Software vulnerability detection method based on pointer analysis
A software vulnerability and pointer analysis technology, applied in the field of software vulnerability detection, can solve the problems of insufficient use of pointer variable information and inaccurate recovery of complex data types, etc., to achieve the effect of improving security and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
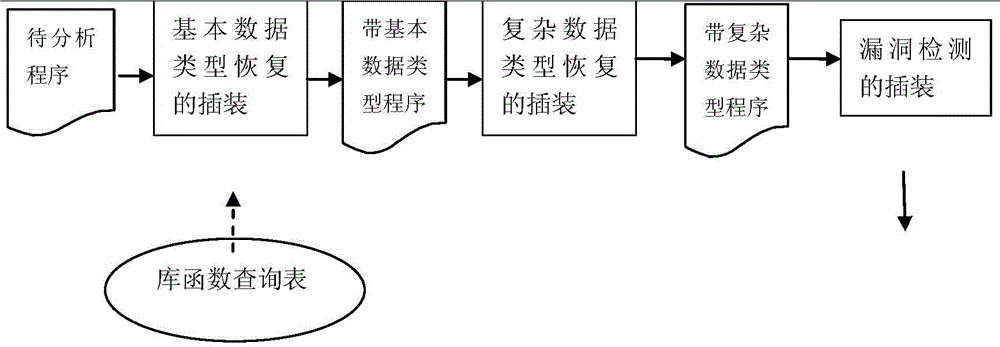
[0017] like figure 1 As shown, Valgrind is an instrumentation software that enables dynamic analysis of executable programs. Instrumentation of executable programs is accomplished with this platform. The instrumented program is executed, the instrumented code is executed, and data type recovery and software vulnerability detection are implemented. Start the Valgrind program, specify the instrumentation operation to be used, the program to be instrumented, the library function query file and the output file, etc., and then the corresponding instrumentation operation can be realized.
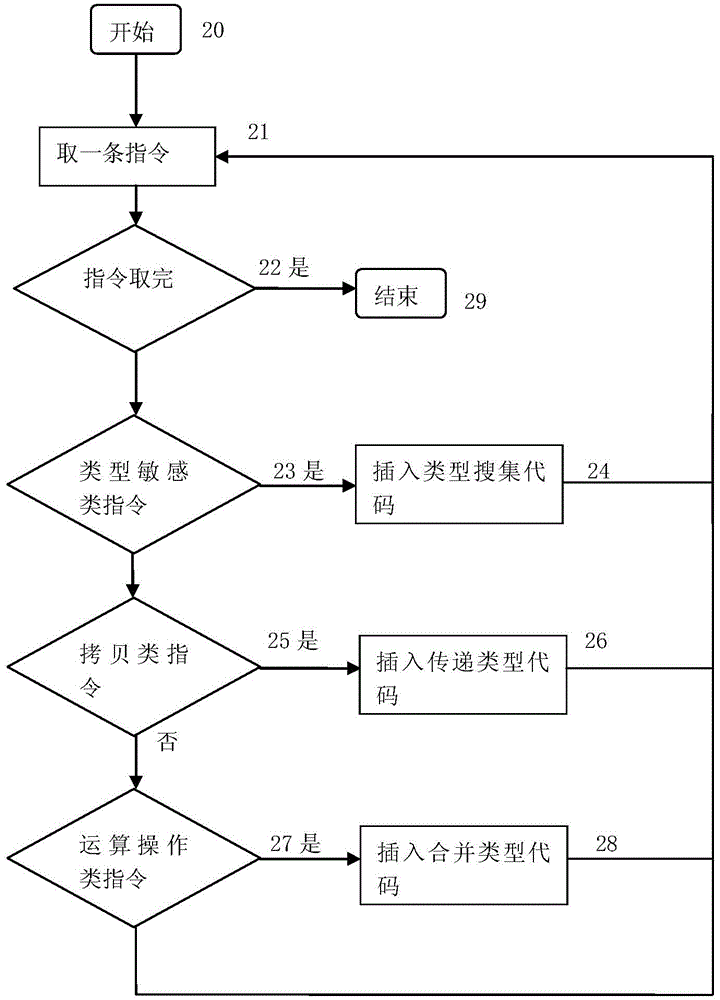
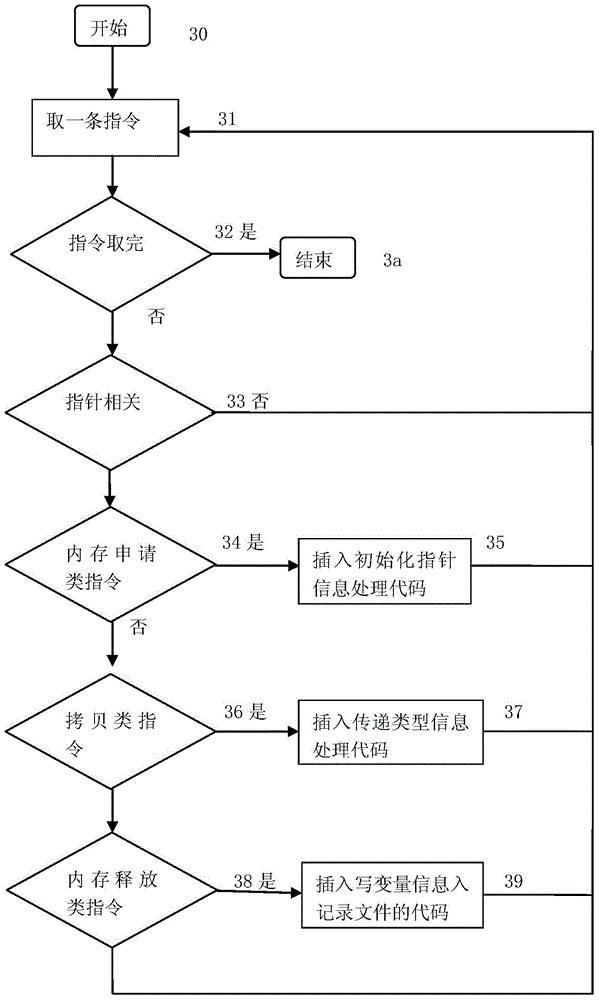
[0018] The three main instrumentation operations are recovery of basic data types, recovery of complex data types, and vulnerability detection. For the instrumentation of basic data type recovery, the input file is the executable program to be instrumented. The instrumentation operation is: insert the type collection code after the instructions belonging to the type-sensitive instruction set, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com