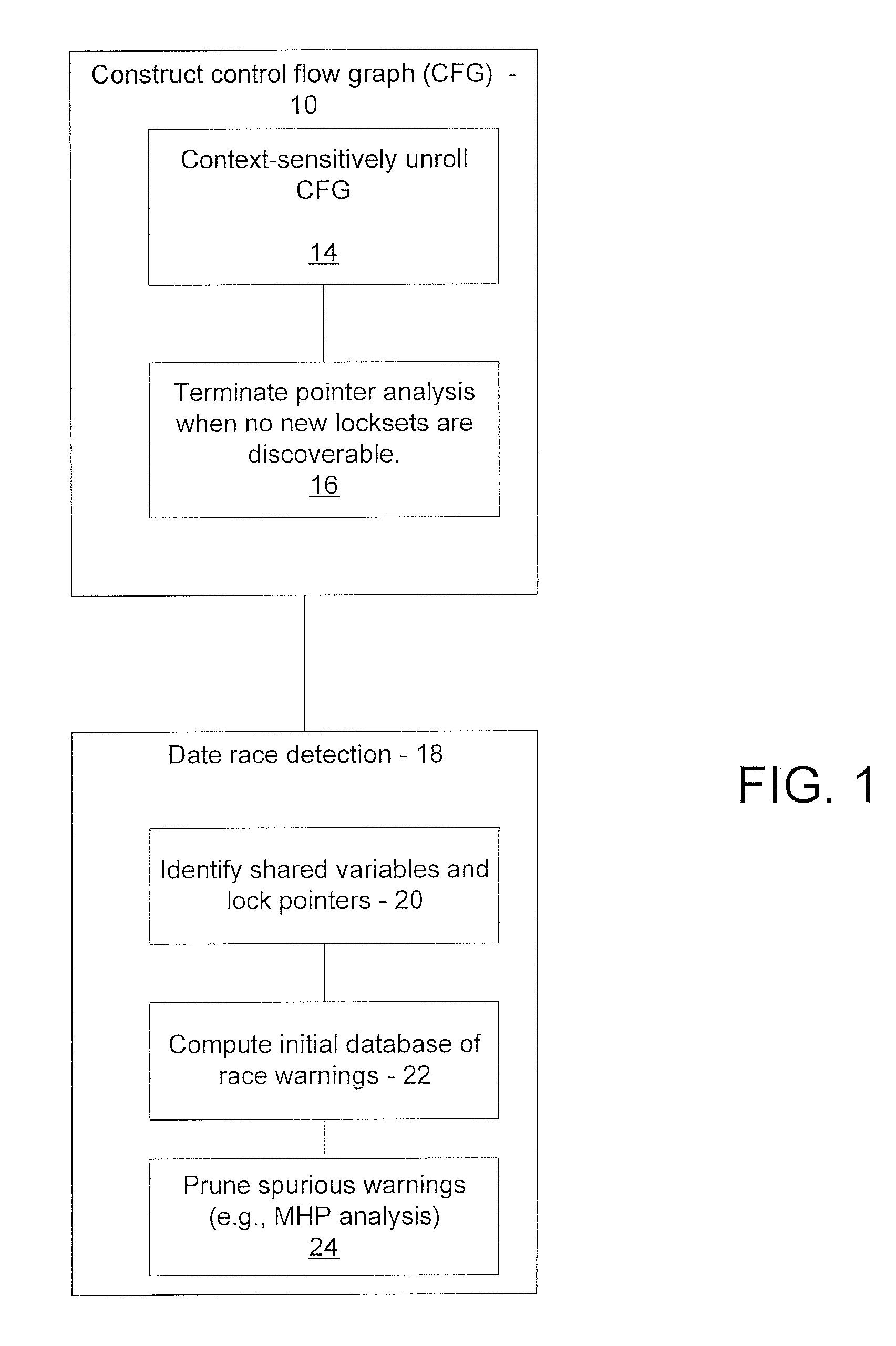
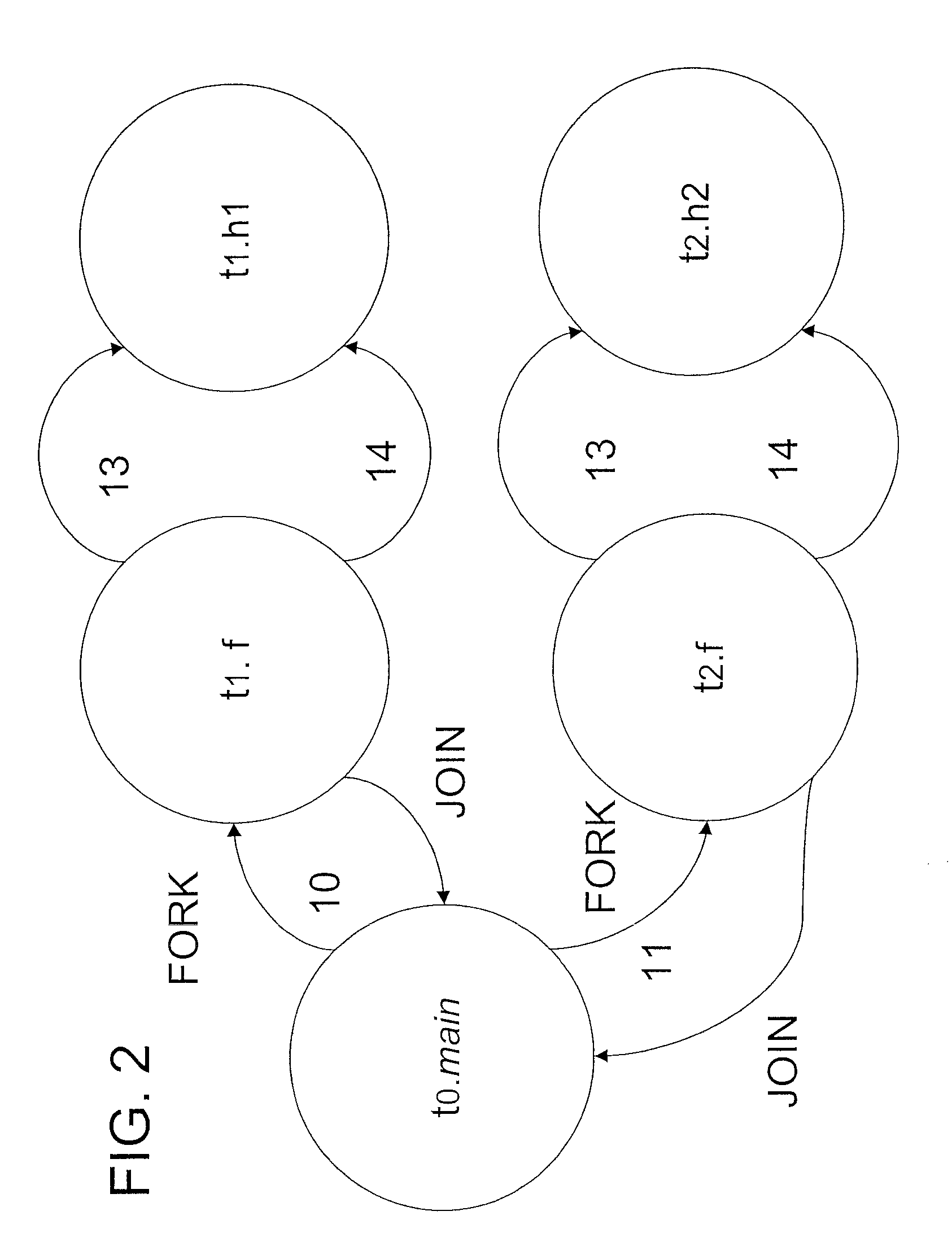
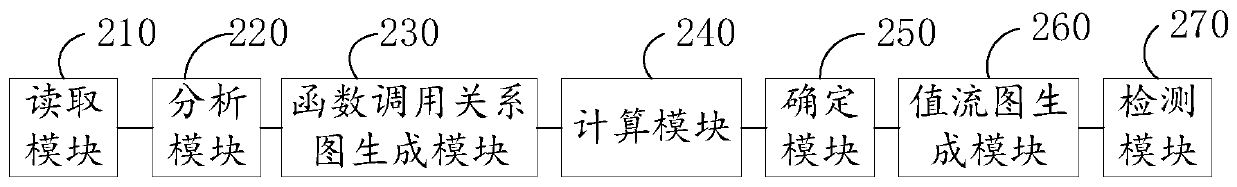
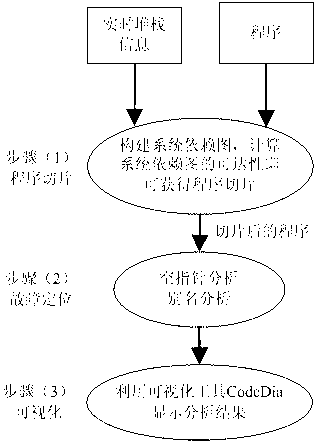
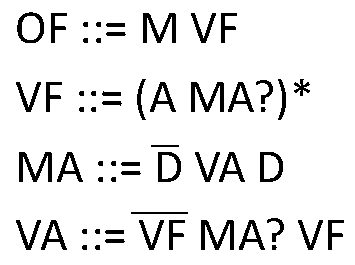Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Pointer analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, pointer analysis, or points-to analysis, is a static code analysis technique that establishes which pointers, or heap references, can point to which variables, or storage locations. It is often a component of more complex analyses such as escape analysis. A closely related technique is shape analysis.
Compiler method for extracting and accelerator template program
InactiveUS20070169059A1Software engineeringSpecific program execution arrangementsSemantic translationSemantics
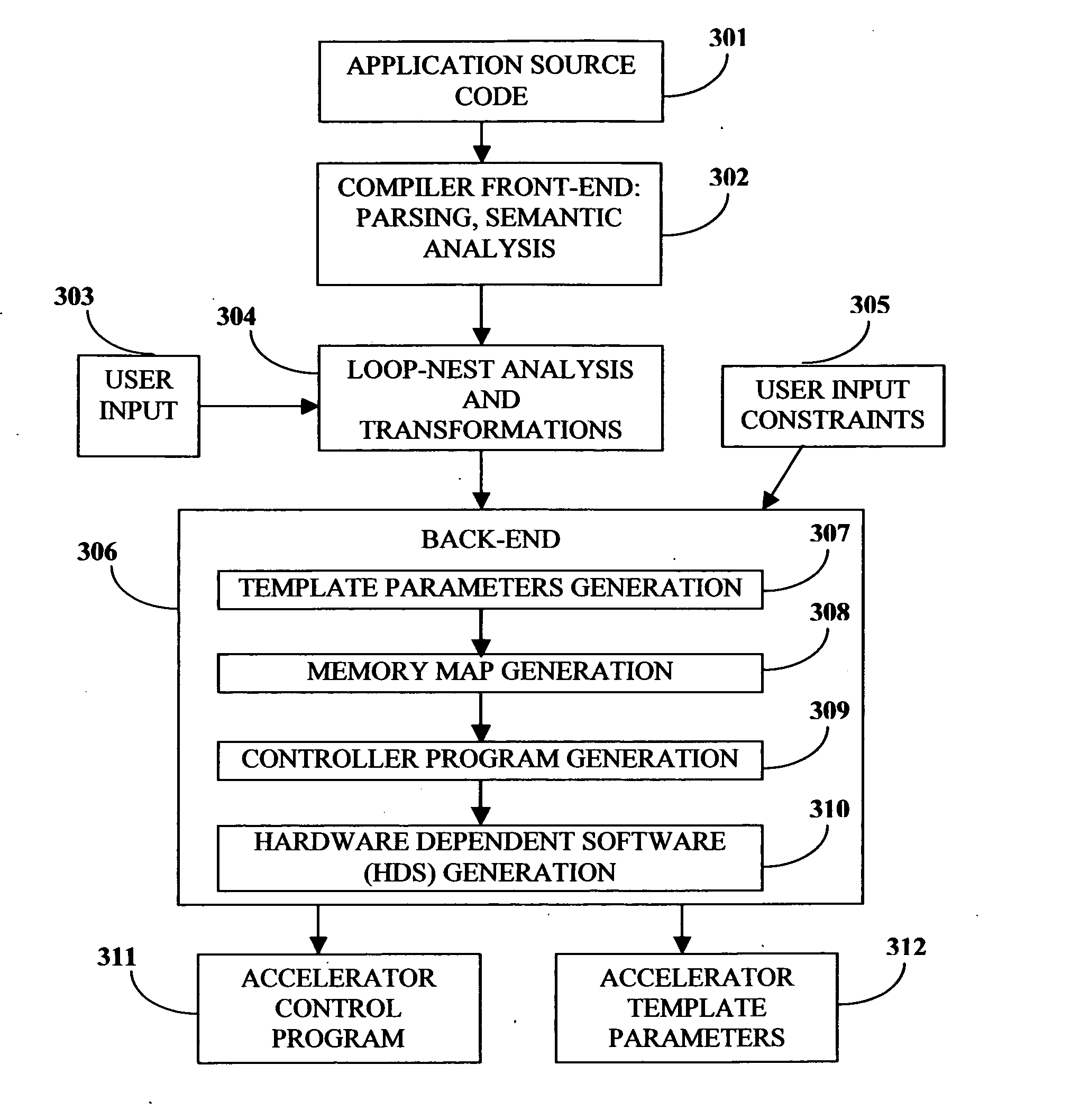
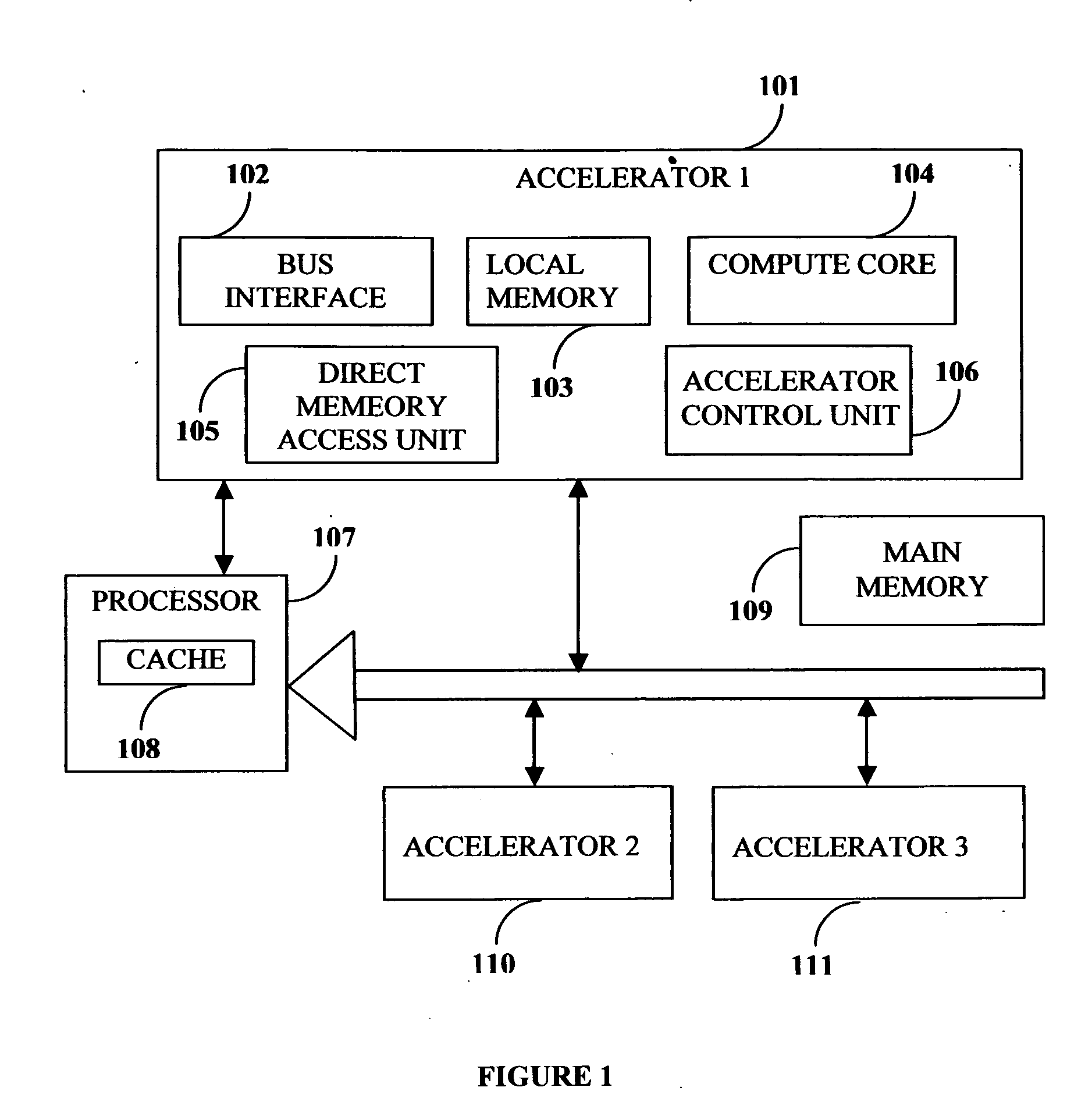
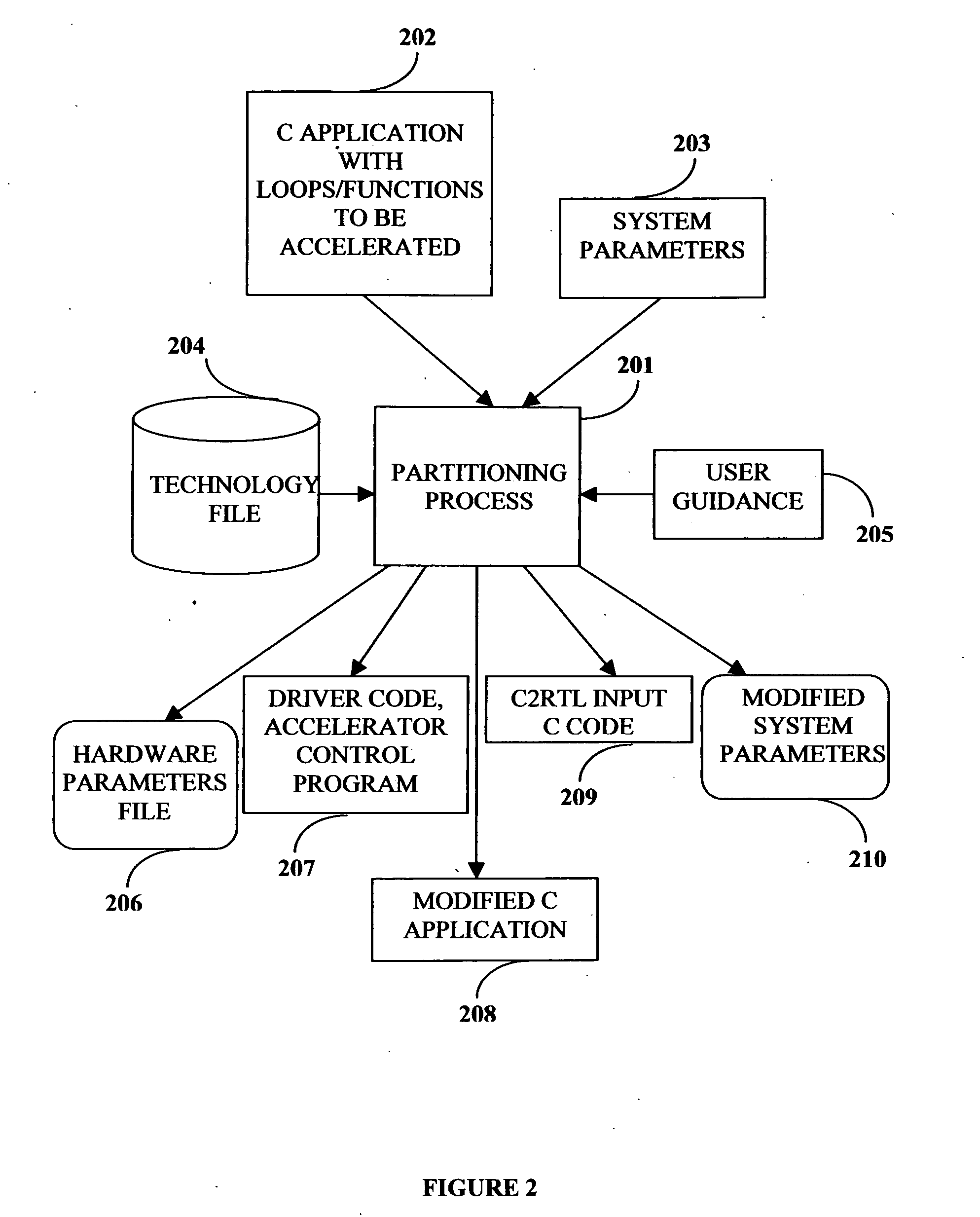
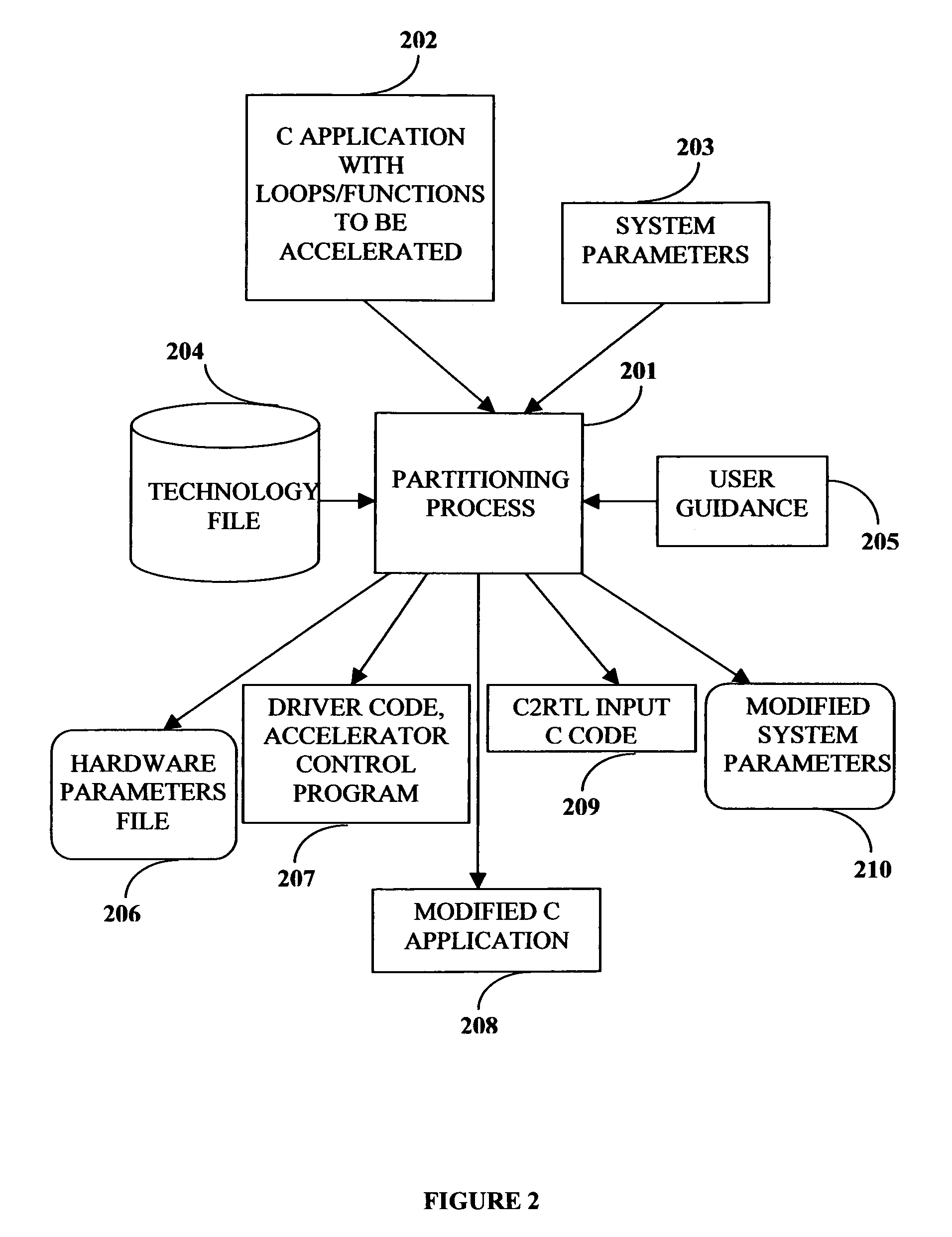
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
Compiler method for extracting and accelerator template program
InactiveUS7926046B2Software engineeringSpecific program execution arrangementsArray data structureSemantic translation
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
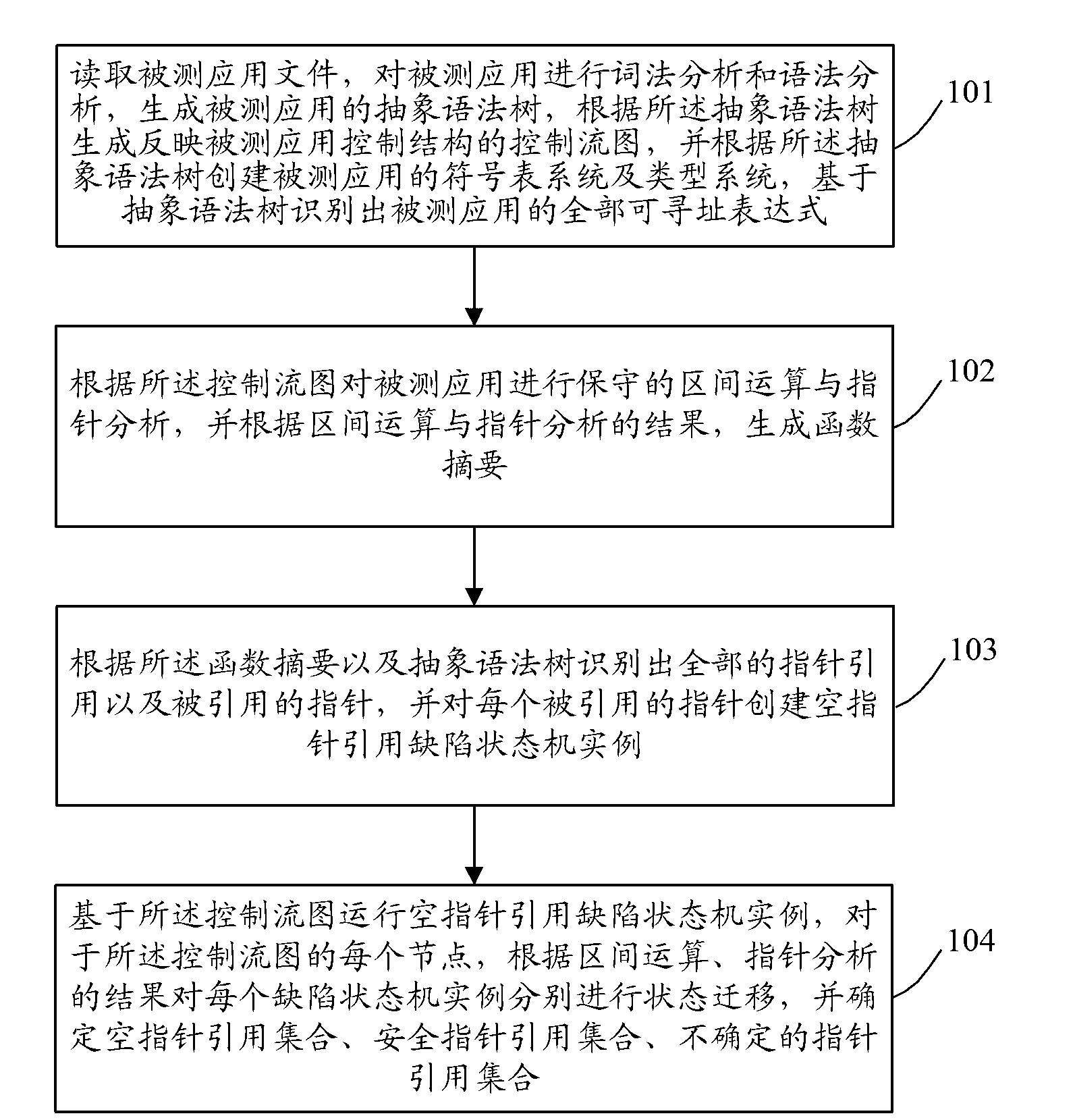
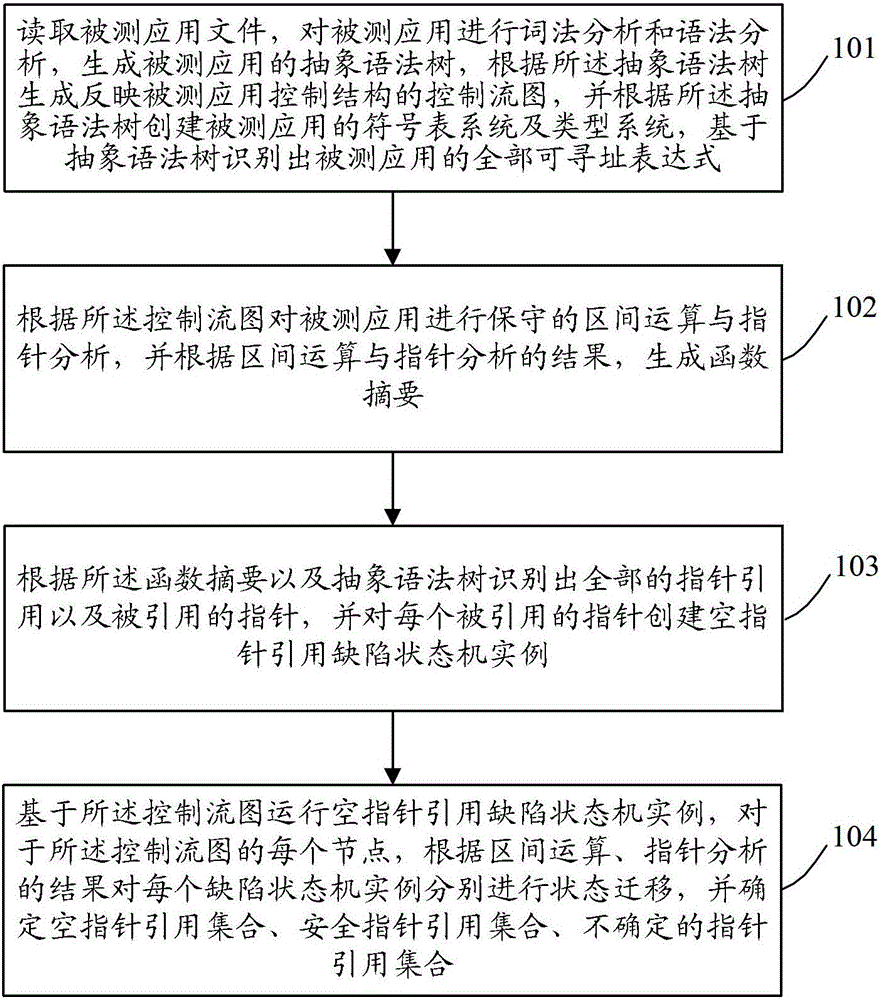
Method of fully detecting null pointer reference defects
InactiveCN103218296ASolve the problem of false positivesAchieve zero false negativesSoftware testing/debuggingInterval arithmeticTheoretical computer science
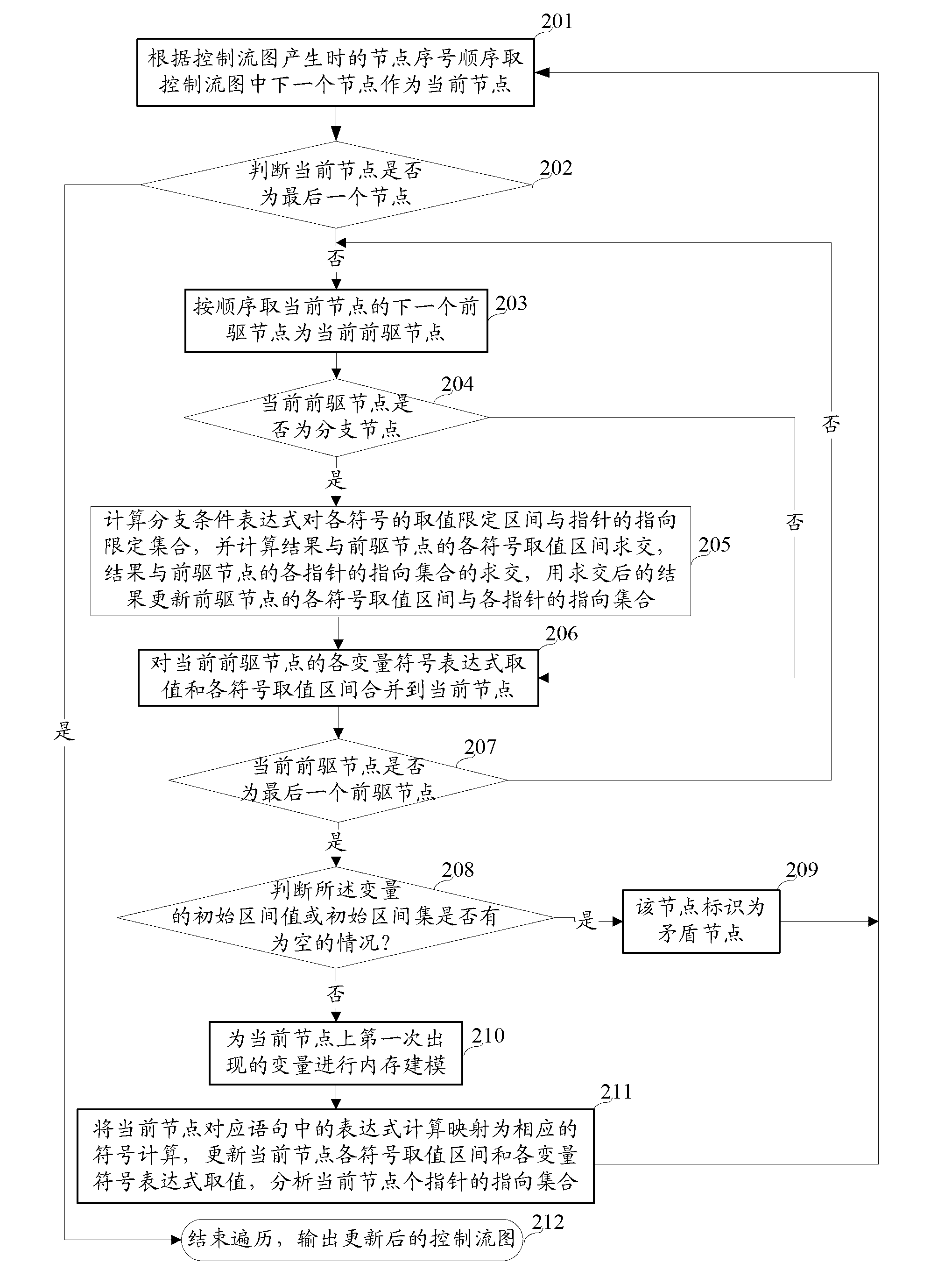
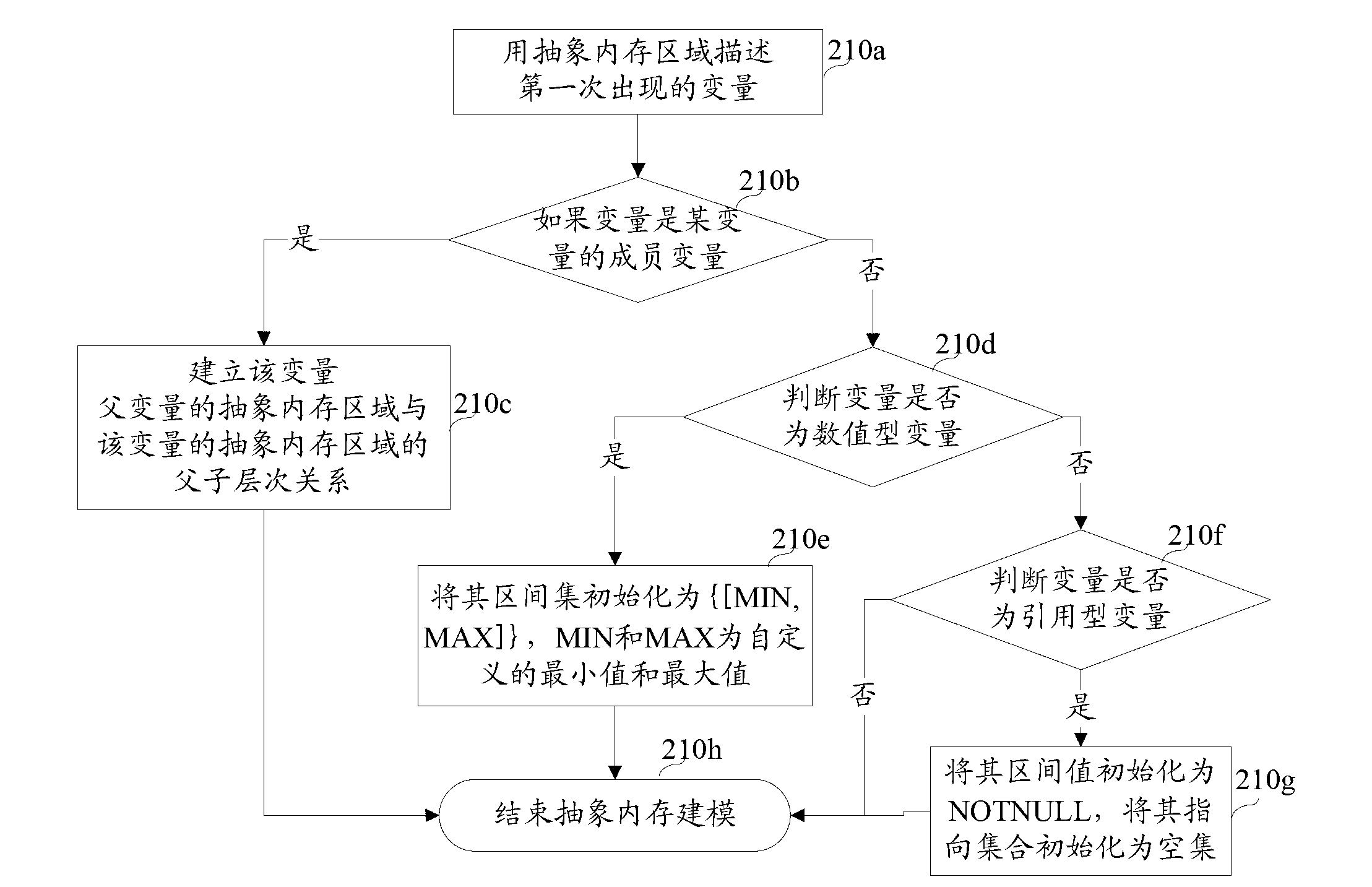
The invention discloses a method of fully detecting null pointer reference defects. The method comprises recognizing all addressable expressions of an application to be detected based on an abstract syntax tree; carrying out conservative interval arithmetic and pointer analysis on the application to be detected according to a control flow