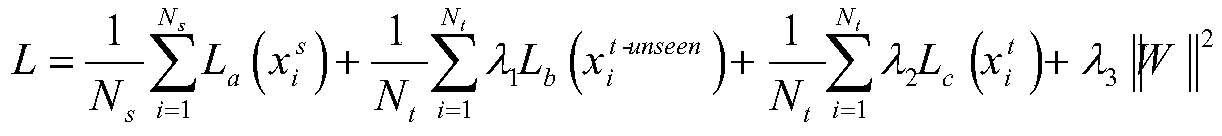Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
91 results about "Semantic translation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Semantic translation is the process of using semantic information to aid in the translation of data in one representation or data model to another representation or data model. Semantic translation takes advantage of semantics that associate meaning with individual data elements in one dictionary to create an equivalent meaning in a second system.
Compiler method for extracting and accelerator template program
InactiveUS20070169059A1Software engineeringSpecific program execution arrangementsSemantic translationSemantics
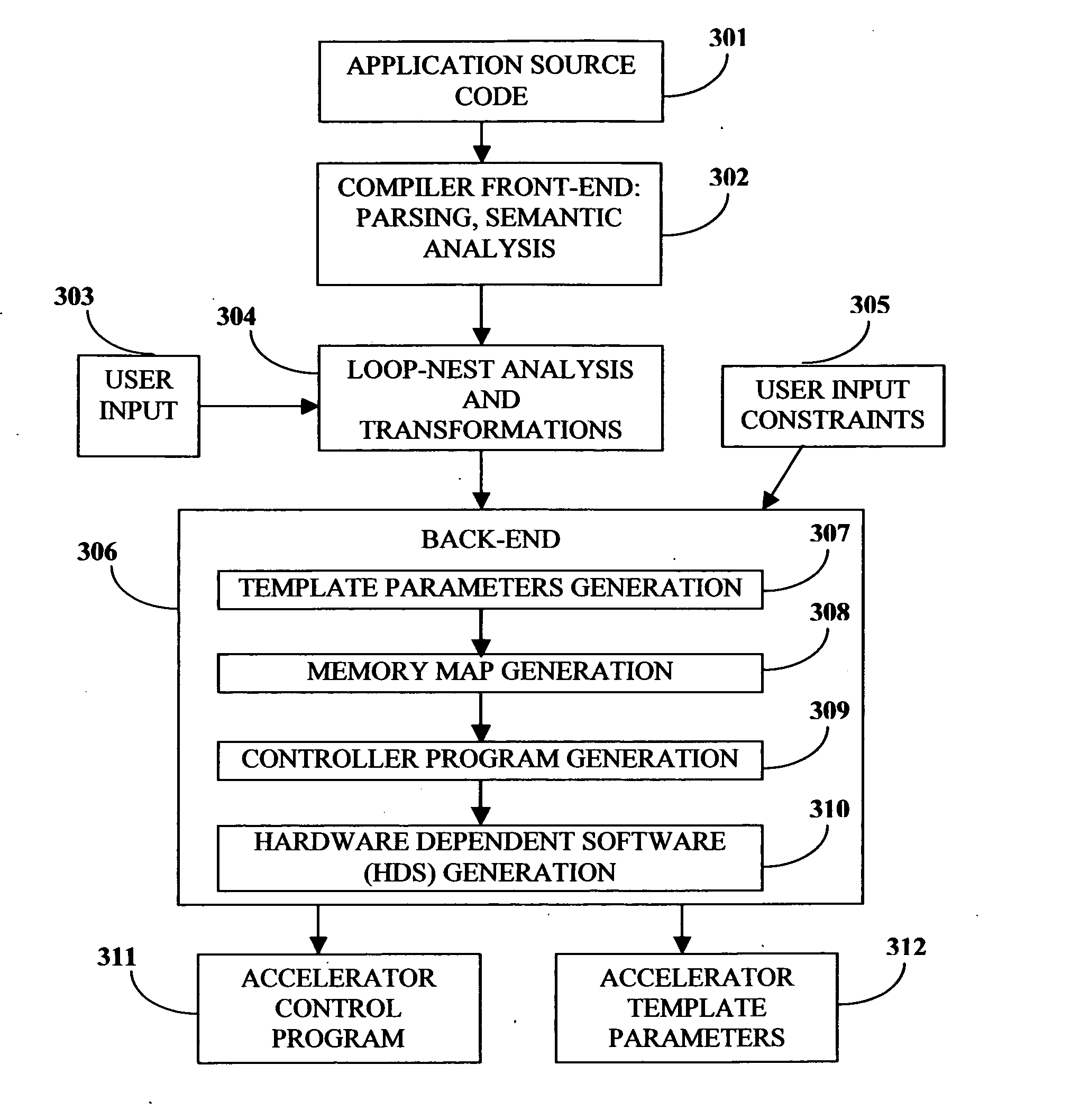
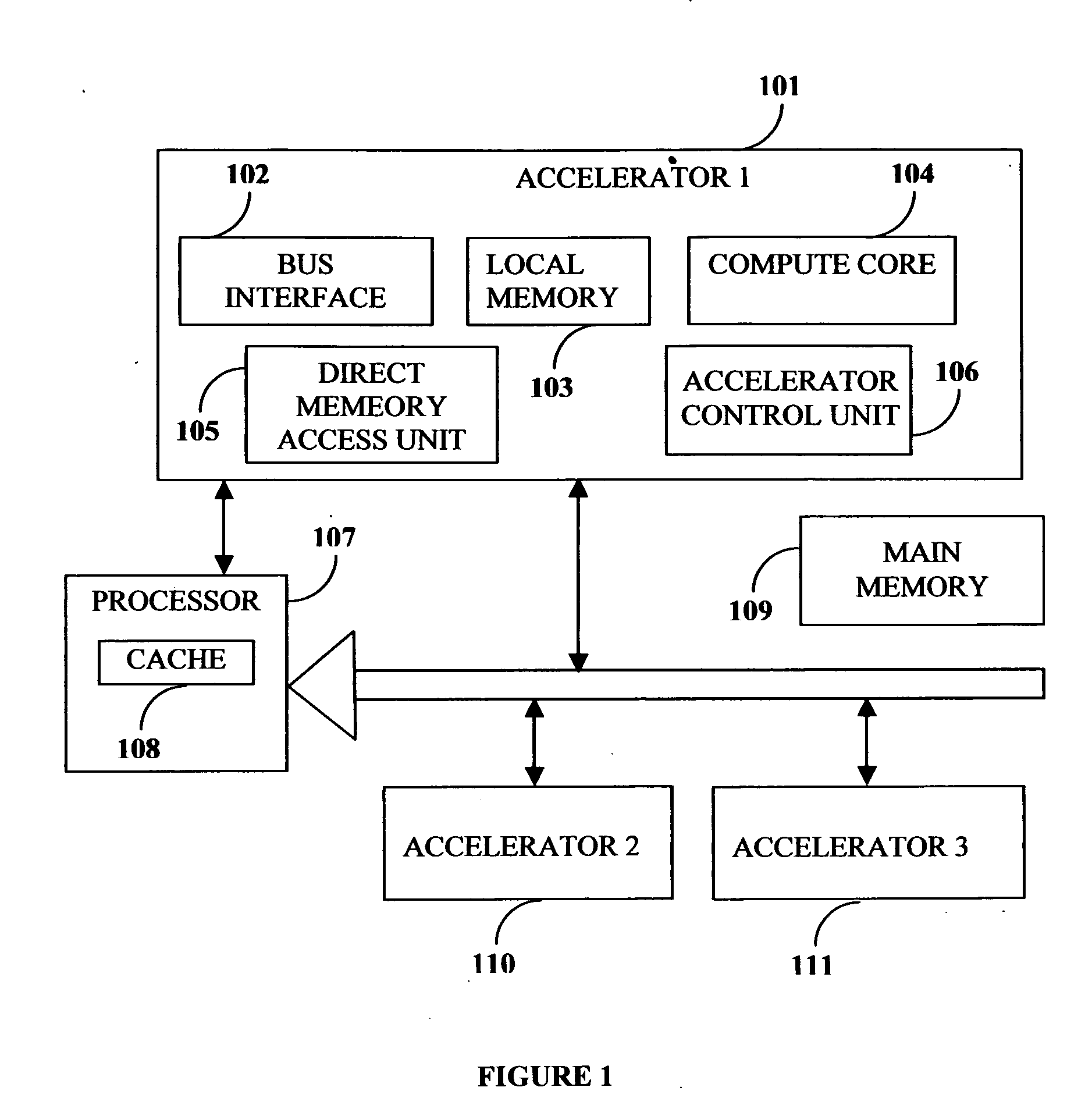
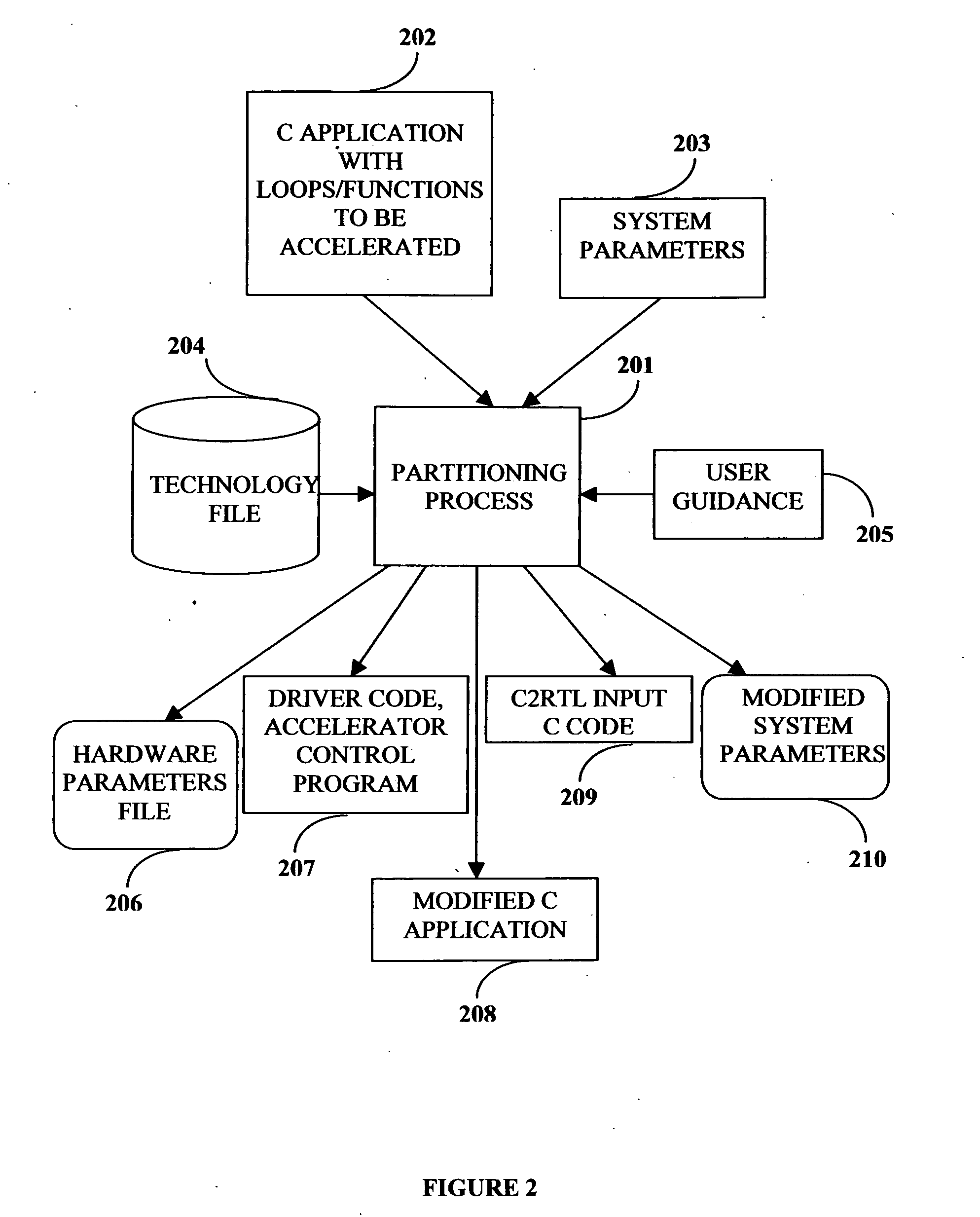
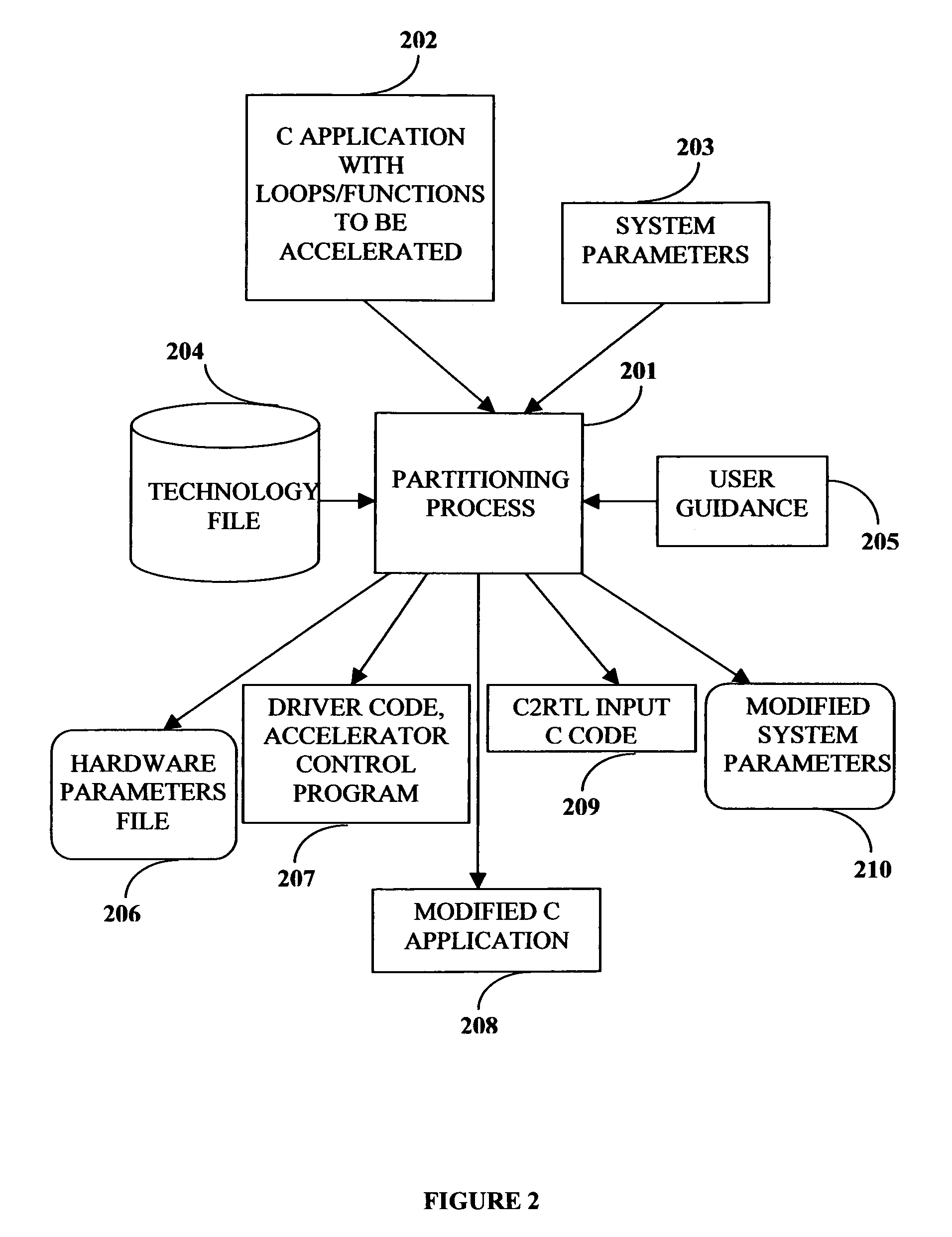
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
Compiler method for extracting and accelerator template program
InactiveUS7926046B2Software engineeringSpecific program execution arrangementsArray data structureSemantic translation
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
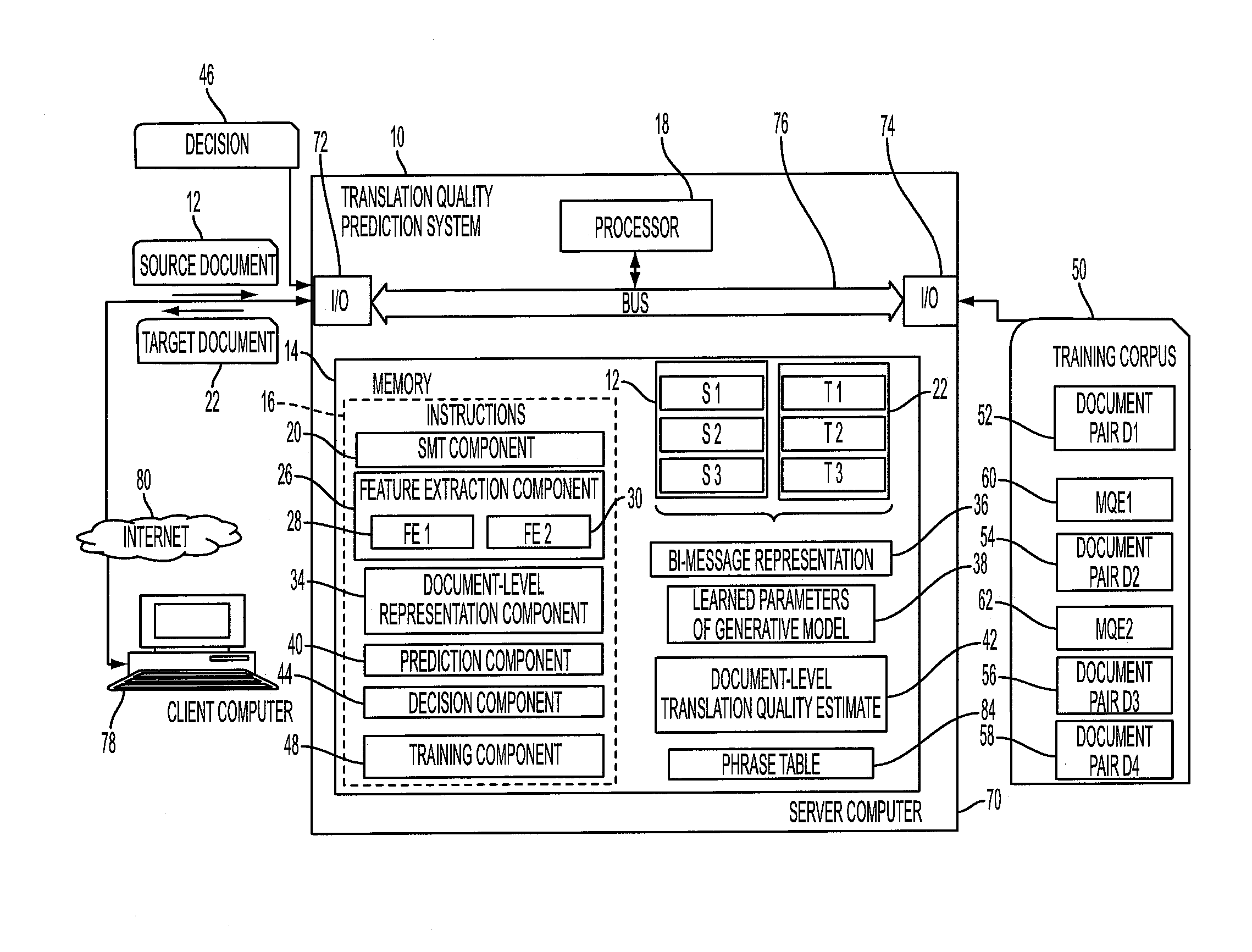
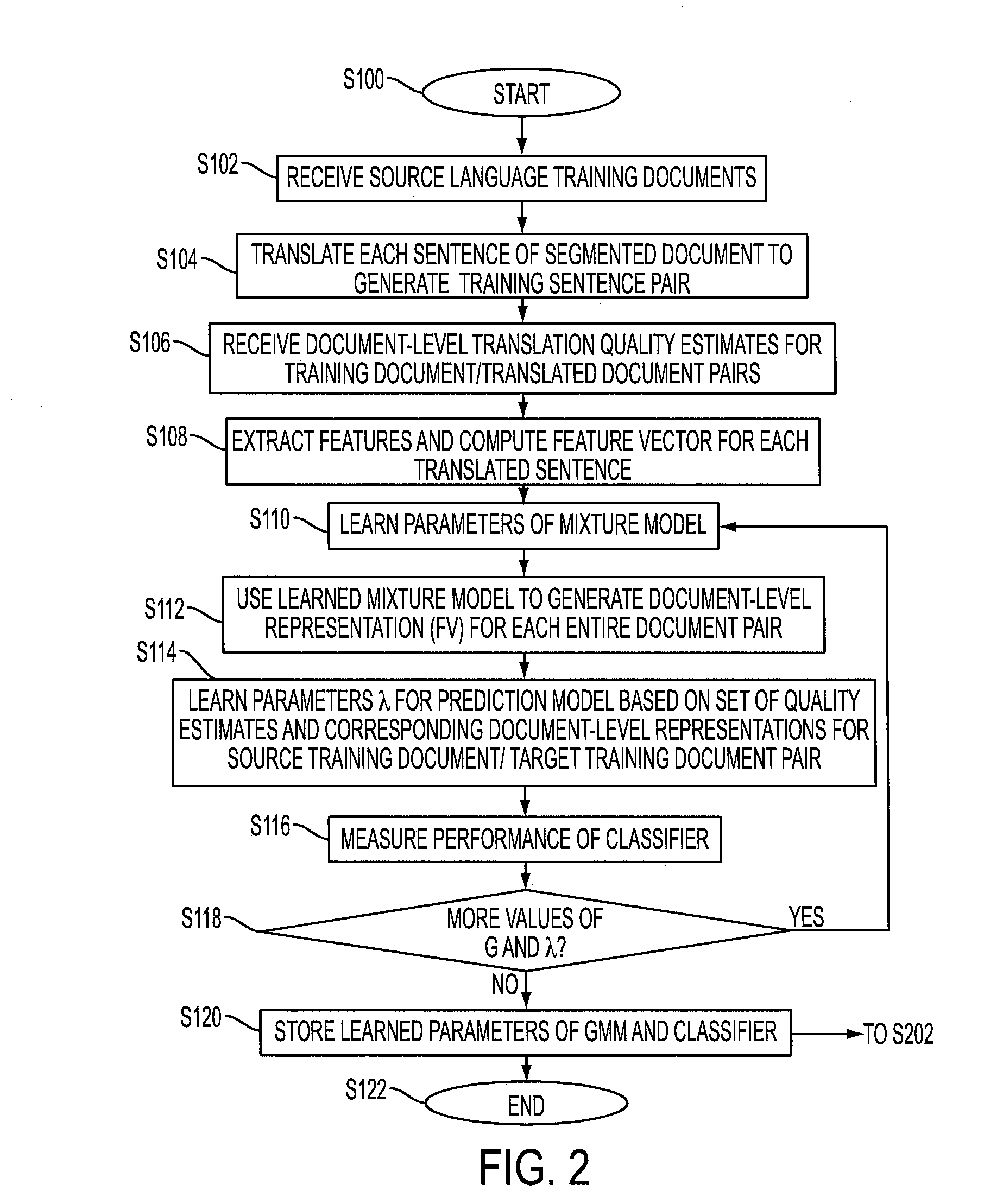
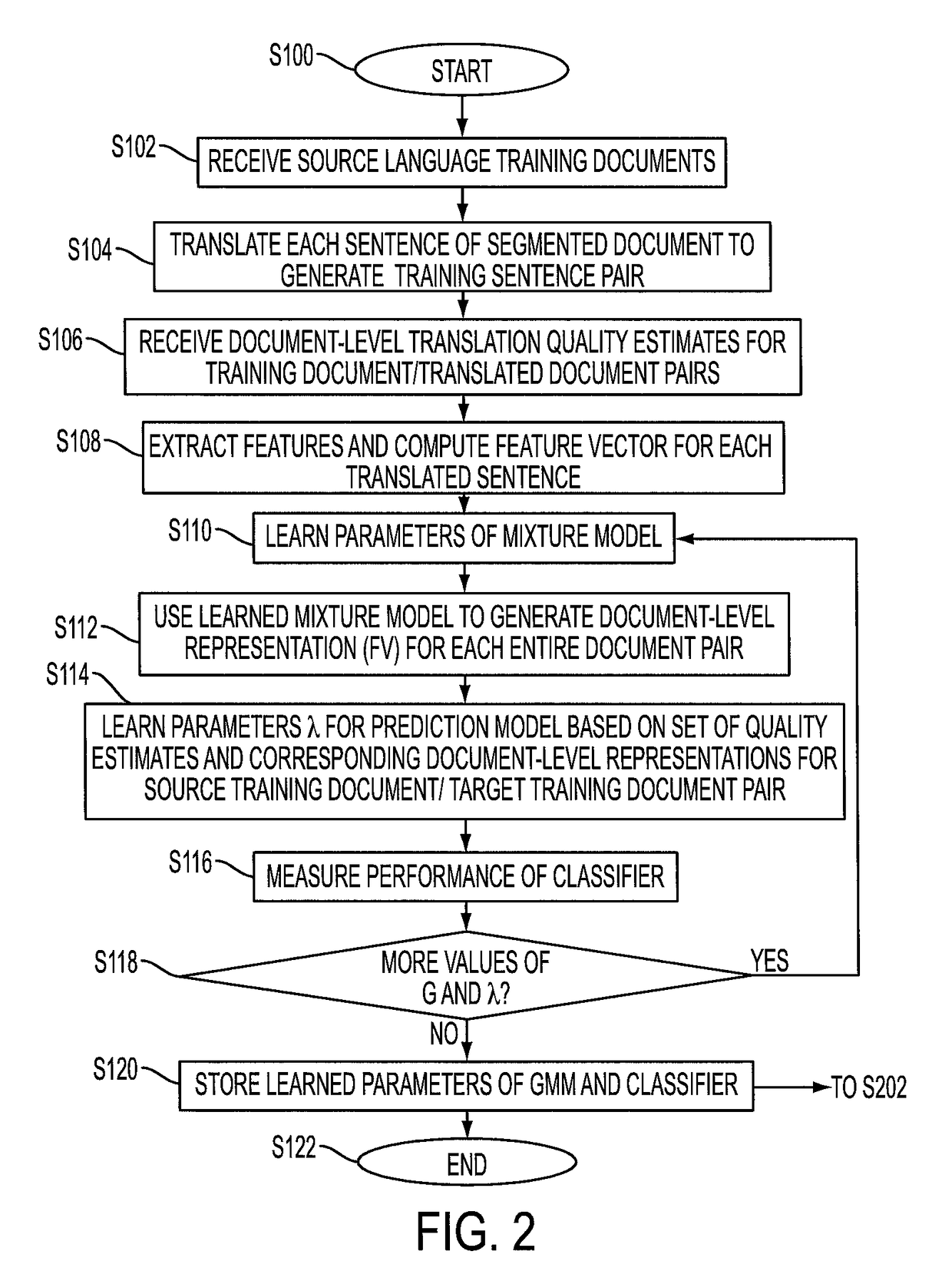
Predicting the quality of automatic translation of an entire document
InactiveUS20160124944A1Natural language translationSpecial data processing applicationsSentence pairSemantic translation
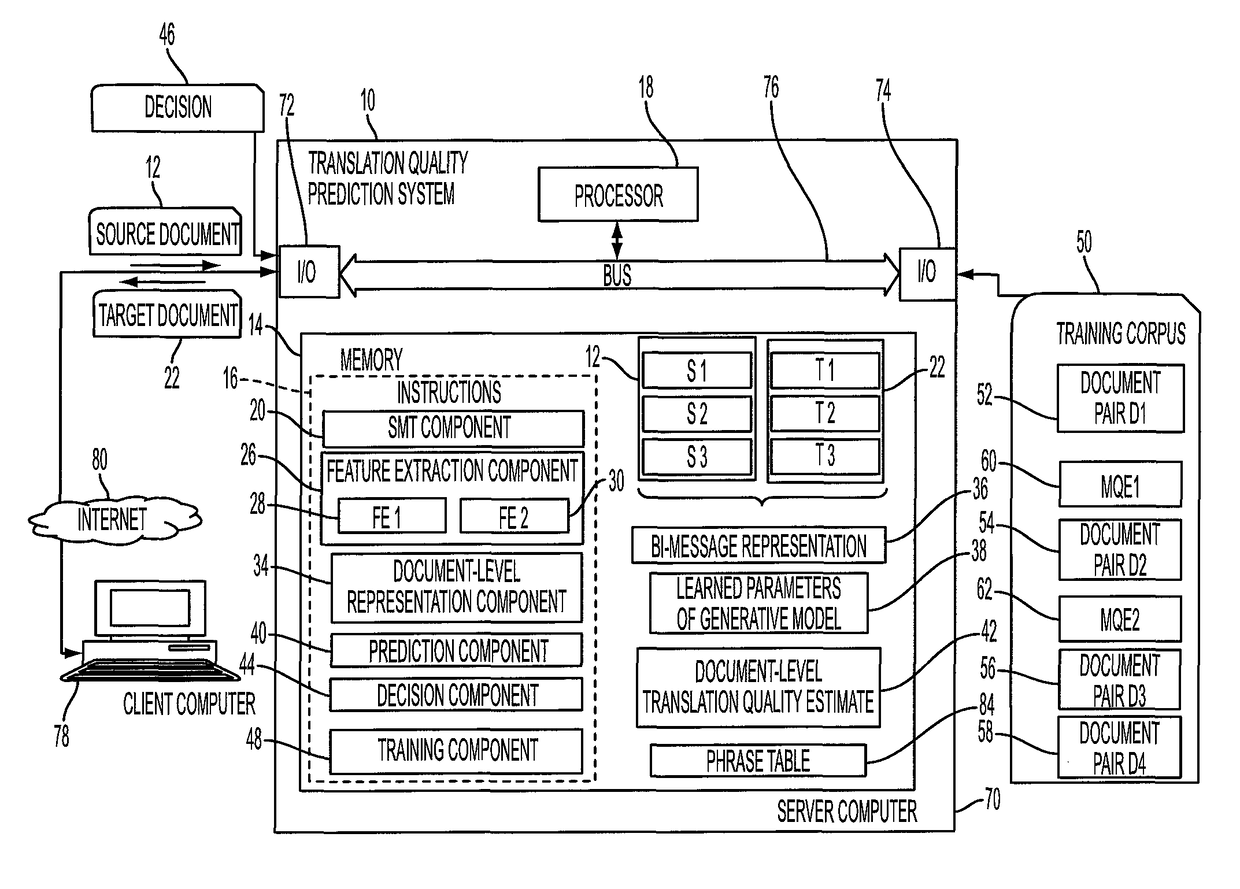
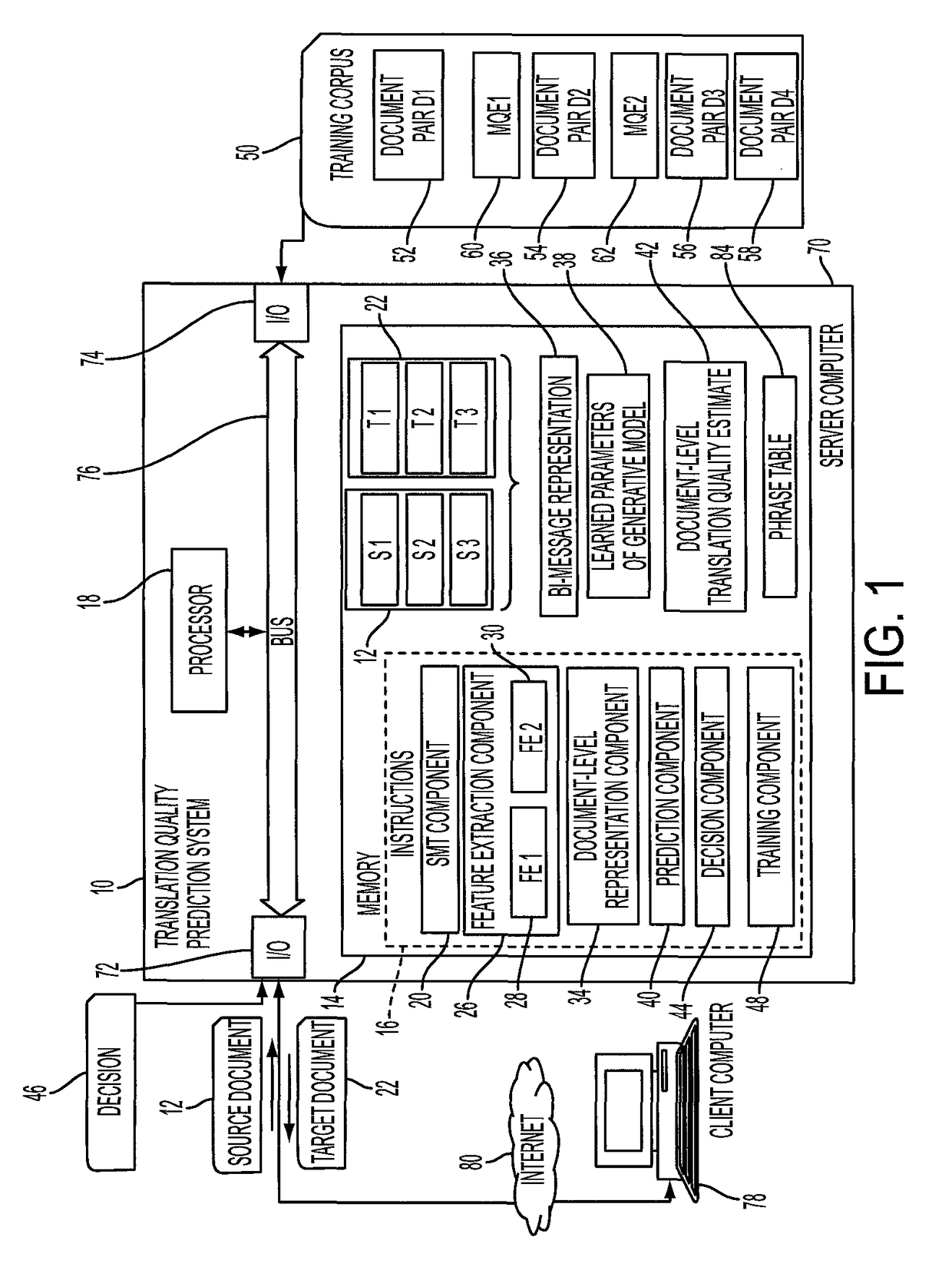
A system and method predict the translation quality of a translated input document. The method includes receiving an input document pair composed of a plurality of sentence pairs, each sentence pair including a source sentence in a source language and a machine translation of the source language sentence to a target language sentence. For each of the sentence pairs, a representation of the sentence pair is generated, based on a set of features extracted for the sentence pair. Using a generative model, a representation of the input document pair is generated, based on the sentence pair representations. A translation quality of the translated input document is computed, based on the representation of the input document pair.
