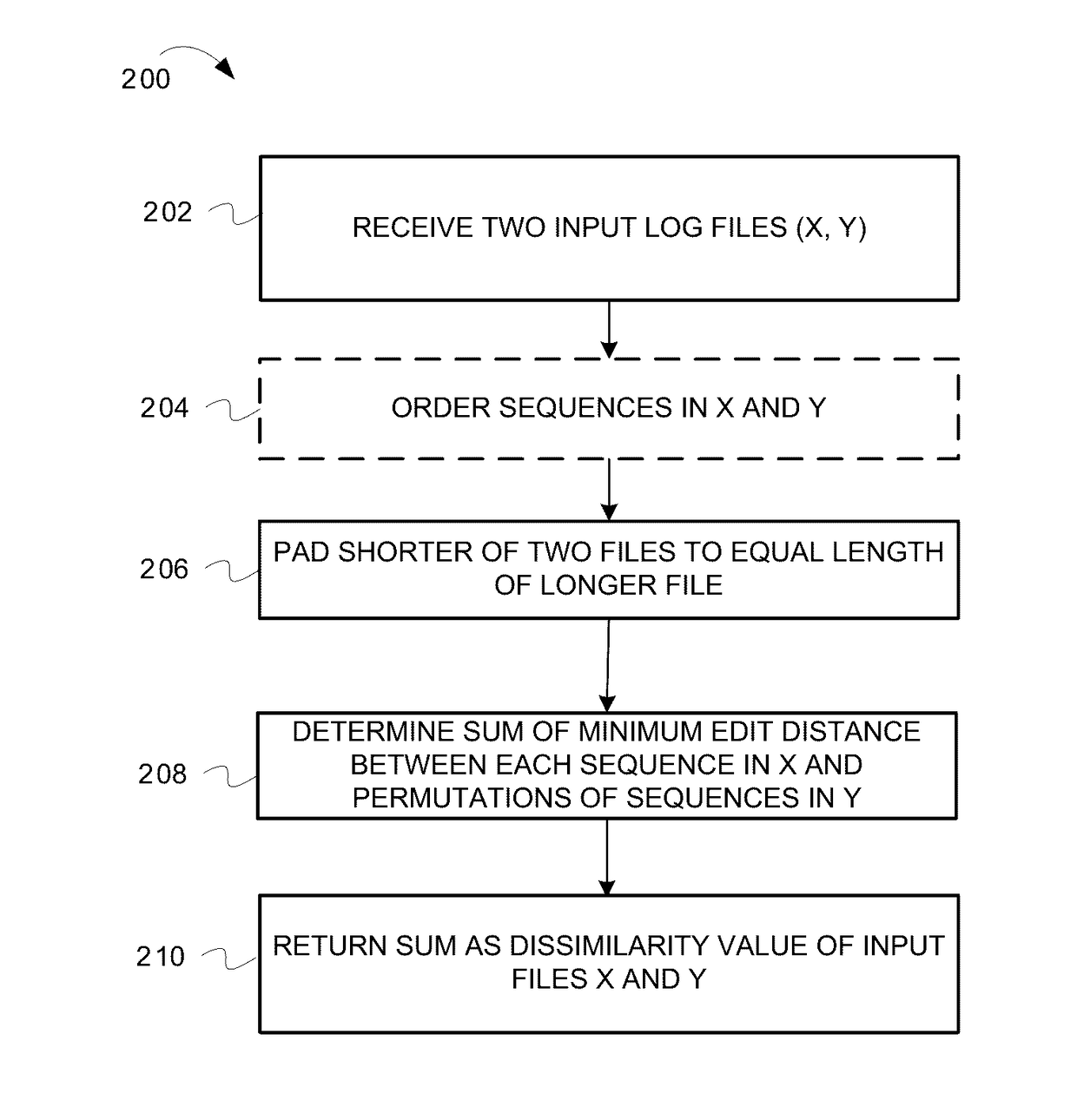
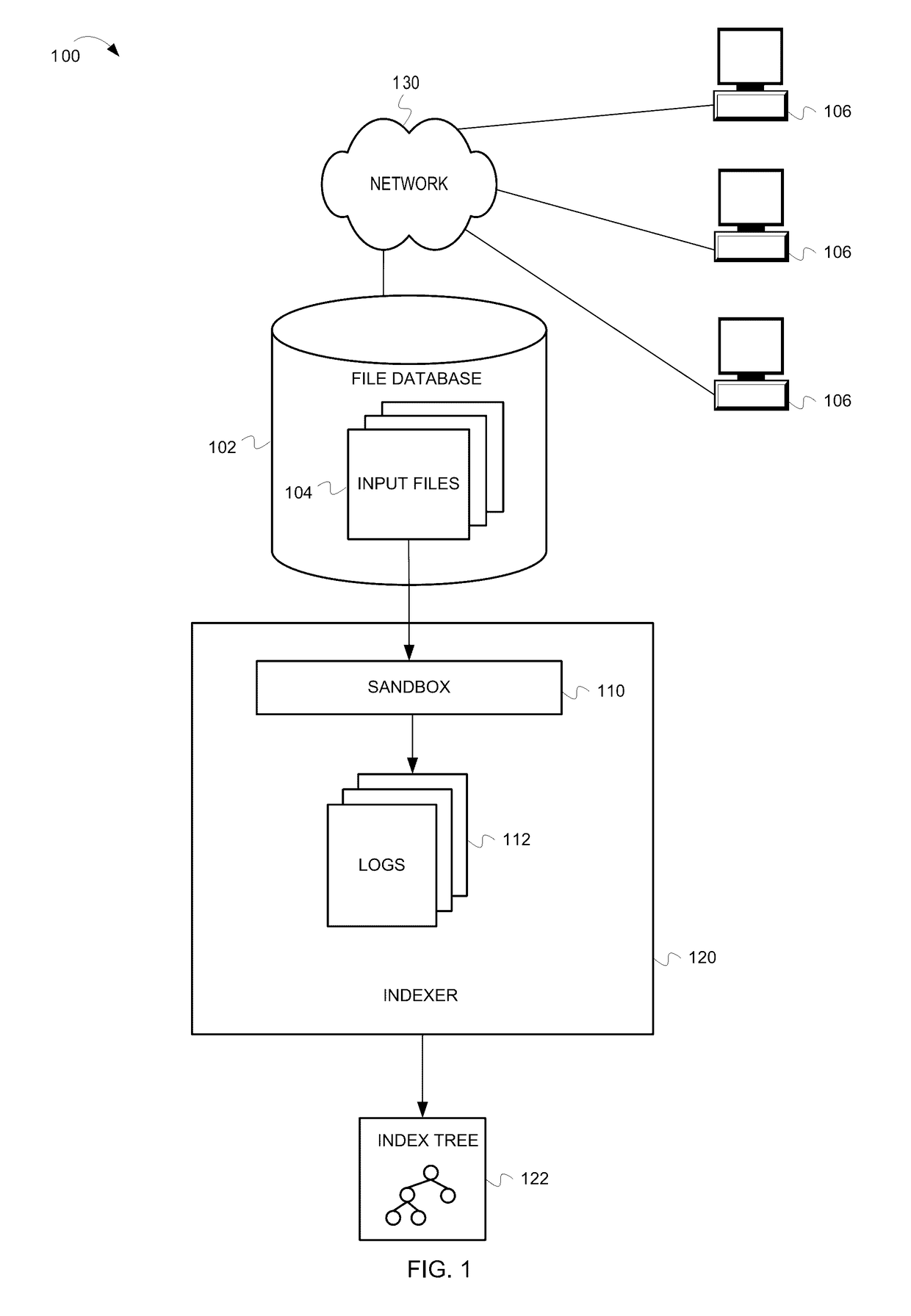
Distance and method of indexing sandbox logs for mapping program behavior
ActiveUS20170169214A1Digital data information retrievalPlatform