diagram, and generating a procedural summary according to results of the interval arithmetic and the pointer analysis; recognizing all pointer reference and referred pointers according to the procedural summary and the abstract syntax tree, and creating a null pointer reference defect state machine example on each referred pointer; and running the null pointer reference defect state machine examples based on the control flow diagram, carrying out state transition on each defect state machine example on each node of the control flow diagram according to the results of the interval arithmetic and the pointer analysis, and carrying out null pointer reference detection. By adopting the method of fully detecting the null pointer reference defects, the problem of failing to report the null pointer reference defects can be effectively solved, and zero omission and low misinformation of the null pointer reference defect detection are achieved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
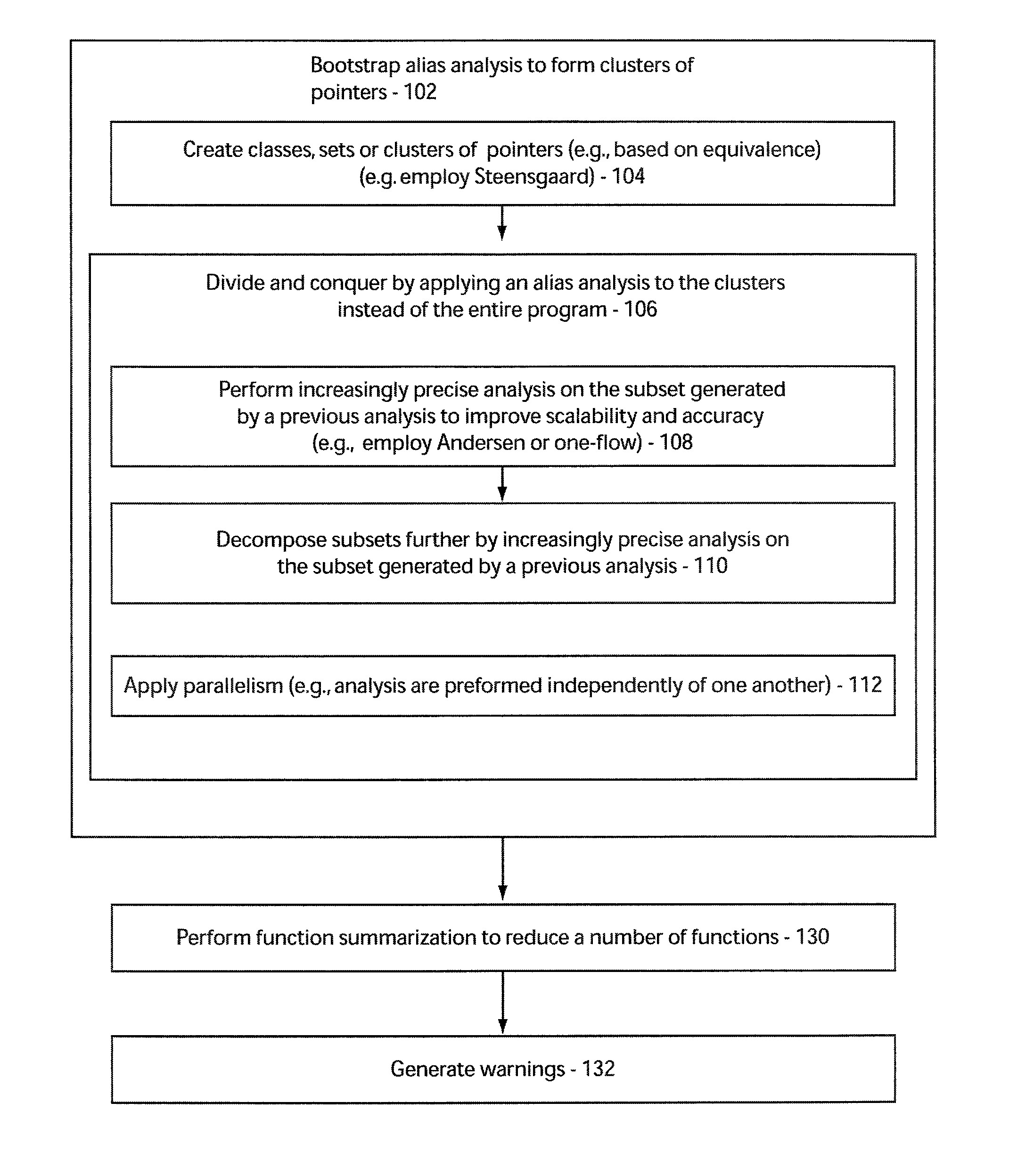
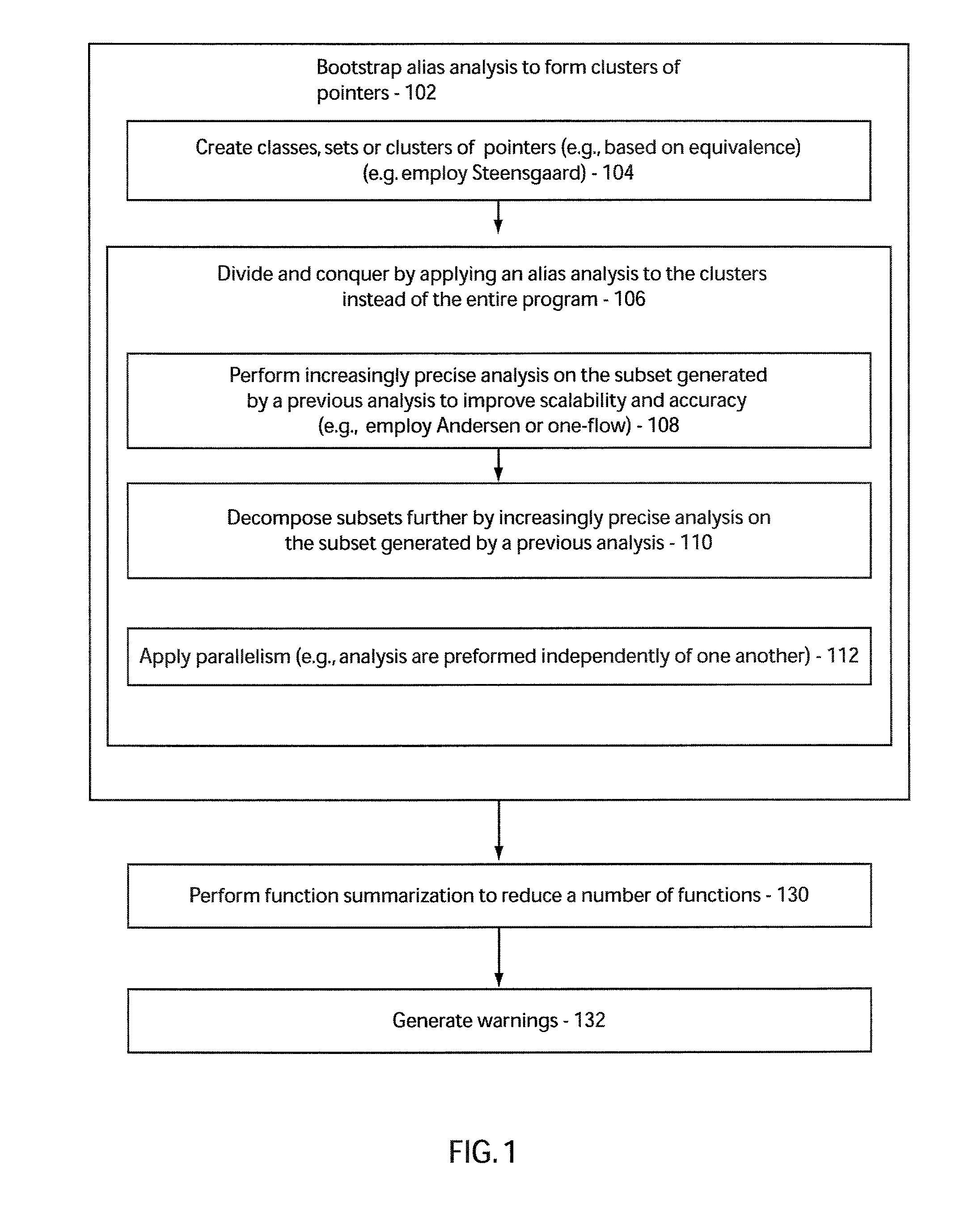
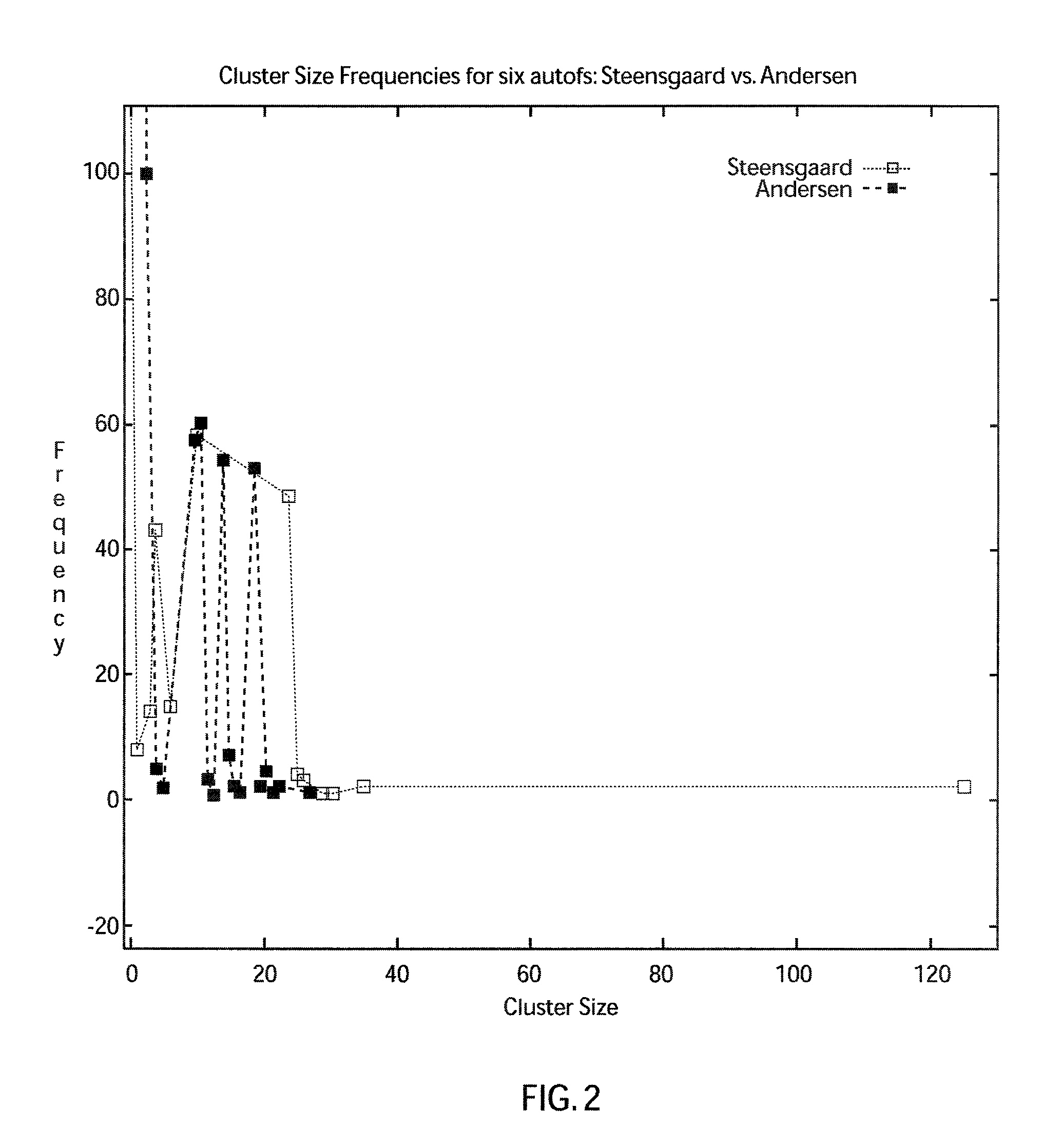
System and method for scalable flow and context-sensitive pointer alias analysis
ActiveUS8141049B2Increase ratingsError detection/correctionSpecific program execution arrangementsTheoretical computer scienceAnalysis working
A system and method for pointer analysis for computer program verification includes forming a subset or cluster of pointers from pointers in a program by applying increasingly accurate alias analyses in a cascaded fashion such that each analysis works on a subset of pointers generated by a previous analysis's results. Aliases are computed for any pointer by computing aliases in the subsets in parallel instead of an entire program. For carrying out context and flow-sensitive alias analysis, function summaries are computed on small subsets in a top-down manner based on the points-to hierarchy which reduces the sizes of the summaries.