Owner:XEROX CORP
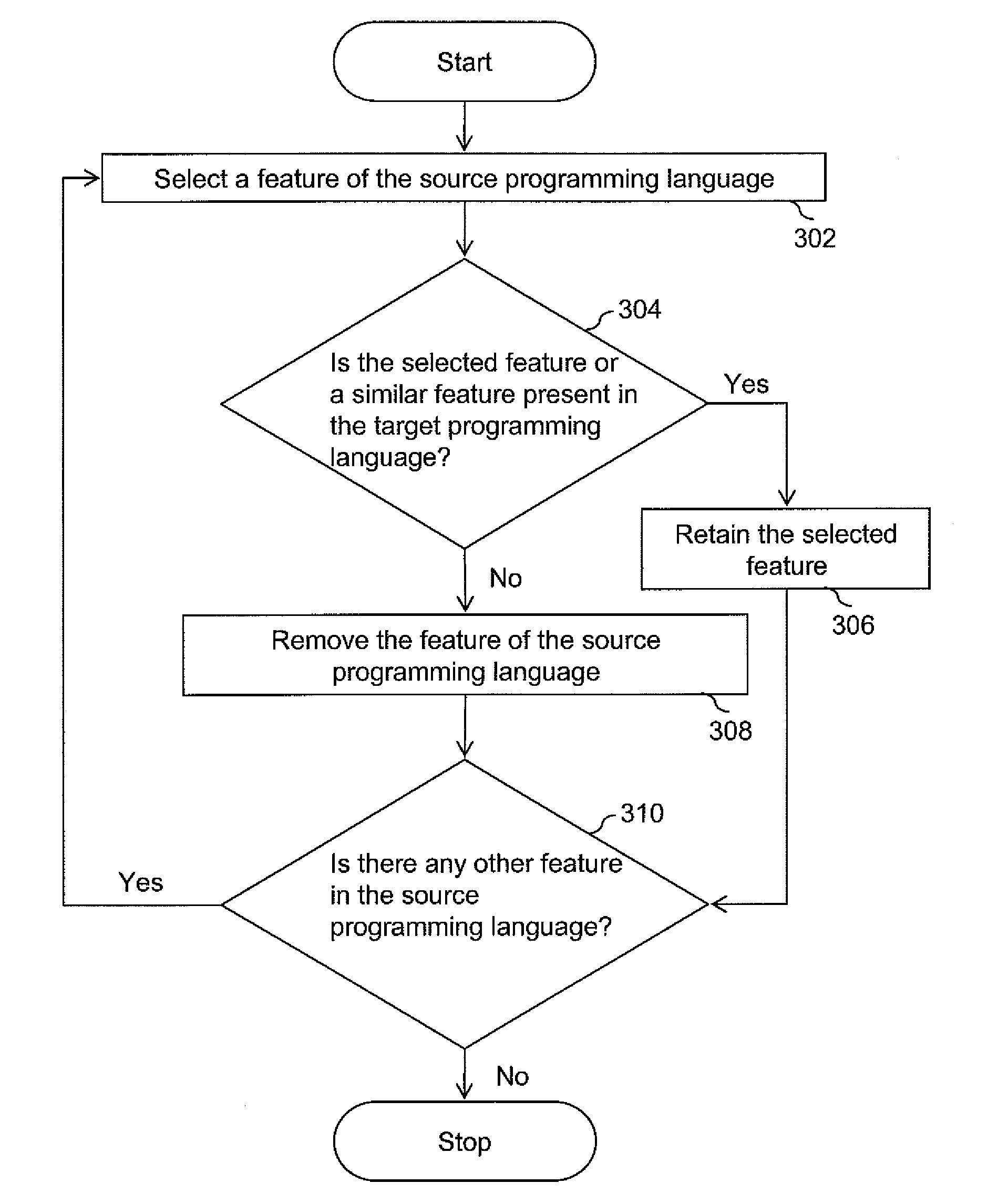
Methods and apparatus for automatic translation of a computer program language code
Embodiments of the methods and apparatus for automatic cross language program code translation are provided. One or more characters of a source programming language code are tokenized to generate a list of tokens. Thereafter, the list of tokens is parsed to generate a grammatical data structure comprising one or more data nodes. The grammatical data structure may be an abstract syntax tree. The one or more data nodes of the grammatical data structure are processed to generate a document object model comprising one or more portable data nodes. Subsequently, the one or more portable data nodes in the document object model are analyzed to generate one or more characters of a target programming language code.
Owner:XENOGENIC DEV LLC
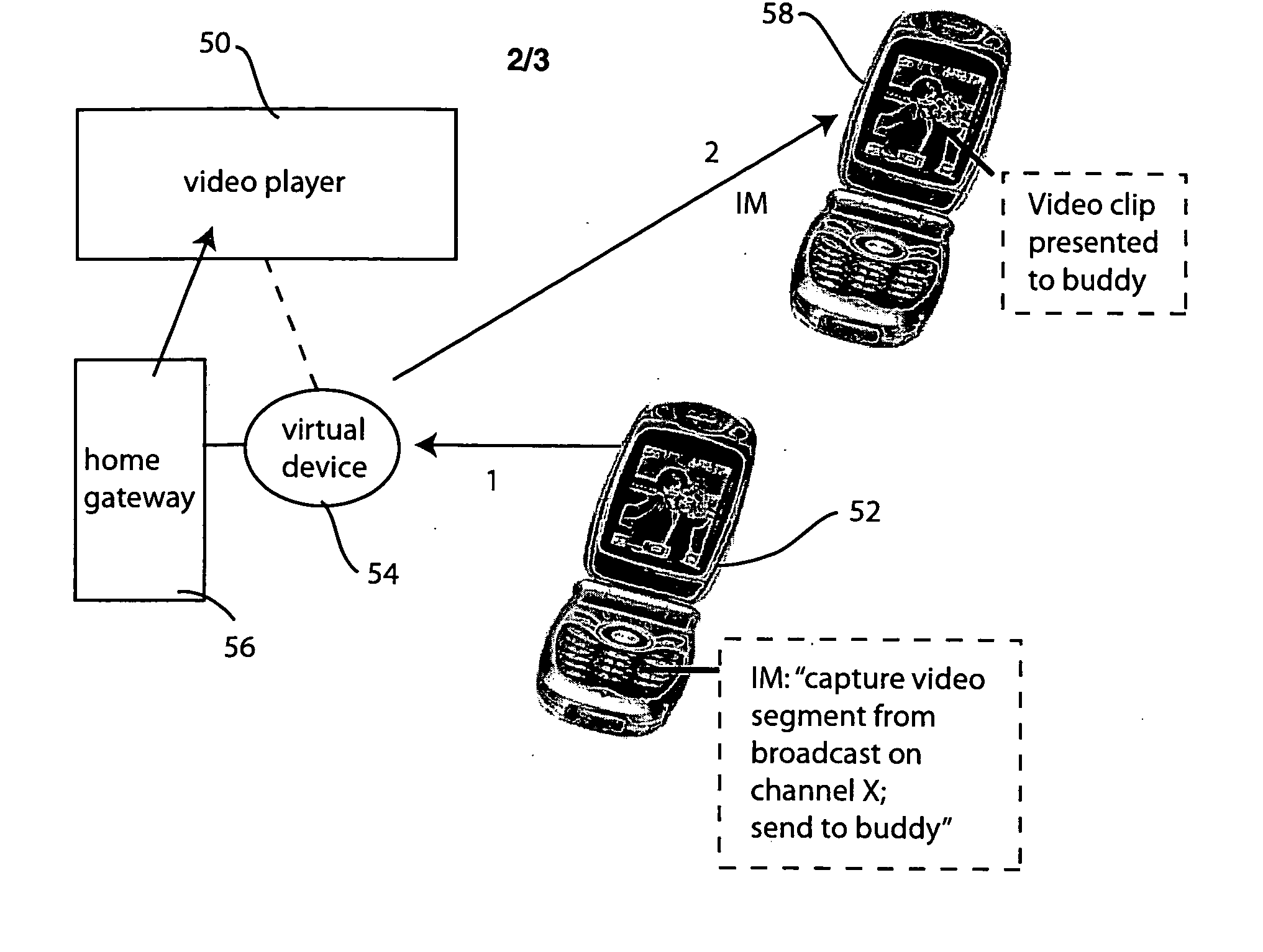
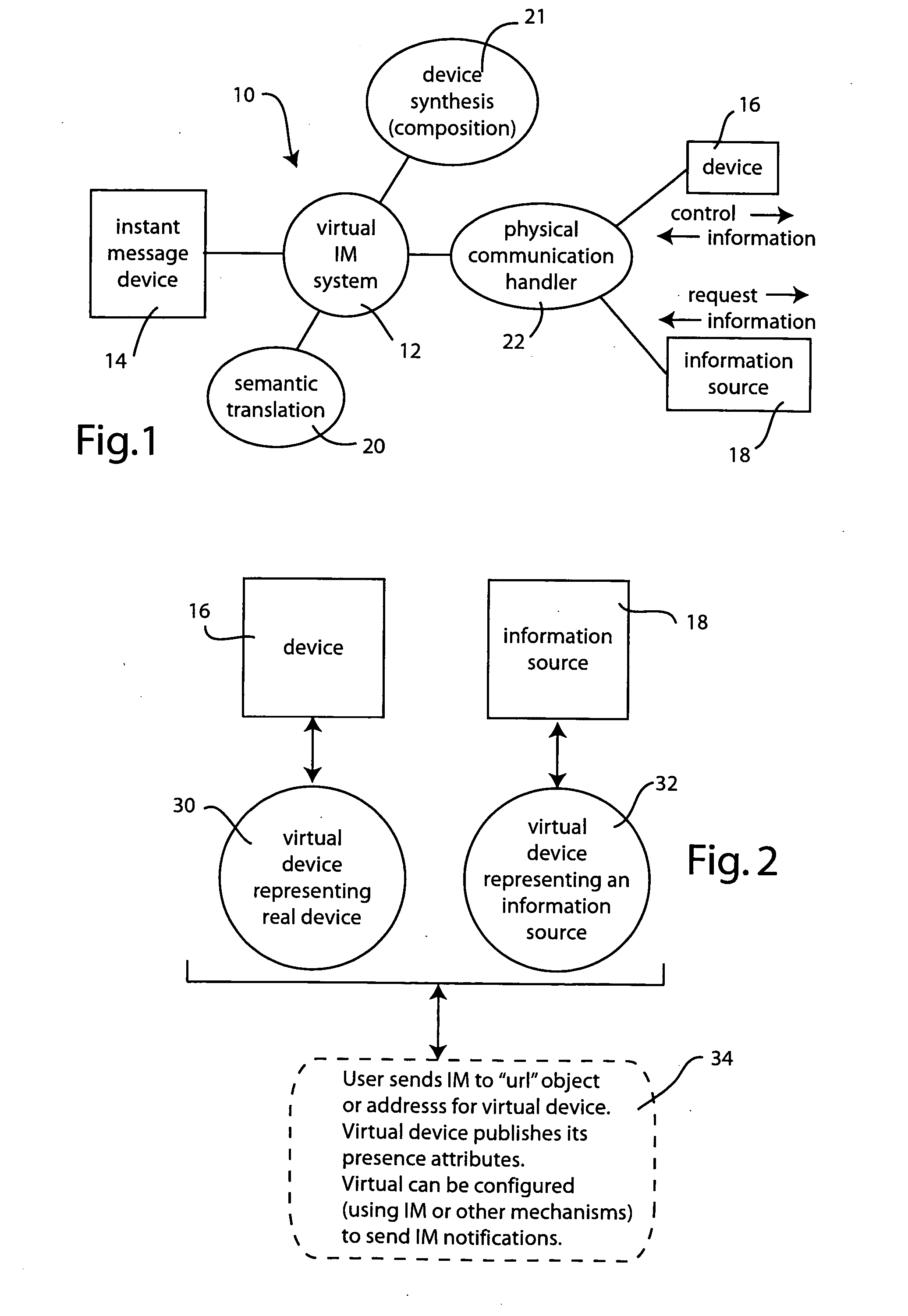
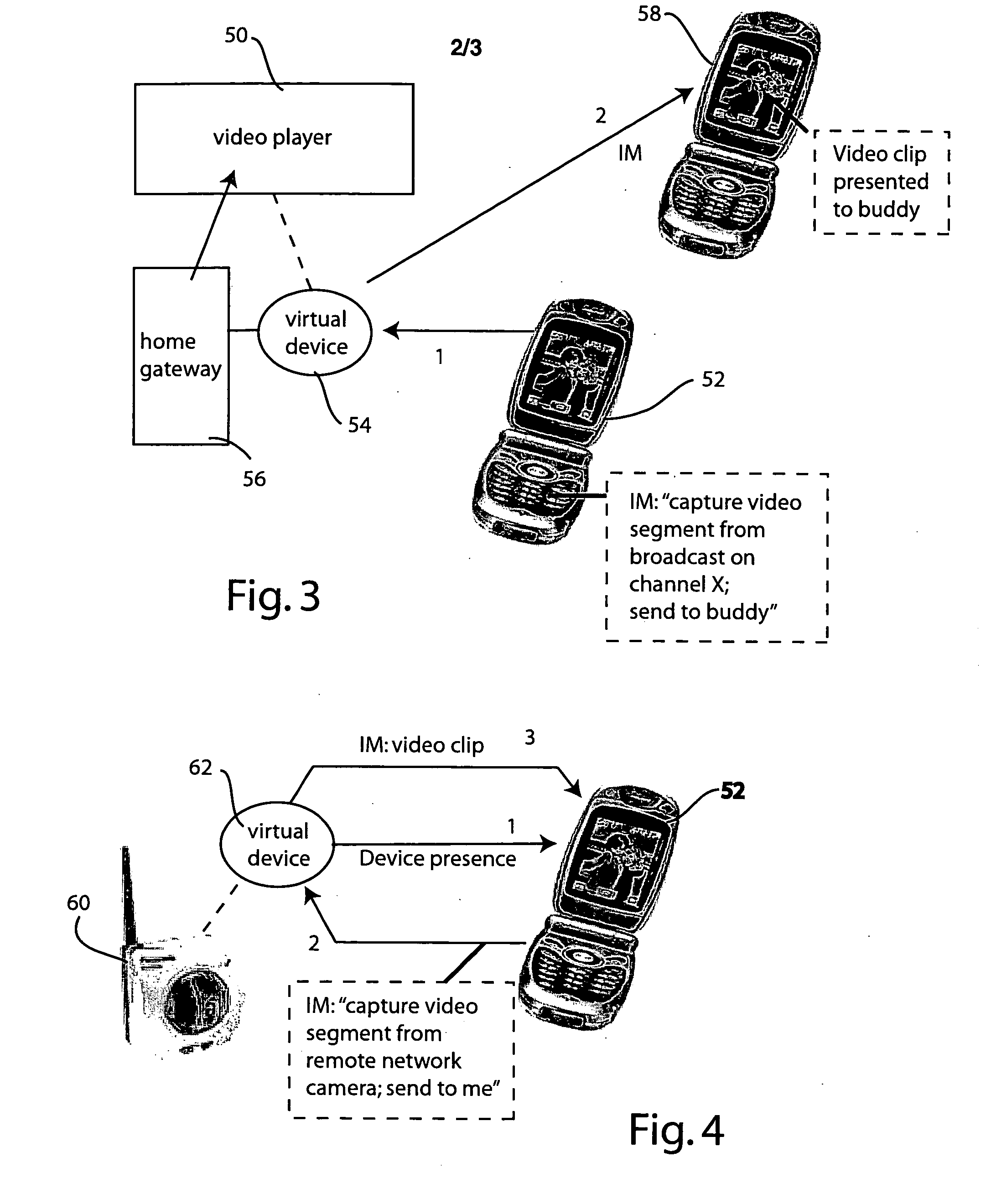
Instant messaging and presence using virtual devices
InactiveUS20060031367A1Low costMultiple digital computer combinationsData switching networksSemantic translationVirtual device
The virtual instant messaging system adds instant messaging and presence capability to devices and appliances which are not natively designed for instant messaging. The virtual instant messaging system performs the physical communication handling and semantic translation issues to allow legacy devices to operate within the instant messaging paradigm. Virtual devices, representing real devices or information sources, may be constructed, on the fly as needed, or on a more permanent or persistent basis. Multiple virtual devices may be combined to compose or synthesize a new virtual device, affording capabilities not found in the real world devices or information sources themselves.
Owner:PANASONIC CORP
Natural expression information processing method, natural expression information processing and responding method, equipment and system
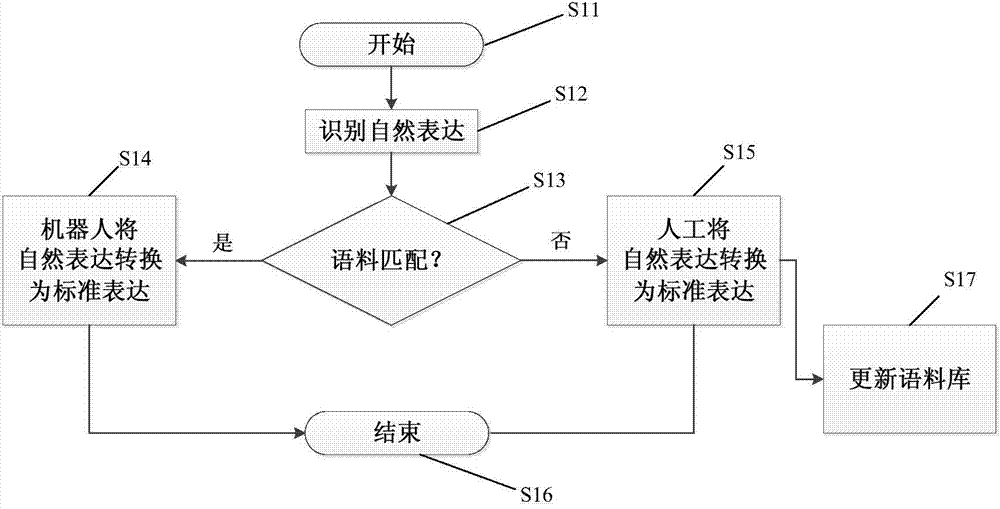
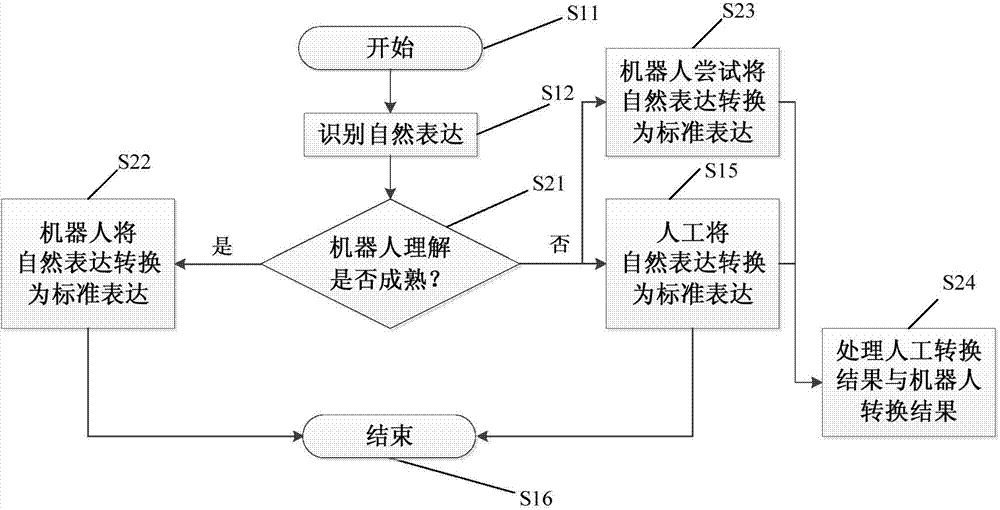
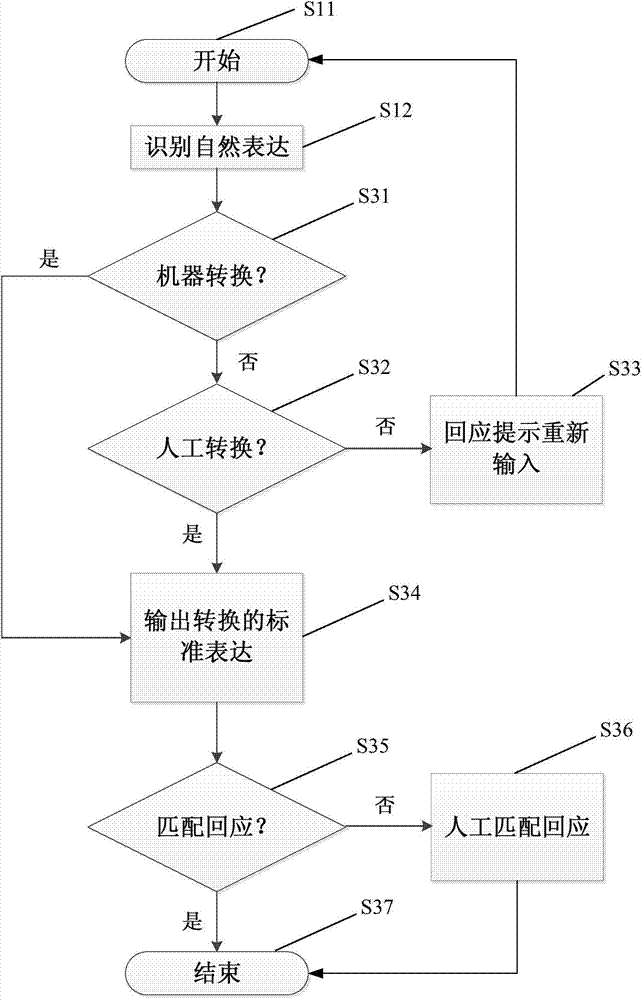
InactiveCN103593340AReduced precision requirementsReduce complexityNatural language translationMathematical modelsInformation processingSemantic translation
The invention provides a natural expression information processing method. The natural expression information processing method includes identifying natural expression information from users to acquire natural expression in the form of characters, and transforming the identified natural expression into standard expression in the form of codes. According to the natural expression information processing method, ruleless natural expression information can be transformed into encoded standard expression; transformation of the standard expression refers to transformation from semanteme of the natural expression to the codes, and no accurate language translation is needed, so that accuracy requirements of machine translation can be reduced, complexity of databases used for expression transformation (machine translation) is lowered, data inquiry and update speeds are increased, and performance of intelligent processing is improved; in addition, by simple encoded expression, workload for human-assisted intervention can be reduced.