integrity maintainanceTheoretical computer scienceEngineering
Owner:AVAST SOFTWARE +1
System and method for improved fractional binary to fractional residue converter and multipler
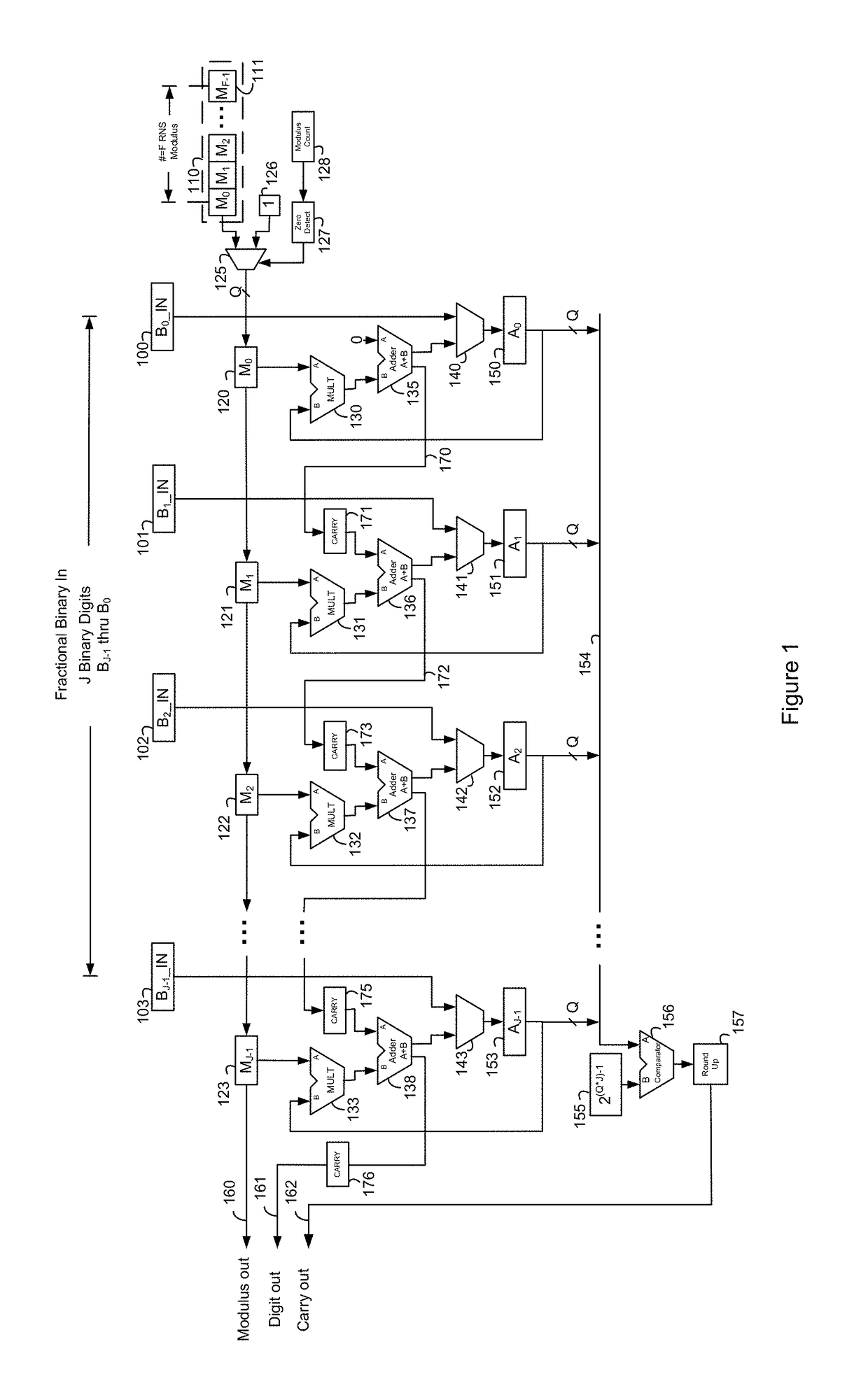