Owner:NEC CORP
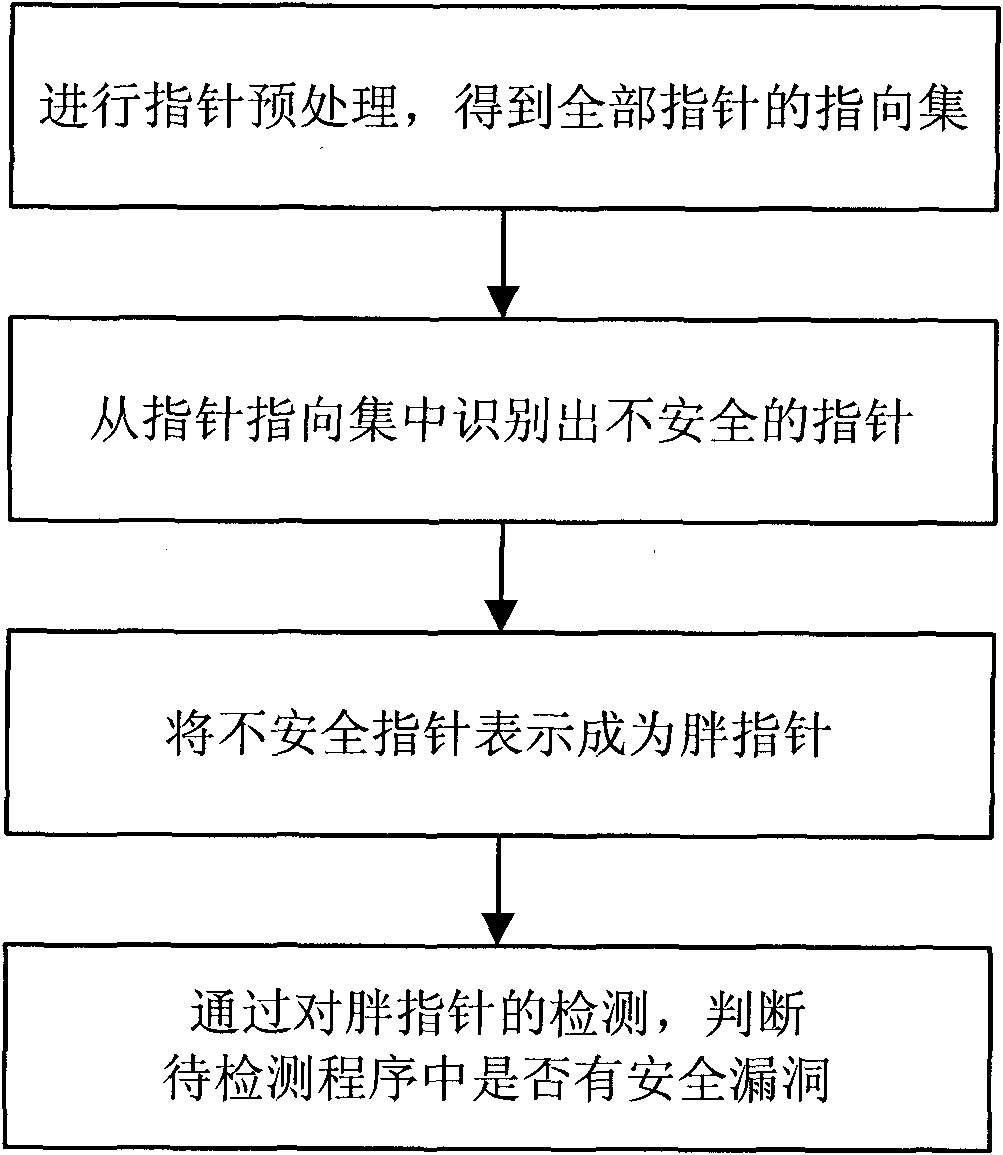
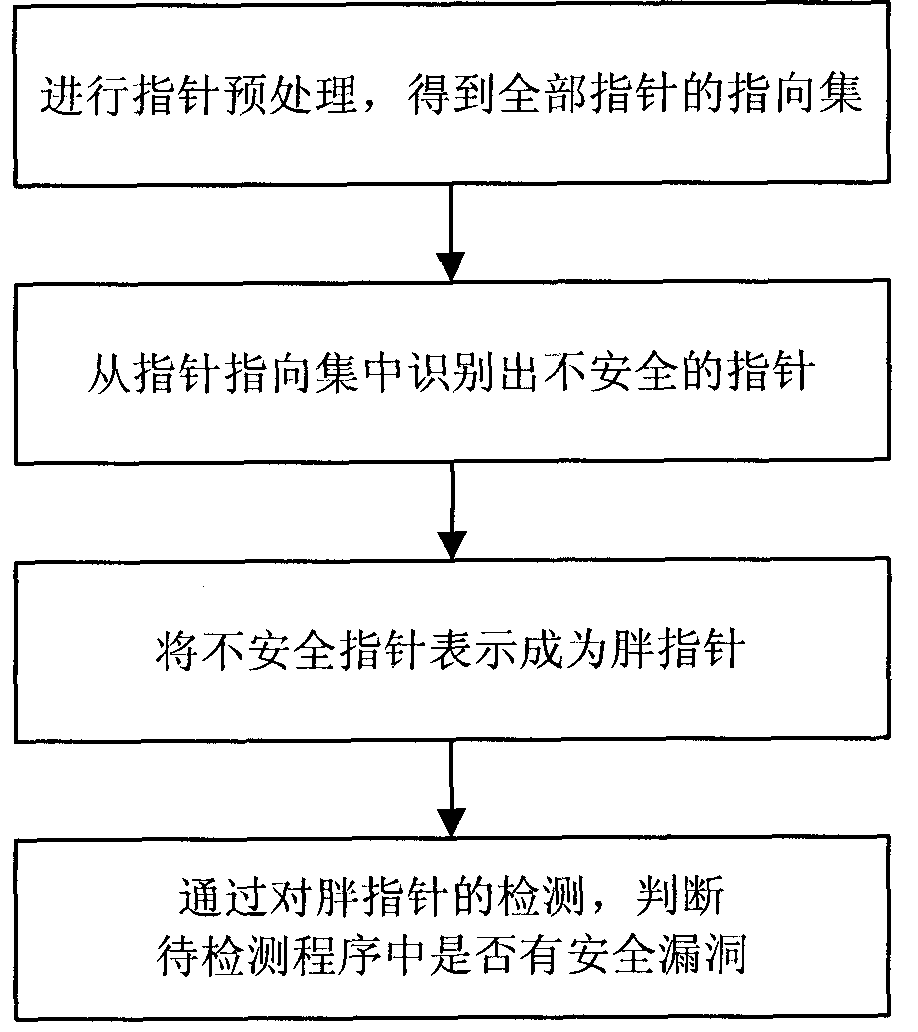
Pointer analysis-combined software security hole dynamic detection method
InactiveCN101833631AReduce resource consumptionProgram/content distribution protectionSoftware engineeringBuffer overflow
The invention relates to a software security hole dynamic detection method, in particular to a pointer analysis-combined software security hole dynamic detection method, and belongs to the technical field of information security. The software security hole dynamic detection method comprises the following steps of: identifying insecure pointers in a program to be detected; expressing the insecure pointers as fat pointers; and continuously checking the pointer state information contained in the fat pointers and finding the hole existing in the program to be detected by operating the program to be detected. The software security hole dynamic detection method can detect various holes simultaneously, such as a buffer area overflow hole, a suspended pointer hole, and the like, and can reduce the consumption of the system resources simultaneously.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Procedure summaries for pointer analysis
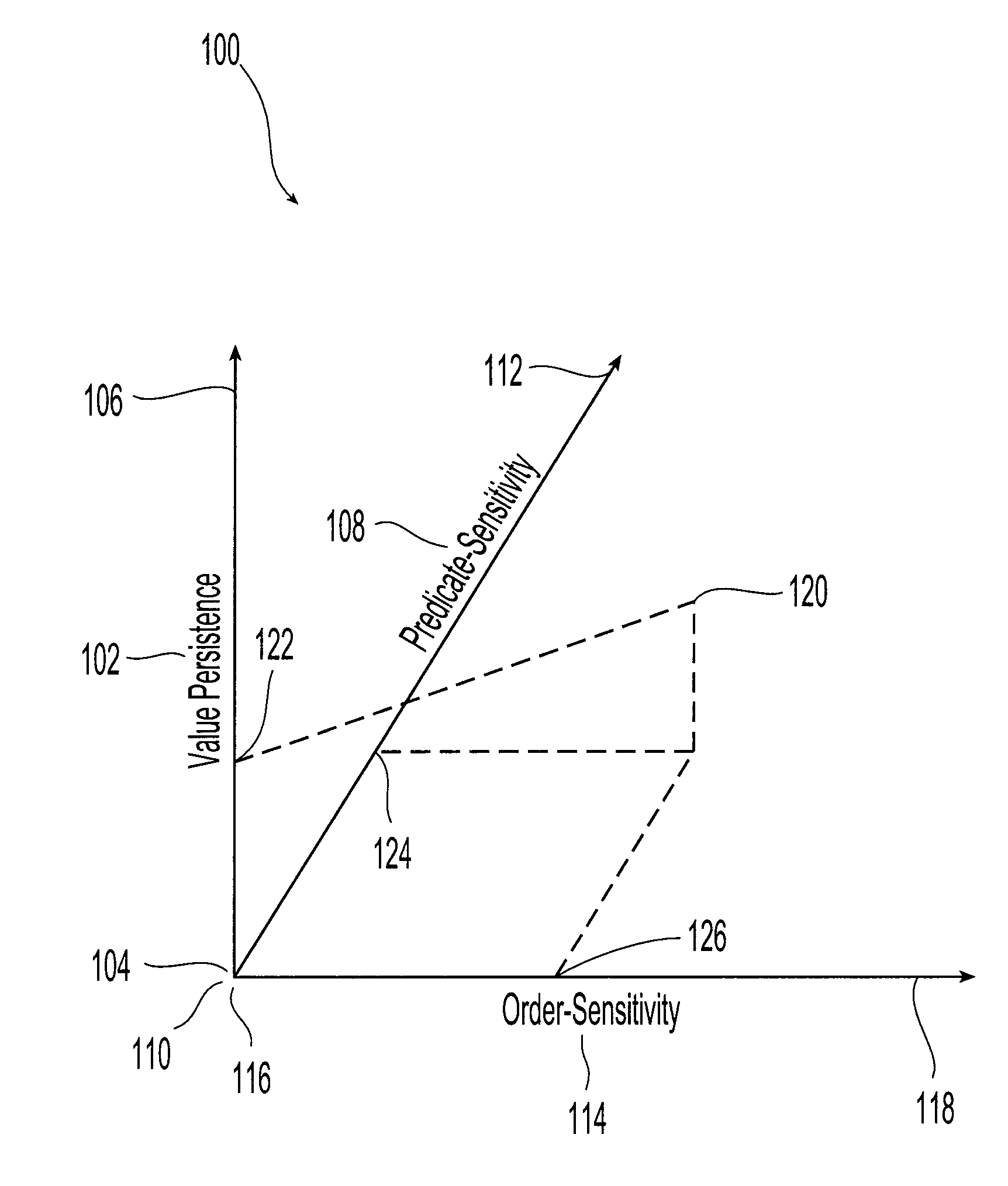
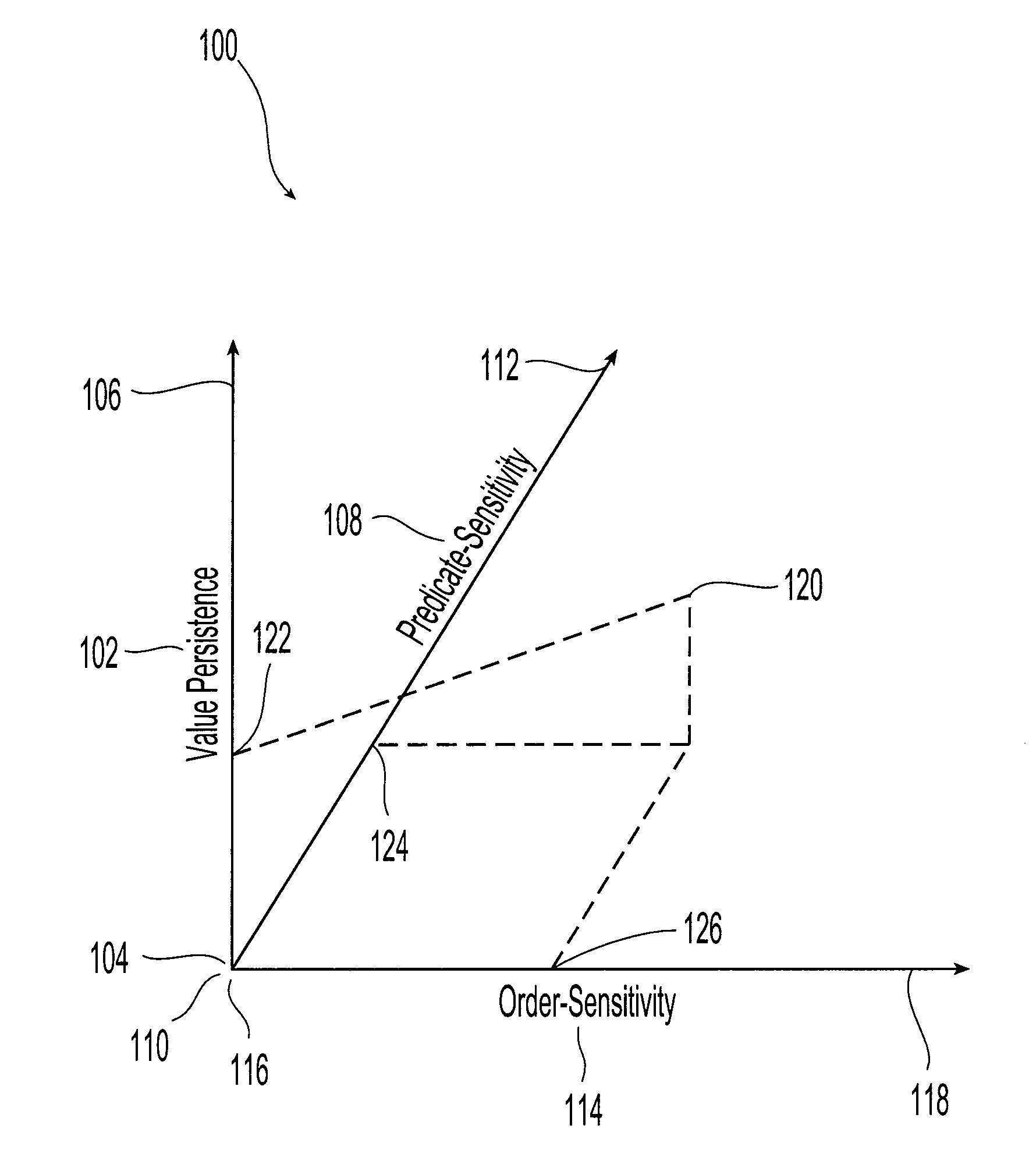
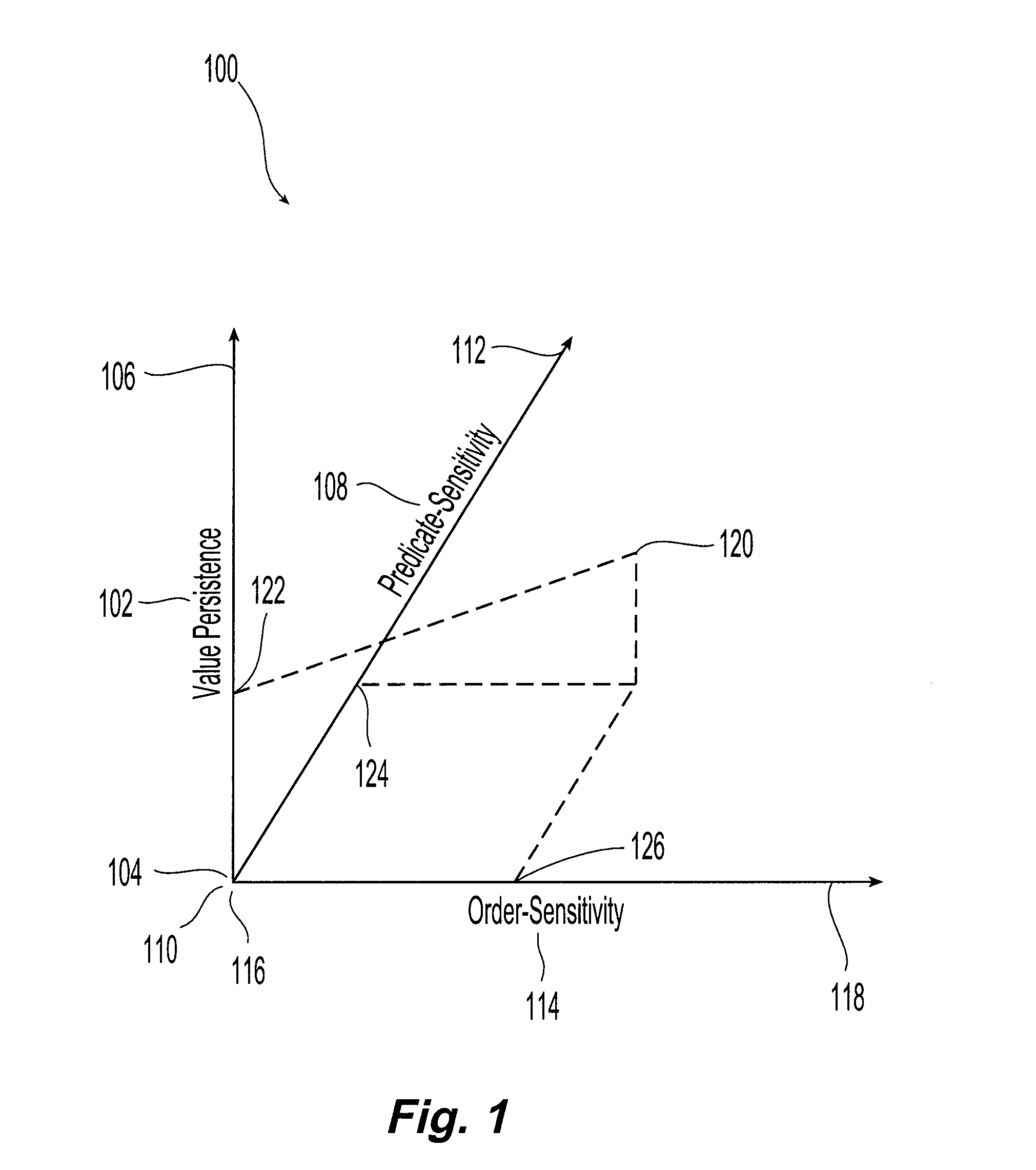
Pointer analysis is used for different applications, e.g., compilers, debugging tools and programs understanding tools, each having different requirements. A framework for pointer analysis is provided that defines a multidimensional space, for example a three-dimensional space, containing an order sensitivity dimension, a predicate sensitivity dimension and a value persistence dimension. A point in the three-dimensional space is identified. This point yields values for order sensitivity, predicate sensitivity and value persistence. Pointer analysis is then conducted on a computer program in accordance with the identified values for order sensitivity, predicate sensitivity and value persistence.
Owner:GLOBALFOUNDRIES INC
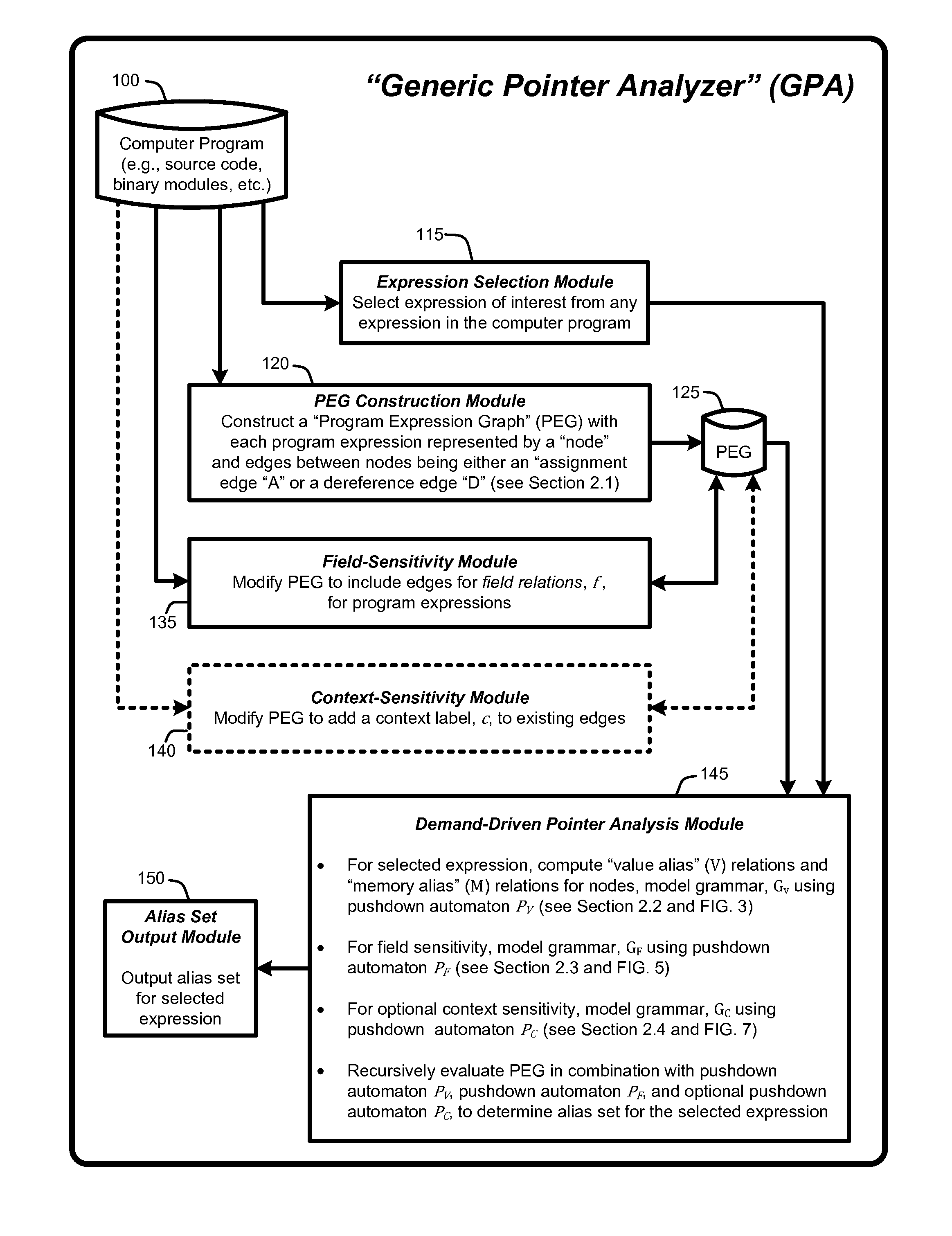
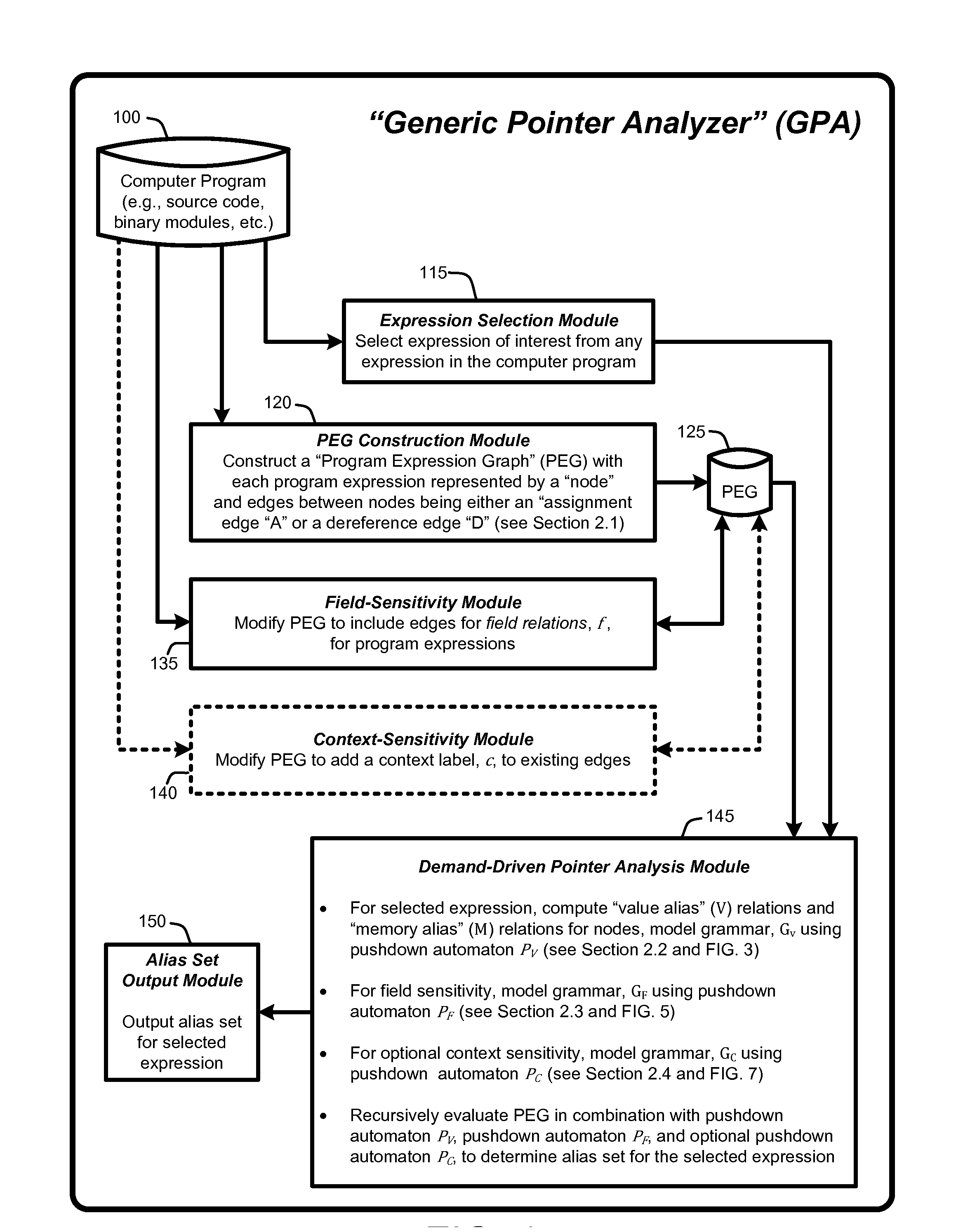
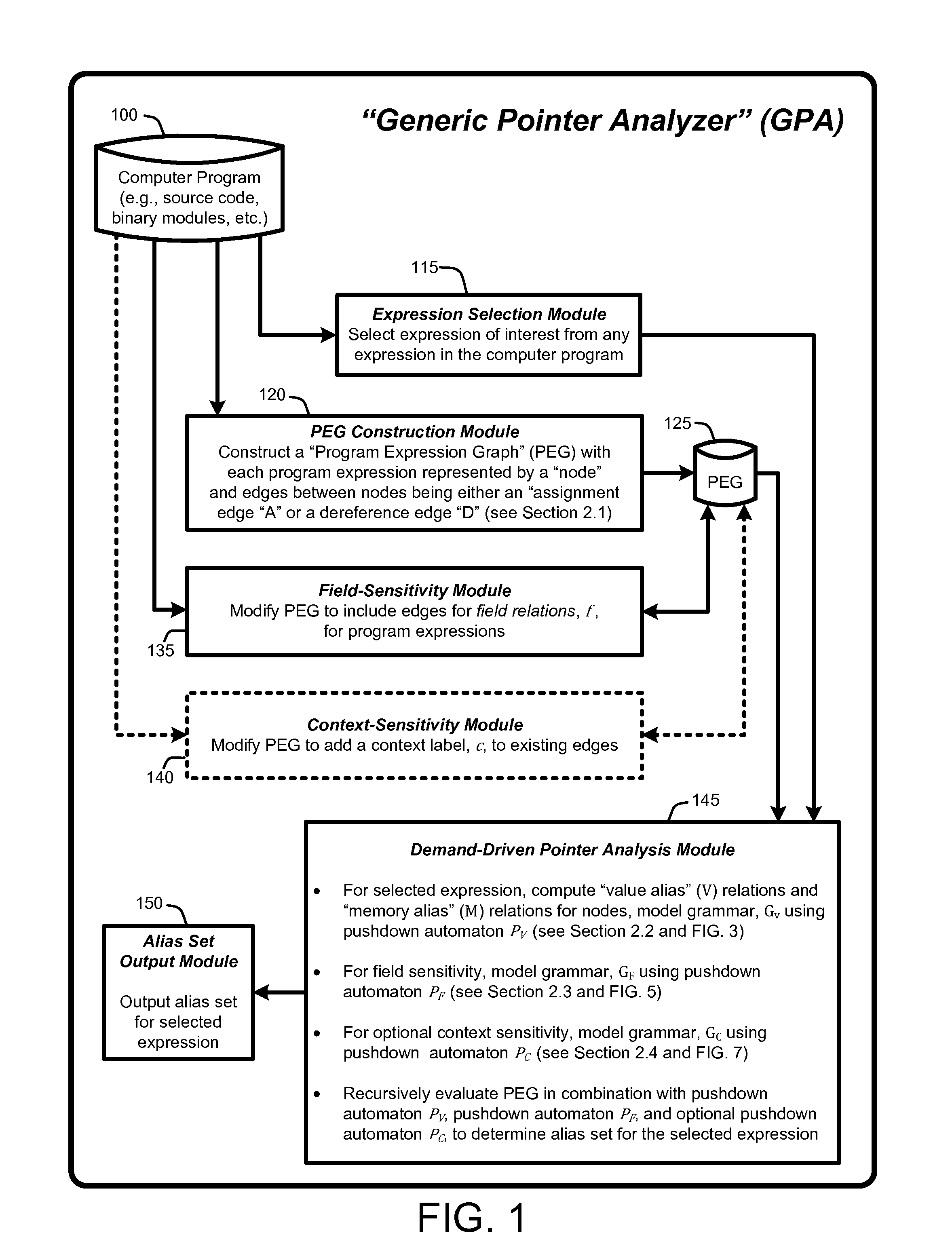
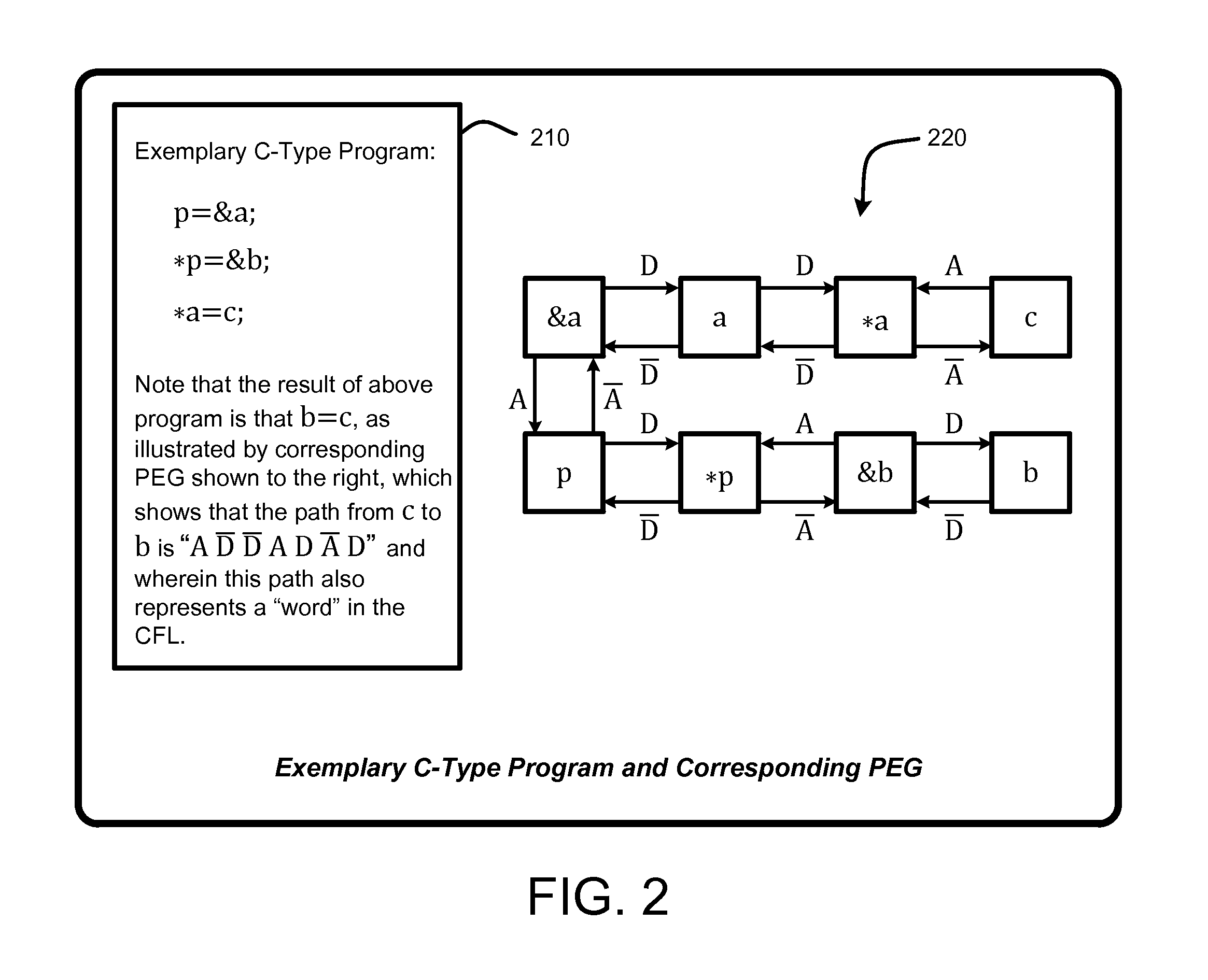
Demand-driven analysis of pointers for software program analysis and debugging
InactiveUS8589888B2Accurate settingRapidly identify aliasError detection/correctionSoftware engineeringGraphicsOperational system
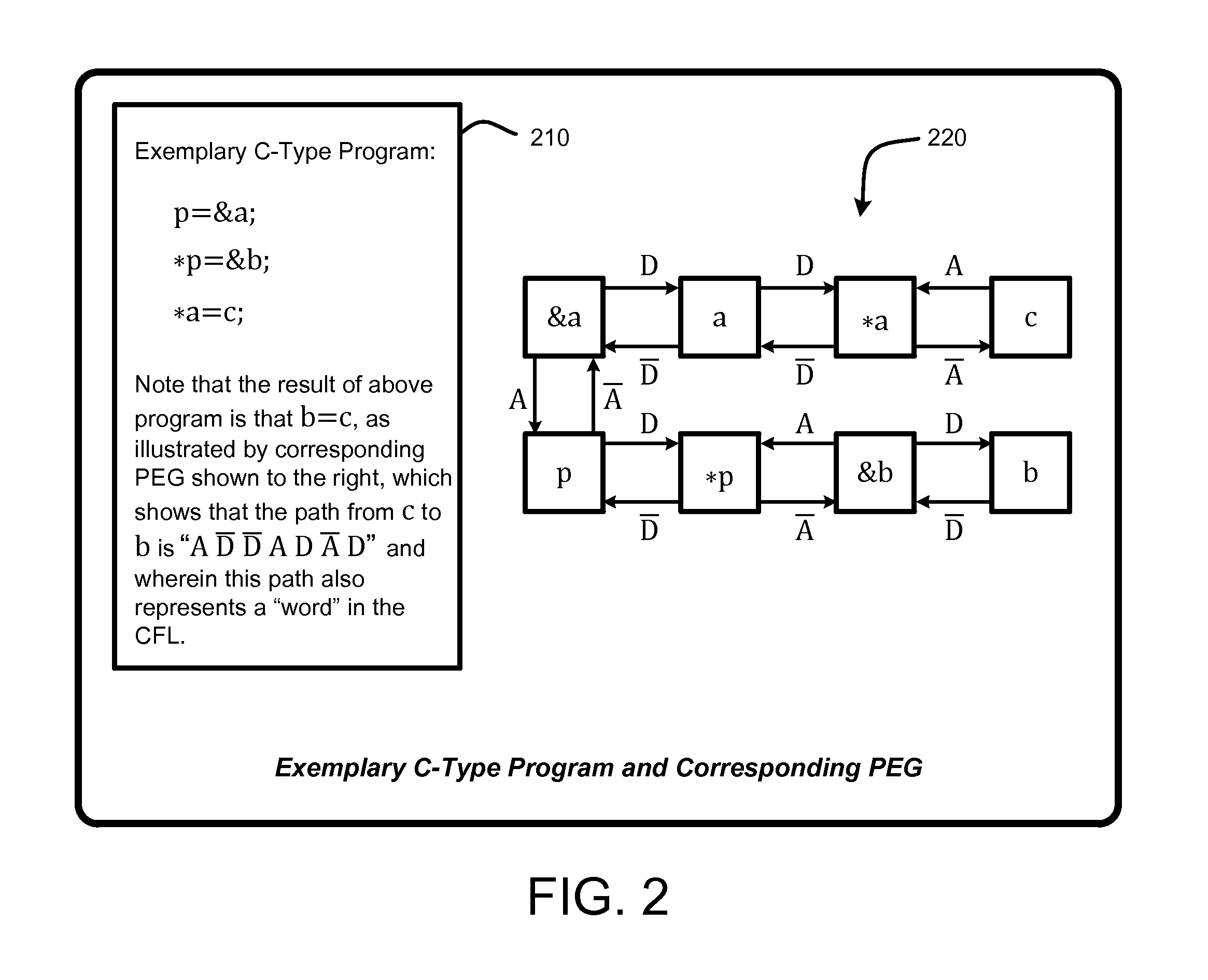
A “Demand-Driven Pointer Analyzer” (DDPA) provides a “demand-driven” field-sensitive pointer analysis process. This process rapidly and accurately identifies alias sets for selected pointers in software modules or programs of any size, including large-scale C / C++ programs such as a complete operating system (OS). The DDPA formulates the pointer analysis task as a Context-Free Language (CFL) reachability problem that operates using a Program Expression Graph (PEG) automatically constructed from the program code. The PEG provides a node and edge-based graph representation of all expressions and assignments in the program and allows the DDPA to rapidly identify aliases for pointers in the program by traversing the graph as a CFL reachability problem to determine pointer alias sets. In various embodiments, the DDPA is also context-sensitive.