Owner:ICONTEK CORP
Symbolized model detection method
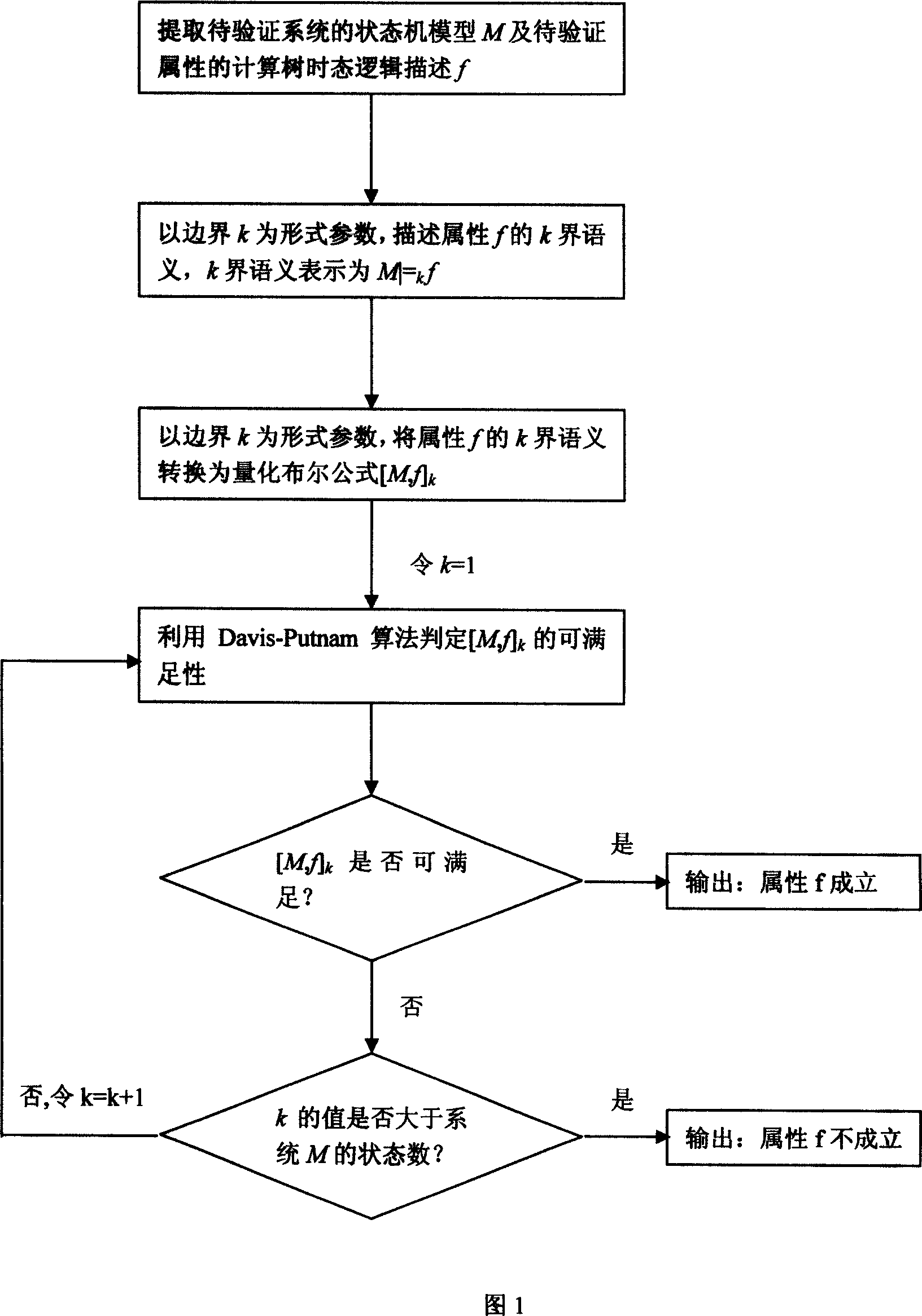
InactiveCN101013452AOvercoming the state space explosion problemImprove reliabilitySpecial data processing applicationsTemporal logicModel testing
This symbol model detection method is a method to make the model testing practical; the main principle is to use Boolean formula quantitative determination to instead of the CTL model testing. Their method: 1.) extract state machine M of the tested system and the attributes of the tested tree temporal logic description; 2.) taking border k as the form parameters, describe k sector semantics of the attributes f; 3.) taking border k as the form parameters, convert the k sector semantic of attribute f to quantify Boolean formula [M, f] k: 4.) progressive determine whether the system M meets the reliable attribute f: the approach integrates the advantages of symbol model testing based on binary decision diagram and bounded model checking based proposition equitation meeting judgment, also overcomes their shortcomings, which are not dependent on the sort of Boolean variables, or dependent on the property to verify the full name attribute.
Owner:JIANGSU UNIV
Graphical method of semantic oriented model analysis and transformation design
InactiveUS20090024965A1Input/output for user-computer interactionSemantic analysisInstrumental functionGraphics
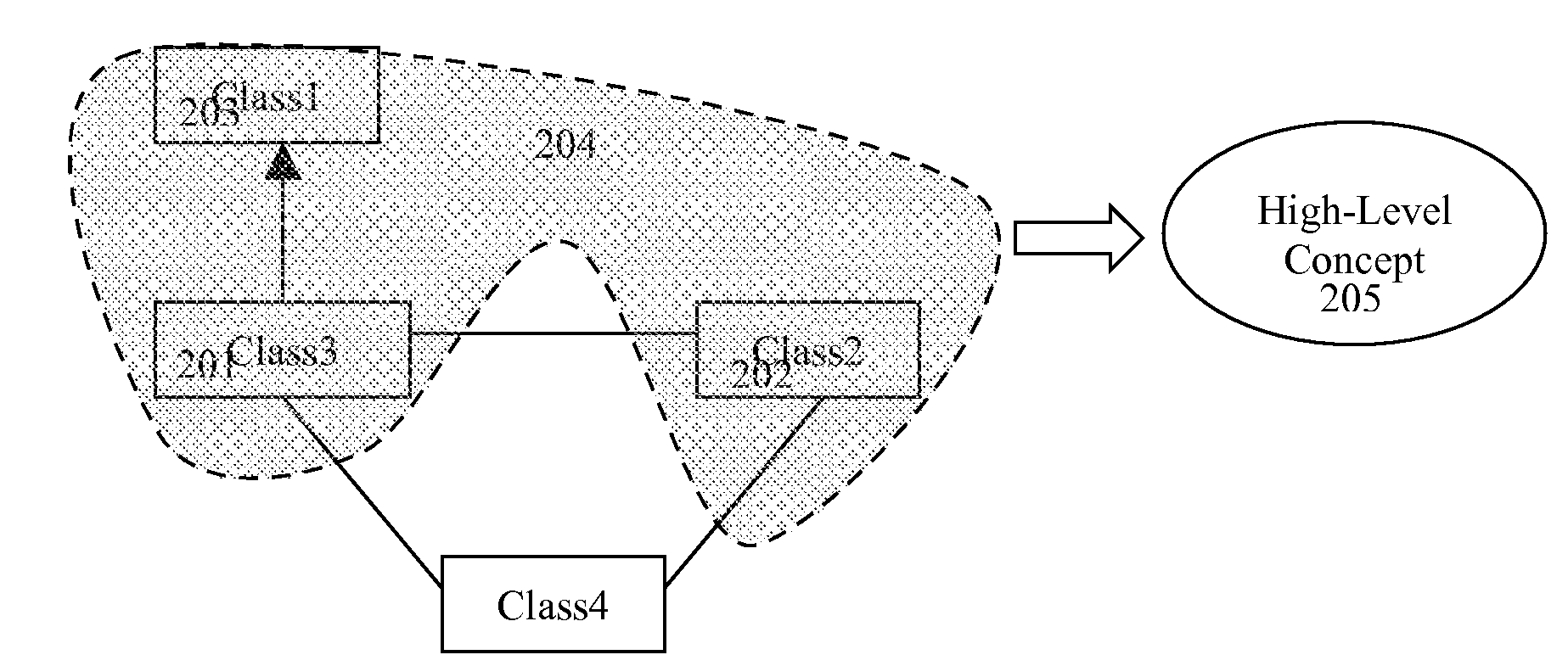
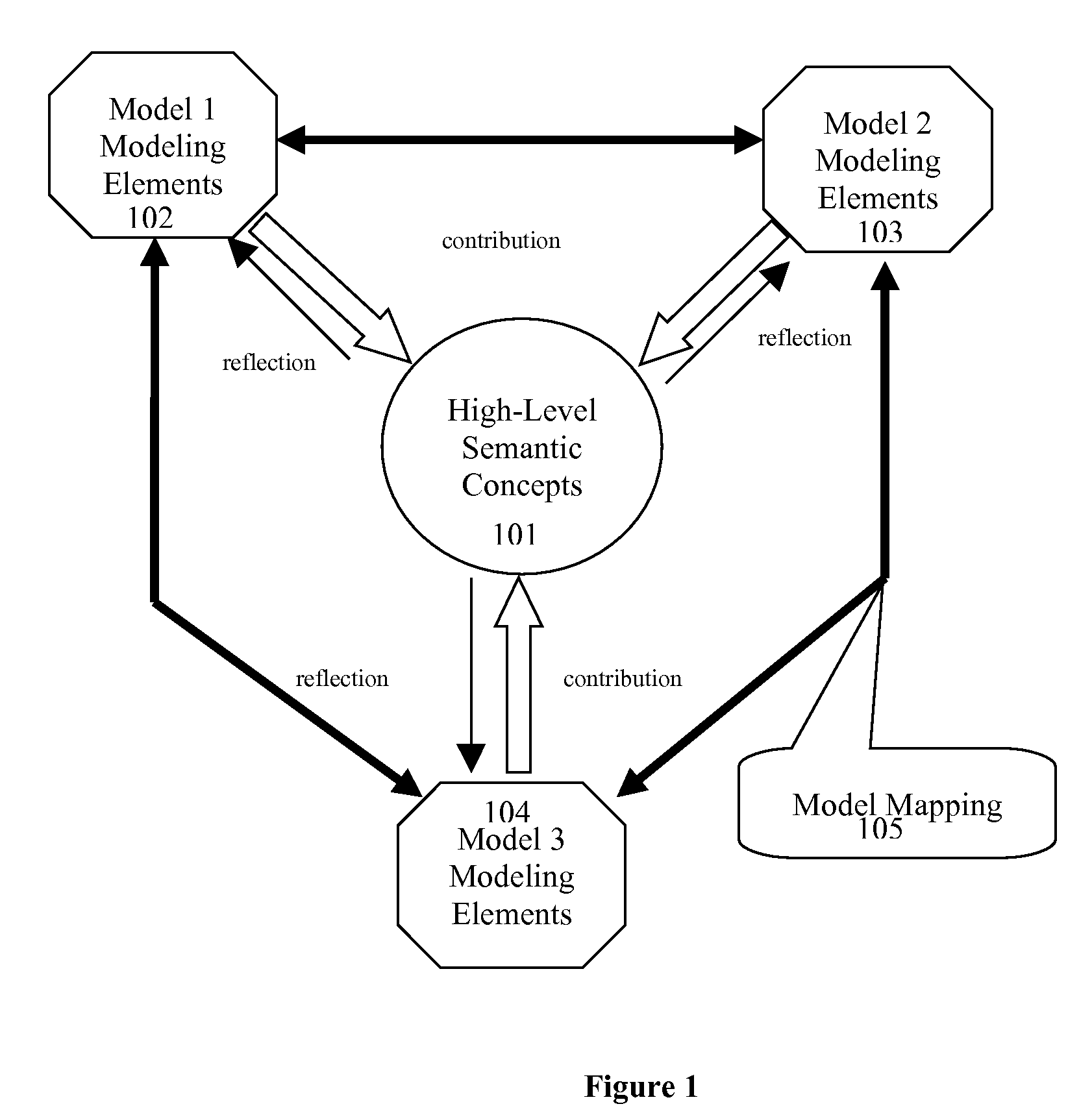
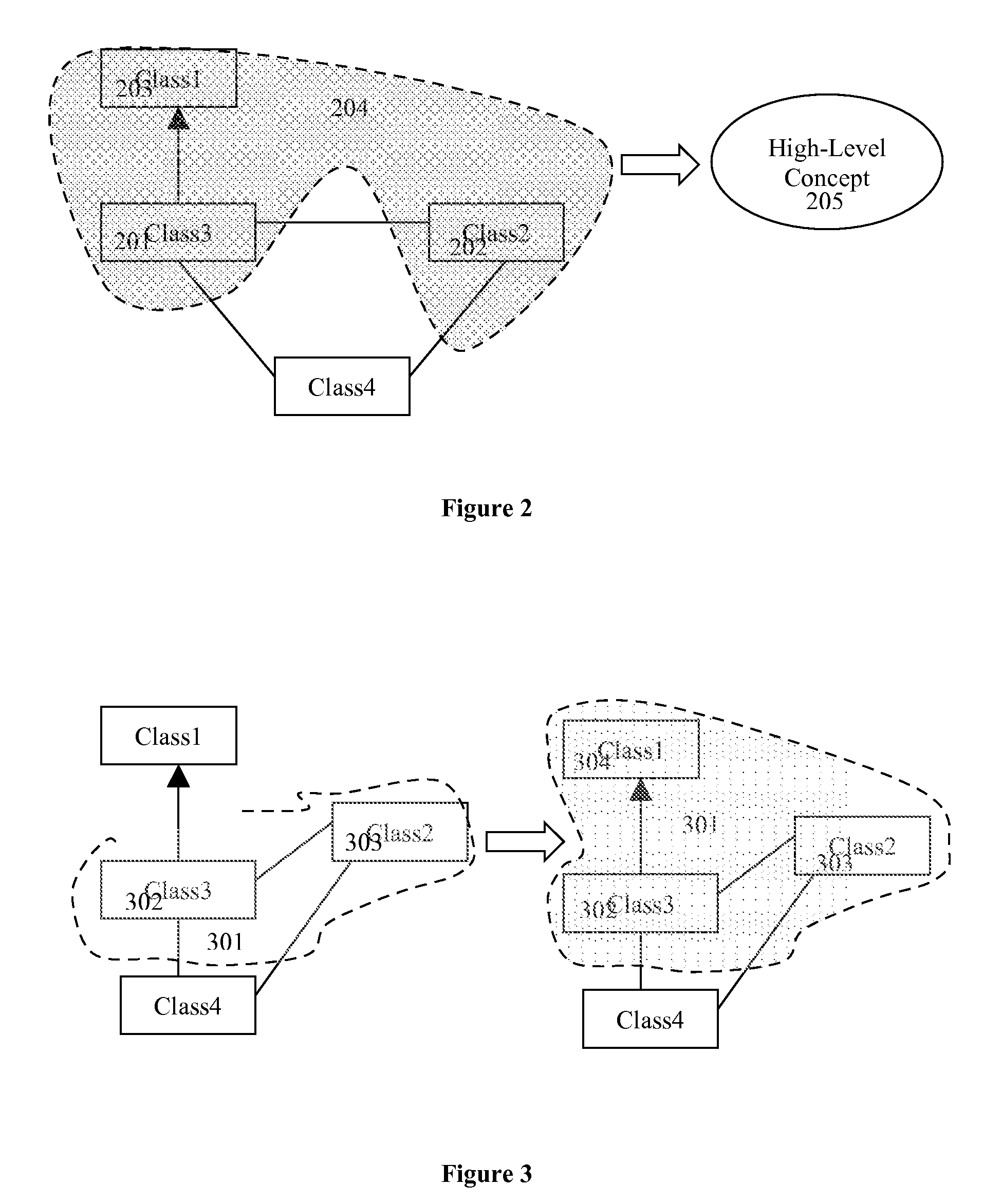
User is given the new modeling capability, a Semantic Lasso, which allows grouping of the model elements, so they can be mapped or transformed to the high-level concepts of business ontology. Such grouping is done by drawing of the line contour around relevant to advertised high-level concept model elements on one of the OMG Unified Modeling Language (UML) class diagrams. In addition the user is given a capability to specify extension points of the high-level concepts and the projection of such extension points to the individual model. Another tooling capability, a Semantic Transformation Lens, allows dynamic graphical projection of the individual model fragments to the high-level concepts as those elements are being selected. Semantic Transformation Lens provides the mechanism of reasoning-based smart selection.
Owner:ZHDANKIN ALEKSANDR +1
Server and database access method
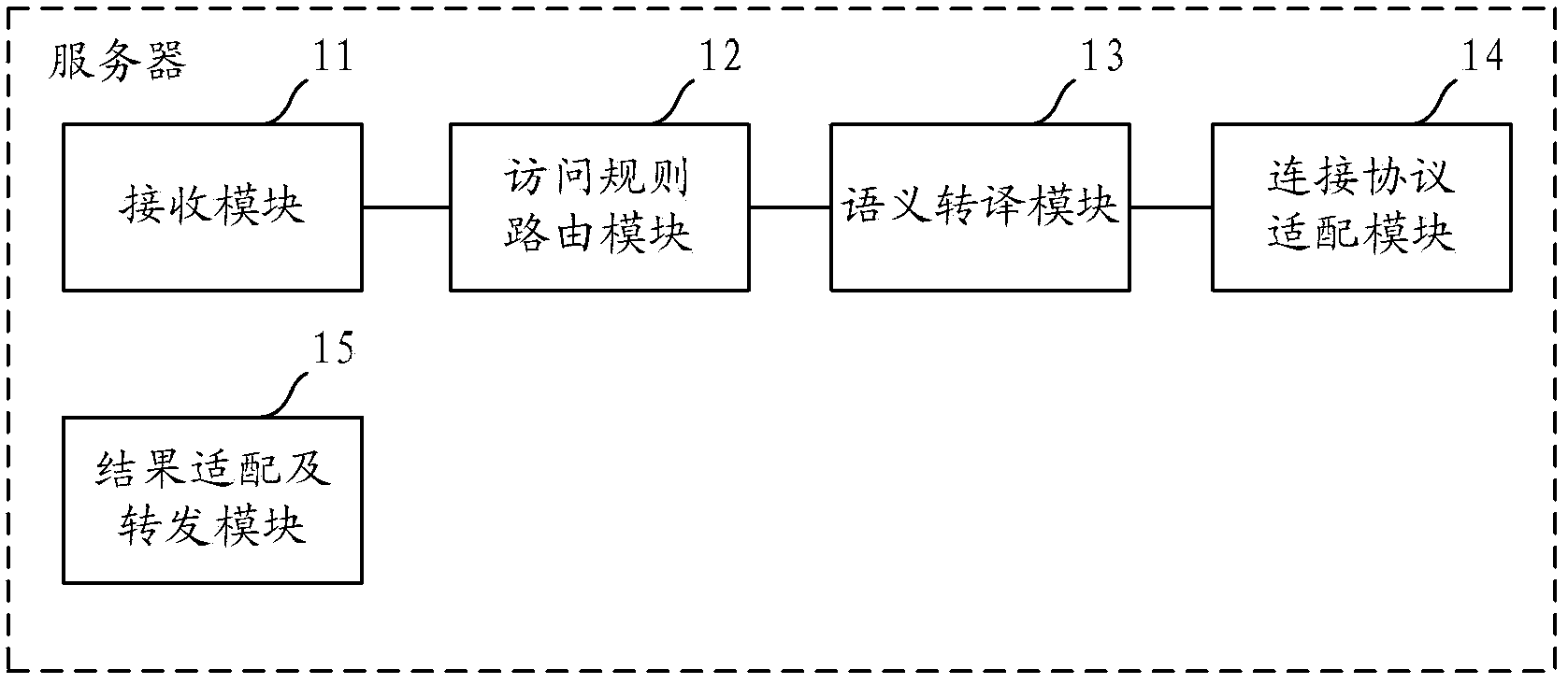
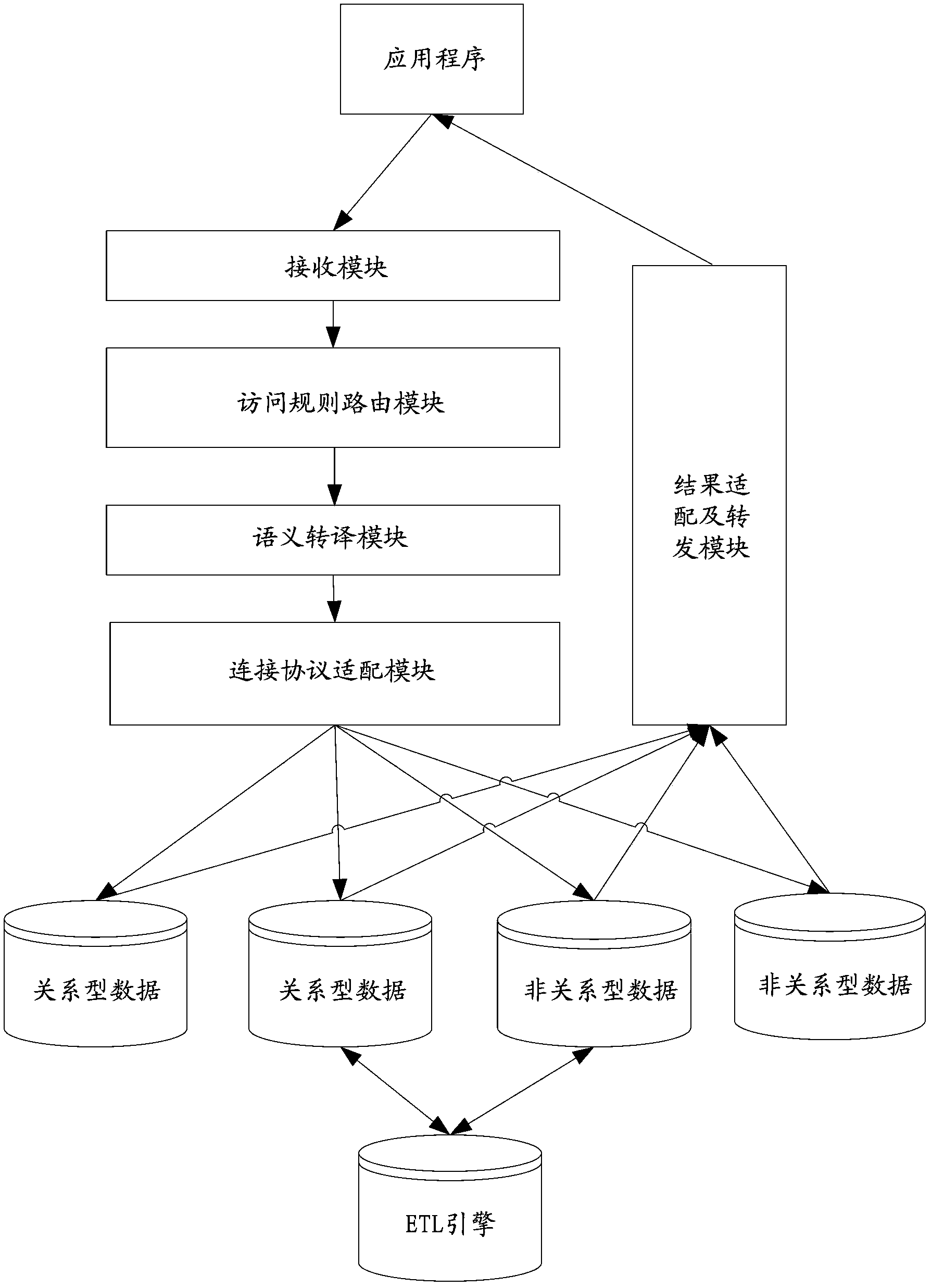
ActiveCN103823815AHigh concurrent read and writeImprove scalabilitySpecial data processing applicationsRelational databaseSemantic translation
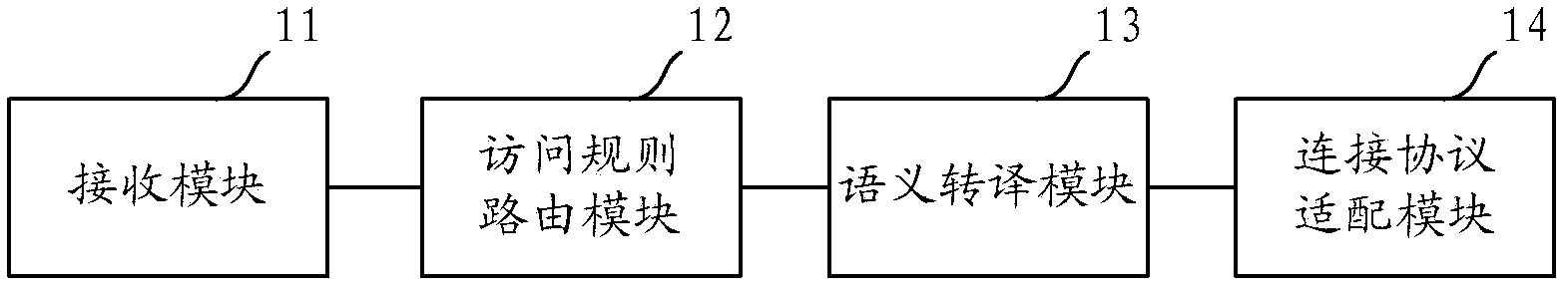
The invention provides a server and a database access method. The server comprises a receiving module, an access rule routing module, a semantic translation module and a connection protocol fitting module. The receiving module is used for receiving a first access statement; the access rule routing module is used for acquiring a first operating command and data-table identification information both carried in the first access statement, and judging whether or not data in a data table corresponding to the identification information is extracted into a non-relational database when the first operating command is an operation capable of being performed by the non-relational database; the semantic translation module is used for determining the non-relational database as a target non-relational database and translating the first operating command into a second operating command capable of being analyzed by the target non-relational database when the data in the data table corresponding to the identification information is extracted into the non-relational database is judged; the connection protocol fitting module is used for sending the second operating command and the data-table identification information to the target non-relational database. According to the server and the database access method, requirements on high-concurrency database read-write and the like are met by the non-relational database.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Information storing method and method for converting search inquiry into inquiry statement
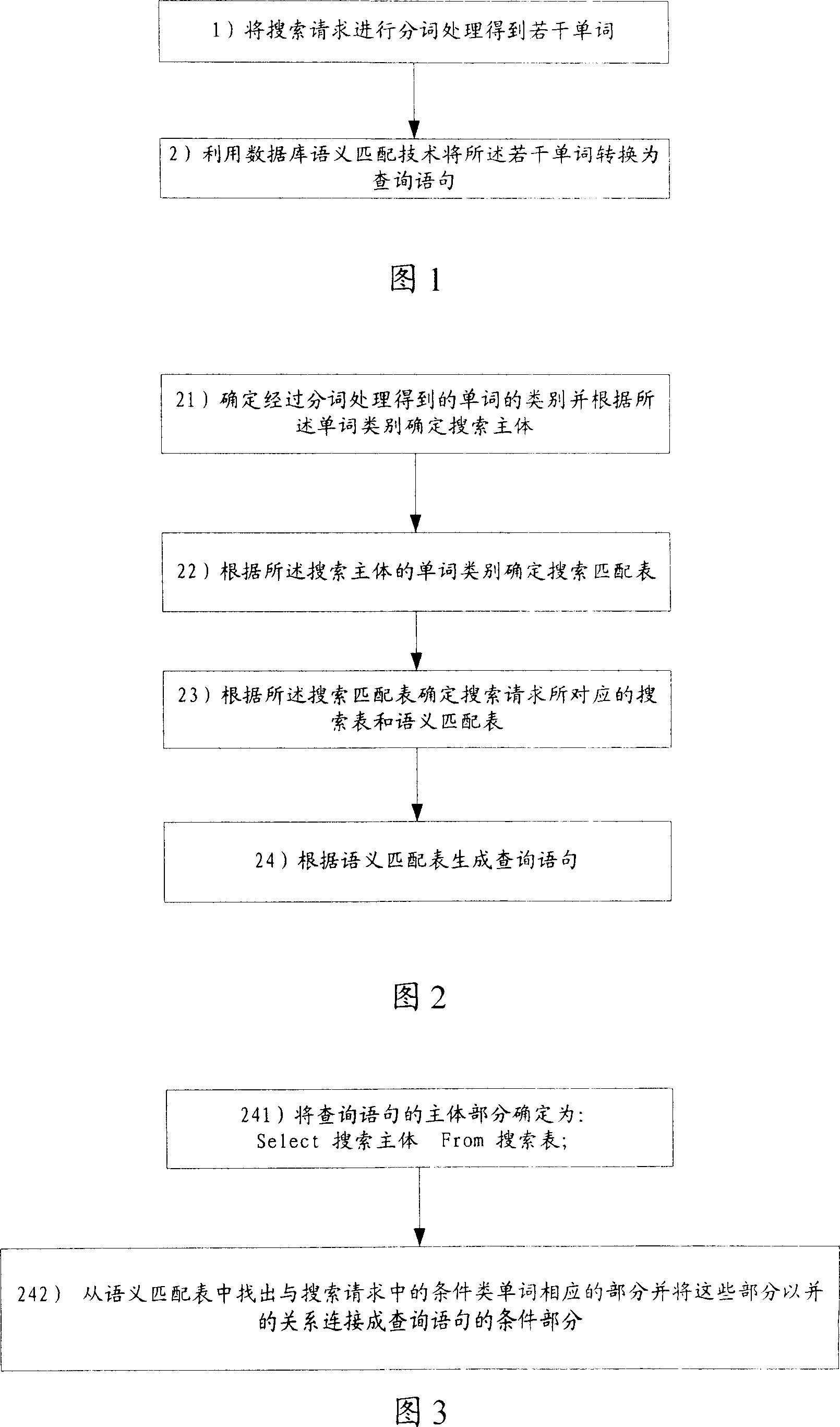
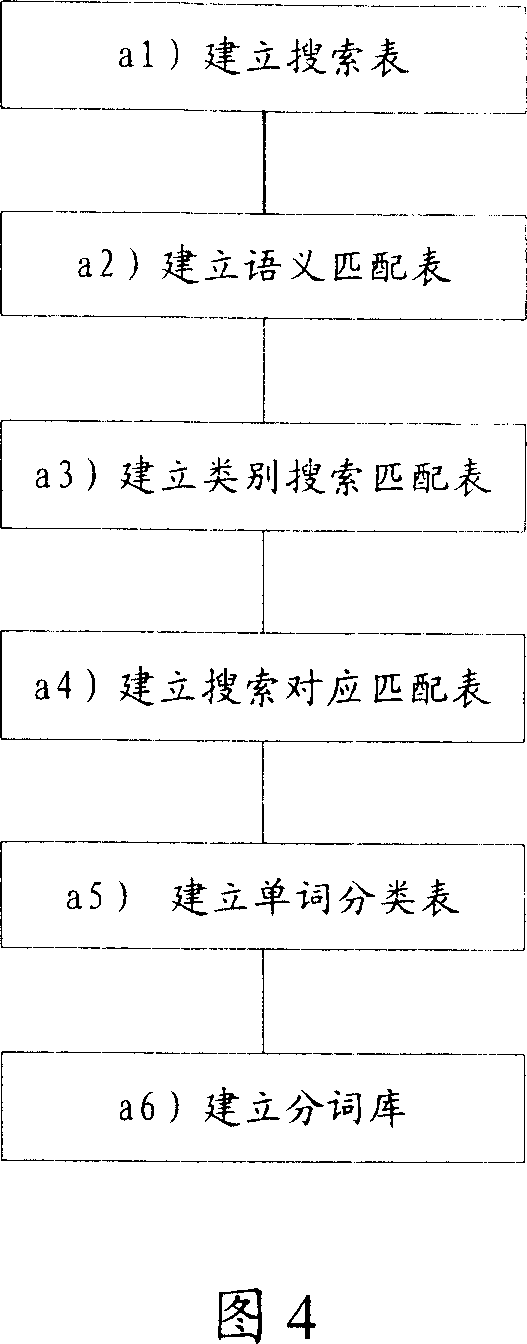
InactiveCN101000626AImprove search accuracyExact searchSpecial data processing applicationsSemantic translationTheoretical computer science
A method for storing information includes setting-up search table and semanteme matching table, setting up classification search matching table and setting up search corresponding-matching table. The method for converting search request to be query statement includes carrying out word treatment to obtain a numbers of words, converting said words to be query statement by utilizing databank semanteme matching technique and converting semanteme to be query statement by utilizing said technique and by querying match-table of statement section.