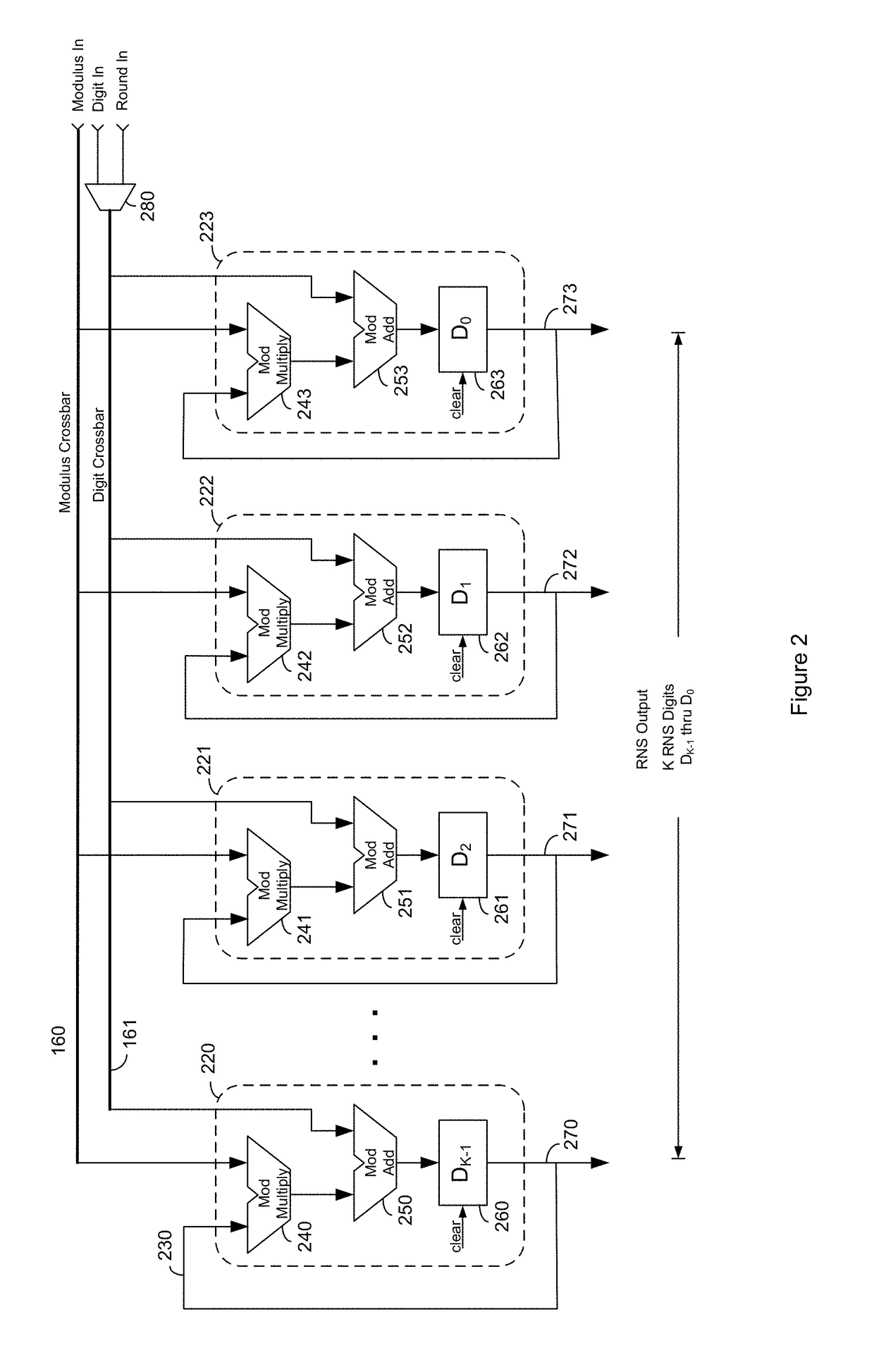
ActiveUS9712185B2Code conversionComputations using residue arithmeticParallel computingTheoretical computer science
Methods and systems for residue number system based ALUs, processors, and other hardware provide the full range of arithmetic operations while taking advantage of the benefits of the residue numbers in certain operations.
Owner:OLSEN IP RESERVE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com