Owner:MICROSOFT TECH LICENSING LLC
Multi-level hybrid vulnerability automatic mining method
ActiveCN111859388ARich semantic informationImplement extractionSoftware testing/debuggingPlatform integrity maintainanceMemory addressRepresentation language
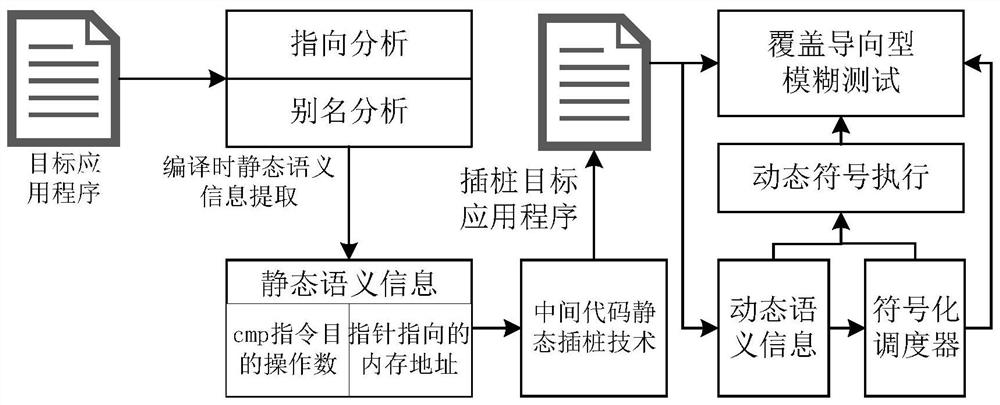
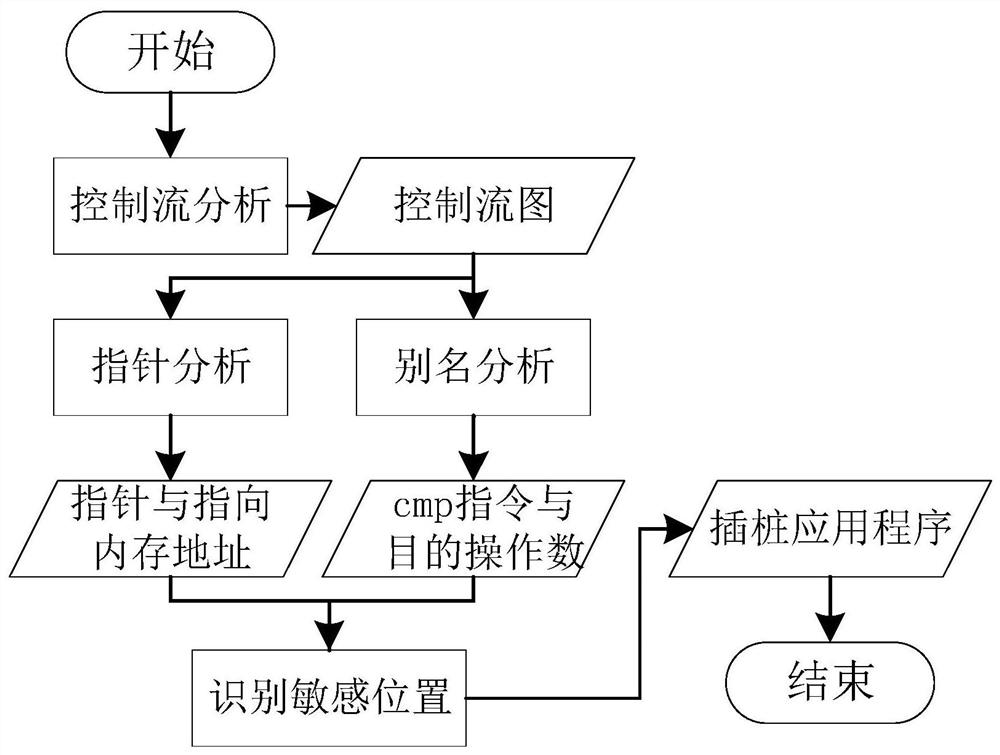
The invention belongs to the technical field of computers, and particularly relates to a multi-level hybrid vulnerability automatic mining method, which comprises the following steps: S1, obtaining pointer distribution and assignment processes in a program by utilizing pointer analysis through a static analysis technology, and recording memory address positions pointed by all pointers; obtaining adestination operand of the CMP type instruction by using an alias analysis technology so as to clarify a jump address of the target program; and S2, realizing instrumentation of the monitoring code to the key position of the target program through an intermediate code static instrumentation technology. According to the invention, the binary executable program is translated into the middle-layer representation language of the compiler, and compared with the binary executable program, the middle-layer representation language source code obtained through processing of the method has more semantic information; compared with C / C + + language analysis, the static analysis technology for the LLVM IR intermediate representation language can realize finer-grained static semantic information extraction during compiling.
Owner:GUANGZHOU UNIVERSITY
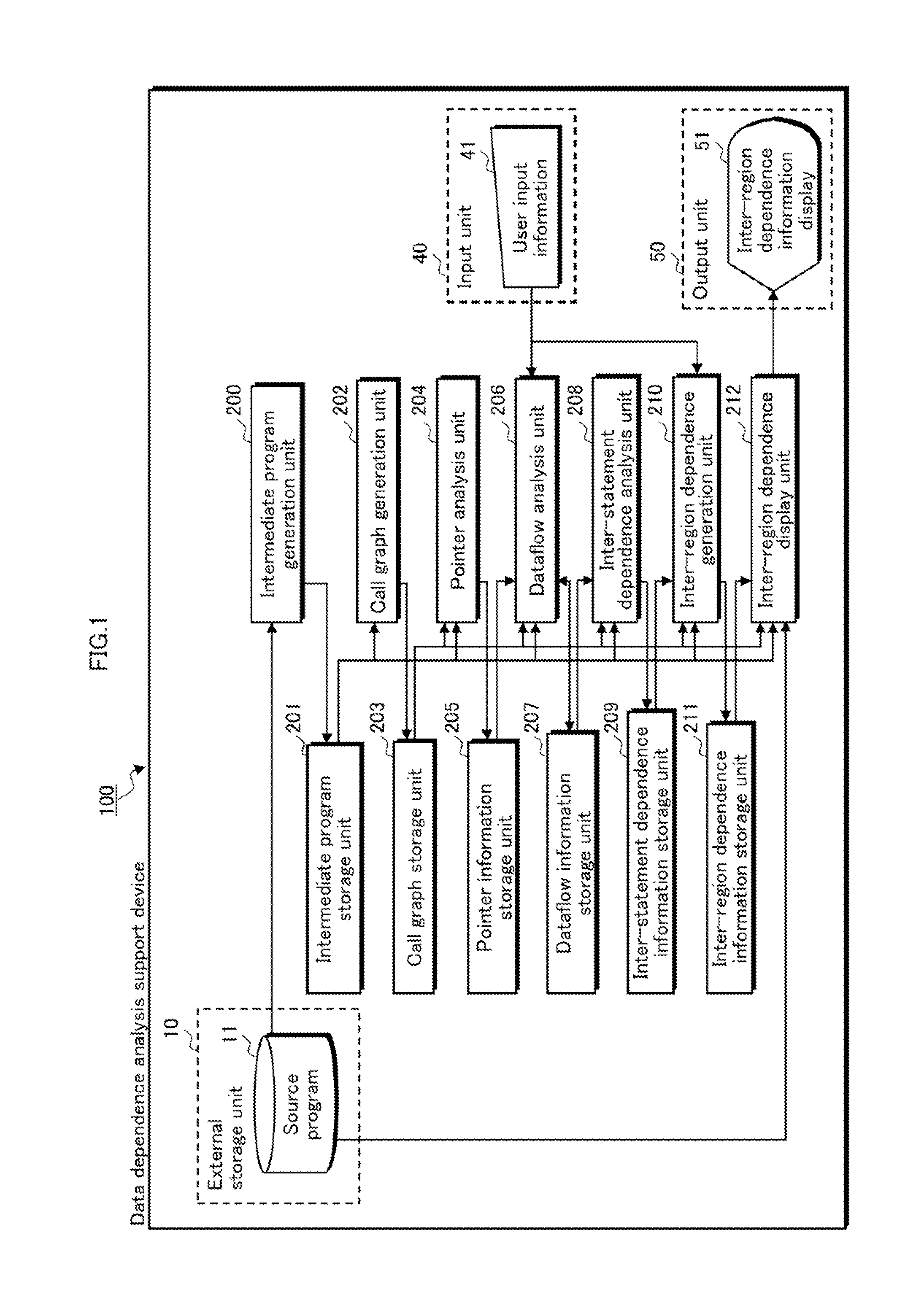
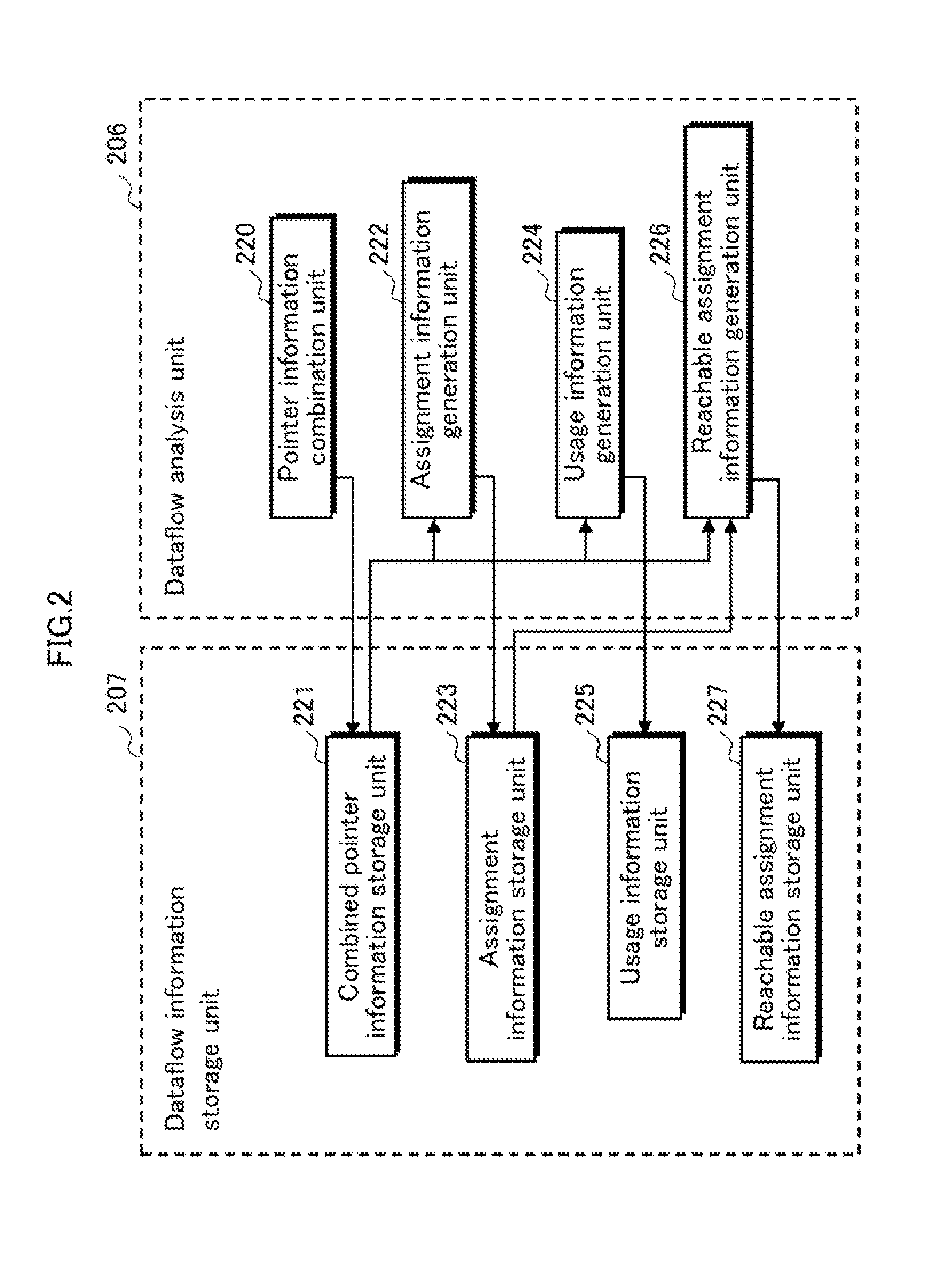
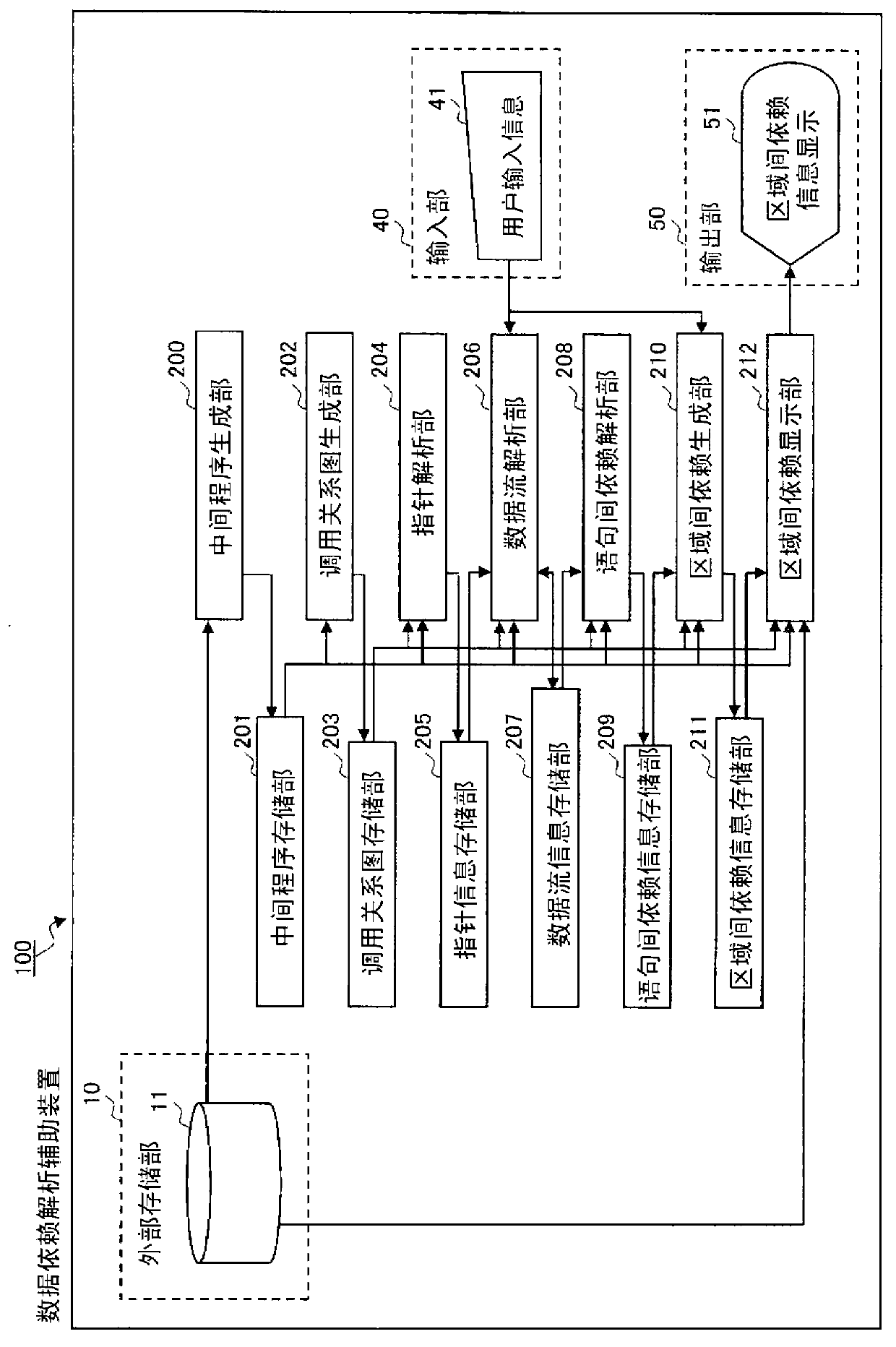
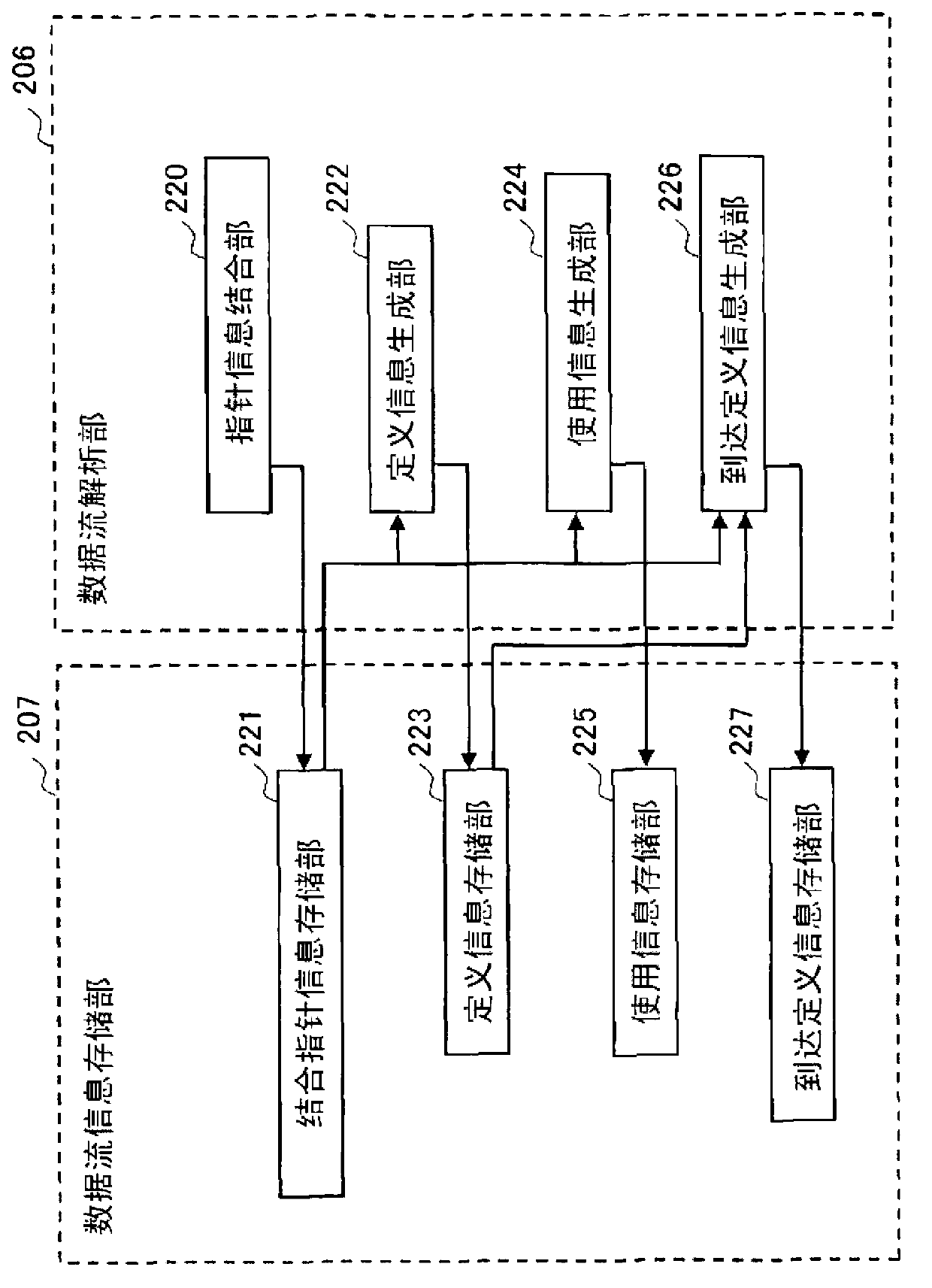
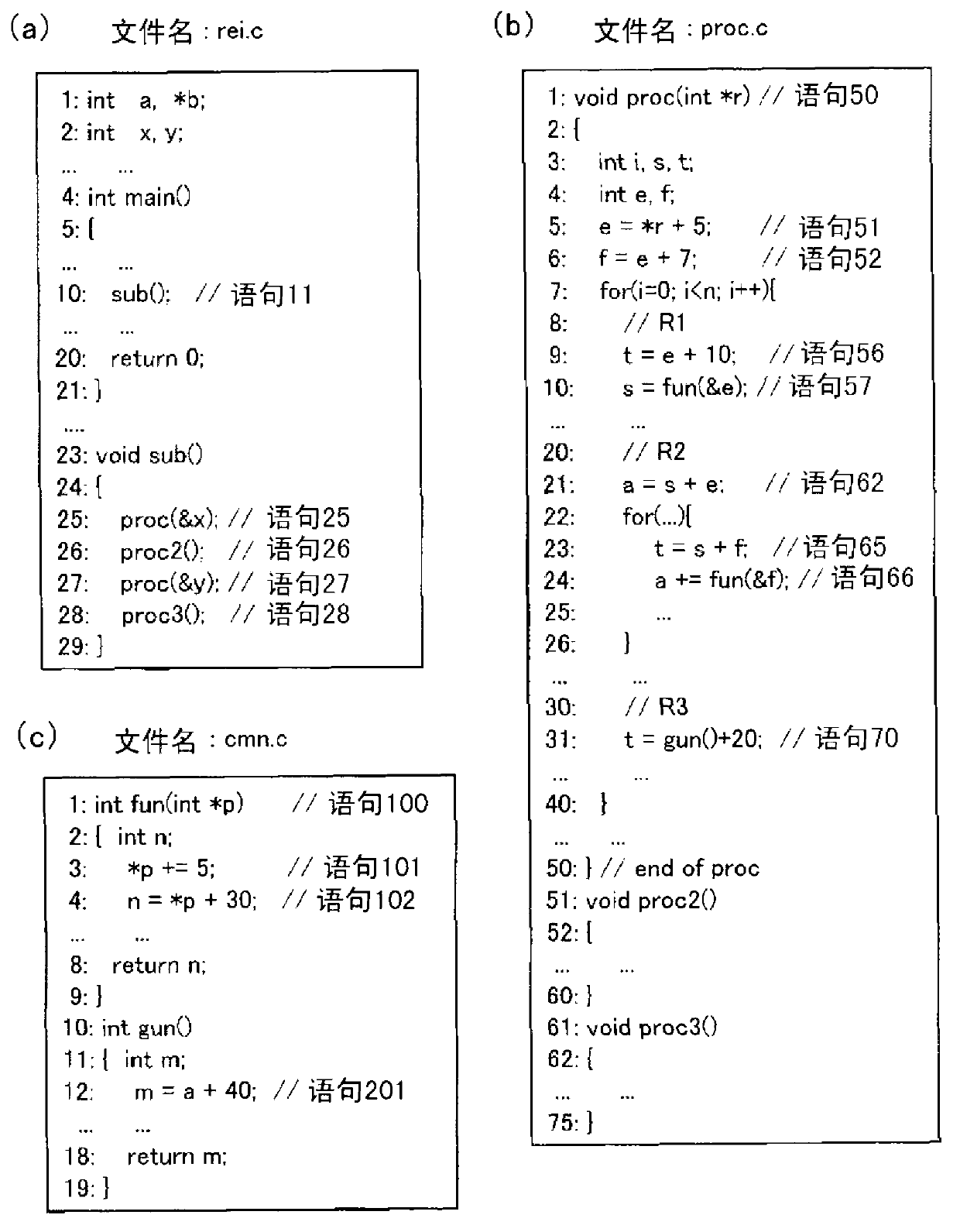
Data dependence analysis support device, data dependence analysis support program, and data dependence analysis support method
InactiveUS20140096117A1Shorten analysis timeAccurate analysisSoftware engineeringProgram controlData dependenceContext sensitivity
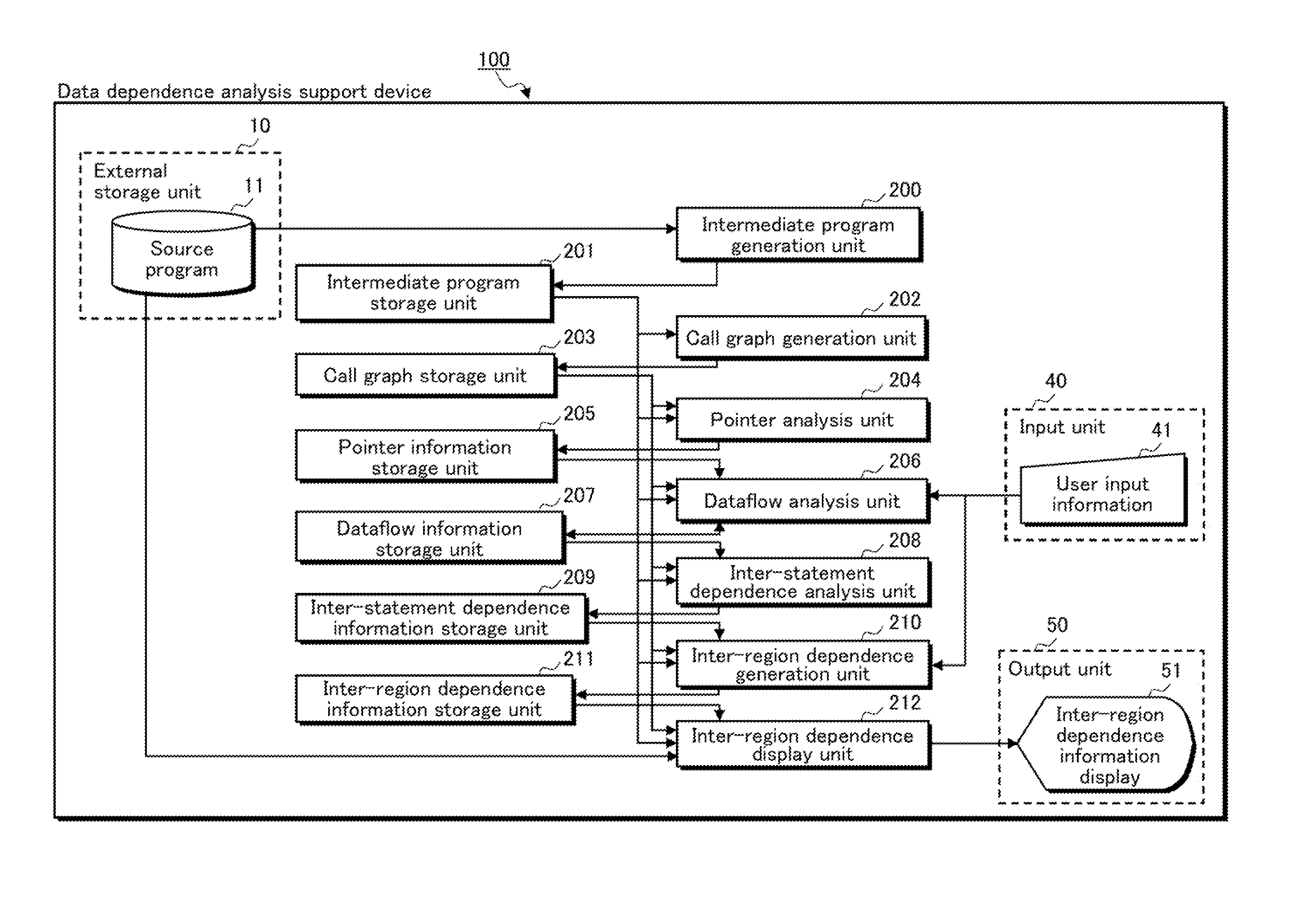
A data dependence analysis support device calculates pointer information by performing a context-sensitive pointer analysis on every pointer used in a program; calculates dataflow information between statements by performing a context-sensitive dataflow analysis, using the context-sensitive pointer information, on all statements in an analysis target region and all statements that might be called upon execution of the analysis target region; and calculates inter-region data dependence information, using the dataflow information, for two or more threaded regions included in the source program.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Wave beam residence scheduling method of cooperative distributed system
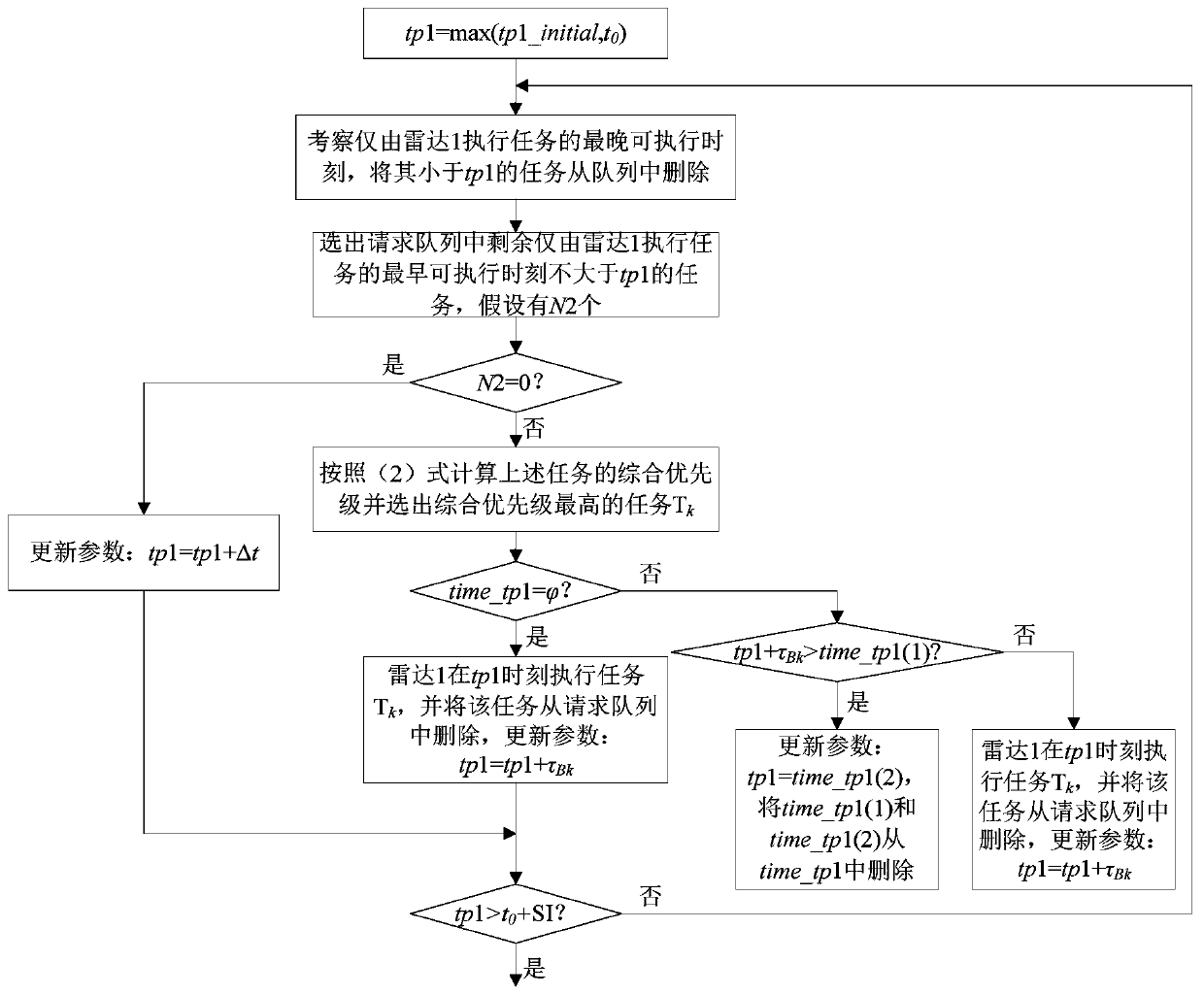
ActiveCN109709535AEffectively play the comprehensive effectRich work flexibilityTotal factory controlRadio wave reradiation/reflectionRadar systemsResidence