Owner:宋晓伟
System and Method of Content Generation
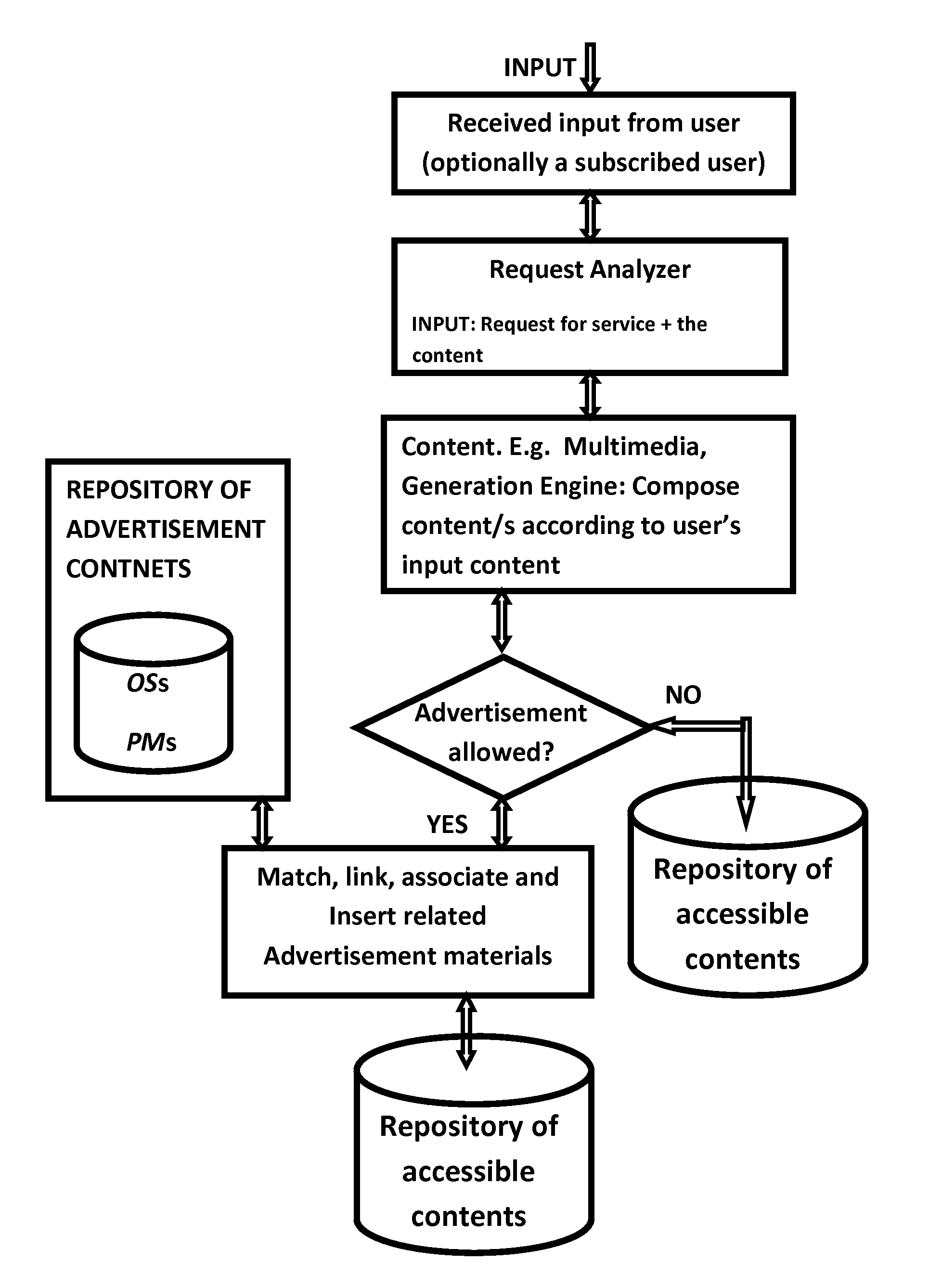
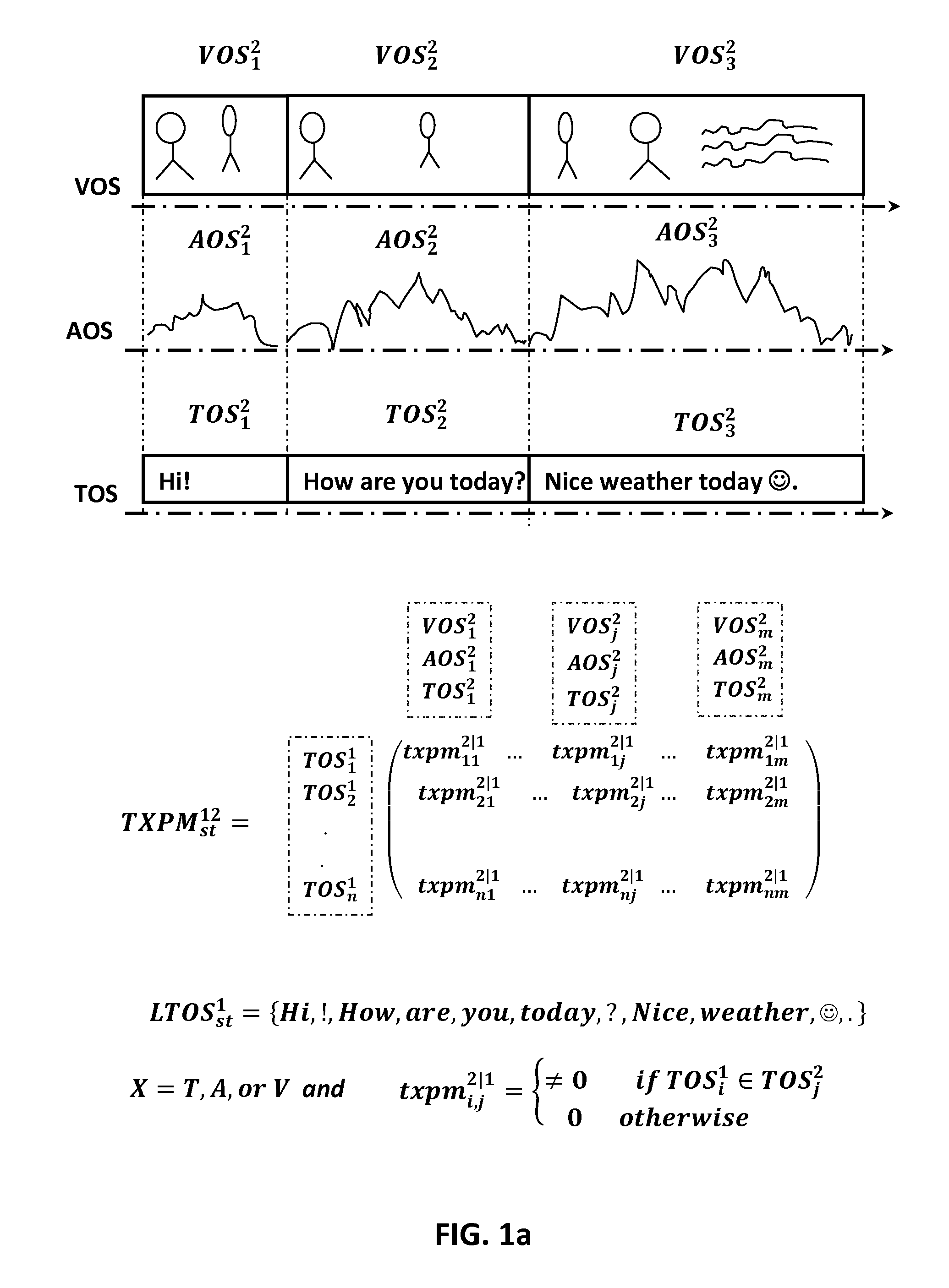
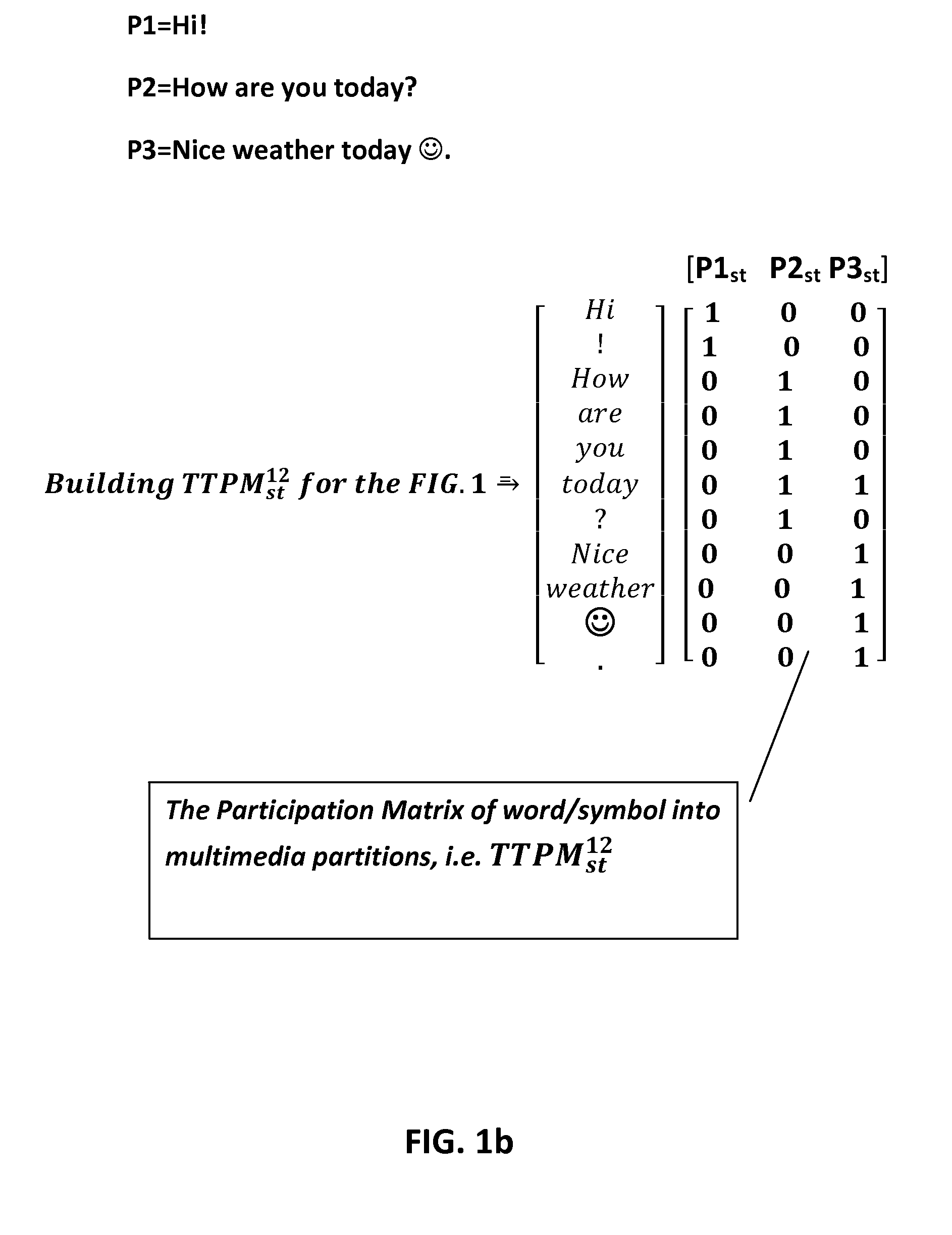
InactiveUS20110093343A1Increase investmentDigital data processing detailsMetadata multimedia retrievalSpoken languageSemantics
Methods and systems are given for representing and generating contents from pre-existed and pre-built contents for a given content. Methods are given for transforming information representation from one medium, type, or language to another medium, type and language. Exemplary embodiment is given for transforming the semantics of a given text or spoken language to a visual representation or combination of them. The systems and methods generate new contents in general and multimedia contents in particular in response to or for representing an input composition utilizing pre-existed and pre-built contents of various types, languages, and forms. The associated client server systems over the communication network are also given for generating contents for the contents given by the clients.
Owner:HATAMI HANZA HAMID
Software defined network cross-domain security agent method and software defined network cross-domain security agent system
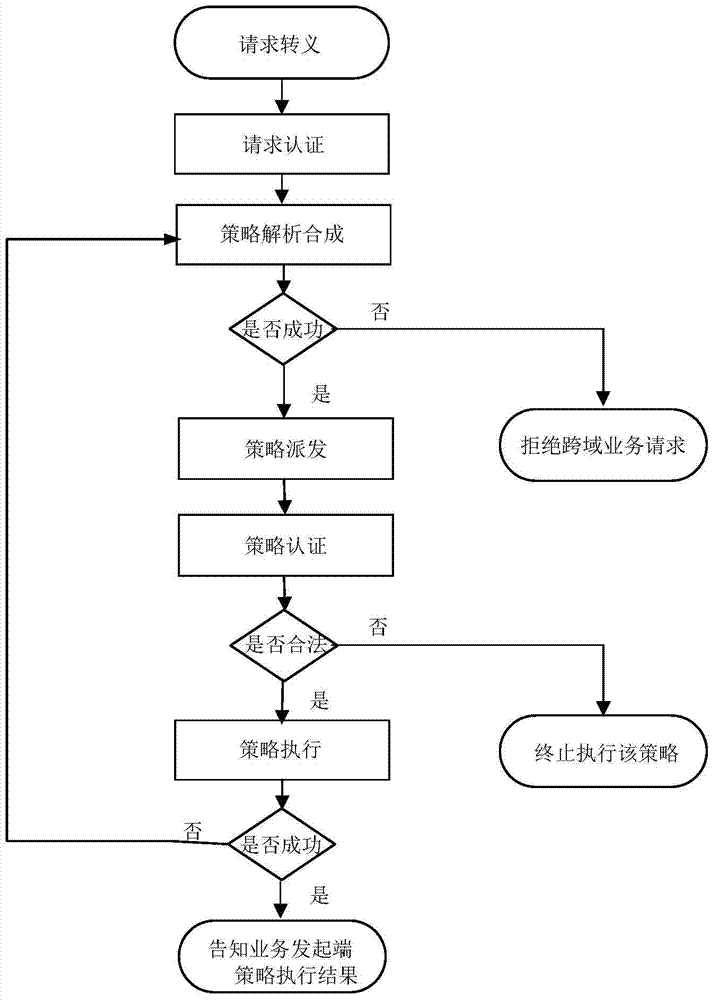
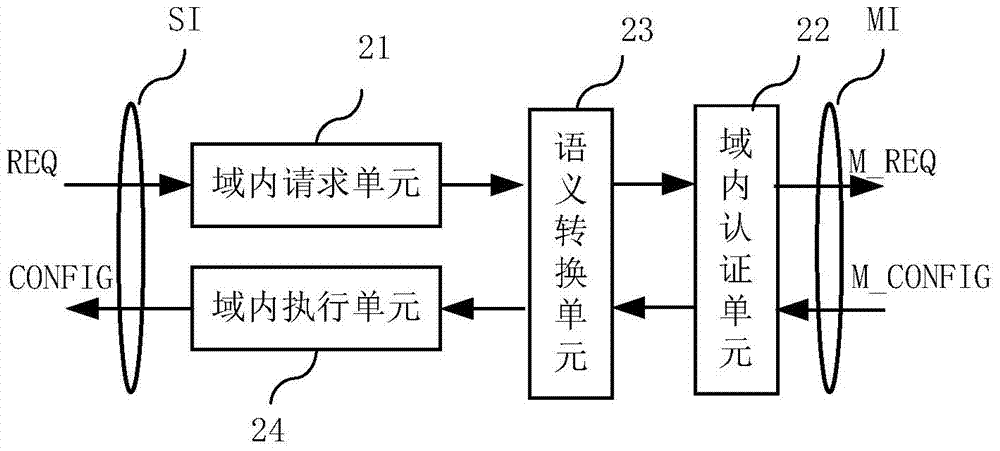
ActiveCN104243496ASimplify the interaction processIntegrated reductionTransmissionStrategy executionSemantic translation
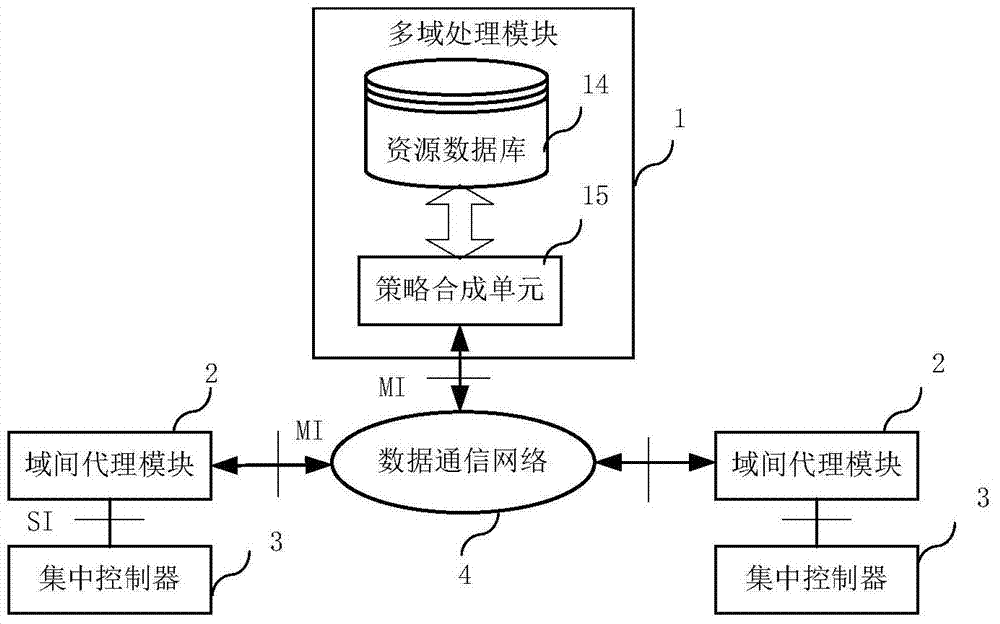
The invention provides a software defined network cross-domain security agent method and a software defined network cross-domain security agent system. Unified access control and management are performed on cross-domain shared resources, security policy conflict is eliminated, and strategy synthetic efficiency is improved. The software defined network cross-domain security agent system comprises at least two integrated controllers, at least one multi-domain processing module and at least two inter-domain agent modules, wherein the inter-domain agent modules transmit cross-domain business requests to the multi-domain processing modules after performing semantic translation; each multi-domain processing module comprises a resource database and a strategy synthesis unit; and after the strategy synthesis units receive the cross-domain business requests, the resource databases are queried, the strategy synthesis is carried out, and cross-domain strategy configuration commands are transmitted to the inter-domain agent modules. The software defined network cross-domain security agent method comprises the following steps of transferred meaning requesting, authentication requesting, strategy analysis and synthesis, strategy distribution, strategy authentication, strategy execution and the like. By the software defined network cross-domain security agent method and the software defined network cross-domain security agent system, information exchange of a heterogeneous network is simplified, information integration and synchronization difficulty of the heterogeneous network are reduced, resource scheduling safety is guaranteed, multi-domain resource sharing is realized, and business load of the centralized controllers in various domains can be adjusted.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Semantic-based audio-driven digital human generation method and system
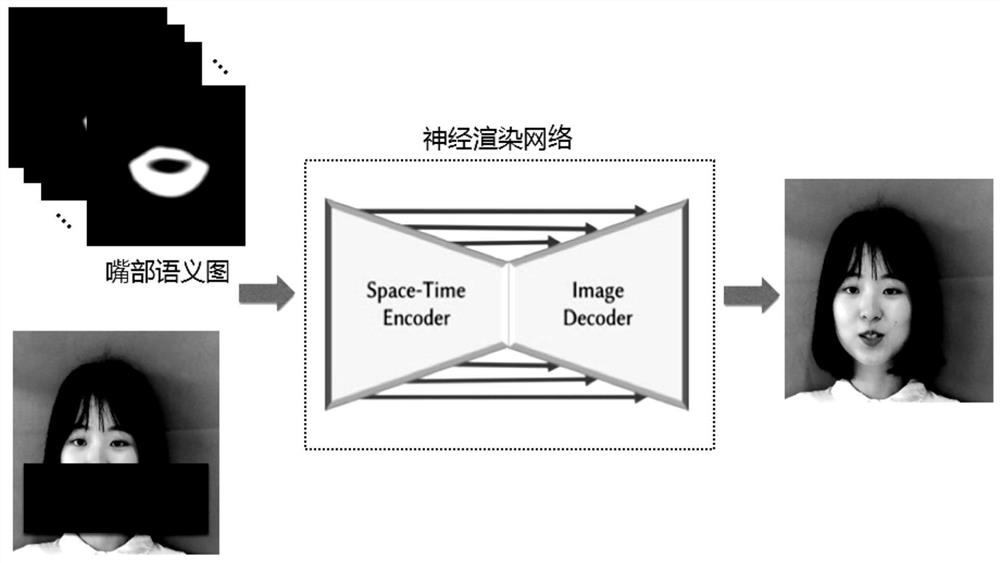
PendingCN112562722AGood technical effectAccurate and fine expressionCharacter and pattern recognitionSpeech recognitionFeature extractionSemantic translation
The invention discloses a semantic-based audio-driven digital human generation method and system. The generation method comprises the following steps of obtaining a target audio and a first human faceimage sequence; performing feature extraction on the target audio to obtain corresponding audio features; inputting the audio features into a pre-trained semantic conversion network, and performing semantic conversion on the audio features by the semantic conversion network to obtain a corresponding semantic motion sequence which comprises a plurality of mouth semantic graphs; and acquiring to-be-rendered face images with the same number as the mouth semantic graphs based on a first face image sequence, shielding mouth areas of the to-be-rendered face images, performing face synthesis based on the mouth semantic graphs and the to-be-rendered face images, and generating a synthesized face sequence. According to the invention, conversion between audio and facial semantics is realized through the semantic conversion network, and accurate expression of mouth shapes is realized by utilizing the facial semantics.
Owner:新华智云科技有限公司
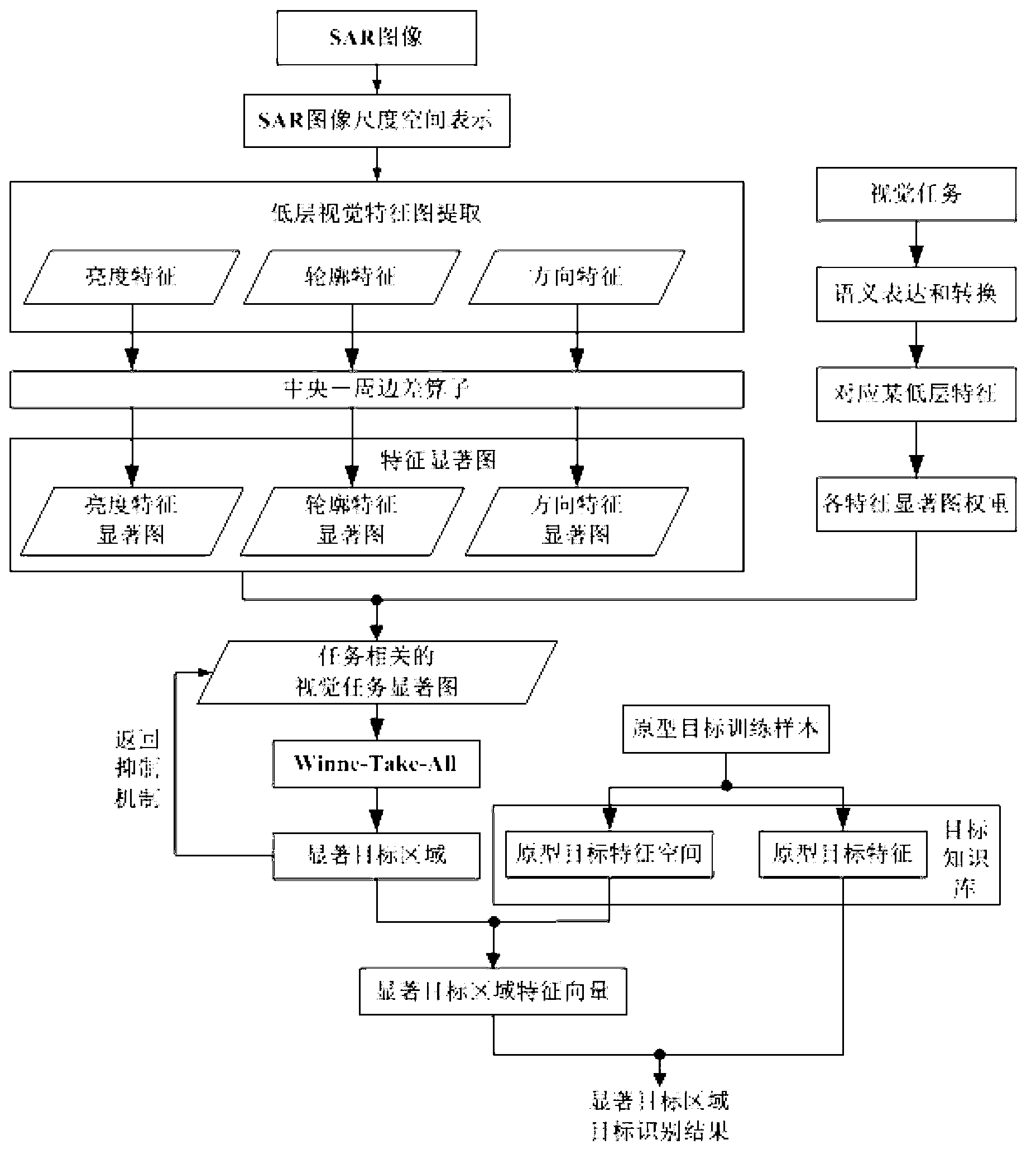
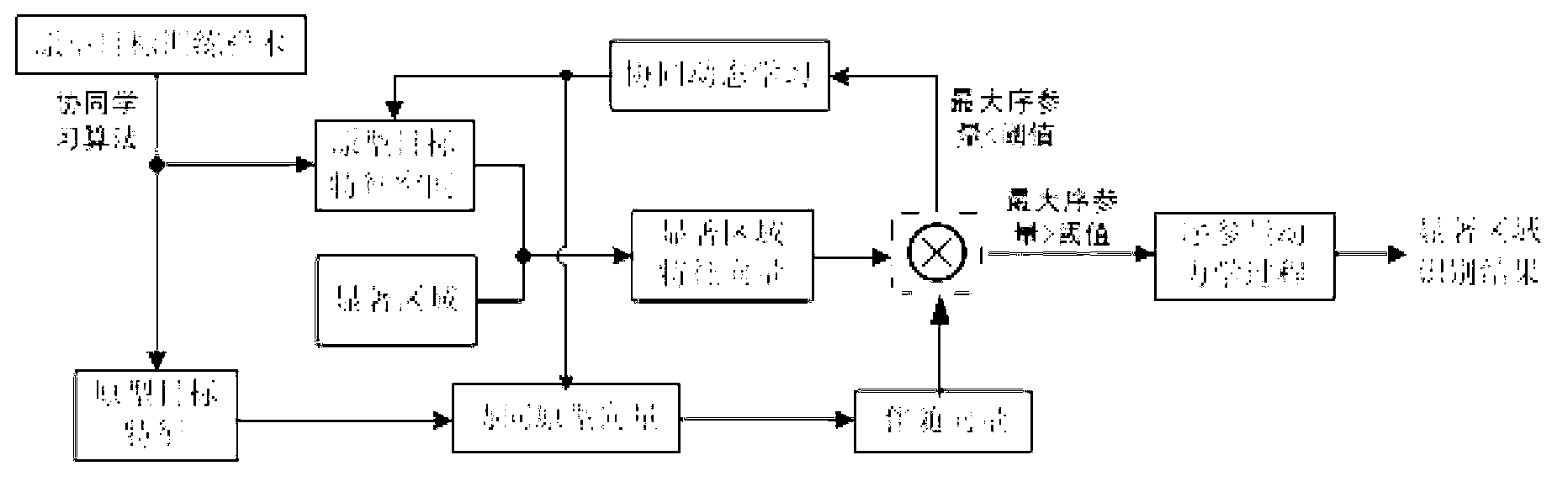
Method for recognizing collaborative target in SAR (Synthetic Aperture Radar) image based on visual attention mechanism
InactiveCN103065136AAbility to learn onlineQuick selectionCharacter and pattern recognitionPattern recognitionSynthetic aperture radar
The invention provides a method for recognizing a collaborative target in an SAR (Synthetic Aperture Radar) image based on a visual attention mechanism. The method comprises the following steps of: establishing the scale spatial presentation of an SAR image; extracting a low-layer visual feature map, carrying out semantic translation on a visual task, translating the visual task, decomposing the visual feature map, calculating the weight of each visual feature map, and generating a visual task saliency map relevant to the visual task; selecting a salient target region in the SAR image by utilizing the visual task saliency map to realize the separation of a foreground and a background of the target region in the SAR image; learning samples of various known prototype targets through a collaborative learning algorithm to obtain features and feature spaces of the known prototype targets and generate a known prototype target knowledge base; and recognizing collaboration of targets in the salient target region: recognizing the targets in the salient target region of the selected SAR image based on the known prototype target knowledge base by utilizing a collaboration pattern recognition order parameter dynamic iteration process.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Cloud storage access control method based on attribute-based encryption
InactiveCN107846397AAvoid VulnerabilityAvoid the disadvantage of high loadabilityTransmissionUser needsAttribute-based encryption
The invention provides a cloud storage access control method based on attribute-based encryption. The specific process is as follows: firstly, defining an access control policy of a file, and storingthe access policy information of the file in the access control policy; secondly, performing primary encryption on the file by using a symmetric encryption algorithm; thirdly, extracting attributes ina standard policy, converting the attributes into the form of character strings necessary for CP-ABE according to the semantics, and receiving, by the CP-ABE, the character strings to serve as an attribute set; finally, performing secondary encryption on a symmetric key used in symmetrical encryption through the attribute set by adopting an attribute-based encryption algorithm, and storing the cipher corresponding to the key; and when the user needs to access the file stored in the encryption manner, firstly, decrypting the cipher of the symmetric key used for encrypting the file according tothe attribute information of the user to obtain the symmetric key, and then performing decryption access on the encrypted file by using the symmetric key. The method provides a dynamically scalable and efficient access control mechanism for user data.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
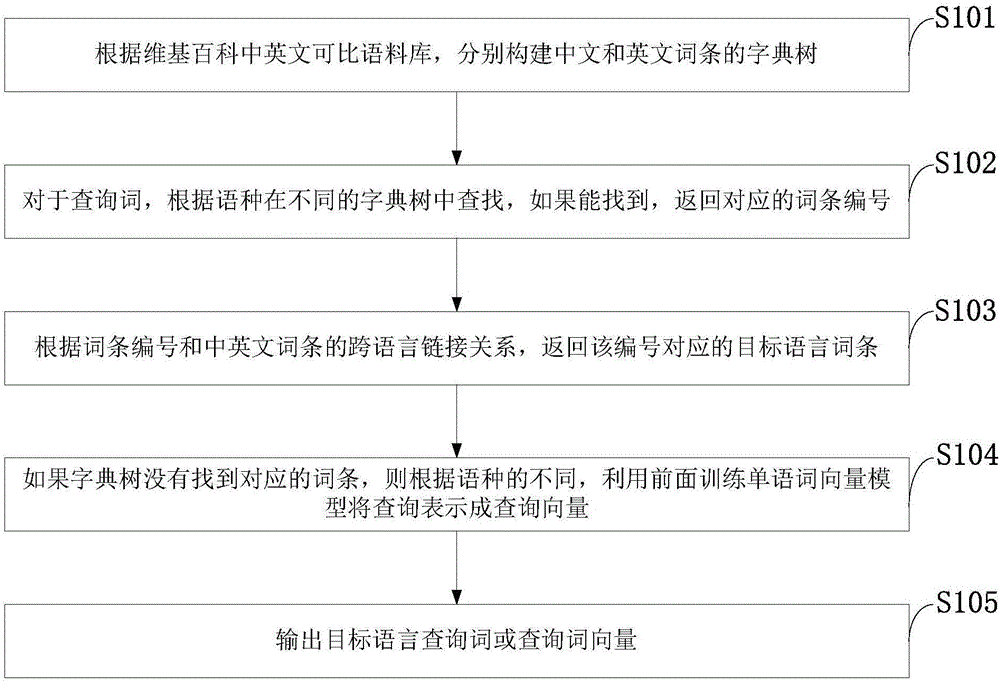
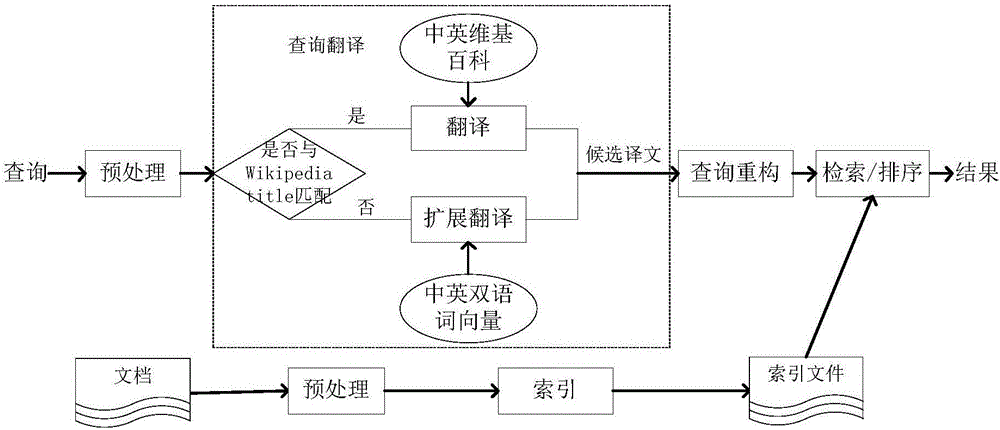
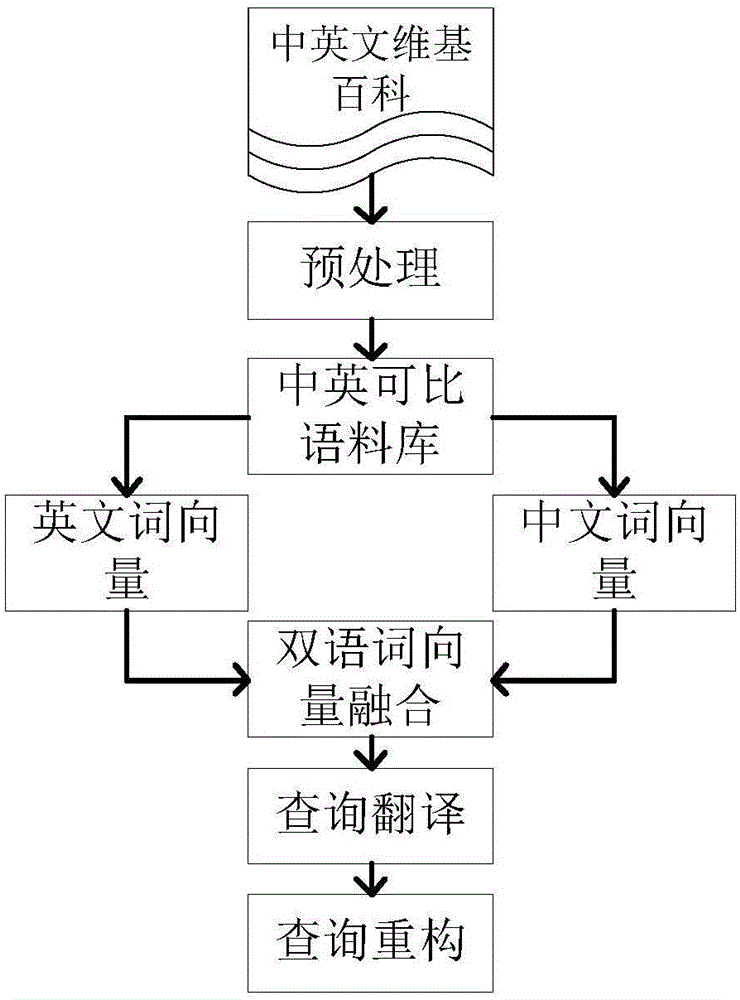
Cross-language retrieval method oriented to big data
ActiveCN106372187ANatural language translationSemantic analysisSemantic translationTranslation function
The invention discloses a cross-language retrieval method oriented to big data. The cross-language retrieval method oriented to the big data comprises the following steps: constructing a bilingual word vector model by use of cross-language relationship between Chinese-English Wikipedia entries; translating query by use of the bilingual word vector model; finally, constructing a new query execution retrieval according to a candidate translation. The bilingual vector model utilizes source language query vectors as input, and the similarity degree of target language documents similar to query vector semantics is output; during a query translation process, a canonical correlation analysis result is adopted. Through starting from the angle of automatic query translation and utilizing the document semantic similarity characteristic of different languages, a shared semantic space of two languages is found, and semantic translation on query is performed in the shared space, so that an automatic query translation function is realized.
Owner:GLOBAL TONE COMM TECH
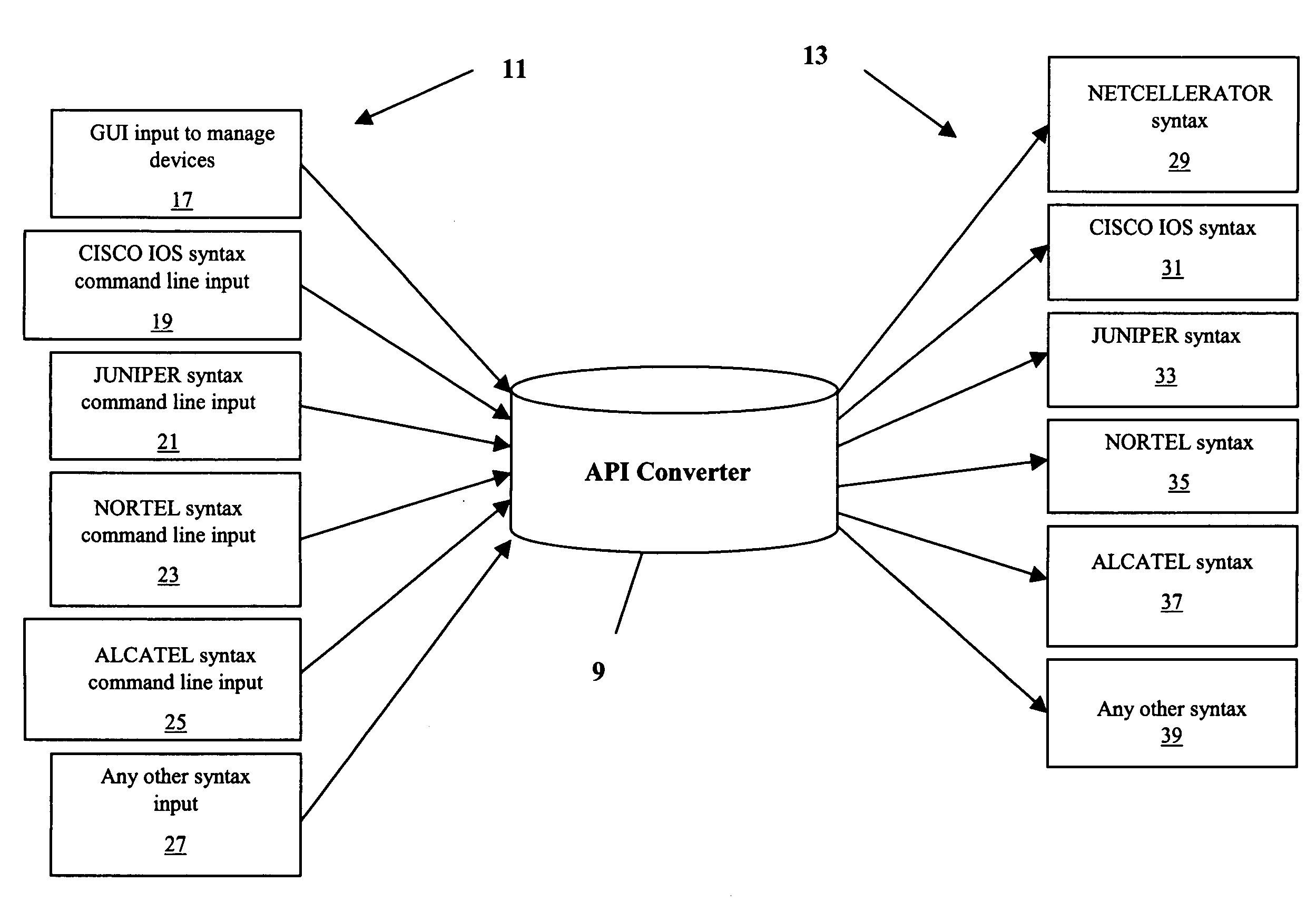
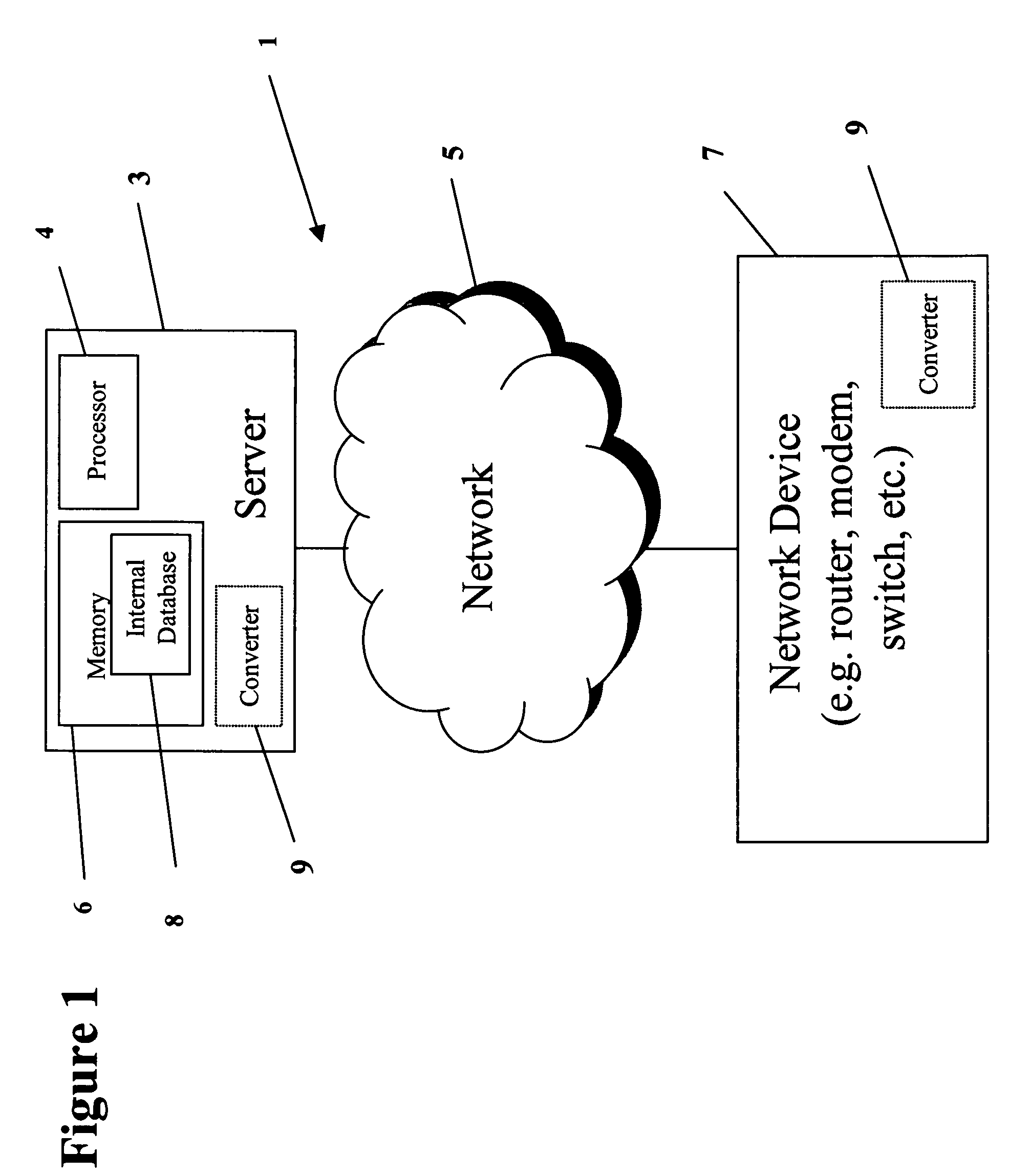
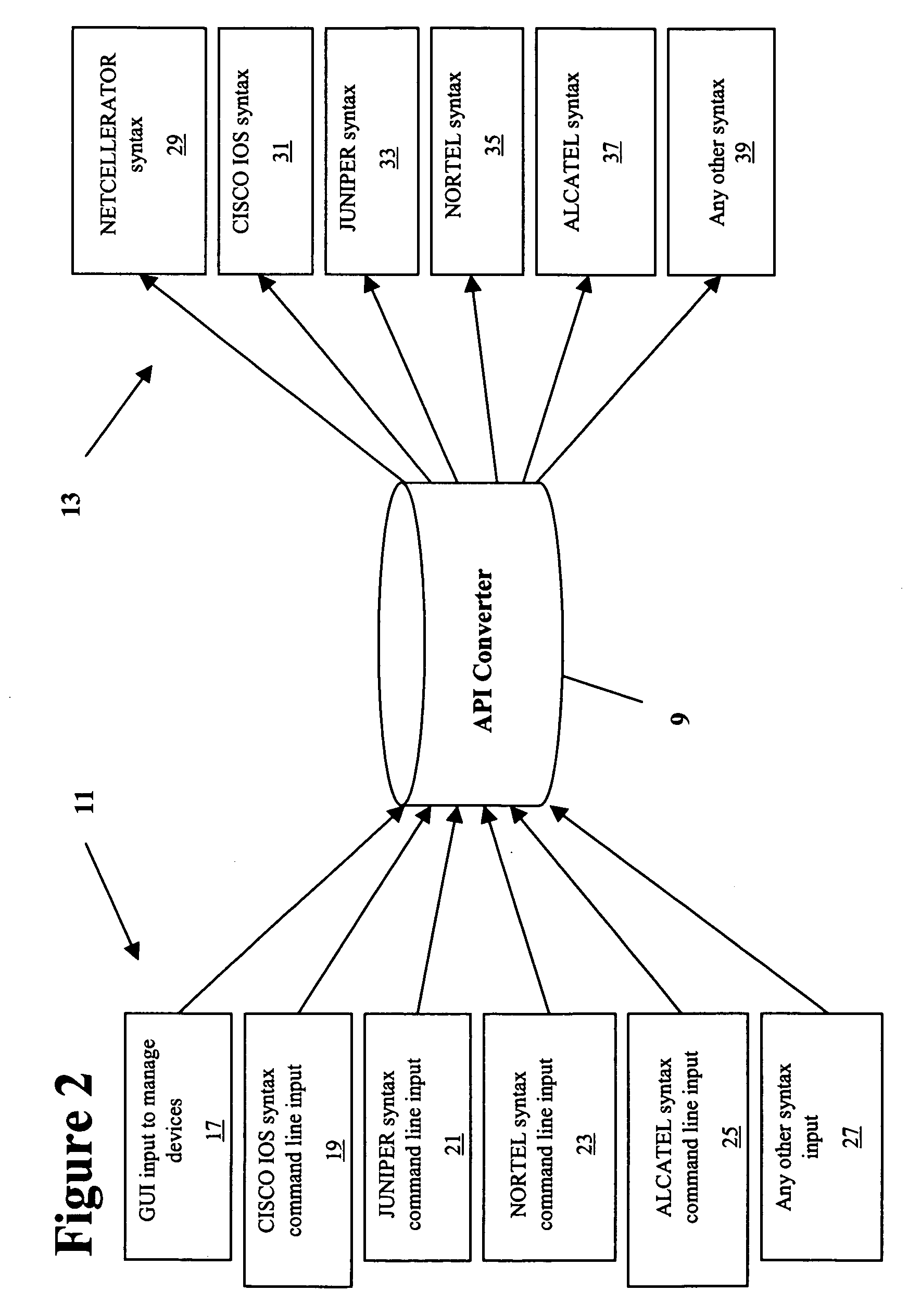
Devices, systems and methods for network device conversion
InactiveUS20080126520A1Easy to useDigital computer detailsTransmissionComputer hardwareCommand-line interface
The present invention is a converter for abstracting network devices away from manufacturer specific syntax and / or semantic capabilities by making the network devices configuration independent trough syntax and / or semantic conversion. An application program interface converts between input options and output options. The converter allows the user to choose from any input module to program end devices. The converter may function as a point and click option, a command line interface or any other interface. The present invention allows for the choice of output module based on requirements of a target network device.