The invention relates to a wave beam residence scheduling method of a cooperative distributed system, and belongs to the field of radar system resource management. The priority of a task work manner and influence of deadline on the task priority are both taken into consideration, an HPEDF method is used to calculate the integrated priority, a wave beam residence scheduling model is established according to characteristics of radar task scheduling enforced by multiple stations cooperatively in the cooperative distributed system, a time pointer analysis based heuristic method is used for solution, and the method is formed. The problem that a sub-radar needs to work independently but also needs wave beam residence scheduling during cooperative work is solved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
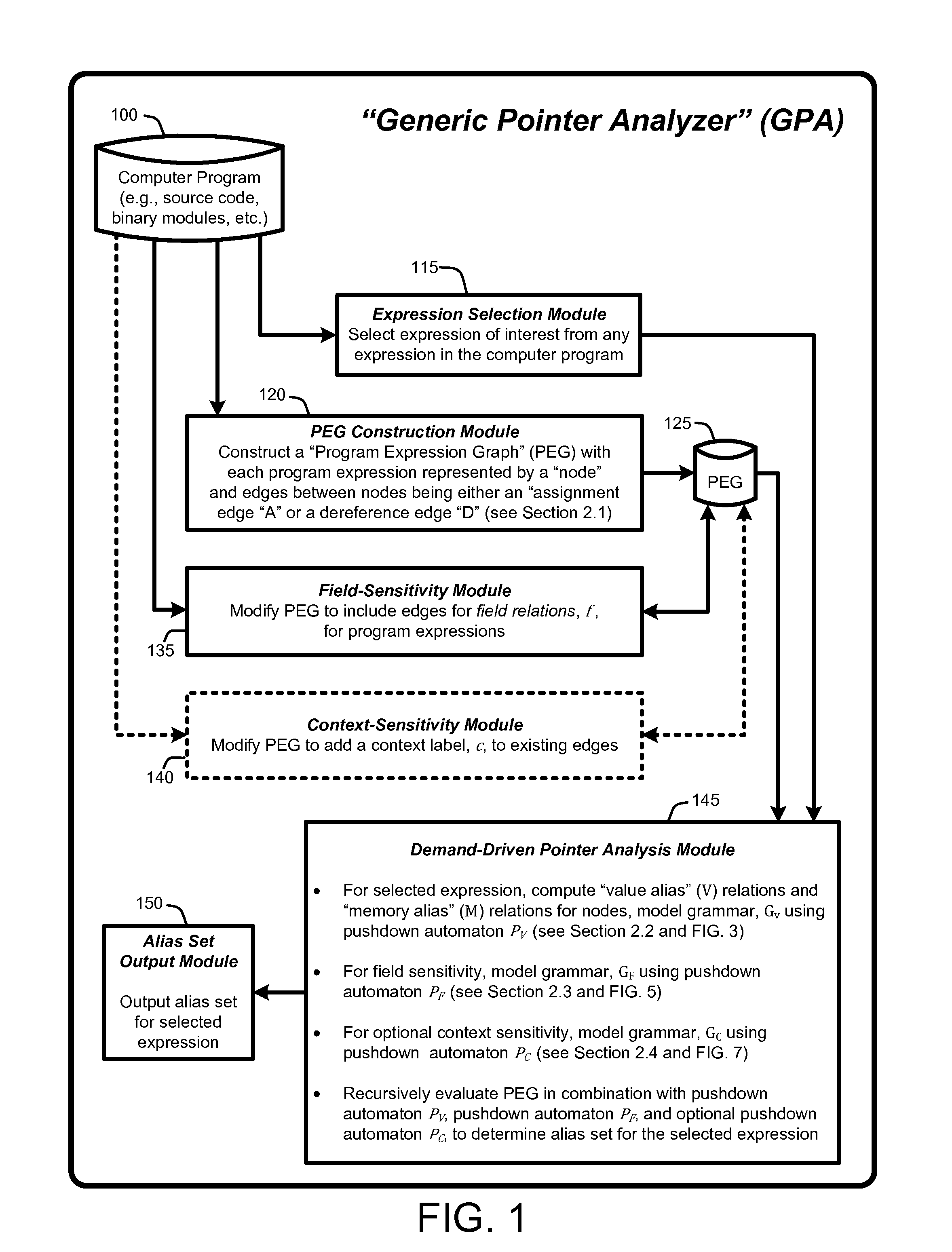
Demand-driven analysis of pointers for software program analysis and debugging
InactiveUS20130055207A1Rapidly identify aliasAccurate settingSoftware engineeringError detection/correctionGraphicsOperational system
A “Demand-Driven Pointer Analyzer” (DDPA) provides a “demand-driven” field-sensitive pointer analysis process. This process rapidly and accurately identifies alias sets for selected pointers in software modules or programs of any size, including large-scale C / C++ programs such as a complete operating system (OS). The DDPA formulates the pointer analysis task as a Context-Free Language (CFL) reachability problem that operates using a Program Expression Graph (PEG) automatically constructed from the program code. The PEG provides a node and edge-based graph representation of all expressions and assignments in the program and allows the DDPA to rapidly identify aliases for pointers in the program by traversing the graph as a CFL reachability problem to determine pointer alias sets. In various embodiments, the DDPA is also context-sensitive.
Owner:MICROSOFT TECH LICENSING LLC
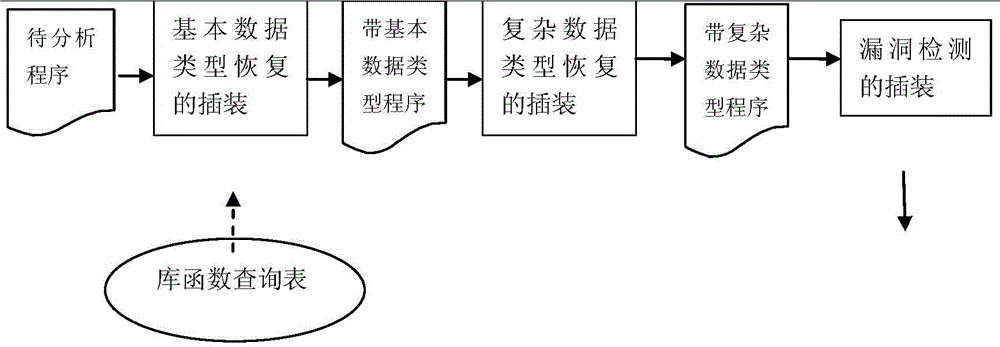
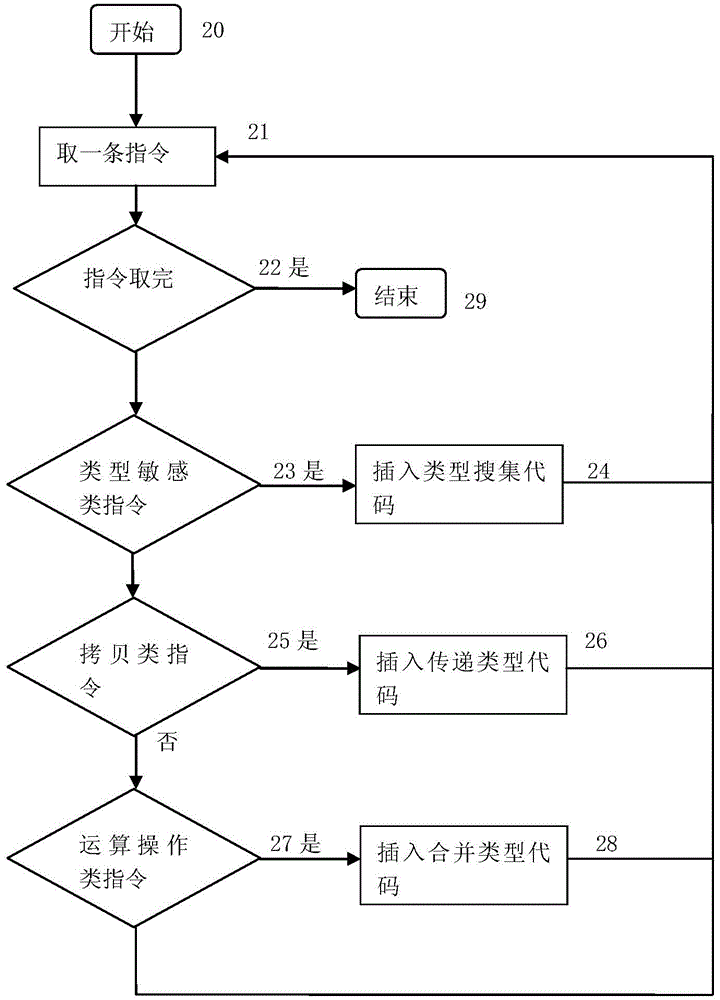
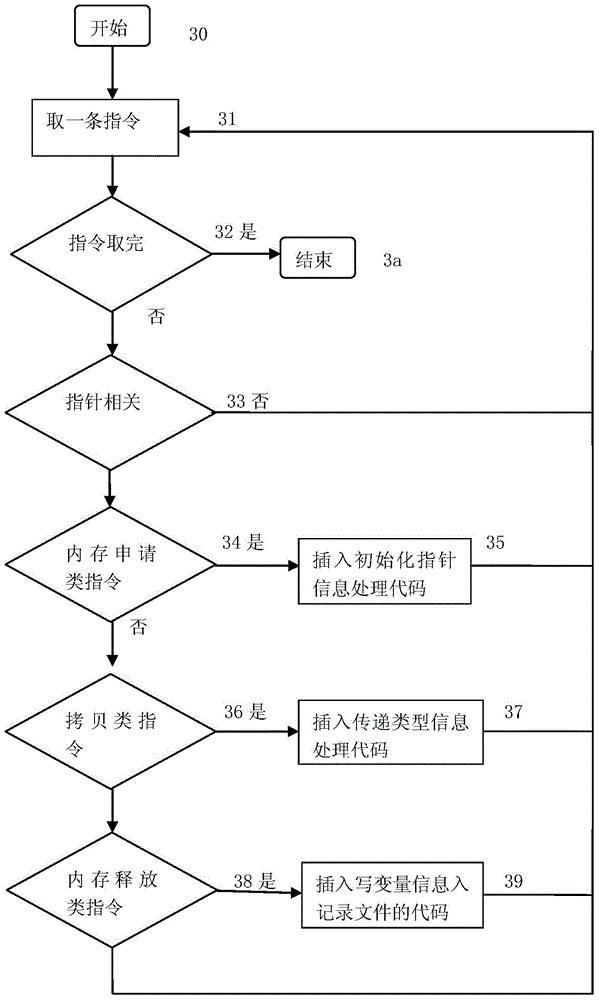
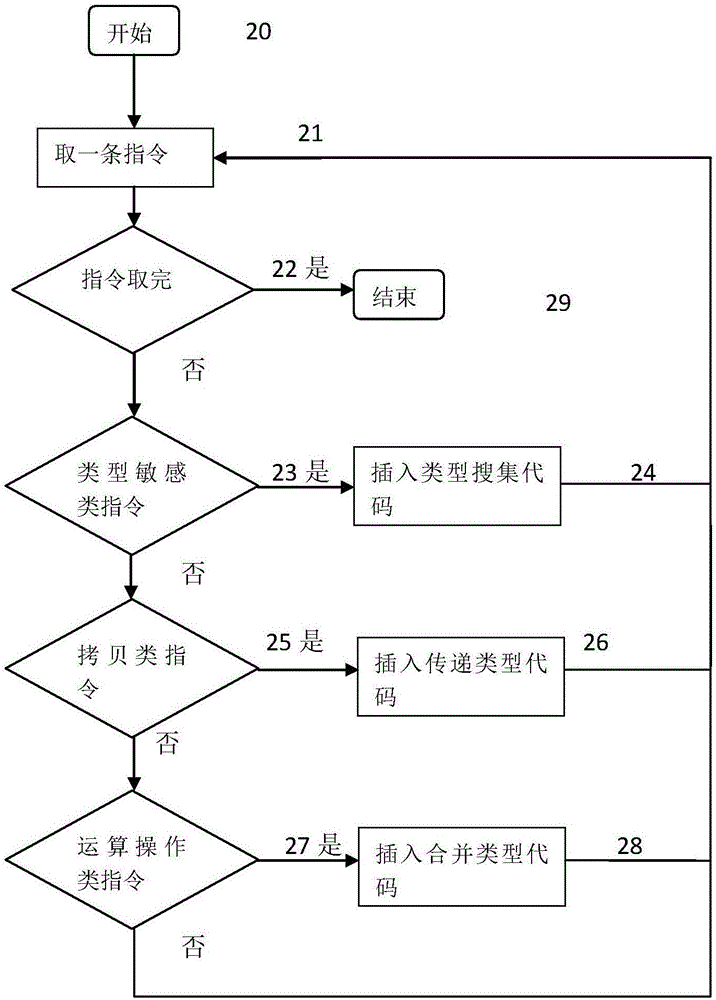
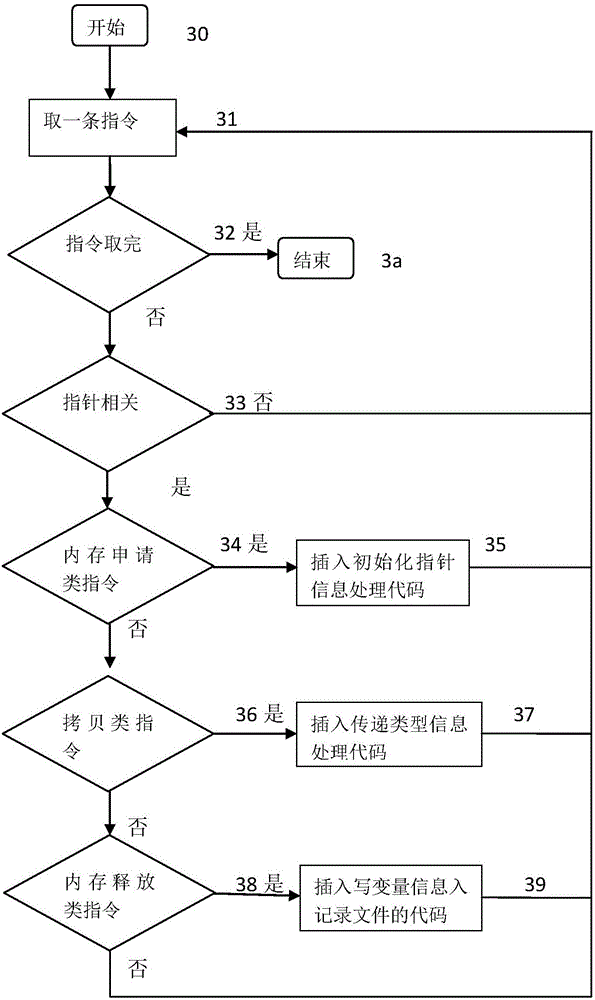
Software vulnerability detection method based on pointer analysis
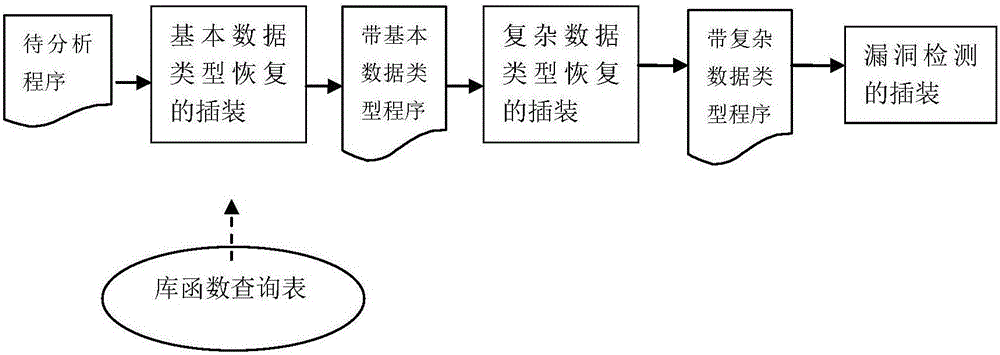
InactiveCN104021073ADiscover and troubleshoot vulnerabilitiesHigh precisionSoftware testing/debuggingComplex data typeData type
A software vulnerability detection method based on pointer analysis includes the following steps that with the help of instrumentation software, three main instrumentation operations of basic data type recovery, complex data type recovery and vulnerability detection are respectively finished, wherein the instrumentation operation of basic data type recovery includes the processes that type collection codes are inserted behind instructions belonging to a type sensitive instruction set, and then propagation codes of different types are inserted according to different assembly instructions; the instrumentation operation of complex data type recovery includes the processes that pointer collection codes are inserted behind a memory application instruction set, pointer analysis codes are inserted according to different assembly instructions, and then complex data types are recovered in the pointer analysis process; the instrumentation operation of vulnerability detection includes the processes that pollution marking codes are inserted to external input positions of programs, stain spreading codes are inserted according to assembly instructions, and security detection codes are inserted to security sensitive points.