Owner:NET CONEX
Data stream tracking method
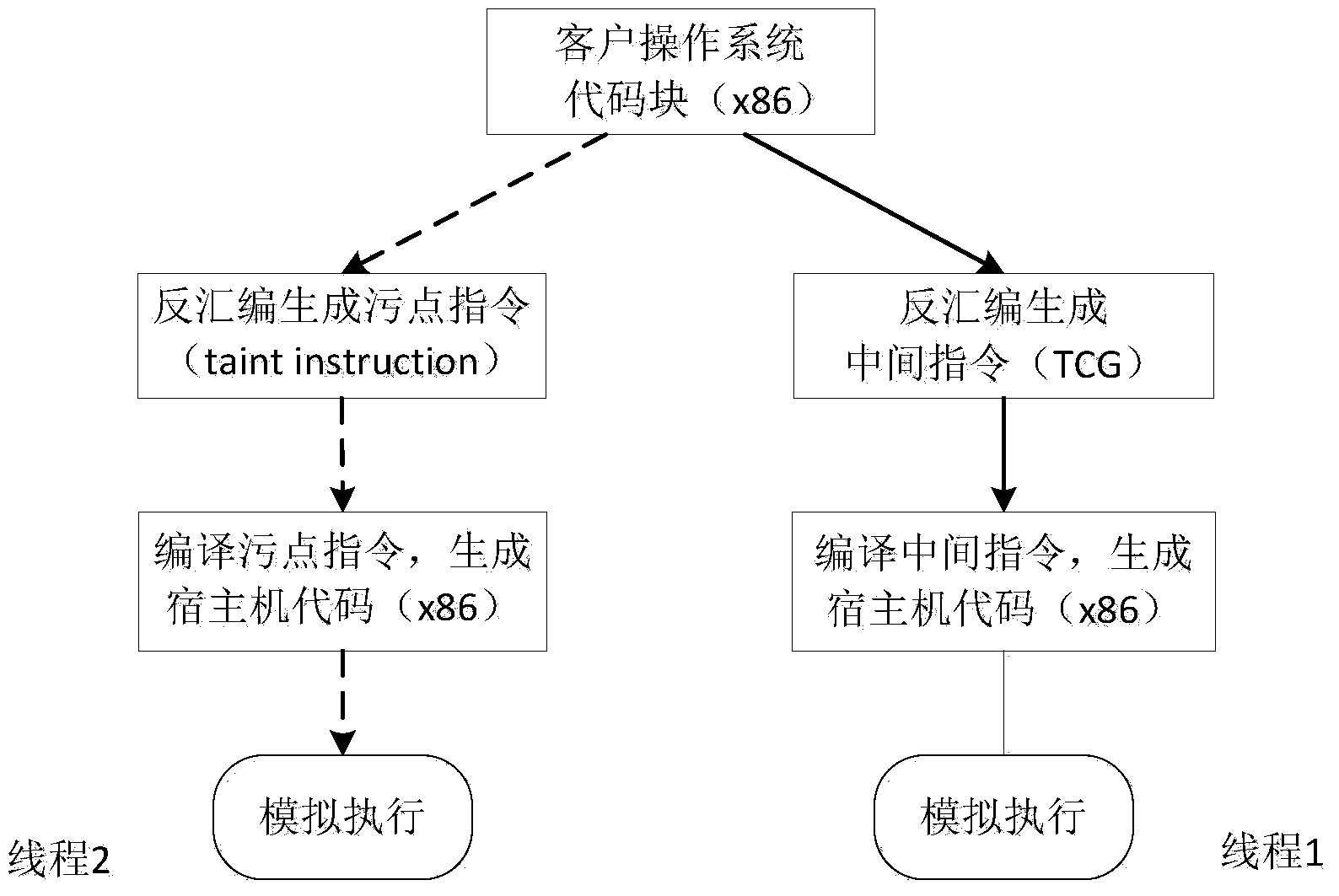
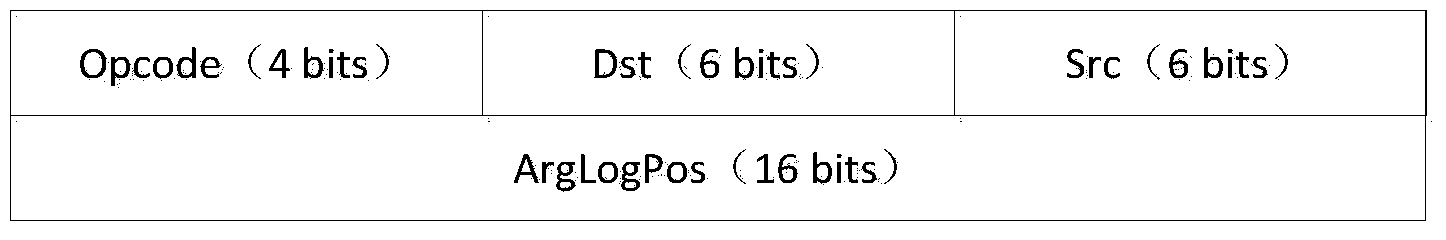
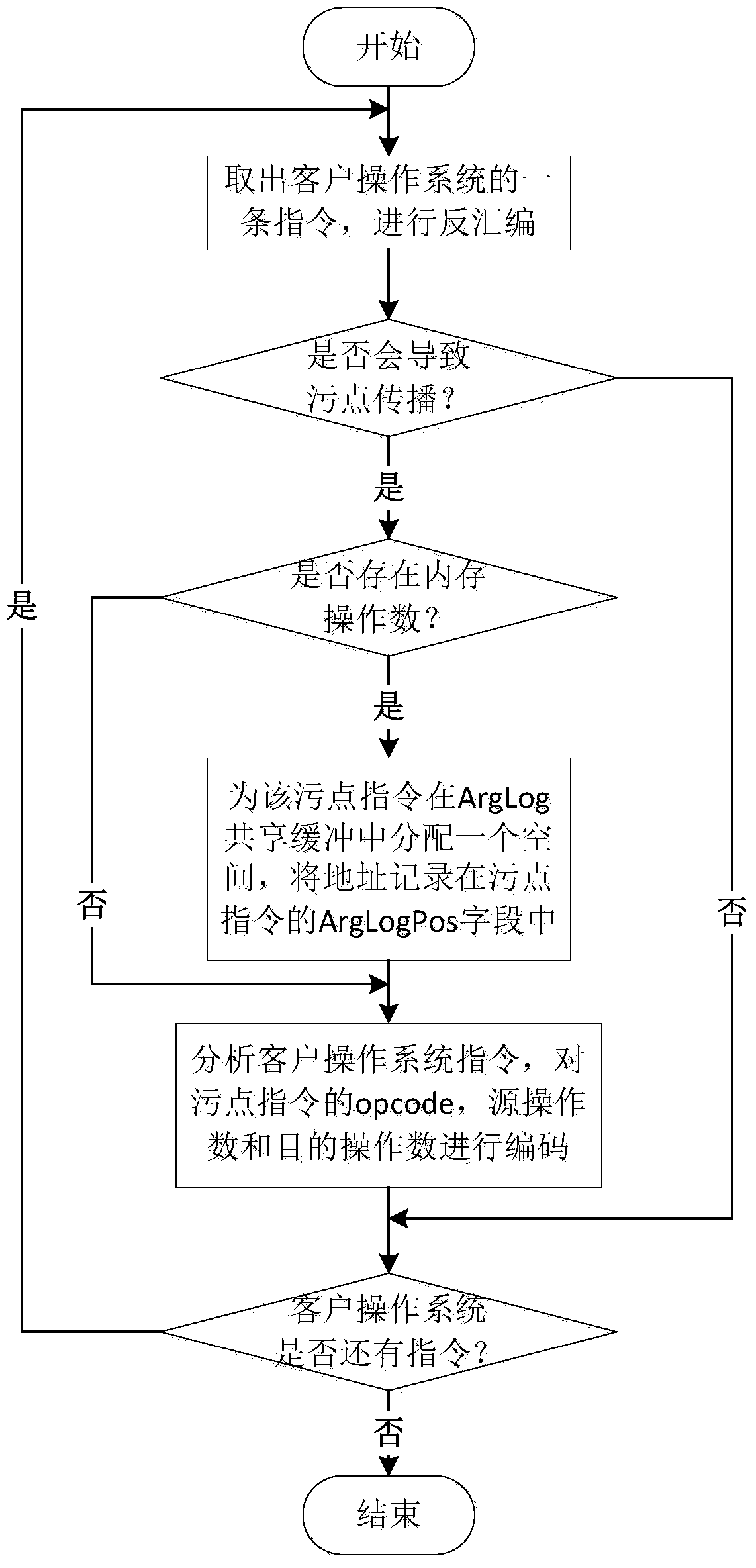
ActiveCN103714288AStrong coupling abilityHigh taint tracking performancePlatform integrity maintainanceOperational systemData stream
The invention discloses a data stream tracking method. The data stream tracking method comprises the following three stages: in the first stage, customer operating system instructions are disassembled in a static mode, wherein corresponding stain spreading instructions are generated according to a static client x86 instruction, stain data spreading updating operation is conducted, and an internal storage operand physical address which can not be acquired in the static disassembling process is acquired in a dynamic execution process by adopting a shared cache; in the second stage, a host machine execution code is generated through compiling, wherein an executable code on a host machine is generated according to stain instructions in the first stage in the form of a manipulation function so as to facilitate execution of the third stage; in the third stage, a new thread of execution is opened up, wherein the stain instructions are executed and fetched one by one, and the manipulation function of the stain instructions is called. According to the data stream tracking method, stain tracking operation is separated from a simulator dynamic binary translation execution module, so that stain spreading updating based on stain semantic translation and parallelization of an x86 instruction level is realized, useless stain tracking operation is reduced, and interactive experience between a system and a user is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
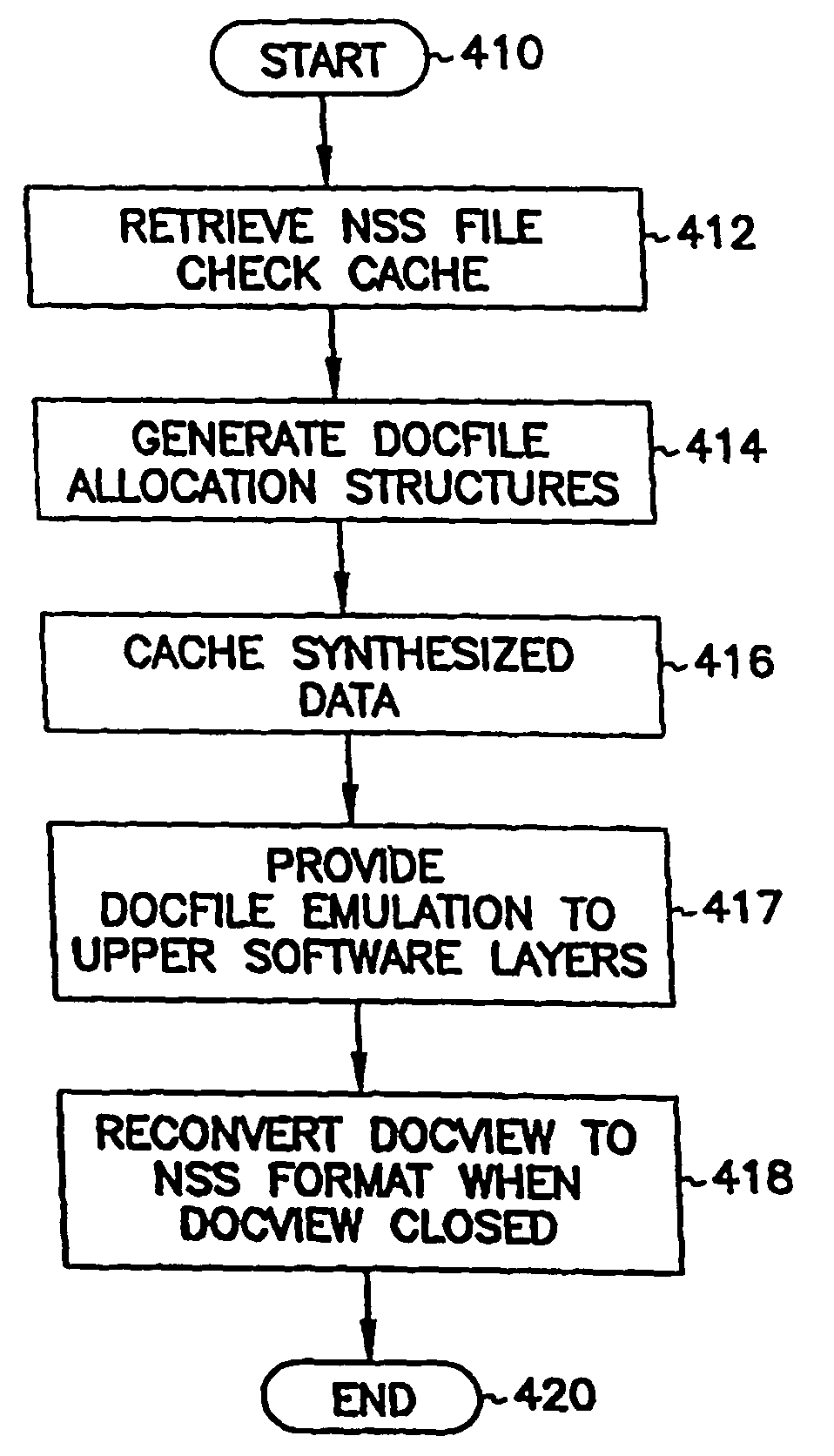
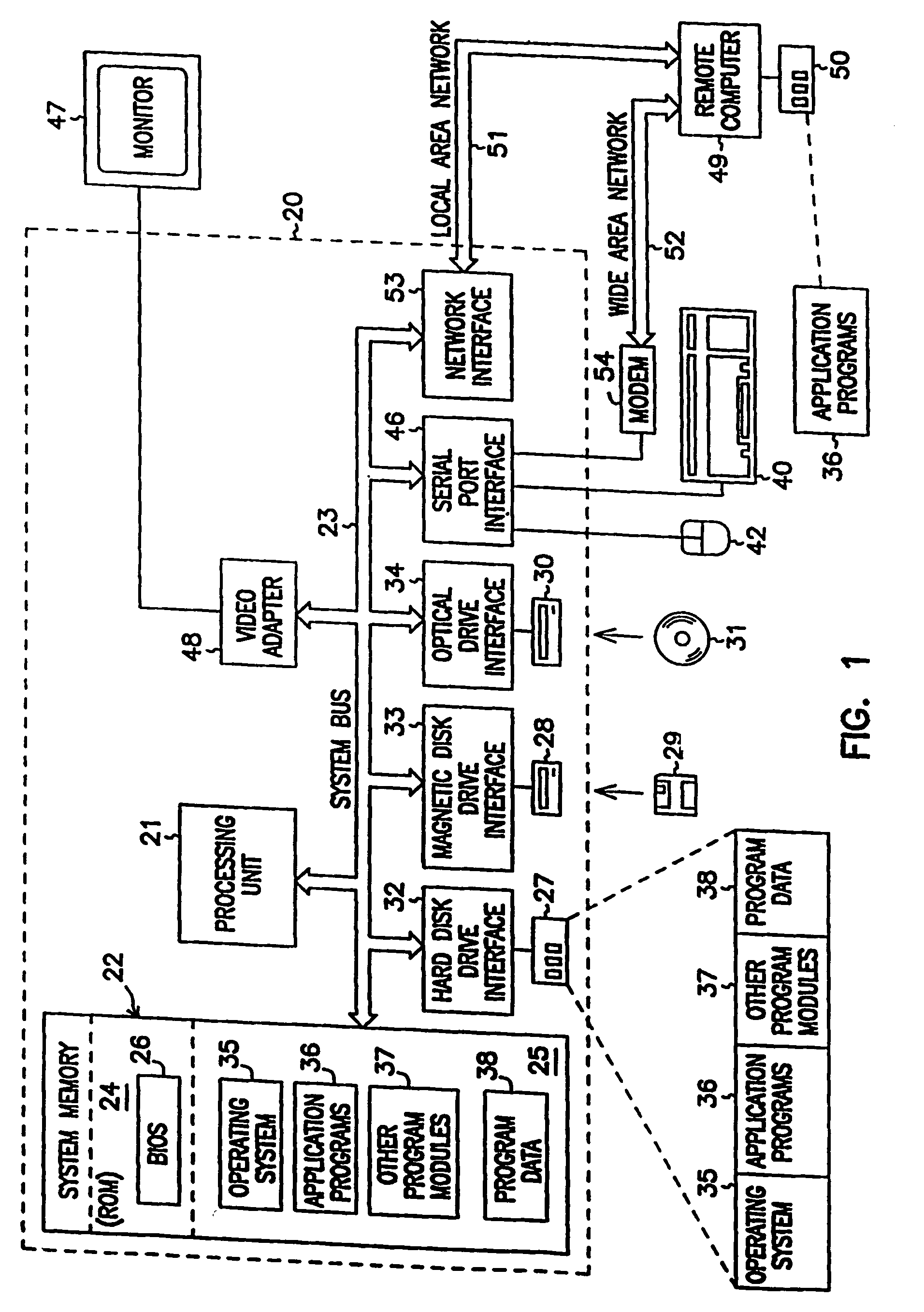
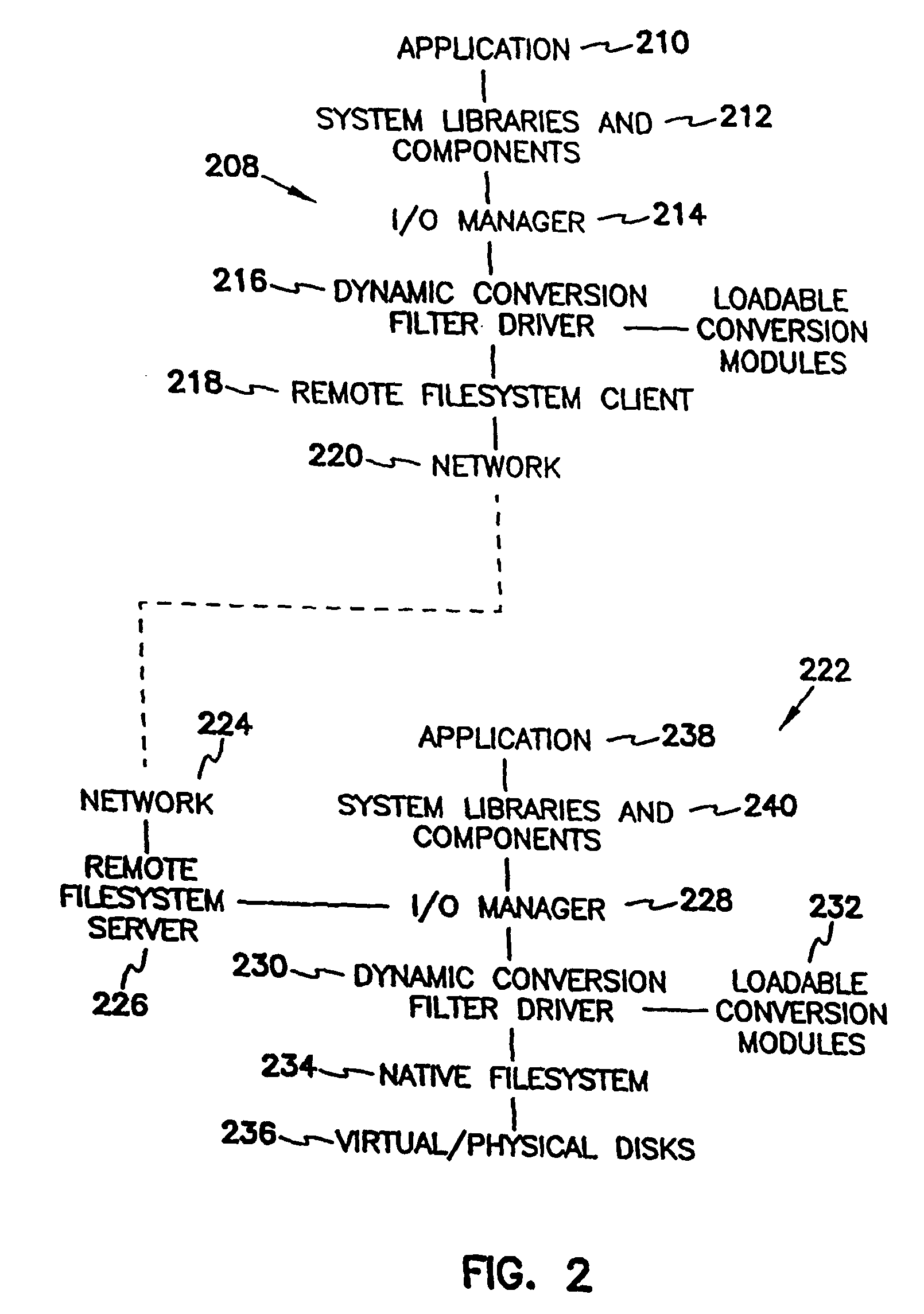
Converting information into different formats
InactiveUS7747594B2Easy to implementConversion is transparentData processing applicationsDigital data information retrievalOperational systemSystem requirements
A software layer (filter driver) residing between software components or application programs running locally or on a client across a network and a persistent store of an operating system provides on-the-fly conversions of persistent information formats. The filter driver determines which format a program expects, and dynamically converts the information from its storage format to the format expected by the program. Conversion includes both data format conversion, and conversion of access semantics. Loadable conversion modules are provided for converting application specific formats due to the potential large number of such formats which can be encountered. The filter driver may change the format that information is stored in based on access history or other system requirements. The software components or application programs may be ignorant of the true storage format used by the system, and thus the filter driver can be used to give old versions of software access to information stored in newer formats.
Owner:MICROSOFT TECH LICENSING LLC
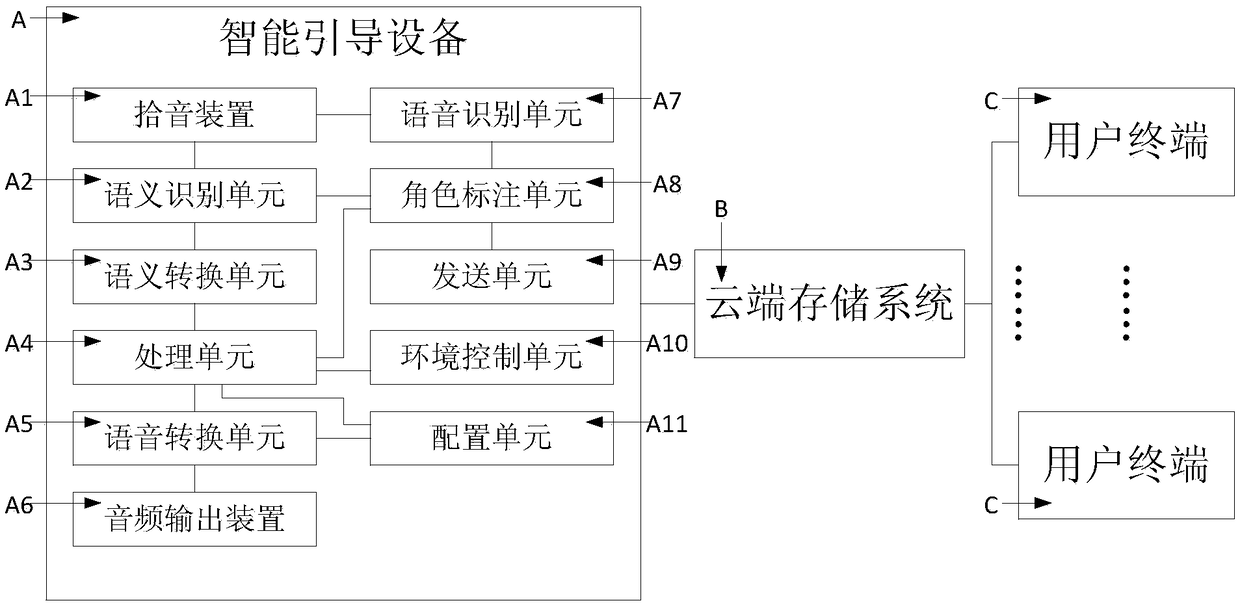
Automatic guide system based on multi-person interaction process and intelligent speaker box equipment
ActiveCN108159687AImprove engagement experienceWork around missing parameters that act as bootstrap rolesSpeech recognitionVideo gamesSemantic translationOutput device
The invention discloses an automatic guide system based on a multi-person interaction process and intelligent speaker box equipment, and belongs to the technical field of human-computer interaction. The system comprises a semantic recognition unit, a semantic conversion unit, a processing unit and a voice conversion unit, wherein the semantic recognition unit is connected with a pickup device andis used for recognizing input voice and converting the input voice into corresponding input characters; the semantic conversion unit is used for performing processing according to the input charactersso as to obtain a corresponding input instruction; the processing unit executes a current execution node according to the input instruction and outputs the execution state obtained after the execution of the execution node; the processing unit simultaneously transfers to a next execution node according to the execution state so as to wait for a next input instruction; the voice conversion unit isused for converting the executing state into the corresponding output voice; and the output voice is output through one audio output device of the intelligent device, and is known by a participant. The technical scheme has the beneficial effects that the problem of lack of a guide role in the multi-person interaction process is solved; the interaction flow process is precisely mastered; and the experience of the participant is improved.
Owner:YUTOU TECH HANGZHOU
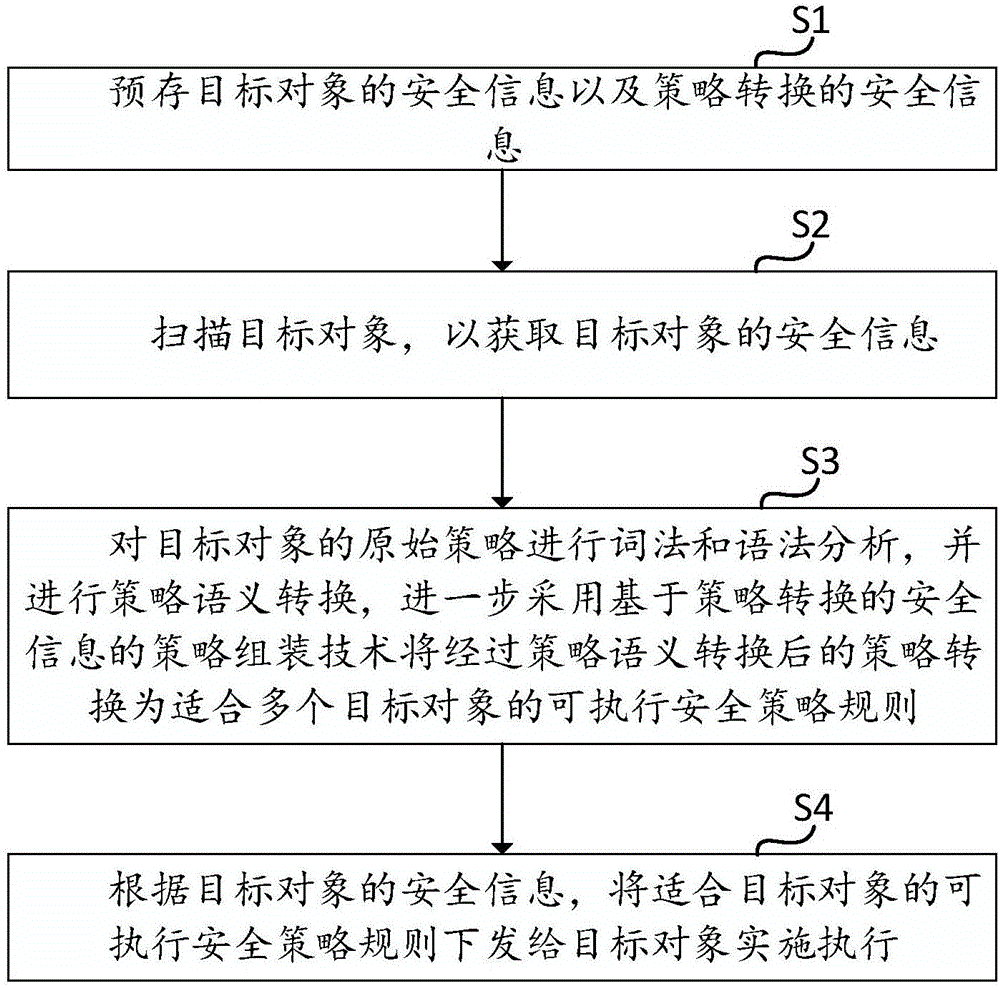
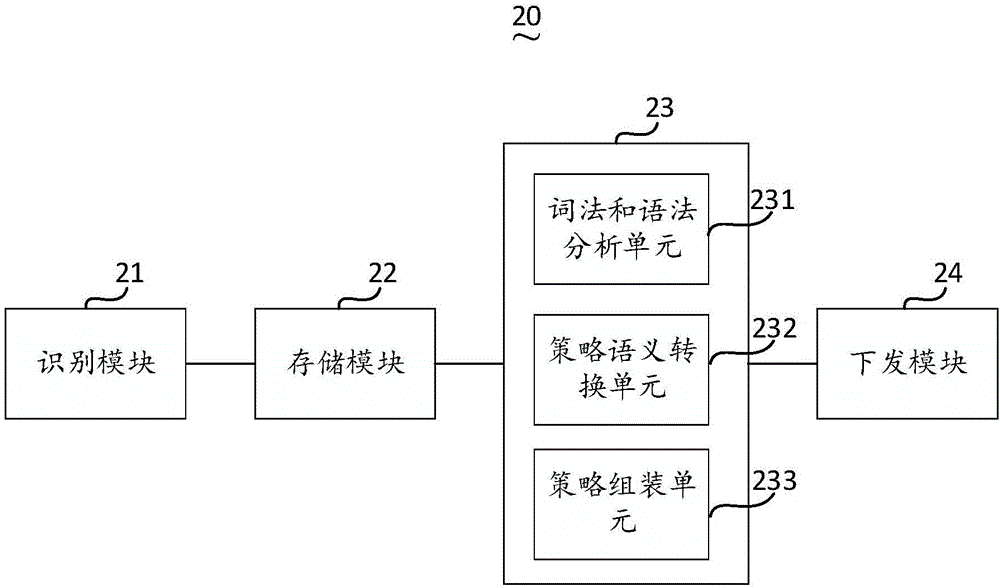
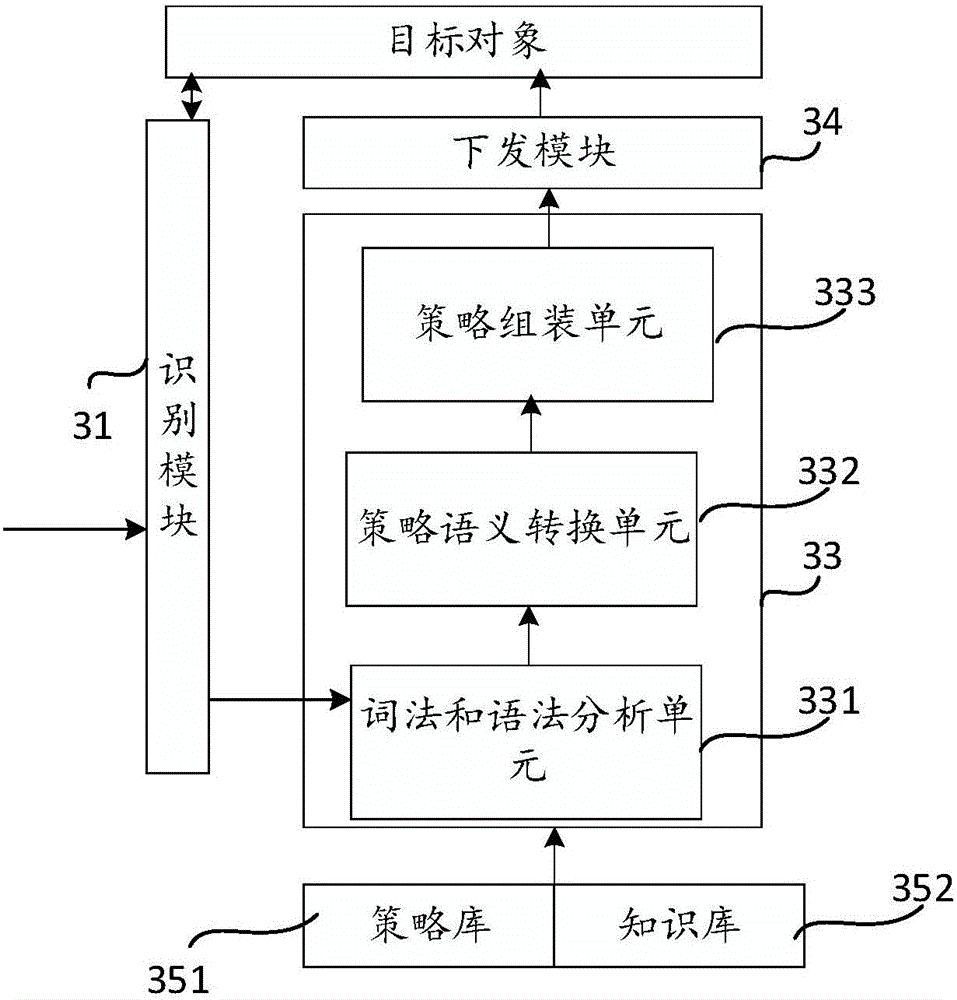
Safety strategy adapting frame and method thereof
ActiveCN106845246AImprove general performanceSupport unified managementPlatform integrity maintainanceTransmissionSemantic translationSecurity policy
The embodiment of the invention discloses a safety strategy adapting frame and a method thereof. The method comprises the steps that safety information of a target object and safety information of strategy transformation are prestored; the target object is scanned to obtain the safety information of the target object; morphological and grammatical analysis is conducted on an original strategy of the target object, semantic translation of the strategy is performed, and the strategy obtained after semantic translation of the strategy is further transformed into an executable safety strategy rule suitable for multiple target objects by adopting a strategy packaging technique of safety information based on the safety strategy; according to the safety information of the target object, the executable safety strategy rule suitable for the target objects is issued to the target object for execution. In the mode, a general safety strategy described by using a natural language can be converted into the executable safety strategy rule suitable for the target objects, and the method has high universality and supports centralized and unified management of safety strategies of multiple heterogeneous safety devices.
Owner:北京爱普安信息技术有限公司
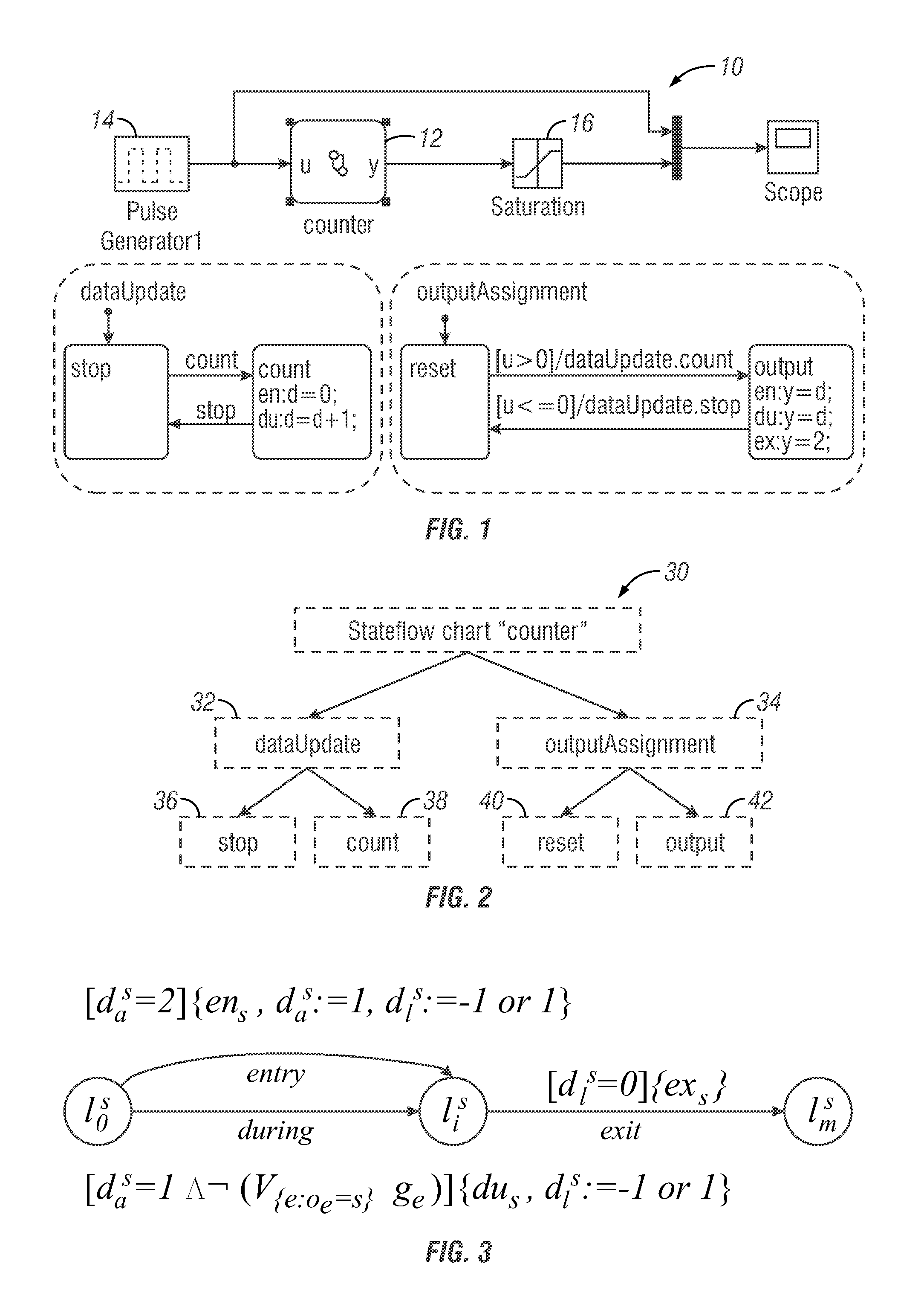
Semantic translation of stateflow diagrams into input/output extended finite automata and automated test generation for simulink/stateflow diagrams
ActiveUS8849626B1Analogue computers for electric apparatusComputation using non-denominational number representationGraphicsCombining rules
A method of translation of a chart associated with a graphical modeling environment into an input / output-extended finite automata (I / O-EFA) model is provided. The method includes receiving a representation of the chart and processing the representation of the chart with a computing device by (a) representing atomic models for each individual state of the chart, (b) applying composition rules to interconnect the atomic models while preserving state execution and transition behaviors to obtain the I / O-EFA model.
Owner:IOWA STATE UNIV RES FOUND
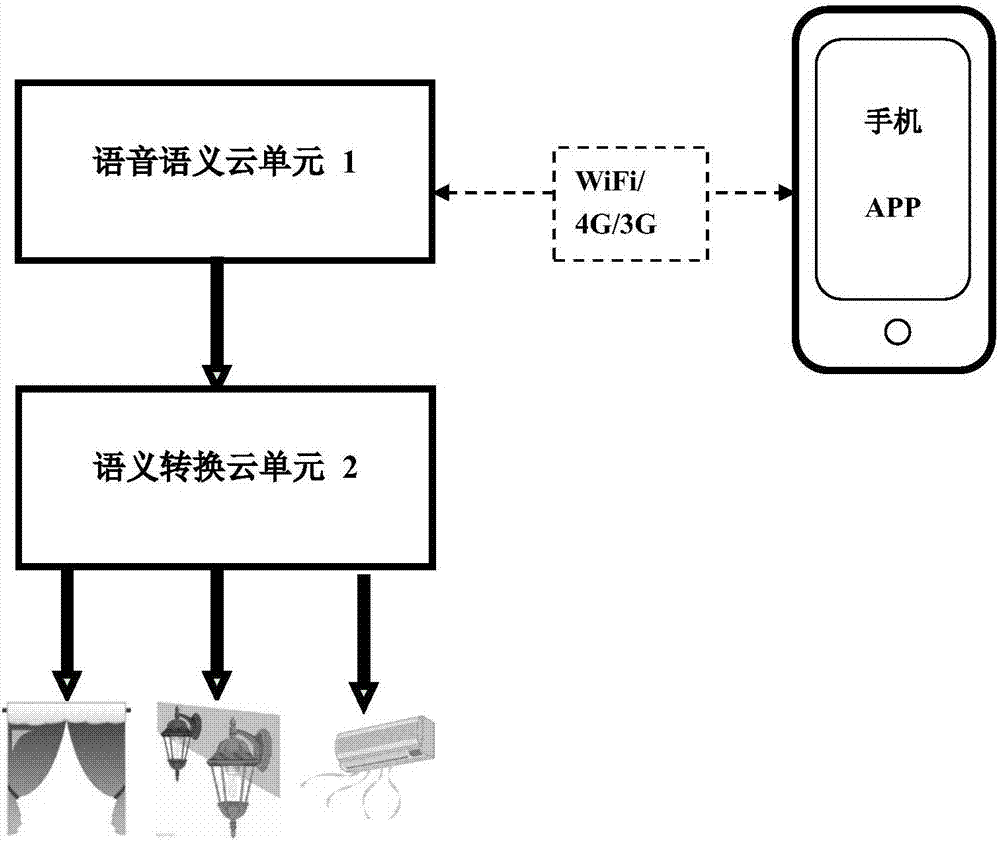
Smart home system and control method thereof
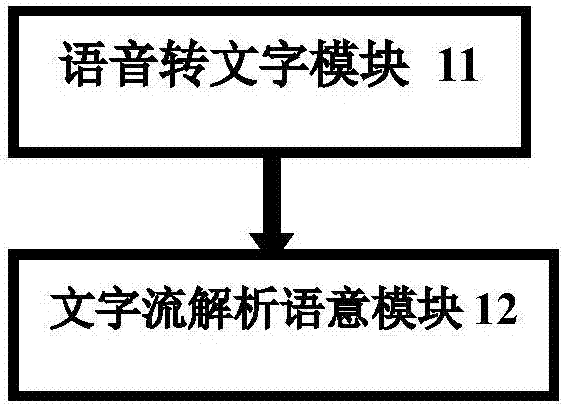
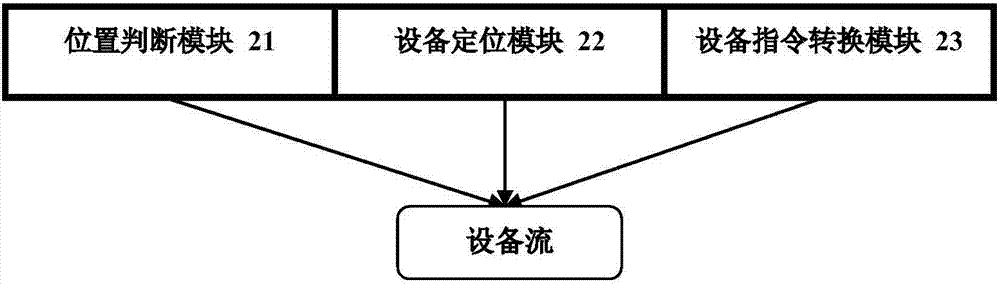
InactiveCN107170449AImprove portabilityIncreased comfort needsSpeech recognitionHome automation networksDevice typeSemantics
The invention discloses a smart home system and a control method thereof. The system comprises a voice semantic cloud unit and a semantic transformation cloud unit. The voice semantic cloud unit comprises a voice-to-text module and a text flow analytical semantic module. The semantic transformation cloud unit comprises a position judgment module, an equipment positioning module and an equipment instruction transformation module. The position judgment module is used for determining the concrete position of a target equipment cluster through the position keywords in semantic information and all the position groups of user controllable equipment. The equipment positioning module is used for determining the concrete equipment type of the target equipment cluster through the equipment keywords in the semantics and all the controllable equipment of the user. The equipment instruction transformation module is used for determining the concrete control type of the target equipment cluster in the selected equipment cluster through the instruction keywords in the semantics. According to the smart home system and the control method thereof, the voice is used as the input so that the demands for portability and comfortableness of smart home control can be enhanced.
Owner:SHANGHAI ACADIATECH
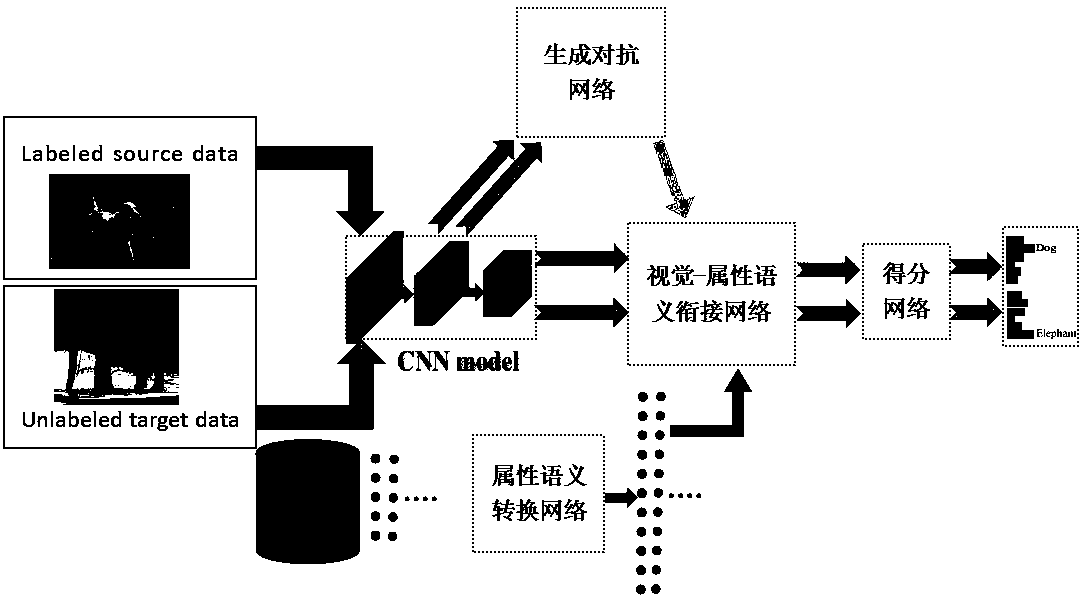
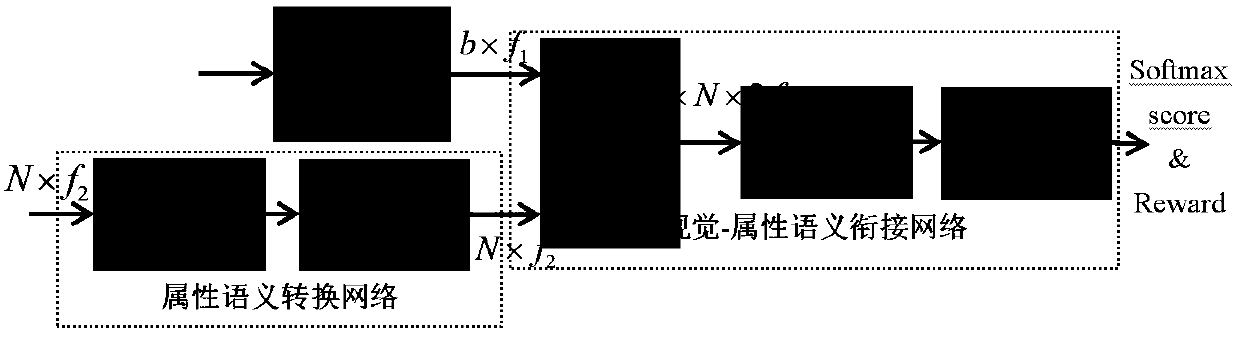
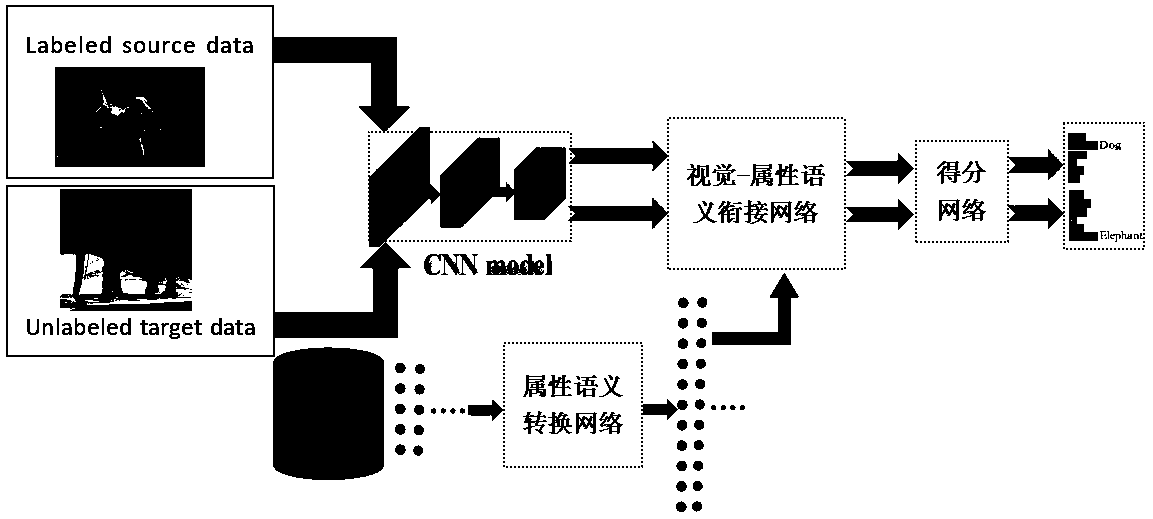
Zero-sample image classification model based on generative adversarial network and method thereof
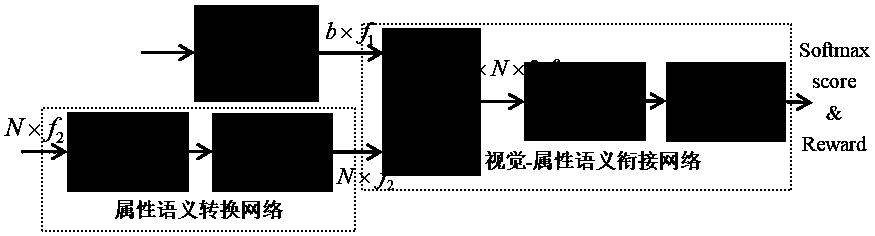
ActiveCN110795585AHelps to learn data distributionAdd categoryCharacter and pattern recognitionStill image data clustering/classificationSemantic vectorFeature vector
The invention relates to a zero-sample image classification model based on a generative adversarial network, and the model comprises a generative adversarial network module which is used for obtainingvisual error information; a visual feature extraction network processing module used for obtaining a one-dimensional visual feature vector of an image; an attribute semantic conversion network moduleused for mapping a low-dimensional attribute semantic vector to a high-dimensional feature vector with the same dimension as the visual feature vector by using two linear activation layers; a vision-attribute semantic connection network used for realizing fusion of a vision feature vector and an attribute semantic feature vector; and a score classification result and reward output module usedfor classifying the types with the labels seen by adopting cross entropy loss, and reward output is used for punishing the unseen data without the labels and punishing the prediction result with the highest possibility of the seen types and the unseen types in the data without the labels. According to the invention, the problem of image category label missing can be effectively solved.