Owner:NANJING UNIV
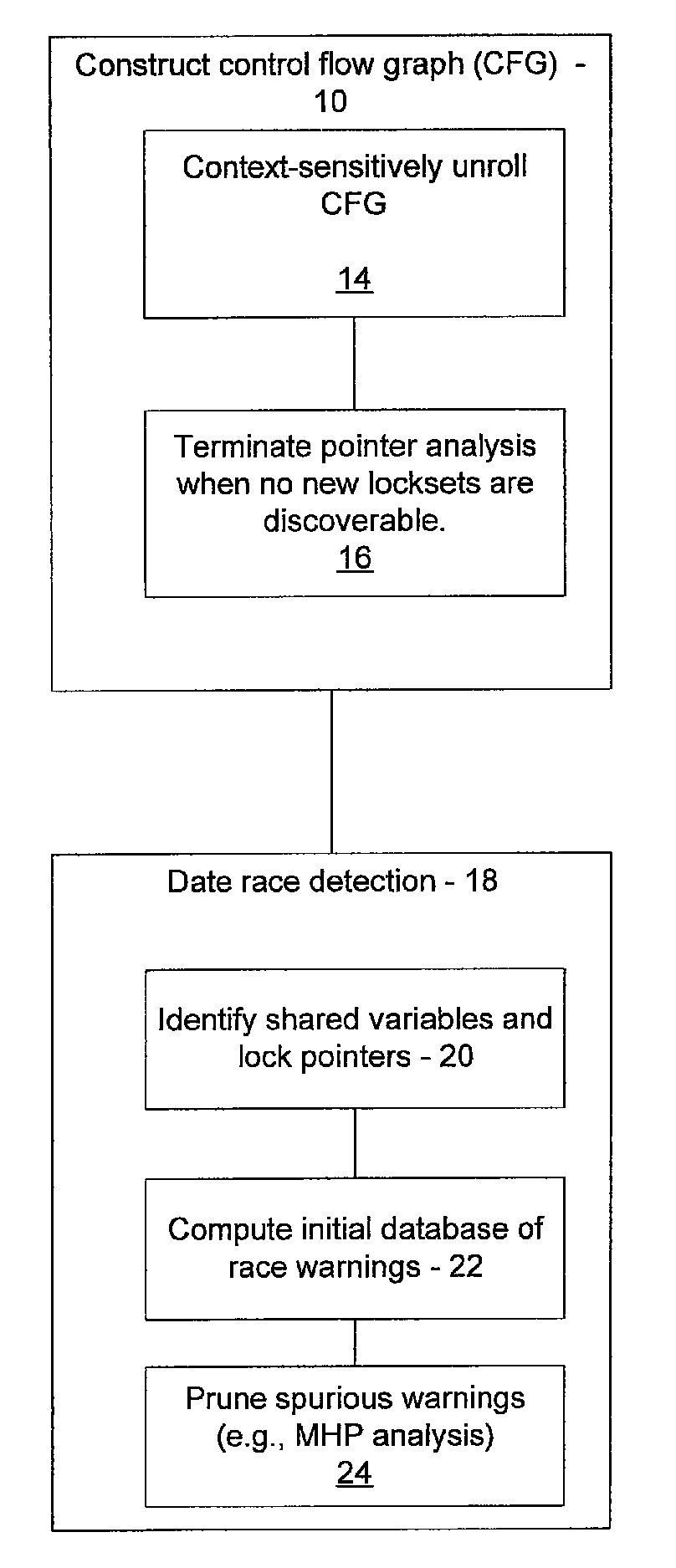
Fast and accurate data race detection for concurrent programs with asynchronous calls
ActiveUS8539450B2Error detection/correctionSoftware engineeringPointer aliasingTheoretical computer science
Owner:NEC CORP
C language defect detection method and device based on multi-level analysis
ActiveCN111104335AGuaranteed accuracyImprove defect detection efficiencyReverse engineeringSoftware testing/debuggingPathPingRelation graph
The embodiment of the invention discloses a C language defect detection method and device based on multi-level analysis. The method comprises the following steps: calculating pointer pointing information of each function in the function call relation graph based on a path-sensitive pointer analysis method; performing inter-process analysis on a calling function corresponding to a function callingstatement in the function calling relational graph to obtain abstract information of the calling function; aiming at each node in the control flow graph, determining a control dependence correspondingrelation and a data dependence corresponding relation corresponding to the node; and generating a value flow graph according to the pointer pointing information of each function, the abstract information of the calling function, the control dependence corresponding relation corresponding to each node and the data dependence corresponding relation, and performing defect detection on the to-be-detected C language program according to the value flow graph to obtain a detection result. By applying the scheme provided by the embodiment of the invention, the accuracy and efficiency of defect detection can be considered.
Owner:TSINGHUA UNIV
Breakdown automatically-positioning method for null pointer abnormity
InactiveCN102981953AOvercome the flaw of imprecise analysis resultsSoftware testing/debuggingTime informationAlgorithm
The invention relates to a breakdown automatically-positioning method for a null pointer abnormity. The method includes the three steps: (1) slicing a procedure, (2) positioning a breakdown, null pointer analyzing and alias analyzing the procedure after slicing, (3) being visualized. The method of combining a static analysis and real-time information stacking is adopted, a source of the null pointer abnormity is led out through automatic positioning, the shortcomings that analyzing results are not accurate due to the single use of the static analysis method, and the real-time information stacking is too tough and cannot be independently applied are overcome, and meanwhile dynamic information can be collected with no price is paid.
Owner:CHINA UNIV OF MINING & TECH
Assembly level interprocedual pointer analysis method based on speculative multithreading
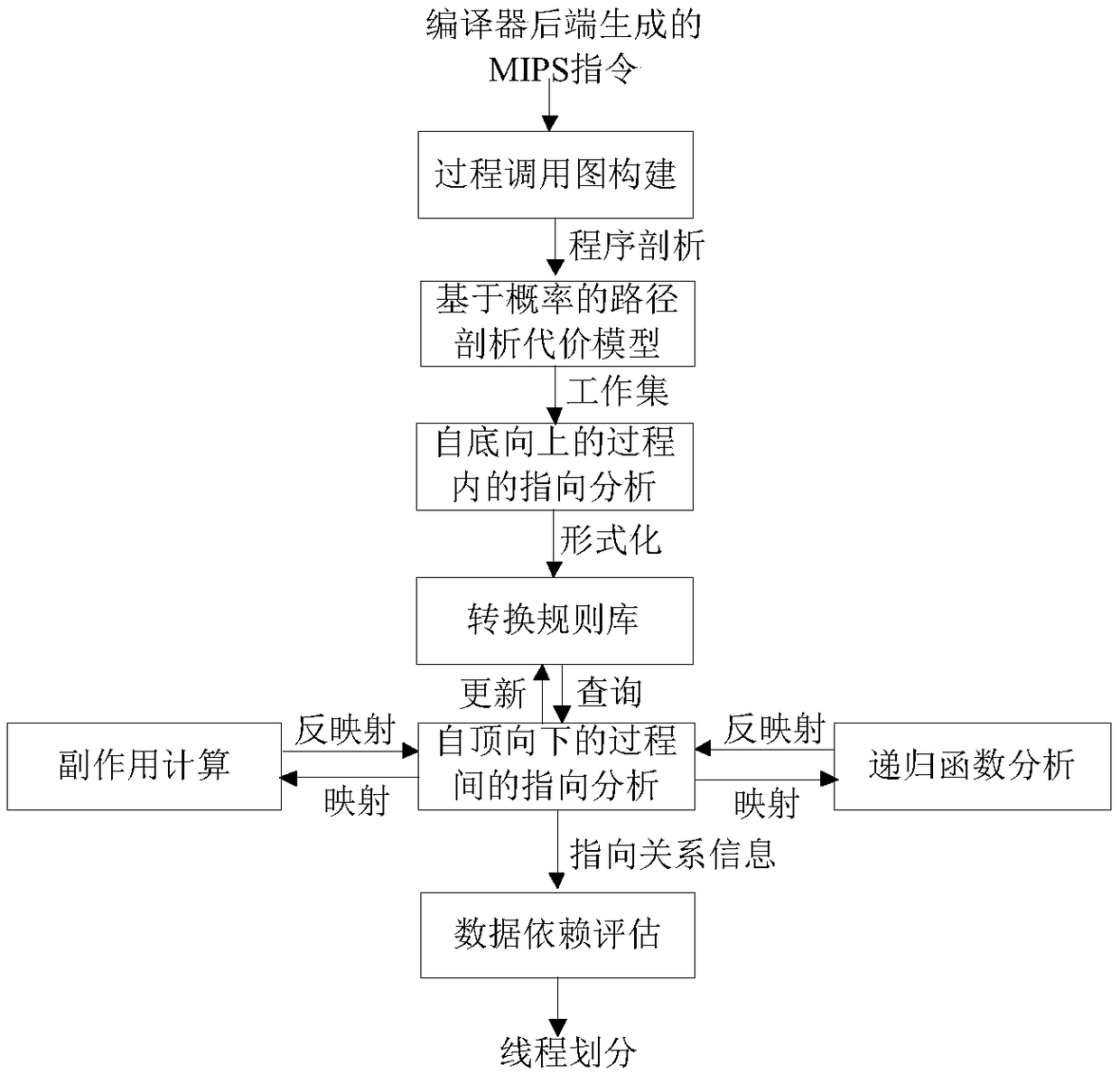
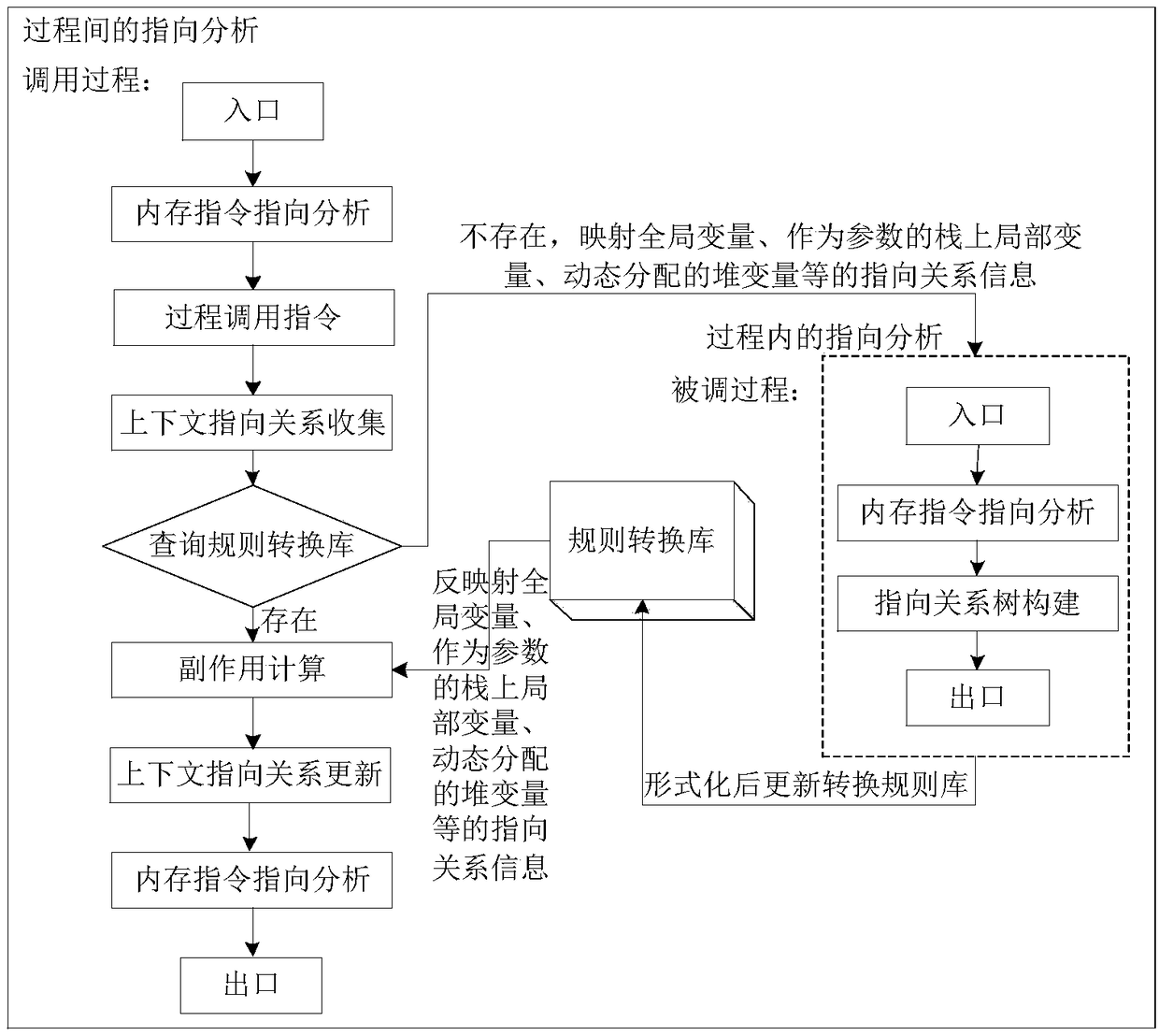
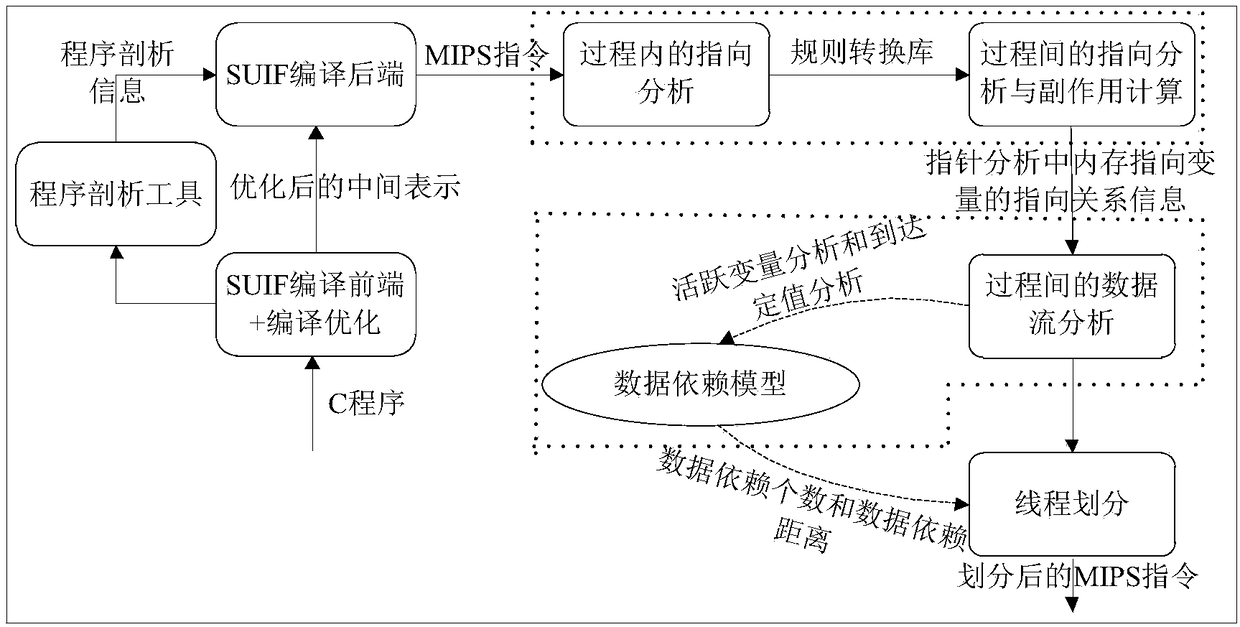
ActiveCN108932137ARefine Data DependenciesAccurate analysisInstruction analysisConcurrent instruction executionProcedure callsPath profile
The invention discloses an assembly level interprocedual pointer analysis method based on speculative multithreading. Through assembly level interprocedual points-to analysis, a procedure call graph of all processes is established in a source program before the interprocedual points-to analysis is carried out, and after establishment, points-to analysis is carried out in two stages. The method comprises: in the first stage, firstly, establishing a path profiling cost model based on probability, extracting speculative paths selected by all process nodes in the procedure call graph, and then performing points-to analysis in a process; in the second stage, performing interprocedual points-to analysis and interprocedual side-effect calculation, on each process calling point, performing mappingand inverse mapping on points-to relations using a points-to analysis result in a process, to obtain an interprocedual side-effect calculation result, and realize context points-to relation update ofa calling procedure. On this basis, the method guides a whole procedure to perform interprocedual data flow analysis, evaluates data dependence degree among pointer variable memory points-to relations, and obtains a more accurate thread partitioning result.
Owner:XIAN AERONAUTICAL UNIV
Method for intelligently detecting C program memory leakage based on machine learning
ActiveCN108804332AThe classifier results are accurateQuick checkSoftware testing/debuggingData setThree stage
The invention discloses a method for intelligently detecting C program memory leakage based on machine learning. The method has three stages; in a model construction stage, two data sets are constructed according to original memory leakage; memory leakage characteristics are extracted respectively from the two data sets; the memory leakage characteristics are input into a machine learning classifier, so that training and cross validation are carried out; the type and the parameter of the classifier are modified; the memory leakage is detected by taking the classifier having highest classification accuracy rate as the classifier model; in a program analysis and characteristic obtaining stage, a source program is pre-analyzed; all memory allocation points o are obtained; then, pointer analysis is carried out; a VFG (Value Flow Graph) at the beginning of o is constructed; the memory leakage characteristics corresponding to each path in the VFG are extracted; in a defect detection and report stage, the memory leakage characteristics in the program analysis and characteristic obtaining stage are input into the classifier model in the model construction stage and detected; whether memoryleakage exists in a path at the beginning of o or not is judged; and thus, a memory leakage report is obtained.
Owner:NANJING UNIV
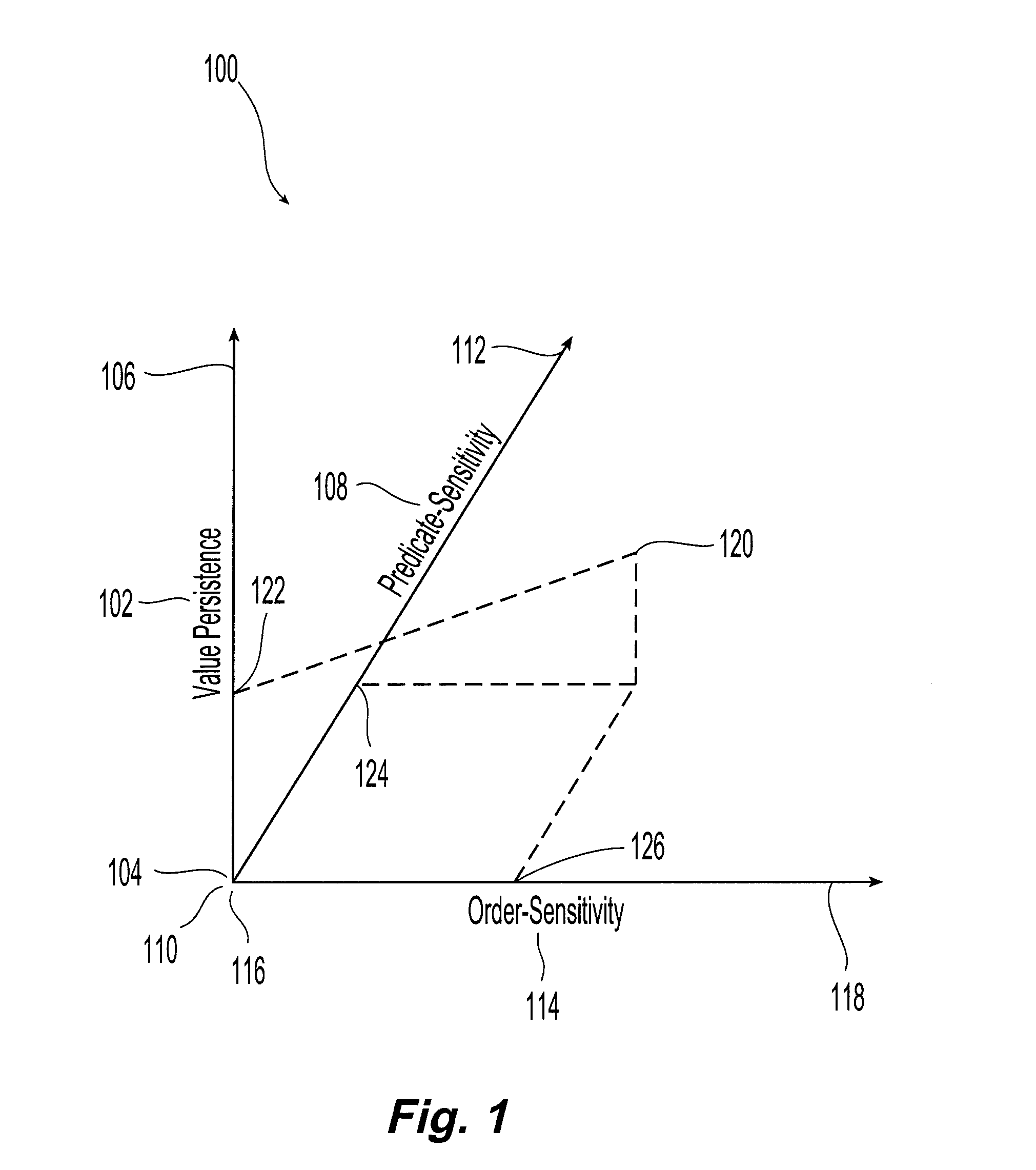
Procedure Summaries for Pointer Analysis
Pointer analysis is used for different applications, e.g., compilers, debugging tools and programs understanding tools, each having different requirements. A framework for pointer analysis is provided that defines a multidimensional space, for example a three-dimensional space, containing an order sensitivity dimension, a predicate sensitivity dimension and a value persistence dimension. A point in the three-dimensional space is identified. This point yields values for order sensitivity, predicate sensitivity and value persistence. Pointer analysis is then conducted on a computer program in accordance with the identified values for order sensitivity, predicate sensitivity and value persistence.