Owner:FUZHOU UNIV
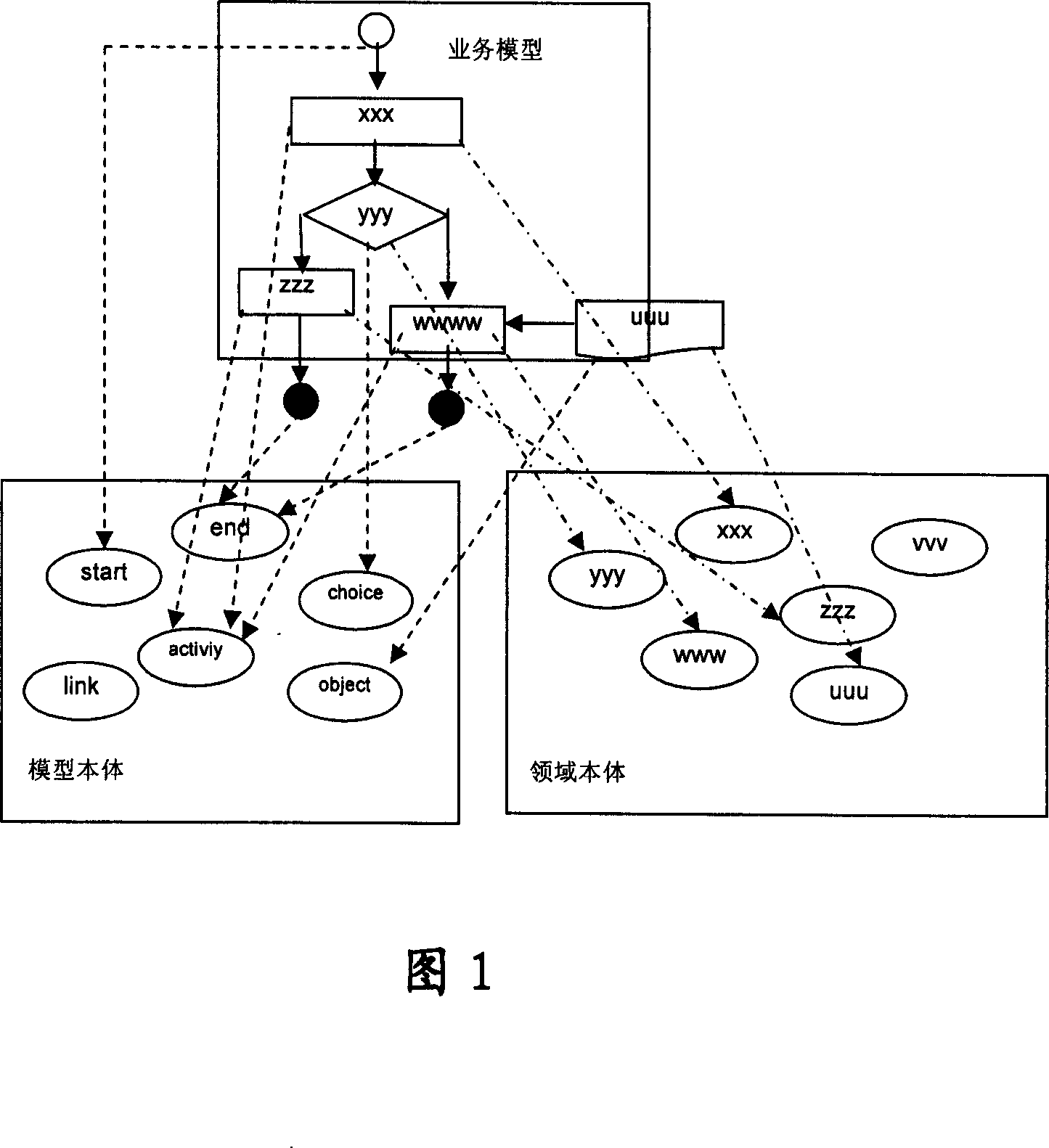
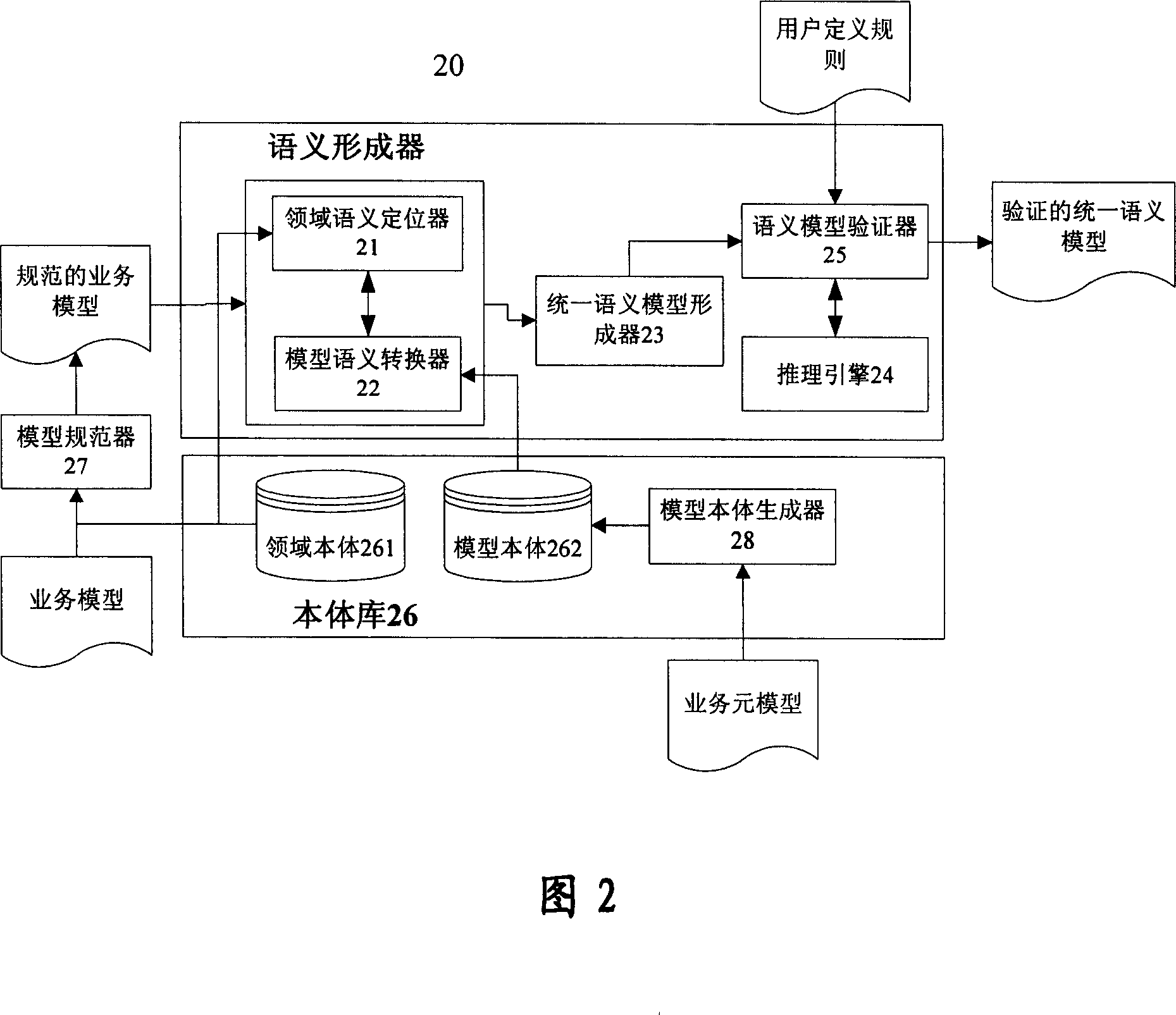
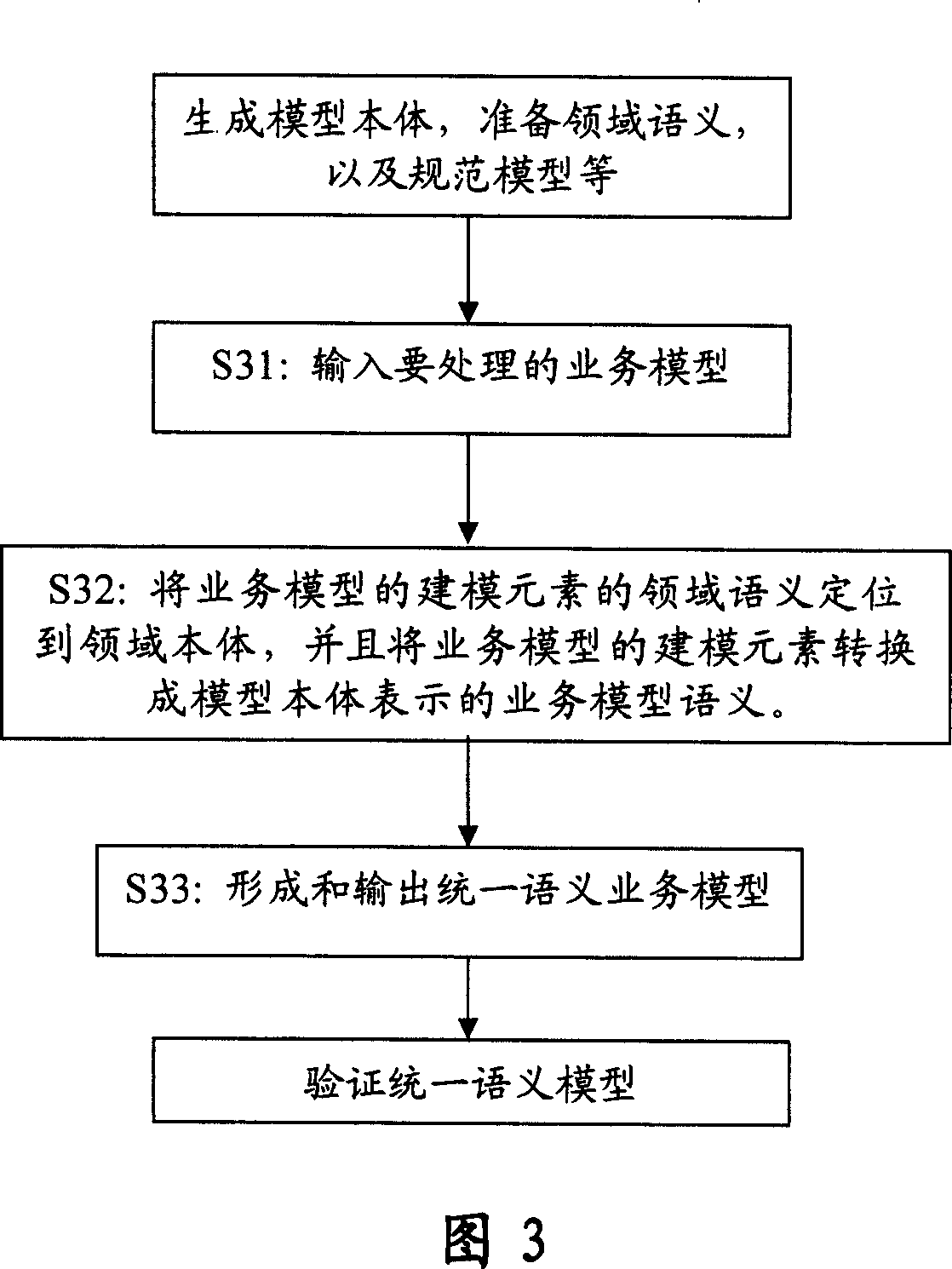
Method and device for integrating model sementics and field sementics in service model
InactiveCN1955991AGreat business valueKnowledge representationSpecific program execution arrangementsService modelDomain model
A method for integrating model semantic and domain semantic in service model includes inputting service model to be realized, positioning domain semantic of modeling element on service module onto domain body and outputting relevant domain model semantic, converting said modeling element of service model to be service model semantic presented by model body, combining said service model semantic with domain mode semantic for outputting a unified semantic model.
Owner:INT BUSINESS MASCH CORP
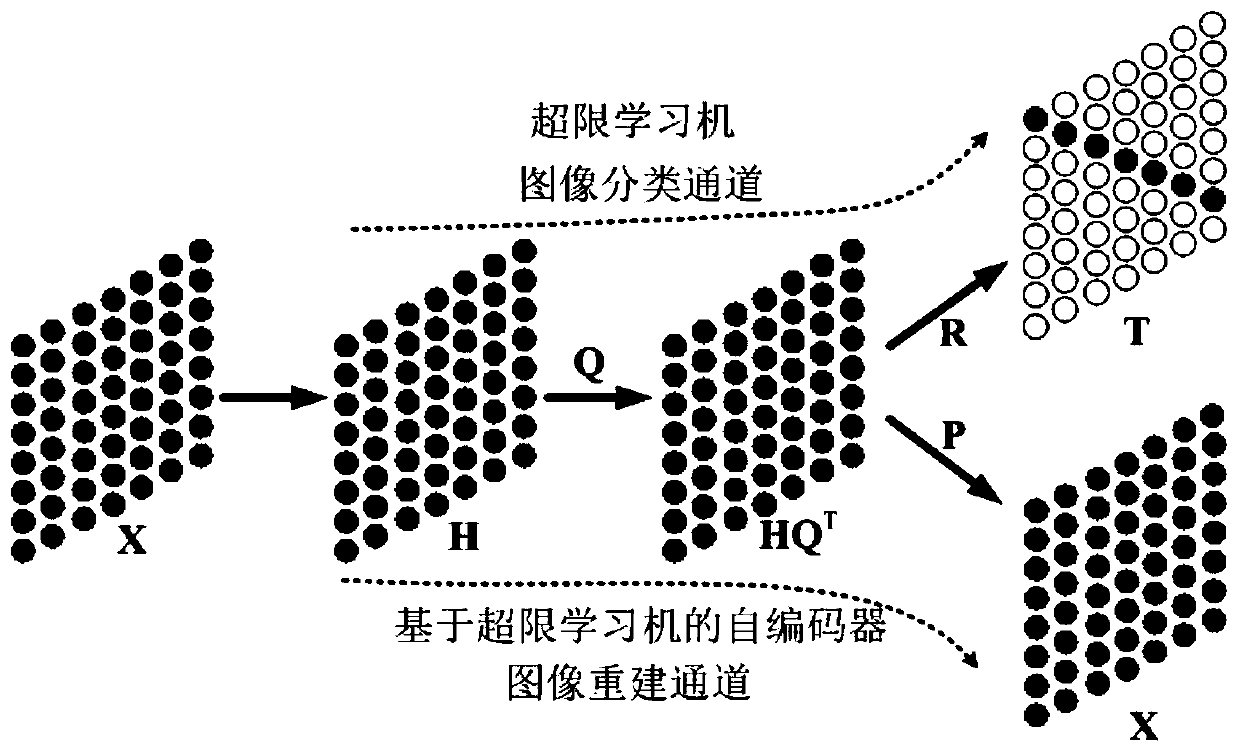
Image classification and reconstruction method based on extreme implicit feature learning model
ActiveCN109934295AImprove classification accuracyReveal potential relationshipsCharacter and pattern recognitionNeural architecturesOriginal dataSemantic translation
The invention discloses an image classification and reconstruction method based on an extreme implicit feature learning model, and the method employs a data reconstruction strategy to carry out the feature learning, and efficiently learns the original perception data and a corresponding high-level semantic conversion relation. In particular, ELM and ELM-AE (an auto-encoder based on ELM) are unified in one learning model, the model has image classification capability and image reconstruction capability, the potential relationship between original image data and advanced semantics can be betterdisclosed, information loss is reduced, image classification precision is improved, and the model has excellent image data reconstruction capability. ELF (Extreme Limited Hidden Feature Learning) inherits advantages of the ELM and ELM-AE, good image classification and image reconstruction effects can be obtained under the condition that the original data information is protected. In addition, an efficient algorithm based on a staggered direction method is used for solving and optimizing the ELF model, and the precision of the ELF model is further improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
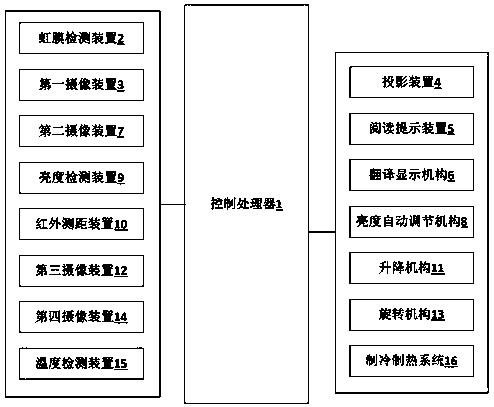
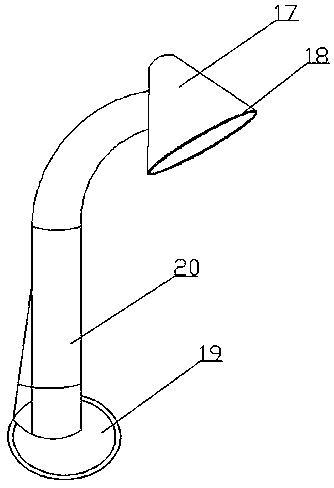
Reading table lamp based on artificial intelligence
InactiveCN108826071APrevent the phenomenon that the reading effect is not obviousServe as a reminderElectric circuit arrangementsLighting elementsSemantic translationLight head
The invention relates to a reading table lamp based on artificial intelligence. The reading table lamp comprises a table lamp body and a control processor. The lamp body is disposed on the surface ofa reading desk, and the table lamp body comprises a lamp cap, a table lamp base, a projection device, an automatic brightness adjusting mechanism and a reading prompting device. An annular ring is arranged at the bottom of the lamp cap, and a bulb is disposed in the lamp cap. An iris detecting device is disposed in the annular ring, and the table lamp is internally provided with a memory storage system. A first camera device is disposed in the annular ring, and the reading prompting device is further provided with a timer. The projection device is connected with a translation display mechanism, and the translation display mechanism comprises a pinyin display module, a semantic translation display module and a language translation display module. The projection device is disposed on the surface of the annular ring, and the automatic brightness adjusting mechanism is disposed in the table lamp base. A second camera device is further disposed inside the annular ring, and the table lamp base is further provided with a brightness detecting device.
Owner:TAICANG YUHE NETWORK TECH CO LTD
Method for training zero-sample image classification by using total data
ActiveCN110826639AAvoid missingIncrease lossCharacter and pattern recognitionSample graphFeature vector
The invention relates to a method for training zero-sample image classification by using total data. The method comprises the following steps: S1, dividing the total data into source data and target data; S2, inputting the source data set and the target data set into a visual feature network, and mapping the original image to a visual feature space to obtain an image visual feature vector; S3, mapping the low-dimensional attribute semantics of the original image to a high dimension through a semantic conversion network to obtain a semantic feature vector; S4, completing fusion by using a vision-attribute semantic connection network according to the obtained image visual feature vector and semantic feature vector to obtain a splicing result; and S5, according to the splicing result, generating a score of each type of the original image in the semantic space through the obtained molecular network, and outputting a final prediction result according to the scores. According to the invention, the problem of image category label missing can be effectively solved.
Owner:FUZHOU UNIV
Predicting the quality of automatic translation of an entire document
InactiveUS9606988B2Natural language translationSpecial data processing applicationsSentence pairSemantic translation
A system and method predict the translation quality of a translated input document. The method includes receiving an input document pair composed of a plurality of sentence pairs, each sentence pair including a source sentence in a source language and a machine translation of the source language sentence to a target language sentence. For each of the sentence pairs, a representation of the sentence pair is generated, based on a set of features extracted for the sentence pair. Using a generative model, a representation of the input document pair is generated, based on the sentence pair representations. A translation quality of the translated input document is computed, based on the representation of the input document pair.
Owner:XEROX CORP
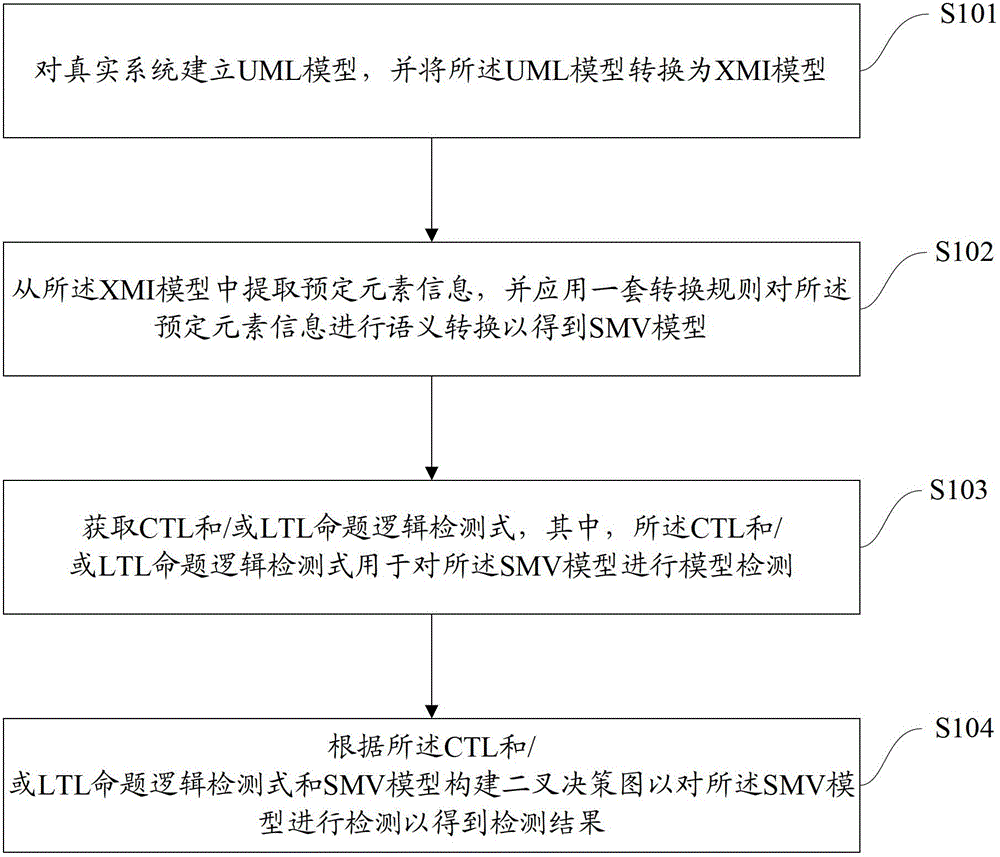
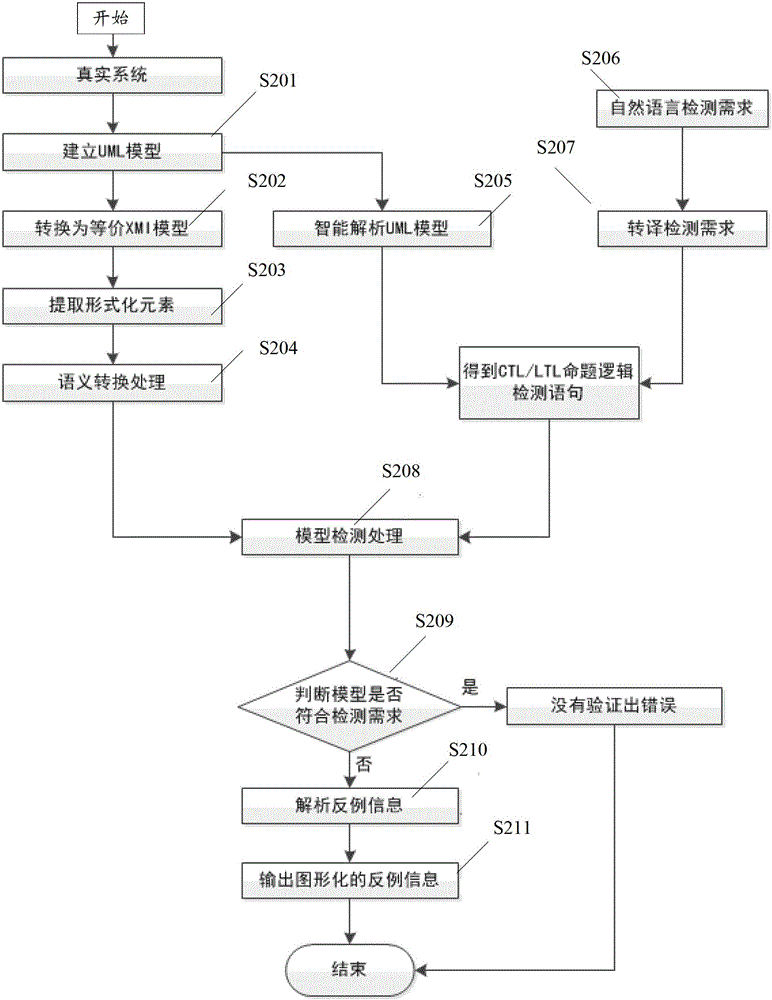
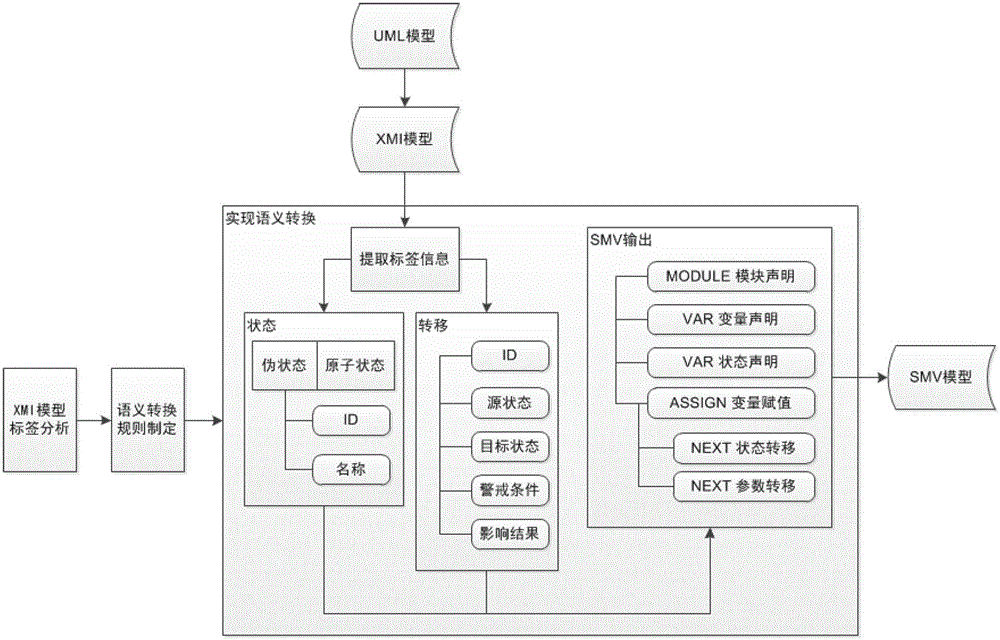
Formalized detection method of intelligent UML (Unified Modeling Language) model and device
ActiveCN102722441AImprove user experienceGood application effectSoftware testing/debuggingSoftware development processBinary decision diagram
The invention provides a formalized detection method of an intelligent UML (Unified Modeling Language) model and a device. The method comprises the steps of: establishing an UML model for a true system and converting the UML model into an XMI (Extensible Markup Language) model; extracting predetermined element information from the XMI model and converting the predetermined element information semantically to obtain an SMV (Symbolic Modeling Verification) model by applying a set of conversion rule; acquiring an CTL (Complementary Transistor Logic) and / or an LTL (Linear Temporal Logic) propositional logic detection formula, wherein the CTL and / or LTL propositional logic detection formula are / is used for detecting the SMV model; and constructing a binary decision diagram according to the CTL and / or LTL propositional logic detection formula and the SMV model to detect the SMV model so as to obtain a detection result. According to the embodiment disclosed by the invention, the formalized detection method has the advantages of high detection accuracy and wide application, and can comprehensively detect the UML model which has higher demand on safety in a software development process.
Owner:TSINGHUA UNIV
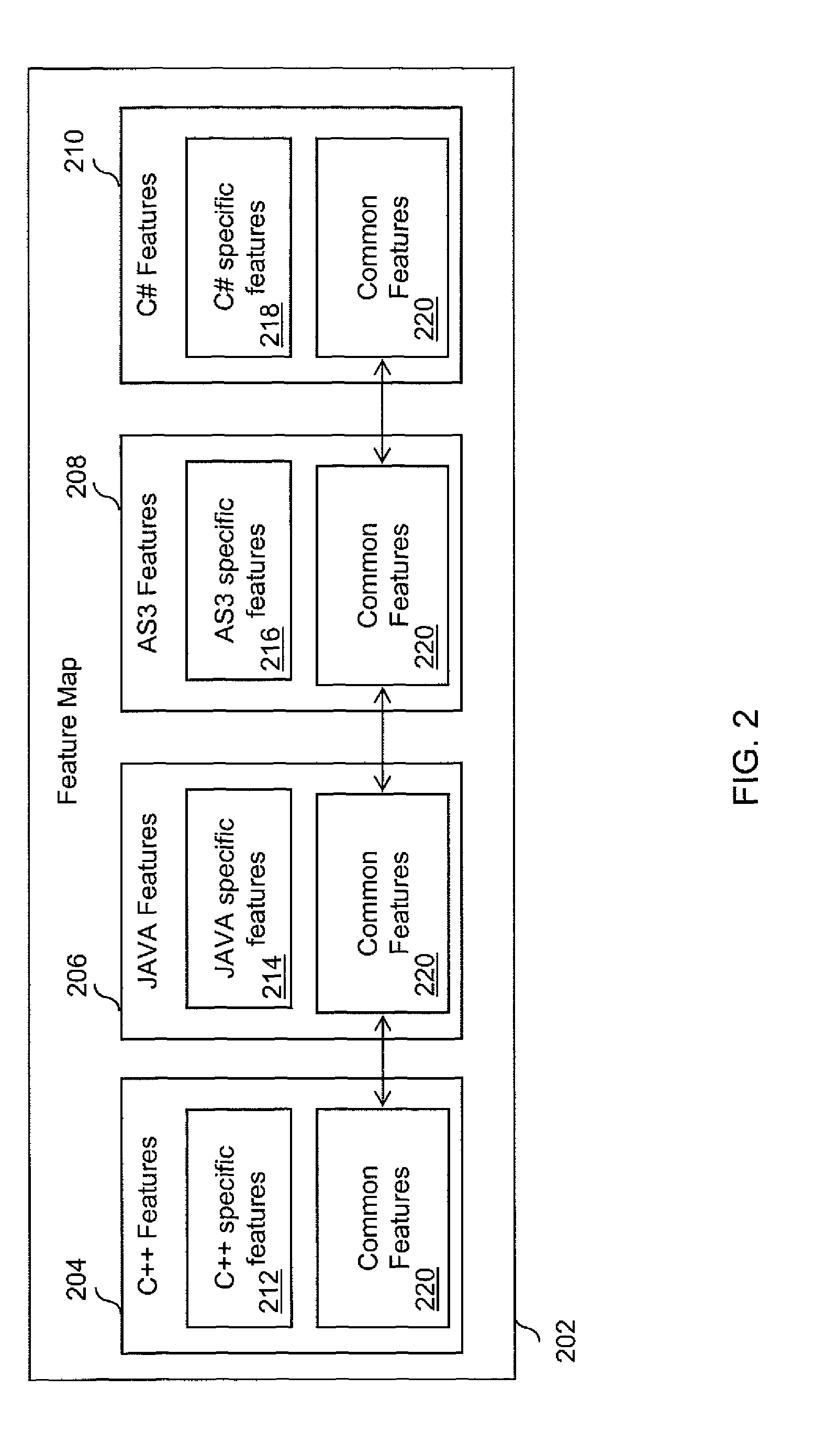
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com