Owner:GLOBALFOUNDRIES INC
GPU-based large-scale software high-precision static analysis method
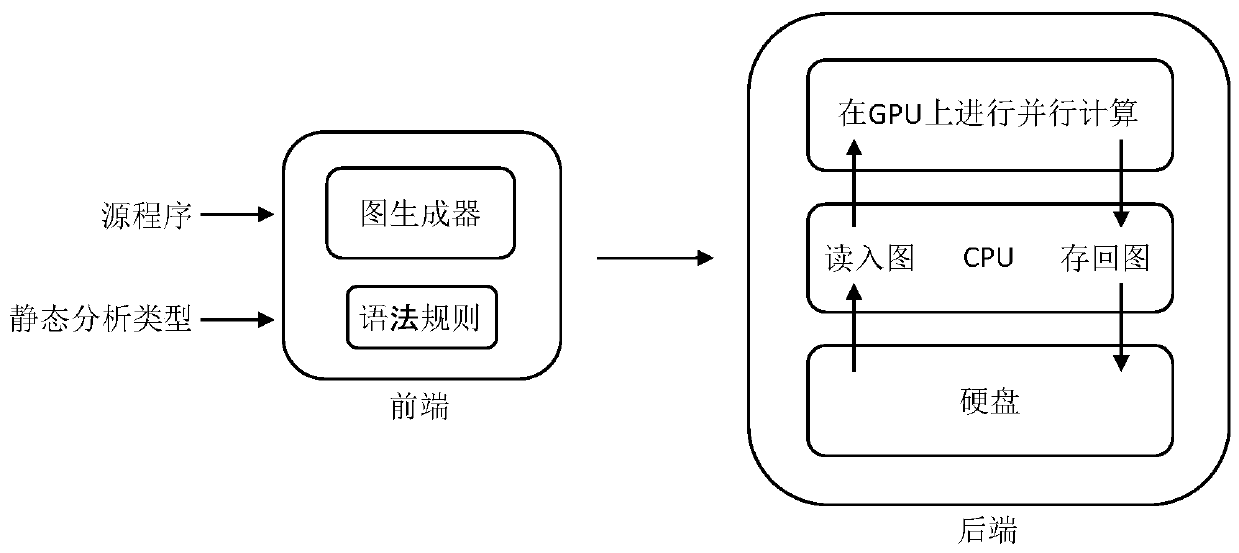
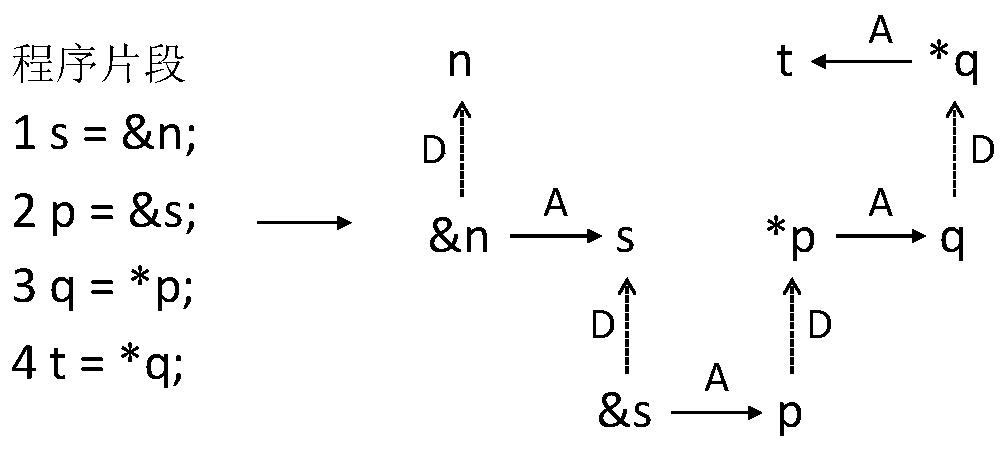
InactiveCN109783386AFast analysisImprove efficiencyResource allocationSoftware testing/debuggingVideo memoryExtensibility
The invention discloses a GPU-based large-scale software high-precision static analysis method. The method comprises the following steps of: firstly, converting a series of specific program analysis,such as pointer analysis, data flow analysis, program slicing and the like, into a special graph accessibility problem, namely a context independent language (CFL) accessibility problem; Transmittingthe converted program chart and the corresponding grammar rule to a graphics processing unit (GPU) to carry out parallel CFL reachability calculation, namely dynamically adding edges according to thegrammar rule until a fixed point is reached; And if the size of the graph exceeds the limited value of the video memory, only part of data can be called to participate in calculation each time, and the rest is stored in a hard disk. By utilizing the GPU and the external memory, the method disclosed by the invention has relatively high efficiency and expandability, and can be used for carrying outcomplex code analysis on a large-scale software system.
Owner:NANJING UNIV
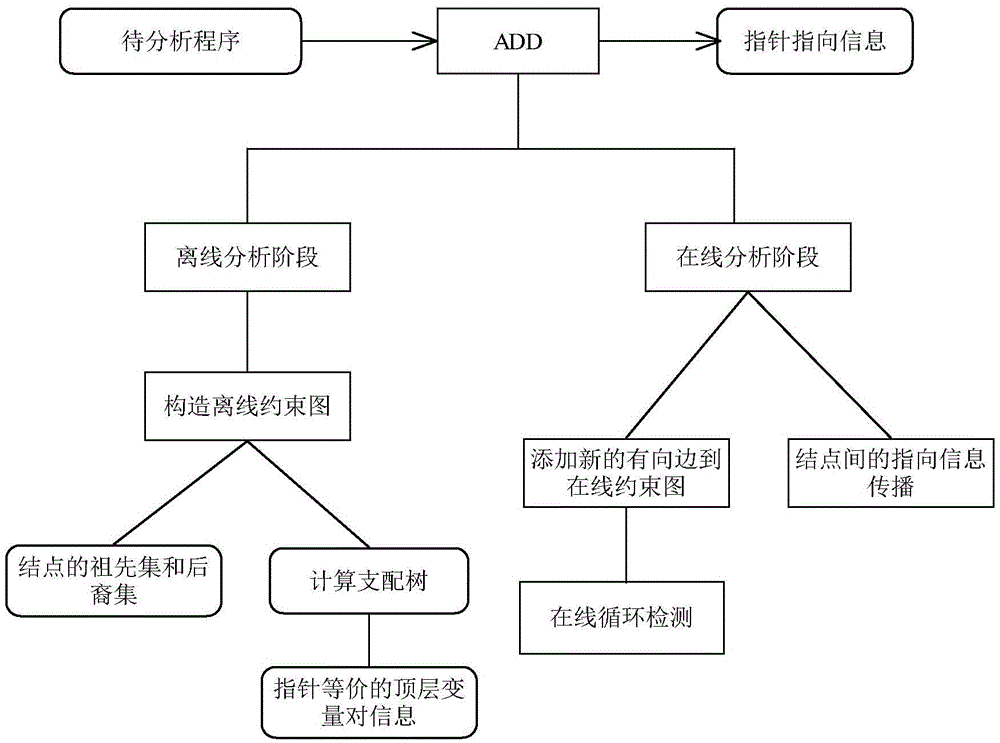
Pointer analysis method based on offline constraint graph
ActiveCN105589730AQuality improvementImprove analysis efficiencySoftware engineeringProgram controlTheoretical computer scienceConstraint graph
The present invention discloses a pointer analysis method based on an offline constraint graph. The method comprises two phases: an offline analysis phase and an online analysis phase. In the offline analysis phase, ADD firstly constructs an offline constraint graph, next defines and calculates an ancestor set and a descendant set for each node in the offline constraint graph, then calculates a domination tree corresponding to the offline constraint graph, and based on domination node information, calculates equivalent top-layer variable pair information of a pointer. In the online analysis phase, the ADD performs online cycle detection by using the ancestor set and the descendant set of the node on the one hand, and reduces spreading overheads of inter-node point information in an analysis process by using the equivalent top-layer variable pair information of the pointer on the other hand. Compared with the conventional LCD based on the contained pointer analysis method, the ADD is capable of improving pointer analysis efficiency without affecting precision of the point information.
Owner:SOUTHEAST UNIV
Data-dependent analysis assistance device, data-dependent analysis assistance program and data-dependent analysis assistance method
InactiveCN103314360AAccurate acquisitionShorten analysis timeSoftware engineeringProgram controlProgramming languageData stream
A data-dependent analysis assistance device: for all pointers used in a program, performs context-sensitive pointer analysis and computes pointer information; for an area for analysis and for all program lines that could be called when the area for analysis is executed, performs context-sensitive data flow analysis using the context-sensitive pointer information; computes program line-to-program line data flow information; and, using the data flow information, computes area-to-area data-dependent information in two or more threaded areas contained in a source program.
Owner:PANASONIC CORP
A Method to Sufficiently Detect Null Pointer Reference Defects
InactiveCN103218296BSolve the problem of false positivesImprove sufficiencySoftware testing/debuggingNODALInterval arithmetic
Owner:BEIJING UNIV OF POSTS & TELECOMM
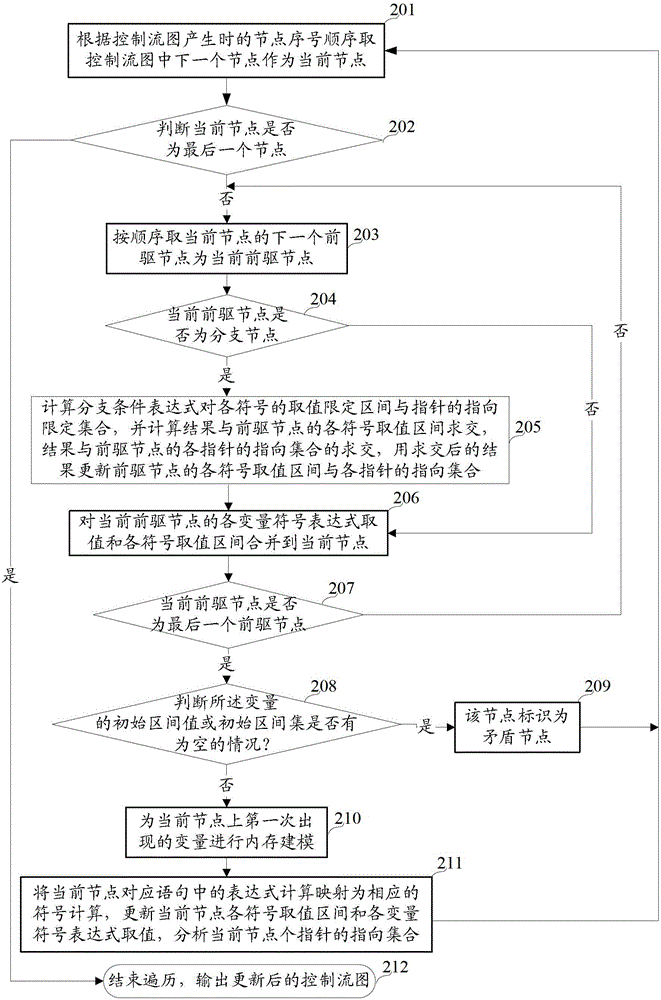
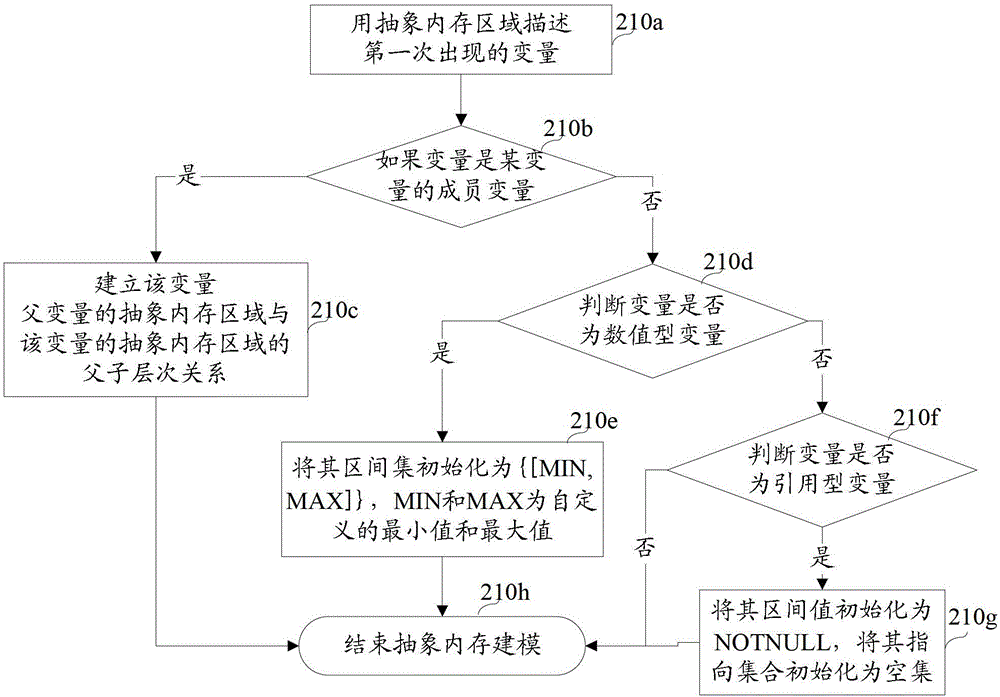
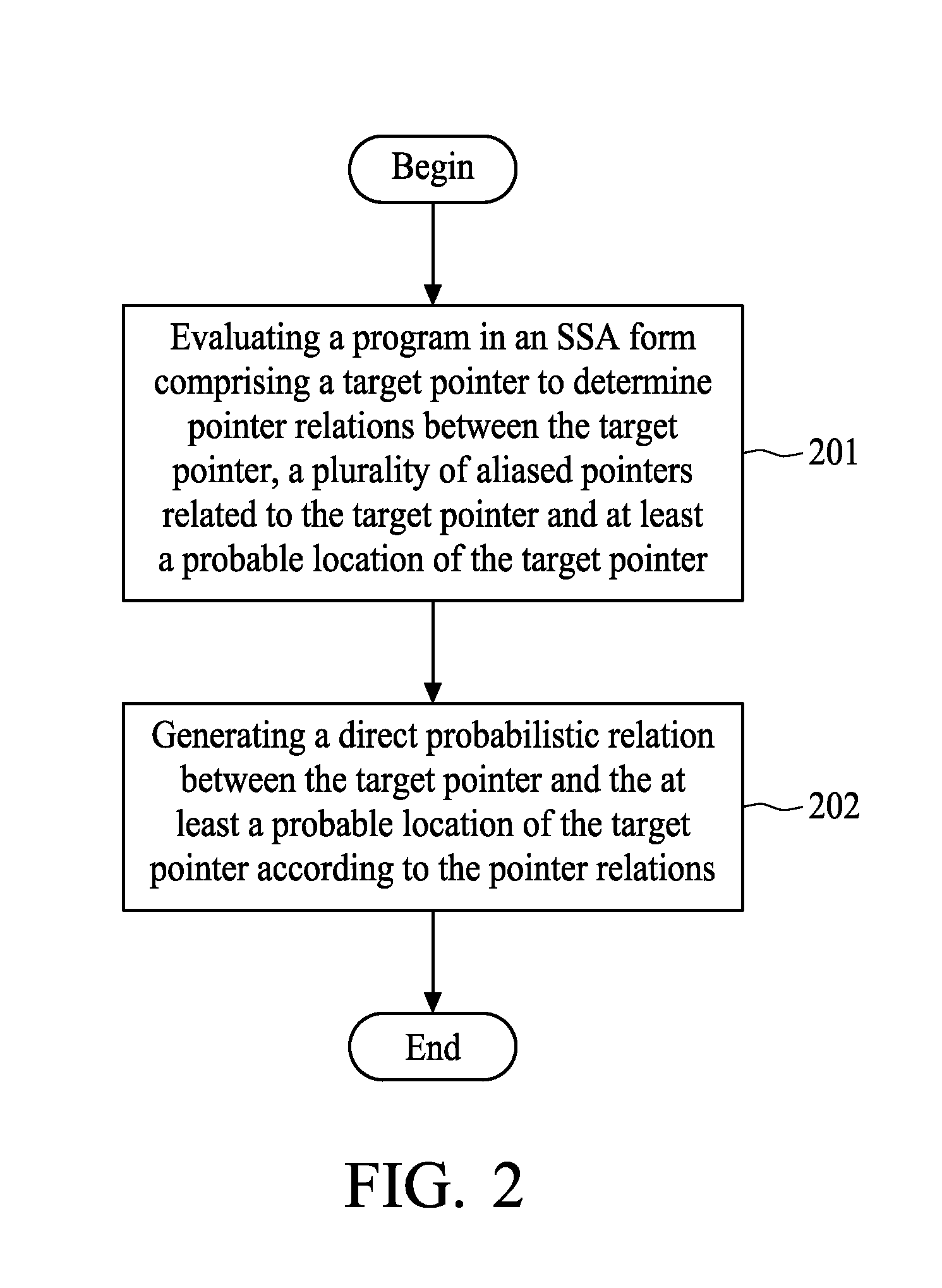
Probabilistic pointer analysis method using ssa form
A computer-implemented probabilistic pointer analysis method using SSA form comprises the steps of: evaluating a program in an SSA form comprising a target pointer to determine pointer relations between the target pointer, a plurality of aliased pointers related to the target pointer and at least a probable location of the target pointer; and generating a direct probabilistic relation between the target pointer and the at least a probable location of the target pointer according to the pointer relation.
Owner:NATIONAL TSING HUA UNIVERSITY
Java null pointer analysis system based on constant value arrival analysis method
InactiveCN110188029AIntuitive and convenient to viewImprove legibilitySoftware testing/debuggingSoftware systemComputer module
The invention relates to the field of software static analysis, in particular to a Java null pointer analysis system based on a fixed value arrival analysis method. The system comprises a project module, a filter module, a source code module, a console module, a null pointer analysis module and a result display module. According to the system, a developer can be helped to timely discover suspectedsource code lines with null pointer abnormity in a source code in a development process. Through the tool, the source codes can be directly displayed and jumped to suspected abnormal source code lines, developers can check and analyze the source codes more conveniently and visually, accordingly, the corresponding source codes can be modified, the source code structure is further perfected, the readability of the source codes is enhanced, a better source code style is formed, and a more perfect software system is developed.
Owner:SUN YAT SEN UNIV
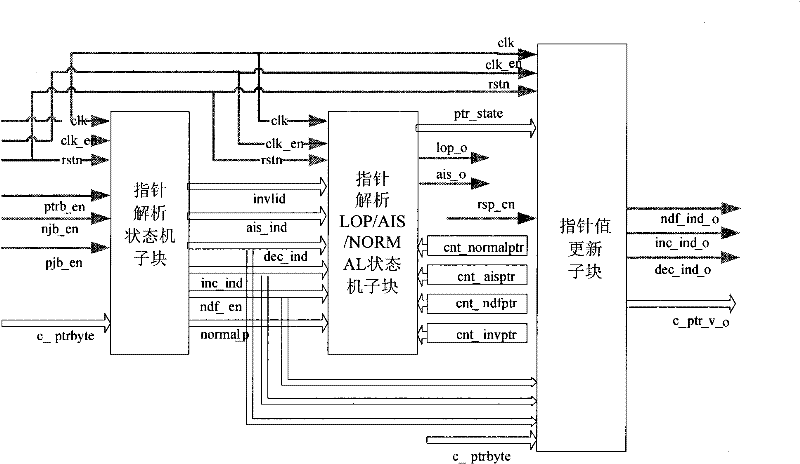
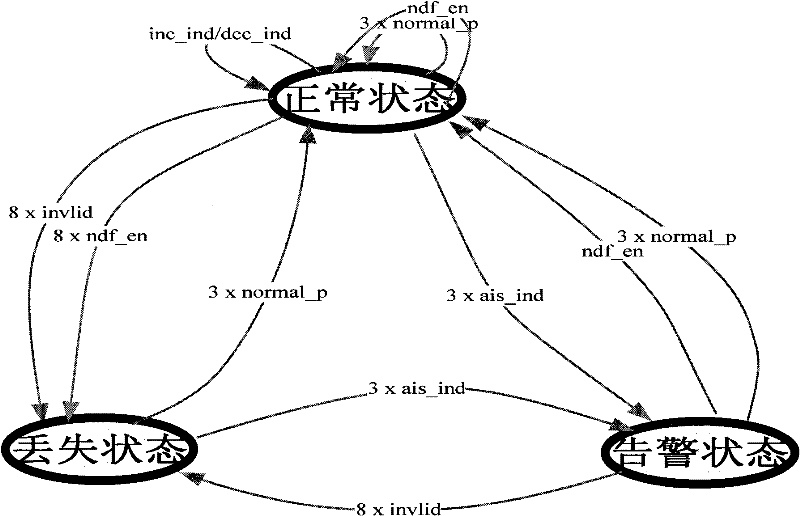
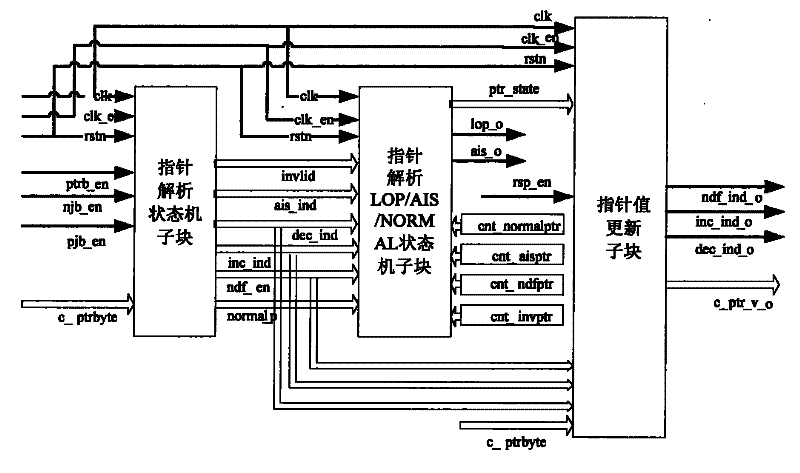
System suitable for analysis control of AU/TU pointer
ActiveCN102195734ASolve the problem of parsing (Pointer generation)Solving Dispersion ProblemsMultiplex system selection arrangementsTime-division multiplexDispersityAlarm state
The invention discloses a system suitable for the analysis control of an AU / TU pointer, which comprises the sub-block of a pointer analysis state machine, a pointer type state machine and an I / D bit inversion detection module, wherein the pointer type state machine is used for judging and outputting the type of state indication according to the current pointer value; the I / D bit inversion detection module is used for indicating the adjustment indication type of the pointer; the pointer analysis LOP / AIS / NORMAL state machine sub-block uses the pointer type which is generated by the pointer analysis state machine as the basis to carry out the state skip and output pointer loss state indication and alarm state indication; the initial state in the resetting course is used as the loss state of the pointer; and the pointer value updating sub-block updates the value of the pointer and outputs positive adjustment indication signals, negative adjustment indication signals and new pointer adjustment indication signals according to the positive and negative adjustment indication and new data pointer adjustment indication which are generated by the pointer analysis state machine. The system disclosed by the invention solves the dispersity of the existing pointer analysis treatment of an SDH (synchronous digital hierarchy).
Owner:LIUZHOU DADI TELECOMM EQUIP
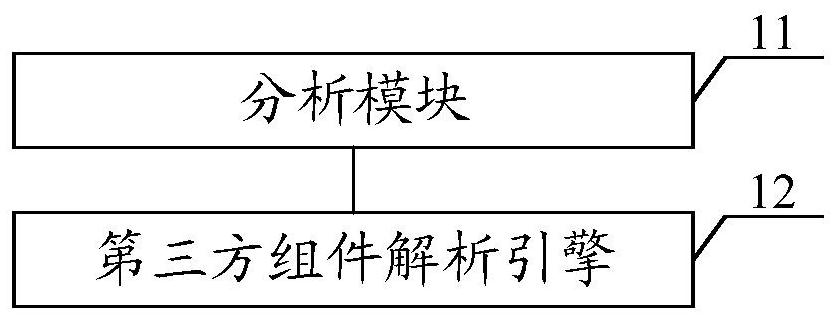
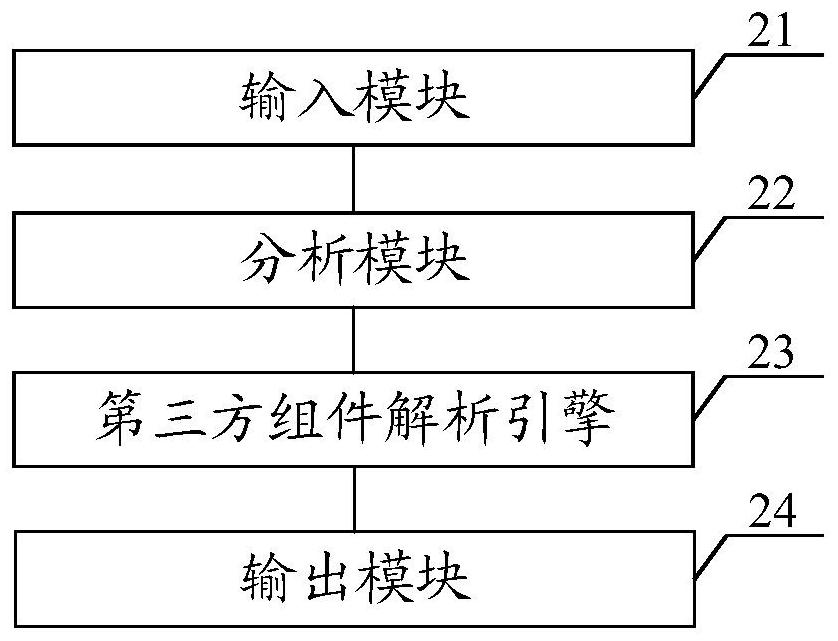
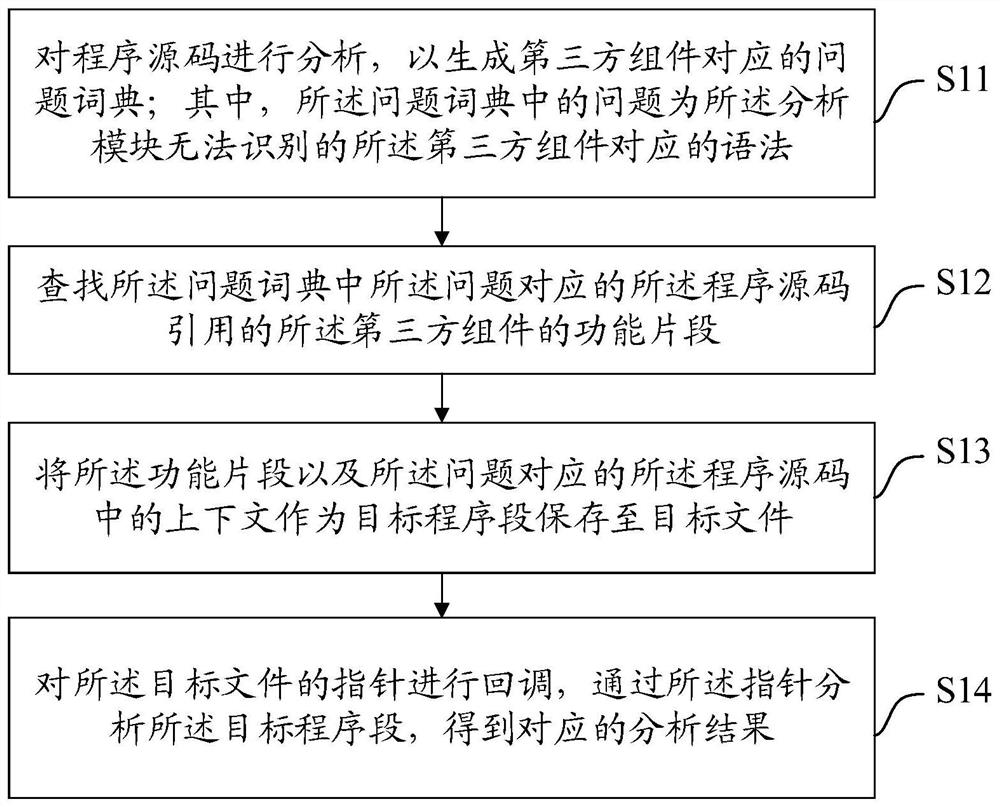
Source code scanning tool, method, equipment and medium
ActiveCN112000572AReduce false negative rateImprove accuracySoftware testing/debuggingThird partyProgram segment
The invention discloses a source code scanning tool, method and device and a medium, and the tool comprises an analysis module which is used for analyzing a program source code, so as to generate a question dictionary corresponding to a third-party assembly; wherein a problem in the problem dictionary is a grammar corresponding to the third-party part which cannot be identified by the analysis module; third-party part parsing engine, the searching module is used for searching a function fragment of the third-party part referenced by the program source code corresponding to the question in thequestion dictionary; and storing the function segment and a context in the program source code corresponding to the problem as a target program segment in a target file, and calling back a pointer ofthe target file to the analysis module, so that the analysis module analyzes the target program segment through the pointer to obtain a corresponding analysis result. Therefore, the missing report rate of the source code problem can be reduced, and the accuracy of reporting the source code problem is improved.
Owner:北京浪潮数据技术有限公司
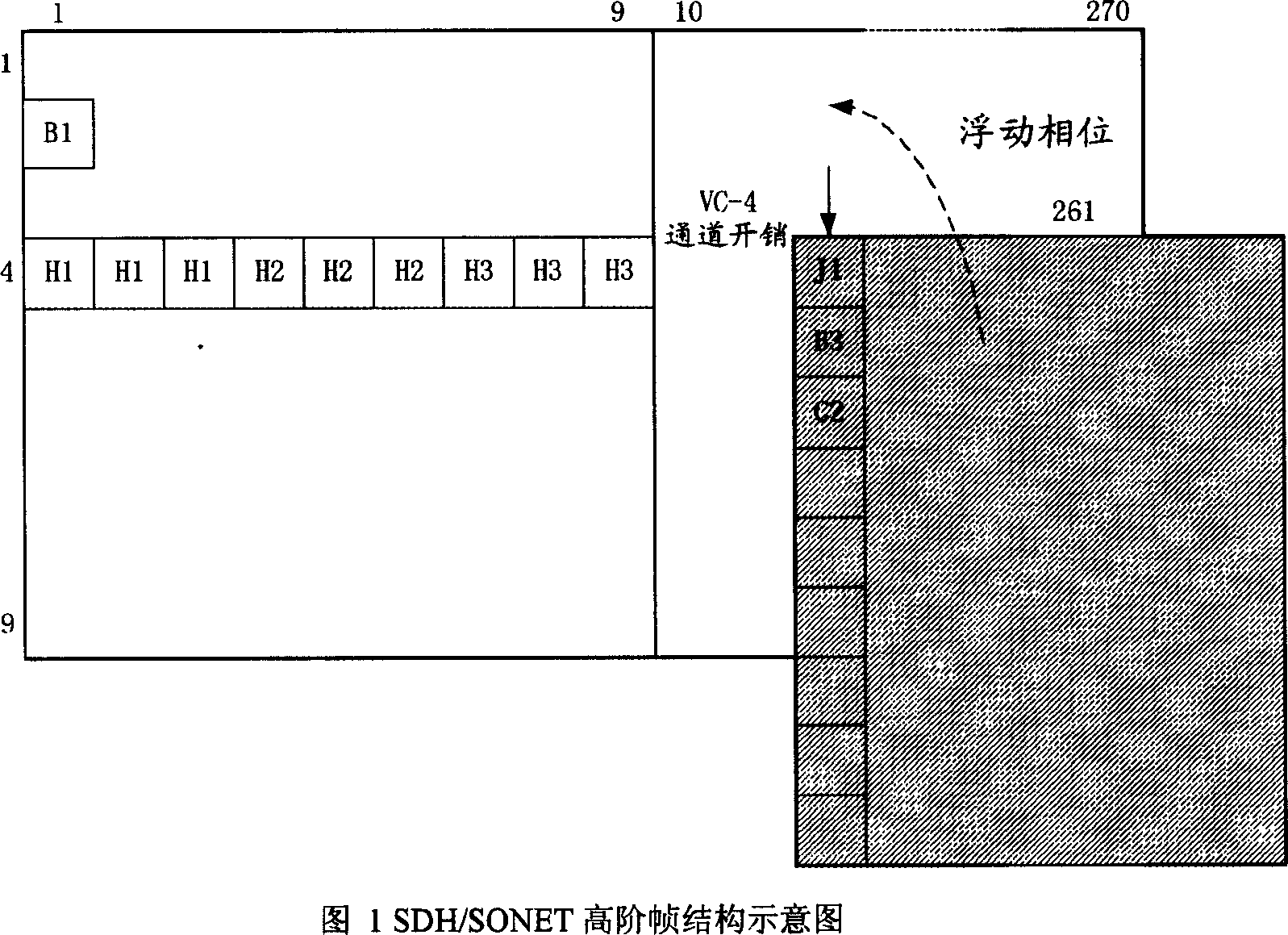
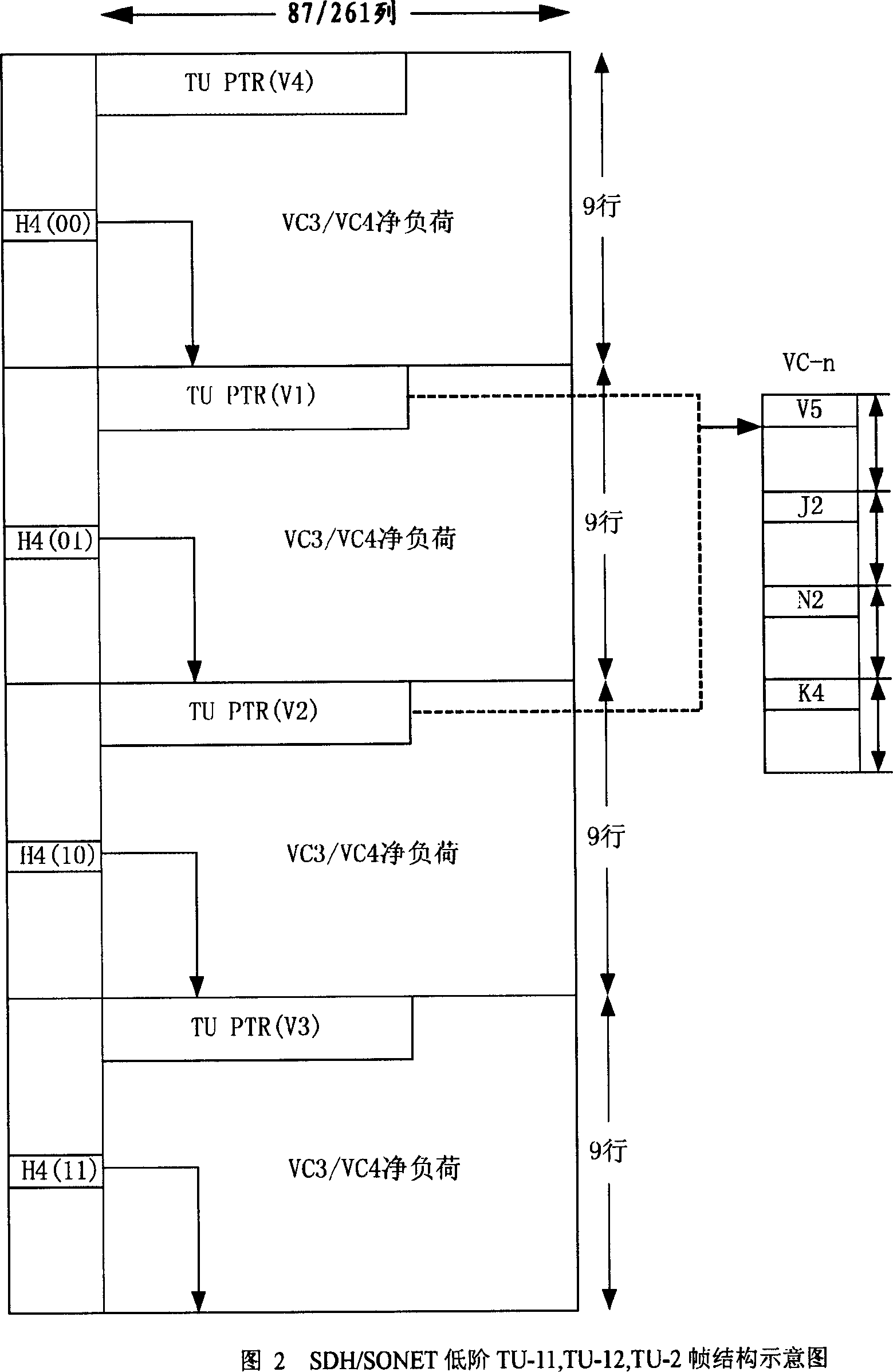
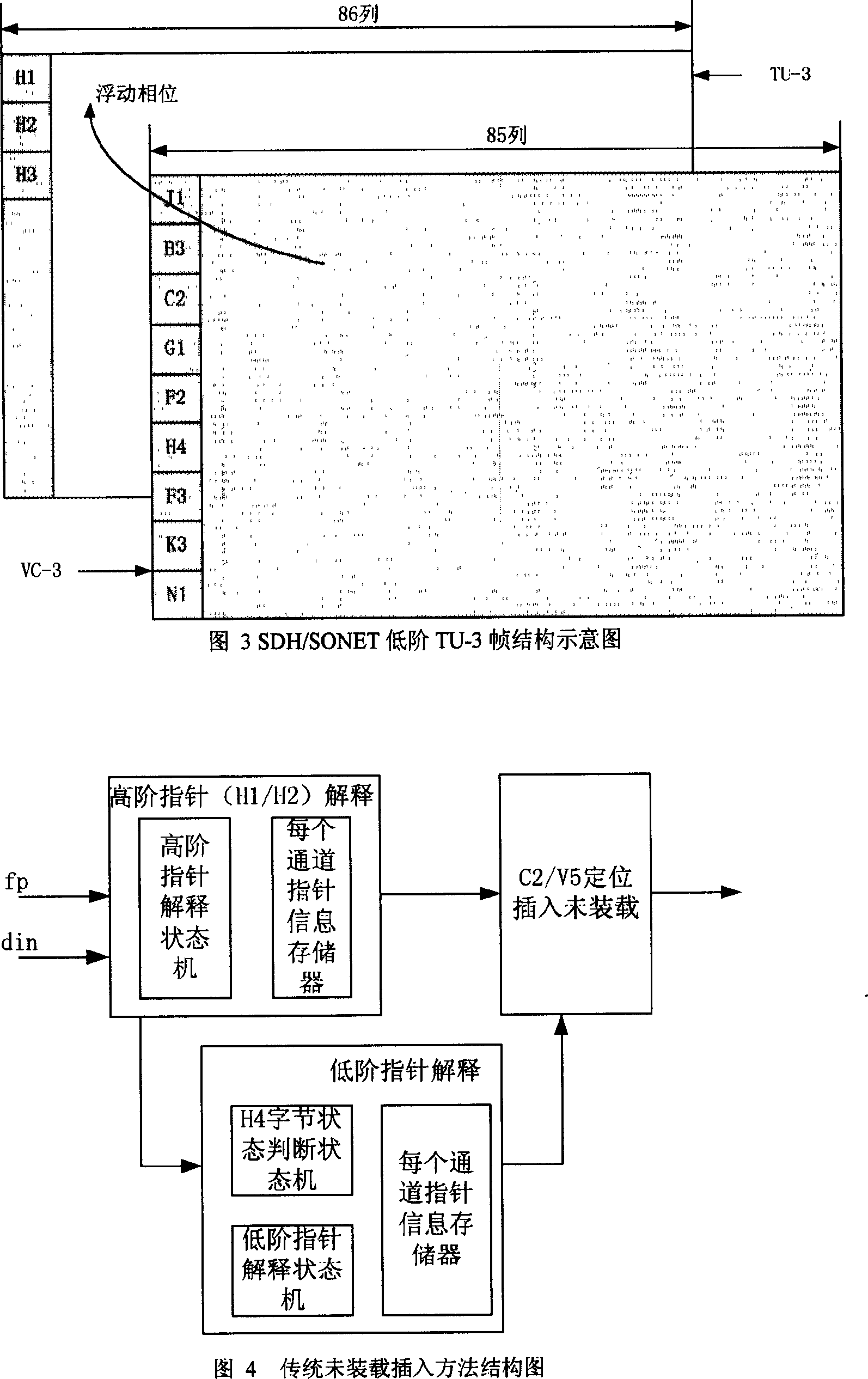
SDH/SONET non-loading plug-in method and apparatus
This invention relates to a method for plugging unload bytes of SDH / SONET and a circuit including generating high-low order channel to load the data stream, among which, the effective pointer value is plugged into H6, H2 high-order pointer positions to the high-order channel, zero bytes are plugged into other overhead bytes and net charge positions, thus, C2 bytes are zero and the lower reach device receives the channel without loading instruction information, the effective pointer value is given at V1, V2 bytes and zero is plugged into other overhead and net charge positions to realize that zero is plugged into the V5 byte unload bit so as to realize low order unload plug, which omits the pointer analysis circuit.
Owner:UTSTARCOM TELECOM CO LTD
A Deep Structure Pointer Analysis Optimization Method for Analyzing Source-Database Pattern Defect Detectors
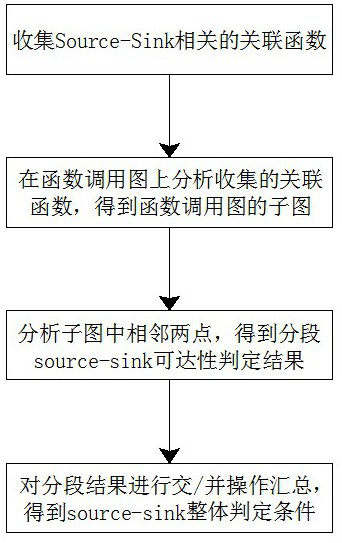
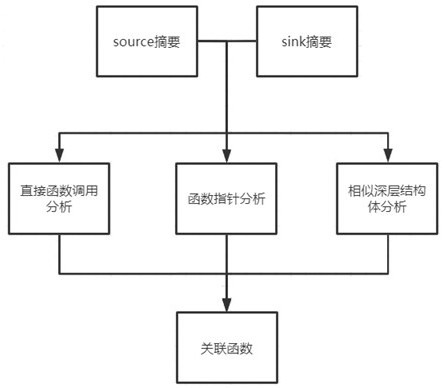
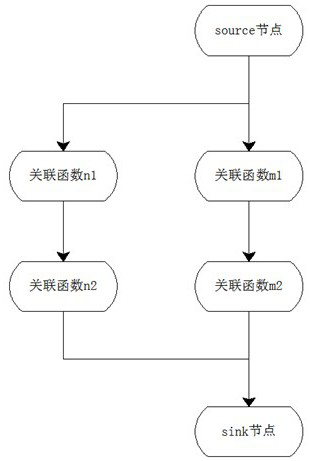
ActiveCN113741969BReduce false negative rateSmall area of influenceReverse engineeringPlatform integrity maintainanceCall graphReachability
The present invention discloses a method for analyzing and optimizing a deep structure pointer of a source library pattern defect detector, comprising the following steps: first collecting related functions related to Source-Sink, and then analyzing the collected related functions on a function call graph to obtain the function call graph Subgraph, then analyze the adjacent two points in the subgraph to obtain the segmented source-sink reachability judgment result, and finally carry out the cross / merge operation summary to the segmented results to obtain the source-sink overall judgment condition; the present invention comprehensively utilizes multiple A static code analysis technology that uses a heuristic algorithm to automatically split the source-sink pattern problem with high complexity into several simple sub-problems, and then judges each sub-problem individually. For undecidable problems, it can narrow the scope of influence, Correlation functions with relatively close correlation levels are given to facilitate manual verification and can effectively reduce the false negative rate of code analysis results.
Owner:北京鸿渐科技有限公司
A Software Vulnerability Detection Method Based on Pointer Analysis
InactiveCN104021073BDiscover and troubleshoot vulnerabilitiesHigh precisionSoftware testing/debuggingComplex data typeData type
A software vulnerability detection method based on pointer analysis includes the following steps that with the help of instrumentation software, three main instrumentation operations of basic data type recovery, complex data type recovery and vulnerability detection are respectively finished, wherein the instrumentation operation of basic data type recovery includes the processes that type collection codes are inserted behind instructions belonging to a type sensitive instruction set, and then propagation codes of different types are inserted according to different assembly instructions; the instrumentation operation of complex data type recovery includes the processes that pointer collection codes are inserted behind a memory application instruction set, pointer analysis codes are inserted according to different assembly instructions, and then complex data types are recovered in the pointer analysis process; the instrumentation operation of vulnerability detection includes the processes that pollution marking codes are inserted to external input positions of programs, stain spreading codes are inserted according to assembly instructions, and security detection codes are inserted to security sensitive points.
Owner:NANJING UNIV
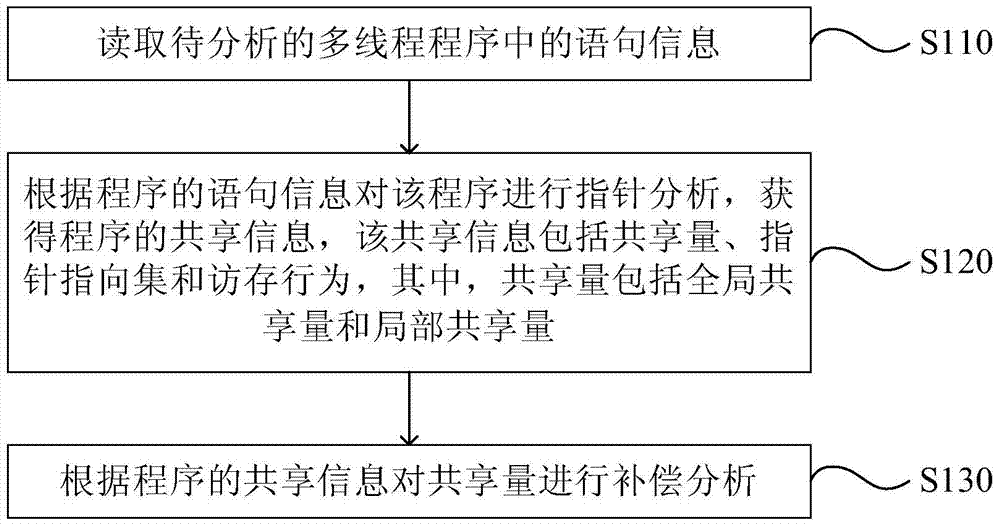
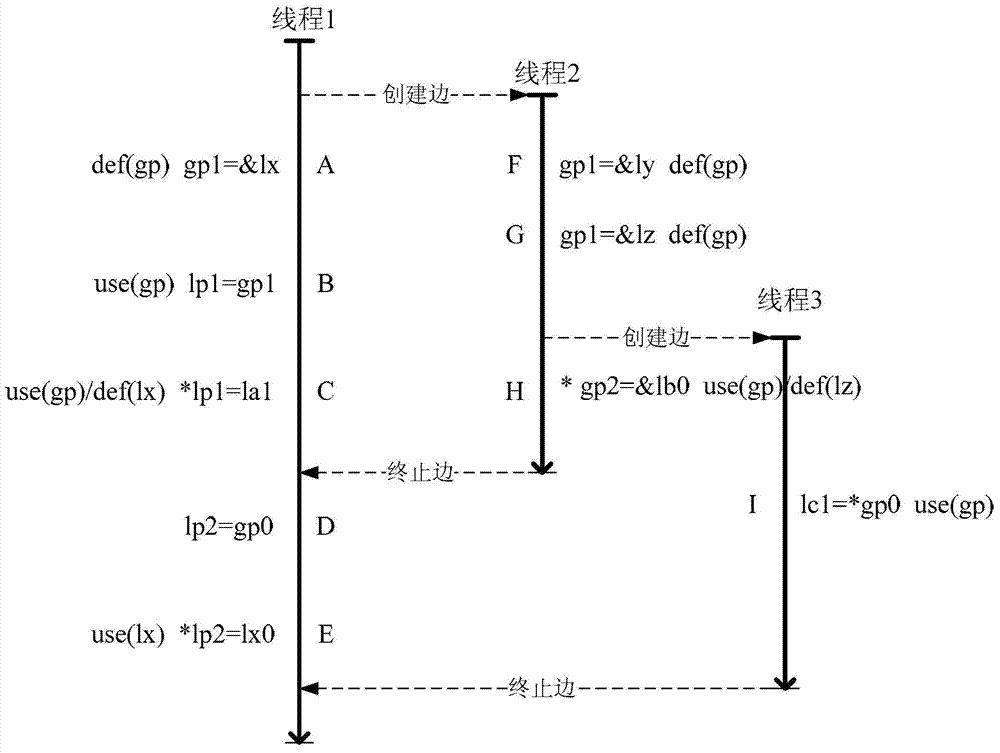
Pointer analysis method and device
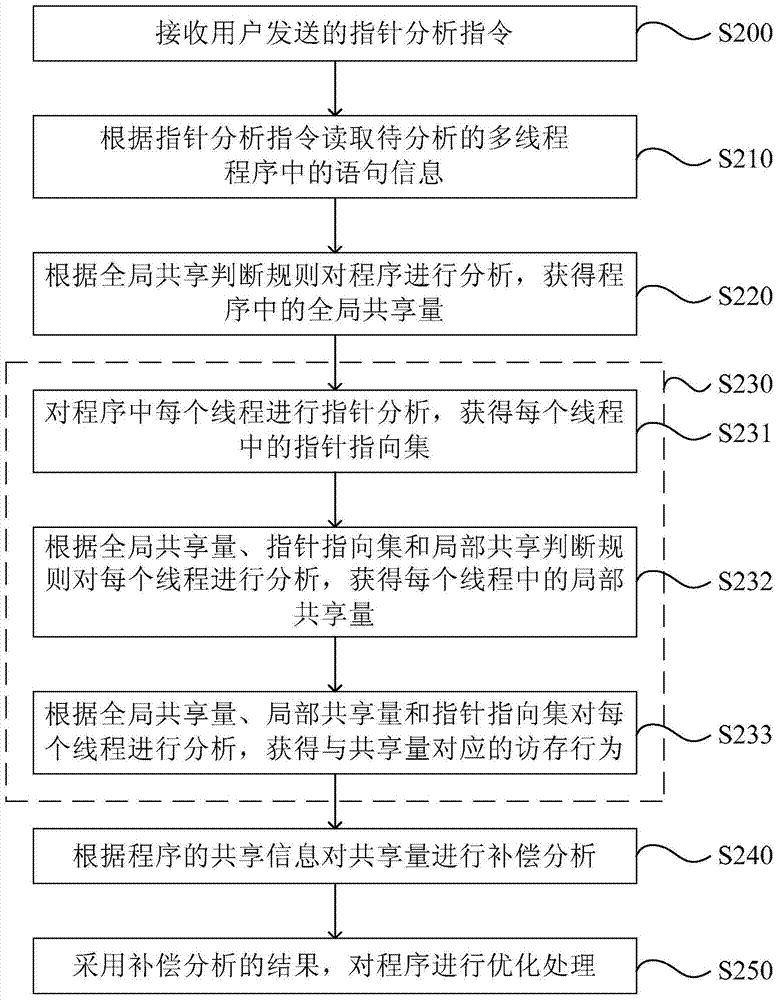
InactiveCN104657257BHigh precisionGood effectSoftware testing/debuggingProgramming languageInformation sharing
Embodiments of the present invention provide a pointer analysis method and device. The pointer analysis method provided by the present invention includes: reading statement information in the multi-threaded program to be analyzed; performing pointer analysis on the program according to the statement information of the program to obtain shared information of the program, the shared information It includes shared amount, pointer pointing set and memory access behavior, wherein the shared amount includes global shared amount and local shared amount; compensation analysis is performed on the shared amount according to the shared information of the program. The embodiment of the present invention solves the problem in the prior art that the pointer analysis of multi-threaded programs is limited to the global share in the program, and the analysis results are not comprehensive, improves the accuracy of pointer analysis, and correspondingly improves the implementation scope of program optimization and effects.
Owner:HUAWEI TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com